We download files on the Internet, and sometimes we often see that the author of the file will attach the program's md5 value. The purpose is to allow users to compare the md5 value of the downloaded files. If the MD5 value of the file you download does not match the original author's provided, it means that the file has been modified by someone else. If it is a program, it is possible that someone else has joined a malicious backdoor.
The computer uses multiple hashes or message digests for any number of files. At the same time, you can choose to mine the directory structure recursively. By default, the program calculates MD5 and SHA-256 hashes, equivalent to -c md5, sha256. It can also use a known hash list to audit a set of files. Errors will be reported as standard errors. If no files are specified, read from standard input.
Using
hashdeep file name 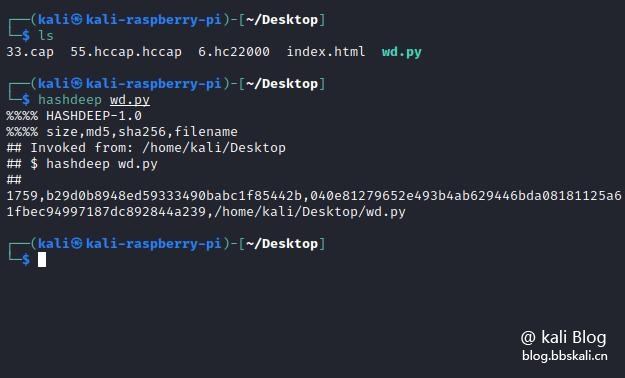
After modifying the file, look at the md5 value 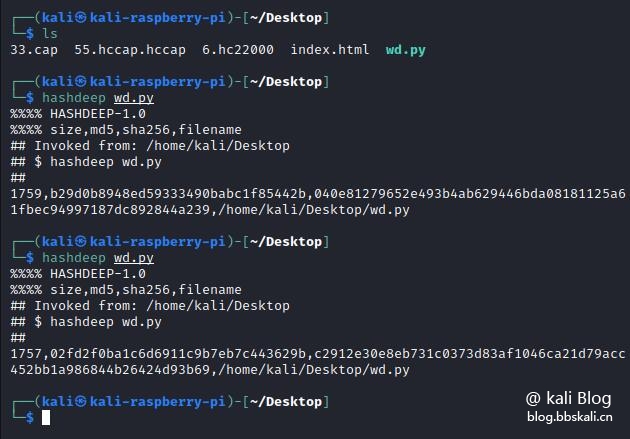
It can be found that the change from b29d0b8948ed59333490babc1f85442b,040e81279652e493b4ab629446bda08181125a61fbec94997187dc892844a239 has become 02fd2f0ba1c6d6911c9b7eb7c443629b,c2912e30e8eb731c0373d83af1046ca21d79acc452bb1a986844b26424d93b69
Other parameters
-c: Mode. Use the specified algorithm to calculate the hash of the file. Support md5, sha1, sha256, tiger and whirlpool.
-r: Enable recursive mode. Iterate through all subdirectories. Note that recursive mode cannot be used to check all files with a given file extension. For example, calling hashdeep -r *.txt will check all files in a directory ending in .txt.
-v : Enable detailed mode. Use again to make the program more detailed.




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
