In a previous article, we talked about how to trace the attacker. But this still cannot avoid attacks. How to solve it? At this time, WAF (web firewall) is needed to protect our website. But the waf of Alibaba Cloud and Tencent Cloud is really expensive, and it can be tens of thousands of times at any time. How to solve it?
Environment
Apache2.4 pagoda 7.9.4 pagoda Although there are firewalls for apache and nginx. But they are all charged. (In fact, it was modified based on open source waf, so the charge is too disgusting.)
http://xiaoyaozi666.oss-cn-beijing.aliyuncs.com/image_20221123140548.png
Mainly, common penetration attacks such as square sql injection, xss, and one-sentence. It costs more than 400 a year, why don’t you grab it?
Introduction to ModSecurity
ModSecurity is an open source, cross-platform Web application firewall (WAF), known as the "Swiss Army Knife" in the WAF industry. It can protect the website by checking the data received by the web service and the data sent out. Function SQLi: Block SQL injection XSS: Block cross-site scripting attack LFI: Block attack exploit local file inclusion vulnerability RFI: Block attack exploit remote file inclusion vulnerability RCE: Block attack exploit remote command execution vulnerability PHP Code: Block attack PHP code injection HTTP Violations: Block malicious access to HTTP violations HTTP protocol: Block attack HTTPoxy: Block attack exploit remote proxy infection vulnerability Sshllshock: Block attack exploit Shellshock vulnerability Session Fixation: Block attack exploit vulnerability Scanner Detection: Block attack exploit vulnerability Metadata/Error Leakages: Block source code/error information leakage Project Honey Pot Blacklist: Honeypot project blacklist GeoIP Country Blocking: IP blocking is performed based on the judgment of IP address home
Installation
Installation dependency yum install -y yajl-devel ssdeep-devel installation cd /usr/local
wget https://github.com/SpiderLabs/ModSecurity/releases/download/v2.9.5/modsecurity-2.9.5.tar.gz
tar -zxvf modsecurity-2.9.5.tar.gz
cd modsecurity-2.9.5
./configure --with-apxs=/www/server/apache/bin/apxs --with-apr=/www/server/apache/bin/apr-1-config --with-apu=/www/server/apache/bin/apu-1-config
Make
make install 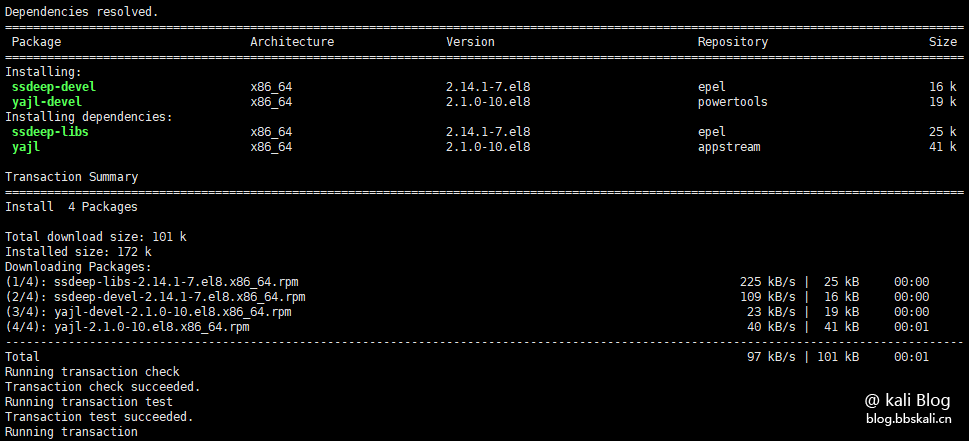
Note that if your environment is not a pagoda, you can also install it according to the above command. The locations that need to be modified are the locations of the three files apxs arp-1-confg`apu-l-config. The default location under the pagoda is: /www/server/apache/bin/You can use the find` command to search.
Configuration Rule File
cd /usr/local
git clone https://github.com/corerulelset/corerulelset.git
#If the local website cannot connect to the official git website, you can try the other two download addresses below
#git clone https://hub.fastgit.org/corerulelset/corerulelset.git
#git clone https://hub.0z.gs/corerulelset/corerulelset.git
mkdir /www/server/apache/conf/modsecurity/
#Copy ModSecurity related configuration files
cp /usr/local/modsecurity-2.9.5/modsecurity.conf-recommended /www/server/apache/conf/modsecurity/modsecurity.conf
cp /usr/local/modsecurity-2.9.5/unicode.mapping /www/server/apache/conf/modsecurity/unicode.mapping
#Copy OWASP related rules files
cp /usr/local/coreruleaset/crs-setup.conf.example /www/server/apache/conf/modsecurity/crs-setup.conf
cp -r /usr/local/coreruleaset/rules//www/server/apache/conf/modsecurity/
#Enable whitelists and rules to disable files
mv /www/server/apache/conf/modsecurity/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example /www/server/apache/conf/modsecurity/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example /www/server/apache/conf/modsecurity/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
mv /www/server/apache/conf/modsecurity/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example /www/server/apache/conf/modsecurity/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
Open waf
Edit httpd.conf, remove the comment # before #LoadModule unique_id_module modules/mod_unique_id.so, and add the following content
LoadModule security2_module modules/mod_security2.so
IfModule security2_module
Include conf/modsecurity/modsecurity.conf
Include conf/modsecurity/crs-setup.conf
Include conf/modsecurity/rules/*.conf
/IfModule edit/www/server/apache/conf/modsecurity/modsecurity.conf, change SecRuleEngine DetectionOnly to SecRuleEngine On and then check whether it is needed for other configurations and close it according to actual needs. (In fact, it is enough to use our configuration rules file. When I installed it, I found that a blank page was displayed when the mobile phone was opened, and the page needed to be refreshed manually before the page could appear. CND problems may occur!)
