In web security testing. We usually use brute-force cracking to log in to the website backend. However, many sites support verification codes, so regular brute-force cracking is no longer useful. How to brute forcefully crack a site containing verification code?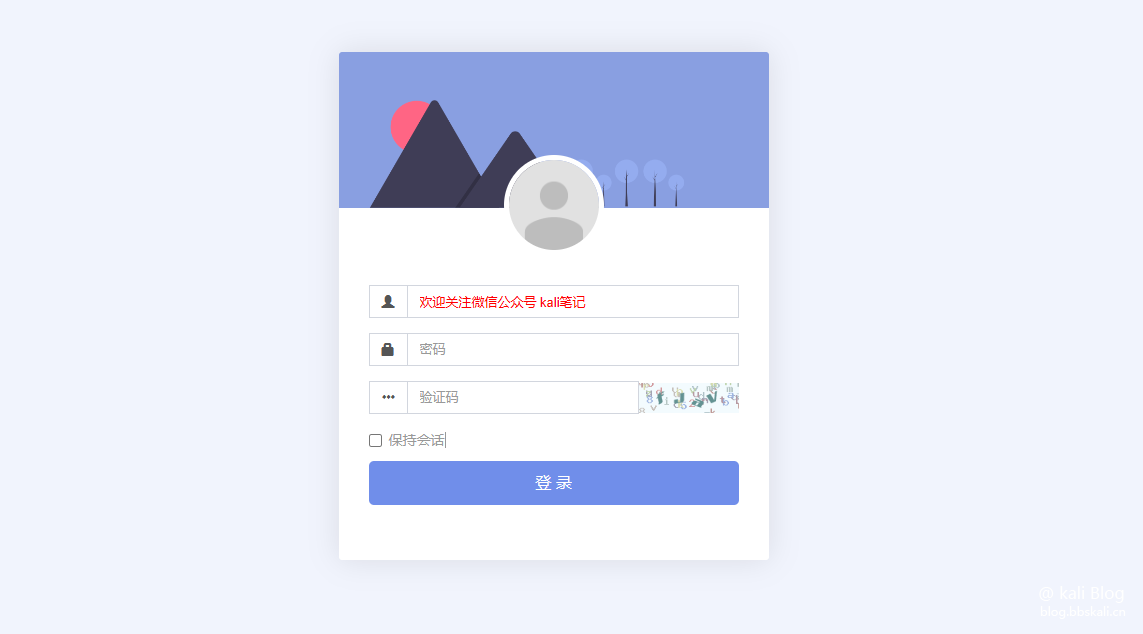
Analyze request data
Next, we first capture packets in burp to analyze what the request data is like after entering information such as account number and password.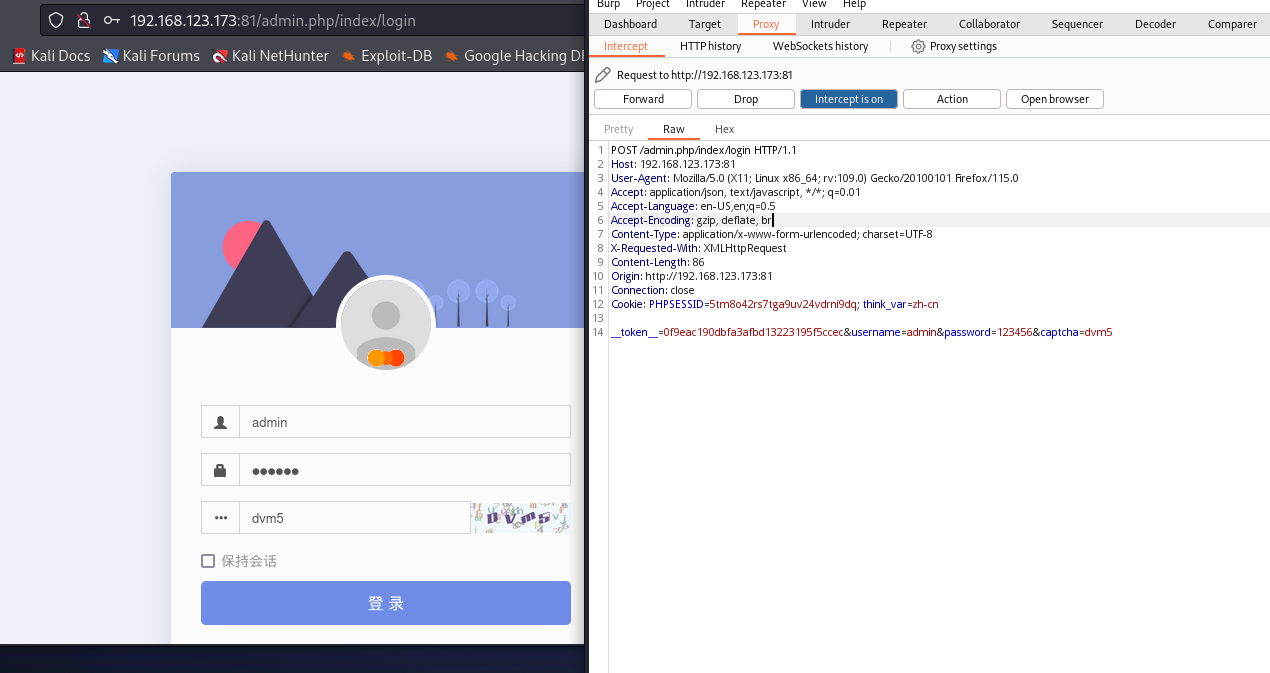
After submitting, we found the following information token__=0f9eac190dbfa3afbd13223195f5ccesername=adminpassword=123456captcha=dvm5
