If you want to do a good job, you must first sharpen your tools. For new friends who are new to network security. You must have some understanding of these tools. In this article, let’s briefly talk about these network security tools!
Web Security Class
The web-class tools mainly use various scanning tools to discover various vulnerabilities in web sites such as sql injection, xss, etc. Therefore, obtain system permissions, commonly used tools include
01 Nmap
nmap is the first tool we use. Using this tool, we can scan the corresponding IP of the site, the information of the ports, services, operating systems, etc. that have been opened. It can also be used as a vulnerability scanning, brute force cracking, fingerprint recognition, fingerprint recognition, etc.
02 dirsearch
Scan the main user site directory. By scanning the site administrator background, backup files, and the site's directory structure that we can obtain. Similar tools include Gobuster DIRB Wfuzz, etc. Each tool has its own strengths, but the principles are similar.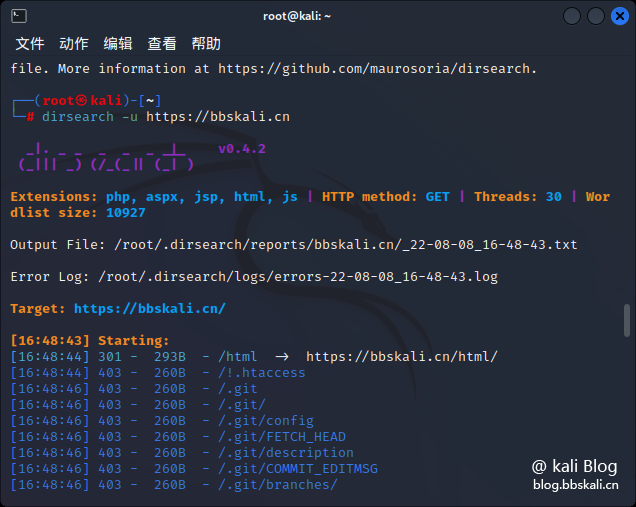
03 dnsmap
dnsmap is a subdomain name collection tool. When the main site does not find a vulnerability, we can also get the directory through the vulnerability on the side site. There are many such limited tools, such as Layer subdomain excavator.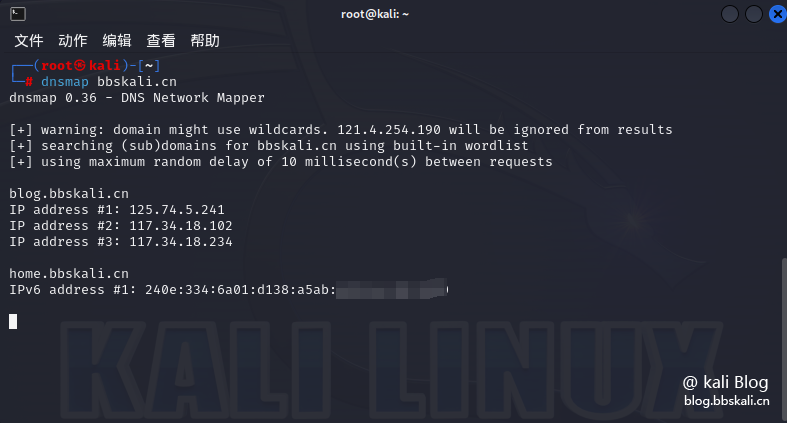
04 web vulnerability scan
Web vulnerability scanning tools are blooming. The most famous tools are Nessus appscan awvs owasp zap xray and so on. Let me give you a brief introduction. NessusNessus is the most used system vulnerability scanning and analysis software in the world. It has very powerful functions, divided into ordinary and professional versions. After entering the target, you can scan for vulnerabilities with one click. The input results are intuitive and clear.
