re-babyre
1、下载得到chall.txt,使用file命令查看文件类型,该文件是python文件
 2.这里将chall.txt重命名为chall.pyc
2.这里将chall.txt重命名为chall.pyc使用在线python反编译得到python(https://tool.lu/pyc)
from ctypes import c_uint32
from base64 import b64encode
def enc(rounds: int, v: list, key: list):
magic = 3735928559
l, r = c_uint32(v[0]), c_uint32(v[1])
total = c_uint32(0)
for _ in range(rounds):
l.value -= (r.value << 4) - (r.value >> 6) + (key[(total.value & 3)] << 2) ^ key[(r.value << 3 & 3)]
total.value -= magic
r.value += ((l.value << 5) + (l.value << 4) ^ key[(total.value & 3)] >> 2) + key[(l.value & 3)]
else:
return (
l.value, r.value)
def ints2bytes(v: list) -> bytes:
n = len(v)
res = b''
for i in range(n // 2):
res += int.to_bytes(v[(2 * i)], 4, 'little')
res += int.to_bytes(v[(2 * i + 1)], 4, 'little')
else:
return res
def bytes2ints(cs: bytes) -> list:
new_length = len(cs) + (8 - len(cs) % 8) % 8
barray = cs.ljust(new_length, b'\x00')
i = 0
v = []
while i < new_length:
v0 = int.from_bytes(barray[i:i + 4], 'little')
v1 = int.from_bytes(barray[i + 4:i + 8], 'little')
v.append(v0)
v.append(v1)
i += 8
return v
def encode(msg):
BASE_CHAR = 'ABCDEFGHIJKLMNOPQRST0123456789+/UVWXYZabcdefghijklmnopqrstuvwxyz'
CHARSET = 'ASCII'
b_msg = bytes(msg, CHARSET)
CHAR_PRE_GROUP = 3
zero_cnt = CHAR_PRE_GROUP - len(b_msg) % CHAR_PRE_GROUP
if zero_cnt == CHAR_PRE_GROUP:
zero_cnt = 0
msg += str(chr(0)) * zero_cnt
b_msg = bytes(msg, CHARSET)
encoded = ''
for i in range(0, len(b_msg), 3):
i_msg = [int(i) for i in b_msg[i:i + 3]]
new_msg = [None] * 4
new_msg[0] = i_msg[0] >> 2
new_msg[1] = ((i_msg[0] & 3) << 6 | i_msg[1] >> 2) >> 2
new_msg[2] = ((i_msg[1] & 15) << 4 | i_msg[2] >> 4) >> 2
new_msg[3] = i_msg[2] & 63
encoded += ''.join([BASE_CHAR[i] for i in new_msg])
else:
return (encoded + '=' * zero_cnt).encode()
if __name__ == '__main__':
flag = input('Input your flag: ').strip().encode()
if len(flag) ^ 42:
exit(0)
u = 0
z = 1
v = flag[:21]
