Arping is used to discover surviving hosts on computer networks. By scanning the IP within the network segment, you can obtain relevant information about the address and survival status. Arping uses the Address Resolution Protocol (ARP) to run work at layer 2 (or the link layer of the OSI model) to detect hosts. Since ARP is not routable, this only applies to local networks.
User Help
arping -h
ARPing 2.22, by Thomas Habets thomas@habets.se
usage: arping [ -0aAbdDeFpPqrRuUv ] [ -w sec ] [ -W sec ] [ -S host/ip ]
[ -T host/ip ] [ -s MAC ] [ -t MAC ] [ -c count ]
[ -C count ] [ -i interface ] [ -m type ] [ -g group ]
[ -V vlan ] [ -Q priority ] host/ip/MAC | -B
For complete usage info, use --help or check the manpage.
Parameter definition
-A: Similar to the -U parameter, but uses the ARP REPLY package instead of the ARP REQUEST package. -b: Send Ethernet broadcast frames, arping uses the broadcast address at the beginning, and unicast unicast address after receiving the reply. -c: Stop after sending the specified count ARP REQUEST packets. If the -w parameter is specified, the same number of ARP REPLY packets will be waited until the timeout is reached. -D: Duplicate address detection mode, that is, Duplicate address detection mode (DAD), is used to detect whether there is an IP address conflict, and if there is no IP conflict, it will return 0. -f: Exit after receiving the first response packet. -h: Show the help page. -I: The name of the network device used to send the ARP REQUEST packet. -q: quite mode, no output is displayed. -U: Unreasonable (forced) ARP mode to update the local information in the ARP CACHE list on other hosts, no response is required. -V: Display the version number of arping. -w: Specify a timeout time in seconds, arping exits after reaching the specified time, regardless of how many packets were sent or received during the period. In this case, arping will not stop after sending the specified count (-c) packets, but will wait until the timeout or the sent count packets will respond before exiting. -s: Set the IP resource address for sending ARP packets. If it is empty, it will be processed as follows:
1. DAD mode (-D) is set to 0.0.0.0;
2. Unsolicited mode (-U) is set to the target address;
3. Other methods are calculated from the routing table.
Example
Obtain the destination MAC address through the IP address
arping -c 5 192.168.123.129 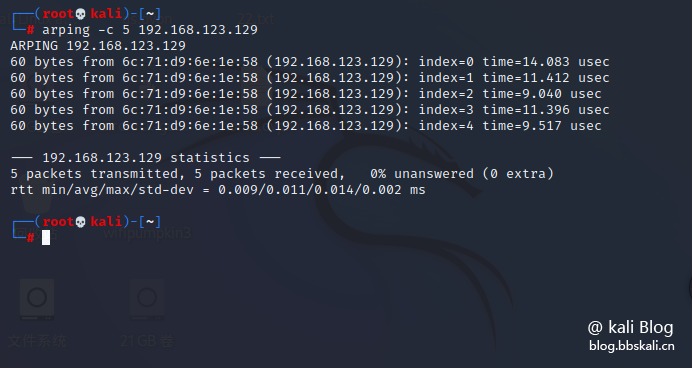
Test the survival status of the target host
arping -c 4 -I eth0 192.168.123.192 -S 4 Send 4 detection messages. If there is a reply, it means that the other party is alive.




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