 appscanAppScan uses a powerful scanning engine to automatically crawl target applications and test vulnerabilities. Test results are prioritized and presented in a way that allows operators to quickly classify problems and dig deep into the most critical vulnerabilities found. Reference article 《WEB漏洞扫描工具HCL AppScan Standard》
appscanAppScan uses a powerful scanning engine to automatically crawl target applications and test vulnerabilities. Test results are prioritized and presented in a way that allows operators to quickly classify problems and dig deep into the most critical vulnerabilities found. Reference article 《WEB漏洞扫描工具HCL AppScan Standard》 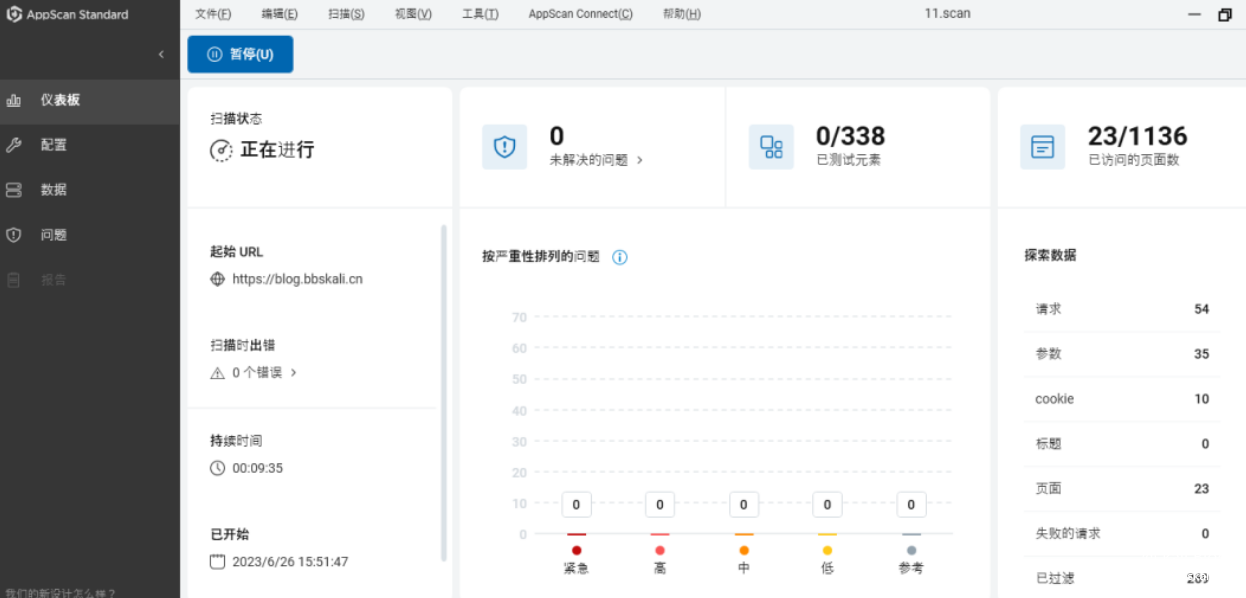 owasp zapOWASP ZAP, full name: OWASP Zed Attack Proxy attack proxy server is one of the most popular free security tools in the world. ZAP can help us automatically discover security vulnerabilities in web applications during the development and testing of applications. In addition, it is also an excellent tool for artificial safety testing for experienced penetration testers.