It consists of three important fields: username (username), password (password) captcha (verification code).
Use Pkav HTTP Fuzzer to crack login with verification code
Pkav HTTP Fuzzer is a classic verification code brute-force cracking tool. Next, let’s take a look at how to use it. First, the effect is as follows:
Next, copy all the requested contents in the packets crawled by burpsuite to the Pkav HTTP Fuzzer tool 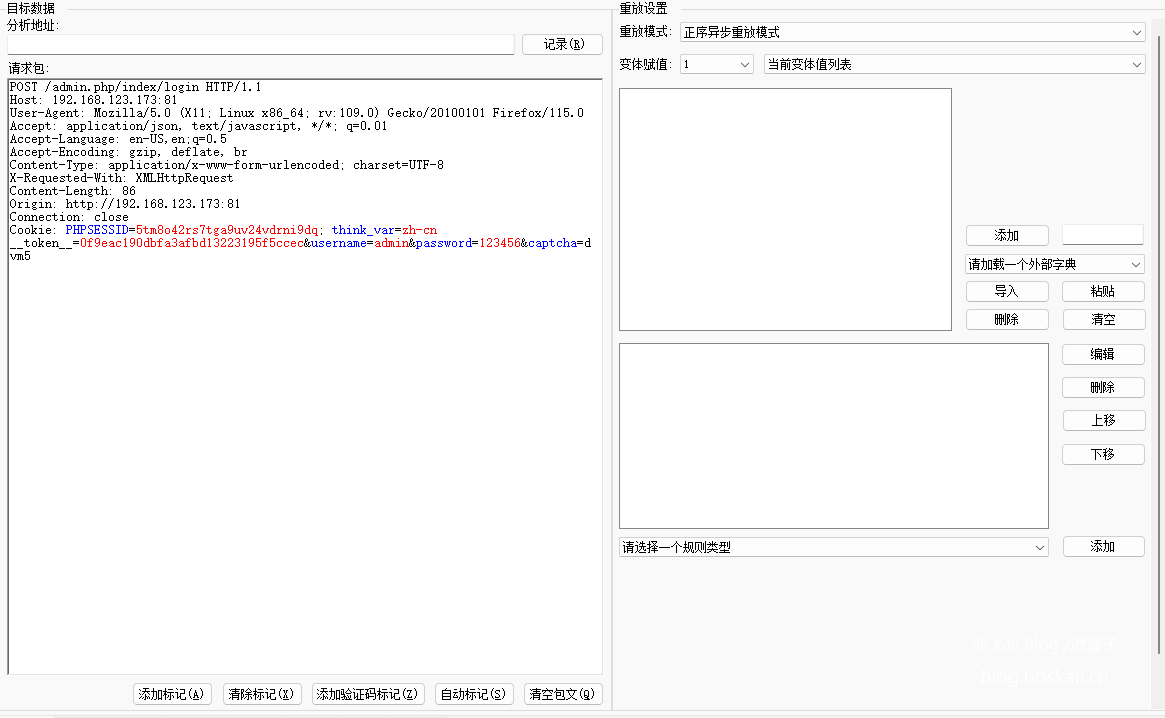
Next, we need to copy the address of the graphic verification code to the analysis address bar.
