0x00 Mhn Honey Can Introduction MHN(Modern Honey Network):オープンソースハニーポット、ハニーポットの展開を簡素化し、ハニーポットデータの収集と統計を促進します。 ThreatStreamを使用して展開され、データはMongoDBに保存され、展開センサーはSnort、Kippo、Conpot、Dionaeaが侵入検知システムのインストールされています。収集された情報は、Webインターフェイスを介して表示できます。公式声明によると、現在、MHNサーバーの展開をサポートするためにテストされたシステムには、Ubuntu 14.04、Ubuntu 16.04、Centos 6.9が含まれます。
githubアドレス(https://github.com/threatstream/mh)
0x01サポートハニーポットタイプの鼻をサポートします
Suricata
dionaea
コンポット
キッポ
アムン
Glastopf
ワードポット
shaockpot
P0F
0x02mhnアーキテクチャ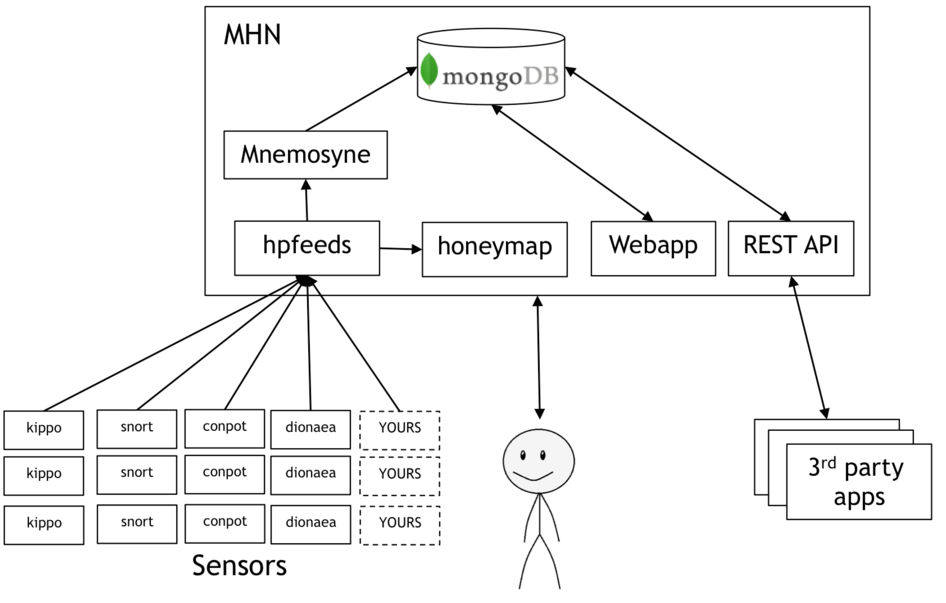
0x03 mhnのインストールと使用1.ubuntuインストールMHN管理エンド#オペレーティングシステム:ubuntu16.04システム更新と自動化スクリプトのインストール
sudo aptアップデート
sudo aptアップグレード-y
sudo apt -get install git -y
CD /OPT
sudo git clone 3https://github.com/threatstream/mhn.git
CD MHN /
sudo ./install.sh
#サーバー情報の構成、メールとパスワードは、インストール後のWebバックグラウンドパスワードです
デバッグモードで実行したいですか? y/n
Superuser Email: root@backlion.org
Superuser Password:(再び):
サーバーベースURL ['http://155.138.147.248'] :
ハネマップURL [':3000'] : http://155.138.147.248:3000
メールサーバーアドレス['localhost'] :