if ((((((-v[0] + v[1] - v[2]) + v[3] + v[4] - v[5] - v[6]) + v[7] - v[8]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + v[18] - v[19]) + v[20] == -321 and ((((((-v[0] + v[1] - v[2]) + v[3] - v[4] - v[5] - v[6] - v[7]) + v[8] + v[9] + v[10] - v[11]) + v[12] - v[13]) + v[14] - v[15] - v[16]) + v[17] - v[18] - v[19]) + v[20] == -265 and ((-2 * v[0] + v[1] + 2 * v[3] + 2 * v[4] - 2 * v[5]) + 2 * v[7] + 2 * v[9] - 2 * v[10] - 2 * v[11] - 2 * v[12] - 2 * v[14] - 2 * v[15] - 2 * v[16]) + 2 * v[18] == -144 and ((-3 * v[0] + 2 * v[1] - v[2]) + 2 * v[4] - 2 * v[5]) + 2 * v[9] - 2 * v[11] - 2 * v[14] - 2 * v[16] - 2 * v[17] - 2 * v[19] == -637 and ((((((-2 * v[0] + v[1] - v[2]) + v[3] + 2 * v[4] - 2 * v[6]) + 2 * v[7] - 2 * v[8]) + 2 * v[9] - 2 * v[11] - 2 * v[12]) + 2 * v[13] - 2 * v[14]) + 2 * v[18] - 2 * v[19]) + 2 * v[20] == -158 and (((-6 * v[0] + 3 * v[1] - v[2]) + 2 * v[4] - 2 * v[6] - 2 * v[12]) + 2 * v[13] - 2 * v[16] - 2 * v[17]) + 2 * v[18] == -449 and (((-6 * v[0] + 3 * v[1] + v[4] - v[5] - 2 * v[6]) + 2 * v[7] - 2 * v[8] - 2 * v[11]) + 2 * v[13] - 2 * v[14] - 2 * v[15] - 2 * v[17]) + 2 * v[20] == -778 and ((-6 * v[0] + 3 * v[1] + v[4] - v[5] - 2 * v[6]) + 2 * v[9] - 2 * v[12] - 2 * v[14] - 2 * v[17]) + 2 * v[18] - 2 * v[19] == -760 and (((-13 * v[0] + 5 * v[1] + 2 * v[2] - v[3]) + v[4] - v[5] - 3 * v[6]) + 2 * v[9] - 2 * v[11] - 2 * v[12]) + 2 * v[13] - 2 * v[14] - 2 * v[17] == -1270 and (((((-22 * v[0] + 8 * v[1] + 3 * v[2] - 4 * v[3]) + 2 * v[4] + v[5] - 2 * v[6] - v[7]) + v[8] - v[9] - v[10]) + v[11] + v[12] - v[13] - v[14] - v[15]) + v[16] + v[17] - v[18]) + v[19] - v[20] == -1494 and ((((-2 * v[0] + v[1] - v[2]) + v[3] + v[4] - v[5] - v[6]) + v[7] - v[8]) + v[9] - 2 * v[10] - 2 * v[11]) + 2 * v[13] - 2 * v[14] - 2 * v[15] == -528 and ((((-21 * v[0] + 8 * v[1] + 4 * v[2] - 2 * v[3]) + 2 * v[4] - v[5] - 4 * v[6] - v[7]) + v[9] - v[10] - 2 * v[11] - 2 * v[12] - 2 * v[14] - 2 * v[16]) + 2 * v[18] - 2 * v[19]) + 2 * v[20] == -1853 and ((((-14 * v[0] + 5 * v[1] - v[3]) + 3 * v[4] - 2 * v[6]) + v[7] - v[8]) + v[9] - 2 * v[10] - v[11] - 