owasp zapOWASP ZAP, full name: OWASP Zed Attack Proxy attack proxy server is one of the most popular free security tools in the world. ZAP can help us automatically discover security vulnerabilities in web applications during the development and testing of applications. In addition, it is also an excellent tool for artificial safety testing for experienced penetration testers.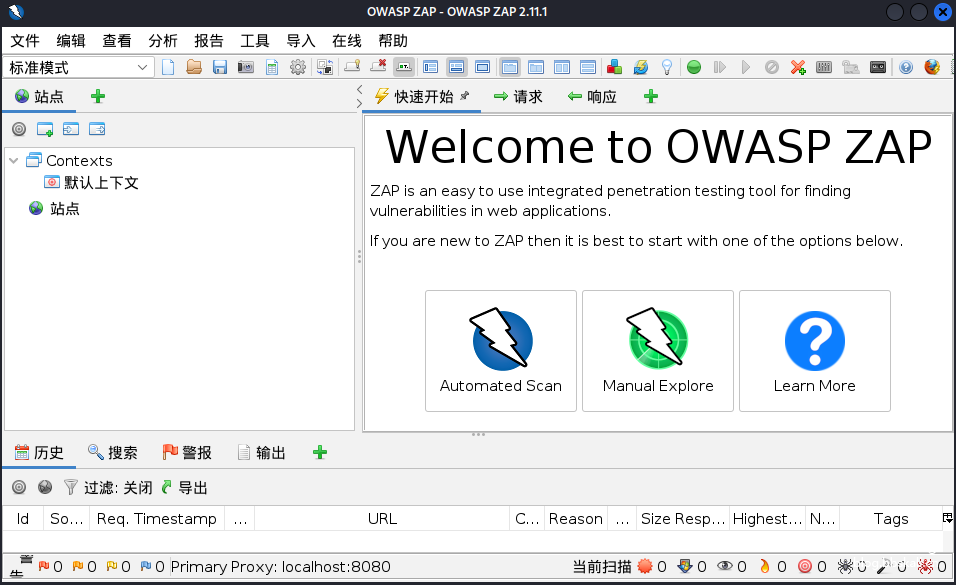 xrayxray is a powerful security assessment tool, created by many experienced front-line security practitioners. The main feature is that : is fast detection speed. Fast packet transmission speed; high efficiency of vulnerability detection algorithm. Wide support range. From OWASP Top 10 general vulnerability detection to various CMS framework POCs, it can be supported. It can also be linked with Burp. Double damage is the most deadly.
xrayxray is a powerful security assessment tool, created by many experienced front-line security practitioners. The main feature is that : is fast detection speed. Fast packet transmission speed; high efficiency of vulnerability detection algorithm. Wide support range. From OWASP Top 10 general vulnerability detection to various CMS framework POCs, it can be supported. It can also be linked with Burp. Double damage is the most deadly.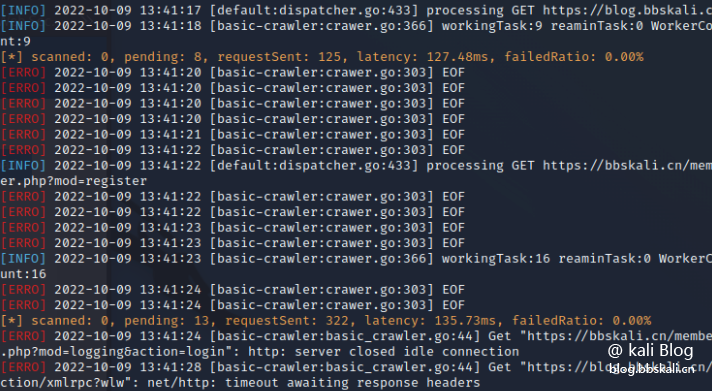
05 sqlmap
sqlmap is an automated SQL injection tool. Its main function is to scan, discover and exploit SQL injection vulnerabilities for a given URL. It is one of the must-have tools for cybersecurity enthusiasts.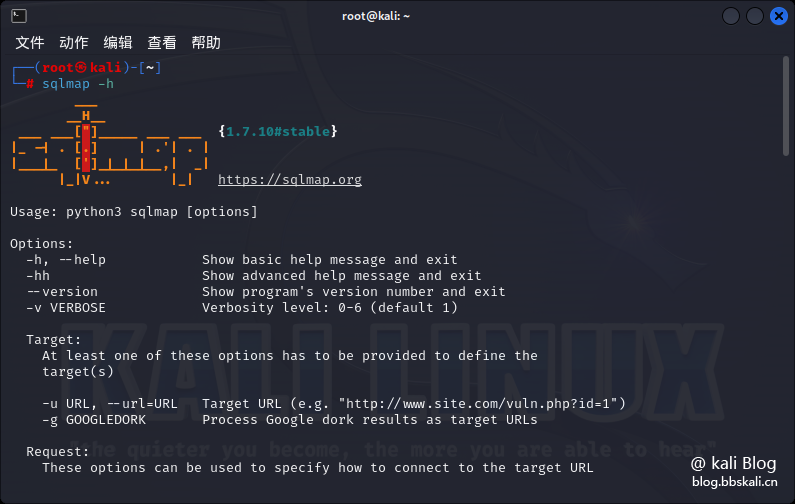
06 Burpsuite
Burp Suite is a graphical tool for testing the security of web applications. In web testing, this tool is commonly used to scan vulnerability, analyze packets, modify packages, and brute-force cracking. It is a very important tool.