メールサーバーポート[25] :
メールにTLSを使用しますか? y/n n
電子メールにSSLを使用しますか? y/n
メールサーバーのユーザー名[''] :
メールサーバーパスワード[''] :
デフォルトの送信者をメールで送信[''] :
ログファイルのパス['/var/log/mhn/mhn.log'] :
Splunkと統合しますか? (y/n)n
エルクをインストールしますか? (y/n)n
#スパンクとエルクを構成して、ここで構成しないことを選択しました
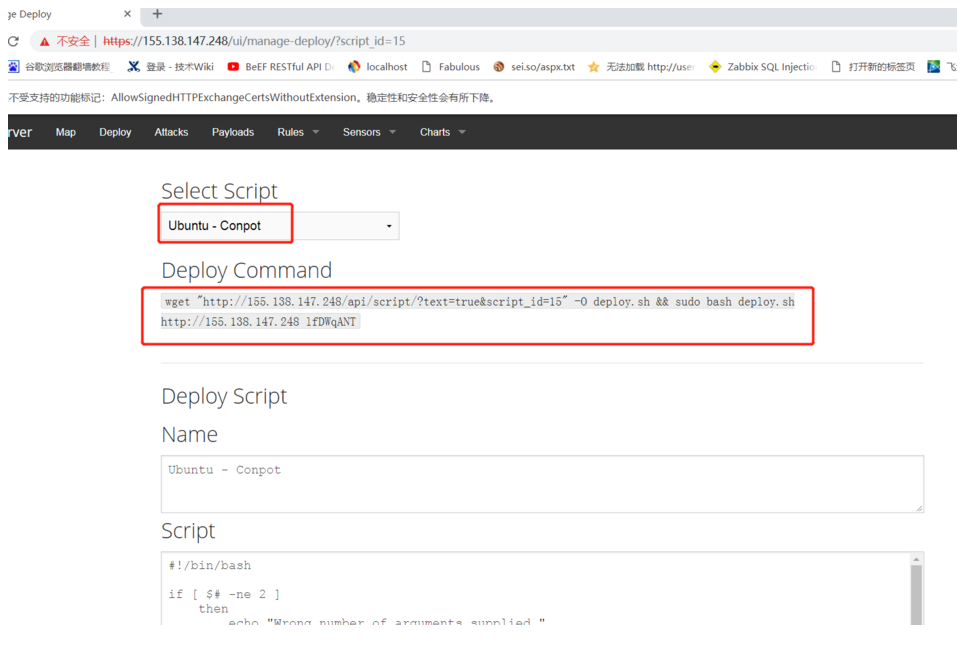
2.MHN構成2.1AGENTデプロイメントハニーポット展開オプションで、展開する必要があるハニーポットのタイプを選択し、インストールのために展開スクリプトをコピーします。
コンポットハニーポットを展開する場合は、次のスクリプト:をそのシステムで実行します
wget 'http://155.138.147.248/api/scrip/?text=truescript_id=15' -o deploy.sh sudo bash deploy.sh http://155.138.147.248 lfdwqan
2.2 SplunkおよびArcsightsplunkcd/opt/mhn/scriptsの統合/
sudo ./install_hpfeeds-logger-splunk.sh
sudo ./install_splunk_universalforwarder.sh
Tail -f /var/log/mhn/mhn-splunk.log
これにより、/var/log/mhn-splunk.logの値としてイベントを記録します。 SplunkunveralForwarderはこのログを監視する必要があります
arcsightcd/opt/mhn/scripts/
sudo ./install_hpfeeds-logger-arcsight.sh
Tail -f /var/log/mhn/mhn-arcsight.log
2.3データの禁止Mhnserverの報告は、デフォルトで分析データをAnomaliに報告します。この構成を無効にする必要がある場合は、次のコマンドを実行します。
CD MHN/スクリプト/