2 * v[12]) + 2 * v[20] == -913 and ((((-20 * v[0] + 7 * v[1] + 3 * v[2] - 2 * v[3]) + 2 * v[4] - 3 * v[6]) + v[9] - 2 * v[10] - v[11] - v[12]) + 2 * v[13] - 2 * v[19]) + 2 * v[20] == -1310 and (((-11 * v[0] + 4 * v[1] + v[2] - v[3]) + v[4] - v[5] - 2 * v[6] - v[8]) + v[9] - 2 * v[10] - v[11] - v[12]) + v[13] - 2 * v[14] - 2 * v[15] - 2 * v[16] - 2 * v[19] == -1576 and (((((-21 * v[0] + 8 * v[1] + 3 * v[2] - 3 * v[3]) + v[4] - v[5] - 4 * v[6]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - 2 * v[17]) + 2 * v[18] - 2 * v[19]) + 2 * v[20] == -1830 and ((((-27 * v[0] + 9 * v[1] + 5 * v[2] - 4 * v[3]) + v[4] - v[5] - 4 * v[6] - v[7]) + v[9] - 3 * v[10] - v[11] - v[12]) + v[13] - 2 * v[14] - v[15] - 2 * v[17]) + 2 * v[18] - 2 * v[19] == -2692 and (((-17 * v[0] + 7 * v[1] - 2 * v[3]) + 3 * v[4] - 2 * v[6] - v[8]) + v[9] - 2 * v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - 2 * v[19] == -1519 and ((((-25 * v[0] + 9 * v[1] + 3 * v[2] - 3 * v[3]) + 3 * v[4] - 4 * v[6] - v[7]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + 2 * v[18] == -1937 and (((((-24 * v[0] + 9 * v[1] + 4 * v[2] - 3 * v[3]) + v[4] - v[5] - 4 * v[6]) + v[9] - 2 * v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + v[18] - 2 * v[19]) + 2 * v[20] == -2078 and (((((-8 * v[0] + 3 * v[1] + v[2] + 2 * v[4] - v[5] - 2 * v[6]) + v[7] - v[8]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + v[18] - v[19]) + 2 * v[20] == -654:
u = 1
vs = bytes2ints(flag[21:-5])
keys = bytes2ints(v[:16])
res = []
for i in range(len(vs) // 2):
pt = vs[2 * i:2 * i + 2]
v0, v1 = enc(len(flag), pt, keys)
res.extend([v0, v1])
else:
res = list(ints2bytes(res))
res.extend(list(encode(flag[-5:].decode())))
check = [86, 2, 249, 121, 139, 89, 236, 10, 233, 193, 135, 89, 22, 235, 221, 127, 52, 113, 82, 87, 79, 72, 111, 65, 61]
for r, c in zip(res, check):
if r ^ c:
z = 0
break
else:
if z & u:
print("Congratulations! You've got the flag!")
else:
print('Nope, try again!')
3、分析步骤,flag分成了三段:
第一段可以用z3求解
