There are a few remaining lamps, and the night is thick. I walked on an unknown small road in the city, complaining about the depression brought to me by work. Looking at the shy wallet and the confused way forward. I fell into deep thought. Today is another day of overtime. New projects are about to be launched, but bugs are emerging one after another, so I can only work overtime to this point. At this time, my wife probably all went to bed.
I came downstairs to the apartment I rented. The small apartment I rented was a two-story building with the landlord living downstairs, and there were two rooms upstairs. Previously, the room was accompanied by adults, and the child moved out after graduation. There is a small courtyard on the second floor, which is why I rented it. Sitting in the yard in summer, looking up at the starry sky, it’s so beautiful!
As soon as I went upstairs, I found that the light next door was on. This is all the point, where do you come from? It's probably a new one. I didn't care, I went to bed just after being tired for a day.
I wake up late every day, but I wake up particularly early today. Because I seemed to hear a woman talking in my dream. And it's a very magnetic sound. For a single dog like me, it is hard to come by! Because I am introverted and shy, I still have no girlfriend. And I seemed to see spring.
When I was at work, I met the landlord and mentioned this matter by the way. From the landlord, I learned that I had just moved here yesterday and seemed to be working in an administrative unit. It was a once-in-a-lifetime opportunity for me, and a new plan lingers in my mind all day.
Information Collection
Target: Collect QQ *bao Xinshou* number and other related information.
Blocking bricks and attracting jade
How to obtain the above information of the target? Some friends say it’s very simple? Just ask, but for people like us who are introverted. This is an insurmountable hurdle.
So how to do it? Although it is 5G now, the expensive costs make workers still like to take advantage of WIFI. She just moved here, and the first thing she did was to see if there was any useful WiFi.
So I turned on the router's guest network, without encryption. The purpose is to make it quickly take the bait. But some have some concerns due to free hotspots. It can also be set to encrypt WiFi and then share the password through the WiFi master key.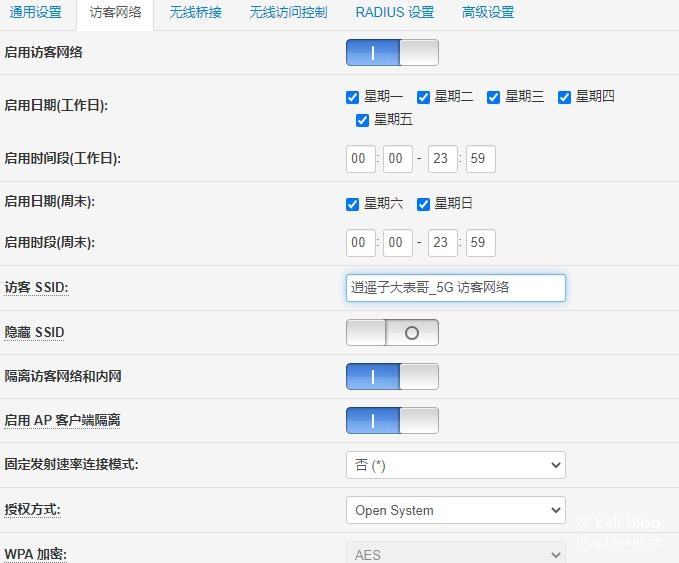
Working servo
After starting my plan, I get off work very early every day. The purpose is to get useful information early. Finally, God pays off and sees a strange device online.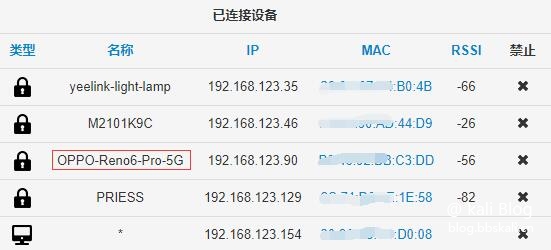
You can see that an OPPO-Reno6-Pro-5G has been quietly launched.
Unexpected
Because it was night, the other party’s mobile phone must be using it. So our mobile phone data was used to capture packets.