sudo ./disable_collector.sh
3。MHNを使用したハニーポットSSHハニーポットテストの展開#ハニーポット展開マシン:155.138.151.176
#honeypot:dionaea
wget
'http://155.138.147.248/api/script/?text=truescript_id=4' -o
deploy.sh sudo bash deploy.sh http://155.138.147.248 lfdwqant
#攻撃をクラックするためにブルートフォースを試してください
hydra -l root -p password.txt mssql: //155.138.151.176
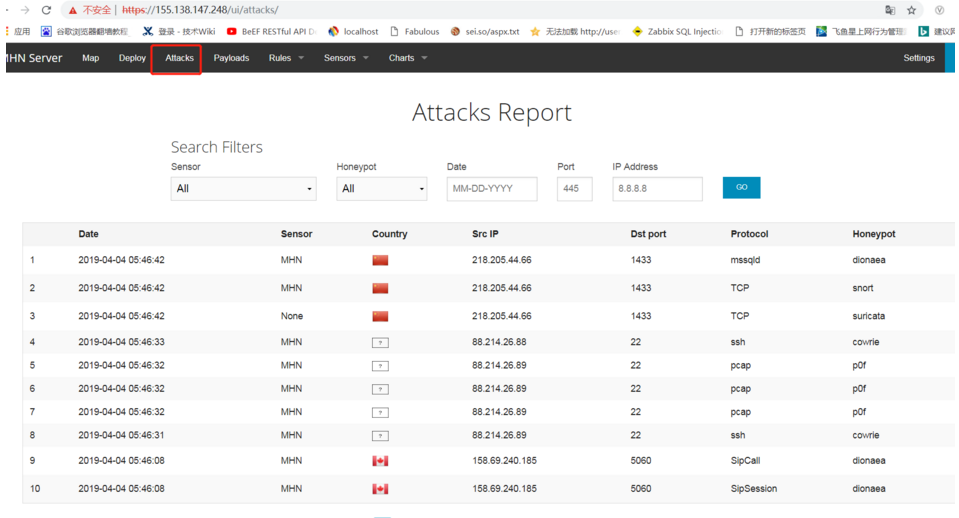
4。インターフェイス関数ディスプレイ1。以下のインターフェイスは、攻撃者のソースIPアドレス、宛先ポート、アフィリエイトプロトコル、およびハニーポットタイプの攻撃レポート情報を示しています。
2.次の図には、攻撃ペイロードレポート情報(センサー、ソースIPアドレス、宛先ポートなど)がリストされています。
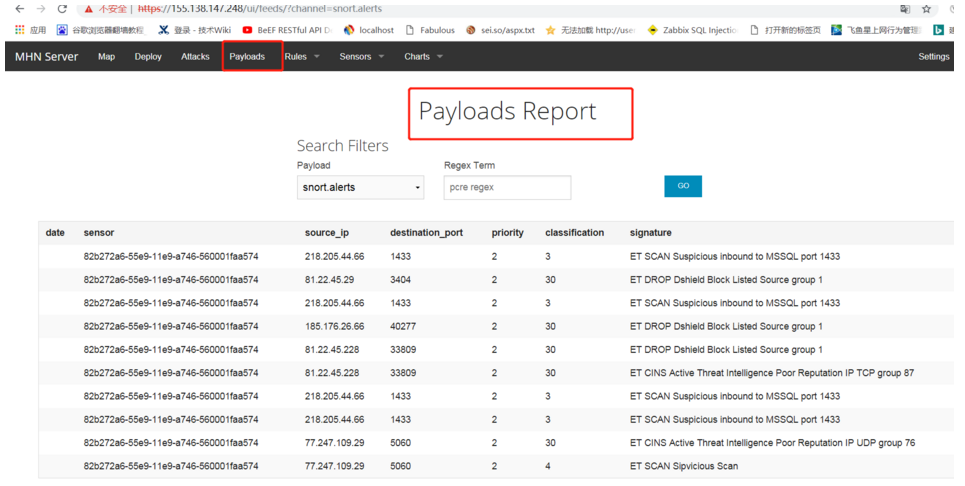
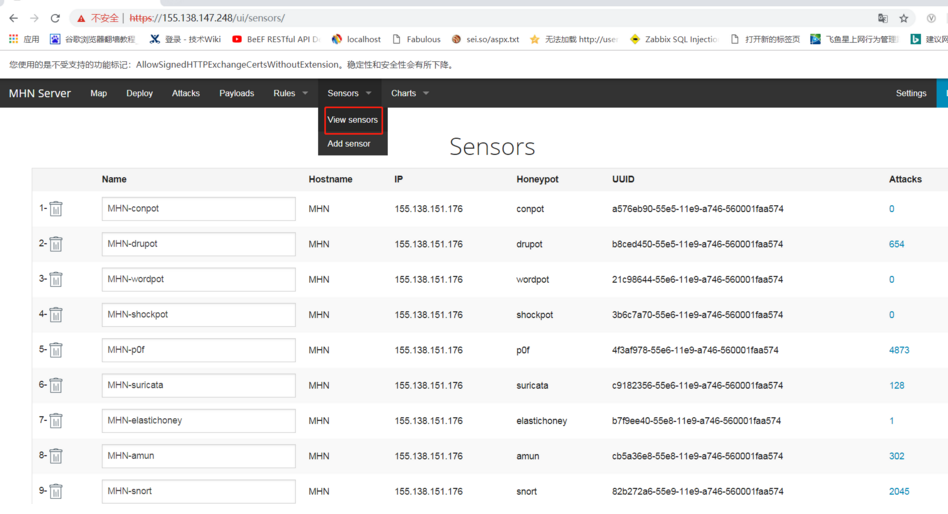
3.次の図には、インストールされているエージェントセンサーがリストされています。
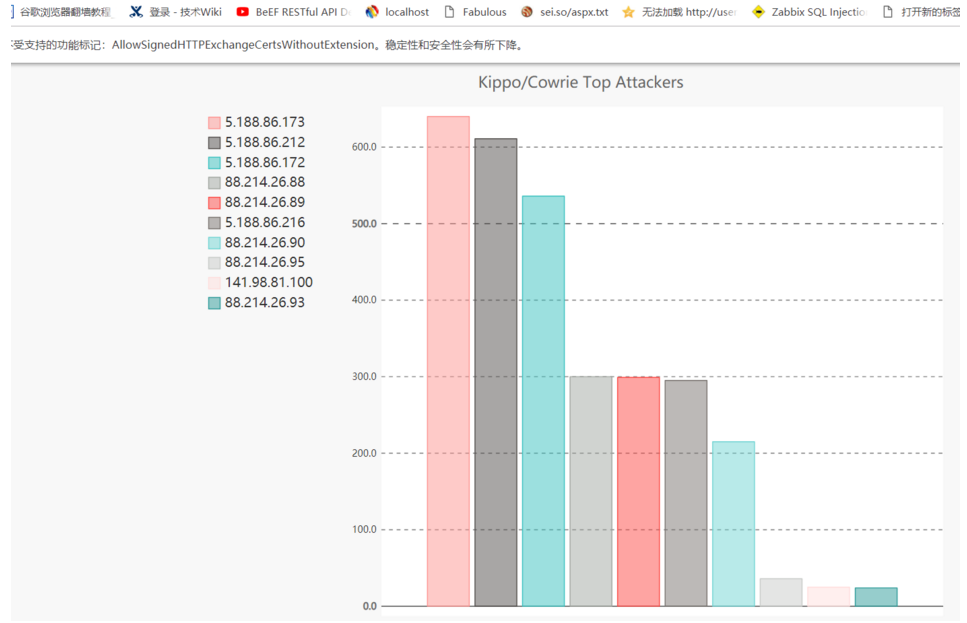
4.次の図には、それぞれ攻撃者のトップのユーザー名とパスワード辞書がリストされています。
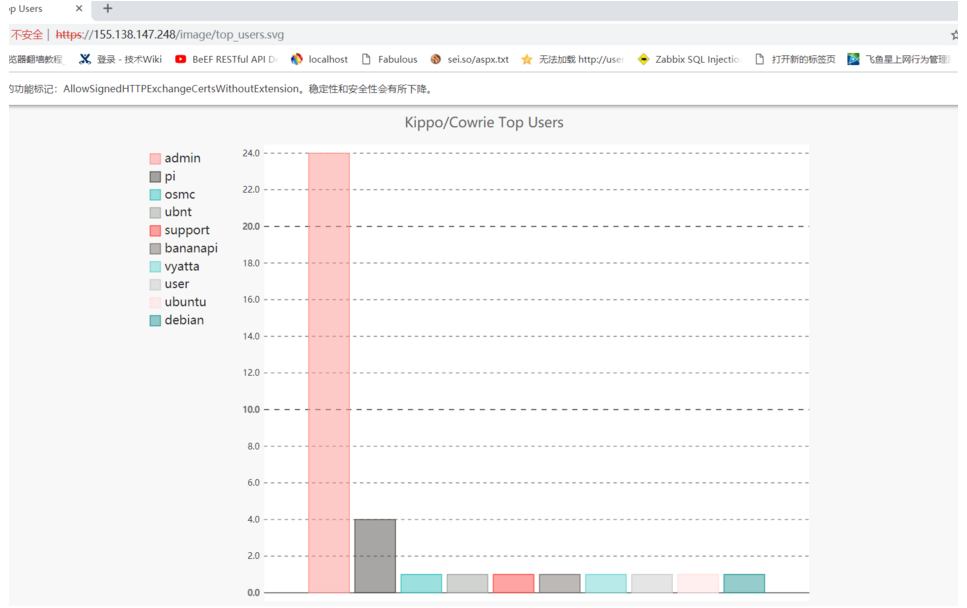
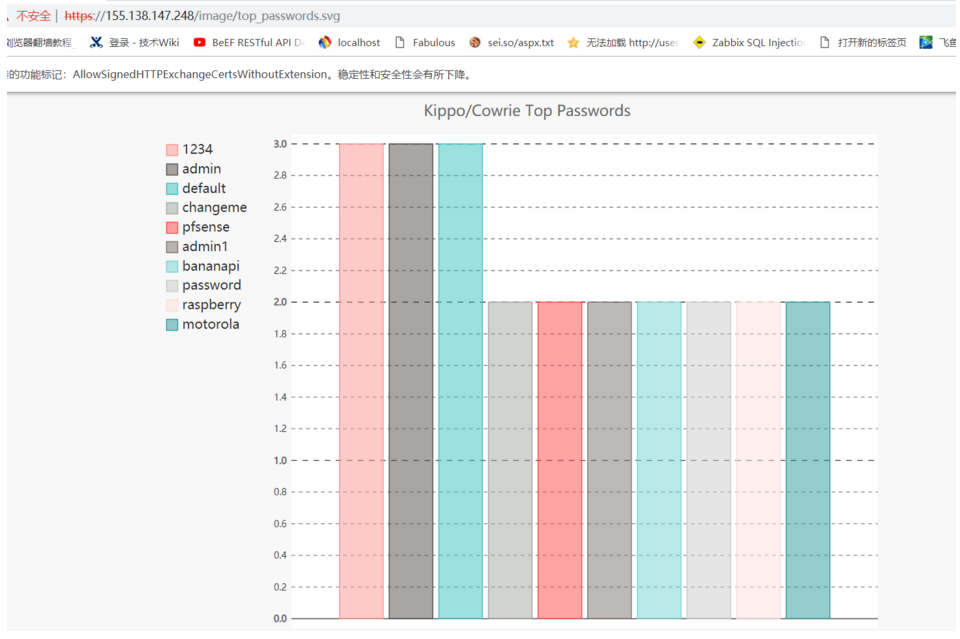
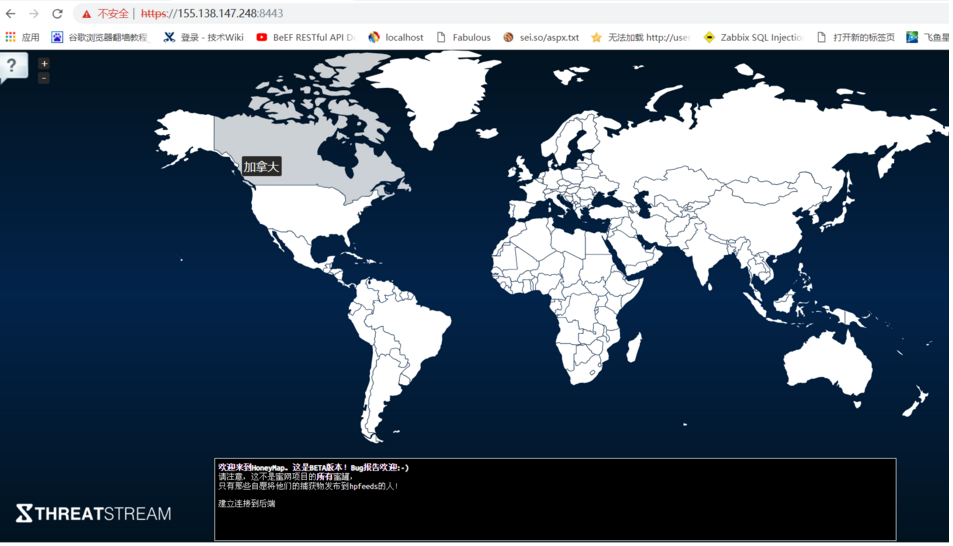
5.次の接続アドレスを開き、リアルタイムの攻撃マップ(ハネマップ)を表示します
0x05システムトラブルシューティングとセキュリティ設定1。システムを確認してくださいステータスroot@mhn:/opt/mhn/scripts#sudo /etc/init.d/nginx status #check nginx status
* nginxが実行されています
