This article includes wireless security protocols including WEP, WPA, WPA2 and WPA3. For each of them, we will try to point out their advantages and disadvantages and describe some possible attacks.
WEP protocol
WEP was introduced as part of the original 802.11 standard approved in 1997 and it is probably the most commonly used WiFi security protocol. Its 10-bit or 26-bit hexadecimal digits (40-bit or 104-bit) key is very easy to identify. In 2004, both WEP-40 and WEP-104 were declared deprecated. There are 128-bit (the most common) and 256-bitWEP variants, but as computing power continues to improve, attackers are able to exploit many security vulnerabilities. In short, this protocol can no longer meet security needs.
It uses an RC4 password to ensure privacy and uses a CRC-32 checksum to ensure the integrity of the transmitted data. First, a key k is shared between network users (the protocol does not specify how to share) To send a message M, the integrity checksum of the message must be calculated and connected: there is now Mc(M). Mc(M) is then encrypted by exOR with the RC4 stream generated by k and a 24-bit common initialization vector (IV) named v. We record it as RC4 (v, k).
The result C=Mc(M) ⊕ RC4(v, k) is sent to the network, and users who know k can get the message through XORing C and RC4(v, k).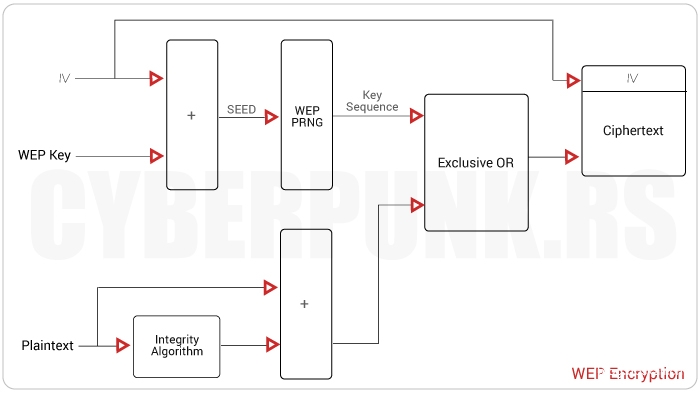
WEP uses RC4 stream cipher based on two algorithms:
The first is RC4-Key Scheduled Algorithm (KSA), which converts a key of length 1 to 256 bits into an initial arrangement S with numbers 0 to N. The internal state of RC4 consists of two numbers i and j, which are used as elements with pointer S.
The second algorithm is the RC4-pseudo-random generation algorithm (PRGA). It generates a single byte key stream from the current internal state of RC4 and then updates the internal state. Initially, N=255, but the algorithm can use different N values.
With CRC32, the original message is XORed with a 32-bit constant followed by as many 0 as possible to reach the length of the message. The result becomes a new "message" and the operation is repeated until the length of the result is lower than the length of the constant. It should be noted that this hash function is linear and bondless.
WEP Attack:
Packet Injection Fake Authentication FMS Attack KoreK Attack Chop Attack Fragment Attack PTW Attack (Pychkine, Tews, Weinmann)
Package Injection
This allows external personnel to generate a large amount of traffic on the network without having to be associated with it in any way. First, he must capture a specific type of packet. Although hidden behind encryption, packet type can be easily guessed based on packet size.
An ARP request package is always 28 bytes. By reinjecting it into the network, the AP will respond to this forgery request and send packets to the legitimate client. The extra traffic is used to collect encrypted packets faster, and the more packets the more likely he is to destroy WEP faster.
Fake authentication
Fake authentication attack allows an attacker to join a WEP-protected network, even if he does not know the root key. Clients can authenticate themselves in WEP-protected networks in two ways:
The first method is to open system authentication, with basically no protection.
The second method is called shared key authentication. This uses a secret root key and challenge-response authentication. The client requires an AP to connect, and the AP sends a frame containing a challenge (random byte string, plaintext), and the client answers using WEP encrypted frames. If there is no problem, the AP will reply successfully.
An attacker who sniffs out a handshake can join the network itself. Except for the AP challenge, all bytes in frame 3 are constant. The challenge is transmitted in plaintext in frame 2, so the attacker can recover the key stream (and IV) used to encrypt frame 3. With it, he can now initiate the authentication handshake and construct a valid frame (number 3).
FMS Attack
Released in 2001 by Fluhrrer, Mantin, and Shamir, it is based on the awareness of RC4 weaknesses with IVs (initialization vectors or random numbers, 3 bytes per packet key).
The attacker can manipulate RC4, allowing him to guess one byte (5% probability) of the key. If the key is wrong, the attacker will try again with the new key. To achieve a 50% success rate, an attacker needs to capture a large number of packets (up to 6 million).
If we know the first "l" bytes of each packet key, we can simulate RC4-KSA. Don't want the math here to go too deep, basically the next byte's key depends on (a bit related) the current byte and can be used to check if we are on the right track. Each iteration, we get one more byte of key and end up testing it. If it is wrong, the bytes of the key are switching with another possible value and restarting the process.
KoreK Attack
This is based on an FMS attack (first appeared in the netstumbler forum, 2004), but allows the attacker to find the key faster.