At this point, the commonly used tools in web security will introduce to you here. Of course, in addition to the above tools, there are many other excellent tools, but due to limited time and energy, I will not list them one by one.
System Security
System security mainly includes scanning of operating system vulnerabilities such as Windows Linux, ssh ftp password cracking, etc. Common tools are as follows:
07 Metasploit
msfconsole, referred to as msf, is a commonly used penetration testing tool, which includes common vulnerability exploit modules and generation of various Trojans. It is a must-have tool for cybersecurity enthusiasts.
08 Cobalt Strike
Cobalt Strike can be understood as a visual Metasploit. It is a penetration testing tool developed by Red Team in the United States, and is often called CS by industry giants.
09 Goby
Goby is a new network security testing tool created by Zwell (author of Pangolin, JSky, FOFA). It can sort out the most comprehensive attack surface information for a target enterprise, while also conducting efficient and practical vulnerability scanning.
10 Yakit
It is a highly integrated security testing platform. It also contains many functions such as port scanning, brute force cracking, rich plug-ins, packet interception and modification, and other conventional functions.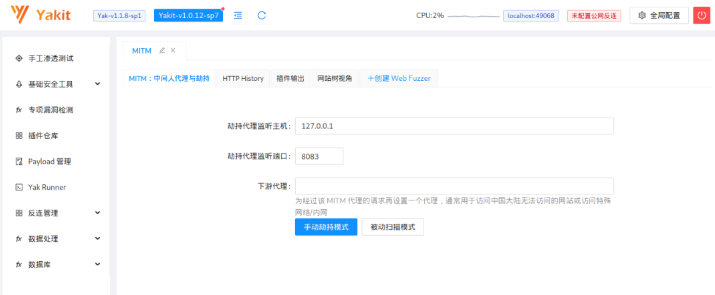
ha
WiFi Security Class
11 hashcat
One of the most popular, fastest and most professional password recovery tools in hashcat. It supports 5 unique attack modes and is suitable for over 300 highly optimized hashing algorithms. It can support CPUs, GPUs and more hardware accelerators and helps with distributed password cracking.
12 John
John can be simply understood as an offline version of hash cracking tool. Supports system passwords, PDF files, ZIP, RAR, wifi passwords, etc.
