UDP introduction:
UDP (User Datagram Protocol) is a connectionless protocol, which is in the fourth layer-transport layer, and is at the upper layer of the IP protocol. UDP has the disadvantage of not providing packet packets, assembling, and not being able to sort data packets. That is, after the message is sent, it is impossible to know whether it has arrived safely and completely.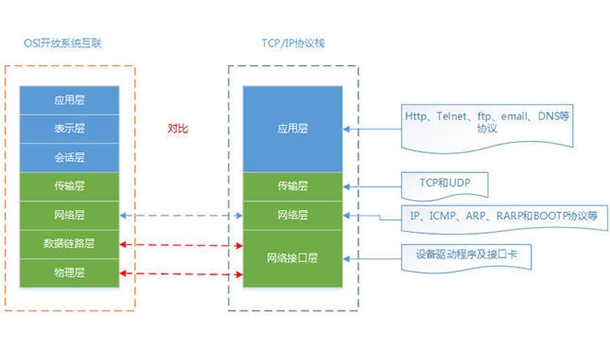
UDP significant features:
1.UDP lacks reliability. UDP itself does not provide mechanisms such as confirmation, timeout retransmission, etc. UDP datagrams may be copied and reordered in the network, and there is no guarantee that each datagram will only arrive once. 2. UDP datagrams have lengths. Each UDP datagram has a length, and if a datagram reaches its destination correctly, the length of the datagram will be passed along with the data to the receiver. TCP is a byte stream protocol without any (on the protocol) record boundary. 3.UDP is connected without connection. There is no need for a long-term relationship between UDP clients and servers. Most UDP implementations choose to ignore the source station suppression errors. When network congestion is caused, the destination cannot receive a large number of UDP datagrams. 4. UDP supports multicast and broadcasting.
Use nmap to scan
nmap -sU -T5 -sV --max-retries 1 192.168.0.1/24 -p 500 or
nmap -sU -T4 -sV 192.168.0.1/24
msf scan
msf5 use auxiliary/scanner/discovery/udp_probe
msf5 auxiliary(scanner/discovery/udp_probe) show options
Module options (auxiliary/scanner/discovery/udp_probe):
Name Current Setting Required Description
---- --------------- -------- -----------
CHOST no The local client address
RHOSTS yes The target address range or CIDR identifier
THREADS 1 yes The number of concurrent threads
msf5 auxiliary(scanner/discovery/udp_probe) set RHOSTS 192.168.0.1/24
RHOSTS=192.168.0.1/24
msf5 auxiliary(scanner/discovery/udp_probe) set THREADS 10
THREADS=10
msf5 auxiliary(scanner/discovery/udp_probe) run
Or execute
use auxiliary/scanner/discovery/udp_sweep
ARP Introduction:
ARP, a network transmission protocol that is extremely important in network protocol packets by parsing network layer addresses. Get a TCP/IP protocol for physical address based on IP address. When the host sends information, it broadcasts an ARP request containing the target IP address to all hosts on the network and receives a return message to determine the target's physical address.
nmap scan
nmap -sn -PR 192.168.0.1/24
Popularization of OSI seven-layer model diagram




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