ChopChop Attack
Also found by "KoreK", it opposed exploiting the weakness of RC4, which attacks the WEP protocol itself (CRC32 checksum and lack of playback protection). It enables an attacker to decrypt packets without knowing the key.
Flip a bit in the ciphertext and then calculate which bit in the encrypted CRC32 value must be flipped so that the packet remains valid. The often mentioned method is to take out the last byte and try to guess its value.
Splitting Attack
If there is currently no client connected to the access point, a good attack can be run. Similar to the ChopChop attack, it speeds up the cracking process by injecting arbitrary packets into the AP. It will generate enough traffic to capture a large number of IVs, thereby improving the chances of cracking the keys (aircrack-ng). "aireplay-ng" and "packetforge-ng" are standard toolkits for such attacks.
PTW Attack
Pyshkin Tews Winmann (PTW) attack, released in 2007.
What makes PTW more powerful than all other attacks is that it can take advantage of every packet captured. Instead of trying all possible key combinations, it implements a key sorting strategy, selects a set of possible keys and continues with the RC4 algorithm based on these keys. Using different voting strategies, an attacker can select the most likely key byte in each decision in the tree to determine the correct key.
Tests show that a 50% chance of success is obtained by just 35,000 to 40,000 packets. Other sources point out that we can get a 95% chance in 85,000 frames.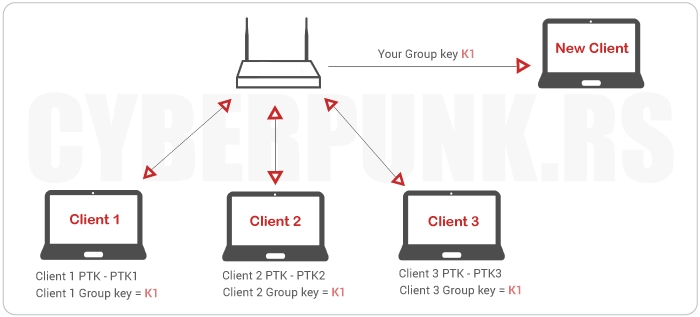
WPA
WPA was launched in 2003 and is a direct response and replacement for the Wi-Fi Alliance to increasingly obvious vulnerabilities in the WEP encryption standard. The most common WPA configuration is WPA-PSK (Pre-Shared Key). The key used by WPA is a significant increase in keys 256-bit than used in WEP systems. 64-bit128-bit
Note: WPA-PSK basically means that the Wi-Fi network has a password shared by each Wi-Fi network client.
WPA includes message integrity checks (to determine if an attacker has captured/changed packets passed between the access point and the client) and Temporary Key Integrity Protocol (TKIP). TKIP uses a per-packet key system, which is more secure than the fixed key system used by WEP. The TKIP encryption standard was later replaced by the Advanced Encryption Standard (AES).
TKIP uses the same underlying mechanism as WEP and is therefore vulnerable to many similar attacks (such as Chop-Chop, MIC key recovery attacks).
Usually people do not directly attack the WPA protocol, but use the supplementary system ——Wi-Fi Protected Setup (WPS), which is launched by WPA.
Note: TKIP (Temporary Key Integrity Protocol) ——RC4 stream cipher is used with 128-bit per packet key, which means it dynamically generates a new key for each packet. Although still in use, it was considered obsolete after being replaced by CCMP in 2009.
WPA Attack:
Back and Tews Improved Attack on RC4, 2008, Inject Ohigashi-Morii Attack (Beck and Tews' + Man in the middle) Michael Attacks Dictionary Attack Handshake, Key Recovery
The attack "requires" to enable Quality of Service (QoS) (actually). This allows multiple channels to be used. Each channel has its own TSC (TKIP sequence counter). Channel 0 has most of the traffic, and the other channels have lower TSCs. The attack requires that the Key Renewal Interval be greater than 15 minutes (the time it takes to decrypt the ARP packet).
The attacker unauthenticates the site and then captures the ARP packet. Next, he will perform the modified ChopChop attack to recover the packet's ICV (integrity check value) and MIC. In this way, the attacker needs to guess the last part of the packet, i.e. the IP address. Finally, he inverts the MICHAEL algorithm and obtains the MIC key. With it, he can now inject custom packets into the network.
Countermeasure: Disable QoS.
Two types of keys used for data encryption:
Pairwise Transient Key (PTK) – Used to protect unicast data frames
Group Temporary Key (GTK) – Used to protect group addressed data frames (such as broadcasting ARP frames)
The attacker sends an ARP request (with his MAC and AP's IP address), so other clients update their ARP table. This way, all clients will send their packets to the attacker. The attacker will receive packets decrypted by the AP and reencrypt them with his own key. Everyone can build and broadcast fake packets using GTK. Messages sent with group keys are not protected against spoofing.
WPA2 protocol
Of course, WPA2 replaces WPA. Certification began in September 2004 and from March 13, 2006, all new devices must be trademarked with Wi-Fi. The most important upgrade is to force the use of the AES algorithm (rather than the previous RC4) and introduce CCMP (AES CCMP, counter cipher mode with block link message verification code protocol, 128 bits) as a replacement for TKIP (still present in WPA2) as a backup system and WPA interoperability).