root@mhn:/opt/mhn/scripts#sudo /etc/init.d/supervisorステータス#viewスーパーバイザーステータス
実行しています
root@mhn:/opt/mhn/scripts#sudo supervisorctlステータス#viewすべてのハニーポットシステムコンポーネントの実行ステータス
Geoloc Running PID 31443、Uptime 0:00:12
PID 30826を実行しているハネマップ、アップタイム0:08:54
PID 10089を実行しているHPFeeds-Broker、Uptime 0:36:42
MHN-CELERY-BEAT RUNSING PID 29909、Uptime 0:18336041
PID 29910、アップタイム0:18:41を実行しているMhn-Celery-Worker
PID 7872を実行しているMHNコレクター、アップタイム0:18:41
PID 29911を実行しているMHN-UWSGI、アップタイム0:18:41
Mnemosyne Running PID 28173、Uptime 0:30:08
root@mhn:/opt/mhn/scripts#sudo superpisorctl alt strestartすべての#restartすべてのハニーポットシステムコマンド
通常、各サービスのステータスは次のとおりです。
Geoloc Running PID 31443、Uptime 0:00:12
PID 30826を実行しているハネマップ、アップタイム0:08:54
PID 10089を実行しているHPFeeds-Broker、Uptime 0:36:42
MHN-CELERY-BEAT RUNSING PID 29909、Uptime 0:18336041
PID 29910、アップタイム0:18:41を実行しているMhn-Celery-Worker
PID 7872を実行しているMHNコレクター、アップタイム0:18:41
PID 29911を実行しているMHN-UWSGI、アップタイム0:18:41
Mnemosyne Running PID 28173、Uptime 0:30:08
2.ハネマップのステータスは、Golangの古いバージョンを削除するための致命的なソリューションです