第二段为魔改tea,key为第一段前16字节
第三段为换标base64
4、分段求解即可
from ctypes import c_uint32
import base64
'''
from z3 import *
v = [ Int(f'v[{i}]') for i in range(21)]
s = Solver()
s.add(((((((-v[0] + v[1] - v[2]) + v[3] + v[4] - v[5] - v[6]) + v[7] - v[8]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + v[18] - v[19]) + v[20] == -321 )
s.add(((((((-v[0] + v[1] - v[2]) + v[3] - v[4] - v[5] - v[6] - v[7]) + v[8] + v[9] + v[10] - v[11]) + v[12] - v[13]) + v[14] - v[15] - v[16]) + v[17] - v[18] - v[19]) + v[20] == -265 )
s.add(((-2 * v[0] + v[1] + 2 * v[3] + 2 * v[4] - 2 * v[5]) + 2 * v[7] + 2 * v[9] - 2 * v[10] - 2 * v[11] - 2 * v[12] - 2 * v[14] - 2 * v[15] - 2 * v[16]) + 2 * v[18] == -144 )
s.add(((-3 * v[0] + 2 * v[1] - v[2]) + 2 * v[4] - 2 * v[5]) + 2 * v[9] - 2 * v[11] - 2 * v[14] - 2 * v[16] - 2 * v[17] - 2 * v[19] == -637 )
s.add(((((((-2 * v[0] + v[1] - v[2]) + v[3] + 2 * v[4] - 2 * v[6]) + 2 * v[7] - 2 * v[8]) + 2 * v[9] - 2 * v[11] - 2 * v[12]) + 2 * v[13] - 2 * v[14]) + 2 * v[18] - 2 * v[19]) + 2 * v[20] == -158 )
s.add((((-6 * v[0] + 3 * v[1] - v[2]) + 2 * v[4] - 2 * v[6] - 2 * v[12]) + 2 * v[13] - 2 * v[16] - 2 * v[17]) + 2 * v[18] == -449 )
s.add((((-6 * v[0] + 3 * v[1] + v[4] - v[5] - 2 * v[6]) + 2 * v[7] - 2 * v[8] - 2 * v[11]) + 2 * v[13] - 2 * v[14] - 2 * v[15] - 2 * v[17]) + 2 * v[20] == -778 )
s.add(((-6 * v[0] + 3 * v[1] + v[4] - v[5] - 2 * v[6]) + 2 * v[9] - 2 * v[12] - 2 * v[14] - 2 * v[17]) + 2 * v[18] - 2 * v[19] == -760 )
s.add((((-13 * v[0] + 5 * v[1] + 2 * v[2] - v[3]) + v[4] - v[5] - 3 * v[6]) + 2 * v[9] - 2 * v[11] - 2 * v[12]) + 2 * v[13] - 2 * v[14] - 2 * v[17] == -1270 )
s.add((((((-22 * v[0] + 8 * v[1] + 3 * v[2] - 4 * v[3]) + 2 * v[4] + v[5] - 2 * v[6] - v[7]) + v[8] - v[9] - v[10]) + v[11] + v[12] - v[13] - v[14] - v[15]) + v[16] + v[17] - v[18]) + v[19] - v[20] == -1494 )
s.add(((((-2 * v[0] + v[1] - v[2]) + v[3] + v[4] - v[5] - v[6]) + v[7] - v[8]) + v[9] - 2 * v[10] - 2 * v[11]) + 2 * v[13] - 2 * v[14] - 2 * v[15] == -528 )