Click the verification code below to identify and enter the verification code address. Make simple adjustments according to your actual situation. Just make the recognition rate the highest.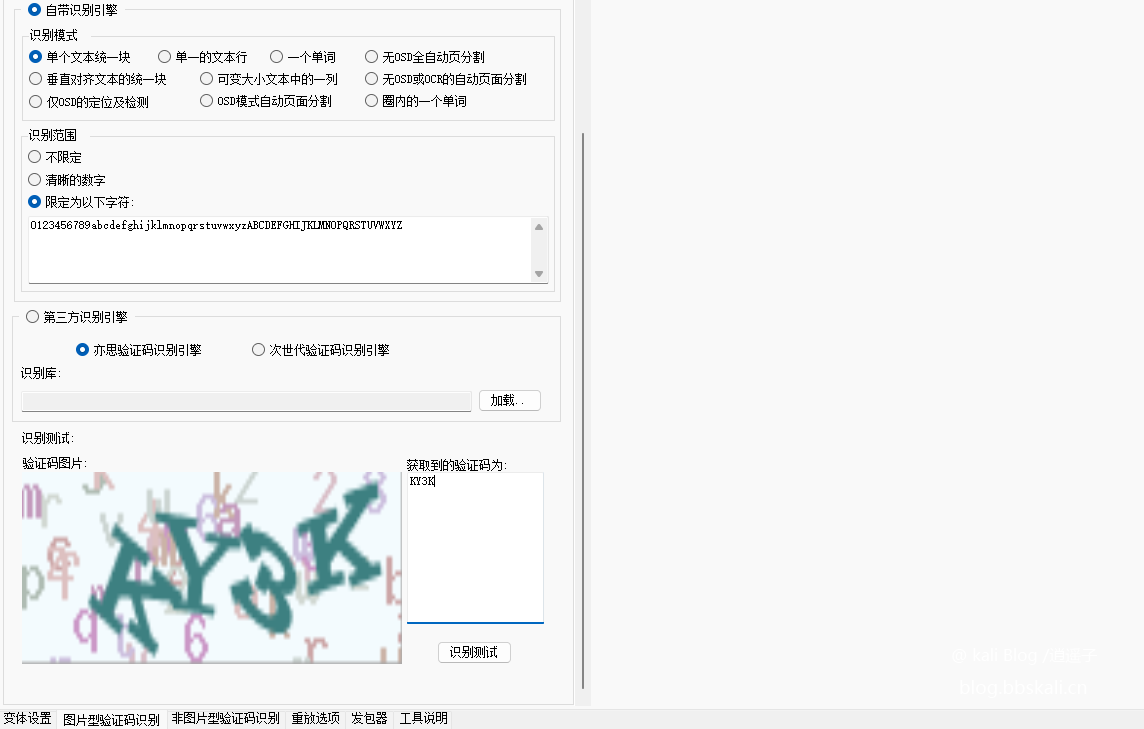
Add tag
This is the same as cracking in burp. We need to add marks to the user name, password, and verification code.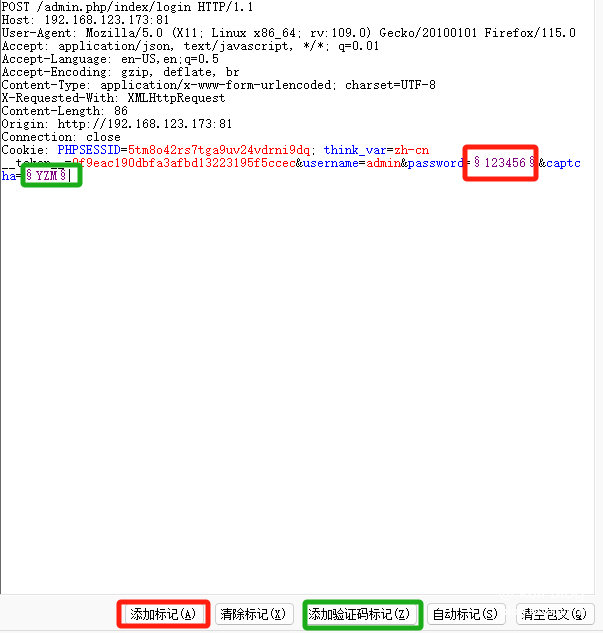
Next, we just add an external dictionary to the marker.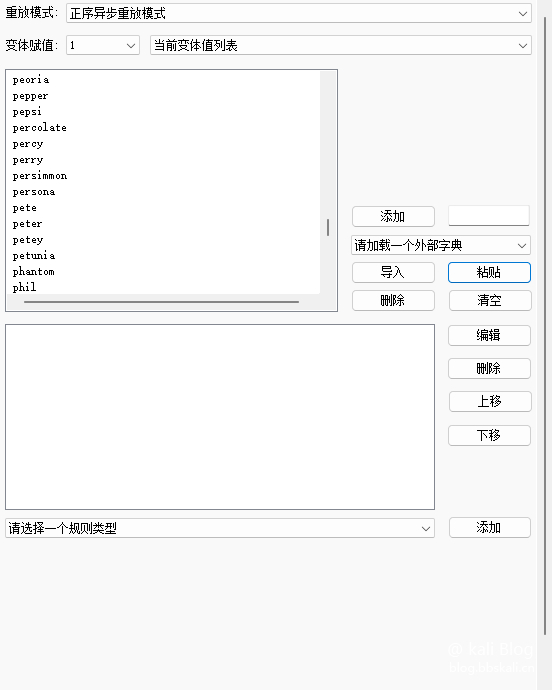
Click the packager to crack