tcpdump -i br0 host 192.168.123.90 -w 14235.cap 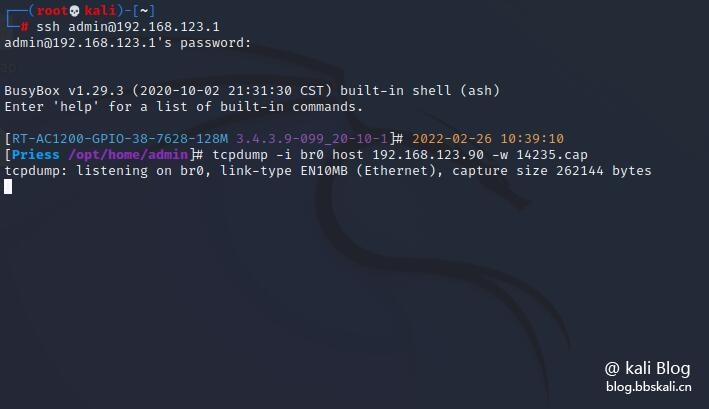
After waiting for a while, we analyze the captured data packets
Download the data packet and open it with Wireshark 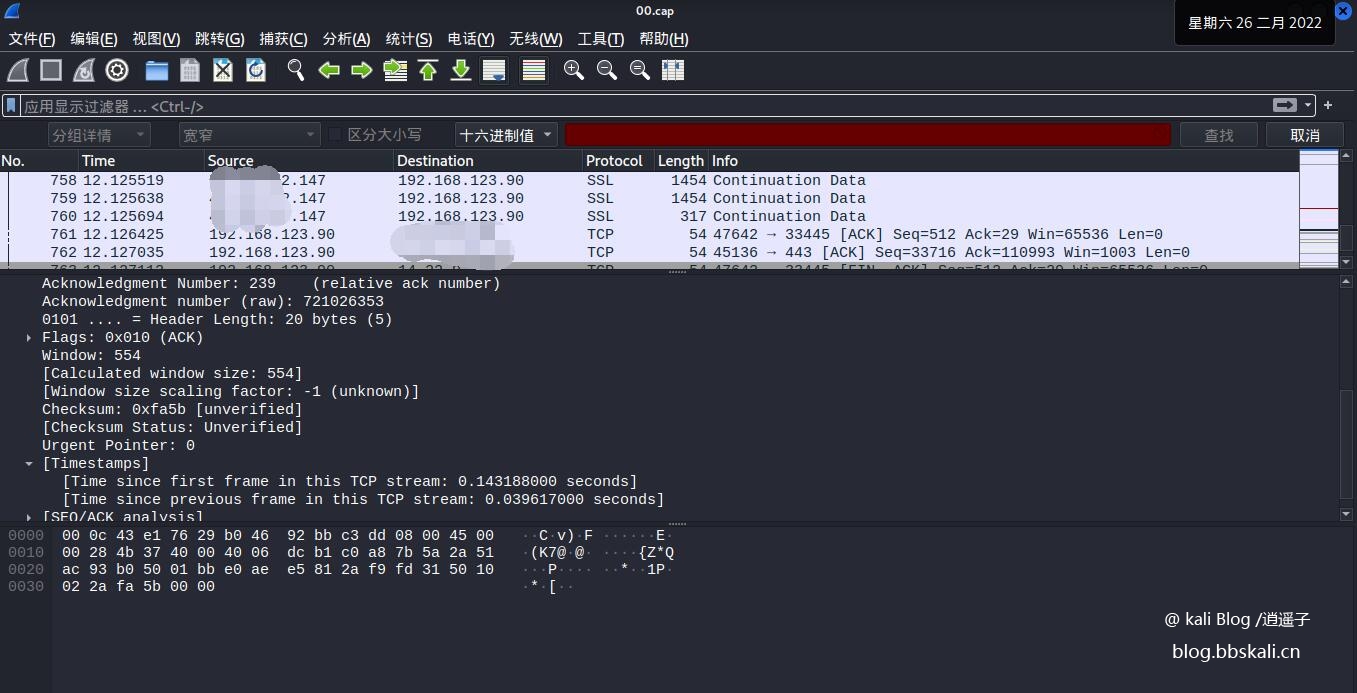
Find QQ
Press ctrl+f to search hexadecimal 00 00 00 0d 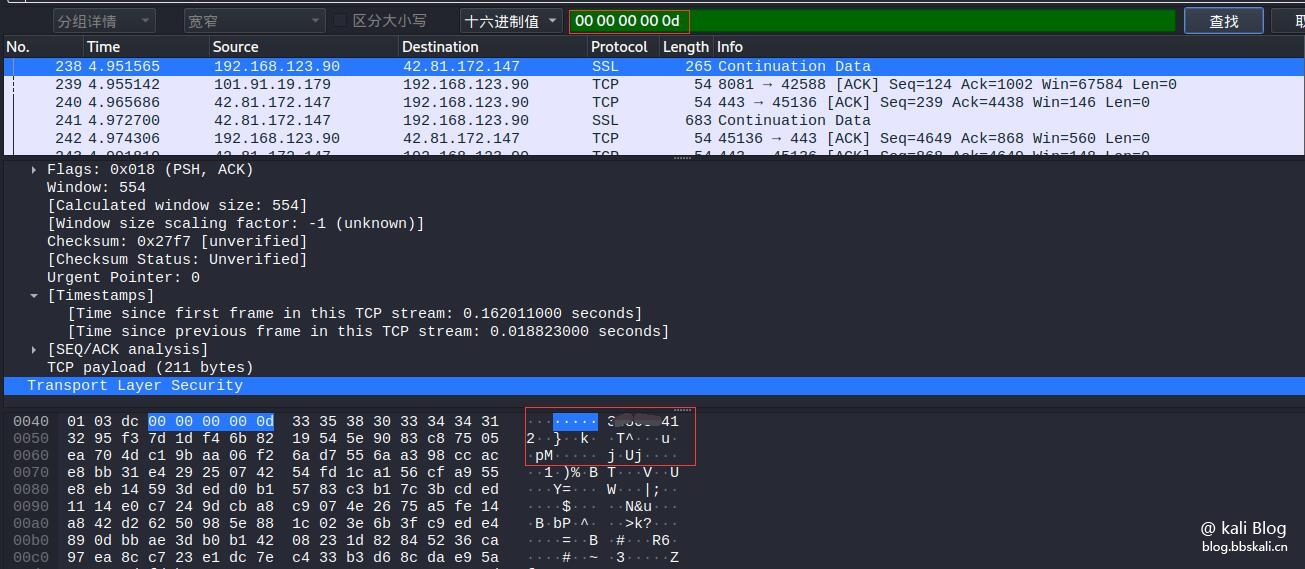
Confirm number 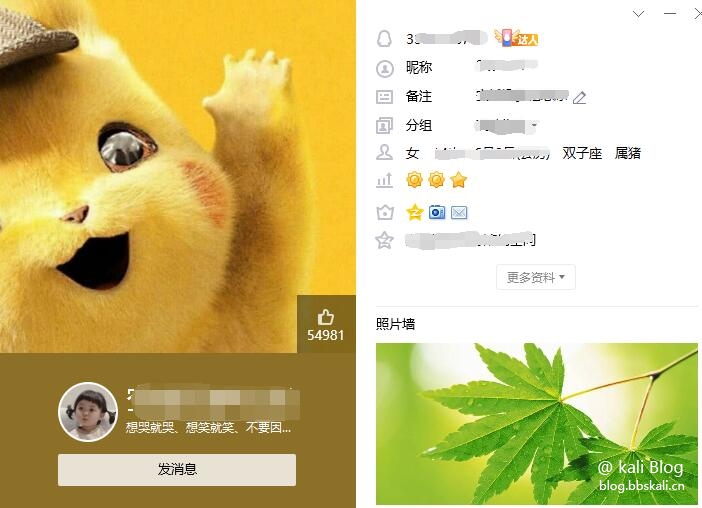
Hand* 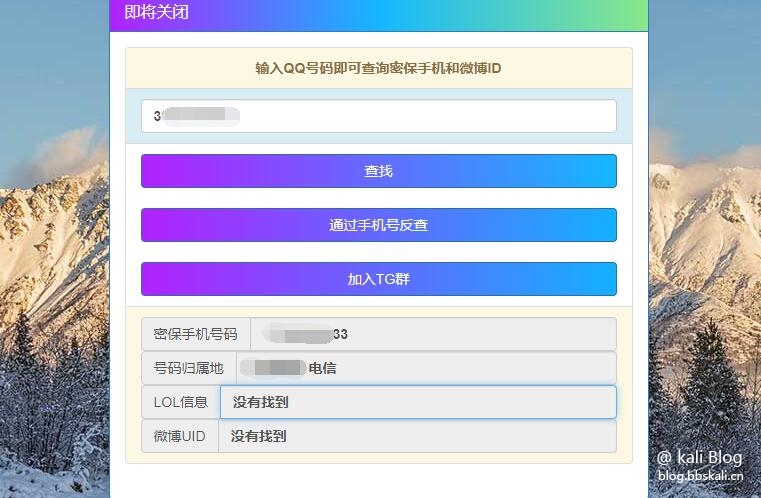