s.add(((((-21 * v[0] + 8 * v[1] + 4 * v[2] - 2 * v[3]) + 2 * v[4] - v[5] - 4 * v[6] - v[7]) + v[9] - v[10] - 2 * v[11] - 2 * v[12] - 2 * v[14] - 2 * v[16]) + 2 * v[18] - 2 * v[19]) + 2 * v[20] == -1853 )
s.add(((((-14 * v[0] + 5 * v[1] - v[3]) + 3 * v[4] - 2 * v[6]) + v[7] - v[8]) + v[9] - 2 * v[10] - v[11] - 2 * v[12]) + 2 * v[20] == -913 )
s.add(((((-20 * v[0] + 7 * v[1] + 3 * v[2] - 2 * v[3]) + 2 * v[4] - 3 * v[6]) + v[9] - 2 * v[10] - v[11] - v[12]) + 2 * v[13] - 2 * v[19]) + 2 * v[20] == -1310 )
s.add((((-11 * v[0] + 4 * v[1] + v[2] - v[3]) + v[4] - v[5] - 2 * v[6] - v[8]) + v[9] - 2 * v[10] - v[11] - v[12]) + v[13] - 2 * v[14] - 2 * v[15] - 2 * v[16] - 2 * v[19] == -1576 )
s.add((((((-21 * v[0] + 8 * v[1] + 3 * v[2] - 3 * v[3]) + v[4] - v[5] - 4 * v[6]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - 2 * v[17]) + 2 * v[18] - 2 * v[19]) + 2 * v[20] == -1830 )
s.add(((((-27 * v[0] + 9 * v[1] + 5 * v[2] - 4 * v[3]) + v[4] - v[5] - 4 * v[6] - v[7]) + v[9] - 3 * v[10] - v[11] - v[12]) + v[13] - 2 * v[14] - v[15] - 2 * v[17]) + 2 * v[18] - 2 * v[19] == -2692 )
s.add((((-17 * v[0] + 7 * v[1] - 2 * v[3]) + 3 * v[4] - 2 * v[6] - v[8]) + v[9] - 2 * v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - 2 * v[19] == -1519 )
s.add(((((-25 * v[0] + 9 * v[1] + 3 * v[2] - 3 * v[3]) + 3 * v[4] - 4 * v[6] - v[7]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + 2 * v[18] == -1937 )
s.add((((((-24 * v[0] + 9 * v[1] + 4 * v[2] - 3 * v[3]) + v[4] - v[5] - 4 * v[6]) + v[9] - 2 * v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + v[18] - 2 * v[19]) + 2 * v[20] == -2078 )
s.add((((((-8 * v[0] + 3 * v[1] + v[2] + 2 * v[4] - v[5] - 2 * v[6]) + v[7] - v[8]) + v[9] - v[10] - v[11] - v[12]) + v[13] - v[14] - v[15] - v[16] - v[17]) + v[18] - v[19]) + 2 * v[20] == -654)
print(s.check())
m=s.model()
print(m)
'''
v=[0]*21
v[6] = 99
v[16] = 49
v[3] = 103
v[0] = 102
v[13] = 45
v[5] = 99
v[12] = 48
v[4] = 123
v[10] = 48
v[1] = 108
v[7] = 102
v[8] = 101
v[2] = 97
v[15] = 54
v[11] = 54
v[9] = 52