Next, we click on the packager to start the cracking process.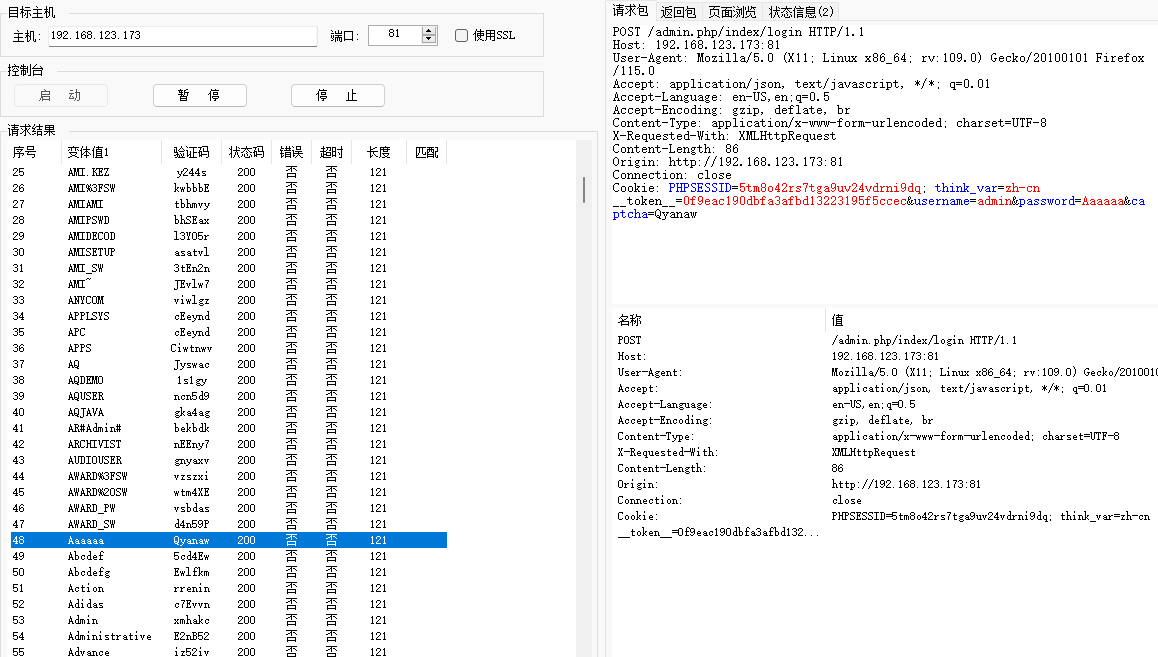
Summary
After testing, the recognition rate of pure numeric verification codes is the highest, and the combination of letters and numbers is low. After adding background interference to the verification code, the recognition rate is greatly reduced. For website developers or webmasters, it is recommended to enable the verification code to be difficult. Prevent the identification of verification codes during brute-force cracking.




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