sudo rm -rf/usr/bin/go
sudo apt-get golang-goを削除します
sudo apt-get remove-auto remove golang-go
Golangをインストールします。 Apt-GetインストールGolangがインストールされている場合、Golangバージョンが低いため、後でエラーが報告されるため、コンパイルされたパッケージを直接ダウンロードします。
WGET https://STORAGE.GOOGLEAPIS.COM/GOLANG/GO1.9.LINUX-AMD64.TAR.GZ
減圧してから、次の構成を実行します
sudo tar -xzf go1.9.linux -amd64.tar.gz -c/usr //local///パッケージ名はあなたと同じように変更する必要があることに注意してください
環境変数をインポートします:
goroot=/usr/local/goをエクスポートします
goarch=amd64をエクスポートします
Goos=Linuxをエクスポートします
export gobin=$ goroot/bin/
export gotools=$ goroot/pkg/tool/
エクスポートパス=$ gobin: $ gotools: $パス
依存関係プラグインネットをインストールし、すべてのハニーポットシステムコンポーネントを再起動します
CD/OPT/HONEYMAP/SERVER
gopath=/opt/honeymap/serverをエクスポートします
mkdir -p $ gopath/src/golang.org/x/
cd $ gopath/src/golang.org/x/
git clone https://github.com/golang/net.git net
ネットをインストールします
sudo supervisorctlはすべてを再起動します
3. MHN-CELERY-WOKERの状態は致命的なソリューションCD/VAR/LOG/MHN/
sudo chmod 777 mhn.log
sudo supervisorctlはMhn-celery-workerを開始します
うまくいかない場合
CD/var/log/mhn/#viewセロリワーカーエラーログ