Test
Restart the apache service
service restart httpd test http://bbskali.cn/?id=%22%3E%3Cscript%3Ealert(1);%3C/script%3E 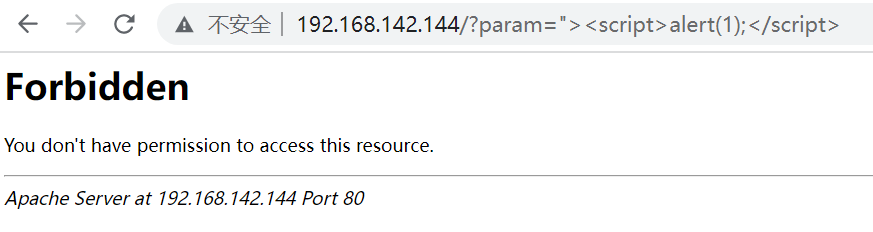
Customize Page
The default 403 page is detrimental to our style, so write a page yourself. (Although lacking design beauty!)
!DOCTYPE html PUBLIC '-//W3C//DTD HTML 4.01 Transitional//EN' 'http://www.w3.org/TR/html4/loose.dtd'
html
head
meta http-equiv='Content-Type' content='text/html; charset=UTF-8'
title system firewall/title
script type='text/javascript'
function getInterceptUrl(){
var url=getQueryString('url');
var domain=getQueryString('intercept_domain');
var tmpstr='The intercepted URL is:';
var div=document.getElementById('interceptdiv');
if(domain !=''){
tmpstr +=domain;
}
if(url !='' url !='/'){
tmpstr +=url;
}
if(domain !='' || url !=''){
var textnode=document.createTextNode(tmpstr);
div.appendChild(textnode);
}
}
function getQueryString(name) {
var result=window.location.search.match(new RegExp('[\?\]' + name + '=([^\]+)', 'i'));
if (result==null || result.length 1) {
return '';
}
return result[1];
}
/script
style type='text/css'
!--
body{margin:0;font-size:7em;font-family:Verdana, Arial, Helvetica, sans-serif;background:#fff;}
fieldset{padding:0 15px 10px 15px;border-color: #fff;border: 0px;}
h1{font-size:2.4em;margin:0;color:#FFF;}
h2{font-size:2.4em;margin:0;color:#CC0000;text-align: center;}
h3{font-size:1.7em;margin:10px 0 0 0;color:#000000;}
#header{width:96%;margin:0 0 0 0;padding:6px 2% 6px 2%;font-family:'trebuchet MS', Verdana, sans-serif;color:#FFF;
background-color:#ffff;}
#content{margin:0 0 0 2%;position:relative;}
.content-container{background:#FFF;width:50%;margin:0 auto;position:0 relative;margin-top:100px}
a{text-decoration:none;color:#009cd6}
a:hover{text-decoration:underline;color:#ff0000}
--
/style
/head
body onload='getInterceptUrl();'
div id='content'
div class='content-container'fieldset
brbrbrbr
img src='Your image address'
h3 style='text-align: center;'The current operation may pose a threat to the security of the website and has been intercepted by the server firewall. /h3
br
div id='interceptdiv' style='color:#F00;text-align: center;font-size: 16px;'/div
/fieldset
/div
/body
/html
Modify the /www/server/apache/conf/modsecurity/crs-setup.conf file and add the following code
SecDefaultAction 'phase:1,log,auditlog,redirect:https://blog.bbskali.cn/waf.html?url=%{REQUEST_FILENAME}intercept_domain=%{request_headers.host}'
SecDefaultAction 'phase:2,log,auditlog,redirect:https://blog.bbskali.cn/waf.html?url=%{REQUEST_FILENAME}intercept_domain=%{request_headers.host}' Comment out the original #SecDefaultAction 'phase:1,log,auditlog,pass'.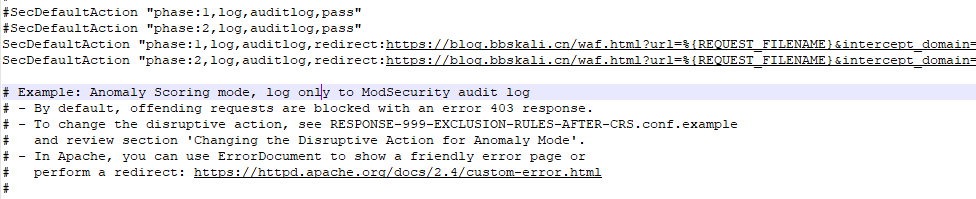
Restart the apache service and view the results.




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