A certain bao 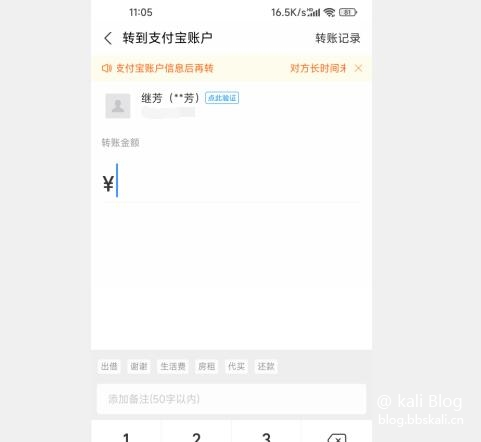
wei xin 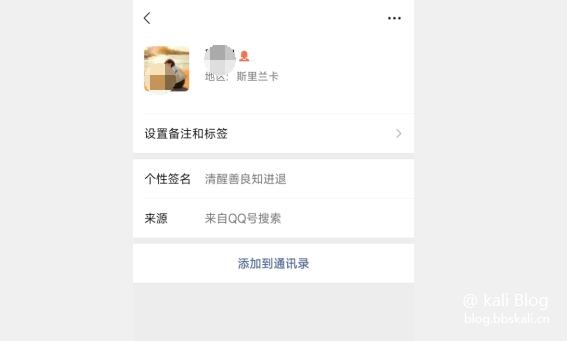
At this point, the basic information is collected. Next is a long road.
(There are many ten thousand words omitted here)
Declaration
The above content is only experimental data, please do not take it seriously. Please do not illegally and maliciously attack others, please do not use them illegally!




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