Tail -f Mhn-celery-worker.err
プロンプトされた特定のエラーは次のとおりです
worker.err supervisor:は/root/mhn/server: eacces supervisor:子どものプロセスが生まれなかった)
ルートとディレクトリの権限を変更します
CHMOD 777 -R /root#アクセス許可を変更します
4.マニュアルパスワードリセットメールベースのパスワードリセットがあなたに適していない場合、これは別の方法です。
#CD/OPT/MHN/SERVER/SERVER//
#aptインストールsqlite3
#sqlite3 mhn.db
SQLiteバージョン3.7.9 2011-11-01 00:52:41
指示のために「.help」を入力します
';'で終了したSQLステートメントを入力します
sqlite select * fromユーザー。
1 | username@site.com | sklfdjhkasdlfhklsadhfklasdhfkldsahklsd | 1 |
sqlite.quit
$ cd/opt/mhn/server/
$ source env/bin/activate
$ CDサーバー
$ python manual_password_reset.py
メールアドレス: your_user@your_site.comを入力してください
新しいPassword:を入力します
新しいパスワードを入力してください(もう一度):
ユーザーが見つかった、パスワードの更新
5。ネットワークトラブルシューティング$ sudo netstat -luntp#ネットワークポートの開口部の状況を確認する
アクティブなインターネット接続(サーバーのみ)
proto recv-q send-qローカルアドレス外国住所状態pid/プログラム名
TCP 0 0 0.0.0.0:22 0.0.0.0:* 561/sshdを聞いてください
TCP6 0 0 :336021 :3360:* 3763/dionaeaを聞いてください
TCP6 0 0 :336022 :3360:*聞いてください561/sshd
TCP6 0 0 :1433 :* 3763/dionaeaを聞いてください