13 Medusa
A common password cracking tool with weaker capabilities than the previous two, but it supports more protocols. For example, SMB, HTTP, POP3, MSSQL, SSH, etc.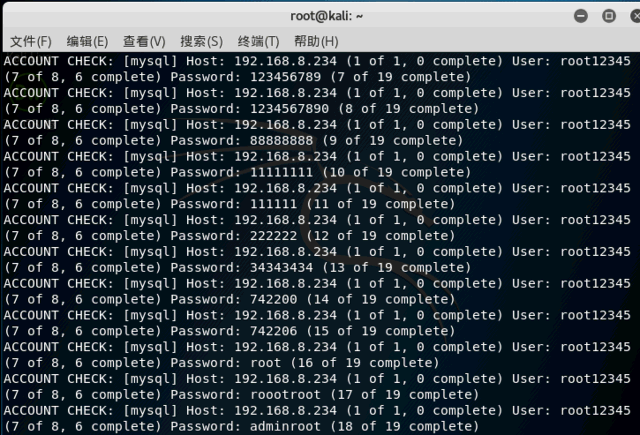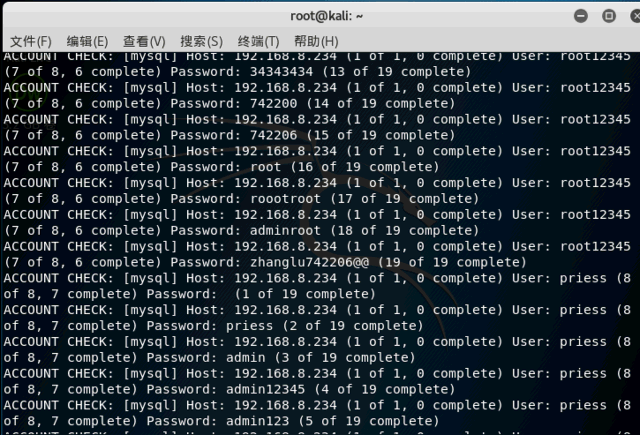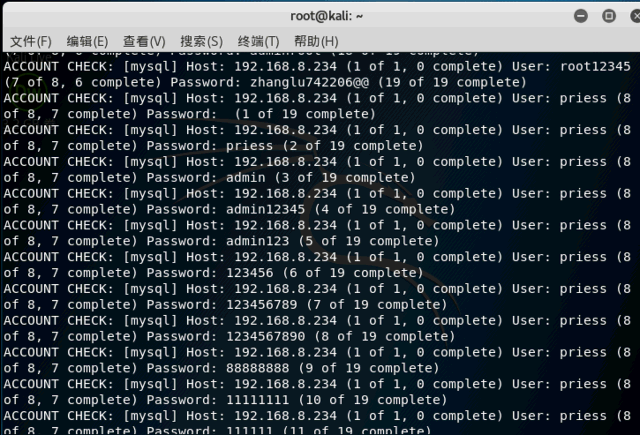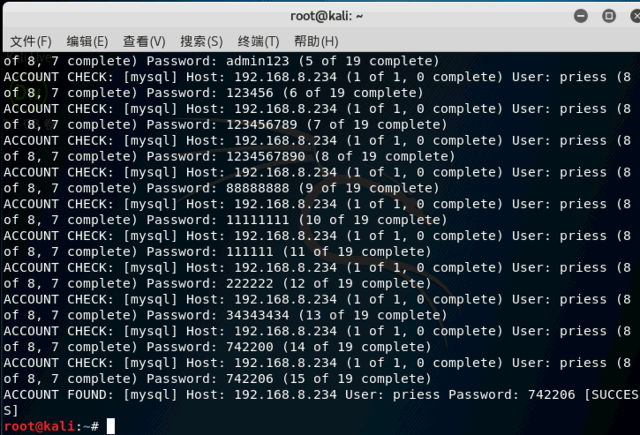
14 Mimikatz
is mainly used to extract passwords, PINs, hash codes and Kerberos tickets from Windows host memory and save them in plain text files.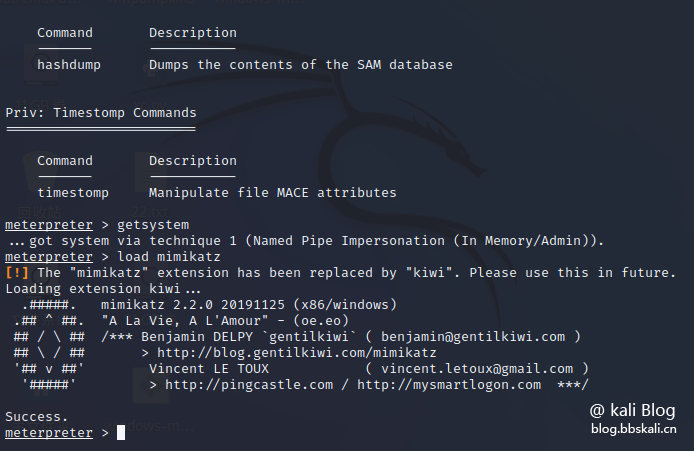
WIFI security class
15 aircrack-ng kit