As in previous versions, attacks on WPS are the most common attacks.
Note: WPA/WPA2 MGT (Administrative) means that the password is not a pre-encrypted key, but uses an authentication service, usually a RADIUS service that verifies the username/password of a Wi-Fi network client. MGT is most often associated with an enterprise/professional environment.
WPA2 Attack:
KRACK Attack PMKID Attack (PSK)WPS Attack Dictionary Attack
KRACK Attack
This attack targets four handshakes used to establish random numbers (a kind of "shared secret") in the WPA2 protocol. The WPA2 standard expects WiFi to be occasionally disconnected and allows reconnection with the same value during the third handshake (for fast reconnection and continuity). Since this standard does not require different keys to be used in this type of reconnection, which may be required at any time, replay attacks are possible.
Countermeasure: The access point has configuration options that can disable EAPOL-Key frame retransmission during key installation.
Useful: Key Reinstall Attack: Force Nonce Reuse in WPA2
PMKID Attack (PSK)
On August 4, 2018, a new exploit was released for Wi-Fi networks using WPA/WPA2-PSK (pre-shared key). The vulnerability allows an attacker to obtain a PSK for a specific SSID.
The attack was unexpectedly discovered while looking for new methods to attack the new WPA3 security standards.
The main difference compared to other attacks is that in this attack, there is no need to capture a complete EAPOL 4 handshake. The new attack is performed against RSN IEs of a single EAPOL frame.
Normal users are no longer needed because the attacker communicates directly with the AP (also known as a "clientless" attack).
You do not need to wait for 4 handshakes between the average user and the AP.
No more retransmission of EAPOL frames (which may lead to uncrackable results) and invalid passwords sent by ordinary users.
EAPOL frames are not lost when a normal user or AP is too far from an attacker.
Nonce and replay counter values are no longer required (causing slightly higher speeds).
There are no more special output formats (pcap, hccapx, etc.) —— final data will be displayed as a regular hexadecimal encoded string.
Source: https ://hashcat.net/forum/thread-7717.html Countermeasures: It is recommended to disable 802.11r on the WPA/WPA2-PSK network.
WPS Attack
WPS was launched in 2006, and the goal of the protocol is to allow Wi-Fi-protected access to home users who know very little about wireless security, and to easily add new devices to existing networks without entering a long password.
In December 2011, a vulnerability was discovered to affect a WPS-capable wireless router. The vulnerability allows remote attackers to recover WPS PIN within a few hours through brute force attacks and use WPS PIN to recover the network's WPA/WPA2 pre-shared key.
WPS enables clients to send 8-bit pins to the access point, which the access point verifies and then allows clients to connect. Pin contains only numbers, and there is a latency in WPS because the attacker needs to wait for the AP to respond. Therefore, an attacker can try several keys per second (or one key per few seconds).
We have 8 numbers and 10 numbers here, 10 8 (100.000.000). This is too much. The 8th bit is the checksum of the top 7 bits, so we have 10 7. Additionally, the password used for verification is divided into two halves, so we can verify the first 4 and last 4 digits independently. It is much easier to guess a 4-digit 2 at a time than an 8-digit 1. Finally, the math finally gets: 10 4 + 10 3=11,000 guesses.
While this strategy used to take hours, the newer WPS Pixie-Dust attacks could crack the network in seconds. Since 2011, many routers now have protections to detect and slow down (rate limit) or turn off Reaver type attacks (locking too many failed PIN attempts).
Routers have updated some settings to prevent WPS, but the way they implement encryption remains flawed. Creating true random numbers is relatively difficult, which is necessary to generate strong encryption. To achieve this, there is usually a function that takes a "seed" and produces a pseudo-random number.
If you use long or variable "seed" numbers, you can get the same results as actually random numbers, but if you use "seed" that is easy to guess, or worse, using the same "seed" time and time again, you end up with weak encryption that is easy to crack. That's what happens with those newer routers, what the WPS Pixie-Dust attacks exploit.
Countermeasure: Turn off WPS function.
Dictionary Attack
This relies on capturing the WPA handshake and then using a word list or brute force to crack the password. Depending on the password strength (length, character set), it can be difficult or impossible to crack it in a "reasonable" time.
Countermeasure: Use long passwords (12+) and different character sets (alphanumeric, special characters, uppercase/lowercase).
WPA3 protocol
In January 2018, the Wi-Fi Alliance announced WPA3 to replace WPA2. The new standard 128-bit uses encryption in WPA3-person mode (WPA-PSK pre-shared key) or 192-bit WPA3-enterprise (RADIUS authentication server).
WPA3 will be harder to attack because its modern key establishment protocol is called "simultaneous verification equality" (SAE) or dragonfly key exchange. SAE improves security of initial key exchange and provides better protection against offline dictionary attacks.
But it is equally vulnerable to man-in-the-middle attacks and cannot resist evil WiFi phishing attacks.




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