TCP6 0 0 :443 :* 3763/dionaeaを聞いてください
TCP6 0 0 :3360445 :* 3763/dionaeaを聞いてください
TCP6 0 0 :33605060 :* 3763/dionaeaを聞いてください
TCP6 0 0 :33605061 :* 3763/dionaeaを聞いてください
TCP6 0 0 :135 :* 3763/dionaeaを聞いてください
TCP6 0 0 :33603306 :* 3763/dionaeaを聞いてください
TCP6 0 0 :336042 :3360:* 3763/dionaeaを聞いてください
TCP6 0 0 :336080 :* 3763/dionaeaを聞いてください
UDP 0 0 0.0.0.0:68 0.0.0.0:* 464/dhclient3
UDP 0 0 0.0.0.0:40077 0.0.0.0:* 3763/dionaea
UDP6 0 0 :33605060 :3360:* 3763/dionaea
UDP6 0 0 :336069 :3360:* 3763/dionaea
$ sudo iptables -l #viewファイアウォールルールステータス
チェーン入力(ポリシーの受け入れ)
ターゲットProTソースの宛先
チェーンフォワード(ポリシーが受け入れる)
ターゲットProTソースの宛先
チェーン出力(ポリシーが受け入れる)
ターゲットProTソースの宛先
$ sudo tcpdump -nnnn tcpポート10000 #listen tcp 10000データ通信情報
tcpdump: verbose出力が抑制され、完全なプロトコルデコードに-vまたは-vvを使用します
ETH0、Link-Type EN10MB(イーサネット)、キャプチャサイズ65535バイトでリスニング
16336046:14.009646 IP 1.2.3.4.42873 5.6.6.8.10000: Flags [P.]、Seq 1180349317:1180349611、ACK 2474834734、Win 913、NOP、NOP、NOP、NOP、TS 169636000]、長さ




.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