v[18] = 45
v[20] = 50
v[14] = 97
v[19] = 52
v[17] = 49
v=bytes(v)
print(v)
flag1=v
def ints2bytes(v = None):
n = len(v)
res = b''
for i in range(n // 2):
res += int.to_bytes(v[2 * i], 4, 'little')
res += int.to_bytes(v[2 * i + 1], 4, 'little')
return res
def bytes2ints(cs = None):
new_length = len(cs) + (8 - len(cs) % 8) % 8
barray = cs.ljust(new_length, b'\x00')
i = 0
v = []
while i < new_length:
v0 = int.from_bytes(barray[i:i + 4], 'little')
v1 = int.from_bytes(barray[i + 4:i + 8], 'little')
v.append(v0)
v.append(v1)
i += 8
continue
return v
keys = bytes2ints(v[:16])
#print(keys)
c = [86,2,249,121,139,89,236,10,233,193,135,89,22,235,221,127,52,113,82,87,79,72,111,65,61]
flag3=bytes(c[-9:])
print(flag3)
c = c[:-9]
#print(c)
c = bytes2ints(bytes(c))
#print(c)
def enc(v = None, key = None):
magic = 0xDEADBEEF
l = c_uint32(v[0])
r = c_uint32(v[1])
total = c_uint32(0)
for _ in range(42):
l.value -= ((r.value << 4) - (r.value >> 6)) + (key[total.value & 3] << 2) ^ key[r.value << 3 & 3]
total.value -= magic
r.value += ((l.value << 5) + (l.value << 4) ^ key[total.value & 3] >> 2) + key[l.value & 3]
return (l.value, r.value)
def dec(v = None, key = None):
magic = 0xDEADBEEF
l = c_uint32(v[0])
r = c_uint32(v[1])
total = c_uint32(0)
for _ in range(42):
total.value -= magic
for _ in range(42):
r.value -= ((l.value << 5) + (l.value << 4) ^ key[total.value & 3] >> 2) + key[l.value & 3]
total.value += magic
l.value += ((r.value << 4) - (r.value >> 6)) + (key[total.value & 3] << 2) ^ key[r.value << 3 & 3]
return (l.value, r.value)
flag2=[]
for i in range(2):
v0,v1 = dec(c[2 * i:2 * i + 2],keys)
flag2.extend([v0, v1])
flag2=ints2bytes(flag2)
print(flag2)
a = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' #标准表
b = 'ABCDEFGHIJKLMNOPQRST0123456789+/UVWXYZabcdefghijklmnopqrstuvwxyz' #新表
flag3=flag3.decode()
trantab = flag3.maketrans(b, a)
flag3 = base64.b64decode(flag3.translate(trantab))
print(flag3)
flag=flag1 + flag2+ flag3
print(flag)
5、运行得到flag