airmon-ng He is a kit, different kits have different homework. For example, use airodump-ng to crack using aircrack-ng for scanning WiFi. The most basic and introductory WiFi password recovery tool.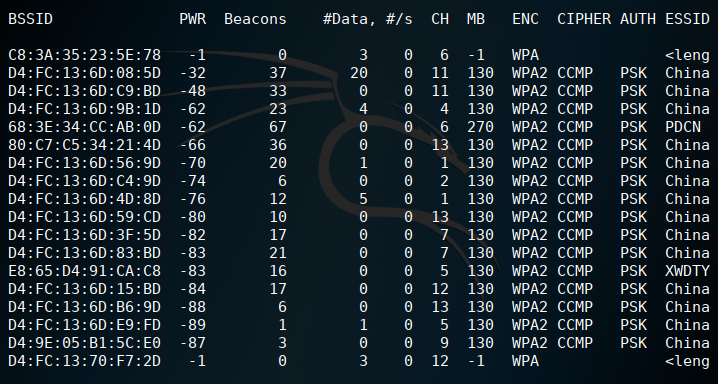
16 wifite
Fool-style one-click WiFi cracking tool. I am unwilling to accept the autocracy.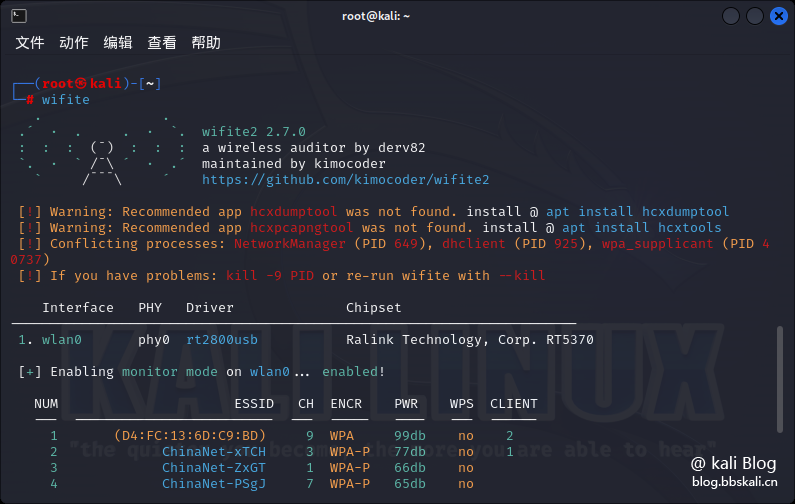
17 fluxion
The most classic WiFi fishing tool. The same type of tool also has airgeddon 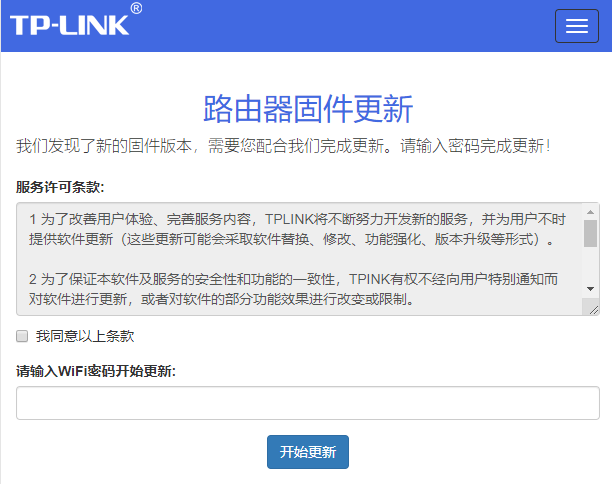
Man in the middle attack
18 Wireshark
Wireshark is the world's top and widely used network protocol analysis tool. Using this tool, we can capture data packet information, and can also capture account, password, picture, chat history and other information in the http protocol.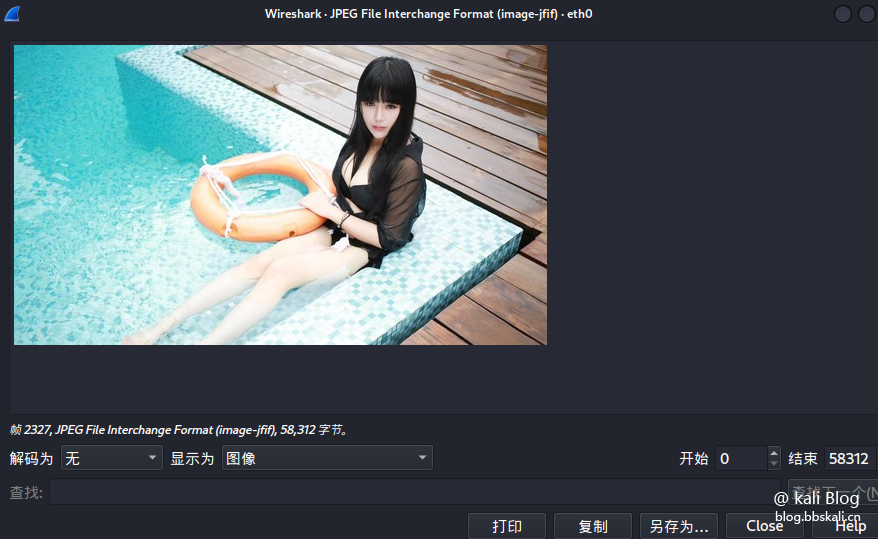
19 ettercap
Ettercap is the most commonly used middleman tool. It should be noted that due to the updates of various protocols, many of the functions of ettercap can no longer be played. But it can still be played in the LAN.
20 Social Engineering Tools
I won’t say much, set is the most awesome. However, every time the dependent environment is started, various errors are reported, but it does not affect the use.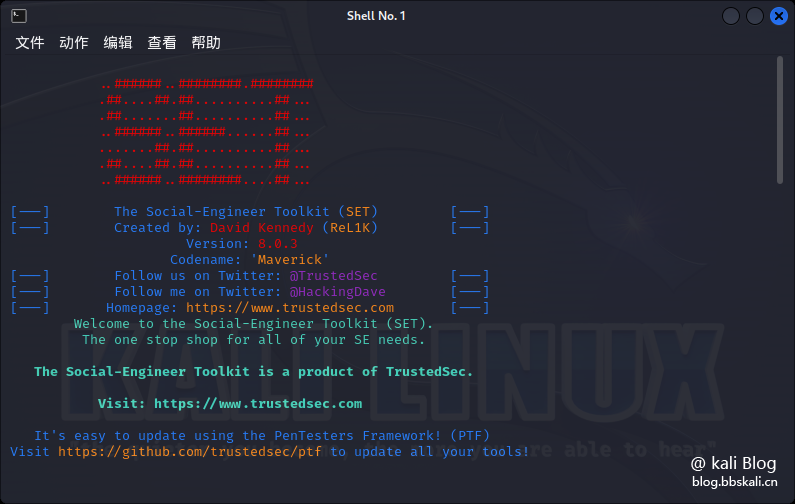




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