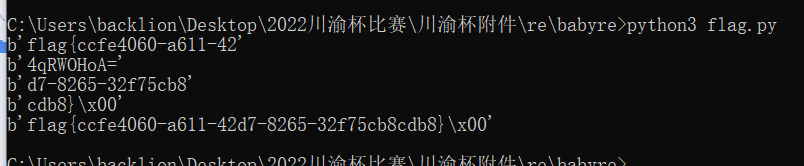
flag{ccfe4060-a611-42d7-8265-32f75cb8cdb8}
MISC-timu
观察一下发现是sql盲注流量,成功时长度为437,SQL注入流量分析
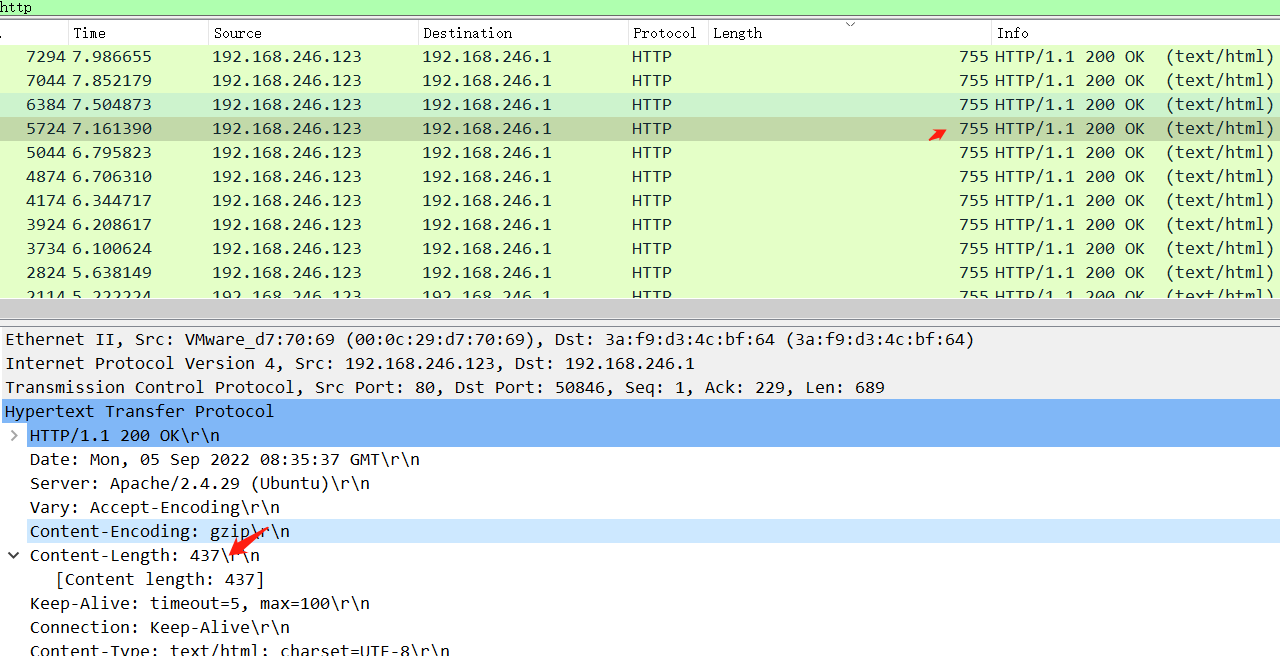
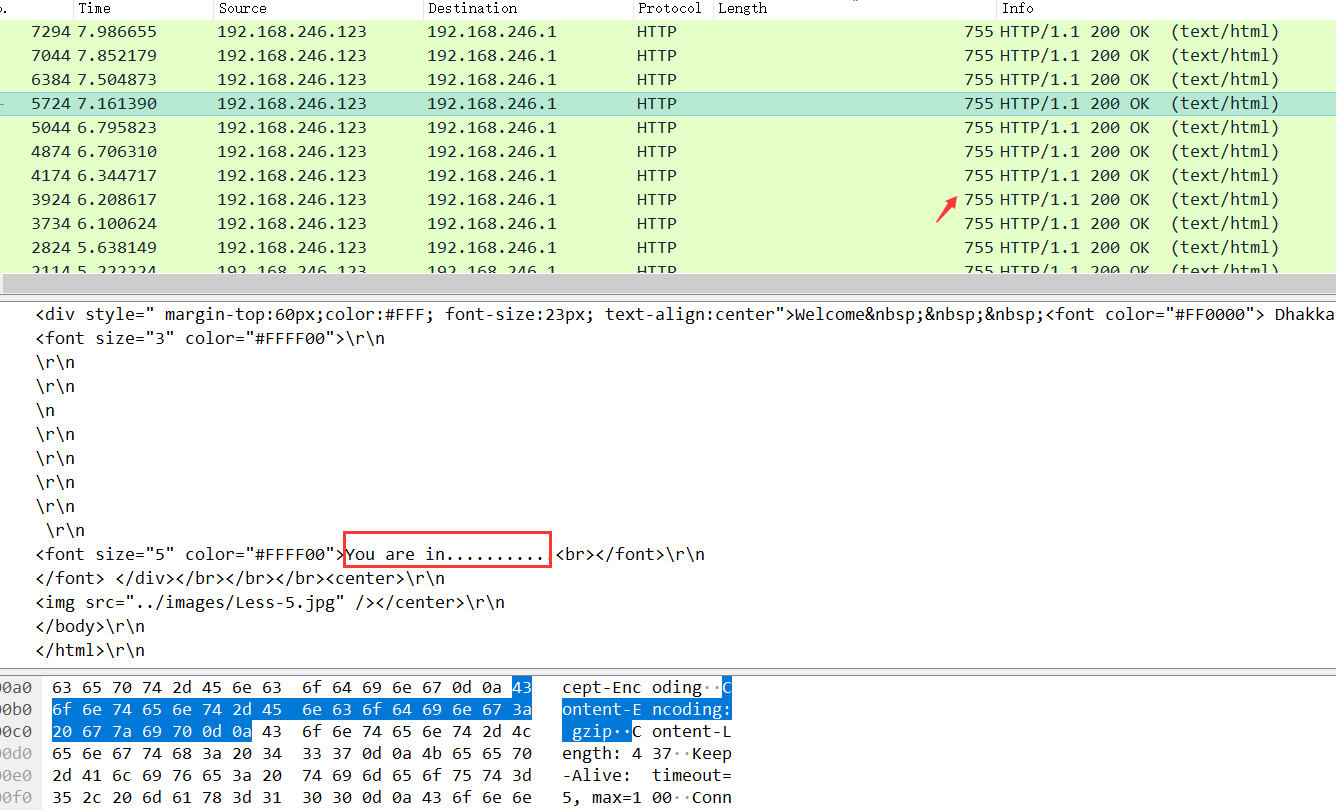
http.content_length == 437筛选一下导出文本
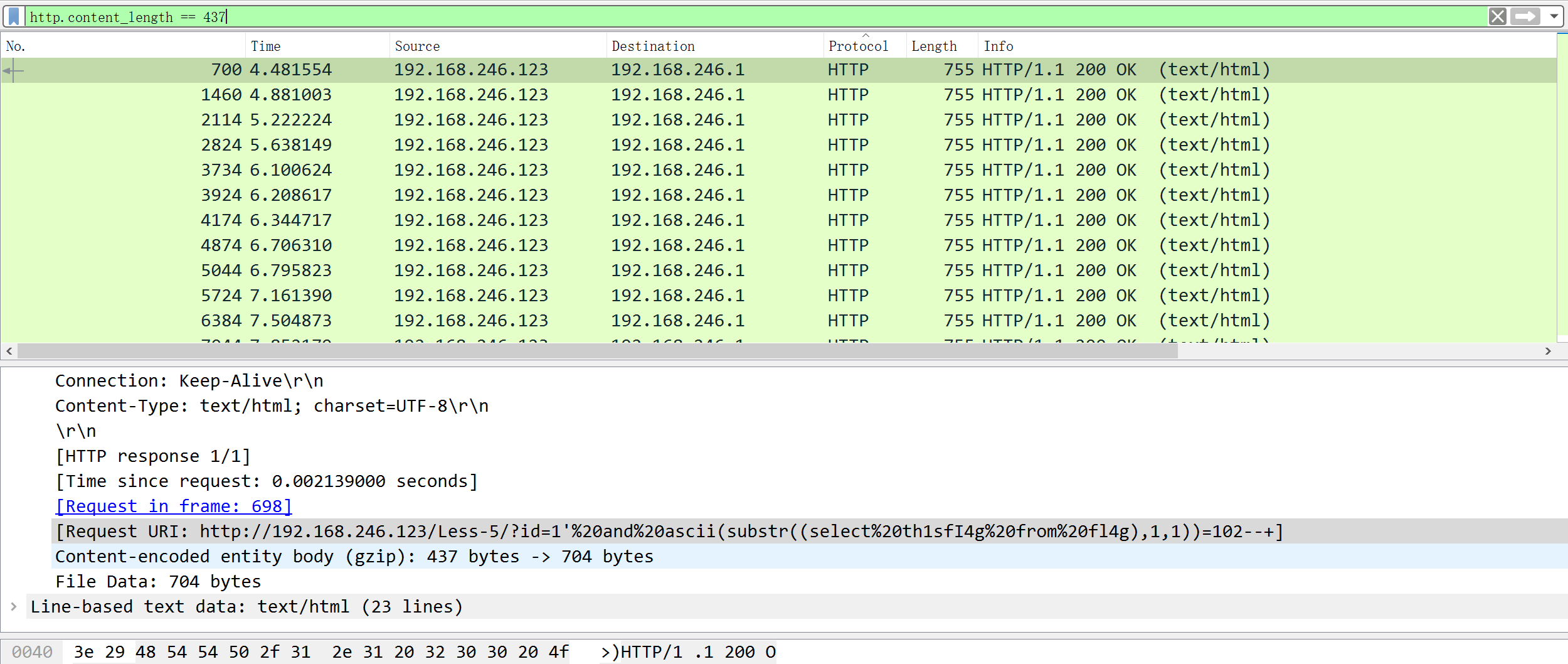
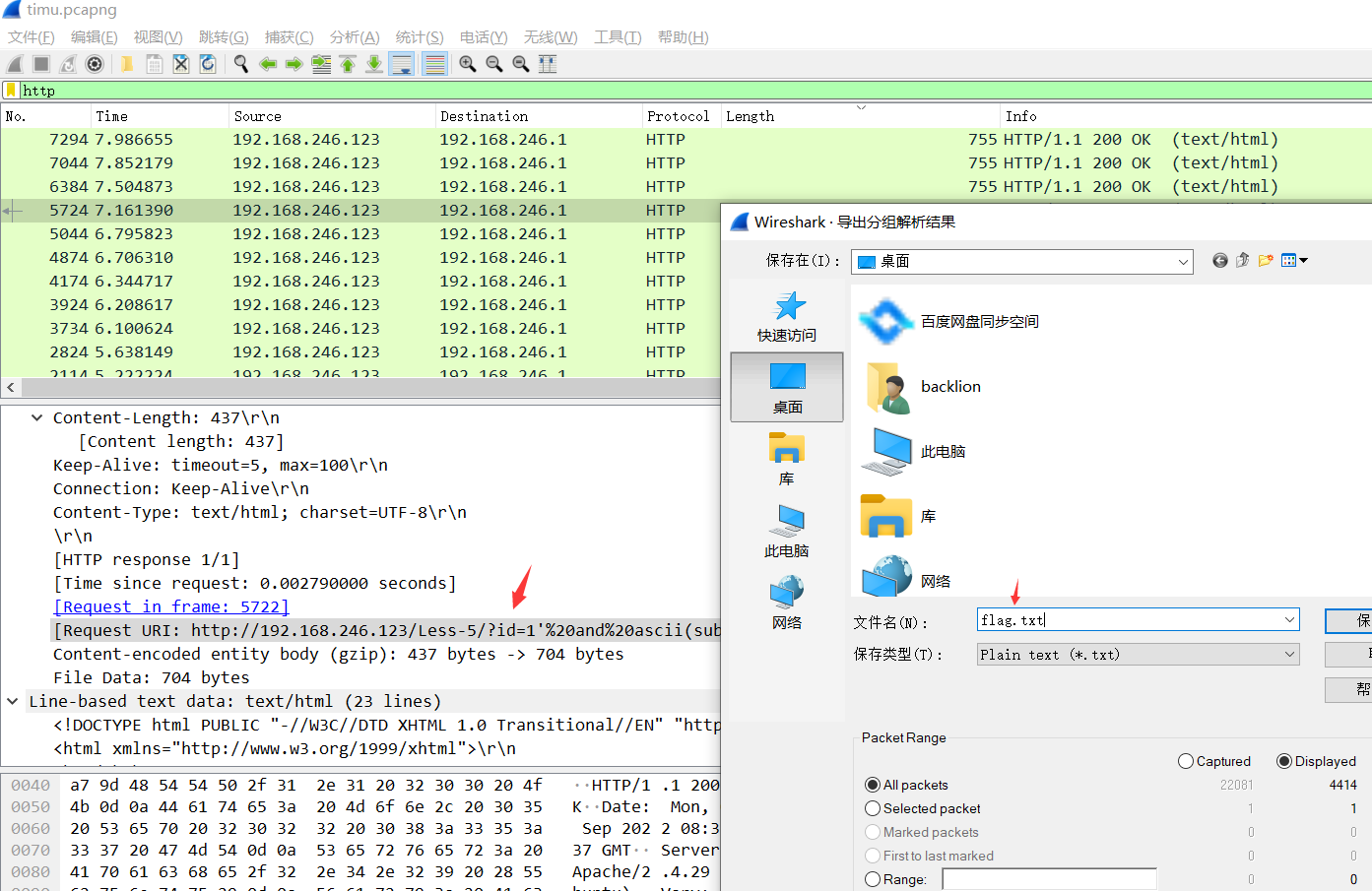
写个脚本提取一下flag
import re
number = []
with open("flag.txt","r",encoding="utf-8") as f:
for i in f.readlines():
flag_number = re.search('\)\)=(.+?)--',i)
if flag_number:
print(chr(int(flag_number.group(1)[::])),end='')
MISC-babymisc
拿到手两个视频,发现key.mp4损坏
使用digital Video repair对MP4进行修复
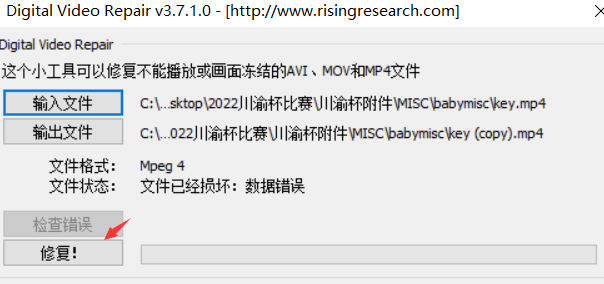
照着help.mp4修改文件头之后打开成功,得到密码
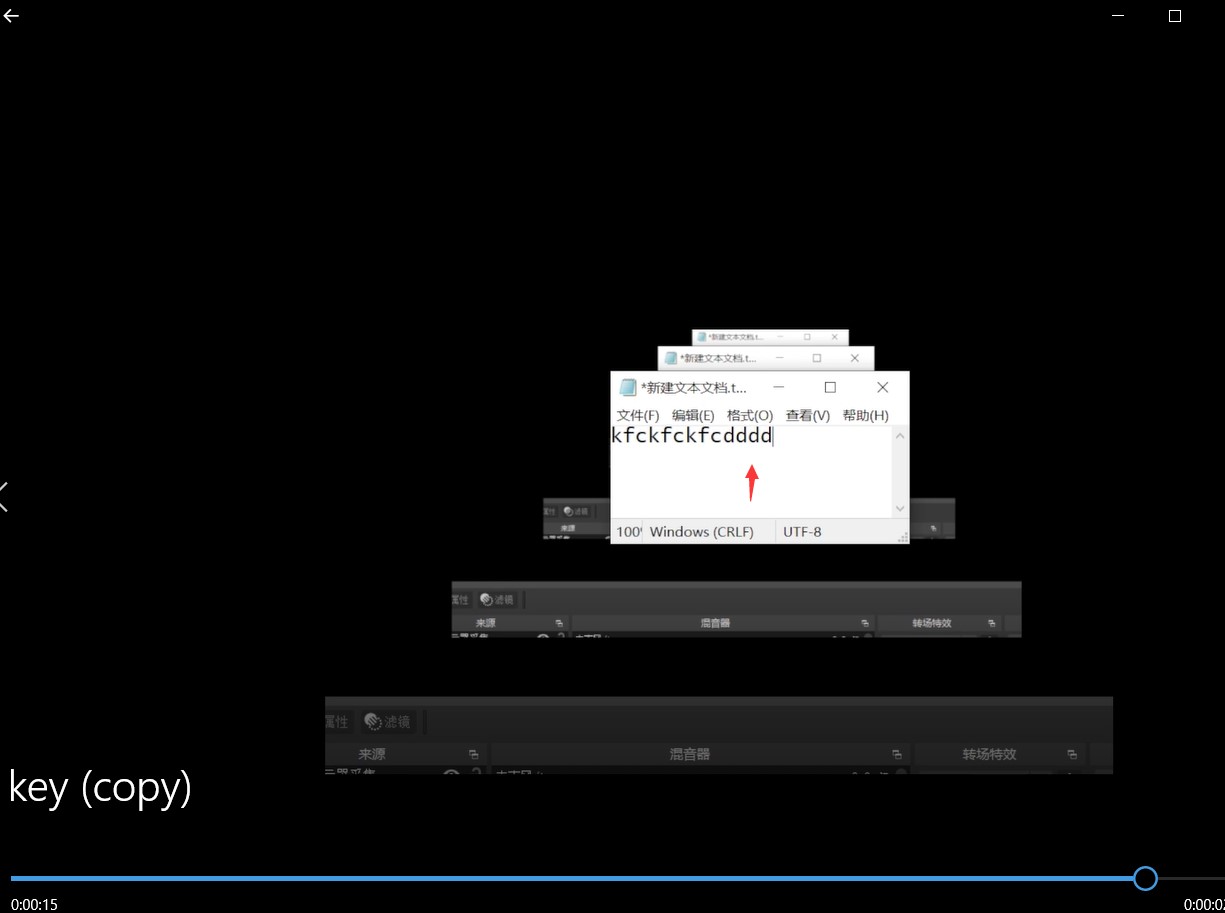 得到CODE压缩包密码:kfckfckfcdddd
得到CODE压缩包密码:kfckfckfcdddd
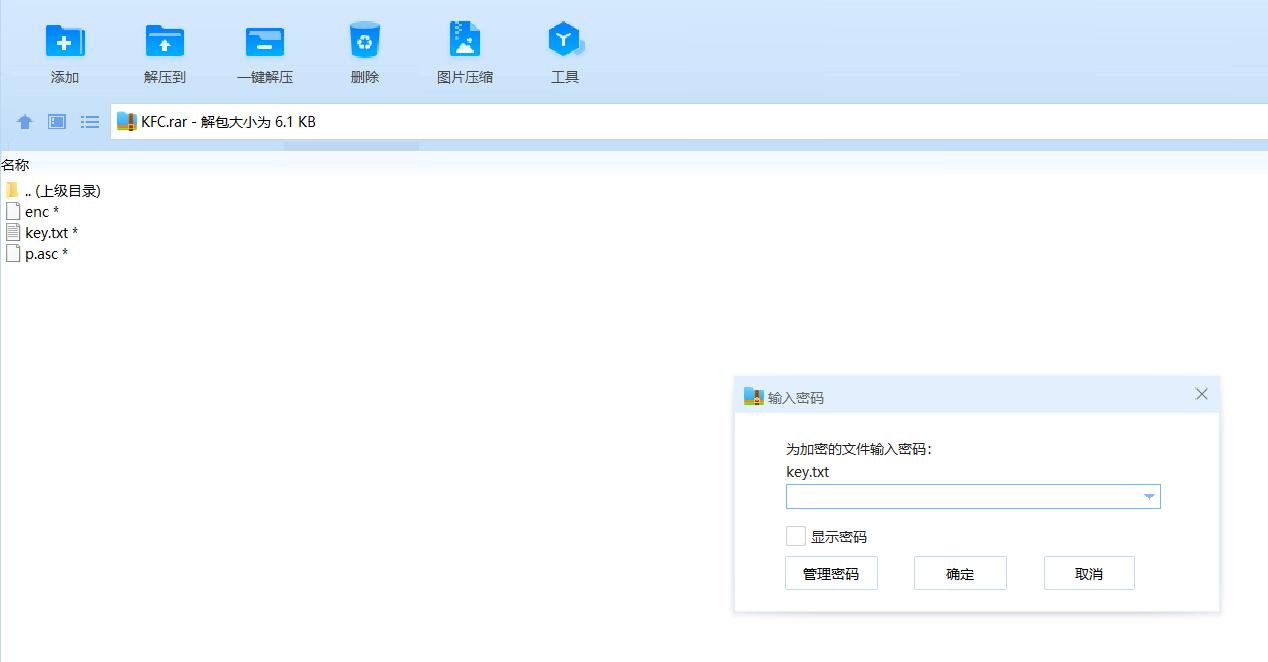
另外三个文本根据文件名的提示依次用8421BCD编码,余3码和5121BCD编码对二进制进行解码,再将得到的三串数字加起来即可得到KFC.zip的密码
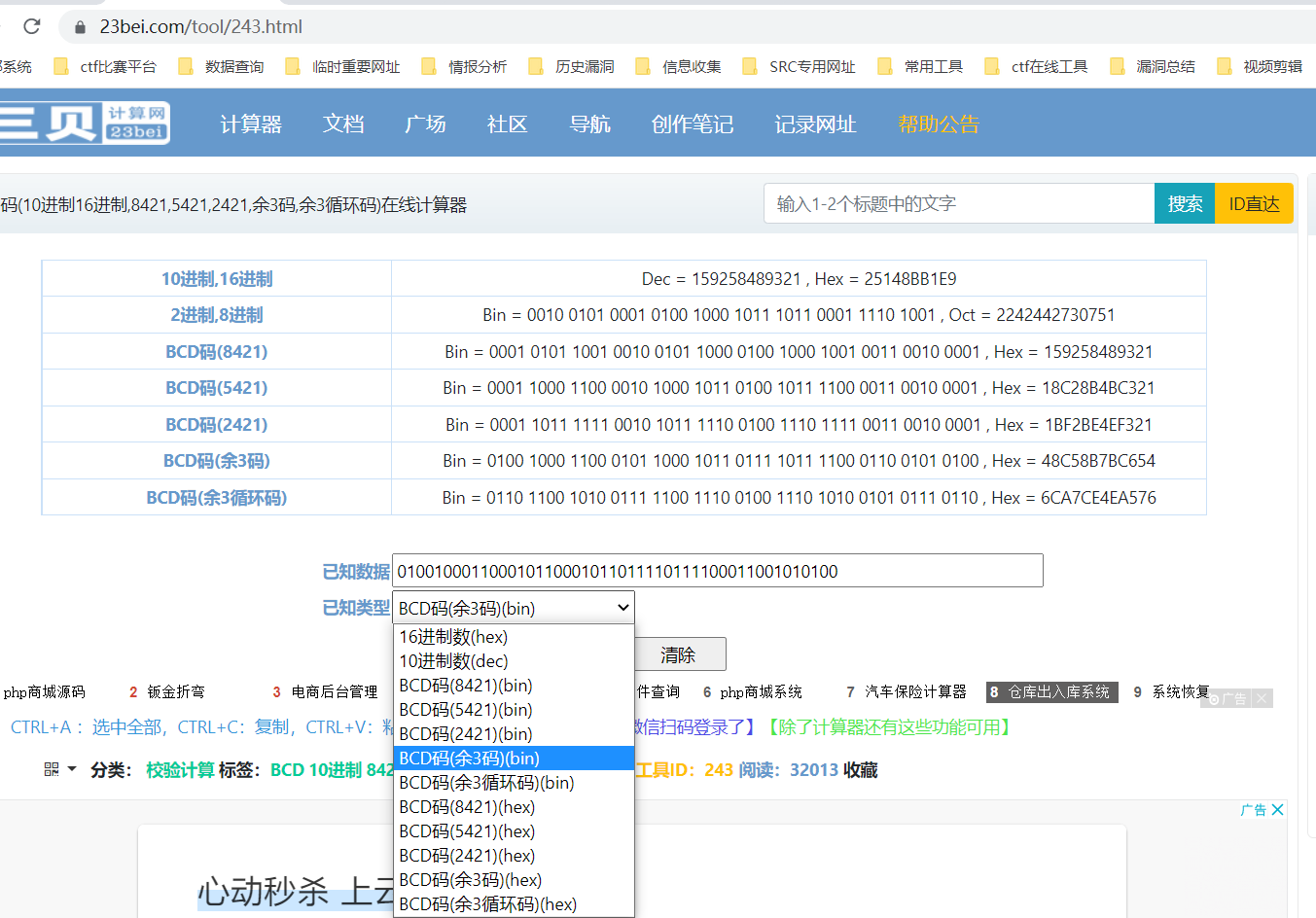
8421:9520131412399
余3: 159258489321
5121:147258
解压密码:9679390048978
又得到了三个文件,根据内容了解是gpg加密。
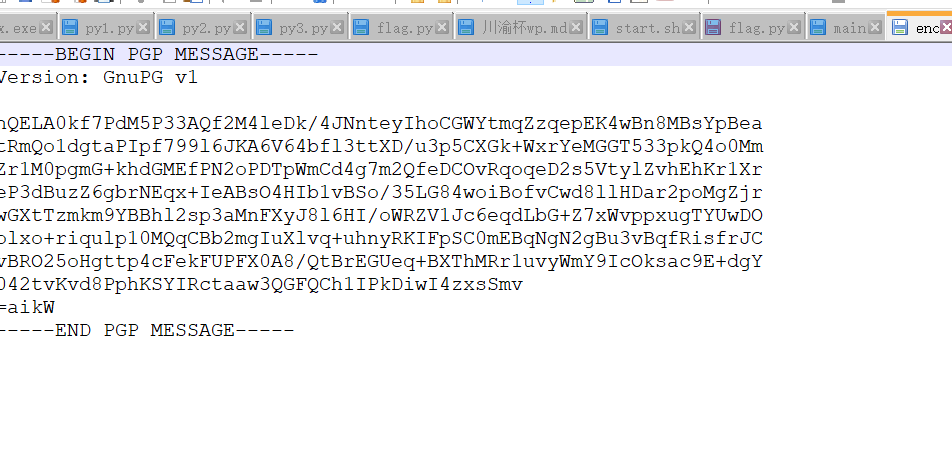
key.txt里的内容
jcI4=S$;@oRcTT_jfYEB]Y3Eh]]Y`Zka7.ePD8:aRHT1"jeSg:J?S(;UunS-k^]VqZ%h>RK]TD<ja`NVJ?S'qKBK5Bk,3jqLof^.YiW+%k*:Y_R'5VJU?JYfjM.taR=OFo[H3=;je\^5OGW(bS`[P<k*V1jOc\_2RHVD_kIeLiWJ9N2U?S,VkF81+^TlpQM<VUaje\^9JZe4OVW>IEkbtrQT;CV_K]nbajM.t`K>$?[K]]qJk+]9HWOCr>YNV=Dk^^,'V5!(AYiV^UkeF"VPD84VJ,
base85解密之后可以得到佛曰加密的文本
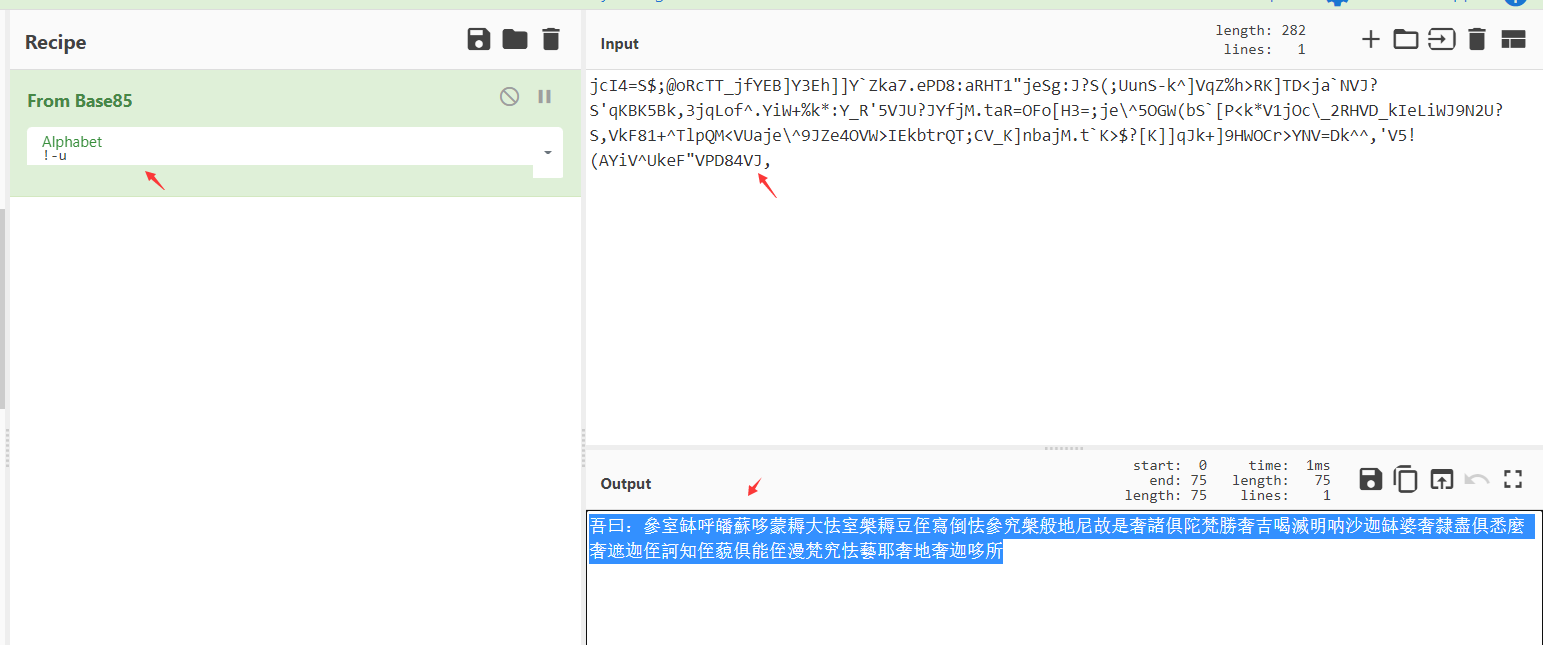
把开头的吾换成佛之后即可成功解密,得到gpg密码
https://www.keyfc.net/bbs/tools/tudoucode.aspx
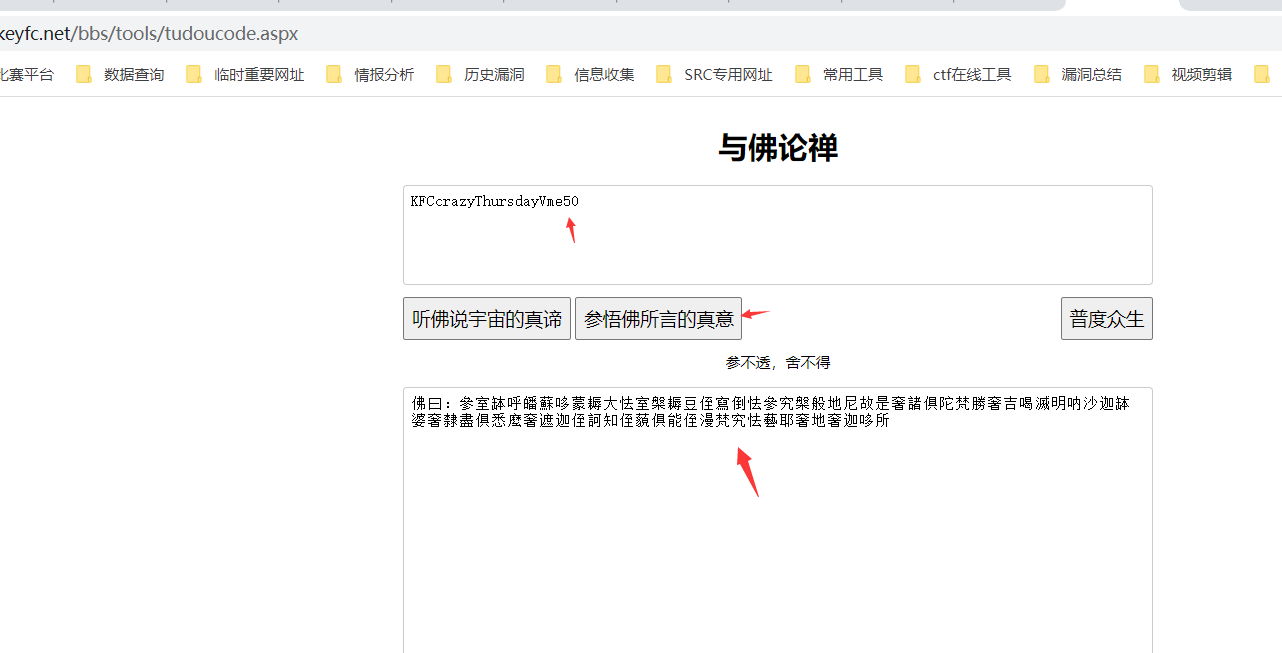
得到gpg密码:KFCcrazyThursdayVme50
然后就是使用gnupg导入私钥,这里输入密码:KFCcrazyThursdayVme50
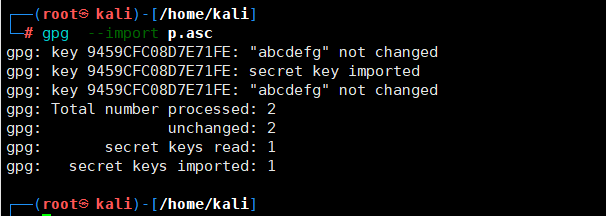
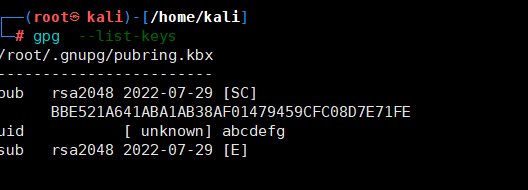
使用gpg --decrypt enc ,并输入密码,j解码得到flag
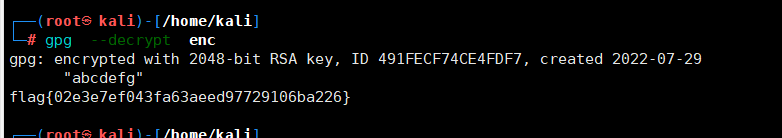
crypto-ezRSA
共模不互素RSA解码脚本:
from gmpy2 import gcdext, iroot
from Crypto.Util.number import long_to_bytes
n=15334568944937927007999900484465008933318606732373890322662758402635604904264667848527624432918429375075528808825616270959632486002311971836554591848781563095705366553616002512404398788966973097823043515475930194538283976927496112772470447937619132674710993584070843393450092524523160279299624451370719909878959576969398084280115463732579954724508652349756110176703496308636810989451987779509636118628086540986338888325501247197248272357069233416661506310524030484892275300358493956190791539925164498005723797931221417357134562381130881466267058989667933251564895613135627072396134981492993661899429352449683777587209
e1=27
c1=12986025840528664605029703071663558675501785717478309954653498440612589963048159389429665580606645713091596074128667194086739183824746224776044505827397154734845975260817293507509629880984219447666390126778735042575927584431041809412129358169629481686396038656480335466512102391890656372814903856027069054914435182728702353752096261176489806655455180097921073991840434590847811340528129253635512407064432360667518609177665325443979726996323560146227981931306518381574311791478479870050796181080300960066337033348776336649326992736515374354805162513674023608490939211117916740904072712484071608280826638537071430473813
e2=39
c2=6565386561126377566205122052098859256761850660695107175286649909808306124644179105628309902060507618319280856871171458108016540215224251721808589269898666208382953255344110718521884982317209269392886709868323886328303134746004772279271980557082263084385403484745749464251594821997308103907619284485485066324857517197751975558892533102067555683357635646156697977091058441721633786527229804348932128713515500689116444655902831314054143308572380052547505012526648205677796482004437411380302150565229313601140113069775555419804631455611599060297651400855376162690324232629639053723597992360016809065382185021672739721475
g,x,y=gcdext(e1,e2)
m=pow(c1,x,n)*pow(c2,y,n)%n
m=iroot(m,3)[0]
print(long_to_bytes(m))
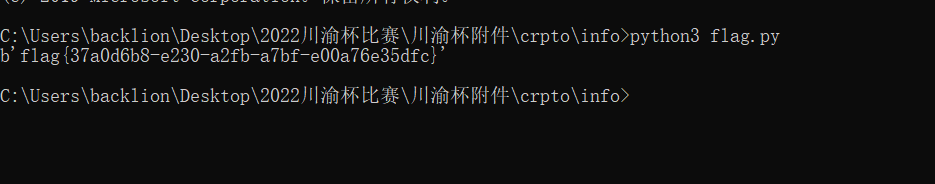
题目附件内容:链接:https://pan.baidu.com/s/1_kP1FmyA5xi3Qy24xW-_rQ 提取码:7ggd
来自为知笔记(Wiz)




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
